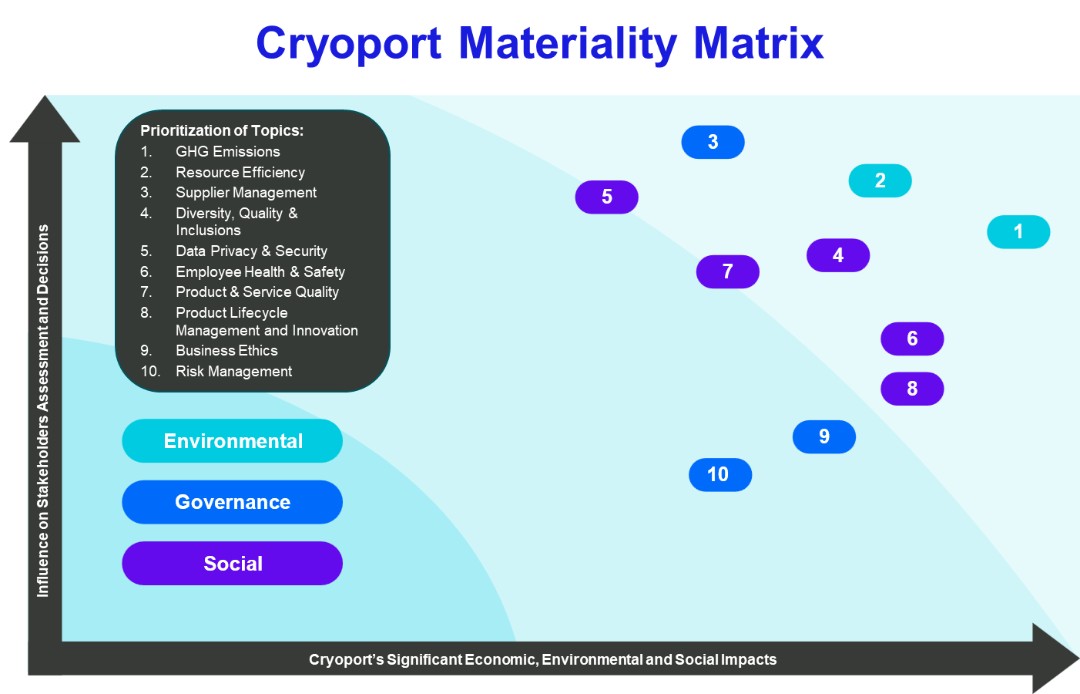
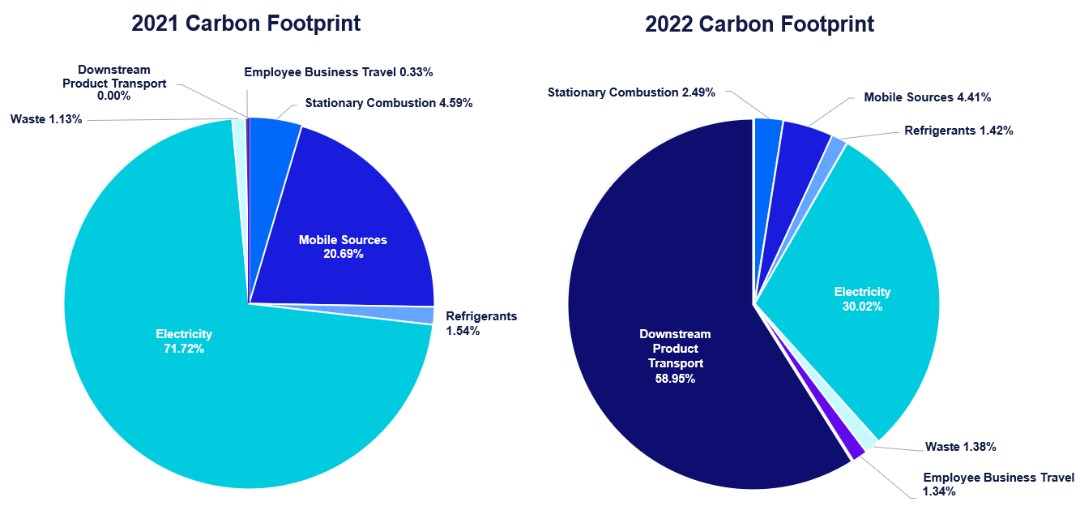
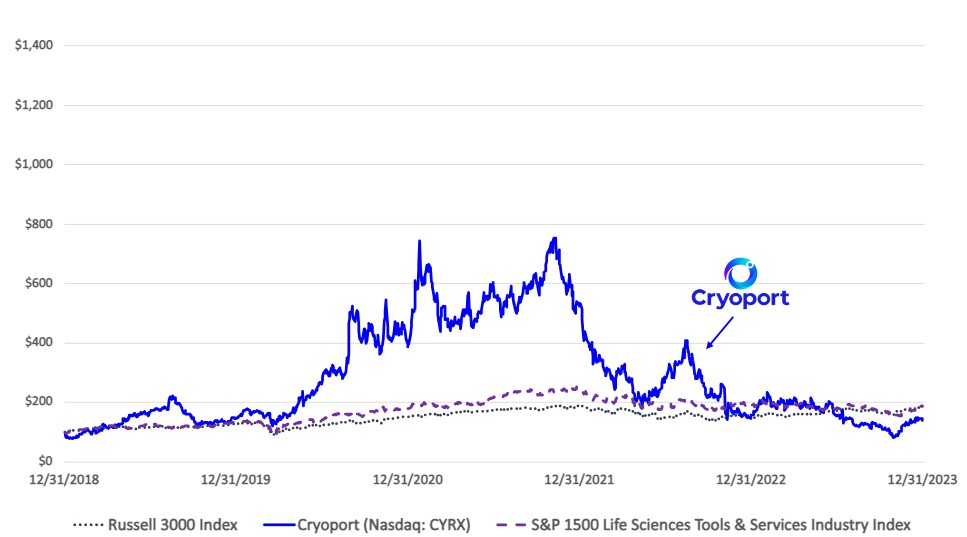
Risks Related to Our Technology and Intellectual Property
We rely upon certain critical information systems, including our Cryoportal® software platform, for the operation of our business; the failure of any critical information system could adversely impact our reputation and future revenues, and we may be required to increase our spending on data and system security.
We rely upon certain critical information systems, including our Cryoportal® software platform which is used by our customers and business partners to automate the entry of orders, prepare customs documentation and facilitate status and location monitoring of shipped orders while in transit. In addition, the provision of services to our customers and the operation of our networks and systems involve the storage and transmission of significant amounts of proprietary information and sensitive or confidential data, including personal information of customers, employees and others. Our technology infrastructure and critical information systems are subject to damage or interruption from a number of potential sources, including unauthorized intrusions, cyberattacks, software viruses or other malware, natural disasters, power failures, employee error or malfeasances and other events. Despite our best efforts, no cybersecurity or emergency recovery process is failsafe, and if our safeguards fail or our technology infrastructure or critical information systems are compromised, the safety and efficiency of our operations could be materially harmed, our reputation could suffer, and we could face additional costs, liabilities, costly legal challenges.
Cyberattacks, data incidents and breaches in the security of our information systems and networks and of the electronic and confidential information in our possession could materially adversely impact our business, financial condition and results of operations, in addition to our reputation and relationships with our employees, customers, suppliers and business partners.
As part of our normal business activities, we collect and store or have access to certain proprietary confidential, and personal information, including information about our employees, customers, suppliers and business partners, which may be entitled to protection under a number of regulatory regimes. The protection and security of our network systems and our own information, as well as information relating to our employees, customers, suppliers, business partners and others, is vitally important to us. Any failure of us to maintain the security of our network systems and the proprietary, confidential, and personal data in our possession, including via the penetration of our network security and the misappropriation of proprietary, confidential and personal information, could result in costly investigations and remediation, business disruption, damage to our reputation, financial obligations to third parties, fines, penalties, regulatory proceedings and private litigation with potentially large costs, and also result in deterioration in our employees’, customers’, suppliers’ and business partners’ confidence in us and other competitive disadvantages, and thus could have a material adverse effect on our business, financial condition and results of operations.
The frequency, intensity, and sophistication of cyberattacks and data security incidents has significantly increased in recent years and is constant. As with many other businesses, we are continually subject to cyberattacks and the risk of data security incidents. Due to the increased risk of these types of attacks and incidents, we have implemented information technology and data security tools, measures, and processes designed to protect our networks systems, services, and the personal, confidential or proprietary information in our possession, and to ensure an effective response to any cyberattack or data security incident. We also have privacy and data security policies in place that are designed to detect, prevent, and/or mitigate cyberattacks and data security incidents. Whether or not these policies, tools, and measures are ultimately successful, the expenditures could have an adverse impact on our financial condition and results of operations, and divert management’s attention from pursuing our strategic objectives. As newer technologies evolve, we could be exposed to increased risks from cyberattacks, data security events, and data breaches, including those from human error, negligence or mismanagement or from illegal or fraudulent acts.
Although we take the security of our network systems and information seriously, there can be no assurance that the security measures we employ will effectively prevent unauthorized persons from obtaining unauthorized access to our systems and information due to the evolving nature and intensity of cyberattacks and threats to data security, in light of new and sophisticated tools and methods used by criminals and cyberterrorists to penetrate and compromise systems, including computer viruses, malware, ransomware, phishing, misrepresentation, social engineering and forgery, which make it increasingly challenging to anticipate, harder to detect, and more difficult to adequately mitigate these risks. While we have cyber security insurance, we may incur significant costs in the event of a successful cyber incident against us or in responding to and recovering from a cyber incident that are not covered by, or exceed the limits of, such insurance. Additionally, the cost and operational consequences of implementing, maintaining and enhancing further data or system protection measures could increase significantly to overcome increasingly intense, complex and sophisticated global cyber threats.