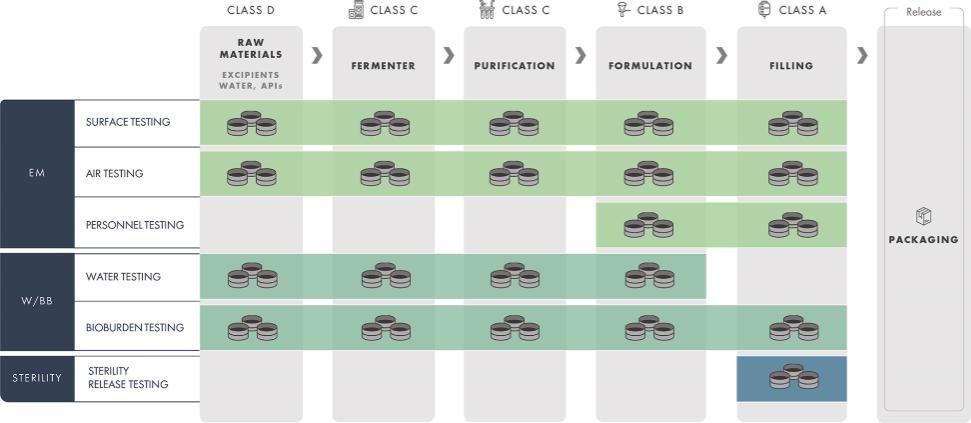
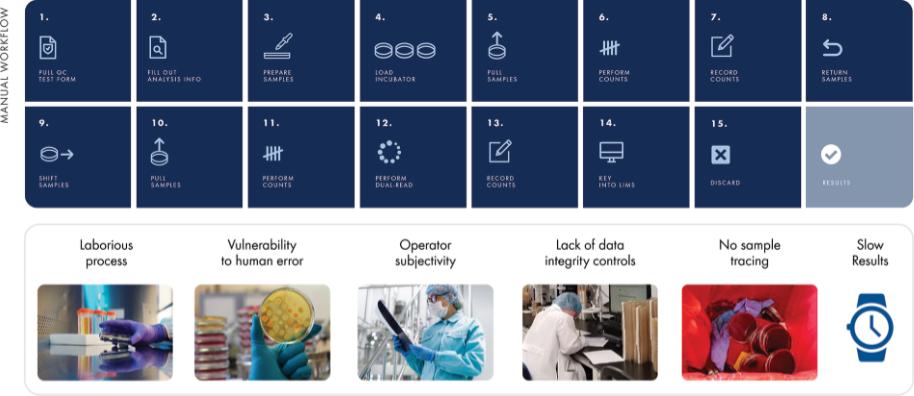
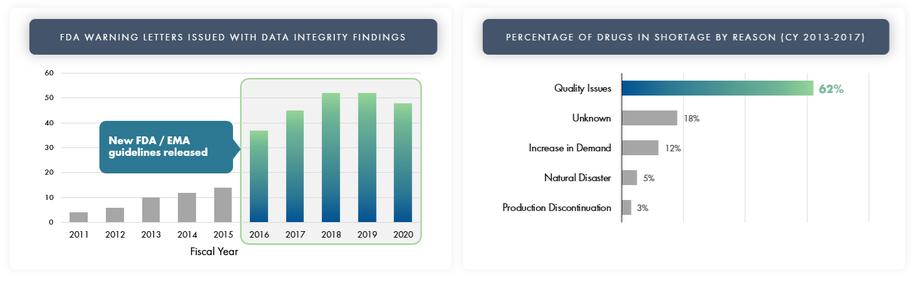
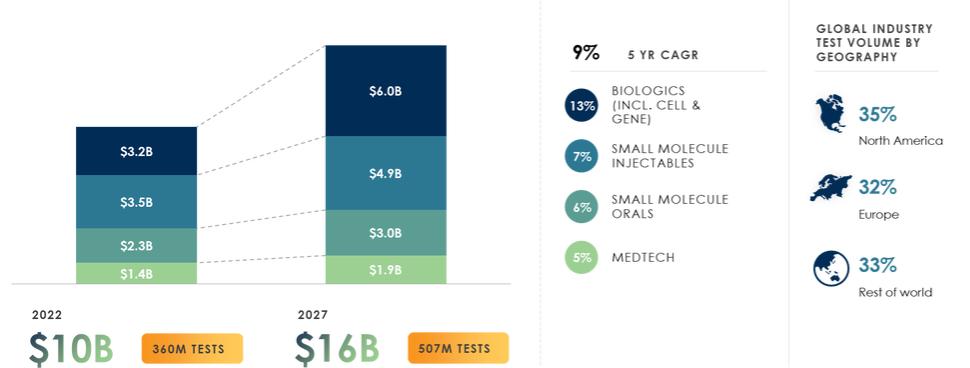
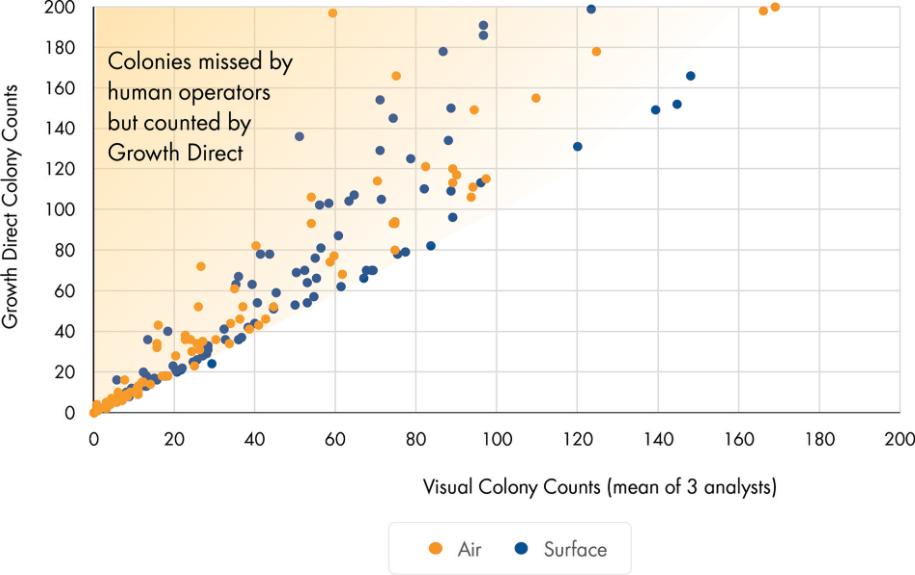
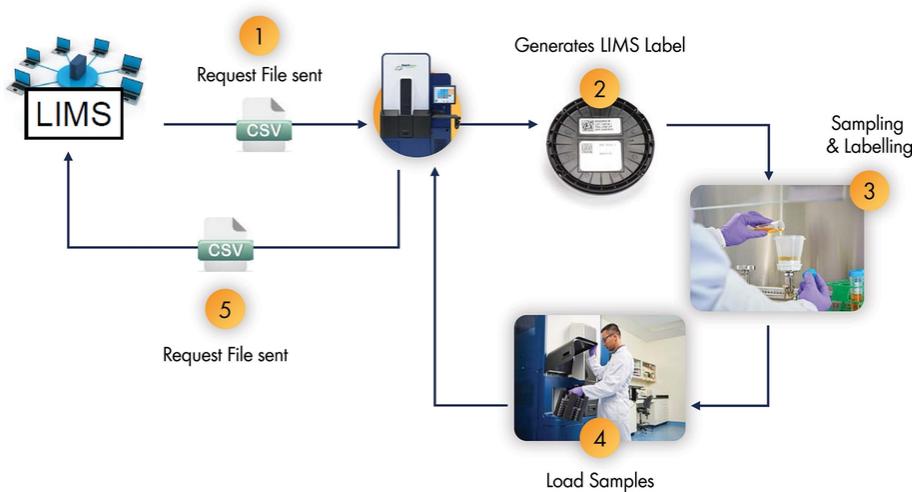
use or disclosure, our information technology and infrastructure may still be vulnerable to, and we have in the past experienced, attacks by hackers or viruses or breaches due to employee error, malfeasance or other malicious or inadvertent disruptions. Further, attacks upon information technology systems are increasing in their frequency, levels of persistence, sophistication and intensity, and are being conducted by sophisticated and organized groups and individuals with a wide range of motives and expertise. As a result of the COVID-19 pandemic, we may also face increased cybersecurity risks due to our reliance on internet technology and the number of our employees who are working remotely, which may create additional opportunities for cybercriminals to exploit vulnerabilities. Furthermore, because the techniques used to obtain unauthorized access to, or to sabotage, systems change frequently and often are not recognized until launched against a target, we may be unable to anticipate these techniques or implement adequate preventative measures. While we have measures in place to detect and mitigate security breaches, they are not failproof, so we may also experience security breaches that may remain undetected for an extended period. Any such breach or interruption could compromise our networks and the information stored there could be accessed or frozen by unauthorized parties, publicly disclosed, lost or stolen. Any such access, breach, or other loss of information could result in legal claims or proceedings, including for breaches of confidential information obligations with contractual counterparties, and liability under federal or state laws that protect the privacy of personal information, and regulatory penalties. Notice of breaches may be required to affected individuals, customers, or other state, federal or foreign regulators, and for extensive breaches, notice may need to be made to the media or State Attorneys General. Such a notice could harm our reputation and our ability to compete. Although we have implemented security measures to prevent unauthorized access, such data is currently accessible through multiple channels, and there is no guarantee we can protect our data from breach. Unauthorized access, loss or dissemination could also disrupt or halt our operations and damage our reputation, any of which could adversely affect our business.
We are currently subject to, and may in the future become subject to additional, U.S., state, federal, and foreign laws and regulations imposing obligations on how we collect, store and process personal information. Our actual or perceived failure to comply with such obligations could harm our business. Ensuring compliance with such laws could also impair our efforts to maintain and expand our customer base, and thereby decrease our revenue.
We are, and may increasingly become, subject to various laws and regulations, as well as contractual obligations, relating to data privacy and security in the jurisdictions in which we operate. The regulatory environment related to data privacy and security is increasingly rigorous, with new and constantly changing requirements applicable to our business, and enforcement practices are likely to remain uncertain for the foreseeable future. These laws and regulations may be interpreted and applied differently over time and from jurisdiction to jurisdiction, and it is possible that they will be interpreted and applied in ways that may have a material adverse effect on our business, financial condition, results of operations and prospects.
In the United States, various federal and state regulators, including governmental agencies like the Federal Trade Commission, have adopted, or are considering adopting, laws and regulations concerning personal information and data security. Certain state laws may be more stringent or broader in scope, or offer greater individual rights, with respect to personal information than federal, international or other state laws, and such laws may differ from each other, all of which may complicate compliance efforts. For example, the California Consumer Privacy Act, or CCPA, which increases privacy rights for California residents and imposes obligations on companies that process their personal information, came into effect on January 1, 2020. Among other things, the CCPA requires covered companies to provide new disclosures to California consumers and provide such consumers new data protection and privacy rights, including the ability to opt-out of sales of personal information. The CCPA provides for civil penalties for violations, as well as a private right of action for certain data breaches that result in the loss of personal information. This private right of action may increase the likelihood of, and risks associated with, data breach litigation. In 2020, the California residents voted the California Privacy Rights Act (the “CPRA”) into law. The CPRA will impose additional data protection obligations on covered businesses, including additional consumer rights processes, limitations on data uses, new audit requirements for higher risk data, and opt outs for certain uses of sensitive data. The CPRA also created a new California data protection agency authorized to issue substantive regulations and could result in increased privacy and information security enforcement. The majority of the CPRA provisions will go into effect on January 1, 2023, and additional compliance investment and potential business process changes may be required. Similar laws have been proposed, and likely will be proposed, in other states and at the federal level, and if passed, such laws may have potentially conflicting requirements that would make compliance challenging.