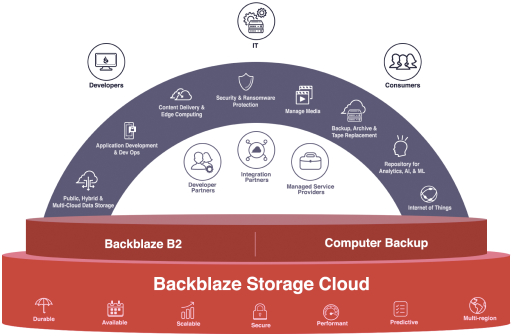
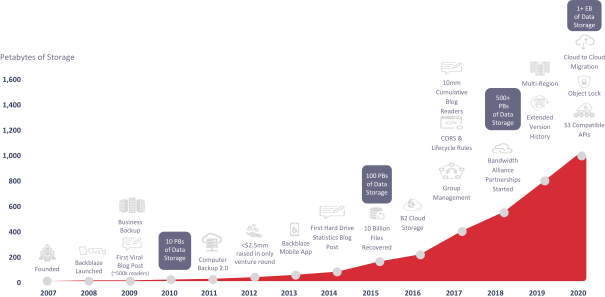
and partners. Our customers rely on our platform to store and access their data, including financial records, business information, personal information, documents, media, and other important content. There are various reasons that our platform, or the systems that are used to access or support our platform, could experience a disruption in service, some of which are entirely outside of our control. For example, our facilities as well as the data centers that we use are vulnerable to damage or interruption from human error, intentional bad acts, earthquakes, floods, fires, war, terrorist attacks, power losses, hardware failures, systems failures, telecommunications failures, and similar events, any of which could disrupt our service, destroy user content, or prevent us from being able to continuously back up or record changes in our users’ content. If any of these events occur, customer data could be lost and it may take a significant period of time to achieve full resumption of our cloud services. Our disaster recovery planning cannot account for all eventualities and even if we anticipate an incident, our disaster recovery plans may not be sufficient to timely and effectively address the issue. Moreover, our platform and technical infrastructure may not be adequately designed with sufficient reliability and redundancy to avoid delays or outages that could be harmful to our business. If our platform is unavailable when users attempt to access it, or if it does not load as quickly as they expect, or if data is lost, users may not use our platform as often in the future, or at all.
If we are unable to maintain our brand and reputation, our business, results of operations, and financial condition may be adversely affected.
The successful promotion of our brand and our ability to maintain our reputation will depend on a number of factors, including our performance and the reliability of our cloud services; our advertising and marketing efforts, including our blog and social media presence, which have been important to building and maintaining our brand and reputation; our ability to continue to develop high-quality features and cloud services; and our ability to successfully differentiate our cloud services from competitive products and services. Our brand promotion activities may not be successful or yield increased revenue.
The promotion of our brand may require us to make substantial expenditures, particularly as our markets become more competitive and we expand into new markets or offer additional features. Expenditures intended to maintain and enhance our brand may not be cost-effective or effective at all. If we do not successfully maintain and enhance our brand, we may have reduced pricing power relative to our competitors, we could lose customers, we could fail to attract potential new customers or retain our existing customers, or our blog and thought leadership in our industry may decline in popularity, all of which could materially and adversely affect our business.
If our information technology systems, including the data of our customers stored in our systems, are breached or subject to cybersecurity attacks, our reputation and business may be harmed.
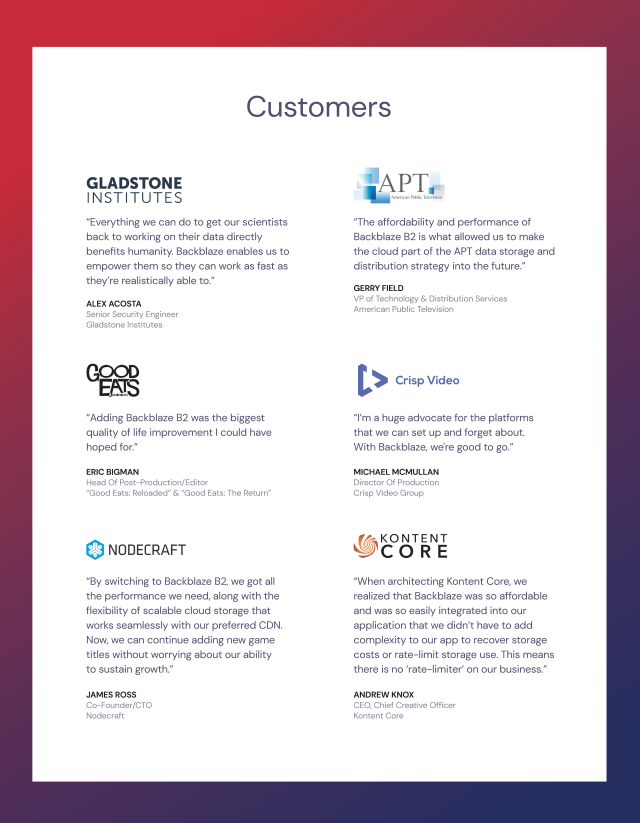
Our customers rely on our solutions to store their files, which may include confidential or personally identifiable information, critical business information, photos, and other meaningful content. To manage and maintain such data, we are highly dependent on internal and external information technology systems and infrastructure, including the internet, to securely process, transmit, and store critical information. Although we take measures to protect sensitive information from unauthorized access or disclosure, third parties may be able to circumvent our security by deploying viruses, worms, and other malicious software programs that are designed to attack or attempt to infiltrate our systems and networks, including distributed denial of service (DDoS) attacks that can undermine the availability and performance of our systems and cloud services, or phishing attacks that can be used to fraudulently steal data. Moreover, cybersecurity attacks evolve rapidly and may utilize new methods not recognized. We may be unable to successfully identify, stop, or resolve such attacks, or implement adequate preventative measures. In addition, employee or consultant error, malfeasance, or other errors in the storage, use, or transmission of customer data could result in a breach. For example, in late March 2021, it was discovered that a Backblaze marketing campaign leveraging the Facebook ad network, which had been launched two weeks earlier, had been incorrectly configured to run on all Backblaze platform pages instead of only the Backblaze marketing pages as intended. Once we became aware of the issue, it was promptly resolved. Although we believe that less than 2% of Backblaze customers may have been affected, and no actual customer files, file contents, or user account information were shared at any time, certain file metadata may have been inadvertently
20