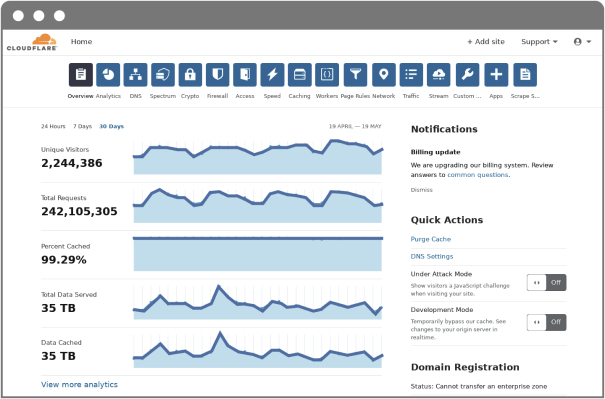
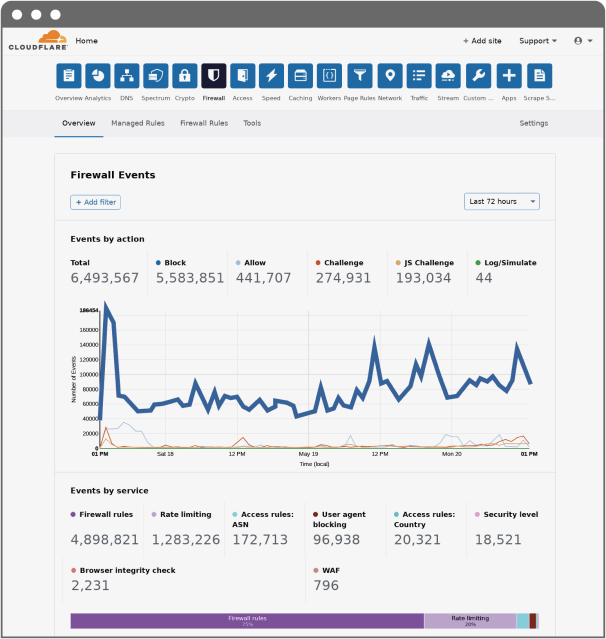
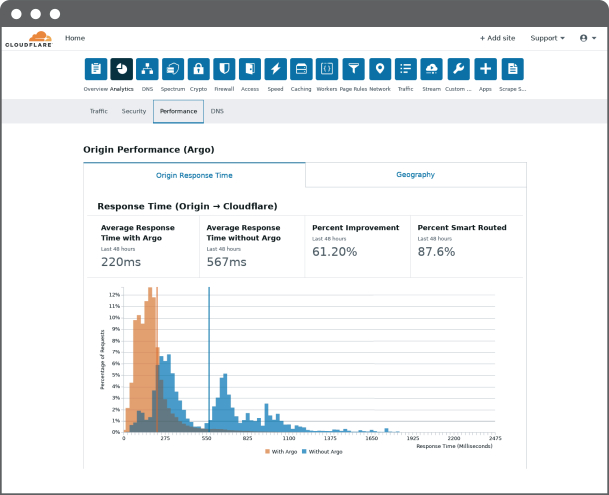
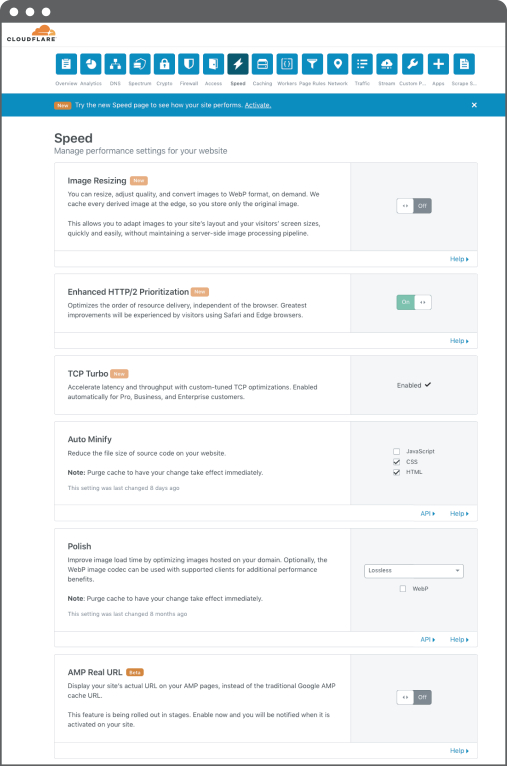
which could have an adverse effect on our business or reputation. These cybersecurity risks pose a particularly significant risk to a business like ours that is focused on providing highly secure products to customers.
Unauthorized access to, other security breaches of, or security incidents affecting, systems, networks, and data used in our business, including those of our vendors, contractors, or those with which we have strategic relationships, even if not resulting in an actual or perceived breach of our customers’ networks, systems, or data, could result in the loss, compromise or corruption of data, loss of business, reputational damage adversely affecting customer or investor confidence, regulatory investigations and orders, litigation, indemnity obligations, damages for contract breach, penalties for violation of applicable laws or regulations, significant costs for remediation, and other liabilities.
Additionally, in the absence of malicious actions, our platform and products may experience errors, failures, vulnerabilities, or bugs that cause our products not to perform as intended. For example, from time to time we are subject to “route leaks” that involve the accidental or, less commonly, illegitimate advertisement of prefixes, or blocks of IP addresses, which propagate across networks such as ours and can lead to incorrect routing of traffic across our network, taking traffic offline, or in extreme cases, potential interception of customers’ traffic by attackers. In June 2019, a route leak spread by a major telecommunications services provider caused significant disruption to our traffic and that of many other providers. Although events like this are outside our control, they could materially harm our reputation and diminish the confidence of our current and potential customers in our platform and products. In addition, deployment of our platform and products into other computing environments may expose these errors, failures, vulnerabilities, or bugs in our products. Any such errors, failures, vulnerabilities, or bugs may not be found until after they are deployed to our customers and may create the perception that our platform and products are insecure, underperforming, or unreliable. We also provide frequent updates and fundamental enhancements to our platform and products, which increase the possibility of errors. Our quality assurance procedures and efforts to report, track, and monitor issues with our network may not be sufficient to ensure we detect any such defects in a timely manner. For example, in February 2017, a bug in our software code that processes computer information requests was identified. Instead of the requested data, in certain circumstances this bug, which became known as “Cloudbleed,” caused our servers to output data that was not requested. The erroneous data output by our system included, but was not limited to, a portion of our customers’ secure data. There can be no assurance that our software code is or will remain free from actual or perceived errors, failures, vulnerabilities, or bugs, or that we will accurately route or process all requests and traffic on our network. Given the trillions of Internet requests that route through our network on a monthly basis and the large array of Internet properties (e.g., domains, websites, application programming interfaces (APIs), and mobile applications) we service, the impact of any such error, failure, vulnerability, or bug can be large in terms of absolute numbers of affected requests and customers.
Problems with our network or systems, or those of our vendors, contractors, or those with which we have strategic relationships, could result in actual or perceived breaches of our or our customers’ networks and systems or data. Actual or perceived breaches or other security incidents from these or other causes could lead to claims and litigation, indemnity obligations, regulatory audits, proceedings, and investigations and significant legal fees, significant costs for remediation, the expenditure of significant financial resources in efforts to analyze, correct, eliminate, remediate, or work around errors or defects, to address and eliminate vulnerabilities, and to address any applicable legal or contractual obligations relating to any actual or perceived security breach. They could damage our relationships with our existing customers and have a negative impact on our ability to attract and retain new customers. Because our business is focused on providing secure and high performing network services to our customers, we believe that our products and the networks and systems we use in our business could be targets for hackers and others, and that an actual or perceived breach of, or security incident affecting, our networks, systems, or data, could be especially detrimental to our reputation,
18

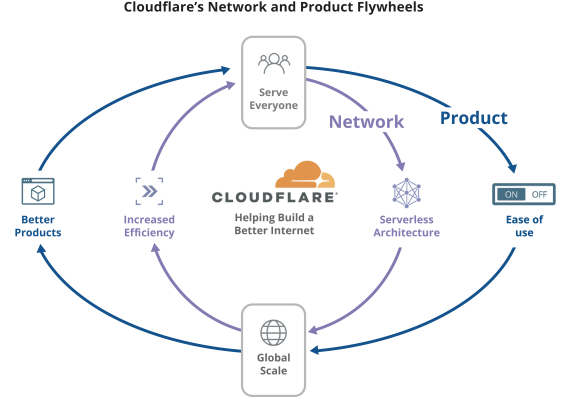
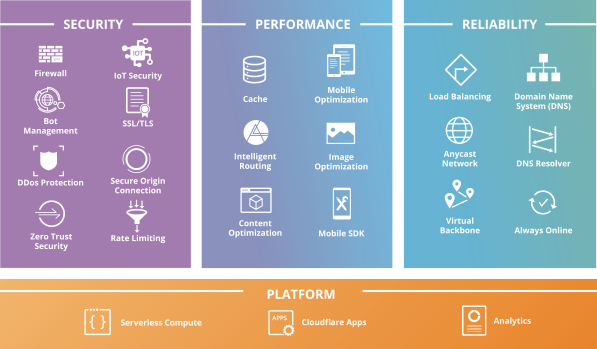 Our Products SECURITY Firewall Lot Security Bot Management SSL/TLS DDos Protection Secure Origin Connection Zero Trust Security Rate Limiting PERFORMANCE Cache Mobile Optimization Intelligent Routing Image Optimization Content Optimization Mobile SDK RELIABILITY LOAD Balancing Domain Name System (DNS) Anycast Network DNS Resolver Virtual Backbone Always Online PLATFORM Serverless Compute Cloudfare Apps Analytics
Our Products SECURITY Firewall Lot Security Bot Management SSL/TLS DDos Protection Secure Origin Connection Zero Trust Security Rate Limiting PERFORMANCE Cache Mobile Optimization Intelligent Routing Image Optimization Content Optimization Mobile SDK RELIABILITY LOAD Balancing Domain Name System (DNS) Anycast Network DNS Resolver Virtual Backbone Always Online PLATFORM Serverless Compute Cloudfare Apps Analytics