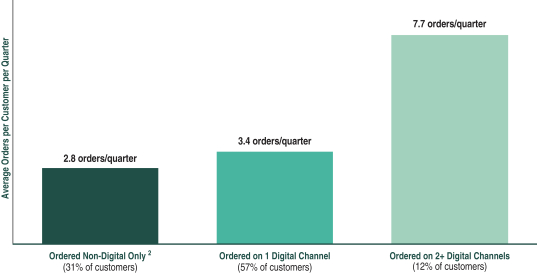
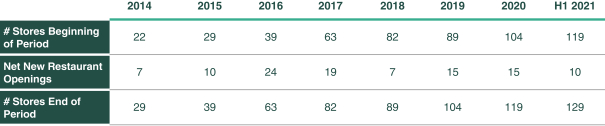
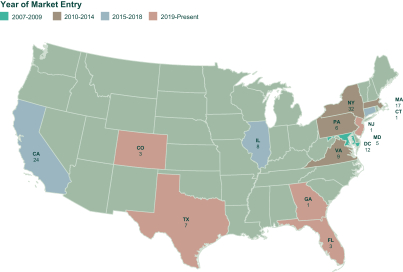
additional costs could include exposure (for prior and future periods) under federal, state, and local tax laws, and workers’ compensation, unemployment benefits, labor, and employment laws, as well as potential liability for penalties and interest. Additionally, in the event a courier that contracts with SG Logistics commits a serious crime in connection with providing services on the SG Logistics platform, we could potentially be responsible for any losses as a result of such incident, and such incident could have a material adverse impact on our brand.
Risks Related to Our Intellectual Property and Information Technology
If we experience a serious cybersecurity incident, or the confidentiality, integrity, or availability of our information technology, software, services, communications, or data is compromised, our platform may be perceived as not being secure, our reputation may be harmed, demand for our products and services may be reduced, and we may incur significant liabilities.
Operating our business and platform involves the collection, use, storage, and transmission of sensitive, proprietary, and confidential information, including personal information of customers, personnel, business contacts, and others, and our sensitive, proprietary and confidential business information. For example, we collect certain customers’ home and/or business addresses for processing delivery orders, mobile phone numbers from users of our platform, and personal information from our personnel, including in the administration of our benefit plans. Cybersecurity incidents compromising the confidentiality, integrity, and availability of this information or our systems could result from cyber attacks, software bugs and vulnerabilities, viruses, supply chain attacks and vulnerabilities through our third-party partners, credential stuffing, efforts by individuals or groups of hackers and sophisticated organizations, including state-sponsored organizations, errors or malfeasance of our personnel, and security vulnerabilities in the software or systems on which we rely. Such incidents have occurred in the past, and may occur in the future, resulting in unauthorized, unlawful, or inappropriate access to, inability to access, disclosure of, or loss of the sensitive, proprietary and confidential information that we handle. In addition, we have experienced an increase in credential stuffing activity in which malicious third parties try to access an online service by using credentials compromised in cybersecurity incidents suffered by different services. We have security measures in place to mitigate our risk to these vulnerabilities, but these measures may not be adequate to ensure that our operations are not disrupted or that security incidents do not occur. Risks relating to security incidents are likely to increase as we continue to grow and collect, process, store, and transmit increasingly large amounts of data.
We also rely on a number of third parties to support and operate our critical business systems and process confidential and personal information, such as LevelUp, our account management provider, and the payment processors that process customer credit card payments. These third parties may not have adequate security measures and could experience a security incident that compromises the confidentiality, integrity, or availability of the systems they operate for us or the information they process on our behalf. Moreover, the risk of circumvention of our security measures or those of our third parties on whom we rely has been heightened by advances in computer and software capabilities and the increasing sophistication of actors who employ complex techniques, including, without limitation, “phishing” or social engineering incidents, ransomware, extortion, account takeover attacks, denial or degradation of service attacks, and malware. Cybercrime and hacking techniques are constantly evolving, and we or third parties who we work with may be unable to anticipate attempted cybersecurity incidents, react in a timely manner, or implement adequate preventative measures, particularly given increasing use of hacking techniques designed to circumvent controls, avoid detection, and remove or obfuscate forensic artifacts.
Because of the prominence of our brand, we believe that we are an attractive target for cyberattacks. We have taken measures designed to detect and prevent security incidents, and to protect the confidentiality, integrity, and availability of our systems and the sensitive, proprietary, and
46