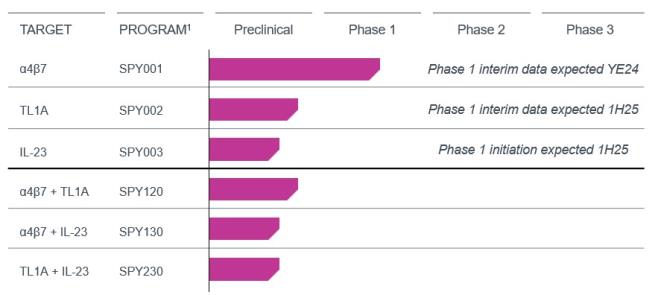
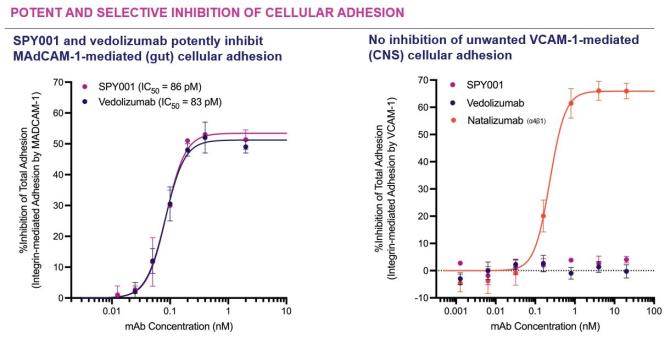
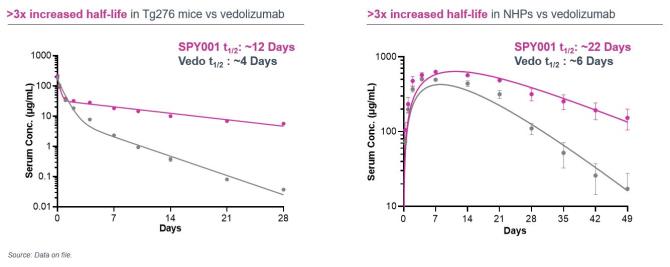
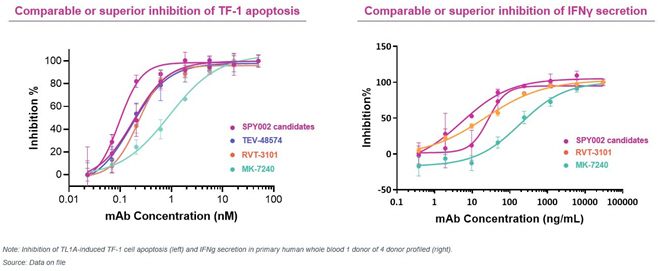
Despite our employee training and compliance programs, we are exposed to the risk that our employees, independent contractors, consultants, commercial collaborators, principal investigators, CROs, CMOs, suppliers and vendors acting for or on our behalf may engage in misconduct or other improper activities. We have adopted a code of conduct and ethics, policies, standard operating procedures and other compliance efforts but it is not always possible to identify and deter misconduct by these parties and the precautions we take to detect and prevent this activity may not be effective in controlling unknown or unmanaged risks or losses or in protecting us from governmental investigations or other actions or lawsuits stemming from a failure to comply with these laws or regulations.
Our internal information technology systems, or those of any of our CROs, manufacturers, other contractors or consultants, third-party service providers, or potential future collaborators, may fail or suffer security or data privacy breaches or other unauthorized or improper access to, use of, or destruction of our proprietary or confidential data, employee data or personal data, which could result in additional costs, loss of revenue, significant liabilities, harm to our brand and material disruption of our operations.
In the ordinary course of our business, we and the third-parties upon which we rely collect, receive, store, process, generate, use, transfer, disclose, make accessible, protect, secure, dispose of, transmit, and share (collectively, process) proprietary, confidential, and sensitive data, including personal data, intellectual property, trade secrets, and other sensitive data (collectively, sensitive information).
Despite the implementation of security measures in an effort to protect systems that store our information, given their size and complexity and the increasing amounts of information maintained on our internal information technology systems and those of our third-party CROs, other contractors (including sites performing our clinical trials), third-party service providers and supply chain companies, and consultants, these systems are potentially vulnerable to breakdown or other damage or interruption from service interruptions, system malfunction, natural disasters, terrorism, war and telecommunication and electrical failures, as well as security breaches from inadvertent or intentional actions by our employees, contractors, consultants, business partners and/or other third-parties, or from cyber-attacks by malicious third-parties, which may compromise our system infrastructure or lead to the loss, destruction, alteration or dissemination of, or damage to, our data.
Some actors now engage and are expected to continue to engage in cyber-attacks, including without limitation nation-state actors for geopolitical reasons and in conjunction with military conflicts and defense activities. During times of war and other major conflicts, we, and the third-parties upon which we rely, may be vulnerable to a heightened risk of these attacks, including retaliatory cyber-attacks, that could materially disrupt our systems and operations, supply chain, and ability to produce, sell and distribute our goods and services. In particular, severe ransomware attacks are becoming increasingly prevalent and can lead to significant interruptions in our operations, ability to provide our products or services, loss of sensitive data and income, reputational harm, and diversion of funds. Extortion payments may alleviate the negative impact of a ransomware attack, but we may be unwilling or unable to make such payments due to, for example, applicable laws or regulations prohibiting such payments.
To the extent that any disruption or security breach were to result in loss, destruction, unavailability, alteration or dissemination of, or damage to, our data or applications, or for it to be believed or reported that any of these occurred, we could incur liability and reputational damage and the development and commercialization of our product candidates could be delayed. Further, our insurance policies may not be adequate to compensate us for the potential losses arising from any such disruption in, or failure or security breach of, our systems or third-party systems where information important to our business operations or commercial development is stored.
Our fully-remote workforce may create additional risks for our information technology systems and data because our employees work remotely and utilize network connections, computers, and devices working at home, while in transit and in public locations. Additionally, business transactions (such as acquisitions or integrations) could expose us to additional cybersecurity risks and vulnerabilities, as our systems could be negatively affected by vulnerabilities present in acquired or integrated entities’ systems and technologies.
75