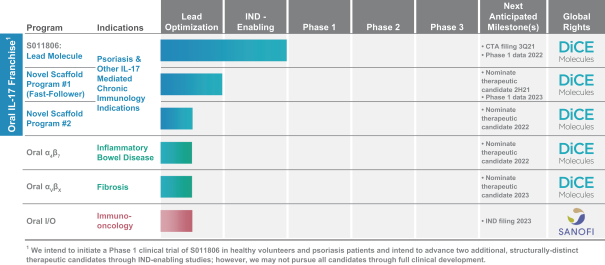
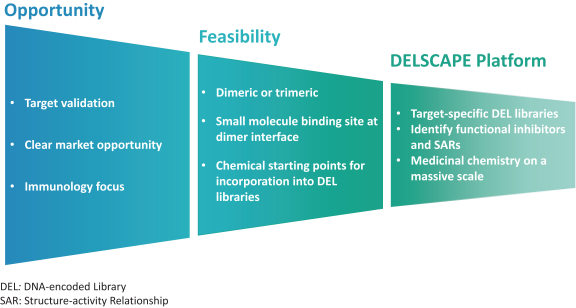
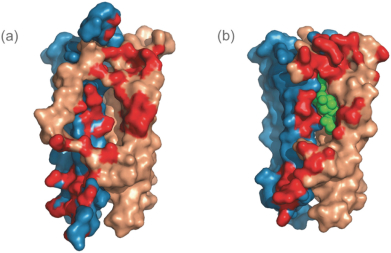
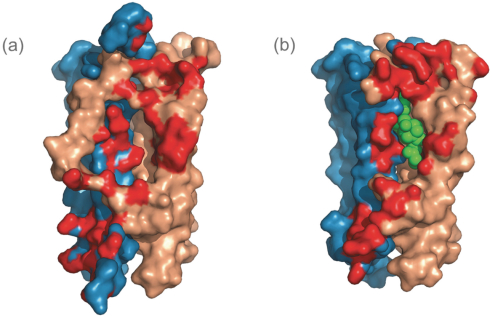
reimbursement or other government programs, including Medicare and Medicaid, integrity oversight and reporting obligations, or reputational harm.
We depend on our information technology systems, and any failure of these systems, or those of our CROs or other third parties with whom we may work, could harm our business. Security breaches, cyber-attacks, loss of data, and other disruptions could compromise sensitive information related to our business or prevent us from accessing critical information and expose us to liability, which could adversely affect our business, results of operations, financial condition and prospects.
We collect and maintain information in that is necessary to conduct our business, and we are increasingly dependent on information technology systems and infrastructure to operate our business. In the ordinary course of our business, we may collect, store, process and transmit large amounts of proprietary, sensitive and confidential information, including intellectual property, business information and personal information. It is critical that we do so in a secure manner to maintain the confidentiality, integrity and availability of such information. We have established physical, electronic and organizational measures to safeguard and secure our systems to prevent a data compromise, and rely on commercially available systems, software, tools, and monitoring to provide security for our information technology systems and the processing, transmission and storage of information. We face a number of risks relative to protecting this critical information, including loss of access risk, inappropriate use or disclosure, inappropriate modification, and the risk of our being unable to adequately monitor, audit, and modify our controls over our critical information. We have also outsourced elements of our information technology infrastructure, and as a result these risks extend to third parties with whom we work, and those third parties may have access to our information.
Despite the implementation of security measures, given the size, complexity, and increasing amounts of proprietary, sensitive, and confidential information maintained by our internal information technology systems and those of our CROs, contract manufacturing organizations (CMOs), vendors, contractors, consultants, and other third party partners, such systems are vulnerable to breakdown, service interruptions, system malfunction, accidents by our personnel or third party partners, natural disasters, terrorism, global pandemics, war and telecommunication and electrical failures, as well as security breaches from inadvertent or intentional actions by our personnel or those of our CROs, CMOs, vendors, contractors, consultants, business partners and/or other third party partners, or from cyber-attacks (including through viruses, phishing attacks, spamming, worms, malicious code, malware, ransomware, denial-of-service attacks, social engineering and other means to affect service reliability and the confidentiality, integrity and availability of information), which may compromise our system infrastructure or data, or that of our third party partners, or lead to data leakage.
The risk of a security breach or disruption or data loss, particularly through cyber-attacks or cyber intrusion, including by computer hackers, foreign governments and cyber terrorists, has generally increased as the number, intensity and sophistication of attempted attacks and intrusions from around the world have increased. In addition, the prevalent use of mobile devices that access confidential information increases the risk of data security breaches, which could lead to the loss of sensitive, proprietary or confidential information.
The COVID-19 pandemic is generally increasing the attack surface available for exploitation, as more companies and individuals work online and work remotely, and as such, the risk of a cybersecurity incident potentially occurring, and our investment in risk mitigations against such an incident, is increasing. For example, there has been an increase in phishing and spam emails as well as social engineering attempts from hackers hoping to use the recent COVID-19 pandemic to their advantage. Additionally, ransomware attacks, including those from organized criminal threat actors, nation-states and nation-state supported actors, are becoming increasingly prevalent and severe and can lead to significant interruptions, delays, or outages in our operations, disruption of clinical trials, loss of data (including data related to clinical trials), loss of income, significant extra expenses to restore data or systems, reputational loss and the diversion of funds. To alleviate the financial,
operational and reputational impact of a ransomware attack it may be necessary to make extortion payments, but we may be unable to do so if applicable laws prohibit such payments.
44