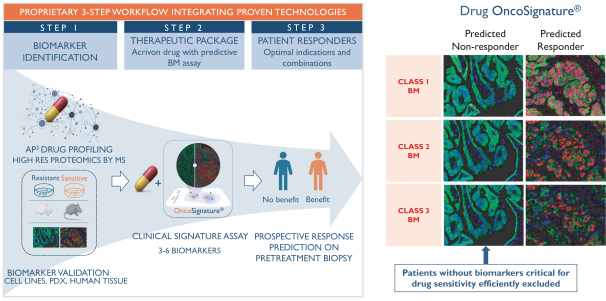
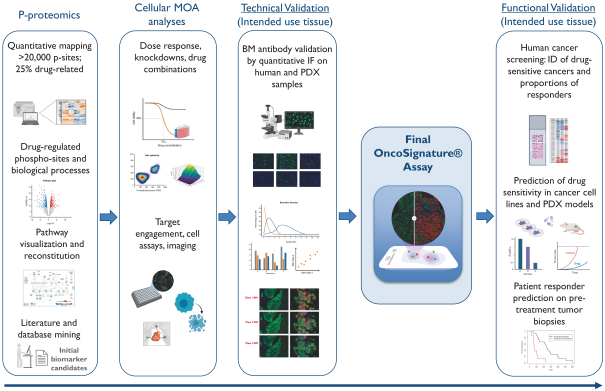
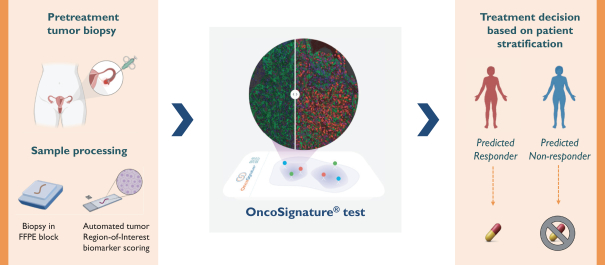
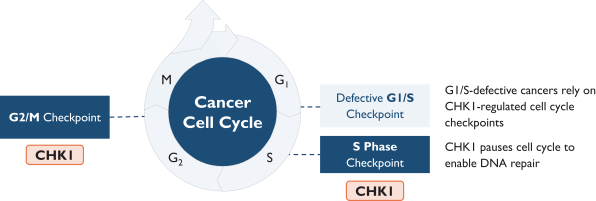
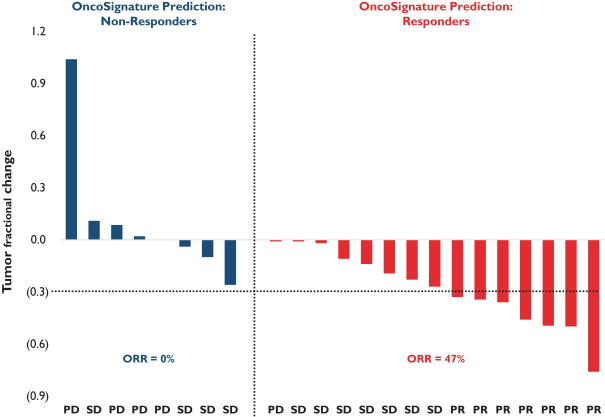
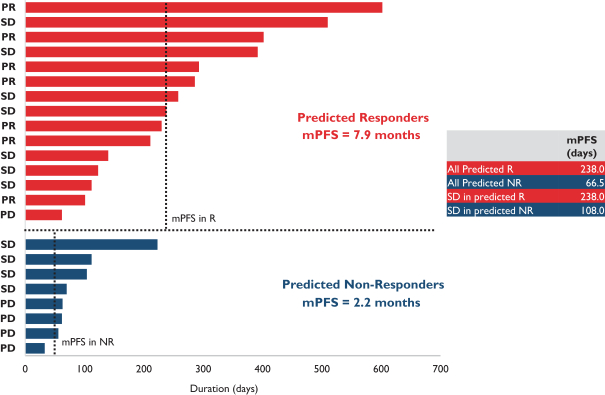
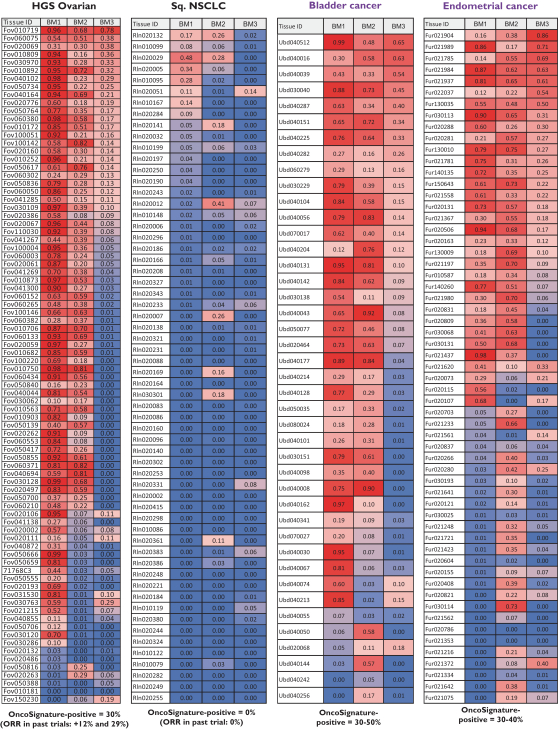
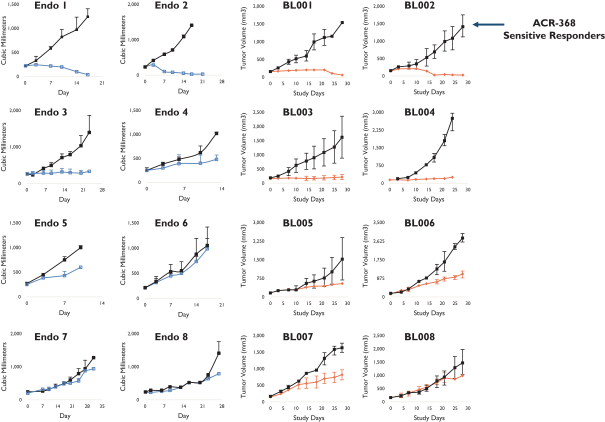
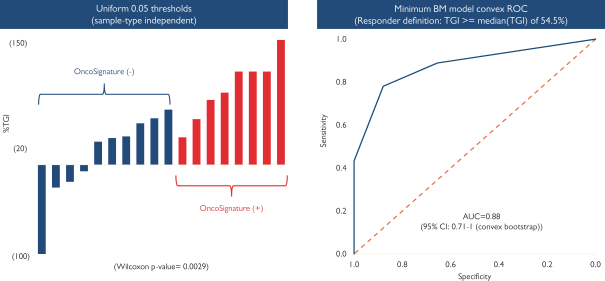
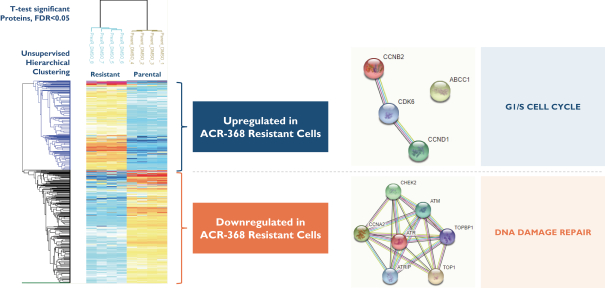
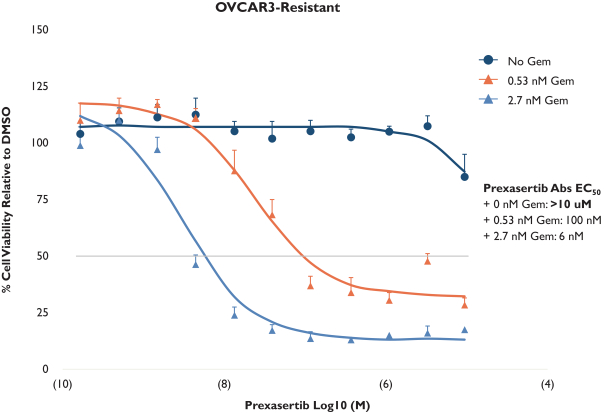
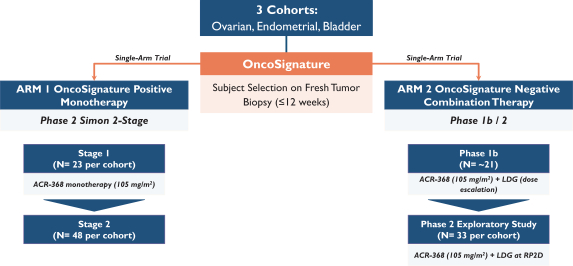
develop adequately the specialized capability and expertise necessary for operations. The expansion of our operations may lead to significant costs and may divert our management and business development resources. Any inability to manage growth could delay the execution of our business plans or disrupt our operations.
Our employees, independent contractors, consultants, collaborators, principal investigators, CROs, suppliers and vendors may be improperly classified and may engage in misconduct or other improper activities, including non-compliance with regulatory standards and requirements.
Our endeavors to properly classify our employees as exempt or non-exempt with respect to wage and hour laws, including, but not limited to, for purposes of minimum wage, overtime and applicable meal and rest periods, and we monitor and evaluate such classifications. Although there are no current, pending, or threatened claims or investigations against us asserting that any employees have been incorrectly classified as exempt, the possibility nevertheless exists that certain job roles could be deemed to have been incorrectly classified as exempt. In addition, we endeavor to classify our workforce properly, and we monitor and evaluate such classifications. Although there are no current, pending, or threatened claims or investigations against us asserting that any independent contractors have been incorrectly classified, the possibility nevertheless exists that certain contractors could be deemed to be employees
We are exposed to the risk that our employees, independent contractors, consultants, collaborators, principal investigators, CROs, suppliers and vendors may engage in fraudulent conduct or other illegal activity. Misconduct by these parties could include intentional, reckless and/or negligent conduct that violates FDA regulations, including those laws requiring the reporting of true, complete and accurate information to the FDA, manufacturing standards, federal and state healthcare laws and regulations, and laws that require the true, complete and accurate reporting of financial information or data. In particular, sales, marketing and business arrangements in the healthcare industry are subject to extensive laws and regulations intended to prevent fraud, kickbacks, self-dealing and other abusive practices. These laws and regulations may restrict or prohibit a wide range of pricing, discounting, marketing and promotion, sales commission, customer incentive programs and other business arrangements. Misconduct by these parties could also involve the improper use of individually identifiable information, including, without limitation, information obtained in the course of clinical trials, which could result in regulatory sanctions and serious harm to our reputation. We have adopted a code of business conduct and ethics, but it is not always possible to identify and deter misconduct, and the precautions we take to detect and prevent this activity may not be effective in controlling unknown or unmanaged risks or losses or in protecting us from governmental investigations or other actions or lawsuits stemming from a failure to be in compliance with such laws or regulations. If any such actions are instituted against us, and we are not successful in defending ourselves or asserting our rights, those actions could have a significant impact on our business, including the imposition of significant civil, criminal and administrative penalties, including, without limitation, damages, fines, disgorgement, imprisonment, exclusion from participation in government healthcare programs, such as Medicare and Medicaid, additional reporting requirements and oversight if we become subject to a corporate integrity agreement or similar agreement to resolve allegations of non-compliance with these laws, and the curtailment or restructuring of our operations.
Our business and operations would suffer in the event of system failures, cyberattacks or a deficiency in our or our CROs’, manufacturers’ contractors’, consultants’ or collaborators’ cybersecurity.
Despite the implementation of security measures, our internal computer systems, as well as those of third parties on which we rely, are vulnerable to damage from, among other things, computer viruses, malware, unauthorized access, natural disasters, terrorism, war, telecommunication and electrical failures, system malfunctions, cyberattacks or cyber-intrusions over the Internet, attachments to emails, phishing attacks, persons inside our organization, or persons with access to systems inside our organization. The risk of a security breach or disruption, particularly through cyberattacks or cyber intrusion, including by computer hackers, foreign governments and cyber terrorists, has generally increased as the number, intensity and sophistication of
49