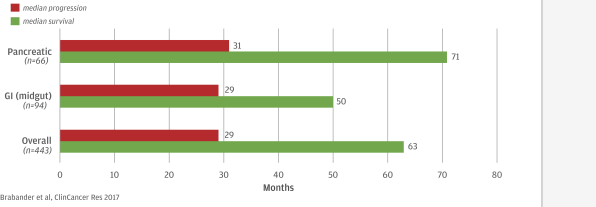
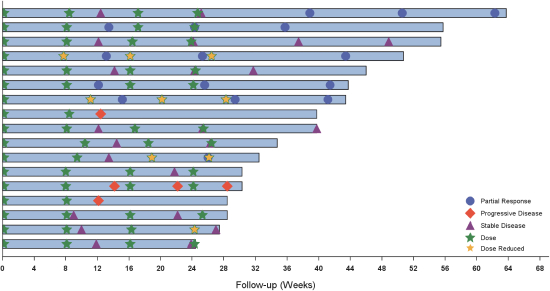
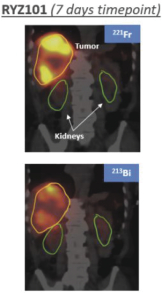
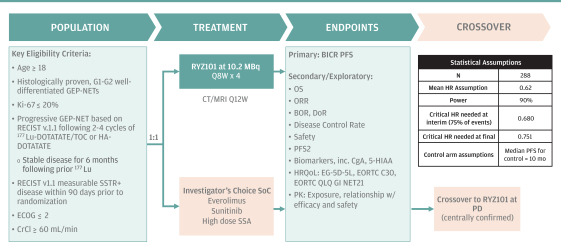
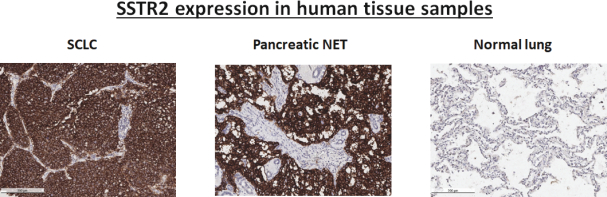
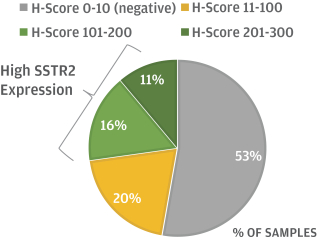
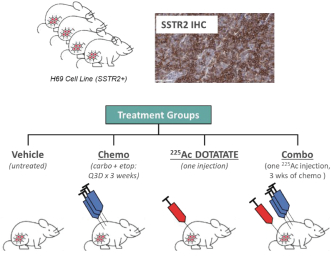
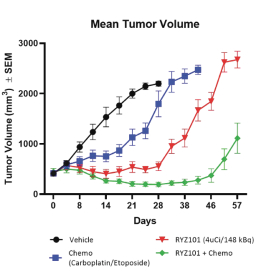
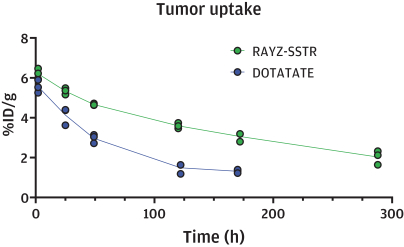
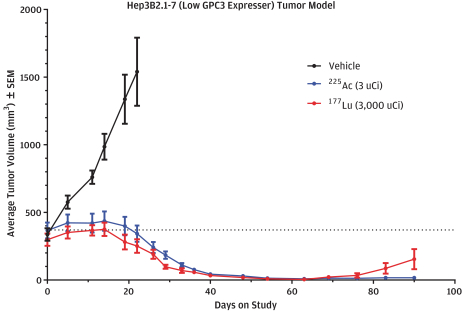
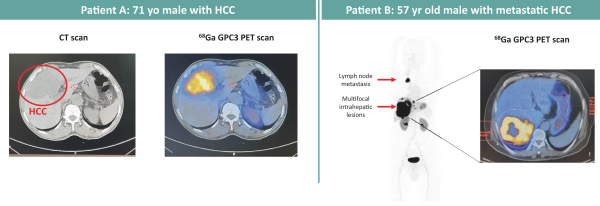
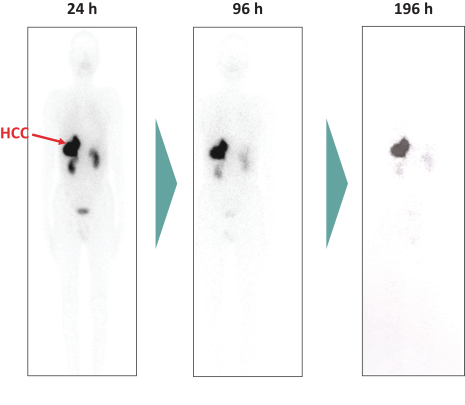
limited to regulatory investigations or actions, litigation, fines and penalties, disruptions of our business operations, reputational harm, loss of revenue or profits, and other adverse consequences. Our internal computer systems, or those of our third-party CROs, manufacturers, contractors or consultants, or current or future collaborators or other third parties, may fail or suffer security breaches or other unauthorized or improper access, which could result in a material disruption of our development programs.
We are increasingly dependent upon information technology systems, infrastructure and data to operate our business. In the ordinary course of business, we collect, store, handle, share, use, retain, safeguard, transmit, analyze and otherwise process large amounts of data, including, without limitation, confidential information, such as proprietary business information, health information, and personal information. It is critical that we do so in a manner to maintain the confidentiality and integrity of such confidential information.
Despite the implementation of security measures, given the size and complexity of our internal information technology systems and those of our third-party vendors and other contractors and consultants, and the increasing amounts of confidential information that they maintain, such internal computer and technology systems and those of our current and any future third-party CROs, manufacturers, and other contractors, consultants and collaborators are potentially vulnerable to breakdown or other damage or interruption from service interruptions, system malfunction, information security threats, such as data breaches, damage from computer viruses, cyber-attacks (such as the deployment of social engineering malware, denial-of-service attacks, ransomware attacks, and supply chain attacks), unauthorized access, intentional or accidental actions or inaction by our employees, third-party vendors, contractors, consultants, business partners or other third parties that introduce vulnerabilities, natural disasters, terrorism, war and telecommunication and electrical failures. While we have not experienced any material system failures, accidents, security breaches or intrusions to date, if such an event were to occur and cause interruptions in our operations or result in any inadvertent or unauthorized disclosure of or access to personal information, protected health information, or other sensitive, confidential or proprietary information, it could result in a material disruption of our programs and/or material liability and reputation harm. For example, the loss of data from preclinical studies or clinical trials could result in delays in our regulatory approval efforts and significantly increase our costs to recover or reproduce the data. Undetected security breaches of our computer systems could result in the theft of our proprietary chemical structures and fraudulent filing of patent claims by competitors that could limit our freedom to operate in the future. To the extent that any disruption or security breach results in a loss of or damage to our data or applications, other data or applications relating to our technology, RYZ101, RYZ801 or future drug candidates, or those of our third-party vendors and other contractors and consultants, or inappropriate disclosure of confidential or proprietary information, we could incur liabilities and the further development of RYZ101, RYZ801 or future drug candidates could be compromised or delayed. Any of the foregoing could result in significant legal and financial exposure and reputational damage that could potentially have a material adverse effect on our business, financial condition, results of operations, and prospects. We may be unable to adequately protect our information systems from cyberattacks, which could result in the disclosure of confidential or proprietary information, including personal data, damage our reputation, and subject us to significant financial and legal exposure.
We rely on information technology systems that we or our third-party service providers operate to collect, store, handle, share, use, retain, safeguard, transmit, analyze and otherwise process electronic information in our day-to-day operations. In connection with our drug discovery efforts, we may collect, store, handle, use or otherwise process a variety of personal information and data, such as name, mailing address, email addresses, phone number and clinical trial information. A successful cyberattack could result in the theft or destruction of intellectual property, data (such as personal information) or other misappropriation of assets, or otherwise compromise our confidential or proprietary information and disrupt our operations. Cyberattacks are increasing in their frequency, sophistication and intensity, and have become increasingly difficult to detect. Cyberattacks could include wrongful conduct by computer hackers, hostile foreign governments or agencies, industrial espionage,
90