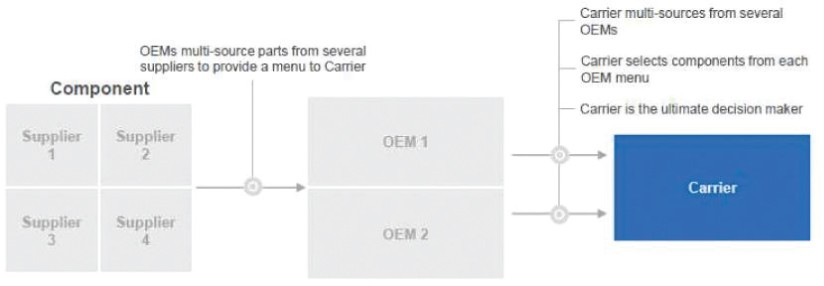
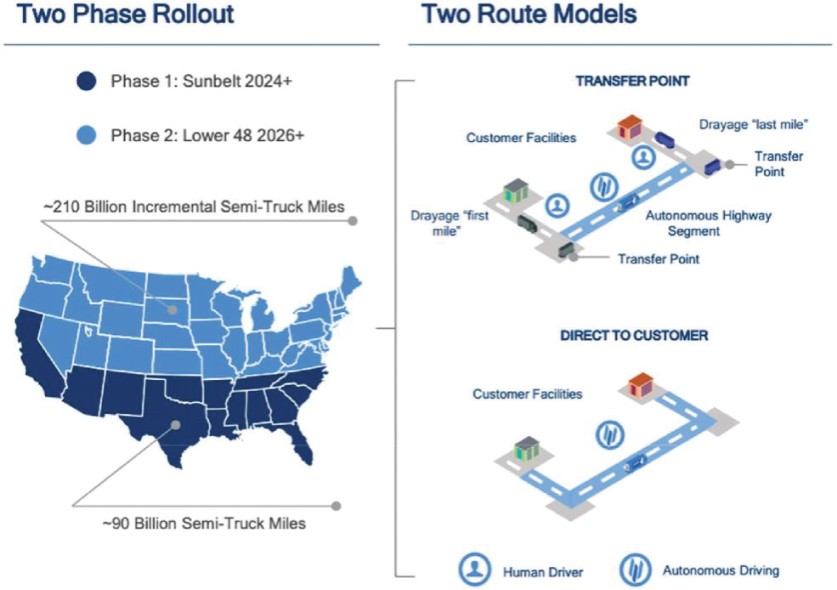
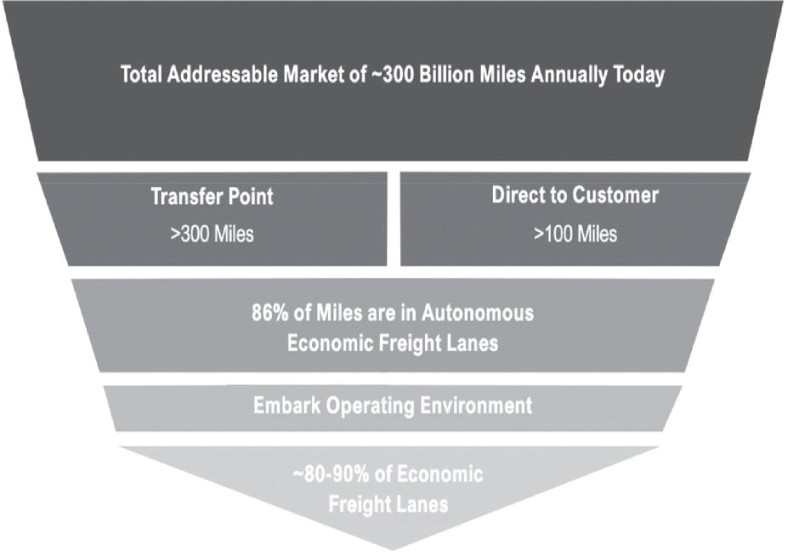
for open source software, and Embark cannot ensure that the authors of such open source software will implement or push updates to address security risks or will not abandon further development and maintenance. Many of the risks associated with the use of open source software, such as the lack of warranties or assurances of title, non-infringement, or performance, cannot be eliminated, and could, if not properly addressed, negatively affect Embark’s business. Embark has processes to help alleviate these risks, including a review process for screening requests from Embark’s developers for the use of open source software, but Embark cannot be sure that all open source software is identified or submitted for approval prior to use in its products and services. Any of these risks could be difficult to eliminate or manage, and, if not addressed, could adversely affect Embark’s ownership of proprietary intellectual property, the security of Embark’s vehicles, or its business, results of operations, and financial condition.
If Embark’s software contains serious errors or defects, Embark may lose revenue and market acceptance and may incur costs to defend or settle claims with its licensees, franchisees or other parties.
Software often contains errors, defects, security vulnerabilities or software bugs, some of which are difficult to detect and correct, particularly when first introduced or when new versions or enhancements are released. Despite internal testing, Embark’s software may contain serious errors or defects, security vulnerabilities or software bugs that Embark may be unable to successfully detect or correct in a timely manner or at all, which could result in security incidents, data breaches, vehicle safety issues, product liability claims, lost revenue, significant expenditures of capital, a delay or loss in market acceptance, and damage to Embark’s reputation and brand, any of which could adversely affect Embark’s business, results of operations, and financial condition.
Embark is exposed to, and may be adversely affected by, interruptions to its information technology systems and networks and sophisticated cyber-attacks.
Embark collects and maintains information in digital form that is necessary to conduct its business, and it relies on information technology systems and networks (“IT systems”) in connection with many of its business activities. Some of these networks and systems are managed by third-party service providers and are not under Embark’s direct control, and as a result, a number of third-party service providers may or could have access to its confidential information. Embark’s operations routinely involve receiving, storing, processing, and transmitting confidential or sensitive information pertaining to its business, users, dealers, suppliers, employees, and other sensitive matters, including intellectual property, proprietary business information, and personal information. It is critical that Embark does so in a secure manner to maintain the confidentiality and integrity of such confidential or sensitive information. Embark has established physical, electronic, and organizational measures designed to safeguard and secure its systems to prevent a data compromise, and relies on commercially available systems, software, tools, and monitoring to provide security for its IT systems and the processing, transmission, and storage of digital information. Despite the implementation of preventative and detective security controls, such IT systems are vulnerable to damage or interruption from a variety of sources, including telecommunications or network failures or interruptions, system malfunction, natural disasters, malicious human acts, terrorism, and war. Such IT systems, including Embark’s servers, are additionally vulnerable to physical or electronic break-ins, security breaches from inadvertent or intentional actions by Embark’s employees, third-party service providers, contractors, consultants, business partners, and/or other third parties, or from cyber-attacks by malicious third parties (including the deployment of harmful malware, ransomware, denial-of-service attacks, social engineering, and other means to affect service reliability and threaten the confidentiality, integrity, and availability of information).
Any future cyber incidents could materially disrupt operational systems, result in the loss of trade secrets or other proprietary or competitively sensitive information, compromise personally identifiable information regarding users or employees and jeopardize the security of Embark’s facilities. The risk of a security breach or disruption, particularly through cyber-attacks or cyber intrusion, including by computer hackers, foreign governments, and cyber terrorists, has generally increased as the number, intensity, and sophistication of attempted attacks and intrusions from around the world have increased. Embark can provide no assurance that its current IT systems, or those of the third parties upon which Embark relies, are fully protected against cybersecurity threats. It is possible that Embark or its third-party service providers may experience cybersecurity and other breach incidents that remain undetected for an extended period. Even when a security breach is detected, the full extent of the breach may not be determined immediately. Because techniques used to obtain unauthorized access or to sabotage systems change frequently and generally are not recognized until they are launched against a target, Embark may be unable to anticipate these techniques or to implement adequate preventative measures. Information technology security threats, including security breaches, computer malware, and other cyber-attacks are increasing in both frequency and sophistication and could cause Embark to incur financial liability, subject Embark to legal or regulatory sanctions or damage its reputation with users, dealers, suppliers, and other stakeholders. Embark continuously seeks to maintain information security and controls, however its efforts to mitigate and address network security problems, bugs, viruses, worms, malicious software programs, and security vulnerabilities may not be successful and the impact of a material cybersecurity event could have a material adverse effect on its competitive position, reputation, results of operations, financial condition, and cash flows.