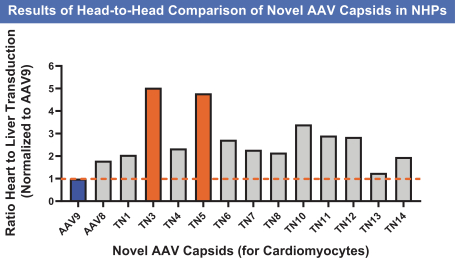
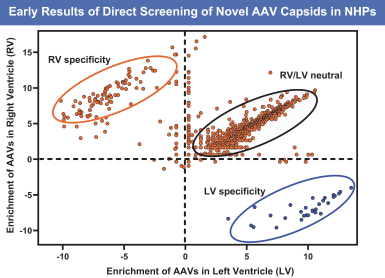
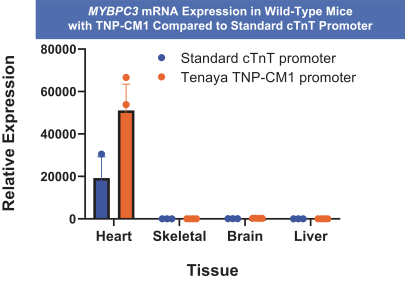
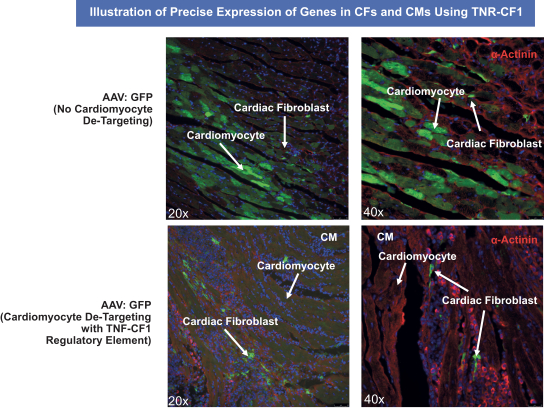
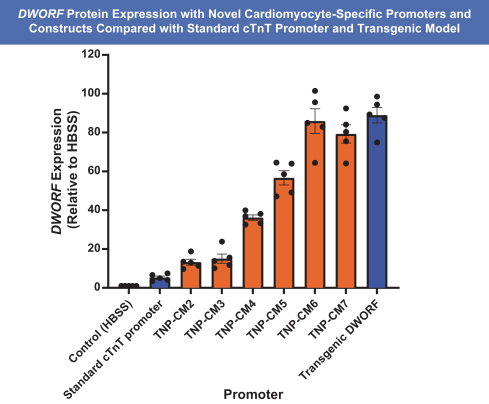
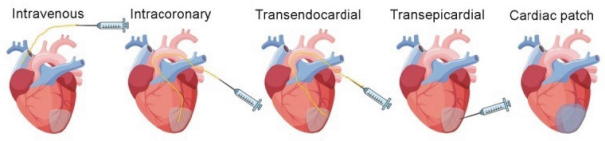
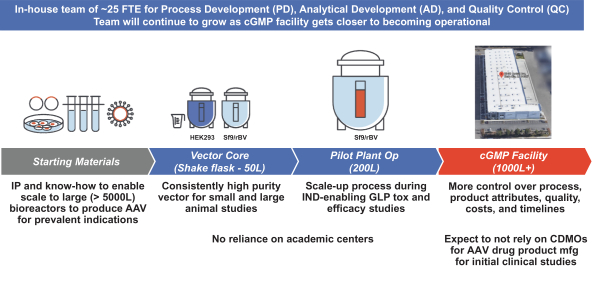
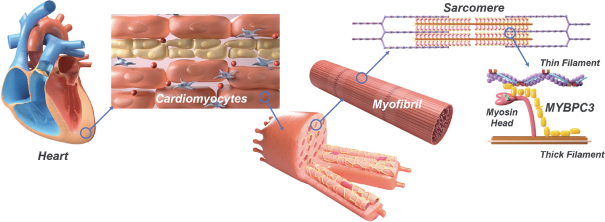
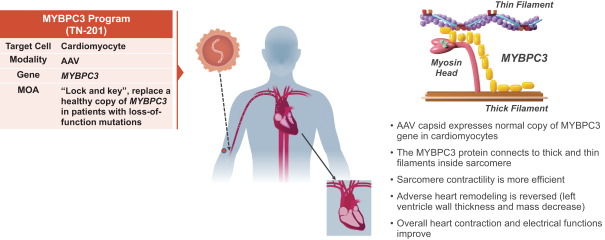
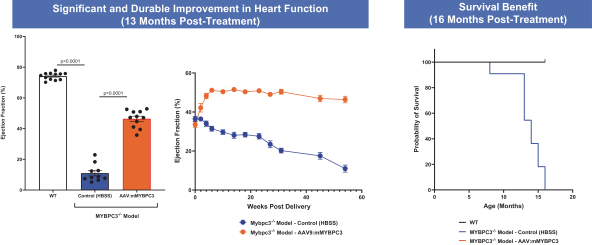
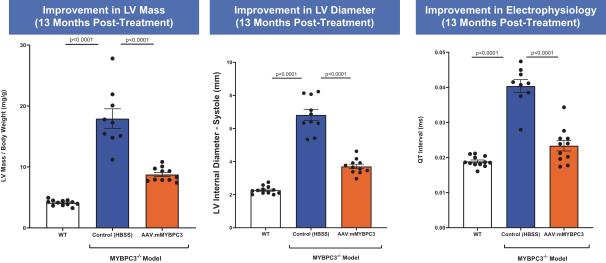
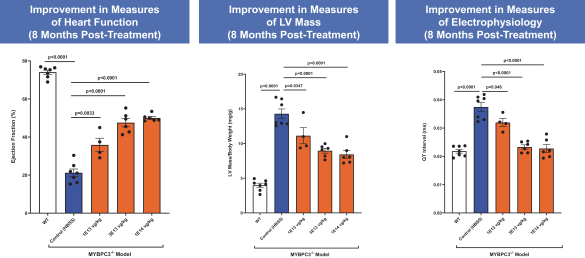
on our own. If we are unable to enter into such arrangements when needed, on acceptable terms, or at all, we may not be able to successfully commercialize any of our product candidates that receive regulatory approval, or any such commercialization may experience delays or limitations. If we are unable to successfully commercialize our approved product candidates, either on our own or through collaborations with one or more third parties, our future product revenue will suffer, and we may incur significant additional losses.
Our computer systems, or those of any of our CROs, manufacturers, contractors, consultants or other third parties or potential future collaborators, may fail or suffer security incidents or data privacy breaches or other unauthorized or improper access to, use of, or destruction of our proprietary or confidential data, employee data, or personal data, which could result in additional costs, loss of revenue, significant liabilities, harm to our brand and material disruption of our operations.
Despite the implementation of security measures in an effort to protect systems that store our information, given their size and complexity and the increasing amounts of information maintained on our internal information technology systems, and those of our third-party CROs, other contractors (including sites performing our clinical trials), consultants and other third parties, such systems are vulnerable to breakdown or other damage or interruption from, among other things, service interruptions, system malfunctions, natural disasters, terrorism, war, telecommunication and electrical failures, security breaches from inadvertent or intentional actions by our employees, contractors, consultants, business partners, and other third parties, cyber-attacks by malicious third parties (including supply chain cyber-attacks or attacks by nation-state or nation-state supported actors, or the deployment of harmful malware, ransomware, denial-of-service attacks, phishing attacks, social engineering and other means to affect service reliability and threaten the confidentiality, integrity and availability of information), which may compromise our system infrastructure or lead to the loss, destruction, alteration, prevention of access to, disclosure, dissemination of, or damage or unauthorized access to, our data (including trade secrets or other confidential information, intellectual property, proprietary business information and personal data) or data that is processed or maintained on our behalf, or other assets, which could result in financial, legal, business and reputational harm to us.
We have in the past and may in the future experience phishing attempts, and companies have, in general, experienced an increase in phishing and social engineering attacks from third parties in connection with the COVID-19 pandemic, and the increase in remote working further increases security threats. To the extent that any data breach, disruption or security incident were to result in any loss, destruction, unavailability, alteration, disclosure, dissemination of, or damage or unauthorized access to, our personal data, applications, assets or any other data processed or maintained on our behalf, or for it to be believed or reported that any of the foregoing occurred, we could incur significant liability, financial harm and reputational damage and the development and commercialization of our product candidates could be delayed. We cannot ensure that our data protection efforts and our investment in information technology, or the efforts or investments of CROs, consultants or other third parties, will prevent breakdowns or breaches in our or their systems or other cybersecurity incidents that cause loss, destruction, unavailability, alteration, dissemination of, or damage or unauthorized access to, our data, including personal data, assets and other data processed or maintained on our behalf, that could have a material adverse effect upon our reputation, business, operations or financial condition. We also rely on third parties to manufacture our product candidates, and any data breaches or other security events relating to their computer systems could also have a material adverse effect on our business. Controls employed by our information technology department and our CROs, consultants and other third parties could prove inadequate, and our ability to monitor such third parties’ data security practices is limited. Due to applicable laws, rules, regulations and standards or contractual obligations, we may be held responsible for any information security failure or cyber-attack attributed to our third-party service providers as they relate to the information we share with them.
If any data breach or other security incident were to occur and cause interruptions in our operations, it could result in a material disruption of our programs and the development of our product candidates could be delayed. In addition, the loss of clinical trial data for our product candidates could result in delays in our marketing approval efforts and significantly increase our costs to recover or reproduce the data. Further, any such event that
59