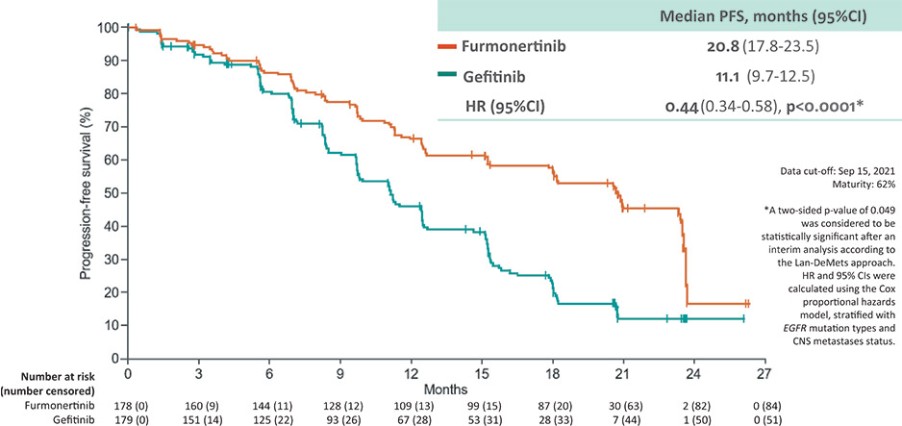
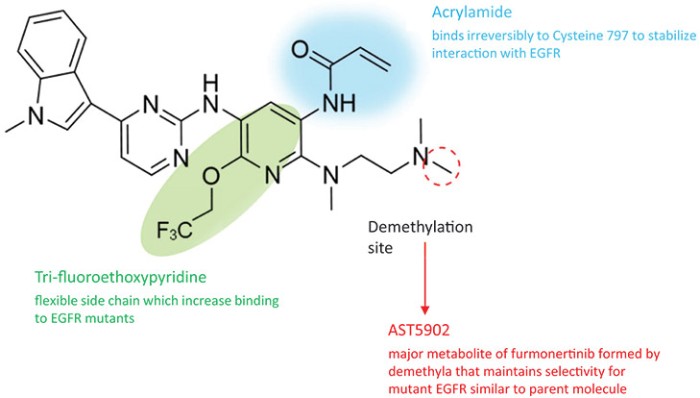
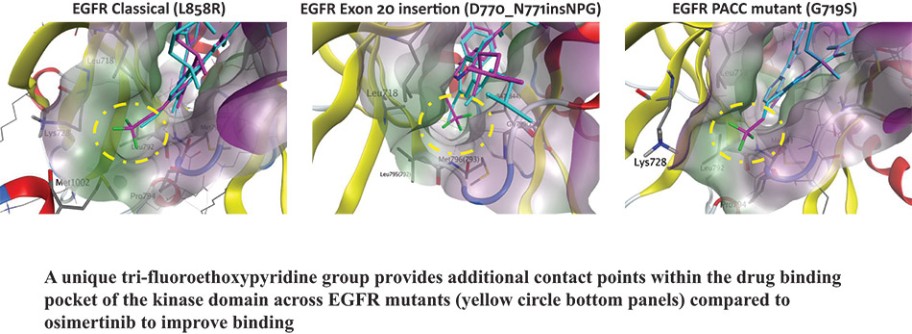
corresponding effect on our business, including putting us in breach of our obligations under privacy laws and regulations and/or which could in turn adversely affect our business, financial condition, results of operations and prospects. We cannot assure you that our contractual measures and our own privacy and security-related safeguards will protect us from the risks associated with the third-party processing of such information. Any of the foregoing could adversely affect our business, financial condition, results of operations and prospects.
We also publicly post our privacy policies and practices concerning our collection, use, disclosure and other processing of the personal information provided to us by our website visitors and by our customers. Although we endeavor to comply with our public statements and documentation, we may at times fail to do so or be perceived to have failed to do so. Our publication of our privacy policies and other statements we publish that provide promises and assurances about privacy and security can subject us to potential state and federal action if they are found to be deceptive, unfair or misrepresentative of our actual practices. Any actual or perceived failure by us to comply with federal, state or foreign laws, rules or regulations, industry standards, contractual or other legal obligations, or any actual, perceived or suspected cybersecurity incident, whether or not resulting in unauthorized access to, or acquisition, release or transfer of personal information or other data, may result in enforcement actions and prosecutions, private litigation, significant fines, penalties and censure, claims for damages by customers and other affected individuals, regulatory inquiries and investigations or adverse publicity and could cause our customers and collaborators to lose trust in us, any of which could adversely affect our business, financial condition, results of operations and prospects.
The successful assertion of one or more large claims against us that exceeds our available insurance coverage, or results in changes to our insurance policies (including premium increases or the imposition of large deductible or co-insurance requirements), could have an adverse effect on our business. In addition, we cannot be sure that our existing insurance coverage will continue to be available on acceptable terms or that our insurers will not deny coverage as to any future claim.
If our internal information technology systems, or those used by our CROs, clinical sites, or other contractors or consultants upon which we rely, are or were compromised, become unavailable or suffer security breaches, loss or leakage of data or other disruptions, we could suffer material adverse consequences resulting from such compromise, including but not limited to, operational or service interruption, harm to our reputation, litigation, fines, penalties and liability, compromise of sensitive information related our business, and other adverse consequences.
In the ordinary course of our business, we, and the third parties upon which we rely, process sensitive data and as a result, we and the third parties upon which we rely face a variety of evolving threats which could cause security incidents.
Our internal information technology systems and those of our CROs, clinical sites, and other contractors and consultants upon which we rely are vulnerable to cyberattacks, computer viruses, bugs, worms, or other malicious codes, malware, including as a result of advanced persistent threat intrusions, and other attacks by computer hackers, cracking, application security attacks, social engineering, including through phishing attacks, supply chain attacks and vulnerabilities through our third-party service providers, denial-of-service attacks, such as credential stuffing, credential harvesting, personnel misconduct or error, supply-chain attacks, software bugs, server malfunctions, software or hardware failures, loss of data or other information technology assets, adware, telecommunications failures, earthquakes, fires, floods, and other similar threats.
Such threats are prevalent and continue to rise, are increasingly difficult to detect, and come from a variety of sources, including traditional computer “hackers,” threat actors, “hacktivists,” organized criminal threat actors, personnel, such as through theft or misuse, sophisticated nation states, and nation-state-supported actors. In particular, ransomware attacks, including those from organized criminal threat actors, nation-states and nation-state supported actors, are becoming increasingly prevalent and severe and can lead to significant interruptions, delays, or outages in our operations, loss of data, including sensitive customer information, loss of income, significant extra expenses to restore data or systems, reputational loss and the diversion of funds. To alleviate the negative impact of a ransomware attack, it may be preferable to make extortion payments, but we may be unwilling or unable to do so, including, for example, if applicable laws or regulations prohibit such payments.