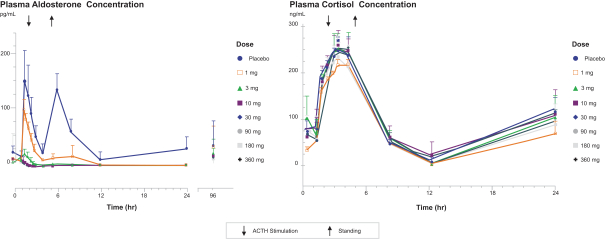
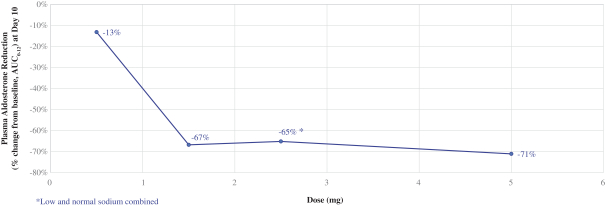
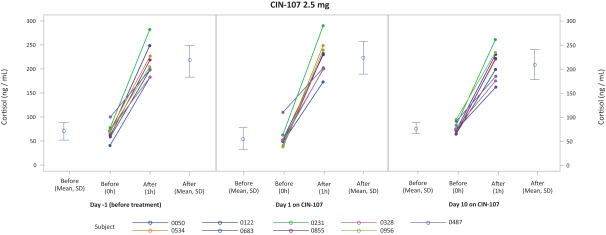
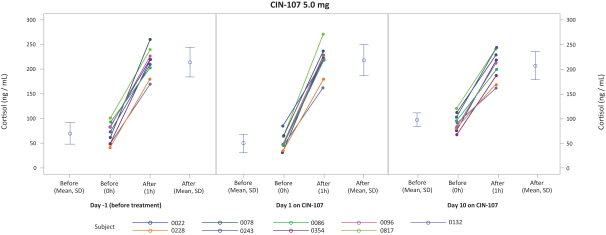
weaknesses will not exist or otherwise be discovered. If other material weaknesses or other deficiencies occur, our ability to accurately and timely report our financial position could be impaired, which could result in late filings of our required reports under the Exchange Act, restatements of our financial statements, a decline in the price of our common stock, suspension or delisting of our common stock from Nasdaq, and could adversely affect our reputation, results of operations and financial condition.
Our internal computer systems, or those of our collaborators or other contractors or consultants, may fail or suffer security breaches, which could result in a significant disruption of our product development programs and our ability to operate our business effectively.
Our internal computer systems and those of our current and future collaborators, contractors or consultants may be vulnerable to damage from computer viruses, unauthorized access, natural disasters, terrorism, war and telecommunication and electrical failures. Cyberattacks are increasing in their frequency, sophistication and intensity, and have become increasingly difficult to detect. Cyberattacks could include the deployment of harmful malware, ransomware, denial-of-service attacks, social engineering and other means to affect service reliability and threaten the confidentiality, integrity and availability of information. Cyberattacks also could include phishing attempts or e-mail fraud to cause payments or information to be transmitted to an unintended recipient.
Despite our efforts to ensure the security, privacy, integrity, confidentiality, availability, and authenticity information technology networks and systems, processing and information, we may not be able to anticipate or to implement effective preventive and remedial measures against all data security and privacy threats. The recovery systems, security protocols, network protection mechanisms and other security measures that we have integrated into our systems, networks and physical facilities, which are designed to protect against, detect and minimize security breaches, may not be adequate to prevent or detect service interruption, system failure data loss or theft, or other material adverse consequences. No security solution, strategy, or measures can address all possible security threats or block all methods of penetrating a network or otherwise perpetrating a security incident. The risk of unauthorized circumvention of our security measures or those of our third-party providers, clients and partners has been heightened by advances in computer and software capabilities and the increasing sophistication of hackers who employ complex techniques, including without limitation, the theft or misuse of personal and financial information, counterfeiting, “phishing” or social engineering incidents, ransomware, extortion, publicly announcing security breaches, account takeover attacks, denial or degradation of service attacks, malware, fraudulent payment and identity theft. Because the techniques used by hackers change frequently, we may be unable to anticipate these techniques or implement adequate preventive measures. Our applications, systems, networks, software and physical facilities could have material vulnerabilities, be breached or personal or confidential information could be otherwise compromised due to employee error or malfeasance, if, for example, third parties attempt to fraudulently induce our personnel or our customers to disclose information or user names and/or passwords, or otherwise compromise the security of our networks, systems and/or physical facilities. Third parties may also exploit vulnerabilities in, or obtain unauthorized access to, platforms, software, applications, systems, networks, sensitive information, and/or physical facilities utilized by our vendors. Improper access to our systems or databases could result in the theft, publication, deletion or modification of personal information, confidential or proprietary information, financial information and other information. An actual or perceived breach of our security systems or those of our third-party service providers may require notification under applicable data privacy regulations or contractual obligations, or for customer relations or publicity purposes, which could result in reputational harm, costly litigation (including class action litigation), material contract breaches, liability, settlement costs, loss of sales, regulatory scrutiny, actions or investigations, a loss of confidence in our business, systems and processing, a diversion of management’s time and attention, and significant fines, penalties, assessments, fees and expenses.
The costs to respond to a security breach and/or to mitigate any security vulnerabilities that may be identified could be significant, our efforts to address these problems may not be successful, and these problems could result in unexpected interruptions, delays, cessation of service, negative publicity, and other harm to our business and our competitive position. We could be required to fundamentally change our business activities and
62