Various government and consumer agencies have called for new laws, rules, regulations, and changes in industry practices and are continuing to review the need for greater regulation for the collection of information concerning consumer behavior on the internet. Because the interpretation and application of many data privacy and security laws, rules, and regulations, along with contractually imposed standards, are uncertain, it is possible that these laws, rules, regulations, and standards may be interpreted and applied in a manner that is inconsistent with our existing data management practices or the features of our products and e-commerce risk management platform capabilities. If so, in addition to the possibility of fines, lawsuits, and other claims and penalties, we could be required to fundamentally change our business activities and practices or modify our products and platform capabilities, which could have an adverse effect on our business, financial condition, and results of operations. For example, we may not be legally permitted to collect and store information on transactions we process that enable us to improve our products. Any inability to adequately address privacy and security concerns, even if unfounded, or to comply with applicable data privacy and security laws, rules, regulations, policies, industry standards, or social expectations of corporate fairness, could result in additional cost and liability to us, damage our reputation, inhibit sales, and adversely affect our business, financial condition, and results of operations. Data privacy and security concerns, whether valid or not valid, may inhibit market adoption of our products, particularly in certain industries and foreign countries. If we are not able to adjust to changing laws, rules, regulations, and standards related to the internet, our business, financial condition, and results of operations may be adversely affected.
We rely significantly on the use of information technology, including technology provided by third-party service providers. Any failure, error, defect, inadequacy, interruption, or data breach or other security incident involving our information technology systems, or those of our third-party service providers, could have an adverse effect on our business, reputation, financial condition, and results of operations.
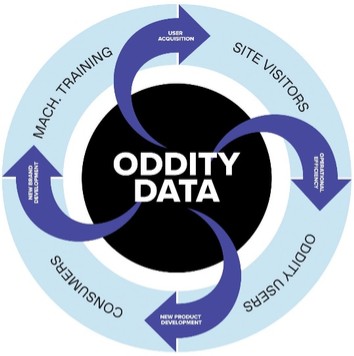
We increasingly rely on information technology systems to collect, store, share, use, retain, safeguard, transmit, analyze, and otherwise process electronic information. Our ability to effectively manage our business and coordinate the manufacturing, sourcing, distribution, and sale of our products depends significantly on the reliability and capacity of these systems. We rely on information technology systems to effectively manage, among other things, our business data, communications, supply chain, inventory management, consumer order entry and order fulfillment, processing transactions, summarizing and reporting results of operations, human resources benefits and payroll management, compliance with regulatory, legal, and tax requirements, and other processes and data necessary to manage our business. Disruptions to our information technology systems, including any disruptions to our current systems and/or as a result of transitioning to additional or replacement information technology systems, as the case may be, could disrupt our business and could result in, among other things, transaction errors, processing inefficiencies, loss of data, including personal data, and the loss of sales and customers, which could have an adverse effect on our reputation, business, financial condition, and results of operations. Additionally, the future operation, success, and growth of our business depends on streamlined processes made available through information systems, global communications, internet activity, and other network processes.
Our information technology systems, including our AI models, may be subject to damage, interruptions, or shutdowns, including from breaches, attacks by computer hackers, malicious code (such as malware, viruses and worms), ransomware attacks, insider threats, unauthorized activity or access, password-spraying, acts of vandalism, software or hardware vulnerabilities, employee or contractor theft, misplaced or lost data, fraud, misconduct or misuse, social engineering, phishing, denial-of-service attacks, organized cyberattacks, programming or human errors, telecommunication failures, or failures during the process of upgrading or replacing software, databases, or components, any of which could result in the loss or disclosure of confidential or personal information or our own proprietary information, software, methodologies, or business information. Our existing safety systems, data backup, access protection, user management, and information technology emergency planning may not be sufficient to prevent data loss or long-term network outages. In addition, we may have to upgrade our existing information technology systems or choose to incorporate new technology systems from time to time in order for such systems to support the increasing needs of our expanding business. Costs and potential problems and interruptions associated with the implementation of new or upgraded systems and technology or with maintenance or adequate support of existing systems could disrupt or reduce the efficiency of our operations.