- BAER Dashboard
- Financials
- Filings
-
Holdings
- Transcripts
- ETFs
- Insider
- Institutional
- Shorts
-
S-1 Filing
Bridger Aerospace Group Holdings, Inc. Common Stock (BAER) S-1IPO registration
Filed: 17 Oct 23, 4:14pm
Delaware | 7389 | 88-3599336 | ||
(State or other jurisdiction of incorporation or organization) | (Primary Standard Industrial Classification Code Number) | (I.R.S. Employer Identification Number) |
Michael P. Heinz | David S. B aks t | |
Sidley Austin LLP | John R. Ablan | |
787 Seventh Avenue | Mayer Brown LLP | |
New York, NY 10019 | 1221 Avenue of the Americas | |
(212) 839-5444 | New York, N Y 100 20 | |
(212) 506-2551 |
| Large accelerated filer | ☐ | Accelerated filer | ☐ | |||
Non-accelerated filer | ☒ | Smaller reporting company | ☒ | |||
| Emerging growth company | ☒ | |||||
The information in this preliminary prospectus is not complete and may be changed. These securities may not be sold until the registration statement filed with the Securities and Exchange Commission is effective. This preliminary prospectus is not an offer to sell these securities, and we are not soliciting offers to buy these securities, in any jurisdiction where the offer or sale is not permitted.
PRELIMINARY PROSPECTUS
SUBJECT TO COMPLETION, DATED OCTOBER 17, 2023
$70,000,000

Shares of Common Stock
We are offering shares of our common stock, par value $0.0001 per share (“Common Stock”). Our Common Stock is listed on The Nasdaq Global Market under the symbol “BAER.” On October 16, 2023, the last reported sale price for our Common Stock on The Nasdaq Global Market was $6.45 per share.
We are an “emerging growth company,” as defined under the federal securities laws, and, as such, are subject to certain reduced public company reporting requirements.
INVESTING IN OUR COMMON STOCK INVOLVES SUBSTANTIAL RISKS. YOU SHOULD CAREFULLY READ THE SECTION OF THIS PROSPECTUS ENTITLED “RISK FACTORS” BEGINNING ON PAGE 19 OF THIS PROSPECTUS, AS WELL AS OTHER INFORMATION INCLUDED IN THIS PROSPECTUS, BEFORE BUYING ANY SHARES OF OUR COMMON STOCK.
| Per Share | Total(2) | |||||||
Public offering price | $ | $ | ||||||
Underwriting discounts and commissions(1) | $ | $ | ||||||
Proceeds, before expenses, to us | $ | $ | ||||||
| (1) | We will reimburse the underwriters for certain expenses. See the section of this prospectus entitled “Underwriting” for additional disclosure regarding underwriting discounts, commissions and expenses. |
| (2) | Assumes no exercise of the underwriters’ option to purchase additional shares described below. |
We have granted the underwriters an option to purchase up to an additional shares of our Common Stock from us at the public offering price, less the underwriting discounts and commissions, at any time within 30 days from the date of this prospectus.
The underwriters expect to deliver the shares on , 2023 through the facilities of The Depository Trust Company.
You should rely only on the information contained in this prospectus or amendment hereto. We have not authorized anyone to provide you with different information.
Neither the Securities and Exchange Commission nor any state securities commission has approved or disapproved of these securities or passed upon the adequacy or accuracy of this prospectus. Any representation to the contrary is a criminal offense.
Joint Book-Running Managers
Stifel
| BTIG | Canaccord Genuity |
The date of this prospectus is , 2023.
TABLE OF CONTENTS
| Page | ||||
| ii | ||||
| iii | ||||
| iv | ||||
| v | ||||
| 1 | ||||
| 19 | ||||
| 56 | ||||
| 57 | ||||
| 59 | ||||
| 61 | ||||
Management’s Discussion and Analysis of Financial Condition and Results of Operations | 63 | |||
| 91 | ||||
| 104 | ||||
| 114 | ||||
| 118 | ||||
| 125 | ||||
| 129 | ||||
Material United States Federal Income Tax Considerations for Holders | 143 | |||
| 148 | ||||
| 158 | ||||
| 158 | ||||
| 158 | ||||
| F-1 | ||||
i
ABOUT THIS PROSPECTUS
The registration statement on Form S-1 of which this prospectus forms a part and that we have filed with the U.S. Securities and Exchange Commission (the “SEC”), includes exhibits that provide more detail of the matters discussed in this prospectus. Neither we nor the underwriters have authorized anyone to provide you with different information or to make any representations other than those contained in this prospectus prepared by us or to which we have referred you. Neither we nor the underwriters take responsibility for, and can provide no assurance as to the reliability of, any other information that others may give you. Neither we nor the underwriters are making an offer of these securities in any jurisdiction where the offer is not permitted. The information in this prospectus or any amendment to this prospectus is accurate only as of its date, regardless of the time of delivery of this prospectus or any amendment to this prospectus, as applicable, or any sale of the shares of our Common Stock covered by this prospectus. Our business, financial condition, results of operations and prospects may have changed since that date. You should read this prospectus in its entirety before making an investment decision.
We may also provide a post-effective amendment to the registration statement to add information to, or update or change information contained in, this prospectus. Any statement contained in this prospectus will be deemed to be modified or superseded for purposes of this prospectus to the extent that a statement contained in such post-effective amendment modifies or supersedes such statement. Any statement so modified will be deemed to constitute a part of this prospectus only as so modified, and any statement so superseded will not be deemed to constitute a part of this prospectus. We urge you to carefully read both this prospectus and any applicable post-effective amendment to the registration statement together with the additional information to which we refer you in the section of this prospectus entitled “Where You Can Find More Information.” These documents contain important information that you should consider when making your investment decision.
This prospectus includes our trademarks, trade names and service marks, all of which are our property and are protected under applicable intellectual property laws. This prospectus also contains trademarks, trade names and service marks of other companies, which are the property of their respective owners. Solely for convenience, trademarks, trade names and service marks may appear in this prospectus without the ®, ™ and SM symbols, but such references are not intended to indicate, in any way, that we or the applicable owner forgo or will not assert, to the fullest extent permitted under applicable law, our rights or the rights of any applicable licensors to these trademarks, trade names and service marks. We do not intend our use or display of other parties’ trademarks, trade names or service marks to imply, and such use or display should not be construed to imply, a relationship with, or endorsement or sponsorship of us by, these other parties.
On January 24, 2023 (the “Closing Date”), as contemplated by, the Agreement and Plan of Merger, dated as of August 3, 2022 (the “Merger Agreement”), by and among Jack Creek Investment Corp., a Cayman Islands exempted company (“JCIC”), Wildfire New PubCo, Inc., a Delaware corporation and direct, wholly-owned subsidiary of JCIC (“Bridger”), Wildfire Merger Sub I, Inc., a Delaware corporation and direct, wholly-owned subsidiary of Bridger, Wildfire Merger Sub II, Inc., a Delaware corporation and direct, wholly-owned subsidiary of Bridger, Wildfire Merger Sub III, LLC, a Delaware limited liability company and direct, wholly-owned subsidiary of Bridger, Wildfire GP Sub IV, LLC, a Delaware limited liability company and direct, wholly-owned subsidiary of Bridger, BTOF (Grannus Feeder)—NQ L.P., a Delaware limited partnership, and Bridger Aerospace Group Holdings, LLC, a Delaware limited liability company (“Legacy Bridger”), consummated the transactions contemplated by the Merger Agreement (the “Business Combination”), whereby Bridger became a publicly traded company, with JCIC and Legacy Bridger becoming wholly-owned subsidiaries of Bridger. On the Closing Date, Bridger changed its name to Bridger Aerospace Group Holdings, Inc.
Unless the context indicates otherwise, references in this prospectus to the “Company,” “Bridger,” “we,” “us,” “our,” and similar terms refer to Bridger Aerospace Group Holdings, Inc., a Delaware corporation (formerly known as Wildfire New PubCo, Inc.), and its consolidated subsidiaries.
ii
MARKET AND INDUSTRY DATA
This prospectus includes, and any amendment to this prospectus may include, estimates regarding market and industry data and forecasts, which are based on our own estimates utilizing our management’s knowledge of and experience in, as well as from independent market research, industry and general publications and surveys, governmental agencies, publicly available information and research, surveys and studies conducted by third parties. Internal estimates are derived from publicly available information released by industry analysts and third-party sources, our internal research and our industry experience, and are based on assumptions made by us based on such data and our knowledge of our industry and market, which we believe to be reasonable. However, we cannot assure you that any third-party information, and therefore the information contained in this prospectus or any amendment to this prospectus that is derived therefrom, is accurate or complete. In addition, while we believe the industry and market data included in this prospectus is reliable and based on reasonable assumptions, such data involve material risks and other uncertainties and are subject to change based on various factors, including those discussed in the sections entitled “Risk Factors” and “Cautionary Statement Regarding Forward-Looking Statements.” These and other factors could cause results to differ materially from those expressed in the estimates made by the independent parties or by us.
iii
CAUTIONARY STATEMENT REGARDING FORWARD-LOOKING STATEMENTS
Certain statements included in this prospectus are not historical facts but are forward-looking statements, including for purposes of the safe harbor provisions under the United States Private Securities Litigation Reform Act of 1995. Forward-looking statements generally are accompanied by words such as “believe,” “may,” “will,” “estimate,” “continue,” “anticipate,” “intend,” “expect,” “should,” “would,” “plan,” “project,” “forecast,” “predict,” “positioned,” “potential,” “seem,” “seek,” “future,” “outlook,” “target,” and similar expressions that predict or indicate future events or trends or that are not statements of historical matters, but the absence of these words does not mean that a statement is not forward-looking. These forward-looking statements include, but are not limited to, (1) Bridger’s preliminary unaudited third quarter and year-to-date 2023 financial results, including anticipated revenue, net income and Adjusted EBITDA for the three-month and nine-month periods ended September 30, 2023; (2) Bridger’s updated full-year 2023 guidance, including projected revenue, net income and Adjusted EBITDA for the year ending December 31, 2023; (3) Bridger’s potential revenue, net income or loss, and Adjusted EBITDA for the fourth quarter of 2023, including the equivalent potential deployment of aircraft in Bridger’s fleet; (4) references with respect to anticipated expansion of Bridger’s operations and increased deployment of Bridger’s aircraft fleet, including references to Bridger’s pending Bighorn Acquisition and Spanish Super Scooper Acquisition (each as defined below), including the expected closing timing thereof and the anticipated benefits therefrom; (5) the anticipated demand for and expansion of Bridger’s operations, including for certain customers, and the underlying causes for such anticipated demand, as well as the amount of revenues that may be generated pursuant to any particular customer contract; (6) Bridger’s operations and performance; (7) Bridger’s business and growth plans; (8) the types of services Bridger may offer; and (9) Bridger’s capital expenditures and acquisitions strategies, including anticipated investments in additional aircraft, renovation and upgrade costs, capital resources, and research and development and the effect of these investments. These statements are based on various assumptions and estimates, whether or not identified in this prospectus, and on the current expectations of Bridger’s management and are not predictions of actual performance. These forward-looking statements are provided for illustrative purposes only and are not intended to serve as, and must not be relied on by any investor as, a guarantee, an assurance, a prediction or a definitive statement of fact or probability. Actual events and circumstances are difficult or impossible to predict and will differ from assumptions. Many actual events and circumstances are beyond the control of Bridger. These forward-looking statements are subject to a number of risks and uncertainties, including: changes in domestic and foreign business, market, financial, political and legal conditions; failure to realize the anticipated benefits of the Business Combination; failure to realize the anticipated benefits of any acquisitions; Bridger’s successful integration of the aircraft (including achievement of synergies and cost reductions); Bridger’s ability to successfully and timely develop, sell and expand its services, and otherwise implement its growth strategy; risks relating to Bridger’s ongoing operations and businesses, including information technology (“IT”) and cybersecurity risks, loss of requisite licenses, flight safety risks, loss of key customers and deterioration in relationships between Bridger and its employees, including as a result of any acquisition; risks related to increased competition; risks relating to potential disruption of current plans, operations and infrastructure of Bridger as a result of the consummation of the Business Combination or any acquisition; risks that Bridger is unable to secure or protect its intellectual property; risks that Bridger experiences difficulties managing its growth and expanding operations; the ability to compete with existing or new companies that could cause downward pressure on prices, fewer customer orders, reduced margins, the inability to take advantage of new business opportunities, and the loss of market share; the impact of the coronavirus (“COVID-19”) pandemic; the ability to successfully select, execute or integrate future acquisitions into the business, which could result in material adverse effects to operations and financial conditions; and those factors discussed in the section of this prospectus entitled “Risk Factors.” If any of these risks materialize or our assumptions prove incorrect, actual results could differ materially from the results implied by these forward-looking statements. The risks and uncertainties above are not exhaustive, and there may be additional risks that Bridger presently does not know or that Bridger currently believes are immaterial that could also cause actual results to differ from those contained in the forward-looking statements. In addition, forward-looking statements reflect Bridger’s expectations, plans or forecasts of future events and views as of the date of this prospectus. Bridger anticipates that subsequent events and developments will cause Bridger’s assessments to change. However, while Bridger may elect to update these forward-looking statements at some point in the future, Bridger specifically disclaims any obligation to do so. These forward-looking statements should not be relied upon as representing Bridger’s assessments as of any date subsequent to the date of this prospectus. Accordingly, undue reliance should not be placed upon the forward-looking statements contained in this prospectus.
iv
FREQUENTLY USED TERMS
“Amended and Restated Bylaws” means the Amended and Restated Bylaws of Bridger, dated as of January 24, 2023.
“Amended and Restated Charter” means the Amended and Restated Certificate of Incorporation of Bridger, dated as of January 24, 2023.
“Amended and Restated Registration Rights Agreement” means the Amended and Restated Registration Rights Agreement, dated as of January 24, 2023, by and among Bridger, JCIC Sponsor, the BTO Stockholders and certain stockholders of Legacy Bridger.
“Available Sponsor Shares” means the number of JCIC Class B Ordinary Shares to be held by JCIC Sponsor immediately prior to Closing in accordance with the following calculation: (i) if the amount remaining in the Trust Account was less than or equal to $50,000,000, after deducting all amounts payable in respect of the JCIC Shareholder Redemption, 4,275,000 JCIC Class B Ordinary Shares and (ii) if the amount remaining in the Trust Account was greater than $50,000,000, after deducting all amounts payable in respect of the JCIC Shareholder Redemption, a number of JCIC Class B Ordinary Shares equal to (A) 8,550,000, multiplied by (B) (1) the amount remaining in the Trust Account after deducting all amounts payable in respect of the JCIC Shareholder Redemption, divided by (2) $100,000,000; provided, that in no event would the Available Sponsor Shares exceed 8,550,000 JCIC Class B Ordinary Shares.
“Board” means the Bridger Board of Directors.
“Blackstone” means Blackstone Inc.
“Blocker” means BTOF (Grannus Feeder) – NQ L.P., a Delaware limited partnership.
“Bridger Management Stockholders” means Debra Coleman, a Legacy Bridger director, Dean Heller, a Legacy Bridger director, and Darren Wilkins, Legacy Bridger’s Chief Operating Officer.
“BTO Stockholders” means certain direct and indirect equityholders of Bridger Aerospace Group Holdings, LLC that are affiliates of Blackstone Inc.
“Cal Fire” means the California Department of Forestry and Fire Protection.
“Closing” means the closing of the Business Combination.
“DOI” means the Department of the Interior.
“DGCL” means the Delaware General Corporation Law.
“Earnout Shares” means the 855,000 shares of Common Stock received by JCIC Sponsor as merger consideration that are subject to forfeiture, which amount shall be equal to twenty percent (20%) of the Available Sponsor Shares, as more fully described in the section of this prospectus entitled “Certain Relationships and Related Person Transactions — Certain Relationships and Related Person Transactions – JCIC — Sponsor Agreement.”
“ESPP” means the Bridger Aerospace Group Holdings, Inc. 2023 Employee Stock Purchase Plan.
“Existing Warrant Agreement” means that certain Warrant Agreement, dated as of January 26, 2021, by and between JCIC and Continental Stock Transfer & Trust Company.
v
“Founder Stockholders” means the former direct and indirect equityholders of Bridger Element LLC.
“JCIC” means Jack Creek Investment Corp., a special purpose acquisition company which participated in the Business Combination with Bridger and Legacy Bridger”.
“JCIC Board” means the board of directors of JCIC.
“JCIC Class A Ordinary Share” means the JCIC’s Class A ordinary shares, par value $0.0001 per share.
“JCIC IPO” means JCIC’s initial public offering, which was consummated on January 26, 2021.
“JCIC Shareholder Redemption” means the offer to redeem JCIC Class A Ordinary Shares in connection with the solicitation of proxies for the approval of the Business Combination, as contemplated by JCIC’s Amended and Restated Memorandum and Articles of Association, as amended from time to time.
“JCIC Sponsor” means JCIC Sponsor LLC, a Cayman Islands exempted limited partnership.
“JCIC Sponsor Agreement” means that certain agreement, dated as of August 3, 2022, by and among JCIC, JCIC Sponsor, each of the officers and directors of JCIC (collectively, the “Sponsor Persons”) and Bridger.
“JCIC Units” means the 34,500,000 units originally issued and outstanding in connection with JCIC’s initial public offering, each of which originally consisted of one JCIC Class A Ordinary Share, and one-half of one redeemable warrant of JCIC, each whole warrant entitling the holder thereof to purchase one JCIC Class A Ordinary Share at an exercise price of $11.50 per share.
“JCIC Warrants” means the 26,650,000 warrants to purchase one JCIC Class A Ordinary Share at an exercise price of $11.50 originally issued in connection with JCIC’s initial public offering.
“Legacy Bridger Class A Common Shares” are to Class A common shares of Legacy Bridger, which were converted into Common Stock at the Closing.
“Legacy Bridger Class B Common Shares” are to Class B common shares of Legacy Bridger, which were converted into Common Stock at the Closing.
“Legacy Bridger Class C Common Shares” are to Class C common shares of Legacy Bridger, which were converted into Common Stock at the Closing.
“Legacy Bridger Class D Common Shares” are to Class D common shares of Legacy Bridger, which were converted into Common Stock at the Closing.
“Legacy Bridger Common Shares” are to Class A, Class B, Class C and Class D common shares of Legacy Bridger, which were converted into Common Stock at the Closing.
“Legacy Bridger Equityholders” means (a) the holders of Legacy Bridger’s equity immediately prior to the Closing Date, which include Founder Stockholders, Bridger Management Stockholders, BTO Stockholders, and Series C Shareholders, except for Blocker and (b) Blocker’s equityholders, collectively
“Legacy Bridger incentive units” are to Legacy Bridger Class D Common Shares, which were converted into Common Stock upon the Closing.
“Legacy Bridger Series A Preferred Shares” means Legacy Bridger Series A-1 Preferred Shares and Legacy Bridger Series A-2 Preferred Shares.
vi
“Legacy Bridger Series A-1 Preferred Shares” means Series A-1 preferred shares of Legacy Bridger, which were fully redeemed prior to Closing.
“Legacy Bridger Series A-2 Preferred Shares” means Series A-2 preferred shares of Legacy Bridger, which were fully redeemed prior to Closing.
“Legacy Bridger Series B Preferred Shares” means Series B preferred shares of Legacy Bridger, which were fully redeemed prior to Closing.
“Legacy Bridger Series C Preferred Shares” means Series C preferred shares of Legacy Bridger, which were surrendered and exchanged into Bridger Series A Preferred Stock on a one-to-one basis in connection with the Business Combination.
“Nasdaq” means The Nasdaq Global Market.
“Nasdaq Listing Rules” means the rules and listing standards of Nasdaq.
“NCEI” means the National Centers for Environmental Information – National Oceanic and Atmospheric Administration.
“NIFC” means the National Interagency Fire Center.
“Omnibus Incentive Plan” means the Bridger Aerospace Group Holdings, Inc. 2023 Omnibus Incentive Plan.
“Preferred Stock” means preferred stock of Bridger, par value $0.0001 per share.
“Private Placement Warrants” means the 9,400,000 warrants to purchase a share of Common Stock at an exercise price of $11.50 per share, as further described the section of this prospectus entitled “Description of Securities — Warrants — Private Placement Warrants,” which were issued in exchange for the 9,400,000 JCIC Warrants originally purchased in a private placement by JCIC Sponsor at a purchase price of $1.00 per share contemporaneously with JCIC’s initial public offering.
“Promissory Note” means that certain Promissory Note, dated as of February 16, 2022, by and between JCIC Sponsor and JCIC.
“Public Warrants” means the 17,250,000 warrants to purchase a share of Common Stock at an exercise price of $11.50 per share, as further described the section of this prospectus entitled “Description of Securities — Warrants—Public Warrants,” which were issued in exchange for the 17,250,000 JCIC Warrants originally issued as part of the units JCIC issued in its initial public offering.
“Rule 144” means Rule 144 under the Securities Act.
“Securities Act” means the Securities Act of 1933, as amended from time to time.
“Series 2021 Bond” means the Gallatin County municipal bond historically issued by Legacy Bridger and that has been fully settled with the issuance of Series 2022 Bonds.
“Series 2022 Bonds” means the Gallatin municipal bond issuances by Bridger Aerospace Group Holdings, LLC totaling $160,000,000 of gross proceeds that closed in July and August 2022.
“Series A Preferred Stock” means the 1,000,000 shares of Preferred Stock that have the rights, powers, designations, preferences, and qualifications, limitations and restrictions set forth in Section 4.5 of the Amended and Restated Charter.
vii
“Stockholders Agreement” means that certain agreement, dated January 24, 2023, by and among the Company, the Founder Stockholders and the BTO Stockholders.
“Super Scooper” means a CL-215 or CL-415 aircraft.
“Transaction Agreements” means the Merger Agreement, JCIC Sponsor Agreement, the Stockholders Agreement and the Amended and Restated Registration Rights Agreement, in each case, including all annexes, exhibits, schedules, attachments and appendices thereto, and any certificate or other instrument delivered by any party to any other party pursuant to any of the foregoing.
“Trust Account” means the trust account that was established at the consummation of JCIC’s initial public offering and was maintained by Continental Stock Transfer & Trust Company, acting as trustee.
“Trust Amount” means the amount of cash that was available in the Trust Account as of the Closing Date, after deducting the amount required to satisfy JCIC’s obligations to its shareholders that exercised their redemption rights.
“USFS” means the United States Forest Service.
“Warrant Agreement” means the Existing Warrant Agreement as assumed by the Company by virtue of the Warrant Assumption Agreement.
“Warrant Assumption Agreement” means the Warrant Assumption Agreement, dated January 24, 2023, by and among JCIC, the Company and Continental Stock Transfer & Trust Company.
“Warrants” means the Public Warrants and Private Placement Warrants.
“Warrant Agent” means Continental Stock Transfer & Trust Company.
“Warrant Holders” means the holders of the Warrants.
“Wildland-urban interface” or “WUI” means the areas in which human development meets or intermingles with undeveloped wildland and vegetative fuels that are both fire-dependent and fire-prone.
viii
PROSPECTUS SUMMARY
This summary highlights information contained in greater detail elsewhere in this prospectus. Because it is a summary, it may not contain all of the information that may be important to you. To understand this offering fully, you should read this entire document carefully, including the information set forth under the sections of this prospectus entitled “Risk Factors,” “Cautionary Statement Regarding Forward-Looking Statements,” “Business,” and “Management’s Discussion and Analysis of Financial Condition and Results of Operations” and the consolidated financial statements and related notes included elsewhere in this prospectus before making an investment decision.
Overview of the Company
Bridger provides aerial wildfire surveillance, relief and suppression and aerial firefighting services using next-generation technology and environmentally friendly and sustainable firefighting methods primarily throughout the United States. Our mission is to save lives, property and habitats threatened by wildfires, leveraging our high-quality team, specialized aircraft and innovative use of technology and data. We are meeting an underserved and growing need for next-generation full-service aerial firefighting platforms.
Bridger was founded by our Chief Executive Officer and former Navy SEAL officer Timothy Sheehy, in Bozeman, Montana in 2014 with one aircraft and a vision to build a global enterprise to fight wildfires. Bridger has since grown into a full-spectrum aerial firefighting service provider in the U.S. and in the field of aerial wildfire management, offering technology and services to provide front-line firefighters and fire suppression decision-makers access to key fire data in order to effectively combat wildfires. As of September 30, 2023, the Company has a team of 173 employees and has developed an ecosystem of solutions, services and technologies supporting firefighting ground crews and the public.
Wildland-urban interface has grown by more than 179 thousand square kilometers in the U.S. from 1980 to 2020, according to a 2022 article by the USFS. WUI areas, which comprise 9.4% of the U.S. land area, now include nearly one-third of all residences, according to a 2022 article by the USFS. At the same time, the annual acres burned per fire between 1985 and 2020 have increased by nearly five-fold according to data published by the NIFC. As the WUI areas continue to grow and wildfires grow larger, more aggressive firefighting strategies are necessary to ensure public safety. Additionally, data published by the NIFC shows that the total number of U.S. acres burned annually has increased more than three-fold from 1985 to 2020.
These trends have led to a response by the U.S. federal government to increase spending on fire suppression since 1985 with a compound annual growth rate of 8.4% to $4.4 billion in 2021, according to the NIFC Suppression Costs Data. Even with this increased spending and demand, unfulfilled requests for fixed wing aircraft for aerial firefighting grew at a compound annual growth rate of 4.7% between 2002 and 2022, with 654 unfulfilled requests in 2022, according to the National Interagency Coordination Center.
Bridger’s management estimates that aerial suppression spend represented approximately 42.7% of an estimated $21.9 billion firefighting market globally in 2021. There is a rapidly growing global need for fire suppression assets, and Bridger’s management believes that a shift away from ground services to air-based suppression has already commenced. The market is anticipated to continue to expand as wildfires rage across Europe and the U.S.
The Company’s executive office is located at 90 Aviation Lane, Belgrade, Montana 59714, and the Company’s phone number is (406) 813-0079. Our website address is www.bridgeraerospace.com. Information contained on our website or connected thereto does not constitute part of, and is not incorporated by reference into, this prospectus or the registration statement of which it is a part.
1
Recent Developments
Recent Acquisitions
The Bighorn Acquisition: On July 21, 2023, we entered into a Purchase and Sale Agreement (the “Bighorn Purchase Agreement”) through our subsidiary Bridger Bighorn, LLC with Robert Eisele and Christopher Eisele (the “Bighorn Sellers”), the owners of Big Horn Airways, Inc. (“Bighorn”), pursuant to which we agreed to acquire 100% of the outstanding equity interests of Bighorn (the “Bighorn Acquisition”). Pursuant to the terms and subject to the conditions of the Bighorn Purchase Agreement, upon the closing of the Bighorn Acquisition, we will acquire Bighorn’s fleet of 12 aircraft used for wildfire smoke jumping, as well as special mission transport and delivery for government customers.
The aggregate consideration for the Bighorn Acquisition is $39.25 million, with $14.75 million payable in unregistered shares of Common Stock, and the remainder of $24.50 million payable in cash, as may be adjusted pursuant to the terms of the Bighorn Purchase Agreement, including for Bighorn’s cash, indebtedness, and net working capital as of the closing of the Bighorn Acquisition. The total number of shares of Common Stock issuable to the Bighorn Sellers at the closing of the Bighorn Acquisition is 2,219,467 (determined based upon a 60-day volume-weighted average per-share price (VWAP) of Common Stock, consisting of the 30 consecutive trading days ending on the trading day immediately preceding July 21, 2023 and the 30 consecutive trading days beginning on July 21, 2023).
The Common Stock consideration will be subject to transfer restrictions for a three-year period post-Closing, with 1/36th of the total shares of Common Stock issued to the Bighorn Sellers vesting each month over such three-year period.
The consummation of the Bighorn Acquisition is expected to be completed in the first half of the fourth quarter of 2023, subject to the satisfaction or waiver of customary closing conditions, including the payment of the approximately $24.50 million cash consideration to the Bighorn Sellers. The Bighorn Purchase Agreement may be terminated under certain customary and limited circumstances at any time prior to the closing of the Bighorn Acquisition, including by mutual written consent, and will automatically terminate if the closing of the Bighorn Acquisition does not occur on or before January 31, 2024.
The Bighorn Purchase Agreement contains customary representations, warranties, covenants, and post-closing indemnification obligations of the parties thereto. The Bighorn Sellers have agreed to certain customary non-competition and non-solicitation covenants for a period of five (5) years following the closing of the Bighorn Acquisition.
The foregoing description of the Bighorn Purchase Agreement is not complete and is qualified in its entirety by reference to the copy of the Bighorn Purchase Agreement filed as Exhibit 2.2 to the registration statement of which this prospectus forms a part.
The Ignis Acquisition: On September 12, 2023, we acquired 100% of the outstanding equity interests of Ignis Technologies, Inc. (“Ignis” and the “Ignis Acquisition”). The aggregate consideration for the Ignis Acquisition was $12.0 million, payable in unregistered shares of Common Stock, consisting of $3 million payable at the closing of the Ignis Acquisition and $9.0 million of contingent earn-out consideration. At the closing of the Ignis Acquisition, 426,531 restricted shares of Common Stock were issued to the Ignis shareholders (with the price per share determined based on the VWAP of the Common Stock for the 30 consecutive trading days ended September 11, 2023). The remaining $9.0 million of Common Stock consideration is contingent upon the achievement of certain operational milestones and, assuming achievement of such milestones, including the successful completion of certain software integration with FireTRAC, will be issued to the Ignis shareholders in 2024, 2025 and 2026, with the price per share determined based upon a trailing
2
120-day VWAP of the Common Stock at the time of each issuance. All of the shares of Common Stock issued and issuable in the Ignis Acquisition are subject to transfer restrictions for a 12-month period after each issuance, with 1/12th of the total shares of Common Stock vesting each month after each issuance.
All of the shares issued and issuable in both the Bighorn Acquisition and the Ignis Acquisition are being issued in reliance on the exemption from registration pursuant to Section 4(a)(2) of the Securities Act. Recipients of shares of Common Stock in both the Bighorn Acquisition and the Ignis Acquisition are entitled to customary resale registration rights with respect to such shares pursuant to the terms and conditions of the respective acquisition agreements.
The Spanish Super Scooper Acquisition: On September 20, 2023, we announced that our bid (via a public tender process) to purchase four Canadair CL-215T Amphibious Aircraft from the Spanish Ministry for Ecological Transition and Demographic Challenge had been accepted by the Spanish government (the “Spanish Super Scooper Acquisition”). Per the terms of the bid, we will purchase the four Super Scoopers from the Spanish government for approximately €40.3 million (approximately $42.5 million as of October 16, 2023) in cash. The closing of the Spanish Super Scooper Acquisition is expected to be completed in the first half of the fourth quarter of 2023 and is subject to the terms and conditions of the Spanish public tender process. Upon completion, Bridger plans to move the first Super Scooper to a Maintenance, Repair and Overhaul (“MRO”) facility for overhaul work resulting in an anticipated return-to-service for the second half of the 2024 North America fire season. The second Super Scooper is planned to be moved to an MRO facility in the first half of 2024 for an anticipated return-to-service for the 2025 North America fire season. The remaining two Super Scoopers will follow with an anticipated return-to service for the 2026 North America fire season. Bridger’s management team estimates that the cost to renovate and upgrade these Super Scoopers will be approximately $8 million to $12 million per airframe. These modified Super Scoopers are expected to generate revenue and Adjusted EBITDA in-line with Bridger’s current fleet of Super Scoopers once contracting mechanics are negotiated with various foreign governments during their respective return-to-service timeframes.
Preliminary Third Quarter 2023 Financial Results
Bridger’s “Super Scooper” fleet experienced its highest level of utilization during the third quarter of 2023.
For the quarter ended September 30, 2023, Bridger’s revenue is expected to be approximately $51 million to $55 million, net income is estimated to range between approximately $15 million and $19 million and Adjusted EBITDA is estimated to range between approximately $36 million and $40 million. This is the best quarter in Bridger’s history. By comparison, for the quarter ended September 30, 2022, Bridger’s revenue was $32.5 million, net loss was $5.6 million and Adjusted EBITDA was $19.2 million.
For the nine-month period ended September 30, 2023, Bridger’s revenue is expected to be approximately $63 million to $67 million, net loss is estimated to range between approximately $45 million and $49 million and Adjusted EBITDA is estimated to range between approximately $26 million and $30 million, as compared to revenue of $45.3 million, net loss of $25.1 million, and Adjusted EBITDA of $12.3 million for the nine-month period ended September 30, 2022.
A definition of “Adjusted EBITDA” and reconciliations of Adjusted EBITDA to net income or net loss, as applicable, as determined in accordance with U.S. generally accepted accounting principles (“GAAP”), are set forth below under “—Non-GAAP Financial Measures.”
Despite the record quarterly results, the last two weeks of September were slower due to cooler, wet weather in the U.S. and Canada. As a result, to achieve the mid-point of Bridger’s previously announced 2023 guidance range of $84 million to $96 million in revenue and $37 million to $45 million in Adjusted EBITDA, Bridger
3
would need to generate approximately $25 million of revenue in the fourth quarter of 2023. This equates to approximately one deployment of Bridger’s six Super Scooper fleet for two-thirds of one month. Although historically Bridger’s fourth quarter tends to be slower than the second and third quarters due to the timing and duration of the North American fire season, some of the most destructive wildfires in U.S. history have occurred from October through December due to the strong seasonal Santa Ana winds experienced on the west coast of the United States.
The unaudited preliminary estimated financial results for the three and nine month periods ended September 30, 2023 included in this prospectus are preliminary and subject to change, and such changes may be material. These preliminary estimates represent Bridger’s management’s unaudited estimates as of the date of this prospectus and are based upon a number of assumptions that are inherently uncertain. Bridger’s normal reporting processes with respect to the foregoing preliminary estimates have not been fully completed. During the course of Bridger’s and its independent auditors’ review of these preliminary estimates, Bridger could identify items that would require Bridger to make adjustments that could affect its subsequently reported results. Any such adjustments could be material. In light of the foregoing, investors are urged to put Bridger’s preliminary estimates in context and not to place undue reliance upon such preliminary estimates.
Non-GAAP Financial Measures
Although Bridger believes that net income or loss, as determined in accordance with GAAP, is the most appropriate earnings measure, Bridger uses EBITDA and Adjusted EBITDA as key profitability measures to assess the performance of its business. Bridger believes these measures help illustrate underlying trends in its business and uses the measures to establish budgets and operational goals, and communicate internally and externally, for managing its business and evaluating its performance. Bridger also believes these measures help investors compare Bridger’s operating performance with its results in prior periods in a way that is consistent with how management evaluates such performance.
Each of the profitability measures described below are not recognized under GAAP and do not purport to be an alternative to net income or loss determined in accordance with GAAP as a measure of Bridger’s performance. Such measures have limitations as analytical tools, and you should not consider any of such measures in isolation or as substitutes for Bridger’s results as reported under GAAP. EBITDA and Adjusted EBITDA exclude items that can have a significant effect on Bridger’s profit or loss and should, therefore, be used only in conjunction with GAAP profit or loss for the period. Bridger’s management compensates for the limitations of using non-GAAP financial measures by using them to supplement GAAP results to provide a more complete understanding of the factors and trends affecting the business than GAAP results alone. Because not all companies use identical calculations, these measures may not be comparable to other similarly titled measures of other companies.
Bridger does not provide a reconciliation of forward-looking measures where Bridger believes such a reconciliation would imply a degree of precision and certainty that could be confusing to investors and is unable to reasonably predict certain items contained in the GAAP measures without unreasonable efforts, such as acquisition costs, integration costs and loss on the disposal or obsolescence of aging aircraft. This is due to the inherent difficulty of forecasting the timing or amount of various items that have not yet occurred and are out of Bridger’s control or cannot be reasonably predicted. For the same reasons, Bridger is unable to address the probable significance of the unavailable information. Forward-looking non-GAAP financial measures provided without the most directly comparable GAAP financial measures may vary materially from the corresponding GAAP financial measures.
4
EBITDA and Adjusted EBITDA
EBITDA is a non-GAAP profitability measure that represents net income or loss for the period before the impact of the interest expense, income tax expense (benefit) and depreciation and amortization of property, plant and equipment and intangible assets. EBITDA eliminates potential differences in performance caused by variations in capital structures (affecting financing expenses), the cost and age of tangible assets (affecting relative depreciation expense) and the extent to which intangible assets are identifiable (affecting relative amortization expense).
Adjusted EBITDA is a non-GAAP profitability measure that represents EBITDA before certain items that are considered to hinder comparison of the performance of Bridger’s businesses on a period-over-period basis or with other businesses. During the periods presented, Bridger excludes from Adjusted EBITDA gains and losses on disposals of assets, legal fees and offering costs related to financing and other transactions, which include costs that are required to be expensed in accordance with GAAP. In addition, Bridger excludes from Adjusted EBITDA non-cash stock-based compensation and business development expenses. Bridger’s management believes that the inclusion of supplementary adjustments to EBITDA applied in presenting Adjusted EBITDA are appropriate to provide additional information to investors about certain material non-cash items and about unusual items that Bridger does not expect to continue at the same level in the future.
The following table reconciles net loss, the most directly comparable GAAP measure, to EBITDA and Adjusted EBITDA for the three and nine months ended September 30, 2022.
| Nine Months Ended | Three Months Ended | |||||||
| (Unaudited, $ in Millions) | September 30, 2022 | September 30, 2022 | ||||||
Net loss | $ | (25.1 | ) | $ | (5.6 | ) | ||
Depreciation and amortization | 8.6 | 4.5 | ||||||
Interest expense | 13.1 | 7.0 | ||||||
|
|
|
| |||||
EBITDA | (3.4 | ) | 5.9 | |||||
Loss on disposals and non-cash impairment(1) | 1.6 | 0.8 | ||||||
Offering costs(2) | 2.6 | 1.4 | ||||||
Loss on extinguishment of debt(3) | 0.8 | 0.8 | ||||||
Discretionary bonuses to employees and executives(4) | 10.1 | 10.1 | ||||||
Business development expenses(5) | 0.6 | 0.2 | ||||||
|
|
|
| |||||
Adjusted EBITDA | $ | 12.3 | $ | 19.2 | ||||
|
|
|
| |||||
| (1) | Represents loss on the disposal or obsolescence of aging aircraft and non-cash impairment charges on a retired aircraft. |
| (2) | Represents one-time professional service fees related to the preparation for the business combination that have been expensed during the period. |
| (3) | Represents loss on extinguishment of debt related to the Series 2021 Bond and forgiveness of the Paycheck Protection Program (“PPP”) loan. |
| (4) | Represents one-time discretionary bonuses to certain employees and executives of Bridger in connection with the issuance of the Legacy Bridger Series C Preferred Shares, the issuance of the Series 2022 Bonds, execution of the Transaction Agreements and the initial filing of the proxy statement/prospectus prepared in connection with the Business Combination. |
| (5) | Represents expenses related to potential acquisition targets and additional business lines. |
5
The following table reconciles net income (loss), the most directly comparable GAAP measure, to EBITDA and Adjusted EBITDA for the three and nine months ended September 30, 2023.
| Preliminary Unaudited Results (Three Months Ended September 30, 2023 ) | Preliminary Unaudited Results (Nine Months Ended September 30, 2023 ) | |||||||||||||||
| (Unaudited, $ in Millions) | Low | High | Low | High | ||||||||||||
Net income (loss) | $ | 15.0 | $ | 19.0 | $ | (48.7 | ) | $ | (44.7 | ) | ||||||
Depreciation and amortization | 6.4 | 6.4 | 11.4 | 11.4 | ||||||||||||
Interest expense | 5.7 | 5.7 | 16.9 | 16.9 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
EBITDA | 27.1 | 31.1 | (20.5 | ) | (16.5 | ) | ||||||||||
Loss on disposals and non-cash impairment(1) | 0.0 | 0.0 | 1.1 | 1.1 | ||||||||||||
Offering costs(2) | 0.0 | 0.0 | 3.3 | 3.3 | ||||||||||||
Stock-based compensation expense(3) | 7.7 | 7.7 | 40.3 | 40.3 | ||||||||||||
Business development expenses(4) | 1.4 | 1.4 | 2.3 | 2.3 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Adjusted EBITDA | $ | 36.2 | $ | 40.2 | $ | 26.4 | $ | 30.4 | ||||||||
|
|
|
|
|
|
|
| |||||||||
| (1) | Represents loss on the disposal or obsolescence of aging aircraft and non-cash impairment charges on a retired aircraft. |
| (2) | Represents one-time professional service fees related to the preparation for the Business Combination that have been expensed during the period. |
| (3) | Represents stock-based compensation expense recognized of the incentive units granted to selected board members and executives. |
| (4) | Represents expenses related to potential acquisition targets and additional business lines. |
New Contracts
In September 2023, Bridger was awarded a 10-year air attack contract for up to $166 million from the USFS to provide various fixed wing missions for aerial supervision, incident awareness, fire detection and reconnaissance. Additionally, in July 2023 Bridger was awarded separate contracts for up to $68 million with the U.S. Department of the Interior.
Our Services
Our portfolio is organized across two core offerings:
| • | Fire Suppression: Consists of deploying specialized Super Scooper aircraft to drop large amounts of water quickly and directly on wildfires. |
| • | Aerial Surveillance: Consists of providing aerial surveillance for fire suppression aircraft over an incident and providing tactical coordination with the incident commander. Aerial surveillance uses both manned aircraft and unmanned aircraft. |
6
Key Market Drivers and Opportunities
There are several key market drivers and opportunities for our business, including:
Longer and more severe fire seasons drive demand for fire suppression and aerial surveillance services
NIFC Suppression Costs Data supports that the acreage burned in the U.S. has increased over time. While there is variability in the acreage burned in any given year, the annual average of 7.0 million acres burned since 2000 has more than doubled the annual average acreage burned in the 1990s of 3.3 million. The year 2020 was one of the most intense fire years recorded in U.S. history with over 10.1 million acres burned.
While the North American wildfire off-season is typically between November and April, fires are starting earlier in the spring and lasting deeper into the fall according to a 2023 article by the EPA. The U.S. fire season is also lengthening on a consistent basis – according to a 2016 article by Climate Central, the U.S. fire season is on average 105 days longer than it was in 1970. Climate Central also reported that the average number of large fires (larger than 1,000 acres) burning each year had tripled between the period of the 1970s to the 2010s, and the acres burned by such fires showed a six-fold increase in the 2010s compared to the 1970s. Climate Central attributes the lengthening wildfire season to factors including warmer springs, longer summer dry seasons and drier soils and vegetation, with climate change threatening to increase the extent and severity of these fires. The United States national fire preparedness level has increased over time. The five preparedness levels range from the lowest (1) to the highest (5) and are dictated by fuel and weather conditions, fire activity, and fire suppression resource availability throughout the country. Level 5 represents that several geographic areas are experiencing large, complex wildland fire incidents, which have the potential to exhaust national wildland firefighting resources, while Level 1 represents there is very minimal fire activity. According to data provided by the NIFC, the average U.S. fire preparedness level during the main wildfire season (June through September) has increased over time by almost half of a level: during the past five years (2018 – 2022) the average U.S. fire preparedness level was 3.24, while the average U.S. fire preparedness level since 1990 was 2.80.
Increasing federal and state funding for wildfire control
National funding for wildfire management is appropriated by U.S. Congress and each state pays for wildland firefighting slightly differently. While fire suppression activities on wildlands in the U.S. are financed through federal funds, budget-making processes may restrict the amount allocated. According to the NIFC Suppression Costs Data, federal government fire suppression spending in 2021 increased by 93.0% from 2020 to $4.4 billion. The funding is allocated to the DOI and the USFS. Our company then enters into short, medium and long-term contracts with federal agencies during the firefighting season. Additionally, on the state level, we are generally seeing significant increases in several state governments and private entities who are preparing themselves for the new fire reality. For example, in December 2022, the federal government announced the allocation of an additional $228.0 million in fiscal year 2023 to wildfire mitigation efforts, and Washington State invested $328.0 million over the five following years to fight wildfires. While this level of commitment is unique, it is reflective of the increased awareness across many levels of government and private entities that wildfire risk has entered a new era of severity.
Given our long-standing customer relationships with governmental bodies, we have an opportunity to fulfill this increased demand for firefighting services driven by longer and more severe fire seasons. We view the increased demand as a means to further government agency ties and to capitalize on new aircraft investments.
Increased demand and limited supply of purpose-built suppression aircraft
According to the reports published by the National Interagency Coordination Center, demand for Type 3 multi-engine airtankers, which includes the Super Scooper aircraft, increased by over 56% for the two-year
7
period of 2021 and 2022 compared to the prior two-year period of 2019 and 2020. The Wildland Fire Reports showed that the increase in demand led to a higher percentage of unfulfilled requests, and in 2022, 34.9% of Type 3 multi-engine airtankers requests were unfulfilled compared to 8.9% in 2020. Super Scoopers are multi-engine airtankers built specifically for aerial firefighting. They are highly effective at fighting fires and have historically been owned and operated by foreign governments throughout Europe (there are approximately 40 amphibious scooping aircraft owned by France, Greece, Italy and Spain) and as a result, used amphibious scooping aircraft are difficult to locate and obtain in the United States. We are an original customer for LAS’ launch of their Super Scooper CL-415EAF (Enhanced Aerial Firefighter) Program. Longview Aviation Services (“LAS”) has only made a limited number of new Super Scoopers available for sale between 2020 and 2025, and pursuant to our purchase agreement with LAS and Viking Air Limited (“Viking”), dated April 13, 2018 (as amended and supplemented from time to time, the “LAS Purchase Agreement”), which has been amended numerous times to add additional planes and upgrades, we agreed to purchase six of the limited number of Super Scoopers. On February 17, 2023, we received our sixth Super Scooper, which will allow greater deployment of the Bridger aircraft fleet across the U.S. As we are a long-standing customer of LAS, and as LAS develops their next generation of aerial firefighting solutions, our continuous feedback informs advancements in firefighting technology.
Given the limited supply of purpose-built multi-engine airtankers, upkeep and maintenance of existing aircraft is vital to minimize lapses in firefighting services occurring during wildfire season and to reduce the impact of any disruptions that occur. The Super Scooper is the only aerial fire suppression aircraft with factory original equipment manufacturer (“OEM”) support which aids in reducing downtime.
Our Competitive Strengths
Full spectrum of aerial firefighting services
We provide full-spectrum aerial firefighting services, offering both fire suppression and aerial surveillance services in the U.S. and internationally. We emphasize continued investment in new aerial surveillance and aerial fire suppression aircraft, as well as innovation in the realm of unmanned platforms. Our aerial surveillance fleet has evolved since our inception from a single aircraft and pilot to the fleet operated today. The diversity of our service offerings affords customers the opportunity to select the appropriate services for their specific needs.
Purpose-built aircraft that can drop higher volumes of water
Our six CL-415EAF Super Scooper aircraft are the latest model in the LAS production line and feature enhanced industry technology. Viking, a subsidiary of LAS, purchased the type certificate and is the OEM for the design of all the CL-215 and CL-415 models from Bombardier Aerospace. LAS then made significant improvements and introduced the CL-415EAF Super Scooper, which includes the following improvements over the CL-415:
| • | Higher cruising speed; |
| • | Improved air safety; |
| • | Latest-generation technological reliability; |
| • | New avionics and instrumentation; |
| • | More accurate water discharge technology; |
| • | Suitability for mountainous terrain; |
| • | STOL on asphalt, gravel and water; |
8
| • | Lower speed during water-bombing (low and slow flight); |
| • | Improved operational efficiency; and |
| • | Structural integrity. |
The CL-415EAF Super Scooper leverages modern turbine engines to deliver superior high-altitude performance. The CL-415EAF Super Scooper is able to reload in under a minute, compared to a reload time of approximately 30 minutes to one hour, depending on base capabilities, for other air tankers enabling the CL-415EAF Super Scooper to make more drops in the same amount of time. The CL-415EAF Super Scooper can drop approximately 50,000 gallons before requiring refueling, while the largest tanker in the market can only drop 30 thousand gallons of retardant before needing to refuel and reload retardant. The Super Scooper aircraft allow for rapid delivery of water strikes to extinguish wildfires, particularly when deployed in tandem or larger groups to allow for continuous water-delivery as aircraft return to the water source.
Highly-skilled crew of pilots and maintenance personnel
As of September 30, 2023, we have 18 captains on staff as part of the Super Scooper flight crew. Each captain has thousands of hours of flight time in the Super Scooper conducting firefighting operations. All flight crew have a minimum of four years of aerial firefighting experience. Recurrent training for all flight crew is required in a Level D full motion flight simulator.
Each of our pilots attends annual and recurrent training specific to the aircraft they operate and to meet our standards of safety and standard operating procedures. Each pilot that flies an aircraft on contract for a government agency receives a certification card on an annual basis that validates they are qualified by the government to safely operate the aircraft while on contract.
As of September 30, 2023, we have 13 crew chiefs on staff as part of the Super Scooper maintenance crew. Each crew chief has thousands of hours maintaining aircraft in the Viking family and are familiar with firefighting operations. Factory training is mandatory for all of the maintenance team specific to the aircraft and components they maintain. They are also required to complete company-specific training courses regarding safety, standard operating procedures and systems in which they track and sign-off on maintenance logs.
Long-standing client relationships
We have provided aerial firefighting services for six years to government agencies, including the USFS, Cal Fire and multiple other state governments. The Company was awarded the first contract by the DOI to operate a fleet of UAS on-call over active wildfires throughout the U.S. We have been praised as an industry leader, specifically by the USFS, with regards to the SMS program and have been recommended by the USFS as a model for safe aircraft operations. Currently, we maintain active contracts with multiple federal agencies and the state governments of many high wildfire risk states, and we have a 100% renewal rate on our federal and state contracts. We bid upon and were awarded a USFS multi-year contract beginning with the 2021 fire season through the beginning of the 2025 fire season for the use of our Super Scooper planes.
Our relationship with the USFS involves three material service agreements: Contract No. 1202SA21T9009, dated as of June 3, 2021 (“Call-When-Needed Water Scooper Contract”), Contract No. 12024B19C9025, dated as of May 15, 2019 (“Exclusive Use Light Fixed Wing Contract”), and Contract No. 1202SA21G5100, dated as of February 22, 2021 (“Call-When-Needed Light Fixed Wing Contract”). Under the Call-When-Needed Water Scooper Contract, we provide Super Scooper aircraft services for wildland firefighting on a national basis for a period of four years from June 3, 2021. We generate revenue under the Call-When-Needed Water Scooper Contract from task orders placed by the USFS. Under the terms of the Call-When-Needed Water Scooper
9
Contract, the USFS reserves the right to terminate the Call-When-Needed Water Scooper Contract, or any part thereof, for its sole convenience or in the event of any default by us. Under the Exclusive Use Light Fixed Wing Contract, we provide light fixed wing aircraft firefighting services on an exclusive use basis for the Northern, Rocky Mountain, Southwestern, Intermountain and Pacific Southwest regions, as defined by the U.S. Department of Agriculture. The original term of the Exclusive Use Light Fixed Wing Contract was for 12-months from May 15, 2019; however, the contract included an option to extend the contract for four additional periods of one year each, and the USFS has exercised its annual option to extend the contract for 12-month periods on each of March 18, 2020, April, 21, 2021, April 18, 2022 and March 14, 2023. We generate revenue under the Exclusive Use Light Fixed Wing Contract by providing guaranteed availability of our services for 120 calendar days per year, with different rates charged for standby hours and flight hours. Under the terms of the Exclusive Use Light Fixed Wing Contract, the USFS reserves the right to terminate the Exclusive Use Light Fixed Wing Contract, or any part thereof, for its sole convenience or in the event of any default by us. Under the Call-When-Needed Light Fixed Wing Contract, we provide light fixed wing aircraft firefighting services, on a call-when-needed basis, for the air tactical group supervision mission on behalf of the Northern Region, as defined by the USFS. The term of the Call-When-Needed Light Fixed Wing Contract is for a period of four years. We generate revenue under the Call-When-Needed Light Fixed Wing Contract by providing our services when called upon by the USFS, if available at time of call, with different rates charged for standby hours and flight hours. Under the terms of the Call-When-Needed Light Fixed Wing Contract, the USFS reserves the right to terminate the Call-When-Needed Light Fixed Wing Contract, or any part thereof, for its sole convenience or in the event of any default by us. In September 2023, Bridger was awarded a 10-year air attack contract for up to $166 million from the USFS to provide various fixed wing missions for aerial supervision, incident awareness, fire detection and reconnaissance.
Our Growth Strategy
Acquire and deploy additional aircraft to meet increased demand
We are an original customer for LAS’s launch of its Super Scooper CL-415EAF Program. There are approximately 40 amphibious scooping aircraft owned by France, Greece, Italy and Spain and as a result, used amphibious scooping aircraft are difficult to locate and obtain. LAS has only made a limited number available for sale between 2020 and 2025, and we agreed to purchase six of this limited number.
Expanding our services
Fire Monitoring Technology: With roughly 70,000 wildfires occurring each year in the U.S. (according to the NIFC Suppression Costs Data), news feeds are saturated with reports of wildfires that have grown quickly and are out of control. Current consolidated fire data is controlled by wildfire agencies with limited to no access publicly available. We launched FireTRAC in April 2022 to provide a resource to the general public in easy to use mobile and web applications. FireTRAC notifies users of potential fire danger and provides maps and high-resolution photo overlays so users can learn where the fires are located and find safety. FireTRAC provides near real-time data directly to citizens, landowners, insurance companies, utilities, municipal and county governments and potentially federal agencies. The app provides consolidated information, imagery and data regarding critical wildfire incidents in a seamless and user-friendly interface. The app puts this critical information in one place, providing rapid updates and building a user community along the way.
Maintenance, Repair, Overhaul: We have an experienced and well-trained crew of maintenance professionals. Maintenance personnel and their maintenance support staff are current on all general aviation standards and requirements and are specifically trained to service our fleet of aircraft. We ensure our maintenance team has all the necessary equipment needed to exceed FAA maintenance standards and maintain USFS and DOI contract aircraft requirements. We are a FAA Certified Part 145 Repair Station offering Airframe and Avionics repair capabilities for the Aerial Firefighting Fleet. In April 2022, our Part 145 Certified Repair
10
Station was awarded an ISO 9110, certification which is one of the highest standards in a repair organization recognized by the FAA. This certification was completed by the British Standards Institution, recognized as an industry leader in quality management systems.
Domestic and international expansion
We are committed to increasing our market share and service offering domestically. Given our competitive strengths, we believe we are well-positioned to take advantage of the growth in domestic demand for fire safety and environmental awareness. We currently have contracts in place with the USFS, the DOI, Washington State Department of Natural Resources, Alaska Department of Natural Resources, Cal Fire, Colorado Department of Public Safety, Minnesota Department of Natural Resources, Montana Department of Natural Resources and Conservation, Nevada Department of Conservation and Natural Resources, and Oregon Department of Forestry.
We intend to penetrate certain additional domestic markets through leveraging existing relationships and building local market teams. We have established this historically by maintaining relationships in the field with customers, gathering near real-time feedback to improve operations, as well as holding regular feedback sessions to incorporate points of improvement and planning for subsequent years.
We are exploring the possibility of operating internationally during the North American wildfire off-season, which generally occurs between November and April. We seek to become a global entity that provides aerial firefighting services worldwide. Our goal is to bring the Super Scooper to Europe, Asia and/or South America as our first international expansions in the future and to demonstrate the platform’s effectiveness. Currently, Super Scoopers are either not utilized on wildland fires in these areas or are not operated in a contractor-owned, contractor-operated business model. We plan to fill an underserved need to provide an alternative solution to aging and obsolete government-owned, government-operated fleets.
Pursuing Opportunistic M&A
We intend to continue to evaluate M&A opportunities to expand our fleet, add new geographies or add additional services. Consistent with this strategy, we regularly evaluate potential acquisition opportunities, including ones that would be significant to us. Currently, we are pursuing the Bighorn Acquisition and the Spanish Super Scooper Acquisition and have recently completed the Ignis Acquisition. We cannot predict the timing of any other contemplated transactions.
Summary Risk Factors
An investment in our Common Stock involves substantial risk. The occurrence of one or more of the events or circumstances described in the section of this prospectus entitled “Risk Factors,” alone or in combination with other events or circumstances, may have a material adverse effect on our business, cash flows, financial condition or results of operations. These risks include the following:
| • | Our operation of aircraft involves a degree of inherent risk, and we could suffer losses and adverse publicity stemming from any accident, whether related to us or not, involving aircraft, helicopters, or commercial drones similar to the assets we use in our operations. |
| • | Our business is inherently risky in that it is fighting wildfires which are powerful and unpredictable. |
| • | The unavailability of an aircraft due to loss, delayed delivery of new aircraft, maintenance failure, lack of pilots or mechanical personnel, especially a Super Scooper, would result in lower operating revenues for us for a period of time that would likely be prolonged, particularly as we lack diversification with respect to our fire suppression aircraft. |
11
| • | Our inability to source and hire personnel with appropriate skills and experience would inhibit operations. |
| • | The development of superior alternative firefighting tactics, technology or other businesses or government entities who provide the services we provide could reduce demand for our services. |
| • | A cyber-based attack of our IT systems could disrupt our ability to deliver services to our customers and could lead to increased overhead costs, decreased sales, and harm to our reputation. |
| • | Any failure to offer high-quality aerial firefighting services may harm relationships with our customers and could adversely affect our reputation, brand, business, financial condition, and results of operations. |
| • | We are subject to risks associated with climate change, including the potential increased impacts of severe weather events on our operations and infrastructure, and changes in weather patterns may result in lower demand for our services if such changes result in a reduced risk of wildfires. |
| • | We are highly dependent on our senior management team and other highly skilled personnel with unique skills. |
| • | There is a seasonal fluctuation in the need to fight forest fires based upon location, and a substantial majority of our revenue is currently concentrated in the Western United States. As a result, our operating results may fluctuate significantly from quarter to quarter and from year to year. |
| • | The aerial firefighting industry is expected to grow in the near future and is volatile, and if it does not develop, if it develops slower than we expect, if it develops in a manner that does not require use of our services, if it encounters negative publicity or if our solution does not drive commercial or governmental engagement, the growth of our business will be harmed. |
| • | We depend significantly on government customers, which subjects us to risks including early termination, audits, investigations, sanctions and penalties. We are also subject to regulations applicable to government contractors which increase our operating costs and if we fail to comply, could result in the termination of our contracts with government entities. |
| • | We may be unable to manage our future growth effectively, which could make it difficult to execute our business strategy. |
| • | We rely on a few large customers for a majority of our business, and the loss of any of these customers, or other adverse developments with respect to these customers could materially reduce our net income and operating results. |
| • | We rely on a limited number of suppliers for certain raw materials, supplied components and new CL-415EAF aircraft. We may not be able to obtain sufficient raw materials, supplied components or CL-415EAF aircraft to meet our maintenance or operating needs or obtain such materials on favorable terms or at all, which could impede our ability to increase our revenue and net income. |
| • | We currently rely and will continue to rely on third-party partners to provide and store the parts and components required to service and maintain our aircraft, and to supply critical components and systems, which exposes us to a number of risks and uncertainties outside our control. |
| • | We may require substantial additional funding to finance our operations and growth strategy, but adequate additional financing may not be available when we need it, on acceptable terms, or at all, and may depend in part on the market price of our Common Stock. |
| • | Our systems, aircraft, technologies and services and related equipment may have shorter useful lives than we anticipate. |
| • | We have a substantial amount of debt and servicing future interests or principal payments may require us to change our business strategy to accommodate the repayment of our debt. |
12
| • | We have incurred significant losses since inception, and we may not be able to achieve, maintain or increase profitability or positive cash flow. |
| • | The requirements of being a public company may strain our resources, divert our management’s attention and affect our ability to attract and retain additional executive management and qualified board members. |
| • | We have identified material weaknesses in our internal control over financial reporting, which we are in the process of, and focused on, remediating. |
| • | The sale and issuance of our Common Stock pursuant to this offering will cause dilution to purchasing stockholders. |
| • | Our management team will have broad discretion over the use of the net proceeds from this offering, and you may not agree with how the proceeds are used and the proceeds may not be invested successfully. |
| • | The price of our Common Stock and Warrants are likely to be highly volatile. |
| • | Our Common Stock is subject to restrictions on ownership by non-U.S. citizens, which could require divestiture by non-U.S. citizen stockholders and could have a negative impact on the transferability of our Common Stock, its liquidity and market value, and such restrictions may deter a potential change of control transaction. |
| • | We may issue additional shares of our Common Stock or other equity securities, which would dilute your ownership interest in us and may depress the market price of our Common Stock. |
| • | There can be no assurance that we will be able to comply with Nasdaq’s continued listing standards. |
| • | The holders of shares of Series A Preferred Stock have rights, preferences and privileges that are not held by, and are preferential to, the rights of holders of our Common Stock. |
| • | A small number of our stockholders could significantly influence our business. |
| • | Warrants are exercisable for our Common Stock, and if exercised, will increase the number of shares eligible for future resale in the public market and result in dilution to our shareholders. |
| • | Future sales, or the perception of future sales, of a substantial number of shares of our Common Stock by us or our stockholders in the public market may cause the price of our Common Stock and Warrants to decline. |
| • | The COVID-19 pandemic or other future global health emergencies may materially and adversely impact our business. |
Implications of Being an Emerging Growth Company and a Smaller Reporting Company
The Jumpstart Our Business Startups Act (the “JOBS Act”) was enacted in April 2012 with the intention of encouraging capital formation in the United States and reducing the regulatory burden on newly public companies that qualify as emerging growth companies. We are an “emerging growth company” within the meaning of the JOBS Act. We may take advantage of certain exemptions from various public reporting requirements, including the requirement that we provide more than two years of audited financial statements and related management’s discussion and analysis of financial condition and results of operations, and that our internal control over financial reporting be audited by our independent registered public accounting firm pursuant to Section 404 of the Sarbanes-Oxley Act of 2002 (the “Sarbanes-Oxley Act”). In addition, the JOBS Act provides that an “emerging growth company” can delay adopting new or revised accounting standards until those standards apply to private companies. We intend to take advantage of these exemptions until we are no longer an emerging growth company. We have elected to use the extended transition period to enable us to comply with new or revised accounting standards that have different effective dates for public and private companies until the earlier of the date we (1) are no longer an emerging growth company and (2) affirmatively and irrevocably opt out of the extended transition period provided in the JOBS Act. As a result, our financial statements may not be
13
comparable to companies that comply with new or revised accounting pronouncements as of public company effective dates.
We will remain an emerging growth company until the earlier of (1) the last day of the fiscal year (a) following the fifth anniversary of the Closing (December 31, 2028), (b) in which we have a total annual gross revenue of at least $1.235 billion or (c) in which we are deemed to be a large accelerated filer, which means the market value of shares of our common stock that are held by non-affiliates exceeds $700.0 million as of the prior June 30, and (2) the date on which we have issued more than $1.0 billion in non-convertible debt during the prior three-year period. See the section of this prospectus entitled “Risk Factors — Risks Related to the Ownership of Our Securities.” We are an ‘emerging growth company,’ and any decision on our part to comply only with certain reduced reporting and disclosure requirements applicable to emerging growth companies could make our common stock less attractive to investors.
We are also a “smaller reporting company” as defined in Rule 12b-2 under the Exchange Act. We may continue to be a smaller reporting company even after we are no longer an emerging growth company. We may take advantage of certain reduced disclosure obligations, including, among other things, providing only two years of audited financial statements until the last day of the fiscal year in which (i) the market value of our common stock held by non-affiliates is greater than or equal to $250 million as of the end of that fiscal year’s second fiscal quarter, and (ii) our annual revenues are greater than or equal to $100 million during the last completed fiscal year or the market value of our common stock held by non-affiliates exceeds $700 million as of the end of that fiscal year’s second fiscal quarter.
14
THE OFFERING
Issuer | Bridger Aerospace Group Holdings, Inc. |
Common Stock offered by us, excluding underwriters’ option | shares. |
Underwriters’ option to purchase additional shares | We have granted the underwriters an option to purchase up to an additional shares of our Common Stock from us at the public offering price, less underwriting discounts and commissions, at any time within 30 days from the date of this prospectus. See the section of this prospectus entitled “Underwriting.” |
Common Stock outstanding immediately after the offering(1) | shares (or shares if the underwriters exercise their option to purchase additional shares in full). |
Use of Proceeds | We estimate that the net proceeds to us from the offering will be approximately $ million, or approximately $ million if the underwriters exercise their option to purchase additional shares in full, and, after deducting the underwriting discounts and commissions and estimated offering expenses payable by us. We intend to use the net proceeds of this offering to finance the cash purchase price for the Spanish Super Scooper Acquisition and the Bighorn Acquisition, and the remainder for general corporate purposes, including funding the upgrade costs for the acquired Super Scoopers and other working capital needs. See the section of this prospectus entitled “Use of Proceeds.” |
Risk Factors | Investing in our Common Stock involves substantial risks. See the section of this prospectus entitled “Risk Factors” and other information included in this prospectus for a discussion of factors that you should consider carefully before deciding to invest in our Common Stock. |
Lock-Up Agreements | We, our directors and officers and certain of our significant stockholders, have agreed with the underwriters not to offer for sale, issue, sell, contract to sell, pledge or otherwise dispose of any shares of our Common Stock or securities convertible into Common Stock for a period of 90 days from the date of this prospectus without the prior written consent of the representative of the underwriters. See the section of this prospectus entitled “Underwriting — Lock-Up Agreements.” |
NASDAQ Global Market Symbol | “BAER.” |
Dividend Policy | We have never declared or paid any dividends on our shares of our Common Stock. We do not anticipate declaring or paying any cash dividends on our Common Stock in the foreseeable future. See the section of this prospectus entitled “Market Information for Common Stock and Dividend Policy – Dividend Policy”. |
15
| (1) | The number of shares of Common Stock outstanding is based on the sum of (i) 44,776,926 shares of Common Stock as of September 30, 2023 and (ii) 2,400,355 shares issuable in respect of vested but unsettled RSUs, but excludes the following, in each case as of September 30, 2023, except as otherwise noted: |
| • | 9,400,000 shares of our Common Stock issuable upon the exercise of Private Placement Warrants, with an exercise price of $11.50 per share; |
| • | 17,249,874 shares of our Common Stock issuable upon the exercise of Public Warrants, with an exercise price of $11.50 per share; |
| • | 31,701,931 shares of our Common Stock that may be issuable upon the conversion of any shares of Series A Preferred Stock, at the election of the holders of the Series A Preferred Stock; |
| • | 14,362,583 shares of our Common Stock reserved for future issuance under the Omnibus Incentive Plan (inclusive of 6,789,763 RSUs that have been granted or promised prior to September 30, 2023 that are unvested); |
| • | 1,006,609 shares of our Common Stock reserved for future issuance under the ESPP; |
| • | $9.0 million of our Common Stock issuable to the former shareholders of Ignis as additional contingent consideration, subject to the achievement of certain operational milestones in 2024, 2025 and 2026 (with the number of shares based upon a trailing 120-day VWAP of the Common Stock at the time of each issuance); and |
| • | 2,219,467 shares of our Common Stock that would be issuable to the Bighorn Sellers upon closing of the Bighorn Acquisition. |
Unless indicated otherwise, all information in this prospectus assumes (1) no exercise of outstanding warrants or settlement of unvested RSUs referred to above; (2) no issuance of Common Stock upon conversion of the Series A Preferred Stock referred to above and (3) no exercise of the underwriters’ option to purchase additional shares of our Common Stock in this offering.
16
SUMMARY FINANCIAL DATA
The following tables present a summary of our historical financial results for the periods ended on and as of the dates indicated. We have derived the summary statements of operations data for the years ended December 31, 2021 and 2022 and the summary balance sheet data as of December 31, 2022 from our audited financial statements included elsewhere in this prospectus. We have derived the summary statements of operations data for the six months ended June 30, 2022 and 2023 and the summary balance sheet data as of June 30, 2023 from our unaudited condensed financial statements included elsewhere in this prospectus. The unaudited condensed financial statements have been prepared on a basis consistent with our audited financial statements included in this prospectus and, in the opinion of management, reflect all adjustments, consisting only of normal recurring adjustments, necessary to fairly state the financial information in those statements. You should read these data together with our financial statements and related notes included elsewhere in this prospectus and the section titled “Management’s Discussion and Analysis of Financial Condition and Results of Operations.” Our historical results for any prior period are not necessarily indicative of our future results, and in particular results for the six months ended June 30, 2023 are not necessarily indicative of our expected results for the year ending December 31, 2023.
17
The following table summarizes Bridger’s key operating measures for each period presented below, which are audited for the years ended December 31, 2022 and December 31, 2021 and unaudited for the six months ended June 30, 2023 and the six months ended June 30, 2022.
| (All amounts in U.S. dollars, in thousands except share and per share data) | Six Months Ended June 30, 2023 | Six Months Ended June 30, 2022 | Year Ended December 31, 2022 | Year Ended December 31, 2021 | ||||||||||||
Statements of Operations Data: | ||||||||||||||||
Total Revenues | $ | 11,981 | $ | 12,823 | $ | 46,388 | $ | 39,384 | ||||||||
Cost of revenues | ||||||||||||||||
Flight Operations | 10,032 | 9,515 | 18,762 | 15,824 | ||||||||||||
Maintenance | 7,727 | 6,434 | 15,124 | 10,755 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Total cost of revenues | 17,759 | 15,949 | 33,886 | 26,579 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Gross (loss) income | (5,778 | ) | (3,126 | ) | 12,502 | 12,805 | ||||||||||
Selling, general and administrative expense | 48,416 | 10,577 | 35,128 | 11,215 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Operating (loss) income | (54,194 | ) | (13,703 | ) | (22,626 | ) | 1,590 | |||||||||
Interest expense | (11,206 | ) | (6,008 | ) | (20,020 | ) | (9,294 | ) | ||||||||
Other income | 1,693 | 275 | 521 | 1,163 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Net loss | (63,707 | ) | (19,436 | ) | (42,125 | ) | (6,541 | ) | ||||||||
Series A Preferred Stock—adjustment for deemed dividend upon Closing | (48,300 | ) | — | — | — | |||||||||||
Series A Preferred Stock—adjustment to eliminate 50% multiplier | 156,363 | — | — | — | ||||||||||||
Series A Preferred Stock—adjustment to maximum redemption value | (10,080 | ) | — | — | — | |||||||||||
Legacy Bridger Series C preferred Shares adjustment to maximum value | — | (191,241 | ) | (202,689 | ) | — | ||||||||||
Legacy Bridger Series A Preferred Shares—adjustment for redemption, extinguishment and accrued interest | — | (85,663 | ) | (85,663 | ) | (15,913 | ) | |||||||||
|
|
|
|
|
|
|
| |||||||||
Net income (loss) attributable to Common Stockholders—basic and diluted | $ | 34,276 | $ | (296,340 | ) | $ | (330,477 | ) | $ | (22,454 | ) | |||||
|
|
|
|
|
|
|
| |||||||||
Net income (loss) per Common Stock—basic | $ | 0.77 | $ | (7.64 | ) | $ | (8.20 | ) | $ | (0.56 | ) | |||||
Net income (loss) per Common Stock—diluted | $ | 0.44 | $ | (7.64 | ) | $ | (8.20 | ) | $ | (0.56 | ) | |||||
The following table summarizes Bridger’s summary balance sheet as of June 30, 2023, which is unaudited.
| (All amounts in U.S. dollars, in thousands) | As of June 30, 2023 | As of December 31, 2022 | ||||||
Balance Sheet Data: | ||||||||
Cash, cash equivalents and marketable securities | $ | 13,418 | $ | 85,143 | ||||
Working Capital | 24,314 | 82,558 | ||||||
Total assets | 253,436 | 305,979 | ||||||
Redeemable preferred stock | 342,739 | 489,022 | ||||||
Total stockholder’s deficit | $ | (319,552 | ) | $ | (413,622 | ) | ||
18
RISK FACTORS
Investing in our Common Stock involves a high degree of risk. Before you make a decision to buy our Common Stock, in addition to the risks and uncertainties discussed above under “Cautionary Statement Regarding Forward-Looking Statements,” you should carefully consider the specific risks set forth herein together with all of the other information contained in this prospectus, including our financial statements and related notes appearing at the end of this prospectus. If any of these risks actually occur, it may materially harm our business, financial condition, liquidity and results of operations. As a result, the market price of our Common Stock could decline, and you could lose all or part of your investment. Additionally, the risks and uncertainties described in this prospectus or any amendment to this prospectus are not the only risks and uncertainties that we face. Additional risks and uncertainties not presently known to us or that we currently believe to be immaterial may become material and adversely affect our business. Unless the context otherwise requires, all references in this section to “Bridger,” the “Company,” “we,” “us,” “our,” and other similar terms refer to the business of Legacy Bridger and its subsidiaries prior to the Business Combination and Bridger Aerospace Group Holdings, Inc. and its subsidiaries following the Business Combination.
Aviation and Firefighting Risks
Our operation of aircraft involves a degree of inherent risk, and we could suffer losses and adverse publicity stemming from any accident, whether related to us or not, involving aircraft, helicopters, or commercial drones similar to the assets we use in our operations.
The operation of aircraft is subject to various risks, and demand for firefighting services, may in the future be impacted by accidents or other safety issues regardless of whether such accidents or issues involve Bridger flights, our aircraft operators, or aircraft flown by our aircraft operators. Air transportation hazards, such as adverse weather conditions and fire and mechanical failures, may result in death or injury to personnel and passengers which could impact client confidence in a particular aircraft type. Safety statistics for air travel are reported by multiple parties, including the Department of Transportation (the “DOT”) and National Transportation Safety Board, and are often separated into categories of transportation. Because our aerial firefighting services include a variety of aircraft, our clients may have a hard time determining how safe aerial firefighting services are, and their confidence in aerial firefighting may be impacted by, among other things, the classification of accidents in ways that reflect poorly on aerial firefighting services or the methods that aerial firefighting services utilize.
As the owners and operators of certain aircraft, including the CL-415EAFs, we believe that safety and reliability are two of the primary attributes that customers consider when selecting aerial firefighting services. Our failure to maintain standards of safety and reliability that are satisfactory to our customers may adversely impact our ability to retain current customers and attract new customers. We are at risk of adverse publicity stemming from any public incident involving our company, our people, or our brand. Such an incident could involve the actual or alleged behavior of any of our employees.
Increased accident history could bar us from certain contracts, thereby reducing demand for our services. Further, if our personnel or one of the aircraft models that is used by us is involved in a public incident, accident, catastrophe, or regulatory enforcement action, we could be exposed to significant reputational harm and potential legal liability. The insurance we carry may be inapplicable or inadequate to cover any such incident, accident, catastrophe, or action. In the event that our insurance is inapplicable or inadequate, we may be forced to bear substantial losses from an incident or accident. In addition, any such incident, accident, catastrophe, or action involving our employees or one of the aircraft models used by us could create an adverse public perception, which could harm our reputation, resulting in existing or potential customers being reluctant to use our services and adversely impacting our business, results of operations, and financial condition. If one or more of our operators were to suffer an accident or lose the ability to fly certain aircraft due to safety concerns or investigations, we may be required to cancel or delay certain aerial firefighting services until replacement aircraft and personnel are obtained.
19
Our operations may also be negatively impacted by accidents or other safety-related events or investigations that occur in or near the airports and the hangars we utilize for our aerial firefighting services. For example, if an accident were to occur at or near one of our hangars that rely on for certain flights, we may be unable to utilize that hangar until the accident has been cleared, any damages to the facilities have been repaired, and any insurance, regulatory, or other investigations have been completed. Similarly, an adverse safety event by a third-party with respect to the Super Scooper or any of the other planes in our fleet could result in temporary or permanent bans on certain aircraft models by our current or future customers.
Our business is inherently risky in that it is fighting wildfires which are powerful and unpredictable.
The performance of our services necessitates that we interact with wildfires. Wildfires can be massively unpredictable, and while we have implemented safety protocols and systems, these protocols and systems cannot eliminate the risk of accidents. Further, to effectively fight fires, flight operations often require low-level flights and involve performing services in mountainous terrain, both of which increase the risks involved with our services. To protect against these dangers, we may be required to incur more expenses and/or implement time-consuming safety protocols and systems, which could cause our expenses to be higher than anticipated. We may also be more likely to experience an adverse safety event.
The unavailability of an aircraft due to loss, delayed delivery of new aircraft, maintenance failure, lack of pilots or mechanical personnel, especially one of the Viking Air CL-415EAFs, would result in lower operating revenues for us for a period of time that cannot be determined and would likely be prolonged.
Aircraft loss for any reason could impact our ability to provide services. Short- or long-term unavailability of an aircraft may also result from an aging fleet or parts obsolescence. Replacement aircraft or replacement parts may not be available or only available with significant delays.
Our revenues are disproportionately derived from the services of our Super Scoopers. The unavailability of one or more of our Super Scoopers could result in a significant reduction in our revenues and adversely affect our results of operations. For example, in 2022, we experienced a delay with the delivery of our fifth and sixth Super Scooper aircraft and two Unmanned Aerial Systems (“UAS”) drones. We originally expected that the fifth Super Scooper, sixth Super Scooper, and the two UAS drones would be delivered in May 2022, July 2022 and May 2022, respectively, but ultimately, the delivery and subsequent preparation for deployment of the fifth Super Scooper was delayed until September 2022, the two UAS drones were delivered in October 2022 and the sixth Super Scooper was not delivered until February 2023. As a result of such delays, our results of operations for the 2022 wildfire season were materially affected. Additionally, only pilots with significant flight hours can operate Super Scoopers, and there is a limited number of available pilots due to the demanding levels of training. There is a limited number of Super Scoopers in operation globally. Certain replacement parts may be unavailable or difficult to obtain, and we may be unable to hire sufficient mechanics trained to service Super Scoopers.
Our pilots and mechanics are required by contract to meet a minimum standard of operational experience. Finding and employing individuals with the necessary level of experience and certification has required us to hire U.S. and Canadian personnel. Inability to source and hire personnel with appropriate skills and experience would inhibit operations.
Our business’s success depends on our continued ability to attract, retain, and motivate highly qualified personnel with experience in the aviation space, including pilots and mechanics. However, competition for qualified personnel is intense. Our business may not be successful in attracting qualified personnel to fulfill our current or future needs. In the event that we are unable to fill critical open employment positions, we may need to delay our operational activities and goals, including the development and expansion of our business, and may have difficulty in meeting our obligations as a public company.
20
In addition, competitors and others may attempt to recruit our employees. The loss of the services of any of our key personnel, the inability to attract or retain highly qualified personnel in the future or delays in hiring such personnel, particularly senior management, pilots, and other technical personnel, could materially and adversely affect our business, financial condition and results of operations. In addition, the replacement of key personnel likely would involve significant time and costs and may significantly delay or prevent the achievement of our business objectives.
The development of superior alternative firefighting tactics or technology that do not rely on our existing and planned capital assets could reduce demand for our services and result in a material reduction in our revenue and results of operations.
Our aircraft have been modified to deploy our technology and support our existing firefighting tactics to fight wildfires. In particular, the Super Scooper is specially designed to fight forest fires with water and to refill from open bodies of water. If new technology or firefighting tactics are created or discovered that provide more powerful, more economic, faster, safer, more environmentally friendly or services that are otherwise superior in certain aspects to our current services, then we may see reduced demand for our services or be required to incur additional costs to adapt our fleet to such technologies or firefighting tactics. Additionally, current and potential government customers may push towards contracting services from customers with modernized fleets. All of these changes could narrow the scope of future contracts to exclude our existing assets, which could reduce demand for our services, our revenues, and earnings.
Operations Risks
We rely on our IT systems to manage numerous aspects of our business. A cyber-based attack of these systems could disrupt our ability to deliver services to our customers and could lead to increased overhead costs, decreased sales, and harm to our reputation.
We rely on IT networks and systems to operate and manage our business, including the FireTRAC application (“FireTRAC”), which combines proprietary data and technology to deliver certain insights on fire risks. Our IT networks and systems process, transmit and store personal and financial information, and proprietary information of our business. The technology also allows us to coordinate our business across our operation bases and communicate with our employees and externally with customers, suppliers, partners, and other third parties. While we believe we take reasonable steps to secure these IT networks and systems, and the data processed, transmitted, and stored thereon, such networks, systems, and data may be susceptible to cyberattacks, viruses, malware, or other unauthorized access or damage (including by environmental, malicious, or negligent acts), which could result in unauthorized access to, or the release and public exposure of, our proprietary information or our users’ personal information. In addition, cyberattacks, viruses, malware, or other damage or unauthorized access to our IT networks and systems could result in damage, disruptions, or shutdowns to our platform. Any of the foregoing could cause substantial harm to our business, require us to make notifications to our customers, governmental authorities, or the media, and could result in litigation, investigations or inquiries by government authorities, or subject us to penalties, fines, and other losses relating to the investigation and remediation of such an attack or other unauthorized access or damage to our IT systems and networks.
Our service, data and systems may be critical to operations or involve the storage, processing and transmission of sensitive data, including valuable intellectual property, other proprietary or confidential data, regulated data, and personal information of employees, and others. Successful breaches, employee malfeasance, or human or technological error could result in, for example, unauthorized access to, disclosure, modification, misuse, loss, or destruction of our or other third-party data or systems; theft of sensitive, regulated, or confidential data including personal information and intellectual property; the loss of access to critical data or systems; service or system disruptions or denials of service.
Our ability to attract and retain customers, to efficiently operate our business, and to compete effectively depends in part upon the sophistication, security, and reliability of our technology network, including our ability
21
to provide features of service that are important to our customers, to protect our confidential business information and the information provided by our customers, and to maintain customer confidence in our ability to protect our systems and to provide services consistent with their expectations. As a result, we are subject to risks imposed by data breaches and operational disruptions, including through cyberattack or cyber-intrusion, by computer hackers, foreign governments, cyber terrorists and activists, cyber criminals, malicious employees or other insiders of the Company or third-party service providers, and other groups and individuals.
Data breaches of companies and governments continue to increase as the number, intensity, and sophistication of attempted attacks and intrusions from around the world have increased and we, our customers, and third parties increasingly store and transmit data by means of connected IT systems. Additionally, risks such as code anomalies, “Acts of God,” data leakage, cyber-fraud, and human error pose a direct threat to our services, systems, and data and could result in unauthorized or block legitimate access to sensitive or confidential data regarding our operations, customers, employees, and suppliers, including personal information.
We also depend on and interact with the technology and systems of third parties, including our customers and third-party service providers such as cloud service providers. Such third parties may host, process, or have access to information we maintain about our company, customers, employees, and vendors or operate systems that are critical to our business operations and services. Like us, these third parties are subject to risks imposed by data breaches, cyberattacks, and other events or actions that could damage, disrupt, or close down their networks or systems. We have security processes, protocols, and standards in place, including contractual provisions requiring such security measures, that are applicable to such third parties and are designed to protect information that is held by them, or to which they have access, as a result of their engagements with us. Nevertheless, a cyberattack could defeat one or more of such third parties’ security measures, allowing an attacker to obtain information about our company, customers, employees, and vendors or disrupt our operations. These third parties may also experience operational disruptions or human error that could result in unauthorized access to sensitive or confidential data regarding our operations, customers, employees, and suppliers, including personal information.
A disruption to our complex, global technology infrastructure, including those impacting our computer systems and website, could result in the loss of confidential business or customer information, require substantial repairs or replacements, resulting in significant costs, and lead to the temporary or permanent transfer by customers of some or all of their business to our competitors. The foregoing could harm our reputation and adversely impact our operations, customer service, and results of operations. Additionally, a security breach could require us to devote significant management resources to address the problems created. A significant data breach or any failure, or perceived failure, by us to comply with any federal, state, or foreign privacy laws, regulations, or other principles or orders to which we may be subject could adversely affect our reputation, brand, and business, and may result in claims, investigations, proceedings, or actions against us by governmental entities, litigation, including class action litigation, from our customers, fines, penalties, or other liabilities, or require us to change our operations or cease using certain data sets. Depending on the nature of the information compromised, we may also have obligations to notify users, law enforcement, government authorities, payment companies, consumer reporting agencies, or the media about the incident and may be required to expend additional resources in connection with investigating and remediating such an incident, and otherwise complying with applicable privacy and data security laws.
These types of adverse impacts could also occur in the event the confidentiality, integrity, or availability of company and customer information was compromised due to a data loss by us or a trusted third party. We or the third parties with which we share information may not discover any security breach and loss of information for a significant period of time after the security breach occurs.
We have invested and continue to invest in technology security initiatives, information-technology risk management, business continuity, and disaster recovery plans, including investments to retire and replace end-of-life systems. The development and maintenance of these measures is costly and requires ongoing
22
monitoring and updating as technologies change and efforts to overcome security measures become increasingly more frequent, intense, and sophisticated. Despite our efforts, we are not fully insulated from data breaches, technology disruptions, data loss, and cyber-fraud, which could adversely impact our competitiveness and results of operations.
While we have significant security processes and initiatives in place, we may be unable to detect or prevent a breach or disruption in the future. Additionally, while we have insurance coverage designed to address certain aspects of cyber risks in place, such insurance coverage may be insufficient to cover all losses or all types of claims that may arise.
Failure to comply with federal, state and foreign laws and regulations relating to privacy, data protection and consumer protection, or the expansion of current laws and regulations or the enactment of new laws or regulations in these areas, could adversely affect our business and our financial condition.
We are subject to a wide variety of laws in the United States and other jurisdictions related to privacy, data protection, and consumer protection that are often complex and subject to varying interpretations. As a result, these privacy, data protection, and consumer protection laws may change or develop over time through judicial decisions or as new guidance or interpretations are provided by regulatory and governing bodies and such changes or developments may be contrary to our existing practices. This may cause us to expend resources on updating, changing, or eliminating some of our privacy and data protection practices.
Our reputation and ability to do business may be impacted by the improper conduct of our employees, agents or business partners.
We have implemented compliance controls, training, policies and procedures designed to prevent and detect reckless or criminal acts from being committed by our employees, agents or business partners that would violate the laws of the jurisdictions in which we operate, including laws governing payments to government officials, such as the U.S. Foreign Corrupt Practices Act, the protection of export controlled or classified information, such as the International Traffic in Arms Regulations (“ITAR”), false claims, procurement integrity, cost accounting and billing, competition, information security and data privacy and the terms of our contracts. This risk of improper conduct may increase as we continue to grow and expand our operations. We cannot ensure, however, that our controls, training, policies and procedures will prevent or detect all such reckless or criminal acts, and we have been adversely impacted by such acts in the past, which have been immaterial in nature. If not prevented, such reckless or criminal acts could subject us to civil or criminal investigations, monetary and non-monetary penalties and suspension and debarment by the U.S. government and could have a material adverse effect on our ability to conduct business, our results of operations and our reputation. In addition, misconduct involving data security lapses resulting in the compromise of personal information or the improper use of our customer’s sensitive or classified information could result in remediation costs, regulatory sanctions against us and serious harm to our reputation and could adversely impact our ability to continue to contract with the U.S. government.
Any failure to offer high-quality aerial firefighting services to customers may harm our relationships with our customers and could adversely affect our reputation, brand, business, financial condition, and results of operations.
We strive to create high levels of customer satisfaction and brand trust through our services and the support provided by our employees. Our customers depend on our team to resolve any issues relating to our services, which are often emergencies, in an efficient and accurate manner. Our ability to provide effective and timely services is largely dependent on numerous factors, including our ability to maintain our existing fleet and our ability to attract and retain skilled employees who can support our customers and are sufficiently knowledgeable about our services. As we continue to grow our business and improve our platform, we will face challenges related to providing quality support at scale. Any failure to provide efficient and timely services, or a market perception that we do not maintain high-quality or dependable services, could adversely affect our reputation, brand, business, financial condition, and results of operations.
23
Natural disasters, unusual weather conditions, pandemic or epidemic outbreaks, terrorist acts and political events could disrupt our business.
The occurrence of one or more natural disasters such as fires, tornados, hurricanes, floods and earthquakes, unusual weather conditions, epidemic or pandemic outbreaks, terrorist attacks or disruptive political events where our facilities or the hangars where our aircraft fleets are located, could damage our fleet or other property and adversely affect our business, financial condition and results of operations. Severe weather, such as rainfall, snowfall or extreme temperatures, may impact the ability for our aerial firefighting services to occur as planned, resulting in additional expense to reschedule or cancel altogether, thereby reducing our sales and profitability. Terrorist attacks, actual or threatened acts of war or the escalation of current hostilities, or any other military or trade disruptions impacting our domestic or foreign suppliers of components of our aircraft, may impact our operations by, among other things, causing supply chain disruptions and increases in commodity prices, which could adversely affect our raw materials or transportation costs. To the extent these events also impact one or more of our suppliers or result in the closure of any of their facilities or our facilities, we may be unable to fulfill our other contracts.
We are subject to risks associated with climate change, including the potential increased impacts of severe weather events on our operations and infrastructure, and changes in weather patterns may result in lower demand for our services if such changes result in a reduced risk of wildfires.
All climate change-related regulatory activity and developments may adversely affect our business and financial results by requiring us to reduce our emissions, make capital investments to modernize certain aspects of our operations, purchase carbon offsets, or otherwise pay for our emissions. Such activity may also impact us indirectly by increasing our operating costs.
The potential physical effects of climate change, such as increased frequency and severity of storms, floods, fires, fog, mist, freezing conditions, sea-level rise, and other climate-related events, could affect our operations, infrastructure, and financial results. We could incur significant costs to improve the climate resiliency of our infrastructure and otherwise prepare for, respond to, and mitigate such physical effects of climate change. We are not able to accurately predict the materiality of any potential losses or costs associated with the physical effects of climate change. We believe that rising global temperatures have been, and in the future are expected to be, one factor contributing to increasing rates and severity of wildfires. Climate change and global temperatures are impacted my many variables, however, and cannot be predicted with certainty. If global temperatures were to decrease, then the rate and severity of wildfires may decrease as well, resulting in lower demand for our services.
Our business is dependent on the availability of aircraft fuel. Continued periods of significant disruption in the supply or cost of aircraft fuel could have a significant negative impact on consumer demand, our operating results, and liquidity.
We are currently able to obtain adequate supplies of aircraft fuel but we cannot predict the future availability. Natural disasters (including hurricanes or similar events in the U.S. Southeast and on the Gulf Coast, where we have performed our aerial firefighting services), political disruptions or military conflicts involving oil-producing countries, economic sanctions imposed against oil-producing countries or specific industry participants, changes in fuel-related governmental policy, the strength of the U.S. dollar against foreign currencies, changes in the cost to transport or store petroleum products, changes in access to petroleum product pipelines and terminals, speculation in the energy futures markets, changes in aircraft fuel production capacity, environmental concerns and other unpredictable events may result in fuel supply shortages or distribution challenges in the future. Any of these factors or events could cause a disruption in or increased demands on oil production, refinery operations, pipeline capacity, or terminal access and possibly result in diminished availability of aircraft fuel supply for our business. The impact of such events may limit our ability to perform our aerial firefighting services, which could result in loss of revenue and adversely affect our ability to provide our services.
24
System failures, defects, errors, or vulnerabilities in our website, applications, backend systems, or other technology systems or those of third-party technology providers could harm our reputation and brand and adversely impact our business, financial condition, and results of operations.
Our systems, or those of third parties upon which we rely, may experience service interruptions, outages, or degradation because of hardware and software defects or malfunctions, human error, or malfeasance by third parties or our employees, contractors, or service providers, earthquakes, hurricanes, floods, fires, natural disasters, power losses, disruptions in telecommunications services, fraud, military or political conflicts, terrorist attacks, cyberattacks, or other events. Our insurance may not be sufficient, and we may not have sufficient remedies available to us from our third-party service providers, to cover all of our losses that may result from such interruptions, outages, or degradation.
If we fail to adequately protect our proprietary intellectual property rights, our competitive position could be impaired and we may lose market share, generate reduced revenue, and/or incur costly litigation to protect our rights.
Our success depends, in part, on our ability to protect our proprietary intellectual property rights, including certain technologies we utilize in arranging air firefighting services. To date, we have relied primarily on trade secrets and trademarks to protect our proprietary technology. Our software is also subject to certain protection under copyright law, though we have chosen not to register any of our copyrights. We routinely enter into non-disclosure agreements with our employees, consultants, third party aircraft operators, and other relevant persons and take other measures to protect our intellectual property rights, such as limiting access to our trade secrets and other confidential information. We intend to continue to rely on these and other means, including patent protection, in the future. However, the steps we take to protect our intellectual property may be inadequate, and unauthorized parties may attempt to copy aspects of our intellectual property or obtain and use information that we regard as proprietary and, if successful, may potentially cause us to lose market share, harm our ability to compete, and result in reduced revenue. Moreover, our non-disclosure agreements do not prevent our competitors from independently developing technologies that are substantially equivalent or superior to our products, and there can be no assurance that our competitors or third parties will comply with the terms of these agreements, or that we will be able to successfully enforce such agreements or obtain sufficient remedies if they are breached. There can be no assurance that the intellectual property rights we own or license will provide competitive advantages or will not be challenged or circumvented by our competitors.
Further, obtaining and maintaining patent, copyright, and trademark protection can be costly, and we may choose not to, or may fail to, pursue or maintain such forms of protection for our technology in the United States or foreign jurisdictions, which could harm our ability to maintain our competitive advantage in such jurisdictions. It is also possible that we will fail to identify patentable aspects of our technology before it is too late to obtain patent protection, that we will be unable to devote the resources to file and prosecute all patent applications for such technology, or that we will inadvertently lose protection for failing to comply with all procedural, documentary, payment, and similar obligations during the patent prosecution process. The laws of some countries do not protect proprietary rights to the same extent as the laws of the United States, and mechanisms for enforcement of intellectual property rights in some foreign countries may be inadequate to prevent other parties from infringing our proprietary technology. To the extent we expand our international activities, our exposure to unauthorized use of our technologies and proprietary information may increase. We may also fail to detect unauthorized use of our intellectual property or be required to expend significant resources to monitor and protect our intellectual property rights, including engaging in litigation, which may be costly, time-consuming, and divert the attention of management and resources, and may not ultimately be successful. If we fail to meaningfully establish, maintain, protect, and enforce our intellectual property rights, our business, financial condition, and results of operations could be adversely affected.
25
We use open-source software in connection with our platform, which may pose risks to our intellectual property.
We use open source software in connection with our technology products and plan to continue using open-source software in the future. Some licenses governing the use of open-source software contain requirements that we make available source code for modifications or derivative works we create based upon the open-source software. If we combine or link our proprietary source code with open-source software in certain ways, we may be required, under the terms of the applicable open-source licenses, to make our proprietary source code available to third parties. Although we monitor our use of open-source software, we cannot provide assurance that all open-source software is reviewed prior to use in our platform, that our developers have not incorporated open-source software into our platform that we are unaware of, or that they will not do so in the future. Additionally, the terms of open-source licenses have not been extensively interpreted by United States or international courts, and so there is a risk that open-source software licenses could be construed in a manner that imposes unanticipated conditions or restrictions on us or our proprietary software. If an author or other third party that distributes such open-source software were to allege that we had not complied with the conditions of an open-source license, we could incur significant legal costs defending ourselves against such allegations or remediating any alleged non-compliance with open-source licenses. Any such remediation efforts could require significant additional resources, and we may not be able to successfully complete any such remediation. Further, in addition to risks related to license requirements, use of certain open-source software can lead to greater risks than use of third-party commercial software, as open-source licensors generally do not provide warranties, and the open-source software may contain security vulnerabilities.
Our insurance may become too difficult or expensive for us to obtain or maintain. Increases in insurance costs or reductions in insurance coverage may materially and adversely impact our results of operations and financial position.
As the owners and operators of certain aircraft, we maintain general liability aviation premise insurance, non-owned aircraft liability coverage, and directors and officers insurance, and we believe our level of coverage is customary in the industry and adequate to protect against claims. However, there can be no assurance that it will be sufficient to cover potential claims or that present levels of coverage will be available in the future at reasonable cost. Additionally, replacement aircraft, especially new Super Scoopers, may not be readily available for purchase, potentially resulting in lost revenue for extended periods of time. Further, we expect our insurance costs to increase as we anticipate adding aircraft, expanding our services, and entering into new markets.
We are highly dependent on our senior management team and other highly skilled personnel with unique skills. We will need to be able to continue to grow our workforce with highly skilled workers in the future. If we are not successful in attracting or retaining highly qualified personnel, we may not be able to successfully implement our business strategy.
Our success depends, in significant part, on the continued services of our senior management team and on our ability to attract, motivate, develop, and retain a sufficient number of other highly skilled personnel, including finance, marketing, sales, and technology and support personnel. We believe that the breadth and depth of our senior management team’s experience across multiple industries will be instrumental to our success. The loss of any one or more members of our senior management team, for any reason, including resignation or retirement, could impair our ability to execute our business strategy and have a material adverse effect on our business, financial condition, and results of operations. Additionally, our financial condition and results of operations may be adversely affected if we are unable to attract and retain skilled employees to support our operations and growth. In particular, Mr. Timothy Sheehy, our Chief Executive Officer, Co-Founder and a Director of Bridger, will resign as Chief Executive Officer if he is elected to U.S. Senate, as further described in the section of this prospectus entitled “Risk Factors — We are highly dependent on the services of Mr. Timothy Sheehy, our Chief Executive Officer, Co-Founder and a Director of Bridger, who is currently running for a seat in the U.S. Senate.”
26
We are highly dependent on the services of Mr. Timothy Sheehy, our Chief Executive Officer, Co-Founder and a Director of Bridger, who is currently running for a seat in the U.S. Senate.
We are highly dependent on the services of Mr. Timothy Sheehy, the Company’s Chief Executive Officer, Co-Founder and Director. On June 27, 2023, Mr. Timothy Sheehy announced his entrance into the 2024 race for the U.S. Senate for the State of Montana. During his candidacy, Mr. Timothy Sheehy has continued to serve as our Chief Executive Officer with the continued support of Bridger’s existing management team, and Mr. Sheehy has not publicly announced a specific intention of resigning as our Chief Executive Officer. However, in the event that Mr. Timothy Sheehy is elected to serve as a U.S. Senator for the State of Montana, Mr. Timothy Sheehy would be required to resign as an officer and director of the Company pursuant to certain conflict of interest rules contained in the Senate Code of Official Conduct. The loss of Mr. Timothy Sheehy as an officer and director of the Company could adversely affect our business because this could make it more difficult to, among other things, compete with other market participants, manage our operations, execute our growth strategy and retain existing customers or cultivate new ones.
Although Mr. Timothy Sheehy continues to spend significant time with Bridger and remain highly active in our management during his candidacy, he has not devoted his full time and attention to Bridger. Mr. Timothy Sheehy has spent, and expects to continue to spend, time campaigning for the U.S. Senate seat.
Additionally, Mr. Timothy Sheehy and we may be the targets of one or more negative media campaigns in connection with Mr. Timothy Sheehy’s U.S. Senate campaign. Public perception of, or news related to Mr. Timothy Sheehy or his U.S. Senate campaign may adversely affect our brand, relationship with customers, suppliers, employees or other of our stakeholders or our standing in the industry, any of which could materially impair our business and results of operations.
Our business may be adversely affected by labor and union activities.
None of our employees are currently represented by a labor union. However, it is common throughout the aerospace industry generally for many employees at aerospace companies to belong to a union, which can result in higher employee costs and increased risk of work stoppages. We may also directly and indirectly depend upon other companies with unionized work forces, such as parts suppliers and trucking and freight companies, and work stoppages or strikes organized by such unions could harm our business, financial condition or operating results.
Past performance by our management team or their respective affiliates may not be indicative of future performance of an investment in us.
Our management team has successfully grown and exited prior business ventures, including Ascent Vision Technologies by our founders, Mr. Matthew Sheehy and Mr. Timothy Sheehy. Any past experience or performance of our management team and their respective affiliates is not a guarantee of success with respect to Bridger.
We have entered into ground leases with terms of twenty (20) years and ten (10) years with the Gallatin Airport Authority for each of our hangars. If the Airport Authority declines to renew any of our ground leases, our operations and results of operations could be materially and adversely impacted.
Our current hangars are, and the additional hangars we plan to add in the near-term will be, located on certain land owned by Gallatin Airport Authority (the “Airport Authority”) and leased to our subsidiaries. The initial term of each Ground Lease is either twenty (20) years or ten (10) years from its respective commencement date. These hangars are critical to our ability to provide maintenance on our aircraft. If the Airport Authority terminates our leases, or refuses to renew them when expired, we may incur significant costs to locate suitable alternative hangar locations and may incur increased costs to modify any replacement hangars for our business, and the process may require significant management attention.
27
Additionally, we currently have two hangars under contract with a general contractor based in Bozeman, Montana. Construction of the hangars is subject to the risks of cost overruns and delays due to a variety of factors including, among other things, site difficulties, labor strife, delays in and shortages of materials, weather conditions, fire and casualty. Any delay in completion of the hangars could materially adversely affect the timing of the commencement of operations at the hangars, which could affect receipt of future revenues.
Our lack of diversification with respect to the aircraft we use may subject us to negative economic, competitive and regulatory developments that disproportionately impact our aviation assets as compared to other fire suppression aircraft or alternative fire suppression services, which could adversely affect our ability to market and sell our services and our reputation.
Our fleet is comprised mainly of CL-415EAF aircraft, which is currently limited in supply (see the section of this prospectus entitled “Risk Factors — There is a limited supply of new CL-415EAF aircraft to purchase, and an inability to purchase additional CL-415EAF aircraft could impede our ability to increase our revenue and net income.”). Furthermore, regulations or restrictions that cause us to ground the fleet after a safety or maintenance event, whether or not in connection with us or our services, have the potential to significantly affect our ability to carry out our operations and generate revenue. A similar incident could also damage our reputation or the perception of safety or efficacy of the CL-415EAF in fighting wildfires, which could negatively impact our business and results of operations.
Any delays in the development, design and engineering of our products and services may adversely impact our business, financial condition and results of operations.
We have previously experienced, and may experience in the future, delays or other complications in the design, production, delivery and servicing ramp of our systems, products, technologies, services, and related technology, including on account of the global COVID-19 health crisis. If delays like this arise or recur, if our remediation measures and process changes do not continue to be successful or if we experience issues with design and safety, we could experience issues or delays in increasing production further.
If we encounter difficulties in scaling our delivery or servicing capabilities, if we fail to develop and successfully commercialize our products and services, if we fail to develop such technologies before our competitors, or if such technologies fail to perform as expected, are inferior to those of our competitors or are perceived to offer less mission assurance than those of our competitors, our business, financial condition and results of operations could be materially and adversely impacted.
Seasonality Risks
There is a seasonal fluctuation in the need to fight forest fires based upon location. A significant portion of our total revenue currently occurs during the second and third quarters of the year due to the North American fire season, and the intensity of the fire season varies from year to year. As a result, our operating results may fluctuate significantly from quarter to quarter and from year to year.
Our quarterly and annual operating results may fluctuate significantly, which makes our future operating results difficult to predict and could cause our operating results to fall below expectations or any guidance we may provide. These fluctuations may occur due to a variety of factors, many of which are outside of our control, including but not limited to: forest fires tend to have a higher occurrence during the summer months and during times of drought, but are ultimately unpredictable; climate change and changes in global temperatures occur of time; unexpected weather patterns, natural disasters or other events that increase or decrease the rate or intensity of wildfires or impair our ability to perform firefighting services; changes in governmental regulations or in the status of our regulatory approvals or applications. The individual or cumulative effects of factors discussed above could result in large fluctuations and unpredictability in our quarterly and annual operating results. As a result, comparing our operating results on a period-to-period basis may not be meaningful or be a good indication of our
28
current or future performance. For example, due to the condensed and less intense 2022 wildfire season, we experienced a decrease in demand for our wildfire surveillance, relief and suppression and aerial firefighting services and had less flight hours and standby days than prior years, which negatively impacted our results of operations for the 2022 wildfire season.
This variability and unpredictability could also result in our failing to meet the expectations of industry or financial analysts or investors for any period. If our revenue or operating results fall below the expectations of analysts or investors or below any guidance we may provide, or if any guidance we provide is below the expectations of analysts or investors, the price of our common stock could decline substantially. Such a stock price decline could occur even when we have met any previously publicly stated guidance we may provide. Furthermore, if we are unable to obtain access to working capital or if seasonal fluctuations are greater than anticipated, there could be a material adverse effect on our financial condition, results of operations, or cash flows.
Extreme weather, drought and shifting climate patterns have intensified the challenges associated with many of the risks facing the Company, particularly wildfire management.
Extreme weather, drought and shifting climate patterns have intensified the challenges associated with many of the other risks facing our business, particularly wildfire management. Our service territory encompasses some of the most densely forested areas in the United States and, as a consequence, is subject to risks from vegetation-related ignition events. Further, environmental extremes, such as drought conditions and extreme heat followed by periods of wet weather, can drive additional vegetation growth (which can then fuel fires) and influence both the likelihood and severity of extraordinary wildfire events. In particular, the risk posed by wildfires, including during the 2021 wildfire season, increased in the United States as a result of an ongoing extended period of drought, bark beetle infestations in forests and wildfire fuel increases due to rising temperatures and record rainfall following the drought, and strong wind events, among other environmental factors. Contributing factors other than environmental can include local land use policies and historical forestry management practices. The combined effects of extreme weather and climate change also impact this risk.
Further, we have been studying the potential effects of climate change (increased severity and frequency of storm events, sea level rise, land subsidence, change in temperature extremes, changes in precipitation patterns and drought, and wildfire) on Bridger’s assets, operations, and services, and we are developing adaptation plans to set forth a strategy for those events and conditions that we believe are most significant. Consequences of these climate-driven events may vary widely and could include increased stress on our services due to new patterns of demand, physical damage to our fleet and infrastructure, higher operational costs, and an increase in the number requests for our services. In addition, we could incur substantial costs to repair or replace aircraft and facilities.
Events or conditions caused by climate change could have a greater impact on our operations than our studies suggest and could result in a fluctuation in revenues and expenses. Conversely, the impact could be less than we anticipate, which we expect would result in reduce demand for our aerial firefighting services.
The substantial majority of our revenue currently is concentrated in the Western United States.
Currently, the substantial majority of our revenue is generated in the states of the United States located west of the Mississippi River, and if the weather patterns result in fewer wildfires in this region, demand for “flight hour” services would decrease and potentially result in a material decrease in revenue or net income.
29
Sales and Customer Risks
The aerial firefighting industry is expected to grow in the near future and is volatile, and if it does not develop, if it develops slower than we expect, if it develops in a manner that does not require use of our services, if it encounters negative publicity or if our solution does not drive commercial or governmental engagement, the growth of our business will be harmed.
The market for aerial firefighting is still rapidly evolving, characterized by rapidly changing technologies, competitive pricing and competitive factors, evolving government regulation and industry standards, and changing customer demands and behaviors. If the market for our services in general does not develop as expected, or develops more slowly than expected, our business, prospects, financial condition and operating results could be harmed.
In the future, there may be other businesses who attempt to provide the services that we provide, or our main private competitors could attempt to increase operations. In the future, federal, state, and local governments and foreign governments may also decide to directly provide such services.
The industry in which we operate may become increasingly competitive as a result of the expansion of the demand for aerial firefighting operations or the entrance of federal, state, and local governments and foreign governments into the aerial firefighting space. We compete against a number of private operators with different business models, and new entrants may begin offering aerial firefighting services. Factors that affect competition in our industry include price, reliability, safety, regulations, professional reputation, aircraft availability, equipment and quality, consistency and ease of service, and willingness and ability to serve specific regions. There can be no assurance that our competitors will not be successful in capturing a share of our present or potential customer base. Certain governments may decide a government owned, government operated model is preferable, from a cost perspective or otherwise, to perform aerial firefighting services directly or to own their own aircraft and contract with independent operators. The materialization of any of these risks could adversely affect our business, financial condition and results of operations.
If we experience harm to our reputation and brand, our business, financial condition and results of operations could be adversely affected.
Continuing to increase the strength of our reputation and brand for reliable, experience-driven, and cost-effective aerial firefighting services is critical to our ability to attract and retain qualified aircraft operators. In addition, our growth strategy may include international expansion through joint ventures, minority investments, or other partnerships with local companies, as well as event activations and cross-marketing with other established brands, all of which benefit from our reputation and brand recognition. If we fail to protect our reputation and brand recognition, it could adversely affect our business, financial condition, and results of operations.
We have government customers, which subjects us to risks including early termination, audits, investigations, sanctions and penalties. We are also subject to regulations applicable to government contractors which increase our operating costs and if we fail to comply, could result in the termination of our contracts with government entities.
We derive a substantial portion of our revenue from contracts with the U.S. government (accounting for approximately 96% of our total revenue in the year ended December 31, 2022) and may enter into additional contracts with the U.S. or foreign governments in the future. This subjects us to statutes and regulations applicable to companies doing business with the government, including the Federal Aviation Administration (the “FAA”). These government contracts customarily contain provisions that give the government substantial rights and remedies, many of which are not typically found in commercial contracts and which are unfavorable to contractors. For instance, most U.S. government agencies include provisions that allow the government to unilaterally terminate or modify contracts for convenience, and in that event, the counterparty to the contract may
30
generally recover only its incurred or committed costs and settlement expenses and profit on work completed prior to the termination. In addition, as a small business, we have been awarded certain government contracts based on our status under the applicable regulations of the Small Business Association. If we continue to expand and are unable to maintain this small business status, we may no longer be eligible to utilize the small business status to grow our business. If the government terminates a contract for default, the defaulting party may be liable for any extra costs incurred by the government in procuring undelivered items from another source.
All of our federal and state government contracts (accounting for approximately 99.1% of our total revenue in the year ended December 31, 2022) are subject to the annual approval of appropriations being made by the applicable state or federal legislative bodies to fund the expenditures under these contracts. In addition, government contracts normally contain additional requirements that may increase our costs of doing business, reduce our profits, and expose us to liability for failure to comply with these terms and conditions. These requirements include, for example:
| • | specialized disclosure and accounting requirements unique to government contracts; |
| • | financial and compliance audits that may result in potential liability for price adjustments, recoupment of government funds after such funds have been spent, civil and criminal penalties, or administrative sanctions such as suspension or debarment from doing business with the U.S. government; |
| • | public disclosures of certain contract and company information; and |
| • | mandatory socioeconomic compliance requirements, including labor requirements, non-discrimination and affirmative action programs and environmental compliance requirements. |
Government contracts are also generally subject to greater scrutiny by the government, which can initiate reviews, audits and investigations regarding our compliance with government contract requirements. In addition, if we fail to comply with government contracting laws, regulations and contract requirements, our contracts may be subject to termination, and we may be subject to financial and/or other liability under our contracts, the Federal Civil False Claims Act (including treble damages and other penalties), or criminal law. In particular, the False Claims Act’s “whistleblower” provisions also allow private individuals, including present and former employees, to sue on behalf of the U.S. government. Any penalties, damages, fines, suspension, or damages could adversely affect our ability to operate our business and our financial results.
The U.S. government’s budget deficit and the national debt, as well as any inability of the U.S. government to complete its budget process for any government fiscal year and consequently having to shut down or operate on funding levels equivalent to its prior fiscal year pursuant to a “continuing resolution,” could have an adverse impact on our business, financial condition, results of operations and cash flows.
Considerable uncertainty exists regarding how future budget and program decisions will unfold, including the aerial firefighting spending priorities of the U.S. government, what challenges budget reductions will present for the aerial firefighting industry and whether annual appropriations bills for all agencies will be enacted for U.S. government fiscal year 2024 and thereafter due to many factors, including but not limited to, changes in the political environment, including before or after a change to the leadership within the government administration, and any resulting uncertainty or changes in policy or priorities and resultant funding. The U.S. government’s budget deficit and the national debt could have an adverse impact on our business, financial condition, results of operations and cash flows in a number of ways, including the following:
| • | The U.S. government could reduce or delay its spending on, reprioritize its spending away from, or decline to provide funding for the government programs in which we participate; |
| • | U.S. government spending could be impacted by alternate arrangements to sequestration, which increases the uncertainty as to, and the difficulty in predicting, U.S. government spending priorities and levels; and |
31
| • | We may experience declines in revenue, profitability and cash flows as a result of reduced or delayed orders or payments or other factors caused by economic difficulties of our customers and prospective customers, including U.S. federal, state and local governments. |
Furthermore, we believe continued budget pressures could have serious negative consequences for the aerial firefighting industrial base and the customers, employees, suppliers, investors and communities that rely on companies in the aerial firefighting industrial base. Budget and program decisions made in this environment would have long-term implications for us and the entire aerial firefighting industry.
We depend significantly on U.S. government contracts, which often are only partially funded, subject to immediate termination, and heavily regulated and audited. The termination or failure to fund, or negative audit findings for, one or more of these contracts could have an adverse impact on our business, financial condition, results of operations and cash flows.
Over its lifetime, a U.S. government program may be implemented by the award of many different individual contracts and subcontracts. The funding of U.S. government programs is subject to U.S. Congressional appropriations. In recent years, U.S. government appropriations have been affected by larger U.S. government budgetary issues and related legislation. Although multi-year contracts may be authorized and appropriated in connection with major procurements, the U.S. Congress (“Congress”) generally appropriates funds on a government fiscal year basis. Procurement funds are typically made available for obligation over the course of one to three years. Consequently, programs often initially receive only partial funding, and additional funds are obligated only as Congress authorizes further appropriations. As a result of the restrictions on the authority of federal agencies to obligate federal funds without annual appropriations from Congress, most of our contracts are structured for one base year with options for up to four additional years. We cannot predict the extent to which total funding and/or funding for individual programs will be included, increased or reduced as part of the annual appropriations process ultimately approved by Congress and the President of the United States or in separate supplemental appropriations or continuing resolutions, as applicable. The termination of funding for a U.S. government program would result in a loss of anticipated future revenue attributable to that program, which could have an adverse impact on our operations. In addition, the termination of a program or the failure to commit additional funds to a program that already has been started could result in lost revenue and increase our overall costs of doing business.
Generally, U.S. government contracts are subject to oversight audits by U.S. government representatives. Such audits could result in adjustments to our contract costs. Any costs found to be improperly allocated to a specific contract will not be reimbursed, and such costs already reimbursed must be refunded. We have recorded contract revenue based on costs we expect to realize upon final audit. However, we do not know the outcome of any future audits and adjustments, and we may be required to materially reduce our revenue or profits upon completion and final negotiation of audits. Negative audit findings could also result in termination of a contract, forfeiture of profits, suspension of payments, fines or suspension or debarment from U.S. Government contracting or subcontracting for a period of time.
In addition, U.S. government contracts generally contain provisions permitting termination, in whole or in part, without prior notice at the U.S. government’s convenience upon payment only for work done and commitments made at the time of termination. For some contracts, we are a subcontractor and not the prime contractor, and in those arrangements, the U.S. Government could terminate the prime contractor for convenience without regard for our performance as a subcontractor. We can give no assurance that one or more of our U.S. government contracts will not be terminated under those circumstances. Also, we can give no assurance that we would be able to procure new contracts to offset the revenue or backlog lost as a result of any termination of our U.S. government contracts. Because a significant portion of our revenue is dependent on our performance and payment under our U.S. government contracts, the loss of one or more large contracts could have a material adverse impact on our business, financial condition, results of operations and cash flows.
32
Our U.S. government business also is subject to specific procurement regulations and a variety of socioeconomic and other requirements. These requirements, although customary in U.S. government contracts, increase our performance and compliance costs. These costs might increase in the future, thereby reducing our margins, which could have an adverse effect on our business, financial condition, results of operations and cash flows. In addition, the U.S. government has and may continue to implement initiatives focused on efficiencies, affordability and cost growth and other changes to its procurement practices. These initiatives and changes to procurement practices may change the way U.S. government contracts are solicited, negotiated and managed, which may affect whether and how we pursue opportunities to provide our products and services to the U.S. government, including the terms and conditions under which we do so, which may have an adverse impact on our business, financial condition, results of operations and cash flows. For example, contracts awarded under the Department of Defense’s Other Transaction Authority for research and prototypes generally require cost-sharing and may not follow, or may follow only in part, standard U.S. government contracting practices and terms, such as the Federal Acquisition Regulation and Cost Accounting Standards.
Failure to comply with applicable regulations and requirements could lead to fines, penalties, repayments, or compensatory or treble damages, or suspension or debarment from U.S. government contracting or subcontracting for a period of time. Among the causes for debarment are violations of various laws and regulations, including those related to procurement integrity, export control (including ITAR), U.S. government security, employment practices, protection of the environment, accuracy of records, proper recording of costs and foreign corruption. The termination of a U.S. government contract or relationship as a result of any of these acts would have an adverse impact on our operations and could have an adverse effect on our standing and eligibility for future U.S. government contracts.
We may be blocked from or limited in providing or offering our services in certain jurisdictions and may be required to modify our business model in those jurisdictions as a result.
We face regulatory obstacles, including those lobbied for in local government, which could prevent us from operating our aerial firefighting services. We may incur significant costs in defending our right to operate in accordance with our business model in many jurisdictions. To the extent that efforts to block or limit our operations are successful, or we or third-party aircraft operators are required to comply with regulatory and other requirements applicable to our services, our revenue and growth would be adversely affected.
We may enter into firefighting contracts in the future with foreign governments, which may result in increased compliance and oversight risks and expenses.
If we enter into contracts with foreign governments in the future, we may be subject to further regulations and complicated procurement processes that require significant expense and/or management attention. Additionally, contracts with foreign governments often necessitate higher levels of compliance and oversight functions, which could increase our costs, making us less competitive and hurting our results from operations.
We may be unable to manage our future growth effectively, which could make it difficult to execute our business strategy.
If our operations continue to grow as planned, of which there can be no assurance, we will need to expand our sales, marketing, operations, and the number of aircraft that we own and operate in connection with our aerial firefighting services. Our continued growth could increase the strain on our resources, and we could experience operating difficulties, including difficulties in hiring, training, and managing an increasing number of employees. These difficulties may result in the erosion of our brand image, divert the attention of management and key employees, and impact financial and operational results. In addition, in order to continue to increase our presence, we expect to incur substantial expenses and capital expenditures as we continue to attempt to increase our coverage areas, aircraft fleet, and employee base. The continued expansion of our business may also require additional space for administrative support. If we are unable to drive commensurate growth, these costs, which
33
include lease commitments, marketing costs and headcount, could result in decreased margins, which could have a material adverse effect on our business, financial condition, and results of operations.
We rely on a few large customers for a majority of our business, and the loss of any of these customers, significant changes in the prices, marketing allowances or other important terms provided to any of these customers or adverse developments with respect to the financial condition of these customers could materially reduce our net income and operating results.
Our total revenues are concentrated among a small number of large customers. Sales to our three largest customers in the aggregate represented 99.1%, sales to our largest customer represented 94.8% of our total revenues during the year ended December 31, 2022, and one customer that accounted for 62% of accounts receivable as of December 31, 2022. We are under continued pressure from our major customers to offer lower prices, extended payment terms, increased marketing and other allowances and other terms more favorable to these customers because our sales to these customers are concentrated, and the market in which we operate is very competitive. These customer demands have put continued pressure on our operating margins and profitability, resulted in periodic negotiations in connection with open requests for proposals to provide more favorable prices and terms to these customers and significantly increased our working capital needs. In addition, this customer concentration leaves us vulnerable to any adverse change in the financial condition of these customers. Changes in terms with, significant allowances for and collections from these customers could affect our operating results and cash flows. The loss of our main customers could adversely affect our business.
Our cash flow and profitability could be reduced if expenditures are incurred prior to the final receipt of a contract.
We provide services on behalf of our customers under various contractual arrangements. From time to time, in order to ensure that we satisfy our customers’ requirements and time-sensitive needs, we may elect to initiate procurement in advance of receiving final authorization from the government customer or a prime contractor. If our government or prime contractor customer’s requirements should change or if the government or the prime contractor should direct the anticipated procurement to another contractor, or if the anticipated contract award does not materialize, our investment might be at risk. This could reduce anticipated earnings or result in a loss, negatively affecting our cash flow and profitability.
If we are not able to successfully enter into new markets and offer new services and enhance our existing offerings, our business, financial condition and results of operations could be adversely affected.
Our growth will depend in part on our ability to successfully enter into new markets and expand on our existing services. Significant changes to our existing services may require us to obtain and maintain applicable permits, authorizations or other regulatory approvals. If these new services are unsuccessful or fail to attract a sufficient number of customers to be profitable, or we are unable to bring new or expanded services to market efficiently, our business, financial condition and results of operations could be adversely affected. Furthermore, new demands regarding our services, including the availability of superior services or a deterioration in the quality of our existing services, could negatively affect the attractiveness of our platform and the economics of our business and require us to make substantial changes to and additional investments in our routes or our business model. Developing and launching new services or enhancements to our existing services involves significant risks and uncertainties, including risks related to the reception of such services by existing and potential future customers, increases in operational complexity, unanticipated delays or challenges in implementing such services or enhancements, increased strain on our operational and internal resources (including an impairment of our ability to accurately forecast flier demand and the number of customers using our platform) and negative publicity in the event such new or enhanced routes are perceived to be unsuccessful. We have scaled our business rapidly, and significant new initiatives have in the past resulted in such operational challenges affecting our business. In addition, developing and launching new services and enhancements to our existing services may involve significant upfront investment, such as purchasing additional aircraft, and such investments may not generate return on investment.
34
Supplier Risks
We rely on a limited number of suppliers for certain raw materials and supplied components. We may not be able to obtain sufficient raw materials or supplied components to meet our maintenance or operating needs or obtain such materials on favorable terms or at all, which could impair our ability to provide our services in a timely manner or increase our costs of services and maintenance.
Our ability to produce our current and future systems, technologies and services and other components of operation is dependent upon sufficient availability of raw materials and supplied components, which we secure from a limited number of suppliers. Global supply chains have recently experienced disruption as a result of industry capacity constraints, tariffs, material availability and global logistics delays arising from transportation capacity of ocean shipping containers and a prolonged delay in resumption of operations by one or more key suppliers as a result of COVID-19. Our reliance on suppliers to secure raw materials and supplied components exposes us to volatility in the prices and availability of these materials. We may not be able to obtain sufficient supplies of raw materials or supplied components on favorable terms or at all, which could result in delays in the provision of our services, our ability to repair and service our assets, or increased costs, any of which could harm our business, financial condition and results of operations. In particular, we rely on Viking, the manufacturer of our Super Scooper aircraft and an affiliate of LAS, to source and acquire the parts and materials needed to maintain our Super Scoopers and Bridger has not identified a readily available alternative supplier for certain of such parts. If we are unable to obtain (including as a result of a disruption to Viking’s business operations or supply lines) the necessary parts and materials to maintain our Super Scooper aircraft from Viking, and if we are unable to identify an alternative supplier for such parts and materials in a timely manner, then our business operations, including the maintenance and performance of our Super Scooper aircraft, and results of operations would be adversely affected.
Additionally, to maintain compliance with certain contractual structural inspection and analysis requirements under our agreements with the USFS, on January 5, 2021 we entered into Amendment 8 (SSLMP) (the “SSLMP Amendment”) to the LAS Purchase Agreement, for Viking’s provision of a Supplemental Structural Life Management Program. Viking agreed to provide us with a 5-year subscription service to a Super Scooper life management program based on the applicable FAA advisory material related to fatigue management and supplemental structural inspection programs, for which we pay a fixed subscription price. Viking does not have a termination for convenience right in respect of the services rendered pursuant to the SSLMP Amendment. If such services are nonetheless terminated or if Viking ceases to perform its obligations in respect thereof, or if we are unable to renew such services, then our business operations could be significantly disrupted and our results of operations could be adversely affected.
There is a limited supply of new CL-415EAF aircraft to purchase, and an inability to purchase additional CL-415EAF aircraft could impede our ability to increase our revenue and net income.
Currently, a majority of our revenue derives from services performed by the CL-415EAF. LAS has only made a limited number of CL-415EAFs available for sale between 2020 and 2025, and LAS has not publicly committed to continuing production of CL-415EAFs after 2025. If we continue to focus operations on a single airframe for fire suppression and does not expand its fleet to other aircraft, our operations may be impacted by the limited supply of new CL-415EAF aircraft available to purchase, which creates a revenue ceiling until additional aircraft can be produced or acquired, which could adversely affect our results of operation and ability to obtain efficiencies of scale.
35
We currently rely and will continue to rely on third-party partners to provide and store the parts and components required to service and maintain our aircraft, and to supply critical components and systems, which exposes us to a number of risks and uncertainties outside our control. Disputes with our suppliers or the inability of our suppliers to perform, or our key suppliers to timely deliver our components, parts or services, could cause our services to be provided in an untimely or unsatisfactory manner.
We are substantially reliant on our relationships with our suppliers and service providers for the parts and components in our aircraft. If any of these suppliers or service partners were to experience delays, disruptions, capacity constraints or quality control problems in their manufacturing operations, or if they choose to not do business with us, we would have significant difficulty in procuring and preparing our aircraft for service, and our business prospects would be significantly harmed. These disruptions would negatively impact our revenues, competitive position and reputation. In addition, our suppliers or service partners may rely on certain state tax incentives that may be subject to change or elimination in the future, which could result in additional costs and delays in production if a new manufacturing site must be obtained. Further, if we are unable to successfully manage our relationship with our suppliers or service partners, the quality and availability of our aircraft may be harmed. Our suppliers or service partners could, under some circumstances, decline to accept new purchase orders from or otherwise reduce their business with us. If our suppliers or service partners stopped manufacturing our aircraft components for any reason or reduced manufacturing capacity, we may be unable to replace the lost manufacturing capacity on a timely and comparatively cost-effective basis, which would adversely impact our operations.
The manufacturing facilities of our suppliers or service partners and the equipment used to manufacture the components for our aircraft would be costly to replace and could require substantial lead time to replace and qualify for use. The manufacturing facilities of our suppliers or service partners may be harmed or rendered inoperable by natural or man-made disasters, including earthquakes, flooding, fire and power outages, or by public health issues, such as the ongoing COVID-19 pandemic, which may render it difficult or impossible for us to manufacture our aircraft for some period of time. The inability to manufacture our aircraft components or the backlog that could develop if the manufacturing facilities of our suppliers or service partners are inoperable for even a short period of time may result in the loss of customers or harm our reputation.
We do not control our suppliers or service partners or such parties’ labor and other legal compliance practices, including their environmental, health and safety practices. If our current suppliers or service partners, or any other suppliers or service partners which we may use in the future, violate U.S. or foreign laws or regulations, we may be subjected to extra duties, significant monetary penalties, adverse publicity, the seizure and forfeiture of products that we are attempting to import or the loss of our import privileges. The effects of these factors could render the conduct of our business in a particular country undesirable or impractical and have a negative impact on our operating results.
Legal and Regulatory Risks
Our business is subject to a wide variety of additional extensive and evolving government laws and regulations. Failure to comply with such laws and regulations could have a material adverse effect on our business.
We are subject to a wide variety of laws and regulations relating to various aspects of our business, including with respect to employment and labor, health care, tax, privacy and data security, health and safety, and environmental issues. Laws and regulations at the foreign, federal, state and local levels frequently change, especially in relation to new and emerging industries, and we cannot always reasonably predict the impact from, or the ultimate cost of compliance with, current or future regulatory or administrative changes. We monitor these developments and devote a significant amount of management’s time and external resources towards compliance with these laws, regulations and guidelines, and such compliance places a significant burden on management’s time and other resources, and it may limit our ability to expand into certain jurisdictions. Moreover, changes in law, the imposition of new or additional regulations or the enactment of any new or more stringent legislation
36
that impacts our business could require us to change the way we operate and could have a material adverse effect on our sales, profitability, cash flows and financial condition.
Failure to comply with these laws, such as with respect to obtaining and maintaining licenses, certificates, authorizations and permits critical for the operation of our business, may result in civil penalties or private lawsuits, or the suspension or revocation of licenses, certificates, authorizations or permits, which would prevent us from operating our business. For example, aerial firefighting and the operation of any aircraft in the United States require licenses and permits from the FAA and review by other agencies of the U.S. government, including the USFS and the DOI. License approval can include an interagency review of safety, operational, national security, and foreign policy and international obligations implications, as well as a review of foreign ownership.
Compliance with existing or new laws can delay our operations and impair our ability to fully utilize our assets. For example, each of the aircraft acquired and operated by us is subject to a conformance and registration process with the FAA prior to use in commercial operations. This conformance carding and registration process takes some time and can be delayed from time to time due to events outside of our control, including such events as federal government shutdowns or slowdowns in operations of the FAA. In 2020, the first two Viking Air CL-415EAFs were delivered to us three months later than anticipated due to federal government restrictions imposed because of the COVID-19 pandemic. As such, we were not able to execute a firefighting contract for 2020 with the USFS.
Additionally, regulation of our industry is still evolving, and new or different laws or regulations could affect our operations, increase direct compliance costs for us or cause any third-party suppliers or contractors to raise the prices they charge us because of increased compliance costs. Application of these laws to our business may negatively impact our performance in various ways, limiting the collaborations we may pursue, further regulating the export and re-export of our services and technology from the United States and abroad and increasing our costs and the time necessary to obtain required authorization. The adoption of a multi-layered regulatory approach to any one of the laws or regulations to which we are or may become subject, particularly where the layers are in conflict, could require changes to the performance of our services or operational parameters which may adversely impact our business. We may not be in complete compliance with all such requirements at all times and, even when we believe we are in complete compliance, a regulatory agency may determine that we are not.
Our operations are subject to various federal, state and local laws and regulations governing health and the environment.
We are subject to a wide variety of various federal, state and local laws and regulations governing health and the environment due to the nature of our operations. Changes in the legal and or regulatory framework relating to the environment could have significant impact on our operations. For example, certain local land use policies and forestry management practices could be restricted to reduce the construction and development of residential and commercial projects in high-risk fire areas, which could lead to a reduction in demand for our services. Likewise, certain or future state and local water use and access policies could restrict our ability to access the bodies of water necessary to combat wildfires with our existing fire suppression aircraft. In the future, we may be unable to secure exemptions to these policies, and demand for our services could decrease. If these or any other change in the legal or regulatory framework relating to the environmental impact the operation of our business and the provision of our services, our costs, revenue and results of operations may be adversely affected.
Financial and Capital Strategy Risks
We may in the future invest significant resources in developing new offerings and exploring the application of our technologies for other uses and those opportunities may never materialize.
While our primary focus for the foreseeable future will be on our aerial firefighting services, we may invest significant resources in developing new technologies, services, products and offerings. However, we may not
37
realize the expected benefits of these investments, and these anticipated technologies are unproven and these products or technologies may never materialize or be commercialized in a way that would allow us to generate ancillary revenue streams. Relatedly, if such technologies become viable offerings in the future, we may be subject to competition from our competitors.
Such research and development initiatives may also have a high degree of risk and involve unproven business strategies and technologies with which we have limited operating or development experience. They may involve claims and liabilities (including, but not limited to, personal injury claims), expenses, regulatory challenges and other risks that we may not be able to anticipate. There can be no assurance that consumer demand for such initiatives will exist or be sustained at the levels that we anticipate, or that any of these initiatives will gain sufficient traction or market acceptance to generate sufficient revenue to offset any new expenses or liabilities associated with these new investments. Further, any such research and development efforts could distract management from current operations and would divert capital and other resources from our more established offerings and technologies. Even if we were to be successful in developing new products, services, offerings or technologies, regulatory authorities may subject us to new rules or restrictions in response to our innovations that may increase our expenses or prevent us from successfully commercializing new products, services, offerings or technologies.
We may require substantial additional funding to finance our operations and growth strategy, but adequate additional financing may not be available when we need it, on acceptable terms, or at all, and our ability to pursue equity financings may depend in part on the market price of our Common Stock.
We financed our operations and capital expenditures primarily through private financing rounds, including the $160 million aggregate municipal bond financing that closed on July 21, 2022 and August 10, 2022. In the future, we could be required to raise capital through public or private financing or other arrangements. Such financing may not be available on acceptable terms, or at all, and our failure to raise capital when needed could harm our business. For example, the global COVID-19 health crisis and related financial impact has resulted in, and may continue to result in, significant disruption and volatility of global financial markets that could adversely impact our ability to access capital. We may sell equity securities or debt securities in one or more transactions at prices and in a manner as we may determine from time to time for general corporate purposes or for specific purposes, including in order to pursue growth initiatives. Any debt financing, if available, may involve restrictive covenants and could reduce our operational flexibility or profitability. If we sell any securities in subsequent transactions, our current investors may be materially diluted. If we cannot raise funds on acceptable terms, we may not be able to grow our business or respond to competitive pressures.
In addition, our ability to generate proceeds from equity financings will significantly depend on the market price of our Common Stock. The Common Stock being offered for sale in this prospectus represent a substantial percentage of our total outstanding Common Stock as of the date of this prospectus, and could cause the market price of our Common Stock to drop significantly, even if our business is doing well. For additional information about how the sales of our securities, including the shares of Common Stock being offered for sale in this prospectus could decrease our stock price, see the sections of this prospectus entitled “Risk Factors — Risks Related to the Ownership of Our Securities — Future sales, or the perception of future sales, of a substantial number of shares of our Common Stock by us or our stockholders in the public market may cause the price of our Common Stock and Warrants to decline” and “Risk Factors — Risks Related to this Offering — If you purchase shares of our Common Stock in this offering, you will incur immediate and substantial dilution in the book value of your shares.”
38
Any acquisitions, partnerships or joint ventures that we enter into could disrupt our operations and have a material adverse effect on our business, financial condition and results of operations. As part of growing our business, we have and may make acquisitions. If we fail to successfully select, execute or integrate our acquisitions including our pending Bighorn Acquisition and Spanish Super Scooper Acquisition and recently completed Ignis Acquisition, then our business, results of operations and financial condition could be materially adversely affected, and our stock price could decline.
From time to time, we may evaluate potential strategic acquisitions of businesses, including partnerships or joint ventures with third parties. We may not be successful in identifying acquisition, partnership and joint venture candidates. In addition, we may not be able to continue the operational success of such businesses or successfully finance or integrate any businesses that we acquire or with which we form a partnership or joint venture. We may have potential write-offs of acquired assets and/or an impairment of any goodwill recorded as a result of acquisitions. Furthermore, the integration of any acquisition may divert management’s time and resources from our core business and disrupt our operations or may result in conflicts with our business. Any acquisition, partnership or joint venture may not be successful, may reduce our cash reserves, may negatively affect our earnings and financial performance and, to the extent financed with the proceeds of debt, may increase our indebtedness. Further, depending on market conditions, investor perceptions of us and other factors, we might not be able to obtain financing on acceptable terms, or at all, to implement any such transaction. We cannot ensure that any acquisition, partnership or joint venture we make will not have a material adverse effect on our business, financial condition and results of operations.
As described above under the section of this prospectus entitled “Prospectus Summary — Recent Developments — Recent Acquisitions,” we are currently pursuing the Bighorn Acquisition and the Spanish Super Scooper Acquisition and recently completed the Ignis Acquisition. Both the Bighorn Acquisition and the Spanish Super Scooper Acquisition are subject to the satisfaction and waiver of various closing conditions, some of which are outside of our control, and, as a result, we may not be able to complete such acquisitions on the timeframe we expect or at all. In addition, the integration of the Bighorn Acquisition (if completed), the Spanish Super Scooper Acquisition (if completed) and the Ignis Acquisition could be more costly or time-consuming than we anticipate, and we may not realize the anticipated benefits from such acquisitions.
Our systems, aircraft, technologies and services and related equipment may have shorter useful lives than we anticipate.
Our growth strategy depends in part on the acquisition of additional assets, including Super Scoopers, Air Attack aircraft, UAV, and airport hangars. A number of factors will impact the useful lives of our aircraft and facilities, including, among other things, the quality of their design and construction, the durability of their component parts and availability of any replacement components, and the occurrence of any anomaly or series of anomalies or other risks affecting the technology during firefighting and surveillance operations. In addition, any improvements in technology may make our existing aircraft, designs, or any component of our aircraft prior to the end of its life obsolete. If our systems, aircraft, facilities, technologies, and related equipment have shorter useful lives than we currently anticipate, this may lead to higher costs, lower returns on capital, or customer price increases that could hinder our ability to obtain new business, any of which would have a material adverse effect on our business, financial condition and results of operations.
39
We have a substantial amount of debt and servicing future interests or principal payments may impair our ability to operate our business or require us to change our business strategy to accommodate the repayment of our debt. Our ability to operate our business is limited by certain agreements governing our debt, including restrictions on the use of the loan proceeds, operational and financial covenants, and restrictions on additional indebtedness. If we are unable to comply with the financial covenants or other terms of our debt agreements, we may become subject to cross-default or cross-acceleration provisions that could result in our debt being declared immediately due and payable.
We completed municipal bond financings in July 2022 and August 2022 that raised gross proceeds in the aggregate of $160 million. As of December 31, 2022, we had $214 million of total debt outstanding. In connection with such bond financings, we have entered into various loan agreements, which contain certain financial covenants, that require, among other things, that we operate in a manner and to the extent permitted by applicable law, to produce sufficient gross revenues so as to be at all relevant times in compliance with the terms of such covenants, including that we maintain (i) beginning with the fiscal quarter ending December 31, 2023, a minimum debt service coverage ratio (generally calculated as the aggregate amount of our total gross revenues, minus operating expenses, plus interest, depreciation and amortization expense, excluding extraordinary gains and loss, unrealized and realized gains and losses on investments and non-recurring accounting charges for any period, over our maximum annual debt service requirements, as determined under such loan agreement) that exceeds 1.25x and (ii) beginning with the fiscal quarter ending September 30, 2022, a minimum liquidity of not less than $8 million in the form of unrestricted cash and cash equivalents, plus liquid investments and unrestricted marketable securities at all times.
Subject to the terms of the loan agreements, in the event we are unable to comply with the terms of the financial covenants, we may be required (among other potential remedial actions) to engage an independent consultant to review, analyze and make recommendations with respect to our operations or in some instances, this could result in an event of default and/or the acceleration of our debt obligations under the loan agreements. In addition, the acceleration of our debt obligations may in some instances (as set forth in the Amended and Restated Charter) result in an increase in the dividend rate of the Series A Preferred Stock of 2.00% per annum from the dividend rate otherwise in effect with respect to the Series A Preferred Stock.
As further described under the section of this prospectus entitled “Management’s Discussion and Analysis of Financial Condition and Results of Operations — Liquidity and Capital Resources — Indebtedness,” we have also entered into various term loan agreements and other long-term debt to fund the purchase of additional aircraft and finance the construction of aircraft hangars. Under the terms of such agreements, we are subject to certain financial covenants including, a debt service coverage ratio, current assets to liabilities ratio and senior leverage ratio. As of December 31, 2021 and September 30, 2022, we were in violation of the current assets to liabilities and senior leverage ratios requirements, respectively, under the agreements of our credit facilities with Rocky Mountain Bank. On both occasions, Rocky Mountain Bank agreed to waive the violation of such covenants and not enforce its rights and remedies from the resulting events of default under such credit facilities. Additionally, we were considered in violation of a senior leverage ratio requirement as of June 30, 2023. The calculation for this Rocky Mountain Bank covenant based on quarterly financials is a violation for only June 30, 2023. The acceleration of the obligation has been waived for such quarter. No assurance can be provided that we will be able to satisfy such financial covenants in future periods or that we will be able to obtain a waiver from our lenders in the event of non-compliance. A breach of any of these covenants or the occurrence of other events specified in the agreements or related debt documents could result in an event of default under the same and give rise to the lenders’ right to accelerate our debt obligations thereunder and pursue other remedial actions under our credit facilities and/or trigger a cross-default under our other debt agreements, including our Series 2022 Bonds.
Subject to the limits contained in some of the agreements governing our outstanding debt, we may incur additional debt in the future. Our maintenance of higher levels of indebtedness could have adverse consequences including impairing our ability to obtain additional debt and/or equity financing in the future.
40
Our level of debt places significant demands on our cash resources, which could:
| • | make it more difficult to satisfy our outstanding debt obligations; |
| • | require us to dedicate a substantial portion of our cash for payments related to our debt, reducing the amount of cash flow available for working capital, capital expenditures, entitlement of our real estate assets, contributions to our tax-qualified pension plan, and other general corporate purposes; |
| • | make it more difficult for us to satisfy certain financial tests and ratios under our loan or debt agreements, requiring us to seek waivers from lenders to not enforce its rights and remedies under the applicable agreements; |
| • | limit our flexibility in planning for, or reacting to, changes in the industries in which we compete; |
| • | place us at a competitive disadvantage with respect to our competitors, some of which have lower debt service obligations and greater financial resources than we do; |
| • | limit our ability to borrow additional funds; |
| • | limit our ability to expand our operations through acquisitions; and |
| • | increase our vulnerability to general adverse economic and industry conditions if we are unable to generate sufficient cash flow to service our debt and fund our operating costs, our liquidity may be adversely affected. |
There are no assurances that we will maintain a level of liquidity sufficient to permit us to pay the principal, premium and interest on our indebtedness. In addition to competitive conditions in the industry in which we operate, our financial condition and operating performance are also subject to prevailing economic conditions and certain financial, business and other factors beyond our control.
We do not expect to declare any dividends in the foreseeable future.
We intend to retain future earnings, if any, for future operations and expansion and there are no current plans to pay any cash dividends for the foreseeable future. The declaration, amount, and payment of any future dividends on shares of our common stock will be at the sole discretion of the Board. The Board may take into account general and economic conditions, our financial condition and results of operations, our available cash and current and anticipated cash needs, capital requirements, contractual, legal, tax, and regulatory restrictions, implications on the payment of dividends by us to our stockholders or by our subsidiaries to us, and such other factors as the Board may deem relevant. As a result, you may not receive any return on an investment in our common stock unless you sell our common stock for a price greater than that which you paid for it.
Our variable interest entities (or “VIEs”) may subject us to potential conflicts of interest, and such arrangements may not be as effective as direct ownership with respect to our relationships with the VIEs, which could have a material adverse effect on our ability to effectively control the VIEs and receive economic benefits from them.
We historically had four variable interest entities (or “VIEs”), two of which have been consolidated in Bridger’s financial statements: Northern Fire and Mountain Air. Northern Fire is owned 50% by BAG, one of our wholly-owned subsidiaries, and 50% by a former employee of BAG, who is a Canadian national. We assisted in designing and organizing Northern Fire with a business purpose of employing Canadian aviation professionals for our business. We have a master services agreement with Northern Fire and Bridger Air Tanker, LLC (“Bridger Air”), our wholly-owned subsidiary, to transfer all annual expenses incurred to us in exchange for the Canadian employees to support our water scooper aircraft. Mountain Air was a VIE for 2021, but subsequent to its acquisition on November 7, 2022 for $1.00 it has been a wholly-owned subsidiary.
The contractual arrangements we have with the VIEs may not be as effective as direct ownership in respect of our relationship with the VIE. For example, the VIE and its shareholders could breach their contractual arrangements with us by, among other things, failing to conduct their operations in an acceptable manner or taking other actions that are detrimental to our interests. If we had direct ownership of the VIE, we would be able
41
to exercise our rights as a shareholder to effect changes in the board of directors of the VIE, which in turn could implement changes, subject to any applicable fiduciary obligations, at the management and operational level. However, under the agreements with our VIEs, we rely on the performance by the VIE and its shareholders of their obligations under the contracts to exercise control over the VIE. The shareholders of the consolidated VIE may not act in the best interests of our company or may not perform their obligations under these contracts. Such risks exist throughout the period in which we intend to operate certain portions of our business through the contractual arrangements with the VIE.
As of the date of this prospectus, we are not aware of any conflicts between the shareholders of the VIE and us. However, the shareholders of the VIE may have actual or potential conflicts of interest with us in the future. These shareholders may refuse to sign or breach, or cause the VIE to breach, or refuse to renew, the existing contractual arrangements we have with them and the VIE, which would have a material adverse effect on our ability to effectively control the VIE and receive economic benefits from it. For example, the shareholders may be able to cause our agreements with the VIE to be performed in a manner adverse to us by, among other things, failing to remit payments due under the contractual arrangements to us on a timely basis. We cannot assure you that when conflicts of interest arise any or all of these shareholders will act in the best interests of our company or such conflicts will be resolved in our favor. Currently, we do not have any arrangements to address potential conflicts of interest between these shareholders and our company. If we cannot resolve any conflict of interest or dispute between us and these shareholders, we would have to rely on legal proceedings to enforce such arrangements, which could result in disruption of our business, require us to incur substantial costs and expend additional resources, and subject us to substantial uncertainty as to the outcome of any such legal proceedings.
Our results of operations may be adversely affected by other-than-temporary impairment charges related to our marketable securities.
We make investments in marketable securities classified as available-for-sale debt securities, consisting of commercial paper, corporate bonds and notes, and government securities. As of June 30, 2023, we had $12.6 million of investments in debt securities classified as available-for-sale with short-term maturities of less than one year and carried at fair value. We are exposed to the risk that the issuers of these debt securities may experience significant deterioration in credit quality which could impact the market value of such issuer’s securities. We periodically evaluate our debt securities to determine if market value declines are other-than-temporary. If a decline is determined to be other-than-temporary, the credit related portion of the impairment would be recognized as an adjustment to income.
Early-Stage Company Risks
We have incurred significant losses since inception, and we may not be able to achieve, maintain or increase profitability or positive cash flow.
We have incurred significant losses since inception. While we currently generate revenue from our aerial firefighting services, we are not currently profitable, and it is difficult for us to predict our future operating results. As a result, our losses may be larger than anticipated, and we may not be able to reach profitability in the foreseeable future. Further, our future growth is heavily dependent upon the necessity for our services.
The requirements of being a public company may strain our resources, divert our management’s attention and affect our ability to attract and retain additional executive management and qualified board members.
Prior to Closing, we were not subject to the reporting requirements of the Exchange Act, the Sarbanes-Oxley Act, the Dodd-Frank Wall Street Reform and Consumer Protection Act of 2010, or the listing requirements of Nasdaq. Compliance with these rules and regulations has increased, and will continue to increase, our legal and financial compliance costs, make some activities more difficult, time-consuming, or costly, and increase demand on our systems and resources, particularly after we are no longer an emerging
42
growth company. The Exchange Act requires, among other things, that we file annual, quarterly, and current reports with respect to our business and operating results. The Sarbanes-Oxley Act requires, among other things, that we maintain effective disclosure controls and procedures and internal control over financial reporting. In order to maintain and improve our disclosure controls and procedures and internal control over financial reporting to meet this standard, significant resources and management oversight have been and may in the future be required. As a result, management’s attention may be diverted from other business concerns, which could adversely affect our business and operating results. We may need to hire more employees in the future or engage outside consultants, which would increase our costs and expenses.
In addition, changing laws, regulations, and standards relating to corporate governance and public disclosure are creating uncertainty for public companies, increasing legal and financial compliance costs, and making some activities more time consuming. These laws, regulations, and standards are subject to varying interpretations, in many cases due to their lack of specificity, and, as a result, their application in practice may evolve or otherwise change over time as new guidance is provided by regulatory and governing bodies. This could result in continuing uncertainty regarding compliance matters and higher costs necessitated by ongoing revisions to disclosure and governance practices. We intend to invest resources to comply with evolving laws, regulations, and standards (or changing interpretations of them), and this investment may result in increased selling, general and administrative expenses and a diversion of management’s time and attention from revenue-generating activities to compliance activities. If our efforts to comply with new laws, regulations, and standards differ from the activities intended by regulatory or governing bodies due to ambiguities related to their application and practice, regulatory authorities may initiate legal proceedings against us, and our business may be adversely affected. As a public company, we have also had to incur increased expenses in order to obtain director and officer liability insurance, and we may be required to accept reduced coverage or incur substantially higher costs to maintain the same or similar coverage or obtain coverage in the future. These factors could also make it more difficult for us to attract and retain qualified members of our board of directors, particularly to serve on our audit committee, compensation committee, and nominating and governance committee, and qualified executive officers.
As a result of disclosure of information in the filings required of a public company, our business and financial condition is more visible, which may result in threatened or actual litigation, including by competitors. If such claims are successful, our business and operating results could be adversely affected, and even if the claims do not result in litigation or are resolved in our favor, these claims, and the time and resources necessary to resolve them, could divert the resources of our management and adversely affect our business and operating results. In addition, as a result of our disclosure obligations as a public company, we have reduced flexibility and are under pressure to focus on short-term results, which may adversely affect our ability to achieve long-term profitability.
If we do not develop and implement all required accounting practices and policies, we may be unable to provide the financial information required of a U.S. publicly traded company in a timely and reliable manner.
Prior to the Closing, we were a privately held company, and we were not required to adopt all of the financial reporting and disclosure procedures and controls required of a U.S. publicly traded company. The implementation of all required accounting practices and policies and the hiring of additional financial staff has increased and may continue to increase our operating costs and requires our management to devote significant time and resources to such implementation. If we fail to develop and maintain effective internal controls and procedures and disclosure procedures and controls, we may be unable to provide financial information and required U.S. Securities and Exchange Commission (the “SEC”) reports that are timely and reliable. Any such delays or deficiencies could harm us, including by limiting our ability to obtain financing, either in the public capital markets or from private sources and damaging our reputation, which in either cause could impede our ability to implement our growth strategy. In addition, any such delays or deficiencies could result in our failure to meet the requirements for continued listing of our Common Stock on Nasdaq.
43
The Series 2022 Bonds were marketed on the basis of our compliance with certain green and social bond principles. We may not continue to satisfy such principles and we may be unable to market bonds under such principles in the future.
We have publicly advertised, and the Series 2022 Bonds were marketed on the basis of, our compliance with the core components of International Capital Market Association (ICMA) Green Bond Principles and Social Bond Principles. There is no assurance that the eligible projects to which we allocate proceeds from such Series 2022 Bonds will satisfy, or continue to satisfy, investor criteria and expectations regarding environmental impact and sustainability performance, and no assurance is given that the use or allocation will satisfy present or future investor expectations or requirements, voluntary taxonomies or standards regarding any investment criteria or guidelines with which investors or their investments are required to comply, whether by any present or future applicable laws or regulations, by their own governing rules or investment portfolio mandates, ratings criteria, voluntary taxonomies or standards or other independent expectations. As a result, there may be impacts of failing to satisfy bond conditions under the Series 2022 Bonds, and we may be unable to market future bonds, which may result in increased financing costs for us.
Pursuant to the Jumpstart Our Business Startups Act of 2012 (the “JOBS Act”), our independent registered public accounting firm will not be required to attest to the effectiveness of our internal control over financial reporting pursuant to Section 404 of the Sarbanes-Oxley Act for so long as we are an “emerging growth company.”
A company’s internal control over financial reporting is a process designed by, or under the supervision of, that company’s principal executive and principal financial officers, or persons performing similar functions, and influenced by that company’s board of directors, management and other personnel, to provide reasonable assurance regarding the reliability of financial reporting and the preparation of financial statements in accordance with U.S. GAAP.
Prior to the Closing, Legacy Bridger was not required to evaluate our internal control over financial reporting in a manner that meets the standards of publicly traded companies required by Section 404(a) of the Sarbanes-Oxley Act. We are now required to adhere to these SEC rules, which will require management to certify financial and other information in our quarterly and annual reports and provide an annual management report on the effectiveness of internal controls over financial reporting beginning for the year ending December 31, 2023. Additionally, once we are no longer an emerging growth company, if we are an “accelerated filer” or a “large accelerated filer” (as defined in Rule 12b-2 of the Exchange Act), then we will be required to comply with the independent registered public accounting firm attestation requirement on our internal controls over financial reporting. If we are unable to establish or maintain appropriate internal control over financial reporting or implement these additional requirements in a timely manner or with adequate compliance, it could result in material misstatements in our consolidated financial statements, failure to meet our reporting obligations on a timely basis, increases in compliance costs, and subject us to adverse regulatory consequences, all of which may adversely affect investor confidence in, and the value of, our securities. Furthermore, if some investors find our securities less attractive as a result of the exemptions available us as an emerging growth company, there may be a less active trading market for our securities (assuming a market develops), and the trading price of our securities may be more volatile than that of an otherwise comparable company that does not avail itself of the same or similar exemptions.
44
We have identified material weaknesses in our internal control over financial reporting, which we are in the process of, and are focused on, remediating. If we are unable to maintain an effective system of internal control over financial reporting, we may not be able to accurately report our financial results in a timely manner, which may adversely affect investor confidence in us and materially and adversely affect our business and operating results.
A material weakness is a deficiency or combination of deficiencies, in internal control over financial reporting, such that there is a reasonable possibility that a material misstatement of our annual or interim financial statements will not be prevented or detected on a timely basis.
We have identified material weaknesses in our internal control over financial reporting, which we are in the process of, and are focused on, remediating. The first material weakness is related to properly accounting for complex transactions within our financial statement closing and reporting process. The second material weakness arises from our failure to design and maintain effective IT general controls over the IT systems used within the processing of key financial transactions. Specifically, we did not design and maintain user access controls to ensure appropriate segregation of duties and that adequately restrict user and privileged access to financial applications, programs, and data to appropriate company personnel.
Additionally, we identified a material weakness in our internal control over financial reporting related to the period end account reconciliation review and entity level financial statement review controls which did not operate within a sufficient level of precision.
We have begun the process of, and are focused on, designing and implementing effective internal controls measures to improve our internal control over financial reporting and remediate the material weaknesses. Future remediation of the material weaknesses is subject to ongoing management evaluation and will require validation and testing of the design and operating effectiveness of internal controls over a sustained period of financial reporting cycles.
Although we plan to complete this remediation process as quickly as possible, we are unable, at this time, to estimate how long it will take, and our efforts may not be successful in remediating the identified material weaknesses. In addition, even if we are successful in strengthening our controls and procedures, we can give no assurances that in the future such controls and procedures will be adequate to prevent or identify errors or irregularities or to facilitate the fair preparation and presentation of our consolidated financial statements. Any failure to design or maintain effective internal controls over financial reporting or any difficulties encountered in their implementation or improvement could increase compliance costs, negatively impact share trading prices, or otherwise harm our operating results or cause us to fail to meet our reporting obligations.
Risks Related to this Offering
If you purchase shares of our Common Stock in this offering, you will incur immediate and substantial dilution in the book value of your shares.
Investors purchasing Common Stock in this offering will pay a price per share that substantially exceeds the as adjusted book value per share of our tangible assets after subtracting our liabilities. As a result, investors purchasing Common Stock in this offering will incur immediate dilution of $ per share, after deducting underwriting discounts and commissions and estimated offering expenses payable by us. Furthermore, if the underwriters exercise their over-allotment option, or outstanding options or warrants are exercised, you could experience further dilution. For more information on the dilution you may suffer as a result of investing in this offering, see the section of this prospectus entitled “Dilution.” As a result of the dilution to investors purchasing shares in this offering, investors may receive significantly less than the purchase price paid in this offering, if anything, in the event of our liquidation.
45
Our management team will have broad discretion over the use of the net proceeds from this offering, and you may not agree with how we use the proceeds and the proceeds may not be invested successfully.
Our management team will have broad discretion as to the use of the net proceeds from this offering, and we could use such proceeds for purposes other than those contemplated at the time of commencement of this offering. Accordingly, you will be relying on the judgment of our management team with regard to the use of those net proceeds, and you will not have the opportunity, as part of your investment decision, to assess whether the proceeds are being used appropriately. It is possible that, pending their use, we may invest those net proceeds in a way that does not yield a favorable, or any, return for us. The failure of our management team to use such funds effectively could have a material adverse effect on our business, financial condition, operating results and cash flows.
Risks Related to the Ownership of Our Securities
The price of our Common Stock and Warrants are likely to be highly volatile, and you may lose some or all of your investment.
The price of our Common Stock and Warrants may fluctuate significantly due to a number of factors, some of which may be beyond our control, including those factors discussed in this “Risk Factors” section and many others, such as:
| • | actual or anticipated fluctuations in our financial condition and operating results, including fluctuations in our quarterly and annual results; |
| • | developments involving our competitors; |
| • | changes in laws and regulations affecting our business; |
| • | variations in our operating performance and the performance of our competitors in general; |
| • | the public’s reaction to our press releases, our other public announcements and our filings with the SEC; |
| • | additions and departures of key personnel; |
| • | announcements of significant acquisitions, strategic partnerships, joint ventures or capital commitments by us or our competitors; |
| • | our failure to meet the estimates and projections of the investment community or that we may otherwise provide to the public; |
| • | publication of research reports about us or our industry, or positive or negative recommendations or withdrawal of research coverage by securities analysts; |
| • | changes in the market valuations of similar companies; |
| • | overall performance of the equity markets; |
| • | sales of our Common Stock and Warrants by us or our stockholders in the future; |
| • | trading volume of our Common Stock and Warrants; |
| • | significant lawsuits, including shareholder litigation; |
| • | failure to comply with the requirements of Nasdaq; |
| • | the impact of any natural disasters or public health emergencies, such as the COVID-19 pandemic; |
| • | general economic, industry and market conditions other events or factors, many of which are beyond our control; and |
| • | changes in accounting standards, policies, guidelines, interpretations or principles. |
46
These market and industry factors may materially reduce the market price of our Common Stock and our Warrants regardless of our operating performance.
Our Common Stock is subject to restrictions on ownership by non-U.S. citizens, which could require divestiture by non-U.S. citizen stockholders and could have a negative impact on the transferability of our Common Stock, its liquidity and market value, and such restrictions may deter a potential change of control transaction.
Under the Amended and Restated Charter and the Amended and Restated Bylaws, we have limited the ownership of non-U.S. citizens to 24.9% of the aggregate votes of all outstanding equity securities of our company or 49.0% of the aggregate number of outstanding equities securities in compliance with the regulations set forth by the FAA and the DOT. As a result, if we approach these limits, non-U.S. citizen demand for our equity securities may be reduced, and the price of our Common Stock may suffer.
We may issue additional shares of our Common Stock or other equity securities, which would dilute your ownership interest in us and may depress the market price of our Common Stock.
We may issue additional shares of our Common Stock or other equity securities in the future in connection with, among other things, future acquisitions, repayment of outstanding indebtedness or grants under the Omnibus Incentive Plan and ESPP without stockholder approval in a number of circumstances. Our issuance of additional our Common Stock or other equity securities could have one or more of the following effects:
| • | our existing stockholders’ proportionate ownership interest in us will decrease; |
| • | the amount of cash available per share, including for payment of dividends in the future, may decrease; |
| • | the relative voting strength of each previously outstanding share of our Common Stock may be diminished; and |
| • | the market price of our Common Stock may decline. |
We are an “emerging growth company” and a “smaller reporting company” within the meaning of the Securities Act, and if we take advantage of certain exemptions from disclosure requirements available to “emerging growth companies” or “smaller reporting companies,” this could make our securities less attractive to investors and may make it more difficult to compare our performance with other public companies.
We are an “emerging growth company” within the meaning of the Securities Act, as modified by the JOBS Act, and we may take advantage of certain exemptions from various reporting requirements that are applicable to other public companies that are not “emerging growth companies” including, but not limited to, not being required to comply with the auditor attestation requirements of Section 404, reduced disclosure obligations regarding executive compensation in our periodic reports and proxy statements, and exemptions from the requirements of holding a nonbinding advisory vote on executive compensation and stockholder approval of any golden parachute payments not previously approved. As a result, our stockholders may not have access to certain information they may deem important. We could be an emerging growth company for up to five years, although circumstances could cause us to lose that status earlier, including if the market value of our common stock held by non-affiliates exceeds $700 million as of the end of any second quarter of a fiscal year, in which case we would no longer be an emerging growth company as of the last day of such fiscal year. We cannot predict whether investors will find our securities less attractive because we will rely on these exemptions. If some investors find our securities less attractive as a result of our reliance on these exemptions, the trading prices of our securities may be lower than they otherwise would be, there may be a less active trading market for our securities and the trading prices of our securities may be more volatile.
Further, Section 102(b)(1) of the JOBS Act exempts “emerging growth companies” from being required to comply with new or revised financial accounting standards until private companies (that is, those that have not
47
had a registration statement under the Securities Act declared effective or do not have a class of securities registered under the Exchange Act) are required to comply with the new or revised financial accounting standards. The JOBS Act provides that a company can elect to opt out of the extended transition period and comply with the requirements that apply to “non-emerging growth companies” but any such election to opt out is irrevocable. We have elected not to opt out of such extended transition period, which means that when a standard is issued or revised and it has different application dates for public or private companies, we, as an “emerging growth company”, can adopt the new or revised standard at the time private companies adopt the new or revised standard. This may make comparison of our financial statements with another public company that is not an “emerging growth company” or is an “emerging growth company” which has opted out of using the extended transition period difficult or impossible because of the potential differences in accounting standards used.
Additionally, we are a “smaller reporting company” as defined in Item 10(f)(1) of Regulation S-K. Smaller reporting companies may take advantage of certain reduced disclosure obligations, including, among other things, providing only two years of audited financial statements. We will remain a smaller reporting company until the last day of the fiscal year in which (i) the market value of our common stock held by non-affiliates is greater than or equal to $250 million as of the end of that fiscal year’s second fiscal quarter, and (ii) our annual revenues are greater than or equal to $100 million during the last completed fiscal year or the market value of our common stock held by non-affiliates exceeds $700 million as of the end of that fiscal year’s second fiscal quarter. To the extent we take advantage of such reduced disclosure obligations, it may also make comparison of our financial statements with other public companies difficult or impossible.
Provisions in the Amended and Restated Charter, the Amended and Restated Bylaws, the Stockholders Agreement and Delaware law could discourage a takeover that stockholders may consider favorable which could limit the price investors might be willing to pay in the future for our Common Stock and may lead to entrenchment of management.
The Amended and Restated Charter and the Amended and Restated Bylaws contain provisions that could significantly reduce the value of our securities to a potential acquiror or delay or prevent changes in control or changes in our management without the consent of the Board. Such provisions may discourage unsolicited takeover proposals that stockholders may consider to be in their best interests. Our organizational documents include the following:
| • | a classified board of directors with three-year staggered terms, which may delay the ability of stockholders to change the membership of a majority of the Board; |
| • | no cumulative voting in the election of directors, which limits the ability of minority stockholders to elect director candidates; |
| • | the exclusive right of the Board, unless the Board grants such a right to the holders of any series of preferred stock, to elect a director to fill a vacancy created by the expansion of the Board or the resignation, death or removal of a director, which prevents stockholders from being able to fill vacancies on the Board; |
| • | the prohibition on removal of directors without cause; |
| • | the ability of the Board to authorize the issuance of shares of preferred stock and to determine the price and other terms of those shares, including preferences and voting rights, without stockholder approval, which could be used to significantly dilute the ownership of a hostile acquiror; |
| • | the ability of the Board to alter the Amended and Restated Bylaws without obtaining stockholder approval; |
| • | the required approval of at least 66-2/3% of the shares of our Common Stock entitled to vote to amend or repeal the Amended and Restated Bylaws or amend, alter or repeal certain provisions of the Amended and Restated Charter; |
48
| • | a prohibition on stockholder action by written consent, which forces stockholder action to be taken at an annual or special meeting of our stockholders; |
| • | an exclusive forum provision providing that the Court of Chancery of the State of Delaware will be the exclusive forum for certain actions and proceedings; |
| • | the requirement that a special meeting of stockholders may be called only by the Board, the chair of the Board, the chief executive officer or the president, which may delay the ability of our stockholders to force consideration of a proposal or to take action, including the removal of directors; and |
| • | advance notice procedures that stockholders must comply with in order to nominate candidates to the Board or to propose matters to be acted upon at a stockholders’ meeting, which may discourage or deter a potential acquiror from conducting a solicitation of proxies to elect the acquiror’s own slate of directors or otherwise attempting to obtain control of the company. |
We are not subject to the anti-takeover provisions contained in Section 203 of the Delaware General Corporation Law. However, we may not, engage in a business combination with any holder of 15% or more of our capital stock unless the holder has held the stock for three years or, among other exceptions, the Board has approved the transaction.
Additionally, the Stockholders Agreement permits Blackstone to nominate up two directors to our board of directors while Blackstone holds a requisite amount of our Common Stock, which could have the effect of increasing the difficulty of shareholders engaged in a proxy campaign against an incumbent board of directors of the Company. Individually and collectively, these anti-takeover defenses could discourage, delay, or prevent a transaction involving a change in control of the Company. These provisions could also discourage proxy contests and make it more difficult for you and other stockholders to elect directors of your choosing and cause the Company to take corporate actions other than those you desire.
There can be no assurance that we will be able to comply with the continued listing standards of Nasdaq. Nasdaq may delist our securities from trading on its exchange, which could limit investors’ ability to make transactions in our securities and subject us to additional trading restrictions.
Our Common Stock and the Public Warrants are listed on Nasdaq under the symbols “BAER” and “BAERW,” respectively. We are required to demonstrate compliance with Nasdaq’s continued listing requirements in order to continue to maintain the listing of our securities on Nasdaq. If Nasdaq delists our securities from trading on its exchange and we are not able to list our securities on another national securities exchange, our securities could be quoted on an over-the-counter market. If this were to occur, we could face significant adverse consequences, including:
| • | a limited availability of market quotations for our securities; |
| • | reduced liquidity for our securities; |
| • | a determination that our Common Stock is a “penny stock” which will require brokers trading in our Common Stock to adhere to more stringent rules and possibly result in a reduced level of trading activity in the secondary trading market for our securities; |
| • | a limited amount of news and analyst coverage; and |
| • | a decreased ability to issue additional securities or obtain additional financing in the future. |
The National Securities Markets Improvement Act of 1996, which is a federal statute, prevents or preempts the states from regulating the sale of certain securities, which are referred to as “covered securities.” Because our Common Stock and Bridger Public Warrants are listed on Nasdaq, our Common Stock and Bridger Public Warrants qualify as covered securities. Although states are preempted from regulating the sale of our securities, the federal statute does allow states to investigate companies if there is a suspicion of fraud. If there is a finding
49
of fraudulent activity, then states can regulate or bar the sale of covered securities in a particular case. Further, if we were no longer listed on Nasdaq, our securities would not be covered securities and we would be subject to regulation in each state in which we offer our securities.
The holders of shares of Series A Preferred Stock have rights, preferences and privileges that are not held by, and are preferential to, the rights of holders of our Common Stock. We may be required, under certain circumstances, to repurchase the outstanding shares of Series A Preferred Stock for cash, and such obligations could adversely affect our liquidity and financial condition.
In connection with the Business Combination, we issued 315,789.473684 shares of Series A Preferred Stock in respect of certain equity securities of Bridger. The Series A Preferred Stock is convertible non-participating preferred stock, with a conversion price of $11.00 per share and accrues dividends at a rate of 7.0% per annum (payable in cash or in-kind, subject to specified limitations) to but excluding April 25, 2028, 9.0% per annum from (and including) April 25, 2028 to but excluding April 25, 2029, and 11.00% per annum from (and including) April 25, 2029.
In addition, under the terms of the Series A Preferred Stock, we may, at our option, redeem all or any portion of the outstanding shares of Preferred Stock under certain circumstances any time after April 25, 2027, and we must redeem the shares by on or before April 25, 2032. Upon certain fundamental changes to us and our ownership structure, the holders of Series A Preferred Stock may require us to redeem their shares of Series A Preferred Stock. The redemption price is generally equal to original purchase price of the Series A Preferred Stock plus all accrued and unpaid dividends thereon, and in certain circumstances, also includes a “make-whole” payment. Our obligations to the holders of Preferred Stock could also limit our ability to obtain additional financing or increase our borrowing costs, which could have an adverse effect on our financial condition. The preferential rights could also result in divergent interests between the holders of the Series A Preferred Stock and our common stockholders. If we elect to redeem all or a portion of the Series A Preferred Stock, our liquidity, financial condition, and amount of cash available for working capital, capital expenditures, growth opportunities, acquisitions, and other general corporate purposes would be adversely affected.
The Series A Preferred Stock may be converted at any time at the option of the holder into shares of our Common Stock. The conversion price of the Series A Preferred Stock is subject to customary anti-dilution adjustments, including in the event of any stock split, stock dividend, recapitalization or similar event. Adjustments to the conversion price could dilute the ownership interest of our common stockholders. Any conversion of the Series A Preferred Stock may significantly dilute our common stockholders and adversely affect both our net income per share and the market price of our common stock.
The holders of Series A Preferred Stock have consent rights over the issuance of any equity securities senior or pari passu with the Series A Preferred Stock; any amendments to the Amended and Restated Charter that would adversely affect the rights, preferences or privileges of the Series A Preferred Stock; payment of dividends; mergers, consolidations, or a sale of substantially all of our assets and liquidations, dissolutions and winding up, in certain cases, unless we satisfy certain conditions. Otherwise, holders of the Series A Preferred Stock have no voting rights with respect to the election of directors or other matters submitted for a vote of holders of our Common Stock.
A small number of our stockholders could significantly influence our business.
As of September 30, 2023, the executive officers of Bridger and Mr. Matthew Sheehy (a co-founder and director of Bridger and the brother of Mr. Timothy Sheehy, the Bridger CEO), collectively beneficially own 41.3% of the outstanding Common Stock, assuming no shares of Series A Preferred Stock have been converted. As a result, Bridger has a small number of significant stockholders who could significantly influence its business and operations.
50
In addition, the BTO Stockholders collectively beneficially own 21.5% (assuming no shares of Series A Preferred Stock have been converted) of the outstanding Common Stock as of September 30, 2023. The BTO Stockholders may also exercise influence over the business through their rights under the Stockholder Agreement, pursuant to which, among other matters, the BTO stockholders can nominate up to two (2) directors for election to the Board and require at least one director nominated by the BTO Stockholders to be included on any committee of the Board, in each case subject to the terms and conditions set forth in the Stockholders Agreement.
As indicated above, Bridger has a few significant stockholders who own a substantial percentage of the outstanding Common Stock. These few significant stockholders, either individually or acting together, are able to exercise significant influence over matters requiring stockholder approval, including the election of directors and approval of significant corporate transactions, such as a merger or other sale of Bridger or its assets. In addition, Bridger’s executive officers and Mr. Matthew Sheehy collectively beneficially own a majority of the outstanding Common Stock (assuming no shares of Series A Preferred Stock have been converted) and may be able to control the outcome of most matters submitted to Bridger’s stockholders for a stockholder vote, including director elections. This concentration of ownership may make it more difficult for other stockholders to effect substantial changes in Bridger, may have the effect of delaying, preventing or expediting, as the case may be, a change in control of Bridger and may adversely affect the market price of our Common Stock. Further, the possibility that one or more of these significant stockholders may sell all or a large portion of their Common Stock in a short period of time could adversely affect the trading price of our Common Stock. The interests of these significant stockholders may not be in the best interests of all stockholders.
For additional information about the holdings of certain of our beneficial owners, see the section of this prospectus entitled “Principal Stockholders.”
If our estimates or judgments relating to its critical accounting policies prove to be incorrect or financial reporting standards or interpretations change, our results of operations could be adversely affected.
The preparation of financial statements in conformity with generally accepted accounting principles in the United States requires management to make estimates and assumptions that affect the amounts reported in the financial statements and accompanying notes. We will base our estimates on historical experience, known trends and events, and various other factors that it believes to be reasonable under the circumstances, as provided in the section of this prospectus entitled “Management’s Discussion and Analysis of Financial Condition and Results of Operations — Critical Accounting Policies and Estimates.” The results of these estimates form the basis for making judgments about the carrying values of assets and liabilities that are not readily apparent from other sources. Significant assumptions and estimates used in preparing our financial statements include: (a) excess and aging aircraft support parts reserves, (b) allowance for doubtful accounts, (c) useful lives of property, plant and equipment, net (d) impairment of long-lived assets, goodwill and other intangible assets, (e) disclosure of fair value of financial instruments, (f) variable interest entities, (g) accounting for Legacy Bridger Series A Preferred Shares, Legacy Bridger Series B Preferred Shares and Legacy Bridger Series C Preferred Shares, (h) revenue recognition,(i) estimates and assumptions made in determining the carrying values of goodwill and other intangible assets and (j) incentive units. Our results of operations may be adversely affected if our assumptions change or if actual circumstances differ from those in our assumptions, which could cause its results of operations to fall below the expectations of securities analysts and investors, resulting in a decline in the trading price of our Common Stock.
Additionally, we will regularly monitor its compliance with applicable financial reporting standards and review new pronouncements and drafts thereof that are relevant to it. As a result of new standards, changes to existing standards and changes in their interpretation, we might be required to change its accounting policies, alter its operational policies, and implement new or enhance existing systems so that they reflect new or amended financial reporting standards, or we may be required to restate its published financial statements. Such changes to existing standards or changes in their interpretation may have an adverse effect on its reputation, business, financial position, and profit.
51
If securities or industry analysts do not publish research or reports about us or publish negative reports, then the price of our securities and trading volumes could decline.
The trading market for our Common Stock and Warrants will depend, in part, on the research and reports that securities or industry analysts publish about us. We do not have any control over these analysts. If our financial performance fails to meet analyst estimates or one or more of the analysts who cover us downgrade our Common Stock or change their opinion, then the trading prices of our securities would likely decline. If one or more of these analysts cease coverage of us or fail to regularly publish reports on us, we could lose visibility in the financial markets, which could cause the trading prices of our securities or trading volume to decline.
Volatility in our share price could subject us to securities class action litigation.
In the past, securities class action litigation has often been brought against a company following a decline in the market price of its securities. If we face such litigation, it could result in substantial costs and a diversion of management’s attention and resources, which could harm our business.
Future sales, or the perception of future sales, of a substantial number of shares of our Common Stock by us or our stockholders in the public market may cause the price of our Common Stock and Warrants to decline.
If we or our existing stockholders sell, or indicate an intention to sell, substantial amounts of shares of our Common Stock or Warrants in the public market, the trading price of our Common Stock or Warrants could decline. In addition, the perception that such sales could occur, could harm the prevailing market price of shares of our Common Stock or Warrants. These sales, or the possibility that these sales may occur, also might make it more difficult for us to sell equity securities in the future at a time and at a price that we deem appropriate and to raise additional funds through future offerings of our shares of Common Stock or other securities.
Additionally, following the expiration of the lock-up agreements described under “Underwriting — Lock-Up Agreements” and the immediately succeeding paragraph, we, as well as our directors, executive officers and certain other significant holders, will no longer be restricted by such lock-up agreements from selling shares of our Common Stock held by them, other than by applicable securities laws. The holders of currently restricted shares will hold large amounts of our Common Stock and may sell those shares, when allowed to do so under applicable securities laws, in block trades or other large dispositions. The sale or possibility of sale of these shares could have an effect of increasing the volatility in our share price or the market price of our Common Stock could decline if the holders of currently restricted shares sell them or are perceived by the market as intending to sell them.
Further, subject to certain exceptions, the Amended and Restated Registration Rights Agreement provides for certain restrictions on transfer with respect to our securities, including founder shares, Private Placement Warrants, and securities held by directors and officers of JCIC and Bridger and certain equity holders of Bridger. Such restrictions began on the Closing Date and will end (i) with respect to the founder shares and shares held by certain equity holders of Bridger (other than the BTO Stockholders), at the earliest of (A) one year after the Closing Date and (B) the first date on which (x) the last reported sale price of a share of our Common Stock equals or exceeds $12.00 per share for any 20 trading days within any 30-trading day period commencing at least 150 days after the Closing Date or (y) JCIC completing a liquidation, merger, share exchange, reorganization or other similar transaction that results in our stockholders having the right to exchange their shares of Common Stock for cash, securities or other property; (ii) with respect to the Private Placement Warrants, that are held by the initial purchasers of such warrants (or permitted transferees under the Amended and Restated Registration Rights Agreement), and any of the shares of our Common Stock issued or issuable upon the exercise or conversion of such warrants and that are held by the initial purchasers of the applicable warrants being converted (or permitted transferees under the Amended and Restated Registration Rights Agreement), the period ending 30 days after the closing and (iii) with respect to the shares held by BTO Stockholders, at the earliest of (A) six months after the Closing Date and (B) the first date on which (x) the last reported sale price of a share of our
52
Common Stock equals or exceeds $12.00 per share for any 20 trading days within any 30-trading day period or (y) Bridger completing a liquidation, merger, share exchange, reorganization or other similar transaction that results in our stockholders having the right to exchange their shares of our Common Stock for cash, securities or other property. Additionally, we may agree to waive and release the holders of our securities from the applicable restrictions on transfer under the Amended and Restated Registration Rights Agreement, or to amend the duration of such restrictions on transfer.
If we agree to waive and release our equityholders subject to lock-up restrictions, or as any restrictions on resale end or following the expiration of the applicable lock-up period, such equityholders will not be restricted from selling shares of our Common Stock held by them, other than by applicable securities laws. As restrictions on resale end, lock-up periods expire or the restrictions described above are otherwise waived, and registration statements (filed after the Closing Date to provide for the resale of such shares from time to time) are available for use, the sale or possibility of sale of these shares could have the effect of increasing the volatility in the share price of our Common Stock or the market price of our Common Stock and Warrants could decline if the holders of currently restricted shares sell them or are perceived by the market as intending to sell them. These factors could also make it more difficult for us to raise additional funds through future offerings of Common Stock or other securities.
Warrants are exercisable for our Common Stock, and if exercised, will increase the number of shares eligible for future resale in the public market and result in dilution to our stockholders.
Outstanding Warrants to purchase an aggregate of 26,649,874 shares of our Common Stock became exercisable in accordance with the terms of the Warrant Agreement governing those securities. These Warrants became exercisable commencing on February 23, 2023 (30 days after the completion of the Business Combination). The exercise price of these Warrants is $11.50 per share, subject to certain potential future adjustments. To the extent such warrants are exercised, additional shares of our Common Stock will be issued, which will result in dilution to our holders and increase the number of shares eligible for resale in the public market. Sales of substantial numbers of such shares in the public market or the fact that the Warrants may be exercised could adversely affect the market price of our Common Stock. The price of our Common Stock may remain below $11.50 until expiration of the Warrant exercise period and as such, the Warrants may expire worthless. See the section of this prospectus entitled “— The price of our Common Stock may remain below $11.50 until expiration of the Warrant exercise period, and the Warrants may expire worthless and the terms of the Warrants may be amended in a manner adverse to a holder if holders of at least 65% of (i) the then-outstanding Public Warrants and/or (ii) the then-outstanding Private Placement Warrants, as applicable, approve of such amendment.”
General Risk Factors
The COVID-19 pandemic or other future global health emergencies may materially and adversely impact our business, operating results, financial condition and liquidity. If the impacts from the COVID-19 pandemic extend beyond our assumed timelines or new global health emergencies emerge, our actual results may vary significantly from our expectations.
In response to the spread of COVID-19, in 2020 the United States government, state governments, local governments, foreign governments and private industries took measures to limit social interactions in an effort to limit the spread of COVID-19, including “stay in place” orders for their residents. Although many of these restrictions have been lifted, the effects of the spread of COVID-19 and the government and private responses to the spread continue to rapidly evolve, including in response to new COVID-19 strains or other potential global health emergencies.
COVID-19 has caused significant disruptions to the global, national and State economy. The extent to which COVID-19 impacts the Company’s operations and their financial condition will depend on future developments, which are highly uncertain and cannot be predicted, including the duration of the outbreak and measures taken
53
to address the outbreak. For example, as mentioned above, the carding and registration process for the first two Viking Air CL-415EAFs delivered to the Company were delayed by three months as a result of restrictions put in place due to the COVID-19 pandemic.
In addition, the Viking Air CL-415EAF aircraft are produced at a manufacturer in Canada. Canada has highly specific COVID-19 safeguards and governmental orders in place (and may place more restrictions in place in the future) that could adversely affect the timing of delivery of future Viking Air CL-415EAF aircraft.
Net earnings and net assets could be materially affected by an impairment of goodwill.
We have, or in the future may have, a significant amount of goodwill recorded on our consolidated balance sheet. We are required at least annually to test the recoverability of goodwill. The recoverability test of goodwill is based on the current fair value of our identified reporting units. Fair value measurement requires assumptions and estimates of many critical factors, including revenue and market growth, operating cash flows and discount rates. If general market conditions deteriorate in portions of our business, we could experience a significant decline in the fair value of reporting units. This decline could lead to an impairment of all or a significant portion of the goodwill balance, which could materially affect our U.S. GAAP net earnings and net assets.
Changes in tax laws or regulations may increase tax uncertainty and adversely affect results of our operations and our effective tax rate.
The Company is subject to taxes in the United States and certain foreign jurisdictions. Due to economic and political conditions, tax rates in various jurisdictions, including the United States, may be subject to change. The Company’s future effective tax rates could be affected by changes in the mix of earnings in countries with differing statutory tax rates, changes in the valuation of deferred tax assets and liabilities and changes in tax laws or their interpretation. In addition, the Company may be or become subject to income tax audits by various tax jurisdictions. For example, the Inflation Reduction Act of 2022, which was recently enacted, imposed a 1% excise tax on certain share repurchases by publicly traded corporations, which may apply to share repurchases by the Company in the future, and imposed a 15% minimum tax on certain large corporations. Although the Company believes its income tax liabilities are reasonably estimated and accounted for in accordance with applicable laws and principles, an adverse resolution by one or more taxing authorities could have a material impact on the results of its operations.
Certain U.S. state tax authorities may assert that we have a state nexus and seek to impose state and local income taxes which could harm our results of operations.
There is a risk that certain state tax authorities where we do not currently file a state income tax return could assert that we are liable for state and local income taxes based upon income or gross receipts allocable to such states. States are becoming increasingly aggressive in asserting a nexus for state income tax purposes. If a state tax authority successfully asserts that our activities give rise to a nexus, we could be subject to state and local taxation, including penalties and interest attributable to prior periods. Such tax assessments, penalties and interest may adversely impact our results of operations.
The Amended and Restated Charter requires, to the fullest extent permitted by law, that derivative actions brought in our name, actions against our directors, officers, other employees or stockholders for breach of fiduciary duty and other similar actions may be brought only in the Court of Chancery in the State of Delaware, which may have the effect of discouraging lawsuits against our directors, officers, other employees or stockholders.
The Amended and Restated Charter provides that, unless a majority of the Board of Directors, acting on behalf of Bridger, consents in writing to the selection of an alternative forum (which consent may be given at any time, including during the pendency of litigation), the Court of Chancery of the State of Delaware (or, if the Court of Chancery does not have jurisdiction, another state court located within the State of Delaware or, if no
54
court located within the State of Delaware has jurisdiction, the federal district court for the District of Delaware), to the fullest extent permitted by law, shall be the sole and exclusive forum for (i) any derivative action or proceeding brought on behalf of the Corporation, (ii) any action asserting a claim of breach of a fiduciary duty owed by any current or former director, officer or other employee of the Corporation to the Corporation or the Corporation’s stockholders, (iii) any action asserting a claim against the Corporation or any of its directors, officers or other employees arising pursuant to any provision of the DGCL, the Amended and Restated Charter or the Amended and Restated Bylaws (in each case, as may be amended from time to time), (iv) any action asserting a claim against the Corporation or any of its directors, officers or other employees governed by the internal affairs doctrine of the State of Delaware or (v) any other action asserting an “internal corporate claim,” as defined in Section 115 of the DGCL, in all cases subject to the court’s having personal jurisdiction over all indispensable parties named as defendants. Unless a majority of the Board, acting on behalf of the Corporation, consents in writing to the selection of an alternative forum (which consent may be given at any time, including during the pendency of litigation), the federal district courts of the United States of America, to the fullest extent permitted by law, shall be the sole and exclusive forum for the resolution of any action asserting a cause of action arising under the Securities Act.
We believe these provisions may benefit us by providing increased consistency in the application of Delaware law and federal securities laws by chancellors and judges, as applicable, particularly experienced in resolving corporate disputes, efficient administration of cases on a more expedited schedule relative to other forums and protection against the burdens of multi-forum litigation. Alternatively, if a court were to find these provisions of the Amended and Restated Charter inapplicable or unenforceable with respect to one or more of the specified types of actions or proceedings, we may incur additional costs associated with resolving such matters in other jurisdictions, which could materially adversely affect our business, financial condition, and results of operations and result in a diversion of the time and resources of our management and Board of Directors. For example, Section 22 of the Securities Act creates concurrent jurisdiction for federal and state courts over all suits brought to enforce any duty or liability created by the Securities Act or the rules and regulations thereunder. Accordingly, there is uncertainty as to whether a court would enforce such a forum selection provision as written in connection with claims arising under the Securities Act.
We may be required to take write-downs or write-offs, restructuring and impairment or other charges that could have a significant negative effect on our financial condition, results of operations and the price of our securities, which could cause you to lose some or all of your investment.
Factors outside of our control may, at any time, arise. As a result of these factors, we may be forced to later write-down or write-off assets, restructure operations, or incur impairment or other charges that could result in reporting losses. Unexpected risks may arise, and previously known risks may materialize. Even though these charges may be non-cash items and therefore not have an immediate impact on our liquidity, we must report charges of this nature which could contribute to negative market perceptions about us or our securities. In addition, charges of this nature may cause us to be unable to obtain future financing on favorable terms or at all.
55
USE OF PROCEEDS
We estimate that the net proceeds to us from the offering will be approximately $ million, or approximately $ million if the underwriters exercise their option to purchase additional shares in full, after deducting the underwriting discounts and commissions and estimated offering expenses payable by us.
We intend to use the net proceeds of this offering to finance the cash purchase price for the Spanish Super Scooper Acquisition and the Bighorn Acquisition, and the remainder for general corporate purposes, including funding the upgrade costs for the acquired Super Scoopers and other working capital needs.
On July 21, 2023, we entered into the Bighorn Purchase Agreement through our subsidiary Bridger Bighorn LLC, with the Bighorn Sellers, pursuant to which we agreed to acquire 100% of the outstanding equity interests of Bighorn. The aggregate consideration for the Bighorn Acquisition is $39.25 million, with $14.75 million payable in unregistered shares of Common Stock, and the remainder of $24.50 million payable in cash, as may be adjusted pursuant to the terms of the Bighorn Purchase Agreement, including for Bighorn’s cash, indebtedness, and net working capital as of the closing of the Bighorn Acquisition. The consummation of the Bighorn Acquisition is expected to be completed in the first half of the fourth quarter of 2023, subject to the satisfaction or waiver of customary closing conditions, including the payment of the approximately $24.50 million cash consideration to the Bighorn Sellers.
On September 20, 2023, we announced that our bid (via a public tender process) to purchase four Super Scoopers from the Spanish Ministry for Ecological Transition and Demographic Challenge had been accepted by the Spanish government. Per the terms of the bid, we will purchase the four Super Scoopers from the Spanish government for approximately €40.3 million (approximately $42.5 million as of October 16, 2023) in cash. The closing of the Spanish Super Scooper Acquisition is expected to be completed in the first half of the fourth quarter of 2023 and is subject to the terms and conditions of the Spanish public tender process.
This offering is not conditioned upon the consummation of either of the Bighorn Acquisition or the Spanish Super Scooper Acquisition. If either the Bighorn Acquisition or the Spanish Super Scooper Acquisition is not consummated, we intend to use the net proceeds from this offering for general corporate purposes, including working capital, capital expenditures and/or the financing of other potential future acquisitions. The precise amount and timing of the application of such proceeds will depend upon our liquidity needs and the availability and cost of other capital. Accordingly, we will have broad discretion in the way that we use the remaining net proceeds of the offering after payment of the cash purchase price for the Bighorn Acquisition and the Spanish Super Scooper Acquisition. Pending their ultimate use, we intend to invest the net proceeds in cash equivalents or short-term securities.
56
MARKET INFORMATION FOR COMMON STOCK AND DIVIDEND POLICY
Market Information and Holders
Our Common Stock and Warrants are currently listed on Nasdaq under the symbols “BAER” and “BAERW,” respectively.
As of September 30, 2023 there were 60 holders of record of our Common Stock and 4 holders of record of our Warrants.
Dividend Policy
We have never declared or paid any cash dividends on our Common Stock, Series A Preferred Stock or the Warrants to date. Any determination to pay cash dividends or to institute a dividend policy will be at the discretion of the Board and will depend upon a number of factors, including our results of operations, financial condition, future prospects, contractual restrictions, covenants in the agreements governing current and future indebtedness, industry trends, restrictions imposed by applicable law and other factors the Board deems relevant. We currently intend to retain any future earnings for the development, operation and expansion of the business, and we do not anticipate declaring or paying any cash dividends on our Common Stock for the foreseeable future.
Notwithstanding the foregoing, our holders of the Series A Preferred Stock are entitled to receive dividends to be paid twice a year, in cash or, at our election, by increasing the per share liquidation preference for such shares of Series A Preferred Stock (such liquidation preference is equal to the initial issuance price plus all accrued and unpaid dividends, whether or not declared). The dividends on the Series A Preferred Stock accrue daily and are computed on the basis of a 365-day year, at a compounding rate initially anticipated to be 7.00% per annum. Such rate will increase to 9.00% per for the period from (and including) April 25, 2028 to (but excluding) April 25, 2029 and eventually will increase to 11.00% per annum from and after April 25, 2029 and subject to further increase upon the occurrence of certain events. No dividends shall be paid or payable to any other holders of our capital stock unless and until the holders of the Series A Preferred Stock have received cumulative distributions equal to the aggregate liquidation preference of the Series A Preferred Stock. For more information see the section of this prospectus entitled “Description of Securities — Preferred Stock — Series A Preferred Stock.”
Securities Authorized for Issuance Under Equity Compensation Plans
As of December 31, 2022, Bridger did not have any securities authorized for issuance under equity compensation plans.
In connection with the Business Combination, Legacy Bridger’s stockholders adopted the Omnibus Incentive Plan on January 23, 2023. Bridger assumed and adopted the Omnibus Incentive Plan and adopted the ESPP, which actions were approved by JCIC’s shareholders on January 24, 2023. On January 24, 2023, at an extraordinary general meeting of shareholders of JCIC (the “Shareholder Meeting”), the shareholders of JCIC considered and approved and assumed the Omnibus Incentive Plan and approved the ESPP. On the Closing Date, Bridger assumed the Omnibus Incentive Plan and the ESPP became effective.
On April 19, 2023, Bridger filed a registration statement on Form S-8 under the Securities Act to register the Common Stock issuable under the Omnibus Incentive Plan and the ESPP, which became effective automatically upon filing. As these shares are registered, they can be sold in the public market upon issuance, subject to applicable restrictions.
The Omnibus Incentive Plan reserves for issuance of 15,099,137 shares of Common Stock. Additionally, the Omnibus Incentive Plan provides that the aggregate number of shares of Common Stock available under the
57
Omnibus Incentive Plan shall automatically be increased on the first day of each fiscal year following the effective date of the Omnibus Incentive Plan, by the lesser of (i) 2% of outstanding shares of Common Stock on the last business day of the immediately preceding fiscal year and (ii) such smaller number of shares as determined by the Board.
The ESPP reserves for issuance 1,006,609 shares of Common Stock. The ESPP provides that the number of shares reserved and available for sale thereunder will increase automatically on the first day of each fiscal year following the effective date of the ESPP, by the lesser of (i) 1% of the outstanding shares of our Common Stock on the last business day of the immediately preceding fiscal year and (ii) such smaller number of shares as determined by the Board; provided that the maximum number of shares of Common Stock that may be issued under the ESPP in any event shall be 10,066,091 shares (subject to any adjustment in accordance with Section 18 of the ESPP).
58
CAPITALIZATION
The following table sets forth our consolidated cash and cash equivalents and capitalization as of June 30, 2023:
| • | on an actual basis; and |
| • | on an as adjusted basis to give effect to the sale and issuance by us of shares of our Common Stock in this offering (assuming no exercise of the underwriters’ option to purchase additional shares), after deducting the underwriting discounts and commissions and estimated offering expenses payable by us. See the section of this prosectus entitled “Use of Proceeds.” |
Our capitalization following the closing of this offering will depend on the actual public offering price and other terms of this offering determined at pricing. You should read the following table in conjunction with the sections entitled “Use of Proceeds” and “Management’s Discussion and Analysis of Financial Condition and Results of Operations” and our unaudited consolidated financial statements, all included elsewhere in this prospectus.
| As of June 30, 2023 | ||||||||
| Actual | As Adjusted(1) | |||||||
| (unaudited) | ||||||||
| (in thousands, except share data) | ||||||||
Cash and cash equivalents | $ | 845 | $ | |||||
|
|
|
| |||||
Debt, including current portion: | ||||||||
Total long term debt, net | $ | 207,520 | $ | |||||
Mezzanine equity | ||||||||
Series A Preferred Stock, $0.0001 par value; 315,789.473684 shares authorized, issued and outstanding, actual; 315,789.473684 shares issued and outstanding, as adjusted | 342,739 | |||||||
Stockholders’ equity: | ||||||||
Common Stock, $0.0001 par value; 1,000,000,000 shares authorized; 44,505,944 shares issued and outstanding, actual; shares issued and outstanding, as adjusted | 5 | |||||||
Additional paid-in capital | 78,977 | |||||||
Accumulated deficit | (400,054 | ) | ||||||
Accumulated other comprehensive income | 1,520 | |||||||
|
|
|
| |||||
Total stockholders’ deficit | (319,552 | ) | ||||||
|
|
|
| |||||
Total capitalization | $ | 231,552 | $ | |||||
|
|
|
| |||||
| (1) | As adjusted to give effect to the receipt of net proceeds of approximately $ million from this offering, after deducting estimated commissions, fees and other offering expenses payable by us, assuming no sale of the additional shares pursuant to the underwriters’ option to purchase additional shares. |
The outstanding share information in the table above is based on 44,505,944 shares outstanding as of June 30, 2023, and assumes no exercise of the underwriters’ option to purchase additional shares in the offering, and excludes as of that date the following, except as otherwise noted:
| • | 9,400,000 shares of our Common Stock issuable upon the exercise of Private Placement Warrants, with an exercise price of $11.50 per share; |
| • | 17,249,874 shares of our Common Stock issuable upon the exercise of Public Warrants, with an exercise price of $11.50 per share; |
59
| • | 31,152,280 shares of our Common Stock that may be issuable upon the conversion of any shares of Series A Preferred Stock, at the election of the holders of the Series A Preferred Stock; |
| • | 14,362,583 shares of our Common Stock reserved for future issuance under the Omnibus Incentive Plan (inclusive of 8,801,246 RSUs that have been granted prior to June 30, 2023); and |
| • | 1,006,609 shares of our Common Stock reserved for future issuance under the ESPP. |
60
DILUTION
If you purchase shares of our Common Stock in this offering, you will experience immediate dilution to the extent of the difference between the public offering price per share in this offering and our net tangible book value per share immediately after this offering. Net tangible book value per share is equal to the amount of our total tangible assets, less total liabilities, divided by the number of outstanding shares of our Common Stock. As of June 30, 2023, our historical net tangible book value was approximately $20.6 million, or approximately $0.46 per share. Our historical net tangible book value is the amount of our total tangible assets less our total liabilities. Historical net tangible book value per share represents historical net tangible book value divided by the 44,505,944 shares of our Common Stock outstanding as of June 30, 2023.
After giving effect to the sale by us of shares of our Common Stock in this offering at the public offering price of $ per share, and after deducting the underwriting discounts and commissions and estimated offering expenses payable by us, our as adjusted net tangible book value as of June 30, 2023 would have been approximately $ million, or approximately $ per share. This represents an immediate increase in as adjusted net tangible book value of $ per share to existing stockholders and an immediate dilution of $ per share to new investors purchasing shares of our Common Stock in this offering.
The following table illustrates this dilution on a per-share basis (unaudited):
Public offering price per share of Common Stock | $ | |||||||
Historical net tangible book value per share as of June 30, 2023 | $ | 0.46 | ||||||
Increase in as adjusted net tangible book value per share attributable to this offering | $ | |||||||
|
| |||||||
As adjusted net tangible book value per share after this offering | ||||||||
|
| |||||||
Dilution per share to new investors participating in this offering | $ | |||||||
|
|
If the underwriters exercise their over-allotment option in full, the as adjusted net tangible book value per share after giving effect to this offering would be approximately $ per share, which represents an immediate increase in the as adjusted net tangible book value of $ per share to existing stockholders and an immediate dilution in the as adjusted net tangible book value of $ per share to new investors purchasing shares of our Common Stock in this offering.
The foregoing table is based on 44,505,944 shares outstanding as of June 30, 2023, and assumes no exercise of the underwriters’ option to purchase additional shares in the offering, and excludes as of that date the following, except as otherwise noted:
| • | 9,400,000 shares of our Common Stock issuable upon the exercise of Private Placement Warrants, with an exercise price of $11.50 per share; |
| • | 17,249,874 shares of our Common Stock issuable upon the exercise of Public Warrants, with an exercise price of $11.50 per share; |
| • | 31,152,280 shares of our Common Stock that may be issuable upon the conversion of any shares of Series A Preferred Stock, at the election of the holders of the Series A Preferred Stock; |
| • | 14,362,538 shares of our Common Stock reserved for future issuance under the Omnibus Incentive Plan (inclusive of 8,801,246 RSUs that have been granted prior to June 30, 2023); and |
| • | 1,006,609 shares of our Common Stock reserved for future issuance under the ESPP. |
61
The information discussed above is illustrative only and will be adjusted based on the actual public offering price, the actual number of shares of Common Stock that we sell in this offering, and the other terms of this offering determined at pricing. To the extent that any of our outstanding Warrants or stock options are exercised, shares of Series A Preferred Stock are converted into shares of Common Stock, restricted stock units or awards vest, we grant additional stock options or other awards under our Omnibus Incentive Plan or ESPP, or we issue additional shares of Common Stock in the future, there will be further dilution to the investor.
62
MANAGEMENT’S DISCUSSION AND ANALYSIS OF FINANCIAL CONDITION AND RESULTS OF OPERATIONS
The following discussion and analysis is intended to help you understand our business, financial condition, results of operations, liquidity and capital resources. This discussion and analysis should be read together with our financial statements, and the related notes thereto, that are included elsewhere in this prospectus.
This discussion and analysis contains forward-looking statements based upon our current expectations, estimates and projections that involve risks and uncertainties. Actual results could differ materially from those anticipated in these forward-looking statements due to, among other considerations, the matters discussed in the sections entitled “Risk Factors” and “Cautionary Statement Regarding Forward-Looking Statements.” Unless the context otherwise requires, all references in this section to “Bridger,” the “Company,” “we,” “us,” “our,” and other similar terms refer to the business of Legacy Bridger and its subsidiaries prior to the Business Combination and Bridger Aerospace Group Holdings, Inc. and its subsidiaries following the Business Combination.
Business Overview
Bridger provides aerial wildfire surveillance, relief, suppression and aerial firefighting services using next-generation technology and environmentally friendly and sustainable firefighting methods primarily throughout the United States. Our mission is to save lives, property and habitats threatened by wildfires, leveraging our high-quality team, specialized aircraft and innovative use of technology and data. We are meeting an underserved and growing need for next-generation full-service aerial firefighting platforms.
Our portfolio is organized across two core offerings:
| • | Fire Suppression: Consists of deploying specialized aircraft to drop large amounts of water quickly and directly on wildfires. |
| • | Aerial Surveillance: Consists of providing aerial surveillance for fire suppression aircraft over an incident and providing tactical coordination with the incident commander. Aerial surveillance uses both manned aircraft and unmanned aircraft. |
We manage our operations as a single segment for purposes of assessing performance, making operating decisions and allocating resources.
We have made and will continue to make significant investments in capital expenditures to build and expand our aerial forest fire management technologies. We expect that our existing cash and cash equivalents provided by equity and debt financing will be sufficient to meet our current working capital and capital expenditure requirements for a period of at least twelve months from the date of this prospectus.
The Business Combination
On January 24, 2023, we consummated the Business Combination. As a result of the Business Combination, Legacy Bridger and JCIC each became wholly-owned subsidiaries of the Company, and the JCIC shareholders and the equityholders of Legacy Bridger converted their equity ownership in JCIC and Legacy Bridger, respectively, into equity ownership in the Company. Legacy Bridger has been determined to be the accounting acquirer with respect to the Business Combination, which will be accounted for as a reverse capitalization, with no goodwill or other intangible assets recorded, in accordance with GAAP.
Upon consummation of the Business Combination, the most significant change in Legacy Bridger’s future reported financial position and results of operations was a gross decrease in cash and cash equivalents (as compared to Legacy Bridger’s balance sheet at December 31, 2022), of approximately $17.0 million. Total direct
63
and incremental transaction costs of Bridger, JCIC and Legacy Bridger paid at the Closing were approximately $16.6 million and have been treated as a reduction of the cash proceeds and deducted from our additional paid-in capital.
Public Company Costs
We have become the successor to a company registered with the SEC and listed on the Nasdaq Global Market, which has required, and in the future may require, us to hire additional staff and implement procedures and processes to address public company regulatory requirements and customary practices. We have incurred and expect to incur additional annual expenses for, among other things, directors’ and officers’ liability insurance, director fees, and additional internal and external accounting, legal and administrative resources and fees.
Key Factors Affecting Our Results of Operations
We are exposed to certain risks inherent to an aerial firefighting business. These risks are further described in the section of this prospectus entitled “Risk Factors.”
Seasonality Due to the North American Fire Season
Our operating results are impacted by seasonality. Climate conditions and other factors that may influence the revenues of our services may vary each season and year. Historically, the demand for our services has been higher in the second and third quarters of each fiscal year due to the timing and duration of the North American fire season. Consequently, revenues, expenses, and operating cash flows from our services are generated mostly in the second and third quarters of our fiscal year. However, the seasonal fluctuations in the need to fight wildfires based upon location and the varying intensity of the fire season have and may continue to lead our operating results to fluctuate significantly from quarter to quarter and year to year.
Weather Conditions and Climate Trends
Our business is highly dependent on the needs of government agencies to surveil and suppress fires. As such, our financial condition and results of operations are significantly affected by the weather, as well as environmental and other factors affecting climate change, which impact the number and severity of fires in any given period. The intensity and duration of the North American fire season is affected by multiple factors, some of which, according to the Climate Central Article, a nonprofit climate science news organization, are weather patterns including warmer springs and longer summers, lower levels of mountaintop snowpack which lead to drier soils and vegetation and frequency of lightning strikes.1 Based on the climate change indicators published by the Environmental Protection Agency (“EPA”), these factors have shown year over year increases linked to the effects of climate change and the overall trend in increased temperatures. We believe that rising global temperatures have been, and in the future are expected to be, one factor contributing to increasing rates and severity of wildfires. Historically, sales of our services have been higher in the summer season of each fiscal year due to weather patterns which are generally correlated to a higher prevalence of wildfires in North America. Larger wildfires and longer seasons are expected to continue as droughts increase in frequency and duration, according to the EPA Climate Change Indicators Article.2
| 1 | Climate Central, Climate Change is Tipping Scales Toward More Wildfires, Jun. 23, 2016 (https://www.climatesignals.org/headlines/climate-change-tipping-scales-toward-more-wildfires) (the “Climate Central Article”). |
| 2 | United States Environmental Protection Agency, Climate Change Indicators: Wildfires, last accessed Apr. 4, 2023 (https://www.epa.gov/climate-indicators/climate-change-indicators-wildfires) (the “EPA Climate Change Indicators Article”). |
64
Limited Supply of Specialized Aircraft and Replacement and Maintenance Parts
Our results of operations are dependent on sufficient availability of aircraft, raw materials and supplied components provided by a limited number of suppliers. Our reliance on limited suppliers exposes us to volatility in the prices and availability of these materials, which may lead to increased costs and delays in operations.
In March 2020, the World Health Organization declared a global pandemic related to the outbreak of a respiratory illness caused by COVID-19. Due to the COVID-19 pandemic, in 2020, 2021 and 2022 we experienced delays on the delivery of aircraft. Should such conditions become protracted or worsen or should longer-term budgets or priorities of our clients be impacted, the COVID-19 pandemic could negatively affect our financial condition and results of operations. Given the dynamic nature of the COVID-19 pandemic and its global consequences, the ultimate impact on our operations, cash flows and financial condition cannot be reasonably estimated at this time. The outbreak of COVID-19 may also have the effect of heightening many of the other risks described in the section of this prospectus entitled “Risk Factors,” such as those related to the market for our securities and cross-border transactions.
Economic and Market Factors
Our operations, supply chain, partners, and suppliers have been subject to various global macroeconomic factors. We expect to continue to remain vulnerable to a number of industry-specific and global macroeconomic factors that may cause our actual results of operations to differ from our historical results of operations or current expectations. The factors and trends that we currently believe are or will be most impactful to our financial condition and results of operations include the following: the impact on us of significant operational challenges by third parties on which we rely; inflationary pressures; short- and long-term weather patterns; potential labor and supply chain shortages affecting us and our partners; volatile fuel prices; aircraft delivery delays; and changes in general economic conditions in the markets in which we operate.
Historically, our results of operations have not been materially impacted by other factors, other than the COVID-19 global pandemic. We continue to monitor the potential favorable or unfavorable impacts of these and other factors on our business, operations, financial condition and future results of operations, which are dependent on future developments. Our future results of operations may be subject to volatility and our growth plans may be delayed, particularly in the short term, due to the impact of the above factors and trends. For instance, the impact of the COVID-19 pandemic directly affected the delivery of our aircraft and the support related to their deployment while on contract. Deployment of two Super Scoopers was delayed in 2020 as a result of the FAA’s transition to a work-from-home environment and a reduction in its ability to process carding and registration matters; two other Super Scoopers were delayed in 2021 as a result of modified manufacturing procedures at the OEM in response to COVID-19 that increased production time, which we understood was compounded by the OEM’s delays in receiving certain parts and components; and prior production delays pushed completion and delivery of another two Super Scoopers later in 2022 and early 2023 than we had previously anticipated receiving them. However, we believe that our long-term outlook remains positive due to the increasing demand for our services and our ability to meet those demands consistently, despite adverse market factors. We believe that this expected long-term increase in demand will offset increased costs and that the operational challenges we may experience in the near term can be managed in a manner that will allow us to support increased demand, though we cannot provide any assurances.
Key Components of Our Results of Operations
Revenues
Our primary source of revenues is from providing services, which are disaggregated into fire suppression, aerial surveillance and other services. Revenues and growth for our fire suppression and aerial surveillance services are driven by climate trends, specifically the intensity and timing of the North American fire season. Other services primarily consist of extraneous fulfillment of contractual services such as extended availability and mobilizations. Other services also include maintenance services performed externally for third parties.
65
We charge daily and hourly rates depending upon the type of firefighting service rendered and under which contract the services are performed. The recognition of revenues for our services are primarily split into flight, standby and other revenues. Flight revenue is primarily earned at an hourly rate when the engines of the aircraft are cycled, upon request of the customer. Standby revenue is primarily earned as a daily rate when aircraft are available for use at a fire base, awaiting request from the customer for flight deployment. Other revenue consists of additional contractual items that can be charged to the customer, such as leasing revenues for facilities, as well as maintenance and repair on externally owned aircraft.
Cost of Revenues
Cost of revenues includes costs incurred directly related to flight operations including expenses associated with operating the aircraft on revenue generating contracts. These include labor, depreciation, subscriptions and fees, travel and fuel. Cost of revenues also includes maintenance expenses for our aircraft including costs of routine maintenance expenses and repairs. This consists of labor, parts, consumables, travel and subscriptions unique to each airframe.
Selling, General and Administrative Expense
Selling, general and administrative expenses include all costs that are not directly related to satisfaction of customer contracts. Selling, general and administrative expenses include costs for our administrative functions, such as finance, legal, human resources, and IT support, and business development costs that include contract procurement, public relations and business opportunity advancement. These functions include costs for items such as salaries, benefits, stock-based compensation and other personnel-related costs, maintenance and supplies, professional fees for external legal, accounting, and other consulting services, insurance, intangible asset amortization and depreciation expense. Selling, general and administrative expenses also contain any gain or loss on the disposal of fixed assets.
Interest Expense
Interest expense consists of interest expense related to our loan agreements, the Legacy Bridger Series B Preferred Shares, which were fully redeemed prior to Closing, the Series 2022 Bonds, Legacy Bridger Series C Preferred Shares for the changes in fair values of the embedded derivative and the freestanding derivative, and interest rate swaps agreements. Interest expense also includes amortization of debt issuance costs associated with our loan agreements. Refer to discussion of our loan commitments further below under the section of this prospectus entitled “— Liquidity and Capital Resources — Indebtedness.”
Other Income
Other income consists of interest income and realized gains on available-for-sale debt securities. This also includes the reimbursement from an insurance claim against a damaged asset.
66
Results of Operations
Comparison of the Three Months Ended June 30, 2023 to the Three Months Ended June 30, 2022
The following table sets forth our unaudited condensed consolidated statements of operations information for the three months ended June 30, 2023 and 2022 and should be reviewed in conjunction with the financial statements and notes included elsewhere in this prospectus.
(All amounts in U.S. dollars) | Three Months Ended June 30, 2023 | Three Months Ended June 30, 2022 | Period Over Period Change ($) | Period Over Period Change (%) | ||||||||||||
Revenues | $ | 11,615,280 | $ | 12,753,671 | $ | (1,138,391 | ) | (9 | %) | |||||||
Cost of revenues: | ||||||||||||||||
Flight operations | 6,299,122 | 5,849,562 | 449,560 | 8 | % | |||||||||||
Maintenance | 4,210,976 | 3,571,986 | 638,990 | 18 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Total cost of revenues | 10,510,098 | 9,421,548 | 1,088,550 | 12 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Gross income | 1,105,182 | 3,332,123 | (2,226,941 | ) | (67 | %) | ||||||||||
Selling, general and administrative expense | 15,187,808 | 5,735,627 | 9,452,181 | 165 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Operating loss | (14,082,626 | ) | (2,403,504 | ) | (11,679,122 | ) | 486 | % | ||||||||
Interest expense | (5,540,867 | ) | (2,293,682 | ) | (3,247,185 | ) | 142 | % | ||||||||
Other income | 601,891 | 134,311 | 467,580 | 348 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Net loss | (19,021,602 | ) | (4,562,875 | ) | (14,458,727 | ) | 317 | % | ||||||||
Series A Preferred Stock—adjustment to maximum redemption value | (5,805,582 | ) | — | |||||||||||||
Legacy Bridger Series C Preferred Shares—adjustment to maximum redemption value | — | (191,240,782 | ) | |||||||||||||
Legacy Bridger Series A Preferred Shares—adjustment for redemption, extinguishment, accrued interest, and change in fair value | — | (81,323,569 | ) | |||||||||||||
|
|
|
| |||||||||||||
Net loss attributable to Common stockholders—basic and diluted | $ | (24,827,184 | ) | $ | (277,127,226 | ) | ||||||||||
|
|
|
| |||||||||||||
Net loss per Common Stock—basic and diluted | $ | (0.55 | ) | $ | (7.15 | ) | ||||||||||
Revenues
Revenues decreased by $1.1 million, or 9%, to $11.6 million for the three months ended June 30, 2023, from $12.8 million for the three months ended June 30, 2022.
The following table shows revenues by service offering for each period.
| (All amounts in U.S. dollars) | Three Months Ended June 30, 2023 | Three Months Ended June 30, 2022 | Period Over Period Change ($) | Period Over Period Change (%) | ||||||||||||
Fire suppression | $ | 10,449,427 | $ | 11,682,263 | $ | (1,232,836 | ) | (11 | )% | |||||||
Aerial surveillance | 1,123,753 | 1,002,025 | 121,728 | 12 | % | |||||||||||
Other services | 42,100 | 69,383 | (27,283 | ) | (39 | )% | ||||||||||
|
|
|
|
|
| |||||||||||
Total revenues | $ | 11,615,280 | $ | 12,753,671 | $ | (1,138,391 | ) | (9 | )% | |||||||
|
|
|
|
|
| |||||||||||
67
Fire suppression revenue decreased by $1.2 million, or 11%, to $10.4 million for the three months ended June 30, 2023, from $11.7 million for the three months ended June 30, 2022. The decrease in fire suppression revenue accounted for 108% of the total decrease in revenues for the three months ended June 30, 2023. The decrease was primarily driven by a later start to the 2023 U.S. wildfire season. The Company actively worked to partially offset the impact of wet spring weather and slower start to the U.S. wildfire season by expanding its aerial firefighting operations into Canada where wildfire activity began earlier.
Aerial surveillance revenue increased by $0.1 million, or 12%, to $1.1 million for the three months ended June 30, 2023, from $1.0 million for the three months ended June 30, 2022. The increase was primarily driven by the number of aircraft operating for the three months ended June 30, 2023 compared to the three months ended June 30, 2022.
Other services revenue decreased by $27 thousand, or 39%, to $42 thousand for the three months ended June 30, 2023, from $69 thousand for the three months ended June 30, 2022. The decrease was primarily driven by decreased maintenance services.
The following table shows revenues by revenue type for each period.
| (All amounts in U.S. dollars) | Three Months Ended June 30, 2023 | Three Months Ended June 30, 2022 | Period Over Period Change ($) | Period Over Period Change (%) | ||||||||||||
Flight revenue | $ | 5,794,315 | $ | 6,417,520 | $ | (623,205 | ) | (10 | )% | |||||||
Standby revenue | 5,135,937 | 6,210,976 | (1,075,039 | ) | (17 | )% | ||||||||||
Other revenue | 685,028 | 125,175 | 559,853 | 447 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Total revenues | $ | 11,615,280 | $ | 12,753,671 | $ | (1,138,391 | ) | (9 | )% | |||||||
|
|
|
|
|
| |||||||||||
Flight revenue decreased by $0.6 million, or 10%, to $5.8 million for the three months ended June 30, 2023, from $6.4 million for the three months ended June 30, 2022. The decrease was primarily driven by a later start to the 2023 U.S. wildfire season.
Standby revenue decreased by $1.1 million, or 17%, to $5.1 million for the three months ended June 30, 2023, from $6.2 million for the three months ended June 30, 2022. The decrease was primarily driven by a later start to the 2023 U.S. wildfire season.
Other revenue increased by $0.6 million, or 447%, to $0.7 million for the three months ended June 30, 2023, from $0.1 million for the three months ended June 30, 2022. The increase was primarily due to labor, maintenance and improvements to an aircraft under the ownership of a related party. Refer to “Note 16—Related Party Transactions” of the Notes to the Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional details.
Cost of Revenues
Cost of revenues increased by $1.1 million, or 12%, to $10.5 million for the three months ended June 30, 2023, from $9.4 million for the three months ended June 30, 2022 due to the following drivers:
Flight Operations
Flight operations expenses increased by 0.4 million, or 8%, to $6.3 million for the three months ended June 30, 2023, from $5.8 million for the three months ended June 30, 2022. The increase was primarily attributable to higher depreciation expense due to increase in flight hours due to the two additional Super Scooper aircraft placed into service in September 2022 and February 2023, respectively.
68
Maintenance
Maintenance expenses increased by $0.6 million, or 18%, to $4.2 million for the three months ended June 30, 2023, from $3.6 million for the three months ended June 30, 2022. The increase was primarily driven by higher aircraft maintenance costs of $0.5 million and depreciation expense of $0.1 million required for the two additional Super Scooper aircraft placed into service in September 2022 and February 2023, respectively.
Selling, General and Administrative Expense
Selling, general and administrative expense increased by $9.5 million, or 165%, to $15.2 million for the three months ended June 30, 2023, from $5.7 million for the three months ended June 30, 2022. The increase was primarily driven by $7.9 million of non-cash stock-based compensation expense for the RSUs issued to employees of Bridger in connection. Refer to “Note 15—Stock-Based Compensation” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional details. The increase was also partially driven by a loss on disposal and an asset impairment charge of $1.1 million related to aging surveillance aircraft. The increase was also partially driven by higher insurance costs of $0.6 million and higher operating costs of $0.4 million primarily associated with the two additional Super Scooper aircraft placed into service in September 2022 and February 2023, respectively.
Interest Expense
Interest expense increased by $3.2 million, or 142%, to $5.5 million for the three months ended June 30, 2023, from $2.3 million for the three months ended June 30, 2022. The increase was primarily driven by the additional interest expense for the Series 2022 Bonds of $4.9 million partially offset by a decrease in interest expense for the Series A-1 and Series A-2 preferred shares of Legacy Bridger of $1.7 million.
Other Income
Other income increased by $0.5 million, or 348%, to $0.6 million for the three months ended June 30, 2023, from $0.1 million for the three months ended June 30, 2022. The increase was primarily driven by interest income for the embedded derivative of Legacy Bridger Series C Preferred Shares of $0.2 million. Refer to “Note 17—Mezzanine Equity” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional details. The increase was partially driven by realized gains from available-for-sale securities of $0.3 million. Refer to “Note 3—Cash Equivalents and Investments in Marketable Securities” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional details.
69
Comparison of the Six Months Ended June 30, 2023 to the Six Months Ended June 30, 2022
The following table sets forth our unaudited condensed consolidated statement of operations information for the six months ended June 30, 2023 and 2022 and should be reviewed in conjunction with the financial statements and notes included elsewhere in this prospectus.
| (All amounts in U.S. dollars) | Six Months Ended June 30, 2023 | Six Months Ended June 30, 2022 | Period Over Period Change ($) | Period Over Period Change (%) | ||||||||||||
Revenues | $ | 11,980,653 | $ | 12,822,963 | $ | (842,310 | ) | (7 | %) | |||||||
Cost of revenues: | ||||||||||||||||
Flight operations | 10,032,383 | 9,514,914 | 517,469 | 5 | % | |||||||||||
Maintenance | 7,726,427 | 6,433,973 | 1,292,454 | 20 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Total cost of revenues | 17,758,810 | 15,948,887 | 1,809,923 | 11 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Gross loss | (5,778,157 | ) | (3,125,924 | ) | (2,652,233 | ) | 85 | % | ||||||||
Selling, general and administrative expense | 48,416,299 | 10,576,886 | 37,839,413 | 358 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Operating loss | (54,194,456 | ) | (13,702,810 | ) | (40,491,646 | ) | 295 | % | ||||||||
Interest expense | (11,205,412 | ) | (6,008,228 | ) | (5,197,184 | ) | 87 | % | ||||||||
Other income | 1,693,328 | 275,154 | 1,418,174 | 515 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Net loss | (63,706,540 | ) | (19,435,884 | ) | (44,270,656 | ) | 228 | % | ||||||||
Series A Preferred Stock—adjustment for deemed dividend upon Closing | (48,300,000 | ) | — | |||||||||||||
Series A Preferred Stock—adjustment to eliminate 50% multiplier | 156,362,598 | — | ||||||||||||||
Series A Preferred Stock—adjustment to maximum redemption value | (10,080,022 | ) | — | |||||||||||||
Legacy Bridger Series A Preferred Shares—adjustment for redemption, extinguishment and accrued interest | — | (85,663,336 | ) | |||||||||||||
Legacy Bridger Series C Preferred Shares—adjustment to maximum redemption value | — | (191,240,782 | ) | |||||||||||||
|
|
|
| |||||||||||||
Net income (loss) attributable to Common Stockholders—basic and diluted | $ | 34,276,036 | $ | (296,340,002 | ) | |||||||||||
|
|
|
| |||||||||||||
Net income (loss) per Common Stock-basic | $ | 0.77 | $ | (7.64 | ) | |||||||||||
Net income (loss) per Common Stock-diluted | $ | 0.44 | $ | (7.64 | ) | |||||||||||
Revenues
Revenues decreased by $0.8 million, or 7%, to $12.0 million for the six months ended June 30, 2023, from $12.8 million for the six months ended June 30, 2022.
70
The following table shows revenues by service offering for each period.
(All amounts in U.S. dollars) | Six Months Ended June 30, 2023 | Six Months Ended June 30, 2022 | Period Over Period Change ($) | Period Over Period Change (%) | ||||||||||||
Fire suppression | $ | 10,449,427 | $ | 11,682,263 | $ | (1,232,836 | ) | (11 | )% | |||||||
Aerial surveillance | 1,123,753 | 1,002,025 | 121,728 | 12 | % | |||||||||||
Other services | 407,473 | 138,675 | 268,798 | 194 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Total revenues | $ | 11,980,653 | $ | 12,822,963 | $ | (842,310 | ) | (7 | )% | |||||||
|
|
|
|
|
| |||||||||||
Fire suppression revenue decreased by $1.2 million, or 11%, to $10.4 million for the six months ended June 30, 2023, from $11.7 million for the six months ended June 30, 2022. The decrease in fire suppression revenue accounted for 146% of the total decrease in revenues for the six months ended June 30, 2023. The decrease was primarily driven by a later start to the 2023 U.S. wildfire season. The Company actively worked to partially offset the impact of wet spring weather and slower start to the U.S wildfire season by expanding its aerial firefighting operations into Canada where wildfire activity began earlier.
Aerial surveillance revenue increased by $0.1 million, or 12%, to $1.1 million for the six months ended June 30, 2023, from $1.0 million for the six months ended June 30, 2022. The increase was primarily driven by the number of aircraft operating for the six months ended June 30, 2023 compared to the six months ended June 30, 2022.
Other services revenue increased by $0.3 million, or 194%, to $0.4 million for the six months ended June 30, 2023, from $0.1 million for the six months ended June 30, 2022. The increase was primarily driven by maintenance services performed on an externally owned aircraft.
The following table shows revenues by revenue type for each period.
(All amounts in U.S. dollars) | Six Months Ended June 30, 2023 | Six Months Ended June 30, 2022 | Period Over Period Change ($) | Period Over Period Change (%) | ||||||||||||
Flight revenue | $ | 5,794,315 | $ | 6,417,520 | $ | (623,205 | ) | (10 | )% | |||||||
Standby revenue | 5,135,937 | 6,210,976 | (1,075,039 | ) | (17 | )% | ||||||||||
Other revenue | 1,050,401 | 194,467 | 855,934 | 440 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Total revenues | $ | 11,980,653 | $ | 12,822,963 | $ | (842,310 | ) | (7 | )% | |||||||
|
|
|
|
|
| |||||||||||
Flight revenue decreased by $0.6 million, or 10%, to $5.8 million for the six months ended June 30, 2023, from $6.4 million for the six months ended June 30, 2022. The decrease was primarily driven by a later start to the 2023 U.S. wildfire season.
Standby revenue decreased by $1.1 million, or 17%, to $5.1 million for the six months ended June 30, 2023, from $6.2 million for the six months ended June 30, 2022. The decrease was primarily driven by a later start to the 2023 U.S. wildfire season.
Other revenue increased by $0.9 million, or 440%, to $1.1 million for the six months ended June 30, 2023, from $0.2 million for the six months ended June 30, 2022. The increase was primarily due to labor, maintenance and improvements to an aircraft under the ownership of a related party and additional contractually specified items. Refer to “Note 16 – Related Party Transactions” of the Notes to the Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional details.
71
Cost of Revenues
Cost of revenues increased by $1.8 million, or 11%, to $17.8 million for the six months ended June 30, 2023, from $15.9 million for the six months ended June 30, 2022 due to the following drivers:
Flight Operations
Flight operations expenses increased by $0.5 million, or 5%, to $10.0 million for the six months ended June 30, 2023, from $9.5 million for the six months ended June 30, 2022. The increase was primarily attributable to higher expenses of $0.5 million for the RSUs granted to all employees in April 2023. Refer to “Note 15 – Stock-Based Compensation” of the Notes to the Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional details.
Maintenance
Maintenance expenses increased by $1.3 million, or 20%, to $7.7 million for the six months ended June 30, 2023, from $6.4 million for the six months ended June 30, 2022. The increase was primarily driven by aircraft maintenance of $0.7 million and higher subscriptions, licenses, and fees of $0.4 million required for the two additional Super Scooper aircraft placed into service in September 2022 and February 2023, respectively. The increase was partially driven by higher expenses of $0.2 million for the RSUs granted to all employees in April 2023. Refer to “Note 15 – Stock-Based Compensation” of the Notes to the Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional details.
Selling, General and Administrative Expense
Selling, general and administrative expense increased by $37.8 million, or 358%, to $48.4 million for the six months ended June 30, 2023, from $10.6 million for the six months ended June 30, 2022. The increase was primarily driven by $31.9 million of non-cash stock-based compensation expense for the RSUs issued to management and all employees of Bridger in connection. Refer to “Note 15 – Stock-Based Compensation” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional details. The increase was partially driven by a loss on disposal of assets related to the impairment of a Twin Commander surveillance platform of $0.6 million. The increase was partially driven by higher operating costs of $4.1 million and higher insurance costs of $1.2 million primarily associated with the two additional Super Scooper aircraft placed into service in September 2022 and February 2023, respectively.
Interest Expense
Interest expense increased by $5.2 million, or 87%, to $11.2 million for the six months ended June 30, 2023, from $6.0 million for the six months ended June 30, 2022. The increase was primarily driven by the additional interest expense for the Series 2022 Bonds of $9.4 million, decrease in interest expense for the Legacy Bridger Series A Preferred Shares of $4.6 million and an increase in interest expense for the two loan agreements in connection with the two separate credit facilities brokered through Live Oak Bank and backed by the U.S. Department of Agriculture for the completed purchase of the Company’s first two Super Scooper aircraft of $0.4 million. Refer to discussion of our loan commitments further below under the section of this prospectus entitled “Liquidity and Capital Resources—Indebtedness.”
Other Income
Other income increased by $1.4 million, or 515%, to $1.7 million for the six months ended June 30, 2023, from $0.3 million for the six months ended June 30, 2022. The increase was primarily driven by interest income for the embedded derivative of Legacy Bridger Series C Preferred Shares of $0.9 million. Refer to “Note 17 – Mezzanine Equity” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this
72
prospectus for additional details. The increase was partially driven by realized gains from available-for-sale securities of $0.6 million. Refer to “Note 3 – Cash Equivalents and Investments in Marketable Securities” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional details.
Comparison of the Year Ended December 31, 2022 to the Year Ended December 31, 2021
The following table sets forth our consolidated statement of operations information for the years ended December 31, 2022 and 2021 and should be reviewed in conjunction with the financial statements and notes included elsewhere in this prospectus.
| (All amounts in U.S. dollars) | Year Ended December 31, 2022 | Year Ended December 31, 2021 | Period Over Period Change ($) | Period Over Period Change (%) | ||||||||||||
Total revenues | $ | 46,387,963 | $ | 39,384,182 | $ | 7,003,781 | 18 | % | ||||||||
Cost of revenues: | ||||||||||||||||
Flight operations | 18,762,172 | 15,823,713 | 2,938,459 | 19 | % | |||||||||||
Maintenance | 15,123,806 | 10,755,471 | 4,368,335 | 41 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Total cost of revenues | 33,885,978 | 26,579,184 | 7,306,794 | 27 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Gross profit | 12,501,985 | 12,804,998 | (303,013 | ) | (2 | )% | ||||||||||
Selling, general and administrative expense | 35,128,322 | 11,215,027 | 23,913,295 | 213 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Operating (loss) income | (22,626,337 | ) | 1,589,971 | (24,216,308 | ) | (1,523 | )% | |||||||||
Interest expense | (20,019,886 | ) | (9,293,928 | ) | (10,725,958 | ) | 115 | % | ||||||||
Other income | 521,555 | 1,163,160 | (641,605 | ) | (55 | )% | ||||||||||
|
|
|
|
|
| |||||||||||
Net loss | (42,124,668 | ) | (6,540,797 | ) | (35,583,871 | ) | 544 | % | ||||||||
Legacy Bridger Series C Preferred Shares adjustment to maximum value | (202,688,810 | ) | — | |||||||||||||
Legacy Bridger Series A Preferred Shares adjustment for redemption, extinguishment and accrued interest | (85,663,336 | ) | (15,913,184 | ) | ||||||||||||
|
|
|
| |||||||||||||
Net loss attributable to common shareholders—basic and diluted | $ | (330,476,814 | ) | $ | (22,453,981 | ) | ||||||||||
|
|
|
| |||||||||||||
Net loss per share attributable to common shareholders—basic and diluted | $ | (8.20 | ) | $ | (0.56 | ) | ||||||||||
Revenue
Revenue increased by $7.0 million, or 18%, to $46.4 million for the year ended December 31, 2022, from $39.4 million for the year ended December 31, 2021.
73
The following table shows revenues by service offering for each period.
| (All amounts in U.S. dollars) | Year Ended December 31, 2022 | Year Ended December 31, 2021 | Period Over Period Change ($) | Period Over Period Change (%) | ||||||||||||
Fire suppression | $ | 38,845,227 | $ | 30,442,001 | $ | 8,403,226 | 28 | % | ||||||||
Aerial surveillance | 7,215,997 | 8,632,535 | (1,416,538 | ) | (16 | )% | ||||||||||
Other services | 326,739 | 309,646 | 17,093 | 6 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Total revenues | $ | 46,387,963 | $ | 39,384,182 | $ | 7,003,781 | 18 | % | ||||||||
|
|
|
|
|
| |||||||||||
Fire suppression revenue increased by $8.4 million, or 28%, to $38.8 million for the year ended December 31, 2022, from $30.4 million for the year ended December 31, 2021. The increase was primarily driven by the addition of two additional Super Scooper aircraft placed into service during the year ended December 31, 2022, which was partially offset by a decrease in revenue attributable to existing Super Scooper aircraft as a result of the decreased number of fires with high-incident levels in 2022 compared to 2021. The increase in fire suppression revenue accounted for 120% of the total increase in revenues for the year ended December 31, 2022.
Aerial surveillance revenue decreased by $1.4 million, or 16%, to $7.2 million for the year ended December 31, 2022, from $8.6 million for the year ended December 31, 2021. The decrease was primarily driven by the decreased number of fires with high-incident levels in 2022 compared to 2021.
Other services revenue decreased 6%, to $0.3 million for the year ended December 31, 2022, from $0.3 million for the year ended December 31, 2021. The slight decrease was primarily driven by decreased maintenance services.
The following table shows revenues by revenue type for each period.
| (All amounts in U.S. dollars) | Year Ended December 31, 2022 | Year Ended December 31, 2021 | Period Over Period Change ($) | Period Over Period Change (%) | ||||||||||||
Flight revenue | $ | 25,105,027 | $ | 20,377,442 | $ | 4,727,585 | 23 | % | ||||||||
Standby revenue | 20,772,018 | 18,550,067 | 2,221,951 | 12 | % | |||||||||||
Other revenue | 510,918 | 456,673 | 54,245 | 12 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Total revenues | $ | 46,387,963 | $ | 39,384,182 | $ | 7,003,781 | 18 | % | ||||||||
|
|
|
|
|
| |||||||||||
Flight revenue increased by $4.7 million, or 23%, to $25.1 million for the year ended December 31, 2022, from $20.4 million for the year ended December 31, 2021. The increase was primarily driven by the increased number of Super Scooper aircraft flying on deployment.
Standby revenue increased by $2.2 million, or 12%, to $20.8 million for the year ended December 31, 2022, from $18.6 million for the year ended December 31, 2021. The increase was primarily driven by the increased number of Super Scooper aircraft available for deployment.
Other revenue increased by $0.1 million, or 12%, to $0.5 million for the year ended December 31, 2022, from $0.5 million for the year ended December 31, 2021. The increase was primarily driven by additional contractual items charged to the customer with an increased number of Super Scooper aircraft on deployment.
74
Cost of Revenues
Cost of revenues increased by $7.3 million, or 27%, to $33.9 million for the year ended December 31, 2022, from $26.6 million for the year ended December 31, 2021, due to the following drivers:
Flight Operations
Flight operations expenses increased by $2.9 million, or 19%, to $18.8 million for the year ended December 31, 2022, from $15.8 million for the year ended December 31, 2021. The increase was partially attributable to higher depreciation of $1.4 million and subscription, licenses and fees expenses of $0.2 million primarily as a result of two additional Super Scooper aircraft placed into service in 2022. The increase was also partially due to higher personnel and travel expenses of $1.5 million mostly attributable to increased travel and the number of personnel required for a full season of flight deployment. The increase was partially offset by a decrease in aircraft leasing expenses due to a lower utilization of leased aircraft.
Maintenance
Maintenance expenses increased by $4.4 million, or 41%, to $15.1 million for the year ended December 31, 2022, from $10.8 million for the year ended December 31, 2021. The increase was partially driven by higher subscriptions, licenses and fees of $1.5 million mostly attributable to the additional two Super Scooper aircraft placed into service in 2022. The increase was also partially attributable to higher personnel and travel expenses of $1.7 million due to increased travel and the number of personnel required for a full season of flight deployment. The increase was also partially driven by an increase in aircraft maintenance of $0.7 million in 2022.
Selling, General and Administrative Expense
Selling, general and administrative expense increased by $23.9 million, or 213%, to $35.1 million for the year ended December 31, 2022, from $11.2 million for the year ended December 31, 2021. The increase was partially driven by higher personnel expenses of $16.5 million which included $10.1 million of transaction related bonuses for employees and executives in connection with the issuance of the Legacy Bridger Series C Preferred Shares, issuance of the Series 2022 Bonds, execution of the Transaction Agreements and initial filing of the proxy statement/prospectus prepared in connection with the Business Combination. The increase was also partially driven by higher professional services of $5.3 million associated primarily with third-party consultants and auditors’ fees to support the growth of the business and preparation of becoming a public company upon the consummation of the Business Combination, as well as advertising and public relation services. The increase was also partially attributable to the loss on disposal of two aging aircraft and other rotables of $1.8 million.
Interest Expense
Interest expense increased by $10.7 million, or 115%, to $20.0 million for the year ended December 31, 2022, from $9.3 million for the year ended December 31, 2021. The increase was primarily driven by the additional interest expense for Legacy Bridger Series A Preferred Shares of $3.9 million, decrease in interest expense for Legacy Bridger Series B Preferred Shares of $2.8 million and the additional interest expense for the Series 2022 Bonds of $7.8 million. Refer to discussion of our loan commitments further below under the section of this prospectus entitled “Liquidity and Capital Resources — Indebtedness.”
Other Income
Other income decreased by $0.6 million, or 55%, to $0.5 million for the year ended December 31, 2022, from $1.2 million for the year ended December 31, 2021. The decrease was driven by the loss on extinguishment of Series 2021 Bond of $0.8 million in the year ended December 31, 2022, versus a gain on the forgiveness of our PPP debt of $0.8 million in the year ended December 31, 2021.
75
Non-GAAP Financial Measures
Although we believe that net income or loss, as determined in accordance with GAAP, is the most appropriate earnings measure, we use EBITDA and Adjusted EBITDA as key profitability measures to assess the performance of our business. We believe these measures help illustrate underlying trends in our business and use the measures to establish budgets and operational goals, and communicate internally and externally, for managing our business and evaluating its performance. We also believe these measures help investors compare our operating performance with its results in prior periods in a way that is consistent with how management evaluates such performance.
Each of the profitability measures described below are not recognized under GAAP and do not purport to be an alternative to net income or loss determined in accordance with GAAP as a measure of our performance. Such measures have limitations as analytical tools and should not be considered in isolation or as substitutes for our results as reported under GAAP. EBITDA and Adjusted EBITDA exclude items that can have a significant effect on our profit or loss and should, therefore, be used only in conjunction with our GAAP profit or loss for the period. Our management compensates for the limitations of using non-GAAP financial measures by using them to supplement GAAP results to provide a more complete understanding of the factors and trends affecting the business than GAAP results alone. Because not all companies use identical calculations, these measures may not be comparable to other similarly titled measures of other companies.
EBITDA and Adjusted EBITDA
EBITDA is a non-GAAP profitability measure that represents net income or loss for the period before the impact of the interest expense, income tax expense (benefit) and depreciation and amortization of property, plant and equipment and intangible assets. EBITDA eliminates potential differences in performance caused by variations in capital structures (affecting financing expenses), the cost and age of tangible assets (affecting relative depreciation expense) and the extent to which intangible assets are identifiable (affecting relative amortization expense).
Adjusted EBITDA is a non-GAAP profitability measure that represents EBITDA before certain items that are considered to hinder comparison of the performance of our businesses on a period-over-period basis or with other businesses. During the periods presented, we exclude from Adjusted EBITDA gains and losses on disposals of assets, legal fees and offering costs related to financing and other transactions, which include costs that are required to be expensed in accordance with GAAP. In addition, we exclude from Adjusted EBITDA non-cash stock-based compensation and business development expenses. Our management believes that the inclusion of supplementary adjustments to EBITDA applied in presenting Adjusted EBITDA are appropriate to provide additional information to investors about certain material non-cash items and about unusual items that we do not expect to continue at the same level in the future.
76
The following table reconciles net loss, the most directly comparable GAAP measure, to EBITDA and Adjusted EBITDA for the three months ended June 30, 2023 and 2022.
| Three Months Ended June 30, 2023 | Three Months Ended June 30, 2022 | Period Over Period Change ($) | Period Over Period Change (%) | |||||||||||||
Net loss | $ | (19,021,602 | ) | $ | (4,562,875 | ) | $ | (14,458,727 | ) | 317 | % | |||||
Depreciation and amortization | 3,235,147 | 2,827,932 | 407,215 | 14 | % | |||||||||||
Interest expense | 5,540,867 | 2,293,682 | 3,247,185 | 142 | % | |||||||||||
|
|
|
|
|
| |||||||||||
EBITDA | (10,245,588 | ) | 558,739 | (10,804,327 | ) | (1934 | %) | |||||||||
Loss on disposals and non-cash impairment charges(i) | 1,053,866 | — | 1,053,866 | NM | ||||||||||||
Offering costs(ii) | 1,184,487 | 1,213,198 | (28,711 | ) | (2 | %) | ||||||||||
Stock-based compensation(iii) | 8,612,514 | 2,222 | 8,610,292 | NM | ||||||||||||
Business development & integration expenses(iv) | 354,455 | 236,603 | 117,852 | 50 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Adjusted EBITDA | $ | 959,734 | $ | 2,010,762 | $ | (1,051,028 | ) | (52 | %) | |||||||
|
|
|
|
|
| |||||||||||
Net loss margin(v) | (164 | )% | (36 | )% | ||||||||||||
Adjusted EBITDA margin(v) | 8 | % | 16 | % | ||||||||||||
NM - Not Meaningful
| (i) | Represents loss on the disposal of an aging aircraft and the non-cash impairment charges on a retired aircraft. |
| (ii) | Represents one-time professional service fees related to the preparation for potential offerings that have been expensed during the period. |
| (iii) | Represents stock-based compensation expense recognized of RSUs granted to all employees and the fair value adjustment for warrants issued in connection with the Business Combination. |
| (iv) | Represents expenses related to potential acquisition targets and additional business lines. |
| (v) | Net loss margin represents Net loss divided by Total revenue and Adjusted EBITDA margin represents Adjusted EBITDA divided by Total revenue. |
The following table reconciles net loss, the most directly comparable GAAP measure, to EBITDA and Adjusted EBITDA for the six months ended June 30, 2023 and 2022.
| Six Months Ended June 30, 2023 | Six Months Ended June 30, 2022 | Period Over Period Change ($) | Period Over Period Change (%) | |||||||||||||
Net loss | $ | (63,706,540 | ) | $ | (19,435,884 | ) | $ | (44,270,656 | ) | 228 | % | |||||
Depreciation and amortization | 4,986,192 | 4,094,854 | 891,338 | 22 | % | |||||||||||
Interest expense | 11,205,412 | 6,008,228 | 5,197,184 | 87 | % | |||||||||||
|
|
|
|
|
| |||||||||||
EBITDA | (47,514,936 | ) | (9,332,802 | ) | (38,182,134 | ) | 409 | % | ||||||||
Loss on disposals and non-cash impairment charges(i) | 1,052,407 | 781,492 | 270,915 | 35 | % | |||||||||||
Offering costs(ii) | 3,267,607 | 1,213,198 | 2,054,409 | 169 | % | |||||||||||
Stock-based compensation(iii) | 32,610,530 | 4,780 | 32,605,750 | NM | ||||||||||||
Business development & integration expenses(iv) | 873,277 | 391,976 | 481,301 | 123 | % | |||||||||||
|
|
|
|
|
| |||||||||||
Adjusted EBITDA | $ | (9,711,115 | ) | $ | (6,941,356 | ) | $ | (2,769,759 | ) | 40 | % | |||||
|
|
|
|
|
| |||||||||||
Net loss margin(v) | (532 | )% | (152 | )% | ||||||||||||
Adjusted EBITDA margin(v) | (81 | )% | (54 | )% | ||||||||||||
77
NM - Not Meaningful
| (i) | Represents loss on the disposal of an aging aircraft and the non-cash impairment charges on a retired aircraft. |
| (ii) | Represents one-time professional service fees related to the preparation for potential offerings that have been expensed during the period. |
| (iii) | Represents stock-based compensation expense recognized of RSUs granted to all employees and the fair value adjustment for warrants issued in connection with the Business Combination. |
| (iv) | Represents expenses related to potential acquisition targets and additional business lines. |
| (v) | Net loss margin represents Net loss divided by Total revenue and Adjusted EBITDA margin represents Adjusted EBITDA divided by Total revenue. |
The following table reconciles net loss, the most directly comparable GAAP measure, to EBITDA and Adjusted EBITDA for the years ended December 31, 2022 and 2021.
| Year Ended December 31, 2022 | Year Ended December 31, 2021 | Period Over Period Change ($) | Period Over Period Change (%) | |||||||||||||
Net loss | $ | (42,124,668 | ) | $ | (6,540,797 | ) | $ | (35,583,871 | ) | 544 | % | |||||
Depreciation and amortization | 9,091,219 | 6,673,685 | 2,417,534 | 36 | % | |||||||||||
Interest expense | 20,019,886 | 9,293,928 | 10,725,958 | 115 | % | |||||||||||
|
|
|
|
|
| |||||||||||
EBITDA | (13,013,563 | ) | 9,426,816 | (22,440,379 | ) | (238 | )% | |||||||||
Loss on disposals(i) | 1,769,732 | 995,528 | 774,204 | 78 | % | |||||||||||
Legal Fees(ii) | — | 110,000 | (110,000 | ) | (100 | )% | ||||||||||
Offering costs(iii) | 2,961,643 | — | 2,961,643 | — | ||||||||||||
Loss (gain) on extinguishment of debt(iv) | 844,925 | (774,300 | ) | 1,619,225 | (209 | )% | ||||||||||
Discretionary bonuses to employees and executives(v) | 10,136,530 | — | 10,136,530 | — | ||||||||||||
Stock-based compensation(vi) | 9,224 | — | 9,224 | — | ||||||||||||
Business development(vii) | 953,994 | — | 953,994 | — | ||||||||||||
|
|
|
|
|
| |||||||||||
Adjusted EBITDA | $ | 3,662,485 | $ | 9,758,044 | $ | (6,095,559 | ) | (62 | )% | |||||||
|
|
|
|
|
| |||||||||||
Net loss margin(viii) | (91 | )% | (17 | )% | ||||||||||||
Adjusted EBITDA margin(viii) | 8 | % | 25 | % | ||||||||||||
| (i) | Represents loss on the disposal or obsolescence of aging aircraft. |
| (ii) | Represents one-time costs associated with legal fees for infrequent or unusual transactions that were not capitalizable per GAAP. |
| (iii) | Represents one-time professional service fees related to the preparation for the Business Combination that have been expensed during the period. |
| (iv) | Represents loss on extinguishment of debt related to the Series 2021 Bond and forgiveness of the PPP loan. |
| (v) | Represents one-time discretionary bonuses to certain employees and executives of Bridger in connection with the issuance of the Legacy Bridger Series C Preferred Shares, issuance of the Series 2022 Bonds, execution of the Transaction Agreements and initial filing of the proxy statement/ prospectus prepared in connection with the Business Combination. |
| (vi) | Represents stock-based compensation expense recognized of the incentive units granted to selected board members and executives. |
| (vii) | Represents expenses related to potential acquisition targets and additional business lines. |
| (viii) | Net loss margin represents Net loss divided by Total revenue and Adjusted EBITDA margin represents Adjusted EBITDA divided by Total revenue. |
78
Liquidity and Capital Resources
Cash and Marketable Securities
As of June 30, 2023, our principal sources of liquidity were cash and cash equivalents of $0.8 million which were held for working capital purposes and restricted cash of $12.2 million. The restricted cash was procured through a county bond and is accessed for financing capital projects. As of June 30, 2023, the Company had $12.6 million of investments in debt securities classified as available-for-sale with short-term maturities of less than one year and carried at fair value. The Company’s available-for-sale securities investment portfolio is primarily invested in highly rated securities, with the primary objective of minimizing the potential risk of principal loss.
In connection with the Business Combination, stockholders owning 34,245,643 shares of JCIC Class A Ordinary Shares exercised their rights to have those shares redeemed for cash at a redemption price of approximately $10.16 per share, or an aggregate of $347.8 million. Following the payment of redemptions and expenses related to the Trust Account, there was approximately $2.4 million in remaining cash in the Trust Account, which was paid to UBS Securities LLC as a portion of its deferred underwriting fee from JCIC’s initial public offering.
As a result, we did not receive any cash proceeds from the Business Combination. Total direct and incremental transaction costs of Bridger, JCIC and Legacy Bridger paid at Closing were approximately $16.6 million.
We may receive up to $306.5 million from the exercise of the Warrants after the Closing, assuming the exercise in full of all the Warrants for cash, but not from the sale of the shares of Common Stock issuable upon such exercise. On October 16, 2023, the closing price of our Common Stock was $6.45 per share. For so long as the market price of our Common Stock is below the exercise price of our Warrants ($11.50 per share), our Warrants remain “out-of-the money,” and holders of our Warrants are unlikely to cash exercise their Warrants, resulting in little or no cash proceeds to us. There can be no assurance that our Warrants will be in the money prior to their January 24, 2028 expiration date, and therefore, we may not receive any cash proceeds from the exercise of our Warrants to fund our operations.
Even if the Warrants remain “out-of-the-money”, we believe that our cash on hand and debt securities will be sufficient to meet our working capital and capital expenditure requirements for a period of at least twelve months from the date of this prospectus. In considering our capital requirements and sources of liquidity, we have not relied on the receipt of proceeds from the Business Combination or from the exercise of our Warrants. For so long as the exercise price of our Warrants exceeds the trading prices for shares of our Common Stock, it is unlikely that we will receive significant proceeds, if any, from the exercise of our Warrants in the near future. Nonetheless, we believe we will be sufficiently funded, and will not require substantial additional funds for operations in order to meet our short-term liquidity needs and the execution of our business plan for at least twelve months from the date of this prospectus. Refer to the discussion further below under the section entitled “Liquidity and Capital Resources — Contractual Obligations.”
While we do not need to raise capital in order to fund our current operations for at least twelve months from the date of this prospectus, we may in the future seek to raise additional funds through various potential sources, such as equity and debt financing for general corporate purposes or for specific purposes, including in order to pursue growth initiatives. Due to the gross decrease in cash and cash equivalents (as compared to Legacy Bridger’s balance sheet at December 31, 2022), consisting of approximately $13.6 million as a result of the Business Combination, we would anticipate the need to raise additional funds through equity or debt financing (or the issuance of stock as acquisition consideration) to pursue any significant acquisition opportunity, at the time of such acquisition opportunity. Our ability to generate proceeds from equity financings will significantly depend on the market price of our Common Stock.
79
Indebtedness
As of June 30, 2023, we held $16.9 million of current liabilities, $7.8 million of which was accrued expenses and other current liabilities.
As of June 30, 2023, we held $213.4 million of long-term liabilities with $205.1 million of total long-term debt, net of debt issuance costs, which are comprised of the Series 2022 Bonds, eight (8) support vehicle loans, two (2) hangar loans and three (3) loans on six (6) aircraft.
Rocky Mountain Bank Loans
Through certain of our subsidiaries, we entered into two credit facilities with Rocky Mountain Bank to finance in part (i) the construction of airplane hangars on September 30, 2019 and (ii) the purchase of four Quest Kodiak aircraft on February 3, 2020. In connection with such credit facilities, we also entered into various term loan and other long-term debt agreements which contain certain financial covenants, including, that we maintain (i) a debt service coverage ratio that exceeds 1.25x (generally calculated as the ratio of the net operating income over the debt service payments made or as the ratio of adjusted EBITDA over the aggregate amount of interest and principal payments, in each case, as determined in the applicable agreement) and (ii) certain senior leverage ratios that do not exceed 7.00x through the third quarter of 2024, 6.00x through the third quarter of 2025, or 5.00x thereafter (generally calculated as the ratio of the senior funded debt over EBITDA, as determined in the applicable agreement). We were not considered in violation of the debt service coverage ratio requirement as of June 30, 2023. We were considered in violation of the senior leverage ratio requirements as of June 30, 2023. The calculation for this RMB covenant based on quarterly financials is a violation for only June 30, 2023. The acceleration of the obligation has been waived for the most recent quarter.
Series 2022 Bonds
On July 21, 2022, we closed a bond offering for the Series 2022 Bonds in a taxable industrial development revenue bond transaction with Gallatin County, Montana for $160.0 million (the “Series 2022 Bond Offering”). Pursuant to the Series 2022 Bond Offering, Gallatin County issued $135.0 million of bonds on July 21, 2022 and an additional $25.0 million of bonds on August 10, 2022. The proceeds from the offering, together with cash on hand, were used to redeem the capital contributions plus accrued interest for all of the remaining Legacy Bridger Series A-1 Preferred Shares and Legacy Bridger Series A-2 Preferred Shares totaling $134.0 million, the principal plus accrued interest for the Series 2021 Bond, totaling $7.7 million, to finance the construction and equipping of the Company’s third and fourth aircraft hangars in Belgrade, Montana and to fund the purchase of additional Super Scooper aircraft. The Series 2022 Bonds mature on September 1, 2027, with an annual interest rate of 11.5%. Interest will be payable semiannually on March 1 and September 1 of each year until maturity and commenced on September 1, 2022. Debt issuance costs for the Series 2022 Bonds was $4.2 million.
Optional Redemption — We may redeem the Series 2022 Bonds (i) during the period beginning on September 1, 2025 through August 31, 2026, at a redemption price equal to 103% of the principal amount plus accrued interest; (ii) during the period beginning on September 1, 2026 through August 31, 2027, at a redemption price equal to 102% of the principal amount plus accrued interest; and (iii) on or after September 1, 2027, at a redemption price equal to 100% of the principal amount plus accrued interest. At our direction, the Series 2022 Bonds may be redeemed by Gallatin County at any time, at a redemption price equal to 100% of the principal amount plus accrued interest upon the occurrence of certain events set forth in that certain Amended and Restated Trust Indenture, dated as of June 1, 2022 (the “Indenture”), between Gallatin County and U.S. Bank Trust Company, National Association, Salt Lake City, Utah (the “Trustee”).
Mandatory and Extraordinary Redemptions — Subject to the terms of the Indenture, the Series 2022 Bonds must be redeemed, including, among other things, (i) from all the proceeds of the sale of any Super Scooper, (ii) in an amount equal to (a) 50% of our operating revenues less the portion used to pay or establish reserves for all our expenses, debt payments, capital improvements, replacements, and contingencies (“Excess Cash Flow”)
80
or (b) 100% of Excess Cash Flow, in each case, in the event we fall below certain debt service coverage ratio requirements set forth in the Indenture, and (iii) upon a change of control (each a “Mandatory Redemption”). For each Mandatory Redemption, the Series 2022 Bonds will be redeemed in whole or in part, at a redemption price equal to 100% of the principal amount of each Series 2022 Bond redeemed plus any premium that would be applicable to an optional redemption of the Series 2022 Bonds on such date (and if such redemption occurs prior to September 1, 2025, the applicable premium shall be three percent (3%)) and accrued interest. Furthermore, subject to the terms of the Indenture, at our direction, the Series 2022 Bonds may be redeemed by Gallatin County at any time, at a redemption price equal to 100% of the principal amount plus accrued interest upon the occurrence of certain events, including, among other things, casualty, condemnation, or other unexpected events set forth in the Indenture.
Financial Covenants — In connection with the Series 2022 Bonds, we are a party to certain loan agreements that contain customary representation and warranties, negative covenants, including, limitations on indebtedness, reduction of liquidity below certain levels, and asset sales, merger and other transactions, and remedies on and events of default.
Under the terms of such loan agreements, we are subject to certain financial covenants, that require, among other things, that we operate in a manner and to the extent permitted by applicable law, to produce sufficient gross revenues so as to be at all relevant times in compliance with the terms of such covenants, including that we maintain (i) beginning with the fiscal quarter ending December 31, 2023, a minimum debt service coverage ratio (generally calculated as the aggregate amount of our total gross revenues, minus operating expenses, plus interest, depreciation and amortization expense, for any period, over our maximum annual debt service requirements, as determined under such loan agreement) that exceeds 1.25x and (ii) beginning with the fiscal quarter ending September 30, 2022, a minimum liquidity of not less than $8 million in the form of unrestricted cash and cash equivalents, plus liquid investments and unrestricted marketable securities at all times.
Subject to the terms of the loan agreements, in the event we are unable to comply with the terms of the financial covenants, we may be required (among other potential remedial actions) to engage an independent consultant to review, analyze and make recommendations with respect to our operations or in some instances, this could result in an event of default and/or the acceleration of our debt obligations under the loan agreements. In addition, the acceleration of our debt obligations may in some instances (as set forth in the Amended and Restated Charter) result in an increase in the dividend rate of the Series A Preferred Stock by 2.00% per annum from the dividend rate otherwise in effect at such time.
Mandatorily Redeemable Preferred Stock
Legacy Bridger Series B Preferred Shares
On April 25, 2022, we used a portion of the proceeds from the issuance of the Legacy Bridger Series C Preferred Shares, to redeem all 60,000,000 of our outstanding Legacy Bridger Series B Preferred Shares for $70.0 million, inclusive of $10.0 million in accrued interest.
Legacy Bridger Series A Preferred Shares
On April 25, 2022, we and our investors included a new mandatory redemption provision requiring Legacy Bridger Series A Preferred Shares to be redeemed on April 25, 2032. Due to the mandatory redemption provision, Legacy Bridger Series A Preferred Shares were reclassified from mezzanine equity to liability. We elected the fair value option to measure the modification of the Legacy Bridger Series A Preferred Shares. On July 25, 2022, we used the proceeds from the Series 2022 Bonds plus cash on hand to redeem in full the remaining 6,055,556 shares of the Legacy Bridger Series A Preferred Shares for aggregate proceeds of $136.3 million. The fair values of the Legacy Bridger Series A Preferred Shares increased by $3.9 million from interest accrued since the modification on April 25, 2022 and no gain or loss were recorded to net loss upon redemption.
81
Mezzanine and Permanent Equity
Series A Preferred Stock
On April 25, 2022, we authorized and issued 315,789.473684 Legacy Bridger Series C Preferred Shares for aggregate proceeds of $288.5 million, net of issuance costs of $11.5 million. Legacy Bridger Series C Preferred Shares rank senior to our Common Stock and ranked subordinate to Legacy Bridger Series A Preferred Shares with respect to the distribution of assets upon liquidation or certain triggering events. Upon the Closing, Legacy Bridger Series C Preferred Shares were exchanged for shares of Series A Preferred Stock on a one-to-one basis as a portion of the merger consideration issued in connection with the Business Combination. The Series A Preferred Stock is classified as mezzanine equity as it remains probable that they may become redeemable upon the mandatory redemption date of April 25, 2032. Series A Preferred Stock does not participate in earnings and is non-voting. For additional information regarding the terms and conditions of the Series A Preferred Stock, see “Note 17 – Mezzanine Equity” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional details.
Prior to the Closing, Legacy Bridger Series C Preferred Shares accrued interest daily at 7% per annum for the first year, 9% per annum for the second year and 11% per annum thereafter. Following the Closing, the Series A Preferred Stock will continue to accrue interest daily at 7% per annum for the first six years, 9% per annum for the seventh year, and 11% per annum thereafter. Accrued interest for the Series A Preferred Stock was $10.1 million as of June 30, 2023.
As of June 30, 2023, it was probable that the Series A Preferred Stock may become redeemable at the holder’s option on or after March 29, 2027. We have elected to recognize changes in redemption value immediately, adjusting the preferred shares to the maximum redemption value at each reporting date. Upon the Closing and exchange of Legacy Bridger Series C Preferred Shares for shares of Series A Preferred Stock, the 50% multiplier applicable to redemptions of Legacy Bridger Series C Preferred Shares, valued at $157.9 million as of December 31, 2022, was removed and treated as a deemed dividend. As of June 30, 2023, Series A Preferred Stock had a carrying value and redemption value of $342.7 million.
Common Stock
Legacy Bridger had 30,000,000 Legacy Bridger Class A Common Shares issued and outstanding as of December 31, 2022. The holders of these shares were entitled to one vote for each share held of record on all matters submitted to a vote of our shareholders. These Legacy Bridger Class A Common Shares were issued to ElementCompany, LLC.
Legacy Bridger had 9,756,130 Legacy Bridger Class B Common Shares issued and outstanding as of December 31, 2022. The holders of these Legacy Bridger Class B Common Shares were entitled to one vote for each share held of record on all matters submitted to a vote of our shareholders.
Legacy Bridger had 243,871 Legacy Bridger Class C Common Shares issued and outstanding as of December 31, 2022. Legacy Bridger also had 606,061 shares of Legacy Bridger Class D Common Shares issued and outstanding as of December 31, 2022. These Legacy Bridger Class C Common Shares and Legacy Bridger Class D Common Shares are non-voting shares.
Prior to the Closing, Legacy Bridger’s voting power followed the structure of the elected board members with three (3) designees from the holders of Legacy Bridger Class A Common Shares and two (2) designees from the holders of Legacy Bridger Class B Common Shares. This remained in place until the Closing.
Upon the Closing on January 24, 2023 and at June 30, 2023, we had 43,769,290 and 44,505,944 shares of Common Stock issued and outstanding.
82
Historical Cash Flows
The following table presents a summary of our consolidated cash flows from operating, investing and financing activities for the periods indicated.
| Six Months Ended June 30, 2023 | Six Months Ended June 30, 2022 | |||||||
Net cash used in operating activities | $ | (53,444,612 | ) | $ | (10,029,205 | ) | ||
Net cash provided by (used in) investing activities | 28,565,247 | (8,998,304 | ) | |||||
Net cash (used in) provided by financing activities | (4,496,266 | ) | 122,921,765 | |||||
Effect of exchange rate changes | 406 | (263 | ) | |||||
|
|
|
| |||||
Net change in cash and cash equivalents | $ | (29,375,225 | ) | $ | 103,893,993 | |||
|
|
|
| |||||
Operating Activities
Net cash used in operating activities was $53.4 million for the six months ended June 30, 2023, compared to Net cash used in operating activities of $10.0 million for the six months ended June 30, 2022. Net cash used in operating activities reflects net loss of $63.7 million for the six months ended June 30, 2023 compared to $19.4 million for the six months ended June 30, 2022. Net cash used in operating activities for the six months ended June 30, 2023 reflects add-backs to Net loss for non-cash charges totaling $37.4 million, primarily driven by stock-based compensation expense associated with the RSUs granted to certain executives and senior management. Net cash used in operating activities for the six months ended June 30, 2022 reflects add-backs to Net loss for non-cash charges totaling $9.5 million, primarily driven by interest accrued on Legacy Bridger Series B Preferred Shares and depreciation and amortization.
Investing Activities
Net cash provided by investing activities was $28.6 million for the six months ended June 30, 2023, compared to Net cash used in investing activities of $9.0 million for the six months ended June 30, 2022. Net cash provided by investing activities for the six months ended June 30, 2023 reflects proceeds from maturities of marketable securities of $42.7 million, purchases of property, plant and equipment of $12.5 million, which primarily comprised of purchases of aircraft and aircraft improvements, and the construction in progress of the third hangar of $2.4 million. Net cash used in investing activities for the six months ended June 30, 2022 reflects purchases of property, plant and equipment of $5.3 million, which primarily comprised of aircraft improvements.
Financing Activities
Net cash used in financing activities was $4.5 million for the six months ended June 30, 2023, compared to Net cash provided by financing activities of $122.9 million for the six months ended June 30, 2022. Net cash used in financing activities for the six months ended June 30, 2023 reflects costs incurred related to the Closing of $6.8 million, proceeds from the Closing of $3.2 million, and repayments on debt of $0.9 million. Net cash provided by financing activities for the six months ended June 30, 2022 reflects borrowings from Legacy Bridger Series C Preferred Shares members of $293.7 million, payments to Legacy Bridger Series A Preferred Shares of $100.0 million, and payments to Legacy Bridger Series B Preferred Shares of $70.0 million.
83
The following table presents a summary of our consolidated cash flows from operating, investing and financing activities for the periods indicated.
| Year Ended December 31, 2022 | Year Ended December 31, 2021 | |||||||
Net cash (used in) provided by operating activities | $ | (9,917,608 | ) | $ | 6,020,870 | |||
Net cash used in investing activities | (89,813,216 | ) | (54,762,852 | ) | ||||
Net cash provided by financing activities | 124,929,731 | 60,758,004 | ||||||
Effect of exchange rate changes | (413 | ) | (776 | ) | ||||
|
|
|
| |||||
Net change in cash and cash equivalents | $ | 25,198,494 | $ | 12,015,246 | ||||
|
|
|
| |||||
Operating Activities
Net cash used in operating activities was $9.9 million for the year ended December 31, 2022, compared to Net cash provided by operating activities of $6.0 million for the year ended December 31, 2021. Net cash used in operating activities reflects net loss of $42.1 million for the year ended December 31, 2022 compared to $6.5 million for the year ended December 31, 2021. Net cash used in operating activities for the year ended December 31, 2022 reflects add-backs to Net loss for non-cash charges totaling $20.9 million, primarily driven by depreciation and amortization, change in fair value of Legacy Bridger Series A Preferred Shares and interest accrued on Legacy Bridger Series B Preferred Shares. Net cash provided by operating activities for the year ended December 31, 2021 reflects add-backs to Net loss for non-cash charges totaling $13.4 million, primarily driven by $6.7 million of depreciation and amortization.
Investing Activities
Net cash used in investing activities was $89.8 million for the year ended December 31, 2022, compared to Net cash used in investing activities of $54.8 million for the year ended December 31, 2021. Net cash used in investing activities for the year ended December 31, 2022 reflects purchases of marketable securities of $60.2 million, purchases of property, plant and equipment of $25.6 million, which primarily comprised of purchases of aircraft and aircraft improvements, the construction in progress of the third hangar of $9.8 million, and proceeds from maturities of marketable securities of $5.5 million. Net cash used in investing activities for the year ended December 31, 2021 reflects investments in the construction currently in progress for Super Scoopers and hangars of $31.2 million and purchases of property, plant and equipment of $22.6 million.
Financing Activities
Net cash provided by financing activities was $124.9 million for the year ended December 31, 2022, compared to Net cash provided in financing activities of $60.8 million for the year ended December 31, 2021. Net cash provided by financing activities for the year ended December 31, 2022 reflects proceeds from the issuance of the Legacy Bridger Series C Preferred Shares, net of issuance costs, of $288.5 million, borrowings from the Series 2022 Bonds of $160.0 million, payments to the holders of Legacy Bridger Series A Preferred Shares and Legacy Bridger Series B Preferred Shares of $236.3 million and $70.0 million, respectively, payment for the extinguishment of the Series 2021 Bond of $7.5 million and payment of debt issuance costs for the Series 2022 Bonds of $4.4 million. Net cash provided by financing activities for the year ended December 31, 2021 reflects proceeds of $50.0 million from the issuance of Legacy Bridger Series B Preferred Shares, $7.3 million of borrowings from the Series 2021 Bond and proceeds of $5.0 million from the issuance Legacy Bridger Series A Preferred Shares.
84
Off-Balance Sheet Arrangements
As of June 30, 2023 and 2022, we did not have any relationships with special purpose or variable interest entities or other which would have been established for the purpose of facilitating off-balance sheet arrangements or other off-balance sheet arrangements.
Contractual Obligations
Our principal commitments consist of obligations for outstanding debt, hangar construction obligations, and leases. The following table summarizes our contractual obligations as of June 30, 2023.
| Payments Due by Period | ||||||||||||
| Total | Current | Noncurrent | ||||||||||
Hangar construction obligations | $ | 758,960 | $ | 758,960 | $ | — | ||||||
Lease obligations | 1,855,179 | 338,697 | 1,516,482 | |||||||||
Debt obligations | 212,694,648 | 3,455,019 | 209,239,629 | |||||||||
|
|
|
|
|
| |||||||
Total | $ | 215,308,787 | $ | 4,552,676 | $ | 210,756,111 | ||||||
|
|
|
|
|
| |||||||
On February 14, 2023, we made a payment of $9.1 million for the purchase of aircraft under our purchase agreement with Longview Aviation Services Inc. and Viking Air Limited (the manufacturer of our Super Scooper aircraft and an affiliate of Longview Aviation Services Inc.), dated April 13, 2018.
Quantitative and Qualitative Disclosures About Market Risk
Bridger is a smaller reporting company as defined by Rule 12b-2 of the Exchange Act and is not required to provide the information otherwise required under this item.
Critical Accounting Policies and Estimates
Our financial statements and the related notes included elsewhere in this prospectus are prepared in accordance with GAAP. The preparation of these financial statements requires us to make estimates and assumptions that affect the reported amounts of assets, liabilities, revenue, costs and expenses, provision for income taxes and related disclosures. We base our estimates on historical experience and on various other assumptions that we believe to be reasonable under the circumstances. Changes in accounting estimates are reasonably likely to occur from period to period. Accordingly, actual results could differ significantly from the estimates made by our management. We evaluate our estimates and assumptions on an ongoing basis. To the extent that there are material differences between these estimates and actual results, our future financial statement presentation, financial condition, results of operations and cash flows will be affected.
We believe that the following critical accounting policies involve a greater degree of judgment or complexity than our other accounting policies. Accordingly, these are the policies we believe are the most critical to aid in fully understanding and evaluating our financial condition and results of operations.
Investments in Marketable Securities
Investments in debt securities are classified as available-for-sale and are carried at fair value, with unrealized gains and losses reported as accumulated other comprehensive income. Gains and losses are recognized when realized. Unrealized losses are evaluated for impairment to determine if the impairment is credit related. An other-than-temporary credit impairment would be recognized as an adjustment to income. Gains and losses are determined using the first-in first-out method. Investments in marketable securities are classified as current assets with short-term maturities of less than one year.
Revenue Recognition
We charge daily and hourly rates depending upon the type of firefighting services rendered and under which contract the services are performed. These services are primarily split into flight revenue and standby revenue.
85
Flight revenue is primarily earned at an hourly rate when the engines of the aircraft are started and stopped upon request of the customer, tracked via a Hobbs meter. Standby revenue is earned primarily as a daily rate when aircraft are available for use at a fire base, awaiting request from the customer for flight deployment.
We enter into short, medium and long-term contracts with customers, primarily with government agencies to deploy aerial fire management assets during the firefighting season. Revenue is recognized when performance obligations under the terms of a contract with our customers are satisfied and payment is typically due within 30 days of invoicing. This occurs as the services are rendered and include the use of the aircraft, pilot, and field maintenance personnel to support the contract.
Contracts are based on either a CWN or EU basis. Rates established are generally more competitive based on the security of the revenue from the contract (i.e., an EU versus only on an as-needed basis in CWN). These rates are delineated by the type of service, generally flight time or time available for deployment. Once an aircraft is deployed on a contract the fees are earned at these rates and cannot be obligated to another customer. Contracts have no financing components and consideration is at pre-determined rates. No variable considerations are constrained within the contracts.
The transaction prices are allocated on the service performed and tracked real-time by each operator in a duty log. On at least a monthly basis, the services performed and rates are validated by each customer. Acceptance by the customer is evidenced by the provision of their funded task order or accepted invoice.
Other revenue consists of leasing revenues from the rental of BSI, LLC facilities to another related party as well as external repair work performed on customer aircraft by Bridger Aviation Repair, LLC.
Payment terms vary by customer and type of revenue contract. We generally expect that the period of time between payment and transfer of promised goods or services will be less than one year. In such instances, we have elected the practical expedient to not evaluate whether a significant financing component exists. As permitted under the practical expedient available under ASC 606, we do not disclose the value of unsatisfied performance obligations for (i) contracts with an original expected length of one year or less and (ii) contracts for which we recognize revenue at the amount which we have the right to invoice for services performed.
Stock-Based Compensation
Incentive Units
During the years ended December 31, 2022 and 2021, we granted incentive units (the “Legacy Bridger Incentive Units”) to selected board members and executives. Within each grant, 80% of the Legacy Bridger Incentive Units vest annually over a four-year period subject to continued service by the grantee (the “Time-Vesting Incentive Units”) and the remaining 20% of the Legacy Bridger Incentive Units vest upon a qualifying change of control event (the “Exit-Vesting Incentive Units”). Notwithstanding the above, any unvested Time-Vesting Incentive Units will become vested Time-Vesting Incentive Units if a qualifying change of control event occurs prior to the respective award’s four-year service-based vesting period. Upon termination of the board member or executive, the Company has the right, but not the obligation, to repurchase all or any portion of the vested Incentive Units at fair market value. We did not grant any Legacy Bridger Incentive Units for the three and six months ended June 30, 2023.
For the Time-Vesting Incentive Units, compensation cost is recognized over the requisite service period on a straight-line basis. Upon a qualifying change of control event, the unrecognized compensation expense related to the Time-Vesting Incentive Units will be recognized when the change of control event is considered probable. For the Exit-Vesting Incentive Units, expense is recognized when a qualifying change of control event is considered probable, which has not occurred as of June 30, 2023. Forfeitures are accounted for as they occur.
Compensation cost for the Legacy Bridger Incentive Units is measured at their grant-date fair value. The value of Legacy Bridger Common Shares is derived through an option pricing model, which incorporates various
86
assumptions. Use of a valuation model requires management to make certain assumptions with respect to selected model inputs. Expected volatility was calculated based on the observed equity volatility for comparable companies. The expected time to liquidity event is based on management’s estimate of time to an expected liquidity event. The dividend yield was based on our expected dividend rate. The risk-free interest rate is based on U.S. Treasury zero-coupon issues. The weighted-average assumptions we used in the option pricing model for its 2021 grants are as follows.
Dividend yield (%) | 0 | |||
Expected volatility (%) | 46.5 | |||
Risk-free interest rate (%) | 1.26 | |||
Term (in years) | 5.00 | |||
Discount for lack of marketability (%) | 30 |
Restricted Stock Units
In January 2023, in connection with the Closing, the Company and its board of directors established and approved the 2023 Omnibus Incentive Plan (the “Plan”) which allowed the Company to grant RSUs to Bridger directors and employees (the “Participants”). RSUs are settled in shares of the Company’s Common Stock as the RSUs become vested. The RSUs accrue dividend equivalents associated with the underlying shares of Common Stock as the Company declares dividends. Dividends will be paid to holders of RSUs in cash upon the vesting date of the associated RSU and will be forfeited if the RSU does not vest.
On January 24, 2023, the Company granted 6,581,496 RSUs, of which 2,400,354 RSUs vested immediately upon Closing, subject to a one-year lock up period ending January 24, 2024. The fair value of the RSUs that vested immediately upon Closing of the Transactions is the closing stock price on the date of grant, subject to a discount for lack of marketability due to the post-vesting restrictions. The remaining 4,181,142 RSUs vest over a period ranging from three to six years, subject to the Participant’s continued employment. The fair value of the RSUs that vest over time is the closing stock price on the date of grant. Upon vesting of the award, the Company will issue shares of Common Stock to the award holder.
On April 13, 2023, the Company granted 2,234,750 RSUs to employees of the Company. These RSUs vest over a period of one to six years, subject to the participant’s continued employment. The fair value of the RSUs that vest over time is the closing stock price on the date of grant. Upon vesting of the award, the Company will issue shares of Common Stock to the award holder.
Impairment of Goodwill, Other Intangibles Assets and Long-Lived Assets
Goodwill
Goodwill represents the excess of purchase price over fair value of the net assets acquired in an acquisition. We assess goodwill for impairment as of December 31 annually or more frequently upon an indicator of impairment. Goodwill is tested for impairment at the reporting unit level by first performing a qualitative assessment to determine whether it is more likely than not that the fair value of the reporting unit is less than its carrying value.
When we elect to perform a qualitative assessment and conclude it is more likely that the fair value of the reporting unit is greater than its carrying value, no further assessment of that reporting unit’s goodwill is necessary. Otherwise, a quantitative assessment is performed, and the fair value of the reporting unit is determined. If the carrying value of the reporting unit exceeds its fair value, an impairment loss equal to the excess is recorded. Conditions that would trigger an impairment assessment include, but are not limited to, a significant adverse change in legal factors or the business climate that could affect the value of an asset or an adverse reaction. As of the December 31, 2022 annual goodwill impairment test, the Company’s qualitative analysis indicated the fair value of the Company’s reporting unit exceeded its carrying value. No impairment charge for goodwill was recorded for the three and six months ended June 30, 2023 and 2022, respectively.
87
Long-Lived Assets
A long-lived asset (including amortizable identifiable intangible assets) or asset group is tested for recoverability whenever events or changes in circumstances indicate that its carrying amount may not be recoverable. Conditions that may indicate impairment include, but are not limited to, a significant adverse change in customer demand or business climate that could affect the value of an asset, a product recall or an adverse action or assessment by a regulator. When indicators of impairment are present, we evaluate the carrying value of the long-lived assets in relation to the operating performance and future undiscounted cash flows of the underlying assets. We adjust the net book value of the long-lived assets to fair value if the sum of the expected future cash flows is less than book value.
Property, Plant and Equipment, Net
Property, plant and equipment is stated at net book value, cost less depreciation. Depreciation for aircraft, engines and rotable parts is recorded over the estimated useful life based on flight hours. Depreciation for unmanned aerial vehicles, vehicles and equipment and buildings is computed using the straight-line method over the estimated useful lives of the property, plant and equipment. The table below summarizes depreciable lives by asset category:
| Estimated useful life | ||||
Aircraft, engines and rotable parts | 1,500 -6,000 flight hours | |||
Unmanned aerial vehicles | 5 — 10 years | |||
Vehicles and equipment | 3 — 5 years | |||
Buildings | 40 years | |||
Property, plant and equipment are reviewed for impairment as discussed above under “— Impairment of Goodwill, Other Intangibles Assets and Long-Lived Assets — Long-Lived Assets.”
Cost Method Investments
We hold equity securities without a readily determinable fair value, which are only adjusted for observable price changes in orderly transactions for the same or similar equity securities or any impairment, totaling $1,000 thousand as of June 30, 2023 and December 31, 2022, respectively.
Variable Interest Entities
We follow ASC 810-10-15 guidance with respect to accounting for VIEs. These entities do not have sufficient equity at risk to finance their activities without additional subordinated financial support from other parties or whose equity investors lack any of the characteristics of a controlling financial interest. A variable interest is an investment or other interest that will absorb portions of a VIE’s expected losses or receive portions of its expected returns and are contractual, ownership or pecuniary in nature and that change with changes in the fair value of the entity’s net assets. A reporting entity is the primary beneficiary of a VIE and must consolidate it when that party has a variable interest, or combination of variable interests, that provide it with a controlling financial interest. A party is deemed to have a controlling financial interest if it meets both of the power and loss/benefits criteria. The power criterion is the ability to direct the activities of the VIE that most significantly impact its economic performance. The losses/benefits criterion is the obligation to absorb losses from, or right to receive benefits from, the VIE that could potentially be significant to the VIE. The VIE model requires an ongoing reconsideration of whether a reporting entity is the primary beneficiary of a VIE due to changes in the facts and circumstances. For the three and six months ended June 30, 2023 and 2022, the VIE, NFMS, LLC, is consolidated into our financial statements. See “Note 2 – Summary of Significant Accounting Policies” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional information.
On November 7, 2022, we acquired all of the outstanding equity interests of MA, LLC, and it has not been accounted for as a VIE in subsequent reporting periods.
88
Fair Value of Financial Instruments
We follow guidance in ASC 820, Fair Value Measurement, where fair value is defined as the price that would be received to sell an asset or paid to transfer a liability in an orderly transaction between market participants at the measurement date. Fair value measurements are determined within a framework that establishes a three-tier hierarchy which maximizes the use of observable market data and minimizes the use of unobservable inputs to establish a classification of fair value measurements for disclosure purposes. Inputs may be observable or unobservable. Observable inputs reflect the assumptions market participants would use in pricing the asset or liability based on market data obtained from sources independent of our business. Unobservable inputs reflect our own assumptions about the assumptions market participants would use in pricing the asset or liability based on the information available.
Warrant Liabilities
We account for the Warrants issued in connection with the Business Combination in accordance with the guidance contained in accordance with ASC 480, Distinguishing Liabilities from Equity and ASC 815-40, Derivatives and Hedging-Contracts in Entity’s Own Equity, under which the Warrants do not meet the criteria for equity treatment and must be recorded as liabilities. Accordingly, we classify the Warrants as liabilities at their fair value and adjust the Warrants to fair value at each reporting period. The warrant liabilities are subject to remeasurement at each balance sheet date until exercised. See “Note 2 – Summary of Significant Accounting Policies” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this prospectus for additional information.
Recent Accounting Pronouncements
For additional information regarding recent accounting pronouncements adopted and under evaluation, refer to “Note 2 – Summary of Significant Accounting Policies” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this prospectus.
Emerging Growth Company and Smaller Reporting Company Status
Section 102(b)(1) of the JOBS Act exempts “emerging growth companies” as defined in Section 2(A) of the Securities Act of 1933, from being required to comply with new or revised financial accounting standards until private companies are required to comply with the new or revised financial accounting standards. The JOBS Act provides that a company can choose not to take advantage of the extended transition period and comply with the requirements that apply to non-emerging growth companies, and any such election to not take advantage of the extended transition period is irrevocable. We are an “emerging growth company” and have elected to take advantage of the benefits of this extended transition period.
We will use this extended transition period for complying with new or revised accounting standards that have different effective dates for public business entities and non-public business entities until the earlier of the date that we (a) are no longer an emerging growth company or (b) affirmatively and irrevocably opt out of the extended transition period provided in the JOBS Act. The extended transition period exemptions afforded by our emerging growth company status may make it difficult or impossible to compare our financial results with the financial results of another public company that is either not an emerging growth company or is an emerging growth company that has chosen not to take advantage of this exemption because of the potential differences in accounting standards used. Refer to “Note 2 – Summary of Significant Accounting Policies” of the Notes to Unaudited Condensed Consolidated Financial Statements included in this prospectus for the recent accounting pronouncements adopted and the recent accounting pronouncements not yet adopted for the three and six months ended June 30, 2023 and the year ended December 31, 2022.
We will remain an “emerging growth company” under the JOBS Act until the earliest of (a) December 31, 2028, (b) the last date of our fiscal year in which we have total annual gross revenue of at least $1.235 billion,
89
(c) the last date of our fiscal year in which we are deemed to be a “large accelerated filer” under the rules of SEC with at least $700.0 million of outstanding securities held by non-affiliates or (d) the date on which we have issued more than $1.0 billion in non-convertible debt securities during the previous three years.
We will be a “smaller reporting company” as defined in Item 10(f)(1) of Regulation S-K. Smaller reporting companies may take advantage of certain reduced disclosure obligations, including, among other things, providing only two years of audited financial statements. We will remain a smaller reporting company until the last day of the fiscal year in which (i) the market value of our common stock held by non-affiliates is greater than or equal to $250 million as of the end of that fiscal year’s second fiscal quarter, and (ii) our annual revenues are greater than or equal to $100 million during the last completed fiscal year or the market value of our common stock held by non-affiliates exceeds $700 million as of the end of that fiscal year’s second fiscal quarter.
Internal Control Over Financial Reporting
We have identified material weaknesses in our internal control over financial reporting, which we are in the process of, and are focused on, remediating. The first material weakness is related to properly accounting for complex transactions within our financial statement closing and reporting process. The second material weakness arises from our failure to design and maintain effective IT general controls over the IT systems used within the processing of key financial transactions. Specifically, we did not design and maintain user access controls to ensure appropriate segregation of duties and that adequately restrict user and privileged access to financial applications, programs, and data to appropriate company personnel. Additionally, we identified a material weakness in our internal control over financial reporting related to the period end account reconciliation review and entity level financial statement review controls which did not operate within a sufficient level of precision.
We have begun the process of and are focused on designing and implementing effective internal controls measures to improve our internal control over financial reporting and remediate the material weaknesses, including:
| • | actively recruiting additional personnel with knowledge of GAAP, in addition to engaging and utilizing third-party consultants and specialists to supplement our internal resources and implementing processes and controls to segregate key functions within our finance systems, as appropriate; |
| • | designing and implementing a formalized control plan related to IT general controls, including controls related to managing access to financially significant systems within our IT environment; and |
| • | engaging a third-party consultant to assist with evaluating and documenting the design and operating effectiveness of internal controls and assisting with the remediation of deficiencies, as necessary. |
While these actions and planned actions are subject to ongoing management evaluation and will require validation and testing of the design and operating effectiveness of internal controls over a sustained period of financial reporting cycles, we are committed to the continuous improvement of our internal control over financial reporting and will continue to diligently review our internal control over financial reporting.
Although we plan to complete this remediation process as quickly as possible, we are unable, at this time, to estimate how long it will take and our efforts may not be successful in remediating the deficiencies or material weaknesses. In addition, even if we are successful in strengthening our controls and procedures, we can give no assurances that in the future such controls and procedures will be adequate to prevent or identify errors or irregularities or to facilitate the fair preparation and presentation of our financial statements.
90
BUSINESS
Unless the context otherwise requires, all references in this section to “Bridger,” “we”, “us”, “our” or “the Company” refer to the business of Legacy Bridger and its subsidiaries prior to the consummation of the Business Combination and the business of Bridger Aerospace Group Holdings, Inc. and its subsidiaries after the consummation of the Business Combination.
Company Overview
Bridger provides aerial wildfire surveillance, relief and suppression and aerial firefighting services using next-generation technology and environmentally friendly and sustainable firefighting methods primarily throughout the United States. Our mission is to save lives, property and habitats threatened by wildfires, leveraging our high-quality team, specialized aircraft and innovative use of technology and data. We are meeting an underserved and growing need for next-generation full-service aerial firefighting platforms.
Bridger was founded by our Chief Executive Officer and former Navy SEAL officer Timothy Sheehy, in Bozeman, Montana in 2014 with one aircraft and a vision to build a global enterprise to fight wildfires. Bridger has since grown into a full-spectrum aerial firefighting service provider in the U.S. and in the field of aerial wildfire management, offering technology and services to provide front-line firefighters and fire suppression decision-makers access to key fire data in order to effectively combat wildfires. As of September 30, 2023, the Company has a team of 179 employees and has developed an ecosystem of solutions, services and technologies supporting firefighting ground crews and the public.
Wildland-urban interface has grown by more than 179 thousand square kilometers in the U.S. from 1980 to 2020, according to a 2022 article by the USFS (the “USFS WUI Increase Article”). WUI areas, which comprise 9.4% of the U.S. land area, now include nearly one-third of all residences, according to the USFS WUI Increase Article. At the same time, the annual acres burned per fire between 1985 and 2020 have increased by nearly five-fold according to data published by the NIFC.3 As the WUI areas continue to grow and wildfires grow larger, more aggressive firefighting strategies are necessary to ensure public safety. Additionally, the NIFC Suppression Costs Data shows total number of U.S. acres burned annually has increased more than three-fold from 1985 to 2020.
These trends have led to a response by the U.S. federal government to increase spending on fire suppression since 1985 with a compound annual growth rate of 8.4% to $4.4 billion in 2021, according to the NIFC Suppression Costs Data. Even with this increased spending and demand, unfulfilled requests for fixed wing aircraft for aerial firefighting grew at a compound annual growth rate of 4.7% between 2002 and 2022, with 654 unfulfilled requests in 2022, according to the National Interagency Coordination Center Wildland Fire Summary Statistics Annual Report 2022 (the “NICC 2022 Annual Report”).
Bridger’s management estimates that aerial suppression spend represented approximately 42.7% of an estimated $21.9 billion firefighting market globally in 2021.4 There is a rapidly growing global need for fire
| 3 | NIFC, Suppression Costs, last accessed Oct. 9, 2023 (https://www.nifc.gov/fire-information/statistics/suppression-costs) (the “NIFC Suppression Costs Data”). |
| 4 | Bridger management defines the global firefighting market as the sum of the air-based suppression, ground, and fire data, aerial imagery-related, and emergency mobile application markets. The air-based suppression market is based on the global aerial firefighting market size from the June 2021 Verified Market Research report. The ground market is based on Bridger management’s estimated $4.3 billion US ground market based on budgeted wildfire expenditures for key federal and state agencies; Bridger management estimated that the US ground market represented approximately 45% of the global ground market. The fire data, aerial imagery-related, and emergency mobile application market is based on Bridger management’s estimated $0.9 billion US market for the fire data and surveillance-related emergency market based on review of available peer company data; Bridger management estimated that the U.S. fire data and surveillance-related emergency market represented approximately 30% of the global fire data, aerial imagery-related, and emergency mobile application market. |
91
suppression assets, and Bridger’s management believes that a shift away from ground services to air-based suppression has already commenced. The market is anticipated to continue to expand as wildfires rage across Europe and the U.S.
Our Services
Our portfolio is organized across two core offerings:
| • | Fire Suppression: Consists of deploying specialized Super Scooper aircraft to drop large amounts of water quickly and directly on wildfires. |
| • | Aerial Surveillance: Consists of providing aerial surveillance for fire suppression aircraft over an incident and providing tactical coordination with the incident commander. Aerial surveillance uses both manned aircraft (“Air Attack”) and unmanned aircraft. |
Fire Suppression
We provide direct fire suppression aerial firefighting support for ground crews by operating Super Scoopers. Aerial fire suppression is provided in conjunction with traditional ground firefighting approaches, and specialized aircraft drop high volumes of water directly onto active wildfires. Because wildfires largely occur within close proximity to a major water source, leveraging readily available resources is more time- and fuel-efficient in combating wildfires when time is of the essence. The Super Scooper aircraft allow for rapid delivery of water strikes to extinguish wildfires, particularly when deployed in tandem or larger groups to allow for continuous water delivery as aircraft return to the water source. In 2020, we were the first launch customer for the CL-415EAF Super Scooper aircraft produced by LAS, and we immediately deployed the aircraft to combat wildfires in Nevada, Oregon and Washington.
Aerial Surveillance
Wildfires can spread quickly and change course in an instant. Our aerial surveillance services provide decision-makers rapid, current intelligence from useful aerial vantage points, giving them access to key information to support more effective deployment of ground firefighters and improved safety for the public at large. Our aerial surveillance services leverage manned and unmanned aircraft.
Our manned aerial surveillance services operate twelve aircraft, including four Twin Commanders (“Twin Commanders”), four Daher Kodiak 100s (“Daher Kodiak”), three Pilatus PC-12 and one DeHaviland Twin Otter (“Twin Otter”). We have seven years of experience in providing USFS Type 1 Air Tactical Group Supervisors (“ATGS”) the aerial platform to relay the necessary information to ground-based Interagency Incident Commanders (“Incident Commanders”) who are responsible for the overall management of the wildfire and determine how resources are deployed. We are one of the largest ATGS platform providers in the U.S. and have contracts covering 100% of the U.S.
Our unmanned aerial surveillance services use UAS to fly in low-visibility or in hazardous conditions over active wildfires where manned aircraft are not optimal due to safety concerns. UAS surveillance services provide near real-time data to USFS Incident Commanders using infrared and optical imagery to track the movement and status of the entire fire area and inform decisions in allocating resources. The data from UAS surveillance is displayed on a tablet, providing decision-makers with near real-time data from the aircraft in flight. Our current UAS include two Aurora Vertical Take-Off and Landing (“eVTOL”) Skiron systems (“Aurora eVTOL Skiron”). The two Aurora eVTOL Skiron aircraft are fully electric and emit zero emissions during operations, supporting our sustainable and environmentally friendly firefighting methods. Our UAS operations have logged over 385 hours of flight time in multiple wildland complexes since inception. As a result, the U.S. Department of the Interior chose us to be the first ever Type I UAS on a call-when-needed basis over active wildfires throughout the U.S.
92
Our Aircraft
We deploy modern technology to track and attack wildland fires and have an expansive fleet of specialized firefighting aircraft stationed at two existing hangars at the Bozeman Yellowstone International Airport in Belgrade, Montana. Our aircraft form the basis of our service offerings and, as such, we strive to continually invest in advancements in aerial firefighting platforms. We continually invest in our fleet to expand our capabilities while assessing opportunities to acquire next-generation firefighting assets to combat the rising threat of wildfires.
We currently operate an aircraft fleet of 20 planes comprised of the following:
| • | 6 Super Scoopers |
| • | 4 Twin Commanders |
| • | 4 Daher Kodiak |
| • | 3 Pilatus PC-12 (one owned and two unowned) |
| • | 2 Aurora eVTOL Skiron |
| • | 1 Twin Otter (unowned) |
Additionally, upon the successful consummations of the Bighorn Acquisition and the Spanish Super Scooper Acquisition, our fleet would be expanded by the following aircraft:
| • | 12 aircraft used for wildfire smoke jumping, as well as special mission transport and delivery for government customers, to be purchased in connection with the Bighorn Acquisition (consisting of 4 CASA 212-200 Aviocar aircraft, 5 Dornier 228-200 aircraft and 3 Bombardier DHC-8-106 ‘Dash 8’ aircraft); and |
| • | 4 Super Scoopers (to be purchased in connection with the Spanish Super Scooper Acquisition). |
93
Super Scooper
The Super Scooper is the only aircraft designed and built to fight fires and can fly more aggressively in extreme terrains over all other aircraft with equal or greater water capacity. The Super Scooper is an amphibious aircraft that skims the surface of a body of water to scoop water into onboard tanks to drop on a fire. The purposeful design of the Super Scooper allows for an aggressive low-altitude flight profile, which enables pilots to deliver their drops with more precision, hitting the fire harder and extinguishing it faster. Super Scoopers can scoop up to 1,412 gallons of water in approximately 12 seconds, and with 90% of wildfires within 20 miles of a major water source (see graph below), Super Scoopers provide an extremely effective tool to economically and expeditiously deliver water to a fire without having to return to an airport to refill the water tanks. With a water source within a five-mile radius, the Super Scooper can drop on its target up to every seven minutes for a total of approximately 35 drops, or 50,000 gallons of water, before needing to refuel. As a result of our operations of these Super Scooper assets, in conjunction with our Air Attack and UAS fleet, we believe that we are one of the most full-spectrum aerial fire service providers in North America.
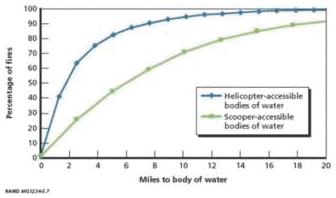
Source: 2012 Air Attack Against Wildfire Study by the Rand Homeland Security and Defense Center.
The Super Scooper aircraft has an impeccable safety record, direct support from the OEM, short take-off and landing capabilities (“STOL”) and a multi-crew flight deck. The Super Scooper has a cruising speed of 207 miles per hour. Additionally, the Super Scooper is a highly efficient aircraft when fighting wildland fires and has the ability to drop a higher volume of liquid than retardant-dropping fixed-wing aircraft over the same amount of time due to its ability to gather water from nearby bodies of water.
Our Super Scoopers have an immaculate safety record, as we have never been assessed with any safety violations and/or citations, nor have any of our aircraft ever been involved in any crashes or serious injuries. We have also adopted a safety management system (“SMS”) designed to reduce the likelihood of safety-related issues from arising in the course of our overall operations. The SMS program has been audited by both the FAA and the USFS.
Furthermore, the Super Scooper has the ability to operate from smaller airports with runways as short as 2,500 feet in length while larger jet-powered aerial firefighting aircraft often need a runway of at least 4,000 feet in length. The Super Scooper is capable of scooping water in 12 seconds from bodies of water of 4,900 feet or more in length and can empty the water load in 3 seconds in one drop or split the drop into two. The Super Scooper’s water tank capacity is shown in the table below:
| Volume Liters | Imp Gal | U.S. Gal | Weight Kg | Lbs | ||||||||||||||||
Each tank | 2,673 | 588 | 706 | 2,722 | 6,000 | |||||||||||||||
Total both tanks | 5,346 | 1,176 | 1,412 | 5,443 | 12,000 | |||||||||||||||
94
A summary graphic of the Super Scooper and its efficiency in collecting water is provided below.
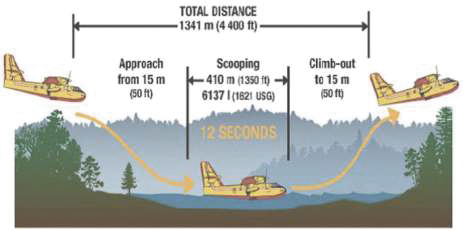
Source: United States Department of Agriculture Amphibious Water Scooper Aircraft Operations Plan 2016.
Air Attack Fleet
Air Attack aircraft provide high level situational awareness of fire growth, ground firefighting elements, other aircraft within the fire traffic area, and changing weather conditions to Incident Commanders. Each aircraft is outfitted with a broad suite of communication technologies. The Daher Kodiak and Pilatus PC-12 aircraft, the newest additions to our Air Attack fleet, are particularly renowned for their rugged build and versatility in landing on challenging terrain which is an asset given the inconsistent and harsh flying conditions that challenge aerial firefighting. Our Air Attack fleet is suitable for STOL, allowing for deployment in a greater range of scenarios. A high level of reliability allows the aircraft to be serviced and available for contract for more days, with fewer unscheduled maintenance events in-field. Above active wildfires, the aircraft can maintain the fuel efficiency required to loiter for four to seven hours with slow and stable flight characteristics, offering the ATGS greater visibility.
Unmanned Aircraft Systems
We own and operate two Aurora eVTOL Skiron UAS as part of our unmanned aerial surveillance services. The Aurora eVTOL Skiron provide real time data to firefighters using infrared and optical imagery and have extended flight endurance of two to four hours. Our dual-sensor imaging systems are capable of single-pass fire perimeter mapping. The data can be displayed on a tablet, allowing decision-makers to leverage near real-time data from the aircraft in flight. Belly-mounted compact dual-sensor imaging systems generate large scale orthographic images and fire perimeter mapping, which can be overlayed on a Google Earth image for greater ease of use. Our Aurora eVTOL Skiron use a hybrid vertical take-off and landing to facilitate agile flight operations, have an extended flight endurance of two to four hours and provide persistent intelligence, surveillance and reconnaissance to Incident Commanders while minimizing downtime. The two Aurora eVTOL Skiron aircraft are fully electric and emit zero emissions during operations, supporting our sustainable and environmentally friendly firefighting methods. Our Aurora eVTOL Skiron, while still a burgeoning capability, offer our clients consistent surveillance when traditional manned solutions are limited.
95
Key Market Drivers and Opportunities
There are several key market drivers and opportunities for our business, including:
Longer and more severe fire seasons drive demand for fire suppression and aerial surveillance services
NIFC Suppression Costs Data supports that the acreage burned in the U.S. has increased over time. While there is variability in the acreage burned in any given year, the annual average of 7.0 million acres burned since 2000 has more than doubled the annual average acreage burned in the 1990s of 3.3 million. The year 2020 was one of the most intense fire years recorded in U.S. history with over 10.1 million acres burned.
While the North American wildfire off-season is typically between November and April, fires are starting earlier in the spring and lasting deeper into the fall according to the EPA Climate Change Indicators Article. The U.S. fire season is also lengthening on a consistent basis – according to the Climate Central Article, the U.S. fire season is on average 105 days longer than it was in 1970. Climate Central also reported that the average number of large fires (larger than 1,000 acres) burning each year had tripled between the period of the 1970s to the 2010s, and the acres burned by such fires showed a six-fold increase in the 2010s compared to the 1970s. Climate Central attributes the lengthening wildfire season to factors including warmer springs, longer summer dry seasons and drier soils and vegetation, with climate change threatening to increase the extent and severity of these fires. The United States national fire preparedness level has increased over time. The five preparedness levels range from the lowest (1) to the highest (5) and are dictated by fuel and weather conditions, fire activity, and fire suppression resource availability throughout the country. Level 5 represents that several geographic areas are experiencing large, complex wildland fire incidents, which have the potential to exhaust national wildland firefighting resources, while Level 1 represents there is very minimal fire activity. According to data provided by the NIFC, the average U.S. fire preparedness level during the main wildfire season (June through September) has increased over time by almost half of a level: during the past five years (2018 – 2022) the average U.S. fire preparedness level was 3.24, while the average U.S. fire preparedness level since 1990 was 2.80.5
Increasing federal and state funding for wildfire control
National funding for wildfire management is appropriated by Congress and each state pays for wildland firefighting slightly differently. While fire suppression activities on wildlands in the U.S. are financed through federal funds, budget-making processes may restrict the amount allocated. According to the NIFC Suppression Costs Data, federal government fire suppression spending in 2021 increased by 93.0% from 2020 to $4.4 billion. The funding is allocated to the DOI and the USFS. Our company then enters into short, medium and long-term contracts with federal agencies during the firefighting season. Additionally, on the state level, we are generally seeing significant increases in several state governments and private entities who are preparing themselves for the new fire reality. For example, in December 2022, the federal government announced the allocation of an additional $228.0 million in fiscal year 2023 to wildfire mitigation efforts, and Washington State invested $328.0 million over the five following years to fight wildfires.6 While this level of commitment is unique, it is reflective of the increased awareness across many levels of government and private entities that wildfire risk has entered a new era of severity.
| 5 | NIFC, Fire Information, last accessed Oct. 9, 2023 (https://www.nifc.gov/fire-information#current-level). |
| 6 | U.S. Department of the Interior, Deputy Secretary Beaudreau Announces $228 Million for Wildfire Mitigation and Resilience from Bipartisan Infrastructure Law, Dec. 14, 2022 (https://www.doi.gov/pressreleases/deputy-secretary-beaudreau-announces-228-million-wildfire-mitigation-and-resilience#:~:text= The%20%24228%20million%20announced%20today,of%20%24408%20million%20in%20funding.); L. Pulkkinen, Inside Washington’s $328M push to prevent disastrous wildfires, CrossCut, Apr. 16, 2021 (https://crosscut.com/politics/2021/04/inside-washingtons-328m-push-prevent-disastrous-wildfires); Washington State Legislature, HB 1168—2021-22, last accessed Oct. 9, 2023 (https://app.leg.wa.gov/billsummary?BillNumber=1168&Year=2021). |
96
Given our long-standing customer relationships with governmental bodies, we have an opportunity to fulfill this increased demand for firefighting services driven by longer and more severe fire seasons. We view the increased demand as a means to further government agency ties and to capitalize on new aircraft investments.
Increased demand and limited supply of purpose-built suppression aircraft
According to the reports published by the National Interagency Coordination Center, demand for Type 3 multi-engine airtankers, which includes the Super Scooper aircraft, increased by over 56% for the two-year period of 2021 and 2022 compared to the prior two-year period of 2019 and 2020.7 The Wildland Fire Reports showed that the increase in demand led to a higher percentage of unfulfilled requests, and in 2022, 34.9% of Type 3 multi-engine airtankers requests were unfulfilled compared to 8.9% in 2020. Super Scoopers are multi-engine airtankers built specifically for aerial firefighting. They are highly effective at fighting fires and have historically been owned and operated by foreign governments throughout Europe (there are approximately 40 amphibious scooping aircraft owned by France, Greece, Italy and Spain) and as a result, used amphibious scooping aircraft are difficult to locate and obtain in the United States. We are an original customer for LAS’ launch of their Super Scooper CL-415EAF (Enhanced Aerial Firefighter) Program. LAS has only made a limited number of new Super Scoopers available for sale between 2020 and 2025, and pursuant to the LAS Purchase Agreement, which has been amended numerous times to add additional planes and upgrades, we agreed to purchase six of the limited number of Super Scoopers. On February 17, 2023, we received our sixth Super Scooper, which will allow greater deployment of the Bridger aircraft fleet across the U.S. As we are a long-standing customer of LAS, and as LAS develops their next generation of aerial firefighting solutions, our continuous feedback informs advancements in firefighting technology.
Given the limited supply of purpose-built multi-engine airtankers, upkeep and maintenance of existing aircraft is vital to minimize lapses in firefighting services occurring during wildfire season and to reduce the impact of any disruptions that occur. The Super Scooper is the only aerial fire suppression aircraft with factory OEM support which aids in reducing downtime.
Our Competitive Strengths
Full spectrum of aerial firefighting services
We provide full-spectrum aerial firefighting services, offering both fire suppression and aerial surveillance services in the U.S. and internationally. We emphasize continued investment in new aerial surveillance and aerial fire suppression aircraft, as well as innovation in the realm of unmanned platforms. Our aerial surveillance fleet has evolved since our inception from a single aircraft and pilot to the fleet operated today. The diversity of our service offerings affords customers the opportunity to select the appropriate services for their specific needs.
Purpose-built aircraft that can drop higher volumes of water
Our six CL-415EAF Super Scooper aircraft are the latest model in the LAS production line and feature enhanced industry technology. Viking, a subsidiary of LAS, purchased the type certificate and is the OEM for the design of all the CL-215 and CL-415 models from Bombardier Aerospace. LAS then made significant
| 7 | The NICC 2022 Annual Report; National Interagency Coordination Center, Wildland Fire Summary and Statistics Annual Report 2021, last accessed Oct. 9, 2023 (https://www.nifc.gov/sites/default/files/NICC/2-Predictive%20Services/Intelligence/Annual%20Reports/2021/annual_report_0.pdf); National Interagency Coordination Center, Wildland Fire Summary and Statistics Annual Report 2020, last accessed Oct. 9, 2023 (https://www.nifc.gov/sites/default/files/NICC/2-Predictive%20Services/Intelligence/Annual%20Reports/2020/annual_report_0.pdf); National Interagency Coordination Center, Wildland Fire Summary and Statistics Annual Report 2019, last accessed Oct. 9, 2023 (https://www.nifc.gov/sites/default/files/NICC/2-Predictive%20Services/Intelligence/Annual%20Reports/2019/annual_report_0.pdf) (the “Wildland Fire Reports”). |
97
improvements and introduced the CL-415EAF Super Scooper, which includes the following improvements over the CL-415:
| • | Higher cruising speed; |
| • | Improved air safety; |
| • | Latest-generation technological reliability; |
| • | New avionics and instrumentation; |
| • | More accurate water discharge technology; |
| • | Suitability for mountainous terrain; |
| • | STOL on asphalt, gravel and water; |
| • | Lower speed during water-bombing (low and slow flight); |
| • | Improved operational efficiency; and |
| • | Structural integrity. |
The CL-415EAF Super Scooper leverages modern turbine engines to deliver superior high-altitude performance. The CL-415EAF Super Scooper is able to reload in under a minute, compared to a reload time of approximately 30 minutes to one hour, depending on base capabilities, for other air tankers enabling the CL-415EAF Super Scooper to make more drops in the same amount of time. The CL-415EAF Super Scooper can drop approximately 50,000 gallons before requiring refueling, while the largest tanker in the market can only drop 30 thousand gallons of retardant before needing to refuel and reload retardant. The CL-415EAF Super Scooper aircraft allow for rapid delivery of water strikes to extinguish wildfires, particularly when deployed in tandem or larger groups to allow for continuous water-delivery as aircraft return to the water source.
Highly-skilled crew of pilots and maintenance personnel
As of September 30, 2023, we have 18 captains on staff as part of the Super Scooper flight crew. Each captain has thousands of hours of flight time in the Super Scooper conducting firefighting operations. All flight crew have a minimum of four years of aerial firefighting experience. Recurrent training for all flight crew is required in a Level D full motion flight simulator.
Each of our pilots attends annual and recurrent training specific to the aircraft they operate and to meet our standards of safety and standard operating procedures. Each pilot that flies an aircraft on contract for a government agency receives a certification card on an annual basis that validates they are qualified by the government to safely operate the aircraft while on contract.
As of September 30, 2023, we have 13 crew chiefs on staff as part of the Super Scooper maintenance crew. Each crew chief has thousands of hours maintaining aircraft in the Viking family and are familiar with firefighting operations. Factory training is mandatory for all of the maintenance team specific to the aircraft and components they maintain. They are also required to complete company-specific training courses regarding safety, standard operating procedures and systems in which they track and sign-off on maintenance logs.
Long-standing client relationships
We have provided aerial firefighting services for six years to government agencies, including the USFS, Cal Fire and multiple other state governments. The Company was awarded the first contract by the DOI to operate a fleet of UAS on-call over active wildfires throughout the U.S. We have been praised as an industry leader, specifically by the USFS, with regards to the SMS program and have been recommended by the USFS as a model for safe aircraft operations. Currently, we maintain active contracts with multiple federal agencies and the state governments of many high wildfire risk states, and we have a 100% renewal rate on our federal and state contracts. We bid upon and were awarded a USFS multi-year contract beginning with the 2021 fire season through the beginning of the 2025 fire season for the use of our Super Scooper planes.
98
Our relationship with the USFS involves three material service agreements: Call-When-Needed Water Scooper Contract Exclusive Use Light Fixed Wing Contract, and Call-When-Needed Light Fixed Wing Contract. Under the Call-When-Needed Water Scooper Contract, we provide Super Scooper aircraft services for wildland firefighting on a national basis for a period of four years from June 3, 2021. We generate revenue under the Call-When-Needed Water Scooper Contract from task orders placed by the USFS. Under the terms of the Call-When-Needed Water Scooper Contract, the USFS reserves the right to terminate the Call-When-Needed Water Scooper Contract, or any part thereof, for its sole convenience or in the event of any default by us. Under the Exclusive Use Light Fixed Wing Contract, we provide light fixed wing aircraft firefighting services on an exclusive use basis for the Northern, Rocky Mountain, Southwestern, Intermountain and Pacific Southwest regions, as defined by the U.S. Department of Agriculture. The original term of the Exclusive Use Light Fixed Wing Contract was for 12-months from May 15, 2019; however, the contract included an option to extend the contract for four additional periods of one year each, and the USFS has exercised its annual option to extend the contract for 12-month periods on each of March 18, 2020, April, 21, 2021, April 18, 2022 and March 14, 2023. We generate revenue under the Exclusive Use Light Fixed Wing Contract by providing guaranteed availability of our services for 120 calendar days per year, with different rates charged for standby hours and flight hours. Under the terms of the Exclusive Use Light Fixed Wing Contract, the USFS reserves the right to terminate the Exclusive Use Light Fixed Wing Contract, or any part thereof, for its sole convenience or in the event of any default by us. Under the Call-When-Needed Light Fixed Wing Contract, we provide light fixed wing aircraft firefighting services, on a call-when-needed basis, for the air tactical group supervision mission on behalf of the Northern Region, as defined by the USFS. The term of the Call-When-Needed Light Fixed Wing Contract is for a period of four years. We generate revenue under the Call-When-Needed Light Fixed Wing Contract by providing our services when called upon by the USFS, if available at time of call, with different rates charged for standby hours and flight hours. Under the terms of the Call-When-Needed Light Fixed Wing Contract, the USFS reserves the right to terminate the Call-When-Needed Light Fixed Wing Contract, or any part thereof, for its sole convenience or in the event of any default by us. In September 2023, Bridger was awarded a 10-year air attack contract for up to $166 million from the USFS to provide various fixed wing missions for aerial supervision, incident awareness, fire detection and reconnaissance.
Our Growth Strategy
Acquire and deploy additional aircraft to meet increased demand
We are an original customer for LAS’s launch of its Super Scooper CL-415EAF Program. There are approximately 40 amphibious scooping aircraft owned by France, Greece, Italy and Spain and as a result, used amphibious scooping aircraft are difficult to locate and obtain. LAS has only made a limited number available for sale between 2020 and 2025, and we agreed to purchase six of this limited number.
Expanding our services
Fire Monitoring Technology: With roughly 70,000 wildfires occurring each year in the U.S. (according to the NIFC Suppression Costs Data), news feeds are saturated with reports of wildfires that have grown quickly and are out of control. Current consolidated fire data is controlled by wildfire agencies with limited to no access publicly available. We launched FireTRAC in April 2022 to provide a resource to the general public in easy to use mobile and web applications. FireTRAC notifies users of potential fire danger and provides maps and high-resolution photo overlays so users can learn where the fires are located and find safety. FireTRAC provides near real-time data directly to citizens, landowners, insurance companies, utilities, municipal and county governments and potentially federal agencies. The app provides consolidated information, imagery and data regarding critical wildfire incidents in a seamless and user-friendly interface. The app puts this critical information in one place, providing rapid updates and building a user community along the way.
Maintenance, Repair, Overhaul: We have an experienced and well-trained crew of maintenance professionals. Maintenance personnel and their maintenance support staff are current on all general aviation
99
standards and requirements and are specifically trained to service our fleet of aircraft. We ensure our maintenance team has all the necessary equipment needed to exceed FAA maintenance standards and maintain USFS and DOI contract aircraft requirements. We are a FAA Certified Part 145 Repair Station offering Airframe and Avionics repair capabilities for the Aerial Firefighting Fleet. In April 2022, our Part 145 Certified Repair Station was awarded an ISO 9110, certification which is one of the highest standards in a repair organization recognized by the FAA. This certification was completed by the British Standards Institution, recognized as an industry leader in quality management systems.
Domestic and international expansion
We are committed to increasing our market share and service offering domestically. Given our competitive strengths, we believe we are well-positioned to take advantage of the growth in domestic demand for fire safety and environmental awareness. We currently have contracts in place with the USFS, the DOI, Washington State Department of Natural Resources, Alaska Department of Natural Resources, Cal Fire, Colorado Department of Public Safety, Minnesota Department of Natural Resources, Montana Department of Natural Resources and Conservation, Nevada Department of Conservation and Natural Resources, and Oregon Department of Forestry.
We intend to penetrate certain additional domestic markets through leveraging existing relationships and building local market teams. We have established this historically by maintaining relationships in the field with customers, gathering near real-time feedback to improve operations, as well as holding regular feedback sessions to incorporate points of improvement and planning for subsequent years.
We are exploring the possibility of operating internationally during the North American wildfire off-season, which generally occurs between November and April. We seek to become a global entity that provides aerial firefighting services worldwide. Our goal is to bring the Super Scooper to Europe, Asia and/or South America as our first international expansions in the future and to demonstrate the platform’s effectiveness. Currently, Super Scoopers are either not utilized on wildland fires in these areas or are not operated in a contractor-owned, contractor-operated business model. We plan to fill an underserved need to provide an alternative solution to aging and obsolete government-owned, government-operated fleets.
Pursuing Opportunistic M&A
We intend to continue to evaluate M&A opportunities to expand our fleet, add new geographies or add additional services. Consistent with this strategy, we regularly evaluate potential acquisition opportunities, including ones that would be significant to us. Currently, we are pursuing the Bighorn Acquisition and the Spanish Super Scooper Acquisition and have recently completed the Ignis Acquisition. We cannot predict the timing of any other contemplated transactions.
Seasonality
Our operating results are impacted by seasonality. Climate conditions and other factors that may influence our revenues may vary each quarter and year. Many of these factors are outside of our control, including but not limited to:
| • | forest fires tend to have a higher occurrence during the summer months and during times of drought, but are ultimately unpredictable; |
| • | climate change and changes in global temperatures occur over time; |
| • | unexpected weather patterns, natural disasters or other events that increase or decrease the rate or intensity of wildfires or impair our ability to perform firefighting services; and |
| • | changes in governmental regulations or in the status of our regulatory approvals or applications. |
100
Historically, the demand for our services has been higher in the second and third quarters of each fiscal year due to the timing and duration of the North American fire season. Consequently, revenues, expenses, and operating cash flows from our services are generated mostly in the second and third quarters of our fiscal year. However, the seasonal fluctuation in the need to fight wildfires based upon location and the varying intensity of the fire season may lead our operating results to fluctuate significantly from quarter to quarter and year to year.
Our Customers
Our high-performing aircraft, including the Super Scooper, and full-service support platform have allowed us to enter into contracts with U.S. federal, state and local governmental entities and focus on growth while building additional services to map and analyze fire boundaries. Currently, we are engaged in short, medium and long-term contracts with multiple federal agencies such as the USFS and DOI and the state governments of many of the states most endangered by wildfires. Automatically renewing contracts with governmental entities provide stable revenue streams, allowing us to innovate in the aerial firefighting industry and diversify offerings to customers. We were awarded the first contract by the DOI to operate a fleet of UAS on-call over active wildfires throughout the U.S. We bid upon and were awarded a contract with the USFS for use of our Super Scooper aircraft, beginning in 2021 into 2025.
While a majority of our existing contracts are for a one-year base term, we enter into short, medium and long-term contracts with customers, primarily with the aforementioned government agencies during the firefighting season, to deploy aerial fire management assets. Contracts are based on either a call-when needed (“CWN”) or exclusive use (“EU”) basis. Rates established are generally more competitive based on the security of the revenue from the contract (i.e., an EU versus only on an as-needed basis in CWN). We have a 100% renewal rate on our federal and state contracts.
Facilities
Our headquarters are located in Belgrade, Montana, and our aircraft fleet resides at the Bozeman Yellowstone International Airport. We lease five existing lots at the airport on 20-year and 10-year ground leases. We own two hangars and plan to construct two additional hangars adjacent to our existing hangars.
Our Competitors
Our primary competition is a private aerial firefighting operator that currently manages 4 CL-415s, 3 Type II Dash 8-400AT and 7 Avro RJ85s, which are designed to drop retardant. Additionally, from time-to-time we may compete with aerial firefighting companies that drop water from helicopters. However, our management does not view helicopters as a direct threat to our operations because while many helicopters are only able to pursue two-hour missions due to fuel capacity, our Super Scooper aircraft have four-hour fuel capacity.
Our Super Scooper program is not designed to replace the use of aircraft that drop fire retardant on wildfires. Fire retardant is a substance frequently deployed by large air tankers to slow down or stop the spread of fire and is frequently used to create a perimeter or border around a fire. While it is possible for a fire to burn through a fire line created by fire retardant, fire retardant remains a valuable tool in the fight and management of wildfires, and when combined with the deployment of Super Scoopers dropping water, can be effective in managing, controlling and slowing the spread of wildfires.
We believe our ability to compete successfully as an aerial firefighting service will depend on a number of factors, which may change in the future due to increased competition, including the price of our offerings, consumer confidence in the safety and efficacy of our offerings and consumer satisfaction for the solutions we offer.
101
Our Environmental Impact
According to the EPA Climate Change Indicators Article, multiple studies have found that “climate change has already led to an increase in wildfire season length, wildfire frequency and burned area”, “climate change threatens to increase the frequency, extent and severity of fires through increased temperatures and drought” and wildfires release a significant amount of carbon emissions each year.
Amid raging wildfires, changing climate and year-round fire season, we use sustainable and environmentally friendly firefighting methods. By sourcing water near the fire for our fire suppression services, we minimize harm to the local water system by keeping water in the local ecology and reducing flight time between scoops and drops. Our mission is to save lives, property, and habitats through our world-class team, specialized aircraft, and innovative use of technology and data.
Human Capital
Our employees are critical to our success. As of September 30, 2023, we had 173 employees. We have high selection standards, recruiting individuals with specific technical skills and demonstrated ability to work independently in a wide variety of work environments. Prior to joining our company, many of our employees had prior experience working for a wide variety of reputed research, commercial and military aerospace and non-aerospace organizations. As a company founded by veterans, we seek to employ qualified veterans and draw upon the experiences of their shared military background including their strategic mindset, management skillset and high level of discipline. As of September 30, 2023, approximately 1 out of 5 of our employees is a veteran of the U.S. military.
To date, we have not experienced any work stoppages, and we consider our relationship with our employees to be good. We routinely solicit feedback from our entire employee base and empower individuals by encouraging them to formulate solutions and process improvements no matter the level of role. Accordingly, our voluntary turnover is very low, employee engagement is high, and we have not experienced any interruptions of operations due to labor disagreements. Our employees are not subject to collective bargaining agreements or represented by labor union.
Health and Safety
We are committed to the safety of our employees. We maintain environmental, health and safety policies that seek to promote the operation of our business in a manner that is protective of the health and safety of the public and its employees, particularly in response to the global COVID-19 pandemic. Depending on the current circumstances of the evolving COVID-19 pandemic, we have implemented actions to maintain the health of our employees including social distancing measures, the use of masks, restricting visitors and unnecessary travel and working from home, where appropriate. Our operations offer several health and welfare programs to employees to promote fitness and wellness and to encourage preventative healthcare. In addition, our employees are offered a confidential employee assistance program that provides professional counseling to employees and their family members. We have a holistic philosophy for our benefits offerings, supporting physical health, mental health, financial health, community support and a wide variety of insurance plans to hedge against uncertain losses (e.g., accident, short term disability, paid leaves, and life insurance).
Employee Trainings
To address the inherently dangerous nature of the job, we adhere to achieving operational excellence and providing our employees with the means to further their development. All of our pilots are given extensive training during the winter months, regardless of tenure or previous experience. The trainings include classroom/online courses, simulators, and in-plane time. We strive to have high industry standards and employ several dedicated pilot and airframe-specific trainers. Routinely, we fund enhanced workforce training in specific technical fields related to those employees’ desires. In one instance, we have had an employee who was hired as a facility cleaner. With further training and investment, the employee became a ground vehicle support manager and is now an aircraft mechanic. We also hire entry level mechanics and train them to obtain their airframe and powerplant certification, which allows them to perform maintenance on any aircraft unsupervised.
102
In addition to technical training, we invest heavily in leadership and management training as well as some of the most advanced safety training available in our industry. The State of Montana Job Grant program has been a tremendous help to us through our early years by providing state funded training to employees attending schooling to better their position as employees within the State of Montana. Before hiring externally as needs are identified, a careful analysis is done of our current staff to determine if the aptitude and interest is already in our employee base. By prioritizing training and promoting current employees, we enhance employee engagement and cut costs simultaneously.
Employee Retention and Opportunity
We believe that the attraction and retention of top talent from a variety of backgrounds is important and we employ policies and procedures to recruit diverse talent as well as policies to ensure pay equality. We have an Equal Employment Opportunity Policy whereby we commit to providing equal employment opportunity, promotion, services, or activities which operates for all qualified employees and applicants without regard to race, color, sex, sexual orientation, gender identity, gender expression, parental status, citizenship status, religion, national origin, disability, veteran status, age, marital status, pregnancy, genetic information or other legally protected status. We drive a culture that understands and respects differences. We rely heavily on recruiting internationally to work on our purpose-built aerial firefighting aircraft and identify the cultural benefits that these individuals bring to our company.
Governmental Regulation
Federal Aviation Administration
The regulations, policies and guidance issued by the FAA apply to the use and operation of our aircraft. Operators of aircraft are required to have proper licenses, permits and authorizations from the FAA and comply with the FAA’s insurance requirements for third-party liability and government property. While our aircraft are currently registered with the FAA, in the event of a change in ownership, the FAA license will be updated with current information. In that instance, once any such new vehicle registration applications are filed, the applications will serve as registrations until the FAA issues the new vehicle registrations, which will allow operations to continue during that period.
Failure to comply with the FAA’s aviation or space transportation regulations may result in civil penalties or private lawsuits, or the suspension or revocation of licenses or permits, which would prevent operating our aircraft.
In addition to the FAA, our industry is regulated by multiple federal agencies who, in some cases, act as both customer and regulator. We are proud to have a stellar record of performance both in flight and on the ground with respect to all of our regulatory bodies.
Legal Proceedings
We are, from time to time, subject to various claims, lawsuits and other legal and administrative proceedings arising in the ordinary course of business. Some of these claims, lawsuits and other proceedings may involve highly complex issues that are subject to substantial uncertainties, and could result in damages, fines, penalties, non-monetary sanctions or relief. However, we do not consider any such claims, lawsuits or proceedings that are currently pending, individually or in the aggregate, to be material to our business or likely to result in a material adverse effect on our future operating results, financial condition or cash flows.
103
MANAGEMENT
Executive Officers and Board of Directors
The following sets forth as of September 30, 2023 certain information concerning our executive officers and directors.
Name | Age | Title | ||
| Executive Officers | ||||
| Timothy Sheehy | 37 | Chief Executive Officer, Founder and Director | ||
| McAndrew Rudisill | 44 | Chief Investment Officer and Director | ||
| Eric Gerratt | 52 | Chief Financial Officer | ||
| James Muchmore | 49 | Chief Legal Officer and Executive Vice President | ||
| Darren Wilkins | 50 | President of Operations | ||
| Directors | ||||
| Jeffrey Kelter | 69 | Chairman of the Board | ||
| Anne Hayes | 41 | Director | ||
| Dean Heller | 63 | Director | ||
| Todd Hirsch | 49 | Director | ||
| Wyman Howard | 54 | Director | ||
| Robert Savage | 55 | Director | ||
| Matthew Sheehy | 43 | Director | ||
Executive Officers
Timothy Sheehy serves as our Chief Executive Officer and a Class I Director. Mr. Sheehy has served as the Chief Executive Officer and a Director of Bridger and Legacy Bridger since 2014. From 2008 until 2014, Mr. Sheehy served as a Navy SEAL officer and team leader. In 2014, Mr. Sheehy left the Navy and co-founded the Company and its former affiliate, Ascent Vision Technologies LLC (“Ascent”). Mr. Sheehy is a recipient of the Bronze Star with Valor and Purple Heart and is an active pilot with Bridger’s Air Attack and Super Scooper fleets. Mr. Sheehy earned his Bachelor of Science in History from the United States Naval Academy. Mr. Sheehy is well qualified to serve on the Board due to his significant leadership experience, in both corporate and military settings, as well as his extensive aviation operations background.
McAndrew Rudisill serves as our Chief Investment Officer and a Class I Director. Mr. Rudisill has served as the Chief Investment Officer and Director of Bridger and Legacy Bridger since 2017. From 2017 to 2021, Mr. Rudisill was the Chief Investment Officer of Capital Vacations LLC, a resort management company. From 2011 to 2016, Mr. Rudisill was the Chief Executive Officer and President of Emerald Oil, Inc. (“Emerald Oil”), a US oil and gas producer. In March 2016, Emerald Oil filed a petition for voluntary reorganization under Chapter 11 of the U.S. Bankruptcy Code. In 2007, Mr. Rudisill founded Pelagic Capital Advisors LLC, a private investment fund focused on public and private equity investments, where he served as Managing Partner and Chief Investment Officer from 2007 until 2011. Mr. Rudisill earned a Bachelor of Arts in Economics from Middlebury College. Mr. Rudisill is well qualified to serve on the Board due to his strategic investment experience and management experience in both the public and private sectors.
Eric Gerratt serves as our Chief Financial Officer. Mr. Gerratt has served as the Chief Financial Officer of Bridger and Legacy Bridger since October 2022. Prior to joining Bridger, Mr. Gerratt served as the Executive Vice President, Chief Financial Officer and Treasurer of US Ecology, Inc., a leader in environmental services from November 2012 to September 2022, and during his time at US Ecology, Inc., Mr. Gerratt helped grow its revenue to nearly $1 billion. Prior to joining US Ecology, Inc., Mr. Gerratt served as Vice President of Accounting for SuperValu, Inc. and held various director level accounting and finance positions at Albertsons, Inc. Mr. Gerratt has also spent six (6) years with PricewaterhouseCoopers LLP. Mr. Gerratt is a Certified Public Accountant and received his Bachelor of Science in Accounting from the University of Idaho.
104
James Muchmore serves as our Chief Legal Officer and Executive Vice President. Mr. Muchmore has served as the Chief Legal Officer and Executive Vice President of Bridger and Legacy Bridger since 2017. From 2017 until 2021, Mr. Muchmore served as Chief Securities Counsel to Capital Vacations, LLC. From 2014 until 2016, Mr. Muchmore served as General Counsel to Emerald Oil, Inc., a U.S. oil and gas producer. In March 2016, Emerald Oil filed a petition for voluntary reorganization under Chapter 11 of the U.S. Bankruptcy Code. From 2000 until 2014, Mr. Muchmore was in private legal practice, focusing on securities transactions, mergers and acquisitions, and the execution of public and private offerings in multiple industries. Mr. Muchmore earned a Bachelor of Arts in Government and Law and English from Lafayette College and a Juris Doctor from Syracuse University College of Law.
Darren Wilkins serves as our President of Operations. Mr. Wilkins has served as President of Operations of Bridger and Legacy Bridger since August 2019. Mr. Wilkins originally joined the Company in May 2018 as the Director of Airframe Programs. From March 2013 until his retirement in November 2016, Mr. Wilkins served as the Commanding Officer of an EA-18G squadron in Naval Aviation and Air Boss of a deployed aircraft carrier. From January 2017 until April 2018, Mr. Wilkins was the Director of Federal Services for Century Companies, Inc., a construction services company, where he managed highly sensitive construction projects and contracts with the U.S. Department of Defense. Mr. Wilkins earned his Bachelor of Science in Oceanography from the United States Naval Academy and his Master of Arts in National Security and Strategic Studies from the United States Naval War College.
Non-Employee Directors
Jeffrey Kelter serves as our Non-Executive Chairman and a Class III Director. Mr. Kelter served as a Director of JCIC from 2021 until the Closing. Mr. Kelter is a Co-Founder and a Partner of KSH Capital since 2015. KSH Capital provides real estate entrepreneurs with capital and expertise to seed or grow their platform. KSH Capital is focused on the deployment of the principals’ capital in domestic and international strategies that offer compelling long-term returns. Prior to founding KSH Capital, Mr. Kelter was a Founding Partner and Chief Executive Officer of KTR Capital Partners (“KTR”) from 2005 to 2015, a leading private equity real estate investment and operating company focused on the industrial property sector in North America. KTR and its commingled investment funds were sold in May 2015 to a joint venture of Prologis Inc. and Norges Bank Investment Management. Since its inception in 2004, KTR had raised three funds which totaled over $7.0 billion of investment capacity. Prior to founding KTR, Mr. Kelter was President, Chief Executive Officer and Trustee of Keystone Property Trust, an industrial real estate investment trust. Mr. Kelter founded the predecessor to Keystone in 1982, and took the company public in 1997, where he and the management team directed its operations until its sale in 2004 to Prologis. Prior to forming Keystone, he served as president and CEO of Penn Square Properties, Inc. in Philadelphia, Pennsylvania, a real estate company which he founded in 1982. Mr. Kelter currently serves on the Board of Directors of Invitation Homes (NYSE: INVH). From January 2014 to November 2017, Mr. Kelter served on the Board of Starwood Waypoint Homes, its predecessor. Mr. Kelter currently serves as a trustee of the Cold Spring Harbor Laboratory. Mr. Kelter previously served as a trustee for Trinity College from 2010 to April 2020 and Westminister School from September 2011 to April 2020. Mr. Kelter formerly served on the Board of Gramercy Property Trust (NYSE: GPT) from 2015 to 2018. Mr. Kelter received a B.A. in Urban Studies from Trinity College. Mr. Kelter is well qualified to serve as the Non-Executive Chairman of the Board due to his extensive experience founding and growing successful companies, as well as his significant executive leadership background.
Anne Hayes serves as a Class II Director. Ms. Hayes has served as a Director of Bridger since September 2023. Ms. Hayes has served as a Director at Quadrant Capital Advisors Inc. since 2008, where she has worked in private equity investing, including minority and majority stakes across a wide range of sectors in early and growth-stage companies in the U.S. and global markets. From 2006 to 2007, she worked in venture capital and real estate investing with GDBA Investments. Ms. Hayes has over five years of accounting experience in roles of advisory and outsourced Chief Financial Officer with PricewaterhouseCoopers LLP and Councilor, Buchanan & Mitchell, P.C. In these capacities she conducted forensic investigations and business valuations, implemented Sarbanes Oxley controls, and
105
advised management and boards of directors. Ms. Hayes received her Bachelor of Science in Finance with honors from Villanova University and Master of Science in Finance from the University of Denver Daniels College of Business. Ms. Hayes is well qualified to serve on the Board due to her strategic investment experience as well as her significant knowledge of corporate finance and controls.
Dean Heller serves as a Class II Director. From May 2011 until his retirement in January 2019, Mr. Heller served as a Senator from Nevada in the United States Senate. During his time in the Senate, Mr. Heller served on the Committees on Finance, Banking, Veterans’ Affairs and Commerce. Prior to his service in the Senate, Mr. Heller was the United States Representative for Nevada’s Second Congressional District. Mr. Heller has also previously served as Nevada’s Secretary of State and in the Nevada State Assembly representing Carson City. Prior to his political career, Mr. Heller worked as a broker on the Pacific Stock Exchange as an institutional equities trader and also served as a banking Municipal Finance Representative. Mr. Heller received a Bachelor of Science in Business Administration from the University of Southern California. Mr. Heller received the Distinguished USC Alumni Award from the University of Southern California Marshall School of Business in 2012. From January 2019 through September 2021, Mr. Heller served as a director of Toyota Financial Savings Bank, a Nevada corporation that provides banking products and services to Toyota dealers. Mr. Heller is well qualified to serve on the Board due to his significant experience and in-depth knowledge in the areas of public policy and governmental matters and demonstrated leadership experience serving in the United States Senate and House of Representatives, as well as his background in business and finance.
Todd Hirsch serves as a Class III Director. Mr. Hirsch has served as a Director of Bridger and Legacy Bridger since December 2018. Since July 2013, Mr. Hirsch has been employed by Blackstone (NYSE: BX), one of the world’s leading investment firms. Mr. Hirsch is currently a Senior Managing Director in the Tactical Opportunities Fund at Blackstone. Prior to Blackstone, Mr. Hirsch worked at Deutsche Bank (NYSE: DB), an investment bank, where he sourced and structured transactions for a wide range of corporate and institutional clients across multiple products. Mr. Hirsch graduated magna cum laude from Duke University in 1996. Mr. Hirsch is well qualified to serve on the Board due to his significant experience structuring corporate and finance transactions in a variety of commercial settings, as well as background in management.
Wyman Howard serves as a Class I Director. Mr. Howard retired from the U.S. Navy in September 2022 as Rear Admiral (Upper Half) with over thirty-two (32) years in the SEAL Teams and Joint Special Operations. Mr. Howard has had multiple tours in command of Special Operations Joint Task Forces and was among the first to deploy into Afghanistan following the attacks of September 11, 2001. The combat contributions of the teams Mr. Howard commanded, and with whom he served, were recognized with five (5) Presidential Unit Citations, Navy Unit Commendation medal and four (4) Joint Meritorious Unit Awards. Mr. Howard graduated from the United States Naval Academy and holds a Master of Business Administration from the TRIUM consortium of the London School of Economics, HEC Paris School of Management, and New York University’s Stern School of Business. Mr. Howard holds a Master of Science in National Security and Resource Strategy with a focus on commercial, civil and military space sectors from the Eisenhower School and a Professional Certificate in Artificial Intelligence and Business Strategy from the Massachusetts Institute of Technology’s Computer Science and Artificial Intelligence Laboratory. Mr. Howard’s joint, interagency and intelligence experience include service as the second Director of Operations for the National Geospatial-Intelligence Agency in 2016 and as the Commander, Naval Special Warfare Command from 2020 to 2022, which are equivalent leadership roles of a Chief Operating Officer and Chief Executive Officer, respectively. Mr. Howard is acknowledged for his leadership in designing new irregular deterrence capabilities and options that increase Unites States leverage to deter the nation’s adversaries. He is well qualified to serve on the Board due to his distinctive leadership, at the strategic, operational and tactical levels, where he was at the helm in command for outcomes that advanced the security of the United States and its allies. He has a unique sensitivity to geo-strategic risk and a deep set of intelligence, interagency and foreign partner relationships set on a foundation of trust and the culture for humility and stewardship he established during his career as a Naval Officer.
Robert Savage serves as a Class II Director. Mr. Savage served as a Director of JCIC from 2021 until the Closing. Mr. Savage is a Co-Founder and President of KSH Capital since 2015. KSH Capital provides real estate
106
entrepreneurs with capital and expertise to see or grow their platform. KSH Capital is focused on the deployment of the principals’ capital in domestic and international strategies that offer compelling long-term returns. Prior to founding KSH Capital, Mr. Savage was Co-founder, President of KTR from 2005 to 2015, an investment, development and operating company focused exclusively on the industrial property sector in North America. At KTR, Mr. Savage was co-head of the firm’s Investment Committee and responsible for management of the firm’s day-to-day operations, including oversight of capital deployment, portfolio management and capital markets activities. Previously, Mr. Savage was a Partner at Hudson Bay Partners, L.P. a private equity firm focused on investing in real estate-intensive operating businesses. Mr. Savage also worked in the Investment Banking Division at Merrill Lynch & Co. where he specialized in corporate finance and M&A advisory services for REITs, private equity funds and hospitality companies. Mr. Savage is Chairman of the Board of Directors of VolunteerMatch.org, a San Francisco based 501(c)(3) that operates the largest volunteer network in the nonprofit world. Mr. Savage is a member of the Board of Trustees of Mount Sinai and the Taft School and is Director of Environmental Waste International Inc. (TSX: EWS). He was previously Chairman of the Board of Directors of New Senior Investment Group (NYSE: SNR). Mr. Savage received a A.B. in Business Economics and Urban Studies from Brown University. Mr. Savage is well qualified to serve on the Board due to his significant experience leading the strategic growth and development of companies, as well as his management background with respect to investment of capital.
Matthew Sheehy serves as a Class III Director. Mr. Sheehy is a Co-Founder of the Company and served as Chairman of the Board of Legacy Bridger from 2014 until the Closing of the Business Combination. In addition to his service at Bridger, Mr. Sheehy serves as President and Chief Executive Officer of Tallgrass Energy LLP (“Tallgrass”), where he was named CEO July 1, 2022 and has served as President since December 2019. He has been a member of the Board of Directors of Tallgrass since April 2020, and he was Chairman of the Rockies Express Pipeline LLC Board from December 2019 until July 2021. Mr. Sheehy joined Tallgrass in November 2012 and held a number of positions, including Senior Vice President and Chief Commercial Officer of Tallgrass. In addition, he served as the President of Rockies Express Pipeline LLC from December 2013 until July 2017 and as a board member of Rockies Express Pipeline LLC from November 2016 to March 2018. Prior to joining Tallgrass, he served as a Principal and General Partner at Silverhawk Capital Partners LLC (“Silverhawk”). Mr. Sheehy was an Analyst at Wachovia Securities and Wachovia Capital Partners before joining Silverhawk. He earned a Bachelor of Arts degree in Economics from Vanderbilt University in 2002. Mr. Sheehy is well qualified to serve on the Board due to his extensive investment, ownership and operational experience in aviation and financial settings, as well as his demonstrated leadership as a member of several boards of directors throughout his career.
Corporate Governance
Composition of the Board
Our Board is divided into three classes of directors that serve staggered three-year terms. At each annual meeting of stockholders, a class of directors will be elected for a three-year term to succeed the same class whose term is then expiring. As a result, only one class of directors will be elected at each annual meeting of our stockholders, with the other classes continuing for the remainder of their respective three-year terms.
Each director’s term continues until the election and qualification of his or her successor, or his or her earlier death, resignation or removal. Our Amended and Restated Charter and Amended and Restated Bylaws authorize only our Board to fill vacancies on our Board. Any increase or decrease in the number of directors will be apportioned by the Board among the classes as to make all classes as nearly equal in number as is practicable. This classification of our Board may have the effect of delaying or preventing changes in control of our company.
Pursuant to the Stockholders Agreement, the BTO Stockholders, collectively, have the right, but not the obligation, to nominate for election to the Board up to two (2) directors, for so long as the BTO Entities (as defined in the Stockholders Agreement) collectively beneficially own (directly or indirectly) at least 10% of the
107
outstanding Stock (as defined in the Stockholders Agreement); and (ii) one (1) director, for so long as the BTO Entities collectively beneficially own (directly or indirectly) less than 10% of the outstanding Stock, but at least 33% of the shares of Stock held by the BTO Entities as of the Closing. In the event that a vacancy is created at any time by the death, disqualification, resignation or removal of a director nominated by BTO Stockholders, the BTO Stockholders, collectively, will have the right to designate a replacement to fill such vacancy. Ms. Hayes and Mr. Hirsch are the current BTO Stockholders director designees.
Director Independence
As a result of our Common Stock being listed on Nasdaq, the Company is required to comply with the applicable rules of such exchange in determining whether a director is independent. Our Board has undertaken a review of the independence of each director and considered whether each director has a material relationship with us that could compromise his or her ability to exercise independent judgment in carrying out his or her responsibilities. As a result of this review, our Board determined that each of Ms. Hayes, Mr. Heller, Mr. Hirsch, Mr. Howard, Mr. Kelter and Mr. Savage qualifies as “independent” as defined under the applicable Nasdaq rules. In making these determinations, our Board reviewed and discussed information provided by the directors and by us with regard to each director’s business and personal activities and relationships as they may relate to us and our management, including the beneficial ownership of our Common Stock by each non-employee director and the transactions involving them described in the section entitled “Principal Stockholders.” Mr. Timothy Sheehy, the Company’s Chief Executive Officer and a Director, is the brother of Mr. Matthew Sheehy, one of the Company’s Directors. There are no other family relationships among any of the Company’s directors or executive officers that are required to be disclosed by Regulation S-K.
Board Leadership Structure
Our corporate governance guidelines provide that the roles of Chairman of the Board and CEO may be separated or combined. Our Board has appointed Mr. Kelter, a non-employee director, to serve as Non-Executive Chairman of the Board. As Non-Executive Chairman of the Board, Mr. Kelter will, among other roles, preside at, and chair, board meetings and meetings of our stockholders, serve as liaison for stockholders who request direct communication with the board, and perform such additional duties as our Board may otherwise request.
Role of the Board in Risk Oversight
One of the key functions of the Board is informed oversight of the Company’s risk management process. The Board does not have a standing risk management committee, but rather administers this oversight function directly through the Board as a whole, and it accomplishes this oversight through (among other things) the regular reporting to the Board by its audit committee (the “Audit Committee”) and from time to time by key advisors. The Audit Committee represents the Board by periodically reviewing our accounting, reporting and financial practices, including the integrity of our financial statements, the surveillance of administrative and financial controls and our compliance with legal and regulatory requirements. Through its periodic meetings with management, including the finance, accounting, legal, human resources, and information technology (including cybersecurity) functions, the Audit Committee reviews and discusses all significant areas of our business and summarizes for the Board all areas of risk and the appropriate mitigating factors.
Evaluations of the Board
The Board evaluates its performance and the performance of its committees and individual directors on an annual basis through an evaluation process administered by the Company’s nominating and corporate governance committee (the “Nominating and Corporate Governance Committee”). The Board discusses each evaluation to determine what, if any, actions should be taken to improve the effectiveness of the Board or any committee thereof or of the directors.
108
Meetings of the Board
Our directors were appointed in connection with the Closing of the Business Combination on January 24, 2023, and therefore the Board did not meet during the year ended December 31, 2022. The Company’s corporate governance guidelines state that all directors are expected to make every effort to attend all meetings of the Board and all meetings of the committees on which they serve. Each director is also encouraged and generally expected to attend the Company’s annual meeting of stockholders.
Board Committees
Our Board has established the Audit Committee, a compensation committee (the “Compensation Committee”), and the Nominating and Corporate Governance Committee. The composition and responsibilities of each of the committees of our Board are described below. Copies of the charters for each committee are available on the investor relations page of our website at https://www.bridgeraerospace.com. The information in or accessible through our website is not incorporated into, and is not considered part of, this prospectus. Members serve on these committees until their resignation or until otherwise determined by our Board. Our Board may establish other committees as it deems necessary or appropriate from time to time.
Our current Board standing committees and membership is as follows:
Audit | Compensation | Nominating and Corporate Governance | ||
| Anne Hayes (Chair) | Dean Heller (Chair) | Wyman Howard (Chair) | ||
| Wyman Howard | Todd Hirsch | Dean Heller | ||
| Jeffrey Kelter | Jeffrey Kelter | Todd Hirsch |
Pursuant to the Stockholders Agreement, the Founder Stockholders, to the extent they collectively beneficially own (directly or indirectly) at least 10% of the outstanding Stock have the right, but not the obligation, to nominate the Chairperson of the Compensation and Nominating and Corporate Governance Committees of the Board, subject to satisfaction of applicable SEC and stock exchange requirements. In addition, for so long as the BTO Entities have director nomination rights, the Board will use reasonable best efforts to cause any committee of the Board to include in its membership at least one director nominated by the BTO Stockholders provided that such individual satisfies all applicable SEC and stock exchange requirements.
The Company’s Chief Executive Officer and other executive officers regularly report to the non-executive directors and each standing committee to ensure effective and efficient oversight of its activities and to assist in proper risk management and the ongoing evaluation of management controls.
Audit Committee
The members of the Company’s Audit Committee consist of Ms. Hayes (since September 8, 2023), Mr. Howard (since April 25, 2023) and Mr. Kelter (since January 24, 2023), with Ms. Hayes serving as the chair of the committee. Mr. Savage served as a member of the Audit Committee from January 24, 2023 until April 25, 2023. The Board has determined that each of Ms. Hayes and Mr. Howard meets the independence requirements of the Sarbanes-Oxley Act, as amended, Rule 10A-3 under the Exchange Act and the applicable listing standards of Nasdaq. Mr. Kelter does not satisfy such heightened audit committee independence requirements because Mr. Kelter indirectly controls JCIC Sponsor and therefore is deemed to beneficially own approximately 22.0% of the outstanding shares of Common Stock, assuming the exercise of all of the Private Placement Warrants that are held by JCIC Sponsor. The Company is relying on the exemption provided in Rule 10A-3(b)(iv) of the Exchange Act and does not believe that the reliance on such exemption would materially adversely affect the ability of the Audit Committee to act independently and to satisfy the other requirements of Rule 10A-3. Each member of the Audit Committee can read and understand fundamental financial statements in accordance with Nasdaq audit committee requirements. In making this determination, the Board has examined
109
each Audit Committee member’s scope of experience and the nature of their prior and/or current employment. The Audit Committee did not meet in 2022 because it was formed in connection with the Closing of the Business Combination on January 24, 2023.
The Board has determined that each of Ms. Hayes, Mr. Howard and Mr. Kelter qualifies as financially literate under the Nasdaq rules and that Ms. Hayes qualifies as an “audit committee financial expert” within the meaning of Regulation S-K. In making this determination, the Board considered Ms. Hayes’s, Mr. Howard’s and Mr. Kelter’s formal education and previous and current experience in financial and accounting roles. Both the Company’s independent registered public accounting firm and management periodically will meet privately with the Audit Committee.
The Audit Committee’s responsibilities include, among other things:
| • | appointing, retaining, setting compensation of, and supervising the Company’s independent registered public accounting firm (the “Independent Auditor”); |
| • | reviewing the results and scope of the audit and other accounting related services and reviewing the Company’s accounting practices; |
| • | monitoring systems of internal accounting and disclosure controls; |
| • | overseeing the Company’s accounting and financial reporting processes and the audit of the Company’s financial statements; |
| • | overseeing the Company’s compliance with legal and regulatory requirements; |
| • | reviewing the qualifications and independence of the Independent Auditor; and |
| • | reviewing the performance of the Company’s internal auditing function and the Independent Auditor. |
Compensation Committee
The members of the Compensation Committee consist of Mr. Heller, Mr. Hirsch and Mr. Kelter with Mr. Heller serving as the chair of the Compensation Committee. Mr. Heller, Mr. Hirsch and Mr. Kelter are non-employee directors, as defined in Rule 16b-3 promulgated under the Exchange Act. The Board has determined that Mr. Heller, Mr. Hirsch and Mr. Kelter are “independent” as defined under the applicable Nasdaq listing standards, including the standards specific to members of a compensation committee. The Compensation Committee did not meet in 2022 because it was formed in connection with the Closing of the Business Combination on January 24, 2023.
The Compensation Committee’s responsibilities include, among other things:
| • | reviewing and approving compensation paid to the Company’s officers and directors; |
| • | administering the Company’s incentive compensation plans, including authority to make and modify awards under such plans; |
| • | preparing the compensation committee report required to be included in our proxy statement under the rules and regulations of the SEC; and |
| • | discharging the Board’s responsibilities relating to compensation of the Company’s executive officers and directors. |
The Compensation Committee may delegate its authority under its charter to one or more subcommittees as it deems appropriate from time to time as further described in its charter. The Compensation Committee may also delegate to one or more executive officers the authority to grant equity awards to certain employees, as further described in its charter and subject to the terms of our equity plans and applicable law.
110
The Compensation Committee charter also provides that the Compensation Committee shall have the sole authority to retain or obtain the advice of a compensation consultant, legal counsel or other adviser. The Compensation Committee approved the engagement of PricewaterhouseCoopers LLP (“PwC”) as the compensation consultant for the Compensation Committee. In connection with such engagement, the Compensation Committee assessed the independence of PwC pursuant to the Nasdaq rules and the Company concluded that the work to be performed by PwC for the Compensation Committee did not raise any conflict of interest. In connection with the Business Combination, the management of Legacy Bridger engaged PwC to review and provide advice regarding the planned executive and director compensation for Bridger. During the year ended December 31, 2022, Legacy Bridger paid PwC approximately $60,000 for such services and $4,000,000 for additional services, which included technical accounting, reporting, valuation, internal controls and transaction services. The decision to engage PwC for the additional services was made by Legacy Bridger’s management. Neither the Compensation Committee nor the Board has approved such other additional services of PwC.
Nominating and Corporate Governance Committee
The members of the Nominating and Corporate Governance Committee consist of Mr. Howard, Mr. Heller and Mr. Hirsch, with Mr. Howard serving as the chair of the committee. The Board has determined that each of these individuals is “independent” as defined under the applicable listing standards of Nasdaq and SEC rules and regulations. The Nominating and Corporate Governance Committee did not meet in 2022 because it was formed in connection with the Closing of the Business Combination on January 24, 2023.
The Nominating and Corporate Governance Committee’s responsibilities include, among other things:
| • | oversee the selection of persons to be nominated to serve on the Board; |
| • | reviewing the qualifications of incumbent directors to determine whether to recommend them for reelection and selecting, or recommending that the Board select, the director nominees for the next annual meeting of stockholders; |
| • | develop and recommend to the Board a set of corporate governance guidelines applicable to the Company; and |
| • | oversee the annual performance evaluation of the Board and its committees. |
In the process of identifying, screening and recommending director candidates to the full Board, the Nominating and Corporate Governance Committee takes into consideration the needs of the Board after taking into account the current composition of the Board and the qualifications of the candidates, such as their general understanding of various business disciplines and the Company’s business environment, their educational and professional background, professional skills, analytical ability, independence, diversity of experience and viewpoints, and their ability and willingness to devote adequate time to Board duties. The Board evaluates each individual in the context of the Board as a whole with the objective of retaining a group that is best equipped to help ensure that the long-term interests of the stockholders are served. The Nominating and Corporate Governance Committee has not set specific minimum qualifications for director positions. Whenever a new seat or a vacated seat (other than a vacancy created by the death, disqualification, resignation or removal of a director nominated by the BTO Stockholders) on the Board is being filled, candidates that appear to best fit the needs of the Board and the Company will be identified, interviewed and evaluated by the Nominating and Corporate Governance Committee. In the event that a vacancy is created at any time by the death, disqualification, resignation or removal of a director nominated by the BTO Stockholders, the BTO Stockholders, collectively, will have the right to designate a replacement to fill such vacancy. The Nominating and Corporate Governance Committee will consider director candidates recommended by stockholders on the same basis that it evaluates other nominees for director. Candidates selected by the Nominating and Corporate Governance Committee will then be recommended to the full Board.
111
Corporate Governance Guidelines
Our Board has adopted corporate governance guidelines, which provide the framework for our corporate governance along with our Amended and Restated Charter, our Amended and Restated Bylaws, committee charters and other key governance practices and policies. Our corporate governance guidelines cover a wide range of subjects, including the conduct of board meetings, independence and selection of directors, board membership criteria, conflicts of interest, and board committee composition.
Code of Ethics
The Company has adopted a code of ethical business conduct that applies to all of its directors, officers and employees, which is available on the Company’s website: https://www.bridgeraerospace.com. The Company’s code of business conduct is a “code of ethics,” as defined in Item 406(b) of Regulation S-K. Please note that the Company’s internet website address is provided as an inactive textual reference only. The Company will make any legally required disclosures regarding amendments to, or waivers of, provisions of its code of ethics on its internet website.
Prohibition on Hedging and Pledging of Company Securities
The Company has a policy that prohibits officers, directors, independent contractors and employees from engaging in hedging transactions, such as the purchase or sale of puts or calls, or the use of any other derivative instruments. Officers, directors, independent contractors and employees of the Company are also prohibited from holding Company securities in a margin account or pledging Company securities as collateral for a loan.
Stockholder Communications
Any stockholder or other interested party who wishes to communicate with our Board or any individual director may send written communications to our Board or such director c/o Chief Legal Officer, Bridger Aerospace Group Holdings, Inc., 90 Aviation Lane, Belgrade, Montana 59714. The communication must include the stockholder’s full legal name (and, with respect to entity stockholders, the full legal names of such entity’s owners), address, email, phone number, and an indication that the person is our stockholder. The Chief Legal Officer will review any communications received from stockholders and will forward such communications to the appropriate director or directors, or committee of our Board, based on the subject.
Stockholders Agreement
In connection with the Merger Agreement, the Company, the Founder Stockholders and the BTO Stockholders entered into the Stockholders Agreement at the Closing. Pursuant to terms of the Stockholders Agreement, effective as of the Closing Date, the Board is comprised of nine (9) directors. Further, the BTO Stockholders, collectively, have the right, but not the obligation, to nominate for election to the Board (i) up to two (2) directors, for so long as the BTO Entities (as defined in the Stockholders Agreement) collectively beneficially own (directly or indirectly) at least 10% of the outstanding Stock (as defined in the Stockholders Agreement); and (ii) one (1) director, for so long as the BTO Entities collectively beneficially own (directly or indirectly) less than 10% of the outstanding Stock, but at least 33% of the shares of Stock held by the BTO Entities as of the Closing. In the event that a vacancy is created at any time by the death, disqualification, resignation or removal of a director nominated by the BTO Stockholders, the BTO Stockholders, collectively, will have the right to designate a replacement to fill such a vacancy. In addition, for so long as the BTO Entities have such nomination rights, (i) the Board will use reasonable best efforts to cause any committee of the Board to include in its membership at least one (1) director nominated by the BTO Stockholders provided that such individual satisfies all applicable SEC and stock exchange requirements and (ii) the BTO Stockholders have a consent right over affiliate transactions entered into by the Company or any of its subsidiaries, subject to customary exceptions.
112
The Founder Stockholders, to the extent they collectively beneficially own (directly or indirectly) at least 10% of the outstanding Stock have the right, but not the obligation, to nominate the chairperson of the Compensation and Nominating and Corporate Governance Committees of the Board, subject to satisfaction of applicable SEC and stock exchange requirements.
Subject to the terms and conditions of the Stockholders Agreement and applicable securities laws, the BTO Stockholders have preemptive rights to acquire their pro rata share of any new issuance of equity securities (or any securities convertible into or exercisable or exchangeable for equity securities) by the Company, subject to customary exceptions. The BTO Stockholders are entitled to apportion the preemptive rights granted to it in such proportions as it deems appropriate, among (i) itself and (ii) any BTO Entity; provided that each such BTO Entity agrees to enter into the Stockholders Agreement, as a “Stockholder” under the Stockholders Agreement.
113
EXECUTIVE AND DIRECTOR COMPENSATION
This section describes the executive compensation of Legacy Bridger’s directors and named executive officers during Legacy Bridger’s fiscal year ended December 31, 2022. Unless the context otherwise requires, all references in this section to “Bridger,” the “Company,” “we,” “us,” “our,” and other similar terms refer to the business of Legacy Bridger and its subsidiaries prior to the Business Combination and Bridger Aerospace Group Holdings, Inc. and its subsidiaries following the Business Combination.
This section discusses the material components of the executive compensation program for Bridger’s named executive officers who are identified in the 2022 Summary Compensation Table below. This discussion may contain forward-looking statements that are based on Bridger’s current plans, considerations, expectations and determinations regarding future compensation programs. Actual compensation programs that Bridger adopts may differ materially from the existing and currently planned programs summarized or referred to in this discussion.
Overview
Bridger has opted to comply with the executive compensation disclosure rules applicable to emerging growth companies, as Bridger is an emerging growth company. The scaled down disclosure rules are those applicable to “smaller reporting companies,” as such term is defined in the rules promulgated under the Securities Act. Such rules require compensation disclosure for Bridger’s principal executive officer and its two (2) most highly compensated executive officers other than the principal executive officer whose total compensation for 2022 exceeded $100,000, who were serving as executive officers as of December 31, 2022 and who will continue with the combined company. We refer to these individuals as “named executive officers.” For 2022, Bridger’s named executive officers were:
| • | Timothy Sheehy, Chief Executive Officer; |
| • | James Muchmore, Chief Legal Officer; and |
| • | McAndrew Rudisill, Chief Investment Officer. |
We expect that Bridger’s executive compensation program will evolve to reflect its status as a newly publicly-traded company, while still supporting Bridger’s overall business and compensation objectives.
2022 Compensation of Named Executive Officers
Base Salary
Base salaries are intended to provide a level of compensation sufficient to attract and retain an effective management team, when considered in combination with the other components of the executive compensation program. In general, Bridger provides a base salary level designed to reflect each executive officer’s scope of responsibility and accountability. Please see the “Salary” column in the 2022 Summary Compensation Table for the base salary amounts received by the named executive officers in 2022 and 2021.
Bonus
Bridger provided the named executive officers with certain transaction bonuses and discretionary bonuses. Please see the “Bonus” column in the 2022 Summary Compensation Table for the bonus amounts earned by the named executive officers during calendar year 2022. Messrs. Timothy Sheehy, Muchmore and Rudisill received transaction bonus payments of $2,137,838, $1,558,681 and $1,637,838, respectively, in August 2022 representing a portion of the transaction bonuses earned in calendar year 2022. In addition, Messrs. Timothy Sheehy, Muchmore and Rudisill were paid during calendar year 2023 $2,307,162 ($1,072,500 of which represents the remaining transaction bonus amount earned in calendar year 2022 and $1,234,662 of which
114
represents the discretionary bonus amount earned in calendar year 2022), $848,819 ($503,750 of which represents the remaining transaction bonus amount earned in calendar year 2022 and $345,069 of which represents the discretionary bonus amount earned in calendar year 2022) and $1,807,162 ($1,072,500 of which represents the remaining transaction bonus amount earned in calendar year 2022 and $734,662 of which represents the discretionary bonus amount earned in calendar year 2022), respectively.
2022 Summary Compensation Table
The following table shows information regarding the compensation of the named executive officers for services performed in the years ended December 31, 2022 and December 31, 2021.
Name and Principal Position | Year | Salary($) | Bonus($)(1) | All Other Compensation ($)(2) | Total($) | |||||||||||||||
Timothy Sheehy | 2022 | $ | 450,000 | $ | 4,445,000 | $ | 1,558 | $ | 4,896,558 | |||||||||||
Chief Executive Officer | 2021 | $ | 450,000 | $ | 0 | $ | 0 | $ | 450,000 | |||||||||||
James Muchmore | 2022 | $ | 350,000 | $ | 2,407,500 | $ | 1,615 | $ | 2,759,115 | |||||||||||
Chief Legal Officer | 2021 | $ | 350,000 | $ | 0 | $ | 0 | $ | 350,000 | |||||||||||
McAndrew Rudisill | 2022 | $ | 325,000 | $ | 3,445,000 | $ | 0 | $ | 3,770,000 | |||||||||||
Chief Investment Officer | 2021 | $ | 325,000 | $ | 0 | $ | 0 | $ | 325,000 | |||||||||||
| (1) | Amounts reported in this column represent a transaction bonus of $3,210,338, $2,062,431, and $2,710,338 for Messrs. Timothy Sheehy, Muchmore and Rudisill, respectively, and a 2022 discretionary bonus of $1,234,662, $345,069, and $734,662 for Messrs. Timothy Sheehy, Muchmore and Rudisill, respectively. |
| (2) | Amounts reported for Messrs. Timothy Sheehy and Muchmore represent 401(k) employer matching contributions. |
Outstanding Equity Awards at 2022 Fiscal Year-End
None of Bridger’s named executive officers received an equity award with respect to calendar year 2022 and none of Bridger’s named executive officers held any equity awards as of the end of calendar year 2022. As noted above, in connection with the Business Combination, the Company assumed and adopted the 2023 Omnibus Incentive Plan and the outstanding RSUs granted under such plan, with each RSU representing the right to receive one (1) share of Common Stock, subject to certain vesting conditions. Messrs. Timothy Sheehy, Muchmore and Rudisill received RSUs with respect to 1,742,182, 871,147, and 1,451,874 shares of Common Stock, respectively, with 871,091, 87,115, and 725,937 shares, respectively, vested upon the consummation of the Business Combination and the remaining RSUs (x) granted to Messrs. Timothy Sheehy and Rudisill vesting (i) 20% on January 24, 2024 and (ii) 20% on January 24, 2025, and (iii) 10% on January 24, 2026, and (y) granted to Mr. Muchmore vesting (i) 10% on January 24, 2024, (ii) 10% on January 24, 2025, (iii) 10% on January 24, 2026, (iv) 25% on January 24, 2027, (v) 10% on January 24, 2028, and (vi) 25% on January 24, 2029.
Additional Narrative Disclosure
Existing Employment Agreements
Timothy Sheehy
Mr. Timothy Sheehy entered into an employment agreement dated December 6, 2018 that provides for his employment as Bridger’s Chief Executive Officer. The agreement provides that Mr. Sheehy will receive an annual base salary of $450,000, which may be increased as may be approved in writing by the Board. Mr. Sheehy is also entitled to receive a discretionary annual bonus as determined by the Board in its sole and absolute discretion. Mr. Sheehy’s employment agreement term ended on December 31, 2020 and automatically renews thereafter for one-year periods unless either party provides at least 60 days’ prior notice of non-renewal. The agreement provides that if Mr. Sheehy is terminated without cause (other than due to death or disability) or if he
115
resigns for good reason (as such terms are defined in the agreement), then Mr. Sheehy will be entitled to (i) any unpaid annual bonus in respect of any completed fiscal year that has ended prior to the date of such termination with such amount determined based on actual performance during such fiscal year as determined by the Board; (ii) a lump sum cash payment equal to (x) 24 months of base salary in effect at the time of termination plus (y) an amount equal to the total value of the annual bonus paid during the fiscal year immediately preceding the year of such termination; and (iii) a lump sum cash payment equal to (18) times the applicable percentage of the COBRA premium cost applicable to Mr. Sheehy (and any dependents). In addition, if Bridger provides notice of non-renewal without cause or Mr. Sheehy provides notice of non-renewal for good reason, then Mr. Sheehy will be entitled to the payments outlined in prongs (i) and (iii) in the immediately preceding sentence (the benefits outlined in this sentence and the immediately preceding sentence, collectively, the “Severance Benefits”). The Severance Benefits will be paid on the sixtieth (60th) day following the date of Mr. Sheehy’s termination of employment subject to his execution and non-revocation of a release of claims.
The agreement contains customary confidentiality obligations, non-competition restrictions for two (2) years from the date of termination of employment and non-solicitation restrictions for two (2) years from the date of termination of employment.
James Muchmore
Mr. Muchmore entered into an employment agreement dated August 1, 2018, as amended and restated on December 6, 2018, that provides for his employment as Bridger’s Chief Legal Officer. The agreement provides that Mr. Muchmore will receive an annual base salary of $350,000, which may be increased as may be approved in writing by the Board. Mr. Muchmore is also entitled to receive a discretionary annual bonus as determined by the Board in its sole and absolute discretion. Mr. Muchmore’s employment agreement term ended on December 31, 2020 and automatically renews thereafter for one-year periods unless either party provides at least 60 days’ prior notice of non-renewal. Mr. Muchmore’s employment agreement has the same Severance Benefits as those summarized above for Mr. Timothy Sheehy.
The agreement contains customary confidentiality obligations, non-competition restrictions for two (2) years from the date of termination of employment and non-solicitation restrictions for two (2) years from the date of termination of employment.
McAndrew Rudisill
Mr. Rudisill entered into an employment agreement dated August 1, 2018, as amended and restated on December 6, 2018, that provides for his employment as Bridger’s Chief Investment Officer. The agreement provides that Mr. Rudisill will receive an annual base salary of $325,000, which may be increased as may be approved in writing by the Board. Mr. Rudisill is also entitled to receive a discretionary annual bonus as determined by the Board in its sole and absolute discretion. Mr. Rudisill’s employment agreement term ended on December 31, 2020 and automatically renews thereafter for one-year periods unless either party provides at least 60 days’ prior notice of non-renewal. Mr. Rudisill’s employment agreement has the same Severance Benefits as those summarized above for Mr. Timothy Sheehy.
The agreement contains customary confidentiality obligations, non-competition restrictions for two (2) years from the date of termination of employment and non-solicitation restrictions for two (2) years from the date of termination of employment.
401(k) Plan
Bridger maintains a qualified 401(k) savings plan that provides eligible employees with an opportunity to save for retirement on a tax advantaged basis. For calendar year 2022, Bridger provided each of Messrs. Timothy Sheehy and Muchmore with employer matching contributions totaling $1,558 and $1,615, respectively, as set forth in the “All Other Compensation” column of the 2022 Summary Compensation Table.
116
Executive Compensation Arrangements
Following the Closing, Bridger has been developing an executive compensation program that is designed to align compensation with Bridger’s business objectives and the creation of shareholder value, while enabling Bridger to attract, motivate and retain individuals who contribute to the long-term success of Bridger. Decisions on the executive compensation program will be made by the Compensation Committee.
Director Compensation
Cash fees
Bridger pays its non-employee and non-affiliated directors an annual cash retainer of $100,000.
With respect to calendar year 2022, Ms. Coleman earned cash fees of $100,000.
With respect to calendar year 2022, Mr. Matthew Sheehy earned both a transaction and discretionary bonus totaling $1,825,000. Mr. Matthew Sheehy received a transaction bonus payment of $1,133,088 in August 2022 representing a portion of the transaction bonus earned in calendar year 2022. In addition, Mr. Matthew Sheehy was paid during calendar year 2023 $691,912 ($162,500 of which represents the remaining transaction bonus amount earned in calendar year 2022 and $529,412 of which represents the discretionary bonus amount earned in calendar year 2022).
The following table sets forth information for the year ended December 31, 2022 regarding the compensation awarded to certain of Bridger’s non-employee directors. Todd Hirsch is a Blackstone Inc. appointed director and did not receive any compensation for his services as a member of Board.
2022 Director Compensation Table
Name | Fees Earned or Paid in Cash ($) | All Other Compensation ($)(1) | Total ($) | |||||||||
Matthew Sheehy | — | $ | 1,825,000 | $ | 1,825,000 | |||||||
Debra Coleman(2) | $ | 100,000 | — | $ | 100,000 | |||||||
Todd Hirsch | — | — | — | |||||||||
| (1) | The amount reported in this column represents both a transaction and discretionary bonus totaling $1,825,000. Mr. Matthew Sheehy received a transaction bonus payment of $1,133,088 in August 2022 representing a portion of the transaction bonus earned in calendar year 2022. In addition, Mr. Matthew Sheehy was paid during calendar year 2023 $691,912 ($162,500 of which represents the remaining transaction bonus amount earned in calendar year 2022 and $529,412 of which represents the discretionary bonus amount earned in calendar year 2022). |
| (2) | Ms. Coleman resigned from the Board on September 8, 2023. |
117
CERTAIN RELATIONSHIPS AND RELATED PERSON TRANSACTIONS
Certain Relationships and Related Person Transactions – Company
Business Combination Agreement
On the Closing Date, Legacy Bridger and JCIC consummated the Business Combination pursuant to the terms of the Merger Agreement.
In connection with the Business Combination, stockholders owning 34,245,643 shares of JCIC Class A Ordinary Shares exercised their rights to have those shares redeemed for cash at a redemption price of approximately $10.16 per share, or an aggregate of $347,805,923.74. The Legacy Bridger Equityholders were issued shares of our Common Stock at the Closing and 315,789.473684 shares of Series A Preferred Stock. Upon consummation of the Business Combination, each public stockholder’s JCIC ordinary shares that were not redeemed and the outstanding JCIC Warrants were automatically converted into an equivalent number of shares of our Common Stock and our Warrants as a result of the Business Combination. Additionally, upon consummation of the Business Combination, 4,318,189 shares of JCIC Class B Ordinary Shares were converted to 4,318,189 shares of our Common Stock (of which 855,000 of those shares are subject to certain vesting and forfeiture provisions set forth in that certain Sponsor Agreement, dated August 3, 2022, by and among JCIC, JCIC Sponsor, each of the officers and directors of JCIC (collectively, the “JCIC Sponsor Persons”) and the Company (the “Sponsor Agreement”). The Business Combination valued Legacy Bridger in the aggregate at an implied pre-money enterprise value of $807,600,000.
Warrant Agreement Assignment, Assumption and Amendment
On the Closing Date, the Company entered into the Warrant Assumption Agreement (the “Warrant Assumption Agreement”), by and among the Company, JCIC and Continental Stock Transfer & Trust Company. The Warrant Assumption Agreement assigned the Existing Warrant Agreement to the Company, and the Company agreed to perform all applicable obligations of JCIC under the existing agreement.
Pursuant to the Warrant Assumption Agreement, JCIC assigned all its rights, title and interest in the Existing Warrant Agreement to the Company and all warrants of JCIC to purchase JCIC Class A Ordinary Shares, as contemplated under the Existing Warrant Agreement, are no longer exercisable for JCIC Class A Ordinary Shares, but instead are Warrants exercisable for shares of Common Stock on the same terms that were in effect prior to the Closing under the terms of the Existing Warrant Agreement, except as described in the Warrant Assumption Agreement.
The foregoing description of the Warrant Agreement and the Warrant Assumption Agreement is a summary only and is qualified in its entirety by reference to the Warrant Agreement and the Warrant Assumption Agreement, copies of which are incorporated by reference and included as Exhibit 4.1 and Exhibit 4.2, respectively, to the registration statement of which this prospectus forms a part.
Amended and Restated Registration Rights Agreement
At the Closing, Bridger, JCIC Sponsor, the BTO Stockholders and certain other stockholders of Legacy Bridger became parties to the Amended and Restated Registration Rights Agreement. The Amended and Restated Registration Rights Agreement provides these holders (and their permitted transferees) with the right to require the Company, at the Company’s expense, to file a resale shelf registration statement on behalf of the stockholder parties thereto no later than fifteen (15) business days after the Closing and to register the shares of Common Stock that they hold on customary terms for a transaction of this type, including customary demand and piggyback registration rights, subject to certain specified underwriter cutbacks and issuer blackout periods. The Amended and Restated Registration Rights Agreement also provides that the Company pay certain expenses of the electing holders relating to such registrations and indemnify them against certain liabilities that may arise in
118
connection therewith. In addition, pursuant to the Amended and Restated Registration Rights Agreement, the Legacy Bridger Equityholders (other than the BTO Stockholders) and JCIC Sponsor are subject to a restriction on transfer of their Common Stock for a period of twelve (12) months following the Closing, and the BTO Stockholders are subject to a restriction on transfer of their Common Stock for a period of six (6) months following the Closing, in each case subject to certain exceptions.
The foregoing description of the A&R Registration Rights Agreement does not purport to be complete and is qualified in its entirety by the full text of the A&R Registration Rights Agreement, a copy of which is incorporated by reference and included as Exhibit 10.1 to the registration statement of which this prospectus forms a part.
Indemnification Agreements
On the Closing Date, Bridger entered into indemnification agreements (the “Indemnification Agreements”) effective as of the Closing with all of its directors and executive officers. These Indemnification Agreements require Bridger to indemnify its directors and executive officers for certain expenses, including attorneys’ fees, judgments, fines and settlement amounts incurred by a director or executive officer in any action or proceeding arising out of their services as one of Bridger’s directors or executive officers or any other company or enterprise to which the person provides services at Bridger’s request.
The foregoing description of the Indemnification Agreements does not purport to be complete and is qualified in its entirety by the full text of the form of Indemnification Agreement, a copy of which is attached incorporated by reference and included as Exhibit 10.10 to the registration statement of which this prospectus forms a part.
Stockholders Agreement
At the Closing, in connection with the Merger Agreement, the Company, the Founder Stockholders and the BTO Stockholders entered into the Stockholders Agreement at the Closing. Pursuant to terms of the Stockholders Agreement, effective as of the Closing Date, the Board is comprised of nine (9) directors. Further, the BTO Stockholders, collectively, have the right, but not the obligation, to nominate for election to the Board (i) up to two (2) directors, for so long as the BTO Entities (as defined in the Stockholders Agreement) collectively beneficially own (directly or indirectly) at least 10% of the outstanding Stock (as defined in the Stockholders Agreement); and (ii) one (1) director, for so long as the BTO Entities collectively beneficially own (directly or indirectly) less than 10% of the outstanding Stock, but at least 33% of the shares of Stock held by the BTO Entities as of the Closing. In the event that a vacancy is created at any time by the death, disqualification, resignation or removal of a director nominated by the BTO Stockholders, the BTO Stockholders, collectively, will have the right to designate a replacement to fill such vacancy. In addition, for so long as the BTO Entities have such nomination rights, (i) the Board will use reasonable best efforts to cause any committee of the Board to include in its membership at least one (1) director nominated by the BTO Stockholders provided that such individual satisfies all applicable SEC and stock exchange requirements and (ii) the BTO Stockholders have a consent right over affiliate transactions entered into by the Company or any of its subsidiaries, subject to customary exceptions.
The Founder Stockholders, to the extent they collectively beneficially own (directly or indirectly) at least 10% of the outstanding Stock have the right, but not the obligation, to nominate the chairperson of the Compensation and Nominating and Corporate Governance Committees of the Board, subject to satisfaction of applicable SEC and stock exchange requirements.
Subject to the terms and conditions of the Stockholders Agreement and applicable securities laws, the BTO Stockholders have preemptive rights to acquire their pro rata share of any new issuance of equity securities (or any securities convertible into or exercisable or exchangeable for equity securities) by the Company, subject to customary exceptions. The BTO Stockholders are entitled to apportion the preemptive rights granted to it in such proportions as it deems appropriate, among (i) itself and (ii) any BTO Entity; provided that each such BTO Entity agrees to enter into the Stockholders Agreement, as a “Stockholder” under the Stockholders Agreement.
119
The foregoing description of the Stockholders Agreement does not purport to be complete and is qualified in its entirety by the full text of the Stockholders Agreement, a copy of which is incorporated by reference and included as Exhibit 10.2 to the registration statement of which this prospectus forms a part.
PC-12 Aircraft Leases
On July 10, 2023, BAG entered into two Aircraft Operating Lease Agreements (the “PC-12 Lease Agreements”) for the lease of two Pilatus PC-12/47 aircraft from Element Aviation Services, LLC. Element Aviation Services, LLC is owned by Mr. Timothy Sheehy, the Chief Executive Officer and a director of Bridger. Each of the PC-12 Lease Agreements has a term of 60 months. The monthly lease payments for the first PC-12/47 is $62,190, and the monthly lease payments for the second PC-12/47 is $77,195. Under the PC-12 Lease Agreements, BAG has the option until July 10, 2024 to purchase the first leased PC-12/47 aircraft for $5,800,000 and to purchase the second leased PC-12/47 aircraft for $6,950,000. Pursuant to the terms of the PC-12 Lease Agreements, BAG agreed to service, repair and maintain each of the PC-12/47 aircraft at BAG’s cost and expense. The terms of the PC-12 Lease Agreements were approved by the Board, with Mr. Timothy Sheehy and Mr. Matthew Sheehy abstaining from such vote.
The foregoing description of the PC-12 Lease Agreements does not purport to be complete and is qualified in its entirety by the full text of the PC-12 Lease Agreements, copies of which are incorporated by reference and included as Exhibits 10.39 and 10.40 to the registration statement of which this prospectus forms a part.
Certain Relationships and Related Person Transactions – Legacy Bridger
Legacy Bridger Series A Preferred Shares Financing
In November 2021, Legacy Bridger issued 500 thousand Legacy Bridger Series A Preferred Shares at $10.00 per share for an aggregate purchase price of $5 million. The BTO Stockholders were the sole purchasers. The Legacy Bridger Series A Preferred Shares accrued interest at 12%. The Legacy Bridger Series A-1 Preferred Shares had management rights, while the Legacy Bridger Series A-2 Preferred Shares had no voting or management rights. The Legacy Bridger Series A Preferred Shares were redeemable at any time at the option of Legacy Bridger at a redemption price equal to the greater of (i) the product of the amount invested, multiplied by 2.25, plus any indemnification amounts, or (ii) the aggregate liquidation preference.
Legacy Bridger Series B Preferred Shares Financing
In December 2020, Bridger issued 10 million Legacy Bridger Series B Preferred Shares at $1.00 per share. In November 2021, Legacy Bridger issued an additional 50 million Legacy Bridger Series B Preferred Shares at $1.00 per share. The BTO Stockholders and Bridger Element LLC were the sole purchasers. The Legacy Bridger Series B Preferred Shares were non-voting and accrued interest at 17.5% per annum, compounded quarterly. The shares were redeemable at any time at the option of Legacy Bridger at a redemption price equal to face value, plus accrued, but unpaid interest. If not redeemed on or prior to March 31, 2022, the Legacy Bridger Series B Preferred Shares accrued interest at 21.5% annually, compounded quarterly. The Legacy Bridger Series B Preferred Shares were redeemed in April 2022. The BTO Stockholder and Bridger Element LLC purchased $44.5 million and $15.5 million, respectively, of the Legacy Bridger Series B Preferred Shares.
Legacy Bridger Series C Preferred Shares Financing
On April 25, 2022, Bridger raised $300 million from the issuance of Legacy Bridger Series C Preferred Shares. The proceeds were used as follows: (i) $70 million to redeem all of the Legacy Bridger Series B Preferred Shares, (ii) $100 million to redeem a portion of the outstanding Legacy Bridger Series A Preferred Shares and (iii) the remainder to fund growth capital expenditures and for general corporate purposes. The Legacy Bridger Series C Preferred Shares were non-voting and accrued interest initially at 7.0% accruing daily, computed on the basis of a 365-day year. The BTO Stockholders and Bridger Element LLC received in the aggregate $100 million and $70 million, respectively, of aggregate proceeds in connection with the redemption of the Legacy Bridger Series A Preferred Shares and Legacy Bridger Series B Preferred Shares.
120
Series 2022 Bonds
On July 21, 2022, Legacy Bridger closed on the Series 2022 Bond Offering with Gallatin County, Montana for a total of $160.0 million of gross proceeds. Pursuant to the Series 2022 Bond Offering, Legacy Bridger received aggregate proceeds of $135.0 million on July 21, 2022 and an additional $25.0 million on August 10, 2022. The proceeds were used as follows: (i) $134.0 million to redeem all of the remaining Legacy Bridger Series A 1 Preferred Shares and Legacy Bridger Series A-2 Preferred Shares, (ii) $7.7 million to redeem the Series 2021 Bond and (iii) the remainder to finance the construction and equipping of the Company’s third and fourth aircraft hangars in Belgrade, Montana and to fund the purchase of additional CL415EAF aircraft. In connection with the Series 2022 Bond Offering, CMH, LLC purchased approximately $10 million of the Series 2022 Bonds. Mr. Timothy Sheehy, Chief Executive Officer and director of Legacy Bridger, Mr. Matthew Sheehy, Co-Founder and Chairman of the Board of Legacy Bridger and Mr. McAndrew Rudisill, Chief Investment Officer and director of Legacy Bridger, have economic interests in the Series 2022 Bonds acquired by CMH, LLC in the amounts of approximately $4.5 million, $4.4 million and $1.0 million, respectively. CMH, LLC purchased the Series 2022 Bonds on an arms’ length basis and on the same terms and conditions that were offered to the public during the offering. As of December 31, 2022, CMH, LLC has received approximately $128,000 in interest. The Series 2022 Bonds mature on September 1, 2027, with an annual interest rate of 11.5%. Interest will be payable semiannually on March 1 and September 1 of each year until maturity and commenced on September 1, 2022.
Pilatus PC-12/47 Purchase
In September 2021, Mr. Timothy Sheehy, the Chief Executive Officer and a director of Bridger, acquired a Pilatus PC-12/47 aircraft for $3.0 million, which was then repaired and upgraded. In July 2022, Legacy Bridger purchased the plane from Mr. Timothy Sheehy for $3.85 million. The purchase price was based on an independent third-party valuation from July 2022 that valued the plane at between $4,009,000 and $3,562,000. In addition, Mr. Timothy Sheehy permitted Legacy Bridger to use the plane for company business for no compensation until Legacy Bridger acquired the aircraft from Mr. Timothy Sheehy.
Mountain Air
Bridger Aviation Services, LLC (“Bridger Aviation”) was a party to that certain Management Services Agreement (the “Aviation Agreement”), dated April 13, 2018, with Mountain Air, LLC (“Mountain Air”). The original term of the agreement was ten (10) years. On August 3, 2022 and in connection with the execution of the Merger Agreement, the parties to the Aviation Agreement amended the Aviation Agreement to revise the list of covered aircraft, revise the termination provisions and update the service standards to comply with Federal Aviation Regulations.
Pursuant to the Aviation Agreement, Bridger Aviation leased certain aircraft to Mountain Air. Mountain Air operated the aircraft and paid Bridger Aviation a fee equal to 99% of all revenue it received from the use and deployment of Bridger Aviation’s aircraft. Mountain Air was obligated to operate and maintain the aircraft in accordance with Federal Aviation Regulations. During 2020, 2021 and 2022, the aggregate amounts of revenue received by Mountain Air for services performed with Legacy Bridger aircraft was $6,869 thousand, $8,604 thousand, and $7,215 thousand, respectively, and the aggregate amounts Mountain Air paid to Legacy Bridger pursuant to the Aviation Agreement were $6,804 thousand and $8,520 thousand and $7,150 thousand, respectively. Mountain Air recognized income of $56 thousand in 2020, $77 thousand in 2021 and $64 thousand in 2022.
Additionally, in order to further secure the benefits of the Aviation Agreement post-Closing, the Aviation Agreement, as amended, was supplemented by a Side Letter, dated August 3, 2022, among JCIC, Legacy Bridger, Bridger Air Tanker, LLC (“Bridger Air”), Red Cloud Holdings, LLC and Mr. Timothy Sheehy, obligating the parties to promptly cause Red Cloud Holdings, LLC, of which Mr. Matthew Sheehy is the sole managing member, and Mr. Timothy Sheehy, as sole holders of the equity interests in Mountain Air, to transfer such equity interests to Legacy Bridger or one of its subsidiaries, prior to the Closing for $1.00 and on the terms and conditions set forth on Exhibit K to the Merger Agreement. On November 7, 2022, the transfer was
121
consummated, and Mountain Air is now a wholly-owned subsidiary of Bridger. Mountain Air has not paid a dividend to its former equityholders.
Northern Fire
Bridger Air is a party to that certain Support Services Agreement (the “NFMS Agreement”), dated April 22, 2019, with Northern Fire Management Services, LLC (“Northern Fire”). The original term of the agreement was five (5) years. On August 3, 2022, in connection with the execution of the Merger Agreement, the parties to the NFMS Agreement amended the NFMS Agreement to provide that the NFMS Agreement would not terminate in the event Mr. Al Hymers or Mr. Timothy Sheehy ceased to be employed by Northern Fire.
Pursuant to the NFMS Agreement, Northern Fire agreed to provide pilot, mechanic and support services to Bridger in connection with the deployment and use of Bridger Air’s aircraft. Northern Fire provides services solely for Bridger and its subsidiaries. Historically, Legacy Bridger has paid on behalf of Northern Fire all amounts owed to Northern Fire’s employees and no additional amounts were owed by either party under the NFMS Agreement. As a result, there are no direct cash payments between Bridger Air and Northern Fire, and Northern Fire has historically had no profits. The aggregate amounts paid by Legacy Bridger to Northern Fire’s employees on behalf of Northern Fire pursuant to the NFMS Agreement were $1,443 thousand, $1,231 thousand and $1,758 thousand during 2020, 2021 and 2022, respectively.
Northern Fire was organized in 2019, and Mr. Timothy Sheehy and Mr. Al Hymers each originally owned 50% of the equity interests. In June 2022, Mr. Timothy Sheehy assigned his equity interests in Northern Fire to Bridger Aerospace Group, LLC (“BAG”). Additionally, in order to further secure the benefits of the NFMS Agreement post-Closing, the NFMS Agreement, as amended, was supplemented by a Side Letter, dated August 3, 2022, by and among JCIC, Legacy Bridger, Bridger Air and Al Hymers, pursuant to which BAG and Al Hymers, as sole holders of the equity interests in Northern Fire, agreed to cause Northern Fire to operate in a manner consistent with its past practice and, to the extent permitted by law, for the exclusive benefit of Bridger and its subsidiaries, in accordance with the terms and conditions of the NFMS Agreement and the operating agreement of Northern Fire.
Related Person Transaction Policy
The Board maintains a written related person transaction policy that sets forth the Company’s policies and procedures regarding the identification, review, consideration and oversight of “related person transactions.” For purposes of the Company’s policy only, a “related person transaction” is any transaction, arrangement or relationship, or any series of similar transactions, arrangements or relationships in which: (i) the aggregate amount involved will or may be expected to exceed $120,000 in any fiscal year; (ii) the Company or any of its consolidated subsidiaries is or will be a participant; and (iii) a “related person” has or will have a direct or indirect material interest (including any indebtedness or guarantee of indebtedness), including any material amendment or modification to an existing related person transaction.
Under the policy, prior to entering into any related person transaction, the related person or the Company’s Chief Legal Officer on their behalf (or if the related Person is an immediate family member of an executive officer, director or nominee for director of the Company, such executive officer, director or nominee for director or the Company’s Chief Legal Officer on their behalf) shall advise the Audit Committee of all relevant material information regarding the related person transaction. The Audit Committee shall consider such proposed transaction at its next regularly scheduled meeting or, if it deems it advisable, prior thereto at an interim meeting called for such purpose, unless the Audit Committee determines that the review, approval or ratification of such proposed transaction should be considered by all of the disinterested, independent members of the Board, in which case such disinterested, independent members of the Board shall consider such proposed transaction at the Board’s next regularly scheduled meeting or, if they deem it advisable, prior thereto at an interim meeting called for such purpose. The Audit Committee (or the disinterested, independent members of the Board) will assess whether the proposed transaction is a related person transaction for purposes of the policy. If the Audit Committee (or the disinterested, independent members of the Board) determines that the proposed transaction is
122
a related person transaction for purposes of the policy, the proposed related person transaction shall be reviewed. In considering related person transactions, the Audit Committee (or the disinterested, independent members of the Board) will take into account the relevant available facts and circumstances.
The Audit Committee (or the disinterested, independent members of the Board) may approve only those transactions that are in, or are not inconsistent with, the best interests of the Company and its stockholders, as the Audit Committee (or the disinterested, independent members of the Board) determines in good faith. Unless noted otherwise, all of the transactions described in the section of this prospectus entitled “Certain Relationships and Related Person Transactions” were entered into prior to the adoption of such policy.
The Audit Committee may determine certain transactions or categories of transactions with related persons are not considered related person transactions for purposes of the related person transactions policy given their nature, size and degree of significance to the Company and/or the immateriality of such transaction to the relevant related person, and that such transactions are not required to be individually reported to, reviewed by, and/or approved or ratified under the policy.
Certain Relationships and Related Person Transactions – JCIC
Founder Shares
On August 24, 2020, JCIC Sponsor paid an aggregate of $25,000, or approximately $0.003 per share, to cover certain JCIC expenses in consideration of 8,625,000 JCIC Class B Ordinary Shares, par value $0.0001 per share. The number of JCIC Class B Ordinary Shares issued was determined based on the expectation that such JCIC Class B Ordinary Shares would represent 20% of the outstanding shares upon completion of the offering. On September 25, 2020, JCIC Sponsor transferred 25,000 JCIC Class B Ordinary Shares to each of Heather Hartnett and Samir Kaul, each of whom served on the JCIC Board, at their original per share purchase price. On January 13, 2021, JCIC Sponsor surrendered 1,437,500 JCIC Class B Ordinary Shares to JCIC for cancellation for no consideration. On January 21, 2021, JCIC effected a share capitalization of 1,437,500 JCIC Class B Ordinary Shares, resulting in an aggregate of 8,625,000 JCIC Class B Ordinary Shares outstanding. On March 8, 2021, JCIC Sponsor transferred 25,000 JCIC Class B Ordinary Shares to Richard Noll, who served on the JCIC Board, at their original per share purchase price.
JCIC Private Placement Warrants
On January 26, 2021, JCIC completed the sale to JCIC Sponsor of an aggregate of 9,400,000 Private Placement Warrants for a purchase price of $1.00 per whole warrant for an aggregate of $9,400,000. Each Private Placement Warrant entitled the holder to purchase one JCIC Class A Ordinary Share at $11.50 per share. Pursuant to the terms of the Warrant Assumption Agreement, the Private Placement Warrants are currently exercisable for shares of Common Stock, on the same terms and conditions and with the same exercise price. The Private Placement Warrants (including the shares of Common Stock upon exercise thereof) could not, subject to certain limited exceptions, be transferred, assigned or sold by the holder until January 24, 2024 and entitles the holders thereof to certain registration rights.
Original Sponsor Letter Agreement
On January 26, 2021, JCIC entered into a letter agreement (“JCIC Sponsor Letter Agreement”) with JCIC Sponsor, pursuant to which, among other things, JCIC Sponsor agreed to vote all JCIC Class B Ordinary Shares held by it to approve a proposed business combination (including any proposals recommended by the JCIC Board in connection with such business combination and not to redeem any JCIC shares held by them in connection with such shareholder approval in order to induce JCIC and the underwriters in JCIC’s initial public offering to enter into an underwriting agreement and to proceed with JCIC’s initial public offering.
Sponsor Agreement
On August 3, 2022, in connection with the execution of the Merger Agreement, JCIC, JCIC Sponsor Persons and Bridger entered into JCIC Sponsor Agreement, pursuant to which, among other things, JCIC
123
Sponsor agreed to a forfeiture, effective as of immediately prior to the Closing, of the number of JCIC Class B Ordinary Shares equal to the sum of (a) 8,550,000 minus the number of Available Sponsor Shares (as defined therein), and (b) if the Trust Amount is less than $20,000,000, (i) the excess of the aggregate of fees and expenses for legal counsel, accounting advisors, external auditors and financial advisors incurred by JCIC in connection with the Transactions prior to Closing, but excluding any deferred underwriting fees, over $6,500,000, if any, divided by (ii) $10.00. In accordance with such provisions, JCIC Sponsor forfeited 4,306,811 shares of JCIC Class B Ordinary Shares immediately prior to Closing.
In addition, pursuant to JCIC Sponsor Agreement, JCIC Sponsor agreed to subject the Earnout Shares to a performance-based vesting schedule such that 50% of the Earnout Shares will vest on the first date during the Earnout Period (as defined therein) on which the VWAP of our Common Stock is greater than $11.50 for a period of at least twenty (20) days out of thirty (30) consecutive trading days and 50% of the Earnout Shares will vest on the first date during the Earnout Period on which the volume-weighted average closing sale price of a share of our Common Stock is greater than $13.00 for a period of at least twenty (20) days out of thirty (30) consecutive trading days.
If the Trust Amount after deducting all amounts payable in respect of the JCIC Shareholder Redemption was less than $50,000,000, then immediately prior to Closing, each of JCIC and JCIC Sponsor agreed to convert any outstanding loan balance under the Promissory Note between JCIC and JCIC Sponsor, under which $1,150,000 had been drawn as of the Closing, into a number of JCIC Class A Ordinary Shares equal to the amount of outstanding loan balance under the Promissory Note divided by $10.00, rounded up to the nearest whole share. In accordance with such provisions, JCIC Sponsor converted its outstanding loan balance into 115,000 shares of JCIC Class A Ordinary Shares immediately prior to Closing.
Related Party Loans
On August 24, 2020, JCIC issued an unsecured promissory note (the “IPO Promissory Note”) to JCIC Sponsor, pursuant to which JCIC may borrow up to an aggregate principal amount of $300,000. The IPO Promissory Note was non-interest bearing and payable on the earlier of (i) March 31, 2021 and (ii) the completion of JCIC’s initial public offering. The outstanding balance under the IPO Promissory Note of $114,031 was repaid on January 25, 2021. JCIC was unable to borrow any future amounts against this note.
On February 16, 2022, JCIC entered into a $1,500,000 convertible promissory note (the “Promissory Note”) with JCIC Sponsor in order to fund working capital deficiencies or finance transaction costs in connection with a Business Combination. The Promissory Note accrued no interest and was payable upon completion of a Business Combination. The Promissory Note’s entire or partial balance could be converted into warrants at the discretion of JCIC Sponsor at the time of Business Combination. The warrants would have been identical to the Private Placement Warrants, however, pursuant to JCIC Sponsor Agreement, if the Trust Amount was less than $50 million after taking account of public shareholder redemptions, the balance of the Promissory Note would be converted into shares of our Common Stock at $10.00 per share. As of the Closing, the aggregate balance of the Promissory Note was $1,150,000, and JCIC Sponsor converted its outstanding loan balance into 115,000 shares of JCIC Class A Ordinary Shares immediately prior to Closing.
Administrative Services Agreement
Commencing on January 21, 2021, JCIC entered into an agreement pursuant to which it will pay an affiliate of JCIC Sponsor up to $10,000 per month for office space, secretarial and administrative services. Upon completion of the Business Combination, JCIC ceased paying these monthly fees. For the year ended December 31, 2022, JCIC incurred $120,000 of such fees and $10,000 is included in accrued expenses in the accompanying consolidated balance sheets of JCIC for the year ended December 31, 2022. For the year ended December 31, 2021, JCIC incurred $113,226, in fees for these services, of which $10,000 is included in accrued expenses in the accompanying consolidated balance sheets.
124
PRINCIPAL STOCKHOLDERS
The following table and accompanying footnotes set forth information with respect to the beneficial ownership of Common Stock, as of September 30, 2023, for (1) each person known by us to be the beneficial owner of more than 5% of the outstanding shares of Common Stock, (2) each member of the Board, (3) each of Bridger’s executive officers and (4) all of the members of the Board and Bridger’s executive officers, as a group.
Beneficial ownership is determined according to the rules of the SEC, which generally provide that a person has beneficial ownership of a security if he, she or it possesses sole or shared voting or investment power over that security, including options and warrants that are currently exercisable or exercisable within 60 days. Shares of Common Stock issuable pursuant to options or warrants are deemed to be outstanding for purposes of computing the beneficial ownership percentage of the person or group holding such options or warrants but are not deemed to be outstanding for purposes of computing the beneficial ownership percentage of any other person. In addition, in calculating percentages of shares of Common Stock owned by any holder of shares of Series A Preferred Stock, we have assumed that particular holder has exercised its conversion rights at a conversion price of $11.00 per share and treated as outstanding the number of shares of Common Stock issuable to that particular holder upon conversion of that particular holder’s shares of Series A Preferred Stock, and we did not assume the conversion or exercise of any other holder’s Series A Preferred Stock in calculating the percentage ownership of any other holder listed below.
As of September 30, 2023, there were outstanding 44,776,926 shares of Common Stock.
125
Unless otherwise noted in the footnotes to the following table, and subject to applicable community property laws, the persons and entities named in the table have sole voting and investment power with respect to their beneficially owned shares of Common Stock.
| Amount and Nature of the Beneficial Ownership Prior to the Offering | ||||||||
Name and Address of Beneficial Owner† | Number of Shares of Common Stock | % of Outstanding Shares of Common Stock | ||||||
Directors and Executive Officers of Bridger | ||||||||
Jeffrey E. Kelter(1) | 11,928,189 | 22.0 | % | |||||
Eric Gerratt | — | — | ||||||
Anne Hayes | — | — | ||||||
Dean Heller | 194,436 | * | ||||||
Todd Hirsch | — | — | ||||||
Wyman Howard | — | — | ||||||
McAndrew Rudisill(2) | 5,280,166 | 11.8 | % | |||||
Robert F. Savage(1) | 11,928,189 | 22.0 | % | |||||
Timothy Sheehy(3) | 10,294,788 | 23.0 | % | |||||
Matthew Sheehy(4) | 10,114,402 | 22.6 | % | |||||
James Muchmore(5) | 1,986,345 | 4.4 | % | |||||
Darren Wilkins | 207,968 | * | ||||||
All Directors and Executive Officers of Bridger as a Group (12 individuals) | 38,102,733 | 70.3 | % | |||||
Other 5% Shareholders | ||||||||
Avenue Capital(6) | 3,170,193 | 6.6 | % | |||||
Barings LLC(7) | 5,019,471 | 10.1 | % | |||||
Bear Creek(8) | 4,460,547 | 9.5 | % | |||||
Blackstone(9) | 9,624,610 | 21.5 | % | |||||
JCIC Sponsor LLC(1) | 11,928,189 | 22.0 | % | |||||
JPMorgan Chase Funding Inc.(10) | 20,342,074 | 31.2 | % | |||||
KSH Capital LP(1) | 11,928,189 | 22.0 | % | |||||
Thomas Jermoluk(1) | 11,928,189 | 22.0 | % | |||||
| * | Denotes less than 1%. |
| † | Unless otherwise noted, the business address of each of the following individuals is c/o Bridger Aerospace Group Holdings, Inc., 90 Aviation Lane, Belgrade, MT 59714. |
| (1) | Represents shares of Common Stock held by JCIC Sponsor and includes (i) 855,000 Earnout Shares and (ii) 9,400,000 shares of Common Stock issuable upon exercise of the Private Placement Warrants at an exercise price of $11.50 per share. Per applicable SEC rules, the shares beneficially owned by JCIC Sponsor are also listed as being beneficially owned by KSH Capital LP and Messrs. Kelter, Savage and Jermoluk, as JCIC Sponsor is managed by KSH Capital LP and is controlled indirectly by Messrs. Kelter, Savage and Jermoluk. The business address of each of the foregoing entities and individuals is c/o JCIC Sponsor LLC, 386 Park Avenue South, FL 20 New York, NY 10016. |
| (2) | Consists of 2,255,470 shares of Common Stock held by Pelagic Capital Advisors LLC and 3,024,696 shares of Common Stock (including 175,051 shares of Common Stock issued under the Omnibus Incentive Plan) held by PCAO LLC, each of which are managed by Mr. Rudisill. Mr. Rudisill received RSUs with respect to 1,451,874 shares of Common Stock, 725,937 of which vested upon the Closing but will settle after January 24, 2024. |
| (3) | Consists of 263,833 shares of Common Stock issued under the Omnibus Incentive Plan held by Mr. Timothy Sheehy, 2,081,409 shares of Common Stock held by Turtle Lake Holding Company, LLC, 6,045,985 shares of Common Stock held by the Timothy P. Sheehy Revocable Trust, and 1,903,561 shares |
126
| of Common Stock held by ElementCompany, LLC. Turtle Lake Holding Company, LLC is managed by Mr. Timothy Sheehy, and Mr. Timothy Sheehy is the trustee of the Timothy P. Sheehy Revocable Trust. ElementCompany, LLC is co-managed by Mr. Matthew Sheehy and Mr. Timothy Sheehy, each of whom are deemed to be beneficial owners of the shares of Common Stock held by ElementCompany, LLC. Mr. Timothy Sheehy received RSUs with respect to 1,742,182 shares of Common Stock, 871,091 of which vested upon the Closing but will settle after January 24, 2024. Per applicable SEC rules, the shares beneficially owned by ElementCompany, LLC are listed as being beneficially owned by both Matthew P. Sheehy and Timothy P. Sheehy, as each of these individuals serve as co-managers of ElementCompany, LLC. |
| (4) | Consists of 7,515,514 shares of Common Stock (including 129,571 shares of Common Stock issued under the Omnibus Incentive Plan) held by Red Cloud Holding Investments, LLC, 695,327 shares of Common Stock held by the Matthew P. Sheehy Revocable Trust, and 1,903,561 shares of Common Stock held by ElementCompany, LLC. Red Cloud Holding Investments, LLC is managed by Mr. Matthew Sheehy, and Mr. Matthew Sheehy is the trustee of the Matthew P. Sheehy Revocable Trust. ElementCompany, LLC is co-managed by Mr. Matthew Sheehy and Mr. Timothy Sheehy, each of whom are deemed to be beneficial owners of the shares of Common Stock held by ElementCompany, LLC. Mr. Matthew Sheehy received RSUs with respect to 1,161,455 shares of Common Stock, 580,728 of which vested upon the Closing but will settle after January 24, 2024. Per applicable SEC rules, the shares owned by ElementCompany, LLC are listed as being beneficially owned by both Matthew P. Sheehy and Timothy P. Sheehy, as each of these individuals serve as co-managers of ElementCompany, LLC. |
| (5) | Consists of 1,986,345 shares of Common Stock (including 113,255 shares of Common Stock issued under the Omnibus Incentive Plan) held by Black River Group LLC, which is managed by Mr. Muchmore. Mr. Muchmore received RSUs with respect to 871,147 shares of Common Stock, 87,115 of which vested upon the Closing but will settle after January 24, 2024. |
| (6) | Consists of 31,578.947368 shares of Series A Preferred Stock that are convertible at the election of the holder into shares of Common Stock pursuant to the terms of such Series A Preferred Stock. These shares are held by ASSF Holdings, L.P., which is 100% owned by Avenue Sustainable Solutions Fund, L.P. (“ASSF”). Avenue Capital Management II, L.P. (“ACMII”) serves as the investment manager of ASSF. ACMII may be deemed to have or to share voting and investment power with respect to the shares held by ASSF. Avenue Capital Management II GenPar, LLC is the general partner of ACMII. Marc Lasry is the managing member of Avenue Capital Management II GenPar, LLC. Marc Lasry may be deemed to be the indirect beneficial owner of the securities reported by ASSF by reason of his ability to direct the vote and/or disposition of such securities, and his pecuniary interest in such shares (within the meaning of Rule 16a-1(a)(2) under the Exchange Act) is a fractional interest in such amount. The address for the foregoing person is 11 West 42nd Street, 9th Floor, New York, New York 10036. |
| (7) | Consists of 4,250.000000 shares of Series A Preferred Stock held by Barings SS4 (LUX) LLC; 750.000000 shares of Series A Preferred Stock held by Barings Global Special Situations Credit Fund 4 (Delaware), L.P.; 14,618.000000 shares of Series A Preferred Stock held by Barings BDC, Inc.; 7,309.000000 shares of Series A Preferred Stock held by Barings Capital Investment Corporation; 17,725.000000 shares of Series A Preferred Stock held by Barings Private Credit Corporation; 365.000000 shares of Series A Preferred Stock held by Barings Corporate Investors; 183.000000 shares of Series A Preferred Stock held by Barings Participation Investors; and 4,800.000000 shares of Series A Preferred Stock held by Martello Re Limited, all of which are convertible at the election of the holder into shares of Common Stock pursuant to the terms of such Series A Preferred Stock. Barings LLC is a registered investment adviser and serves as the investment adviser to the entities and/or funds included in the prior sentence, and therefore has the power to vote and dispose of the aggregate of such shares of Series A Preferred Stock. Bryan High is the managing director of the investment team at Barings LLC that manages the shares of Series A Preferred Stock held by such Barings entities and/or funds. Each of Barings LLC and Mr. High expressly disclaims beneficial ownership of any securities reported herein except to the extent Barings LLC and Mr. High exercises voting or dispositive power with respect to such securities. The business address of Barings LLC and Mr. High is 300 South Tryon, Suite 2500, Charlotte, NC 28202. |
127
| (8) | Consists of 21,052.631579 shares of Series A Preferred Stock that are convertible at the election of the holder into shares of Common Stock pursuant to the terms of such Series A Preferred Stock held by BC Super Scooper LLC (“Bear Creek LLC”) and 2,347,085 shares of Common Stock held by Bear Creek Products 2018-1 (CNI), LLLP (“Bear Creek LLLP”). BCGP-2016, LLC (“Bear Creek GP”) is the manager and general partner of Bear Creek LLC and Bear Creek LLLP, respectively. Joseph H. M. Roddy is the manager of Bear Creek GP. Joseph H. M. Roddy may be deemed to beneficially own the securities held directly or indirectly by Bear Creek LLC, Bear Creek LLLP and Bear Creek GP. The address for Bear Creek LLC, Bear Creek LLLP, Bear Creek GP, and Joseph H. M. Roddy is 1200 17th Street, Suite 970, Denver, Colorado 80202. |
| (9) | Consists of 9,389,895 shares of Common Stock held by BTO Grannus Holdings IV – NQ LLC (“BTO Grannus IV”), 162,194 shares of Common Stock held by Blackstone Tactical Opportunities Fund – FD L.P. (“BTOF FD”) and 72,521 shares of Common Stock held by Blackstone Family Tactical Opportunities Investment Partnership III – NQ – ESC L.P. (“BFTOIP III”). |
BTO Grannus IV is managed by Grannus Holdings Manager – NQ L.L.C. and Blackstone Tactical Opportunities Advisors L.L.C. is the investment adviser to BTO Grannus IV. The managing member of Blackstone Tactical Opportunities Advisors L.L.C. is Blackstone Intermediary Holdco L.L.C. The sole member of Blackstone Intermediary Holdco L.L.C. is Blackstone Securities Partners L.P. The general partner of Blackstone Securities Partners L.P. is Blackstone Advisory Services L.L.C. The sole member of Blackstone Advisory Services L.L.C. is Blackstone Holdings I L.P.
The general partner of BFTOIP III is BTO – NQ Side-by-Side GP L.L.C. The sole member of BTO-NQ Side-by-Side GP L.L.C. is Blackstone Holdings II L.P. The general partner with management authority over BTOF FD with respect to Common Stock held thereby is Blackstone Tactical Opportunities Associates III – NQ L.P. The general partner of Blackstone Tactical Opportunities Associates III – NQ L.P. is BTO DE GP – NQ L.L.C. The managing member of BTO DE GP – NQ L.L.C. is Blackstone Holdings II L.P.
The general partner of Blackstone Holdings I L.P. and Blackstone Holdings II L.P. is Blackstone Holdings I/II GP L.L.C. The sole member of Blackstone Holdings I/II GP L.L.C. is Blackstone Inc. The sole holder of the Series II preferred stock of Blackstone Inc. is Blackstone Group Management L.L.C. Blackstone Group Management L.L.C. is wholly-owned by Blackstone’s senior managing directors and controlled by its founder, Stephen A. Schwarzman.
Each of the Blackstone entities described in this footnote and Mr. Schwarzman (other than to the extent it or he directly holds securities as described herein) may be deemed to beneficially own the securities directly or indirectly controlled by such Blackstone entities or him, but each disclaims beneficial ownership of such securities. The address of each of such Blackstone entities and Mr. Schwarzman is c/o Blackstone Inc., 345 Park Avenue, New York, New York 10154.
| (10) | Consists of 202,631.578948 shares of Series A Preferred Stock that are convertible at the election of the holder into shares of Common Stock pursuant to the terms of such Series A Preferred Stock. JPMorgan Chase Funding Inc. is a wholly-owned subsidiary of publicly traded JPMorgan Chase & Co., the board of directors and chief executive officer of which are identified in JPMorgan Chase & Co.’s filings with the SEC. The address for JPMorgan Chase Funding Inc. is 383 Madison Avenue, New York, NY 10179. |
128
DESCRIPTION OF SECURITIES
The following summary of the material terms of our securities is not intended to be a complete summary of the rights and preferences of such securities and is qualified by reference to the Amended and Restated Charter, the Amended and Restated Bylaws and the warrant-related documents described herein, which are exhibits to the registration statement of which this prospectus is a part. We urge to you read each of the Amended and Restated Charter, the Amended and Restated Bylaws and the warrant-related documents described herein in their entirety for a complete description of the rights and preferences of our securities.
Authorized Capitalization
The Amended and Restated Charter authorizes the issuance of 1,010,000,000 shares, consisting of (a) 1,000,000,000 shares of Common Stock and (b) 10,000,000 shares of preferred stock, $0.0001 par value per share (of which 1,000,000 shares are designated as the “Series A Preferred Stock”).
As of September 30, 2023, there were outstanding 44,776,926 shares of Common Stock, 315,789.473684 shares of Series A Preferred Stock and 26,649,874 Warrants, consisting of 17,249,874 Public Warrants and 9,400,000 Private Placement Warrants.
Common Stock
The holders of Common Stock are entitled to one vote for each share held on all matters to be voted on by stockholders. There is no cumulative voting with respect to the election of directors.
Subject to the DGCL and the rights of holders of Preferred Stock, holders of Common Stock are entitled to receive ratable dividends when, as and if declared by the Board out of funds legally available therefor.
If the Company liquidates, dissolves or wind ups, holders of Common Stock are entitled to share ratably in all assets remaining available for distribution to them after payment of liabilities and after provision is made for each class of stock, if any, having preference over Common Stock.
Subject to the DGCL and the rights of holders of Series A Preferred Stock, holders of our Common Stock have no preemptive or other subscription rights and there are no sinking fund or redemption provisions applicable to our Common Stock.
Preferred Stock
The Amended and Restated Charter authorizes the issuance of Series A Preferred Stock (as described below) and provides that shares of preferred stock may be issued from time to time in one or more additional series. The Board is authorized to fix the powers, designations, preferences and relative, participating, optional or other special rights, if any, and the qualifications, limitations or restrictions thereof, if any, of any wholly unissued series of preferred stock, including, without limitation, dividend rights, dividend rate, conversion rights, voting rights, rights and terms of redemption (including, without limitation, sinking fund provisions), redemption price or prices and liquidation preferences of any such series, and the number of shares constituting any such series and the designation thereof, or any of the foregoing. Subject to the terms of any outstanding preferred stock, the Board may, without stockholder approval, issue preferred stock with voting and other rights that could adversely affect the voting power and other rights of the holders of Common Stock and could have anti-takeover effects. The ability of the Board to issue preferred stock without stockholder approval could have the effect of delaying, deferring or preventing a change of control of the Company or the removal of existing management.
Series A Preferred Stock
Dividends. Holders of the Series A Preferred Stock are entitled to receive dividends, paid twice per year, in cash or, at the election of the Company, by increasing the per share liquidation preference for such shares of
129
Series A Preferred Stock. Dividends accrue on the Series A Preferred Stock daily, computed on the basis of a 365-day year, at a compounding rate initially anticipated to be 7.00% per annum but to increase to 9.00% per for the period from (and including) April 25, 2028 to (but excluding) April 25, 2029 and eventually to increase to 11.00% per annum from and after April 25, 2029 and subject to further increase upon the occurrence of certain events. The per share liquidation preference is equal to the initial issuance price plus all accrued and unpaid dividends, whether or not declared. All payments and dividends in respect of the Series A Preferred Stock will be allocated among the holders thereof pro rata in proportion to the value of the shares of Series A Preferred Stock held thereby. No dividends shall be paid or payable to any other holders the Company’s capital stock unless and until the holders of Series A Preferred Stock have received cumulative distributions equal to the aggregate liquidation preference of the Series A Preferred Stock.
Conversion. Each share of Series A Preferred Stock is convertible, at the holder’s election at any time, into such number of shares of common stock (or such other applicable securities in the case of merger, reorganization, recapitalization, reclassification or consolidation) as is determined by dividing (x) the then current accrued liquidation preference of such shares (including any accrued and unpaid dividends since the most recent dividend payment date) by (y) a conversion price of $11.00 per share for such share of Series A Preferred Stock, subject to specified adjustments as set forth in Article IV of the Amended and Restated Charter. No fractional securities will be issued upon conversion of a share of Series A Preferred Stock, and, in lieu of such fractional shares, the Company will pay cash equal to such fraction multiplied by the applicable conversion price.
Optional Redemption. At any time and from time to time on or after April 25, 2027, the Company will have the right, in its sole discretion, to give notice of its election to redeem all or any portion of the outstanding shares of Series A Preferred Stock, for an amount in cash equal to the then current accrued liquidation preference of such shares (including any accrued and unpaid dividends since the most recent dividend payment date). Prior to April 25, 2027, in connection with the consummation of certain fundamental changes (as more fully described in the Amended and Restated Charter but including, among other things, certain change-in- control transactions and asset sales), the Company will have the right, in its sole discretion, to give notice of election to redeem all or any portion of the outstanding shares of Series A Preferred Stock, for an amount in cash equal to the then current accrued liquidation preference of such shares (including any accrued and unpaid dividends since the most recent dividend payment date) plus a make-whole amount determined by reference to the dividends that would be accrued through April 25, 2027, discounted to the date of redemption on a quarterly basis at the treasury rate on the date of the redemption plus 50 basis points. Any redemption of fewer than all of the outstanding shares of Series A Preferred Stock will be made pro rata in proportion to the value of the shares of Series A Preferred Stock held. No share of Series A Preferred Stock that is converted into common stock prior to the applicable redemption date shall be subject to redemption.
Mandatory Redemption. On April 25, 2032, the Company will be required to redeem and purchase all outstanding shares of Series A Preferred Stock for an amount, in cash, equal to the then current accrued liquidation preference of such shares (including any accrued and unpaid dividends since the most recent dividend payment date), up to but not including April 25, 2032.
Redemption in Connection with Reorganization Events and Fundamental Change Transactions. If the Company undergoes certain fundamental changes (as more fully described in Article IV of the Amended and Restated Charter but including, among other things, certain change-in-control transactions and asset sales), a holder of Series A Preferred Stock may give notice of its election to have us fully redeem all of such holder’s outstanding Series A Preferred Stock, for an amount in cash equal to the then current accrued liquidation preference of such shares (including any accrued and unpaid dividends since the most recent dividend payment date). Such redemption shall not be required if the shares of Series A Preferred Stock are purchased at the abovementioned redemption price (determined by reference to the date upon which such transaction is consummated) in connection with (and no later than the time of consummation of) such fundamental change transaction. If applicable law does not permit us to consummate any such redemption, the Company will be restricted from consummating the applicable fundamental change transaction unless (x) at the closing of the
130
transaction, all of the shares of Series A Preferred Stock are purchased for an amount in cash equal to the abovementioned redemption price (determined by reference to the date upon which such fundamental change occurs) or (y) the Company gives a written notice of the terms and conditions of such transaction, which such notice affords the holders of the Series A Preferred Stock the right, but not the obligation, to elect to engage with us in an alternative transaction on terms that are the same as those of the applicable proposed fundamental change transaction (such right of first refusal described more fully in Article IV of the Amended and Restated Charter).
Voting Rights. The shares of Series A Preferred Stock have no voting rights except as required by Delaware law or with respect to the amendment, alteration or repeal of any provision of the Amended and Restated Charter, whether by merger, consolidation or otherwise, so as to materially and adversely affect any right, preference, privilege or voting powers of the share of Series A Preferred Stock.
Consent Rights. For so long as any shares of Series A Preferred Stock remain outstanding, the Company may not, and shall cause its subsidiaries not to, without the written consent or approval of the holders of Series A Preferred Stock representing not less than 55% of the outstanding value of Series A Preferred Stock (provided that at any time during which there are two or more unaffiliated holders of Series A Preferred Stock, this 55% must include at least two unaffiliated holders of Series A Preferred Stock), (i) create, authorize or issue (by reclassification or otherwise) any equity securities of the Company, including any additional shares of Series A Preferred Stock or other security convertible into or exchangeable for any of the Company’s equity securities, having rights, preferences or privileges ranking senior to the Series A Preferred Stock or pari passu with the Series A Preferred Stock, (ii) amend, modify, restate, repeal or make any other change (by amendment, merger, consolidation, operation of law or otherwise) to any provision of the Company’s or the Company’s subsidiaries’ organizational documents in a manner which adversely alters or changes the rights, preferences or privileges of the Series A Preferred Stock (provided that any issuance of securities junior to the Series A Preferred Stock shall not be deemed to be adverse to the Series A Preferred Stock), (iii) prior to payment in full in cash of the liquidation preference on all outstanding shares of Series A Preferred Stock, effect any dividend or distribution to or redemption of any other shares of the Company’s capital stock or equity securities (other than the shares of Series A Preferred Stock), (iv) amend, modify or waive the terms of the Series A Preferred Stock, (v) effect certain mergers or consolidations or sell all or substantially all of the Company’s and the Company’s subsidiaries’ assets (as more fully described in Article IV of the Amended and Restated Charter) unless the liquidation preference in respect of the Series A Preferred Stock is fully repaid, or in certain circumstances, the Series A Preferred Stock remains outstanding, (vi) consent to the Company’s or any of the Company’s subsidiaries’ liquidation, dissolution or winding up unless, in the case of the Company’s liquidation, dissolution or winding up, the Company shall have delivered to the holders of Series A Preferred Stock not less than 10 business days’ prior written notice of such transaction. The Company also may not, without the prior written consent or approval of the holders of Series A Preferred Stock representing not less than 85% of the outstanding value of Series A Preferred Stock, amend, waive, or modify the Amended and Restated Charter in ways (as more fully described in Article IV of the Amended and Restated Charter) that adversely alter or change the rights, preferences, privileges or obligations of the shares of Series A Preferred Stock. In addition, the Company shall not redeem or otherwise make any dividend or payment on the shares of Series A Preferred Stock other than in cash without the prior written consent or approval of each affected holder of such Series A Preferred Stock.
Warrants
Public Warrants
Each Warrant entitles the registered holder to purchase one share of Common Stock at a price of $11.50 per share, subject to adjustment as discussed below. Pursuant to the Warrant Agreement, a Warrant holder may exercise its Warrants only for a whole number of shares of Common Stock. The Warrants will expire January 24, 2028, at 5:00 p.m., New York City time.
131
We will not be obligated to deliver any shares of Common Stock pursuant to the exercise of a Warrant and will have no obligation to settle such Warrant exercise unless a registration statement under the Securities Act with respect to the shares of Common Stock underlying the Warrants is then effective and a prospectus relating thereto is current, subject to us satisfying our obligations described below with respect to registration, or a valid exemption from registration is available. No Warrant will be exercisable and we will not be obligated to issue a share of Common Stock upon exercise of a Warrant unless the shares of Common Stock issuable upon such Warrant exercise has been registered, qualified or deemed to be exempt under the securities laws of the state of residence of the registered holder of the Warrants. In the event that the conditions in the two immediately preceding sentences are not satisfied with respect to a Warrant, the holder of such Warrant will not be entitled to exercise such Warrant and such Warrant may have no value and expire worthless. In no event will we be required to net cash settle any Warrant.
Pursuant to the Warrant Agreement, we have filed with the SEC a registration statement for the registration, under the Securities Act, of the shares of Common Stock issuable upon exercise of the Warrants, and caused the same to become effective within 60 business days after the Closing, and we have agreed to use our commercially reasonable efforts to maintain the effectiveness of such registration statement and a current prospectus relating to those shares of Common Stock until the Warrants expire or are redeemed, as specified in the Warrant Agreement; provided that if shares of Common Stock are at the time of any exercise of a Warrant not listed on a national securities exchange such that they satisfy the definition of a “covered security” under Section 18(b)(1) of the Securities Act, the Company may, at our option, require holders of Public Warrants who exercise their Warrants to do so on a “cashless basis” in accordance with Section 3(a)(9) of the Securities Act and, in the event the Company so elects, the Company will not be required to file or maintain in effect a registration statement, but it will use its commercially reasonably efforts to register or qualify the shares under applicable blue sky laws to the extent an exemption is not available. Warrant holders may, during any period when the Company will have failed to maintain an effective registration statement, exercise Warrants on a “cashless basis” in accordance with Section 3(a)(9) of the Securities Act or another exemption, but the Company will use its commercially reasonably efforts to register or qualify the shares under applicable blue sky laws to the extent an exemption is not available. In such event, each holder would pay the exercise price by surrendering the Warrants for that number of shares of Common Stock equal to the lesser of (A) the quotient obtained by dividing (x) the product of the number of shares of Common Stock underlying the Warrants, multiplied by the excess of the “fair market value” (defined below) less the exercise price of the Warrants by (y) the fair market value and (B) 0.361. The “fair market value” as used in this paragraph shall mean the volume weighted average price of the shares of Common Stock for the 10 trading days ending on the trading day prior to the date on which the notice of exercise is received by the Warrant Agent.
Redemption of Warrants When the price per Share of Common Stock Equals or Exceeds $18.00.
The Company may redeem the Warrants (except as described herein with respect to the Private Placement Warrants):
| • | in whole and not in part; |
| • | at a price of $0.01 per Warrant; |
| • | upon a minimum of 30 days’ prior written notice of redemption to each Warrant holder; and |
| • | if, and only if, the closing price per share of Common Stock equals or exceeds $18.00 per share (as adjusted for adjustments to the number of shares issuable upon exercise or the exercise price of a Warrant as described under the heading “—Warrants—Public Warrants—Anti- dilution Adjustments”) for any 20 trading days within a 30-trading day period ending three trading days before the Company sends the notice of redemption to the Warrant holders. |
The Company will not redeem the Warrants as described above unless the registration statement under the Securities Act covering the issuance of the shares of Common Stock issuable upon exercise of the Warrants is
132
then effective and a current prospectus relating to those shares of Common Stock is available throughout the 30-day redemption period. If and when the Warrants become redeemable by the Company, the Company may exercise its redemption right even if the Company is unable to register or qualify the underlying securities for sale under all applicable state securities laws.
The Company has established the last of the redemption criterion discussed above to prevent a redemption call unless there is at the time of the call a significant premium to the Warrant exercise price. If the foregoing conditions are satisfied and the Company issues a notice of redemption of the Warrants, each Warrant holder will be entitled to exercise his, her or its Warrant prior to the scheduled redemption date. However, the price per share of Common Stock may fall below the $18.00 redemption trigger price (as adjusted for adjustments to the number of shares issuable upon exercise or the exercise price of a Warrant as described under the heading “—Warrants—Public Warrants—Anti-dilution Adjustments”) as well as the $11.50 (for whole shares) Warrant exercise price after the redemption notice is issued.
Redemption of Warrants When the Price per Share of Common Stock Equals or Exceeds $10.00.
The Company may redeem the outstanding Warrants:
| • | in whole and not in part; |
| • | at $0.10 per Warrant upon a minimum of 30 days’ prior written notice of redemption provided that holders will be able to exercise their Warrants on a cashless basis prior to redemption and receive that number of shares determined by reference to the table below, based on the redemption date and the “fair market value” (as defined below) per share of Common Stock except as otherwise described below; if, and only if, the closing price per share of Common Stock equals or exceeds $10.00 per public share (as adjusted for adjustments to the number of shares issuable upon exercise or the exercise price of a Warrant as described under the heading “—Warrants—Public Warrants—Anti- dilution Adjustments”) for any 20 trading days within the 30-trading day period ending three trading days before the Company sends the notice of redemption to the Warrant holders; and |
| • | if the closing price per share of Common Stock for any 20 trading days within a 30- trading day period ending on the third trading day prior to the date on which the Company sends the notice of redemption to the Warrant holders is less than $18.00 per share (as adjusted for adjustments to the number of shares issuable upon exercise or the exercise price of a Warrant as described under the heading “—Warrants—Public Warrants—Anti-dilution Adjustments”), the Private Placement Warrants must also be concurrently called for redemption on the same terms as the outstanding Public Warrants, as described above. |
Beginning on the date the notice of redemption is given until the Warrants are redeemed or exercised, holders may elect to exercise their Warrants on a cashless basis. The numbers in the table below represent the number of shares of Common Stock that a Warrant holder will receive upon such cashless exercise in connection with a redemption by the Company pursuant to this redemption feature, based on the “fair market value” per share of Common Stock on the corresponding redemption date (assuming holders elect to exercise their Warrants and such Warrants are not redeemed for $0.10 per Warrant), determined for these purposes based on volume weighted average price per share of Common Stock during the 10 trading days immediately following the date on which the notice of redemption is sent to the holders of Warrants, and the number of months that the corresponding redemption date precedes the expiration date of the Warrants, each as set forth in the table below. The Company will provide the Warrant holders with the final fair market value no later than one business day after the 10-trading day period described above ends.
The share prices set forth in the column headings of the table below will be adjusted as of any date on which the number of shares issuable upon exercise of a Warrant or the exercise price of a Warrant is adjusted as set forth under the heading “ —Anti-dilution Adjustments” below. If the number of shares issuable upon exercise of a
133
Warrant is adjusted, the adjusted share prices in the column headings will equal the share prices immediately prior to such adjustment, multiplied by a fraction, the numerator of which is the number of shares deliverable upon exercise of a Warrant immediately prior to such adjustment and the denominator of which is the number of shares deliverable upon exercise of a Warrant as so adjusted. The number of shares in the table below shall be adjusted in the same manner and at the same time as the number of shares issuable upon exercise of a Warrant. If the exercise price of a Warrant is adjusted, (a) in the case of an adjustment pursuant to the fifth paragraph under the heading “—Anti-dilution Adjustments”, the adjusted share prices in the column headings will equal the unadjusted share price multiplied by a fraction, the numerator of which is the higher of the Market Value and the Newly Issued Price as set forth under the heading “ —Anti-dilution Adjustments” and the denominator of which is $10.00 and (b) in the case of an adjustment pursuant to the second paragraph under the heading “ —Anti-dilution Adjustments”, the adjusted share prices in the column headings will equal the unadjusted share price less the decrease in the exercise price of a Warrant pursuant to such exercise price adjustment.
| Redemption date | Fair Market value per share of Common Stock | |||||||||||||||||||||||||||||||||||
| (period to expiration of Warrants) | ≤$10.00 | 11.00 | 12.00 | 13.00 | 14.00 | 15.00 | 16.00 | 17.00 | ≥18.00 | |||||||||||||||||||||||||||
60 months | 0.261 | 0.281 | 0.297 | 0.311 | 0.324 | 0.337 | 0.348 | 0.358 | 0.361 | |||||||||||||||||||||||||||
57 months | 0.257 | 0.277 | 0.294 | 0.310 | 0.324 | 0.337 | 0.348 | 0.358 | 0.361 | |||||||||||||||||||||||||||
54 months | 0.252 | 0.272 | 0.291 | 0.307 | 0.322 | 0.335 | 0.347 | 0.357 | 0.361 | |||||||||||||||||||||||||||
51 months | 0.246 | 0.268 | 0.287 | 0.304 | 0.320 | 0.333 | 0.346 | 0.357 | 0.361 | |||||||||||||||||||||||||||
48 months | 0.241 | 0.263 | 0.283 | 0.301 | 0.317 | 0.332 | 0.344 | 0.356 | 0.361 | |||||||||||||||||||||||||||
45 months | 0.235 | 0.258 | 0.279 | 0.298 | 0.315 | 0.330 | 0.343 | 0.356 | 0.361 | |||||||||||||||||||||||||||
42 months | 0.228 | 0.252 | 0.274 | 0.294 | 0.312 | 0.328 | 0.342 | 0.355 | 0.361 | |||||||||||||||||||||||||||
39 months | 0.221 | 0.246 | 0.269 | 0.290 | 0.309 | 0.325 | 0.340 | 0.354 | 0.361 | |||||||||||||||||||||||||||
36 months | 0.213 | 0.239 | 0.263 | 0.285 | 0.305 | 0.323 | 0.339 | 0.353 | 0.361 | |||||||||||||||||||||||||||
33 months | 0.205 | 0.232 | 0.257 | 0.280 | 0.301 | 0.320 | 0.337 | 0.352 | 0.361 | |||||||||||||||||||||||||||
30 months | 0.196 | 0.224 | 0.250 | 0.274 | 0.297 | 0.316 | 0.335 | 0.351 | 0.361 | |||||||||||||||||||||||||||
27 months | 0.185 | 0.214 | 0.242 | 0.268 | 0.291 | 0.313 | 0.332 | 0.350 | 0.361 | |||||||||||||||||||||||||||
24 months | 0.173 | 0.204 | 0.233 | 0.260 | 0.285 | 0.308 | 0.329 | 0.348 | 0.361 | |||||||||||||||||||||||||||
21 months | 0.161 | 0.193 | 0.223 | 0.252 | 0.279 | 0.304 | 0.326 | 0.347 | 0.361 | |||||||||||||||||||||||||||
18 months | 0.146 | 0.179 | 0.211 | 0.242 | 0.271 | 0.298 | 0.322 | 0.345 | 0.361 | |||||||||||||||||||||||||||
15 months | 0.130 | 0.164 | 0.197 | 0.230 | 0.262 | 0.291 | 0.317 | 0.342 | 0.361 | |||||||||||||||||||||||||||
12 months | 0.111 | 0.146 | 0.181 | 0.216 | 0.250 | 0.282 | 0.312 | 0.339 | 0.361 | |||||||||||||||||||||||||||
9 months | 0.090 | 0.125 | 0.162 | 0.199 | 0.237 | 0.272 | 0.305 | 0.336 | 0.361 | |||||||||||||||||||||||||||
6 months | 0.065 | 0.099 | 0.137 | 0.178 | 0.219 | 0.259 | 0.296 | 0.331 | 0.361 | |||||||||||||||||||||||||||
3 months | 0.034 | 0.065 | 0.104 | 0.150 | 0.197 | 0.243 | 0.286 | 0.326 | 0.361 | |||||||||||||||||||||||||||
0 months | — | — | 0.042 | 0.115 | 0.179 | 0.233 | 0.281 | 0.323 | 0.361 | |||||||||||||||||||||||||||
The exact fair market value and redemption date may not be set forth in the table above, in which case, if the fair market value is between two values in the table or the redemption date is between two redemption dates in the table, the number of shares of Common Stock to be issued for each Warrant exercised will be determined by a straight-line interpolation between the number of shares set forth for the higher and lower fair market values and the earlier and later redemption dates, as applicable, based on a 365 or 366-day year, as applicable. For example, if the volume weighted average price per share of Common Stock during the 10 trading days immediately following the date on which the notice of redemption is sent to the holders of the Warrants is $11.00 per share, and at such time there are 57 months until the expiration of the Warrants, holders may choose to, in connection with this redemption feature, exercise their Warrants for 0.277 shares of Common Stock for each whole Warrant. For an example where the exact fair market value and redemption date are not as set forth in the table above, if the volume weighted average price per share of Common Stock during the 10 trading days immediately following the date on which the notice of redemption is sent to the holders of the Warrants is $13.50 per share, and at such time there are 38 months until the expiration of the Warrants, holders may choose to, in connection with this redemption feature, exercise their Warrants for 0.298 shares of Common Stock for each whole Warrant. In no event will the Warrants be exercisable on a cashless basis in connection with this
134
redemption feature for more than 0.361 shares of Common Stock per Warrant (subject to adjustment). Finally, as reflected in the table above, if the Warrants are out of the money and about to expire, they cannot be exercised on a cashless basis in connection with a redemption by the Company pursuant to this redemption feature, since they will not be exercisable for any shares of Common Stock.
This redemption feature is structured to allow for all of the outstanding Warrants to be redeemed when the shares of Common Stock are trading at or above $10.00 per public share, which may be at a time when the trading price per share of Common Stock is below the exercise price of the Warrants.
As stated above, the Company can redeem the Warrants when the shares of Common Stock are trading at a price starting at $10.00 per share, which is below the exercise price of $11.50 per share, because it will provide certainty with respect to the capital structure and cash position while providing Warrant holders with the opportunity to exercise their Warrants on a cashless basis for the applicable number of shares. If the Company chooses to redeem the Warrants when the shares of Common Stock are trading at a price below the exercise price of the Warrants, this could result in the Warrant holders receiving fewer shares of Common Stock than they would have received if they had chosen to wait to exercise their Warrants for shares of Common Stock if and when such shares of Common Stock were trading at a price higher than the exercise price of $11.50 per share.
No fractional shares of Common Stock will be issued upon exercise. If, upon exercise, a holder would be entitled to receive a fractional interest in a share, the Company will round down to the nearest whole number of the number of shares of the Company’s Common Stock to be issued to the holder. If, at the time of redemption, the Warrants are exercisable for a security other than shares of the Company’s Common Stock pursuant to the Warrant Agreement, the Warrants may be exercised for such security. At such time as the Warrants become exercisable for a security other than shares of the Company’s Common Stock, the Company (or surviving company) will use its commercially reasonable efforts to register under the Securities Act the security issuable upon the exercise of the Warrants.
Redemption Procedures
A holder of a Warrant may notify the Company in writing in the event it elects to be subject to a requirement that such holder will not have the right to exercise such Warrant, to the extent that after giving effect to such exercise, such person (together with such person’s affiliates), to the Warrant Agent’s actual knowledge, would beneficially own in excess of 9.8% (or such other amount as a holder may specify) of the shares of Common Stock issued and outstanding immediately after giving effect to such exercise.
Anti-dilution Adjustments
If the number of outstanding shares of Common Stock is increased by a capitalization or share dividend payable in shares of Common Stock, or by a split-up of ordinary shares or other similar event, then, on the effective date of such capitalization or share dividend, split-up or similar event, the number of shares of Common Stock issuable on exercise of each Warrant will be increased in proportion to such increase in the outstanding shares of Common Stock. A rights offering made to all or substantially all holders of shares of Common Stock entitling holders to purchase shares of Common Stock at a price less than the “historical fair market value” (as defined below) will be deemed a share dividend of a number of shares of Common Stock equal to the product of (i) the number of shares of Common Stock actually sold in such rights offering (or issuable under any other equity securities sold in such rights offering that are convertible into or exercisable for shares of Common Stock) and (ii) one minus the quotient of (x) the price per share of Common Stock paid in such rights offering and (y) the historical fair market value. For these purposes, (i) if the rights offering is for securities convertible into or exercisable for shares of Common Stock, in determining the price payable per share of Common Stock, there will be taken into account any consideration received for such rights, as well as any additional amount payable upon exercise or conversion and (ii) “historical fair market value” means the volume weighted average price per share of Common Stock as reported during the 10 trading day period ending on the trading day prior to the first date on
135
which the shares of Common Stock trade on the applicable exchange or in the applicable market, regular way, without the right to receive such rights.
In addition, if the Company, at any time while the Warrants are outstanding and unexpired, pays a dividend or makes a distribution in cash, securities or other assets to the holders of shares of Common Stock on account of such shares (or other securities into which the Warrants are convertible), other than (a) as described above or (b) any cash dividends or cash distributions which, when combined on a per share basis with all other cash dividends and cash distributions paid on the shares during the 365-day period ending on the date of declaration of such dividend or distribution does not exceed $0.50 (as adjusted to appropriately reflect any other adjustments and excluding cash dividends or cash distributions that resulted in an adjustment to the exercise price or to the number of shares issuable on exercise of each Warrant) but only with respect to the amount of the aggregate cash dividends or cash distributions equal to or less than $0.50 per share, then the Warrant exercise price will be decreased, effective immediately after the effective date of such event, by the amount of cash and/or the fair market value of any securities or other assets paid on each share in respect of such event.
If the number of outstanding share of Common Stock is decreased by a consolidation, combination, reverse share sub-division or reclassification of the shares of Common Stock or other similar event, then, on the effective date of such consolidation, combination, reverse share sub-division, reclassification or similar event, the number of shares of Common Stock issuable on exercise of each Warrant will be decreased in proportion to such decrease in outstanding shares of Common Stock.
Whenever the number of shares of Common Stock purchasable upon the exercise of the Warrants is adjusted, as described above, the Warrant exercise price will be adjusted by multiplying the Warrant exercise price immediately prior to such adjustment by a fraction (x) the numerator of which will be the number of shares of Common Stock purchasable upon the exercise of the Warrants immediately prior to such adjustment and (y) the denominator of which will be the number of shares of Common Stock so purchasable immediately thereafter.
In case of any reclassification or reorganization of the outstanding shares of Common Stock (other than those described above or that solely affects the par value of such shares of Common Stock), or in the case of any merger or consolidation of the Company with or into another corporation (other than a consolidation or merger in which the Company is the continuing corporation and that does not result in any reclassification or reorganization of our outstanding shares of Common Stock), or in the case of any sale or conveyance to another corporation or entity of the assets or other property of the Company as an entirety or substantially as an entirety in connection with which the Company is dissolved, the holders of the Warrants will thereafter have the right to purchase and receive, upon the basis and upon the terms and conditions specified in the Warrants and in lieu of the shares of Common Stock immediately theretofore purchasable and receivable upon the exercise of the rights represented thereby, the kind and amount of shares of Common Stock or other securities or property (including cash) receivable upon such reclassification, reorganization, merger or consolidation, or upon a dissolution following any such sale or transfer, that the holder of the Warrants would have received if such holder had exercised their Warrants immediately prior to such event. However, if such holders were entitled to exercise a right of election as to the kind or amount of securities, cash or other assets receivable upon such consolidation or merger, then the kind and amount of securities, cash or other assets for which each Warrant will become exercisable will be deemed to be the weighted average of the kind and amount received per share by such holders in such consolidation or merger that affirmatively make such election, and if a tender, exchange or redemption offer has been made to and accepted by such holders under circumstances in which, upon completion of such tender or exchange offer, the maker thereof, together with members of any group (within the meaning of Rule 13d-5(b)(1) under the Exchange Act) of which such maker is a part, and together with any affiliate or associate of such maker (within the meaning of Rule 12b-2 under the Exchange Act) and any members of any such group of which any such affiliate or associate is a part, own beneficially (within the meaning of Rule 13d-3 under the Exchange Act) more than 50% of the issued and outstanding shares of Common Stock, the holder of a Warrant will be entitled to receive the highest amount of cash, securities or other property to which such holder would actually have been
136
entitled as a shareholder if such Warrant holder had exercised the Warrant prior to the expiration of such tender or exchange offer, accepted such offer and all of the shares of Common Stock held by such holder had been purchased pursuant to such tender or exchange offer, subject to adjustment (from and after the consummation of such tender or exchange offer) as nearly equivalent as possible to the adjustments provided for in the Warrant Agreement. If less than 70% of the consideration receivable by the holders of shares of Common Stock in such a transaction is payable in the form of shares of Common Stock in the successor entity that is listed for trading on a national securities exchange or is quoted in an established over-the-counter market, or is to be so listed for trading or quoted immediately following such event, and if the registered holder of the Warrant properly exercises the Warrant within thirty days following public disclosure of such transaction, the Warrant exercise price will be reduced as specified in the Warrant Agreement based on the Black-Scholes value (as defined in the Warrant Agreement) of the Warrant. The purpose of such exercise price reduction is to provide additional value to holders of the Warrants when an extraordinary transaction occurs during the exercise period of the Warrants pursuant to which the holders of the Warrants otherwise do not receive the full potential value of the Warrants. The purpose of such exercise price reduction is to provide additional value to holders of the Warrants when an extraordinary transaction occurs during the exercise period of the Warrants pursuant to which the holders of the Warrants otherwise do not receive the full potential value of the Warrants.
The Warrants were issued in registered form under the Warrant Agreement. The Warrant Agreement provides that the terms of the Warrants may be amended without the consent of any holder for the purpose of (i) curing any ambiguity or correct any mistake, including to conform the provisions of the Warrant Agreement to the description of the terms of the Warrants and the Warrant Agreement set forth in the prospectus filed by JCIC with the SEC on January 21, 2021, or defective provision (ii) amending the provisions relating to cash dividends on shares of Common Stock as contemplated by and in accordance with the Warrant Agreement or (iii) adding or changing any provisions with respect to matters or questions arising under the Warrant Agreement as the parties to the Warrant Agreement may deem necessary or desirable and that the parties deem to not adversely affect the rights of the registered holders of the Warrants, provided that the approval by the holders of at least 65% of the then-outstanding Public Warrants is required to make any change that adversely affects the interests of the registered holders. You should review a copy of the Warrant Agreement, which has been filed as an exhibit to our 10-K, for a complete description of the terms and conditions applicable to the Warrants.
The Warrant holders do not have the rights or privileges of holders of shares of Common Stock and any voting rights until they exercise their Warrants and receive shares of Common Stock. After the issuance of the shares of Common Stock upon exercise of the Warrants, each holder will be entitled to one vote for each share held of record on all matters to be voted on by stockholder.
Private Placement Warrants
Except as described below, the Private Placement Warrants have terms and provisions that are identical to those of the Public Warrants. JCIC Sponsor, or its permitted transferees, has the option to exercise the Private Placement Warrants on a cashless basis. If the Private Placement Warrants are held by holders other than JCIC Sponsor or its permitted transferees, the Private Placement Warrants will be redeemable by the Company in all redemption scenarios and exercisable by the holders on the same basis as the Public Warrants. The Private Placement Warrants are also redeemable in accordance with the Warrant Agreement (and must be redeemed if the Public Warrants are being redeemed) if the Reference Value (defined above) equals or exceeds $10.00 per share and does not equal or exceed $18.00 per share.
Except as described above under the heading “—Public Shareholders’ Warrants—Redemption of warrants when the price per Share of Common Stock equals or exceeds $10.00,” if holders of the Private Placement Warrants elect to exercise them on a cashless basis, they would pay the exercise price by surrendering his, her or its Warrants for that number of shares of Common Stock equal to the quotient obtained by dividing (x) the product of the number of shares of Common Stock underlying the Warrants, multiplied by the excess of the “Sponsor fair market value” (defined below) over the exercise price of the Warrants by (y) JCIC Sponsor fair
137
market value. For these purposes, the “Sponsor fair market value” shall mean the average reported closing price per share of Common Stock for the 10 trading days ending on the third trading day prior to the date on which the notice of Warrant exercise is sent to the Warrant Agent.
Any amendment to the terms of the Private Placement Warrants or any provision of the Warrant Agreement with respect to the Private Placement Warrants will require a vote of holders of at least 65% of the number of the then outstanding Private Placement Warrants.
Board of Directors
The Company’s business and affairs is managed under the direction of its board of directors. Under the Amended and Restated Charter, the Board is divided into three classes, designated as Class I, Class II and Class III, with each class consisting of three (3) directors. Class I directors will hold office for a term expiring at the 2026 annual meeting of stockholders; Class II directors will hold office for a term expiring at the 2024 annual meeting of stockholders; and Class III directors will hold office for a term expiring at the 2025 annual meeting of stockholders. At each succeeding annual meeting of the stockholders of the Company, the successors to the class of directors whose term expires at that meeting will be elected by plurality vote of all votes cast at such meeting to hold office for a term expiring at the annual meeting of stockholders held in the third year following the year of their election.
Pursuant to the Stockholders Agreement, the BTO Stockholders, collectively, have the right, but not the obligation, to nominate for election to the Board up to two (2) directors, for so long as the BTO Entities (as defined in the Stockholders Agreement) collectively beneficially own (directly or indirectly) at least 10% of the outstanding Stock (as defined in the Stockholders Agreement); and (ii) one (1) director, for so long as the BTO Entities collectively beneficially own (directly or indirectly) less than 10% of the outstanding Stock, but at least 33% of the shares of Stock held by the BTO Entities as of the Closing. In addition, for so long as the BTO Entities have such nomination rights, the Board will use reasonable best efforts to cause any committee of the Board to include in its membership at least one director nominated by the BTO Stockholders provided that such individual satisfies all applicable SEC and stock exchange requirements. In the event that a vacancy is created at any time by the death, disqualification, resignation or removal of a director nominated by BTO Stockholders, the BTO Stockholders, collectively, shall have the right to designate a replacement to fill such vacancy. Ms. Hayes and Mr. Hirsch are the current BTO Stockholders director designees. See the section of this prospectus entitled “Management – Corporate Governance – Stockholders Agreement” for additional information.
Committees of the Board of Directors
Pursuant to the Amended and Restated Bylaws, the Board may establish one or more committees to which may be delegated any or all of the powers and duties of the Board to the full extent permitted by law. The Board has established and maintained an audit committee, a governance committee and a compensation committee, and may establish such other committees as it determines from time to time. See the section of this prospectus entitled “Management.”
Pursuant to the Stockholders Agreement, Bridger Element LLC and its former equityholders, to the extent they collectively beneficially own (directly or indirectly) at least 10% of the outstanding Stock have the right, but not the obligation, to nominate the Chairperson of the Compensation and Nominating and Corporate Governance Committees of the Board, subject to satisfaction of applicable SEC and stock exchange requirements.
Limitations on Non-Citizens
To assist with the Company’s compliance with Subtitle VII of Title 49 of the United States Code, as the same may be amended from time to time, Article X of the Amended and Restated Charter and Article V of the
138
Amended and Restated Bylaws contain provisions that limit Non-Citizens to not more than (x) 24.9% of the aggregate votes of all the Company’s outstanding voting securities or (y) 49.0% of the aggregate number of the Company’s outstanding equity securities and prohibit certain voting right and transfers of the Company’s securities to ensure that ownership by Non-Citizens will not exceed these amounts. Additionally, such equity securities owned by Non-Citizens may not be voted unless such shares are registered on the separate stock record maintained by the Company or any transfer agent (on behalf of the Company) for the registration of the Company’s equity securities held by Non-Citizens.
Pursuant to the Amended and Restated Bylaws, at no time shall the number of Non-Citizens who serve as officers or director, respectively, of the Company exceed the limitations provided under Section 40102(a)(15) of Title 49 of the United States Code (which, as of the effective date of the Amended and Restated Bylaws and for informational purposes only, is one-third (1/3) of the total number of officers or director, respectively, then holding office).
“Non-Citizen” means persons or entities who are not “citizens of the United States” as defined in Section 40102(a)(15) under Subtitle VII of Title 49 of the United States Code, as the same may be amended from time to time.
Amendment of Our Charter or Bylaws
The DGCL generally provides that the affirmative vote of a majority of the outstanding shares entitled to vote on amendments to a corporation’s certificate of incorporation or bylaws is required to approve such amendment, unless a corporation’s certificate of incorporation or bylaws, as applicable, imposes a higher voting standard.
The affirmative vote of the holders of at least 66 2/3% of the voting power of all then-outstanding Company Common Stock entitled to vote generally in the election of directors, voting together as a single class, is required to adopt, amend or repeal the Amended and Restated Bylaws and the provisions in the Amended and Restated Charter related to directors, indemnification and limitation of liability on directors and officers, Bylaw amendments, special stockholder meetings and no action by written consent of the stockholders, corporate opportunities waiver, forum selection and amendments to the Charter.
Anti-Takeover Effects of Delaware Law, the Amended and Restated Charter and the Amended and Restated Bylaws
Some provisions of the DGCL, the Amended and Restated Charter and the Amended and Restated Bylaws contain provisions that could make the following transactions more difficult: an acquisition the Company by means of a tender offer; an acquisition of the Company by means of a proxy contest or otherwise; or the removal of the Company’s incumbent officers and directors. It is possible that these provisions could make it more difficult to accomplish or could deter transactions that stockholders may otherwise consider to be in their best interest or in the Company’s best interests, including transactions which provide for payment of a premium over the market price for the Company’s shares.
Stockholder Meetings
The Amended and Restated Bylaws provide that a special meeting of stockholders may be called only by the Chairperson of the Board, chief executive officer or the Board.
Requirements for Advance Notification of Stockholder Nominations and Proposals
The Amended and Restated Bylaws establish advance notice procedures with respect to stockholder proposals to be brought before a stockholder meeting and the nomination of candidates for election as directors, other than nominations made by or at the direction of the Board or a committee of Board.
139
Elimination of Stockholder Action by Written Consent
The Amended and Restated Bylaws do not permit stockholders to act by written consent without a meeting.
Staggered Board
The Board is divided into three (3) classes. Except for the directors first elected as Class I directors and Class II directors, the directors in each class serve for a three-year term, one class being elected each year by the Company’s stockholders. See the section of this prospectus entitled “Management” for additional information. This system of electing and removing directors may tend to discourage a third-party from making a tender offer or otherwise attempting to obtain control of the Company, because it generally makes it more difficult for stockholders to replace a majority of the directors.
Removal of Directors
The Amended and Restated Charter provides that no member of the Board may be removed from office by the Company’s stockholders except for cause and, in addition to any other vote required by law, upon the approval of at least a majority of the total voting power of all then-outstanding shares of capital stock then entitled to vote in the election of directors.
Stockholders Not Entitled to Cumulative Voting
The Amended and Restated Charter does not permit stockholders to cumulate their votes in the election of directors. Accordingly, the holders of a majority of the outstanding shares of Common Stock entitled to vote in any election of directors can elect all of the directors standing for election, if they choose, other than any directors that holders of our preferred stock may be entitled to elect.
Delaware Anti-Takeover Statute
The Amended and Restated Charter provides that the Company is not governed by Section 203 of the DGCL which, in the absence of such provisions, would have imposed additional requirements regarding mergers and other business combinations.
However, the Amended and Restated Charter includes a provision that restricts the Company from engaging in any business combination with an interested stockholder for three (3) years following the date that person becomes an interested stockholder. Such restrictions do not apply to any business combination between JCIC Sponsor, the BTO Stockholders, Banc of America Strategic Investments Corporation, JPMorgan Chase Funding Inc., Bridger Element LLC, Mr. McAndrew Rudisill, Mr. Timothy Sheehy and Mr. Matthew Sheehy and any successors or affiliate thereof or their direct and indirect transferees, on the one hand, and us, on the other.
The Company would be able to enter into a business combination with an interested stockholder if:
(a) before that person became an interested stockholder, the Board approved the business combination or the transaction in which the interested stockholder became an interested stockholder;
(b) upon consummation of the transaction that resulted in the stockholder becoming an interested stockholder, the interested stockholder owned at least 85% of the voting stock outstanding at the time the transaction commenced, excluding for purposes of determining the voting stock outstanding (but not the outstanding voting stock owned by the interested stockholder) those shares owned by (i) persons who are directors and also officers and (ii) employee stock plans in which employee participants do not have the right to determine confidentially whether shares held subject to the plan will be tendered in a tender or exchange offer;
140
(c) at or subsequent to such time, the business combination is approved by the Board and authorized at an annual or special meeting of stockholders, and not by written consent, by the affirmative vote of at least 66 2/3% of the outstanding voting stock of the Company that is not owned by the interested stockholder; or
(d) the stockholder became an interested stockholder inadvertently and (i) as soon as practicable divested itself of ownership of sufficient shares so that the stockholder ceased to be an interested stockholder and (ii) was not, at any time within the three-year period immediately prior to a business combination between the Company and such stockholder, an interested stockholder but for the inadvertent acquisition of ownership.
In general, a “business combination” is defined to include mergers, asset sales and other transactions resulting in financial benefit to a stockholder and an “interested stockholder” is any person who, together with affiliates and associates, is the owner of 15% or more of the Company’s outstanding voting stock or is the Company’s affiliate or associate and was the owner of 15% or more of the Company’s outstanding voting stock at any time within the three-year period immediately before the date of determination. Under the Amended and Restated Charter, an “interested stockholder” does not include JCIC Sponsor, the BTO Stockholders, Banc of America Strategic Investments Corporation, JPMorgan Chase Funding Inc., Bridger Element LLC, Mr. McAndrew Rudisill, Mr. Timothy Sheehy and Mr. Matthew Sheehy and any successors or affiliate thereof or their direct and indirect transferees.
This provision of the Amended and Restated Charter could prohibit or delay mergers or other takeover or change in control attempts and, accordingly, may discourage attempts to acquire the Company even though such a transaction may offer the Company’s stockholders the opportunity to sell their stock at a price above the prevailing market price. The existence of this provision may have an anti-takeover effect with respect to transactions not approved in advance by the Board.
Exclusive Forum
The Amended and Restated Charter provides that unless a majority of the Board, acting on behalf of the Company, consents in writing to the selection of an alternative forum (which consent may be given at any time, including during the pendency of litigation), the Court of Chancery of the State of Delaware (or, if the Court of Chancery does not have jurisdiction, another state court located within the State of Delaware or, if no court located within the State of Delaware has jurisdiction, the federal district court for the District of Delaware), to the fullest extent permitted by law, shall be the sole and exclusive forum for (i) any derivative action or proceeding brought on behalf of the Company, (ii) any action asserting a claim of breach of a fiduciary duty owed by any current or former director, officer or other employee of the Company to the Company or the Company’s stockholders, (iii) any action asserting a claim against the Company or any of its directors, officers or other employees arising pursuant to any provision of the DGCL, the Amended and Restated Charter or the Amended and Restated Bylaws (in each case, as may be amended from time to time), (iv) any action asserting a claim against the Company or any of its directors, officers or other employees governed by the internal affairs doctrine of the State of Delaware or (v) any other action asserting an “internal corporate claim,” as defined in Section 115 of the DGCL, in all cases subject to the court’s having personal jurisdiction over all indispensable parties named as defendants. Subject to the preceding provisions and unless a majority of the Board, acting on behalf of the Company, consents in writing to the selection of an alternative forum (which consent may be given at any time, including during the pendency of litigation), the federal district courts of the United States of America, to the fullest extent permitted by law, shall be the sole and exclusive forum for the resolution of any action asserting a cause of action arising under the Securities Act.
Limitations on Liability and Indemnification of Officers and Directors
The DGCL authorizes corporations to limit or eliminate the personal liability of directors and stockholders of corporations for monetary damages for breaches of directors’ fiduciary duties, subject to certain exceptions. The Amended and Restated Charter includes a provision that eliminates, to the fullest extent permitted by the DGCL (as currently in effect or as it may in the future be amended), the personal liability of the Company’s directors for damages for any breach of fiduciary duty as a director.
141
Dissenters’ Rights of Appraisal and Payment
Under the DGCL, with certain exceptions, the Company’s stockholders will have appraisal rights in connection with a merger or consolidation of the Company. Pursuant to the DGCL, stockholders who properly demand and perfect appraisal rights in connection with such merger or consolidation will have the right to receive payment of the fair value of their shares as determined by the Delaware Court of Chancery.
Stockholders’ Derivative Actions
Under the DGCL, any of the Company’s stockholders may bring an action in the Company’s name to procure a judgment in the Company’s favor, also known as a derivative action, provided that the stockholder bringing the action is a holder of the Company’s shares at the time of the transaction to which the action relates or such stockholder’s stock thereafter devolved by operation of law.
Transfer Agent and Warrant Agent
Continental Stock Transfer & Trust Company is the transfer agent for our Common Stock and the Warrant Agent for our Warrants.
Listing of our Common Stock and our Warrants
Shares of our Common Stock and our Warrants are listed on Nasdaq under the symbols “BAER” and “BAERW,” respectively.
142
MATERIAL UNITED STATES FEDERAL INCOME TAX CONSIDERATIONS FOR HOLDERS
The following discussion is a summary of the U.S. federal income tax considerations generally applicable to the ownership and disposition of our Common Stock. This summary is based upon provisions of the United States Internal Revenue Code of 1986, as amended (the “Code”), United States Treasury regulations promulgated thereunder, rulings, judicial decisions, published positions of the Internal Revenue Service (the “IRS”) and other applicable authorities, as of the date hereof. Those authorities are subject to different interpretations and may be changed, perhaps retroactively, so as to result in United States federal income tax consequences different from those summarized below. This summary does not discuss all aspects of U.S. federal income taxation that may be important to particular investors in light of their individual circumstances, including investors subject to special tax rules (e.g., financial institutions, insurance companies, traders or broker-dealers, tax-exempt organizations (including private foundations), governmental organizations, foreign pension funds, tax qualified retirement plans, taxpayers that have elected mark-to-market accounting, accrual-method taxpayers subject to special tax accounting rules under Section 451(b) of the Code, persons subject to the alternative minimum tax, partnerships or other pass-through entities for United States federal income tax purposes (or an investor in such pass-through entities), S corporations, regulated investment companies, real estate investment trusts, passive foreign investment companies, controlled foreign corporations, investors that will hold Common Stock as part of a straddle, hedge, conversion, or other integrated transaction for U.S. federal income tax purposes, former citizens or long-term residents of the United States or U.S. Holders (as defined below) that have a functional currency other than the U.S. dollar), all of whom may be subject to tax rules that differ materially from those summarized below. In addition, this summary does not discuss other U.S. federal tax consequences (e.g., estate or gift tax), any state, local, or non-U.S. tax considerations or the Medicare tax. In addition, this summary is limited to investors that will hold our securities as “capital assets” (generally, property held for investment) under the Code. No ruling from the IRS has been or will be sought regarding any matter discussed herein. No assurance can be given that the IRS would not assert, or that a court would not sustain a position contrary to any of the tax aspects set forth below.
For purposes of this summary, a “U.S. Holder” is a beneficial holder of securities who or that, for U.S. federal income tax purposes is:
| • | an individual who is a United States citizen or resident of the United States; |
| • | a corporation or other entity treated as a corporation for United States federal income tax purposes created in, or organized under the law of, the United States or any state or political subdivision thereof; |
| • | an estate the income of which is includible in gross income for United States federal income tax purposes regardless of its source; or |
| • | a trust (A) the administration of which is subject to the primary supervision of a United States court and which has one or more United States persons (within the meaning of the Code) who have the authority to control all substantial decisions of the trust or (B) that has in effect a valid election under applicable Treasury regulations to be treated as a United States person. |
A “non-U.S. Holder” is a beneficial holder of securities that is neither a U.S. Holder nor a partnership for U.S. federal income tax purposes.
If a partnership (including an entity or arrangement treated as a partnership for U.S. federal income tax purposes) holds our securities, the tax treatment of a partner, member or other beneficial owner in such partnership will generally depend upon the status of the partner, member or other beneficial owner, the activities of the partnership and certain determinations made at the partner, member or other beneficial owner level. If you are a partner, member or other beneficial owner of a partnership holding our securities, you are urged to consult your tax advisor regarding the tax consequences of the ownership and disposition of our securities.
THIS DISCUSSION OF U.S. FEDERAL INCOME TAX CONSIDERATIONS IS FOR GENERAL INFORMATION PURPOSES ONLY AND IS NOT TAX ADVICE. PROSPECTIVE HOLDERS SHOULD
143
CONSULT THEIR TAX ADVISORS CONCERNING THE U.S. FEDERAL INCOME TAX CONSEQUENCES TO THEM OF OWNING AND DISPOSING OF OUR SECURITIES, AS WELL AS THE APPLICATION OF ANY, STATE, LOCAL AND NON-U.S. INCOME, ESTATE AND OTHER TAX CONSIDERATIONS. IN ADDITION, PROSPECTIVE HOLDERS SHOULD CONSULT WITH THEIR TAX ADVISORS WITH RESPECT TO POTENTIAL CHANGES IN UNITED STATES FEDERAL TAX LAW AS WELL AS POTENTIAL CHANGES IN STATE, LOCAL OR NON-U.S. TAX LAWS.
U.S. Holders
Taxation of Distributions
If we pay distributions to U.S. Holders of shares of our Common Stock, such distributions will constitute dividends for U.S. federal income tax purposes to the extent paid from our current or accumulated earnings and profits, as determined under U.S. federal income tax principles. Distributions in excess of current and accumulated earnings and profits will constitute a return of capital that will be applied against and reduce (but not below zero) the U.S. Holder’s adjusted tax basis in our Common Stock. Any remaining excess will be treated as gain realized on the sale or other disposition of the Common Stock and will be treated as described under the section of this prospectus entitled “— Gain or Loss on Sale, Taxable Exchange or Other Taxable Disposition of Common Stock” below.
Dividends we pay to a U.S. Holder that is a taxable corporation generally will qualify for the dividends received deduction if the requisite holding period is satisfied. With certain exceptions (including dividends treated as investment income for purposes of investment interest deduction limitations), and provided certain holding period requirements are met, dividends we pay to a non-corporate U.S. Holder will generally constitute “qualified dividends” that will be subject to tax at the maximum tax rate accorded to long-term capital gains.
Gain or Loss on Sale, Taxable Exchange or Other Taxable Disposition of Common Stock
A U.S. Holder will recognize gain or loss on the sale, taxable exchange or other taxable disposition of our Common Stock. Any such gain or loss will be capital gain or loss, and will be long-term capital gain or loss if the U.S. Holder’s holding period for the Common Stock so disposed of exceeds one year. The amount of gain or loss recognized will generally be equal to the difference between (1) the sum of the amount of cash and the fair market value of any property received in such disposition and (2) the U.S. Holder’s adjusted tax basis in its Common Stock so disposed of. A U.S. Holder’s adjusted tax basis in its Common Stock will generally equal the U.S. Holder’s acquisition cost less any prior distributions treated as a return of capital. The deductibility of capital losses is subject to limitations.
Non-U.S. Holders
Taxation of Distributions
Subject to the discussions below regarding the Foreign Account Tax Compliance Act and backup withholding, in general, any distributions we make to a non-U.S. Holder of shares of our Common Stock, to the extent paid out of our current or accumulated earnings and profits (as determined under U.S. federal income tax principles), will constitute dividends for U.S. federal income tax purposes and, provided such dividends are not effectively connected with the non-U.S. Holder’s conduct of a trade or business within the United States (or, if a tax treaty applies, are not attributable to a U.S. permanent establishment or fixed base maintained by the non-U.S. Holder), we will be required to withhold tax from the gross amount of the dividend at a rate of 30%, unless such non-U.S. Holder is eligible for a reduced rate of withholding tax under an applicable income tax treaty and provides proper certification of its eligibility for such reduced rate (usually on an IRS Form W-8BEN or W-8BEN-E, as applicable). Any distribution not constituting a dividend paid to non-U.S. Holders of our Common Stock will be treated first as reducing (but not below zero) the non-U.S. Holder’s adjusted tax basis in its shares of our Common Stock and, to the extent such distribution exceeds the non-U.S. Holder’s adjusted tax
144
basis, as gain realized from the sale or other disposition of the Common Stock, which will be treated as described under the section of this prospectus entitled “— Gain on Sale, Taxable Exchange or Other Taxable Disposition of Common Stock” below.
Dividends we pay to a non-U.S. Holder that are effectively connected with such non-U.S. Holder’s conduct of a trade or business within the United States (or if a tax treaty applies are attributable to a U.S. permanent establishment or fixed base maintained by the non-U.S. Holder) will generally not be subject to U.S. withholding tax, provided such non-U.S. Holder complies with certain certification and disclosure requirements (usually by providing an IRS Form W-8ECI). Instead, such dividends will generally be subject to U.S. federal income tax, net of certain deductions, at the same graduated individual or corporate rates applicable to U.S. Holders. If the non-U.S. Holder is a corporation, dividends that are effectively connected income may also be subject to a “branch profits tax” at a rate of 30% (or such lower rate as may be specified by an applicable income tax treaty).
Gain on Sale, Exchange or Other Taxable Disposition of Common Stock
Subject to the discussions below regarding the Foreign Account Tax Compliance Act and backup withholding, a non-U.S. Holder will generally not be subject to U.S. federal income or withholding tax in respect of gain recognized on a sale, taxable exchange or other taxable disposition of our Common Stock unless:
| • | the gain is effectively connected with the conduct of a trade or business by the non-U.S. Holder within the United States (and, if an applicable tax treaty so requires, is attributable to a U.S. permanent establishment or fixed base maintained by the non-U.S. Holder); |
| • | the non-U.S. Holder is an individual who is present in the United States for 183 days or more in the taxable year of disposition and certain other conditions are met; or |
| • | we are or have been a “United States real property holding corporation” for U.S. federal income tax purposes. |
Gain described in the first bullet point above will be subject to tax at generally applicable U.S. federal income tax rates. Any gains described in the first bullet point above of a non-U.S. Holder that is a foreign corporation may also be subject to an additional “branch profits tax” at a 30% rate (or lower applicable treaty rate). Gain described in the second bullet point above will generally be subject to a flat 30% U.S. federal income tax. Non-U.S. Holders are urged to consult their tax advisors regarding possible eligibility for benefits under income tax treaties.
We will be classified as a United States real property holding corporation if the fair market value of our “United States real property interests” equals or exceeds 50% of the sum of the fair market value of our worldwide real property interests plus our other assets used or held for use in a trade or business, as determined for U.S. federal income tax purposes. We do not believe we currently are or will become a United States real property holding corporation; however, there can be no assurance in this regard. Non-U.S. Holders are urged to consult their tax advisors regarding the application of these rules.
Foreign Account Tax Compliance Act
Sections 1471 through 1474 of the Code and the Treasury Regulations and administrative guidance promulgated thereunder (commonly referred as the “Foreign Account Tax Compliance Act” or “FATCA”) generally impose withholding at a rate of 30% in certain circumstances on dividends in respect of, and the gross proceeds of dispositions of, our securities which are held by or through certain foreign financial institutions (including investment funds), unless any such institution (1) enters into, and complies with, an agreement with the IRS to report, on an annual basis, information with respect to interests in, and accounts maintained by, the institution that are owned by certain U.S. persons and by certain non-U.S. entities that are wholly or partially owned by U.S. persons and to withhold on certain payments, or (2) if required under an intergovernmental
145
agreement between the United States and an applicable foreign country, reports such information to its local tax authority, which will exchange such information with the U.S. authorities. Under proposed Treasury Regulations promulgated by the Treasury Department on December 13, 2018, which state that taxpayers may rely on the proposed Treasury Regulations until final Treasury Regulations are issued, this withholding tax will not apply to the gross proceeds from the sale or disposition of our securities. An intergovernmental agreement between the United States and an applicable foreign country may modify these requirements. Accordingly, the entity through which our securities are held will affect the determination of whether such withholding is required. Similarly, dividends in respect of our securities held by an investor that is a non-financial non-U.S. entity that does not qualify under certain exceptions will generally be subject to withholding at a rate of 30%, unless such entity either (1) certifies to us or the applicable withholding agent that such entity does not have any “substantial United States owners” or (2) provides certain information regarding the entity’s “substantial United States owners,” which will in turn be provided to the U.S. Department of Treasury. Prospective investors should consult their tax advisors regarding the possible implications of FATCA on their investment in our securities.
Backup Withholding, Information Reporting and Other Reporting Requirements
We must report annually to the IRS and to each holder of our securities the amount of dividends paid to such holder, and the tax withheld (if any) with respect to such dividends (in the case of a non-U.S. Holder, regardless of whether withholding was reduced or eliminated by an applicable income tax treaty). Copies of this information reporting may also be made available under the provisions of a specific income tax treaty or agreement with the tax authorities in the country in which a non-U.S. Holder resides or is established.
A U.S. Holder may be subject, under certain circumstances, to backup withholding (currently at a rate of 24%) with respect to dividends on our Common Stock paid to such holder or proceeds of a sale or other taxable disposition of shares of our Common Stock. Backup withholding may apply to a non-corporate U.S. Holder that (i) fails to furnish its taxpayer identification number, or TIN, (ii) furnishes an incorrect TIN, (iii) is notified by the IRS that it failed properly to report certain interest or dividends, or (iv) fails, under certain circumstances, to provide a certified statement, signed under penalty of perjury, that it is a U.S. person, that the TIN provided is correct, and that it has not been notified by the IRS that it is subject to backup withholding. The application for exemption is available by providing a properly completed IRS Form W-9 (or successor form). These requirements generally do not apply with respect to certain U.S. Holders, including corporations, tax-exempt organizations, qualified pension and profit-sharing trusts, certain financial institutions and individual retirement accounts, provided that such U.S. Holders, when required, demonstrate their status as such.
A non-U.S. Holder will generally be subject to backup withholding from dividends on our Common Stock paid to such holder unless such holder certifies under penalties of perjury that, among other things, it is a non-U.S. Holder (and the payor does not have actual knowledge or reason to know that such holder is a U.S. person) or otherwise establishes an exemption.
Information reporting and backup withholding generally are not required with respect to the amount of any proceeds from the sale or other disposition of our Common Stock by a non-U.S. Holder outside the United States through a foreign office of a foreign broker that does not have certain specified connections to the United States. However, if a non-U.S. Holder sells or otherwise disposes of its shares of Common Stock through a U.S. broker or the U.S. offices of a foreign broker, the broker will generally be required to report the amount of proceeds paid to the non-U.S. Holder to the IRS and also backup withhold on that amount unless such non-U.S. Holder provides appropriate certification to the broker of its status as a non-U.S. person (and the payor does not have actual knowledge or reason to know that such holder is a U.S. person) or otherwise establishes an exemption. Information reporting will also apply if a non-U.S. Holder sells its shares of Common Stock through a foreign broker deriving more than a specified percentage of its income from U.S. sources or having certain other connections to the United States, unless such broker has documentary evidence in its records that such non-U.S. Holder is a non-U.S. person (and the payor does not have actual knowledge or reason to know that such holder is a U.S. person) and certain other conditions are met, or such non-U.S. holder otherwise establishes an exemption.
146
Backup withholding is not an additional income tax. Any amounts withheld under the backup withholding rules from a payment to a holder of our securities generally can be credited against the holder’s U.S. federal income tax liability, if any, or refunded, provided that the required information is furnished to the Internal Revenue Service in a timely manner. U.S. Holders and Non-U.S. Holders should consult their tax advisors regarding the application of the information reporting and backup withholding rules to them.
147
UNDERWRITING
Subject to the terms and conditions set forth in the underwriting agreement to be entered into between us and Stifel, Nicolaus & Company, Incorporated, as the representative of the underwriters named below, we will agree to sell to the underwriters, and each of the underwriters will agree, severally and not jointly, to purchase from us, at the public offering price less the underwriting discounts and commissions set forth on the cover page of this prospectus, the number of shares of our Common Stock listed opposite its name below.
| Underwriter | Number of Shares | |||
Stifel, Nicolaus & Company, Incorporated | ||||
BTIG LLC | ||||
Canaccord Genuity LLC | ||||
|
| |||
Total | ||||
|
| |||
The underwriting agreement will provide that the obligations of the several underwriters are subject to certain conditions precedent such as the receipt by the underwriters of officers’ certificates and legal opinions and approval of certain legal matters by their counsel. The underwriting agreement will provide that the underwriters will purchase all of the shares of Common Stock if any of them are purchased. If an underwriter defaults, the underwriting agreement will provide that the purchase commitments of the nondefaulting underwriter may be increased or the underwriting agreement may be terminated.
The underwriters are offering the shares of Common Stock subject to their acceptance of the shares of Common Stock from us and subject to prior sale. The underwriters reserve the right to withdraw, cancel or modify offers to the public and to reject orders in whole or in part.
Option to Purchase Additional Shares
We have granted the underwriters an option to purchase up to additional shares of Common Stock from us. The underwriters have 30 days from the date of this prospectus to exercise this option to purchase additional shares. If any shares are purchased with this option to purchase additional shares, the underwriters will purchase shares in approximately the same proportion as shown in the table above. If any additional shares of Common Stock are purchased, the underwriters will offer the additional shares on the same terms as those on which the shares are being offered.
Discounts, Commissions and Expenses
The underwriting fee is equal to the public offering price per share of Common Stock less the amount paid by the underwriters to us per share of Common Stock. The following table shows the per share and total underwriting discounts and commissions to be paid to the underwriters in connection with this offering, assuming both no exercise and full exercise of the underwriters’ option to purchase additional shares:
| Per Share | Total Without Option Exercise | Total With Full Option Exercise | ||||||||||
Public offering price | $ | $ | $ | |||||||||
Underwriting discounts and commissions | $ | $ | $ | |||||||||
Proceeds, before expenses, to us | $ | $ | $ | |||||||||
We estimate that the total fees and expenses payable by us in connection with this offering, excluding underwriting discounts and commissions referred to above, will be approximately $0.8 million. We have also
148
agreed to reimburse the underwriters for certain expenses incurred by them in connection with the offering, including up to $25,000 relating to the clearance of this offering with the Financial Industry Regulatory Authority.
The underwriters have advised us that they propose to offer the shares of Common Stock to the public at the public offering price set forth on the cover of this prospectus and to certain dealers, which may include the underwriters, at that price less a concession not in excess of $ per share of Common Stock. After the offering, if all of the shares of Common Stock are not sold at the public offering price, the public offering price and concession may be reduced by the representative. No such reduction will change the amount of proceeds to be received by us as set forth on the cover of this prospectus.
Indemnification of Underwriters
The underwriting agreement will provide that we will indemnify the underwriters against certain liabilities, including liabilities under the Securities Act, or to contribute to payments that the underwriters may be required to make in respect of those liabilities.
Listing
Our Common Stock is listed on The Nasdaq Global Market under the symbol “BAER.”
Lock-Up Agreements
The underwriting agreement, will provide that the we will not during a period of 90 days from the date of this prospectus (i) offer, pledge, sell, contract to sell, sell any option or contract to purchase, purchase any option or contract to sell, grant any option, right or warrant to purchase, lend or otherwise transfer or dispose of, directly or indirectly, any Common Stock or any securities convertible into or exercisable or exchangeable for Common Stock or (ii) enter into any swap or other agreement that transfers, in whole or in part, any of the economic consequences of ownership of Common Stock, whether any such transaction is to be settled by delivery of Common Stock or such other securities, in cash or otherwise, other than (1) the shares to be sold pursuant to this prospectus, (2) any shares of Common Stock issued upon the exercise of an option or warrant to acquire shares of Common Stock outstanding on the date of this prospectus, (3) any shares of Common Stock issued upon the settlement of any deferred stock unit or vesting or settlement of any restricted stock unit, incentive unit or performance share or upon the conversion of any shares of Series A Preferred Stock in accordance with its terms, (4) any shares of Common Stock issued or options to purchase Common Stock or restricted stock units, incentive units or other equity-based awards granted pursuant to employee benefit or compensation plans of the Company referred to in this prospectus, as such plans may be amended from time to time, in each case outstanding on the date hereof, or (5) the issuance or vesting of any shares of Common Stock in connection with the Bighorn Acquisition and the Ignis Acquisition or the filing of a resale registration statement under the Securities Act for the benefit of recipients of shares of Common Stock in the Bighorn Acquisition and the Ignis Acquisition, in each case pursuant to the terms of the definitive agreements governing the Bighorn Acquisition and the Ignis Acquisition, in each case, as in effect on the date of this prospectus.
Our directors, executive officers and certain other significant holders of our outstanding capital stock and other securities will agree, subject to certain exceptions, that, without the prior written consent of Stifel, Nicolaus & Company, Incorporated as representative of the underwriters, they will not, during the period ending 90 days after the date of this prospectus:
| • | offer, sell, contract to sell (including any short sale), pledge, hypothecate, establish an open “put equivalent position” within the meaning of Rule 16a-1(h) under the Exchange Act, grant any option, right or warrant for the sale of, purchase any option or contract to sell, sell any option or contract to purchase, or otherwise encumber, dispose of or transfer, or grant any rights with respect to, directly or indirectly, any shares of Common Stock or securities convertible into or exchangeable or exercisable for any shares of Common Stock; |
149
| • | enter into any swap, hedge or other arrangement that transfers, in whole or in part, any of the economic consequences of ownership of shares of Common Stock, whether any such aforementioned transaction is to be settled by delivery of the Common Stock or such other securities, in cash or otherwise; or |
| • | publicly disclose the intention to do any of the foregoing. |
The restrictions described in the immediately preceding paragraph contained in the lock-up agreements with our directors, executive officers and certain other significant holders will not apply to:
| • | bona fide gifts; |
| • | in the case of an entity, transfers (including by way of distributions) to any direct or indirect equity holders or to any other affiliates of such entity; |
| • | in the case of an individual, transfers to members of such individual’s immediate family or to a trust, the beneficiary of which is a member of one of such individual’s immediate family, an affiliate of such person or to a charitable organization; |
| • | in the case of an individual, transfers by virtue of laws of descent and distribution (including by will or intestate succession) upon death of the individual; |
| • | in the case of an individual, transfers by operation of law, including pursuant to a qualified domestic relations order or in connection with a divorce settlement or other order of a court or administrative or regulatory agency; |
| • | in the case of an entity, transfers by virtue of the laws of the state of the entity’s organization and the entity’s organizational documents upon dissolution of the entity; |
| • | transfers to the extent required by applicable law, statute, ordinance, treaty, regulation or legal or self-regulatory requirement or to the extent required by any governmental or self-regulatory authority of competent jurisdiction; |
| • | exercises of any options or warrants to purchase Common Stock (which exercises may be effected on a cashless basis to the extent the instruments representing such options or warrants permit exercises on a cashless basis); |
| • | transfers to the Company to satisfy tax withholding obligations pursuant to the Company’s equity incentive plans or arrangements; |
| • | in the case of an individual, transfers to the Company pursuant to any contractual arrangement existing on the date hereof that provides for the repurchase or forfeiture of such individual’s Common Stock or other securities convertible into or exercisable or exchangeable for Common Stock in connection with the termination of such individual’s service to the Company; |
| • | entry into, at any time after the date of this prospectus, any trading plan providing for the sale of the Company’s securities, which trading plan meets the requirements of Rule 10b5-1(c) under the Exchange Act, provided, however, that such plan does not provide for, or permit, the sale of any shares of Common Stock during the lock-up period and no public announcement or filing is voluntarily made or required regarding such plan during the lock-up period; |
| • | entry into transactions in the event of completion of a liquidation, merger, stock exchange, tender offer or other similar transaction which results in all of the Company’s stockholders having the right to exchange their shares of Common Stock for cash, securities or other property; and |
| • | in the case of the Blackstone Holders (as defined below) and any other Blackstone Entities (as defined below), any direct or indirect sale, exchange, assignment, transfer, distribution, contribution or other disposition of any shares of Common Stock (or any direct or indirect interests therein), whether in a single transaction or a series of related transactions, to any other Blackstone Entity; |
150
provided, that with respect to transfers described in the first six bullet points above and the final bullet point above, (a) each resulting transferee of securities will be required to execute and deliver to Stifel, Nicolaus & Company, Incorporated a reasonably satisfactory agreement to be bound by the terms of the lock-up agreement and (b) to the extent any interest in the Company’s securities is retained by the transferor (or such spouse or family member), such securities shall remain subject to the restrictions contained in the lock-up agreement.
“Blackstone Entities” means (a) Blackstone Inc. or any affiliate thereof, or (b) any entity, investment vehicle, account or fund that is directly or indirectly owned, managed or controlled by or under common control or ownership with Blackstone Inc. or any affiliate thereof (including Blackstone Tactical Opportunities Advisors L.L.C.). “Blackstone Holders” means BTO Grannus Holdings IV - NQ LLC, Blackstone Tactical Opportunities Fund - FD L.P., and Blackstone Family Tactical Opportunities Investment Partnership III - NQ - ESC L.P.
Stifel, Nicolaus & Company, Incorporated as representative of the underwriters, in its sole discretion, may release the Common Stock and other securities subject to the lock-up agreements described above in whole or in part at any time.
Short Sales, Stabilizing Transactions and Penalty Bids
The underwriters have advised us that, in order to facilitate this offering, persons participating in the offering may engage in transactions that stabilize, maintain or otherwise affect the price of the shares during and after this offering. Specifically, the underwriters may engage in the following activities in accordance with the rules of the SEC.
Short Sales
Short sales involve the sales by the underwriters of a greater number of shares of Common Stock than they are required to purchase in the offering. Covered short sales are short sales made in an amount not greater than the underwriters’ option to purchase additional shares of Common Stock. The underwriters may close out any covered short position by either exercising their option to purchase additional shares or purchasing shares in the open market. In determining the source of shares to close out the covered short position, the underwriters will consider, among other things, the price of our Common Stock available for purchase in the open market as compared to the price at which they may purchase the shares through their option.
Naked short sales are any short sales in excess of such option to purchase additional shares of Common Stock. The underwriters must close out any naked short position by purchasing shares of our Common Stock in the open market. A naked short position is more likely to be created if the underwriters are concerned that there may be downward pressure on the price of our Common Stock in the open market after pricing that could adversely affect investors who purchase in this offering.
Stabilizing Transactions
The underwriters may make bids for or purchases of shares of our Common Stock for the purpose of pegging, fixing or maintaining the price of our Common Stock so long as stabilizing bids do not exceed a specified maximum.
Penalty Bids
If the underwriters purchase shares of our Common Stock in the open market in a stabilizing transaction or syndicate covering transaction, they may reclaim a selling concession from the underwriters and selling group members who sold those shares as part of this offering. Stabilization and syndicate covering transactions may cause the price of our Common Stock to be higher than it would be in the absence of these transactions. The imposition of a penalty bid might also have an effect on the price of the shares if it discourages resales of the shares.
151
The transactions above may occur on the Nasdaq Global Market or otherwise. Neither we nor the underwriters make any representation or prediction as to the effect that the transactions described above may have on the price of our Common Stock. If such transactions are commenced, they may be discontinued without notice at any time.
Discretionary Sales
The underwriters have informed us that they do not expect to confirm sales of the shares of Common Stock offered by this prospectus to accounts over which they exercise discretionary authority without obtaining the specific approval of the account holder.
Electronic Distribution
A prospectus in electronic format may be made available by e-mail or on the websites or through online services maintained by one or more of the underwriters or their affiliates. In those cases, prospective investors may view offering terms online and may be allowed to place orders online. The underwriters may agree with us to allocate a specific number of shares of Common Stock for sale to online brokerage account holders. Any such allocation for online distributions will be made by the underwriters on the same basis as other allocations. Other than the prospectus in electronic format, the information on each underwriter’s or its affiliates’ websites and any information contained in any other website maintained by either of the underwriters or an affiliate is not part of this prospectus, has not been approved and/or endorsed by us or the underwriters and should not be relied upon by investors.
Other Activities and Relationships
The underwriters and certain of their respective affiliates are full service financial institutions engaged in various activities, which may include securities trading, commercial and investment banking, financial advisory, investment management, investment research, principal investment, hedging, financing and brokerage activities. The underwriters and certain of their respective affiliates have, from time to time, performed, and may in the future perform, various commercial and investment banking and financial advisory services for us and our affiliates, for which they received or will receive customary fees and expenses. In addition, from time to time, certain of the underwriters and their respective affiliates may effect transactions for their own account or the account of customers, and hold on behalf of themselves or their customers, long or short positions in our debt or equity securities or loans, and may do so in the future.
Offer Restrictions Outside the United States
Other than in the United States, no action has been taken by us or the underwriters that would permit a public offering of the securities offered by this prospectus in any jurisdiction where action for that purpose is required. The securities offered by this prospectus may not be offered or sold, directly or indirectly, nor may this prospectus or any other offering material or advertisements in connection with the offer and sale of any such securities be distributed or published in any jurisdiction, except under circumstances that will result in compliance with the applicable rules and regulations of that jurisdiction. Persons into whose possession this prospectus comes are advised to inform themselves about and to observe any restrictions relating to this offering and the distribution of this prospectus. This prospectus does not constitute an offer to sell or a solicitation of an offer to buy any securities offered by this prospectus in any jurisdiction in which such an offer or a solicitation is unlawful.
Notice to Prospective Investors in the European Economic Area
This prospectus is not a prospectus for the purposes of Regulation (EU) 2017/1129, as amended (the “Prospectus Regulation”). This prospectus has been prepared on the basis that any offer of shares of Common
152
Stock in any Member State of the European Economic Area (the “EEA”) will be made pursuant to an exemption under the Prospectus Regulation from the requirement to publish a prospectus for offers of shares of Common Stock. Accordingly any person making or intending to make an offer in any Member State of the EEA of shares of Common Stock which are the subject of the offering contemplated in this prospectus may only do so in circumstances in which no obligation arises for the Company or any of the underwriters to publish a prospectus pursuant to Article 3 of the Prospectus Regulation in relation to such offer. Neither Bridger Aerospace Group Holdings, Inc. nor the underwriters have authorized, nor do they authorize, the making of any offer of shares of Common Stock in any Member State of the EEA in circumstances in which an obligation arises for Bridger Aerospace Group Holdings, Inc. or the underwriters to publish a prospectus for such offer.
In relation to each Member State of the EEA (each a “Relevant State”), no shares of Common Stock have been offered or will be offered pursuant to the offering to the public in that Relevant State prior to the publication of a prospectus in relation to the shares of Common Stock which has been approved by the competent authority in that Relevant State or, where appropriate, approved in another Relevant State and notified to the competent authority in that Relevant State, all in accordance with the Prospectus Regulation, except that the shares of Common Stock may be offered to the public in that Relevant State at any time:
| • | to any legal entity which is a qualified investor as defined under Article 2 of the Prospectus Regulation; |
| • | to fewer than 150 natural or legal persons (other than qualified investors as defined under Article 2 of the Prospectus Regulation, subject to obtaining the prior consent of the representative of the underwriters for any such offer; or |
| • | in any other circumstances falling within Article 1(4) of the Prospectus Regulation, |
provided that no such offer of shares of Common Stock shall require us or any underwriter to publish a prospectus pursuant to Article 3 of the EU Prospectus Regulation.
For the purposes of this provision, the expression an “offer to the public" in relation to the shares of Common Stock in any Relevant State means the communication in any form and by any means of sufficient information on the terms of the offer and any shares of Common Stock to be offered so as to enable an investor to decide to purchase or subscribe for any shares of Common Stock.
Notice to Prospective Investors in the United Kingdom
The communication of this prospectus and any other document or materials relating to the issue of the shares of Common Stock offered hereby is not being made, and such documents and/or materials have not been approved, by an authorized person for the purposes of section 21 of the United Kingdom’s Financial Services and Markets Act 2000, as amended (the “FSMA”). Accordingly, this prospectus and such other documents and/or materials are not being distributed to, and must not be passed on to, the general public in the United Kingdom. This prospectus and such other documents and/or materials are for distribution only to persons who (i) have professional experience in matters relating to investments and who fall within the definition of investment professionals (as defined in Article 19(5) of the Financial Services and Markets Act 2000 (Financial Promotion) Order 2005, as amended (the “Financial Promotion Order”)), (ii) fall within Article 49(2)(a) to (d) of the Financial Promotion Order, (iii) are outside the United Kingdom, or (iv) are other persons to whom it may otherwise lawfully be made under the Financial Promotion Order (all such persons together being referred to as “relevant persons”). This document is directed only at relevant persons and must not be acted on or relied on by persons who are not relevant persons. Any investment or investment activity to which this prospectus and any other document or materials relates will be engaged in only with relevant persons. Any person that is not a relevant person should not act or rely on this prospectus or any other documents and/or materials relating to the issue of the shares of Common Stock offered hereby or any of their contents.
This prospectus is not a prospectus for the purposes of Regulation (EU) 2017/1129 (as amended) as it forms part of domestic law in the United Kingdom by virtue of the European Union (Withdrawal) Act 2018, as
153
amended (the “EUWA”) (the “UK Prospectus Regulation”). This prospectus has been prepared on the basis that any offer of shares of Common Stock in the United Kingdom will be made pursuant to an exemption under the UK Prospectus Regulation from the requirement to publish a prospectus for offers of shares of Common Stock. Accordingly any person making or intending to make an offer in the United Kingdom of shares of Common Stock which are the subject of the offering contemplated in this prospectus may only do so in circumstances in which no obligation arises for Bridger Aerospace Group Holdings, Inc. or any of the underwriters to publish a prospectus pursuant to Section 85 of the FSMA in relation to such offer. Neither Bridger Aerospace Group Holdings, Inc. nor the underwriters has authorized, nor do they authorize, the making of any offer of shares of Common Stock in the United Kingdom in circumstances in which an obligation arises for Bridger Aerospace Group Holdings, Inc. or the underwriters to publish a prospectus for such offer.
No shares of Common Stock have been offered or will be offered pursuant to the offering to the public in the United Kingdom prior to the publication of a prospectus in relation to the shares of Common Stock which has been approved by the Financial Conduct Authority, except that the shares of Common Stock may be offered to the public in the United Kingdom at any time:
| • | to any legal entity which is a qualified investor as defined under Article 2 of the UK Prospectus Regulation; |
| • | to fewer than 150 natural or legal persons (other than qualified investors as defined under Article 2 of the UK Prospectus Regulation), subject to obtaining the prior consent of the representative of the underwriters for any such offer; or |
| • | in any other circumstances falling within Section 86 of the FSMA, |
provided that no such offer of shares of Common Stock shall require Bridger Aerospace Group Holdings, Inc. or any underwriter to publish a prospectus pursuant to Section 85 of the FSMA.
For the purposes of this provision, the expression “an offer to the public” in relation to the shares of Common Stock in the United Kingdom means the communication in any form and by any means of sufficient information on the terms of the offer and any shares of Common Stock to be offered so as to enable an investor to decide to purchase or subscribe for the any shares of Common Stock.
Notice to Residents of Switzerland
The securities which are the subject of the offering contemplated by this prospectus may not be publicly offered in Switzerland and will not be listed on the SIX Swiss Exchange, or SIX, or on any other stock exchange or regulated trading facility in Switzerland. This prospectus has been prepared without regard to the disclosure standards for issuance prospectuses under art. 652a or art. 1156 of the Swiss Code of Obligations or the disclosure standards for listing prospectuses under art. 27 ff. of the SIX Listing Rules or the listing rules of any other stock exchange or regulated trading facility in Switzerland. None of this prospectus or any other offering or marketing material relating to the securities or the offering may be publicly distributed or otherwise made publicly available in Switzerland.
None of this prospectus or any other offering or marketing material relating to the offering, us or the securities have been or will be filed with or approved by any Swiss regulatory authority. In particular, this prospectus will not be filed with, and the offer of securities will not be supervised by the Swiss Financial Market Supervisory Authority, or FINMA, and the offer of securities has not been and will not be authorized under the Swiss Federal Act on Collective Investment Schemes, or CISA. The investor protection afforded to acquirers of interests in collective investment schemes under the CISA does not extend to acquirers of the securities.
Notice to Residents of Japan
The underwriters will not offer or sell any of the shares of common stock directly or indirectly in Japan or to, or for the benefit of, any Japanese person or to others, for reoffering or resale directly or indirectly in Japan or to any Japanese person, except in each case pursuant to an exemption from the registration requirements of, and
154
otherwise in compliance with, the Financial Instruments and Exchange Law of Japan and any other applicable laws and regulations of Japan. For purposes of this paragraph, “Japanese person” means any person resident in Japan, including any corporation or other entity organized under the laws of Japan.
Notice to Residents of Hong Kong
The underwriters and each of their affiliates have not (i) offered or sold, and will not offer or sell, in Hong Kong, by means of any document, any shares of common stock other than (a) to “professional investors” within the meaning of the Securities and Futures Ordinance (Cap. 571) of Hong Kong and any rules made under that Ordinance or (b) in other circumstances which do not result in the document being a “prospectus” as defined in the Companies Ordinance (Cap. 32) of Hong Kong or which do not constitute an offer to the public within the meaning of that Ordinance; and (ii) issued or had in its possession for the purposes of issue, and will not issue or have in its possession for the purposes of issue, whether in Hong Kong or elsewhere any advertisement, invitation or document relating to the shares of common stock which is directed at, or the contents of which are likely to be accessed or read by, the public in Hong Kong (except if permitted to do so under the securities laws of Hong Kong) other than with respect to the shares of common stock which are or are intended to be disposed of only to persons outside Hong Kong or only to “professional investors” within the meaning of the Securities and Futures Ordinance and any rules made under that Ordinance. The contents of this document have not been reviewed by any regulatory authority in Hong Kong. You are advised to exercise caution in relation to the offer. If you are in any doubt about any of the contents of this document, you should obtain independent professional advice.
Notice to Residents of Singapore
This document has not been registered as a prospectus with the Monetary Authority of Singapore. Accordingly, this document and any other document or material in connection with the offer or sale, or invitation for subscription or purchase, of the shares of common stock may not be circulated or distributed, nor may the shares of common stock be offered or sold, or be made the subject of an invitation for subscription or purchase, whether directly or indirectly, to persons in Singapore other than (i) to an institutional investor under Section 274 of the Securities and Futures Act, Chapter 289 of Singapore (the Securities and Futures Act), (ii) to a relevant person, or any person pursuant to Section 275(1A), and in accordance with the conditions, specified in Section 275 of the Securities and Futures Act or (iii) otherwise pursuant to, and in accordance with the conditions of, any other applicable provision of the Securities and Futures Act.
Where the shares of common stock are subscribed or purchased under Section 275 by a relevant person, which is:
| (a) | a corporation (which is not an accredited investor), the sole business of which is to hold investments and the entire share capital of which is owned by one or more individuals, each of whom is an accredited investor; or |
| (b) | a trust (where the trustee is not an accredited investor) whose sole purpose is to hold investments and each beneficiary is an accredited investor, shares, debentures and units of shares and debentures of that corporation or the beneficiaries’ rights and interest in that trust shall not be transferable for six months after that corporation or that trust has acquired the shares of common stock under Section 275 except: |
| (1) | to an institutional investor or to a relevant person, or to any person pursuant to an offer that is made on terms that such rights or interest are acquired at a consideration of not less than $200,000 (or its equivalent in a foreign currency) for each transaction, whether such amount is to be paid for in cash or by exchange of securities or other assets; |
| (2) | where no consideration is given for the transfer; or |
| (3) | by operation of law. |
155
Notice to Residents of Canada
This document constitutes an “exempt offering document” as defined in and for the purposes of applicable Canadian securities laws. No prospectus has been filed with any securities commission or similar regulatory authority in Canada in connection with the offer and sale of the shares. No securities commission or similar regulatory authority in Canada has reviewed or in any way passed upon this document or on the merits of the shares and any representation to the contrary is an offence.
Canadian investors are advised that this document has been prepared in reliance on section 3A.3 of National Instrument 33-105 Underwriting Conflicts (“NI 33-105”). Pursuant to section 3A.3 of NI 33-105, this document is exempt from the requirement that the company and the underwriters provide investors with certain conflicts of interest disclosure pertaining to “connected issuer” and/or “related issuer” relationships that may exist between the company and the underwriters as would otherwise be required pursuant to subsection 2.1(1) of NI 33-105.
Resale Restrictions
The offer and sale of the shares in Canada is being made on a private placement basis only and is exempt from the requirement that the company prepares and files a prospectus under applicable Canadian securities laws. Any resale of shares acquired by a Canadian investor in this offering must be made in accordance with applicable Canadian securities laws, which may vary depending on the relevant jurisdiction, and which may require resales to be made in accordance with Canadian prospectus requirements, a statutory exemption from the prospectus requirements, in a transaction exempt from the prospectus requirements or otherwise under a discretionary exemption from the prospectus requirements granted by the applicable local Canadian securities regulatory authority. These resale restrictions may under certain circumstances apply to resales of the shares outside of Canada.
Representations of Purchasers
Each Canadian investor who purchases the shares will be deemed to have represented to the company, the underwriters and to each dealer from whom a purchase confirmation is received, as applicable, that the investor (i) is purchasing as principal, or is deemed to be purchasing as principal in accordance with applicable Canadian securities laws, for investment only and not with a view to resale or redistribution; (ii) is an “accredited investor” as such term is defined in section 1.1 of National Instrument 45-106 Prospectus Exemptions (“NI 45-106”) or, in Ontario, as such term is defined in section 73.3(1) of the Securities Act (Ontario); and (iii) is a “permitted client” as such term is defined in section 1.1 of National Instrument 31103 Registration Requirements, Exemptions and Ongoing Registrant Obligations.
Taxation and Eligibility for Investment
Any discussion of taxation and related matters contained in this document does not purport to be a comprehensive description of all of the tax considerations that may be relevant to a Canadian investor when deciding to purchase the shares and, in particular, does not address any Canadian tax considerations. No representation or warranty is hereby made as to the tax consequences to a resident, or deemed resident, of Canada of an investment in the shares or with respect to the eligibility of the shares for investment by such investor under relevant Canadian federal and provincial legislation and regulations.
Rights of Action for Damages or Rescission
Securities legislation in certain of the Canadian jurisdictions provides certain purchasers of securities pursuant to an offering memorandum, including where the distribution involves an “eligible foreign security” as such term is defined in Ontario Securities Commission Rule 45-501 Ontario Prospectus and Registration Exemptions and in Multilateral Instrument 45-107 Listing Representation and Statutory Rights of Action Disclosure Exemptions, as applicable, with a remedy for damages or rescission, or both, in addition to any other rights they may have at law, where the offering memorandum, or other offering document that constitutes an
156
offering memorandum, and any amendment thereto, contains a “misrepresentation” as defined under applicable Canadian securities laws. These remedies, or notice with respect to these remedies, must be exercised or delivered, as the case may be, by the purchaser within the time limits prescribed under, and are subject to limitations and defenses under, applicable Canadian securities legislation. In addition, these remedies are in addition to and without derogation from any other right or remedy available at law to the investor.
Language of Documents
Upon receipt of this document, each Canadian investor hereby confirms that it has expressly requested that all documents evidencing or relating in any way to the sale of the securities described herein (including for greater certainty any purchase confirmation or any notice) be drawn up in the English language only. Par la réception de ce document, chaque investisseur canadien confirme par les présentes qu’il a expressément exigé que tous les documents faisant foi ou se rapportant de quelque manière que ce soit à la vente des valeurs mobilières décrites aux présentes (incluant, pour plus de certitude, toute confirmation d’achat ou tout avis) soient rédigés en anglais seulement.
157
LEGAL MATTERS
The validity of the securities offered by this prospectus has been passed upon for us by Sidley Austin LLP. Mayer Brown LLP has acted as counsel for the underwriters in connection with this offering.
EXPERTS
The consolidated financial statements of Bridger Aerospace Group Holdings, LLC, as of December 31, 2022 and 2021 and for the years ended December 31, 2022 and 2021, included in this prospectus have been so included in reliance on the report of Crowe LLP, independent registered public accounting firm, given on the authority of said firm as experts in auditing and accounting.
WHERE YOU CAN FIND MORE INFORMATION
We have filed with the SEC a registration statement on Form S-1 under the Securities Act with respect to the securities offered by this prospectus. This prospectus, which forms a part of such registration statement, does not contain all of the information included in the registration statement. For further information pertaining to us and our securities, you should refer to the registration statement and to its exhibits. The registration statement has been filed electronically and may be obtained in any manner listed below. Whenever we make reference in this prospectus to any of our contracts, agreements or other documents, the references are not necessarily complete. If a contract or document has been filed as an exhibit to the registration statement or a report we file under the Exchange Act, you should refer to the copy of the contract or document that has been filed. Each statement in this prospectus relating to a contract or document filed as an exhibit to a registration statement or report is qualified in all respects by the filed exhibit.
We file annual, quarterly and current reports, proxy statements and other information with the SEC. Our SEC filings are available to the public over the internet at the SEC’s website at www.sec.gov and on our website, free of charge, at www.bridgeraerospace.com/investors. The information found on, or that can be accessed from or that is hyperlinked to, our website is not part of and is not incorporated into, this prospectus. You may inspect a copy of the registration statement through the SEC’s website, as provided herein.
158
Page | ||||
| F-3 | ||||
Audited Consolidated Financial Statements | ||||
| F-2 | ||||
| F-3 | ||||
| F-4 | ||||
| F-5 | ||||
| F-6 | ||||
| F-7 | ||||
| F-8 | ||||
| F-41 | ||||
Unaudited Condensed Consolidated Financial Statements | ||||
| F-41 | ||||
| F-42 | ||||
| F-43 | ||||
| F-44 | ||||
| F-46 | ||||
| F-47 | ||||
As of December 31, | ||||||||
2022 | 2021 | |||||||
ASSETS | ||||||||
Current assets: | ||||||||
Cash and cash equivalents | $ | 30,162,475 | $ | 13,689,091 | ||||
Restricted cash | 12,297,151 | 3,572,041 | ||||||
Investments in marketable securities | 54,980,156 | — | ||||||
Accounts receivable | 28,902 | 34,992 | ||||||
Aircraft support parts | 1,761,270 | 1,944,660 | ||||||
Prepaid expenses and other current assets | 1,835,032 | 2,825,687 | ||||||
Deferred offering costs | 5,800,144 | — | ||||||
Total current assets | 106,865,130 | 22,066,471 | ||||||
Property, plant and equipment, net | 192,091,413 | 168,677,309 | ||||||
Intangible assets, net | 208,196 | 307,954 | ||||||
Goodwill | 2,457,937 | 2,457,937 | ||||||
Other noncurrent assets | 4,356,225 | 1,602,568 | ||||||
Total assets | $ | 305,978,901 | $ | 195,112,239 | ||||
LIABILITIES, MEZZANINE EQUITY AND MEMBERS’ DEFICIT | ||||||||
Current liabilities: | ||||||||
Accounts payable | $ | 3,170,354 | $ | 4,021,177 | ||||
Accrued expenses and other current liabilities | 18,669,572 | 474,644 | ||||||
Operating right-of-use | 21,484 | 4,973 | ||||||
Current portion of Series B Preferred shares | — | 66,412,637 | ||||||
Current portion of long-term debt, net of debt issuance costs | 2,445,594 | 2,155,926 | ||||||
Total current liabilities | 24,307,004 | 73,069,357 | ||||||
Long-term accrued expenses and other noncurrent liabilities | 45,659 | 1,456,949 | ||||||
Operating right-of-use | 754,673 | 608,571 | ||||||
Long-term debt, net of debt issuance costs 1 | 205,471,958 | 58,117,473 | ||||||
Total liabilities | 230,579,294 | 133,252,350 | ||||||
COMMITMENTS AND CONTINGENCIES | ||||||||
MEZZANINE EQUITY | ||||||||
Series A Preferred shares, $0.001 par value; 10,500,000 shares authorized, issued and outstanding at December 31, 2021 | — | 146,668,028 | ||||||
Series C Preferred shares, $0.001 par value; 315,789.473684 shares authorized, issued and outstanding at December 31, 2022 | 489,021,545 | — | ||||||
MEMBERS’ DEFICIT | ||||||||
Accumulated deficit | (415,300,435 | ) | (84,832,845 | ) | ||||
Accumulated other comprehensive income | 1,678,497 | 24,706 | ||||||
Total members’ deficit | (413,621,938 | ) | (84,808,139 | ) | ||||
Total liabilities, mezzanine equity and members’ deficit | $ | 305,978,901 | $ | 195,112,239 | ||||
| 1 | Includes related party debt of $10,000,000 for the 2022 taxable industrial revenue bond. |
For the years ended December 31, | ||||||||
2022 | 2021 | |||||||
Revenues | $ | 46,387,963 | $ | 39,384,182 | ||||
Cost of revenues: | ||||||||
Flight operations | 18,762,172 | 15,823,713 | ||||||
Maintenance | 15,123,806 | 10,755,471 | ||||||
Total cost of revenues | 33,885,978 | 26,579,184 | ||||||
Gross profit | 12,501,985 | 12,804,998 | ||||||
Selling, general and administrative expense | 35,128,322 | 11,215,027 | ||||||
Operating (loss) income | (22,626,337 | ) | 1,589,971 | |||||
Interest expense 1 | (20,019,886 | ) | (9,293,928 | ) | ||||
Other income | 521,555 | 1,163,160 | ||||||
Net loss | $ | (42,124,668 | ) | $ | (6,540,797 | ) | ||
Series C Preferred shares adjustment to maximum redemption value | (202,688,810 | ) | — | |||||
Series A Preferred shares adjustment for redemption, extinguishment, and accrued interest | (85,663,336 | ) | (15,913,184 | ) | ||||
Net loss attributable to common shareholders – basic and diluted | (330,476,814 | ) | (22,453,981 | ) | ||||
Net loss per share attributable to common shareholders – basic and diluted | $ | (8.20 | ) | $ | (0.56 | ) | ||
Weighted-average shares outstanding – basic and diluted | 40,287,478 | 40,122,651 | ||||||
| 1 | Includes related party interest of approximately $517,000 for the 2022 taxable industrial revenue bond. |
For the years ended December 31, | ||||||||
2022 | 2021 | |||||||
Net loss | $ | (42,124,668 | ) | $ | (6,540,797 | ) | ||
Other comprehensive income: | ||||||||
Foreign currency translation adjustment | (413 | ) | (776 | ) | ||||
Unrealized gain on derivative instruments | 1,381,653 | 527,610 | ||||||
Unrealized gain on investments in marketable securities | 272,551 | — | ||||||
Total other comprehensive income | 1,653,791 | 526,834 | ||||||
Comprehensive loss | $ | (40,470,877 | ) | $ | (6,013,963 | ) | ||
Accumulated Deficit | Accumulated Other Comprehensive Income (Loss) | Total Members’ Deficit | ||||||||||
Balance at January 1, 2021 | $ | (62,378,864 | ) | $ | (502,128 | ) | $ | (62,880,992 | ) | |||
Liquidation preference on Series A Preferred shares | (15,913,184 | ) | — | (15,913,184 | ) | |||||||
Unrealized gain on derivative instruments | — | 527,610 | 527,610 | |||||||||
Foreign currency translation adjustment | — | (776 | ) | (776 | ) | |||||||
Net loss | (6,540,797 | ) | — | (6,540,797 | ) | |||||||
Balance at December 31, 2021 | $ | (84,832,845 | ) | $ | 24,706 | $ | (84,808,139 | ) | ||||
Series A Preferred shares adjustment for redemption, extinguishment and revaluation | (85,663,336 | ) | — | (85,663,336 | ) | |||||||
Series C Preferred shares adjustment to maximum redemption value | (202,688,810 | ) | — | (202,688,810 | ) | |||||||
Unrealized gain on derivative instruments | — | 1,381,653 | 1,381,653 | |||||||||
Unrealized gain on investments in marketable securities | — | 272,551 | 272,551 | |||||||||
Foreign currency translation adjustment | — | (413 | ) | (413 | ) | |||||||
Stock based compensation | 9,224 | — | 9,224 | |||||||||
Net loss | (42,124,668 | ) | — | (42,124,668 | ) | |||||||
Balance at December 31, 2022 | $ | (415,300,435 | ) | $ | 1,678,497 | $ | (413,621,938 | ) | ||||
For the years ended December 31, | ||||||||
2022 | 2021 | |||||||
Cash Flows from Operating Activities: | ||||||||
Net loss | $ | (42,124,668 | ) | $ | (6,540,797 | ) | ||
Adjustments to reconcile net loss to net cash provided by (used in) operating activities | ||||||||
Loss on sale of fixed assets | 1,769,732 | 995,528 | ||||||
Depreciation and amortization | 9,091,219 | 6,673,685 | ||||||
Stock based compensation expense | 9,224 | — | ||||||
Change in fair value of freestanding derivative | 2,709 | — | ||||||
Amortization of debt issuance costs | 601,161 | 173,761 | ||||||
Loss (gain) on extinguishment of debt | 844,925 | (774,300 | ) | |||||
Change in fair value of Series A Preferred shares | 3,918,636 | — | ||||||
Change in fair value of Series C Preferred shares embedded derivatives | 1,039,330 | — | ||||||
Accrued interest on Series B Preferred shares | 3,586,586 | 6,335,608 | ||||||
Changes in operating assets and liabilities | ||||||||
Accounts receivable | 6,090 | 2,227,649 | ||||||
Aircraft support parts | 183,390 | (1,195,346 | ) | |||||
Prepaid expense and other current and non current assets | (372,287 | ) | (1,807,123 | ) | ||||
Accounts payable, accrued expenses and other liabilities | 11,526,345 | (67,795 | ) | |||||
Net cash (used in) provided by operating activities | (9,917,608 | ) | 6,020,870 | |||||
Cash Flows from Investing Activities: | ||||||||
Investments in construction in progress - aircraft | — | (28,000,000 | ) | |||||
Investments in construction in progress - buildings | (9,809,946 | ) | (3,195,769 | ) | ||||
Purchases of marketable securities | (60,207,605 | ) | — | |||||
Proceeds from sales and maturities of marketable securities | 5,500,000 | — | ||||||
Investment in Overwatch Imaging, Inc. | — | (1,000,000 | ) | |||||
Sale of property, plant and equipment | 286,400 | — | ||||||
Purchases of property, plant and equipment | (25,582,065 | ) | (22,567,083 | ) | ||||
Net cash used in investing activities | (89,813,216 | ) | (54,762,852 | ) | ||||
Cash Flows from Financing Activities: | ||||||||
Contributions from Series A Preferred shares members | — | 5,000,000 | ||||||
Contributions from Series B Preferred shares members | — | 50,000,000 | ||||||
Payment to Series A Preferred shares members | (236,250,000 | ) | — | |||||
Payment to Series B Preferred shares members | (69,999,223 | ) | — | |||||
Borrowings from Series C Preferred shares members, net of issuance costs | 288,516,309 | — | ||||||
Payment of finance lease liability | (26,747 | ) | (23,310 | ) | ||||
Borrowings from 2022 taxable industrial revenue bond 1 | 160,000,000 | — | ||||||
Borrowings from 2021 taxable industrial revenue bond | — | 7,330,000 | ||||||
Extinguishment of 2021 taxable industrial revenue bond | (7,549,900 | ) | — | |||||
Borrowings from IPFS insurance loan | — | 667,013 | ||||||
Borrowings from various First Interstate Bank vehicle loans | 202,217 | 175,712 | ||||||
Payment of debt issuance costs | (4,417,807 | ) | (670,298 | ) | ||||
Payment of offering costs | (3,508,675 | ) | — | |||||
Repayments on debt | (2,036,443 | ) | (1,721,113 | ) | ||||
Net cash provided by financing activities | 124,929,731 | 60,758,004 | ||||||
Effects of exchange rate changes | (413 | ) | (776 | ) | ||||
Net change in cash, cash equivalents and restricted cash | 25,198,494 | 12,015,246 | ||||||
Cash, cash equivalents and restricted cash – beginning of the year | 17,261,132 | 5,245,886 | ||||||
Cash, cash equivalents and restricted cash – end of the year | $ | 42,459,626 | $ | 17,261,132 | ||||
Less: Restricted cash – end of the year | 12,297,151 | 3,572,041 | ||||||
Cash and cash equivalents – end of the year | $ | 30,162,475 | $ | 13,689,091 | ||||
Supplemental cash flow information | ||||||||
Interest paid 2 | $ | 12,746,793 | $ | 2,686,442 | ||||
Deferred offering costs included in accrued expenses and other current liabilities | $ | 2,291,469 | $ | — | ||||
Fixed assets in accounts payable | $ | 910,581 | $ | 2,446,383 | ||||
Adjustment of Series C Preferred shares to maximum redemption value | $ | 200,505,236 | $ | — | ||||
| 2 | Includes related party interest paid of approximately $ 128,000 for the 2022 taxable industrial revenue bond. |
Estimated useful life | ||||
Aircraft, engines and rotable parts | 1,500 – 6,000 flight hours | |||
Unmanned aerial vehicles | 5 – 10 years | |||
Vehicles and equipment | 3 – 5 years | |||
Buildings | 40 years | |||
For the years ended December 31, | ||||||||
2022 | 2021 | |||||||
Fire suppression | $ | 38,845,227 | $ | 30,442,001 | ||||
Aerial surveillance | 7,215,997 | 8,632,535 | ||||||
Other services | 326,739 | 309,646 | ||||||
Total revenues | $ | 46,387,963 | $ | 39,384,182 | ||||
For the years ended December 31, | ||||||||
2022 | 2021 | |||||||
Flight revenue | $ | 25,105,027 | $ | 20,377,442 | ||||
Standby revenue | 20,772,018 | 18,550,067 | ||||||
Other revenue | 510,918 | 456,673 | ||||||
Total revenues | $ | 46,387,963 | $ | 39,384,182 | ||||
As of December 31, 2022 | ||||
Carrying Value | ||||
Cash equivalents | ||||
Commercial paper | $ | 29,890,313 | ||
Money market fund | 12,640 | |||
Total cash equivalents | $ | 29,902,953 | ||
Restricted cash | ||||
Money market fund | $ | 9,284,362 | ||
As of December 31, 2022 | ||||||||||||||||
Purchase Price | Unrealized Gains | Unrealized Losses | Fair Value | |||||||||||||
Investment in marketable securities | ||||||||||||||||
Commercial paper | $ | 32,635,849 | $ | 277,674 | $ | — | $ | 32,913,523 | ||||||||
Corporate bonds and notes | 15,413,122 | 3,668 | — | 15,416,790 | ||||||||||||
Government securities | 6,658,634 | — | (8,791 | ) | 6,649,843 | |||||||||||
Total marketable securities | $ | 54,707,605 | $ | 281,342 | $ | (8,791 | ) | $ | 54,980,156 | |||||||
As of December 31, | ||||||||
2022 | 2021 | |||||||
Trade accounts receivable | $ | 28,902 | $ | — | ||||
Other receivables | — | 34,992 | ||||||
Total accounts receivable | $ | 28,902 | $ | 34,992 | ||||
As of December 31, | ||||||||
2022 | 2021 | |||||||
Repairables and expendables | $ | 1,734,292 | $ | 1,855,143 | ||||
Other support parts | 26,978 | 89,517 | ||||||
Total aircraft support parts | $ | 1,761,270 | $ | 1,944,660 | ||||
As of December 31, | ||||||||
2022 | 2021 | |||||||
Prepaid insurance | $ | 968,721 | $ | 1,202,946 | ||||
Prepaid subscriptions | 770,724 | 1,559,266 | ||||||
Other current assets | 95,587 | 63,475 | ||||||
Total prepaid expenses and other current assets | $ | 1,835,032 | $ | 2,825,687 | ||||
As of December 31, | ||||||||
2022 | 2021 | |||||||
Aircraft | $ | 158,235,666 | $ | 121,824,576 | ||||
Less: accumulated depreciation | (16,418,098 | ) | (8,451,678 | ) | ||||
Aircraft, net | 141,817,568 | 113,372,898 | ||||||
Construction-in-progress | 16,992,010 | 33,792,009 | ||||||
Buildings | 16,519,231 | 16,465,087 | ||||||
Vehicles and equipment | 4,687,955 | 2,859,568 | ||||||
Construction-in-progress | 13,780,316 | 3,293,229 | ||||||
Finance lease right-of-use-asset | 130,378 | 121,399 | ||||||
Licenses | 234,682 | — | ||||||
Less: accumulated depreciation | (2,070,727 | ) | (1,226,881 | ) | ||||
Buildings and equipment, net | 33,281,835 | 21,512,402 | ||||||
Property, plant and equipment, net | $ | 192,091,413 | $ | 168,677,309 | ||||
As of December 31, 2022 | ||||||||||||||
Estimated Life (Years) | Gross Carrying amount | Accumulated Amortization | Net Carrying Amount | |||||||||||
Licenses | 10 | $ | 67,623 | $ | (47,177 | ) | $ | 20,446 | ||||||
Internal-use software | 3 | 296,675 | (108,925 | ) | 187,750 | |||||||||
Total intangible assets | $ | 364,298 | $ | (156,102 | ) | $ | 208,196 | |||||||
As of December 31, 2021 | ||||||||||||||||
Estimated Life (Years) | Gross Carrying amount | Accumulated Amortization | Net Carrying Amount | |||||||||||||
Licenses | 10 | $ | 85,131 | $ | (45,229 | ) | $ | 39,902 | ||||||||
Internal-use software | 3 | 73,601 | (28,623 | ) | 44,978 | |||||||||||
Capitalized internal-use software in progress | N/A | 223,074 | — | 223,074 | ||||||||||||
Total intangible assets | $ | 381,806 | $ | (73,852 | ) | $ | 307,954 | |||||||||
Year Ending December 31: | ||||
2023 | $ | 105,654 | ||
2024 | 95,621 | |||
2025 | 6,762 | |||
2026 | 159 | |||
2027 | — | |||
Thereafter | — | |||
Total | $ | 208,196 | ||
As of December 31, | ||||||||
2022 | 2021 | |||||||
Investment in Overwatch | $ | 1,000,000 | $ | 1,000,000 | ||||
Operating lease right-of-use | 671,054 | 577,086 | ||||||
Interest rate swap | 1,407,135 | 25,482 | ||||||
Prepaid subscriptions | 1,246,128 | — | ||||||
Other assets | 31,908 | — | ||||||
Total other noncurrent assets | $ | 4,356,225 | $ | 1,602,568 | ||||
As of December 31, | ||||||||
2022 | 2021 | |||||||
Accrued salaries, wages, and bonuses | $ | 6,515,774 | $ | 1,636,000 | ||||
Finance right-of-use | 68,310 | 82,944 | ||||||
Accrued professional fees | 2,291,469 | — | ||||||
Embedded derivative of Series C Preferred shares | 1,039,330 | — | ||||||
Freestanding derivative on Series C Preferred shares | 2,186,283 | — | ||||||
Accrued interest expense and other accrued liabilities | 6,614,065 | 212,649 | ||||||
Total accrued expenses and other liabilities | 18,715,231 | 1,931,593 | ||||||
Less: Current accrued expenses and other current liabilities | (18,669,572 | ) | (474,644 | ) | ||||
Total long-term accrued expenses and other noncurrent liabilities | $ | 45,659 | $ | 1,456,949 | ||||
As of December 31, 2022 | ||||||||||
Effective Date | Maturity Date | Notional Amount | Fair Value | Pay Fixed | Receive Rate | |||||
4/15/2020 | 3/15/2030 | $11,110,484 | $1,407,135 | 3.887% | 1 Month LIBOR + 2.5% | |||||
As of December 31, 2021 | ||||||||||
Effective Date | Maturity Date | Notional Amount | Fair Value | Pay Fixed | Receive Rate | |||||
4/15/2020 | 3/15/2030 | $11,754,570 | $25,482 | 3.887% | 1 Month LIBOR + 2.5% | |||||
As of December 31, 2022 | ||||||||||||
Level 1 | Level 2 | Level 3 | ||||||||||
Assets | ||||||||||||
Cash | $ | 259,522 | $ | — | $ | — | ||||||
Cash equivalents: | ||||||||||||
Commercial paper | — | 29,890,313 | — | |||||||||
Money market fund | 12,640 | — | — | |||||||||
Total Cash and cash equivalents | 272,162 | 29,890,313 | — | |||||||||
Restricted cash: | ||||||||||||
Money market fund | 9,284,362 | — | — | |||||||||
Other restricted cash | 3,012,789 | — | — | |||||||||
Total Restricted cash | 12,297,151 | — | — | |||||||||
Investments in marketable securities | 54,980,156 | — | ||||||||||
Interest rate swap | 1,407,135 | — | ||||||||||
Total assets | $ | 12,569,313 | $ | 86,277,604 | $ | — | ||||||
Liabilities | ||||||||||||
Freestanding derivative on Series C Preferred Shares | $ | — | $ | — | $ | 2,186,283 | ||||||
Embedded derivative of Series C Preferred shares | — | — | $ | 1,039,330 | ||||||||
Total liabilities | $ | — | $ | — | $ | 3,225,613 | ||||||
As of December 31, 2021 | ||||||||||||
Level 1 | Level 2 | Level 3 | ||||||||||
Assets | ||||||||||||
Cash and cash equivalents | $ | 13,689,091 | $ | — | $ | — | ||||||
Restricted cash | 3,572,041 | — | — | |||||||||
Interest rate swap | — | 25,482 | — | |||||||||
Total assets | $ | 17,261,132 | $ | 25,482 | $ | — | ||||||
Liabilities | ||||||||||||
Mandatorily redeemable Series B Preferred shares | $ | — | $ | 66,412,637 | $ | — | ||||||
Total liabilities | $ | — | $ | 66,412,637 | $ | — | ||||||
As of December 31, | ||||||||
2022 | 2021 | |||||||
Permanent loan agreement, dated August 21, 2020, greater of Prime + 1.5% or 4.75% interest rate, maturing August 21, 2035 | $ | 18,852,476 | $ | 19,000,000 | ||||
Permanent loan agreement, dated October 1, 2020, greater of Prime + 1.5% or 4.75% interest rate, maturing October 1, 2035 | 18,924,229 | 19,000,000 | ||||||
Term loan agreement dated September 30, 2019, LIBOR + 2.5%, maturing March 15, 2030 | 11,110,484 | 11,754,570 | ||||||
Term loan agreement dated February 3, 2020, LIBOR + 2.5%, maturing February 3, 2027 | 4,371,000 | 4,929,000 | ||||||
Taxable industrial revenue bonds, dated February 24, 2021, 6.5% interest rates, maturing February 21, 2040 | — | 7,330,000 | ||||||
Taxable industrial revenue bonds, dated July 21, 2022, 11.5% interest rates, maturing September 1, 2027 | 160,000,000 | — | ||||||
Various term loan agreements with earliest start at November 18, 2020, 3.89-4.52% interest rates, latest maturation on November 18, 2022 | — | 554,940 | ||||||
Various term loan agreements, with earliest start at September 9, 2021, 5-5.5% interest rates, latest maturation on November 17, 2027 | 317,073 | 170,763 | ||||||
Loans payable | 213,575,262 | 62,739,273 | ||||||
Less: noncurrent debt issuance costs | (4,664,552 | ) | (2,303,974 | ) | ||||
Less: current debt issuance costs | (993,157 | ) | (161,900 | ) | ||||
Less: current portion of long-term debt, net of debt issuance costs | (2,445,595 | ) | (2,155,926 | ) | ||||
Total long-term debt, net of debt issuance costs | $ | 205,471,958 | $ | 58,117,473 | ||||
Year Ending December 31: | ||||
2023 | $ | 3,438,752 | ||
2024 | 3,544,234 | |||
2025 | 3,664,628 | |||
2026 | 3,780,164 | |||
2027 | 165,430,178 | |||
Thereafter | 33,717,306 | |||
Total | $ | 213,575,262 | ||
As of December 31: | Aircraft | Hangar | ||||||
2023 | $ | 9,097,771 | 3,755,517 | |||||
2024 | — | — | ||||||
2025 | — | — | ||||||
2026 | — | — | ||||||
2027 | — | — | ||||||
Thereafter | — | — | ||||||
Total | $ | 9,097,771 | 3,755,517 | |||||
As of December 31, | ||||||||||
Leases | Classification | 2022 | 2021 | |||||||
Assets | ||||||||||
Operating lease right-of-use | Other noncurrent assets | $ | 671,054 | $ | 577,086 | |||||
Finance lease right-of-use | Property, plant and equipment, net | $ | 61,933 | $ | 79,701 | |||||
Liabilities | ||||||||||
Operating lease right-of-use | Operating right-of-use | $ | 21,484 | $ | 4,973 | |||||
Finance lease right-of-use | Accrued expenses and other current liabilities | $ | 22,651 | $ | 6,928 | |||||
Operating lease right-of-use (non-current) | Operating right-of-use | $ | 754,673 | $ | 608,571 | |||||
Finance lease right-of-use (non-current) | Accrued expenses and other noncurrent liabilities | $ | 45,659 | $ | 76,016 | |||||
Year Ended December 31, | ||||||||
2022 | 2021 | |||||||
Cash paid for amounts included in the measurement of lease liabilities: | ||||||||
Operating cash flows from operating leases | $ | (58,047 | ) | $ | (51,039 | ) | ||
Operating cash flows from finance leases | $ | (8,671 | ) | $ | (9,613 | ) | ||
Financing cash flows from finance leases | $ | (26,747 | ) | $ | (23,310 | ) | ||
Right-of-use | ||||||||
Operating leases | $ | 129,576 | $ | 619,599 | ||||
Operating Leases | Finance Leases | |||||||
Year Ending December 31: | ||||||||
2023 | $ | 56,702 | $ | 28,700 | ||||
2024 | 60,501 | 25,616 | ||||||
2025 | 60,501 | 21,036 | ||||||
2026 | 65,046 | 4,369 | ||||||
2027 | 69,592 | — | ||||||
Thereafter | 2,376,822 | — | ||||||
Total lease payments | 2,689,164 | 79,721 | ||||||
Less: interest | 1,913,007 | 11,411 | ||||||
Total lease liabilities | $ | 776,157 | $ | 68,310 | ||||
Dividend yield (%) | 0 | |||
Expected volatility (%) | 46.5 | |||
Risk-free interest rate (%) | 1.26 | |||
Term (in years) | 5.00 | |||
Discount for lack of marketability (%) | 30 |
Time-Vesting Incentive Units | Exit-Vesting Incentive Units | |||||||||||||||
Number of Awards | Weighted average grant date fair value | Number of Awards | Weighted average grant date fair value | |||||||||||||
Unvested as of January 1, 2022 | 242,424 | $ | 0.15 | 80,808 | $ | 0.11 | ||||||||||
Granted | — | — | — | — | ||||||||||||
Vested | 80,808 | 0.11 | — | — | ||||||||||||
Forfeited | — | — | — | — | ||||||||||||
Unvested as of December 31, 2022 | 161,616 | $ | 0.17 | 80,808 | $ | 0.11 | ||||||||||
Redeemable Series C Preferred Shares | ||||||||
Shares | Amounts | |||||||
Issuance of Series C Preferred shares | 315,789.473684 | $ | 288,332,735 | |||||
Adjustment to maximum redemption value | — | 202,688,810 | ||||||
Balance as of December 31, 2022 | 315,789.473684 | $ | 489,021,545 | |||||
Year Ended December 31, | ||||||||
2022 | 2021 | |||||||
B asic and diluted net loss per share | ||||||||
Numerator: | ||||||||
Net loss | $ | (42,124,668 | ) | $ | (6,540,797 | ) | ||
Series C Preferred shares adjustment to maximum redemption value | (202,688,810 | ) | — | |||||
Series A Preferred shares adjustment for redemption, extinguishment and accrued interest | (85,663,336 | ) | (15,913,184 | ) | ||||
Net loss attributable to common shareholders – basic and diluted | $ | (330,476,814 | ) | $ | (22,453,981 | ) | ||
Denominator: | ||||||||
Weighted average shares outstanding - basic and diluted | 40,287,478 | 40,122,651 | ||||||
Net loss per share attributable to common shareholders - basic and diluted | $ | (8.20 | ) | $ | (0.56 | ) | ||
For the year ended December 31, | ||||||||
2022 | 2021 | |||||||
Series C Preferred shares | 25,611,505 | — | ||||||
Class D common shares upon vesting | 242,424 | 323,232 | ||||||
Total | 25,853,929 | 323,232 | ||||||
| (i) | an error in the accounting for a freestanding instrument which requires separate accounting under ASC 815, Derivatives and Hedging |
As of December 31, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Balance Sheets: | ||||||||||||
Total assets | $ | 305,978,901 | $ | — | $ | 305,978,901 | ||||||
Accrued expenses and other current liabilities | 16,483,289 | 2,186,283 | 18,669,572 | |||||||||
Total current liabilities | 22,120,721 | 2,186,283 | 24,307,004 | |||||||||
Total liabilities | 228,393,011 | 2,186,283 | 230,579,294 | |||||||||
Series C Preferred Shares | 489,021,545 | — | 489,021,545 | |||||||||
Accumulated deficit | (413,114,152 | ) | (2,186,283 | ) | (415,300,435 | ) | ||||||
Total members’ deficit | (411,435,655 | ) | (2,186,283 | ) | (413,621,938 | ) | ||||||
Total liabilities, mezzanine equity and members’ deficit | $ | 305,978,901 | $ | — | $ | 305,978,901 | ||||||
For the year ended December 31, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Operations: | ||||||||||||
Interest expense | $ | (20,017,177 | ) | $ | (2,709 | ) | $ | (20,019,886 | ) | |||
Net loss | $ | (42,121,959 | ) | $ | (2,709 | ) | $ | (42,124,668 | ) | |||
Series C Preferred Shares adjustment for maximum redemption value | (200,505,236 | ) | (2,183,574 | ) | (202,688,810 | ) | ||||||
Net loss attributable to common shareholders | $ | (328,290,531 | ) | $ | (2,186,283 | ) | $ | (330,476,814 | ) | |||
Net loss per share attributable to common shareholders – basic and diluted | $ | (8.15 | ) | $ | (0.05 | ) | $ | (8.20 | ) | |||
For the year ended December 31, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Members’ Equity: | ||||||||||||
Series C Preferred Shares adjustment for maximum redemption value | $ | (200,505,236 | ) | $ | (2,183,574 | ) | $ | (202,688,810 | ) | |||
Net loss | (42,121,959 | ) | (2,709 | ) | (42,124,668 | ) | ||||||
Accumulated deficit | (413,114,152 | ) | (2,186,283 | ) | (415,300,435 | ) | ||||||
Accumulated other comprehensive income | 1,678,497 | — | 1,678,497 | |||||||||
Total members’ deficit | $ | (411,435,655 | ) | $ | (2,186,283 | ) | $ | (413,621,938 | ) | |||
For the year ended December 31, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Cash Flows: | ||||||||||||
Cash Flows from Operating Activities: | ||||||||||||
Net loss | $ | (42,121,959 | ) | $ | (2,709 | ) | $ | (42,124,668 | ) | |||
Change in fair value of freestanding derivative | — | 2,709 | 2,709 | |||||||||
Net cash used in operating activities | (9,917,608 | ) | — | (9,917,608 | ) | |||||||
Net change in cash, cash equivalents, and restricted cash | 25,198,494 | — | 25,198,494 | |||||||||
Cash, cash equivalents and restricted cash and cash equivalents – end of period | $ | 42,459,626 | $ | — | $ | 42,459,626 | ||||||
Cash and cash equivalents – end of period | $ | 30,162,475 | $ | — | $ | 30,162,475 | ||||||
As of September 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Balance Sheets: | ||||||||||||
Total assets | $ | 320,554,139 | $ | — | $ | 320,554,139 | ||||||
Accrued expenses and other current liabilities | 12,355,584 | 2,124,265 | 14,479,849 | |||||||||
Total current liabilities | 19,472,020 | 2,124,265 | 21,596,285 | |||||||||
Total liabilities | $ | 226,008,817 | $ | 2,124,265 | $ | 228,133,082 | ||||||
Series C Preferred shares | 483,385,214 | — | 483,385,214 | |||||||||
Accumulated deficit | (390,307,424 | ) | (2,124,265 | ) | (392,431,689 | ) | ||||||
Total members’ deficit | (388,839,892 | ) | (2,124,265 | ) | (391,036,037 | ) | ||||||
Total liabilities, mezzanine equity and members’ deficit | $ | 320,554,139 | $ | — | $ | 320,554,139 | ||||||
For the nine months ended September 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Operations: | ||||||||||||
Interest expense | $ | (13,052,438 | ) | $ | 59,309 | $ | (12,993,129 | ) | ||||
Net loss | $ | (25,117,707 | ) | $ | 59,309 | $ | (25,058,398 | ) | ||||
Series C Preferred Shares adjustment for maximum redemption value | (194,700,545 | ) | (2,183,574 | ) | (196,884,119 | ) | ||||||
Net loss attributable to common shareholders | $ | (305,481,588 | ) | $ | (2,124,265 | ) | $ | (307,605,853 | ) | |||
Net loss per share attributable to common shareholders – basic and diluted | $ | (7.58 | ) | $ | (0.06 | ) | $ | (7.64 | ) | |||
For the nine months ended September 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Members’ Equity: | ||||||||||||
Series C Preferred Shares adjustment for maximum redemption value | $ | (194,700,545 | ) | $ | (2,183,574 | ) | $ | (196,884,119 | ) | |||
Net loss | (25,117,707 | ) | 59,309 | (25,058,398 | ) | |||||||
Accumulated deficit | (390,307,424 | ) | (2,124,265 | ) | (392,431,689 | ) | ||||||
Total members’ deficit | $ | (388,839,892 | ) | $ | (2,124,265 | ) | $ | (390,964,157 | ) | |||
For the nine months ended September 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Cash Flows: | ||||||||||||
Cash Flows from Operating Activities: | ||||||||||||
Net loss | $ | (25,117,707 | ) | $ | 59,309 | $ | (25,058,398 | ) | ||||
Change in fair value of freestanding derivative | — | (59,309 | ) | (59,309 | ) | |||||||
Net cash used in by operating activities | (7,930,502 | ) | — | (7,930,502 | ) | |||||||
Net change in cash, cash equivalents, and restricted cash | 89,107,304 | — | 89,107,304 | |||||||||
Cash, cash equivalents and restricted cash and cash equivalents – end of period | $ | 106,368,436 | $ | — | $ | 106,368,436 | ||||||
Cash and cash equivalents – end of period | $ | 94,143,466 | $ | — | $ | 94,143,466 | ||||||
As of June 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Balance Sheets: | ||||||||||||
Total assets | $ | 309,603,293 | $ | — | $ | 309,603,293 | ||||||
Accrued expenses and other current liabilities | 10,359,417 | 2,183,574 | 12,542,991 | |||||||||
Total current liabilities | 32,207,636 | 2,183,574 | 34,391,210 | |||||||||
Total liabilities | 209,837,425 | 2,183,574 | 212,020,999 | |||||||||
Series C Preferred shares | 477,741,883 | — | 475,558,309 | |||||||||
Accumulated deficit | (378,984,493 | ) | (2,183,574 | ) | (381,168,067 | ) | ||||||
Total members’ deficit | (377,976,015 | ) | (2,183,574 | ) | (380,159,589 | ) | ||||||
Total liabilities, mezzanine equity and members’ deficit | $ | 309,603,293 | $ | — | $ | 309,603,293 | ||||||
For the six months ended June 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Operations: | ||||||||||||
Net loss | $ | (19,435,884 | ) | $ | — | $ | (19,435,884 | ) | ||||
Series C Preferred Shares adjustment for maximum redemption value | (189,057,208 | ) | (2,183,574 | ) | (191,240,782 | ) | ||||||
Net loss attributable to common shareholders | $ | (294,156,428 | ) | $ | (2,183,574 | ) | $ | (296,340,002 | ) | |||
Net loss per share attributable to common shareholders – basic and diluted | $ | (7.30 | ) | $ | (0.06 | ) | $ | (7.36 | ) | |||
For the six months ended June 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Members’ Equity: | ||||||||||||
Series C Preferred Shares adjustment for maximum redemption value | $ | (189,057,208 | ) | $ | (2,183,574 | ) | $ | (191,240,782 | ) | |||
Net loss | (19,435,884 | ) | — | (19,435,884 | ) | |||||||
Accumulated deficit | (378,984,493 | ) | (2,183,574 | ) | (381,168,067 | ) | ||||||
Accumulated other comprehensive income | 1,008,478 | — | 1,008,478 | |||||||||
Total members’ deficit | $ | (377,976,015 | ) | $ | (2,183,574 | ) | $ | (380,159,589 | ) | |||
As of June 30, 2023 | As of December 31, 2022 | |||||||
ASSETS | ||||||||
| Current assets: | ||||||||
| Cash and cash equivalents | $ | 844,582 | $ | 30,162,475 | ||||
| Restricted cash | 12,239,819 | 12,297,151 | ||||||
| Investments in marketable securities | 12,572,950 | 54,980,156 | ||||||
Accounts receivable 1 | 11,815,732 | 28,902 | ||||||
| Aircraft support parts | 434,894 | 1,761,270 | ||||||
| Prepaid expenses and other current assets | 2,892,240 | 1,835,032 | ||||||
| Deferred offering costs | 388,120 | 5,800,144 | ||||||
| Total current assets | 41,188,337 | 106,865,130 | ||||||
| Property, plant and equipment, net | 202,050,389 | 192,091,413 | ||||||
| Intangible assets, net | 155,369 | 208,196 | ||||||
| Goodwill | 2,457,937 | 2,457,937 | ||||||
| Other noncurrent assets | 7,583,603 | 4,356,225 | ||||||
| Total assets | $ | 253,435,635 | $ | 305,978,901 | ||||
LIABILITIES, MEZZANINE EQUITY AND STOCKHOLDERS’ DEFICIT | ||||||||
| Current liabilities: | ||||||||
| Accounts payable | $ | 6,235,941 | $ | 3,170,354 | ||||
| Accrued expenses and other current liabilities | 7,823,154 | 18,669,572 | ||||||
Operating right-of-use | 355,119 | 21,484 | ||||||
| Current portion of long-term debt, net of debt issuance costs | 2,459,654 | 2,445,594 | ||||||
| Total current liabilities | 16,873,868 | 24,307,004 | ||||||
| Long-term accrued expenses and other noncurrent liabilities | 6,864,516 | 45,659 | ||||||
Operating right-of-use | 1,449,911 | 754,673 | ||||||
Long-term debt, net of debt issuance costs 2 | 205,060,810 | 205,471,958 | ||||||
| Total liabilities | $ | 230,249,105 | $ | 230,579,294 | ||||
COMMITMENTS AND CONTINGENCIES | ||||||||
MEZZANINE EQUITY | ||||||||
Series A Preferred Stock, $0.0001 par value; 315,789.473684 s | 342,738,969 | — | ||||||
| Legacy Bridger Series C Preferred Shares, $0.001 par value; 315,789.473684 shares authorized, issued and outstanding at December 31, 2022 | — | 489,021,545 | ||||||
STOCKHOLDERS’ DEFICIT | ||||||||
Common Stock, $0.0001 par value; 1,000,000,000 shares authorized; 44,505,944 shares issued and outstanding at June 30, 2023; 39,081,744 shares issued and outstanding at December 31, 2022 | 4,906 | 3,908 | ||||||
Additional paid-in capital | 78,977,391 | — | ||||||
| Accumulated deficit | (400,054,307 | ) | (415,304,343 | ) | ||||
| Accumulated other comprehensive income | 1,519,571 | 1,678,497 | ||||||
| Total stockholders’ deficit | (319,552,439 | ) | (413,621,938 | ) | ||||
| Total liabilities, mezzanine equity, and stockholders’ deficit | $ | 253,435,635 | $ | 305,978,901 | ||||
| 1 | Includes related party accounts receivable of $427,454 as of June 30, 2023. |
| 2 | Includes related party debt of $ 10,000,000 for the 2022 taxable industrial revenue bond as of June 30, 2023 and December 31, 2022, respectively. |
For the Three Months Ended June 30, | For the Six Months Ended June 30, | |||||||||||||||
2023 | 2022 | 2023 | 2022 | |||||||||||||
Revenues 1 | $ | 11,615,280 | $ | 12,753,671 | $ | 11,980,653 | $ | 12,822,963 | ||||||||
| Cost of revenues: | ||||||||||||||||
| Flight operations | 6,299,122 | 5,849,562 | 10,032,383 | 9,514,914 | ||||||||||||
| Maintenance | 4,210,976 | 3,571,986 | 7,726,427 | 6,433,973 | ||||||||||||
| Total cost of revenues | 10,510,098 | 9,421,548 | 17,758,810 | 15,948,887 | ||||||||||||
Gross income (loss) | 1,105,182 | 3,332,123 | (5,778,157 | ) | (3,125,924 | ) | ||||||||||
| Selling, general and administrative expense | 15,187,808 | 5,735,627 | 48,416,299 | 10,576,886 | ||||||||||||
Operating loss | (14,082,626 | ) | (2,403,504 | ) | (54,194,456 | ) | (13,702,810 | ) | ||||||||
Interest expense 2 | (5,540,867 | ) | (2,293,682 | ) | (11,205,412 | ) | (6,008,228 | ) | ||||||||
| Other income | 601,891 | 134,311 | 1,693,328 | 275,154 | ||||||||||||
Net loss | $ | (19,021,602 | ) | $ | (4,562,875 | ) | $ | (63,706,540 | ) | $ | (19,435,884 | ) | ||||
| Series A Preferred Stock – adjustment for deemed dividend upon Closing | $ | — | $ | — | $ | (48,300,000 | ) | $ | — | |||||||
| Series A Preferred Stock – adjustment to eliminate 50% multiplier | $ | — | $ | — | $ | 156,362,598 | $ | — | ||||||||
| Series A Preferred Stock – adjustment to maximum redemption value | $ | (5,805,582 | ) | $ | — | $ | (10,080,022 | ) | $ | — | ||||||
| Legacy Bridger Series A Preferred Shares – adjustment for redemption, extinguishment, accrued interest, and change in fair value | $ | — | $ | (81,323,569 | ) | $ | — | $ | (85,663,336 | ) | ||||||
| Legacy Bridger Series C Preferred Shares - adjustment to maximum redemption value | $ | — | $ | (191,240,782 | ) | $ | — | $ | (191,240,782 | ) | ||||||
| Net (loss) income attributable to Common stockholders - basic and diluted | $ | (24,827,184 | ) | $ | (277,127,226 | ) | $ | 34,276,036 | $ | (296,340,002 | ) | |||||
| Net (loss) income per Common Stock - basic | $ | (0.55 | ) | $ | (7.15 | ) | $ | 0.77 | $ | (7.64 | ) | |||||
| Net (loss) income per Common Stock - diluted | $ | (0.55 | ) | $ | (7.15 | ) | $ | 0.44 | $ | (7.64 | ) | |||||
| Weighted average Common Stock outstanding – basic | 45,388,892 | 38,770,646 | 44,443,930 | 38,770,646 | ||||||||||||
| Weighted average Common Stock outstanding – diluted | 45,388,892 | 38,770,646 | 77,199,129 | 38,770,646 | ||||||||||||
| 1 | Includes related party revenues of $112,210 and $433,454 for the three and six months ended June 30, 2023, respectively. |
| 2 | Includes related party interest for the 2022 taxable industrial revenue bond of approximately $279,000 and $563,000 for the three and six months ended June 30, 2023, respectively. |
For the Three Months Ended June 30, | For the Six Months Ended June 30, | |||||||||||||||
2023 | 2022 | 2023 | 2022 | |||||||||||||
| Net loss | $ | (19,021,602 | ) | $ | (4,562,875 | ) | $ | (63,706,540 | ) | $ | (19,435,884 | ) | ||||
| Other comprehensive (loss) income, net of tax | ||||||||||||||||
| Foreign currency translation adjustment | 214 | 24 | 406 | (263 | ) | |||||||||||
| Unrealized gain (loss) on derivative instruments | 203,467 | 309,654 | (68,334 | ) | 984,035 | |||||||||||
| Unrealized (loss) gain on investments in marketable securities | (28,301 | ) | — | 290,344 | — | |||||||||||
| Reclassification of realized gains on investments in marketable securities to earnings | (208,190 | ) | — | (381,342 | ) | — | ||||||||||
| Total other comprehensive (loss) income, net of tax | (32,810 | ) | 309,678 | (158,926 | ) | 983,772 | ||||||||||
Comprehensive loss | $ | (19,054,412 | ) | $ | (4,253,197 | ) | $ | (63,865,466 | ) | $ | (18,452,112 | ) | ||||
Legacy Bridger Series A Preferred Shares | Legacy Bridger Series B Preferred Shares | Legacy Bridger Series C Preferred Shares / Series A Preferred Stock | Common Stock | Additional Paid-in Capital | Accumulated Deficit | Accumulated Other Comprehensive Income | Total Stockholders’ Deficit | |||||||||||||||||||||||||||||||||||||||||
Share | Value | Share | Value | Share | Value | Share | Value | |||||||||||||||||||||||||||||||||||||||||
| Balance at December 31, 2021 | 10,500,000 | $ | 1,050 | 60,000,000 | $ | 6,000 | — | $ | — | 39,081,744 | $ | 3,908 | $ | — | $ | (84,843,803 | ) | $ | 24,706 | $ | (84,815,189 | ) | ||||||||||||||||||||||||||
| Liquidation preference on Legacy Bridger Series A Preferred Shares | — | — | — | — | — | — | — | — | — | (4,339,767 | ) | — | (4,339,767 | ) | ||||||||||||||||||||||||||||||||||
| Unrealized gain on derivative instruments | — | — | — | — | — | — | — | — | — | — | 674,381 | 674,381 | ||||||||||||||||||||||||||||||||||||
| Foreign currency translation adjustment | — | — | — | — | — | — | — | — | — | — | (287 | ) | (287 | ) | ||||||||||||||||||||||||||||||||||
| Stock based compensation attributable to Legacy Bridger holders prior to reverse recapitalization | — | — | — | — | — | — | — | — | — | 2,558 | — | 2,558 | ||||||||||||||||||||||||||||||||||||
| Net loss | — | — | — | — | — | — | — | — | — | (14,873,009 | ) | — | (14,873,009 | ) | ||||||||||||||||||||||||||||||||||
| Balance at March 31, 2022 | 10,500,000 | $ | 1,050 | 60,000,000 | $ | 6,000 | — | $ | — | 39,081,744 | $ | 3,908 | $ | — | $ | (104,054,021 | ) | $ | 698,800 | $ | (103,351,313 | ) | ||||||||||||||||||||||||||
| Legacy Bridger Series A Preferred Shares adjustment for redemption, extinguishment and revaluation | — | — | — | — | — | — | — | — | — | (81,323,569 | ) | — | (81,323,569 | ) | ||||||||||||||||||||||||||||||||||
| Legacy Bridger Series C Preferred Shares adjustment to maximum redemption value | — | — | — | — | — | — | — | — | — | (191,240,782 | ) | — | (191,240,782 | ) | ||||||||||||||||||||||||||||||||||
| Unrealized gain on derivative instruments | — | — | — | — | — | — | — | — | — | — | 309,654 | 309,654 | ||||||||||||||||||||||||||||||||||||
| Foreign currency translation adjustment | — | — | — | — | — | — | — | — | — | — | 24 | 24 | ||||||||||||||||||||||||||||||||||||
| Stock based compensation attributable to Legacy Bridger holders prior to reverse recapitalization | — | — | — | — | — | — | — | — | — | 2,222 | — | 2,222 | ||||||||||||||||||||||||||||||||||||
| Net loss | — | — | — | — | — | — | — | — | — | (4,562,875 | ) | — | (4,562,875 | ) | ||||||||||||||||||||||||||||||||||
| Balance at June 30, 2022 | 10,500,000 | $ | 1,050 | 60,000,000 | $ | 6,000 | — | $ | — | 39,081,744 | $ | 3,908 | $ | — | $ | (381,179,025 | ) | $ | 1,008,478 | $ | (380,166,639 | ) | ||||||||||||||||||||||||||
Legacy Bridger Series A Preferred Shares | Legacy Bridger Series B Preferred Shares | Legacy Bridger Series C Preferred Shares / Series A Preferred Stock | Common Stock | Additional Paid-in Capital | Accumulated Deficit | Accumulated Other Comprehensive Income | Total Stockholders’ Deficit | |||||||||||||||||||||||||||||||||||||||||
Share | Value | Share | Value | Share | Value | Share | Value | |||||||||||||||||||||||||||||||||||||||||
| Balance at December 31, 2022 | — | $ | — | — | $ | — | 315,789 | $ | 489,021,545 | 39,081,744 | $ | 3,908 | $ | — | $ | (415,304,343 | ) | $ | 1,678,497 | $ | (413,621,938 | ) | ||||||||||||||||||||||||||
| Unrealized loss on derivative instruments | — | — | — | — | — | — | — | — | — | — | (271,801 | ) | (271,801 | ) | ||||||||||||||||||||||||||||||||||
| Unrealized gain on investment in marketable securities | — | — | — | — | — | — | — | — | — | — | 318,645 | 318,645 | ||||||||||||||||||||||||||||||||||||
| Reclassification of realized gains on investments in marketable securities to earnings | — | — | — | — | — | — | — | — | — | — | (173,152 | ) | (173,152 | ) | ||||||||||||||||||||||||||||||||||
| Foreign currency translation adjustment | — | — | — | — | — | — | — | — | — | — | 192 | 192 | ||||||||||||||||||||||||||||||||||||
| Net loss | — | — | — | — | — | — | — | — | — | (44,684,938 | ) | — | (44,684,938 | ) | ||||||||||||||||||||||||||||||||||
| Effect of the Closing | — | — | — | — | — | (156,362,597 | ) | 4,687,546 | 684 | 52,084,522 | 78,956,576 | — | 131,041,782 | |||||||||||||||||||||||||||||||||||
| Series A Preferred Stock adjustment to maximum redemption value | — | — | — | — | — | 4,274,439 | — | — | (4,274,439 | ) | — | — | (4,274,439 | ) | ||||||||||||||||||||||||||||||||||
| Stock based compensation after reverse recapitalization | — | — | — | — | — | — | 2,400,354 | 240 | 25,596,776 | — | — | 25,597,016 | ||||||||||||||||||||||||||||||||||||
| Balance at March 31, 2023 | — | $ | — | — | $ | — | 315,789 | $ | 336,933,387 | 46,169,644 | $ | 4,832 | $ | 73,406,859 | $ | (381,032,705 | ) | $ | 1,552,381 | $ | (306,068,633 | ) | ||||||||||||||||||||||||||
| Unrealized gain on derivative instruments | — | — | — | — | — | — | — | — | — | — | 203,467 | 203,467 | ||||||||||||||||||||||||||||||||||||
| Unrealized loss on investment in marketable securities | — | — | — | — | — | — | — | — | — | — | (28,301 | ) | (28,301 | ) | ||||||||||||||||||||||||||||||||||
| Reclassification of realized gains on investments in marketable securities to earnings | — | — | — | — | — | — | — | — | — | — | (208,190 | ) | (208,190 | ) | ||||||||||||||||||||||||||||||||||
| Foreign currency translation adjustment | — | — | — | — | — | — | — | — | — | — | 214 | 214 | ||||||||||||||||||||||||||||||||||||
| Net loss | — | — | — | — | — | — | — | — | — | (19,021,602 | ) | — | (19,021,602 | ) | ||||||||||||||||||||||||||||||||||
| Series A Preferred Stock adjustment to maximum redemption value | — | — | — | — | — | 5,805,582 | — | — | (5,805,582 | ) | — | — | (5,805,582 | ) | ||||||||||||||||||||||||||||||||||
| Bonuses paid in Class A Common Stock | — | — | — | — | — | — | 736,554 | 74 | 4,927,546 | — | 4,927,620 | |||||||||||||||||||||||||||||||||||||
| Stock based compensation after reverse recapitalization | — | — | — | — | — | — | — | — | 6,448,568 | — | — | 6,448,568 | ||||||||||||||||||||||||||||||||||||
| Balance at June 30, 2023 | — | $ | — | — | $ | — | 315,789 | $ | 342,738,969 | 46,906,198 | $ | 4,906 | $ | 78,977,391 | $ | (400,054,307 | ) | $ | 1,519,571 | $ | (319,552,439 | ) | ||||||||||||||||||||||||||
For the Six Months Ended June 30, | ||||||||
2023 | 2022 | |||||||
| Cash Flows from Operating Activities: | ||||||||
| Net loss | $ | (63,706,540 | ) | $ | (19,435,884 | ) | ||
| Adjustments to reconcile net loss to net cash used in operating activities | ||||||||
| Loss on sale/disposal of fixed assets | 392,472 | 781,492 | ||||||
| Depreciation and amortization | 4,986,192 | 4,094,854 | ||||||
| Impairment of long-lived assets | 626,848 | — | ||||||
| Stock based compensation expense | 32,045,584 | 4,780 | ||||||
| Change in fair value of the Warrants | (533,000 | ) | — | |||||
| Change in fair value of freestanding derivative | 50,559 | — | ||||||
| Amortization of debt issuance costs | 483,526 | 89,732 | ||||||
| Interest accrued on Legacy Bridger Series B Preferred Shares | — | 3,586,587 | ||||||
| Change in fair value of Legacy Bridger Series C Preferred Shares | — | 945,455 | ||||||
| Change in fair value of Series A Preferred Stock | (224,080 | ) | — | |||||
| Realized gain on investments in marketable securities | (407,761 | ) | — | |||||
| Changes in operating assets and liabilities | ||||||||
Accounts receivable 1 | (11,786,830 | ) | (4,611,847 | ) | ||||
| Aircraft support parts | 1,326,376 | 170,475 | ||||||
| Prepaid expense and other current and noncurrent assets | (3,339,409 | ) | 522,745 | |||||
| Accounts payable, accrued expenses and other liabilities | (13,358,549 | ) | 3,822,406 | |||||
| Net cash used in operating activities | (53,444,612 | ) | (10,029,205 | ) | ||||
| Cash Flows from Investing Activities: | ||||||||
| Investments in construction in progress – buildings | (2,444,633 | ) | (3,983,754 | ) | ||||
| Proceeds from sales and maturities of marketable securities | 42,723,969 | — | ||||||
| Sale of property, plant and equipment | 814,000 | 286,400 | ||||||
| Purchases of property, plant and equipment | (12,528,089 | ) | (5,300,950 | ) | ||||
| Net cash provided by (used in) investing activities | 28,565,247 | (8,998,304 | ) | |||||
| Cash Flows from Financing Activities: | ||||||||
| Payment to Legacy Bridger Series A Preferred Shares members | — | (100,000,000 | ) | |||||
| Payment to Legacy Bridger Series B Preferred Shares members | — | (69,999,223 | ) | |||||
| Borrowing from Legacy Bridger Series C Preferred shares members, net of issuance costs | — | 293,684,675 | ||||||
| Payment of finance lease liability | (15,615 | ) | — | |||||
| Proceeds from the Closing | 3,193,536 | — | ||||||
| Costs incurred related to the Closing | (6,793,574 | ) | — | |||||
| Borrowings from various First Interstate Bank vehicle loans | — | 202,217 | ||||||
| Payment of debt issuance costs | — | (3,000 | ) | |||||
| Repayments on debt | (880,613 | ) | (962,904 | ) | ||||
| Net cash (used in) provided by financing activities | (4,496,266 | ) | 122,921,765 | |||||
| Effects of exchange rate changes | 406 | (263 | ) | |||||
| Net change in cash, cash equivalents and restricted cash | (29,375,225 | ) | 103,893,993 | |||||
| Cash, cash equivalents and restricted cash – beginning of the period | 42,459,626 | 17,261,132 | ||||||
| Cash, cash equivalents and restricted cash – end of the period | $ | 13,084,401 | $ | 121,155,125 | ||||
| Less: Restricted cash – end of the period | 12,239,819 | 3,922,506 | ||||||
| Cash and cash equivalents – end of the period | $ | 844,582 | $ | 117,232,619 | ||||
Supplemental disclosure of non-cash operating and financing activities | ||||||||
| Assumption of Jack Creek liabilities | $ | 7,463,673 | $ | — | ||||
| Recognition of warrant liabilities | $ | 5,863,000 | $ | — | ||||
| Recognition of Deferred underwriting fee | $ | 1,500,000 | $ | — | ||||
Recognition of new right-of-use | $ | 1,092,519 | $ | — | ||||
| Bonuses paid in Class A Common Stock | $ | 4,927,620 | $ | — | ||||
| Deferred offering costs included in accrued expenses and other current liabilities | $ | 388,120 | $ | 1,455,840 | ||||
| Issuance costs on Legacy Bridger Series C Preferred Shares | $ | — | $ | 5,000,000 | ||||
| Supplemental cash flow information | ||||||||
Interest paid 2 | $ | 11,489,494 | $ | 3,715,257 | ||||
| Fixed assets in accounts payable | $ | 1,841,142 | $ | 2,640,384 | ||||
| Conversion of Promissory Note to Common Stock | $ | 897,400 | $ | — | ||||
| Series A Preferred Stock – adjustment for deemed dividend upon Closing | $ | 48,300,000 | $ | — | ||||
| Series A Preferred Stock – adjustment to eliminate 50% multiplier | $ | 156,362,597 | $ | — | ||||
| Series A Preferred Stock – adjustment to maximum redemption value | $ | 10,080,021 | $ | — | ||||
| Legacy Bridger Series A Preferred Shares – adjustment for redemption, extinguishment and accrued interest | $ | — | $ | 85,663,336 | ||||
| Legacy Bridger Series C Preferred Shares – adjustment for maximum redemption value | $ | — | $ | 191,240,782 | ||||
| 1 | Includes related party accounts receivable of $427,454 for the six months ended June 30, 2023. |
| 2 | Includes related party interest paid of approximately $575,000 for the 2022 taxable industrial revenue bond for the six months ended June 30, 2023. |
| • | the surrender and exchange of all 606,061 Legacy Bridger incentive units (“Incentive Units”) into 583,308 shares of Bridger’s common stock, par value $0.0001, (“Common Stock”) at a deemed value of $10.00 per share as adjusted by the per share Common Stock consideration of approximately 0.96246 (the “Exchange Ratio”), rounded down to the nearest share for each holder; |
| • | the direct or indirect surrender and exchange of the remaining 40,000,000 issued and outstanding shares of Legacy Bridger common shares (excluding Incentive Units) into 38,498,436 shares of Common Stock at a deemed value of $10.00 per share as adjusted by the Exchange Ratio, rounded down to the nearest share for each holder; and |
| • | the surrender and exchange of all 315,789.473684 issued and outstanding Series C preferred shares of Legacy Bridger (the “Legacy Bridger Series C Preferred Shares”), which were surrendered and exchanged on a one-to-one |
| additional consideration by the holders into such number of shares of Common Stock as determined by dividing the original issue price, plus accrued interest by a conversion price equal to $11 at the time of conversion. |
| • | the filing and effectiveness of the Amended and Restated Certificate of Incorporation of Bridger and the effectiveness of the Amended and Restated Bylaws of Bridger, each of which occurred immediately prior to the Closing; |
| • | the adoption and assumption of the 2023 Omnibus Incentive Plan and any grants or awards issued thereunder and adoption of the 2023 Employee Stock Purchase Plan upon the Closing to grant equity awards to Bridger employees; and |
| • | during the period from the Closing until five years following the Closing, JCIC subjected 20% of JCIC’s issued and outstanding common stock (“Sponsor Earnout Shares”), comprised of two separate tranches of 50% of the Sponsor Earnout Shares per tranche, to potential forfeiture to Bridger for no consideration until the occurrence (or deemed occurrence) of certain triggering events. |
| • | 43,769,290 shares of Common Stock; |
| • | 315,789.473684 shares of Bridger Series A Preferred Stock; |
| • | 9,400,000 private placement warrants (“Private Placement Warrants”) to purchase shares of Common Stock at an exercise price of $11.50 per share; |
| • | 17,250,000 public warrants (“Public Warrants”) to purchase shares of Common Stock at an exercise price of $11.50 per share; and |
| • | 6,581,497 restricted stock units issued to the executives and senior management of the Company. |
| • | Legacy Bridger equity holders have a relative majority of the voting power of Bridger; |
| • | Bridger’s board of directors (the “Board”) has nine (9) members, and representatives or designees of the Legacy Bridger equity holders comprise the majority of the members of the Board; |
| • | Legacy Bridger’s senior management comprise the senior management roles and are responsible for the day-to-day |
| • | Bridger assumed Legacy Bridger’s name of business; |
| • | The strategy and operations of Bridger continue Legacy Bridger’s former strategy and operations; and |
| • | The Reverse Recapitalization created an operating public company, with management continuing to use Legacy Bridger operations to grow the business. |
For the Three Months Ended June 30, | For the Six Months Ended June 30, | |||||||||||||||
2023 | 2022 | 2023 | 2022 | |||||||||||||
| Fire suppression | $ | 10,449,427 | $ | 11,682,263 | $ | 10,449,427 | $ | 11,682,263 | ||||||||
| Aerial surveillance | 1,123,753 | 1,002,025 | 1,123,753 | 1,002,025 | ||||||||||||
| Other services | 42,100 | 69,383 | 407,473 | 138,675 | ||||||||||||
Total revenues | $ | 11,615,280 | $ | 12,753,671 | $ | 11,980,653 | $ | 12,822,963 | ||||||||
For the Three Months Ended June 30, | For the Six Months Ended June 30, | |||||||||||||||
2023 | 2022 | 2023 | 2022 | |||||||||||||
| Flight revenue | $ | 5,794,315 | $ | 6,417,520 | $ | 5,794,315 | $ | 6,417,520 | ||||||||
| Standby revenue | 5,135,937 | 6,210,976 | 5,135,937 | 6,210,976 | ||||||||||||
| Other revenue | 685,028 | 125,175 | 1,050,401 | 194,467 | ||||||||||||
Total revenues | $ | 11,615,280 | $ | 12,753,671 | $ | 11,980,653 | $ | 12,822,963 | ||||||||
As of June 30, 2023 | As of December 31, 2022 | |||||||
Carrying Value | ||||||||
| Cash equivalents | ||||||||
| Commercial paper | $ | — | $ | 29,890,313 | ||||
| Money market fund | 858,047 | 12,640 | ||||||
| Total cash equivalents | $ | 858,047 | $ | 29,902,953 | ||||
| Restricted cash | ||||||||
| Money market fund | $ | 9,211,360 | $ | 9,284,362 | ||||
As of June 30, 2023 | ||||||||||||||||
Purchase Price | Unrealized Gains | Unrealized Losses | Fair Value | |||||||||||||
| Investment in marketable securities | ||||||||||||||||
| Commercial paper | $ | 4,746,204 | $ | 157,419 | $ | — | $ | 4,903,623 | ||||||||
| Corporate bonds and notes | 2,960,620 | 24,420 | — | 2,985,040 | ||||||||||||
| Government securities | 4,684,574 | — | (287 | ) | 4,684,287 | |||||||||||
| Total marketable securities | $ | 12,391,398 | $ | 181,839 | $ | (287 | ) | $ | 12,572,950 | |||||||
As of December 31, 2022 | ||||||||||||||||
Purchase Price | Unrealized Gains | Unrealized Losses | Fair Value | |||||||||||||
| Investment in marketable securities | ||||||||||||||||
| Commercial paper | $ | 32,635,849 | $ | 277,674 | $ | — | $ | 32,913,523 | ||||||||
| Corporate bonds and notes | 15,413,122 | 3,668 | — | 15,416,790 | ||||||||||||
| Government securities | 6,658,634 | — | (8,791 | ) | 6,649,843 | |||||||||||
| Total marketable securities | $ | 54,707,605 | $ | 281,342 | $ | (8,791 | ) | $ | 54,980,156 | |||||||
As of June 30, 2023 | As of December 31, 2022 | |||||||
| Repairables and expendables | $ | 434,894 | $ | 1,734,292 | ||||
| Other support parts | — | 26,978 | ||||||
| Total aircraft support parts | $ | 434,894 | $ | 1,761,270 | ||||
As of June 30, 2023 | As of December 31, 2022 | |||||||
| Prepaid insurance | $ | 1,669,771 | $ | 968,721 | ||||
| Prepaid subscriptions | 1,173,256 | 770,724 | ||||||
| Other current assets | 49,213 | 95,587 | ||||||
| Total prepaid expenses and other current assets | $ | 2,892,240 | $ | 1,835,032 | ||||
As of June 30, 2023 | As of December 31, 2022 | |||||||
| Aircraft | $ | 188,179,561 | $ | 160,113,061 | ||||
| Less: Accumulated depreciation | (20,344,539 | ) | (16,783,360 | ) | ||||
| Aircraft, net | 167,835,022 | 143,329,701 | ||||||
Construction-in-progress—Aircraft | — | 16,992,010 | ||||||
| Buildings | 16,536,319 | 16,519,231 | ||||||
| Vehicles and equipment | 2,895,113 | 2,810,560 | ||||||
Construction-in-progress | 17,047,327 | 13,780,316 | ||||||
Finance lease right-of-use | 130,378 | 130,378 | ||||||
| Licenses | 234,682 | 234,682 | ||||||
| Less: Accumulated depreciation | (2,628,452 | ) | (1,705,465 | ) | ||||
| Buildings and equipment, net | 34,215,367 | 31,769,702 | ||||||
| Total property, plant and equipment, net | $ | 202,050,389 | $ | 192,091,413 | ||||
As of June 30, 2023 | ||||||||||||||||
Estimated Life (Years) | Gross Carrying Amount | Accumulated Amortization | Net Carrying Amount | |||||||||||||
| Licenses | 10 | $ | 67,623 | $ | (50,558 | ) | $ | 17,065 | ||||||||
Internal-use software | 3 | 296,675 | (158,371 | ) | 138,304 | |||||||||||
| Total intangible assets | $ | 364,298 | $ | (208,929 | ) | $ | 155,369 | |||||||||
As of December 31, 2022 | ||||||||||||||||
Estimated Life (Years) | Gross Carrying Amount | Accumulated Amortization | Net Carrying Amount | |||||||||||||
| Licenses | 10 | $ | 67,623 | $ | (47,177 | ) | $ | 20,446 | ||||||||
Internal-use software | 3 | 296,675 | (108,925 | ) | 187,750 | |||||||||||
| Total intangible assets | $ | 364,298 | $ | (156,102 | ) | $ | 208,196 | |||||||||
As of June 30, 2023 | As of December 31, 2022 | |||||||
| Investment in Overwatch | $ | 1,000,000 | $ | 1,000,000 | ||||
Operating lease right-of-use | 1,638,130 | 671,054 | ||||||
| Interest rate swap | 1,338,801 | 1,407,135 | ||||||
| Prepaid subscriptions | 3,574,764 | 1,246,128 | ||||||
| Other assets | 31,908 | 31,908 | ||||||
| Total other noncurrent assets | $ | 7,583,603 | $ | 4,356,225 | ||||
As of June 30 ,2023 | As of December 31, 2022 | |||||||
| Accrued salaries, wages, and bonuses | $ | 484,340 | $ | 6,515,774 | ||||
Finance right-of-use | 56,012 | 68,310 | ||||||
| Accrued professional fees | 87,961 | 2,291,469 | ||||||
| Embedded derivative of Legacy Bridger Series C Preferred Shares | — | 1,039,330 | ||||||
| Embedded derivative of Series A Preferred Stock | 815,250 | — | ||||||
| Warrant liabilities | 5,329,975 | — | ||||||
| Deferred underwriting fee payable | 1,500,000 | — | ||||||
| Freestanding derivative on Legacy Bridger Series C Preferred Shares | — | 2,186,283 | ||||||
| Accrued interest expense and other accrued liabilities | 6,414,132 | 6,614,065 | ||||||
| Total accrued expenses and other liabilities | 14,687,670 | 18,715,231 | ||||||
| Less: Current accrued expenses and other current liabilities | (7,823,154 | ) | (18,669,572 | ) | ||||
| Total long-term accrued expenses and other noncurrent liabilities | $ | 6,864,516 | $ | 45,659 | ||||
As of June 30, 2023 | ||||||||||
Effective Date | Maturity Date | Notional Amount | Fair Value | Pay Fixed | Receive Rate | |||||
| 4/15/2020 | 3/15/2030 | $10,788,441 | $1,338,801 | 3.887% | 1 Month LIBOR + 2.5% | |||||
As of December 31, 2022 | ||||||||||
Effective Date | Maturity Date | Notional Amount | Fair Value | Pay Fixed | Receive Rate | |||||
| 4/15/2020 | 3/15/2030 | $11,110,484 | $1,407,135 | 3.887% | 1 Month LIBOR + 2.5% | |||||
As of June 30, 2023 | ||||||||||||
Level 1 | Level 2 | Level 3 | ||||||||||
Assets | ||||||||||||
| Cash | $ | 844,582 | $ | — | $ | — | ||||||
| Cash equivalents: | ||||||||||||
| Money market fund | — | — | — | |||||||||
| Total Cash and cash equivalents | 844,582 | — | — | |||||||||
| Restricted cash: | ||||||||||||
| Money market fund | 9,211,360 | — | — | |||||||||
| Other restricted cash | 3,028,459 | — | — | |||||||||
| Total Restricted cash | 12,239,819 | — | — | |||||||||
| Investments in marketable securities | — | 12,572,950 | — | |||||||||
| Interest rate swap | — | 1,338,801 | — | |||||||||
| Total assets | $ | 13,084,401 | $ | 13,911,751 | $ | — | ||||||
Liabilities | ||||||||||||
| Warrant liabilities – Public Warrants | $ | 3,450,000 | $ | — | $ | — | ||||||
| Warrant liabilities – Private Placement Warrants | — | 1,880,000 | — | |||||||||
| Embedded derivative of Series A Preferred Stock | — | — | 815,250 | |||||||||
| Total liabilities | $ | 3,450,000 | $ | 1,880,000 | $ | 815,250 | ||||||
As of December 31, 2022 | ||||||||||||
Level 1 | Level 2 | Level 3 | ||||||||||
Assets | ||||||||||||
| Cash | $ | 259,522 | $ | — | $ | — | ||||||
| Cash equivalents: | ||||||||||||
| Commercial paper | — | 29,890,313 | — | |||||||||
| Money market fund | 12,640 | — | — | |||||||||
| Total Cash and cash equivalents | 272,162 | 29,890,313 | — | |||||||||
| Restricted cash: | ||||||||||||
| Money market fund | 9,284,362 | — | — | |||||||||
| Other restricted cash | 3,012,789 | — | — | |||||||||
| Total Restricted cash | 12,297,151 | — | — | |||||||||
| Investments in marketable securities | — | 54,980,156 | — | |||||||||
| Interest rate swap | — | 1,407,135 | — | |||||||||
| �� | ||||||||||||
| Total assets | $ | 12,569,313 | $ | 86,277,604 | $ | — | ||||||
Liabilities | ||||||||||||
| Freestanding derivative on Legacy Bridger Series C Preferred Shares | $ | — | $ | — | $ | 2,186,283 | ||||||
| Embedded derivative of Legacy Bridger Series C Preferred Shares | — | — | 1,039,330 | |||||||||
| Total liabilities | $ | — | $ | — | $ | 3,225,613 | ||||||
As of June 30, 2023 | As of December 31, 2022 | |||||||
| Permanent loan agreement, dated August 21, 2020, greater of Prime + 1.5% or 4.75% interest rate, maturing August 21, 2035 | $ | 18,734,612 | $ | 18,852,476 | ||||
| Permanent loan agreement, dated October 1, 2020, greater of Prime + 1.5% or 4.75% interest rate, maturing October 1, 2035 | 18,797,058 | 18,924,229 | ||||||
| Term loan agreement dated September 30, 2019, LIBOR + 2.5%, maturing March 15, 2030 | 10,788,441 | 11,110,484 | ||||||
| Term loan agreement dated February 3, 2020, LIBOR + 2.5%, maturing February 3, 2027 | 4,092,000 | 4,371,000 | ||||||
| Taxable industrial revenue bonds, dated July 21, 2022, 11.5% interest rates, maturing September 1, 2027 | 160,000,000 | 160,000,000 | ||||||
| Various term loan agreements, with earliest start at September 9, 2021, 5-5.5% interest rates, latest maturation on November 17, 2027 | 282,537 | 317,073 | ||||||
| Loans payable | 212,694,648 | 213,575,262 | ||||||
| Less: noncurrent debt issuance costs | (4,178,819 | ) | (4,664,552 | ) | ||||
| Less: current debt issuance costs | (995,365 | ) | (993,157 | ) | ||||
| Less: current portion of long-term debt, net of debt issuance costs | (2,459,654 | ) | (2,445,595 | ) | ||||
Total long-term debt, net of debt issuance cost s | $ | 205,060,810 | $ | 205,471,958 | ||||
As of June 30, 2023: | Hangar | |||
| Remainder of 2023 | $ | 758,960 | ||
| 2024 | — | |||
| 2025 | — | |||
| 2026 | — | |||
| 2027 | — | |||
| Thereafter | — | |||
| Total | $ | 758,960 | ||
| Dividend yield (%) | 0 | |||
| Expected volatility (%) | 46.5 | |||
| Risk-free interest rate (%) | 1.26 | |||
| Term (in years) | 5.00 | |||
| Discount for lack of marketability (%) | 30 |
Time-Vesting Incentive Units | Exit-Vesting Incentive Units | |||||||||||||||
Number of Awards | Weighted average grant date fair value | Number of Awards | Weighted average grant date fair value | |||||||||||||
| Unvested as of January 1, 2022 | 242,424 | $ | 0.15 | 80,808 | $ | 0.11 | ||||||||||
| Granted | — | — | — | — | ||||||||||||
| Vested | 80,808 | 0.11 | — | — | ||||||||||||
| Forfeited | — | — | — | — | ||||||||||||
| Unvested as of December 31, 2022 | 161,616 | $ | 0.17 | 80,808 | $ | 0.11 | ||||||||||
| Granted | — | — | — | — | ||||||||||||
| Vested | — | — | — | — | ||||||||||||
| Forfeited | — | — | — | — | ||||||||||||
| Unvested as of June 30, 2023 | 161,616 | $ | 0.17 | 80,808 | $ | 0.11 | ||||||||||
Management Awards | Employee Awards | |||||||||||||||
Number of Awards | Weighted average grant date fair value | Number of Awards | Weighted average grant date fair value | |||||||||||||
| Unvested as of December 31, 2022 | — | $ | — | — | $ | — | ||||||||||
| Granted | 6,581,496 | 9.76 | 2,234,750 | 4.56 | ||||||||||||
| Forfeited | — | — | — | — | ||||||||||||
| Vested | (2,400,354 | ) | 9.00 | — | — | |||||||||||
| Unvested as of June 30, 2023 | 4,181,142 | $ | 10.19 | 2,234,750 | $ | 4.56 | ||||||||||
Redeemable Series A Preferred Stock | ||||||||
Shares | Amounts | |||||||
| Issued as of the Closing Date | 315,789.473684 | $ | 332,658,947 | |||||
| Adjustment to maximum redemption value | — | 10,080,022 | ||||||
| Balance as of June 30, 2023 | 315,789.473684 | $ | 342,738,969 | |||||
Redeemable Legacy Bridger Series C Preferred Shares | ||||||||
Shares | Amounts | |||||||
| Issuance of Legacy Bridger Series C Preferred Shares | 315,789.473684 | $ | 288,332,735 | |||||
| Adjustment to maximum redemption value | — | 202,688,810 | ||||||
| Balance as of December 31, 2022 | 315,789.473684 | $ | 489,021,545 | |||||
For the Three Months Ended June 30, | For the Six Months Ended June 30, | |||||||||||||||
(in USD, except share data) | 2023 | 2022 | 2023 | 2022 | ||||||||||||
Numerator—basic and diluted | ||||||||||||||||
Net loss | $ | (19,021,602 | ) | $ | (4,562,875 | ) | $ | (63,706,540 | ) | $ | (19,435,884 | ) | ||||
| Series A Preferred Stock—adjustment for deemed dividend upon Closing | — | — | (48,300,000 | ) | — | |||||||||||
| Legacy Bridger Series A Preferred Shares—adjustment for redemption, extinguishment and accrued interest | — | (81,323,569 | ) | — | (85,663,336 | ) | ||||||||||
| Legacy Bridger Series C Preferred Shares - adjustment to maximum redemption value | — | (191,240,782 | ) | — | (191,240,782 | ) | ||||||||||
| Series A Preferred Stock—adjustment to eliminate 50% multiplier | — | — | 156,362,598 | — | ||||||||||||
| Series A Preferred Stock—adjustment to maximum redemptions value | (5,805,582 | ) | — | (10,080,022 | ) | — | ||||||||||
| Net (loss) income attributable to Common Stockholders – basic and diluted | $ | (24,827,184 | ) | $ | (277,127,226 | ) | $ | 34,276,036 | $ | (296,340,002 | ) | |||||
For the Three Months Ended June 30, | For the Six Months Ended June 30, | |||||||||||||||
(in USD, except share data) | 2023 | 2022 | 2023 | 2022 | ||||||||||||
Denominator—basic | ||||||||||||||||
| Weighted average Common Stock outstanding—Legacy Bridger shareholders | 38,848,420 | 38,770,646 | 38,848,420 | 38,770,646 | ||||||||||||
| Weighted average Common Stock outstanding—Public shareholders | 2,084,357 | — | 1,819,494 | — | ||||||||||||
| Weighted average Common Stock outstanding—Sponsor and independent directors of JCIC | 1,748,189 | — | 1,526,043 | — | ||||||||||||
| Weighted average vested restricted stock units outstanding | 2,400,354 | — | 2,095,337 | — | ||||||||||||
| Weighted average Class A Common Stock outstanding - bonus paid to executives | 307,572 | — | 154,636 | — | ||||||||||||
| Weighted average Common Stock outstanding—basic | 45,388,892 | 38,770,646 | 44,443,930 | 38,770,646 | ||||||||||||
Denominator—diluted | ||||||||||||||||
| Weighted average Common Stock outstanding—basic | 45,388,892 | 38,770,646 | 44,443,930 | 38,770,646 | ||||||||||||
| Weighted average effect of dilutive securities: | ||||||||||||||||
| Series A Preferred Stock | — | — | 31,158,962 | — | ||||||||||||
| Unvested Restricted Stock Units | — | — | 612,940 | — | ||||||||||||
| Unvested Legacy Bridger Incentive Units | — | — | 236,944 | — | ||||||||||||
| Sponsor Earnout Shares | — | — | 746,353 | — | ||||||||||||
| Weighted average Common Stock outstanding—diluted | 45,388,892 | 38,770,646 | 77,199,129 | 38,770,646 | ||||||||||||
Basic and diluted net (loss) income per share | ||||||||||||||||
| Basic net (loss) income per Common Stock | $ | (0.55 | ) | $ | (7.15 | ) | $ | 0.77 | $ | (7.64 | ) | |||||
| Diluted net (loss) income per Common Stock | $ | (0.55 | ) | $ | (7.15 | ) | $ | 0.44 | $ | (7.64 | ) | |||||
For the Three Months Ended June 30, | For the Six Months Ended June 30, | |||||||||||||||
2023 | 2022 | 2023 | 2022 | |||||||||||||
Shares excluded from diluted net (loss) income per share | ||||||||||||||||
| Series A Preferred Stock | 315,789 | — | — | — | ||||||||||||
| Legacy Series C Preferred Shares | — | 315,789 | — | 315,789 | ||||||||||||
| Unvested Restricted Stock Units | 6,400,892 | — | — | — | ||||||||||||
| Public Warrants | 17,250,000 | — | 17,250,000 | — | ||||||||||||
| Private Placement Warrants | 9,400,000 | — | 9,400,000 | — | ||||||||||||
| Unvested Legacy Bridger Incentive Units | 233,324 | 323,232 | — | 323,232 | ||||||||||||
| Sponsor Earnout Shares | 855,000 | — | — | — | ||||||||||||
| (i) | an error in the accounting for a freestanding instrument which requires separate accounting under ASC 815, Derivatives and Hedging |
As of December 31, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Balance Sheets: | ||||||||||||
| Total assets | $ | 305,978,901 | $ | — | $ | 305,978,901 | ||||||
| Accrued expenses and other current liabilities | 16,483,289 | 2,186,283 | 18,669,572 | |||||||||
| Total current liabilities | 22,120,721 | 2,186,283 | 24,307,004 | |||||||||
| Total liabilities | 228,393,011 | 2,186,283 | 230,579,294 | |||||||||
| Legacy Bridger Series C Preferred Shares | 489,021,545 | — | 489,021,545 | |||||||||
| Accumulated deficit | (413,118,060 | ) | (2,186,283 | ) | (415,304,343 | ) | ||||||
| Total members’ deficit | (411,435,655 | ) | (2,186,283 | ) | (413,621,938 | ) | ||||||
| Total liabilities, mezzanine equity and members’ deficit | $ | 305,978,901 | $ | — | $ | 305,978,901 | ||||||
For the year ended December 31, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Operations: | ||||||||||||
| Interest expense | $ | (20,017,177 | ) | $ | (2,709 | ) | $ | (20,019,886 | ) | |||
| Net loss | $ | (42,121,959 | ) | $ | (2,709 | ) | $ | (42,124,668 | ) | |||
| Legacy Bridger Series C Preferred Shares adjustment for maximum redemption value | (200,505,236 | ) | (2,183,574 | ) | (202,688,810 | ) | ||||||
| Net loss attributable to common shareholders | $ | (328,290,531 | ) | $ | (2,186,283 | ) | $ | (330,476,814 | ) | |||
| Net loss per share attributable to common shareholders – basic and diluted | $ | (8.15 | ) | $ | (0.05 | ) | $ | (8.20 | ) | |||
For the year ended December 31, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Members’ Equity: | ||||||||||||
| Legacy Bridger Series C Preferred Shares adjustment for maximum redemption value | $ | (200,505,236 | ) | $ | (2,183,574 | ) | $ | (202,688,810 | ) | |||
| Net loss | (42,121,959 | ) | (2,709 | ) | (42,124,668 | ) | ||||||
| Accumulated deficit | (413,118,060 | ) | (2,186,283 | ) | (415,304,343 | ) | ||||||
| Accumulated other comprehensive income | 1,678,497 | — | 1,678,497 | |||||||||
| Total members’ deficit | $ | (411,435,655 | ) | $ | (2,186,283 | ) | $ | (413,621,938 | ) | |||
For the year ended December 31, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Cash Flows: | ||||||||||||
| Cash Flows from Operating Activities: | ||||||||||||
| Net loss | $ | (42,121,959 | ) | $ | (2,709 | ) | $ | (42,124,668 | ) | |||
| Change in fair value of freestanding derivative | — | 2,709 | 2,709 | |||||||||
| Net cash used in operating activities | (9,917,608 | ) | — | (9,917,608 | ) | |||||||
| Net change in cash, cash equivalents, and restricted cash | 25,198,494 | — | 25,198,494 | |||||||||
| Cash, cash equivalents and restricted cash and cash equivalents – end of period | $ | 42,459,626 | $ | — | $ | 42,459,626 | ||||||
| Cash and cash equivalents – end of period | $ | 30,162,475 | $ | — | $ | 30,162,475 | ||||||
As of September 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Balance Sheets: | ||||||||||||
| Total assets | $ | 320,554,139 | $ | — | $ | 320,554,139 | ||||||
| Accrued expenses and other current liabilities | 12,355,584 | 2,124,265 | 14,479,849 | |||||||||
| Total current liabilities | 19,472,020 | 2,124,265 | 21,596,285 | |||||||||
| Total liabilities | $ | 226,008,817 | $ | 2,124,265 | $ | 228,133,082 | ||||||
| Series C Preferred shares | 483,385,214 | — | 483,385,214 | |||||||||
| Accumulated deficit | (390,307,424 | ) | (2,124,265 | ) | (392,431,689 | ) | ||||||
| Total members’ deficit | (388,839,892 | ) | (2,124,265 | ) | (391,036,037 | ) | ||||||
| Total liabilities, mezzanine equity and members’ deficit | $ | 320,554,139 | $ | — | $ | 320,554,139 | ||||||
For the nine months ended September 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Operations: | ||||||||||||
| Interest expense | $ | (13,052,438 | ) | $ | 59,309 | $ | (12,993,129 | ) | ||||
| Net loss | $ | (25,117,707 | ) | $ | 59,309 | $ | (25,058,398 | ) | ||||
| Legacy Bridger Series C Preferred Shares adjustment for maximum redemption value | (194,700,545 | ) | (2,183,574 | ) | (196,884,119 | ) | ||||||
| Net loss attributable to common shareholders | $ | (305,481,588 | ) | $ | (2,124,265 | ) | $ | (307,605,853 | ) | |||
| Net loss per share attributable to common shareholders – basic and diluted | $ | (7.58 | ) | $ | (0.06 | ) | $ | (7.64 | ) | |||
For the nine months ended September 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Members’ Equity: | ||||||||||||
| Legacy Bridger Series C Preferred Shares adjustment for maximum redemption value | $ | (194,700,545 | ) | $ | (2,183,574 | ) | $ | (196,884,119 | ) | |||
| Net loss | (25,117,707 | ) | 59,309 | (25,058,398 | ) | |||||||
| Accumulated deficit | (390,307,424 | ) | (2,124,265 | ) | (392,431,689 | ) | ||||||
| Total members’ deficit | $ | (388,839,892 | ) | $ | (2,124,265 | ) | $ | (390,964,157 | ) | |||
For the nine months ended September 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Cash Flows: | ||||||||||||
| Cash Flows from Operating Activities: | ||||||||||||
| Net loss | $ | (25,117,707 | ) | $ | 59,309 | $ | (25,058,398 | ) | ||||
| Change in fair value of freestanding derivative | — | (59,309 | ) | (59,309 | ) | |||||||
| Net cash used in by operating activities | (7,930,502 | ) | — | (7,930,502 | ) | |||||||
| Net change in cash, cash equivalents, and restricted cash | 89,107,304 | — | 89,107,304 | |||||||||
| Cash, cash equivalents and restricted cash and cash equivalents – end of period | $ | 106,368,436 | $ | — | $ | 106,368,436 | ||||||
| Cash and cash equivalents – end of period | $ | 94,143,466 | $ | — | $ | 94,143,466 | ||||||
As of June 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Balance Sheets: | ||||||||||||
| Total assets | $ | 309,603,293 | $ | — | $ | 309,603,293 | ||||||
| Accrued expenses and other current liabilities | 10,359,417 | 2,183,574 | 12,542,991 | |||||||||
| Total current liabilities | 32,207,636 | 2,183,574 | 34,391,210 | |||||||||
| Total liabilities | 209,837,425 | 2,183,574 | 212,020,999 | |||||||||
| Series C Preferred shares | 477,741,883 | — | 475,558,309 | |||||||||
| Accumulated deficit | (378,984,493 | ) | (2,183,574 | ) | (381,168,067 | ) | ||||||
| Total members’ deficit | (377,976,015 | ) | (2,183,574 | ) | (380,159,589 | ) | ||||||
| Total liabilities, mezzanine equity and members’ deficit | $ | 309,603,293 | $ | — | $ | 309,603,293 | ||||||
For the six months ended June 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Operations: | ||||||||||||
| Net loss | $ | (19,435,884 | ) | $ | — | $ | (19,435,884 | ) | ||||
| Legacy Bridger Series C Preferred Shares adjustment for maximum redemption value | (189,057,208 | ) | (2,183,574 | ) | (191,240,782 | ) | ||||||
| Net loss attributable to common shareholders | $ | (294,156,428 | ) | $ | (2,183,574 | ) | $ | (296,340,002 | ) | |||
| Net loss per share attributable to common shareholders – basic and diluted | $ | (7.30 | ) | $ | (0.06 | ) | $ | (7.36 | ) | |||
For the six months ended June 30, 2022 | ||||||||||||
As Previously Reported | Impact of Revision | As Revised | ||||||||||
Statements of Members’ Equity: | ||||||||||||
Legacy Bridger Series C Preferred Shares adjustment for maximum redemption value | $ | (189,057,208 | ) | $ | (2,183,574 | ) | $ | (191,240,782 | ) | |||
Net loss | (19,435,884 | ) | — | (19,435,884 | ) | |||||||
Accumulated deficit | (378,984,493 | ) | (2,183,574 | ) | (381,168,067 | ) | ||||||
Accumulated other comprehensive income | 1,008,478 | — | 1,008,478 | |||||||||
Total members’ deficit | $ | (377,976,015 | ) | $ | (2,183,574 | ) | $ | (380,159,589 | ) | |||
$70,000,000

Shares of Common Stock
PROSPECTUS
Joint Book-Running Managers
Stifel
BTIG
Canaccord Genuity
, 2023
PART II
INFORMATION NOT REQUIRED IN PROSPECTUS
| Item 13. | Other Expenses of Issuance and Distribution. |
The following sets forth the estimated costs and expenses (all of which are to be paid by the registrant), other than underwriting discounts and commissions, in connection with the offering of the securities being registered hereby. All of the amounts shown are estimates except for the SEC registration fee and the FINRA filing fee.
SEC registration fee | $ | 11,882 | ||
FINRA filing fee | 12,575 | |||
Legal fees and expenses | 350,000 | |||
Accounting fees and expenses | 150,000 | |||
Transfer agent and registrar fees | 4,500 | |||
Printing, miscellaneous fees and expenses | 225,000 | |||
|
| |||
Total | $ | 753,957 | ||
|
|
| Item 14. | Indemnification of Directors and Officers. |
Section 145(a) of the DGCL provides, in general, that a corporation may indemnify any person who was or is a party to or is threatened to be made a party to any threatened, pending or completed action, suit or proceeding, whether civil, criminal, administrative or investigative (other than an action by or in the right of the corporation), because he or she is or was a director, officer, employee or agent of the corporation, or is or was serving at the request of the corporation as a director, officer, employee or agent of another corporation, partnership, joint venture, trust or other enterprise, against expenses (including attorneys’ fees), judgments, fines and amounts paid in settlement actually and reasonably incurred by the person in connection with such action, suit or proceeding, if he or she acted in good faith and in a manner he or she reasonably believed to be in or not opposed to the best interests of the corporation and, with respect to any criminal action or proceeding, had no reasonable cause to believe his or her conduct was unlawful.
Section 145(b) of the DGCL provides, in general, that a corporation may indemnify any person who was or is a party or is threatened to be made a party to any threatened, pending or completed action or suit by or in the right of the corporation to procure a judgment in its favor because the person is or was a director, officer, employee or agent of the corporation, or is or was serving at the request of the corporation as a director, officer, employee or agent of another corporation, partnership, joint venture, trust or other enterprise, against expenses (including attorneys’ fees) actually and reasonably incurred by the person in connection with the defense or settlement of such action or suit if he or she acted in good faith and in a manner he or she reasonably believed to be in or not opposed to the best interests of the corporation, except that no indemnification shall be made with respect to any claim, issue or matter as to which he or she shall have been adjudged to be liable to the corporation unless and only to the extent that the Court of Chancery or other adjudicating court determines that, despite the adjudication of liability but in view of all of the circumstances of the case, he or she is fairly and reasonably entitled to indemnity for such expenses that the Court of Chancery or other adjudicating court shall deem proper.
Section 145(g) of the DGCL provides, in general, that a corporation may purchase and maintain insurance on behalf of any person who is or was a director, officer, employee or agent of the corporation, or is or was serving at the request of the corporation as a director, officer, employee or agent of another corporation, partnership, joint venture, trust or other enterprise against any liability asserted against such person and incurred by such person in any such capacity, or arising out of his or her status as such, whether or not the corporation would have the power to indemnify the person against such liability under Section 145 of the DGCL.
II-1
Section 102(b)(7) of the DGCL provides that a corporation’s certificate of incorporation may contain a provision eliminating or limiting the personal liability of a director or officer to the corporation or its stockholders for monetary damages for breach of fiduciary duty as a director or officer, provided that such provision shall not eliminate or limit liability (i) for the director or officer for any breach of the director or officer’s duty of loyalty to the corporation or its stockholders, (ii) for the director or officer for acts or omissions not in good faith or which involve intentional misconduct or a knowing violation of law, (iii) for the director under Section 174 of the DGCL (iv) the director or officer for any transaction from which the director derived an improper personal benefit or (v) for the officer for any action by or in the right of the corporation.
The Company’s amended and restated certificate of incorporation provides for indemnification of its directors, officers, employees and other agents to the maximum extent permitted by the DGCL.
In addition, effective upon the consummation of the Business Combination, the Company entered into indemnification agreements with each of its directors and officers. These agreements require the Company to indemnify these individuals to the fullest extent permitted under Delaware law against liabilities that may arise by reason of their service to the Company, and to advance expenses incurred as a result of any proceeding against them as to which they could be indemnified. The Company also intends to enter into indemnification agreements with its future directors and officers.
The underwriting agreement provides for indemnification by the underwriters of the Company and its officers and directors, and by the Company of the underwriters, for certain liabilities arising under the Securities Act or otherwise in connection with the offering.
| Item 15. | Recent Sales of Unregistered Securities. |
In reliance on the exemptions provided by Section 4(a)(2) of the Securities Act as a transaction not involving a public offering and/or Rule 506 promulgated thereunder, we have made sales of the following unregistered securities in the past three years:
| 1. | The issue and sale of 100 shares of our Common Stock to JCIC for the aggregate consideration of $1.00 on July 27, 2022, in connection with the formation of the Company. |
| 2. | The issue and sale of 39,081,744 shares of our Common Stock and 305,263.157895 shares of Series A Preferred Stock on January 24, 2023 to certain former equityholders of Legacy Bridger in connection with the consummation of the Business Combination and in exchange for such equityholders’ equity interests in Legacy Bridger. The Business Combination valued Legacy Bridger in the aggregate at an implied pre-money enterprise value of $807,600,000. |
| 3. | The issue and sale of 426,531 shares of our Common Stock on September 12, 2023 to the sellers of Ignis upon the closing of our acquisition of Ignis. |
| Item 16. | Exhibits and Financial Statement Schedules. |
(a) Exhibits
II-2
II-3
II-4
II-5
II-6
Exhibit Number | Description | |
| 101.SCH* | XBRL Taxonomy Extension Schema Document | |
| 101.CAL* | XBRL Taxonomy Extension Calculation Linkbase Document | |
| 101.DEF* | XBRL Taxonomy Extension Definition Linkbase Document | |
| 101.LAB* | XBRL Taxonomy Extension Label Linkbase Document | |
| 101.PRE* | XBRL Taxonomy Extension Presentation Linkbase Document | |
| 104* | Cover Page Interactive Data File (formatted as Inline XBRL and contained in Exhibit 101). | |
| 107* | Filing Fee Table | |
| * | Filed herewith. |
| + | Schedules and exhibits have been omitted pursuant to Item 601(b)(2) of Regulation S-K. Bridger Aerospace Group Holdings, Inc. agrees to furnish supplementally a copy of any omitted schedule or exhibit to the SEC upon request. |
| ++ | Portions of this exhibit have been redacted pursuant to Item 601(b)(10)(iv) of Regulation S-K. |
| # | Indicates management contract or compensatory plan. |
| Item 17. | Undertakings. |
(a) The undersigned registrant hereby undertakes:
(1) For purposes of determining any liability under the Securities Act, the information omitted from the form of prospectus filed as part of this registration statement in reliance upon Rule 430A and contained in a form of prospectus filed by the registrant pursuant to Rule 424(b)(1) or (4) or 497(h) under the Securities Act shall be deemed to be part of this registration statement as of the time it was declared effective.
(2) For the purpose of determining any liability under the Securities Act, each post-effective amendment that contains a form of prospectus shall be deemed to be a new registration statement relating to the securities offered therein, and the offering of such securities at that time shall be deemed to be the initial bona fide offering thereof.
(b) Insofar as indemnification for liabilities arising under the Securities Act may be permitted to directors, officers and controlling persons of the registrant pursuant to the foregoing provisions, or otherwise, the registrant has been advised that in the opinion of the SEC such indemnification is against public policy as expressed in the Securities Act and is, therefore, unenforceable. In the event that a claim for indemnification against such liabilities (other than the payment by the registrant of expenses incurred or paid by a director, officer or controlling person of the registrant in the successful defense of any action, suit or proceeding) is asserted by such director, officer or controlling person in connection with the securities being registered, the registrant will, unless in the opinion of its counsel the matter has been settled by controlling precedent, submit to a court of appropriate jurisdiction the question whether such indemnification by it is against public policy as expressed in the Securities Act and will be governed by the final adjudication of such issue.
II-7
SIGNATURES
Pursuant to the requirements of the Securities Act of 1933, as amended, Bridger Aerospace Group Holdings, Inc. has duly caused this Registration Statement to be signed on its behalf by the undersigned, thereunto duly authorized, in the city of Belgrade, Montana, on the 17th day of October, 2023.
| BRIDGER AEROSPACE GROUP HOLDINGS, INC. | ||
By: | /s/ Timothy Sheehy | |
| Name: Timothy Sheehy | ||
| Title: Chief Executive Officer | ||
Power of Attorney
KNOW ALL PERSONS BY THESE PRESENTS, that each person whose signature appears below constitutes and appoints Timothy Sheehy and James Muchmore, and each of them, as his or her true and lawful attorneys-in-fact and agents, each with full power of substitution and revocation, for him or her and in his or her name, place and stead, in any and all capacities, to execute any or all amendments (including post-effective amendments) and supplements to this registration statement and any and all related registration statements pursuant to Rule 462(b) of the Securities Act, and to file the same, with all exhibits thereto, and other documents in connection therewith, with the Securities and Exchange Commission, hereby ratifying and confirming all that said attorneys-in-fact and agents, or any of them, or their substitute or substitutes, may lawfully do or cause to be done by virtue hereof.
Pursuant to the requirements of the Securities Act of 1933, this registration statement has been signed by the following persons in the capacities and on the dates indicated:
Signatures | Title | Date | ||
/s/ Timothy Sheehy Timothy Sheehy | Chief Executive Officer and Director (Principal Executive Officer) | October 17, 2023 | ||
/s/ Eric Gerratt Eric Gerratt | Chief Financial Officer (Principal Accounting and Financial Officer) | October 17, 2023 | ||
/s/ Jeffrey Kelter Jeffrey Kelter | Director and Chairman of the Board | October 17, 2023 | ||
/s/ Anne Hayes Anne Hayes | Director | October 17, 2023 | ||
/s/ Dean Heller Dean Heller | Director | October 17, 2023 | ||
/s/ Todd Hirsch Todd Hirsch | Director | October 17, 2023 | ||
/s/ Wyman Howard Wyman Howard | Director | October 17, 2023 | ||
/s/ McAndrew Rudisill McAndrew Rudisill | Chief Investment Officer and Director | October 17, 2023 | ||
/s/ Robert Savage Robert Savage | Director | October 17, 2023 | ||
II-8
Signatures | Title | Date | ||
/s/ Matthew Sheehy Matthew Sheehy | Director | October 17, 2023 | ||
II-9