Security Requires Securing Identities Identity risk is everywhere: - Military and National Defense - Antiterrorism - Law Enforcement and Border Control - Enterprise and e-Government Services - Transportation (automotive, aircraft, and maritime security) - Credit Card / Banking, Healthcare and Education Where There's Identity Risk, There's an L-1 ID Solution.

Identity Risk is Everywhere ID THEFT 101: BEAUTY CONSID THEFT 101: BEAUTY CONS September 22, 2007 Unisys probed for HER WAY ONTO IVYS' ROLLSROLLS September 22, 2007 Unisys probed for Homeland SecurityHomeland Security Spitzer GrantsSpitzer Grants By LUKAS I. ALPERT breach: report breach: report Illegal Immigrants January Children Are8, 2007 -- A cunning co-ed con artist was able to dupe some of the nation's top Illegal Immigrants September 24, 2007 universities January Children 8, - including 2007 -- AHarvard cunning and co-ed Columbia con Areartist - into wasgranting her admission by stealing otherable to dupe some of the nation's top September 24, 2007 people's universities identities, - including including Harvard that of and a woman Columbia Federal Tradewho - into hasgranting been missing her admission by for more than sevenstealing other Easier Access to years, people's Not Immune toinvestigators identities, have including discovered. that of a woman who has been missing for more than seven Easier Access to years, Not investigators Immune have discovered.Commission statisticsto WASHINGTON (Reuters) - The FBI is Esther Elizabeth Reed, 28, managed to attend Columbia University as a graduate student for WASHINGTON (Reuters) - The FBI is two Esther yearsElizabeth under theReed, name28, Brooke managed Henson to attend beforeColumbia investigators University caughtas wind a graduate of the scam laststudent for Driver's Licenses investigating allegations that Unisys Corp failed to summer. two years under the name Brooke Henson indicate that thebefore investigators caught wind of the scam last Driver's Licenses detect a Chinese Web site's cyber break-ins on computers atinvestigating allegations that Unisys Corp failed to Identity Theft summer. Identity Theft the U.S. Department of Homeland Security and then tried todetect Chinese Web site's cyber break-ins on computers at cover up its shortcomings, The Washington Post the U.S. Department of Homeland Security andreported onthen tried to 60% of Americans percentage of identitysay they Monday. cover up its shortcomings, The Washington Post reported on 60% of Americans say they By NINA BERNSTEIN Unisys won a $1 billion contract in 2002 to build and manageMonday. know little abouttheft victims youngerchild By NINA BERNSTEIN information technology networks at the department and theUnisys won a $1 billion contract in 2002 to build and manage know little about child New York State, home to more than 500,000 illegal Transportation Security Administration. But evidence gatheredinformation technology networks the department and identity theft than 18 has virtually immigrants, will issue driver's licenses without regard toNew York State, home to more than 500,000 illegal by the Homeland Security Committee of the U.S. House ofTransportation Administration. But evidence gathered identity theft immigration status under a policy change announcedimmigrants, will issue driver's licenses without regard to Representatives indicates network-intrusion devices were notby the Homeland Security Committee of the U.S. House of immigration status under a policy change announced properly installed and monitored, the Post said. Representatives indicates network-intrusion devices were not More than 60 percent of Americans doubled in the pastsay they know little yesterday by Gov. Eliot Spitzer. properly installed and monitored, the Post said. about child identity theft and nearly half think the problemMore than 60 percent of Americans say they know little The change rolls back rules adopted four years ago under theyesterday by Gov. Eliot Spitzer. As a result, some 150 DHS computers were compromised by As result, some 150 DHS computers were compromised by is not very common, even though Federal about child identity theft and nearly halfTrade think the problem Pataki administration The change rolls back that rules made adopted it difficult, fourifyears not impossible, ago under the hackers using a Chinese-language Web site from June through few years. hackers using a Chinese-language Web site from June through Commission statistics indicate that the percentage ofnot very common, even though Federal Trade for tens of thousands Pataki administration Monster.com Data Theftofthat immigrants made it difficult, to obtainifdriver's not impossible, October in 2006. Monster.com Data TheftOctober in 2006. identity Commission theft victims younger than 18 has virtually doubledstatistics indicate that the percentage of licenses because they could not prove legal status. Under thefor tens of thousands of immigrants to obtain driver's Unisys, based in Blue Bell, Pennsylvania, disputed the charge Unisys, based Blue Bell, Pennsylvania, disputed charge inidentity the past few years. theft victims younger than 18 has virtually doubled new rules, the licenses because Department they could of Motor not prove Vehicles legal will status. accept Under thea with a statement saying: "We Ameritrade lost 6.3can state generally that the with statement saying: "We can state generally that the Although in the past few the FTC reports that 5 percent of all ID theftyears. current foreign new rules, may be Bigger thepassport Department as proof Motor of identity Vehicles without will accept aalso allegation that Unisys did not Ameritrade lost 6.3properly install essential security may be Bigger allegation that Unisys did not properly install essential security victims are children, a recent poll by ConsumerInfo.com, anAlthough the FTC reports that 5 percent of all ID theft requiring a valid yearlong visa or other evidence of legalcurrent foreign passport as proof of identity without also systems is incorrect. In addition, we routinely follow prescribed systems is incorrect. In addition, we routinely follow prescribed Experian victims are company (also known as "Experian Consumerchildren, recent poll by ConsumerInfo.com, an immigration. requiring Symantec says a Trojan targeting the job sitevalid yearlong visa or other evidence of legal security protocols and have million names fromproperly reported incidents to the security protocols and have properly reported incidents to the Direct"), Experian indicates that more than half those polled think itcompany (also known as "Experian Consumer The policy, which immigration. Symantec says a Trojan targeting the job sitedoes not require legislative approval, will be customer in accordance with million names fromthose protocols. customer in accordance with those protocols. unlikely their own children could fall victim to the crime.Direct"), indicates that more than half those polled think it phased in starting The policy, has stolen more than 1.6 million records.which indoes December not require and will legislative be tied to approval, new will be The survey of more than 1,000 adults also indicates thatunlikely their own children could fall victim to the crime. antifraud measures, phased in starting has stolen more than 1.6 million records.the in December governor and said.will Those be tied measures to new will database Americans have major misconceptions about how ID theft -- The survey of more than 1,000 adults also indicates that include the authentication of foreign passports and the use ofantifraud measures, governor said. Those measures will database especially that perpetrated against children -- Americans have major misconceptions about occurs. how ID theft --photo comparison include the Gregg Keizer, Computerworld authentication technology ofto foreign ensure passports that no driver and the has use of especially that perpetrated against children -- occurs. more than one photo comparison Gregg Keizer, Computerworld license. technology to ensure that no driver has By Giselle Abramovich more than Monday, August 20, 2007 08:00 AM PDT one license. By Giselle Abramovich "As soon as a child has a Social Security number, he or she Monday, August 20, 2007 08:00 AM PDT September 26th, 2007 is at risk of becoming a victim of identity theft," says"As soon as a child has a Social Security number, he or she The 46,000 people reportedly infected by ads on job sites may be only a fraction of the victims September 26th, 2007 Maxine Sweet, vice president of public education foris at risk of becoming a victim of identity theft," says of an ambitious, multistage attack that has stolen data belonging to several hundred thousandThe 46,000 people reportedly infected by ads on job sites may be only fraction of the victims Experian. Maxine Sweet, vice president of public education for TD Ameritrade Holding Corporation, an online brokerage company, said people who posted resumes on Monster.com, a researcher said this of an ambitious, multistage attack that has stolen data belonging toweekend. several hundred thousand Experian. one of its databases was hacked into and the personal information forTD Ameritrade Holding Corporation, online brokerage company, said According to Symantec Corp. security analyst Amado Hidalgo, a new Trojan horse calledpeople who posted resumes on Monster.com, researcher said this weekend. one of its databases was hacked into and the personal information for more than 6.3 million customers was stolen. The company found Infostealer.Monstres by Symantec has stolen more than 1.6 million records belonging toAccording to Symantec Corp. security analyst Amado Hidalgo, a new Trojan horse called more than 6.3 million customers was stolen. The company found malicious code in one of its databases. several hundred thousand people from Monster Worldwide Inc.'s job search service. That dataInfostealer.Monstres by Symantec has stolen more than 1.6 million records belonging to malicious code in one of its databases. is then used to target the Monster.com users with credible phishing mail that plants moreseveral hundred thousand people from Monster Worldwide Inc.'s job search service. That data However, the firm said that Social Security numbers and account malware on their machines. is then used to target the Monster.com users with credible phishing mail that plants more However, the firm said that Social Security numbers and account numbers were not taken. Ameritrade started notifying its customers malware on their machines. numbers were not taken. Ameritrade started notifying its customers about the data theft September 14, and posted information about the event on its corporate Web site. about the data theft September 14, and posted information about the event on its corporate Web site.

L-1 Strategic Vision Build the premier identity solutions company - Protect and secure personal identities through leading biometric technologies - Deliver customized multi-modal solutions for unique customer situations - Significant internal research and development program A disciplined fiscal operating model delivers strong and predictable results - Achieve organic growth in excess of 20% annually complimented by a focused acquisition strategy - Profitable, with solid margins and strong cash flow - Deliver exceptional shareholder value

L-1 Identity Solutions Today o L-1 has moved from a niche provider to become a comprehensive global end-to-end identity solutions company - Efficient Enrollment Systems - Effective Large-Scale Biometric ID Capabilities - Customized Usage Applications for Verification and Real Time ID - Solutions that Shape and Conform to Interoperability Standards o Proven Management Team and Over 1,600 employees globally o Headquartered in Stamford, CT with offices located throughout the U.S. and Europe o U.S. Based Technology Development o Achieved EBITDA profitability, publicly-traded on the NYSE: ID
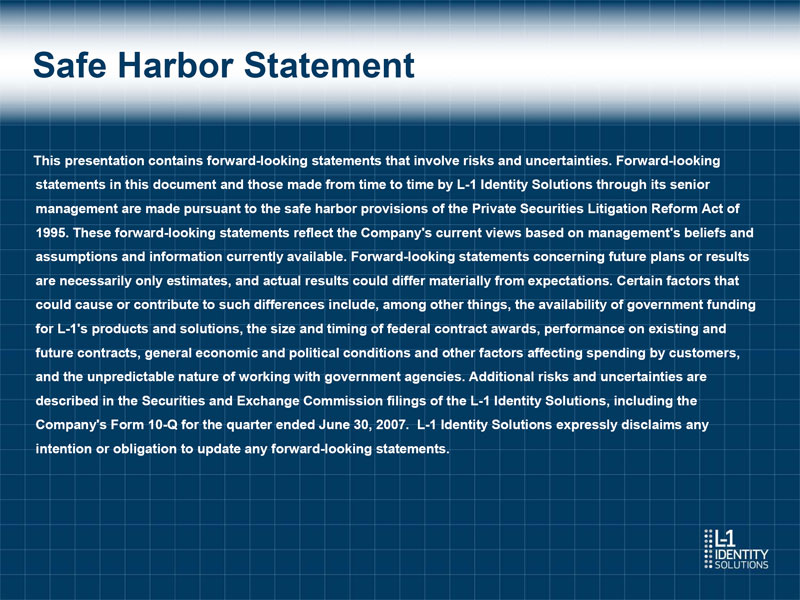
The Largest, Fastest Growing Biometrics Company SOURCE: ASMAG.COM "SECURITY TOP 50" 2007

Team of Industry Experts Corporate Executive Management Team o Robert V. LaPenta Chairman, President and CEO o Dr. Joseph Atick EVP and Chief Strategic Officer o James A. DePalma EVP, Chief Financial Officer and Treasurer o Mark S. Molina EVP, Chief Legal Officer and Secretary o Joe Paresi EVP and Chief Marketing Officer o Doni Fordyce EVP of Corporate Communications o Vincent A. D'Angelo SVP of Finance Experienced and Knowledgeable Board of Directors o Robert V. LaPenta o John E. Lawler o B.G. Beck o Admiral James Loy o Denis K. Berube o Harriet Mouchly-Weiss o Milton Cooper o Peter Nessen o Robert Gelbard o B. Boykin Rose o Malcolm J. Gudis o George J. Tenet
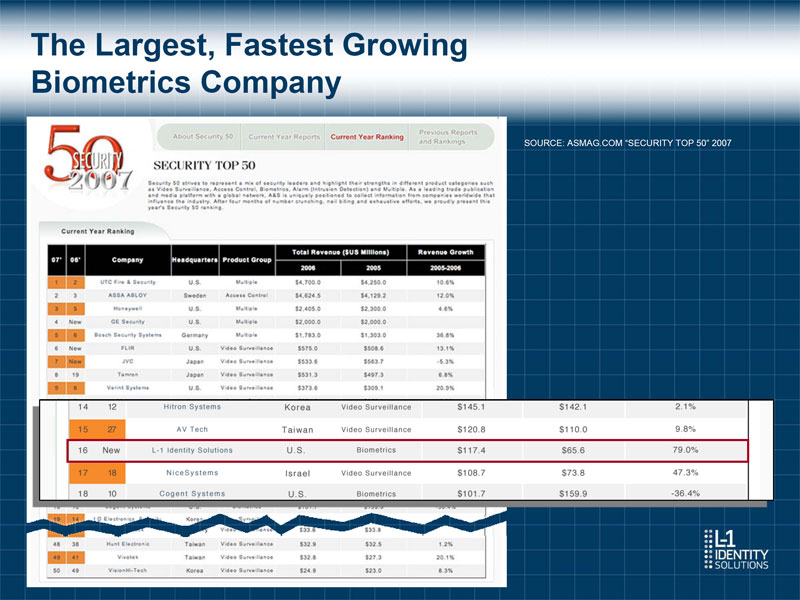
Acquisitions December December February July AutoTest Division of August December Openshaw Media Group 2005 2006 2007 February August October July
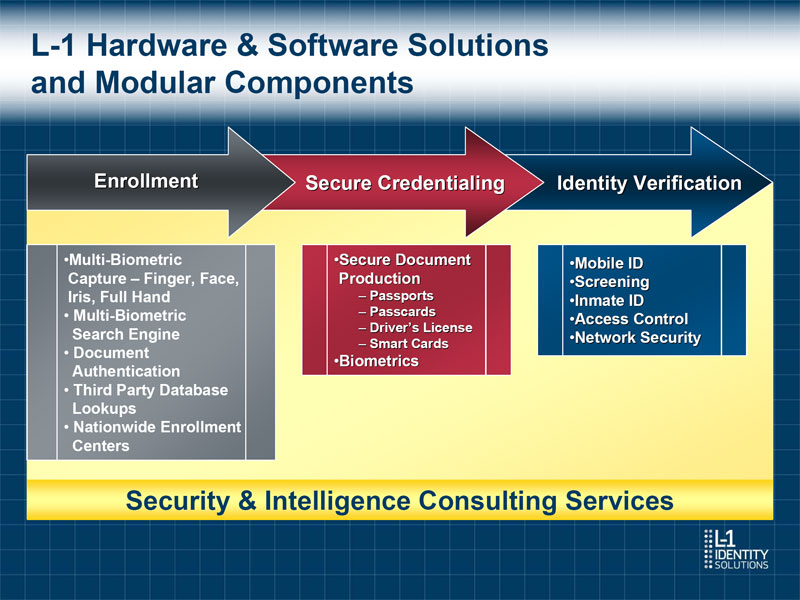
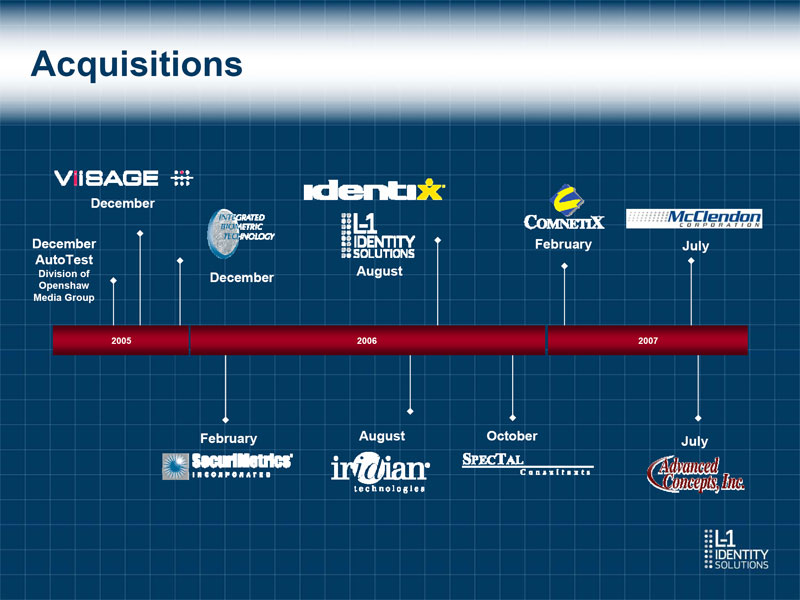
L-1 Hardware & Software Solutions and Modular Components Enrollment Secure Credentialing Identity Verification oMulti-Biometric oSecure Document oMobile ID Capture - Finger, Face, Production oScreening Iris, Full Hand - Passports oInmate ID o Multi-Biometric - Passcards oAccess Control Search Engine - Driver's License - Smart Cards oNetwork Security o Document oBiometrics Authentication o Third Party Database Lookups o Nationwide Enrollment Centers Security & Intelligence Consulting Services

Enrollment: Biometric Capture Systems DFR(R) Readers TP-4100 ED TouchPrint(TM) Enhanced Definition Booking Stations FaceIt(R) Quality HIIDE(TM) Assessment Software
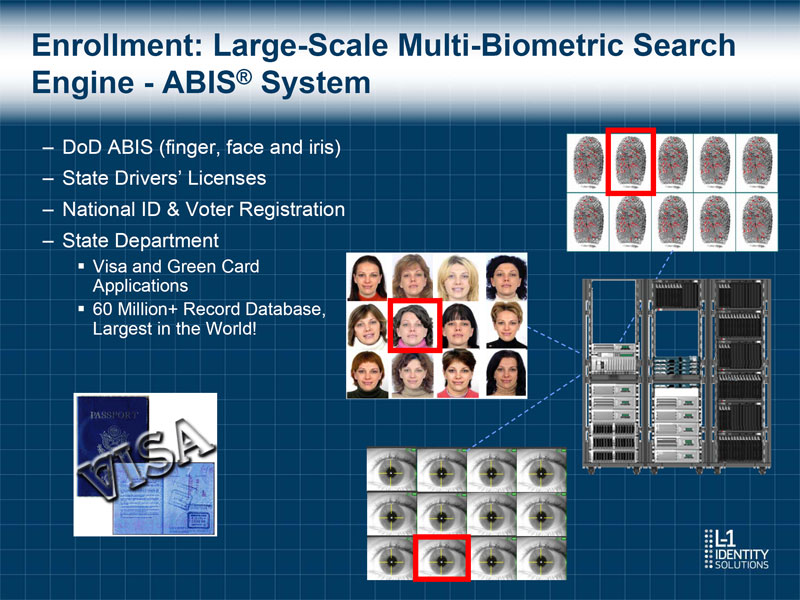
Enrollment: Large-Scale Multi-Biometric Search Engine - ABIS(R) System - DoD ABIS (finger, face and iris) - State Drivers' Licenses - National ID & Voter Registration - State Department o Visa and Green Card Applications o 60 Million+ Record Database, Largest in the World!
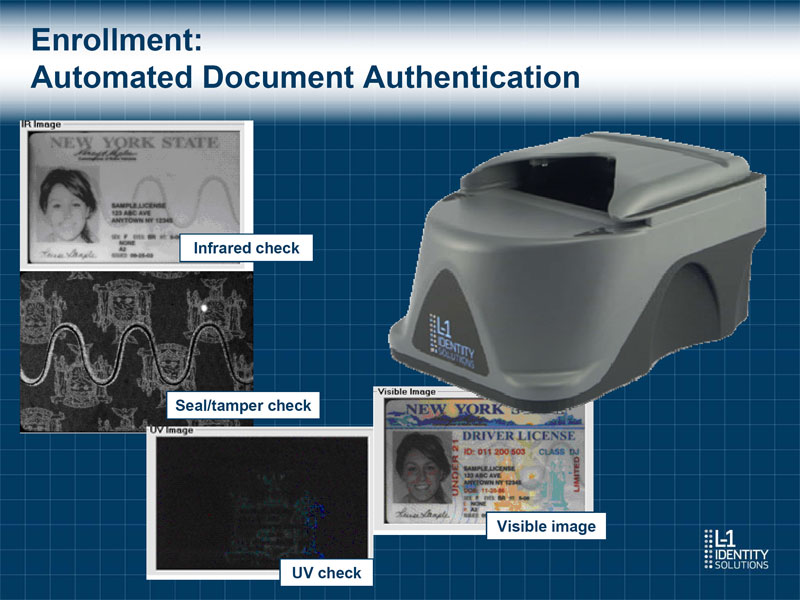
Enrollment: Automated Document Authentication Infrared check Seal/tamper check Visible image UV check

Enrollment: Services o Total Business & Technology Infrastructure for Outsourcing Biometric Capture - ~500 Locations Across the USA and Canada - Four Million People Fingerprinted To-Date - Current Rate 1 Million per Year o Key Contracts - TSA HAZPRINT - HSPD-12 - TWIC

Secure Credentialing o L-1 Has Delivered Over 165 Million Secure Credentials - Produce 35M Credentials/Year at More Than 2000 Locations - High Resolution, Non-Fading Image Printing - Central Issuance and Over-the-Counter DMV Solutions o Key Contracts - U.S. Passport - DoD Common Access Card - 1/3 U.S. DMVs

Identity Verification: Mobile ID PIER(TM) 2.3 IBIS HIIDE(TM) PICS/MIS

Custom-Designed Solutions For Specific Market Segments Drivers' License - AutoTest- Enrollment, Proofing, Facial Law Enforcement - Recognition Card Production Booking, AFIS, Mobile ID Border Crossings - Iris Registered Expedited Traveler - Traveler - Finger, Iris, Document Document Authentication, Authentication Fingerprint VIP Registered Traveler Custom Integrated Kiosks

Government & Intelligence Consulting Services o Human Intelligence (SpecTal) o Imagery Science (McClendon) - Counterterrorism - Imagery Analysis - Information sharing and analysis - Spectral Science, hyperspectral/ - Counterintelligence multi-spectral systems - Behavioral science - Geospatial Systems - Vulnerability assessments - Model making and prototype fabrication - Surveillance and surveillance detection o Information Technology (ACI) - Computer forensics - Information assurance - Operational support - Systems engineering - Training - Telecommunications R&D - Public safety consulting
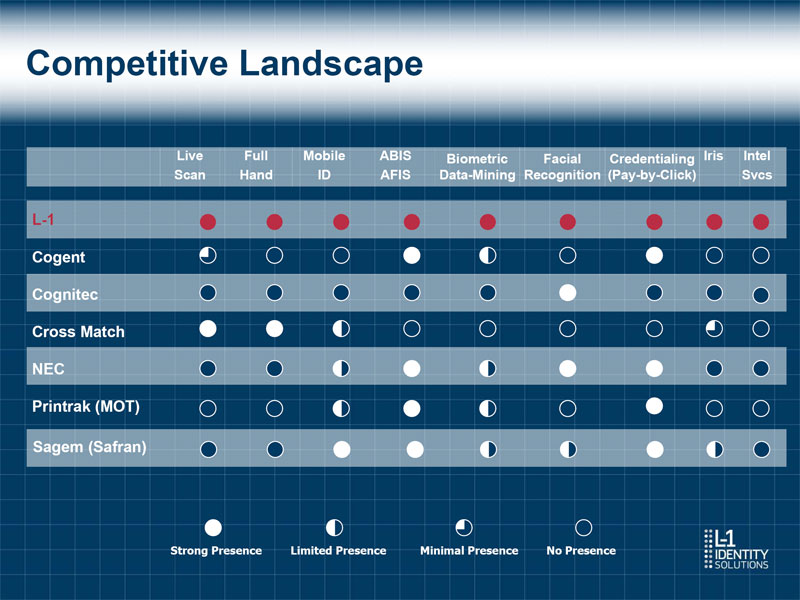
Competitive Landscape Live Full Mobile ABIS Biometric Facial Credentialing Iris Intel Scan Hand ID AFIS Data-Mining Recognition (Pay-by-Click) Svcs L-1 Cogent Cognitec Cross Match NEC Printrak (MOT) Sagem (Safran) Strong Presence Limited Presence Minimal Presence No Presence

Actively Sought By Partners Robust open architecture technologies encourage many prime contractors look to partner on large contracts:
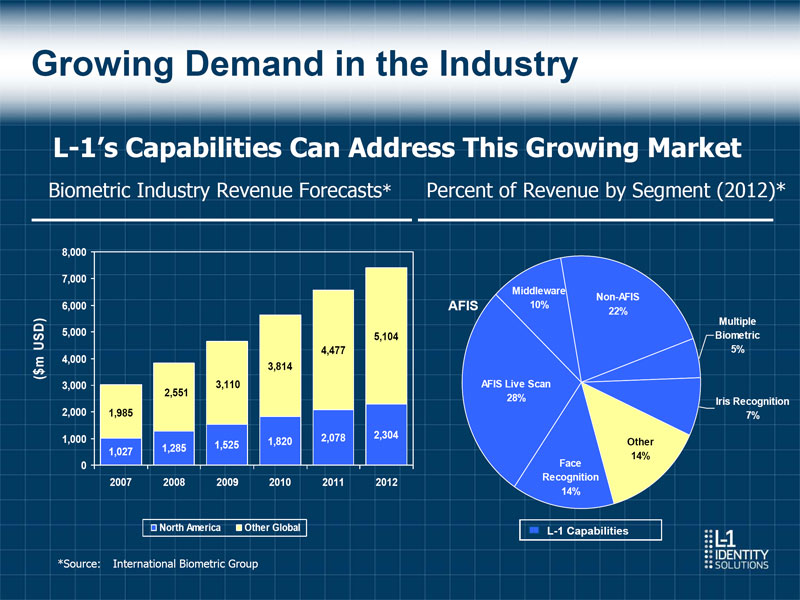
Growing Demand in the Industry L-1's Capabilities Can Address This Growing Market Biometric Industry Revenue Forecasts* Percent of Revenue by Segment (2012)* 8,000 7,000 Middleware Non-AFIS 6,000 AFIS 10% 22% Multiple 5,000 5,104 Biometric 4,477 5% 4,000 ($m USD) 3,814 3,000 3,110 AFIS Live Scan 2,551 28% Iris Recognition 2,000 1,985 7% 1,000 2,078 2,304 1,525 1,820 Other 1,027 1,285 14% 0 Face 2007 2008 2009 2010 2011 2012 Recognition 14% North America Other Global L-1 Capabilities *Source: International Biometric Group
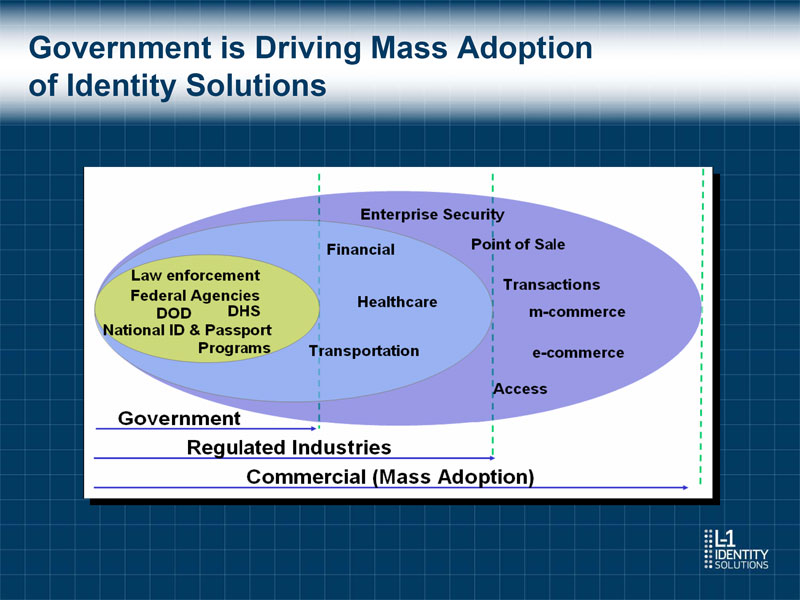
Government is Driving Mass Adoption of Identity Solutions
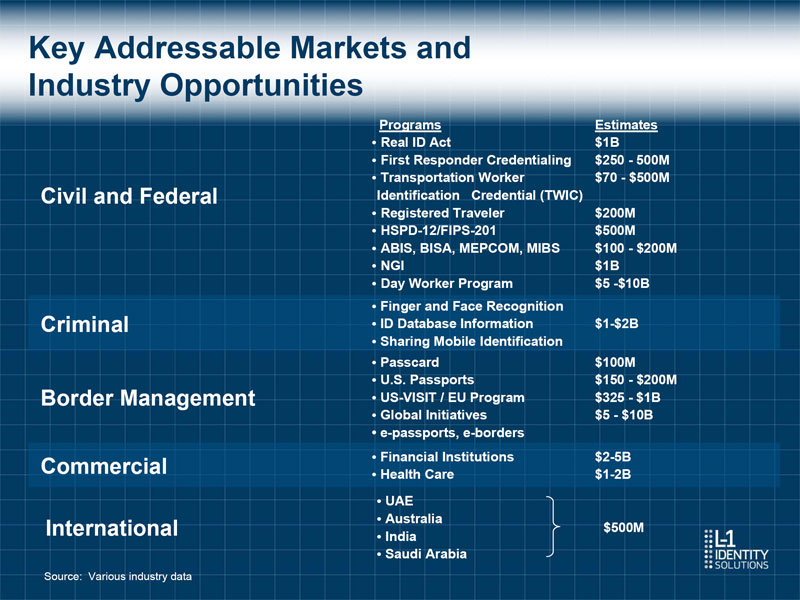
Key Addressable Markets and Industry Opportunities Programs Estimates o Real ID Act $1B o First Responder Credentialing $250 - 500M o Transportation Worker $70 - $500M Civil and Federal Identification Credential (TWIC) o Registered Traveler $200M o HSPD-12/FIPS-201 $500M o ABIS, BISA, MEPCOM, MIBS $100 - $200M o NGI $1B o Day Worker Program $5 -$10B o Finger and Face Recognition Criminal o ID Database Information $1-$2B o Sharing Mobile Identification o Passcard $100M o U.S. Passports $150 - $200M Border Management o US-VISIT / EU Program $325 - $1B o Global Initiatives $5 - $10B o e-passports, e-borders Commercial o Financial Institutions $2-5B o Health Care $1-2B o UAE o Australia International $500M o India o Saudi Arabia Source: Various industry data
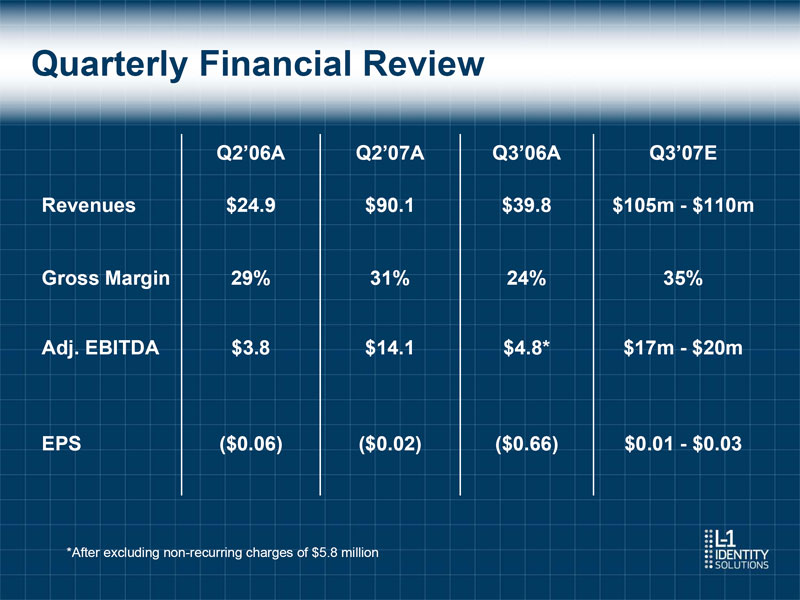
Quarterly Financial Review Q2'06A Q2'07A Q3'06A Q3'07E Revenues $24.9 $90.1 $39.8 $105m - $110m Gross Margin 29% 31% 24% 35% Adj. EBITDA $3.8 $14.1 $4.8* $17m - $20m EPS ($0.06) ($0.02) ($0.66) $0.01 - $0.03 *After excluding non-recurring charges of $5.8 million
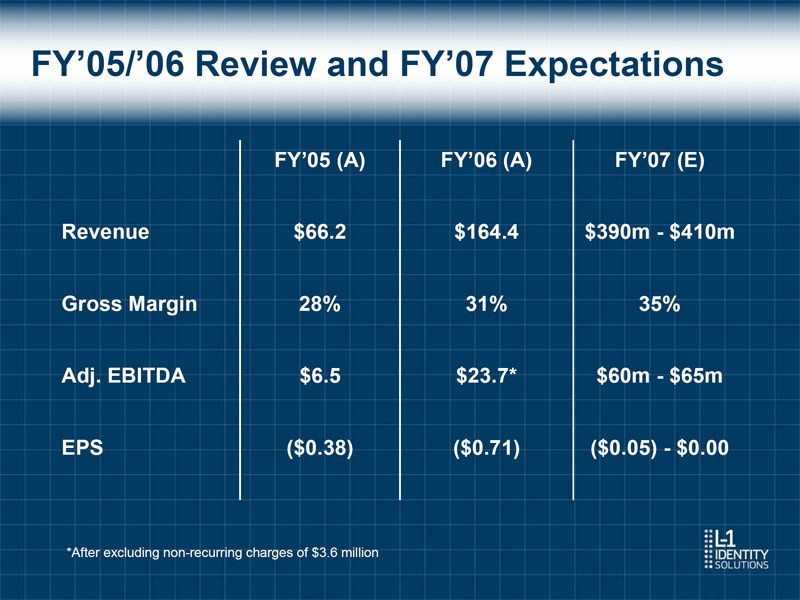
FY'05/'06 Review and FY'07 Expectations FY'05 (A) FY'06 (A) FY'07 (E) Revenue $66.2 $164.4 $390m - $410m Gross Margin 28% 31% 35% Adj. EBITDA $6.5 $23.7* $60m - $65m EPS ($0.38) ($0.71) ($0.05) - $0.00 *After excluding non-recurring charges of $3.6 million
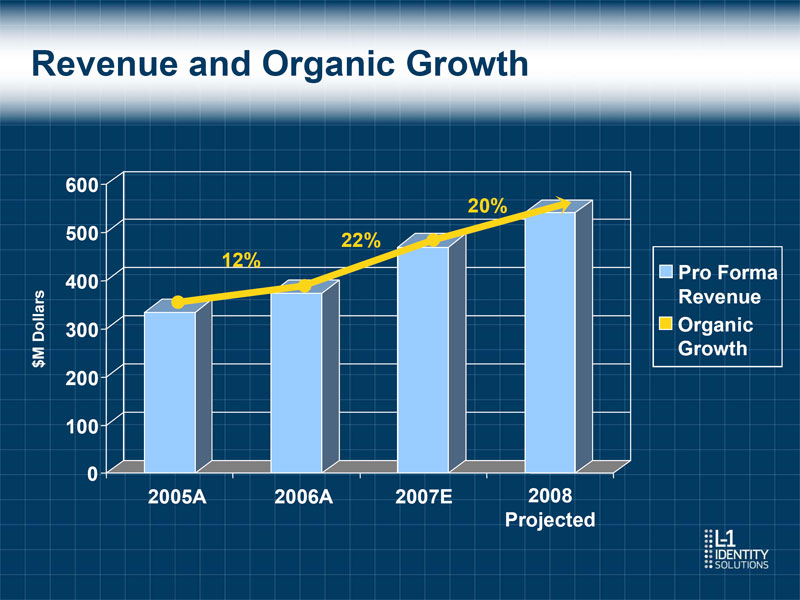
Revenue and Organic Growth 600 20% 500 22% 12% Pro Forma 400 Revenue 300 Organic $M Dollars Growth 200 100 0 2005A 2006A 2007E 2008 Projected
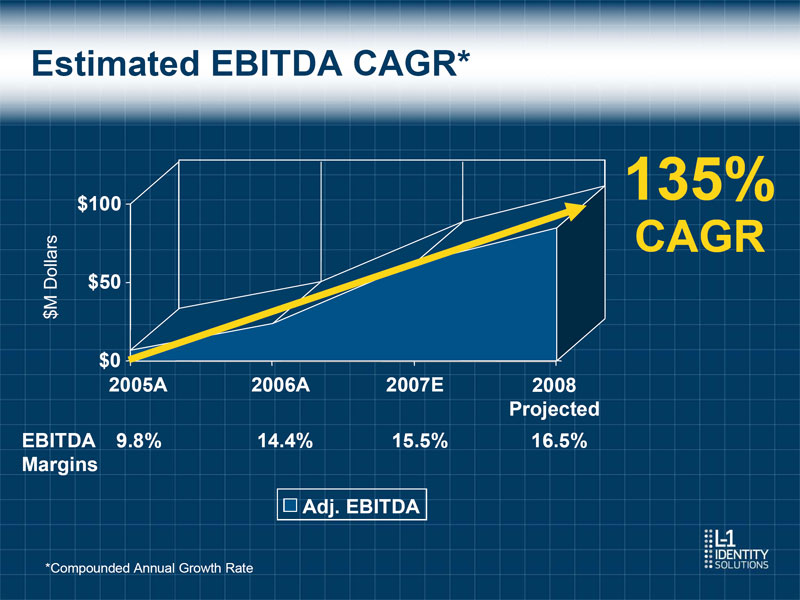
Estimated EBITDA CAGR* 135% $100 CAGR $M Dollars $50 $0 2005A 2006A 2007E 2008 Projected EBITDA 9.8% 14.4% 15.5% 16.5% Margins Adj. EBITDA *Compounded Annual Growth Rate
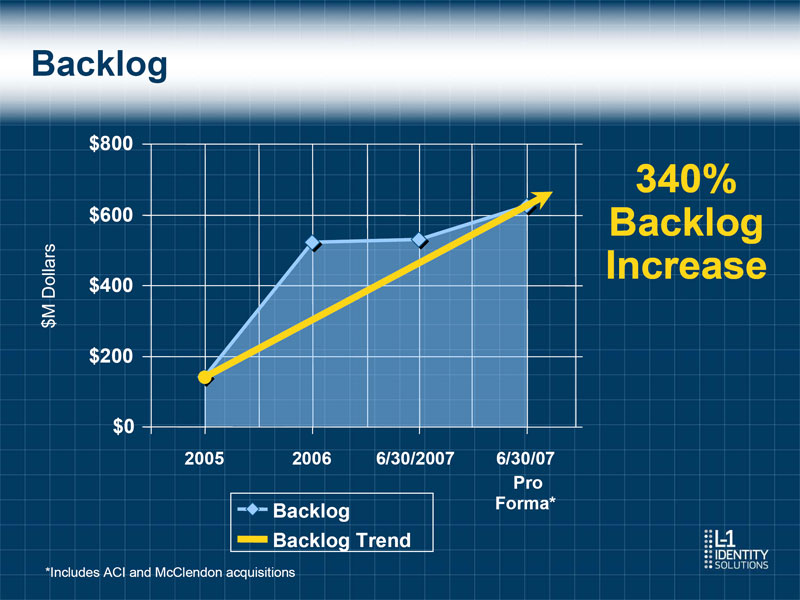
Backlog $800 340% $600 Backlog Increase $M Dollars $400 $200 $0 2005 2006 6/30/2007 6/30/07 Pro Backlog Forma* Backlog Trend *Includes ACI and McClendon acquisitions

Summary o Multi-modal strategy validated by strong customer momentum o Continue to build expertise with talented, experienced professionals o Capabilities to address most viable potential biometric markets o Address ID management challenges with customized solutions o Strong organic revenue and profit growth of 20% o Increase growth margin with emphasis on software and Intellectual Property.

Adjusted EBITDA Legal Disclosure L-1 Identity Solutions uses Adjusted EBITDA as a non-GAAP financial performance measurement. Adjusted EBITDA is calculated by adding back to net income (loss) interest, income taxes, depreciation, amortization, and stock-based compensation expense. Adjusted EBITDA is provided to investors to supplement the results of operations reported in accordance with GAAP. Management believes Adjusted EBITDA is useful to help investors analyze the operating trends of the business before and after the adoption of SFAS 123(R) and to assess the relative underlying performance of businesses with different capital and tax structures. Management believes that Adjusted EBITDA provides an additional tool for investors to use in comparing L-1 Identity Solutions financial results with other companies in the industry, many of which also use Adjusted EBITDA in their communications to investors. By excluding non-cash charges such as amortization, depreciation and stock-based compensation, as well as non-operating charges for interest and income taxes, L-1 Identity Solutions can evaluate its operations and can compare its results on a more consistent basis to the results of other companies in the industry. Management also uses Adjusted EBITDA to evaluate potential acquisitions, establish internal budgets and goals, and evaluate performance. L-1 Identity Solutions considers Adjusted EBITDA to be an important indicator of the Company's operational strength and performance of its business and a useful measure of the Company's historical operating trends. However, there are significant limitations to the use of Adjusted EBITDA since it excludes interest income and expense and income taxes, all of which impact the Company's profitability, as well as depreciation and amortization related to the use of long term assets which benefit multiple periods. L-1 Identity Solutions believes that these limitations are compensated by providing Adjusted EBITDA only with GAAP net income (loss) and clearly identifying the difference between the two measures. Consequently, Adjusted EBITDA should not be considered in isolation or as a substitute for net income (loss) presented in accordance with GAAP. Adjusted EBITDA as defined by the Company may not be comparable with similarly named measures provided by other entities. A reconciliation of GAAP net income (loss) to Adjusted EBITDA is included in the enclosed schedule. A reconciliation of Adjusted EBITDA to Net Income for the past fiscal periods, with respect to which Adjusted EBITDA is provided herein, is available in the filings made by the Company with the Securities and Exchange Commission and on the website of the Company www.l1id.com.