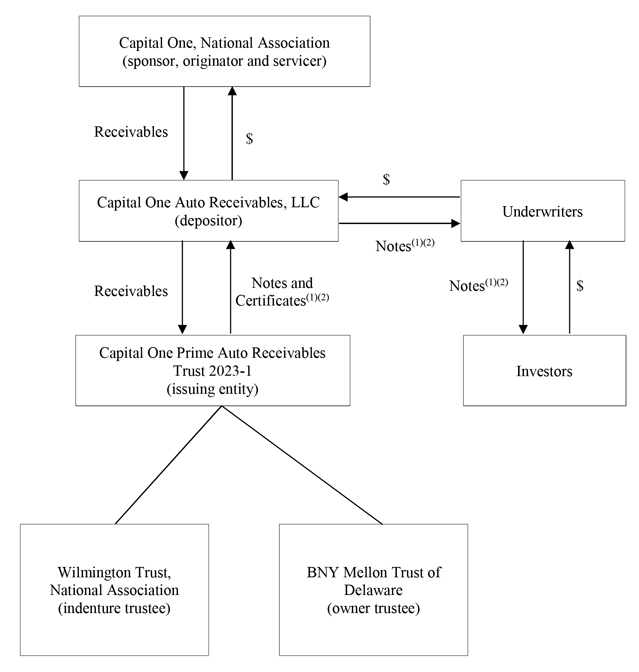
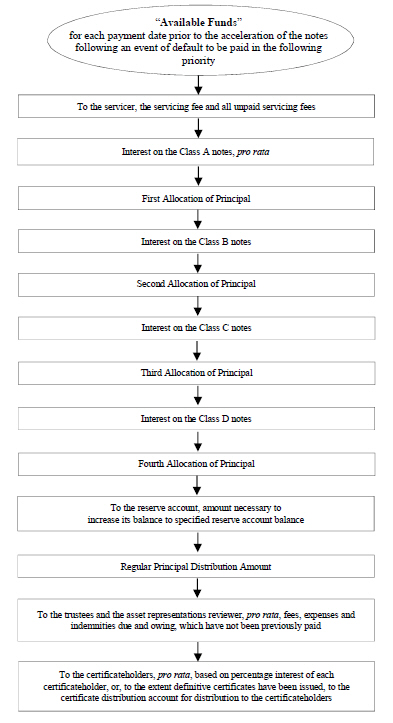
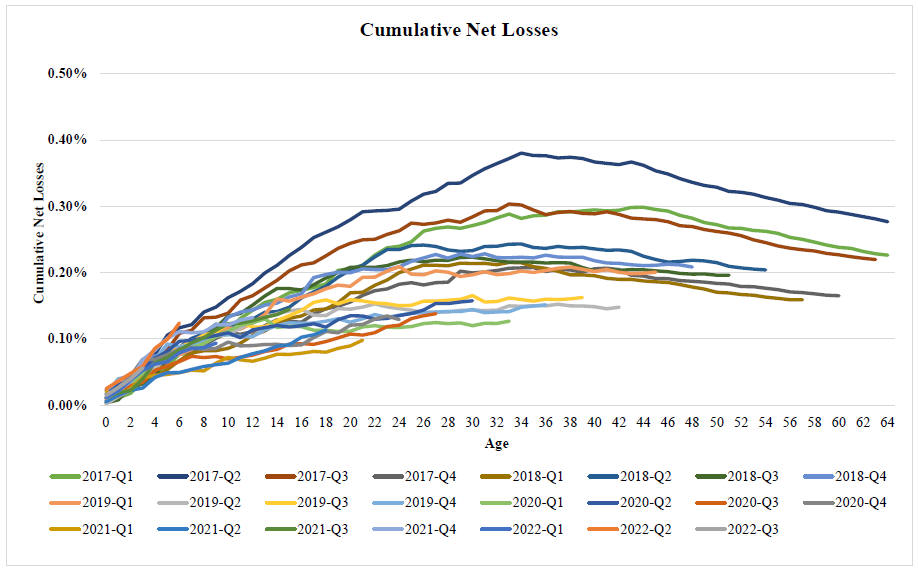
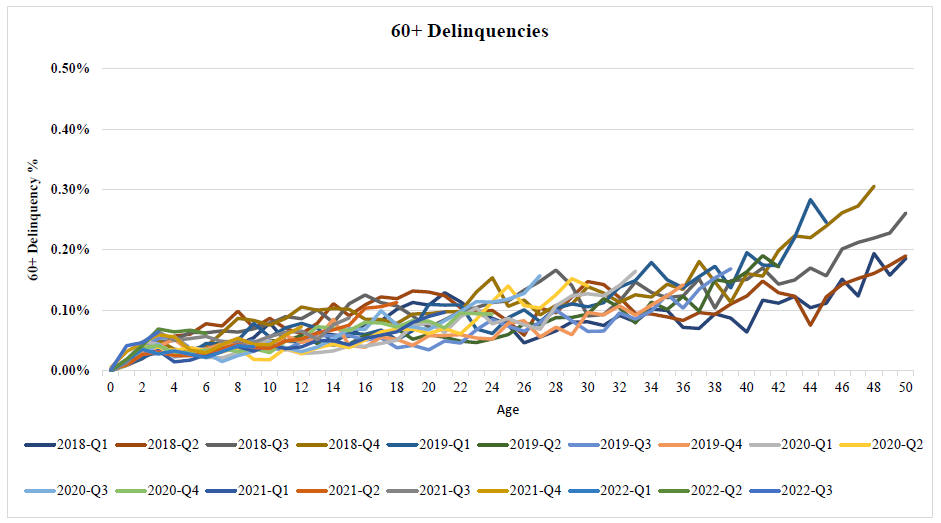
RISKS RELATED TO THE SERVICER AND OTHER TRANSACTION PARTIES.
The sponsor faces risks related to its operational, technological and organizational infrastructure, including risks arising from the theft, loss or misuse of information (including as a result of a cyber-attack), which could adversely affect the liquidity or market value of your notes and the timing and amount of payments on your notes
Similar to other large financial institutions, the sponsor is exposed to operational risk that can manifest itself in many ways, such as errors in execution or inadequate processes, inaccurate models, faulty or disabled technological infrastructure and fraud by employees or persons outside of the company. In addition, the sponsor is heavily dependent on the security, capability and continuous availability of the technology systems that it uses to manage its internal financial and other systems, monitor risk and compliance with regulatory requirements, provide services to its customers, develop and offer new products and communicate with stakeholders.
If the sponsor does not maintain the necessary operational, technological and organizational infrastructure to operate its business, including to maintain the security of that infrastructure, the sponsor’s business and reputation could be materially adversely affected, which could adversely affect the liquidity or market value of your notes. The sponsor is also subject to disruptions to its operating systems arising from events that are wholly or partially beyond its control, which may include, computer viruses, electrical or telecommunications outages, design flaws in foundational components or platforms, availability and quality of vulnerability patches from key vendors, cyber-attacks (including Distributed Denial of Service (“DDOS”) attacks and other attacks on its infrastructure), natural disasters, public health emergencies (including COVID-19 or similar outbreaks), other damage to property or physical assets, or events arising from local or larger scale politics, including terrorist acts, civil unrest, political instability and armed conflict (such as the commencement of hostilities between the United States and a foreign nation or nations or between foreign nations). The sponsor also relies on the business infrastructure and systems of third parties with which it does business and to whom it outsources the operation, maintenance and development of its information technology and communications systems.
The sponsor may incur significant costs in connection with any future cybersecurity incidents, including infrastructure investments or remediation efforts. Technologies, systems, networks and devices of the sponsor or its employees, service providers or other third parties with whom the sponsor interacts may continue to be the subject of cyber-attacks and other security incidents, including DDOS attacks, computer viruses, hacking, malware, ransomware, credential stuffing or phishing or other forms of social engineering. Such cyber-attacks and other security incidents are designed to lead to various harmful outcomes, such as unauthorized transactions in customer accounts, unauthorized or unintended access to or release, gathering, monitoring, disclosure, loss, destruction, corruption, disablement, encryption, misuse, modification or other processing of confidential or sensitive information (including personal information), intellectual property, software, methodologies or business secrets, disruption, sabotage or degradation of service, systems or networks, or other damage. These threats may derive from, among other things, error, fraud or malice on the part of the sponsor’s employees, insiders or third parties or may result from accidental technological failure. For example, on July 29, 2019, the sponsor’s direct parent, Capital One Financial Corporation, announced that on March 22 and 23, 2019, an outside individual gained unauthorized access to its systems. This individual obtained certain types of personal information relating to people who had applied for credit card products and to credit card customers (the “Cybersecurity Incident”). While the Cybersecurity Incident has been remediated, it has resulted in fines, litigation, government investigations, consent orders and other regulatory enforcement inquiries. The Office of the Comptroller of the Currency lifted its consent order on August 31, 2022.
In addition, the sponsor’s customers access its products and services using personal devices that are necessarily external to our security control systems. The ongoing COVID-19 pandemic also increases the risk that we may experience cyber incidents as a result of our employees, service providers, partners and other third parties with which we interact working remotely on systems, networks and environments over which we have less control.
The methods and techniques employed by malicious actors change frequently, are increasingly sophisticated and often are not fully recognized or understood until after they have occurred, and some techniques could occur and persist for an extended period of time before being detected. For example, although Capital One Financial Corporation and its subsidiaries (collectively, “Capital One”) immediately fixed the configuration vulnerability that was exploited in the Cybersecurity Incident once it discovered the unauthorized access, a period of time elapsed between the occurrence of the unauthorized access and the time when unauthorized access was discovered. Capital
23