| 11111 | 11111111 | 01 I~0 0111 I ~ ~I | II | |||||||||||||||||
| 101 1101 ~ | 1010 | |||||||||||||||||||
| US006330317B | ||||||||||||||||||||
| 1 | IIII~ | |||||||||||||||||||
| ~I | ||||||||||||||||||||
| VII | ||||||||||||||||||||
| 1111 | ||||||||||||||||||||
| (1 | Unite State Patent | (10) | Patent No.: US | 6,330,317 Bi | ||||||||||||||||
| 2) | ||||||||||||||||||||
| d | s | |||||||||||||||||||
| Garfinke | (45) | Date of Patent: | I)ec. 11, | |||||||||||||||||
| l | 2001 | |||||||||||||||||||
| (54) | CALL BLOCKING SYSTEM | Rogers et al | ||||||||||||||||||
| 6/19~2 | Mellon | 379/189 | ||||||||||||||||||
| (76) | Inventor: Dean Garfinkel, 255 Piping Rock | 4,346,2 | 8/1982 | Sharvit | 379/198 | |||||||||||||||
| Rd., Old Brookville, NY (US) | 64 | |||||||||||||||||||
| 11545 | 4,358,640 | 11/1982 | Murray | 3791200 | ||||||||||||||||
| (*) | Notice: Subject to any disclaimer, the leun of | 4,482,78 | 11/1984 | Sagara et al | 379/200 | |||||||||||||||
| Ihis | ||||||||||||||||||||
| patent is extended or adjusted | 7 | |||||||||||||||||||
| 4,612,41 | 9/1986 | Smith | 379/200 | |||||||||||||||||
| under 35 | 9 | |||||||||||||||||||
| U.S.C. 154(b) by 0 days. | 4.794,64 | 12/1988 | Arbabzadah at at 379/200 | |||||||||||||||||
| (21) | Appi. No.: 09/435,955 | 2 | ||||||||||||||||||
| (22) | Filed: | Nov. | 31 | |||||||||||||||||
| 9, 1999 | ||||||||||||||||||||
| (51) | hit. Cl.7 | HO4M 1/663; HO4M 1/665; | ||||||||||||||||||
| HO4M 11677 | ||||||||||||||||||||
| (52) | US. CI | 379/196; 379/197; 379/900 | ||||||||||||||||||
| (58) | Field of Search | 379/188, 196. | ||||||||||||||||||
| 379/197, 198, 199, 200, 900 | ||||||||||||||||||||
| (56) | References Cited | |||||||||||||||||||
U.S. PAIENT
34
DOCUMENTS 33
| 31 |
| 3 5 |
| 3,920,93 | Mogtader | |||
| 6 | C~~d.CaI |
| ' U |
| 4,866,76 | 9/1989 | Piatar | 379/200 | |||||
| 2 | ||||||||
| 4,993,06 | 2/1991 | Dula at al 379/88.27 | ||||||
| 2 | ||||||||
| 5,161,18 | Zwick | |||||||
| 1 | ||||||||
| 5,200,99 | 4/1993 | Gaukel at at | 379/200 | |||||
| 5 | ||||||||
| 5,553,12 | 9/1996 | Grimes | 379/211 | |||||
| 8 | ||||||||
| 5,737,4 | 41199 | Zave | - | 319/201 | ||||
| 03 | 8 | |||||||
| 5,751,80 | Axlon | |||||||
| 0 | ||||||||
| Bingamcn at al | ||||||||
| 37 | ||||||||
| 9/88.12 X | ||||||||
| 6 | Fotta . | |||||||
| * cited by examiner | ||||||||
| Pnmar Examiner-Harry S. Hong | ||||||||
| (57) | ABSTRACT | |||||||
The integration of various federally required and state mandated do-not-call lists for telemarketers into a system that automatically blocks outgoing calls from a number of companies ("Customer Companies") taking into account factors such as preexisting customers which may legally he contacted is disclosed. The system reviews outgoing calls by a telemarketer, compares it to the general do-not-call lists and the specific customer company do-not-call list and override permitted call lIst to make a determination if the call should be. completed. This integration is due to the incorporation of a general purpose computer in a central location that is connected to all the major telephone carriers switch cluster locations and operated by a service provider. The "do-not-call" database of originating/destination pails, as well as the logic for blocking or permitting telephone calls, is stored in this computer. This computer makes all blocking decisions in real-time based on the originating and destination number combinations of the call.
10 ClaIms, 6 DrawIng Sheets
| U.S. | Sheet I of 6 | US | ||
| 6,330,317 | ||||
| Patent | Bi | |||
| Dec. 11, 2001 |
| U.S. | US | |
| Patent | 6,330,317 | |
| Dec. 11,2001 | Bi | |
| Sheet 2 of 6 |
| U.S. | 48 | 49 | ||||
| 47 | US | |||||
| Patent | Sheet 3 of 6 | 6,330,317 | ||||
| 74 | B! | |||||
| 48 | 77 | |||||
| Dec. 11,2001 |

| 61 |
| Dec. 11,2001 |
| 55 |
| .56 |
| Is there. CN |
| 5 7 |
58 59
| ~Yes~~fl |
| 60 |
| 66 65 |
| Yes |
78
| U.S. Patent | Sheet 4 of 6 | US 6,330,317 Bi | ||||||
| 85 | ||||||||
| U.S. Patent | Dec. 11,2001 | Sheet 5 of | 80 | |||||
| US 6,330,317 Bi | ||||||||
| [ Customer Logs on to Internet |
| ~ 8 |
| 4 |
| 8 and Passwo |
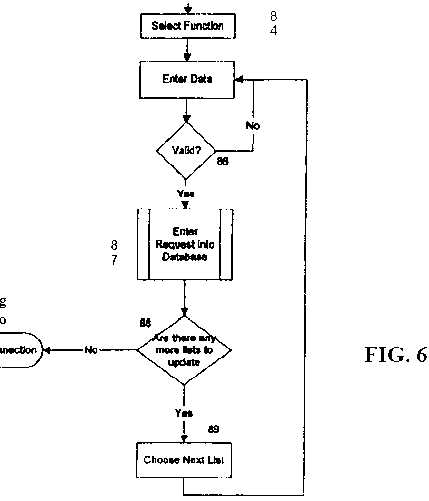
FIG. 4
| 92 | ||||||||||
| U.S. Patent | Sheet 4 of 6 | US 6,330,317 Bi | ||||||||
| U.S. Patent | Dec. 11, | |||||||||
| 2001 | ||||||||||
| Sheet 6 of 6 | ||||||||||
| US | ||||||||||
| 6,330,317 | ||||||||||
| B! | 9 | |||||||||
| 1 | ||||||||||
| Disable Internet | ||
| Site | ||
| 1~ | ||
| Bulk Copy | ||
| Updating | ||
| Database | ||
| .4. | ||
| Re~Enable Internet | ||
| Site | 93 | |
| :____ | ||
| format files | ||
| ! | ||
| Replace Control | ||
| Computer | ||
| Database with | ||
| Reformated | ||
| Updating | ||
| Database | ||
FIG. 4
| U.S. Patent |
| Sheet 4 of 6 |
| US 6,330,317 Bi |
| FIG. 7 |
FIG. 4
| U.S. Patent | Sheet 4 of 6 | US 6,330,317 Bi | ||||
| US 6,330,317 BI | ||||||
| 1 | 65 not eliminate the possibility of an employee innocently | |||||
| CALL BLOCKING SYSTEM | calling a number from an old call list or an employee | |||||
| simply | ||||||
| BACKGROUND OF THE | 2 | |||||
| INVENTION | disregarding the company's do-not-call list altogether in | |||||
| 1. Field of the Invention | the search for commissions. | |||||
| ilie invention concerns telephone systems generally and | In addition, certain ambiguities develop in use. For | |||||
| more specifically, concerns the blocking of outgoing phone | example, a prior purchaser may have placed his name on a | |||||
calls to phone numbers which have been placed on a do- state mandated list. The hand process would eliminate that
| not-call list. | number although the customer may, in fact, wish to | |||
| 2. Prior Air | receive the call and by his former purchases, is a permitted |
In recent years the door to door salesman has been callee replaced by telephone solicitation. Rather than a salesman under the state law.
walking a route, a telemarketer makes a series of telephone Various attempts have been made to control out-calls. The telephone numbers dialed are normally on a call going ~ calls, usually to restrict long distance toll calls or to list given to the telernarketing salesman by his employer. The a single call list may be organized by address, consumer information List of restricted numbers. A number of systems have or by the numbers themselves. Just as the consumer been can slam the door in the face of a door to door salesman, the directed to stopping the making of long distance calls or consumer may hang up upon receiving a telephone solici- specific area calls from a given location. For example, US. tation. However, the call itself is considered by many to be Pat. No. 4,612,419, to Smith, entitled Toll Restriction an intrusive act. The widespread nature of telephone solici- Cii15 cult for Electronic Telephone Station, describes a tation means that certain segments of the public are desirous means of being protected from even receIving such calls. Thus, a controlling toll calls only and is employed within the number of private organizations were created to inform direct telephone station itself. It looks for a 0 and 1 in the first marketers as to those who did not wish to receive such dialed digit, the subscriber can lock and unlock the device phone calls. Organizations produced do-not-call lists from by a key those who do not wish to receive tolemarketing solicitations pad entry with an enabling and disabling code. U.S. and provided such lists to those direct marketeers who Pat. No.
| voluntarily comply with the consumer's request. Upon | '° | 4,358,640, to Murray, entitled Telephone Security | ||
| receipt of these lists, these marketeers would delete the listed | Device, issued Nov. 9, 1982, describes a circuit which has | |||
| numbers from their telemarketer's call lists. Such do not call | means to | |||
| lists work both to the benefit of the people who do not wish to | allow or disallow toll calls on entry of a programmable code | |||
| receive calls and to the soliciting company which has its call | stored. U.S. Pat. No. 4,794,642, to Arbabzadah Ct at., | |||
| list referred to a more select group of potential consumers | Call | |||
| that are more receptive of telephone sales pitches. | - | Screening in a Public Telephone Station, issued Dcc. 27, | ||
| The Federal Government requires each telemarketer to | 2) | 1988, discloses control equipment in a customer owned | ||
| maintain its own 'do-not-call" lists and to add to the list the | public telephone station which prevents a user from | |||
name of anyone so requesting exclusion from telephone calls making unauthorized telephone calls in a telephone system. from their company. Under the statute, fines can be assessed The
against companies that call numbers on the company's do- system restricts telephone numbers a user can dial to those not-call list. The consumer is given the right to sue any numbers preselected by a station owner. U.S. Pat. No. 30 company which calls them after they have requested that the 5,200,995, to Gaukel et at., issued Apr. 6, 1993, entitled company place them on the do-not-call list. In addition, a Universal Outgoing Call Restriction Circuit, discloses a number of state governments, including those of florida, circuit which prevents a telephone or a plurality of tele-Oregon, Arizona, Alaska, Kentucky, Tennessee, Alabama, phones from making unauthorized or restricted calls to Arkansas and Georgia, maintain, or in the near future, will be specific numbers or unspecific groups of numbers. Essen maintaining, statewide do-not-call lists which arc applicable ~ tially the system compares the numbers against prepro-to all vendors calling numbers in the state. grammed internal lists of restricted numbers. Thus, a telemarketer is faced with a legal responsibility None of these patents disclose a system necessary to
under federal and stale law to refrain from calling numbers handle the blocking requirements under federal and state maintained on separate lists including their own internal list law and lists prepared by various blocking organizations. and lists maintained by a number of state governments. On
| penalty of fine and civil action, the responsibility is laid on | SUMMARY OF THE INVENTION | |||||
| the telemarketer to ensure that no do-not-call numbers are, | A system which would monitor and quickly update all | |||||
| in fact, called. In addition, they may have one or more | such lists for a number of companies would be beneficial | |||||
| organizations do-not-call list with which the telemarketer | to | |||||
| wishes to comply. Accordingly, companies developed their | ~ | both the consumers who wish to be protected from | ||||
| final call lists for their telemarkcter by comparing and | telephone | |||||
| matching their federaUy re~uire.d do-not-call list, various | solicitation and the soliciting companies. Such a system | |||||
| state | do-not-call lists and organizational do-not-call list-s | would have to be able to block or specifically permit calls | ||||
| with | their telemarketer's call lists and eliminating any from specific originating numbers to specific destination | |||||
| matching numbers from their call list. This process has until | numbers. To be useful, the do-not-call decision would | |||||
| now been done manually and is subject to human error. | have so to be fully automatic and include the capability | |||||
| There is a large number of employees who must be com- | of dynamically changing the do-not-call list for specific | |||||
| mitted to this effort. Even with this effort, the process does | originating/ | |||||
FIG. 4
| U.S. Patent | Sheet 4 of 6 | US 6,330,317 Bi | ||||
| destination phone number pairs as individuals request | 60 supporting a single company specific do-not-call list for | |||||
| blocking or become clients of the company in question. | multiple offices of the same company in different | |||||
| Each | geographic locations. Finally, it must be able to import, in | |||||
| calling company must be capable of adding or deleting ~ | bulk, large numbers of specific telephone number | |||||
| numbers from the company's specific do-not-call list | combinations. | |||||
| without affecting another company's list. Equally, each | The present invention is directed to integration of | |||||
| company | various do-not-call lists into a system that automatically | |||||
| must have the option of automatically blocking numbers on | blocks outgoing calls from a number of companies | |||||
| the state mandated list or to block only from their own | ("Customer Companies") taking into account factors such | |||||
| do-not-call list. Equally such a system must be capable of | as preexisting | |||||
FIG. 4
| U.S. Patent | Sheet 4 of 6 | US 6,330,317 Bi | ||||||||||||||||||||||||||||||
| US 6,330,317 Bi | ||||||||||||||||||||||||||||||||
| 3 | FUll. 7 is a flow diagram for transferring the updated | |||||||||||||||||||||||||||||||
| customers which may legally be contacted. Thus, rathcr than | database information to the control computers, | |||||||||||||||||||||||||||||||
| modifying the call lists for each customer company, it acts to | ||||||||||||||||||||||||||||||||
| review the outgoing call, compare it to the. general do-not-call | DETAILED DESCRIPTION OF NE | |||||||||||||||||||||||||||||||
| lists and the specific customer company do-not-call list and | PREFERRED EMBODIMENTS | |||||||||||||||||||||||||||||||
| override permitted call list to make a determi- ~ nation if the | ||||||||||||||||||||||||||||||||
| call should be completed. This integration is due to the | The present invention encompasses not only the specific | |||||||||||||||||||||||||||||||
| incorporation of a general purpose computer in a central | method of blocking the telephone calls but of maintaining | |||||||||||||||||||||||||||||||
| location that is connected to all the major telephone carriers | and updating the do-not-call database and its component | |||||||||||||||||||||||||||||||
| switch duster locations and operated by a service provider. | lists | both | in | general and | for specific | customer | ||||||||||||||||||||||||||
| The "do-not-call" database of originating/ destination pairs, | companies. In | |||||||||||||||||||||||||||||||
| as well as the logic for blocking or permitting telephone calls, | ~ particular | the | invention | includes | the | periodic | ||||||||||||||||||||||||||
| is stored in this central computer. This computer makes all | synchronizing | |||||||||||||||||||||||||||||||
| blocking decisions in real-time based on the originating and | of the do-not-call | databases with a master | updating | |||||||||||||||||||||||||||||
| destination number combinations of the call. | database which is periodically updated by customers through | |||||||||||||||||||||||||||||||
| All participating customer companies have access to a | the internet and by state and consumer organizations latest | |||||||||||||||||||||||||||||||
| separate part of this database ("updating do-not-call database") | do-not-call lists. | |||||||||||||||||||||||||||||||
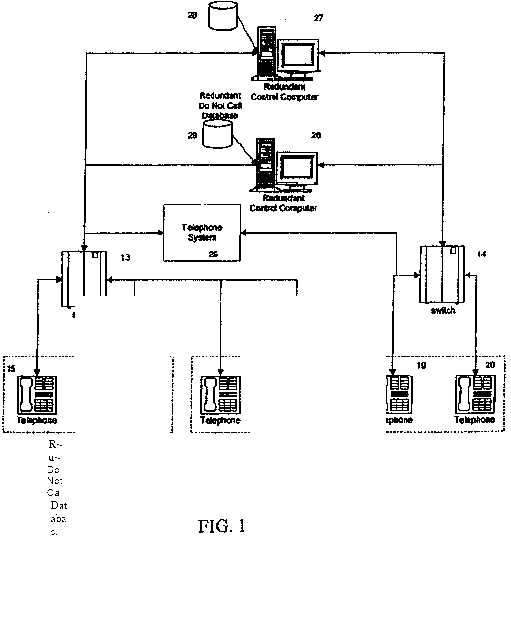
| for the purpose of adding or deleting numbers on their | FIG. | 1 is | a diagrammatic representation | of | how the | |||||||||||||||||||||||||||
| company specific do-not-call lists or to permit override of | control | computer | of the | present invention | interconnects | |||||||||||||||||||||||||||
| specific numbers on any state mandated or organizational do- | with the normal telephone system. Telemarketing customer | |||||||||||||||||||||||||||||||
| not-call lists. Since this database receives information from | companies 10-12 receive their telephone services from one | |||||||||||||||||||||||||||||||
| various companies and from a number of state and | or more telephone | companies or carriers. The | customer | |||||||||||||||||||||||||||||
| organizational do-not-call lists, it must be accessible from | companies | 10-12 | arc | connected | to | its | own | |||||||||||||||||||||||||
| different geographical locations. Accordingly, the database is | telecommunications company | provider by | conventional | |||||||||||||||||||||||||||||
| maintained using the Internet. The Internet acts as a customer | means such as plain old telephone service lines (POTS), Ti | |||||||||||||||||||||||||||||||
| interface that will permit any customer who has access to the | line, feature | I), or any | other | conventional | telephonic | |||||||||||||||||||||||||||
| Internet to enter change requests for specific do-not-call | linkage. The | telecotnrmmication company provides a dial | ||||||||||||||||||||||||||||||
| lists. | tone to the customer for a tclepbone call and performs all | |||||||||||||||||||||||||||||||
| Undernorrnal telephone practice when a call is originated, | normal communication functions. Calls are placed from hand | |||||||||||||||||||||||||||||||
| the information for the call is transported to the primary ~ | sets 15-20 at | the respective customers 10-12 to | their | local | ||||||||||||||||||||||||||||
| switch cluster for the telecommunications carrier. This infor- | primary telephone switch cluster 13-14. | |||||||||||||||||||||||||||||||
| mation includes both the originating number, or where the | As seen in FIG. 1, customer companies 10 and 11 have their | |||||||||||||||||||||||||||||||
| caller has a trunk line, the AuthCode (a seven digit number | telephone | service provided through the same primary | ||||||||||||||||||||||||||||||
| corresponding to the originating trunk group of the caller) and | switch cluster | 13. | Customer company | 12, | has its | |||||||||||||||||||||||||||
| the called number('originatirig/destination pair"). If the caller is | telephone | service | provided | through | primary | switch | ||||||||||||||||||||||||||
| from a participating customer company on the present do-not- | cluster 14. As is normal with any telephone call, when a | |||||||||||||||||||||||||||||||
| call blocking system, the switch cluster recognizes the | call is placed from handsets 15-19 information both as | |||||||||||||||||||||||||||||||
| originating number or authorization code and the | to the originating number of the hand set and the | |||||||||||||||||||||||||||||||
| originating/destination pair information is transported from the | destination number which was dialed by the customer | |||||||||||||||||||||||||||||||
| switch cluster to the control computer while the call is held at | company | (i.e., | the | originaling/ | destination pair) is | |||||||||||||||||||||||||||
| ,~ | ||||||||||||||||||||||||||||||||
| the switch cluster. The control computer's function is to then | supplied | to the switch | cluster | 13-14. | In | normal | ||||||||||||||||||||||||||
| process the information and create a command to either block | operation, the primary switch cluster 13 and 14 would | |||||||||||||||||||||||||||||||
| that call or permit the call to be completed. Once the decision is | then route the signal to the destination number dialed | |||||||||||||||||||||||||||||||
| made, the control computer indicates the. decision to the | at the respective | telemarketer's | hand | sets | 13-20 | |||||||||||||||||||||||||||
| carrier's switch cluster and a command is implemented at the | through the telephone system 25. In the present system, | |||||||||||||||||||||||||||||||
| switch cluster to either allow the call to be completed or to | the | switch | cluster | 13-14 | determines from | the | ||||||||||||||||||||||||||
| return a message to the telernarkctcr indicating that it has been | originating | number or | AuthCode whether the call | is to | ||||||||||||||||||||||||||||
| blocked under the call blocking system. | be reviewed for a do not call determination. If the | |||||||||||||||||||||||||||||||
| originating number is one of the numbers from which | ||||||||||||||||||||||||||||||||
| BRIEF DESCRIPTION OF ThE DRAWINGS | calls are to be reviewed, the switch cluster 13-14 | |||||||||||||||||||||||||||||||
| The invention can be more fully understood from con- | holds the call and forwards the originating destination | |||||||||||||||||||||||||||||||
| sideration of the following detailed description of an illus- | pair to a control computer 26-27 for a determination | |||||||||||||||||||||||||||||||
| trative embodiment of the invention and the accompanying | of whether the call shouki be made or blocked by | |||||||||||||||||||||||||||||||
| drawings in which: | so reference to their respective databases either stored on | |||||||||||||||||||||||||||||||
| FIG. 1 is a diagrammatic representation of the components | that computer | 26-27 or in separate | storage means | |||||||||||||||||||||||||||||
| of the control system; | 28-29. | |||||||||||||||||||||||||||||||
| FIG. 2 is a flow diagram showing the overall call block | In actuality, there | may | be | two | or | more | redundant | |||||||||||||||||||||||||
| processing; | control computers 26-27 performing the function. While | |||||||||||||||||||||||||||||||
| FIG. 3 is a diagrammatic representation of the various | each such | |||||||||||||||||||||||||||||||
| elements forming the control computer do-not-call database; | computer will be designed to handle the complete load | |||||||||||||||||||||||||||||||
| FIG. 4 is a flow diagram of decision making process | of s~c anticipated call traffic, the traffic load may be | |||||||||||||||||||||||||||||||
| performed by the control computer; | divided evenly | |||||||||||||||||||||||||||||||
| FIG. 5 is a diagrammatic representation of the components | between the redundant computers 26-27. Thus, if one | |||||||||||||||||||||||||||||||
| of the system to update the do-not-call database; | of the control computers 26 cannot handle a call muted to | |||||||||||||||||||||||||||||||
| FIG. 6 is a flow diagram of data entry to the customer's | it for any reason, one of the alternative control computers | |||||||||||||||||||||||||||||||
| do-not-call database by the Internet; | 27 can | |||||||||||||||||||||||||||||||
| automatically take over. Although shown as two | ||||||||||||||||||||||||||||||||
| 4 | computers 60 in FIG. 1, a number of such redundant | |||||||||||||||||||||||||||||||
FIG. 4
| U.S. Patent | Sheet 4 of 6 | US 6,330,317 Bi | ||||
| computers may be | 65 more easily adapted to handle. numerous wide-spread | |||||
| used and, in fact, such | control computers may be offices | |||||
| geographically distributed throughout the country, creating a | of a single company in a uniform manner. Of course, | |||||
| system with multiplex redundancies and, therefore, | the do not call database 28-29 for each of the redundant | |||||
| extremely high | computers | |||||
| reliability. Geographic distribution also makes this system | ||||||
FIG. 4
| U.S. Patent | Sheet 4 of 6 | US 6,330,317 Bi | ||||||||||||||||
| US 6,330,317 Bi | ||||||||||||||||||
| 5 | nwnber. | |||||||||||||||||
| would have duplicate information and their updating be | Since the state mandated lists are for all telcmarketing | |||||||||||||||||
| improved so that each blocking computer 26-27 would | done within the state regardless of the source, they are not | |||||||||||||||||
| respond in the same way in making a call blocking decision. | tagged for, or associated with, individual customers. Similar | |||||||||||||||||
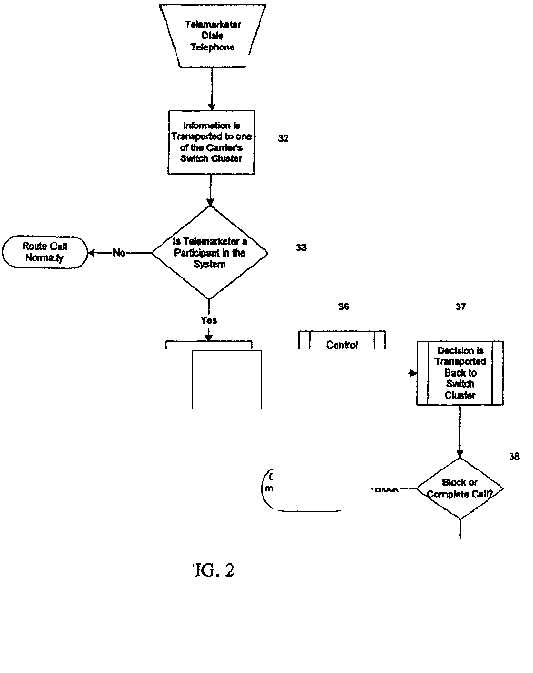
| FIG. 2 is a flow diagram showing the process for | do-not-call lists are maintained by private organizations are | |||||||||||||||||
| blocking | not customer company specific 4'7. Such lists are for all | |||||||||||||||||
| an individual telephone call. The telemarketer of a | relemarketcrs and are thus not tagged by customer compa- | |||||||||||||||||
| customer | nies. List 48 is the federally required do-not-call list which | |||||||||||||||||
| company 10-12 dials his handset 15-20 in a conventional | must be maintained by each telemarketer. This list is a 65 | |||||||||||||||||
| manner 31. As normal in modem telecommunications, | compilation of all those individuals who, when called by a | |||||||||||||||||
| by so dialing the handset 15-20, the customer | customer company 10-U, indicated that they wished no | |||||||||||||||||
| company 10-13 | 6 | |||||||||||||||||
| originates a signal corresponding both to | the dialer's | further calls. Since each such list is peculiar to the customer | ||||||||||||||||
| originating telephone number or where the handset is | company, it is tagged with the customer company's CM. | |||||||||||||||||
| on a private trunk line, its AuthCode, and the | The | |||||||||||||||||
| destination number ,i.e., the originating/destination pair. | final list 49 forming each redundant database 28-29 is the | |||||||||||||||||
| This information is transported in the normal manner | customer company's override/allow lists. The | |||||||||||||||||
| 32 to the telcmarketcr's telecornmunication | ||||||||||||||||||
| company's carrier's primary switch cluster 13-14. | customer | |||||||||||||||||
| At the cluster, the switch 13-14 determines if the | ~ company may have established relations with one or | |||||||||||||||||
| call originates [mm a handset 15-20 which is subject | more | |||||||||||||||||
| to call | individuals who, while unwilling to accept telemarketing | |||||||||||||||||
| blocking 33. If not, the call is then automatically muted | calls in general. are willing to accept telemarketing calls | |||||||||||||||||
| normally 34 to the | destination telephone number. | from this particular customer company. This list contains | ||||||||||||||||
| However, when the call originates from a telephone | all | |||||||||||||||||
| handset 15-16 | such numbers for a customer company and is tagged with | |||||||||||||||||
| which is subject to blockin& the call is so recognized by the | the 10 customer company's CM to permit calls to such persons | |||||||||||||||||
| primary switch cluster 13-14, the call is held at the | 53 | |||||||||||||||||
| switch | by the allowed customer company. | |||||||||||||||||
| cluster 13-14 | and | the originating/destination | pair | FIG. 4 is a flow diagram showing the process for carrying | ||||||||||||||
| information is transported 35 to one of the control | out the Block/Complete Algorithm. Wben an originating/ | |||||||||||||||||
| computers 26-27. The control computer 26-27 then | destination pair arrive at the control computer for review, it | |||||||||||||||||
| determines whether | the calls should be permitted or | is first compared 55 with the customer list 45 to confirm that | ||||||||||||||||
| blocked by execution of a block/complete algorithm 36 as | the originating nurnber is that of a customer company. If it | |||||||||||||||||
| more fully discussed below. | Upon making | the | is not, the call is completed 56. If, however, it is on the | |||||||||||||||
| appropriate determination, the | control computer | 26-27 | customer identification list 45, the CM for the originating | |||||||||||||||
| transports the decision 37 to the switch cluster 13-14. | number is determined and used in obtaining the | |||||||||||||||||
| Depending upon this determination 38, either the call is | appropriate | |||||||||||||||||
| blocked 39 and a message is forwarded to the telemarketer | ~ information from lists 48 and 49. | |||||||||||||||||
| 40 indicating that the call has been blocked or is muted | The called number is then compared 58 to the federally | |||||||||||||||||
| normally 40. The entire decision making process is very | required do-not-call list 48. As previously noted, this do-not- | |||||||||||||||||
| rapid. It is unlikely that a lelemarketcr will | notice any | call list is tagged with the customer company's CN. If the | ||||||||||||||||
| delay in placing the call. | called number is on the federally required do-not-call list | |||||||||||||||||
| The block/complete algorithm used to make the block | for | |||||||||||||||||
| decision 36 is based on the information in the redundant | ~ that customer company, the call is blocked 59. if, on the | |||||||||||||||||
| do not call databases 28-29.As seen most clearly in FIG. | other hand, the called number is not on the federally | |||||||||||||||||
| 3 each redundant database 28-29 consists of a number of | required | |||||||||||||||||
| component lists 45-49. The database 28-29 is structured | list 48 for the customer company, i.e., the number is either | |||||||||||||||||
| around the customer | identification | list 45. | This | list is | not on the list or it is not called with the CM of the calling | |||||||||||||
| composed of an | identification code or | number | ("CN") for | customer company. If the same number is to be blocked | ||||||||||||||
| each customer | and | the telephone numbers | andIor S for :to two different customer companies, the number appears | |||||||||||||||
| AuthCodes corresponding to each customer. All originating ri twice | ||||||||||||||||||
| telephone numbers and AuthCodcs are tagged with the | on the do-not-call list 48, each time with a different tag. | |||||||||||||||||
| customer's CN.AII offices of a single company have a | The | |||||||||||||||||
| single CN. List 45 entries may also contain one or more | number is then compared 60 to the allowed/override list 49 | |||||||||||||||||
| flags called private | organization | or P0 | flags | that | 5 for the particular customer company as indicated by the CM | |||||||||||||
| determines whether or | not a customer has chosen to be | 5 | tag in the allow/override list 49. If the number is on the | |||||||||||||||
| blocked from calling the numbers | on one or more private | ~s allow/override list 49, the call is completed 64. If it is not | ||||||||||||||||
| organization maintained lists. If the value of a P0 flag is | on | |||||||||||||||||
| false, the customer has chosen not to be blocked by that | the allow/override list 49, the call number is then | |||||||||||||||||
| private organization's | do-not-call | list. List 45 allows the | compared 61 to the state mandated list 46. If the call number | |||||||||||||||
| control computer to select the relevant information from | is on the state mandated list 46, the call is then blocked 62. If | |||||||||||||||||
| lists 48-49 and determine whether to use list 47. | it is not | |||||||||||||||||
| List 46 is a composite list of all the state generated Lists | on the state mandated list 46, the programs determines | |||||||||||||||||
| from all relevant states. To this list may be added | ~ whether the private organization dip flag is at true or | |||||||||||||||||
| individuals who have requested the service provider to be so | false | |||||||||||||||||
| protected. The resulting list may be sorted by area code and | 63. 1111 is false, and thus the customer does not with to | |||||||||||||||||
| FIG. 4 | ||||||||||||||||||
| U.S. Patent | Sheet 4 of 6 | US 6,330,317 Bi | ||||
| adhere to the private organization's requested blocking, the | organiz.ation lists 47 are periodically updated, as are | |||||
| call is completed 64. if, on the other hand, the private | allow/override lists. New customer companies arc added to | |||||
| organization dip flag is true and, thus, the customer wishes | the system. All these changes require that the customer | |||||
| to conform to the request of the private organization, the | identification list 45, | |||||
| call number is then compared 65 to the private | the federally required do-not-call list 48 and the customer | |||||
| organization list 47. If it is not on the private organization | on override/allow list 49 be updated accordingly. In order to | |||||
| list 47, the call is completed 64. If, on the other band, it is | keep the redundant do-not-call databases 28 and 29 | |||||
| on the private organization list 47, the call is blocked. | current, the databases are updated daily with information | |||||
| Obviously, the contents of the do-not-call database 26-29 | received from the customers and as received with regard to | |||||
| must be updated as the underlying information changes. | information such as state mandated lists of do-not-call | |||||
| At present, except for Alaska, the states issue new state | numbers. | |||||
| mandated databases quarterly. The federally required do- | In order to accomplisb this result, a separate updating | |||||
| no-call list 48 changes daily as people indicate they do not | do-not-call database 70 is maintained on an updating com- | |||||
| desire a customer company to call them again. The private | puter (not shown) maintained by the service provider. As | |||||
FIG. 4
| U.S. Patent | Sheet 4 of 6 | US 6,330,317 Bi | ||||||||||||||
| US 6,330,317 Bi | ||||||||||||||||
| 7 | the appropriate table in the control computer, the change | |||||||||||||||
| seen in FIG. 5, the updating do-not-call database 70 is | request record in the user-interface | |||||||||||||||
| composed of a number of lists which are periodically updated | S | |||||||||||||||
| as new information becomes available. One of the component | computer is updated with the date of this addition. When | |||||||||||||||
| lists is the customer identification list 71 corresponding to | the | |||||||||||||||
| the customer identification list 45 contained on the control | customer requests a deletion, a record is added to the change | |||||||||||||||
| computer do-not-call database 28. In normal | request table; however, in this case, a record is deleted from | |||||||||||||||
| operation, new customer companies arc added and customer | the requested table. The date of the deletion request is | |||||||||||||||
| companies leave the service. Equally, existing customer | part | |||||||||||||||
| companies may change ielepbonc service, adding or sub- | s of the data entered in the change request table but not in | |||||||||||||||
| trading telephone numbers or AuthCodes for the service. As | the requested table. After verification that tbe requested | |||||||||||||||
| such changes occur, they are inputted into the customer | deletion | |||||||||||||||
| identification list 71 by the service provider to produce an | has been made to the appropriate table in the control | |||||||||||||||
| updated list of telephone numbers and AulhCodes tagged | computer, the change request record in the user-interface | |||||||||||||||
| with the appropriate CN. The updating do-not-call database | computer is updated with the date of this deletion. This | |||||||||||||||
| may also contain customer demographic information 72, | ~o enables the customer to determine, at any time, which | |||||||||||||||
| such as full corporate names, addresses, telephone numbers, | changes have been requested in which customer lists. The | |||||||||||||||
| billing information and the like associated with each CN for | customer can also determine which | changes have been | ||||||||||||||
| use of the service provider. | verified as being written in the control computer by looking | |||||||||||||||
| As each state mandated list is received by the service | at the date of the change. If the change has not occurred | |||||||||||||||
| provider, the service provider updates list 74 to include any | in is the control computer, the date appears as blank; | |||||||||||||||
| new numbers and make any other appropriate changes in the | otherwise, | |||||||||||||||
| list 74. State mandated lists may be provided over the | the date of the verification | of the | change | appears. | ||||||||||||
| Internet or by CD-ROM disk, each state having its own | Records in the change request tables arc never deleted in | |||||||||||||||
| unique protocols and software programs. Using such | order to maintain an audit trail of requested cbanges. | |||||||||||||||
| programs, the data may be converted to a common format | As noted above, the lists 71 through 78 forming the | |||||||||||||||
| for updating the state mandated lists 74. | 20 updating do-not-call database are updated in a number of | |||||||||||||||
| As noted above, in the control computer do-not-call | different fashions depending on the nature of the informa- | |||||||||||||||
| database 28, state mandated information is combined with | tion. Customer identification lists 71 arc inputted directly | |||||||||||||||
| the telephone numbers of individuals who have contacted | in the updating computer by the service provider as would | |||||||||||||||
| the service provider and requested their name be placed on | customer demographic information 72. Equally, state | |||||||||||||||
| the list. This information is kept on a separate private | man- | |||||||||||||||
| individual list 73 which is combined with the state | 25 dated Lists are normally supplied by the. state on CD- | |||||||||||||||
| mandated | ROM | |||||||||||||||
| list 74 to make up a single list in the control do-not-call | in a number of different protocols cacb having their own | |||||||||||||||
| database 28 during the transfer process of updating the | associated software. Thus, in order to make a list 74 the | |||||||||||||||
| control do-not-call base 28. | 35 | service provider would normally have to use each of the | ||||||||||||||
| Similarly, throughout the business day, each customer | separate types of software to transfer the information to a | |||||||||||||||
| company receives do-not-call requests from individuals. The | 30 common format where such information | would | be | |||||||||||||
| customer company stores the changes and periodically | lutegrated. | Similarly, private individuals requesting | the | |||||||||||||
| modifies federally required do-not-call list 76 maintained in | service | |||||||||||||||
| the updating database 70. List 76 is, in reality, a more current | provider place | them on a do-not-call list | would be inputted | |||||||||||||
| list of the federally required do-no-call list 48 forming part of | into its separate list 75 by the service provider which is then | |||||||||||||||
| do-not-call database 28. In a like manner, customer | integrated in the control computer's database 28]. | |||||||||||||||
| override/allow lists may change during the day as | However, the federally required do-not-call list 76 and | |||||||||||||||
| individuals, for example, request a call from the customer | customer override/allow lists 77 are a product of the indi- | |||||||||||||||
| company and, thus, updating do-not-call database 70 main- | vidual customer's business and are periodically changed | |||||||||||||||
| ~s tains an updating customer override/allow list 77. This is a | during the day. It has been found that the best way for | |||||||||||||||
| more current version of the information stored in the cus- | customer companies to forward | information to | the | |||||||||||||
| tomer override/allow list 49 of the control computer do-not- | updating 4° do-not-call database | 70 is by means of | the | |||||||||||||
| call database 28. Finally, the private organizations periodi- | Internet. | |||||||||||||||
| cally update their list and such updated lists are maintained on | FIG. 7 is a flow diagram of the method used to upload | |||||||||||||||
| private organization list 78 of the updating do-not-call | information from individual customers | for alteration of | ||||||||||||||
| database. This list 78 is the current list corresponding to | the federally | required do-not-call list 76 | and the | customer | ||||||||||||
| private organization list 47 on the control computer do-not- | override/allow list 77. A similar program can be used with | |||||||||||||||
| call database. | connection of updating the private organization list 78 and | |||||||||||||||
| Since it is important for control purposes to keep track | other lists where appropriate. | |||||||||||||||
| of ss the customer companies changes in the updating | Each customer is assigned a username and three pass- | |||||||||||||||
| database, a list of requested changes 73 is maintained. This | words at initial set up. The passwords permit the customer | |||||||||||||||
| historical record is contained in tables that are not | to logon to the server and read data (logan/read password), | |||||||||||||||
| necessary for operation in the control computer but must | add data to their "Do Not Call" or Md/Override lists (add | |||||||||||||||
| be maintained to verify that the customer has requested | password), and delete data from their "Do Not Call" or | |||||||||||||||
| these changes. When the customer requests an addition, a | Md/Override lists (delete password). As seen in FIG. 7, to | |||||||||||||||
| record is added to the change request table and to the | update the updating do-not-call | database with | the latest | |||||||||||||
| requested table in this user-interface computer. The date of | customer company information, | the | customer | company | ||||||||||||
| the add request is part of the data entered in the change | logs on to the Internet 80 and loads | the sub.scriber web | ||||||||||||||
| request table but not in the requested table. After | page SI, enters the customer name and password 82. | |||||||||||||||
| verification that the requested addition has been made to | 50 | |||||||||||||||
| FIG. 4 | ||||||||||||||||
| U.S. Patent |
| Sheet 4 of 6 |
| US 6,330,317 Bi |
| 65 Once the customer is accepted onto the system by entering his correct logon/read password, a page of options on a main menu is sent to the customer. This company-specific page shows the company name and other pertinent data to the customer. The data is read from the database by searching for the username and reading the customer's corresponding Customer Number(CN). The only data that the customer is |
60 permitted to see is that which is tagged by the CM that is associated with the company's u.sername. If the customer enters a username or password that is not in the database, or
FIG. 4
| U.S. Patent |
| Sheet 4 of 6 |
| US 6,330,317 Bi |
| US 6,330,317 BI |
| 9 | from the scope and spirit of the appended claims, they | |||||||||||
| does not correspond with each other in the database, an | are | |||||||||||
| error | intended to be encompassed therein. | |||||||||||
| page is sent to the customer and no data is displayed. The | ||||||||||||
| customer cannot obtain access to unauthorized data on any | The claims are: | |||||||||||
| page because the CM retrieved from the database at logon is | 1. A method for blocking outgoing telephone calls for | |||||||||||
| used to validate the customer's right to have the page loaded | a | |||||||||||
| in his internet browser. The validation is in the form of a | number of companies in accordance with one or more | |||||||||||
| - | ||||||||||||
| cookie that is placed on the customer's hard disk and lasts | do-not-call lists comprising the steps of: | |||||||||||
| only for as long as the customer's session lasts. When the | ||||||||||||
| session ends, the cookie disappears. The customer must | reviewing each outgoing telephone call to a telephone | |||||||||||
| enter a valid password to have the cookie placed on his 10 | switch at a | primary switch cluster of a telephone | ||||||||||
| machine. i~ it is not the correct password the customer is | carrier | |||||||||||
| brought back to the subscriber web page 81 and asked to | to determine if the telephone call was made from a | |||||||||||
| enter his name and password 82 again. | telephone subject to call blocking review; | |||||||||||
| The main menu displays options to add or deLete | holding calls subject to call blocking review while for- | |||||||||||
| numbers from the customer's "Do Not Call" list or from | ||||||||||||
| the custom- 15 er's Md/override list. There are also options | warding the | origination/destination | pair information | |||||||||
| corresponding to the originating telephone number or | ||||||||||||
| to display or download any customer list. If the customer has | AuthCode and the destination telephone number to | |||||||||||
| entered a | a control computer; | |||||||||||
| valid add password in addition to a valid uscrnamc and | comparing the destination number to one or more lists | |||||||||||
| read/logon password, requests to add a number to one of his | ||||||||||||
| lists will be. permitted. If the customer has entered a valid 20 | of | |||||||||||
| blocked telephone numbers, said lists having | ||||||||||||
| delete password in addition to a valid usemame and rcad/ | information | relevant to more than | one company; | |||||||||
| logon password, requests to delete a number from one of his | and | |||||||||||
| lists will be permitted. If it is the correct password, the | dcpending only | on whether the origination/destination | ||||||||||
| customer is asked to select a list which it desires to update | pair information appears on one or more of the lists, | |||||||||||
| 84. The caller is then presented with an appropriate web ~ | either blocking the telephone call | at | the switch or | |||||||||
| page for entry of the data and so enters the data 85. Entry | completing the call. | |||||||||||
| may be by hand, by forwarding a completed ~ie or by other | ||||||||||||
| means. Then the data 85 is reviewed to see if it is in a valid | 2. A method | according to claim | 1 | wherein each | ||||||||
| format 86. If it is not in a valid format, the customer is sent | telephone | |||||||||||
| back to reenter the data 85. If it is in a valid format, it is | number or AuihCode corresponding to an originating | |||||||||||
| then 30 entered 87 into the updating do-not-call database 70. | telephone placing a call subject to blocking review has a | |||||||||||
| The customer is then queried whether there arc any more | code associated with said number or AuthCode and the | |||||||||||
| lists to update 88. If so, the customer picks the next list to | numbers on said list or | lists being associated with said | ||||||||||
| update 89 and enters the appropriate data 85. If there arc no | code so that a telephone number appearing on a do-not- | |||||||||||
| further lists, the customer breaks the Internet connection 90. | call list will only block a call from a phone having the | |||||||||||
| The 35 updating do-not-call database is periodically | associated code. | |||||||||||
| transferred to all control computer do-not-call databases, | 3. A method according to cLaim 2 wherein the list or | |||||||||||
| usually once a day at a time traffic would be at a minimum. | lists contain information | for | two or | more groups of | ||||||||
| FIG. 8 is a flow diagram in the process of updating the | telephones from | which | call | originate, each group with | ||||||||
| control computer do-not-call database by the information | different identification codes. | |||||||||||
| contained in the updating do-not-call database 90. First, the | 4. A method according to claim 3 wherein one of the | |||||||||||
| Internet site for receiving updating information from the | lists | |||||||||||
| customers is closed 91. Thc information in the updating | is a list of blocked numbers compiled by an originating | |||||||||||
| database 70 is then bulk copied for transfer 92 and the | telephone group. | |||||||||||
| Internet site is reestablished to allow inputting of data for the | ||||||||||||
| next updating cycle 93. The files are then formatted 94 to | 5. A method according to claim 2 wherein one of the | |||||||||||
| correspond to the control computer do-not-call database. | lists is a list of blocked numbers compiled by other | |||||||||||
| This may include reorganization and integration of files | than the | |||||||||||
| such as the state mandated lists with the individual lists 94. | originating telephone group. | |||||||||||
| The control computer database 28 and 29 arc replaced with | 6. A method according to claim S where a destination | |||||||||||
| the data from the updating database 70. | appears on a list compiled by other than the originating | |||||||||||
| It is understood that the present embodiments described | telephone group, the number may then be compared with | |||||||||||
| above are to be considered as illustrative and not restrictive. | an override list which would allow the call to be placed | |||||||||||
| It will be obvious to those skilled in the art to make various | despite appearing on said list compiled by other than the | |||||||||||
| changes, alterations and modifications to the invention | caller. | |||||||||||
| dcscnbed herein. For example, while particular lists have been | 7. A method according to claim 6 wherein the | |||||||||||
| discussed in the body of this disclosure, other lists may be | destination numbers on the override list are tagged by | |||||||||||
| included or the databases may comprise entirely different lists | originating caller | |||||||||||
| than those set forth in the specification. The lists are ~O 60 be | ||||||||||||
| considered illustrative and not restrictive. To the extent that | code and the do-not-call list compiled by other than a | |||||||||||
| these variations, modifications and alterations depart | group is only overridden when the override number is | |||||||||||
| 10 | tagged with | |||||||||||
FIG. 4
| U.S. Patent | Sheet 4 of 6 | US 6,330,317 Bi | ||||||||
| the number of the originating caller code. | switch is a switch which accepts calls from a number of | |||||||||
| 8. A method according to claim 7 wherein the do-not- | telephones, only some of which are | subject to | call | |||||||
| call | blocking review. | |||||||||
| lists and the override lists for a group are updated by | 10. A method according to claim | 9 wherein | said | |||||||
| the | telephone | |||||||||
| caller through use of the Internet. | switch is a public switch operated by a common carrier. | |||||||||
| ç; 9. A method according to claim I wherein said telephone | ||||||||||
** * 4 *