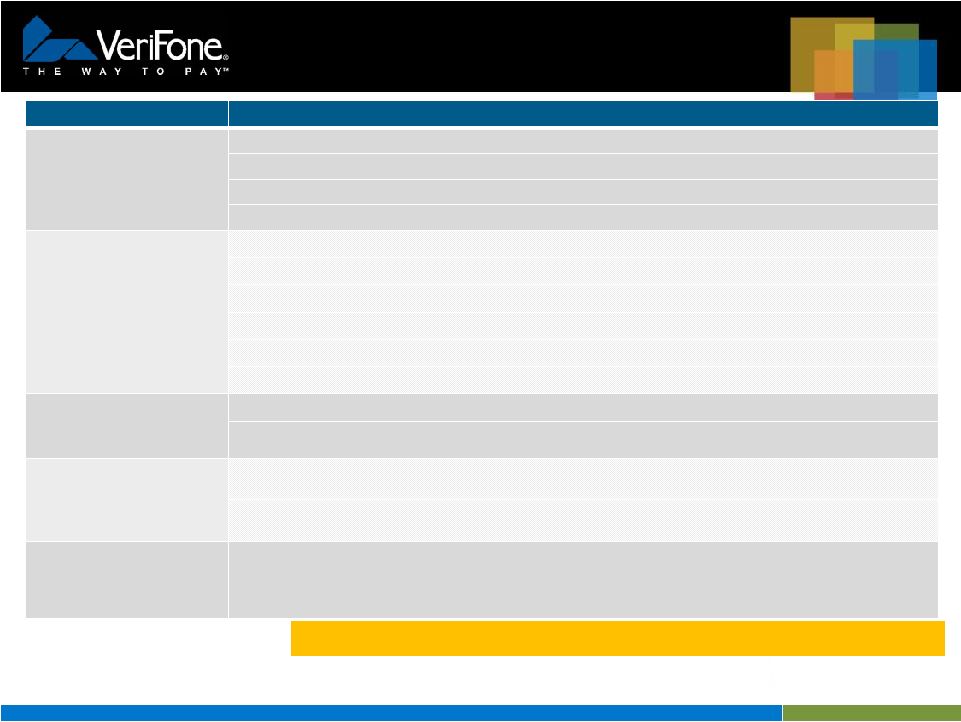
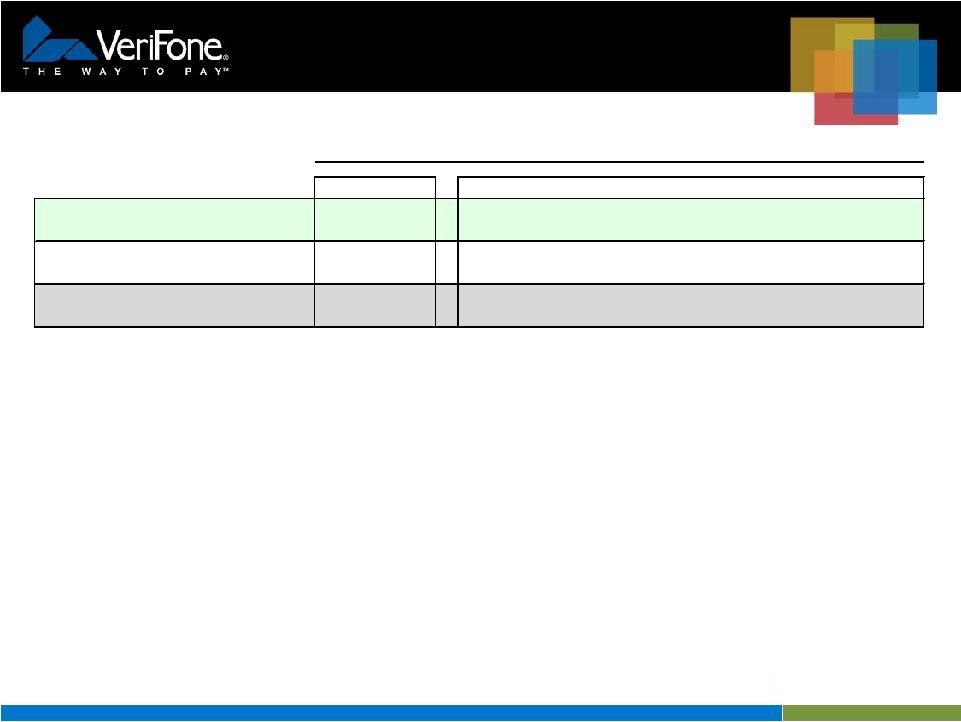
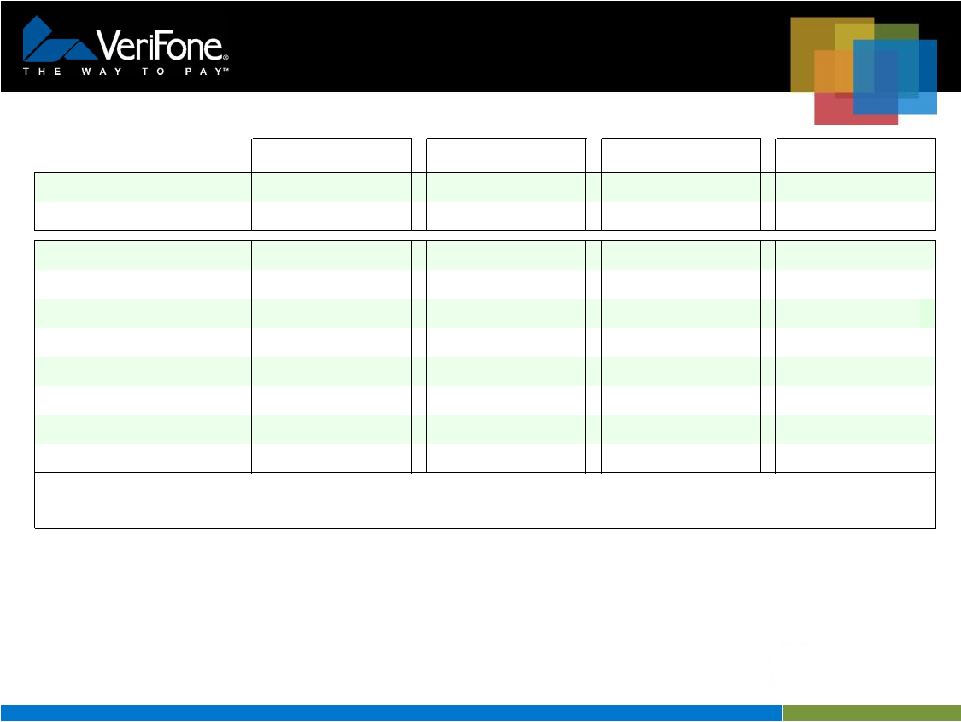
7 Visa Data Field Encryption Best Practices Security Goal Best Practice Limit clear text availability of cardholder data and sensitive authentication data to the point of encryption and the point of decryption. 1. Clear text cardholder and authentication data shall only be available at the point of encryption and decryption. 2. All cardholder data shall be encrypted using only approved encryption algorithms (e.g. AES, TDES). 3. All cardholder data and authentication data shall be encrypted except the first 6 and last 4 digits of the PAN. 4. Sensitive authentication data must not be stored after authorization even if encrypted (per PCI DSS). Use robust key management solutions consistent with international and/or regional standards. 5. Keys shall be managed per ANSI X9.24/ISO 11568 within Secure Cryptographic Devices such as a PED, HSM, etc. 6. All keys and key components shall be generated using an approved random process such as NIST SP 800-22. 7. Documentation describing key management solution must be made available upon request for evaluation purposes. 8. a) Keys shall be conveyed in a secure manner such as the key X9/TR-34 Interoperable Method for Distribution Keys 8 b) If remote key distribution is used, mutual authentication of the sending and receiving devices shall be performed. 9. Keys used in the data field encryption process must be unique per device Use key-lengths and cryptographic algorithms consistent with international and/or regional standards. 10. Encryption keys shall have strength of at least 112 equivalent bit strength. 11. FPE must be evaluated by an independent security evaluation organization and subjected to a peer review. Protect devices used to perform cryptographic operations against physical/logical compromises. 12. Devices used to perform cryptographic operations should undergo independent assessment to ensure that the hardware and software they are using is resilient to attack. 13. Keys shall be protected against physical and logical compromise. Public keys shall be protected from substitution and their integrity and authenticity shall be ensured. Use an alternate account or transaction identifier for business processes that requires the primary account number to be utilized after authorization,. 14. If any cardholder data is needed after authorization, a transaction ID or token should be used instead. VeriShield Protect Meets Visa Data Field Encryption Best Practices |