segregation of duties and the documentation and design of formalized processes and procedures surrounding the creation and posting of journal entries and account reconciliations. Additionally, our management identified a material weakness in our internal control over the fair value calculation of options granted during the quarter ended June 30, 2021. If not remediated, or if we identify further material weaknesses in its internal controls, our failure to establish and maintain effective disclosure controls and procedures and internal control over financial reporting could result in material misstatements in our consolidated financial statements and a failure to meet our reporting and financial obligations.
We may be adversely affected by natural disasters and other catastrophic events and by man-made problems such as terrorism that could disrupt our business operations, and our business continuity and disaster recovery plans may not adequately protect us from a serious disaster.
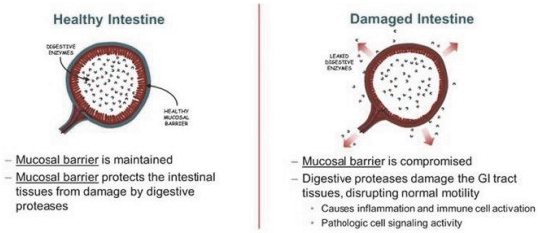
Our headquarters and main research facility are located in the greater San Diego area, which in the past has experienced severe earthquakes and fires. If these earthquakes, fires, other natural disasters, health pandemics or epidemics, terrorism and similar unforeseen events beyond our control, including, for example, the ongoing COVID-19 pandemic, prevented us from using all or a significant portion of our headquarters or research facility, it may be difficult or, in certain cases, impossible for us to continue our business for a substantial period of time. We do not have a disaster recovery or business continuity plan in place and may incur substantial expenses as a result of the absence or limited nature of our internal or third-party service provider disaster recovery and business continuity plans, which, particularly when taken together with our lack of earthquake insurance, could have a material adverse effect on our business. Furthermore, integral parties in our supply chain are operating from single sites, increasing their vulnerability to natural disasters or other sudden, unforeseen and severe adverse events. If such an event were to affect its supply chain, it could have a material adverse effect on our ability to conduct clinical trials, our development plans and our business.
If our information systems or data, or those of third parties upon which we rely, are or were compromised, we could experience adverse consequences resulting from such compromise, including but not limited to regulatory investigations or actions; litigation; fines and penalties; disruptions of our business operations; reputational harm; loss of revenue or profits; loss of customers or sales; and other adverse consequences.
In the ordinary course of our business, we may process, as defined above, proprietary, confidential, and sensitive data, including personal data (such as health-related patient data), intellectual property, and trade secrets (collectively, sensitive information). We may rely upon third-party service providers and technologies to operate critical business systems to process sensitive information in a variety of contexts, including, without limitation, third-party providers of cloud-based infrastructure, employee email, CROs, and other functions. Our ability to monitor these third parties’ information security practices is limited, and these third parties may not have adequate information security measures in place. We may share or receive sensitive information with or from third parties.
The risk of a security breach or disruption, particularly through cyber-attacks, cyber-intrusion, malicious internet-based activity, and online and offline fraud, are prevalent and have generally increased as the number, intensity, and sophistication of attempted attacks and intrusions from around the world have increased. These threats are becoming increasingly difficult to detect and come from a variety of sources, including traditional computer hackers, threat actors, personnel (such as through theft or misuse), sophisticated nation states, and nation-state-supported actors. Some actors now engage and are expected to continue to engage in cyber-attacks, including without limitation nation-state actors for geopolitical reasons and in conjunction with military conflicts and defense activities. During times of war and other major conflicts, we and the third parties upon which we rely may be vulnerable to a heightened risk of these attacks, including cyber-attacks that could materially disrupt our systems and operations, supply chain, and ability to produce, sell and distribute our products.
We and the third parties upon which we rely may be subject to a variety of evolving threats, including but not limited to social engineering attacks (including through phishing attacks), malicious code (such as viruses and
40