UNITED STATES
SECURITIES AND EXCHANGE COMMISSION
Washington, D.C. 20549
FORM 10–K
(Mark One)
| x | ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 |
For the fiscal year ended December 31, 2007
OR
| ¨ | TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 |
For the transition period from to .
Commission File Number 001-33197
GUIDANCE SOFTWARE, INC.
(Exact name of registrant as specified in its charter)
| | |
| Delaware | | 95-4661210 |
(State or other jurisdiction of incorporation or organization) | | (I.R.S. Employer Identification No.) |
| |
215 North Marengo Avenue Pasadena, California 91101 | | (626) 229-9191 |
| (Address of principal executive offices) | | (Registrant’s telephone number, including area code) |
Securities registered pursuant to Section 12(b) of the Act:
| | |
| Common Stock, $0.001 par value per share | | The NASDAQ Stock Market LLC |
| (Title of each class) | | (Name of each exchange on which registered) |
Securities registered pursuant to Section 12(g) of the Act:
None.
Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes ¨ No x
Indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes ¨ No x
Indicate by check mark whether the registrant: (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. Yes x No ¨
Indicate by check mark if disclosure of delinquent filers pursuant to Item 405 of Regulation of S-K is not contained herein, and will not be contained, to the best of the registrant’s knowledge, in definitive proxy or information statements incorporated by reference in Part III of this Form 10-K or any amendment to this Form 10-K. ¨
Indicate by check mark whether the registrant is a large accelerated filer, an accelerated filer, or a non-accelerated filer (as defined in Rule 12b-2 of the Exchange Act):
Large accelerated filer ¨ Accelerated filer x Non-accelerated filer ¨
Indicate by check mark whether the registrant is a shell company (as defined in Rule 12b-2 of the Exchange Act). Yes ¨ No x
The aggregate market value of the voting stock held by non-affiliates of the registrant computed by reference to the price at which the common equity was last sold on March 5, 2008, as reported on the Global Market tier of The NASDAQ Stock Market LLC was approximately $103,900,000.*
As of March 5, 2008, there were approximately 23,095,000 shares of the registrant’s Common Stock outstanding.
| * | Excludes shares of Common Stock held by executive officers, directors and stockholders whose ownership exceeds 5% of the shares outstanding at March 5, 2008. This calculation does not reflect a determination that such persons are affiliates for any other purposes. |
DOCUMENTS INCORPORATED BY REFERENCE
Portions of the registrant’s definitive proxy statement to be filed with the Commission pursuant to Regulation 14A in connection with the registrant’s 2008 Annual Meeting of Stockholders (the “Proxy Statement”) or portions of the registrant’s 10-K/A, to be filed subsequent to the date hereof, are incorporated by reference into Part III of this Report. Such Proxy Statement or 10-K/A will be filed with the Commission not later than 120 days after the conclusion of the registrant’s fiscal year ended December 31, 2007.
GUIDANCE SOFTWARE, INC.
Form 10-K
For the Fiscal Year Ended December 31, 2007
Table of Contents
TRADEMARKS
“Guidance Software,” “EnCase®,” “EnScript®,” “FastBloc®,” “CEIC®,” “EnCE®,” “NeutrinoTM” and other trademarks or service marks of Guidance appearing in this Annual Report are registered trademarks or trademarks of Guidance in the United States and in certain other jurisdictions. This report also contains additional trade names, trademarks and service marks of ours and of other companies. We do not intend our use or display of other companies’ trade names, trademarks or service marks to imply a relationship with, or endorsement or sponsorship of us by these other companies.
i
FORWARD-LOOKING STATEMENTS AND FACTORS THAT MAY AFFECT FUTURE RESULTS
This Annual Report (including the section regarding Management’s Discussion and Analysis of Financial Condition and Results of Operations) contains forward-looking statements regarding our business, financial condition, results of operations and prospects. Words such as “expects,” “anticipates,” “intends,” “plans,” “believes,” “seeks,” “estimates” and similar expressions or variations of such words are intended to identify forward-looking statements, but are not the exclusive means of identifying forward-looking statements in this Annual Report. Additionally, statements concerning future matters such as the development of new products, sales levels, expense levels and other statements regarding matters that are not historical are forward-looking statements.
Although forward-looking statements in this Annual Report reflect the good faith judgment of our management, such statements can only be based on facts and factors currently known by us. Consequently, forward-looking statements are inherently subject to risks and uncertainties and actual results and outcomes may differ materially from the results and outcomes discussed in or anticipated by the forward-looking statements. Factors that could cause or contribute to such differences in results and outcomes include, without limitation, those discussed under the heading “Risk Factors” below, as well as those discussed elsewhere in this Annual Report. Readers are urged not to place undue reliance on these forward-looking statements, which speak only as of the date of this Annual Report. We undertake no obligation to revise or update any forward-looking statements in order to reflect any event or circumstance that may arise after the date of this Annual Report. Readers are urged to carefully review and consider the various disclosures made in this Annual Report, which attempt to advise interested parties of the risks and factors that may affect our business, financial condition, results of operations and prospects.
ii
PART I
Overview
We develop and provide the leading software solutions for digital investigations. EnCase® Enterprise, our flagship product, enables corporations and government agencies to search, collect, preserve and analyze, from a single location, data across the servers, desktops and laptops that comprise their entire network. Our EnCase® Forensic software, which we believe is the industry standard tool in the field of digital forensic software, is used primarily by consultancies and law enforcement and government agencies for searching, collecting, preserving, analyzing and authenticating electronic computer forensic data for use in criminal and civil court proceedings. We also offer a comprehensive array of forensic investigation and training services to help our customers manage their internal digital investigations, including eDiscovery requests, and learn how to effectively and efficiently use our software. Our EnCase® Enterprise customer base currently includes more than half of the Fortune 50, nearly half of the Fortune 100 and more than 100 companies in the Fortune 500, and we have sold our EnCase® Forensic software to more than 1,000 government and law enforcement agencies and other customers worldwide.
We were incorporated in California in November 1997 and reincorporated in Delaware in December 2006.
Industry Background
The widespread reliance on digital business processes and the explosive growth in the volume of electronic data have resulted in exposure to electronic data-related risks and created the need to properly conduct digital investigations.
The global adoption of local area networks, wide area networks, e-mail and the Internet have increased communications within and between organizations and have created the ability to generate, store, share and distribute massive amounts of electronic information instantaneously without regard to physical location. While the adoption and reliance on these technologies has significantly increased productivity and lowered the cost of doing business for Global 2000 companies, government agencies and other organizations, it has also exposed organizations to many increasing areas of risk associated with the continued proliferation of electronic data. Organizations now are increasingly faced with the need to recover and analyze vast amounts of electronic data quickly and efficiently through processes we refer to as digital investigations. Digital investigations are conducted to address various electronic data-related needs, including:
| | • | | searching, collecting and processing litigation-related data, or responding to discovery requests for electronic data, or “eDiscovery” requests, where a company must conduct a thorough yet timely review of electronic data in order to produce forensically sound electronic documents or other digital evidence in connection with a particular civil or administrative proceeding; |
| | • | | responding to regulatory data requests, where an organization must efficiently and rapidly produce electronic documents and digital evidence in connection with a project under regulatory review in a manner acceptable to the regulators; |
| | • | | addressing corporate policy violations, such as intellectual property theft, employee fraud and employee policy violations, all of which must be investigated rapidly, described in a detailed, complete and comprehensible report of the incident and mitigated and remedied across an enterprise network as necessary, all while minimizing business interruption; and |
| | • | | responding to IT security attacks or breaches, where an organization must expeditiously and unobtrusively determine which systems or files were affected, the nature of the attack and how to remediate the issue quickly before any further damage occurs. |
Traditional investigations into electronic data-related threats are inadequate.
Traditional digital investigations involve internal investigators or third-party consultants manually searching through multitudes of electronic data in an attempt to discover traces or “fingerprints” of electronic data-related
1
incidents. Such investigators or third-party consultants typically use software applications, utilities or processes, such as taking the affected servers, desktops and laptops off-line, so that they can remove, image or copy the hard drives, manually extract the data in question on each affected computer and save the affected files to another hard drive for processing and analysis by consultants or other third-party experts. These traditional digital investigations suffer from several distinct problems, including the following:
They are costly and time-consuming. Most electronic data-related incidents that occur today involve more than one machine, and sometimes involve hundreds of thousands of servers, desktops and laptops operating across an enterprise including remote offices or workgroups, making the task of conducting manual investigations time-consuming, costly, and often beyond the resources of internal IT personnel.
They require significant expertise to conduct across complex enterprise network environments. An organization’s enterprise network generally consists of multiple operating system platforms and software applications operating simultaneously across a network of servers, desktops and laptops with layers of data that need to be identified, recovered, organized, analyzed, preserved and presented during the investigative process. In the context of a manual digital investigation, understanding the intricacies of each of the multiple operating system platforms and software applications requires extensive training and a high level of human expertise.
They may not adequately combat attempts to conceal data. An effective digital investigation must uncover and analyze all of the data relevant to the particular issue. This is extremely difficult to achieve in the digital world because perpetrators of malicious acts are typically motivated to hide incriminating evidence. Also, certain forms of IT security exploits, such as rootkits or keystroke loggers, embed themselves deep within the operating system and are undetectable by typical anti-virus software packages. Capturing data to facilitate the investigation is complicated, and traditional digital investigative techniques generally fail to capture all relevant data.
They often result in unwanted exposure of sensitive materials and disrupt business. Traditional digital investigative methods often result in physically removing the machines in question from the users and manually searching the hard drives for relevant data, thereby informing the subject employees and co-workers of the ongoing investigative process. In addition, traditional digital investigations can result in significant business disruption by removing affected machines from their users for extended periods of time.
They are difficult to conduct in a forensically sound manner. Digital investigations must be conducted in a forensically sound manner in order to preserve evidence for effective use in a court proceeding. In order to produce forensically sound evidence that can withstand legal challenges, including chain of custody, storage, cross-contamination and tampering allegations, any digital investigation must be conducted by expert personnel at all stages of the investigative process. Such personnel must be able to competently demonstrate that the chain of custody with respect to the evidence has not been broken or compromised and that the digital evidence has been properly stored in its originally discovered state without changes or alterations. Use of software applications, utilities or processes not designed to meet this legal threshold may damage, alter or overwrite evidence, such as critical dates and times, which may ultimately result in the evidence being refused by the court, or being substantially reduced in evidentiary value.
Establishing a comprehensive digital investigative software platform can help organizations address the inadequacies of traditional digital investigations and cost-effectively mitigate the risk of electronic data-related threats.
In order to effectively address the problems associated with traditional digital investigations, organizations require a comprehensive digital investigative software platform that enables them to cost-effectively conduct digital investigations at any time, quickly respond to eDiscovery requests and take decisive action in response to internal and external IT security and data breaches. Failure to effectively implement such a platform can expose an organization to significant risk and, in the case of the regulatory and legal environment, may subject the organization to criminal or civil penalties, fines or adverse judgments. For example Morgan Stanley incurred a
2
$1.5 billion judgment for failure to find and produce electronically stored information required by the plaintiffs in a timely and comprehensive fashion, Hewlett Packard suffered a high-profile company scandal by failing to properly conduct an internal investigation of their executive team, Phillip Morris USA was fined approximately $2.75 million for non-compliance with eDiscovery requests, and ChoicePoint Inc. failed to properly secure their customer’s private information which resulted in $15 million in fines. Recently, Qualcomm Incorporated was sanctioned over $8.5 million due to their eDiscovery preservation failures. Additionally, six attorneys representing Qualcomm were also sanctioned by the court and referred to the California State Bar, due to their failure to ensure their client was properly addressing and complying with their eDiscovery obligations. Although the order sanctioning the six attorneys was subsequently vacated, the $8.5 million sanction order stands and the fact that there was the initial referral to the State Bar has definitely highlighted this issue and caused concern amongst corporate counsel.
According to IDC, the market for digital investigation and cyber forensic solutions is expected to grow from $950 million in 2007 to $1.45 billion in 2009, representing a compounded annual growth rate of 24%. According to Socha-Gelbman, the market for eDiscovery solutions is expected to grow from $1.9 billion in 2006 to $4.1 billion in 2009, representing a compounded annual growth rate of approximately 29%. According to the 2006 Litigation Trends Survey by Fulbright & Jaworski L.L.P., corporations with over $1 billion in revenues responding to the survey reported that they were involved in an average of approximately 390 lawsuits in the United States.
We believe that amendments to the Federal Rules of Civil Procedure in late 2006 have motivated and will continue to motivate companies regularly involved in litigation in the federal courts to implement digital investigative software. These amendments mandate that litigants must meet after commencing litigation to discuss production of electronic evidence, specify that the general obligation of litigants to identify and preserve relevant evidence explicitly applies to electronic data in their possession, and empower litigants conducting discovery to specify the electronic format in which the other party should produce the electronic data. This is in contrast to the previous rules, under which there was no specific obligation to meet and discuss production of electronic evidence and both the obligation to preserve and identify electronic evidence and the format in which electronic data was to be produced during discovery were themselves the subject of frequent disputes between the parties.
Our Solution
We develop and provide the leading software solutions to conduct digital investigations. The key benefits and advantages of our products and services include:
Our EnCase® Enterprise software is designed to conduct enterprise-class digital investigations and operate across the largest and most complex enterprise network environments.
Our EnCase® Enterprise software is a network-enabled solution that allows corporations and government agencies to search, collect, preserve and analyze, from a single location, data across all of the servers, desktops and laptops that comprise their network and is designed to efficiently conduct enterprise-class digital investigations. EnCase® Enterprise enables our customers to rapidly search across networks of up to hundreds of thousands of servers, desktops or laptops. Our software also interoperates with a wide variety of computing environments that are typically found within the networks of large enterprise companies, including across 14 unique operating systems and 25 unique file systems. Customers can add our EnCase® eDiscovery product to EnCase® Enterprise to enable them to automate the traditionally manual eDiscovery process, or our EnCase® Automated Incident Response Solution to EnCase® Enterprise to automate the response to security breaches. Each of these add-on products is modular, offering customers the option to deploy the entire EnCase® Enterprise solution all at once, or incrementally as their needs arise. In addition, our customers may continue to enhance the capabilities of EnCase® Enterprise by utilizing our EnScript® programming language to write or incorporate customized applications specific to their network environments or investigative needs. These broad-ranging capabilities of EnCase® Enterprise give our customers the essential foundation on which to build a sophisticated, sound and secure platform for digital investigations.
3
Our EnCase® products and services provide cost-effective and efficient digital investigation solutions.
Our EnCase® products and services significantly reduce the disruption and expense entailed in a traditional digital investigation. The sophisticated technological capabilities of our EnCase® products often permit our customers to reduce the use of multiple third-party computer forensics, managed security services and consulting companies, thereby reducing the costs and resources required to conduct a comprehensive digital investigation. In addition, our customers are able to address issues that historically have been ignored or not timely addressed due to prohibitive cost and extensive time requirements to fully pursue such traditional digital investigations.
Our software enables comprehensive digital investigations by discovering concealed data.
One fundamental capability underlying our EnCase® Enterprise and EnCase® Forensic software is the ability to discover hidden or concealed data, such as rootkits. We have designed our software to run “beneath” the operating system, which enables our software to access the hard drive at the sector level, the smallest writeable area on a hard drive. Using EnCase®, our customers are able to collect data from the sectors on the hard drive in a raw format and analyze the entire accessible hard drive, including files not generally accessible to the average user. The software collects and stores this electronic data without any modifications that normally result from the traditional approach of detection, recovery and analysis of such data.
Our products and services are designed to minimize any disruption to business and to preserve the confidentiality of any investigation.
The EnCase® architecture enables customers to easily gain access and visibility into their entire IT infrastructure, which could easily comprise hundreds of thousands of servers, desktops or laptops, and permits trained data security personnel to conduct digital investigations from a single, centralized console, all without disrupting business operations or unnecessarily alerting employees. Our EnCase® products and services enable our customers to not only minimize the disruption to their businesses resulting from the shutdown or removal of servers, desktops and laptops, but also to preserve the sensitivity and confidentiality of any digital investigation.
EnCase®, which is the recognized standard for digital investigations in the courtroom, preserves forensically sound digital evidence for presentation by investigators.
We believe that EnCase® is the most widely recognized and trusted digital investigative solution across the Global 2000 and among federal, state, local and foreign government agencies. Since its introduction in 1998, EnCase® has been used in thousands of criminal and civil cases, including a number of the highest profile criminal cases, such as the Scott Peterson murder trial and the BTK killer case. There is established case law that affirmatively supports the admissibility of digital evidence collected via EnCase®, as it has been cited by name or discussed in over 40 judicial decisions or opinions from federal, state and foreign courts. From our first beta release in 1998 to our sixth generation product released in 2006, EnCase® Forensic has been designed to enable increasingly powerful forensics capabilities for our customers while placing the utmost emphasis on processes and procedures that demonstrate the integrity of the investigative process in court. As a result, EnCase® has become a globally recognized standard for digital investigations and trusted electronic data collection.
Our consulting, implementation and training services enhance the capabilities of our product offerings.
We offer a comprehensive array of consulting, implementation and training services to help our customers. We provide eDiscovery and computer security incident response services, conduct digital investigations on behalf of our customers and perform systems and software maintenance and document retention audits. Many of our professional consultants are asked to testify in court as industry experts in the field of computer forensic investigations. Our training program offerings enable our customers to learn how to maximize the capabilities of EnCase®, which permits our customers to maintain digital investigation expertise within their organizations. In addition to training courses, we also provide an EnCase® Certified Examiner (“EnCE®”) program, which certifies the competency of public and private sector employees in the best practices of digital forensic investigations and in the use of our EnCase® products in such digital investigations.
4
Our EnCase® products are designed to meet the unique digital investigative needs of federal, state, local and foreign government agencies and law enforcement personnel.
Our EnCase® Forensic software enables federal, state, local and foreign government agencies and law enforcement personnel to conduct, on a single machine, the full array of forensic functions, including data capture, analysis and the documentation and reporting of digital evidence, all while preserving the legal integrity of the investigation process. Many of these government agencies also use our EnCase® Enterprise software to address their specific internal digital investigative concerns, including classified message leaks and cyber warfare.
Our Strategy
Our objective is to enhance our position as a leading global provider of digital investigation solutions for large corporations, government organizations and law enforcement agencies. The key elements of our strategy include:
Expand our leadership in enterprise eDiscovery solutions and continue to address compliance investigative needs.
We are the industry leading provider of eDiscovery software. One of our primary objectives is to establish our EnCase® eDiscovery solution as the standard platform from which major organizations perform their eDiscovery operations. To accomplish this, we seek to expand our current market leading position by continuing to be an industry leading enterprise solution for the search, preservation and collection of electronically stored information throughout an organization’s network. We also seek to expand our current capabilities in the processing of collected data, which is an important and typically expensive step subsequent to collection in the eDiscovery workflow. Additionally, we will continue to develop strategic partners and technical integrations with complementary products to complement our solutions and expand the reach into corporate counsel and other executives at target accounts. We will also continue to leverage our Professional Services Division, training program, in-house legal experts and other areas of internal expertise to provide a complete eDiscovery solution and advance this strategy.
EnCase® Enterprise serves as the platform to enable several forms of enterprise computer investigations driven by compliance requirements. We provide high-value modules on the EnCase® Enterprise platform such as EnCase® eDiscovery and EnCase® Information Assurance, which greatly enhance, scale, and automate the search, collection, preservation and analysis of data in order to accomplish specific tasks, such as electronic discovery, internal investigations, electronic content retention audits, or proactive audits to identify the leakage of intellectual property or customer privacy data. We seek to extend our leadership position in this industry by continuing to innovate and launch new products and services addressing these needs.
Continue to drive revenue growth by pursuing new customers, providing additional products and services to our base of existing customers and expanding internationally.
Our sales strategy is primarily focused on securing new customers in the United States in the corporate and government markets. We plan to continue providing additional modules and services to existing EnCase® Enterprise customers to enhance their ability to realize the benefits of a total enterprise investigative infrastructure. Since a portion of our existing EnCase® Enterprise customers only have the introductory level bundle of our EnCase® Enterprise software product, our sales strategy for these customers focuses on follow-on sales of additional products, professional services and training. For the year ended December 31, 2007, we derived approximately 23% of our revenues from sales of products and services outside the United States. We believe that there is a large opportunity to market and sell our EnCase® Enterprise solutions in the Europe, Middle East and Africa (“EMEA”) and Asia-Pacific regions, and therefore we are continuing to invest in sales and distribution infrastructure to address these under-penetrated markets. We have a regional headquarters in EMEA as well as direct and indirect sales efforts in Canada, Mexico, Brazil, Japan and Singapore. Our products are now available in 11 languages and include double-byte capability for Asian languages.
5
Continue to be a leading innovator in the investigative technology industry.
We plan to continue creating new software offerings that enable our customers to further leverage the power of our digital investigation software solutions. We maintain an advanced research group that focuses on developing next generation concepts in digital investigative forensics by responding to user feedback and other key influencers in the digital forensics and legal communities and monitoring industry and technology trends. In addition, our Professional Services Division is often engaged to build customized applications utilizing our EnScript® programming language for specific customer needs. Since we retain the ownership of the code used in such customized applications, we have the ability to develop future products that are applicable to our broad customer base as a result of these professional engagements. When appropriate, we then turn these end products into separate add-on modules available for all customers or incorporate them into the general software code base. We believe our in-house, proprietary approach to software development is a competitive advantage, and we plan to continue to maintain this approach in the future.
Continue to maintain our legal recognition as a barrier to entry into our industry.
We believe that EnCase® software is the leading digital investigative solution across the Global 2000 and among federal, state, local and foreign government agencies. We continue to make great efforts to ensure that our products continue to be respected as the leading digital investigative solution. Our software products are designed to comply with United States federal and state rules of evidence and to withstand legal challenges in civil and criminal proceedings. Our products have been used in thousands of criminal and civil cases in federal, state and foreign courts, and EnCase® software has been cited by name or discussed in over 40 judicial decisions or opinions, including at the appellate court level. This process of judicial recognition and validation is a lengthy, time-consuming process that requires years of litigation and appeals that cannot be easily replicated. We have had members of our team testify in court proceedings or provide affidavits in connection with the development, credibility and proper use of our products. In addition, we place a strong emphasis on training our customers and users on the best practices of digital investigations and the use of our products in such investigations to maintain a reputation for reliability. We also publish the EnCase® Legal Journal and white papers on certain key topics of interest to our user community to further this effort.
Drive a network effect around our software.
We believe that as we continue to train or certify more users on our software products, these users will help us to drive wider adoption of EnCase® Enterprise and emphasize the importance of an enterprise investigative infrastructure. In the year ended December 31, 2007, we trained thousands of individuals through approximately 4,800 courses on various computer forensics and EnCase® software topics, and we offered our training services in 30 countries and eight languages. In turn, the increasing use of EnCase® Enterprise by corporations and federal, state, local and foreign government agencies will continue to drive the need for more users to become trained on our software product offerings, particularly since our training course offerings and EnCE® certification program often make these individuals more sought after in the job marketplace. We believe our annual user conference, known as the Computer and Enterprise Investigations Conference, has become the leading gathering place for the computer forensics and digital investigations industry. Our 2007 Computer and Enterprise Investigations Conference hosted approximately 850 participants, and we will continue to hold this conference to allow our users to connect, share and learn about important topics and products in the computer forensics and digital investigations industry. We also provide all of our users with an online community where they can share ideas with each other and provide feedback to us on the products. Through this online community, hundreds of customized EnScript programs that automate specific processes when run on EnCase® Enterprise or EnCase® Forensic have been published by, and downloaded from, our large user community. In addition, certain third parties have written commercial applications that utilize the EnScript programming language to leverage the capabilities of EnCase® software. We believe this community of developers and users helps to drive a network effect that contributes substantially to our competitive barriers to entry, and we intend to continue to actively drive this network effect in the future.
6
Emphasize customer satisfaction.
Our user community has grown to encompass IT and forensics investigators at a significant number of federal and state governments, local investigative bodies and corporations. We believe this loyal user base is one of our most valuable assets. We maintain a separate group within our sales organization that is responsible for calling on existing customers to ensure full customer satisfaction. In order to promote better customer service, we have expanded our telephone technical support hours, which are now available around the clock from 7:00 PM Sunday to 6 PM Friday Pacific Time, while maintaining online technical support services to our customers 24 hours per day, seven days per week.
Products and Services
Our products and services give our customers the ability to conduct comprehensive, cost-effective and precise digital investigations. Our EnCase® Enterprise software, enhanced with EnCase® eDiscovery and our EnCase® Information Assurance, provide the foundation to build an enterprise investigative infrastructure. Furthermore, we believe our EnCase® Forensic software is the industry standard for searching, collecting, preserving, analyzing and authenticating electronic computer forensic data for use in criminal and civil court proceedings. We also offer a comprehensive array of forensic investigation and training services to help our customers manage their internal digital investigations and learn how to effectively and efficiently use our software.
EnCase® Enterprise Software
EnCase® Enterprise provides an investigative platform that enables an organization to search, collect, preserve and analyze data on the servers, desktops and laptops on its computer network. EnCase® Enterprise enables organizations to respond to electronic discovery requests, conduct internal investigations, whether human resources-related or focused on compliance or fraud, collect and preserve data in response to requests from regulators or for civil litigation matters and take decisive action in the face of security and data breaches, whether the origin of the worm, virus or other exploit is internal (e.g., “rogue employees”) or external (e.g., “hackers”).
EnCase® Enterprise serves as the platform for an enterprise investigative infrastructure, to which additional products can be added to enhance and automate the search, collection, preservation and analysis of data in order to accomplish specific business tasks such as: responding to electronic discovery requests; performing proactive, enterprise-wide, data audits for sensitive information such as personally identifiable information, classified data, and intellectual property; and responding to and remediating network threats or intrusions. These products, which can be added to perform the functions above, include EnCase® eDiscovery, EnCase® Information Assurance, EnCase® Automated Incident Response, and EnCase® Data Audit and Policy Enforcement, which is a new product to be launched in 2008. The core EnCase® Enterprise platform consists of five separate components: the Examiner, the Secure Authentication for EnCase® (“SAFE”), the Servlet, the Enterprise Concurrent Connections and SnapShot.
Examiner. The Examiner provides the user with a graphical user interface through which the user can access, interact and enable the various capabilities of EnCase® Enterprise. Key features of the Examiner include advanced filtering, multiple case management, the ability to search and analyze structured and unstructured data and multi-lingual support.
SAFE. The SAFE (Secure Authentication for EnCase®) is primarily an authentication tool that ensures that the Examiner is properly credentialed before permitting the Examiner to access a server, desktop or laptop on the network. The SAFE allows the organization to control the Examiner’s access to information, which is critical to ensuring the proper segregation of duties and restricting access to sensitive information. The SAFE also controls communications between EnCase® Enterprise components, encrypts data transfer between such components and controls user authentication. Every connection between any two computers is uniquely encrypted and controlled by the SAFE to prevent circumvention of the system or the theft of data in transit.
7
Servlet. The Servlet is a small, non-intrusive piece of software that is deployed on each server, desktop or laptop to which investigative access is sought. The Servlet is designed to be easily deployed over the network across thousands of servers, desktops and laptops within hours and not to interfere with any existing applications or processes. The Servlet enables the Examiner to access information on the target server, desktop or laptop, including the contents of both static and volatile memory.
Enterprise Concurrent Connection. The Enterprise Concurrent Connection is a single secure virtual connection established between the Examiner and the servers, desktops or laptops that are being searched or investigated. In essence, the Enterprise Concurrent Connection is a licensing tool limiting the number of computers that can be analyzed simultaneously; the greater the number of Enterprise Concurrent Connections that are licensed, the more quickly the organization can search large quantities of data residing on its servers, desktops and laptops.
Snapshot. Snapshot is an add-on module to EnCase® Enterprise that captures data and information stored in the Random Access Memory (“RAM”) of servers, desktops and laptops on an organization’s network. Information such as the listings of the logged-on users, open ports and open files currently in use on a system, applications and active processes currently running on the system and the live registry are located in RAM. Snapshot captures this information and provides the user with an easy-to-use report on what was occurring on a system at a given point in time. The Snapshot technology enables the user to scan thousands of computers to detect, collect, preserve and remediate any network intrusion on an enterprise-wide scale. It is also used to determine the scope of certain eDiscovery or human resources investigations.
EnCase® eDiscovery
EnCase® eDiscovery automates the search, collection, preservation and processing of data across multiple servers, desktops or laptops on an organization’s network. The user is able to utilize EnCase® eDiscovery to search specifically targeted computers and then collect and process only the potentially relevant information, thereby eliminating the enormous costs associated with the collection, advanced processing and review of meaningless or duplicate information. EnCase® eDiscovery allows the user to search and collect data from servers, desktops or laptops throughout the enterprise, and searches can be conducted based on a variety of criteria, including, but not limited to, by file type, “keywords”, custodian, file digital fingerprint, or metadata such as creation, modified or last accessed times, or any combination of these criteria. EnCase® eDiscovery is able to collect individual files, including the associated metadata, while preserving the data in its original state, including the associated metadata. Once the initial search has been conducted and the information has been collected, EnCase® eDiscovery is then able to process that data to further reduce the volume of irrelevant or duplicative information. EnCase® eDiscovery’s robust in-house processing capabilities enable secondary culling and “Load File” creation for certain attorney review platforms. EnCase® eDiscovery’s search and collection can be performed around the clock on an automated basis, and can be scaled to the size of large enterprises. The software enables large-scale collections to be performed across the network without disrupting business, degrading network performance or taking the servers off-line. EnCase® eDiscovery tracks collection results in a database so that, at any given time, the status of the data collection effort can be viewed and communicated to others. The collected and processed data is placed in a secure virtual container called a Logical Evidence file, or LEF, and the data can be uploaded to third-party eDiscovery attorney review platforms to complete the eDiscovery process.
EnCase® Information Assurance
EnCase® Information Assurance (“IA”) is a solution specifically designed for government organizations. It enables government organizations to scan thousands of nodes at unprecedented speeds, understand at the disk level what is stored or occurring on the machines, and, if necessary, remediate improper activity without disrupting operations. With EnCase® Information Assurance, government agencies are able to ensure strict
8
compliance with critical information security mandates, such as FISMA, DCID 6/3 and FOIA. EnCase® Information Assurance is comprised of four key subcomponents:
| | • | | Audit and Compliance module. Ensuring the proper access of classified documents is a high priority mandate for government agencies of all types. The Audit and Compliance module enables security professionals to comprehensively search a government network to locate classified documents, and, if required, delete them. |
| | • | | Automated Incident Response Solution (“AIRS”) module. AIRS, described below, is included in EnCase® Information Assurance to provide automated computer security incident detection and response. |
| | • | | Vulnerability and Threat module. Information Assurance Vulnerability Audit (“IAVA”) compliance is a federal standard that requires all government desktops, servers and laptops to be properly patched at all times. The Vulnerability and Threat module enables our government customers to audit their networks to check their compliance and identify machines that are not properly patched. |
| | • | | InfoCon Hardening. Government customers are particularly sensitive to their networks of desktops, servers and laptops being exposed to malware or unapproved applications. The Infocon Hardening module enables an organization to identify and delete unapproved applications, malware and computing processes that are running across their servers, desktops and laptops. |
EnCase® Automated Incident Response Solution
The EnCase® Automated Incident Response Solution (“AIRS”) is an add-on to the EnCase® Enterprise platform that enables both reactive and proactive computer-related incident response.
For reactive incident response, AIRS can integrate with security incident management products. AIRS enables an organization to automate the traditionally time-consuming process of incident detection and response. With AIRS, alerts trigger automated retrieval of volatile data, and can also retrieve hard drive data to search for malware, including hidden processes such as rootkits, keystroke loggers and other forms of spyware. Rootkits are typically hidden applications that provide ongoing and unauthorized access to computers. Keystroke loggers are applications that record the computer user’s keystrokes and deliver the information to a third party. Spyware is any application that is installed without the computer user’s informed consent, and has the ability to change, collect, and transmit information about the user’s activities to a third party. Each event from the alerting system sent to AIRS goes through a two-step triage process to filter out false positives and assess whether a computer was actually compromised. AIRS can then delete the malware from the affected servers, desktops, and laptops. In addition, depending on the severity of the event, as defined by the alerting system and the initial triage, AIRS automatically follows up with additional data retrieval to identify any activity that has occurred on the affected servers, desktops, and laptops after the initial triggering event. The event data from the alerting system and the supporting near-time data collected by AIRS is aggregated into a database that enables thorough analysis by incident responders and security analysts.
For proactive incident response, a customer can use AIRS to sweep its network to identify and delete malware from its servers, desktops, and laptops. Most information security products, such as anti-virus, host intrusion detection and personal firewall software, cannot detect many of the hidden processes that AIRS can identify and remediate. In addition, since AIRS can be used on a proactive basis, our customers can track the frequency and severity of their malware outbreaks.
EnCase® Forensic Software
EnCase® Forensic software is the leading tool for searching, collecting, preserving and analyzing computer forensic data and authenticating such data in court. EnCase® Forensic enables an investigator to conduct the full array of forensic functions on a single machine while preserving the integrity of the evidence for future use in
9
court. Used by investigators and consultants in law enforcement, government agencies, small businesses, consulting firms and corporations, EnCase® Forensic software provides a robust way to authenticate, search and recover computer evidence rapidly and thoroughly.
EnCase® Forensic has the same capabilities as the Examiner in our EnCase® Enterprise software, other than the capability to search across networks. Computer evidence recovered with EnCase® Forensic software has been accepted and admitted into thousands of court proceedings in several countries.
FastBloc® Write-Blocking Hardware and Software
FastBloc® hardware and software is used to connect EnCase® Forensic to a hard drive to which investigators have physical access. FastBloc® hardware acts as a middleman between the operating system and the hard drive and physically blocks any hard drive write requests. This is a system primarily used by law enforcement and is designed to provide the investigator an extra level of protection against the possibility of original evidence being damaged on the hard drive.
FastBloc® SE is the first commercial software write-blocking solution that allows EnCase® to take full control of IDE, SATA and SCSI channels on particular PCI controller cards, as well as the FireWire and USB ports from Windows, thereby permitting an extra level of protection against damaging original evidence without the use of hardware write-blocking devices. In addition, FastBloc® SE allows forensic investigators or consultants to override and access host-protected areas and device configuration overlays.
Neutrino™
In 2007, we released our mobile device investigative solution, Neutrino™, which enables our court-accepted EnCase® Forensic technology can be used to help investigators recover, search, analyze and report on mobile device data. When used in conjunction with EnCase® Forensic, users can analyze and document both mobile device data and computer data simultaneously to correlate all evidence during an investigation. Neutrino™comes with the patent-pending WaveShield™ signal blocking bag. Other signal blocking bags on the market today fail to dependably block wireless signals to the device being examined, thereby, raising the risk of a corrupted investigation. We believe that based on extensive, real-world application, the WaveShield™signal-blocking bag is the only solution that reliably allows for the secure acquisition of mobile device data in the field.
Professional Services
Our Professional Services Division provides various consulting services to our clients, including eDiscovery, network security incident response, civil/criminal digital investigation and implementation services. In addition, we offer certain packaged services based on the specific needs of our customers, including our government customers. We have security clearances that enable us to better service our Department of Defense customers.
eDiscovery. Our consultants provide professional eDiscovery services to clients. Using the power of the EnCase® Enterprise and EnCase® eDiscovery software, our consultants are able to significantly reduce the amount of data collected, thereby reducing the costs and time of processing, hosting, reviewing and producing data relevant to a particular discovery request.
Network Security Incident Response. We provide sophisticated network security incident response services to our clients. Using EnCase® Enterprise software, our consultants seek to locate the data that tells what really happened in a security breach, and to pinpoint the actual method of entry. Our consultants also provide customized EnScript® programming, integration services with respect to information security alerting systems, and can also remediate unknown or malicious processes.
10
Civil/Criminal Digital Investigations. We employ a team of trained criminal/civil computer investigation consultants, many from law enforcement or military backgrounds, who are skilled at conducting computer forensics analysis. Our computer forensics consulting engagements range from straightforward human resources or computer misuse matters to far-reaching complex intellectual property theft investigations. Our consultants also provide expert testimony and present evidence in connection with digital investigations.
Implementation of EnCase® Enterprise. We provide implementation and consulting services in connection with the deployment of our EnCase® Enterprise, Encase® eDiscovery, Encase® Information Assurance and AIRS software. Our implementation typically takes one to two weeks, during which we conduct performance tests to ensure full functionality and integration with existing systems in the organization and provide on-site training to ensure our customers can maximize the use of the EnCase® Enterprise technology. Our consultants are encouraged to recommend our add-on products to our customers in order to further enhance the capabilities of our EnCase® Enterprise software.
Packaged Consulting Services. We also offer pre-packaged services to serve specific customer needs.
| | • | | eRecords Management Audit. We recently began offering an eRecords Management Audit service, in which our consultants utilize EnCase® Enterprise software to audit a customer’s computers or servers for compliance with its record retention policies. We search the individual files on the hard drives and servers of the system by “file created” and “last accessed” dates to identify those files that violate records retention policies, and provide the client with a detailed report identifying the files that are out of compliance. In addition, if desired we can also remediate the offending files from the system. |
| | • | | Compromise Assessment. We offer a packaged “Compromise Assessment” service in which our experts use EnCase® Enterprise software to scan a set number of computers or servers on a client’s network to identify malicious code and remediate where necessary. |
Customer Service and Technical Support
Customers typically purchase software maintenance with each new product license. Customer support generally involves software updates, telephone and e-mail support, on a 24 hours per day, five days per week basis, as well as customer self-service on our website. Customers are typically provided an option to renew their maintenance agreements on an annual basis. Our technical support organization provides product support to our current customers on a multi-tiered offering and includes support availability 24 hours per day, five days per week, in English, and is also available during normal business hours in several other languages, including German and Spanish.
Training
Our Training Division trains thousands of students per year in computer forensics principles and the use of our EnCase®. Because of the sensitive nature of digital investigations and the need to conduct digital investigations in a forensically sound manner, our users will typically take one or more of our courses. We provide an array of training courses on topics such as computer forensics, digital investigations, the proper use of our software products and the EnScript® programming language, which teach our customers’ IT and data security professionals the basic principles of computer forensics, train them on the basic and advanced capabilities of our software products and teach them to write EnScript® programs. We have retained third-party training partners in order to provide training around the world. Our extensive training program has enabled us to create a human capital knowledge base that can expand the recognition and demand for our products and services.
We operate two training classrooms in Pasadena, California, two near Washington, D.C., one near Chicago, Illinois and one near London, England. In addition, our authorized training partners offer certain courses in the U.S., Canada and Australia. In 2007, we conducted training classes in 30 different countries. In addition to offering courses in English, we have begun to localize our courses by converting the course content and manuals into other languages, and delivering the courses in those languages. To date, we have created courses in German, Spanish, Korean, Romanian, Polish, Japanese and Chinese.
11
Unless otherwise indicated below, each of our courses involves 32 hours of classroom instruction. Many of our courses are eligible for credit from a variety of organizations, including the State Bar of California, the International Information Systems Security Consortium, Inc., the National Association of State Boards of Accountancy, Association of Certified Fraud Examiners, the Texas Commission on Law Enforcement and the California Commission on Peace Officer Standards and Training. We are continually expanding our training offerings and we believe that we are the leading corporate provider of this type of digital investigation training.
As of December 31, 2007, we offered the following training courses:
EnCase® Forensic Series:
| | • | | EnCase® Computer Forensics—Phase I; |
| | • | | EnCase® Computer Forensics—Phase II; |
| | • | | EnCase® Advanced Computer Forensics; |
EnCase® Enterprise Series:
| | • | | EnCase® Enterprise—Phase I; |
| | • | | EnCase® Enterprise—Phase II; |
EnCase® Field Intelligence Model (FIM) Network Forensics;
Neutrino Mobile Phone Forensics (16 hours);
Expert Series:
| | • | | EnCase® Advanced Internet Examinations; |
| | • | | EnCase® EnScript® Programming—Phase I; |
| | • | | EnCase® EnScript® Programming—Phase II; |
| | • | | EnCase® Network Intrusion Investigations—Phase I and Phase II; |
| | • | | EnCase® Network Intrusion Investigations—Phase II; |
| | • | | EnCase® New Technology File System (“NTFS”) I: NTFS Artifacts and File Systems; |
| | • | | EnCase® NTFS II: Windows Networking Investigations; and |
EnCase® EnCE Prep (21 hours).
EnCE® Certification
The EnCE® program certifies the competency of public and private sector employees in the best practices of computer forensic investigations and in the proper use of EnCase® while conducting such investigations. In order to obtain EnCE® certification, professionals must have at least 18 months of total investigative experience with at least six months experience in computer forensic investigations, complete extensive training requirements and pass a dual-phase EnCE® examination. EnCE® certification acknowledges that professionals have mastered computer forensic investigation methodology as well as the use of EnCase® during complex computer examinations. Our EnCE® program is recognized by both the law enforcement and corporate communities as a symbol of in-depth computer forensics knowledge, and EnCE® certification illustrates that an investigator is a skilled computer examiner. As of December 31, 2007, more than 1,400 people worldwide had achieved EnCE® certification.
12
Technology
Both our EnCase® Enterprise and EnCase® Forensic software share three primary components of our technology.
EnCase® Evidence File
Our EnCase® Evidence File and EnCase® Logical Evidence File are proprietary solutions that streamline the collection and preservation of digital evidence in investigations. The Evidence File authenticates the digital evidence by verifying that the digital fingerprint and checksums of small blocks of the collected data matches up with the original data. Our technology can verify the data on-the-fly, such that when a user attempts to view any portion of the evidence, it is instantly verified for authenticity first. By collecting the digital evidence from the investigator at the time of collection and writing that data into our EnCase® Evidence Files, we are able to track the chain-of-custody and significantly reduce the burden on the investigator to authenticate the evidence in court. Our customers can use our EnCase® Logical Evidence File to store individual files or fragments of data and preserve them in the Logical Evidence File. The EnCase® Logical Evidence File is a significant component of our eDiscovery products and services.
The key benefits provided by the EnCase® Evidence File are that it:
| | • | | authenticates that the preserved digital evidence is in fact what was originally collected; |
| | • | | prevents damage to the digital evidence by human error; |
| | • | | documents the chain-of-custody; |
| | • | | eliminates cross-contamination concerns; |
| | • | | provides several different means to connect and collect the digital evidence; and |
| | • | | significantly reduces the need for storage resources. |
Specialized Hard Drive Access
While most software applications interact and work within the operating system, we have designed our software to run “beneath” the operating system in order to prevent interference from the operating system and ensure that data is not tampered with or modified. By working beneath the operating system, our technology accesses the hard drive at the sector level, which is the smallest writeable area on a hard drive. It reads data from the sectors on the hard drive in a raw format and makes the entire hard drive accessible to the user of our software, including all files and obscure areas. Importantly, areas of the hard drive that common users cannot access, such as unallocated space and unformatted space, are also made accessible through our technology. While scanning the hard drive, our technology does not modify the metadata, such as filenames, dates, and times, on live systems, which enables our customers to conduct a complete examination of all the data on the hard drive while assuring that the impact on the overall computing environment is substantially non-invasive. This process is critical in order to preserve the forensic integrity of the preserved data.
EnScript® Technology
We have designed a proprietary advanced programming language called EnScript® that permits the development of applications that run inside the EnCase® environment. EnCase® acts as the operating system for these applications. The EnScript® language is optimized for our software and enables our users to quickly write powerful applications that are highly customized to their needs. The EnScript® language permits not only us to develop these applications, but also any other highly skilled programmer, organization or customer who so desires. The EnScript® program can be compiled so the source code is not available to others, thereby allowing developers and organizations to protect their intellectual property. In addition to our own development efforts, EnScript® programs are commonly developed by persons not affiliated with our organization, and are distributed throughout the different investigative communities and organizations.
-13-
EnCase® Enterprise’s Network Level Capability
Our EnCase® Enterprise software extends the capabilities of our EnCase® Forensic software to enable our customers to scan hundreds or thousands of servers, desktops and laptops over a network to provide scalable enterprise-class performance. Using EnCase® Enterprise, our customers can focus on the computers in question in a massive enterprise-scale investigation or emergency, analyze data or files on a network, including volatile memory, and preserve only the data necessary for the investigation into our EnCase® Logical Evidence File. To accomplish this network-level capability securely, we designed and patented a security architecture that is based on a three-tier structure, which includes a Servlet, an Examiner and a SAFE server.
Designed to work across multiple operating systems, our EnCase® Enterprise serves as an investigative platform, the foundation of an enterprise investigative infrastructure, when fully implemented on a network. Our software is currently compatible with many systems, such as:
| | • | | Operating Systems: Windows 95/98/NT/2000/XP/Vista, Windows 2003 Server, Macintosh, Linux Kernel 2.4 and above, Solaris 8/9 (both 32-bit and 64-bit), AIX, and OS X. |
| | • | | File Systems: FAT12, FAT16, FAT32, New Technology File System (“NTFS”), Macintosh HFS, HFS+, Sun Solaris UFS, Linux EXT2/3, Reiser, BSD FFS, Palm, TiVo Series One and Two, AIX JFS, JFS, Joliet, UDF and ISO 9660. |
Sales
We sell our product offerings directly to customers using our direct sales representatives and our internal sales staff and indirectly through third-party value-added resellers, or VARs. As of December 31, 2007, we employed 135 individuals who were involved in our selling and marketing efforts, and had agreements with over 90 third-party distributors.
The sales model for our EnCase® Enterprise products and services involves a high degree of specialization based on the size and sales focus of the target customer. We primarily utilize direct sales field representatives to sell our EnCase® Enterprise products and related services to large and mid-market corporate customers, which we classify as customers with at least $250 million in revenues that are not assigned to specific sales persons. For our largest corporate customers, individual members of our sales force generally target a named list of accounts and work to develop and cultivate long-term relationships with the companies they contact. For our mid-market corporate customers, our direct sales representatives focus on specific regions and certain named accounts in those regions and work to develop relationships in each region.
Our internal sales staff is responsible for sales of our EnCase® Forensic products and our training services. A large portion of the business for our EnCase® Forensic product is generated from pre-existing relationships, allowing our internal sales personnel to execute at a high level of efficiency. Our internal sales personnel spend the bulk of their time targeting our EnCase® Forensic product to law enforcement agencies and consultancies.
In addition to our corporate sales field representatives and our internal sales force, we have a sales team dedicated to our federal customers, a professional services sales force designed to specifically promote sales of professional services to new and existing customers, and a law firm sales force targeted at selling to law firm customers and strategic partners. These teams typically use a direct sales model to focus on those specific verticals given the unique selling dynamics that exist in each target market.
International sales constituted approximately 23% of our sales in the year ended December 31, 2007. Outside of the United States, excluding the United Kingdom, we typically utilize third-party VARs to sell our products to our international customers. In the United Kingdom, we utilize a direct sales model similar to the system in place in the United States.
-14-
Marketing
We believe that organizations can realize significant benefits by installing our EnCase® Enterprise family of applications across their networks in order to address high-value and pervasive business problems such as eDiscovery, data security and loss prevention to include the protection of intellectual property, personally identifiable information, credit card information, and large-scale network security risk mitigation. These applications all leverage the enabling EnCase® Enterprise platform which offers a base-set of capabilities for conducting enterprise-wide digital investigations and serves as a foundation for organizations to build an investigative infrastructure. Our marketing strategy involves communicating the value of our products for these high-priority issues to a targeted audience, developing a scenario where the adoption of the EnCase® Enterprise applications pulls the base platform with every opportunity, and then communicating the value of leveraging the EnCase® Enterprise platform and additional add-on products to the remainder of the organization for future opportunities.
Our marketing resources are focused on regional and vertical lead-generation campaigns that include interlocking activities of eMarketing, webinars, public relations/media placements, search engine pay-per-click, online advertising and regional events and seminars. Each campaign is focused on matching the appropriate EnCase® Enterprise application with the appropriate target audience, in order to provide value-messaging to those individuals that are seeking specific solutions to their most critical business issues. For example, our US Federal lead marketing strategy is centered on EnCase® Information Assurance, which addresses a vast majority of government network security issues. In the US commercial market, however, our lead marketing strategy is focused around the pervasive and extremely urgent issue of electronic discovery and litigation preparedness. Each campaign leverages “best-practice” resources that are designed to be educational and informative, and that result in a high response and revisit rate for each of our activities and events. This educational approach to our marketing strategy helps to position us as though-leaders and trusted-advisors across each of our target markets and drives viral distribution of our promotional resources.
In addition to our regional and vertical marketing initiatives, we also host the industry’s largest conference dedicated solely to the subject of digital investigations. The Computer and Enterprise Investigations Conference (“CEIC®”) serves as our annual user conference and draws attendees from global law enforcement, government agencies, and corporations. This event also draws industry analysts and experts and provides a valuable forum for users to connect, share information and learn about important topics in the industry. It serves as our single best marketing event and enables us to launch new products in a focused environment while simultaneously driving additional add-on sales to customers who have implemented one or more of the core platform products.
Customers
Our customers include government agencies and global corporations in a wide variety of industries such as financial and insurance services, technology, defense contracting, telecom, pharmaceutical, manufacturing and retail. Our EnCase® Enterprise customer base currently includes more than 100 of the Fortune 500 and many federal and international government agencies, and we have deployed our EnCase® Forensic software to more than 1,000 government and law enforcement agencies and other customers worldwide. Our EnCase® Enterprise customers are primarily in North America, and also extend to Europe, Africa, the Middle East and Asia/Pacific Rim. Sales to customers outside of the United States accounted for 25%, 26% and 23% of our revenues for the years ended December 31, 2005, 2006, and 2007, respectively. The majority of our EnCase® Forensic customers are national and local government agencies, law enforcement agencies and other organizations of the United States government. No customer accounted for more than 10% of our total revenue in 2005, 2006, or 2007.
Research and Development
Our research and development effort is focused on the advancement of our core products and the development of new products, as well as the quality assurance of both core and new products. We conduct research on existing or new computer hardware or software technology to develop solutions for our law
-15-
enforcement, government or corporate markets. We conduct research on file system support, search and analysis algorithms, hardware engineering and design, industry standards, technology integrations and user productivity and performance features. Our research and development efforts are often aimed at creating new standards in our industry and streamlining current processes. Under our customer contracts, we typically obtain the rights to use any improvements to our technology developed or discovered on a particular customer deployment on other customer deployments. Our research and development expense was $4.7 million in 2005, $7.1 million in 2006, and $9.0 million in 2007.
Competition
The market for digital investigation solutions is extremely competitive, highly fragmented and subject to rapidly changing technology, shifting customer needs and frequent introductions of new products and services. We believe that the principal competitive factors in this market include depth and breadth of forensic technology, forensic soundness and acceptance in court, time required to complete an investigation, ability to scale across large networks, expertise of consulting personnel and total solution cost. We expect the intensity of competition to increase in the future as new companies enter our markets, existing competitors develop stronger capabilities, and as we expand into other markets. Many of our current competitors have longer operating histories, greater name recognition, access to larger customer bases and substantially more extensive resources than we have. They may be able to devote greater resources to the development, promotion and sale of their products than we can to ours, which could allow them to respond more quickly than we can to new technologies and changes in customer needs and achieve wider market acceptance. We expect to continue to face competition from new entrants.
We compete directly with a significant number of established companies that have developed or are developing and marketing software and applications that currently compete or will compete with our product and service offerings. While no single company competes with us across all of our markets, we face significant competition in each of the core markets in which we operate. Our current principal competitors include:
| | • | | computer forensic companies that develop forensic tools that compete with our EnCase® Forensic product; |
| | • | | information access/federated search companies that compete with our EnCase® eDiscovery solution and focus on an indexing approach to enterprise-wide information; |
| | • | | managed security services companies which offer managed incident response services which compete against our incident response services; and |
| | • | | consulting companies, such as the Big 4 consulting/accounting firms and Kroll Ontrack, that offer consulting services for traditional digital investigations and eDiscovery in place of implementing a packaged software solution. |
We also compete indirectly with a significant number of established companies or organizations that have developed or are developing and marketing software or services that may diminish the need for our solutions or the budget available to our customers to purchase our solutions. Our current principal indirect competitors include:
| | • | | storage infrastructure companies, such as EMC and Symantec, which advertise some eDiscovery capabilities to complement their core product offerings around content management, e-mail archiving and storage software; |
| | • | | internal IT organizations that develop their own security systems; and |
| | • | | providers of corporate insurance to the Global 2000, whose policies permit and pay for the use of consulting or other services to defend against a specific case but not the purchase of products or software to enhance the overall digital investigative capability for the company. |
-16-
Intellectual Property and Proprietary Rights
Our intellectual property rights are important to our business. We rely on a combination of copyrights, trade secrets, trademarks, and patents, as well as confidentiality procedures and contractual provisions to protect our proprietary technology, processes and intellectual property. We currently have three issued U.S. patents and 21 patent applications pending in the United States, the European Union or under the Patent Cooperation Treaty (often more than one pending application relates to a single invention). We own registered copyrights on various versions of our products and associated instructional documentation. We have registered trademarks or trademarks in the United States and in certain other jurisdictions, including the mark EnCase® in the United States, Japan and the European Union, and in the marks EnCE®, EnScript®, FastBloc®, CEIC® and Guidance Software® in the United States. We have a pending trademark application for the mark Neutrino™ in the United States.
Others may develop products that are similar to our technology. We generally enter into confidentiality and other written agreements with our employees and partners, and through these and other written agreements, we attempt to control access to and distribution of our software, documentation and other proprietary technology and other information. Despite our efforts to protect our proprietary rights, third parties may, in an unauthorized manner, attempt to use, copy or otherwise obtain and market or distribute our intellectual property rights or technology or otherwise develop a product with the same functionality as our software. Policing unauthorized use of our software and intellectual property rights is difficult, and nearly impossible on a worldwide basis. Therefore, we cannot be certain that the steps we have taken or will take in the future will prevent misappropriation of our technology or intellectual property rights, particularly in foreign countries where we do business or where our software is sold or used, where the laws may not protect proprietary rights as fully as do the laws of the United States or where the enforcement of such laws is not common or effective.
Substantial litigation regarding intellectual property rights exists in the software industry. From time to time, in the ordinary course of business, we may be subject to, or initiate, claims relating to our intellectual property rights or those of others, and we expect that third parties may commence legal proceedings or otherwise assert intellectual property claims against us in the future, particularly as we expand the complexity and scope of our business, the number of similar products increases and the functionality of these products further overlap. These claims and any resulting litigation could subject us to significant liability for damages. In addition, even if we prevail, litigation could be time-consuming and expensive to defend and could affect our business materially and adversely. Any claims or litigation from third parties may also limit our ability to use various business processes, software and hardware, other systems, technologies or intellectual property subject to these claims or litigation, unless we enter into license agreements with the third parties. However, these agreements may be unavailable on commercially reasonable terms, or not available at all.
In addition to our proprietary technology, we rely on technology that we license from third parties. In particular, the next version of our products will incorporate document viewer technology that we license from Oracle Corporation (formerly, Stellent, Inc.). Our license agreement with Oracle expires on December 15, 2008, and may be renewed by us for an additional two-year term at a higher price. In addition, Oracle may terminate this license agreement prior to the expiration of its term if we fail to make timely payments or fail to comply with any other material term of the license. (See Risk Factors: “Our success depends in part upon our ability to develop new products and enhance our existing products. Failure to successfully introduce new or enhanced products to the market may adversely affect our business, financial condition and results of operations.”)
Employees
As of December 31, 2007, we employed approximately 350 full-time employees, including approximately 55 in research and development, 135 in selling and marketing and 60 in our Professional Services Division. We have never had any work stoppage and none of our employees are represented by a labor organization or are party to any collective bargaining arrangements. We consider our employee relations to be good.
-17-
Available Information
We file reports with the Securities and Exchange Commission (“SEC”). We make available on our website under “Investors/SEC Filings,” free of charge, our annual reports on Form 10-K, quarterly reports on Form 10-Q, current reports on Form 8-K and amendments to those reports as soon as reasonably practicable after we electronically file such materials with or furnish them to the SEC. Our website address iswww.guidancesoftware.com. Please note, however, that the information contained on the website is not incorporated by reference in, or considered part of, this annual report. You can also read and copy any materials we file with the SEC at the SEC’s Public Reference Room at 100 F Street, NE, Washington, DC 20549. You can obtain additional information about the operation of the Public Reference Room by calling the SEC at 1-800-SEC-0330. In addition, the SEC maintains an Internet site (www.sec.gov) that contains reports, proxy and information statements, and other information regarding issuers that file electronically with the SEC, including us.
You should consider each of the following factors as well as the other information in this Annual Report in evaluating our business and our prospects. The risks and uncertainties described below are not the only ones we face. Additional risks and uncertainties not presently known to us or that we currently consider immaterial may also impair our business operations. If any of the following risks actually occurs, our business and financial results could be harmed. In that case, the trading price of our common stock could decline. You should also refer to the other information set forth in this Annual Report, including our financial statements and the related notes.
Our operating results may fluctuate from period to period and within each period, which makes our operating results difficult to predict and could cause our revenues, expenses and profitability to fall short of expectations during certain periods.
Our operating results may fluctuate from period to period or within certain periods as a result of a number of factors, many of which are outside of our control. You should not rely on our past results as an indication of future performance, as our operating results in the future may fall below expectations, expenses could increase and revenues could decrease. Each of the risks described in this section, as well as other factors, may affect our operating results. For example, our quarterly revenues and operating results may fluctuate as a result of a variety of factors, including, but not limited to, our lengthy sales cycle, the proportion of revenues attributable to license fees versus services and maintenance revenue, changes in the level of fixed operating expenses, demand for our products and services, the introduction of new products and product enhancements or upgrades by us or our competitors, changes in customer budgets and capital expenditure plans, competitive conditions in the industry and general economic conditions. In addition, many customers make major software acquisitions near the end of their fiscal years, which tends to cause our revenues to be higher in the third and fourth calendar quarters, the fiscal year ends of many government agencies and corporations, and lower in the first calendar quarter. In addition, many customers tend to make software acquisitions or purchases near the end of a particular quarter, which tends to make our revenues for a particular period unpredictable for a significant portion of the period in question until software purchase decisions have been made. Since our EnCase® Enterprise product sales are generally large scale license agreements, a short delay in just one of these software sales from one quarter into a subsequent quarter or a loss of one of these potential sales could cause us to deliver results for a quarter that are below projections of securities analysts that follow our results. This could cause our stock price to decline significantly. There can be no assurance that we will be able to successfully address these risks, and we may not be profitable in any future period.
If the corporate market for digital investigation software were not to develop, we would not be able to maintain our growth, and our revenues and results of operations would be adversely affected.
The market for digital investigation software is new and is being developed largely through our efforts. Our growth is dependent upon, among other things, the size and pace at which the market for such software develops.
-18-
If the market for such digital investigation software decreases, remains constant or grows more slowly than we anticipate, we will not be able to maintain our recent rate of growth. Continued growth in the demand for our products is uncertain resulting from, among other things, the fact that:
| | • | | customers and potential customers may decide to use traditional methods of conducting enterprise investigations, such as reliance on in-house professionals or outside consultants to conduct manual investigations; |
| | • | | customers may experience technical difficulty in utilizing digital investigation software or otherwise not achieve their expected return on their investment in such software; and |
| | • | | marketing efforts and publicity related to digital investigation software may not be successful. |
Even if digital investigation software gains wide market acceptance, our software may not adequately address market requirements and may not continue to gain market acceptance. If digital investigation software generally, or our software specifically, do not gain wide market acceptance, we may not be able to maintain our recent rate of growth and our revenues and results of operations would be adversely affected.
The failure of the legal community to adopt our eDiscovery solution could negatively affect future sales of EnCase® Enterprise, which could have a material adverse effect on our results of operations.
We expect to derive a significant amount of sales of EnCase® Enterprise from continuing demand for our EnCase® eDiscovery solution. However, widespread adoption of eDiscovery best practices will require a shift in the way the legal community approaches discovery of electronic documents and other electronically stored data. Currently, most large scale electronic discovery projects are conducted by outsourced service providers that manually retrieve documents from each computer subject to review. These service providers have longstanding and entrenched relationships with the corporations that are subject to large-scale discovery inquiries or security breaches and the large law firms that are typically retained in connection with such discovery projects. Corporations and law firms may continue to prefer to use service providers because of these ongoing established relationships, and because the service providers are widely known and accepted within the legal community and may resist adoption of our EnCase® eDiscovery solution. Moreover, the expense of relying on an outsourced service provider may frequently be covered by the corporation’s insurance policy that is otherwise covering the expense of the litigation, including complying with requests for discovery, while implementation of EnCase® Enterprise and our EnCase® eDiscovery would require a significant unreimbursed capital expenditure by the corporation. The failure of corporations and law firms to adopt our EnCase® eDiscovery solution for eDiscovery could have a material adverse effect on our sales and results of operations.
Courts could reject the use of our products, which would harm our reputation and negatively affect future sales of our products and services.
Our software products and services are often used in connection with legal investigations, civil litigation and criminal prosecutions. The admissibility of results generated by our products as evidence in civil and criminal trials is a key component of our customer value proposition. Evidence and the manner used to collect evidence is regularly the subject of challenges in legal investigations and litigation, and our products or personnel may be the direct or indirect subject of such legal challenges. Persons involved in litigation may, for example, challenge the reliability of our products, the admissibility of evidence generated, discovered or collected using our products, and/or the expertise, credibility or reliability of our personnel. Other unpredictable legal challenges may be brought that could reflect upon the reputation of our products or personnel. To date, courts that have addressed challenges to our products or services have ruled against such challenges. If in the future a court were to find that our products are not reliable or that persons representing us or users of our product are not credible, reliable or lack the expertise necessary to serve as a witness or to authenticate evidence, or that our training and certification process does not adequately prepare individuals to conduct competent digital investigations, this could have a material adverse impact on our revenues and results of operations.
-19-
We are dependent on our management and research and development teams, and the loss of any key member of either of these teams may prevent us from executing our business strategy.
Our future success depends in a large part upon the continued services of our executive officers and other key personnel. In particular, Shawn McCreight, our founder, Chairman and Chief Technology Officer, has been significantly responsible for the development of our products. In addition, Victor Limongelli, our President and Chief Executive Officer, is responsible for a number of our significant strategic initiatives. We are also substantially dependent on the continued services of our existing research and development personnel. We have fewer research and development employees than many competitors of comparable size due to the high degree of expertise required to work with our complex technology and our stringent hiring standards. The loss of one or more of our key employees, and in particular our research and development personnel, could seriously harm our business development, culture and strategic direction. We do not maintain key person life insurance policies on any of our executives. Any key person life insurance policy we maintain now or in the future would not be sufficient to cover the loss of any of our key personnel and any such loss could seriously harm our business and our ability to execute our business strategy.
Changes or reforms in the law or regulatory landscape could diminish the need for our solutions, and could have a negative impact on our business.
One factor that drives demand for our products and services is the legal and regulatory framework in which our customers operate. Laws and regulations are subject to drastic changes and these could either help or hurt the demand for our products. Thus, certain changes in the law and regulatory landscape, such as tort law or legislative reforms that limit the scope and size of electronic discovery requests or the admissibility of evidence generated by such requests, as well as court decisions, could significantly harm our business. Changes in domestic and international privacy laws could also affect the demand and acceptance of our products, and such changes could have a material impact on our revenues.
We face direct and indirect competition from other software companies, as well as other companies that provide training, consulting and certification services in computer forensics, which could limit our growth and market share.
The markets for our software products and services are competitive, highly fragmented and subject to rapidly changing technology, shifting customer needs and frequent introductions of new products and services. We expect the intensity of competition to increase in the future as new companies enter our markets, existing competitors develop stronger capabilities and we expand into other markets. Many of our current competitors have longer operating histories, greater name recognition, access to larger customer bases and substantially more extensive resources than we have. They may be able to devote greater resources to the development, promotion and sale of their products than we can to ours, which could allow them to respond more quickly than we can to new technologies and changes in customer needs and achieve wider market acceptance. Because the barriers to entry into software industry segments are generally low, we expect to continue to face competition from new entrants, particularly as we expand into other segments of the software industry.
Several competing companies provide digital investigation software and applications that directly compete or will compete with our products, or offer solutions our products do not address. In addition, if the market for digital investigation software develops as we anticipate, other companies could enter this market through their own software development or through the acquisition of one of our current competitors. If these companies are more successful in providing similar, better or less expensive digital investigation solutions compared to those that we offer, we could experience a decline in customers and revenue. These companies include computer forensic companies, managed security services companies and consulting companies, such as the “Big 4” consulting/accounting firms, many of which have substantially greater resources and customer bases than we do. If our competitors are more successful than we are at generating professional services engagements, our growth rate or revenues may decline.
We also compete with companies or organizations that have developed or are developing and marketing software and services that diminish the need for our solutions or the budget available to our customers to
20
purchase our solutions. These companies include traditional security companies, data storage infrastructure companies and internal IT organizations that develop their own security systems. We also compete indirectly with providers of corporate insurance to the Global 2000, whose policies in question permit and pay for the use of consulting and other services to defend in litigation but not the purchase of digital investigation software to enhance the overall capabilities for a company.
Computer hackers may damage our products, services and systems, which could cause interruptions in our service and harm to our business, and hackers could gain access to our customers’ personal information which could result in the loss of existing clients, negative publicity and legal liability.
Computer hackers often attempt to access information, including personal information for purposes of identify theft and other criminal activity. In particular, due to the nature of our business, the products and services that we offer and the industry in which we operate, we are more likely to be the target of computer hackers who would like to undermine our ability to offer the products and services that we provide to our customers and possibly retaliate for the results or evidence that our products and services generate.
For example, in December 2005, we became aware of a security breach of our electronic records which contained, among other things, credit card information of approximately 5,000 customers. We promptly notified law enforcement authorities as well as each of the customers whose information may have been compromised. We conducted a forensic examination of the incident and took a number of steps to both remediate the underlying cause and strengthen our internal security system, including enhancing our internal information technology security department and redesigning our network architecture.
In early January 2006, the Federal Trade Commission (the “FTC”) commenced an inquiry into the December 2005 security breach. In September 2006, we executed a consent decree proposed by the FTC that includes no monetary penalties. The consent decree finds that we failed to implement proper security measures to protect consumers’ data, and requires us to provide the FTC with initial and biennial third party assessments of our IT security for a period of 10 years. Additionally, the consent decree requires us to maintain a comprehensive IT security program, retain documentation of such program and provide notice of the consent decree to our executives and employees for a period of 20 years. The FTC formally approved the consent decree on November 15, 2006 and subsequently issued a press release announcing the investigation and its conclusion. In April 2007, we received formal notice and service of the decree from the FTC, effectively ending the inquiry. In October 2007, the Company timely filed the first compliance report required by the consent decree.
Given the incident, any subsequent breach of our security could be especially damaging to our reputation and business and may result in monetary penalties if the FTC were to find that the circumstances that lead to the breach constituted a violation of our obligations under the consent decree.
In addition, from time to time we may be targets of computer hackers who, among other things, create viruses to sabotage or otherwise attack companies’ networks, products and services. For example, there was recently a spread of viruses, or worms, that intentionally deleted anti-virus and firewall software. Our products, networks, websites and systems, may be the target of attacks by hackers. If successful, any of these events could damage our computer systems, force us to incur substantial costs to fix technical problems or result in hackers gaining access to our technical and other proprietary information, which could harm our business and results of operations.
If we fail to develop or maintain an effective system of internal controls, we may not be able to accurately or timely report our financial results or prevent fraud. As a result, current and potential stockholders could lose confidence in our financial reporting, which would harm our business and the trading price of our common stock.
Effective internal controls are necessary for us to provide reliable financial reports and effectively prevent fraud and to operate successfully as a public company. If we cannot provide reliable financial reports or prevent
21
fraud, our reputation and operating results would be harmed. We have in the past discovered, and may in the future discover, areas of our internal controls that need improvement.
In November 2006, in conjunction with the audit of our financial statements for the nine months ended September 30, 2006, our independent registered public accounting firm reported to our audit committee a “material weakness” in our internal controls of financial reporting. More specifically, we did not have adequate controls and procedures to assure proper accounts payable accruals for services rendered and billed but not yet paid, and, as a result, we recorded post-closing adjustments to our books and records and financial statements for the nine months ended September 30, 2006. A material weakness is a significant deficiency, or combination of significant deficiencies, that results in more than a remote likelihood that a material misstatement of annual or interim financial statements will not be prevented or detected
In 2006, we began our remediation efforts and, as of December 31, 2007, we have successfully remediated the weakness over financial reporting identified by our auditors.
We also have not yet implemented a complete disaster recovery plan or business continuity plan for our accounting and related information technology systems. Any disaster could therefore materially impair our ability to maintain timely accounting and reporting.
The complexity of accounting regulations and related interpretations and policies, particularly those related to revenue recognition, could materially affect our financial results for a given period.
Although we use standardized sales agreements designed to meet current revenue recognition criteria under accounting principles generally accepted in the United States, we must often negotiate and revise terms and conditions of these standardized agreements, particularly in multi-product license and services transactions. As our transactions have increased in complexity, particularly with the sale of larger, multi-product licenses, negotiation of mutually acceptable terms and conditions may require us to defer recognition of revenue on such licenses. We believe that we are in compliance with Statement of Position 97-2, “Software Revenue Recognition,” as amended; however, more complex, multi-product license transactions require additional accounting analysis to account for them accurately. The professional technical guidance available regarding the application of software revenue recognition is very conceptual, and silent to specific implementation matters. As a consequence of this, we have been required to make assumptions and judgments, in certain circumstances, regarding the application of software revenue recognition. Incorrect assumptions or judgment decisions as well as changes in, or clarification to accounting interpretations, could lead to unanticipated changes in our revenue accounting practices and may affect the timing of revenue recognition, which could adversely affect our financial results for any given period. If we discover that we have interpreted and applied revenue recognition rules differently than prescribed by accounting principles generally accepted in the United States, we could be required to devote significant management resources, and incur the expense associated with an audit, restatement or other examination of our financial statements.
Our effective tax rate may fluctuate, which could increase our income tax expense and reduce our net income.
In preparing our consolidated financial statements, we estimate our income tax liability in each of the foreign and domestic jurisdictions in which we operate by estimating our actual current tax exposure and assessing temporary differences resulting from differing treatment of items for tax and financial statement purposes. Our judgments, assumptions and estimates relative to the current provision for income tax take into account current tax laws and our interpretation of current tax laws. Although we believe our judgments, assumptions and estimates are reasonable, changes in tax laws or our interpretation of tax laws and the resolution of any future tax audits could significantly impact the amounts provided for income taxes in our consolidated financial statements.
We calculate our current and deferred tax provisions based on estimates and assumptions that could differ from the actual results reflected in income tax returns filed during the subsequent year. Adjustments based on
22
filed returns are generally recorded in the period when the tax returns are filed and the global tax implications are known and could significantly impact the amounts provided for income taxes.
In accordance with accounting principles generally accepted in the United States, we have partially reserved our deferred tax asset to what we currently believe is the net realizable value of that asset. In doing so, we have applied judgment regarding the available positive evidence that our tax asset will be realized. A portion of this evidence is based upon forward looking information regarding our expected future taxable income. If we have over-estimated our future taxable income, or otherwise fail to demonstrate sufficient positive evidence of future taxable earnings, we may be required to increase our valuation allowance and record additional income tax expense. Furthermore, if we have under-estimated our future taxable income, we may conversely reduce our valuation allowance and record additional income tax benefit.
We intend to implement a new enterprise resource program to replace our existing internal software solutions in 2008. If we fail to maintain adequate controls over the implementation and roll-out of this new system, we may be unable to obtain accurate financial information in a timely basis in order to meet our public filing deadlines or have periods in which we are unable to ship product due to system issues. This could affect our results of operations, cash flows and financial position.
We have concluded that an entity-wide enterprise resource program is needed to streamline and migrate our disparate databases into a single, integrated software solution. Our future growth depends upon our ability to efficiently and effectively implement a new IT system to allow us to scale our business model and grow the number, and dollar value, of our transactions without the addition of a significant number of additional personnel. In implementing this new enterprise solution in 2008, we will monitor and test the output of transactional data to ensure the results are consistent with our existing business model. In addition, we will monitor and test standing data files and transactional data that is migrated to the new system to ensure the new system is accurate and free from material defect. If we fail to maintain adequate control of this transition, we may be unable to process the necessary accounting data in a timeframe necessary to meet public filing deadline requirements. Furthermore, if we fail to maintain control over operation data and transactions, we may be unable to process and ship orders in a timely basis, resulting in an unexpected reduction of revenues. As a result, our results of operations, cash flows and financial position could be adversely affected.
Our operating results and business would be seriously impaired if our revenues from our EnCase® Enterprise product were to decline.
Historically, we have derived substantially all of our license revenues from sales of our EnCase® Forensic and EnCase® Enterprise product offerings. Although we have introduced new software modules, we expect that our EnCase® Enterprise product offering will account for the largest portion of our software product for the foreseeable future. Although we have no reason to believe that sales of EnCase® Forensic will decline in future periods, we believe that the degree of penetration for our EnCase® Forensic product in the law enforcement market makes it unlikely that revenue from sales of EnCase® Forensic will contribute dramatically to future revenue growth. For this reason, we are dependent on increased sales of EnCase® Enterprise and related products to drive future growth.
As a result, if for any reason revenue from our EnCase® Enterprise product offerings declines or does not increase as rapidly as we anticipate, our operating results and our prospects for growth will be significantly impaired. Further, if these products fail to meet the needs of our existing and target customers, or if they do not compare favorably in price and performance to competing products, our business will be adversely affected.
We may be limited in our ability to utilize indirect sales channels, such as value-added resellers, corporate resellers, professional services firms and other third-party distributors for the sale and distribution of our products, which may limit our ability to expand our customer base and our revenues.
We may be limited in our ability to market and distribute our products through value-added resellers, corporate resellers, professional services firms and other third-party distributors, which we collectively refer to as
23
third-party resellers, due to various factors. Due to the complex nature of our products, sales professionals generally require a significant amount of time and effort to become sufficiently familiar with our products in order to be able to market them effectively, which makes our products unattractive to third-party resellers. In addition, our competitors include professional services organizations, such as accounting, consulting and law firms, that would otherwise serve as a natural distribution channel for our products and related services.
Moreover, there is significant competition in our industry for qualified third-party resellers. Even if we were to succeed in attracting qualified and capable third-party resellers, we would likely have relatively short-term contracts and no minimum purchase commitments with any existing and future third-party resellers. In addition, agreements with such third-party resellers are generally renewable annually, not exclusive and may be terminated by either party within 30 days after the initial six-month period of the agreement, and with 30 days notice after the initial one-year period. If we are not able to recruit new qualified third-party resellers, our sales growth may be constrained and our results of operations would suffer.
Our intellectual property rights are valuable, and if we are unable to protect our proprietary technologies and defend infringement claims, we could lose our competitive advantage and our business could be adversely affected.
Our success depends in part on our ability to protect our proprietary products and services and to defend against infringement claims. If we are unable to do so, our business and financial results may be adversely affected. To protect our proprietary technology, we rely upon a combination of copyright, patent, trademark and trade secret law, confidentiality restrictions in contracts with employees, customers and other third parties, software security measures, and registered copyrights, trademarks and patents. If we fail to protect our intellectual property rights adequately, our competitors may gain access to our technology, and our business may be harmed. Any of our patents, trademarks, copyrights or other intellectual property rights may be challenged by others or invalidated through administrative process or litigation proceedings. In addition, we may be unable to obtain patent, copyright or trademark protection on products that we spend significant time and expense to develop in the future. Despite our efforts to protect our proprietary technology, unauthorized persons may be able to copy, reverse engineer or otherwise use some of our proprietary technology. Furthermore, existing patent and copyright laws may afford only limited protection, and the laws of certain countries in which we operate do not protect proprietary technology as well as established law in the United States. For these reasons, we may have difficulty protecting our proprietary technology against unauthorized copying or use. If any of these events happen, there could be a material adverse effect on the value of our proprietary technology and on our business and financial results. In addition, litigation may be necessary to protect our proprietary technology. This type of litigation is often costly and time-consuming, with no assurance of success.
Claims that we misuse the intellectual property of others could subject us to significant legal liability and disrupt our business, which could have a material adverse effect on our financial condition and results of operations.
Because of the nature of our business, we may become subject to material claims of infringement by competitors and other third parties with respect to our current or future software applications, trademarks or other proprietary rights. The legal framework for software patents is rapidly evolving and we expect that software developers will increasingly be subject to infringement claims as the number of software applications and competitors in our industry segment grows. In certain circumstances, the owners of proprietary software could make copyright and/or patent infringement claims against us in connection with such activity. Any such claims, whether meritorious or not, could be time consuming and difficult to defend against, result in costly litigation, cause shipment delays or require us to enter into royalty or licensing agreements with third parties, which may not be available on terms that we deem acceptable, if at all. Any of these claims could disrupt our business, make it difficult to add or retain important features in our products and have a material adverse effect on our financial condition and results of operations.
24
If we are unable to continue to obtain government licenses, approvals or authorizations regarding the export of our products abroad, or if current or future export laws limit or otherwise restrict our business, we could be prohibited from shipping our products to certain countries, which could negatively impact our business, financial condition and results of operations.
We must comply with United States laws regulating the export of our products to other countries. Our products contain encryption and decryption technologies that require us to obtain certain licenses from the United States government in order to export certain of our products abroad. In addition, we are required to obtain licenses from foreign governments in order to import our products into these countries. We cannot assure you that we will be successful in obtaining such licenses, approvals and other authorizations required from applicable governmental authorities to export our products. The export regimes and the governing policies applicable to our business are subject to change, and we cannot assure you that such export approvals or authorizations will be available to us or for our products in the future. Our failure to receive any required export license, approval or authorization would hinder our ability to sell our products and could negatively impact our business, financial condition and results of operations.
We have grown rapidly, and if we are not able to effectively manage and support our growth or retain and attract highly skilled employees, our business strategy might not succeed.
In the past we have grown rapidly and we will need to continue to grow in all areas of our operations to execute our business strategy. Managing and sustaining our growth will place significant demands on management as well as on our administrative, operational, technical and financial systems and controls and other resources. We may not be able to expand our product offerings, our customer base and markets, or implement other features of our business strategy at the rate or to the extent presently planned. In addition, our traditionally high level of customer service may suffer as we grow, which could cause our software sales to suffer. If we are unable to successfully manage or support our future growth, we may not be able to maximize revenues or profitability.
In addition, in order to be able to effectively execute our rapid growth plan, we must attract and retain highly qualified personnel. We will need to hire additional personnel in virtually all operational areas, including selling and marketing, research and development, professional services, training, customer service and administration. Competition in our industry for experienced and qualified personnel in these areas is extremely intense, especially for software developers with high levels of experience in designing and developing software products and sophisticated technical sales people experienced in selling our complex type of software products and selling into government agencies. In order to expand sales of EnCase® Enterprise, we may need to continue to hire highly qualified commissioned sales personnel to directly target potential EnCase® Enterprise customers. These new commissioned sales personnel require several quarters of training and experience before being able to effectively market EnCase® Enterprise, and, as a result of these hires, our sales and marketing expense will increase at a greater rate than our revenue, at least in the short term. The expense of hiring and training these commissioned sales personnel may never generate a corresponding increase in revenue. We may not be successful in attracting and retaining the necessary qualified personnel that our growth plan requires. We have from time to time in the past experienced, and we expect to continue to experience in the future, difficulty in hiring and retaining highly skilled employees with appropriate qualifications. Many of the companies with which we compete for experienced personnel have greater resources than we have. If we fail to attract new personnel or retain and motivate our current personnel, our business and future growth prospects could be severely harmed.
We also believe that a critical contribution to our successful rapid growth has been our corporate culture which fosters innovation, teamwork and excellence. As our organization grows and we are required to implement more complex organizational structures and institutional programs, we may find it difficult to maintain the beneficial aspects of our corporate culture, which could negatively affect our ability to attract and retain qualified and experienced personnel and therefore our future success in continuing to maintain our rapid growth.
25
Our failure to offer high quality training and to attract and retain high quality training personnel could have a material adverse effect on our sales of software applications and therefore have a negative impact on our business, financial condition and results of operations.
Our services offerings include training programs designed to instruct current and potential customers on the proper process of conducting a competent digital investigation and the most efficient operation of our products. To a significant degree, the pool of potential users of our products is created by the training services we and our partners provide. A high level of training is critical for the successful marketing, sale and implementation of our software products. Finding qualified third-party providers of training services for our complex software products is difficult and time-consuming, and to date we have approved only five such providers. If we or our partners do not effectively train our customers to properly use our software applications, or succeed in helping our customers quickly resolve post-deployment issues, it would adversely affect our ability to sell additional software products to existing customers in the future and could harm our reputation with potential customers of software products. As a result, our failure to attract and maintain high quality training representatives and personnel would have a material adverse effect on our sales of software applications and therefore negatively impact our business, financial condition and results of operations.
Our software applications may be perceived as, or determined by the courts to be, a violation of privacy rights. Any such perception or determination could adversely affect our revenues and results of operations.
Because of the nature of digital investigations, our potential customers and purchasers of our products or the public in general may perceive that use of our products for these investigations result in violations of individual privacy rights. In addition, certain courts, legislative and regulatory authorities could determine that the use of our software solutions or similar products are a violation of privacy rights, particularly in jurisdictions outside of the United States. Any such determination or perception by potential customers, the general public, government entities or the judicial system could harm our reputation and adversely affect the sales of our products and our results of operations.
Our business could be adversely affected based on the fact that, prior to June 2007, we entered into United States General Services Administration (GSA) contracts as a procurement vehicle for federal government agencies that purchase certain of our products and services. These GSA contracts required that we provide our best corporate prices to the government agencies and give the government agencies the right to conduct administrative audits of our performance under such GSA contracts. If we have an unfavorable administrative audit we may be required to reimburse the United States government for costs that they have expended under such contracts.
Prior to June 2007, we have entered into GSA contracts in connection with the sale of certain of our products and services. These GSA contracts were intended to facilitate efficient sales to government agencies and provide the government agencies with “most-favored nation” type pricing for the respective products and services on a comparable basis with sales to other third parties. Since June 2007, we no longer contract directly with the GSA and operate under a Government Reseller Agreement with immixTechnology, to sell our products via the immixTechnology General Services Administration (GSA) contract to government customers.
The GSA and government agencies which purchase our products and services pursuant to GSA contracts are permitted to conduct administrative audits of us as part of their routine audits and investigations of government contracts. For example, the GSA conducted an audit of Guidance for 2005 and issued to us an administrative report card with a rating of “successful.” As part of the audit process, the GSA or a government agency may review our performance under the contract, cost structure, including the cost of comparable products and services to third parties, and compliance with applicable laws, regulations and standards. The GSA or a government agency may also review the adequacy of, and our compliance with, our internal controls systems and policies, including our purchasing, property, estimating, compensation and management information systems. If any of our pricing is found to be improperly discounted to a specific contract, the revenue received by us may have to be
26
refunded and an additional penalty may have to be paid by us. For the years ended December 31, 2005 and 2006, our billings from federal government contracts procured through the GSA were 22% and 17% of total billings, respectively; such billings in 2007 were not significant.
Although our risk has been mitigated through our reseller arrangement, we remain subject to audit for periods prior to June 2007. A future audit with unfavorable results could materially affect our competitive position and result in a material adjustment to our financial results. In addition, if a GSA or government agency audit uncovers improper or illegal activities on our part, we may be subject to civil and criminal penalties and administrative sanctions, including, but not limited to, termination of existing contracts, forfeiture or disgorgement of profits, suspension of future payments owed, fines and suspension from doing future business with the federal government through the GSA. Furthermore, our reputation could suffer serious or irreparable harm if allegations of impropriety were levied against us. If we were suspended from contracting through the GSA, our reputation or relationships with federal government agencies were impaired, or the GSA or these agencies otherwise ceased doing business with us or significantly decreased the amount of business they do with us, our revenues and prospects would be materially harmed.
Our business depends, in part, on sales to governments and governmental entities and significant changes in the contracting or fiscal policies of governments and governmental entities could have a material adverse effect on our business.
We derive a portion of our revenues from contracts with federal, state, local and foreign governments and government agencies, and we believe that the success and growth of our business will continue to depend on our successful procurement of government contracts. Accordingly, changes in government contracting policies or government budgetary constraints could directly affect our business, financial condition and results of operations. Among the factors that could adversely affect our business, financial condition or results of operations are:
| | • | | changes in fiscal policies or decreases in available government funding; |
| | • | | changes in government programs or applicable requirements; |
| | • | | the adoption of new laws or regulations or changes to existing laws or regulations; |
| | • | | changes in political or social attitudes with respect to security issues, computer crimes, discovery of computer files and digital investigations; |
| | • | | potential delays or changes in the government appropriations process; and |
| | • | | delays in the payment of our invoices by government payment offices. |
These and other factors could cause governments and governmental agencies to refrain from purchasing the products and services that we offer in the future, the result of which could have an adverse effect on our business, financial condition and results of operations. In addition, many of our government customers are subject to stringent budgetary constraints. The award of additional contracts from government agencies could be adversely affected by spending reductions or budget cutbacks at government agencies that currently use or are likely to utilize our products and services.
Because we offer our EnScript® programming language for customization of and the creation of add-ons for EnCase®, customers or third-party programmers may be able to develop products that compete with our products or reduce the marketability or value of our products.
We have developed many of our major products, including EnCase® eDiscovery and EnCase® Automated Incident Response Solution, to function as applications running on the EnCase® Enterprise platform. We created these applications using the EnScript® programming language. In order to enhance the attractiveness of EnCase® to potential customers and position EnCase® as a standard software for digital investigations, we have made available without charge the EnScript® programming language, which permits users of EnCase® to develop
27
customized add-on features for their own or others’ use, and we have trained our customers on how to write add-on programs using the EnScript® programming language, which is similar to Java or C Sharp. As part of this strategy, we have encouraged the development of an active community of EnScript® programmers similar to those which have emerged for other software products. While we believe widespread use of our EnScript® programming language will ultimately create demand for our products, customers in the past have developed, and may in the future develop, software for use with EnCase® using the EnScript® programming language, rather than purchasing certain of our product offerings. Losses of sales to potential customers could have a material adverse impact on our revenues and results of operations.
Our success depends in part upon our ability to develop new products and enhance our existing products. Failure to successfully introduce new or enhanced products to the market may adversely affect our business, financial condition and results of operations.
Our future success depends in part on our ability to develop enhancements to our existing products and to introduce new products that keep pace with rapid technological developments and changes in customers’ needs. Although our products are designed to operate on a variety of network hardware and software platforms, we must continue to modify and enhance our products to keep pace with changes in network platforms, operating systems, software technology and changing customer demands. We may not be successful in developing and documenting these modifications and enhancements or in bringing them to market in a timely manner. Any failure of our products to operate effectively with future network platforms and technologies could reduce the demand for our products and result in customer dissatisfaction. In addition, the next version of our products will incorporate document viewer technology that we license from Oracle Corporation. Our license agreement with Oracle expires on December 15, 2008, and may be renewed by us for an additional two-year period at a higher price. In addition, Oracle may terminate this license agreement prior to the expiration of its term if we fail to make timely payments or fail to comply with any other material term of the license agreement. We may be unable to replace this technology if Oracle terminates this license agreement or it expires, or if the Oracle technology becomes obsolete or incompatible with our products.
Furthermore, any new products that we develop may not be released in a timely manner and may not achieve the market acceptance necessary to generate significant sales revenues. As a result, we may expend significant time and expense towards research and development for new or enhanced products, which may not gain market acceptance or generate sufficient sales to offset the costs of research and development. If we are unable to successfully develop new products or enhance and improve our existing products, or if we fail to position or price our products to meet market demand, our business, financial condition and results of operations will be adversely affected.
Errors in our products could adversely affect our reputation, result in significant costs to us, impair our ability to market our products and expose us to legal liability, any of which may adversely affect our operating results.
Products as complex as ours can contain undetected errors or failures. Despite extensive testing by us and by our customers, we have in the past discovered errors in our software applications and will likely continue to do so in the future. As a result of past discovered errors, we experienced delays and lost revenues while we corrected the problems in those software applications. In addition, customers in the past have brought to our attention “bugs” in our software exposed by the customers’ unique operating environments. Although we have been able to fix these software bugs in the past, we may not always be able to do so in the future. In addition, our products may also be subject to intentional attacks by viruses that seek to take advantage of these bugs, errors or other weaknesses. Any of these events may result in the loss of, or delay in, market acceptance of our products and services, which would seriously harm our sales, financial condition and results of operations.
Furthermore, we believe that our reputation and name recognition are critical factors in our ability to compete and generate additional sales of our products and services. Promotion and enhancement of our brand
28
name will depend largely on our success in continuing to provide effective software applications and services. The occurrence of errors in our software applications or the detection of bugs by our customers may damage our reputation in the market as well as our relationships with existing customers, which may result in our inability to attract or retain customers.
In addition, because our products are used in security and forensic functions that are often critical to our customers, the licensing and support of our products makes us potentially subject to product liability claims. Any product liability insurance we carry may not be sufficient to cover our losses resulting from any such product liability claims. The successful assertion of one or more large product liability claims against us could have a material adverse effect on our financial condition.
Incorrect or improper use of our products, our failure to properly train customers on how to utilize our software products or our failure to properly provide consulting and implementation services could result in negative publicity and legal liability.
Our products are complex and are deployed in a wide variety of network environments. The proper use of our software requires extensive training by the end user and, if our software products are not used correctly or as intended, inaccurate results may be produced. Our customers or our professional services personnel may incorrectly implement or use our products. Our products may also be intentionally misused or abused by customers or non-customer third parties who obtain access and use of our products. Because our customers rely on our product and service offerings to manage a wide range of sensitive investigations and security functions, the incorrect or improper use of our products, our failure to properly train customers on how to efficiently and effectively use our products or our failure to properly provide consulting and implementation services to our customers may result in negative publicity or legal claims against us.
We cannot predict our future capital needs and we may be unable to obtain additional financing to develop new products, enhance existing products, offer additional services or fund strategic acquisitions, the failure of which could have a material adverse effect on our business, financial condition and results of operations.
We may need to raise additional funds in the future in order to develop new products, enhance existing products, offer additional services or make strategic acquisitions of complementary businesses, technologies, products or services. Any required additional financing may not be available on terms acceptable to us, or at all. If we raise additional funds by issuing equity securities, you will experience dilution of your ownership interest, which could be significant, and the newly-issued securities may have rights senior to those of the holders of our common stock. If we raise additional funds by obtaining loans from third parties, the terms of those financing arrangements may include negative covenants or other restrictions on our business that could impair our operational and financial flexibility and would also require us to incur additional interest expense. If additional financing is not available when required or is not available on acceptable terms, we may be unable to successfully develop or enhance our software products and services through internal research and development or acquisitions in order to take advantage of business opportunities or respond to competitive pressures, which could negatively impact our software products and services offerings and sales revenues, the failure of which could have a material adverse effect on our business, financial condition and results of operations.
Acquisitions that we may undertake in the future involve risks that could adversely affect our business, financial condition and results of operations.
We may pursue strategic acquisitions of businesses, technologies, products or services that we believe complement or expand our existing business, products and services. Acquisitions involve numerous risks, including, but not limited to, the following:
| | • | | diversion of management’s attention during the acquisition and integration process; |
29
| | • | | costs, delays and difficulties of integrating the acquired company’s operations, technologies and personnel into our existing operations and organization; |
| | • | | adverse impact on earnings as a result of amortizing the acquired company’s intangible assets or impairment charges related to write-downs of goodwill related to any acquisition; |
| | • | | issuance of equity securities to pay for acquisitions, which may be dilutive to existing stockholders; |
| | • | | potential loss of customers or key employees of acquired companies; |
| | • | | impact on our financial condition due to the timing of the acquisition or our failure to meet operating or synergy expectations for any acquired business; and |
| | • | | assumption of unknown liabilities of the acquired company. |
To date, we have not completed an acquisition. Any acquisitions of businesses, technologies, products or services that we may undertake in the future may not generate sufficient revenues or cost-saving synergies necessary to offset the associated costs of the acquisitions or may result in other material adverse effects.
Our international sales and operations are subject to factors that could have an adverse effect on our business, financial condition and results of operations.
We have significant sales and services operations outside the United States, and derive a substantial portion of our revenues from these operations. We also plan to expand our international operations in the future. For the years ended December 31, 2006 and 2007, we derived approximately 26% and 23%, respectively, of our revenues from sales of products and services outside the United States.
Our international operations are subject to risks related to the differing legal, political, social and regulatory requirements and economic conditions of many countries, which risks include, but are not limited to:
| | • | | difficulties in staffing and managing our international operations; |
| | • | | the fact that foreign countries may impose additional withholding taxes or otherwise tax our foreign income, impose tariffs or adopt other restrictions on foreign trade or investment, including currency exchange controls; |
| | • | | the general economic conditions in the countries in which we operate could have an adverse effect on our earnings from operations in those countries; |
| | • | | the imposition of, or unexpected adverse changes in, foreign laws or regulatory requirements, including those pertaining to export duties and quotas, trade and employment restrictions; |
| | • | | longer payment cycles for sales in foreign countries and difficulties in collecting accounts receivable; |
| | • | | U.S. and foreign import and export laws; |
| | • | | fluctuations in currency exchange rates; |
| | • | | compliance with multiple, conflicting and changing governmental laws and regulations, including tax, privacy and data protection laws and regulations; |
| | • | | costs and delays associated with developing software, documentation and training materials in multiple languages; and |
| | • | | political unrest, war or acts of terrorism occurring in the foreign countries in which we currently operate or intend to operate in the future. |
We may not continue to succeed in developing and implementing policies and strategies that will be effective in each location where we currently do business or intend to do business in the future. Furthermore, the occurrence of any of the foregoing factors may have a material adverse effect on our business, financial condition and results of operations.
30
Insiders control a majority of our outstanding stock, and this may delay or prevent a change of control of our company or adversely affect our stock price.
As of March 5, 2008, our executive officers, directors and affiliated entities together beneficially own approximately 56.5% of our common stock outstanding, including 45.3% of our outstanding common stock held by our founder, Shawn McCreight, and his wife. As a result, these stockholders will have control over matters that require approval by our stockholders, including the election of directors and approval of significant corporate transactions. Corporate actions favored by these stockholders might be taken even if other stockholders oppose them. This concentration of ownership might also have the effect of delaying or preventing a change of control that other stockholders may view as beneficial.
Our charter documents and Delaware law may deter potential acquirers of our business and may thus depress our stock price.
Our amended and restated certificate of incorporation and our bylaws contain provisions that could delay or prevent a change of control of our company that our stockholders might consider favorable. In addition, we are governed by the provisions of Section 203 of the Delaware General Corporation Law, which may discourage, delay or prevent certain business combinations with stockholders owning 15% or more of our outstanding voting stock. These and other provisions in our charter documents may make it more difficult for stockholders or potential acquirers to initiate actions that are opposed by the then-current board of directors, including delaying or impeding a merger, tender offer, or proxy contest or other change of control transaction involving our company. Any delay or prevention of a change of control transaction could cause stockholders to lose a substantial premium over the then current market price of their shares.
The trading price of our common stock is volatile.
The trading prices of the securities of technology companies have historically been highly volatile. Accordingly, the trading price of our common stock has been subject to wide fluctuations since our initial public offering in December 2006. Factors that may affect the trading price of our common stock include:
| | • | | variations in our financial results; |
| | • | | announcements of technological innovations, new solutions, strategic alliances or significant agreements by us or by our competitors; |
| | • | | recruitment or departure of key personnel; |
| | • | | changes in the estimates of our financial results or changes in the recommendations of any securities analysts that elect to follow our common stock; and |
| | • | | market conditions in our industry, the industries of our customers and the economy as a whole. |
In addition, if the market for software or other technology stocks or the stock market in general experiences continued or greater loss of investor confidence, the trading price of our common stock could decline for reasons unrelated to our business or financial results. The trading price of our common stock might also decline in reaction to events that affect other companies in our industry even if these events do not directly affect us.
Future sales of shares by existing stockholders could cause our stock price to decline.
All of our outstanding shares are eligible for sale in the public market, subject in certain cases to volume limitations under Rule 144 of the Securities Act of 1933, as amended. Also, shares subject to outstanding options and rights under our First Amended and Restated 2004 Equity Incentive Plan are eligible for sale in the public market to the extent permitted by the provisions of various vesting agreements and Rules 144 and 701 under the Securities Act. If these shares are sold, or if it is perceived that they will be sold in the public market, the trading price of our common stock could decline.
31
In addition, our founder, Shawn McCreight, and his wife, continue to hold a substantial number of shares of our common stock. Sales by Mr. McCreight or his wife of a substantial number of shares, or the expectation that such sales may occur, could significantly reduce the market price of our common stock.
If our prior S Corporation election was not properly made and maintained, we would be liable for federal and certain state income taxes
In October 1998, we elected to be treated for federal income tax purposes as an “S Corporation” under Subchapter S of the Internal Revenue Code. In addition, we elected or were otherwise treated as an S Corporation for certain state tax purposes. As an S Corporation, our earnings were included in the income of our stockholders for federal and certain state income tax purposes. We filed an election to revoke our S Corporation status on December 11, 2006. If your S Corporation election was not properly made and maintained prior to its revocation, we would be liable for federal and certain state income taxes during prior open periods, together with interest thereon and, possibly, penalties. Such taxes and penalties may be material to our operating results.
| Item 1B. | Unresolved Staff Comments |
None.
Our corporate headquarters is located in Pasadena, California, where we lease approximately 85,000 square feet in two locations. We also lease an additional 65,000 square feet at facilities in Houston, Texas, Atlanta, Georgia and New York, New York and near San Francisco, California, Washington, D.C., Chicago, Illinois and London, England. We also maintain small regional facilities in Brazil, Japan and Singapore. Our leases expire at various points through 2015. We believe that our current facilities are suitable and adequate to meet our current needs, and that suitable additional or substitute space will be available as needed to accommodate expansion of our operations.
From time to time, we may become involved in various lawsuits and legal proceedings that arise in the ordinary course of business. Litigation is subject to inherent uncertainties, and an adverse result in these or other matters may arise from time to time that may harm our business. We are not currently aware of any such legal proceedings or claims that we believe will have, individually or in the aggregate, a material adverse effect on our business, financial condition or operating results.
In early January 2006, the Federal Trade Commission (the “FTC”) commenced an inquiry into the December 2005 security breach discussed in “Risk Factors—Computer hackers may damage our products, services and systems, which could cause interruptions in our service and harm to our business, and hackers could gain access to our customers’ personal information which could result in the loss of existing clients, negative publicity and legal liability.” On September 20, 2006, we executed a consent decree proposed by the FTC that includes no monetary penalties. The consent decree finds that we failed to implement proper security measures to protect consumers’ data, and requires us to provide the FTC with initial and biennial third-party assessments of our IT security for a period of 10 years. Additionally, the consent decree requires us to maintain a comprehensive IT security program, retain documentation of such program and provide notice of the consent decree to our executives and employees for a period of 20 years. On April 9, 2007, the Company received formal notice and service of the decree, which effectively ended the inquiry. On October 9, 2007, the Company timely filed the first compliance report required by the consent decree.
| Item 4. | Submission of Matters to a Vote of Security Holders |
None.
32
PART II
| Item 5. | Market for Registrant’s Common Equity, Related Stockholder Matters and Issuer Purchases of Equity Securities |
Our common stock has been traded on the NASDAQ Global Market under the symbol “GUID” since December 13, 2006. Prior to that time, there was no public market for our common stock. The following table sets forth the range of high and low sales prices on the NASDAQ Global Market of the common stock for the periods indicated, as reported by NASDAQ.
| | | | | | |
| | | Common Stock Price |
| | | High | | Low |
Fiscal Year 2006 | | | | | | |
Fourth Quarter 2006 (From December 13, 2006) | | $ | 17.90 | | $ | 12.75 |
Fiscal Year 2007 | | | | | | |
First Quarter | | | 16.25 | | | 11.25 |
Second Quarter | | | 14.59 | | | 11.76 |
Third Quarter | | | 14.20 | | | 10.92 |
Fourth Quarter | | | 14.89 | | | 11.78 |
As of March 5, 2008, there were 18 holders of record of our common stock. On March 5, 2008, the last sale price reported on the NASDAQ Global Market for our common stock was $10.34 per share.
In October 1998, we elected to be treated for federal income tax purposes as an “S Corporation” under Subchapter S of the Internal Revenue Code. In addition, we elected or were otherwise treated as an S Corporation for certain state tax purposes. We filed an election to revoke our S Corporation status on December 31, 2006. As an S Corporation, we historically paid dividends to our stockholders. We anticipate that any future earnings will be retained to finance continuing development of our business. Accordingly, we do not anticipate paying dividends on our common stock in the foreseeable future. Any determination to pay dividends in the future will be at the discretion of our board of directors and will depend upon our results of operation, financial condition and other factors as the board of directors, in its discretion, deems relevant.
Equity Compensation Plan Information
Information about our equity compensation plans at December 31, 2007 that were either approved or not approved by our stockholders was as follows:
| | | | | | | |
Plan Category | | Number of
Shares to be
Issued Upon
Exercise of
Outstanding
Options | | Weighted
Average
Exercise
Price of
Outstanding
Options | | Number of
Shares
Remaining
Available
for Future
Issuance |
Equity compensation plans approved by our stockholders (a) | | 4,227,000 | | $ | 8.83 | | — |
Equity compensation plans not approved by our stockholders (b) | | 300,000 | | $ | 12.80 | | — |
| (a) | Includes our First Amended and Restated 2004 Equity Incentive Plan (“the Plan”). |
| (b) | 300,000 shares of a December 2007 stock option grant were issued in excess of the available option pool. In January 2008, that portion of the award was cancelled and, contemporaneously, the 300,000 options were granted under the Plan. |
33
Performance Measurement Comparison
The following graph illustrates a comparison of the total cumulative stockholder return on our common stock since December 13, 2006, the date of our initial public offering, to two indices: (i) the NASDAQ Composite Index (symbol: IXIC) and (ii) the NASDAQ Computer Index (symbol: IXCO). The graph assumes an initial investment of $100 on December 13, 2006 and that all dividends have been reinvested. No cash dividends have been declared on our common stock since the date of our initial public offering. The quotes were obtained fromwww.bigcharts.com. The comparisons in the graph are required by the SEC and are not intended to forecast or be indicative of the possible future performance of our common stock.
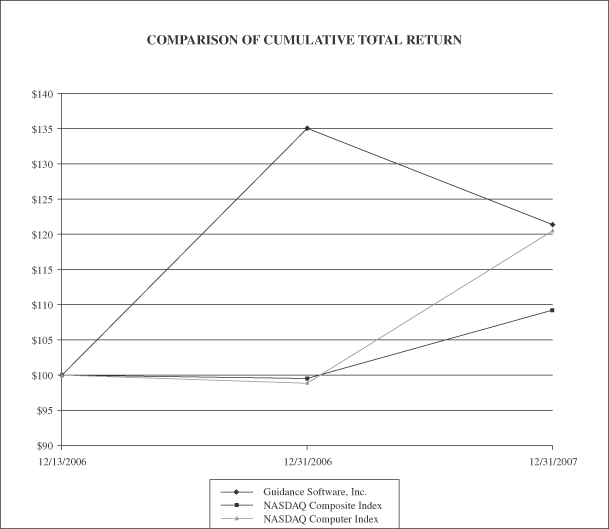
34
| Item 6. | Selected Consolidated Financial Data |
The following selected consolidated financial data should be read together with “Management’s Discussion and Analysis of Financial Condition and Results of Operations” and our consolidated financial statements and related notes included elsewhere in this Annual Report. The selected consolidated balance sheet data as of December 31, 2006 and 2007 and the selected consolidated statement of operations data for each of the three years in the period ended December 31, 2007, have been derived from our audited consolidated financial statements, which are included elsewhere in this Annual Report. The selected consolidated balance sheet data as of December 31, 2003, 2004 and 2005 and selected consolidated statement of operations data for the years ended December 31, 2003 and 2004 have been derived from our audited consolidated financial statements not included in this Annual Report. Historical results are not necessarily indicative of the results to be expected in the future.
| | | | | | | | | | | | | | | | | | | | |
| | | Year Ended December 31, | |
| | | 2003 | | | 2004 | | | 2005 | | | 2006 | | | 2007 | |
| | | (in thousands, except per share data) | |
Consolidated Statements of Operations Data: | | | | | | | | | | | | | | | | | | | | |
Revenues: | | | | | | | | | | | | | | | | | | | | |
Product revenue | | $ | 9,752 | | | $ | 15,812 | | | $ | 23,138 | | | $ | 32,565 | | | $ | 44,314 | |
Services and maintenance revenue | | | 7,949 | | | | 11,792 | | | | 16,367 | | | | 23,300 | | | | 34,566 | |
| | | | | | | | | | | | | | | | | | | | |
Total revenues | | | 17,701 | | | | 27,604 | | | | 39,505 | | | | 55,865 | | | | 78,880 | |
| | | | | | | | | | | | | | | | | | | | |
Cost of revenues: | | | | | | | | | | | | | | | | | | | | |
Cost of product revenue | | | 1,621 | | | | 1,685 | | | | 2,202 | | | | 2,429 | | | | 2,754 | |
Cost of services and maintenance revenue | | | 4,901 | | | | 7,930 | | | | 9,146 | | | | 13,639 | | | | 19,280 | |
| | | | | | | | | | | | | | | | | | | | |
Total cost of revenues | | | 6,522 | | | | 9,615 | | | | 11,348 | | | | 16,068 | | | | 22,034 | |
| | | | | | | | | | | | | | | | | | | | |
Gross profit | | | 11,179 | | | | 17,989 | | | | 28,157 | | | | 39,797 | | | | 56,846 | |
| | | | | | | | | | | | | | | | | | | | |
Operating expenses: | | | | | | | | | | | | | | | | | | | | |
Selling and marketing | | | 6,131 | | | | 10,461 | | | | 15,691 | | | | 26,238 | | | | 32,964 | |
Research and development | | | 1,881 | | | | 3,295 | | | | 4,680 | | | | 7,113 | | | | 9,067 | |
General and administrative | | | 4,185 | | | | 3,894 | | | | 4,923 | | | | 7,840 | | | | 14,637 | |
Depreciation and amortization | | | 613 | | | | 1,158 | | | | 1,357 | | | | 1,823 | | | | 3,453 | |
| | | | | | | | | | | | | | | | | | | | |
Total operating expenses | | | 12,810 | | | | 18,808 | | | | 26,651 | | | | 43,014 | | | | 60,121 | |
| | | | | | | | | | | | | | | | | | | | |
Operating (loss) income | | | (1,631 | ) | | | (819 | ) | | | 1,506 | | | | (3,217 | ) | | | (3,275 | ) |
Other income and expense: | | | | | | | | | | | | | | | | | | | | |
Interest income | | | 1 | | | | 3 | | | | 54 | | | | 105 | | | | 1,463 | |
Interest expense | | | (72 | ) | | | (112 | ) | | | (81 | ) | | | (91 | ) | | | (107 | ) |
Other income, net | | | 12 | | | | 146 | | | | 150 | | | | 173 | | | | 130 | |
| | | | | | | | | | | | | | | | | | | | |
(Loss) income before income taxes | | | (1,690 | ) | | | (782 | ) | | | 1,629 | | | | (3,030 | ) | | | (1,789 | ) |
Income tax provision | | | 1 | | | | 10 | | | | 13 | | | | 39 | | | | 1,078 | |
| | | | | | | | | | | | | | | | | | | | |
Net (loss) income | | $ | (1,691 | ) | | $ | (792 | ) | | $ | 1,616 | | | $ | (3,069 | ) | | $ | (2,867 | ) |
| | | | | | | | | | | | | | | | | | | | |
Net (loss) income per share: | | | | | | | | | | | | | | | | | | | | |
Basic | | $ | (0.10 | ) | | $ | (0.04 | ) | | $ | 0.08 | | | $ | (0.16 | ) | | $ | (0.13 | ) |
Diluted | | $ | (0.10 | ) | | $ | (0.04 | ) | | $ | 0.08 | | | $ | (0.16 | ) | | $ | (0.13 | ) |
Weighted average number of shares used in per share calculations(1): | | | | | | | | | | | | | | | | | | | | |
Basic | | | 17,327 | | | | 19,431 | | | | 20,412 | | | | 19,530 | | | | 22,600 | |
Diluted | | | 17,327 | | | | 19,431 | | | | 21,023 | | | | 19,530 | | | | 22,600 | |
Pro forma net (loss) income data(2): | | | | | | | | | | | | | | | | | | | | |
(Loss) income before income taxes | | $ | (1,690 | ) | | $ | (782 | ) | | $ | 1,629 | | | $ | (3,030 | ) | | | | |
Pro forma provision for income taxes | | | 1 | | | | 10 | | | | 343 | | | | 39 | | | | | |
| | | | | | | | | | | | | | | | | | | | |
Pro forma net (loss) income | | $ | (1,691 | ) | | $ | (792 | ) | | $ | 1,286 | | | $ | (3,069 | ) | | | | |
| | | | | | | | | | | | | | | | | | | | |
35
| | | | | | | | | | | | | | | | | | |
| | | Year Ended December 31, |
| | | 2003 | | | 2004 | | | 2005 | | | 2006 | | 2007 |
| | | (in thousands) |
Non-Cash Share-Based Compensation Data(3): | | | | | | | | | | | | | | | | | | |
Cost of product revenue | | $ | — | | | $ | — | | | $ | — | | | $ | 2 | | $ | 81 |
Cost of services and maintenance revenue | | | 67 | | | | 36 | | | | — | | | | 232 | | | 818 |
Selling and marketing | | | — | | | | — | | | | — | | | | 328 | | | 1,332 |
Research and development | | | — | | | | — | | | | — | | | | 148 | | | 594 |
General and administrative | | | 134 | | | | 72 | | | | — | | | | 392 | | | 1,520 |
| | | | | | | | | | | | | | | | | | |
Total non-cash share-based compensation | | $ | 201 | | | $ | 108 | | | $ | — | | | $ | 1,102 | | $ | 4,345 |
| | | | | | | | | | | | | | | | | | |
| |
| | | Year Ended December 31, |
| | | 2003 | | | 2004 | | | 2005 | | | 2006 | | 2007 |
Balance Sheet Data: | | | | | | | | | | | | | | | | | | |
Cash and cash equivalents | | $ | 2,735 | | | $ | 2,303 | | | $ | 7,556 | | | $ | 8,041 | | $ | 37,591 |
Total assets | | $ | 8,502 | | | $ | 11,993 | | | $ | 21,526 | | | $ | 59,345 | | $ | 75,937 |
Notes payable and capital leases | | $ | 1,520 | | | $ | 1,445 | | | $ | 733 | | | $ | 1,430 | | $ | 771 |
Deferred revenue | | $ | 6,619 | | | $ | 9,810 | | | $ | 16,319 | | | $ | 20,221 | | $ | 27,201 |
Total stockholders’ (deficit) equity | | $ | (2,747 | ) | | $ | (3,431 | ) | | $ | (1,815 | ) | | $ | 26,689 | | $ | 33,896 |
| (1) | See Note 2 to our consolidated financial statements for an explanation of the determination of the number of shares used to compute basic and diluted per share amounts. |
| (2) | In October 1998, we elected to be treated for Federal income tax purposes as an S Corporation and were exempt from paying federal income taxes. In addition, from and after the day we elected or were otherwise treated as an S Corporation for state tax purposes to the day prior to the day our status as an S Corporation was revoked, we paid or are required to pay certain state income taxes at a reduced rate. We filed an election to revoke our S Corporation status on December 11, 2006. Pro forma net (loss) income data is unaudited and reflects the income tax expense that would have been recorded had we not been exempt from paying income taxes due to our S Corporation election. |
| (3) | Non-cash compensation recorded in the years ended December 31, 2003 and 2004 is related to restricted common shares granted to certain key employees. Non-cash compensation recorded in the years ended December 31, 2006 and 2007 relates to stock options granted to employees measured under the fair value method and, in 2007, includes costs related to nonvested share grants (see Note 9 to the consolidated financial statements). |
| Item 7. | Management’s Discussion and Analysis of Financial Condition and Results of Operations |
The following discussion of our financial condition and results of operations should be read together with the financial statements and related notes that are included elsewhere in this Annual Report. This discussion may contain forward-looking statements based upon current expectations that involve risks and uncertainties. Our actual results may differ materially from those anticipated in these forward-looking statements as a result of various factors, including those set forth under “Risk Factors” or in other parts of this Annual Report.
Overview
We develop and provide the leading software solutions for digital investigations, including EnCase® Enterprise, a network-enabled product primarily for large corporations and government agencies, and EnCase® Forensic, a desktop-based product primarily for law enforcement agencies. We were incorporated and commenced operations in 1997. From 1997 through 2002, we generated a substantial portion of our revenues from the sale of our EnCase® Forensic products and related services. We have experienced increases in our revenue as a result of the release of our EnCase® Enterprise products in late 2002, which expanded our customer base into corporate enterprises and federal government agencies. In addition, the releases of our EnCase®
36
eDiscovery solution in late 2005 and EnCase® Information Assurance solution in late 2006 have increased our average transaction size. We anticipate that sales of our EnCase® Enterprise products and related services, in particular our EnCase® eDiscovery and EnCase® Information Assurance solutions, will comprise a substantial portion of our future revenues.
Factors Affecting Our Results of Operations
There are a number of trends that may affect our business and our industry. Some of these trends or other factors include:
| | • | | Legislative and regulatory developments. Our digital investigation solutions allow law enforcement agencies, government organizations and corporations to conduct investigations within the legal and regulatory framework. Historically, the implementation of new laws and regulations surrounding digital investigations has helped create demand for our products. Future changes in applicable laws or regulations could enhance or detract from the desirability of our products. |
| | • | | Information technology budgets. Deployment of our solutions may require a substantial capital expenditure by our customers. Budgets for information technology-related capital expenditures at corporations and all levels of government organizations are typically cyclical in nature, with generally higher budgets in times of improving economic conditions and lower budgets in times of economic slowdowns. |
| | • | | Law enforcement agency budgets. We sell our EnCase® Forensic products and training services primarily to law enforcement agencies. Because of the limited nature of law enforcement budgets, funds are typically initially allocated toward solving issues perceived to be the most pressing. Sales of our products could be impacted by changes in the budgets of law enforcement agencies or in the relative priority assigned to digital law enforcement investigations. |
| | • | | Prevalence and impact of hacking incidents and spread of malicious software. The increasing sophistication of hacking attacks on government and private networks and the global spread of malicious software, such as viruses, worms and rootkits, have increased the focus of corporations and large government organizations on digital investigations and other aspects of network security, which has, in turn, increased demand for our products. Future changes in the number and severity of such attacks or the spread of malicious software could have an effect on the demand for our products. |
| | • | | Seasonality in revenues. We experience seasonality in our revenues, with the third and fourth quarters typically having the highest revenues for the year. We believe that this seasonality results primarily from our customers’ budgeting cycles. The federal government budget year ends in the third calendar quarter of the year and a majority of corporate budget years end in the fourth calendar quarter of the year. In addition, our customers also tend to make software purchases near the end of a particular quarter, which tends to make our revenues for a particular period unpredictable for a significant portion of that period. We expect that this seasonality within particular years and unpredictability within particular quarterly periods will continue for the foreseeable future. |
| | • | | Amount of commercial litigation. Because commercial litigation often involves eDiscovery, an increase in commercial litigation could increase demand for our products and services, while a decrease in commercial litigation could decrease demand. |
Critical Accounting Policies and Estimates
Our discussion and analysis of our financial condition and results of operations are based upon our financial statements, which have been prepared in accordance with accounting principles generally accepted in the United States of America (“GAAP”). Our significant accounting policies are discussed in Note 1 to our financial statements, included herein at Item 8. The application of GAAP requires us to make estimates, judgments and assumptions that affect the reported amounts of our revenues, expenses, assets and liabilities, and related
37
disclosure of contingent assets and liabilities. We base our estimates, judgments and assumptions on historical experience and on various other factors that are believed to be reasonable based upon information available to us at the time these estimates are made. Historically, our critical accounting estimates have not differed materially from actual results; however, changes in these accounting estimates are reasonably likely to occur from period to period. Although we evaluate these estimates, judgments and assumptions on a regular basis and make changes accordingly, actual results could differ significantly from those anticipated based on our estimates and assumptions. To the extent there are significant differences between these estimates and actual results, our future results of operations and financial condition could be materially affected.
We believe that the estimates, judgments and assumptions involved in the accounting policies described below require the most subjective judgment and have the greatest potential impact on our financial statements, so we consider these to be our critical accounting policies. Senior management has reviewed the development and selection of these critical accounting policies and estimates, and their related disclosure in this report, with the Audit Committee of our Board of Directors.
Revenue Recognition
We derive revenue from licenses of our software and sales of related services, which include post-contract customer support, or maintenance, consulting and training. We recognize revenue in accordance with GAAP as prescribed for the software industry, which are substantially governed by AICPA Statement of Position No. 97-2 (“SOP 97-2”), “Software Revenue Recognition,” as amended and interpreted. While these pronouncements govern the basis for revenue recognition, in applying our revenue recognition policy we must determine which portions of our revenue should be recognized currently and which portions, if any, should be deferred. In order to determine current and deferred revenue, we make judgments and estimates with regard to future deliverable products and services and the appropriate pricing for those products and services. In general, we recognize revenue when persuasive evidence of an arrangement exists, we have delivered the product or performed the service, the fee is fixed or determinable and collectibility is probable, as follows:
| | • | | Persuasive evidence of an arrangement. If we either enter into contracts or receive written purchase orders issued by a customer that legally bind us and the customer, we consider that as evidence of an arrangement. |
| | • | | Delivery. We deem delivery of products to have occurred when the title and risk of ownership have passed to the buyer. Services revenue is recognized as services are performed. |
| | • | | Fixed or determinable fee. We consider the fee to be fixed or determinable if the fee is not subject to refund or adjustment and the payment terms are within normal established practices. If the fee is not fixed or determinable, we recognize the revenue as amounts become due and payable, provided all other revenue recognition criteria have been met. |
| | • | | Collection is deemed probable. We conduct a credit review for all significant transactions at the time of the arrangement to determine the credit-worthiness of the customer. Collection is deemed probable if we have a reasonable basis to expect that the customer will pay amounts under the arrangement as payments become due. |
However, determining whether and when some of these criteria have been satisfied often involves assumptions and judgments that can have a significant impact on the timing and amount of revenue reported. For example, for multiple element arrangements we must make assumptions and judgments in order to allocate the total purchase price (irrespective of invoiced allocations) among the various elements we deliver, to determine whether undelivered services are essential to the functionality of the delivered products and services, to determine whether vendor-specific evidence (“VSOE”) of fair value exists for each undelivered element and to determine whether and when each element has been delivered. The VSOE of fair value for all elements of an arrangement is based upon the normal pricing and discounting practices for those products and services when sold separately and, for software license updates and product support services, is additionally measured by the
38
renewal rate offered to the customer. If we were to change our pricing practices or any of our other assumptions or judgments in the future, our future revenue recognition could differ significantly from our historical results.
Amounts for fees collected or invoiced and due relating to arrangements when revenue cannot be recognized are reflected on our balance sheet as deferred revenue and recognized when the product is delivered or over the period in which the service is performed, in accordance with our revenue recognition policy for such element. If we cannot objectively determine the fair value of any undelivered element included in bundled software and service arrangements, we defer revenue until all elements are delivered and services have been performed, or until fair value can objectively be determined for any remaining undelivered elements. When the fair value of a delivered element has not been established, we use the residual method to record revenue if the fair value of all undelivered elements is determinable. Under the residual method, the fair value of the undelivered elements is deferred and the remaining portion of the arrangement fee is allocated to the delivered elements and is recognized as revenue.
Product Revenue. The timing of product revenue recognition is dependent on the nature of the product sold. Product arrangements comprising multiple deliverables, including software and hardware, are generally categorized into one of the following:
| | • | | EnCase® Enterprise, Encase® eDiscovery, EnCase® Information Assurance and AIRS. License revenue associated with these arrangements, exclusive of amounts allocated to maintenance and other undelivered elements for which we have vendor-specific objective evidence (“VSOE”) of fair value, is recognized upon delivery, provided that all other criteria for revenue recognition have been met. |
| | • | | EnCase® Forensic. License revenue from corporate customers, exclusive of amounts allocated to maintenance, for which we have VSOE of fair value, is recognized upon delivery, provided that all other criteria for revenue recognition have been met. Because maintenance is included at no additional cost in governmental Forensic arrangements, VSOE of fair value for the maintenance element for governmental customers is indeterminable, so we allocate governmental Forensic product, services and maintenance revenue ratably over the longer of the contractual maintenance period (12 months) or the implied maintenance period (12-25 months) based on estimated fair values of the various components. |
| | • | | Premium License Support Program Solutions. The Premium License Support Program is a subscription arrangement entitling customers to receive unspecified future products and post-contract customer support for a period of several years. Revenue resulting from Premium License Support Program arrangements is recognized ratably over the contractual period beginning with the delivery of the first product. |
| | • | | Neutrino™. Our mobile device investigative solution is sold to Forensic customers with a related subscription covering future adapters for newly issued cell phones. Revenue is recognized over the related subscription period. For Enterprise customers, Neutrino revenue is recognized upon delivery, provided that all other criteria for revenue recognition have been met. Standard maintenance is charged to entitle customers to future cell phone adapters on an if-and-when available basis. |
| | • | | Hardware. Revenue associated with the sale of hardware is recognized upon shipment to the customer, provided that all other criteria for revenue recognition have been met. |
Services and Maintenance Revenue. Services and maintenance revenue consists of professional services, training, and maintenance. Revenue from such services is recognized as the services are provided. We refer to revenue related to technical product support and software updates on a when-and-if available basis as maintenance revenue, which is recognized ratably over the applicable contractual period. We determine the amount of maintenance revenue to be deferred through reference to substantive maintenance renewal provisions contained in each arrangement. We consider substantive maintenance provisions to be provisions where the cost of the maintenance renewal, stated in the contract with our customer as a percentage of the product fee, is comparable to the normal pricing for maintenance-only renewals. Substantially all of our customers purchase maintenance support when they acquire new software licenses and substantially all renew their maintenance support contracts annually or otherwise.
39
Training revenues are either recognized on a per-class basis upon a participant’s attendance or, for those customers who have subscribed to our Annual Training Passport program, revenue is recognized ratably over the annual period.
Share-Based Compensation
Effective January 1, 2006, we adopted SFAS No. 123R (“SFAS 123R”), “Share-Based Payment.” Prior to the adoption of SFAS 123R, we used the minimum-value method afforded by the SFAS No. 123, “Accounting for Stock-Based Compensation,” for disclosure purposes. Since all options granted prior to January 1, 2006 were granted at exercise prices that were equal to the fair market value of the underlying stock on the date of the grant, no share-based compensation for stock options was recorded in the accompanying financial statements prior to 2006 and we are not required to record compensation expense for stock options granted prior to January 1, 2006 unless the terms of those options are subsequently modified. We adopted SFAS 123R using the prospective transition method and, accordingly, since adoption, we recognize share-based compensation expense for all share-based awards granted after January 1, 2006. Under that transition method, results for prior periods have not been restated.
With the exception of one option granted in December 2007 with market-based vesting conditions, which is discussed further below, we use the Black-Scholes option pricing model to determine the grant date fair value of share-based payments and recognize that cost, net of an estimated forfeiture rate, as compensation expense on a straight-line basis over the vesting period. The determination of the grant date fair value of share-based awards using that model is affected by our stock price as well as assumptions regarding a number of complex and subjective variables. These variables include the estimated number of years that we expect employees to hold their stock options (the option “term”) and our expected stock price volatility, risk-free interest rates and dividends to be paid on our stock over that term.
The expected term (life) of stock option awards has been calculated using the “simplified method” as afforded by Staff Accounting Bulletins (“SAB”) Topic No. 107 and 110 because we lack sufficient historical data to provide a reasonable basis to estimate the expected term. We lack this historical data because of two factors: first, our 2004 Equity Incentive Plan (the “Plan”) was adopted in 2004 and we do not have a sufficient history of exercises and forfeitures over the typical 10-year life of our awards to predict future option holder behavior, which is critical in estimating an expected term for our options, and, second, we believe that our December 2006 initial public offering has likely changed the historical patterns that were experienced during the brief period of time from the Plan’s adoption to our initial public offering. The volatility of our common stock is estimated at the date of grant based on a weighted-average of the implied volatility of publicly traded 30-day to 270-day options on the common stock of a select peer group of similar companies (“Similar Companies”), the historical volatility of the common stock of Similar Companies and, beginning in late 2007, the historical volatility of our common stock, consistent with the requirements of SFAS 123R and SAB 107. The risk-free interest rate used in option valuation is based on the implied yield in effect at the time of each option grant, based on U.S. Treasury zero-coupon issues with equivalent expected terms. We use a dividend yield of zero in the Black-Scholes model, as we have no intention to pay any cash dividends on our common stock in the foreseeable future. SFAS 123R also requires that we estimate forfeitures at the time of grant and revise those estimates in subsequent periods if actual forfeitures differ from those estimates. We use historical data to estimate pre-vesting option forfeitures and record share-based compensation expense only for those awards that are expected to vest. Quarterly changes in the estimated forfeiture rate can potentially have a significant effect on reported share-based compensation, as the cumulative effect of adjusting the forfeiture rate for all expense amortization after January 1, 2006 is recognized in the period the forfeiture estimate is changed.
In December 2007, we granted an option to purchase 500,000 shares of our common stock that vests, in 25% increments, only upon attainment of specified market-based conditions tied to the market value of our common stock and we may continue to award such market-based vesting options from time to time in the future. Under the provisions of SFAS 123R, the fair value of share-based grants with a market vesting condition must be
40
modeled and valued with a path-dependent valuation technique. Accordingly, we estimate the value of such awards using the Monte Carlo binomial simulation model. The primary assumptions used in the model are volatility, a risk-free interest rate, starting stock price, transferability restrictions and the terms of the award, as more fully described in Note 10 to our consolidated financial statements. Using these assumptions and inputs, in valuing the December 2007 grant, we simulated 25,000 possible price paths for our common stock over a ten-year period. For each trial, if the market conditions were met, the fair value of the option was then estimated using the Black-Scholes model; if the market condition was not met, the options were assigned zero value. The fair value of this award was then calculated as the average net present value across the simulation trials and a derived service period was calculated for achievement of each of the four market conditions. Under FAS 123R, the calculated $2.8 million fair value of this award must be recognized as expense over a weighted average period of approximately two years whether the market conditions are met or not so long as the grantee meets the service condition.
If we change the terms of our employee share-based compensation programs, refine future assumptions, such as experiencing forfeiture rates that differ from our estimates, or if we change to other acceptable valuation models, the stock-based compensation expense that we record in future periods may differ significantly from historical trends and could materially affect our results of operations.
The Black-Scholes option-pricing model was developed for use in estimating the fair value of traded put and call options that have no vesting restrictions and are fully transferable, characteristics not present in our stock option grants. Existing valuation models, including the Black-Scholes and Monte Carlo models, may not provide reliable measures of the fair values of our share-based compensation. Consequently, there is a risk that our estimates of the grant date fair value of share-based compensation awards may bear little resemblance to the actual values realized upon the exercise, expiration, early termination or forfeiture of those grants in the future. Certain stock options may be forfeited or expire and result in zero intrinsic value as compared to the fair values originally estimated on the grant date and reported in our financial statements. Alternatively, values may be realized from these instruments that are significantly higher than the fair values originally estimated on the grant date and reported in our financial statements. There currently is no market-based mechanism or other practical application to verify the reliability and accuracy of the estimates stemming from these valuation models.
As of December 31, 2007, there was $22.4 million of total unrecognized compensation cost related to non-vested stock-based compensation that is expected to be recognized over a weighted-average period of 3.23 years for grants subsequent to January 1, 2006. See Notes 9 and 10 of our consolidated financial statements for further information regarding share-based compensation.
Allowance for Doubtful Accounts
We maintain an allowance for doubtful accounts for estimated losses resulting from the inability of our customers to make required payments. The allowance is established through a provision for bad debt expense. We determine the adequacy of this allowance by evaluating individual customer accounts receivable, through consideration of the customer’s financial condition, credit history and current economic conditions. In addition, we analyze our historical credit loss history and apply these loss rates to our current accounts receivable balances to verify the reasonableness of our allowance. If the financial condition of our customers were to deteriorate, resulting in an impairment of their ability to make payments, additional allowances may be required in the future, which would result in increased general and administrative expense.
Accounting for Taxes
In preparing our consolidated financial statements, we estimate our income tax liability in each of the foreign and domestic jurisdictions in which we operate by estimating our actual current tax exposure and assessing temporary differences resulting from differing treatment of items for tax and financial statement purposes. Our judgments, assumptions and estimates relative to the current provision for income tax take into
41
account current tax laws, our interpretation of current tax laws and possible outcomes of audits conducted by foreign and domestic tax authorities. We have established reserves for income taxes to address potential exposures involving tax positions that could be challenged by tax authorities. Although we believe our judgments, assumptions and estimates are reasonable, changes in tax laws or our interpretation of tax laws and the resolution of any future tax audits could significantly impact the amounts provided for income taxes in our consolidated financial statements.
We calculate our current and deferred tax provisions based on estimates and assumptions that could differ from the actual results reflected in income tax returns filed during the subsequent year. Adjustments based on filed returns are generally recorded in the period when the tax returns are filed and the global tax implications are known and could significantly impact the amounts provided for income taxes. Tax law and rate changes are reflected in the income tax provision in the period in which such changes are enacted.
As a result of the termination of our S Corporation status in December 2006, we recorded deferred tax assets, which were fully offset by a valuation allowance. Subsequently, additional deferred tax assets generated have also been offset by partial valuation allowances. Management’s judgment is required in assessing the realizability of these and future deferred tax assets. In performing these assessments, we consider whether it is more likely than not that some portion or all of the deferred tax assets will not be realized. The ultimate realization of our net deferred tax assets is dependent upon our generating sufficient taxable income in future years in appropriate tax jurisdictions to realize a tax benefit from the reversal of temporary differences and net operating loss carryforwards. We consider the scheduled reversal of deferred tax liabilities, projected future taxable income, and tax planning strategies in making this assessment. Management will continue to evaluate the realizability of the deferred tax assets and related valuation allowances. If our assessment of the deferred tax assets or the corresponding valuation allowance were to change, we would record the related adjustment as a component of the income tax provision or benefit during the period in which we make that determination.
Commitments and Contingencies
We are subject to certain legal proceedings, as well as demands, claims and threatened litigation that arise in the normal course of our business. We periodically evaluate all pending or threatened contingencies and commitments, if any, that are reasonably likely to have a material adverse effect on our operations or financial position. We assess the probability of an adverse outcome and determine if it is remote, reasonably possible or probable as defined in accordance with the provisions of SFAS No. 5, “Accounting for Contingencies.” If management determines that it is probable that an asset had been impaired or a liability had been incurred at the date of our financial statements, and the amount of the loss, or the range of probable loss can be reasonably estimated, we record an accrued liability and an expense for the estimated loss. If no accrual is made for a loss contingency because one or both of the conditions pursuant to SFAS No. 5 are not met, but the probability of an adverse outcome is at least reasonably possible, we would disclose the nature of the contingency, if material, and provide an estimate of the possible loss or range of loss, or state that such an estimate cannot be made.
Significant judgment is required in both the determination of probability and the determination of whether an exposure is reasonably estimable. Because of uncertainties related to these matters, any accruals recorded are based on the best information available at the time. As additional information becomes available, we would reassess the potential liability related to our pending claims and litigation and may revise our estimates favorably or unfavorably. Potential legal liabilities and the revision of estimates of potential legal liabilities could have a material impact on our financial position and results of operations.
42
Results of Operations
The following table sets forth selected statements of operations data for each of the periods indicated expressed as a percentage of total revenues:
| | | | | | | | | |
| | | Year Ended December 31 | |
| | | 2005 | | | 2006 | | | 2007 | |
Revenues: | | | | | | | | | |
Product revenue | | 58.6 | % | | 58.3 | % | | 56.2 | % |
Services and maintenance revenue | | 41.4 | | | 41.7 | | | 43.8 | |
| | | | | | | | | |
Total revenues | | 100.0 | | | 100.0 | | | 100.0 | |
| | | | | | | | | |
Cost of revenues: | | | | | | | | | |
Cost of product revenue | | 5.6 | | | 4.3 | | | 3.5 | |
Cost of services and maintenance revenue | | 23.1 | | | 24.4 | | | 24.4 | |
| | | | | | | | | |
Total cost of revenues | | 28.7 | | | 28.7 | | | 27.9 | |
| | | | | | | | | |
Gross profit | | 71.3 | | | 71.3 | | | 72.1 | |
Operating expenses: | | | | | | | | | |
Selling and marketing | | 39.8 | | | 47.0 | | | 41.8 | |
Research and development | | 11.8 | | | 12.7 | | | 11.4 | |
General and administrative | | 12.5 | | | 14.0 | | | 18.6 | |
Depreciation and amortization | | 3.4 | | | 3.3 | | | 4.4 | |
| | | | | | | | | |
Total operating expenses | | 67.5 | | | 77.0 | | | 76.2 | |
| | | | | | | | | |
Operating income (loss) | | 3.8 | | | (5.7 | ) | | (4.1 | ) |
| | | | | | | | | |
Other income and expense: | | | | | | | | | |
Interest income | | 0.1 | | | 0.2 | | | 1.8 | |
Interest expense | | (0.2 | ) | | (0.2 | ) | | (0.1 | ) |
Other income, net | | 0.4 | | | 0.3 | | | 0.1 | |
| | | | | | | | | |
Income (loss) before income taxes | | 4.1 | | | (5.4 | ) | | (2.3 | ) |
Income tax provision | | 0.0 | | | 0.1 | | | 1.3 | |
| | | | | | | | | |
Net income (loss) | | 4.1 | % | | (5.5 | )% | | (3.6 | )% |
| | | | | | | | | |
Comparison of Results of Operations
Revenues
| | | | | | | | | | | | | | | |
| | | Year ended December 31, |
| (Dollars in millions) | | 2005 | | Increase | | | 2006 | | Increase | | | 2007 |
Product revenues: | | | | | | | | | | | | | | | |
Encase® Enterprise(1) | | $ | 11.9 | | 65 | % | | $ | 19.7 | | 63 | % | | $ | 32.1 |
Encase® Forensic(2) | | | 9.8 | | 12 | % | | | 11.0 | | (2 | )% | | | 10.8 |
Other | | | 1.4 | | 32 | % | | | 1.9 | | (23 | )% | | | 1.4 |
| | | | | | | | | | | | | | | |
Total product revenues | | | 23.1 | | 41 | % | | | 32.6 | | 36 | % | | | 44.3 |
| | | | | | | | | | | | | | | |
Services and maintenance revenues: | | | | | | | | | | | | | | | |
Professional services | | | 5.2 | | 72 | % | | | 8.8 | | 40 | % | | | 12.4 |
Training | | | 6.7 | | 4 | % | | | 7.0 | | 22 | % | | | 8.5 |
Maintenance and other | | | 4.5 | | 66 | % | | | 7.5 | | 83 | % | | | 13.7 |
| | | | | | | | | | | | | | | |
Total services and maintenance revenues | | | 16.4 | | 42 | % | | | 23.3 | | 48 | % | | | 34.6 |
| | | | | | | | | | | | | | | |
Total revenues | | $ | 39.5 | | 41 | % | | $ | 55.9 | | 41 | % | | $ | 78.9 |
| | | | | | | | | | | | | | | |
| (1) | Includes perpetual licenses related to our eDiscovery and Information Assurance add-on products. |
| (2) | Includes revenues related to our Premium License Support Program. |
43
We generate product revenue principally from sales of our EnCase® Enterprise and EnCase® Forensic products. A substantial portion of the EnCase® Enterprise and EnCase® Forensic license agreements we enter into include perpetual license terms. In conjunction with our EnCase® Forensic software, we also sell our Premium License Support Program product, which is sold on a subscription basis for a term of several years. In addition, we sell our NeutrinoTM mobile forensic device and certain other forensic hardware which we include in “Other” product revenue. The first two quarters of each fiscal year are typically our period of lowest product sales due to the seasonal budgetary cycles of our customers. The third quarter is typically the strongest sales quarter to our federal government customers. Typically, sales to our corporate customers are highest in the fourth quarter.
We introduced our EnCase® eDiscovery solution in late 2005 and EnCase® Information Assurance in mid 2006, which have significantly increased our average transaction size. During fiscal year 2007, we sold approximately 80 EnCase® eDiscovery, EnCase® Information Assurance and AIRS add-on modules as compared to 50 in 2006 and two in 2005. In addition to the factors noted below, these increases were made possible by increasingly productive selling and marketing efforts. The number of sales and marketing personnel that we employ increased from approximately 90 at year end 2005 to 150 at year end 2006, but declined to approximately 135 at year end 2007. We believe our sales personnel productivity increases with tenure and training.
Product revenues increased by $11.7 million (36%) in 2007 over 2006, with that growth driven by a $12.4 million revenue increase from our Encase® Enterprise product line, which is a reflection of the growth in the eDiscovery industry. Changes in the Federal Rules of Civil Procedure in December 2006 concerning electronic discovery have contributed to the overall growth in the marketplace and sustained selling and marketing efforts also contributed to our 2007 product revenue growth. We recently extended the estimated life of our December 2006 EnCase® Forensic Version 6 release from late 2008 into 2009, which reduced the revenue recognized for that product during 2007 by an estimated $0.3 million. We expect revenues from our forensic products will grow at a moderate rate in 2008.
In 2006, product revenues increased by $9.5 million (41%) over 2005 levels. Revenues generated from EnCase® Enterprise increased to $19.7 million in 2006 from $11.9 million in 2005 due to introduction of the EnCase® eDiscovery solution in late 2005 and EnCase® Information Assurance in mid 2006, overall industry growth and an increase in commissioned sales personnel in later 2006. Prior to 2005, we recognized revenues related to sales of our EnCase® Forensic product to commercial customers ratably over the maintenance period however, beginning in early 2005, we were able to establish VSOE of the elements of such arrangements and recognize product revenues upon delivery. As a result, we recognized an additional $1.2 million of EnCase® Forensic sales product revenue in 2005 that would otherwise have been recognized in subsequent periods.
Services and maintenance revenues increased $11.3 million (48%) in 2007, with our maintenance segment contributing $6.2 million of that total increase by virtue of an on-going overall increase in our installed product base and a high annual renewal rate by customers desiring continuing maintenance support on our products. Revenues for the professional services segment increased $3.6 million as the result of a $3.1 million increase in digital investigation consulting and a $0.5 million increase in implementation engagements. The number of professional services personnel has increased from 30 in 2005 to 50 in 2006 and 62 in 2007. Training services revenue increased $1.5 million in 2007 as a result of increased class offerings and attendance. The number of customers we train on our products tends to grow in tandem with the growth in the installed product base and the number of training seats filled increased from approximately 3,800 in 2006 to 4,800 in 2007. Much of this growth is attributable to the Annual Training Passport program we introduced in August 2006, which generated approximately $1.4 million in 2007 revenue.
In 2006, services and maintenance revenues were $6.9 million (42%) higher than in 2005. Professional services revenue grew by $3.7 million in 2006 as a result of increased digital investigation consulting revenue of $2.8 million and increased software implementation revenue of $0.9 million due to higher staffing and increased customer demand. In addition, maintenance revenue grew by $3.0 million as a result of an increasing installed product base and high maintenance renewal rates.
44
Cost of Revenues
| | | | | | | | | | | | | | | | | | |
| | | Year ended December 31, | |
| (Dollars in millions) | | 2005 | | | Increase | | | 2006 | | | Increase | | | 2007 | |
Cost of product revenues | | $ | 2.2 | | | 10 | % | | $ | 2.4 | | | 13 | % | | $ | 2.7 | |
| | | | | | | | | | | | | | | | | | |
Cost of services and maintenance revenues: | | | | | | | | | | | | | | | | | | |
Professional services | | | 4.3 | | | 75 | % | | | 7.7 | | | 54 | % | | | 11.8 | |
Training | | | 4.0 | | | 25 | % | | | 5.0 | | | 12 | % | | | 5.6 | |
Maintenance and other | | | 0.8 | | | 28 | % | | | 1.0 | | | 91 | % | | | 1.9 | |
| | | | | | | | | | | | | | | | | | |
Total cost of services and maintenance revenues | | | 9.1 | | | 49 | % | | | 13.7 | | | 41 | % | | | 19.3 | |
| | | | | | | | | | | | | | | | | | |
Total cost of revenues | | $ | 11.3 | | | 42 | % | | $ | 16.1 | | | 37 | % | | $ | 22.0 | |
| | | | | | | | | | | | | | | | | | |
Share-based compensation included above: | | | | | | | | | | | | | | | | | | |
Cost of product revenues | | $ | — | | | | | | $ | — | | | | | | $ | 0.1 | |
| | | | | | | | | | | | | | | | | | |
Cost of services and maintenance revenues | | $ | — | | | | | | $ | 0.2 | | | | | | $ | 0.8 | |
| | | | | | | | | | | | | | | | | | |
Gross Margin Percentage | | | | | | | | | | | | | | | | | | |
Products | | | 90.5 | % | | | | | | 92.5 | % | | | | | | 93.8 | % |
| | | | | | | | | | | | | | | | | | |
Services and maintenance | | | 44.1 | % | | | | | | 41.5 | % | | | | | | 44.2 | % |
| | | | | | | | | | | | | | | | | | |
Total | | | 71.3 | % | | | | | | 71.3 | % | | | | | | 72.1 | % |
| | | | | | | | | | | | | | | | | | |
Cost of software product revenue consists principally of the cost of producing and distributing our software, including the cost of compact discs, packaging, shipping, customs duties, and, to a lesser extent, compensation and related overhead expenses. While these costs are primarily variable with respect to sales volumes, they remain very low in relation to the revenues generated. Our gross margins can be affected by product mix, as our EnCase® Enterprise products are generally higher margin products than our EnCase® Forensic product, which is, in turn, higher margin than our hardware products.
The costs of professional services and training revenue, on the other hand, are largely comprised of employee compensation, including share-based compensation, costs and related overhead expenses, travel and facilities costs. The cost of maintenance revenue is primarily outsourced, but also includes employee compensation cost for customer technical support and related overhead costs.
Cost of product revenue increased only 13% in 2007 on an overall product revenue increase of 36% due primarily to the relatively low variable costs associated with higher software volumes and product mix. Sales of EnCase® Enterprise, one of our higher margin products, increased at a higher rate than sales of other, lower margin, products. In 2006, cost of product revenue increased 10% on an overall product revenue increase of 41% for the same reasons as in 2007. Product gross margin increased to 93.8% in 2007 from 92.5% in 2006 and 90.5% in 2005 as the annual revenue growth rates of higher margin EnCase® Enterprise products far outpaced the growth rates in lower margin products.
Total cost of services and maintenance revenue increased $5.6 million, or 41%, in 2007, on an overall increase in services and maintenance revenue of 48% over 2006. In 2007, we increased our team of experienced professional services consulting personnel by ten and opened several new offices, which contributed to increased compensation expense and facilities costs of $2.4 million (including a $0.6 million increase in share-based compensation) and $1.2 million, respectively. In addition, travel expense related to consulting and training increased $0.5 million due to increased activity and bad debt expense increased $0.3 million. Expenses and commissions paid to our third-party maintenance vendor also increased by $0.9 million, which is proportional to the growth in maintenance revenue in 2007. Overall, services and maintenance gross margin was 44.2% in 2007
45
compared to 41.5% in 2006. The additional costs incurred to expand our professional services segment to meet increased demand has negatively impacted the services gross margin in the short-term, which fell from 13% in 2006 to 4% in 2007. By making more efficient use of part-time trainers, we were able to increase the gross margin on training from 29% in 2006 to 35% in 2007 despite additional facilities costs. The gross margin on maintenance revenue remained stable at approximately 86% in the two years.
In 2006, cost of services and maintenance revenues increased $4.6 million, or 49%, on an overall increase in services and maintenance revenue of 42% over 2005. An increase in compensation expense of $3.0 million and an increase in travel related expenses of $0.5 million contributed to the increase in the cost of services and maintenance revenues. In addition, facilities costs and other overhead costs increased by $0.5 million. Overall, services and maintenance gross margin was 41.5% in 2006 compared to 44.1% in 2005, with that decrease largely due to the hiring of new professional services personnel during 2006 to meet the increase in demand for our services and services related costs associated with the release of EnCase® Enterprise Version 6. The gross margin on maintenance revenue increased slightly to 87%, from 83% in 2006.
Selling and Marketing
| | | | | | | | | | | | | | | | | | |
| | | Year ended December 31, | |
| (Dollars in millions) | | 2005 | | | Increase | | | 2006 | | | Increase | | | 2007 | |
Selling and marketing expenses | | $ | 15.7 | | | 67 | % | | $ | 26.2 | | | 26 | % | | $ | 33.0 | |
| | | | | | | | | | | | | | | | | | |
As a percentage of revenue | | | 39.8 | % | | | | | | 47.0 | % | | | | | | 41.8 | % |
| | | | | | | | | | | | | | | | | | |
Share-based compensation included above | | $ | — | | | | | | $ | 0.3 | | | | | | $ | 1.3 | |
| | | | | | | | | | | | | | | | | | |
Selling and marketing expenses consist primarily of base and incentive (sales commissions and share-based) compensation and related overhead expenses for employees engaged in selling and marketing. Selling and marketing expenses also include expenses relating to advertising, brand building, marketing and trade show events (net of amounts received from sponsors and participants), product management, travel and allocated overhead.
Although we expense our sales commissions at the time the related sale is invoiced to the client, revenues from our EnCase® Enterprise term licenses, EnCase® Forensic product, Premium License Support Program, NeutrinoTM, the Annual Training Passport , consulting, maintenance and implementation are recognized over the relevant performance or license period. Accordingly, we generally experience a delay between increased selling and marketing expenses and the recognition of a portion of the corresponding revenue. The number of sales and marketing personnel that we employ was approximately 90 at year end 2005, 150 at year end 2006 and 135 at year end 2007.
Selling and marketing expenses in 2007 increased $6.8 million over 2006; however, these costs as a percentage of revenue decreased from 47% in 2006 to 42% in 2007. Total compensation expense contributed $6.3 million of that increase, with base compensation increasing $3.5 million (34%) in 2007 due primarily to a higher average headcount (approximately 145 in 2007 compared to 120 in 2006), sales commissions increasing $1.7 million (44%) due to higher sales volumes and share-based compensation increasing $1.0 million. In addition, the 2007 increase includes $1.0 million in additional overhead allocations for new facilities and employee benefit costs and $0.5 million in new sales training, which were partially offset by a $1.2 million decline in net expenses for sales promotions and marketing events.
In 2006, selling and marketing expenses increased $10.5 million, or 67%, over 2005, with these costs as a percentage of revenue increasing from 40% to 47%. The increase was primarily attributable to increased compensation expense, including sales commissions, of $6.4 million due to expansion of the sales force and higher sales, combined with an increase in travel expenses of $1.0 million and a $1.0 million increase in costs
46
associated with our Computer and Enterprise Investigations Conference (“CEIC®”) and other tradeshows. General marketing promotions and activities also increased $0.4 million. In addition, facilities costs and other overhead costs associated with selling and marketing activities increased by $0.8 million.
Research and Development
| | | | | | | | | | | | | | | | | | |
| | | Year ended December 31, | |
| (Dollars in millions) | | 2005 | | | Increase | | | 2006 | | | Increase | | | 2007 | |
Research and development expenses | | $ | 4.7 | | | 52 | % | | $ | 7.1 | | | 28 | % | | $ | 9.1 | |
| | | | | | | | | | | | | | | | | | |
As a percentage of revenue | | | 11.8 | % | | | | | | 12.7 | % | | | | | | 11.4 | % |
| | | | | | | | | | | | | | | | | | |
Share-based compensation included above | | $ | — | | | | | | $ | 0.1 | | | | | | $ | 0.6 | |
| | | | | | | | | | | | | | | | | | |
Research and development expenses consist primarily of compensation, including share-based compensation, and related overhead expenses for research and development personnel, including quality assurance and testing. In order to develop new product offerings, continue developing existing products and improve quality assurance, we increased the number of research and development personnel that we employ from 32 in 2005 to 50 in 2006 and to 55 in 2007.
Research and development expenses in 2007 increased $2.0 million, or 28%, from 2006. The higher expenses were driven by increases of $0.7 million (20%) in base compensation, $0.5 million in share-based compensation, and $0.5 million in other employee-related and facilities costs.
In 2006, research and development compensation expense increased $2.4 million from 2005. Higher compensation expenses accounted for $2.1 million of that increase, which was attributable to the significant increase in personnel during the year noted above.
General and Administrative
| | | | | | | | | | | | | | | | | | |
| | | Year ended December 31, | |
| (Dollars in millions) | | 2005 | | | Increase | | | 2006 | | | Increase | | | 2007 | |
General and administrative expenses | | $ | 4.9 | | | 59 | % | | $ | 7.8 | | | 87 | % | | $ | 14.6 | |
| | | | | | | | | | | | | | | | | | |
As a percentage of revenue | | | 12.5 | % | | | | | | 14.0 | % | | | | | | 18.6 | % |
| | | | | | | | | | | | | | | | | | |
Share-based compensation included above | | $ | — | | | | | | $ | 0.4 | | | | | | $ | 1.5 | |
| | | | | | | | | | | | | | | | | | |
General and administrative expenses consist of compensation, including share-based compensation, and related overhead expenses for personnel engaged in the accounting, legal, information systems, human resources and other administrative functions. As a result of our continuing revenue growth and to meet the requirements of becoming a public company in December 2006, we increased the number of general and administrative personnel that we employ from 32 in 2005 to 50 in 2006 and to 62 in 2007. In addition, general and administrative expense includes professional service fees, other corporate expenses and related overhead.
General and administrative expenses in 2007 increased $6.8 million, or 87%, over 2006. The need for additional qualified personnel and professional services to meet the compliance requirements of a public company contributed significantly to the increase in expenses. Base compensation expense increased $2.2 million, or 60%, as we hired personnel with the skills necessary to operate and manage a public company, share-based compensation increased $1.1 million and bonuses increased $0.4 million. Consulting and professional fees associated with audit, legal, consultation on Sarbanes-Oxley Section 404 implementation and tax compliance increased $1.8 million. In addition, increased company-wide recruiting fees and insurance expense increased by $0.4 million and $0.3 million, respectively.
47
In 2006, general and administrative expenses increased $2.9 million over 2005, with a $2.5 million increase in compensation and temporary help expense and higher outside professional fees relating to our preparation to be a public company of $0.5 million accounting for the increase.
Depreciation and Amortization
| | | | | | | | | | | | | | | | | | |
| | | Year ended December 31, | |
| (Dollars in millions) | | 2005 | | | Increase | | | 2006 | | | Increase | | | 2007 | |
Depreciation and amortization expense | | $ | 1.4 | | | 34 | % | | $ | 1.8 | | | 89 | % | | $ | 3.5 | |
| | | | | | | | | | | | | | | | | | |
As a percentage of revenue | | | 3.4 | % | | | | | | 3.3 | % | | | | | | 4.4 | % |
| | | | | | | | | | | | | | | | | | |
Depreciation and amortization expenses consist of depreciation and amortization of our leasehold improvements, furniture and computer hardware and software. In 2006 and 2007, we invested approximately $2.4 million and $8.6 million, respectively, in capital equipment and leasehold improvements, resulting in significant increases in depreciation and amortization expense in those years.
Depreciation and amortization expense in 2007 increased $1.7 million, or 89%, from 2006, primarily due to the opening or expansion of facilities in Pasadena, California and New York City, New York and the investment in leasehold improvements, networks and phone equipment to permit several of our remote offices to safely access our corporate network. In 2006, depreciation and amortization expense increased $0.4 million, primarily due to the purchase of computer equipment for our new employees.
Interest Income
Interest income increased to $1.5 million in 2007, compared to $0.1 million in 2006 and 2005, with the increase resulting largely from the investment of cash received from our initial public offering in mid-December 2006.
Income Tax Provision
Our income tax provisions for 2005 and most of 2006 consist of expenses primarily related to the taxable income incurred based on our tax rate as an S Corporation. We filed an election to revoke our S Corporation status on December 11, 2006. From and after the revocation of our S Corporation status, we have been treated for federal and state income tax purposes as a C Corporation and, as a result, are and will continue to be subject to state and federal corporate income taxes.
The income tax provision for the year ended December 31, 2007 was $1,078,000 as compared to $39,000 for the prior year, with the increase primarily attributable to our C-Corporation status and an increase in the deferred tax valuation allowance for a portion of the deferred tax assets generated during 2007 for which it is more likely than not that the assets will be realized. During the majority of 2006 and all of 2005, the Company’s income tax provision was negligible due to its election to be treated as an S-Corporation for income tax purposes during those periods.
Liquidity and Capital Resources
Since inception, we have largely financed our operations from our cash flow from operations. In December 2006, we issued and sold 3,250,000 primary shares of our common stock at $11.50 per share, for net proceeds of $34.8 million in our initial public offering. As of December 31, 2007, we had $37.6 million in cash and cash equivalents. We believe that our cash flow from operations and our cash and cash equivalents are sufficient to fund our working capital and capital expenditure requirements for at least the next 12 months.
48
We generate cash from operations primarily from cash collections related to the sale of our products and services. Net cash provided by operating activities was $8.5 million in 2007 compared with net cash used in operations of $2.8 million in 2006. The increase in cash provided by operations principally reflects an increase in cash collections from significantly higher sales volumes of existing products and new offerings, including EnCase® Forensic Version 6 released in December 2006, although a notable portion of these cash flows must be deferred for recognition as revenue at a later date. Despite significantly higher revenues in 2007, we were able to reduce the cash used to carry accounts receivable balances from $7.8 million in 2006 to $4.5 million in 2007. The $2.8 million use of cash in operations during 2006 was largely attributable to increased payroll and related costs associated with additional sales, marketing and development personnel and higher accounts receivable balances. The first and fourth quarters of our fiscal year are our strongest quarters for cash collections, a consequence of the higher sales volumes typically experienced in the third and fourth quarters.
Net cash provided by investing activities was $16.1 million in 2007, whereas in 2006, investing activities resulted in a $27.1 million use of cash. This change is largely the result of our decision to invest a considerable portion of the proceeds of our December 2006 initial public offering in short-term investments prior to year end 2006, and subsequent decision to reinvest the proceeds upon maturity into cash equivalents during 2007. Additionally, cash used in investing activities in 2007 consists of capital expenditures of approximately $8.6 million for the purchase of new computer equipment and the construction and build-out of new office facilities in Pasadena, CA, New York, NY, and near San Francisco, Chicago and Washington, D.C., compared with $2.4 million in capital expenditures during 2006. We presently expect capital expenditures to approximate $4 million to $5 million in 2008, which we expect to fund from operating cash flows.
Net cash provided by financing activities decreased to $4.9 million in 2007, compared to $30.4 in 2006, largely due to the nonrecurring net proceeds (after cash paid for related expenses) of $31.0 million received from our 2006 initial public offering. On the other hand, cash received from the exercise of stock options amounted to $4.0 million in 2007 compared to $1.7 million in 2006. In addition, we made a cash distribution to the shareholders in respect of S-Corporation taxable earnings in the amount of $1.7 million during 2006 for which no corresponding payment was required in 2007. In each of the periods, we also paid down capital lease obligations.
We maintain a $3.0 million line of credit with a bank. This line of credit terminates on October 31, 2008. At December 31, 2007, there were no amounts outstanding against this line. The line requires that we maintain certain financial covenants. At December 31, 2007, we were in compliance with the covenants associated with the revolving line of credit.
We currently have no material cash commitments, except our normal recurring trade payables, expense accruals and leases, all of which are currently expected to be funded through existing working capital and future cash flows from operations.
At December 31, 2007, our outstanding contractual cash commitments were largely limited to our non-cancelable lease obligations, primarily relating to office facilities, as follows:
| | | | | | | | | | | | | | | |
| | | Payments Due by Period |
| | | Total | | Less than
1 Year | | 1-3
Years | | 3-5
Years | | More than
5 Years |
| | | (in thousands) |
Capital lease obligations | | $ | 832 | | $ | 650 | | $ | 163 | | $ | 10 | | $ | 9 |
Non-cancelable operating lease obligations | | $ | 23,946 | | $ | 4,096 | | $ | 12,017 | | $ | 6,332 | | $ | 1,501 |
Purchase obligations | | $ | 925 | | $ | 925 | | $ | — | | $ | — | | $ | — |
Our future capital requirements will depend on many factors, including our rate of revenue growth, the expansion of our selling and marketing activities, the timing and extent of research and development spending to support product development and enhancement efforts, costs associated with expansion into new territories or
49
markets, the timing of the introduction of new products and services and the enhancement of existing products and the continuing market acceptance of our products and services. To the extent that our short-term investments and existing cash, the availability under our line of credit and cash from operations are insufficient to fund our future activities and planned growth, we may need to raise additional funds through public or private equity or debt financings. Although we are currently not a party to any agreement or letter of intent with respect to potential investments in, or acquisitions of, complementary businesses, products or technologies, we may enter into these types of arrangements in the future, which could also require us to seek additional debt or equity financing. Additional funds may not be available on terms favorable to us or at all. Furthermore, although we cannot accurately anticipate the effect of inflation or foreign exchange markets on our operations, we do not believe these external economic forces have had, or are likely in the foreseeable future to have, a material impact on our results of operations.
At December 31, 2007, we did not have any relationships with unconsolidated entities or financial partnerships, such as entities often referred to as structured finance, special-purpose, or variable interest entities, which would have been established for the purpose of facilitating off-balance sheet arrangements or other contractually narrow or limited purposes. In addition, we did not engage in trading activities involving non-exchange traded contracts. As a result, we are not exposed to any financing, liquidity, market or credit risks that could arise if we had engaged in such relationships. We do not have material relationships and transactions with persons or entities that derive benefits from their non-independent relationship with us or our related parties except as disclosed in this report.
Recent Accounting Pronouncements
In September 2006, the FASB issued SFAS No. 157, “Fair Value Measurements,” which defines fair value, establishes a framework for consistently measuring fair value for accounting purposes and expands disclosure about fair value measurements. We are required to adopt SFAS 157 effective January 1, 2008 and the provisions of SFAS No. 157 will be applied prospectively as of that date. In February 2008, FASB Staff Position (“FSP”) 157-2 was issued, which delays the implementation of certain aspects of SFAS No. 157 to January 1, 2009. We are evaluating the impact, if any, the adoption of this statement will have on our results of operations, financial position or cash flows.
In February 2007, the FASB issued SFAS No. 159, “The Fair Value Option for Financial Assets and Financial Liabilities,” which permits entities to choose to measure many financial instruments and other items at fair value. SFAS No. 159 also includes an amendment to SFAS No. 115, “Accounting for Certain Investments in Debt and Equity Securities,” which applies to all entities with available-for-sale and trading securities. We are required to adopt SFAS 157 effective January 1, 2008 and are evaluating the impact, if any, the adoption of this statement will have on our results of operations, financial position or cash flows.
In December 2007, the FASB issued SFAS No. 141R, “Business Combinations,” which will significantly change the accounting for business combinations. Under SFAS 141R, an acquiring entity will be required to recognize all the assets acquired and liabilities assumed in a transaction at the acquisition-date fair value with limited exceptions. SFAS 141R will change the accounting treatment for certain specific items, including:
| | • | | acquisition costs will be generally expensed as incurred; |
| | • | | in-process research and development will be recorded at fair value as an indefinite-lived intangible asset at the acquisition date; |
| | • | | restructuring costs associated with a business combination will be generally expensed subsequent to the acquisition date; and |
| | • | | changes in deferred tax asset valuation allowances and income tax uncertainties after the acquisition date generally will affect income tax expense. |
50
SFAS 141R also includes a substantial number of new disclosure requirements. We will be required to adopt SFAS 141R prospectively to any business combinations for which the acquisition date is on or after January 1, 2009. Earlier adoption is prohibited. SFAS 141R will only have an effect on our financial statements in the event that we enter into business combinations subsequent to that date.
In December 2007, the FASB issued SFAS No. 160, “Noncontrolling Interests in Consolidated Financial Statements—An Amendment of ARB No. 51” (“SFAS 160”). SFAS 160 establishes new accounting and reporting standards for the noncontrolling interest in a subsidiary and for the deconsolidation of a subsidiary. Specifically, this statement requires the recognition of a noncontrolling interest (minority interest) as equity in the consolidated financial statements and separate from the parent’s equity. The amount of net income attributable to the noncontrolling interest will be included in consolidated net income on the face of the statement of operations. SFAS 160 clarifies that changes in a parent’s ownership interest in a subsidiary that do not result in deconsolidation are equity transactions if the parent retains its controlling financial interest. In addition, this statement requires that a parent recognize a gain or loss in net income when a subsidiary is deconsolidated. Such gain or loss will be measured using the fair value of the noncontrolling equity investment on the deconsolidation date. SFAS 160 also includes expanded disclosure requirements regarding the interests of the parent and its noncontrolling interest. We will be required to adopt SFAS 160 effective January 1, 2009. Earlier adoption is prohibited. We do not have a noncontrolling interest in one or more subsidiaries. Accordingly, we do not anticipate that the initial application of SFAS No. 160 will have an impact on us.
| Item 7A. | Quantitative and Qualitative Disclosures about Market Risk |
Although we currently bill for our products and services mostly in U.S. dollars, our financial results could be affected by factors such as changes in foreign currency rates or weak economic conditions in foreign markets. A strengthening of the dollar could make our products and services less competitive in foreign markets and therefore could reduce our revenues. We are billed by and pay substantially all of our vendors in U.S. dollars. In the future, an increased portion of our revenues and costs may be denominated in foreign currencies. To date, exchange rate fluctuations have had little impact on our operating results. We do not enter into derivative instrument transactions for trading or speculative purposes.
Our investment portfolio, consisting of fixed-rate financial institution obligations at December 31, 2007, is subject to interest rate risk. The fair value of our investment portfolio would not be significantly impacted by either a 100 basis point increase or decrease in interest rates due mainly to the short-term nature of the major portion of our investment portfolio.
| Item 8. | Financial Statements and Supplementary Data |
Our financial statements and supplementary data are included at the end of this report, beginning on page F-1.
| Item 9. | Changes in and Disagreements with Accountants on Accounting and Financial Disclosure |
None.
| Item 9A. | Controls and Procedures |
Guidance Software, Inc. maintain controls and procedures that are designed to ensure that information required to be disclosed in the reports we file or submit to the Securities and Exchange Commission (“SEC”) is recorded, processed, summarized, and reported within the time periods specified by the SEC’s rules and forms, and is accumulated and communicated to management, including the President and Chief Executive Officer and the Chief Financial Officer as appropriate, to allow timely decisions regarding required disclosure. Our management, under the supervision of and with the participation of our President and Chief Executive Officer
51
and our Chief Financial Officer, performed an evaluation to conclude with reasonable assurance that our disclosure controls and procedures were designed and operating effectively to report the information we are required to disclose in the reports we with the SEC on a timely basis. Based on that evaluation, our President and Chief Executive Officer and our Chief Financial Officer have concluded that as of December 31, 2007, our disclosure controls and procedures were effective.
There has been no change in our internal control over financial reporting during the fiscal quarter ended December 31, 2007 that has materially affected, or is reasonably likely to materially affect, our internal control over financial reporting.
Management Report on Internal Control over Financial Reporting
The management of Guidance Software, Inc. and subsidiaries (“Guidance”) is responsible for establishing and maintaining adequate internal control over financial reporting, as such term is defined in Exchange Act Rules 13a-15(f). Our internal control over financial reporting is designed to provide reasonable assurance regarding the reliability of financial reporting and the preparation of financial statements for external purposes in accordance with generally accepted accounting principles. Because of its inherent limitations, internal control over financial reporting may not prevent or detect misstatements. Also, projections of any evaluation of effectiveness to future periods are subject to the risk that controls may become inadequate because of changes in conditions, or that the degree of compliance with the policies or procedures may deteriorate.
Under the supervision and with the participation of management, including our President and Chief Executive Officer and our Chief Financial Officer, we conducted an evaluation of the design and operating effectiveness of our internal control over financial reporting as of December 31, 2007. In making this assessment, management used the framework set forth in Internal Control—Integrated Framework issued by the Committee of the Sponsoring Organizations of the Treadway Commission. Based on this evaluation, our President and Chief Executive Officer and our Chief Financial Officer concluded that our internal controls over financial reporting were effective as of December 31, 2007.
Our independent registered public accounting firm, Deloitte & Touche LLP, who audited Guidance’s consolidated financial statements included in this Form 10-K, has issued a report on Guidance’s internal control over financial reporting, which appears at page F-2 herein.
| Item 9B. | Other Information |
None.
52
PART III
| Item 10. | Directors, Executive Officers and Corporate Governance |
The information required by this item will be set forth in the Proxy Statement or Form 10-K/A and is incorporated in this report by reference.
| Item 11. | Executive Compensation |
The information required by this item will be set forth in the Proxy Statement or Form 10-K/A and is incorporated in this report by reference.
| Item 12. | Security Ownership of Certain Beneficial Owners and Management and Related Stockholder Matters |
The information required by this item will be set forth in the Proxy Statement or Form 10-K/A and is incorporated in this report by reference.
| Item 13. | Certain Relationships and Related Transactions, and Director Independence |
The information required by this item will be set forth in the Proxy Statement or Form 10-K/A and is incorporated in this report by reference.
| Item 14. | Principal Accountant Fees and Services |
The information required by this item will be set forth in the Proxy Statement or Form 10-K/A and is incorporated in this report by reference.
53
PART IV
| Item 15. | Exhibits and Financial Statement Schedules |
The following documents are filed as part of this report:
Financial statement schedules other than those listed above have been omitted because they are either not required, not applicable or the information is otherwise included.
| | (3) | List of exhibits required by Item 601 of Regulation S-K. See part (b) below. |
The following exhibits are filed or furnished herewith or are incorporated by reference to exhibits previously filed with the SEC (the original Exhibit number is included parenthetically).
| | |
Exhibit Number | | Description of Documents |
3.1(2) | | Amended and Restated Certificate of Incorporation of Guidance Software, Inc. (Exhibit 3.2) |
| |
3.2(2) | | Amended and Restated Bylaws of Guidance Software, Inc. (Exhibit 3.4) |
| |
4.1(1) | | Investor’s Rights Agreement, dated as of September 26, 2003, by and between Guidance Software, Inc. and Matthew Healey. (Exhibit 4.1) |
| |
10.1(1) | | Restated Lease Agreement, dated as of April 1, 2003, by and between Guidance Software, Inc. and The Walnut Plaza. (Exhibit 10.1) |
| |
10.2(2) | | Guidance Software, Inc. First Amended and Restated 2004 Equity Incentive Plan. (Exhibit 10.3) # |
| |
10.3(1) | | Guidance Software, Inc. Executive Retention and Severance Plan, dated as of April 20, 2005. (Exhibit 10.4) # |
| |
10.4(1) | | Employment Agreement, dated January 1, 2000, by and between Guidance Software, Inc. and John Patzakis. (Exhibit 10.5) # |
| |
10.5(1) | | Employment Agreement, dated December 16, 2002, by and between Guidance Software, Inc. and Frank Sansone. (Exhibit 10.7) # |
| |
10.6(4) | | Employment Agreement, dated December 6, 2007, by and between Guidance Software, Inc. and Victor Limongelli. (Exhibit 99.2) # |
10.7(4) | | At Will Employment Agreement Amendment, dated December 6, 2007, between Guidance Software, Inc. and John Colbert. (Exhibit 99.3) # |
54
| | |
Exhibit Number | | Description of Documents |
10.8 | | First Amendment to Employment Agreement, dated January 19, 2008, by and between Guidance Software, Inc. and Victor Limongelli.# |
| |
10.9 | | Amended and Restated Stock Option Agreement, dated January 19, 2008, by and between Guidance Software, Inc. and Victor Limongelli.# |
| |
10.10 | | Stock Option Agreement, dated January 19, 2008, by and between Guidance Software, Inc. and Victor Limongelli.# |
| |
10.11 | | Restricted Stock Cancellation Agreement, dated January 19, 2008, by and between Guidance Software, Inc. and Victor Limongelli.# |
| |
10.12 | | Restricted Stock Agreement, dated January 19, 2008, by and between Guidance Software, Inc. and Victor Limongelli.# |
| |
10.13 | | Amended and Restated Credit Agreement dated as of May 1, 2007, by and between Bank of the West and Guidance Software, Inc. |
| |
10.14(2) | | Form of Tax Matters Agreement. (Exhibit 10.10) |
| |
10.15(2) | | License Agreement, dated as of June 30, 2005, by and between Guidance Software, Inc. and Stellent Chicago Sales, Inc. (Exhibit 10.9)* |
| |
10.16(2) | | Form of Indemnification Agreement. (Exhibit 10.13) |
| |
10.17(3) | | Form of First Amended and Restated 2004 Equity Incentive Plan Stock Option Agreement. (Exhibit 10.14) |
| |
21.1(1) | | List of Subsidiaries. (Exhibit 21.1) |
| |
23.1 | | Consent of Deloitte & Touche LLP, Independent Registered Public Accounting Firm |
| |
31.1 | | Certification of Chief Executive Officer Pursuant to Section 302 of the Sarbanes-Oxley Act of 2002 |
| |
31.2 | | Certification of Chief Financial Officer Pursuant to Section 302 of the Sarbanes-Oxley Act of 2002 |
| |
32.1 | | Certification of Chief Executive Officer Pursuant to Section 906 of the Sarbanes-Oxley Act of 2002 † |
| |
32.2 | | Certification of Chief Financial Officer Pursuant to Section 906 of the Sarbanes-Oxley Act of 2002 † |
| (1) | Incorporated by reference to Guidance Software Inc.’s Form S-1 Registration Statement (File No. 333-137381) filed September 15, 2006. |
| (2) | Incorporated by reference to Amendment No. 4 to Guidance Software Inc.’s Form S-1 Registration Statement (on Form S-1/A) filed November 22, 2006. |
| (3) | Incorporated by reference to Amendment No. 6 to Guidance Software Inc.’s Form S-1 Registration Statement (on Form S-1/A) filed December 8, 2006. |
| (4) | Incorporated by reference to Guidance Software Inc.’s Current Report on Form 8-K dated December 6, 2007 and filed December 7, 2007. |
| # | Indicates management contract or compensatory plan. |
| * | Portions of the exhibit have been omitted pursuant to a request for confidential treatment and submitted separately to the SEC. |
| † | These certifications are being furnished solely to accompany this annual report pursuant to 18 U.S.C. Section 1350, and are not being filed for purposes of Section 18 of the Securities Exchange Act of 1934 and are not to be incorporated by reference into any filing of Guidance Software, Inc., whether made before or after the date hereof, regardless of any general incorporation language in such filing. |
55
INDEX TO CONSOLIDATED FINANCIAL STATEMENTS
F-1
REPORT OF INDEPENDENT REGISTERED
PUBLIC ACCOUNTING FIRM
To the Board of Directors and Stockholders of
Guidance Software, Inc.
Pasadena, California
We have audited the accompanying consolidated balance sheets of Guidance Software, Inc. and subsidiary (the “Company”) as of December 31, 2007 and 2006, and the related consolidated statements of operations, stockholders' equity, and cash flows for each of the three years in the period ended December 31, 2007. Our audits also included the financial statement schedule listed in the Index at Item 15. We also have audited the Company's internal control over financial reporting as of December 31, 2007, based on criteria established inInternal Control—Integrated Framework issued by the Committee of Sponsoring Organizations of the Treadway Commission. The Company's management is responsible for these financial statements and financial statement schedule, for maintaining effective internal control over financial reporting, and for its assessment of the effectiveness of internal control over financial reporting, included in the accompanying “Management’s Report on Internal Control over Financial Reporting.” Our responsibility is to express an opinion on these financial statements and financial statement schedule and an opinion on the Company's internal control over financial reporting based on our audits.
We conducted our audits in accordance with the standards of the Public Company Accounting Oversight Board (United States). Those standards require that we plan and perform the audit to obtain reasonable assurance about whether the financial statements are free of material misstatement and whether effective internal control over financial reporting was maintained in all material respects. Our audits of the financial statements included examining, on a test basis, evidence supporting the amounts and disclosures in the financial statements, assessing the accounting principles used and significant estimates made by management, and evaluating the overall financial statement presentation. Our audit of internal control over financial reporting included obtaining an understanding of internal control over financial reporting, assessing the risk that a material weakness exists, testing and evaluating the design and operating effectiveness of internal control based on the assessed risk. Our audits also included performing such other procedures as we considered necessary in the circumstances. We believe that our audits provide a reasonable basis for our opinions.
A company's internal control over financial reporting is a process designed by, or under the supervision of, the company's principal executive and principal financial officers, or persons performing similar functions, and effected by the company's board of directors, management, and other personnel to provide reasonable assurance regarding the reliability of financial reporting and the preparation of financial statements for external purposes in accordance with generally accepted accounting principles. A company's internal control over financial reporting includes those policies and procedures that (1) pertain to the maintenance of records that, in reasonable detail, accurately and fairly reflect the transactions and dispositions of the assets of the company; (2) provide reasonable assurance that transactions are recorded as necessary to permit preparation of financial statements in accordance with generally accepted accounting principles and that receipts and expenditures of the company are being made only in accordance with authorizations of management and directors of the company; and (3) provide reasonable assurance regarding prevention or timely detection of unauthorized acquisition, use, or disposition of the company's assets that could have a material effect on the financial statements.
Because of the inherent limitations of internal control over financial reporting, including the possibility of collusion or improper management override of controls, material misstatements due to error or fraud may not be prevented or detected on a timely basis. Also, projections of any evaluation of the effectiveness of the internal control over financial reporting to future periods are subject to the risk that the controls may become inadequate because of changes in conditions, or that the degree of compliance with the policies or procedures may deteriorate.
F-2
As discussed in Note 10 to the consolidated financial statements, the Company adopted Financial Accounting Standards Board Statement of Financial Accounting Standards No. 123(R), “Share-Based Payment,” in 2006.
As discussed in Note 5 to the consolidated financial statements, the Company adopted Financial Accounting Standards Board Interpretation No. 48, “Accounting for Uncertainty in Income Taxes—an interpretation of FASB Statement 109,” in 2007.
In our opinion, the consolidated financial statements referred to above present fairly, in all material respects, the financial position of Guidance Software, Inc. and subsidiaries as of December 31, 2007 and 2006, and the results of their operations and their cash flows for each of the three years in the period ended December 31, 2007, in conformity with accounting principles generally accepted in the United States of America. Also, in our opinion, such financial statement schedule, when considered in relation to the basic consolidated financial statements taken as a whole, presents fairly, in all material respects, the information set forth therein. Also, in our opinion, the Company maintained, in all material respects, effective internal control over financial reporting as of December 31, 2007, based on the criteria established inInternal Control—Integrated Frameworkissued by the Committee of Sponsoring Organizations of the Treadway Commission.
/s/ Deloitte & Touche LLP
Los Angeles, California
March 14, 2008
F-3
GUIDANCE SOFTWARE, INC.
CONSOLIDATED BALANCE SHEETS
(in thousands, except share data)
| | | | | | | | |
| | | December 31, | |
| | | 2006 | | | 2007 | |
ASSETS | | | | | | | | |
Current assets: | | | | | | | | |
Cash and cash equivalents | | $ | 8,041 | | | $ | 37,591 | |
Investments in marketable debt securities | | | 24,694 | | | | — | |
Trade receivables, net of allowance for doubtful accounts of $442 and $984, respectively | | | 17,513 | | | | 21,093 | |
Prepaid expenses, inventory and other current assets | | | 2,064 | | | | 2,863 | |
Deferred tax assets | | | — | | | | 1,386 | |
| | | | | | | | |
Total current assets | | | 52,312 | | | | 62,933 | |
Property and equipment, net | | | 6,526 | | | | 12,515 | |
Other assets | | | 507 | | | | 489 | |
| | | | | | | | |
Total assets | | $ | 59,345 | | | $ | 75,937 | |
| | | | | | | | |
LIABILITIES AND STOCKHOLDERS’ EQUITY | | | | | | | | |
Current liabilities: | | | | | | | | |
Accounts payable | | $ | 5,494 | | | $ | 4,595 | |
Accrued expenses | | | 3,974 | | | | 6,421 | |
Capital leases | | | 942 | | | | 586 | |
Deferred revenues | | | 18,123 | | | | 24,895 | |
| | | | | | | | |
Total current liabilities | | | 28,533 | | | | 36,497 | |
| | | | | | | | |
Long-term liabilities: | | | | | | | | |
Rent incentives | | | 1,537 | | | | 3,053 | |
Capital leases | | | 488 | | | | 185 | |
Deferred revenues | | | 2,098 | | | | 2,306 | |
| | | | | | | | |
Total long-term liabilities | | | 4,123 | | | | 5,544 | |
| | | | | | | | |
Commitments and contingencies (Notes 8 and 12) | | | | | | | | |
Stockholders’ equity: | | | | | | | | |
Preferred stock, $0.001 par value: 10,000,000 shares authorized; no shares issued or outstanding | | | — | | | | — | |
Common stock, $0.001 par value; 100,000,000 shares authorized; 22,167,000 and 23,010,000 shares issued and outstanding, respectively | | | 22 | | | | 23 | |
Additional paid-in capital | | | 36,330 | | | | 46,516 | |
Accumulated other comprehensive loss | | | (17 | ) | | | — | |
Accumulated deficit | | | (9,646 | ) | | | (12,643 | ) |
| | | | | | | | |
Total stockholders’ equity | | | 26,689 | | | | 33,896 | |
| | | | | | | | |
Total liabilities and stockholders’ equity | | $ | 59,345 | | | $ | 75,937 | |
| | | | | | | | |
The accompanying notes are an integral part of these consolidated financial statements.
F-4
GUIDANCE SOFTWARE, INC.
CONSOLIDATED STATEMENTS OF OPERATIONS
(in thousands, except per share data)
| | | | | | | | | | | | |
| | | Year Ended December 31, | |
| | | 2005 | | | 2006 | | | 2007 | |
Revenues: | | | | | | | | | | | | |
Product revenue | | $ | 23,138 | | | $ | 32,565 | | | $ | 44,314 | |
Services and maintenance revenue | | | 16,367 | | | | 23,300 | | | | 34,566 | |
| | | | | | | | | | | | |
Total revenues | | | 39,505 | | | | 55,865 | | | | 78,880 | |
| | | | | | | | | | | | |
Cost of revenues: | | | | | | | | | | | | |
Cost of product revenue | | | 2,202 | | | | 2,429 | | | | 2,754 | |
Cost of services and maintenance revenue | | | 9,146 | | | | 13,639 | | | | 19,280 | |
| | | | | | | | | | | | |
Total cost of revenues | | | 11,348 | | | | 16,068 | | | | 22,034 | |
| | | | | | | | | | | | |
Gross profit | | | 28,157 | | | | 39,797 | | | | 56,846 | |
| | | | | | | | | | | | |
Operating expenses: | | | | | | | | | | | | |
Selling and marketing | | | 15,691 | | | | 26,238 | | | | 32,964 | |
Research and development | | | 4,680 | | | | 7,113 | | | | 9,067 | |
General and administrative | | | 4,923 | | | | 7,840 | | | | 14,637 | |
Depreciation and amortization | | | 1,357 | | | | 1,823 | | | | 3,453 | |
| | | | | | | | | | | | |
Total operating expenses | | | 26,651 | | | | 43,014 | | | | 60,121 | |
| | | | | | | | | | | | |
Operating income (loss) | | | 1,506 | | | | (3,217 | ) | | | (3,275 | ) |
Other income and expense: | | | | | | | | | | | | |
Interest income | | | 54 | | | | 105 | | | | 1,463 | |
Interest expense | | | (81 | ) | | | (91 | ) | | | (107 | ) |
Other income, net | | | 150 | | | | 173 | | | | 130 | |
| | | | | | | | | | | | |
Income (loss) before income taxes | | | 1,629 | | | | (3,030 | ) | | | (1,789 | ) |
Income tax provision | | | 13 | | | | 39 | | | | 1,078 | |
| | | | | | | | | | | | |
Net income (loss) | | $ | 1,616 | | | $ | (3,069 | ) | | $ | (2,867 | ) |
| | | | | | | | | | | | |
Net income (loss) per share: | | | | | | | | | | | | |
Basic | | $ | 0.08 | | | $ | (0.16 | ) | | $ | (0.13 | ) |
Diluted | | $ | 0.08 | | | $ | (0.16 | ) | | $ | (0.13 | ) |
Weighted average number of shares used in per share calculation: | | | | | | | | | | | | |
Basic | | | 20,412 | | | | 19,530 | | | | 22,600 | |
Diluted | | | 21,023 | | | | 19,530 | | | | 22,600 | |
Pro forma net income (loss) data (unaudited): | | | | | | | | | | | | |
Income (loss) before income taxes | | $ | 1,629 | | | $ | (3,030 | ) | | | | |
Pro forma provision for income taxes | | | 343 | | | | 39 | | | | | |
| | | | | | | | | | | | |
Pro forma net income (loss) | | $ | 1,286 | | | $ | (3,069 | ) | | | | |
| | | | | | | | | | | | |
The accompanying notes are an integral part of these consolidated financial statements.
F-5
GUIDANCE SOFTWARE, INC.
CONSOLIDATED STATEMENTS OF STOCKHOLDERS’ EQUITY
(in thousands)
| | | | | | | | | | | | | | | | | | | | | | | | | | | | |
| | | Preferred Stock | | Common Stock | | | Additional
Paid-in
Capital | | | Accumulated
Other
Comprehensive
Income | | | Accumulated
Deficit | | | Total
Stockholders’
(Deficit)
Equity | |
| | | Shares | | Amount | | Shares | | | Amount | | | | | |
Balances at December 31, 2004 | | — | | $ | — | | 20,412 | | | $ | 20 | | | $ | 3,032 | | | $ | — | | | $ | (6,483 | ) | | $ | (3,431 | ) |
2005 net income | | — | | | — | | — | | | | — | | | | — | | | | — | | | | 1,616 | | | | 1,616 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Balances at December 31, 2005 | | — | | | — | | 20,412 | | | | 20 | | | | 3,032 | | | | — | | | | (4,867 | ) | | | (1,815 | ) |
Share-based compensation | | — | | | — | | — | | | | — | | | | 1,102 | | | | — | | | | — | | | | 1,102 | |
Exercise of stock options | | — | | | — | | 361 | | | | 1 | | | | 1,651 | | | | — | | | | — | | | | 1,652 | |
Exercise of warrant | | — | | | — | | 206 | | | | — | | | | — | | | | — | | | | — | | | | — | |
Donated capital, retired | | — | | | — | | (2,062 | ) | | | (2 | ) | | | 2 | | | | — | | | | — | | | | — | |
Stockholder distributions | | — | | | — | | — | | | | — | | | | — | | | | — | | | | (1,710 | ) | | | (1,710 | ) |
Issuance of common stock in public offering, net of issuance costs | | — | | | — | | 3,250 | | | | 3 | | | | 30,543 | | | | — | | | | — | | | | 30,546 | |
Unrealized loss on marketable debt securities, net of tax | | — | | | — | | — | | | | — | | | | — | | | | (17 | ) | | | — | | | | (17 | ) |
2006 net loss | | — | | | — | | — | | | | — | | | | — | | | | — | | | | (3,069 | ) | | | (3,069 | ) |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Balances at December 31, 2006 | | — | | | — | | 22,167 | | | | 22 | | | | 36,330 | | | | (17 | ) | | | (9,646 | ) | | | 26,689 | |
Share-based compensation | | — | | | — | | 40 | | | | — | | | | 4,345 | | | | — | | | | — | | | | 4,345 | |
Exercise of stock options | | — | | | — | | 803 | | | | 1 | | | | 3,970 | | | | — | | | | — | | | | 3,971 | |
Excess tax benefit from share-based compensation | | — | | | — | | — | | | | — | | | | 2,113 | | | | — | | | | — | | | | 2,113 | |
2006 public offering issuance costs | | — | | | — | | — | | | | — | | | | (242 | ) | | | — | | | | — | | | | (242 | ) |
Adoption of FIN 48 | | — | | | — | | — | | | | — | | | | — | | | | — | | | | (130 | ) | | | (130 | ) |
Realized gain on marketable debt securities, net of tax | | — | | | — | | — | | | | — | | | | — | | | | 17 | | | | — | | | | 17 | |
2007 net loss | | — | | | — | | — | | | | — | | | | — | | | | — | | | | (2,867 | ) | | | (2,867 | ) |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Balances at December 31, 2007 | | — | | $ | — | | 23,010 | | | $ | 23 | | | $ | 46,516 | | | $ | — | | | $ | (12,643 | ) | | $ | 33,896 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | |
The accompanying notes are an integral part of these consolidated financial statements.
F-6
GUIDANCE SOFTWARE, INC.
CONSOLIDATED STATEMENTS OF CASH FLOWS
(in thousands)
| | | | | | | | | | | | |
| | | Year Ended December 31, | |
| | | 2005 | | | 2006 | | | 2007 | |
Cash flows from operating activities: | | | | | | | | | | | | |
Net income (loss) | | $ | 1,616 | | | $ | (3,069 | ) | | $ | (2,867 | ) |
Adjustments to reconcile net income (loss) to net cash provided by (used in) operating activities: | | | | | | | | | | | | |
Depreciation and amortization | | | 1,357 | | | | 1,823 | | | | 3,453 | |
Provision for doubtful accounts | | | 97 | | | | 514 | | | | 947 | |
Share-based compensation | | | — | | | | 1,102 | | | | 4,345 | |
Excess tax benefit from share-based compensation | | | — | | | | — | | | | (2,113 | ) |
Deferred taxes | | | — | | | | — | | | | (1,386 | ) |
Loss on disposal of assets | | | — | | | | 93 | | | | 152 | |
Changes in operating assets and liabilities: | | | | | | | | | | | | |
Trade receivables | | | (3,822 | ) | | | (7,792 | ) | | | (4,527 | ) |
Prepaid expenses, inventory and other current assets | | | (243 | ) | | | (1,311 | ) | | | (156 | ) |
Accounts payable | | | 775 | | | | 1,476 | | | | (1,313 | ) |
Accrued expenses | | | 1,248 | | | | 459 | | | | 5,006 | |
Deferred revenues | | | 6,509 | | | | 3,902 | | | | 6,980 | |
| | | | | | | | | | | | |
Net cash provided by (used in) operating activities | | | 7,537 | | | | (2,803 | ) | | | 8,521 | |
| | | | | | | | | | | | |
Cash flows from investing activities: | | | | | | | | | | | | |
Purchase of marketable debt securities | | | — | | | | (24,711 | ) | | | (49,386 | ) |
Sale of marketable debt securities | | | — | | | | — | | | | 74,097 | |
Purchase of property and equipment | | | (1,011 | ) | | | (2,363 | ) | | | (8,627 | ) |
| | | | | | | | | | | | |
Net cash (used in) provided by investing activities | | | (1,011 | ) | | | (27,074 | ) | | | 16,084 | |
| | | | | | | | | | | | |
Cash flows from financing activities: | | | | | | | | | | | | |
Proceeds from the exercise of stock options | | | — | | | | 1,652 | | | | 3,971 | |
Excess tax benefit from share-based compensation | | | — | | | | — | | | | 2,113 | |
Proceeds from initial public offering, net of underwriters’ discount | | | — | | | | 34,759 | | | | — | |
Cash paid for offering expenses | | | (24 | ) | | | (3,757 | ) | | | (242 | ) |
Principal payments of capital lease obligations | | | (457 | ) | | | (582 | ) | | | (897 | ) |
Distributions to stockholders | | | — | | | | (1,710 | ) | | | — | |
Proceeds from term loan | | | — | | | | 900 | | | | — | |
Principal payments of term loan | | | — | | | | (900 | ) | | | — | |
Principal payments of line of credit | | | (792 | ) | | | — | | | | — | |
| | | | | | | | | | | | |
Net cash (used in) provided by financing activities | | | (1,273 | ) | | | 30,362 | | | | 4,945 | |
| | | | | | | | | | | | |
Net increase in cash and cash equivalents | | | 5,253 | | | | 485 | | | | 29,550 | |
Cash and cash equivalents, beginning of year | | | 2,303 | | | | 7,556 | | | | 8,041 | |
| | | | | | | | | | | | |
Cash and cash equivalents, end of year | | $ | 7,556 | | | $ | 8,041 | | | $ | 37,591 | |
| | | | | | | | | | | | |
Supplemental disclosures of cash flow information: | | | | | | | | | | | | |
Net cash paid during the year for: | | | | | | | | | | | | |
Interest | | $ | 82 | | | $ | 87 | | | $ | 74 | |
Income taxes | | $ | 13 | | | $ | 39 | | | $ | 227 | |
Non-cash activities: | | | | | | | | | | | | |
Capital lease obligations incurred to acquire assets | | $ | 537 | | | $ | 1,279 | | | $ | 238 | |
Purchase of equipment included in accounts payable | | $ | 97 | | | $ | 1,766 | | | $ | 414 | |
Rent incentives | | $ | — | | | $ | 195 | | | $ | 940 | |
Recognition of uncertain tax liabilities | | $ | — | | | $ | — | | | $ | 130 | |
Accrued offering costs included in accounts payable | | $ | — | | | $ | 432 | | | $ | — | |
The accompanying notes are an integral part of these consolidated financial statements.
F-7
GUIDANCE SOFTWARE, INC.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
| Note | 1. Description of the Business and Summary of Significant Accounting Policies |
General
Guidance Software, Inc. was incorporated in the state of California during 1997 and reincorporated in Delaware on December 11, 2006. Headquartered in Pasadena, California, we are a global provider of software solutions to conduct digital investigations. Our flagship product is EnCase® Enterprise, a comprehensive, network-enabled digital solution that enables corporations and government agencies to search, collect, preserve and analyze data across all of the servers, desktops and laptops that comprise their entire network from a single location. We also sell EnCase® Forensic, primarily for use by law enforcement and government agencies for collecting, preserving, analyzing and authenticating electronic computer forensic data for use in criminal and civil court proceedings. We complement our software offerings with a comprehensive array of professional and training services including technical support and maintenance services to help our customers implement our solutions, conduct investigations and train their IT professionals to effectively and efficiently use our software products.
Basis of Presentation
The accompanying consolidated financial statements have been prepared in accordance with accounting principles generally accepted in the United States (“GAAP”), and include the accounts of Guidance and its wholly owned subsidiaries. All significant intercompany accounts and transactions have been eliminated.
Use of Estimates and Assumptions
The preparation of financial statements in conformity with generally accepted accounting principles requires management to make estimates and judgments that affect the reported amounts of assets, liabilities, revenues and expenses, and related disclosure of contingent assets and liabilities. On an ongoing basis, we evaluate these estimates, including those related to revenue recognition, share-based compensation, bad debts, income taxes, commitments, contingencies and litigation. We base our estimates on historical experience and on various other assumptions that are believed to be reasonable under the circumstances. Actual results may differ from these estimates.
Cash and Cash Equivalents
We invest excess cash in money market funds and in highly liquid debt instruments of the U.S. government and its agencies. Highly liquid investments with stated maturities of three months or less from date of purchase are classified as cash equivalents.
Investments in Marketable Debt Securities
We account for our investments in marketable debt securities in accordance with Financial Accounting Standards Board (“FASB”) Statement No. 115, “Accounting for Certain Investments in Debt and Equity Securities”. We determine the appropriate classification of our investments in marketable debt securities at the time of purchase and reevaluate such designation at each balance sheet date. In response to changes in the availability of and the yield on alternative investments as well as liquidity requirements, we may sell these debt securities prior to their stated maturities. Accordingly, our marketable debt securities have been classified and accounted for as available for sale. These securities are carried at fair value, based on market quotes, with the unrealized gains and losses, net of taxes, reported as a component of stockholders’ equity. When the fair value of an investment declines below its original cost, we consider all available evidence to evaluate whether the decline
F-8
is other-than-temporary. Among other things, we consider the duration and extent of the decline and economic factors influencing the markets. To date, we have had no such other-than-temporary declines below cost. Any realized gains or losses on the sale of marketable securities are determined on a specific identification method and are reflected as a component of other expense.
Fair Value of Financial Instruments
The carrying amounts of cash equivalents, accounts receivable, and accounts payable approximate fair value because of the short-term maturities of these instruments. Based on borrowing rates currently available to us for borrowings with similar terms, the carrying values of our capital lease obligations also approximate fair value. Marketable debt securities are stated at fair value based on market quotes.
Trade Receivables
Trade receivables are carried at original invoice amount less an allowance for doubtful accounts. The allowance is established through a provision for bad debt expense. We determine the adequacy of this allowance by evaluating individual customer accounts receivable, through consideration of the customer’s financial condition, credit history and current economic conditions. In addition, we analyze our historical credit loss history and apply these loss rates to our current accounts receivable balances to verify the reasonableness of our allowance. Trade receivables are written off when deemed uncollectible. A trade receivable is generally considered past due if any portion of the receivable balance is outstanding for more than 45 days unless alternate terms are provided.
Inventory
Inventory is comprised of hardware and packaged software and valued at the lower of cost or market, using the first-in first-out method.
Property and Equipment
The cost of property and equipment, less applicable estimated residual values, is depreciated over the shorter of their estimated useful lives or the life of the capital lease (if applicable), on the straight-line method, from the date the specific asset is completed, installed, and ready for use, as follows:
| | |
| | | Estimated Useful Life (years) |
Leasehold improvements | | Shorter of life of asset or lease term |
Furniture and office equipment | | 5 |
Computer hardware and software | | 2-3 |
Also included in property and equipment is internally developed software. Internally used software, whether purchased or developed, is capitalized and amortized using the straight-line method over an estimated useful life of three years. In accordance with American Institute of Certified Public Accountants’ Statement of Position No. 98-1, “Accounting for the Costs of Computer Software Developed or Obtained for Internal Use”.
Impairment of Long-Lived Assets
We review our long-lived assets in accordance with Statement of Financial Accounting Standards (“SFAS”) No. 144, “Accounting for the Impairment or Disposal of Long-Lived Assets.” Long-lived assets are reviewed for impairment whenever events or changes in circumstances indicate that the carrying amount of an asset may not be recoverable. Recoverability of assets to be held and used is measured by a comparison of the carrying amount of the assets to future net cash flows (undiscounted and without interest) expected to be generated by the asset. If
F-9
such assets are considered to be impaired, the impairment to be recognized is measured by the amount by which the carrying amount of the assets exceeds the fair value of the assets. Assets to be disposed of are reported at the lower of the carrying amount or fair value less costs to sell. To date, we have not determined that any of our long-lived assets have been impaired.
Concentrations of Credit Risk
Financial instruments that potentially subject us to significant concentrations of credit risk consist primarily of cash and cash equivalents, marketable debt securities, and accounts receivable. We restrict our investments in cash and cash equivalents to financial institutions and government or federal agency securities and obligations of corporations with high credit standing. At December 31, 2007, the majority of our cash balances were held at financial institutions located in California, which accounts are insured by the Federal Deposit Insurance Corporation up to $100,000. Uninsured balances aggregate approximately $37.4 million as of December 31, 2007. At December 31, 2007, all of our cash equivalents consisted of financial institution obligations. We periodically perform credit evaluations of our customers and maintain reserves for potential losses on our accounts receivable and do not believe we are subject to concentrations of credit risk with respect to such receivables.
Revenue Recognition
We generate revenues principally from the sale of EnCase® Enterprise and EnCase® Forensic software products. These proprietary products are generally sold with one to three years of maintenance, which can be renewed at a stated renewal rate. Revenue associated with the sale of software licenses is referred to as product revenue and revenue associated with maintenance services is referred to as maintenance revenue. We also generate revenues from training courses and implementation and consulting services, in which we assist customers with the performance of digital investigations and train their IT professionals in the use of our software products, which we collectively refer to as services revenue. To a lesser extent, we also generate revenues from the sale of our Premium License Support Program (“PLSP”), Neutrino™ product and FastBloc® hardware, which are also included in product revenues.
We recognize revenue in accordance with current U.S. GAAP that have been prescribed for the software industry, which are substantially governed by AICPA Statement of Position No. 97-2 (“SOP 97-2”), “Software Revenue Recognition,” as amended and interpreted. While these pronouncements govern the basis for revenue recognition, significant judgment and the use of estimates are required in connection with the allocation of revenue between product revenue and services and maintenance revenue, as well as the amount of deferred revenue to be recognized in each accounting period.
Product revenue.The timing of product revenue recognition is dependent on the nature of the product sold. Product arrangements comprising multiple deliverables including software and hardware are generally categorized into one of the following:
| | • | | EnCase® Enterprise Solutions: Revenue associated with these arrangements, exclusive of amounts allocated to maintenance and other undelivered elements, for which we have vendor-specific objective evidence (“VSOE”) of fair value, is recognized upon delivery, provided that all other criteria for revenue recognition have been met. |
| | • | | EnCase® Forensic Solutions: Revenue from corporate customers, exclusive of amounts allocated to maintenance, for which we have VSOE of fair value, is recognized upon delivery, provided that all other criteria for revenue recognition have been met. We allocate Forensic product, services and maintenance revenue to government customers ratably over the longer of the contractual maintenance period (12 months) or the implied maintenance period (12-25 months) because VSOE of fair value of the maintenance element for governmental customers does not exist; the revenue allocation is based on estimated fair values of the various components. |
F-10
| | • | | Premium License Support Program (“PLSP”) Solutions: Revenue resulting from these arrangements is recognized ratably over the three-year contractual period beginning with the delivery of the first product, as the PLSP is a subscription arrangement entitling the customer to receive unspecified future products and post-contract customer support. |
| | • | | Neutrino™Solution: Our mobile device investigative solution is sold to Forensic customers with a related subscription covering future adapters for newly issued cell phones. Revenue is recognized over the related subscription period. For Enterprise customers, Neutrino revenue is recognized upon delivery, provided that all other criteria for revenue recognition have been met. Standard maintenance is charged to entitle customers to future cell phone adapters on an if-and-when available basis. |
| | • | | Hardware: Revenue associated with the sale of FastBloc® and other hardware is recognized upon shipment to the customer, provided that all other criteria for revenue recognition have been met. |
Services and Maintenance Revenue.The majority of our consulting and implementation services are performed under per hour, per disk drive or fixed fee arrangements. Revenue from such services is recognized as the services are provided or upon expiration of the contractual service period.
Training revenues are either recognized on a per-class basis upon a participant’s attendance or, for those customers who have subscribed to our Annual Training Passport program, revenue is recognized ratably over the annual period.
Revenue related to technical support and software updates on a when-and-if available basis is referred to as maintenance revenue. We recognize maintenance revenue ratably over the applicable maintenance period. We determine the amount of maintenance revenue to be deferred through reference to substantive maintenance renewal provisions contained in multiple element arrangements. We consider substantive maintenance provisions to be provisions where the cost of the maintenance renewal, stated in the contract with our customer as a percentage of the product fee, is comparable to the normal pricing for maintenance only renewals.
Revenue Recognition Criteria. Our basic revenue recognition criteria are as follows:
| | • | | Persuasive evidence of an arrangement: If we either enter into contracts or receive written purchase orders issued by a customer that legally bind us and the customer, we consider that as evidence of an arrangement. |
| | • | | Product delivery: We deem delivery of a product to have occurred when the title and risk of ownership have passed to the buyer. Services revenue is recognized as delivered. |
| | • | | Fixed or determinable fee: We consider the fee to be fixed or determinable if the fee is not subject to refund or adjustment and the payment terms are within normal established practices. If the fee is not fixed or determinable, we recognize revenue as amounts become due and payable provided all other revenue recognition criteria have been met. |
| | • | | Collection is deemed probable: We conduct a credit review for all significant transactions at the time of the arrangement to determine the credit-worthiness of the customer. Collection is deemed probable if we have a reasonable basis to expect that a customer will make pay amounts due under an arrangement as they become due. |
Deferred Revenue
Deferred revenue consists primarily of payments received in advance of delivery of products and services associated with the sale of our PLSP and EnCase® Forensic product offerings and service offerings. Deferred revenue also includes revenue related to undelivered elements that may or may not have been sold in conjunction with the sale of the EnCase® Enterprise product for which VSOE of the undelivered elements exists.
F-11
Research and Development
We maintain a research and development staff to develop new products and enhance or maintain existing products. In accordance with SFAS No. 86, “Accounting for the Costs of Computer Software to Be Sold, Leased, or Otherwise Marketed,” software costs are expensed as incurred until technological feasibility of the software is determined and the recovery of the cost can reasonably be expected, after which any additional costs are capitalized. To date, we have expensed all software development costs because the establishment of technological feasibility of products and their availability for sale has substantially coincided.
Commissions
We record sales commissions as earned, which is generally when the customer has been billed and collection is probable. Related revenue is recognized as described above.
Leases
We lease office facilities under operating leases and certain equipment under capital leases, and account for those leases in accordance with SFAS No. 13, “Accounting for Leases”. For operating leases that contain rent escalation or rent concession provisions, the total rent expense during the lease term is recorded on a straight-line basis over the term of the lease, with the difference between rent payments and the straight-line rent expense recorded as a deferred rent liability in the accompanying consolidated balance sheets.
Advertising Costs
Advertising costs are charged to operations as incurred and were not significant for any period presented.
Income Taxes
On December 11, 2006, we filed an election to revoke our S Corporation status. From and after the termination of S Corporation status, we have been treated for federal and state income tax purposes as a C Corporation under Subchapter C of the Internal Revenue Code and, as a result, are subject to federal and corporate income taxes and, accordingly, a provision for these and certain foreign taxes is included in the accompanying financial statements. Prior to revocation of our S Corporation status, we recorded no provisions or liabilities for federal income taxes as our stockholders reported their proportionate share of the company’s taxable income on their individual income tax returns.
Current income tax expense is the amount of income taxes paid or expected to be payable for the current year. Deferred income tax assets and liabilities are computed annually for differences between the financial statement and income tax bases of assets and liabilities. Such deferred income tax asset and liability computations are based on enacted tax laws and rates applicable to periods in which the differences are expected to reverse. If necessary, a valuation allowance is established to reduce deferred income tax assets to the amount expected to be realized.
Furthermore, we establish reserves for income taxes to address potential exposures involving tax positions that could be challenged by tax authorities in the future.
Foreign Currency Transactions
Assets and liabilities denominated in foreign currencies are remeasured at the balance sheet date. Resulting exchange rate gains or losses are included as a component of current period earnings. No material gains or losses have been incurred.
F-12
Commitments and Contingencies
We periodically evaluate all pending or threatened contingencies and any commitments, if any, that are reasonably likely to have a material adverse effect on its operations or financial position. In so doing, we assess the probability of an adverse outcome and determine if it is remote, reasonably possible or probable as defined in accordance with the provisions of SFAS No. 5, “Accounting for Contingencies.” If information available prior to the issuance of our financial statements indicates that it is probable that an asset had been impaired or a liability had been incurred at the date of the financial statements, and the amount of the loss, or the range of probable loss can be reasonably estimated, then such loss is accrued and charged to operations. If no accrual is made for a loss contingency because one or both of the conditions pursuant to SFAS No. 5 are not met, but the probability of an adverse outcome is at least reasonably possible, we have disclosed the nature of the contingency and provided an estimate of the possible loss or range of loss, or stated that such an estimate cannot be made.
Reclassifications
Certain prior year amounts have been re-classified to conform to the current year presentation. Theses reclassifications had no impact on operating or net (loss) income for the periods presented, and the amounts reclassified were not material.
Recent Accounting Pronouncements
In September 2006, the FASB issued SFAS No. 157, “Fair Value Measurements.” SFAS 157 does not require new fair value measurements but rather defines fair value, establishes a framework for measuring fair value and expands disclosure of fair value measurements. We are required to adopt SFAS 157 in the first quarter of 2008 for financial assets and liabilities and in the first quarter of 2009 for nonfinancial assets and liabilities. We do not expect SFAS 157 to have a material impact on our consolidated financial position and results of operations.
In February 2007, the FASB issued SFAS No. 159, “The Fair Value Option for Financial Assets and Liabilities—Including an amendment of FASB Statement No. 115.” SFAS 159 allows companies to elect fair-value measurement when an eligible financial asset or financial liability is initially recognized or when an event, such as a business combination, triggers a new basis of accounting for that financial asset or financial liability. The election must be applied to individual contracts, is irrevocable for every contract chosen to be measured at fair value, and must be applied to an entire contract, not to only specified risks, specific cash flows, or portions of that contract. Changes in the fair value of contracts elected to be measured at fair value are recognized in earnings each reporting period. We are required to adopt SFAS 159 in the first quarter of 2009 and are currently assessing the impact of SFAS 159 may have on its consolidated financial statements.
In December 2007, the FASB issued SFAS No. 141R, “Business Combinations,” which will significantly change the accounting for business combinations. Under SFAS 141R, an acquiring entity will be required to recognize all the assets acquired and liabilities assumed in a transaction at the acquisition-date fair value with limited exceptions. SFAS 141R will change the accounting treatment for certain specific items, including:
| | • | | acquisition costs will be generally expensed as incurred; |
| | • | | in-process research and development will be recorded at fair value as an indefinite-lived intangible asset at the acquisition date; |
| | • | | restructuring costs associated with a business combination will be generally expensed subsequent to the acquisition date; and |
| | • | | changes in deferred tax asset valuation allowances and income tax uncertainties after the acquisition date generally will affect income tax expense. |
SFAS 141R also includes a substantial number of new disclosure requirements. We will be required to adopt SFAS 141R prospectively to any business combinations for which the acquisition date is on or after January 1,
F-13
2009. Earlier adoption is prohibited. SFAS 141R will only have an effect on our financial statements in the event that we enter into business combinations subsequent to that date.
In December 2007, the FASB issued SFAS No. 160, “Noncontrolling Interests in Consolidated Financial Statements—An Amendment of ARB No. 51” (“SFAS 160”). SFAS 160 establishes new accounting and reporting standards for the noncontrolling interest in a subsidiary and for the deconsolidation of a subsidiary. Specifically, this statement requires the recognition of a noncontrolling interest (minority interest) as equity in the consolidated financial statements and separate from the parent’s equity. The amount of net income attributable to the noncontrolling interest will be included in consolidated net income on the face of the statement of operations. SFAS 160 clarifies that changes in a parent’s ownership interest in a subsidiary that do not result in deconsolidation are equity transactions if the parent retains its controlling financial interest. In addition, this statement requires that a parent recognize a gain or loss in net income when a subsidiary is deconsolidated. Such gain or loss will be measured using the fair value of the noncontrolling equity investment on the deconsolidation date. SFAS 160 also includes expanded disclosure requirements regarding the interests of the parent and its noncontrolling interest. We will be required to adopt SFAS 160 effective January 1, 2009. Earlier adoption is prohibited. We do not have a noncontrolling interest in one or more subsidiaries. Accordingly, we do not anticipate that the initial application of SFAS No. 160 will have an impact on us.
| Note | 2. Net Income (Loss) Per Share |
We calculate net income (loss) per share in accordance with SFAS No. 128, “Earnings Per Share.” Under SFAS No. 128, basic net income per common share is calculated by dividing net income by the weighted-average number of common shares outstanding during the reporting period. Diluted net income per share is calculated based on the weighted average number of common shares and dilutive potential common shares outstanding during the period. Dilutive potential common shares consist of the shares issuable upon the exercise of stock options and, in 2005, a warrant (see Note 11), and upon the vesting of nonvested stock awards under the treasury stock method. In net loss periods, basic net loss per share and diluted net loss per share are identical since the effect of potential common shares is anti-dilutive and therefore excluded. The following is a reconciliation of the numerators and denominators of the income (loss) per share computations for the periods presented (in thousands, except per share amounts):
| | | | | | | | | | | |
| | | Years Ended December 31, | |
| | | 2005 | | 2006 | | | 2007 | |
| | | (in thousands, except per share data) | |
Numerator: | | | | | | | | | | | |
Net income (loss) available to common stockholders | | $ | 1,616 | | $ | (3,069 | ) | | $ | (2,867 | ) |
| | | | | | | | | | | |
Denominator: | | | | | | | | | | | |
Basic weighted average shares outstanding | | | 20,412 | | | 19,530 | | | | 22,600 | |
Effect of dilutive stock options | | | 405 | | | — | | | | — | |
Effect of common stock warrant | | | 206 | | | — | | | | — | |
| | | | | | | | | | | |
Diluted weighted average shares outstanding | | | 21,023 | | | 19,530 | | | | 22,600 | |
| | | | | | | | | | | |
Net income (loss) per share: | | | | | | | | | | | |
Basic | | $ | 0.08 | | $ | (0.16 | ) | | $ | (0.13 | ) |
| | | | | | | | | | | |
Diluted | | $ | 0.08 | | $ | (0.16 | ) | | $ | (0.13 | ) |
| | | | | | | | | | | |
Anti-dilutive options | | | — | | | 1,511 | | | | 640 | |
Anti-dilutive nonvested share awards | | | — | | | — | | | | — | |
F-14
| Note | 3. Fair Value of Investments in Marketable Debt Securities |
We had investments classified as available-for-sale securities categorized as follows:
| | | | | | | |
| | | December 31, |
| | | 2006 | | | 2007 |
Type of security: | | | | | | | |
U.S. Government debt securities with maturities of less than one year | | $ | 24,694 | | | $ | — |
| | | | | | | |
Total investments in marketable debt securities | | $ | 24,694 | | | $ | — |
| | | | | | | |
Unrealized loss | | $ | (17 | ) | | $ | — |
| | | | | | | |
Available-for sale securities are accounted for at fair value. Unrealized gains and losses on these securities are reported as a separate component of stockholders’ equity. We incurred unrealized losses of $17,000 related to the above investments as of December 31, 2006. We determined that these investments were not deemed to be other-than-temporarily impaired. The length of time that the investments had been in a continuous unrealized loss position at December 31, 2006 was not significant as the investments were purchased subsequent to our initial public offering in December 2006.
| Note | 4. Property and Equipment |
Property and equipment, including assets held under capital leases, consist of the following:
| | | | | | | | |
| | | December 31, | |
| | | 2006 | | | 2007 | |
| | | (in thousands) | |
Leasehold improvements | | $ | 1,960 | | | $ | 7,144 | |
Computer hardware and software | | | 4,545 | | | | 6,149 | |
Office equipment and furniture | | | 1,160 | | | | 2,868 | |
Leased computers and office equipment | | | 2,180 | | | | 1,904 | |
Assets not yet placed in service | | | 1,429 | | | | 800 | |
| | | | | | | | |
| | | 11,274 | | | | 18,865 | |
Accumulated depreciation and amortization | | | (4,748 | ) | | | (6,350 | ) |
| | | | | | | | |
Property and equipment, net | | $ | 6,526 | | | $ | 12,515 | |
| | | | | | | | |
Depreciation and amortization expense related to property and equipment was $1,357,000, $1,823,000, and $3,453,000 for the years ended December 31, 2005, 2006, and 2007, respectively.
On December 11, 2006, we terminated our status as an S Corporation for U.S. federal income tax purposes. From and after the termination of S Corporation status, we have been subject to federal, state and foreign corporate income taxes. In December 2006, as a result of this termination, we recorded additional deferred tax assets, net in the amount of $2,261,000, comprised primarily of timing differences related to deferred revenues and accrued expenses. Concurrently, the valuation allowance was increased by $2,261,000 to reduce the carrying value of the deferred tax assets, net.
F-15
The provision for income taxes consists of the following:
| | | | | | | | | | | | |
| | | Year Ended December 31, | |
| | | 2005 | | | 2006 | | | 2007 | |
| | | (in thousands) | |
Current: | | | | | | | | | | | | |
Federal | | $ | — | | | $ | — | | | $ | 2,062 | |
State | | | 13 | | | | 39 | | | | 287 | |
Foreign | | | — | | | | — | | | | 115 | |
| | | | | | | | | | | | |
| | | 13 | | | | 39 | | | | 2,464 | |
Deferred: | | | | | | | | | | | | |
Federal | | | — | | | | (2,207 | ) | | | (2,318 | ) |
State | | | (45 | ) | | | (286 | ) | | | (298 | ) |
| | | | | | | | | | | | |
| | | (45 | ) | | | (2,493 | ) | | | (2,616 | ) |
Valuation allowance | | | 45 | | | | 2,493 | | | | 1,230 | |
| | | | | | | | | | | | |
| | $ | 13 | | | $ | 39 | | | $ | 1,078 | |
| | | | | | | | | | | | |
A reconciliation of the provision for income taxes at the federal statutory rate compared to our actual tax provision is as follows:
| | | | | | | | |
| | | Year Ended December 31, | |
| | | 2006 | | | 2007 | |
| | | (in thousands) | |
Federal income tax benefit at statutory rate | | $ | (1,031 | ) | | $ | (608 | ) |
State income taxes, net of federal benefit | | | (146 | ) | | | (218 | ) |
Foreign income taxes, net of federal benefit | | | — | | | | 76 | |
Research and development tax credits | | | — | | | | (365 | ) |
Nondeductible share-based compensation | | | — | | | | 786 | |
Nondeductible meal and entertainment expense | | | — | | | | 114 | |
Change in valuation allowance affecting income tax expense | | | 181 | | | | 1,230 | |
Tax benefit not realizable due to S-Corporation status | | | 974 | | | | — | |
Recognition of deferred tax assets upon termination of S-Corporation status | | | (2,261 | ) | | | — | |
Valuation allowance increased upon termination of S-Corporation status | | | 2,261 | | | | — | |
Other, net | | | 61 | | | | 63 | |
| | | | | | | | |
| | $ | 39 | | | $ | 1,078 | |
| | | | | | | | |
F-16
The components of deferred tax assets and liabilities are as follows:
| | | | | | | | |
| | | December 31, | |
| | | 2006 | | | 2007 | |
| | | (in thousands) | |
Deferred tax assets: | | | | | | | | |
Accrued expenses | | $ | 1,156 | | | $ | 1,808 | |
Deferred revenue | | | 1,735 | | | | 2,718 | |
Other accruals and reserves | | | 58 | | | | — | |
Share-based compensation | | | — | | | | 593 | |
Tax credits | | | 23 | | | | 428 | |
Net operating losses | | | 98 | | | | — | |
| | | | | | | | |
Total deferred tax assets | | | 3,070 | | | | 5,547 | |
Deferred tax liability: | | | | | | | | |
Depreciable assets | | | (291 | ) | | | (152 | ) |
| | | | | | | | |
Net deferred tax assets prior to valuation allowance | | | 2,779 | | | | 5,395 | |
Valuation allowance | | | (2,779 | ) | | | (4,009 | ) |
| | | | | | | | |
Net deferred tax assets | | $ | — | | | $ | 1,386 | |
| | | | | | | | |
In assessing the realizability of the net deferred tax assets, we consider whether it is more likely than not that some or all of the deferred tax assets will not be realized. The ultimate realization of deferred tax assets depends upon either the generation of future taxable income during the periods in which those temporary differences become deductible or the carryback of losses to recover income taxes previously paid during the carryback period.
At December 31, 2007, we had no federal or state net operating loss carryforwards remaining. At December 31, 2007 we had federal and state research and development credit carryforwards of approximately $213,000 and $215,000, respectively. The federal research and development credit carryforwards begin to expire in 2026, if not previously utilized. The state research and development credit carryforwards have no expiration date.
We file income tax returns in the U.S. federal jurisdiction, and various state and foreign jurisdictions. We adopted the provisions of FASB Interpretation No. 48, “Accounting for Uncertainty in Income Taxes—an interpretation of FASB Statement No. 109” (“FIN 48”), on January 1, 2007 and, accordingly, performed a comprehensive review of our uncertain tax positions as of that date. In this regard, an uncertain tax position represents our expected treatment of a tax position taken in a filed tax return, or planned to be taken in a future tax return, that has not been reflected in measuring income tax expense for financial reporting purposes. As a result of this review, we recorded uncertain tax positions by recognizing additional liabilities totaling $130,000 through a charge to accumulated deficit. A reconciliation of our total unrecognized tax benefits at December 31, 2007 follows (in thousands):
| | | | |
Balance at January 1, 2007 | | $ | 130 | |
Additions based on tax positions in the current period | | | — | |
Additions based on tax positions in prior periods | | | — | |
Reductions based on tax positions in prior periods | | | (117 | ) |
Settlements | | | — | |
Expiration of statutes | | | — | |
| | | | |
Balance at December 31, 2007 | | $ | 13 | |
| | | | |
F-17
During the year ended December 31, 2007, our liability for uncertain tax positions was reduced to $13,000 upon payment of additional taxes to a foreign tax jurisdiction. If our remaining positions are sustained by the taxing authorities in our favor, the entire remaining amounts previously recorded as liabilities would reduce our income tax provision in the period the tax position is sustained. We do not expect there to be any material changes to the estimated amount of liability associated with our uncertain tax positions over the next twelve months. The tax years 2006 to 2007 remain subject to review by the taxing authorities in several jurisdictions.
The liability for uncertain tax positions is recorded in accrued expenses in our consolidated balance sheets. We recognize interest and penalties related to uncertain tax positions in the income tax provision. Interest and penalties are computed based upon the difference between our uncertain tax positions under FIN 48 and the amount deducted or expected to be deducted in our tax returns. During 2007, amounts accrued for interest and penalties were insignificant.
We maintain a $3,000,000 revolving line of credit with a bank which expires on October 31, 2008. Borrowings under this line of credit would bear interest at a rate equal to the bank’s prime rate minus 0.75% or the bank’s LIBOR plus 1.50%, would be due on the expiration date of the facility and be collateralized by substantially all our assets. The facility requires us to maintain cash, cash equivalents, and marketable securities of not less than $10 million, not to allow a cumulative net loss (excluding non-cash share-based compensation) in excess of $4 million during any one fiscal year and limits additional indebtedness to $2,000,000. As of December 31, 2007, we were in compliance with the covenants associated with the revolving line of credit. At December 31, 2007 and 2006, no amounts were outstanding under the line.
In November 2006, we entered into an irrevocable standby letter-of-credit with a bank for $225,000 which expires in November 2015. This letter-of-credit provides collateral for office space we lease in New York, New York.
| Note | 7. Related Party Transactions |
Certain of our stockholders guarantee substantially all of the obligations due under our capital and operating leases (Note 8).
F-18
We lease certain of our operating facilities under non-cancellable operating leases extending through 2015 and also lease certain equipment under capital leases extending through 2015. The Company also subleases certain of its facilities under non-cancellable operating leases. The present value of the remaining future minimum lease payments under capital leases is recorded in the consolidated balance sheets. The following is a schedule of future minimum lease payments under capital leases, operating leases and future non-cancellable sublease income (in thousands):
| | | | | | | | | | | | | | |
Years Ending December 31, | | Future Minimum
Capital Lease
Payments | | | Future Minimum
Operating Lease
Payments | | Future
Non-Cancellable
Sublease Income | | | Net Future
Minimum Lease
Payments |
| | | (in thousands) |
2008 | | $ | 650 | | | $ | 4,096 | | $ | (141 | ) | | $ | 4,605 |
2009 | | | 127 | | | | 4,008 | | | (110 | ) | | | 4,025 |
2010 | | | 31 | | | | 3,951 | | | — | | | | 3,982 |
2011 | | | 5 | | | | 4,058 | | | — | | | | 4,063 |
2012 | | | 5 | | | | 3,586 | | | — | | | | 3,591 |
Thereafter | | | 14 | | | | 4,247 | | | — | | | | 4,261 |
| | | | | | | | | | | | | | |
Total | | | 832 | | | $ | 23,946 | | $ | (251 | ) | | $ | 24,527 |
| | | | | | | | | | | | | | |
Less amounts representing interest (6.75%—16.3%) | | | (61 | ) | | | | | | | | | | |
| | | | | | | | | | | | | | |
| | $ | 771 | | | | | | | | | | | |
| | | | | | | | | | | | | | |
Rent expense related to operating leases for 2005, 2006 and 2007 was $1,592,000, $2,543,000 and $4,110,000, respectively. Sublease rental income in each of the three years 2005, 2006 and 2007 was approximately $125,000. Substantially all of the capital leases and one operating lease are guaranteed by certain stockholders of the Company.
| Note | 9. Equity Incentive Plan and Employee Benefit Plan |
In 2004, our Board of Directors and stockholders approved the 2004 Equity Incentive Plan (the “Plan”). A total of 2,062,000 shares of common stock was initially authorized and reserved for issuance under the Plan in the form of incentive and non-qualified stock options and nonvested share awards (commonly referred to as “restricted stock”). The Plan was amended in 2005 to increase the number of shares available for issuance to 3,977,000. On May 3, 2006, the Board of Directors and stockholders approved increases in the shares available for issuance under the Plan by an additional 1,127,000 shares on May 3, 2006, and an additional 828,000 shares on each of January 1, 2007, 2008 and 2009. Employees, officers and directors are eligible under the Plan, which is administered by the Board of Directors, who determines the terms and conditions of each grant. The terms of the options granted under the Plan are determined at the time of grant, and generally vest 25% annually over a four-year service period and typically must be exercised within 10 years from the date of grant.
In December 2007, we awarded our new Chief Executive Officer with a 500,000 share grant that will vest in 25% increments in the event our common stock price increases to specified levels during his continued employment over the grant’s 10 year term. This grant depleted the authorized option pool. Accordingly, approximately 300,000 options were issued outside of the Plan. Subsequent to December 31, 2007, we amended this grant, effectively cancelling the non-Plan options and reissuing them under the 2004 Equity Incentive Plan (Note 15).
At December 31, 2007, there were no shares available for option or nonvested share award grants under the Plan.
F-19
Stock Options
A summary of stock option activity follows:
| | | | | | | | | |
| | | Number of
Options | | | Weighted
Average
Exercise
Price | | Range of
Exercise Prices |
Outstanding, December 31, 2004 | | 1,462,000 | | | $ | 4.54 | | $ | 4.54 |
Granted | | 1,971,000 | | | | 4.84 | | | 4.54 - 6.32 |
Exercised | | — | | | | — | | | — |
Forfeited or expired | | (104,000 | ) | | | 4.73 | | | 4.54 - 6.32 |
| | | | | | | | | |
Outstanding, December 31, 2005 | | 3,329,000 | | | | 4.71 | | | 4.54 -6.32 |
Granted | | 1,346,000 | | | | 9.29 | | | 6.37 -11.90 |
Exercised | | (360,000 | ) | | | 4.58 | | | 4.54 -6.17 |
Forfeited or expired | | (411,000 | ) | | | 5.02 | | | 4.54 -11.90 |
| | | | | | | | | |
Outstanding, December 31, 2006 | | 3,904,000 | | | | 6.26 | | | 4.54 -11.90 |
Granted | | 1,957,000 | | | | 12.95 | | | 11.45 - 14.32 |
Exercised | | (803,000 | ) | | | 4.95 | | | 4.54 -11.90 |
Forfeited or expired | | (505,000 | ) | | | 8.62 | | | 4.54 -14.32 |
| | | | | | | | | |
Outstanding, December 31, 2007 | | 4,553,000 | | | $ | 9.11 | | $ | 4.54 -14.32 |
| | | | | | | | | |
A summary of non-vested shares is presented below:
| | | |
| | | Number of
Options | |
Nonvested options as of December 31, 2006 | | 2,979,000 | |
Granted | | 1,957,000 | |
Vested | | (906,000 | ) |
Forfeited or expired | | (505,000 | ) |
| | | |
Nonvested options as of December 31, 2007 | | 3,525,000 | |
| | | |
F-20
The following tables summarize information about stock options outstanding at December 31, 2007:
| | | | | | | | | | | | | | | | | | | | |
| | | Options Outstanding | | Options Exercisable |
Exercise Price | | Number of
Options | | Weighted
Average
Remaining
Contract
Life (Years) | | Weighted
Average
Exercise Price | | Intrinsic Value | | Number of
Options | | Weighted
Average
Remaining
Contract Life
(Years) | | Weighted
Average
Exercise Price | | Intrinsic Value |
$ 4.54 – 5.34 | | 1,548,000 | | 6.87 | | $ | 4.61 | | $ | 14,472,000 | | 727,000 | | 6.75 | | $ | 4.60 | | $ | 6,806,000 |
$ 6.17 – 7.64 | | 526,000 | | 8.04 | | | 6.39 | | | 3,980,000 | | 150,000 | | 7.97 | | | 6.35 | | | 1,143,000 |
$10.75 – 11.90 | | 1,073,000 | | 9.04 | | | 11.21 | | | 2,946,000 | | 151,000 | | 8.66 | | | 11.06 | | | 437,000 |
$12.80 – 14.32 | | 1,406,000 | | 9.74 | | | 13.47 | | | 899,000 | | — | | — | | | — | | | — |
| | | | | | | | | | | | | | | | | | | | |
| | 4,553,000 | | 8.40 | | $ | 9.11 | | $ | 22,297,000 | | 1,028,000 | | 7.21 | | $ | 5.80 | | $ | 8,386,000 |
| | | | | | | | | | | | | | | | | | | | |
| | | | | | | | | | |
| | | Options Expected to Vest |
Exercise Price | | Number of
Options | | Weighted Average
Remaining
Contract
Life (Years) | | Weighted Average
Exercise Price | | Intrinsic Value |
$ 4.54 – 5.34 | | 709,000 | | 6.88 | | $ | 4.62 | | $ | 6,623,000 |
$ 6.17 – 7.64 | | 325,000 | | 8.06 | | | 6.41 | | | 2,452,000 |
$ 10.75 – 11.90 | | 796,000 | | 9.10 | | | 11.24 | | | 2,167,000 |
$ 12.80 – 14.32 | | 1,283,000 | | 9.75 | | | 13.44 | | | 855,000 |
| | | | | | | | | | |
| | 3,113,000 | | 8.75 | | $ | 10.13 | | $ | 12,097,000 |
| | | | | | | | | | |
We define in-the-money options at December 31, 2007 as options with exercise prices lower than the $13.96 fair market value of our common stock on that date. The aggregate intrinsic value of options outstanding at December 31, 2007 is calculated as the difference between the exercise price of the underlying options and the fair market value of our common stock for the 3,952,000 options that were in-the-money at that date, of which 1,028,000 were exercisable. The total intrinsic value of stock options exercised, determined as of the date of exercise, was zero, $2,320,000 and $6,210,000 during the years 2005, 2006 and 2007, respectively.
The total fair value of options vested during 2007 was $1,988,000; options vesting during 2006 and 2005 were granted prior to our adoption of FAS 123R and did not have an estimable fair value.
F-21
Nonvested Share Awards
During 2007, we began issuing nonvested share awards (commonly referred to as “restricted stock”) to certain executives and employees under the Plan. Compensation expense for such awards, based on the fair market value of the awards on the grant date, is recorded during the vesting period. The first awards of nonvested share awards were made in February 2007, when approximately 40,000 shares were granted with three-month vesting periods. Later in 2007, additional grants were awarded with four-year vesting periods. A summary of nonvested share awards activity follows:
| | | | | | | | | |
| | | Number of
Shares | | | Weighted
Average
Fair Value | | Range of
Fair Values |
Outstanding, December 31, 2006 | | — | | | $ | — | | $ | — |
Granted | | 546,000 | | | | 13.97 | | | 12.80 – 14.32 |
Vested and issued | | (40,000 | ) | | | 13.41 | | | 12.87 – 13.66 |
Forfeited | | (7,000 | ) | | | 14.12 | | | 12.94 – 14.32 |
| | | | | | | | | |
Outstanding, December 31, 2007 | | 499,000 | | | $ | 14.02 | | $ | 12.80 – 14.32 |
| | | | | | | | | |
The following table summarizes information about nonvested share awards outstanding at December 31, 2007:
| | | | | | | | |
| | | Nonvested Share Awards Outstanding | | Nonvested Share Awards Expected to Vest |
Fair Value | | Number of
Shares | | Weighted Average
Remaining
Vesting Period
(Years) | | Number of
Shares | | Weighted Average
Remaining
Vesting Period
(Years) |
$12.80 | | 100,000 | | 3.93 | | 100,000 | | 3.93 |
$14.32 | | 399,000 | | 3.84 | | 345,000 | | 3.84 |
| | | | | | | | |
| | 499,000 | | 3.85 | | 445,000 | | 3.86 |
| | | | | | | | |
During 2007, the total fair value of shares vested and issued under such grants during 2007 was $535,000.
We experienced disqualifying dispositions of incentive stock options during the year ended December 31, 2007. Disqualifying dispositions result in a tax deduction in our corporate tax return equal to the intrinsic value of the option at exercise. To the extent we have previously recorded share-based compensation expense related to disqualifying dispositions of incentive stock options, we record the benefit from the disqualifying dispositions as a reduction in our income tax provision.
As a result of the disqualifying dispositions of incentive stock options during 2007, the $2.1 million tax benefit related to options that were granted prior to the adoption of SFAS No. 123R (“SFAS 123R”), “Share-Based Payment” (Note 10) was recorded as a reduction of our current year tax liability and an increase to additional paid-in capital. The tax benefit related to the exercise of options granted subsequent to the adoption so SFAS 123R was recorded as a reduction of current year tax expense and the tax liability. There were no material disqualifying dispositions for 2005 or 2006.
We have a 401(k) plan that allows all full-time eligible employees to contribute up to 15% of their annual compensation, subject to certain limitations. We match 50% of the first 6% for each employee’s contribution, and may, at our discretion, make additional contributions regardless of profitability. We recorded contribution related expense of $267,000, $425,000 and $551,000 in the years 2005, 2006, and 2007, respectively.
F-22
In April 2005, the Board of Directors and stockholders approved the Executive Retention and Severance Plan (“ERS”) to promote the interests of our business and stockholders by attracting and retaining executive personnel and other key employees. The ERS is designed to provide certain executive personnel with specified compensation and benefits in the event of a change in control, as defined in the ERS, or termination of employment under certain circumstances. At December 31, 2007 total potential severance obligations in connection with these employment contracts amounted to approximately $2.6 million, which is not recorded as a liability in the accompanying consolidated balance sheets.
We have a profit sharing plan for our employees whereby eligible employees may receive a discretionary amount of operating profits as defined. The amounts expensed under this plan were $1,189,000, $312,000 and $945,000 for 2005, 2006 and 2007, respectively.
| Note | 10. Share-Based Compensation |
Effective January 1, 2006, we adopted SFAS No. 123R (“SFAS 123R”), “Share-Based Payment.” Prior to the adoption of SFAS 123R, we used the minimum-value method afforded by the SFAS No. 123, “Accounting for Stock-Based Compensation,” for disclosure purposes. Since all options granted prior to January 1, 2006 were granted at exercise prices that were equal to the fair market value of the underlying stock on the date of the grant, no share-based compensation for stock options was recorded in the accompanying financial statements prior to 2006 and we are not required to record compensation expense for stock options granted prior to January 1, 2006 unless the terms of those options are subsequently modified. We adopted SFAS 123R using the prospective transition method and, accordingly, since adoption, we recognize share-based compensation expense for all share-based awards granted after January 1, 2006. Under that transition method, results for prior periods have not been restated.
With the exception of one option granted in December 2007 with market-based vesting conditions, discussed further below, the fair values of awards granted under the Plan were estimated at the date of grant using the Black-Scholes option pricing model and the following weighted average assumptions:
| | | | | | | | |
| | | Year Ended December 31, | |
| | | 2006 | | | 2007 | |
Risk-free interest rate | | | 4.60 | % | | | 4.37 | % |
Dividend yield | | | — | % | | | — | % |
Expected life (years) | | | 6.25 | | | | 6.25 | |
Volatility | | | 72.8 | % | | | 61.3 | % |
Weighted average grant date fair value | | $ | 6.67 | | | $ | 7.88 | |
The Securities and Exchange Commission (“SEC”) has issued Staff Accounting Bulletin (“SAB”) Topics No. 107 and No. 110 which provide guidance on the implementation of SFAS 123R. We applied the principles of SAB 107 in conjunction with adoption of SFAS 123R. The volatility of our common stock is estimated at the date of grant based on a weighted-average of the implied volatility of publicly traded 30-day to 270-day options on the common stock of a select peer group of similar companies (“Similar Companies”), the historical volatility of the common stock of Similar Companies and, beginning in late 2007, the historical volatility of our common stock, consistent with the requirements of SFAS 123R and SAB 107. The risk-free interest rate that was used in the Black-Scholes option valuation model is based on the implied yield in effect at the time of each option grant, based on U.S. Treasury zero-coupon issues with equivalent remaining terms. We use an expected dividend yield of zero in the Black-Scholes option valuation model, as we have no intention of paying any cash dividends on our common stock in the foreseeable future. SFAS 123R requires us to estimate forfeitures at the time of grant and revise those estimates in subsequent periods if actual forfeitures differ from those estimates. We use historical data to estimate pre-vesting option forfeitures and record share-based compensation expense only for those awards that are expected to vest. We generally amortize share-based compensation on a straight-line basis over the requisite service period of the awards, which is generally the vesting period. The expected term (life) of
F-23
all stock option awards has been calculated using the “simplified method” as defined by SAB 107 and SAB 110 because, due to the limited time our common stock has been publicly traded, we lack sufficient historical data to provide a reasonable basis to estimate the expected term of these options.
On December 6, 2007, we granted our President and Chief Executive Officer an option to purchase 500,000 shares of our common stock at the price of $12.80 per share which vests, in 25% increments, only upon attainment of specified market-based conditions tied to the market value of our common stock. Under the provisions of SFAS 123R, the fair value of share-based grants with a market vesting condition must be modeled and valued with a path-dependent valuation technique. Accordingly, we estimate the value of such awards using the Monte Carlo binomial simulation model. The primary assumptions used in the model are volatility, a risk-free interest rate, starting stock price, transferability restrictions and the terms of the award, as follows:
| | • | | Risk-free interest rate of 3.98%; |
| | • | | Dividend yield of zero; |
| | • | | Expected option life of 10 years; and |
| | • | | Volatility of the expected market price of our common stock over that term of 53.9%. |
Using these assumptions and inputs, we estimated that the weighted average grant date fair value of this award was $5.68 per option, with derived service periods ranging from 15 to 32 months for the four performance levels, and averaging 24 months. Under FAS 123R, the calculated $2.8 million fair value of this award must be recognized as expense over a weighted average period of approximately two years whether the market conditions are met or not so long as the grantee meets the service condition.
In June 2007, under the terms of an employment agreement and a separation agreement with one of our former executives, we accelerated vesting of options held by the former executive permitting him to purchase approximately 23,500 of previously unvested shares of our common stock within 30 days of termination. The modification of the award resulted in $192,000 in compensation expense during 2007.
The following table summarizes the share-based compensation expense we recorded in accordance with the provisions of FAS 123R:
| | | | | | |
| | | December 31, |
| | | 2006 | | 2007 |
| | | (in thousands) |
Amortization of fair value of stock option grants | | $ | 1,102 | | $ | 3,382 |
Nonvested share awards | | | — | | | 771 |
Acceleration of vesting period for former employee | | | — | | | 192 |
| | | | | | |
Share-based compensation expense | | $ | 1,102 | | $ | 4,345 |
| | | | | | |
As of December 31, 2007, there was $22.4 million of total unrecognized compensation cost related to non-vested share-based compensation that is expected to be recognized over a weighted-average period of 3.23 years. We expect to record approximately $8.0 million in share-based compensation in 2008 related to options and nonvested share awards outstanding at December 31, 2007.
| Note | 11. Stockholders’ Equity |
In December 2006, we completed our initial public offering through the sale of 5,750,000 shares of common stock at $11.50 per share. Of the shares sold in the initial public offering, 3,250,000 shares were primary shares sold by the company and 2,500,000 shares were secondary and sold by selling stockholders, including the underwriters’ exercise of an over-allotment option to purchase up to 750,000 shares from a selling stockholder. Total gross proceeds of $37,375,000 were raised in the initial public offering. After deducting the underwriting
F-24
discount of $2,617,000, we received net proceeds of $34,759,000. We incurred $4,213,000 in costs related to the initial public offering which were recorded as a reduction of additional paid in capital.
In conjunction with our re-incorporation in the State of Delaware in December 2006 (Note 1), the amended and restated certificate of incorporation authorizes the Board of Directors, subject to limitations prescribed by law, to issue up to 10,000,000 shares of preferred stock in one or more series without approval by common shareholders. The rights, preferences, privileges, and restrictions of any such shares will be established by the Board of Directors at the time of issuance. No preferred stock was outstanding at December 31, 2007 or 2006.
In May 2006, the company’s founding stockholders contributed 2,062,000 common shares to the company. The contribution was made as a result of a commitment by the founding stockholders, upon establishment of the 2004 Equity Incentive Plan, to fund the common shares underlying the initial 2,062,000 option grants. Upon receipt of the contribution, the common shares were retired. The contribution and related retirement is reflected as a contribution of common stock by stockholder and retirement in the Consolidated Statements of Stockholders’ Equity.
In connection with hiring an executive officer, we entered into a stock purchase agreement (“Agreement”) in September 2003 with a family member of such officer (“Investor”) pursuant to which we sold the Investor 412,390 shares of common stock and a warrant for an aggregate purchase price of $2,250,000. There were no significant costs incurred in connection with the sale. The term of the warrant was 39 months and was exercised by the Investor in July 2006 for 206,200 shares of common stock. The related proceeds were not material.
Federal Trade Commission Inquiry
In early January 2006, the Federal Trade Commission (“FTC”) commenced an inquiry into a security breach in our computer network, related to which we recorded an accrual of $500,000 during the year ended December 31, 2005. In September 2006, we executed a consent decree proposed by the FTC that requires, among other activities, that we provide biennial third-party assessments of our information technology security for a period of 10 years. During 2006, we incurred costs of $290,000 associated with this matter and, based on the terms of the consent decree, reversed $115,000 of the related accrual. As of December 31, 2007, an immaterial amount remains accrued. In addition, several customers who were notified of the security breach have sought compensation, which in each case has been satisfied by payment of amounts that were not material, and one customer has commenced litigation, which was dismissed by a federal court and subsequently settled with the customer for an insignificant amount. We may face additional legal and administrative action with respect to the security breach.
Indemnifications
We have agreed to indemnify our directors and executive officers for costs associated with any fees, expenses, judgments, fines and settlement amounts incurred by them in any action or proceeding to which any of them is, or is threatened to be, made a party by reason of his or her services in their role as a director or officer.
We have also agreed to indemnify the pre-initial public offering stockholders for any increases in their tax liabilities for the periods during which we were an S Corporation.
Legal Matters
We are subject to legal proceedings, claims, and litigation arising in the ordinary course of business. We are not currently involved in any litigation, the outcome of which would, based on information currently available, have a material adverse effect on our financial position, results of operations, or cash flows, nor are we aware of any such litigation threatened against us.
F-25
| Note | 13. Segment Information |
We have adopted SFAS No. 131, “Disclosures about Segments of an Enterprise and Related Information.” This standard requires segmentation based on our internal organization and reporting of revenue and other performance measures. Our segments are designed to allocate resources internally and provide a framework to determine management responsibility. Operating segments are defined as components of an enterprise about which discrete financial information is available that is evaluated regularly by the chief operating decision maker, or decision making group, in deciding how to allocate resources and in assessing performance. Our chief operating decision maker is our Chief Executive Officer. We have four operating segments, as summarized below:
| | • | | Products segment— includes EnCase® Enterprise, EnCase® Forensic, Premium License Support Program, and hardware sales. |
| | • | | Professional services segment—is our division that performs consulting services and implementations. Consulting services include conducting investigations using our software products. |
| | • | | Training segment—is our division that provides training classes in which we train our customers to effectively and efficiently use our software products. |
| | • | | Maintenance segment—Maintenance (as defined in Note 1) related revenue and costs. |
We refer to the revenue generated by our professional services, training and maintenance segments, collectively, as services revenue.
Currently, we do not separately allocate operating expenses to these segments, nor do we allocate specific assets to these segments. Therefore, the segment information reported includes only revenues, cost of revenues and gross profit. The following tables present the operations by operating segment:
| | | | | | | | | | | | | | | | |
| | | Year Ended December 31, 2005 | |
| | | Product | | Professional
Services | | Training | | Maintenance
& Other | | Total | |
| | | (in thousands) | |
Revenues | | $ | 23,138 | | $ | 5,144 | | $ | 6,705 | | $ | 4,518 | | $ | 39,505 | |
Cost of revenues | | | 2,202 | | | 4,373 | | | 4,000 | | | 773 | | | 11,348 | |
| | | | | | | | | | | | | | | | |
Gross profit | | $ | 20,936 | | $ | 771 | | $ | 2,705 | | $ | 3,745 | | | 28,157 | |
| | | | | | | | | | | | | | | | |
Operating expenses: | | | | | | | | | | | | | | | | |
Selling and marketing | | | | | | | | | | | | | | | 15,691 | |
Research and development | | | | | | | | | | | | | | | 4,680 | |
General and administrative | | | | | | | | | | | | | | | 4,923 | |
Depreciation and amortization | | | | | | | | | | | | | | | 1,357 | |
| | | | | | | | | | | | | | | | |
Total operating expenses | | | | | | | | | | | | | | | 26,651 | |
| | | | �� | | | | | | | | | | | | |
Operating income | | | | | | | | | | | | | | | 1,506 | |
Interest income | | | | | | | | | | | | | | | 54 | |
Interest expense | | | | | | | | | | | | | | | (81 | ) |
Other income, net | | | | | | | | | | | | | | | 150 | |
| | | | | | | | | | | | | | | | |
Income before income taxes | | | | | | | | | | | | | | $ | 1,629 | |
| | | | | | | | | | | | | | | | |
F-26
| | | | | | | | | | | | | | | | |
| | | Year Ended December 31, 2006 | |
| | | Product | | Professional
Services | | Training | | Maintenance
& Other | | Total | |
| | | (in thousands) | |
Revenues | | $ | 32,565 | | $ | 8,822 | | $ | 6,976 | | $ | 7,502 | | $ | 55,865 | |
Cost of revenues | | | 2,429 | | | 7,671 | | | 4,981 | | | 987 | | | 16,068 | |
| | | | | | | | | | | | | | | | |
Gross profit | | $ | 30,136 | | $ | 1,151 | | $ | 1,995 | | $ | 6,515 | | | 39,797 | |
| | | | | | | | | | | | | | | | |
Operating expenses: | | | | | | | | | | | | | | | | |
Selling and marketing | | | | | | | | | | | | | | | 26,238 | |
Research and development | | | | | | | | | | | | | | | 7,113 | |
General and administrative | | | | | | | | | | | | | | | 7,840 | |
Depreciation and amortization | | | | | | | | | | | | | | | 1,823 | |
| | | | | | | | | | | | | | | | |
Total operating expenses | | | | | | | | | | | | | | | 43,014 | |
| | | | | | | | | | | | | | | | |
Operating loss | | | | | | | | | | | | | | | (3,217 | ) |
Interest income | | | | | | | | | | | | | | | 105 | |
Interest expense | | | | | | | | | | | | | | | (91 | ) |
Other income, net | | | | | | | | | | | | | | | 173 | |
| | | | | | | | | | | | | | | | |
Loss before income taxes | | | | | | | | | | | | | | $ | (3,030 | ) |
| | | | | | | | | | | | | | | | |
| | | | | | | | | | | | | | | | |
| | | Year Ended December 31, 2007 | |
| | | Product | | Professional
Services | | Training | | Maintenance
& Other | | Total | |
| | | (in thousands) | |
Revenues | | $ | 44,314 | | $ | 12,332 | | $ | 8,514 | | $ | 13,720 | | $ | 78,880 | |
Cost of revenues | | | 2,754 | | | 11,831 | | | 5,564 | | | 1,885 | | | 22,034 | |
| | | | | | | | | | | | | | | | |
Gross profit | | $ | 41,560 | | $ | 501 | | $ | 2,950 | | $ | 11,835 | | | 56,846 | |
| | | | | | | | | | | | | | | | |
Operating expenses: | | | | | | | | | | | | | | | | |
Selling and marketing | | | | | | | | | | | | | | | 32,964 | |
Research and development | | | | | | | | | | | | | | | 9,067 | |
General and administrative | | | | | | | | | | | | | | | 14,637 | |
Depreciation and amortization | | | | | | | | | | | | | | | 3,453 | |
| | | | | | | | | | | | | | | | |
Total operating expenses | | | | | | | | | | | | | | | 60,121 | |
| | | | | | | | | | | | | | | | |
Operating loss | | | | | | | | | | | | | | | (3,275 | ) |
Interest income | | | | | | | | | | | | | | | 1,463 | |
Interest expense | | | | | | | | | | | | | | | (107 | ) |
Other income, net | | | | | | | | | | | | | | | 130 | |
| | | | | | | | | | | | | | | | |
Loss before income taxes | | | | | | | | | | | | | | $ | (1,789 | ) |
| | | | | | | | | | | | | | | | |
F-27
Revenue, classified by the major geographic areas in which we operate, is as follows:
| | | | | | | | | |
| | | Year Ended December 31, |
| | | 2005 | | 2006 | | 2007 |
| | | (in thousands) |
Revenues | | | | | | | | | |
U.S. | | $ | 29,499 | | $ | 41,229 | | $ | 60,791 |
Europe | | | 6,711 | | | 9,756 | | | 10,166 |
Asia | | | 1,901 | | | 2,063 | | | 4,518 |
Other | | | 1,394 | | | 2,817 | | | 3,405 |
| | | | | | | | | |
| | $ | 39,505 | | $ | 55,865 | | $ | 78,880 |
| | | | | | | | | |
At December 31, 2006 and 2007, property and equipment located in the United States, net of accumulated depreciation and amortization, was approximately $5,710,000 and $11,831,000, respectively. At December 31, 2006 and 2007, property and equipment located in foreign countries, net of accumulated depreciation and amortization was approximately $815,000 and $684,000, respectively.
| Note 14. | Pro Forma Information (Unaudited) |
The pro forma unaudited income tax adjustments presented represent taxes which would have been reported had we been subject to federal and state income taxes as a C-Corporation during the years ended December 31, 2005 and 2006. The pro forma provision for income taxes differs from the statutory income tax rate due to the following (in thousands):
| | | | | | | | |
| | | For the year ended
December 31, | |
| | | 2005 | | | 2006 | |
Federal income taxes at the statutory rate | | $ | 554 | | | $ | (1,030 | ) |
State income taxes, net of federal benefit | | | 9 | | | | (143 | ) |
Extraterritorial income exclusion | | | (103 | ) | | | — | |
Research credits | | | (156 | ) | | | 329 | |
Non-deductible compensation | | | — | | | | (416 | ) |
Change in valuation allowance | | | 27 | | | | 1,120 | |
Other | | | 12 | | | | 179 | |
| | | | | | | | |
| | $ | 343 | | | $ | 39 | |
| | | | | | | | |
F-28
The pro forma benefit for deferred income taxes reflects temporary differences in the recognition of revenue and expenses for tax and financial reporting purposes as follows (in thousands):
| | | | | | | | |
| | | For the year ended
December 31, | |
| | | 2005 | | | 2006 | |
Net operating losses | | $ | — | | | $ | 920 | |
Tax credits | | | 580 | | | | 997 | |
Deferred revenue | | | 2,469 | | | | 1,734 | |
Accrued expenses | | | 634 | | | | 1,156 | |
Depreciable assets | | | (223 | ) | | | (307 | ) |
Other accruals and reserves | | | — | | | | 59 | |
| | | | | | | | |
Net deferred tax assets prior to valuation allowance | | | 3,460 | | | | 4,459 | |
Valuation allowance | | | (3,460 | ) | | | (4,459 | ) |
| | | | | | | | |
Net deferred tax assets | | $ | — | | | $ | — | |
| | | | | | | | |
| Note 15. | Subsequent Events |
In January 2008, we amended the terms of the December 2007 stock option and nonvested share grants to our new Chief Executive Officer. These amendments effectively cancelled certain options and nonvested share grants that had been issued outside the 2004 Equity Incentive Plan (the “Plan”) and reissued them under the Plan. There was no compensation expense recorded upon the amendments as the terms of the grant did not change and there was no incremental value provided to our Chief Executive Officer.
F-29
| Note 16. | Unaudited Quarterly Information |
The following tables set forth below unaudited quarterly data. In the opinion of management, the following unaudited quarterly data has been prepared on the same basis as the audited financial statements and includes all adjustments, consisting of normal recurring adjustments, necessary for a fair presentation of the results of operations for the periods presented.
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
| | | Quarter Ended | |
| | | Mar. 31,
2005 | | | June 30,
2005 | | | Sept. 30,
2005 | | | Dec. 31
2005 | | | Mar. 31,
2006 | | | June 30,
2006 | | | Sept. 30,
2006 | | | Dec. 31
2006 | | | Mar. 31,
2007 | | | June 30,
2007 | | | Sept 30,
2007 | | | Dec. 31
2007 | |
| | | (in thousands, except per share data) | |
Revenue: | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Product revenue | | $ | 4,121 | | | $ | 5,032 | | | $ | 6,290 | | | $ | 7,695 | | | $ | 6,203 | | | $ | 6,953 | | | $ | 9,207 | | | $ | 10,202 | | | $ | 10,088 | | | $ | 10,293 | | | $ | 11,616 | | | $ | 12,317 | |
Services and maintenance revenue | | | 3,721 | | | | 3,951 | | | | 4,039 | | | | 4,656 | | | | 4,968 | | | | 5,920 | | | | 5,588 | | | | 6,824 | | | | 7,508 | | | | 8,241 | | | | 8,661 | | | | 10,156 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Total revenues | | | 7,842 | | | | 8,983 | | | | 10,329 | | | | 12,351 | | | | 11,171 | | | | 12,873 | | | | 14,795 | | | | 17,026 | | | | 17,596 | | | | 18,534 | | | | 20,277 | | | | 22,473 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Cost of revenues: | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Cost of product revenue | | | 454 | | | | 540 | | | | 583 | | | | 625 | | | | 477 | | | | 547 | | | | 599 | | | | 806 | | | | 745 | | | | 656 | | | | 653 | | | | 700 | |
Cost of services and maintenance revenue | | | 1,871 | | | | 2,081 | | | | 2,287 | | | | 2,907 | | | | 2,608 | | | | 3,139 | | | | 3,462 | | | | 4,430 | | | | 4,513 | | | | 4,703 | | | | 4,584 | | | | 5,480 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Total cost of revenues | | | 2,325 | | | | 2,621 | | | | 2,870 | | | | 3,532 | | | | 3,085 | | | | 3,686 | | | | 4,061 | | | | 5,236 | | | | 5,258 | | | | 5,359 | | | | 5,237 | | | | 6,180 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Gross profit | | | 5,517 | | | | 6,362 | | | | 7,459 | | | | 8,819 | | | | 8,086 | | | | 9,187 | | | | 10,734 | | | | 11,790 | | | | 12,338 | | | | 13,175 | | | | 15,040 | | | | 16,293 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Operating expenses: | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Selling and marketing | | | 3,052 | | | | 3,788 | | | | 3,858 | | | | 4,993 | | | | 5,108 | | | | 6,434 | | | | 6,683 | | | | 8,013 | | | | 8,692 | | | | 8,036 | | | | 7,863 | | | | 8,373 | |
Research and development | | | 867 | | | | 858 | | | | 1,484 | | | | 1,471 | | | | 1,452 | | | | 1,734 | | | | 2,062 | | | | 1,865 | | | | 2,048 | | | | 2,195 | | | | 2,294 | | | | 2,530 | |
General and administrative | | | 966 | | | | 1,298 | | | | 1,040 | | | | 1,629 | | | | 1,711 | | | | 1,762 | | | | 2,062 | | | | 2,305 | | | | 3,090 | | | | 3,478 | | | | 3,681 | | | | 4,388 | |
Depreciation and amortization | | | 317 | | | | 332 | | | | 328 | | | | 370 | | | | 360 | | | | 432 | | | | 489 | | | | 542 | | | | 699 | | | | 816 | | | | 909 | | | | 1,029 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Total operating expenses | | | 5,202 | | | | 6,276 | | | | 6,710 | | | | 8,463 | | | | 8,631 | | | | 10,362 | | | | 11,296 | | | | 12,725 | | | | 14,529 | | | | 14,525 | | | | 14,747 | | | | 16,320 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Operating income (loss) | | | 315 | | | | 86 | | | | 749 | | | | 356 | | | | (545 | ) | | | (1,175 | ) | | | (562 | ) | | | (935 | ) | | | (2,191 | ) | | | (1,350 | ) | | | 293 | | | | (27 | ) |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Other income and expense: | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Interest income | | | 3 | | | | 11 | | | | 10 | | | | 30 | | | | 26 | | | | 12 | | | | 9 | | | | 58 | | | | 358 | | | | 374 | | | | 354 | | | | 377 | |
Interest expense | | | (21 | ) | | | (16 | ) | | | (21 | ) | | | (23 | ) | | | (9 | ) | | | (12 | ) | | | (27 | ) | | | (43 | ) | | | (32 | ) | | | (22 | ) | | | (30 | ) | | | (23 | ) |
Other income, net | | | 20 | | | | 43 | | | | 43 | | | | 44 | | | | 34 | | | | 35 | | | | 44 | | | | 60 | | | | 34 | | | | 57 | | | | 4 | | | | 35 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Income (loss) before income taxes | | | 317 | | | | 124 | | | | 781 | | | | 407 | | | | (494 | ) | | | (1,140 | ) | | | (536 | ) | | | (860 | ) | | | (1,831 | ) | | | (941 | ) | | | 621 | | | | 362 | |
Income tax provision | | | 11 | | | | — | | | | 2 | | | | — | | | | 16 | | | | 6 | | | | — | | | | 17 | | | | 25 | | | | 25 | | | | 983 | | | | 45 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Net income (loss) | | $ | 306 | | | $ | 124 | | | $ | 779 | | | $ | 407 | | | $ | (510 | ) | | $ | (1,146 | ) | | $ | (536 | ) | | $ | (877 | ) | | $ | (1,856 | ) | | $ | (966 | ) | | $ | (362 | ) | | $ | 317 | |
| | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Net income (loss) per share: | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Basic | | $ | 0.01 | | | $ | 0.01 | | | $ | 0.04 | | | $ | 0.02 | | | $ | (0.02 | ) | | $ | (0.06 | ) | | $ | (0.03 | ) | | $ | (0.05 | ) | | $ | (0.08 | ) | | $ | (0.04 | ) | | $ | (0.02 | ) | | $ | 0.01 | |
Diluted | | $ | 0.01 | | | $ | 0.01 | | | $ | 0.04 | | | $ | 0.02 | | | $ | (0.02 | ) | | $ | (0.06 | ) | | $ | (0.03 | ) | | $ | (0.05 | ) | | $ | (0.08 | ) | | $ | (0.04 | ) | | $ | (0.02 | ) | | $ | 0.01 | |
Weighted average number of shares used in per share calculation: | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | | |
Basic | | | 20,412 | | | | 20,412 | | | | 20,412 | | | | 20,412 | | | | 20,417 | | | | 19,903 | | | | 18,789 | | | | 19,487 | | | | 22,289 | | | | 22,425 | | | | 22,745 | | | | 22,942 | |
Diluted | | | 20,757 | | | | 20,981 | | | | 21,363 | | | | 21,409 | | | | 20,417 | | | | 19,903 | | | | 18,789 | | | | 19,487 | | | | 22,289 | | | | 22,425 | | | | 22,745 | | | | 23,412 | |
F-30
SIGNATURES
Pursuant to the requirements of Section 13 or 15(d) of the Securities Exchange Act of 1934, the registrant has duly caused this report to be signed on its behalf by the undersigned, thereunto duly authorized.
March 14, 2008
| | |
| Guidance Software, Inc. |
| |
| By | | /s/ VICTOR T. LIMONGELLI |
| | Victor T. Limongelli President and Chief Executive Officer (Principal Executive Officer) |
Pursuant to the requirements of the Securities Exchange Act of 1934, this Report has been signed below by the following persons on behalf of the registrant and in the capacities and on the dates indicated:
| | | | |
Signature | | Title | | Date |
| | |
/s/ VICTOR T. LIMONGELLI Victor T. Limongelli | | President, Chief Executive Officer and Director(Principal Executive Officer) | | March 14, 2008 |
| | |
/s/ FRANK J. SANSONE Frank J. Sansone | | Chief Financial Officer(Principal Financial and Accounting Officer) | | March 14, 2008 |
| | |
/s/ SHAWN MCCREIGHT Shawn McCreight | | Chairman and Chief Technology Officer | | March 14, 2008 |
| | |
/s/ JOHN M. PATZAKIS John M. Patzakis | | Vice Chairman and Chief Strategy Officer | | March 14, 2008 |
| | |
/s/ KATHLEEN O’NEIL Kathleen O’Neil | | Director | | March 14, 2008 |
| | |
/s/ MARSHALL S. GELLER Marshall S. Geller | | Director | | March 14, 2008 |
| | |
/s/ STEPHEN C. RICHARDS Stephen C. Richards | | Director | | March 14, 2008 |
| | |
/s/ ROBERT G.VAN SCHOONENBERG Robert G. van Schoonenberg | | Director | | March 14, 2008 |
S-1
GUIDANCE SOFTWARE, INC.
SCHEDULE II
VALUATION AND QUALIFYING ACCOUNTS
| | | | | | | | | | | | | | | | |
Description | | Balance at
Beginning
of Period | | Additions
Charged to
Costs and
Expenses | | Additions
Charged to
Other
Accounts | | Deductions
and Other
Adjustments | | | Balance at
End of
Period |
| | | (in thousands) |
Allowance for doubtful accounts: | | | | | | | | | | | | | | | | |
Year ended December 31, 2005 | | $ | 134 | | $ | 97 | | $ | — | | $ | (92 | ) | | $ | 139 |
Year ended December 31, 2006 | | $ | 139 | | $ | 514 | | $ | — | | $ | (211 | ) | | $ | 442 |
Year ended December 31, 2007 | | $ | 442 | | $ | 947 | | $ | — | | $ | (405 | ) | | $ | 984 |
Deferred tax asset valuation allowance: | | | | | | | | | | | | | | | | |
Year ended December 31, 2005 | | $ | 241 | | $ | 45 | | $ | — | | $ | — | | | $ | 286 |
Year ended December 31, 2006 | | $ | 286 | | $ | 2,493 | | $ | — | | $ | — | | | $ | 2,779 |
Year ended December 31, 2007 | | $ | 2,779 | | $ | 1,230 | | $ | — | | $ | — | | | $ | 4,009 |
II-1
