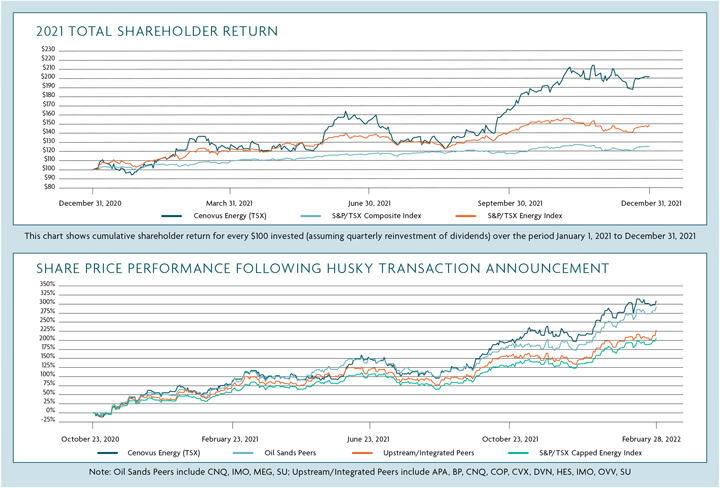
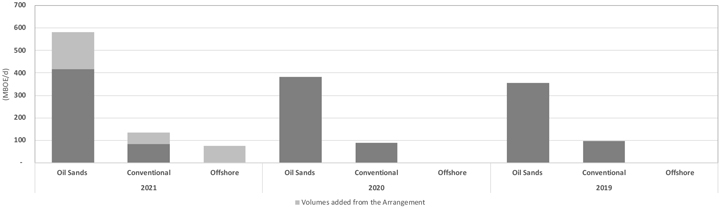
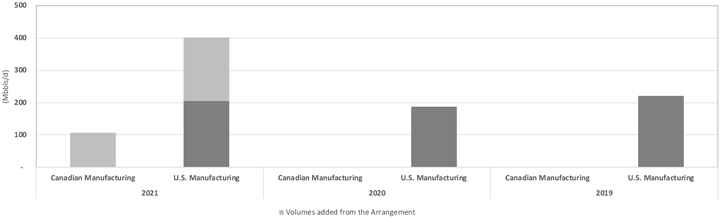
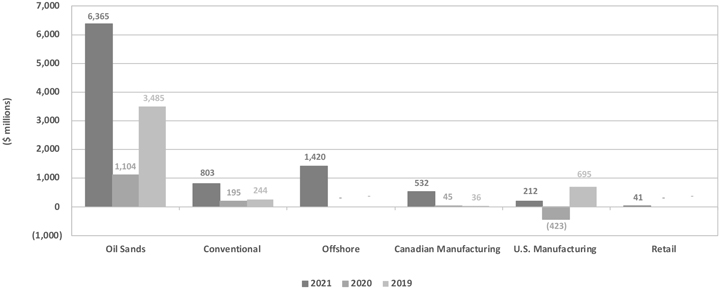
SAGD Technology
Current technologies used for the recovery of bitumen is energy intensive, including SAGD which requires significant consumption of natural gas in the production of steam used in the recovery process. The amount of steam required in the recovery process varies and therefore impacts costs. The performance of the reservoir affects the timing and levels of production using SAGD technology. A large increase in recovery costs could cause certain projects that rely on SAGD technology to become uneconomical, which could have a negative effect on our business, financial condition, results of operations and cash flows. There are risks associated with growth and other capital projects that rely largely or partly on new technologies, the incorporation of such technologies into new or existing operations and acceptance of new technologies in the market. The success of projects incorporating new technologies cannot be assured.
Technology, Information Systems and Privacy
We rely heavily on technology, including operating technology and information technology, to effectively operate our business. This may include on premise systems, (such as networks, computer hardware and software), networks and telecommunications systems, mobile applications, and cloud services. Such systems and services may be provided by third parties. In the event we are unable to regularly and effectively access, use, rely upon, secure, upgrade, and take other steps to maintain or improve the efficiency and efficacy of such systems and services, the operation of such systems and services could be interrupted, resulting in operational interruptions or the loss, corruption, or release of data.
In the ordinary course of business, we collect, use and store sensitive data, including intellectual property, proprietary and business information and personal information, including the information of third parties. Despite our security measures, our technology systems and services may be vulnerable to attacks (such as by hackers, cyberterrorists or other third parties) or to disruption due to staff or third-party error or malfeasance or to other disruptions, including as a result of natural disasters and acts of state or industrial espionage, activism, terrorism or war. Any such incident could compromise information used or stored on our systems or services and result in the loss, theft, inability to access, use or rely upon, the unauthorized access, disclosure, copying, use, modification, disposal or destruction of, or the exposure of, internal, confidential, personal or other sensitive information including information related to our assets and operations, technology, intellectual property, corporate or retail credit card information, customer personal information, employee personal information, exploration activities, corporate actions, executive officer communications and financial results. These could result in legal claims or proceedings, liability under laws that protect the privacy of personal information, regulatory penalties, operational disruption, site shut-down, leaks or other negative consequences, including damage to our reputation, which could have a material adverse effect on our business, financial condition, results of operations and cash flows.
Without limiting the foregoing, these risks include the risk of cyber-related fraud or attacks whereby threat actors attempt to circumvent electronic communications controls or attempt to impersonate internal personnel or business partners to divert payments and financial assets to accounts controlled by the perpetrators or to introduce ransomware into one or more systems or services in an effort to extract a payment. If a threat actor is successful in bypassing our cyber-security measures and business process controls, such cyber-related risks could result in financial losses, remediation and recovery costs, and an adverse reputational impact.
Data protection and privacy is governed by a complex legal and regulatory framework that is rapidly evolving in the areas in which we operate. Such legislation applies to a wide range of data processing activities including, but not limited to, processing personal information. For example, effective November 1, 2021, the Personal Information Protection Law (“PIPL”) became effective in the People’s Republic of China. PIPL is China’s first comprehensive law designed to regulate online data and protect personal information. In addition, on September 1, 2021, the Data Security Law went into effect in the People’s Republic of China. Such legislation applies to a wide range of data processing activities including, but not limited to, processing personal information. With extraterritorial scope and severe fines and penalties, these evolving laws impose an increasingly complex and comprehensive legal framework for the collection, use and processing of personal information. Compliance with such legislation may result in increased operating costs and failure to comply with such legislation may result in severe fines and penalties, each of which may adversely impact our financial condition, results of operations and cash flows.
Security and Terrorist Threats
Security threats and terrorist or activist activities may impact our personnel, or those of partners, customers, and suppliers, and could result in situations of injury, loss of life, extortion, hostage situations and/or kidnapping or unlawful confinement, destruction or damage to property of Cenovus or others, impact to the environment, and business interruption. A security threat, terrorist attack or activist incident targeted at a facility, terminal, pipeline, rail network, office or offshore vessel/ installation owned or operated by Cenovus or any of our systems, services, infrastructure, market access routes, or partnerships could result in the interruption or cessation of key elements of our operations. Outcomes of such incidents could have a material adverse effect on our results of operations, financial condition and business strategy. The potential for detention and/ or incarceration of our employees/contractors entering or working in China remains, and as a result, review and reconsideration for travel into China has become a business/corporate process.