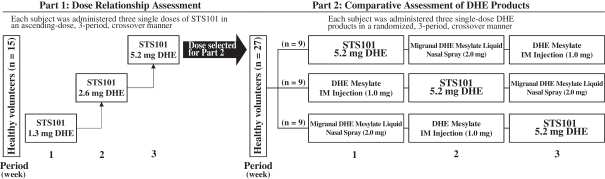
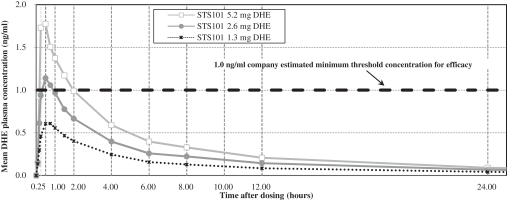
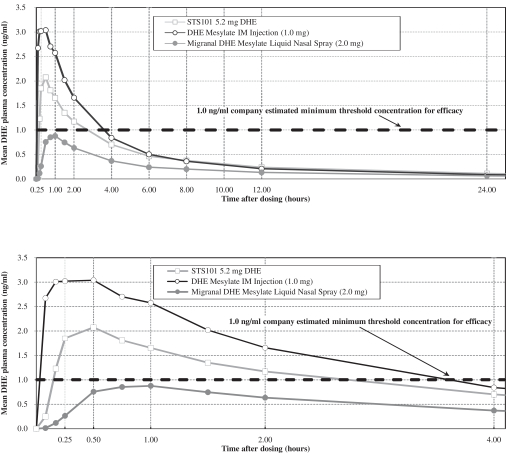
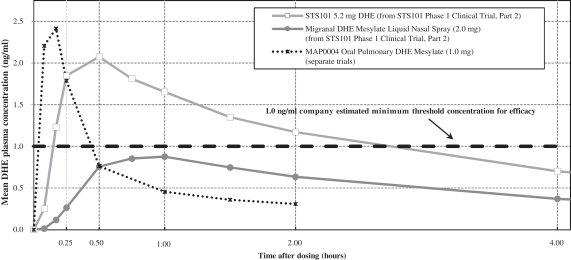
We depend on our information technology systems, and any failure of these systems could harm our business. Any real or perceived security breaches, loss of data, and other disruptions or incidents could compromise the privacy, security, integrity or confidentiality of sensitive information related to our business or prevent us from accessing critical information and expose us to liability and reputational harm, which could adversely affect our business, results of operations and financial condition.
We collect and maintain data and information that is necessary to conduct our business, and we are increasingly dependent on information technology systems and infrastructure to operate our business, including systems infrastructure operated and maintained by our third party suppliers or providers. In the ordinary course of our business, we collect, store and transmit large amounts of confidential information, including intellectual property, proprietary business information and personal information. It is critical that we do so in a secure manner to maintain the privacy, security, confidentiality and integrity of such confidential information. We have established physical, electronic and organizational measures to safeguard and secure our systems and facilities to prevent an information compromise, and rely on commercially available systems, software, tools, and monitoring to provide security for our information technology systems and the processing, transmission and storage of digital information. We have also outsourced elements of our information technology infrastructure, and as a result a number of third-party vendors may or could have access to our confidential information. Our internal information technology systems and infrastructure, and those of our current and any future collaborators, contractors and consultants and other third parties on which we rely, are vulnerable to damage or unauthorized access or use resulting from computer viruses, malware, natural disasters, terrorism, war, telecommunication and electrical failures,denial-of-service attacks, cyber-attacks or cyber-intrusions over the Internet, hacking, phishing and other social engineering attacks, attachments to emails, persons inside our organization (including employees or contractors), lost or stolen devices, or persons with access to systems inside our organization.
The risk of a security breach or disruption or data loss, particularly through social engineering attacks, cyber-attacks or cyber-intrusion, including by computer hackers, foreign governments and cyber terrorists, has generally increased as the number, intensity and sophistication of attempted attacks and intrusions from around the world have increased. In addition, the prevalent use of mobile devices that access confidential information increases the risk of data security breaches, which could lead to the loss of confidential information or other intellectual property. The costs to us to mitigate, investigate and respond to potential security incidents, breaches, disruptions, network security problems, bugs, viruses, worms, malicious software programs and security vulnerabilities could be significant, and while we have implemented security measures to protect our data security and information technology systems, our efforts to address these problems may not be successful, and these problems could result in unexpected interruptions, delays, cessation of service and other harm to our business and our competitive position. If such an event were to occur and cause interruptions in our operations, it could result in a material disruption of our product development programs. For example, the loss of clinical trial data from completed or ongoing or planned clinical trials could result in delays in our regulatory approval efforts and significantly increase our costs to recover or reproduce the data. Moreover, if a real or perceived security breach affects our systems (or those of our third party providers or suppliers) or results in the loss of or accidental, unlawful or unauthorized access to, use of, release of or other processing of personally identifiable information or clinical trial data, our reputation could be materially damaged. In addition, such a breach may require notification to governmental agencies, the media or individuals pursuant to various federal and state privacy and security laws, if applicable, including the Health Insurance Portability and Accountability Act of 1996, or HIPAA, as amended by the Health Information Technology for Clinical Health Act of 2009, or HITECH, and its implementing rules and regulations, as well as regulations promulgated by the Federal Trade Commission and state breach notification laws. We would also be exposed to a risk of loss, negative publicity, harm to our reputation, governmental investigation and/or enforcement actions, claims or litigation and potential liability, which could materially adversely affect our business, results of operations and financial condition. The global data protection landscape is rapidly evolving, and we may be affected by or subject to new, amended or existing laws and regulations in the future, including as our operations continue to expand or if we begin to operate in foreign jurisdictions.
32