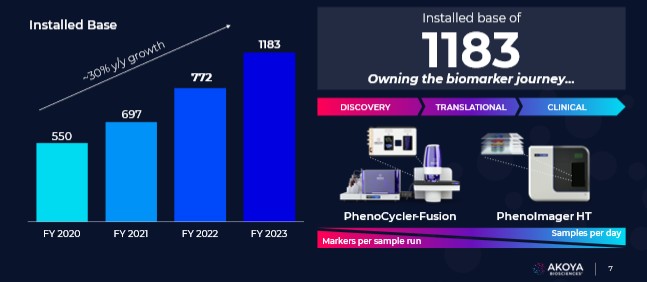
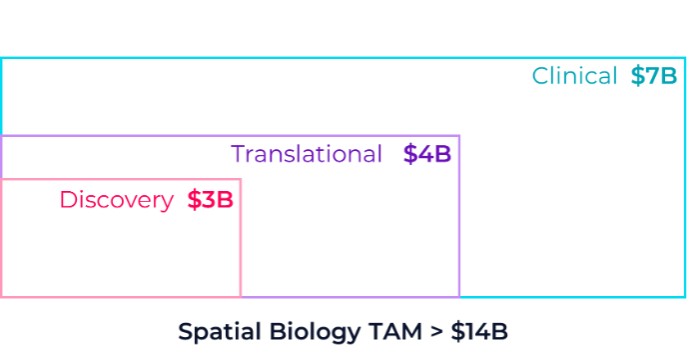
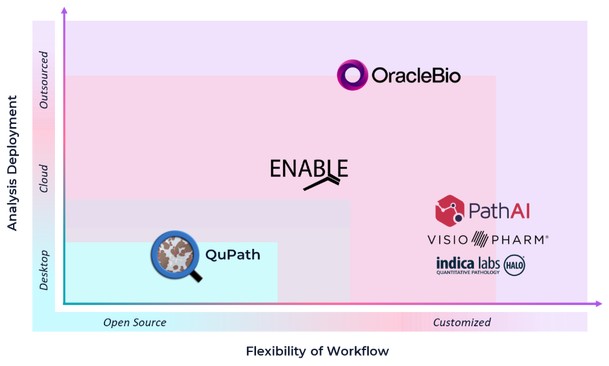
technology to a third-party. Even in the event we are able to find a third-party to assist in our operational efforts, we may be unable to negotiate commercially reasonable terms to engage with the third-party.
We carry insurance for damage to our property and the disruption of our business, but this insurance may not cover all of the risks associated with damage or disruption to our business, may not provide coverage in amounts sufficient to cover our potential losses and may not continue to be available to us on acceptable terms, if at all.
Our insurance policies are expensive and protect us only from some business risks, which leaves us exposed to significant uninsured liabilities.
We do not carry insurance for all categories of risk that our business may encounter and our policies have limits and significant deductibles.
Some of the policies we currently maintain include general liability, property, umbrella and directors’ and officers’ insurance.
Any product liability insurance coverage we maintain may not be sufficient to reimburse us for any expenses or losses we may suffer related to product liability claims. Moreover, insurance coverage is becoming increasingly expensive and in the future we may not be able to maintain insurance coverage at a reasonable cost or in sufficient amounts to protect us against losses. A successful product liability claim or series of claims in which judgments exceed our insurance coverage could adversely affect our business, financial condition, results of operations and prospects, including preventing or limiting the commercialization of any products we develop.
In addition, our director and officer liability insurance includes policy limits which may not provide sufficient coverage in the event of a successful claim or series of claims. Any significant uninsured liability may require us to pay substantial amounts, which would adversely affect our business, financial condition, results of operations and prospects.
Security incidents, loss of data or modification of information, and other disruptions could compromise information related to our business or prevent us from accessing critical information, result in a significant disruption of our activities and expose us to liability, which could adversely affect our business and our reputation.
In the ordinary course of our business, we collect and store information, including personal information, intellectual property and proprietary business information that we own or control or have an obligation to protect. For example, we collect and store research and development information, employee data, commercial information, customer information, business and financial information, and payment card data. We and our service providers, including security and infrastructure vendors, manage and maintain our applications and data using a combination of on-site systems and cloud-based data centers. We face a number of risks related to protecting critical information and our applications, including inappropriate use or disclosure, unauthorized access or acquisition, or inappropriate modification of, critical information. We also face the risk of being unable to access our critical information, applications, or systems due to actual or threats of ransomware, unauthorized encryption, or other malicious activity. We face the risk of our being unable to adequately monitor and audit and modify our controls over our critical information and applications. These risks extend to third-party service providers and subcontractors we use to assist us in managing our information or otherwise process it on our behalf. The secure processing, storage, maintenance and transmission of our critical information are vital to our operations and business strategy, and we devote significant resources to protecting such information.
Although we take reasonable measures to protect critical information and other data from unauthorized access, acquisition, use or disclosure, our information technology and infrastructure and that of our service providers handling and storing information on our behalf may be vulnerable to a variety of disruptions, including data breaches, attacks by hackers and other malicious third parties (including the deployment of computer viruses, malware, ransomware, denial-of-service attacks, social engineering, and other events that affect service reliability and threaten the confidentiality, integrity, and availability of information), unauthorized access, natural disasters, fires, terrorism, war, telecommunications or electrical interruptions or failures, employee error or malfeasance or other malicious or inadvertent disruptions. In particular, the risk of a security breach or disruption, particularly through cyber-attacks or cyber intrusion, has generally increased as the number, intensity, and sophistication of attempted attacks and intrusions