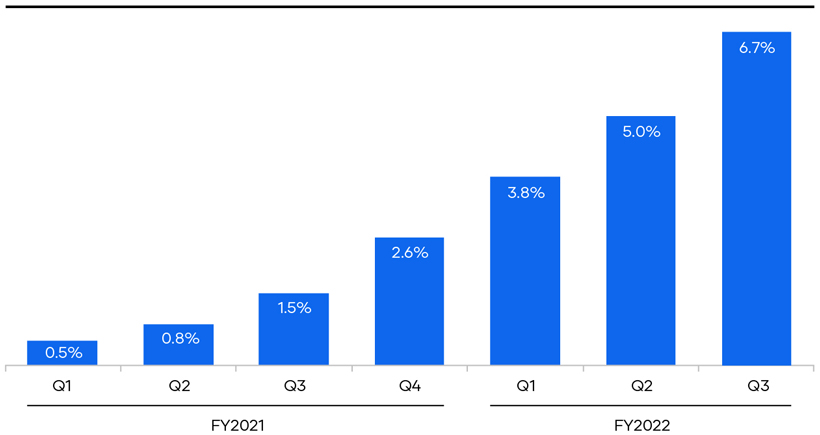
other incidents that may remain undetected for an extended period and, therefore, may have a greater impact on our products, the networks and systems used in our business, and the proprietary and other confidential data contained on such networks and systems. We expect to incur significant costs in our efforts to detect and prevent security breaches and other security-related incidents, and we may face increased costs in the event of an actual or perceived security breach or other security-related incident. These cybersecurity risks pose a particularly significant risk to a business like ours that is focused on providing highly secure products to customers. Additionally, as a remote-first company, our workforce functions in a remote work environment that requires remote access to our corporate network, which in turn imposes additional risks to our business, including increased risk of industrial espionage, theft of assets, phishing, and other cybersecurity attacks, and inadvertent or unauthorized access to or dissemination of sensitive, proprietary, or confidential information.
We also engage third-party vendors and service providers to store and otherwise process some of our and our customers’ data, including sensitive and personal information. Our vendors and service providers may also be the targets of cyberattacks, malicious software, phishing schemes, fraud, and may face other cybersecurity threats and may suffer cybersecurity breaches and incidents from these and other causes. Our ability to monitor these parties’ data security is limited. There can be no assurance that any security measures that we or our third-party service providers, including third-party providers of cloud infrastructure services, have implemented will be effective against current or future security threats, and we cannot guarantee that our systems and networks or those of our third-party service providers have not been breached or that they do not contain exploitable defects or bugs that could result in a breach of or disruption to our systems and networks or the systems and networks of third parties that support us and our products. While we maintain measures designed to protect the integrity, confidentiality, and security of our data and other data we maintain or otherwise process, our security measures or those of our third-party service providers could fail and result in unauthorized access to or disclosure, modification, misuse, loss, or destruction of such data. Unauthorized access to, other security breaches of, or security incidents affecting, systems, networks, and data of our vendors, contractors, or those with which we have strategic relationships, even if not resulting in an actual or perceived breach of our customers’ networks, systems, or data, could result in the loss, compromise, or corruption of data, loss of business, reputational damage adversely affecting customer or investor confidence, regulatory investigations and orders, litigation, indemnity obligations, damages for contract breach, penalties for violation of applicable laws or regulations, significant costs for remediation, and other liabilities.
Our products may experience errors, failures, vulnerabilities, or bugs that cause our products not to perform as intended. Any such errors, failures, vulnerabilities, or bugs may not be found until after they are deployed to our customers and may create the perception that our platform and products are insecure, underperforming, or unreliable. We also provide frequent updates and fundamental enhancements to our platform and products, which increase the possibility of errors. Our quality assurance procedures and efforts to report, track, and monitor issues with our products may not be sufficient to ensure we detect any such defects in a timely manner. There can be no assurance that our software code is or will remain free from actual or perceived errors, failures, vulnerabilities, or bugs.
Many of our customers may use our software for controlling their infrastructure and processing, transmitting, and protecting their sensitive and proprietary information, including business strategies, financial and operational data, personal or identifying information, and other related data. Our Vault product is specifically designed to assist our customers with management of their private and sensitive information. Actual or perceived breaches or other security incidents from actual or perceived errors, failures, vulnerabilities, or bugs in our products or other causes could lead to claims and litigation, indemnity obligations, regulatory audits, proceedings, investigations and significant legal fees, significant costs for remediation, the expenditure of significant financial resources in efforts to analyze, correct, eliminate, remediate, or work around errors or defects, to address and eliminate vulnerabilities,
33