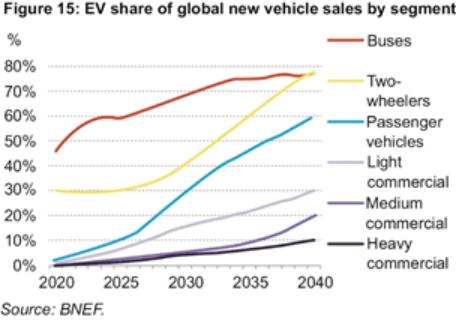
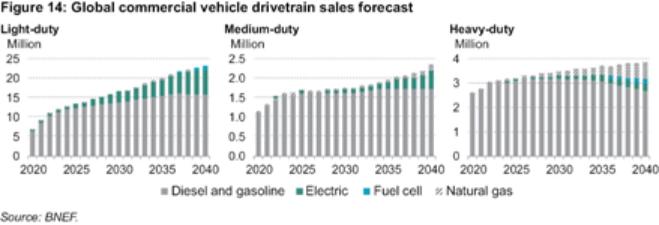
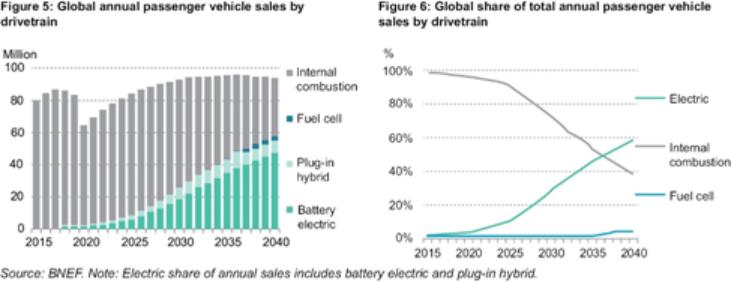
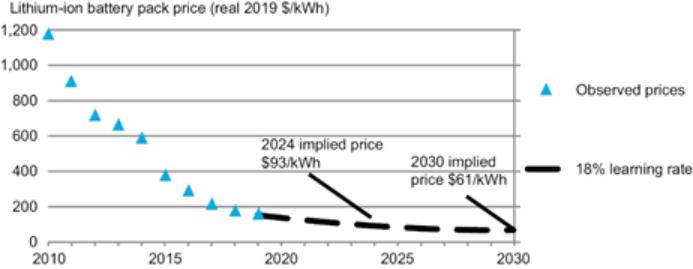
development efforts may not be sufficient to adapt to changes in alternative fuel and EV technology. As technologies change, we plan to upgrade or adapt our EVs with the latest technology. However, our EVs may not compete effectively with alternative systems if we are not able to source and integrate the latest technology into our EVs.
We are subject to cybersecurity risks to our operational systems, security systems, infrastructure, integrated software in our EVs and customer data processed by us or third-party vendors.
We are at risk for interruptions, outages and breaches of our: (a) operational systems, including business, financial, accounting, product development, data processing or production processes, owned by us or our third-party vendors or suppliers; (b) facility security systems, owned by us or our third-party vendors or suppliers; (c) transmission control, battery management, steer-by-wire and autonomous driving systems or other in-product technology, owned by us or our third-party vendors or suppliers; (d) the integrated software in our EVs; or (e) customer data that we process or our third-party vendors or suppliers process on our behalf. Such incidents could: materially disrupt our operational systems; result in loss of intellectual property, trade secrets or other proprietary or competitively sensitive information; compromise certain information of customers, employees, suppliers, or others; jeopardize the security of our facilities; or affect the performance of in-product technology and the integrated software in our EVs.
We plan to include in-vehicle services and functionality that utilize data connectivity to monitor performance and timely capture opportunities to enhance on-the-road performance and for safety and cost-saving preventative maintenance. The availability and effectiveness of our services depend on the continued operation of information technology and communications systems. Our systems or those of third parties upon whom we rely are vulnerable to damage or interruption from, among others, physical theft, fire, terrorist attacks, natural disasters, power loss, war, telecommunications failures, viruses, denial or degradation of service attacks, ransomware, social engineering schemes, employee error or malfeasance, insider theft or misuse or other attempts to harm the systems upon which we rely. We intend to use our in-vehicle services and functionality to log information about each vehicle’s use in order to aid us in vehicle diagnostics and servicing. Our customers may object to the use of this data, which may increase our vehicle maintenance costs and harm our business prospects.
Moreover, there are inherent risks associated with developing, improving, expanding and updating our current systems, such as the disruption of our data management, procurement, production execution, finance, supply chain and sales and service processes. These risks may affect our ability to manage our data and inventory, procure parts or supplies or manufacture, deploy, deliver and service our EVs, adequately protect our intellectual property or achieve and maintain compliance with, or realize available benefits under, applicable laws, regulations and contracts. We cannot be sure that the systems upon which we rely, including those of our third-party vendors or suppliers, will be effectively implemented, maintained or expanded as planned. If we do not successfully implement, maintain or expand these systems as planned, our operations may be disrupted, our ability to accurately and timely report our financial results could be impaired, and deficiencies may arise in our internal control over financial reporting, which may impact our ability to certify our financial results. Moreover, our proprietary information or intellectual property could be compromised or misappropriated and our reputation may be adversely affected. If these systems do not operate as we expect them to, we may be required to expend significant resources to make corrections or find alternative sources for performing these functions.
We retain personal information about our vehicles, drivers, customers, employees or others that, if compromised, could materially adversely affect our financial performance and results of operations or prospects.
We collect, store, transmit, disclose, use and otherwise process data from vehicles, drivers, customers, employees and others as part of our business and operations, which may include personal, confidential or proprietary information. We also work with partners and third-party service providers or vendors that collect, store, transmit, disclose use and otherwise process such data on our behalf and in connection with our EVs. There can be no assurance that any security measures that we or our third-party service providers or vendors have implemented will be effective against current or future security threats. If a compromise of data were to occur, we may become liable under our contracts with other parties and under applicable laws for damages and incur penalties and other costs to respond to, investigate and remedy such an incident. Our systems, networks and physical facilities could be breached or personal information could otherwise be compromised due to employee error or malfeasance, if, for example, third parties attempt to fraudulently induce our employees or our customers to disclose information or usernames and/or passwords. Third parties may also exploit vulnerabilities in, or