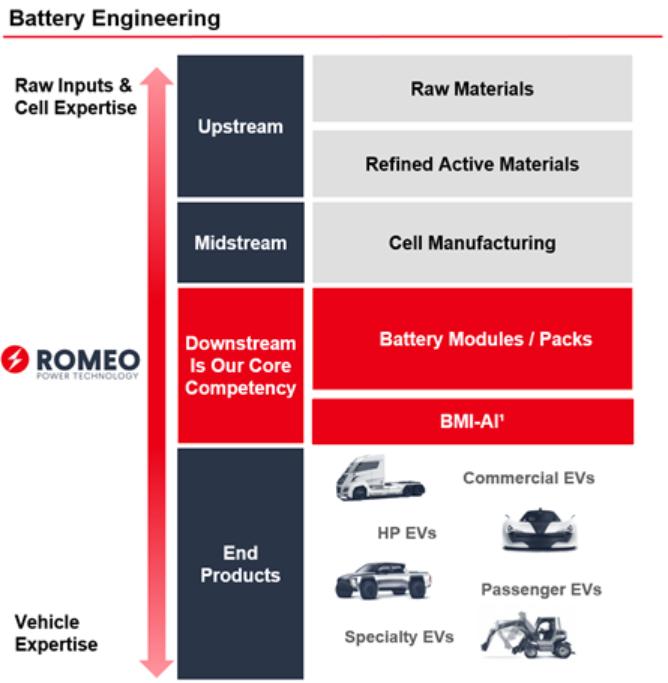
currently releasing a new version of the battery management firmware. Nevertheless, the unauthorized publication of version 1.0 of such firmware may have eliminated trade secret protection for such firmware, which would cause us to have to resort to copyright protection in case of unauthorized use.
We rely on information technology and any failure, inadequacy, interruption or security lapse of that technology, including any cybersecurity incidents, could harm our ability to operate our business effectively.
Experienced computer programmers and hackers may be able to penetrate our network and misappropriate or compromise our confidential information or that of third parties, create system disruptions or cause shutdowns. Computer programmers and hackers also may be able to develop and deploy viruses, worms and other malicious software programs that attack our products or otherwise exploit any security vulnerabilities of our products. While we employ a number of protective measures, including firewalls, network infrastructure vulnerability scanning, anti-virus and endpoint detection and response technologies, these measures may fail to prevent or detect attacks on our systems. We have experienced one intrusion, and we may experience future intrusions, which could adversely affect our business, operations, or products.
In addition, our hardware and software or third-party components and software that we utilize in our products may contain defects in design or manufacture, including “bugs” and other problems that could unexpectedly interfere with the operation or security of the products. The costs to us to eliminate or mitigate cyber or other security problems, bugs, viruses, worms, malicious software programs and security vulnerabilities could be significant and, if our efforts to address these problems are not successful, such problems could result in interruptions, delays, cessation of service and loss of existing or potential customers that may impede our sales, manufacturing, distribution or other critical functions.
Any claim that our products or systems are subject to a cybersecurity risk, whether valid or not, could damage our reputation and adversely impact our revenues and results of operations. We manage and store various proprietary information and sensitive or confidential data relating to our business as well as information from our suppliers and customers. Breaches of our or any of our third-party suppliers’ security measures or the accidental loss, inadvertent disclosure or unapproved dissemination of proprietary information or sensitive or confidential data about us or our customers or suppliers, including the potential loss or disclosure of such information or data as a result of fraud, trickery or other forms of deception, could expose us or our customers or suppliers to a risk of loss or misuse of this information, result in litigation and potential liability for us, damage our brand and reputation or otherwise harm our business.
To the extent we experience cyber-security incidents in the future, our relationships with our customers and suppliers may be materially impacted, our brand and reputation may be harmed and we could incur substantial costs in responding to and remediating the incidents and in resolving any investigations or disputes that may arise with respect to them, any of which would cause our business, operations, or products to be adversely affected. In addition, the cost and operational consequences of implementing and adding further data protection measures could be significant.
Our employees, consultants, distributors and other commercial partners may engage in misconduct or other improper activities, including noncompliance with regulatory standards and requirements, which could have an adverse effect on our business, prospects, financial condition and operating results.
We are exposed to the risk that our employees, consultants, distributors and other commercial partners may engage in misconduct or other illegal activity. Misconduct by these parties could include intentional, reckless or negligent conduct or other activities that violate laws and regulations, including production standards, U.S. federal and state fraud, abuse, data privacy and security laws, other similar non-U.S. laws or laws that require the true, complete and accurate reporting of financial information or data. It is not always possible to identify and deter misconduct by employees and other third parties, and the precautions we take to detect and prevent this activity may not be effective in controlling unknown or unmanaged risks or losses or in protecting us from governmental investigations or other actions or lawsuits stemming from a failure to be in compliance with such laws or regulations. In addition, we are subject to the risk that a person or government could allege such fraud or other misconduct, even if none occurred. If any such actions are instituted against us, and we are not successful in defending ourselves or asserting our rights, those actions could have a significant impact on our business, prospects, financial condition and operating results, including, without limitation, the imposition of significant civil, criminal and administrative penalties, damages, monetary fines, disgorgement, integrity oversight and reporting obligations to resolve allegations of non-compliance, imprisonment, other sanctions, contractual damages,