2.1 Cyber Security Analytics for Large-Scale Protection
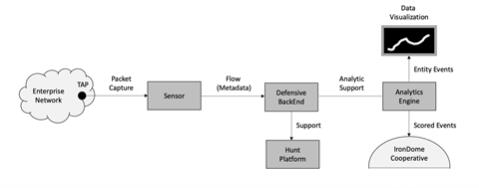
2.2 IronNet Cybersecurity Approach to Infrastructure Protection
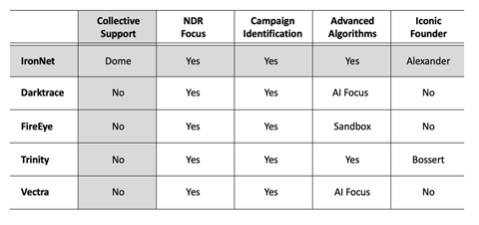
2.3 IronNet Cybersecurity Competitive Assessment
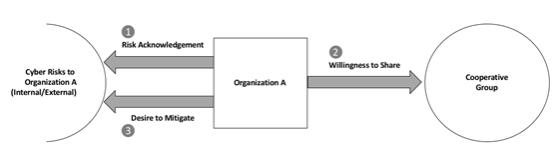
2.4 Developing an Infrastructure Protection Solution
Section 3: Assessment Conclusions
References
Introduction
Cyber security has advanced from a niche technical concern to a mainstream consideration for organizations of all sizes and in all sectors. Security protection concerns are most intense where safety or life-critical consequences might arise in response to a cyber threat. Power companies, financial services firms, telecommunications companies, military organizations, and government agencies thus have the greatest need for security protection, and now make considerable investments in cyber.
The primary security challenge in modern organizations is the complexity that has evolved in the typical business or government entity. Applications, networks, systems, endpoints, and data have experienced considerable sprawl as the costs associated with computing have come down so much. This is especially true for cloud-based infrastructure and SaaS-based applications, where cheap ubiquitous services are now available on-demand and for every purpose imaginable.
Modern organizations must therefore develop security protections that address such growth, often delivered in the context of digital transformation initiatives. An addition complication is that hackers have been augmented by determined, capable adversaries, often funded or otherwise backed by criminal groups or nation-states. Serious consideration must thus be given to the types of protections that are necessary to defend against the threat from such capable threat actors.
An addition dimension is that the velocity associated with computing infrastructure and their associated threats has accelerated. Agile DevOps processes generate new features at increasing rates, sometimes hourly for popular services, and hackers use automated platform to bombard targeted infrastructure with alarming intensity. Security engineers thus require controls that are automated and that address this challenge of increased speed. Manually controlled point solutions no longer stop threats.
A further complication is the massive and increasing scale associated with the types of systems operated by larger enterprise teams. Large-scale IT and network systems remove the ability for organizations to rely on manual maintenance, fixed configurations, and simple asset management. Furthermore, the visibility of assets that might be well-known by smaller organizations can only be approximated in large-scale settings. This greatly complicates the challenge of delivering security in a large-scale setting.
In response to these challenges, modern Chief Information Security Officers (CISOs) put considerable time and effort into designing and implementing a workable security architecture. Individual CISO-led teams – even if they focus their efforts – have come to recognize that they cannot address the cyber challenge on their own. It is well-understood in the cyber security community that enterprise security teams need considerable external assistance, coordination, and cooperative guidance.
Some of this assistance is obvious: Businesses rarely develop their own security tools, but rather buy from vendors or adjust open-source tools. Similarly, information sharing groups have emerged to support cooperative discussions between experts. It is therefore not controversial to suggest that business and agencies need to work together to address cyber threats. The big question, instead, is how this objective can be best achieved. This is one of the challenges addressed by IronNet.
Copyright © TAG Cyber LLC
February 13, 2021
Page 2 of 18