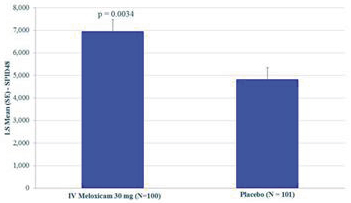
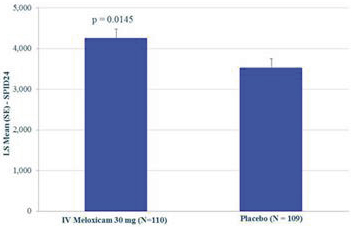
can provide only reasonable, not absolute, assurance that the control system’s objectives will be met. Because of the inherent limitations in all control systems, no evaluation of controls can provide absolute assurance that misstatements due to error or fraud will not occur or that all control issues and instances of fraud will be detected.
If we are not able to comply with the requirements of Section 404 of the Sarbanes-Oxley Act in a timely manner, or if we are unable to maintain proper and effective internal controls over financial reporting, we may not be able to produce timely and accurate financial statements. If that were to happen, our investors could lose confidence in our reported financial information, the market price of our stock could decline, and we could be subject to sanctions or investigations by the SEC or other regulatory authorities.
The security of our information technology systems may be compromised in the event of system failures, unauthorized access, cyberattacks or a deficiency in our cybersecurity, and confidential information, includingnon-public personal information that we maintain, could be improperly disclosed.
We rely extensively on information technology and systems including internet sites, data hosting, physical security, and software applications and platforms. Despite our security measures, our information technology systems, some of which are managed by third parties, may be susceptible to damage, disruptions or shutdowns due to computer viruses, attacks by computer hackers, failures during the process of upgrading or replacing software, power outages, user errors or catastrophic events. A significant breakdown, invasion, corruption, destruction or interruption of critical information technology systems, by our employees, others with authorized access to our systems or unauthorized persons could negatively impact or interrupt operations. For example, the loss of data from completed or ongoing clinical trials for our product candidates could result in delays in our regulatory approval efforts and significantly increase our costs to recover or reproduce the data. The use of technology, including cloud-based computing, creates opportunities for the unintentional dissemination or intentional destruction of confidential information stored in our systems or our third-party systems. We could also experience a business interruption, theft of confidential information or reputational damage from malware or other cyberattacks, which may compromise our systems or lead to data leakage, either internally or at our third-party providers.
As part of our business, we maintain large amounts of confidential information, includingnon-public personal information on patients and our employees. The maintenance of such information is governed by various rules and regulations in the jurisdictions in which we conduct our business, including by the General Data Privacy Regulation, or GDPR, in the European Union. Breaches in security, either internally or at our third-party providers, could result in the loss or misuse of this information, which could, in turn, result in potential regulatory actions or litigation, including material claims for damages, interruption to our operations, damage to our reputation or otherwise have a material adverse effect on our business, financial condition and operating results. Although we believe we have appropriate information security policies and systems in place in order to prevent unauthorized use or disclosure of confidential information, includingnon-public personal information, there can be no assurance that such use or disclosure will not occur.
Any such business interruption, theft of confidential information or reputational damage from malware or other cyberattacks, or violation of personal information laws, could have a material adverse effect on our business, financial condition, and results of operations.
If we fail to comply with data protection laws and regulations, we could be subject to government enforcement actions (which could include civil or criminal penalties), private litigation and/or adverse publicity, which could negatively affect our operating results and business.
We are subject to laws and regulations that address privacy and data security of patients who use our product candidates in the United States and in states in which we conduct our business. In the United States, numerous federal and state laws and regulations, including state data breach notification laws, state health information