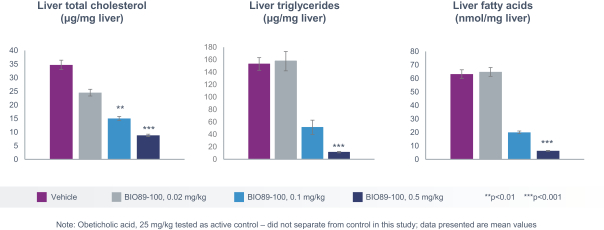
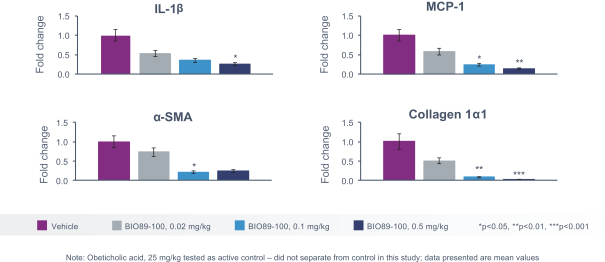
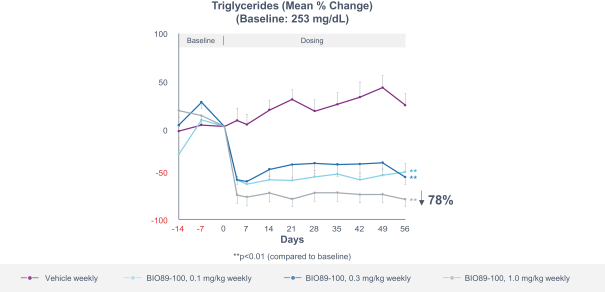
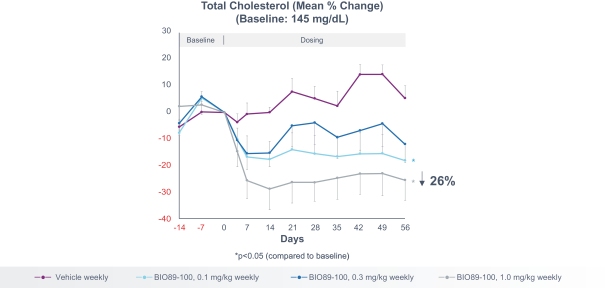
profits and future earnings, and the curtailment or restructuring of our operations. If any of the physicians or other healthcare providers or entities with whom we expect to do business is found not to be in compliance with applicable laws, that person or entity may be subject to significant criminal, civil or administrative sanctions, including exclusions from government funded healthcare programs.
We depend on our information technology systems and those of our third-party collaborators, service providers, contractors or consultants. Our internal computer systems, or those of our third-party collaborators, service providers, contractors or consultants, may fail or suffer security breaches, disruptions, or incidents, which could result in a material disruption of our development programs or loss of data or compromise the privacy, security, integrity or confidentiality of sensitive information related to our business and have a material adverse effect on our reputation, business, financial condition or results of operations.
In the ordinary course of our business, we collect, store and transmit large amounts of confidential information, including intellectual property, proprietary business information and personal information. Our internal technology systems and infrastructure, and those of our current or future third-party collaborators, service providers, contractors and consultants are vulnerable to damage from computer viruses, unauthorized access or use resulting from malware, natural disasters, terrorism, war and telecommunication and electrical failures,denial-of-service attacks, cyber-attacks or cyber-intrusions over the Internet, hacking, phishing and other social engineering attacks, persons inside our organizations (including employees or contractors), loss or theft, or persons with access to systems inside our organization. Attacks on information technology systems are increasing in their frequency, levels of persistence, sophistication and intensity, and they are being conducted by increasingly sophisticated and organized foreign governments, groups and individuals with a wide range of motives and expertise. In addition to extracting or accessing sensitive information, such attacks could include the deployment of harmful malware, ransomware,denial-of-service attacks, social engineering and other means to affect service reliability and threaten the security, confidentiality, integrity and availability of information. The prevalent use of mobile devices that access sensitive information also increases the risk of data security incidents which could lead to the loss of confidential information or other intellectual property. While to our knowledge we have not experienced any material system failure, accident or security breach to date, if such an event were to occur and cause interruptions in our operations or the operations of third-party collaborators, service providers, contractors and consultants, it could result in a material disruption of our development programs and significant reputational, financial, legal, regulatory, business or operational harm. The costs to us to mitigate, investigate and respond to potential security incidents, breaches, disruptions, network security problems, bugs, viruses, worms, malicious software programs and security vulnerabilities could be significant, and while we have implemented security measures to protect our data security and information technology systems, our efforts to address these problems may not be successful, and these problems could result in unexpected interruptions, delays, cessation of service and other harm to our business and our competitive position.
For example, the loss of clinical trial data from completed, ongoing or planned clinical trials for our product candidates could result in delays in our regulatory approval efforts and significantly increase our costs to recover or reproduce the data. To the extent that any real or perceived security breach affects our systems (or those of our third-party collaborators, service providers, contractors or consultants), or results in the loss of or accidental, unlawful or unauthorized access to, use of, release of, or other processing of personally identifiable information or damage to our data or applications or other data or applications relating to our technology or product candidates, or inappropriate disclosure of confidential or proprietary information, we could incur liabilities and the further development of our product candidates could be delayed. Such a breach may require notification to governmental agencies, the media or individuals pursuant to various foreign, domestic (federal and state) privacy and security laws, if applicable, including HIPAA, as amended by HITECH, and its implementing rules and regulations, as well as regulations promulgated by the Federal Trade Commission and state breach notification laws. In addition, our liability insurance may not be sufficient in type or amount to cover us against claims related to security breaches, cyberattacks and other related incidents.
Any failure or perceived failure by us or any third-party collaborators, service providers, contractors or consultants to comply with our privacy, confidentiality, data security or similar obligations, or any data security
39