objectives, we may experience constraints that could significantly impede our ability to achieve our development and commercial objectives, our ability to raise additional capital and our ability to implement our business strategy.
Our business, products or product pricing could be subject to negative publicity, which could have a material adverse effect on our reputation, business, financial position, results of operations, liquidity and cash flows.
In recent years, the pharmaceutical industry has been the subject of public complaints and significant publicity regarding the pricing of pharmaceutical products, including publicity and pressure resulting from prices charged by competitors and peer companies for new products as well as price increases by competitors and peer companies on older products that the public has deemed excessive. We may experience downward pricing pressure on the price of RUCONEST® and any other future approved products due to social or political pressure to lower the cost of drugs, which could reduce our revenue and future profitability. Orphan drugs in particular have received recent negative publicity for the perceived high prices charged for them by their manufacturers, and as a result orphan drug developers such as us may be negatively impacted by such publicity and any U.S. or other government regulatory response. Due to these factors, we may suffer public criticism and negative publicity in media coverage, by industry trade associations and legislators.
Any of the events or developments described above could result in reputational harm and reduced market acceptance and demand for our products, could harm our ability to market our products in the future, could cause us to incur significant expense, could cause our senior management to be distracted from execution of our business strategy, and could have a material adverse effect on our business, reputation, financial condition, results of operations, liquidity, cash flows and/or share price.
We depend on our information technology systems, and any failure of these systems could harm our business. Any real or perceived security breaches, loss of data, and other disruptions or incidents could compromise the privacy, security, integrity or confidentiality of sensitive information related to our business or prevent us from accessing critical information and expose us to liability and reputational harm, which could adversely affect our business, results of operations and financial condition.
We collect and maintain data and information that is necessary to conduct our business, and we are increasingly dependent on information technology systems and infrastructure to operate our business, including systems infrastructure operated and maintained by our third-party suppliers or providers. In the ordinary course of our business, we collect, store and transmit large amounts of confidential information, including intellectual property, proprietary business information and personal information. It is critical that we do so in a secure manner to maintain the privacy, security, confidentiality and integrity of such confidential information. We have established physical, electronic and organizational measures to safeguard and secure our systems and facilities to prevent an information compromise, and rely on commercially available systems, software, tools and monitoring to provide security for our information technology systems and the processing, transmission and storage of digital information. We have also outsourced elements of our information technology infrastructure, and as a result, a number of third-party vendors may or could have access to our confidential information. Our internal information technology systems and infrastructure, and those of our current and any future collaborators, contractors and consultants and other third parties on which we rely, are vulnerable to damage or unauthorized access or use resulting from computer viruses, malware, natural disasters, terrorism, war, telecommunication and electrical failures, denial-of-service attacks, cyber-attacks or cyber-intrusions over the Internet, hacking, phishing and other social engineering attacks, attachments to emails, persons inside our organization (including employees or contractors), lost or stolen devices, or persons with access to systems inside our organization.
The risk of a security breach or disruption or data loss, particularly through social engineering attacks, cyber-attacks or cyber intrusion, including by computer hackers, foreign governments and cyber terrorists, has generally increased as the number, intensity and sophistication of attempted attacks and intrusions from around the world have increased. In addition, the prevalent use of mobile devices that access confidential information increases the risk of data security breaches, which could lead to the loss of confidential information or other intellectual property. The costs to us to mitigate, investigate and respond to potential security incidents, breaches, disruptions, network security problems, bugs, viruses, worms, malicious software programs and security vulnerabilities could be significant, and while we have implemented security measures to protect our data security and information technology systems, our efforts to address these problems may not be successful, and these problems could result in unexpected interruptions, delays, cessation of service and other harm to our
22

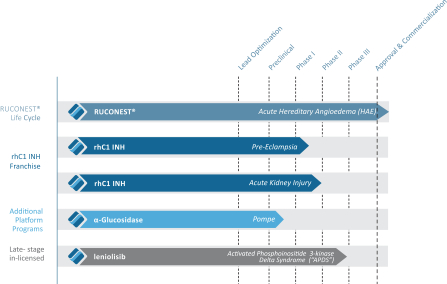
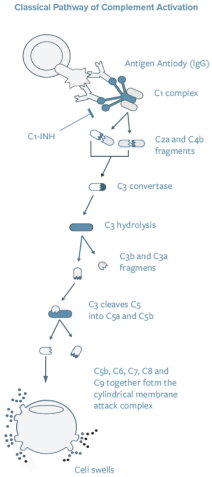
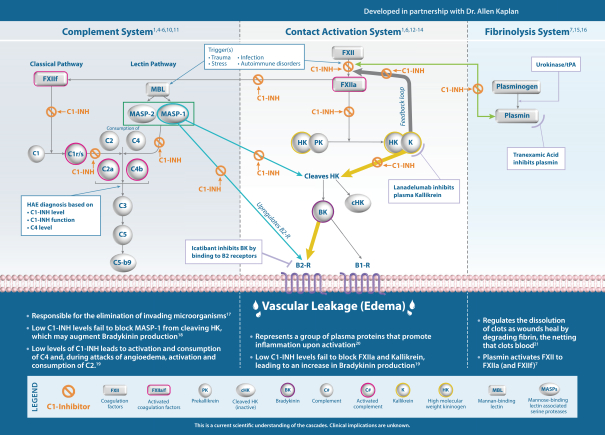
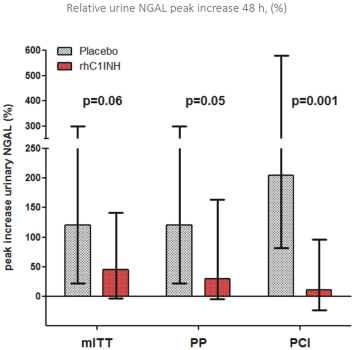
 Pharming Research & Development B.V. *
Pharming Research & Development B.V. *