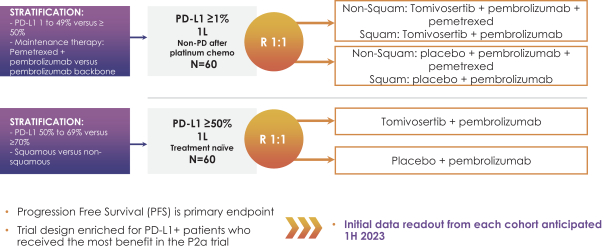
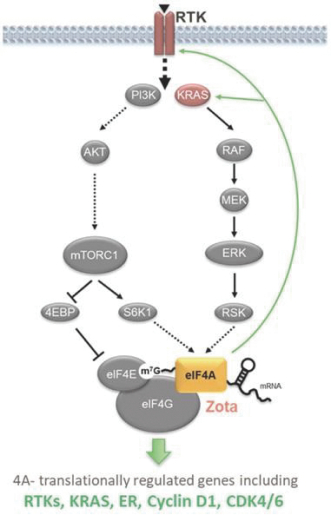
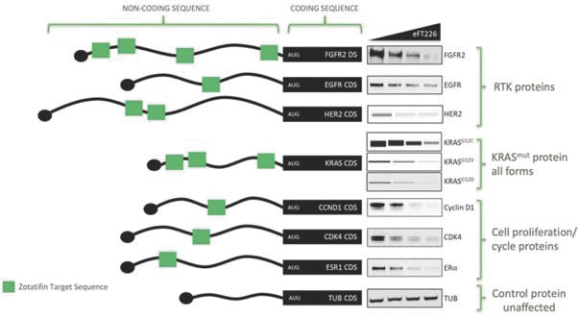
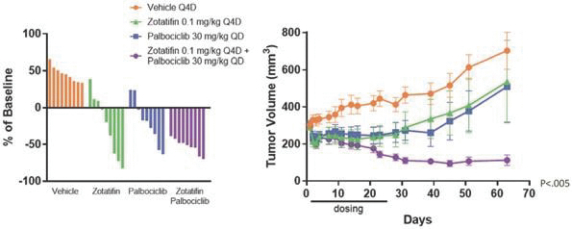
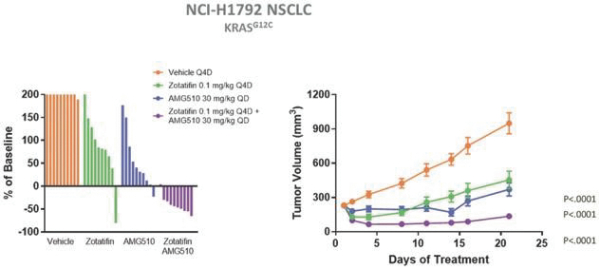
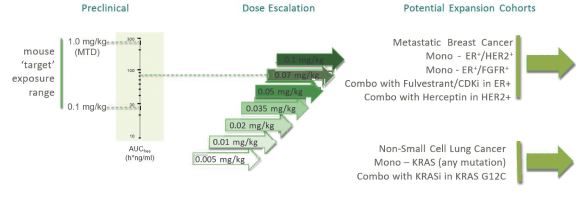
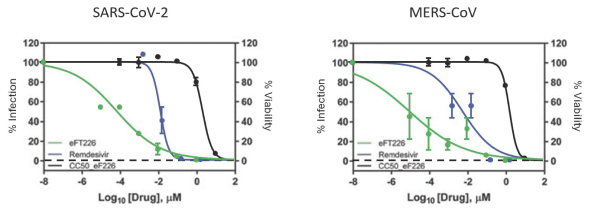
CROs fail to comply with such reporting obligations, the FDA or a foreign regulatory authority could take action, including criminal prosecution, the imposition of civil monetary penalties, seizure of our products or delay in approval or clearance of future products.
Our internal computer systems, or those of any of our CROs, manufacturers, other contractors or consultants or current or potential future collaborators, may fail or suffer security breaches, which could result in a material disruption of our product development programs, harm our reputation, significant fines, penalties and liability and loss of customers or sales.
The U.S. federal and various state and foreign governments have adopted or proposed requirements regarding the collection, distribution, use, security, and storage of personally identifiable information and other data relating to individuals, and federal and state consumer protection laws are being applied to enforce regulations related to the collection, use, and dissemination of such data. In the ordinary course of business, we collect, store, transmit and otherwise process large amounts of data including, without limitation, proprietary business information and personal information. Despite the implementation of security measures, our information technology systems (including infrastructure) and those of our current and any future CROs and other contractors, consultants, third-party service providers and collaborators are vulnerable to damage from computer viruses, cybersecurity threats (such as denial-of-service attacks, ransomware, supply chain attacks, cyber-attacks or cyber-intrusions over the Internet, hacking, phishing and other social engineering attacks), unauthorized access or use, natural disasters, terrorism, war and telecommunication and electrical failures. Our systems are also subject to compromise from internal threats, such as theft, misuse, unauthorized access or other improper or accidental actions by employees, vendors and other third parties with otherwise legitimate access to our systems. Third parties may also attempt to fraudulently induce our employees and contractors into disclosing sensitive information such as usernames, passwords or other information, or otherwise compromise the security of our electronic systems, networks, and/or physical facilities in order to gain access to our data. Additionally, due to the COVID-19 pandemic, our employees are temporarily working remotely, which may pose additional data security risks.
Given the unpredictability of the timing, nature and scope of information technology disruptions, there can be no assurance that any security procedures and controls that we or our third-party partners and service providers have implemented will be sufficient to prevent cyber-attacks from occurring. The latency of a compromise is often measured in months, but could be years, and we may not be able to detect a compromise in a timely manner. New techniques may not be identified until they are launched against a target, and we may be unable to anticipate these techniques or detect an incident, assess its severity or impact, react or appropriately respond in a timely manner or implement adequate preventative measures, resulting in potential data loss or other damage to our information technology systems.
If a security breach were to occur and cause interruptions in our operations or result in the unauthorized disclosure of or access to personally identifiable information or individually identifiable health information (potentially violating certain privacy laws), it could result in a material disruption of our development programs and our business operations, whether due to a loss of our trade secrets or other similar disruptions. Some of the federal, state and foreign government requirements include obligations of companies to notify individuals of security breaches involving particular personally identifiable information, which could result from breaches experienced by us or by our vendors, contractors, or organizations with which we have formed strategic relationships. Any security breach or other incident, whether actual or perceived, could impact our reputation, cause us to incur significant costs, including legal expenses, harm customer confidence, hurt our expansion into new markets, cause us to incur remediation costs, or cause us to lose existing customers. For example, the loss of clinical trial data from clinical trials could result in delays in our regulatory approval efforts and significantly increase our costs to recover or reproduce the data. We also rely on third parties to manufacture our product candidates, and similar events relating to their computer systems could also have a material adverse effect on our business. To the extent that any actual or perceived disruption or security breach affects our systems (or those of our third-party collaborators, service providers, contractors or consultants) or were to result in a loss of or
39