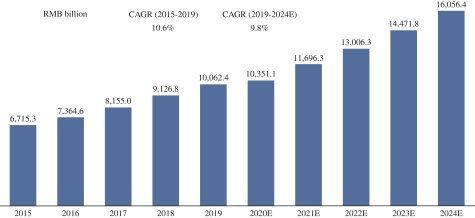
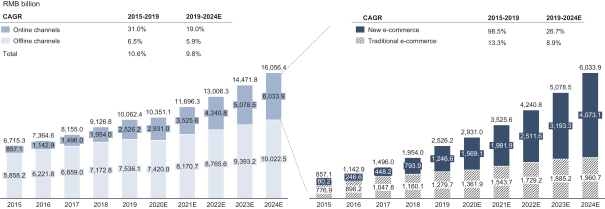
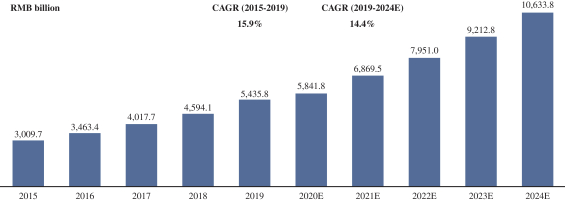
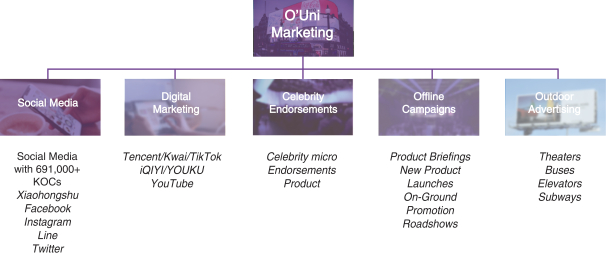
We are subject to a variety of laws and other obligations regarding data protection. Privacy concerns or security breaches could result in economic loss and damage our reputation, and expose us to legal penalties and liability.
We collect, process and store significant amounts of data, through our mobile applications, concerning our KOCs, users, brand partners and employees, including personal and transactional data. Such practices are subject to applicable laws, regulations, contractual obligations and industry standards relating to privacy, data protection, information security and consumer protection, including, among others, the Cybersecurity Law of the PRC and the E-Commerce Law of the PRC. See “Regulation—Regulations Relating to Internet Information Security and Privacy Protection.”
These requirements on our practices may be interpreted and applied in a manner that is inconsistent or may conflict with other rules or our practices. As a result, our practices may have not complied or may not comply in the future with all such laws, regulations, requirements and obligations. Any failure to comply with privacy laws, regulations and policies, or abide by privacy or data protection related contractual obligations could adversely affect our reputation, brand and business, and may result in claims, proceedings or actions against us by governmental entities or others or other liabilities or require us to change our operations.
We are subject to risks resulting from privacy concerns and security breaches. While we have taken reasonable measures to protect our data, we cannot guarantee the effectiveness. Our cybersecurity measures may not detect or prevent all attempts to interrupt or illegally access our systems, including distributed denial-of-service attacks, viruses, malicious software, break-ins, phishing attacks, social engineering, security breaches or other attacks and similar disruptions that may jeopardize the security of information stored in and transmitted by our systems or maintained by us. As techniques used to sabotage or illegally access systems change frequently, we may be unable to anticipate, or implement adequate measures to protect against, these attacks. Breaches of our cybersecurity measures could result in unauthorized access to our systems, misappropriation or deletion of information or data, or other interruption to our business operations.
We may also fail to prevent data leakage due to misconducts of our employees. To the extent necessary and permissible, we share privacy data with certain third parties such as logistic companies. If these third parties fail to preserve privacy data from us, our reputation and operations may also be adversely affected.
Any fraudulent, collusive or illegal activities by our competitors or our employees would adversely affect our business, financial condition and results of operations.
From time to time, we may face unfair competitions from other companies through manipulation of certain operating data, which are critical in attracting active buyers, KOCs and investors. For example, sellers on other third-party platforms may engage in fictitious or “phantom” transactions with themselves or collaborators in order to artificially inflate their sales volume, ratings and search results rankings on the online marketplaces or forge key statistic on social media platforms for the purpose of inflating their reputation and popularity. Such activities may deceive our buyers, KOCs and investors into believing that such platforms are more popular, reliable or trusted than their competitors. If such activities cannot be detected and prohibited properly or promptly by the regulatory bodies or the online marketplaces and platforms, our business may be negatively impacted and our results of operations may be adversely affected.
In addition, we may face other malicious acts from third parties. Malicious orders could also subject us to negative publicity and third-party investigations in relation to fictitious or “phantom” transactions. We have adopted procedures to detect and deal with malicious orders. Despite the measures taken, we cannot assure you that our business would not be adversely affected should we continue to experience this, or that malicious act from third parties.
Moreover, fraudulent, collusive or illegal activities by our employees, such as fraud, bribery or corruption, could also subject us to liability, negative publicity, punishments by the online platforms, including the closure of
29