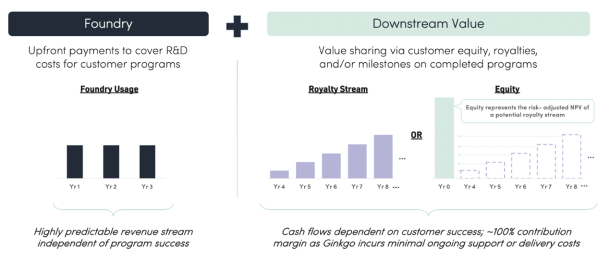
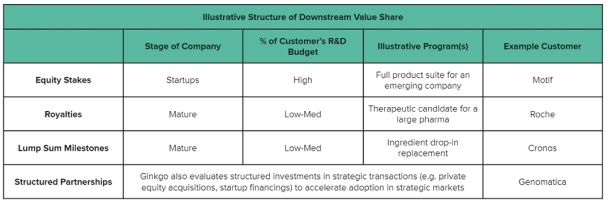
The FCPA also requires that we keep accurate books and records and maintain a system of adequate internal controls. While we have controls to address compliance with such laws, and will continue to review and enhance our compliance program, we cannot assure you that our employees, agents, representatives, business partners or third-party intermediaries will always comply with our policies and applicable law, for which we may be ultimately held responsible.
Any allegations or violation of the FCPA or other applicable anti-bribery, anti-corruption laws and anti-money laundering laws may result in whistleblower complaints, sanctions, settlements, investigations, prosecution, enforcement actions, substantial criminal fines and civil penalties, disgorgement of profits, imprisonment, debarment, tax reassessments, breach of contract and fraud litigation, loss of export privileges, suspension or debarment from U.S. government contracts, adverse media coverage, reputational harm and other consequences, all of which may have an adverse effect on our reputation, business, financial condition, results of operations and prospects. Responding to an investigation or action can also result in a materially significant diversion of management’s attention and resources and significant defense costs and other professional fees.
We are increasingly dependent on information technology systems and infrastructure, including services licensed, leased or purchased from third parties such as cloud computing infrastructure and operating systems, to operate its business. In the ordinary course of business, we collect, store, process and transmit large amounts of sensitive information, including intellectual property, proprietary business information, personal information and other confidential information. It is critical that we do so in a secure manner to maintain the confidentiality, integrity and availability of such sensitive information. We have also outsourced elements of our operations (including elements of its information technology infrastructure) to third parties, and as a result, we manage a number of third-party vendors who may have access to our networks or our confidential information. While we take measures to safeguard and protect this information, threats to network and data security are increasingly diverse and sophisticated. As a result of the
COVID-19
pandemic, we may also face increased cybersecurity risks due to our reliance on internet technology and the number of our employees working remotely, which may create additional opportunities for cybercriminals to exploit vulnerabilities. Despite our efforts, training and processes to prevent security breaches and incidents, our information technology systems, servers, and those of third parties that we use in our operations are vulnerable to cybersecurity risks, including cyberattacks such as viruses and worms, phishing attacks and other forms of social engineering,
attacks, ransomware attacks, physical or electronic
break-ins,
third-party or employee theft or misuse, and other negligent actions, errors or malfeasance by employees or other third parties, and similar disruptions from unauthorized tampering with its servers and computer systems or those of third parties that we use in its operations, which could lead to interruptions, delays, loss or corruption of critical data, unauthorized access to or acquisition of health-related and other personal information. In addition, we may be the target of email scams and other social engineering attacks that attempt to acquire personal information or company assets or access to our systems. Despite our efforts to create security barriers to such threats, we may not be able to entirely mitigate these risks. Our third-party service providers face similar risks. Any cyberattack that attempts to obtain our data or assets, including data that we maintain on behalf of its customers, disrupt its service, or otherwise access its systems, or those of third parties we use, or any other security breach or incident, could adversely affect our business, financial condition and operating results, be expensive to remedy, and damage our reputation. We and our third-party service providers may face difficulties or delays in identifying or otherwise responding to any attacks or actual or potential security breaches or security incidents. We may incur significant costs and operational consequences of investigating, remediating, eliminating and putting in place additional tools and devices designed to prevent actual or perceived security breaches and other security incidents, including in response to any actual or perceived incident we may suffer, and substantial costs to comply with any notification or other legal obligations resulting from any security breaches or other security incidents. In addition, any such breaches or incidents, or the perception that they have occurred, may result in negative publicity, and could have an adverse effect on our business, financial condition, and operating results.