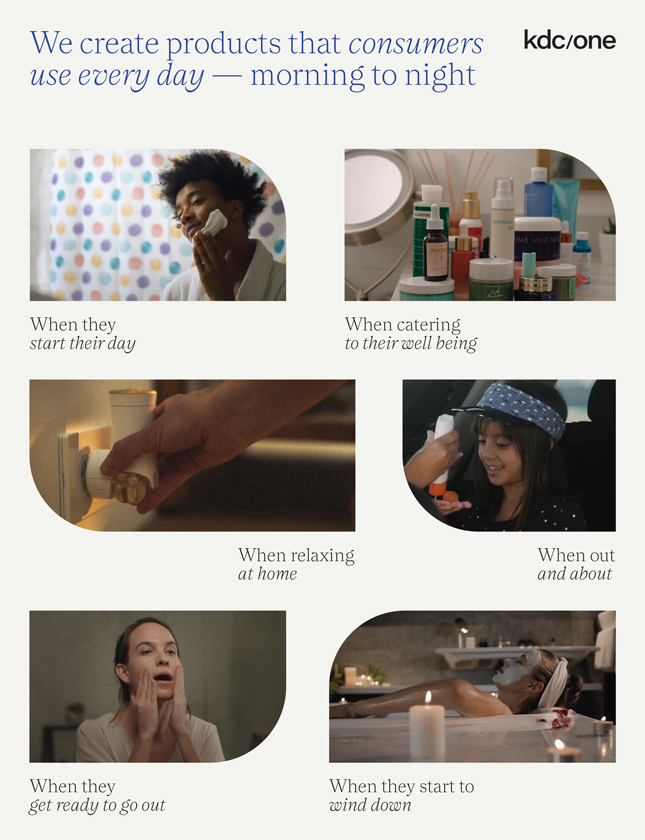
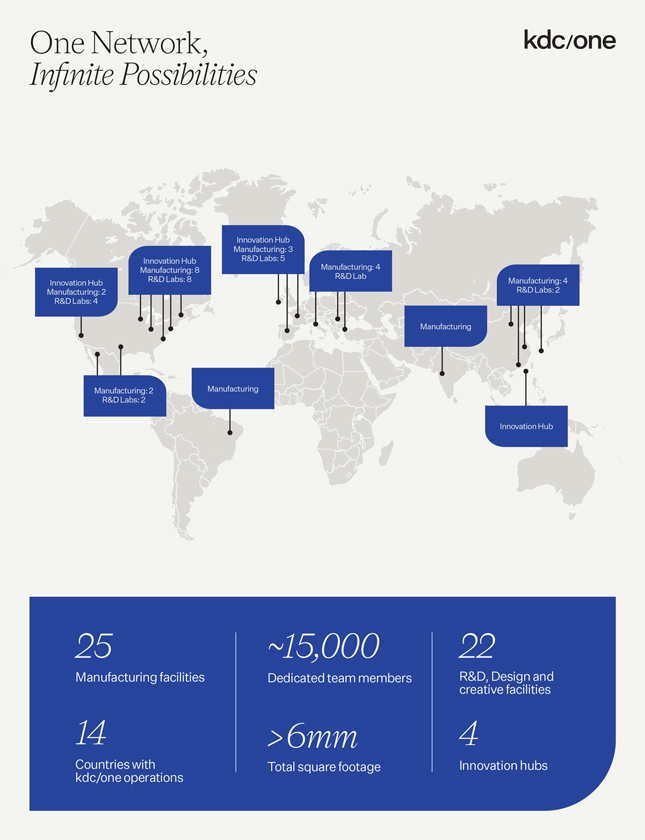
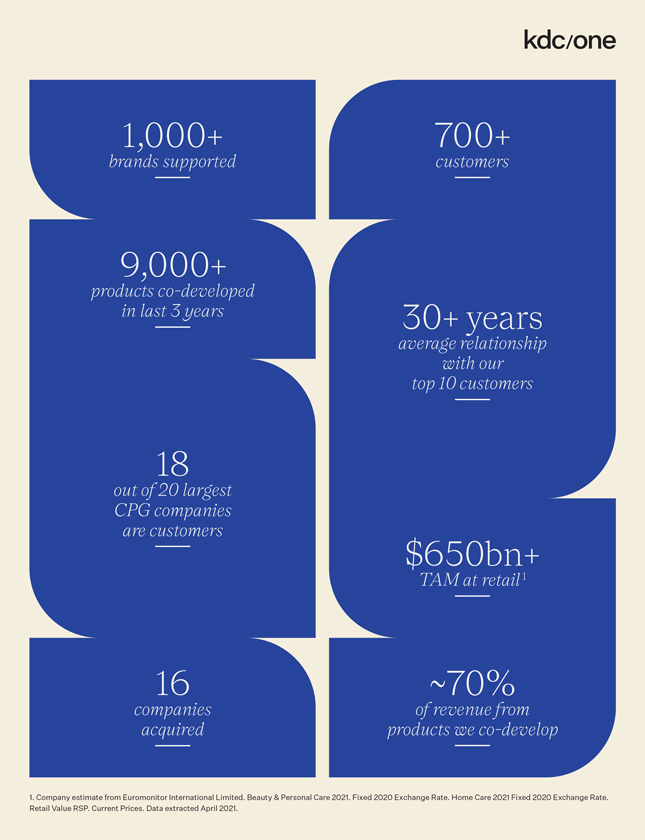
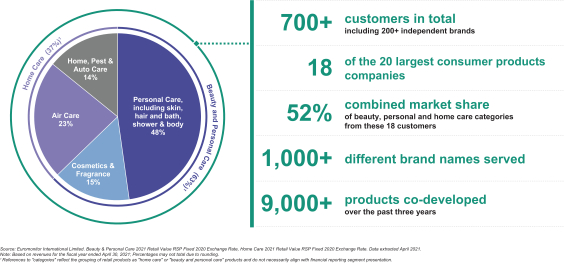
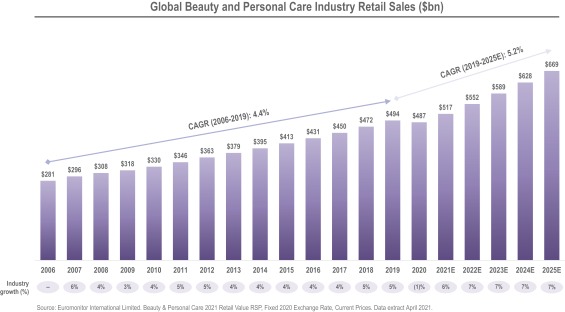
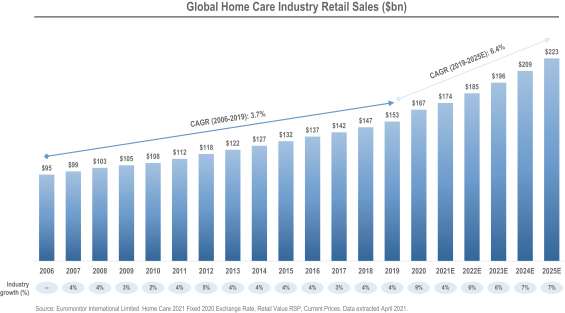
promises and assurances about data privacy and security can subject us to potential government or legal action if they are found to be deceptive, unfair or misrepresentative of our actual practices. Any concerns about our data privacy and security practices, even if unfounded, could damage the reputation of our businesses and discourage potential users from our products and services. Any of the foregoing could have an adverse effect on our business, financial condition, results of operations and prospects.
Risks Related to Our Intellectual Property and Information Technology
Breaches or failures of our information technology systems or website security, the theft, unauthorized access, acquisition, use, disclosure, modification or misappropriation of personal information, the occurrence of fraudulent activity, or other cybersecurity or data security-related incidents may have an adverse impact on our business, financial condition, results of operations and prospects.
In the course of operating our business, we collect, use, store, disclose, transfer and otherwise process personal information and other confidential, proprietary and sensitive data. Breaches or failures of security involving our systems or website or those of any of our external service providers may occur, and could result in the theft, unauthorized access, acquisition, use, disclosure, modification or misappropriation of personal information of our customers, consumers, employees or third parties with whom we conduct business, or other confidential, proprietary and sensitive data, fraudulent activity, or system disruptions or shutdowns. The occurrence of any actual or attempted breach, failure of security or fraudulent activity, the reporting of such an incident, whether accurate or not, or our failure to make adequate or timely disclosures to the public or law enforcement agencies following any such event, whether due to delayed discovery or a failure to follow existing protocols, could result in claims made against us or our external service providers, which could result in state, federal and/or international litigation and related financial liabilities, as well as criminal penalties or civil liabilities, regulatory actions from state, federal and/or international governmental authorities, and significant fines, orders, sanctions, litigation and claims against us by customers or consumers or other third parties and related indemnification obligations. Actual or perceived security breaches or failures could also cause financial losses, increased costs, interruptions in the operations of our businesses, misappropriation of assets, significant damage to our brand and reputation with customers and third parties with whom we do business, and result in adverse publicity, loss of customer confidence, distraction to our management, and reduced sales and profits.
Such breaches, failures and fraudulent activity may take many forms, including check fraud, fraudulent inducement, electronic fraud, wire fraud, computer viruses, phishing, social engineering, denial or degradation of service attacks, malware, ransomware or other cyberattacks, and other dishonest acts, any of which could be the result of a circumvention or failure of our data security processes, procedures, tools, and controls. Our systems are also subject to compromise from internal threats, such as theft, misuse, unauthorized access or other improper actions by employees, external service providers and other third parties with otherwise legitimate access to our systems and website. Data security-related incidents and fraudulent activity are increasing in frequency and evolving in nature and may be exacerbated during the current work-from-home environment. We rely on a framework of security, processes, procedures, tools, training and controls designed to protect our information and assets but, given the unpredictability of the timing, nature and scope of data security-related incidents and fraudulent activity, there can be no assurance that any security procedures and controls that we or our external service providers have implemented will be sufficient to prevent data security-related incidents or other fraudulent activity from occurring. Furthermore, because the methods of attack and deception change frequently, are increasingly complex and sophisticated, and can originate from a wide variety of sources, including third parties such as external service providers and even nation-state actors, despite our reasonable efforts to ensure the integrity of our systems and website, it is possible that we may not be able to anticipate, detect, appropriately react and respond to, or implement effective preventative measures against, all security breaches and failures and fraudulent activity.
We have been, and may in the future be, required to expend significant capital and other resources to protect against, respond to, and recover from any potential, attempted, or existing security breaches or failures and their
43