- SNTI Dashboard
- Financials
- Filings
-
Holdings
-
Transcripts
- ETFs
- Insider
- Institutional
- Shorts
-
S-1/A Filing
Senti Biosciences (SNTI) S-1/AIPO registration (amended)
Filed: 29 Jul 22, 4:23pm
As filed with the Securities and Exchange Commission on July 29, 2022
Registration No. 333-265873
UNITED STATES
SECURITIES AND EXCHANGE COMMISSION
Washington, D.C. 20549
AMENDMENT NO. 1
TO
FORM S-1
REGISTRATION STATEMENT
UNDER
THE SECURITIES ACT OF 1933
SENTI BIOSCIENCES, INC.
(Exact name of registrant as specified in its charter)
| Delaware | 2836 | 86-2437900 | ||
(State or other jurisdiction of incorporation or organization) | (Primary Standard Industrial Classification Code Number) | (I.R.S. Employer Identification No.) |
2 Corporate Drive, First Floor
South San Francisco, CA 94080
(650) 382-3281
(Address, including zip code, and telephone number, including area code, of registrant’s principal executive offices)
Timothy Lu, M.D., Ph.D
Chief Executive Officer
Senti Biosciences, Inc.
2 Corporate Drive, First Floor
South San Francisco, CA 94080
Telephone: (650) 382-3281
(Name, address, including zip code, and telephone number, including area code, of agent for service)
Copies to:
|
Jocelyn M. Arel Maggie Wong Michael R. Patrone Goodwin Procter LLP 620 Eighth Avenue New York, NY 10018 (212) 813-8800 |
Approximate date of commencement of proposed sale to the public: From time to time after this Registration Statement becomes effective.
If any of the securities being registered on this Form are to be offered on a delayed or continuous basis pursuant to Rule 415 under the Securities Act of 1933 check the following box: ☒
If this form is filed to register additional securities for an offering pursuant to Rule 462(b) under the Securities Act, check the following box and list the Securities Act registration statement number of the earlier effective registration statement for the same offering. ☐
If this form is a post-effective amendment filed pursuant to Rule 462(c) under the Securities Act, check the following box and list the Securities Act registration statement number of the earlier effective registration statement for the same offering. ☐
If this form is a post-effective amendment filed pursuant to Rule 462(d) under the Securities Act, check the following box and list the Securities Act registration statement number of the earlier effective registration statement for the same offering. ☐
Indicate by check mark whether the registrant is a large accelerated filer, an accelerated filer, a non-accelerated filer, smaller reporting company, or an emerging growth company. See the definitions of “large accelerated filer,” “accelerated filer,” “smaller reporting company,” and “emerging growth company” in Rule 12b-2 of the Exchange Act.
| Large accelerated filer | ☐ | Accelerated filer | ☐ | |||
| Non-accelerated filer | ☒ | Smaller reporting company | ☒ | |||
| Emerging growth company | ☒ | |||||
If an emerging growth company, indicate by check mark if the registrant has elected not to use the extended transition period for complying with any new or revised financial accounting standards provided pursuant to Section 7(a)(2)(B) of the Securities Act. ☒
The registrant (the “Registrant”) hereby amends this registration statement (this “Registration Statement”) on such date or dates as may be necessary to delay its effective date until the Registrant shall file a further amendment which specifically states that this Registration Statement shall thereafter become effective in accordance with Section 8(a) of the Securities Act of 1933 or until this Registration Statement shall become effective on such date as the Securities and Exchange Commission, acting pursuant to said Section 8(a), may determine.
The information in this preliminary prospectus is not complete and may be changed. These securities may not be issued until the registration statement filed with the U.S. Securities and Exchange Commission is effective. This preliminary prospectus is not an offer to sell these securities and does not constitute the solicitation of an offer to buy these securities in any jurisdiction where the offer or sale is not permitted.
SUBJECT TO COMPLETION, DATED JULY 29, 2022
PRELIMINARY PROSPECTUS

SENTI BIOSCIENCES, INC.
35,444,908 Shares of Common Stock
This prospectus relates to the issuance by us of up to 2,000,000 shares of our common stock, par value $0.0001 per share (“Senti Common Shares”) that may be issued as Contingency Consideration from time to time upon achievement of certain stock price thresholds (the “Earn-out Shares”).
In addition, this prospectus relates to the offer and sale from time to time by the selling securityholders named in this prospectus (collectively, the “Selling Securityholders”), or their permitted transferees, of up to (i) 15,168,616 Senti Common Shares originally issued to certain of our affiliates as consideration in connection with the Business Combination at a per share value of $10.00 per share, (ii) up to 6,233,292 Senti Common Shares issuable upon the exercise of stock options at exercise prices ranging from $2.66 to $9.92 per share, issued to certain of our affiliates upon the conversion of stock options in Senti Sub I, Inc. (formerly Senti Biosciences, Inc.) in connection with the Business Combination, (iii) 4,878,972 Senti Common Shares distributed by Dynamics Sponsor LLC (“Sponsor”) to certain of its members who were affiliates of our predecessor, Dynamics Special Purpose Corp. (“DYNS”) prior to the completion of the Business Combination, which shares were originally issued to Sponsor at a price per share of $0.004, (iv) 715,500 Senti Common Shares distributed by Sponsor to certain of its members who were affiliates of DYNS prior to the completion of the Business Combination, which shares were originally issued to Sponsor at a price per share of $10.00 in a private placement transaction completed concurrently with the initial public offering of DYNS, (v) 871,028 Senti Common Shares issued to certain of the Selling Securityholders (the “Anchor Investors”) in consideration for their agreement not to redeem their shares of Class A Common Stock of DYNS in connection with the Business Combination, (vi) 5,060,000 Senti Common Shares originally purchased at a purchase price of $10.00 per share at the closing of the Business Combination by a number of subscribers pursuant to separate PIPE subscription agreements (the “PIPE Shares”), and (vii) 517,500 Senti Common Shares issued to Bayer Healthcare LLC at an effective exchange price of $10.00 per share at the closing of the Business Combination upon the cancellation and exchange of the Convertible Note. Although approximately 80.7% of the Senti Common Shares registered on behalf of the Selling Securityholders are subject to a lock-up provision in our Amended and Restated Bylaws or pursuant contractual agreements that prohibit sales of such shares until at least June 2023, sales of any of the foregoing Senti Common Shares, which comprise a significant portion of our public float, by the Selling Securityholders, or the perception that such sales may occur, could have a significant negative impact on the trading price of our common stock.
This prospectus provides you with a general description of such securities and the general manner in which the Selling Securityholders may offer or sell the securities. More specific terms of any securities that the Selling Securityholders may offer or sell may be provided in a prospectus supplement that describes, among other things, the specific amounts and prices of the securities being offered and the terms of the offering. The prospectus supplement may also add, update or change information contained in this prospectus.
We will not receive any proceeds from the sale of Senti Common Shares by the Selling Securityholders pursuant to this prospectus. However, we will pay the expenses, other than any underwriting discounts and commissions, associated with the sale of securities pursuant to this prospectus. We are registering certain of the securities for resale pursuant to the Selling Securityholders’ registration rights under certain agreements between us and the Selling Securityholders. Our registration of the securities covered by this prospectus does not mean that either we or the Selling Securityholders will issue, offer or sell, as applicable, any of the securities. The Selling Securityholders may offer and sell the securities covered by this prospectus in a number of different ways and at varying prices. We provide more information about how the Selling Securityholders may sell the shares in the section entitled “Plan of Distribution.”
You should read this prospectus and any prospectus supplement or amendment carefully before you invest in our securities.
Our common stock is listed on The Nasdaq Global Market (“Nasdaq”) under the symbol “SNTI”. On July 28, 2022, the last quoted sale price for the Senti Common Shares as reported on Nasdaq was $1.86 per share.
We are an “emerging growth company” under applicable federal securities laws and will be subject to reduced public company reporting requirements.
Investing in our securities involves a high degree of risk. Before buying any securities, you should carefully read the discussion of the risks of investing in our securities in “Risk Factors” beginning on page 11 of this prospectus.
Neither the Securities and Exchange Commission nor any state securities commission has approved or disapproved of the securities to be issued under this prospectus or determined if this prospectus is truthful or complete. Any representation to the contrary is a criminal offense.
The date of this prospectus is .
| Page | ||||
| 1 | ||||
| 2 | ||||
| 4 | ||||
| 6 | ||||
| 11 | ||||
| 83 | ||||
| 83 | ||||
| 84 | ||||
UNAUDITED PRO FORMA CONDENSED COMBINED FINANCIAL INFORMATION | 85 | |||
| 100 | ||||
SENTI MANAGEMENT’S DISCUSSION AND ANALYSIS OF FINANCIAL CONDITION AND RESULTS OF OPERATIONS | 180 | |||
DYNS MANAGEMENT’S DISCUSSION AND ANALYSIS OF FINANCIAL CONDITION AND RESULTS OF OPERATIONS | 193 | |||
| 198 | ||||
| 204 | ||||
| 221 | ||||
| 222 | ||||
| 225 | ||||
| 230 | ||||
| 237 | ||||
| 240 | ||||
| 242 | ||||
| 247 | ||||
| 250 | ||||
| 250 | ||||
| 251 | ||||
| 252 | ||||
FINANCIAL STATEMENTS AND SUPPLEMENTARY DATA INDEX TO FINANCIAL STATEMENTS | F-1 | |||
i
This document contains references to trademarks, trade names and service marks belonging to other entities. Solely for convenience, trademarks, trade names and service marks referred to in this prospectus may appear without the ® or TM symbols, but such references are not intended to indicate, in any way, that the applicable licensor will not assert, to the fullest extent under applicable law, its rights to these trademarks and trade names. We do not intend our use or display of other companies’ trade names, trademarks or service marks to imply a relationship with, or endorsement or sponsorship of us by, any other companies.
1
As used in this prospectus, unless otherwise noted or the context otherwise requires, references to the following capitalized terms have the meanings set forth below:
“Business Combination” means the transactions contemplated by the Business Combination Agreement, including the merger between Merger Sub and Senti.
“Business Combination Agreement” means the Business Combination Agreement, dated as of December 19, 2021, as amended or modified from time to time, including as amended by Amendment No. 1 to Business Combination Agreement, dated as of February 12, 2022 and Amendment No. 2, dated as of May 19, 2022, in each case, by and among DYNS, Merger Sub and Senti.
“Board” means the board of directors of Senti.
“Bylaws” means the Amended and Restated Bylaws of Senti.
“Closing” or “Closing Date” means June 8, 2022.
“Code” means the Internal Revenue Code of 1986, as amended.
“Contingency Consideration” means the aggregate of 2,000,000 Senti Common Shares that certain of the Selling Securityholders may be eligible to receive based on the share price of Senti Common Shares following the Business Combination or, in some circumstances, upon a change of control of Senti, as described in the Business Combination Agreement.
“Continental” means Continental Stock Transfer & Trust Company, as Senti’s transfer agent.
“Convertible Note” means the unsecured convertible promissory note in the principal amount of $5,175,000 issued by Senti Sub I, Inc. (formerly Senti Biosciences, Inc.), to Bayer Healthcare LLC on May 19, 2022.
“Certificate of Incorporation” or “Charter” means the Second Amended and Restated Certificate of Incorporation of Senti.
“DGCL” means the Delaware General Corporation Law, as may be amended from time to time.
“DYNS” means Dynamics Special Purpose Corp., a Delaware corporation.
“Exchange Act” means the Securities Exchange Act of 1934, as amended.
“Founder Shares” means the DYNS Class B Common Shares and Senti Common Shares issued upon the automatic conversion thereof upon the closing of the Business Combination.
“GAAP” means the generally accepted accounting principles in the United States, as applied on a consistent basis.
“Initial Public Offering” means the initial public offering of DYNS, which closed on May 28, 2021.
“Investment Company Act” means the Investment Company Act of 1940, as amended.
“JOBS Act” means the Jumpstart Our Business Startups Act of 2012.
2
“Merger Sub” means Explore Merger Sub, Inc., a Delaware corporation and wholly-owned subsidiary of DYNS.
“Public Shares” means the shares of DYNS Class A Common Stock issued in the Initial Public Offering.
“Public Stockholders” means holders of Public Shares.
“SEC” means the U.S. Securities and Exchange Commission.
“Securities Act” means the Securities Act of 1933, as amended.
“Senti” means Senti Biosciences, Inc., a Delaware corporation (which, prior to the consummation of the Business Combination, was known as DYNS).
“Senti Common Shares” means the common stock, par value $0.0001 per share, of Senti.
“Special Meeting” means the special meeting of stockholders of DYNS, held on June 7, 2022.
“Sponsor” means Dynamics Sponsor LLC, a Delaware limited liability company.
“Trust Account” means the trust account maintained by Continental, acting as trustee, established for the benefit of Public Stockholders in connection with the Initial Public Offering.
3
This prospectus and some of the information incorporated by reference, includes forward-looking statements regarding, among other things, the plans, strategies, and prospects, both business and financial, of Senti. These statements are based on the beliefs and assumptions of the management of Senti. Although Senti believes that their respective plans, intentions, and expectations reflected in or suggested by these forward-looking statements are reasonable, it cannot assure you that it will achieve or realize these plans, intentions, or expectations. Forward-looking statements are inherently subject to risks, uncertainties, and assumptions. Generally, statements that are not historical facts, including statements concerning possible or assumed future actions, business strategies, events or results of operations, and any statements that refer to projections, forecasts, or other characterizations of future events or circumstances, including any underlying assumptions, are forward-looking statements. These statements may be preceded by, followed by or include the words “believes”, “estimates”, “expects”, “projects”, “forecasts”, “may”, “might”, “will”, “should”, “seeks”, “plans”, “scheduled”, “possible”, “anticipates”, “intends”, “aims”, “works”, “focuses”, “aspires”, “strives” or “sets out” or similar expressions. Forward-looking statements are not guarantees of performance. You should not put undue reliance on these statements which speak only as of the date hereof. Forward-looking statements contained in this prospectus include, for example, statements about:
| • | our ability to realize the benefits expected from the Business Combination; |
| • | the projected financial information, anticipated growth rate, and market opportunities of Senti; |
| • | our ability to maintain the listing of Senti Common Shares on Nasdaq, and the potential liquidity and trading of such securities; |
| • | our ability to grow and manage growth profitably; |
| • | our ability to raise financing in the future, if and when needed; |
| • | our success in retaining or recruiting, or adapting to changes in, our officers, key employees, or directors; |
| • | the initiation, cost, timing, progress and results of research and development activities, preclinical studies or clinical trials with respect to our current and potential future product candidates; |
| • | our ability to develop and advance our gene circuit platform technologies; |
| • | our ability to identify product candidates using our gene circuit platform technologies; |
| • | our ability to identify, develop and commercialize product candidates; |
| • | our ability to advance our current and potential future product candidates into, and successfully complete, preclinical studies and clinical trials; |
| • | our ability to obtain and maintain regulatory approval of our current and potential future product candidates, and any related restrictions, limitations and/or warnings in the label of an approved product candidate; |
| • | our ability to obtain funding for our operations; |
| • | our ability to obtain and maintain intellectual property protection for our technologies and any of our product candidates; |
| • | our ability to successfully commercialize our current and any potential future product candidates; |
| • | the rate and degree of market acceptance of our current and any potential future product candidates; |
| • | regulatory developments in the United States and international jurisdictions; |
| • | potential liability lawsuits and penalties related to our technologies, product candidates and current and future relationships with third parties; |
4
| • | our ability to attract and retain key scientific and management personnel; |
| • | our ability to effectively manage the growth of our operations; |
| • | our ability to contract with third-party suppliers and manufacturers and their ability to perform adequately under those arrangements; |
| • | our ability to compete effectively with existing competitors and new market entrants; |
| • | potential effects of extensive government regulation; |
| • | our future financial performance and capital requirements; |
| • | our ability to implement and maintain effective internal controls; |
| • | the impact of supply chain disruptions; |
| • | the impact of the COVID-19 pandemic on our business, including our preclinical studies and potential future clinical trials; |
| • | unfavorable global economic conditions, including inflationary pressures, market volatility, acts of war and civil and political unrest; and |
| • | other factors detailed under the section entitled “Risk Factors.” |
These and other factors that could cause actual results to differ from those implied by the forward-looking statements in this prospectus described under the heading “Risk Factors” and elsewhere in this prospectus. The risks described under the heading “Risk Factors” are not exhaustive. New risk factors emerge from time to time and it is not possible to predict all such risk factors, nor can we assess the impact of all such risk factors on the business of Senti or the extent to which any factor or combination of factors may cause actual results to differ materially from those contained in any forward-looking statements. All forward-looking statements attributable to Senti or to persons acting on our behalf are expressly qualified in their entirety by the foregoing cautionary statements. We undertake no obligations to update or revise publicly any forward-looking statements, whether as a result of new information, future events, or otherwise, except as required by law.
5
The following summary highlights information contained elsewhere in this prospectus. It does not contain all the information you should consider before investing in the Senti Common Shares. You should read this entire prospectus carefully, including the sections titled “Risk Factors,” “Business,” “Management’s Discussion and Analysis of Financial Condition and Results of Operations,” “Where You Can Find More Information,” “Unaudited Pro Forma Condensed Combined Financial Information,” and our consolidated financial statements and related notes included elsewhere in this prospectus, before making an investment decision. In this prospectus, unless the context requires otherwise, all references to “we,” “our,” “us,” “Senti,” the “Registrant,” and the “Company” refer to Senti Biosciences, Inc. and its consolidated subsidiaries following the Business Combination.
Overview
Senti is a preclinical biotechnology company developing next-generation cell and gene therapies engineered with its gene circuit platform technologies to fight challenging diseases. Our mission is to create a new generation of smarter therapies that can outmaneuver complex diseases in ways previously not implemented by conventional medicines. To accomplish this mission, we have built a synthetic biology platform that we believe may enable us to program next-generation cell and gene therapies with what we refer to as “gene circuits.” These gene circuits, which we created from novel and proprietary combinations of genetic parts, are designed to reprogram cells with biological logic to sense inputs, compute decisions and respond to their respective cellular environments. We aim to design and optimize gene circuits through our Design-Build-Test-Learn Engine, or DBTL Engine, to improve the “intelligence” of cell and gene therapies in order to enhance their therapeutic effectiveness against a broad range of diseases that conventional medicines are unable to address. We are designing our gene circuit platform technologies to be applied in a modality-agnostic manner, with applicability to natural killer (NK) cells, T cells, tumor infiltrating lymphocytes (TILs), stem cells including hematopoietic stem cells (HSCs), in vivo gene therapy and messenger ribonucleic acid (mRNA). All of our current product candidates are in preclinical development. Our lead product candidates currently utilize allogeneic chimeric antigen receptor (CAR) NK cells outfitted with its gene circuit technologies in several oncology indications with currently high unmet need. Subject to the successful completion of IND-enabling studies, we expect to file INDs for multiple product candidates starting in 2023. See “Business” elsewhere in this prospectus for more information.
Going Concern
Prior to the Closing of the Business Combination, we concluded that our recurring losses from operations and need for additional financing to fund future operations raised substantial doubt about our ability to continue as a going concern. Similarly, our independent registered public accounting firm included an explanatory paragraph in its report on our consolidated financial statements as of and for the year ended December 31, 2021 with respect to this uncertainty.
Company Information
We file annual, quarterly and current reports, proxy statements and other information with the SEC. The SEC maintains an Internet website at www.sec.gov that contains reports, proxy and information statements and other information about issuers, like us, that file electronically with the SEC. We also maintain a website at https://sentibio.com. We make available, free of charge, on our investor relations website at https://investors.sentibio.com, our Annual Reports on Form 10-K, Quarterly Reports on Form 10-Q, Current Reports on Form 8-K and amendments to these reports as soon as reasonably practicable after electronically filing or furnishing those reports to the SEC. Information contained on our website is not a part of or incorporated by reference into this prospectus and the inclusion of our website and investor relations website addresses in this prospectus is an inactive textual reference only.
6
Background
On June 8, 2022, DYNS consummated the previously announced business combination pursuant to the terms of the Business Combination Agreement with Senti Sub I, Inc. (formerly Senti Biosciences, Inc.) and Explore Merger Sub, Inc., a Delaware corporation and wholly-owned subsidiary of DYNS (“Merger Sub”). Pursuant to the terms of the Business Combination Agreement, Merger Sub merged with and into Senti Sub I, Inc., with Senti Sub I, Inc. surviving the merger as a wholly-owned subsidiary of DYNS. The Merger was approved by DYNS’s stockholders at a meeting held on June 7, 2022. In connection with the consummation of the Merger on the Closing Date, DYNS changed its name from DYNS to Senti Biosciences, Inc.
On June 9, 2022, our common stock, formerly of DYNS, began trading on The Nasdaq Global Market under the ticker symbol “SNTI”.
As a result of the Merger, we raised gross proceeds of approximately $140.3 million of an expected $156.5 million, which included funds held in DYNS’s trust account (after giving effect to redemptions) and proceeds from the PIPE investment of $50.6 million of an expected $66.8 million, and a $5.2 million investment by Bayer Healthcare LLC through the exchange of the Convertible Note. See “Unaudited Pro Forma Condensed Combined Financial Information” elsewhere in this prospectus for more information.
After taking into account the aggregate amount of redemptions of approximately $145.5 million in connection with the Business Combination and LifeForce Capital’s failure to fund its commitment of $16.2 million upon the closing of the PIPE financing, the $140.3 million in gross proceeds from the Merger and related transactions was less than our anticipated minimum cash condition of $151.7 million. We determined that the shortfall in cash did not require us to implement any material changes to our current business plan, although this may change in the future.
Even with proceeds from the Business Combination, we will need substantial additional funding to support our continuing operations and pursue our growth strategy until such time as we can generate significant revenue from product sales, if ever. In the future, we expect to finance our operations through the issuance of additional equity or debt securities or other capital sources, which may include collaborations with other companies or other strategic transactions.
Summary Risk Factors
Investing in our securities involves risks. If any of these risks actually occur, our business, financial condition and results of operations would likely be materially adversely affected. You should carefully consider all the information contained in this prospectus before making a decision to invest in Senti Common Shares. In particular, you should consider the risk factors described under “Risk Factors” beginning on page 11. Some of these risks related to our business, operations, financial performance and industry are summarized below.
| • | We are a preclinical stage biotechnology company with a history of losses. We expect to continue to incur significant losses for the foreseeable future and may never achieve or maintain profitability. |
| • | We will need substantial additional funds to advance development of product candidates and our gene circuit platform, and we cannot guarantee that we will have sufficient funds available in the future to develop and commercialize our current or potential future product candidates and technologies. |
| • | Sales of the Senti Common Shares registered for resale by the Selling Securityholders pursuant to this Prospectus, which represent a significant portion of our total outstanding shares, or the perception that such sales will occur, may have a negative impact on our stock price and may impair our ability to raise additional capital on terms and conditions acceptable to us, or at all. |
| • | We have identified a material weakness in our internal control over financial reporting. If our remediation of the material weakness is not effective, or if we experience additional material |
7
weaknesses or otherwise fail to maintain an effective system of internal controls in the future, we may not be able to accurately report our financial condition or results of operations, which may adversely affect investor confidence in us and, as a result, the value of our common stock. |
| • | Our history of recurring losses and anticipated expenditures raises substantial doubt about our ability to continue as a going concern. Our ability to continue as a going concern requires that we obtain sufficient funding to finance our operations. |
| • | If any of our current or potential future product candidates is ever tested in humans, it may not demonstrate the safety, purity and potency, or efficacy, necessary to become approvable or commercially viable. |
| • | Our gene circuit platform technologies are based on novel technologies that are unproven and may not result in approvable or marketable products, which exposes us to unforeseen risks and makes it difficult for us to predict the time and cost of product development and potential for regulatory approval. |
| • | Although we intend to explore other therapeutic opportunities in addition to the product candidates we are currently pursuing, we may fail to identify viable new product candidates for clinical development, which could materially harm our business. |
| • | Clinical development includes a lengthy and expensive process with an uncertain outcome, and results of earlier studies and trials may not be predictive of future trial results. |
| • | We rely on third parties to conduct our preclinical studies, and plan to rely on third parties to conduct clinical trials, and those third parties may not perform satisfactorily. If third parties on which we intend to rely to conduct certain preclinical and clinical studies do not perform as contractually required, fail to satisfy regulatory or legal requirements or miss expected deadlines, our development program could be delayed or unsuccessful, and we may not be able to obtain regulatory approval for or commercialize our product candidates when expected, or at all. |
| • | We may not be able to maintain our existing strategic partnerships and collaboration arrangements or enter into new strategic partnerships and collaborations for the development, manufacture and commercialization of product candidates based on our platform technology on terms that are acceptable to us, or at all. |
| • | The manufacturing of our product candidates is complex. We may encounter difficulties in production. If we encounter any such difficulties, our ability to supply our product candidates for clinical trials or, if approved, for commercial sale, could be delayed or halted entirely. |
| • | We face competition from companies that have developed or may develop product candidates for the treatment of the diseases that we may target, including companies developing novel therapies and platform technologies. If these companies develop platform technologies or product candidates more rapidly than we do, or if their platform technologies or product candidates are more effective or have fewer side effects, our ability to develop and successfully commercialize product candidates may be adversely affected. |
| • | Our future success depends on our ability to retain key employees, directors, consultants and advisors and to attract, retain and motivate qualified personnel. |
| • | We may experience difficulties in managing our growth and expanding our operations. We have limited experience in therapeutic development. As our current and potential future product candidates enter and advance through preclinical studies and any clinical trials, we will need to expand our development, regulatory and manufacturing capabilities or contract with other organizations to provide these capabilities for us. |
| • | Our business, operations and clinical development plans and timelines could be adversely affected by the ongoing COVID-19 pandemic, including business interruptions, staffing shortages and supply chain issues arising from the pandemic on the manufacturing, clinical trial and other business activities |
8
performed by us or by third parties with whom we may conduct business, including our anticipated contract manufacturers, contract research organizations (“CROs”), suppliers, shippers and others. |
| • | If we are unable to obtain or protect intellectual property rights related to our technology and current or future product candidates, or if our intellectual property rights are inadequate, our competitors could develop and commercialize products and technology similar or identical to ours, and we may not be able to compete effectively in our market or successfully commercialize any product candidates we may develop. |
| • | We may be unable to obtain U.S. or foreign regulatory approval and, as a result, be unable to commercialize our current or potential future product candidates. |
| • | Even if we are able to commercialize any product candidate, such product candidate may become subject to unfavorable pricing regulations or third-party coverage and reimbursement policies, which would harm our business. |
| • | We or the third parties upon whom we depend may be adversely affected by natural disasters, including earthquake, flood, fire, explosion, extreme weather conditions, or medical epidemics. |
Implications of Being an Emerging Growth Company
We are an “emerging growth company” as defined in the JOBS Act. As such, we may take advantage of reduced disclosure and other requirements otherwise generally applicable to public companies, including:
| • | exemption from the requirement to have our registered independent public accounting firm attest to management’s assessment of our internal control over financial reporting; |
| • | exemption from compliance with the requirement of the Public Company Accounting Oversight Board, or PCAOB, regarding the communication of critical audit matters in the auditor’s report on the financial statements; |
| • | reduced disclosure about our executive compensation arrangements; and |
| • | exemption from the requirement to hold non-binding advisory votes on executive compensation or golden parachute arrangements. |
We will remain an emerging growth company until the earliest to occur of: (1) the last day of the fiscal year in which we have at least $1.07 billion in annual revenue; (2) the date we qualify as a “large accelerated filer,” with at least $700.0 million of equity securities held by non-affiliates; (3) the date on which we have issued more than $1.0 billion in non-convertible debt securities during the prior three-year period; and (4) December 31, 2026, the last day of the fiscal year ending after the fifth anniversary of the DYNS IPO.
As a result of this status, we have taken advantage of reduced reporting requirements in this prospectus and may elect to take advantage of other reduced reporting requirements in our future filings with the SEC. In particular, in this prospectus, we have not included all of the executive compensation-related information that would be required if we were not an emerging growth company.
Additional Information
We were incorporated under the laws of the State of Delaware on June 9, 2016. The mailing address of our principal executive office is 2 Corporate Drive, First Floor, South San Francisco, California 94080, and our telephone number is (650) 382-3281.
Our website address is https://sentibio.com/. The information on, or that can be accessed through, our website is not part of this prospectus, and you should not consider information contained on our website in deciding whether to purchase Senti Common Shares.
9
THE OFFERING
Issuance of Senti Common Shares
Senti Common Shares to be issued upon issuance of all Earn-out Shares | Up to 2,000,000 Senti Common Shares. |
Senti Common Shares outstanding prior to the issuance of the Earn-out Shares (as of June 8, 2022) | 43,657,077 |
Use of Proceeds | We do not expect to receive any proceeds from the issuance of the Earn-out Shares or the resale of the Earn-out Shares by the Selling Securityholders. |
Resale of Senti Common Shares by Selling Securityholders
Senti Common Shares offered by the Selling Securityholders | 33,444,908 Senti Common Shares |
Use of proceeds | We will not receive any proceeds from the sale of the Senti Common Shares to be offered by the Selling Securityholders. |
Lock-up Agreements | The securities that are owned by certain of the Selling Securityholders, including the parties to the Registration Rights Agreement and some of the parties to the PIPE subscription agreements, are subject to lock-up provisions and/or Lock-up Agreements, which provide for certain restrictions on transfer until the termination of applicable lock-up periods. |
Ticker symbol | “SNTI”. |
Risk factors | Any investment in the securities offered hereby is speculative and involves a high degree of risk. You should carefully consider the information set forth under “Risk Factors” and elsewhere in this prospectus. |
10
Investing in the Senti Common Shares involves a high degree of risk. Before you decide to invest in the Senti Common Shares, you should consider carefully the risks described below, together with the other information contained in this prospectus, including our financial statements and the related notes appearing at the end of this prospectus. We believe the risks described below are the risks that are material to us as of the date of this prospectus. If any of the following risks actually occur, our business, results of operations and financial condition would likely be materially and adversely affected. In these circumstances, the market price of the Senti Common Shares could decline, and you may lose part or all of your investment.
Risks Related to Our Limited Operating History and Financial Condition
We are a preclinical stage biotechnology company with a history of losses. We expect to continue to incur significant losses for the foreseeable future and may never achieve or maintain profitability.
We are a preclinical stage biotechnology company with a history of losses. Since our inception, we have devoted substantially all of our resources to research and development, preclinical studies, building our management team and building our intellectual property portfolio, and we have incurred significant operating losses. Our net losses were $55.3 million and $19.9 million for the years ended December 31, 2021 and 2020, respectively. As of December 31, 2021, we had an accumulated deficit of $115.1 million. Substantially all of our losses have resulted from expenses incurred in connection with our research and development programs and from general and administrative costs associated with our operations. To date, we have not generated any revenue from product sales, and we have not sought or obtained regulatory approval for any product candidate. Furthermore, we do not expect to generate any revenue from product sales for the foreseeable future, and we expect to continue to incur significant operating losses for the foreseeable future due to the cost of research and development, preclinical studies, clinical trials, manufacturing and the regulatory approval process for our current and potential future product candidates.
We expect our net losses to increase substantially as we:
| • | continue to advance our gene circuit platform technologies; |
| • | continue preclinical development of our current and future product candidates and initiate additional preclinical studies; |
| • | commence clinical trials of our current and future product candidates; |
| • | establish our manufacturing capability, including developing our contract development and manufacturing organization relationships and building our internal manufacturing facilities; |
| • | acquire and license technologies aligned with our gene circuit platform technologies; |
| • | seek regulatory approval of our current and future product candidates; |
| • | expand our operational, financial, and management systems and increase personnel, including personnel to support our preclinical and clinical development, manufacturing and commercialization efforts; |
| • | continue to develop, perfect, and defend our intellectual property portfolio; and |
| • | incur additional legal, accounting, or other expenses in operating our business, including the additional costs associated with operating as a public company. |
However, the amount of our future losses is uncertain. Our ability to achieve or sustain profitability, if ever, will depend on, among other things, successfully developing product candidates, obtaining regulatory approvals to market and commercialize product candidates, manufacturing any approved products on commercially reasonable terms, entering into potential future alliances, establishing a sales and marketing organization or
11
suitable third-party alternatives for any approved product and raising sufficient funds to finance business activities. If we, or our potential future collaborators, are unable to commercialize one or more of our product candidates, or if sales revenue from any product candidate that receives approval is insufficient, we will not achieve or sustain profitability, which could have a material adverse effect on our business, financial condition, results of operations and prospects.
We will need substantial additional funds to advance development of product candidates and our gene circuit platform, and we cannot guarantee that we will have sufficient funds available in the future to develop and commercialize our current or potential future product candidates and technologies.
The development of biotechnology product candidates is capital-intensive. If any of our current or potential future product candidates enter and advance through preclinical studies and clinical trials, we will need substantial additional funds to expand our development, regulatory, manufacturing, marketing and sales capabilities. We have used substantial funds to develop our gene circuit platform, SENTI-202, SENTI-301, SENTI-401 and other product candidates, and we will require significant funds to continue to develop our platform and conduct further research and development, including preclinical studies and clinical trials. In addition, we expect to incur significant additional costs associated with operating as a public company.
As of March 31, 2022, we had $38.1 million in cash and cash equivalents. Our future capital requirements and the period for which our existing resources will support our operations may vary significantly from what we expect. Our monthly spending levels vary based on new and ongoing research and development and other corporate activities. Because the length of time and activities associated with successful research and development of platform technologies and product candidates is highly uncertain, we are unable to estimate the actual funds we will require for development and any approved marketing and commercialization activities. The timing and amount of our operating expenditures will depend largely on:
| • | the timing and progress of preclinical and clinical development of our current and potential future product candidates; |
| • | the timing and progress of our development of our gene circuit platforms; |
| • | the number and scope of preclinical and clinical programs we decide to pursue; |
| • | the costs of building and operating our own dedicated Current Good Manufacturing Practice (“cGMP”) and Current Good Tissue Practice (“cGTP”) facility to support clinical and commercial-scale production of multiple allogeneic natural killer (NK) cell product candidates, and the terms of any third-party manufacturing contract or biomanufacturing partnership we may enter into; |
| • | our ability to maintain our current licenses and collaborations, conduct our research and development programs and establish new strategic partnerships and collaborations; |
| • | the progress of the development efforts of our existing strategic partners and third parties with whom we may in the future enter into collaboration and research and development agreements; |
| • | the costs involved in obtaining, maintaining, enforcing and defending patents and other intellectual property rights; |
| • | the impact of the COVID-19 pandemic on our business; |
| • | the cost and timing of regulatory approvals; and |
| • | our efforts to enhance operational systems and hire additional personnel, including personnel to support development of our product candidates and satisfy our obligations as a public company. |
To date, we have primarily financed our operations through the sale of equity securities. We may seek to raise any necessary additional capital through a combination of public or private equity offerings, debt financings, collaborations, strategic alliances, licensing arrangements, grants and other marketing and
12
distribution arrangements. We cannot assure you that we will be successful in acquiring additional funding at levels sufficient to fund our operations or on terms favorable to us. If we are unable to obtain adequate financing when needed, we may have to delay, reduce the scope of or suspend one or more of our preclinical studies, clinical trials, research and development programs or commercialization efforts. Because of the numerous risks and uncertainties associated with the development and commercialization of our current and potential future product candidates and the extent to which we may enter into collaborations with third parties to participate in their development and commercialization, we are unable to estimate the amounts of increased capital outlays and operating expenditures associated with our current and anticipated preclinical studies and clinical trials, including related manufacturing costs. To the extent that we raise additional capital through collaborations, strategic alliances or licensing arrangements with third parties, we may have to relinquish valuable rights to our current and potential future product candidates, future revenue streams or research programs or grant licenses on terms that may not be favorable to us. If we do raise additional capital through public or private equity or convertible debt offerings, the ownership interest of our existing stockholders will be diluted, and the terms of these securities may include liquidation or other preferences that adversely affect our stockholders’ rights. If we raise additional capital through debt financing, we may be subject to covenants limiting or restricting our ability to take specific actions, such as incurring additional debt, making capital expenditures or declaring dividends.
We do not expect to realize revenue from product sales or royalties from licensed products for the foreseeable future, if at all, and unless and until our current and potential future product candidates are clinically tested, approved for commercialization and successfully marketed.
We have identified a material weakness in our internal control over financial reporting. If our remediation of the material weakness is not effective, or if we experience additional material weaknesses in the future or otherwise fail to maintain an effective system of internal controls in the future, we may not be able to accurately report our financial condition or results of operations, which may adversely affect investor confidence in us and, as a result, the value of Senti Common Shares.
Prior to the closing of the Business Combination, we were a private company with limited accounting personnel and other resources with which to address our internal control over financial reporting. In connection with our preparation and the audit of our consolidated financial statements as of and for the year ended December 31, 2021, we and our independent registered public accounting firm identified a material weakness, as defined under the Exchange Act and by the Public Company Accounting Oversight Board (United States), in our internal control over financial reporting. The material weakness related to a lack of sufficient and adequate resources in the finance and accounting function that resulted in a lack of formalized risk assessment process, lack of segregation of duties, and ineffective process level control activities over the management review of journal entries, account reconciliations and non-routine transactions. A material weakness is a deficiency, or a combination of deficiencies, in internal control over financial reporting such that there is a reasonable possibility that a material misstatement of our consolidated financial statements will not be prevented or detected on a timely basis.
We are in the process of implementing a risk assessment process and measures designed to improve our internal control over financial reporting and remediate the control deficiencies that led to the material weakness, including hiring additional accounting personnel. The process of designing and implementing effective internal controls is a continuous effort that requires us to anticipate and react to changes in our business and the economic and regulatory environments and to expend significant resources to maintain a system of internal controls that is adequate to satisfy our reporting obligations as a public company. For example, to maintain and improve the effectiveness of our financial reporting, we will need to commit significant resources, implement and strengthen existing disclosure processes, train personnel and provide additional management oversight.
We cannot be certain that the measures we have taken to date, and actions we may take in the future, will be sufficient to remediate the control deficiencies that led to our material weakness in our internal control over financial reporting or that they will prevent or avoid potential future material weaknesses. In addition, neither our
13
management nor an independent registered public accounting firm has performed an evaluation of our internal control over financial reporting because no such evaluation has been previously required. The rules governing the standards that must be met for our management to assess our internal control over financial reporting are complex and require significant documentation, testing and remediation. Testing internal controls may divert our management’s attention from other matters that are important to our business.
Pursuant to Section 404 of the Sarbanes-Oxley Act (“Section 404”), our management will be required to report upon the effectiveness of our internal control over financial reporting beginning with the annual report for our fiscal year ending December 31, 2022. Even if our management concludes that our internal control over financial reporting is effective, our independent registered public accounting firm when required may issue a report that is qualified if it is not satisfied with our controls or the level at which our controls are documented, designed, operated or reviewed. The rules governing the standards that must be met for management to assess our internal control over financial reporting are complex and require significant documentation, testing, and possible remediation. To comply with the requirements of being a reporting company under the Exchange Act, we will need to implement additional financial and management controls, reporting systems, procedures, and hire additional accounting and finance staff.
When we lose our status as an “emerging growth company” and become an “accelerated filer” or a “large accelerated filer,” our independent registered public accounting firm will be required to attest to the effectiveness of our internal control over financial reporting pursuant to Section 404. Accordingly, you may not be able to depend on any attestation concerning our internal control over financial reporting from our independent registered public accountants for the foreseeable future.
Our testing, or the subsequent testing by our independent registered public accounting firm, may reveal deficiencies in our internal controls over financial reporting that are deemed to be material weaknesses. A material weakness in internal controls could result in our failure to detect a material misstatement of our annual or quarterly consolidated financial statements or disclosures. We may not be able to conclude on an ongoing basis that we have effective internal controls over financial reporting in accordance with Section 404. If we are unable to conclude that we have effective internal controls over financial reporting, investors could lose confidence in our reported financial information, which could have a material adverse effect on the trading price of Senti Common Shares.
We cannot be certain as to the timing of completion of our evaluation, testing and any remediation actions or the impact of the same on our operations. If we are unable to successfully remediate our existing or any future material weaknesses in our internal control over financial reporting, or identify any additional material weaknesses, the accuracy and timing of our financial reporting may be negatively impacted, we may be unable to maintain compliance with securities law requirements regarding timely filing of periodic reports in addition to applicable stock exchange listing requirements, investors may lose confidence in our financial reporting and our stock price may decline as a result. If we are not able to implement the requirements of Section 404 in a timely manner or with adequate compliance, our independent registered public accounting firm when required may issue an adverse opinion due to ineffective internal controls over financial reporting, and we may be subject to sanctions or investigation by regulatory authorities, such as the SEC. As a result, there could be a negative reaction in the financial markets due to a loss of confidence in the reliability of our consolidated financial statements. In addition, we may be required to incur costs in improving our internal control system and the hiring of additional personnel. Any such action could negatively affect our results of operations and cash flows.
Members of our management team have limited experience in managing the day-to-day operations of a public company and, as a result, we may incur additional expenses associated with the management of our company.
Members of our management team have limited experience in managing the day-to-day operations of a public company. As a result, we may need to obtain outside assistance from legal, accounting, investor relations, or other professionals that could be more costly than planned. We also plan to hire additional personnel to
14
comply with additional SEC reporting requirements. These compliance costs will make some activities significantly more time-consuming and costly. If we lack cash resources to cover these costs in the future, our failure to comply with reporting requirements and other provisions of securities laws could negatively affect our stock price and adversely affect our potential results of operations, cash flow and financial condition.
Our history of recurring losses and anticipated expenditures raises substantial doubt about our ability to continue as a going concern. Our ability to continue as a going concern requires that we obtain sufficient funding to finance our operations.
We have incurred significant operating losses to date, and it is possible we may never generate a profit. Our consolidated financial statements included elsewhere in this prospectus have been prepared on a going concern basis, which contemplates the realization of assets and satisfaction of liabilities in the ordinary course of business. These consolidated financial statements do not include any adjustments relating to the recoverability and classification of recorded asset amounts or the amounts and classification of liabilities that might result from the outcome of these uncertainties related to our ability to operate on a going concern basis.
We have concluded that our recurring losses from operations and need for additional financing to fund future operations raise substantial doubt about our ability to continue as a going concern. Similarly, our independent registered public accounting firm included an explanatory paragraph in its report on our consolidated financial statements as of and for the year ended December 31, 2021 with respect to this uncertainty. Following the closing of the Business Combination, and based upon our current operating plan and assumptions, we believe that our existing cash and cash equivalents, including the results of the Business Combination, will be sufficient to fund our operations for at least the next 12 months from the issuance date of this filing. This estimate is based on assumptions that may prove to be wrong, and we could use our available capital resources sooner than we expect. Changes may occur beyond our control that would cause us to consume our available capital before that time, including changes in and progress of our development activities and changes in regulation. Our future capital requirements will depend on many factors, including:
| • | the scope, rate of progress, results and costs of platform development activities, preclinical studies, laboratory testing and clinical trials for our product candidates; |
| • | the number and development requirements of product candidates that we may pursue, and other indications for our current product candidates that we may pursue; |
| • | the costs, timing and outcome of regulatory review of our product candidates; |
| • | the scope and costs of constructing and operating our planned cGMP and cGTP facility and any commercial manufacturing activities; |
| • | the cost associated with commercializing any approved product candidates; |
| • | the cost and timing of developing our ability to establish sales and marketing capabilities, if any; |
| • | the cost and timing of maintaining and expanding the applications of our gene circuit platform technology; |
| • | the costs of preparing, filing and prosecuting patent applications, maintaining, enforcing and protecting our intellectual property rights, defending intellectual property-related claims and obtaining licenses to third-party intellectual property; |
| • | the timing and amount of any milestone and royalty payments we are required to make under our present or future license agreements; |
| • | our ability to establish and maintain strategic partnerships and collaborations, including any biomanufacturing partnerships or collaborations involving the use of our platform technology, on favorable terms, if at all; and |
15
| • | the extent to which we acquire or in-license other product candidates and technologies and associated intellectual property. |
We will require additional capital to complete our planned clinical development programs for our current product candidates to obtain regulatory approval. Any additional capital raising efforts may divert our management from their day-to-day activities, which may adversely affect our ability to develop and commercialize our current and future product candidates, if approved.
In addition, we cannot guarantee that future financing will be available on a timely basis, in sufficient amounts or on terms acceptable to us, if at all. Moreover, the terms of any financing may adversely affect the holdings or the rights of our stockholders and the issuance of additional securities by us, whether equity or debt, or the market perception that such issuances are likely to occur, could cause the market price of Senti Common Shares to decline. If we are unable to raise sufficient capital when needed, our business, financial condition and results of operations will be harmed, and we will need to significantly modify our operational plans to continue as a going concern. If we are unable to continue as a going concern, we might have to liquidate our assets and the values we receive for our assets in liquidation or dissolution could be significantly lower than the values reflected in our consolidated financial statements.
Our ability to use net operating loss carryforwards (“ NOLs”) and credits to offset future taxable income may be subject to certain limitations.
Our NOLs could expire unused and be unavailable to offset future income tax liabilities because of their limited duration or because of restrictions under U.S. tax law. NOLs generated in taxable years beginning before January 1, 2018 are permitted to be carried forward for 20 taxable years under applicable U.S. federal income tax law. Under the Tax Cuts and Jobs Act of 2017 (the “Tax Act”), as modified by the Coronavirus Aid, Relief and Economic Security Act (the “CARES Act”), NOLs arising in tax years beginning after December 31, 2020 may not be carried back. Moreover, under the Tax Act as modified by the CARES Act, NOLs generated in taxable years beginning after December 31, 2017 may be carried forward indefinitely, but the deductibility of such NOLs generally will be limited in taxable years beginning after December 31, 2020 to 80% of current year taxable income. As of December 31, 2021, we had NOLs for U.S. federal and state income tax purposes of approximately $145.1 million, a portion of which expire beginning in 2031 if not utilized. NOLs generated in 2021 for U.S. federal tax reporting purposes of approximately $35.5 million have an indefinite life.
In general, under Section 382 of the Code, a corporation that undergoes an “ownership change” (defined under Section 382 of the Code and applicable Treasury Regulations as a greater than 50 percentage point change (by value) in a corporation’s equity ownership by certain stockholders over a rolling three-year period) is subject to limitations on its ability to utilize its pre-change NOLs to offset future taxable income. We have not determined whether our NOLs are limited under Section 382 of the Code. We may have experienced ownership changes in the past and may experience ownership changes in the future, including as a result of the Business Combination or subsequent shifts in our stock ownership (some of which are outside our control). Furthermore, our ability to utilize NOLs of companies that we may acquire in the future may be subject to limitations. There is also a risk that due to regulatory changes, such as suspensions on the use of NOLs or other unforeseen reasons, our existing NOLs could expire or otherwise be unavailable to reduce future income tax liabilities, including for state tax purposes. For these reasons, we may not be able to utilize a material portion of the NOLs reflected on our balance sheet, even if we attain profitability, which could potentially result in increased future tax liability to us and could adversely affect our operating results and financial condition.
16
Risks Related to the Development and Clinical Testing of Our Product Candidates
Our current product candidates are in preclinical development and have never been tested in humans. One or all of our current product candidates may fail in clinical development or suffer delays that materially and adversely affect their commercial viability.
We have no products on the market or that have gained regulatory approval or that have entered clinical trials. None of our product candidates has ever been tested in humans. Our ability to achieve and sustain profitability depends on obtaining regulatory approvals for and successfully commercializing product candidates, either alone or with collaborators.
Before obtaining regulatory approval for the commercial distribution of our product candidates, we or a collaborator must conduct extensive preclinical studies, followed by clinical trials to demonstrate the safety, purity and potency, or efficacy of our product candidates in humans. There is no guarantee that the U.S. Food and Drug Administration (the “FDA”) will permit us to conduct clinical trials. Further, we cannot be certain of the timely completion or outcome of our preclinical studies and cannot predict if the FDA or other regulatory authorities will accept our proposed clinical programs, our clinical protocols or if the outcome of our preclinical studies will ultimately support the further development of our preclinical programs or testing in humans. As a result, we cannot be sure that we will be able to submit IND or similar applications for our proposed clinical programs on the timelines we expect, if at all, and we cannot be sure that submission of INDs or similar applications will result in the FDA or other regulatory authorities allowing clinical trials for any of our product candidates to begin.
Our current product candidates are in preclinical development and we are subject to the risks of failure inherent in the development of product candidates based on novel approaches, targets and mechanisms of action. Although we anticipate initiating clinical trials for our lead product candidates, there is no guarantee that we will be able to proceed with clinical development of any of these product candidates or that any product candidate will demonstrate a clinical benefit once we advance these candidates to testing in patients. Accordingly, you should consider our prospects in light of the costs, uncertainties, delays and difficulties frequently encountered by preclinical stage biotechnology companies such as ours.
We may not be able to access the financial resources to continue development of, or to enter into any collaborations for, any of our current or potential future product candidates. This may be exacerbated if we experience any issues that delay or prevent regulatory approval of, or our ability to commercialize, a product candidate, such as:
| • | negative or inconclusive results from our preclinical studies or clinical trials or the clinical trials of others for product candidates similar to ours, leading to a decision or requirement to conduct additional preclinical studies or clinical trials or abandon any or all of our programs; |
| • | product-related side effects experienced by participants in our clinical trials or by individuals using therapeutics similar to our product candidates; |
| • | delays in submitting INDs or comparable foreign applications, or delays or failures to obtain the necessary approvals from regulatory authorities to commence a clinical trial, or a suspension or termination of a clinical trial once commenced; |
| • | conditions imposed by the FDA or other regulatory authorities regarding the scope or design of our clinical trials; |
| • | delays in enrolling research subjects in clinical trials; |
| • | high drop-out rates of research subjects; |
| • | inadequate supply or quality of product candidate components or materials or other supplies necessary for the conduct of our clinical trials; |
17
| • | chemistry, manufacturing and control (“CMC”) challenges associated with manufacturing and scaling up biologic product candidates to ensure consistent quality, stability, purity and potency among different batches used in clinical trials; |
| • | greater-than-anticipated clinical trial costs; |
| • | poor potency or effectiveness of our product candidates during clinical trials; |
| • | unfavorable FDA or other regulatory authority inspection and review of a clinical trial or manufacturing site; |
| • | delays as a result of the COVID-19 pandemic or events associated with the pandemic; |
| • | failure of our third-party contractors or investigators to comply with regulatory requirements or otherwise meet their contractual obligations in a timely manner, or at all; |
| • | delays and changes in regulatory requirements, policies and guidelines; or |
| • | the FDA or other regulatory authorities interpreting our data differently than we do. |
Further, we and any existing or potential future collaborator may never receive approval to market and commercialize any product candidate. Even if we or any existing or potential future collaborator obtains regulatory approval, the approval may be for targets, disease indications or patient populations that are not as broad as we intended or desired or may require labeling that includes significant use or distribution restrictions or safety warnings. We or an existing or potential future collaborator may also be subject to post-marketing testing requirements to maintain regulatory approval.
If any of our current or potential future product candidates is ever tested in humans, it may not demonstrate the safety, purity and potency, or efficacy, necessary to become approvable or commercially viable.
None of our current product candidates have ever been tested in humans. We may ultimately discover that our current product candidates do not possess certain properties that we believe are helpful for therapeutic effectiveness and safety or would otherwise support the submission of an IND on the timelines we expect, or at all. We do not know if the observations we have made regarding our gene circuits generally and our product candidates in particular will translate into any clinical response when tested in humans. As an example, while the Tumor-Associated Antigen (“TAA”) CD33 has been clinically validated as a target for an approved antibody-drug conjugate therapy, it has not been clinically validated as a target for CAR-NK or CAR-T therapies, and may not prove to be a clinically sufficient target for the CAR-NK therapies we are developing. As a result of these uncertainties related to our gene circuit platform technologies and our product candidates, we may never succeed in developing a marketable product based on our current product candidates. If any of our current or potential future product candidates prove to be ineffective, unsafe or commercially unviable, our entire pipeline could have little, if any, value, which could have a material adverse effect on our business, financial condition, results of operations and prospects.
Our gene circuit platform technologies are based on novel technologies that are unproven and may not result in approvable or marketable products, which exposes us to unforeseen risks and makes it difficult for us to predict the time and cost of product development and potential for regulatory approval.
We are seeking to identify and develop a broad pipeline of product candidates using our gene circuit platform technologies. The scientific research that forms the basis of our efforts to develop product candidates with our platforms is still ongoing. We are not aware of any FDA approved therapeutics utilizing similar technologies as ours. Further, the scientific evidence to support the feasibility of developing therapeutic treatments based on our platform technologies is preliminary. As a result, we are exposed to a number of unforeseen risks and it is difficult to predict the types of challenges and risks that we may encounter during development of our product candidates. For example, we have not tested any of our current product candidates in
18
humans, and our current data is limited to animal models and preclinical cell lines, the results of which may not translate into humans. Further, relevant animal models and assays may not accurately predict the safety and efficacy of our product candidates in humans, and we may encounter significant challenges creating appropriate models and assays for demonstrating the safety and efficacy of our product candidates. In addition, our gene circuit technologies have potential safety risks. For example, if the NOT GATE gene circuit, as described below, engineered into one of our product candidates, such as SENTI-202, does not provide a clinically sufficient level of inhibition, it may kill healthy cells that it has been designed to preserve or may cause systemic immune cytotoxicity. As another example, if the small-molecular regulator dial does not achieve a clinically sufficient level of control over IL-12 secretion, either leaky IL-12 production in the uninduced state or overproduction of IL-12 in the induced state may result in systemic immune toxicity. It is possible that safety events or concerns such as these or others could negatively affect the development of our product candidates, including adversely affecting patient enrollment among the patient populations that we intend to treat.
Given the novelty of our technologies, we intend to work closely with the FDA and comparable foreign regulatory authorities to evaluate our proposed approaches to obtain regulatory approval for our product candidates; however, due to a lack of comparable experiences, the regulatory pathway with the FDA and comparable regulatory authorities may be more complex and time-consuming relative to other more well-known therapeutics. Even if we obtain human data to support our product candidates, the FDA or comparable foreign regulatory agencies may lack experience in evaluating the safety and efficacy of our product candidates developed using our platforms, which could result in a longer than expected regulatory review process, increase our expected development costs, and delay or prevent commercialization of our product candidates. The validation process takes time and resources, may require independent third-party analyses, and may not be accepted or approved by the FDA and comparable foreign regulatory authorities. We cannot be certain that our approach will lead to the development of approvable or marketable products, alone or in combination with other therapies.
We may not be successful in our efforts to use and expand our gene circuit platform to expand our pipeline of product candidates.
A key element of our strategy is to use and advance our gene circuit platform to design, test and build our portfolio of product candidates focused on allogeneic gene circuit-equipped CAR-NK cell therapies for the treatment of cancer. Although our research and development efforts to date have resulted in our discovery and preclinical development of SENTI-202, SENTI-301, SENTI-401 and other potential product candidates, none of these product candidates has advanced to clinical development. We cannot assure you that any of our existing product candidates will advance to clinical trials or, if they do, that such trials will demonstrate these product candidates to be safe or effective therapeutics, and we may not be able to successfully develop any product candidates. Even if we are successful in expanding our pipeline of product candidates, any additional product candidates that we identify may not be suitable for clinical development or generate acceptable clinical data, including as a result of being shown to have unacceptable effects or other characteristics that indicate that they are unlikely to be products that will receive marketing approval from the FDA or other regulatory authorities or achieve market acceptance. If we do not successfully develop and commercialize product candidates, we will not be able to generate product revenue in the future.
Although we intend to explore other therapeutic opportunities in addition to the product candidates that we are currently developing, we may fail to identify viable new product candidates for clinical development for a number of reasons. If we fail to identify additional potential product candidates, our business could be materially harmed.
Although a substantial amount of our efforts will focus on the planned clinical trials and potential approval of the current and potential future product candidates we are evaluating, a key element of our strategy is to discover, develop, manufacture and globally commercialize additional targeted therapies beyond our current
19
product candidates to treat various conditions and in a variety of therapeutic areas. Even if we identify investigational therapies that initially show promise, we may fail to successfully develop and commercialize such products for many reasons, including the following:
| • | the research methodology used may not be successful in identifying potential investigational therapies; |
| • | competitors may develop alternatives that render our investigational therapies obsolete; |
| • | investigational therapies we develop may nevertheless be covered by third parties’ patents or other exclusive rights; |
| • | an investigational therapy may, on further study, be shown to have harmful side effects or other characteristics that indicate it is unlikely to be effective or otherwise does not meet applicable regulatory criteria; |
| • | it may take greater human and financial resources than we will possess to identify additional therapeutic opportunities for our product candidates or to develop suitable potential product candidates through internal research programs, thereby limiting our ability to develop, diversify and expand our product portfolio; |
| • | an investigational therapy may not be capable of being produced in clinical or commercial quantities at an acceptable cost, or at all; and |
| • | an approved product may not be accepted as safe and effective by trial participants, the medical community or third-party payors. |
Identifying new investigational therapies requires substantial technical, financial and human resources, whether or not any investigational therapies are ultimately identified. Because we have limited financial and human resources, we may initially focus on research programs and product candidates for a limited set of indications. As a result, we may forgo or delay pursuit of opportunities with other product candidates or for other indications that later prove to have greater commercial potential or a greater likelihood of success. Our resource allocation decisions may cause us to fail to capitalize on viable commercial products or profitable market opportunities. For example, if we do not accurately evaluate the commercial potential or target market for a particular product candidate or technology, we may relinquish valuable rights to that product candidate or technology through collaborations, licensing or other royalty arrangements in cases in which it would have been more advantageous for us to retain sole development and commercialization rights to such product candidate or technology.
Accordingly, there can be no assurance that we will ever be able to identify additional therapeutic opportunities for our product candidates or to develop suitable potential product candidates through internal research programs, which could materially adversely affect our future growth and prospects. We may focus our efforts and resources on potential product candidates or other potential programs that ultimately prove to be unsuccessful.
The market, physicians, patients, regulators and potential investors, may not be receptive to our current or potential future product candidates and may be skeptical of the viability and benefits of our gene circuit pipeline technology because it is based on a relatively novel and complex technology.
The market, physicians, patients, regulators and potential investors, may be skeptical of the viability and benefits of our gene circuit pipeline technology or our product candidates because they are based on a relatively novel and complex technology and there can be no assurance that our product candidates or platform technologies will be understood, approved, or accepted. If potential investors are skeptical of the success of our pipeline products, our ability to raise capital and the value of our stock may be adversely affected. If physicians, patients, or regulators do not understand or accept our gene circuit platform technologies or our product candidates, we may be delayed in or unable to develop our product candidates.
20
Even if regulatory approval is obtained for a product candidate, including SENTI-202, SENTI-301 and SENTI-401, we may not generate or sustain revenue from sales of approved products. Market acceptance of our gene circuit platform technologies and our current and potential future product candidates, if approved, will depend on, among other factors:
| • | the timing of our receipt of any marketing and commercialization approvals; |
| • | the terms of any approvals and the countries in which approvals are obtained; |
| • | the safety and efficacy of our product candidates and gene circuit technologies in general; |
| • | the prevalence and severity of any adverse side effects associated with our product candidates; |
| • | limitations or warnings contained in any labeling approved by the FDA or other regulatory authority; |
| • | relative convenience and ease of administration of our product candidates; |
| • | the success of our physician education programs; |
| • | the availability of coverage and adequate government and third-party payor reimbursement; |
| • | the pricing of our products, particularly as compared to alternative treatments; and |
| • | availability of alternative effective treatments for the disease indications our product candidates are intended to treat and the relative risks, benefits and costs of those treatments. |
If any product candidate we commercialize fails to achieve market acceptance, it could have a material adverse effect on our business, financial condition, results of operations and prospects.
The occurrence of serious complications or side effects in connection with use of our product candidates, either in clinical trials or post-approval, could lead to discontinuation of our clinical development programs, refusal of regulatory authorities to approve our product candidates or, post-approval, revocation of marketing authorizations or refusal to approve applications for new indications, which could severely harm our business, prospects, operating results and financial condition.
Undesirable side effects caused by any of our current or potential future product candidates could cause regulatory authorities to interrupt, delay or halt clinical trials and could result in a more restrictive label or the delay or denial of regulatory approval by the FDA or other regulatory authorities. While we have not yet initiated clinical trials for SENTI-202, SENTI-301, SENTI-401 or any other product candidate, it is likely that there will be side effects associated with their use. Results of our clinical trials could reveal a high and unacceptable severity and prevalence of these side effects. For example, if the NOT GATE gene circuit engineered into one of our product candidates, such as SENTI-202, does not provide a clinically sufficient level of inhibition, it may kill healthy cells that it has been designed to preserve or may cause systemic immune cytotoxicity. As another example, if the small- molecular regulator dial does not achieve a clinically sufficient level of control over IL-12 secretion, either leaky IL-12 production in the uninduced state or overproduction of IL-12 in the induced state may result in systemic immune toxicity. It is possible that safety events or concerns such as these or others could negatively affect the development of our product candidates, including adversely affecting patient enrollment among the patient populations that we intend to treat. In such an event, our trials could be suspended or terminated, and the FDA or other regulatory authorities could order us to cease further development of or deny approval of a product candidate for any or all targeted indications. Such side effects could also affect patient recruitment or the ability of enrolled patients to complete the trial or result in potential product liability claims. To date, we have not observed any such effects in our preclinical studies, but there can be no guarantee that our current or future product candidates will not cause such effects in clinical trials. Any of these occurrences may materially and adversely affect our business and financial condition and impair our ability to generate revenues.
Further, clinical trials by their nature utilize a sample of the potential patient population. With a limited number of patients and limited duration of exposure, rare and severe side effects of a product candidate may only
21
be uncovered when a significantly larger number of patients are exposed to the product candidate or when patients are exposed for a longer period of time.
In the event that any of our current or potential future product candidates receives regulatory approval and we or others identify undesirable side effects caused by one of these products, any of the following events could occur, which could result in the loss of significant revenue to us and materially and adversely affect our results of operations and business:
| • | regulatory authorities may withdraw their approval of the product or seize the product; |
| • | we may be required to recall the product or change the way the product is administered to patients; |
| • | additional restrictions may be imposed on the marketing of the particular product or the manufacturing processes for the product or any component thereof; |
| • | we may be subject to fines, injunctions or the imposition of civil or criminal penalties; |
| • | regulatory authorities may require the addition of labeling statements, such as a “black box” warning or a contraindication; |
| • | we may be required to create a medication guide outlining the risks of such side effects for distribution to patients; |
| • | we could be sued and held liable for harm caused to patients; |
| • | the product may become less competitive; and |
| • | our reputation may suffer. |
Any of these events could prevent us from achieving or maintaining market acceptance of the particular product candidate, if approved, and could significantly harm our business, results of operations and prospects.
While we believe our pipeline will yield multiple INDs, we may not be able to file INDs to commence clinical trials on the timelines we expect, and even if we are able to, the FDA may not permit us to proceed.
We expect our pipeline to yield multiple INDs beginning as early as 2023, including INDs for SENTI-202 and SENTI-301. We cannot be sure that submission of an IND will result in the FDA allowing testing and clinical trials to begin, or that, once begun, issues will not arise that suspend or terminate such clinical trials. The manufacturing of our product candidates, including SENTI-202, SENTI-301 and SENTI-401, remains an emerging and evolving field. Accordingly, we expect chemistry, manufacturing and control related topics, including product specifications, will be a focus of IND reviews, which may delay the clearance of INDs. Additionally, even if such regulatory authorities agree with the design and implementation of the clinical trials set forth in an IND or clinical trial application, we cannot guarantee that such regulatory authorities will not change their requirements in the future.
In addition to the submission of an IND to the FDA before initiation of a clinical trial in the United States, certain human clinical trials involving recombinant or synthetic nucleic acid molecules are subject to oversight of institutional biosafety committees (“IBCs”), as set forth in the National Institutes of Health (“NIH”) Guidelines for Research Involving Recombinant or Synthetic Nucleic Acid Molecules (“NIH Guidelines”). Under the NIH Guidelines, recombinant and synthetic nucleic acids are defined as: (i) molecules that are constructed by joining nucleic acid molecules and that can replicate in a living cell (i.e., recombinant nucleic acids); (ii) nucleic acid molecules that are chemically or by other means synthesized or amplified, including those that are chemically or otherwise modified but can base pair with naturally occurring nucleic acid molecules (i.e., synthetic nucleic acids); or (iii) molecules that result from the replication of those described in (i) or (ii). Specifically, under the NIH Guidelines, supervision of human gene transfer trials includes evaluation and assessment by an IBC, a local institutional committee that reviews and oversees research utilizing recombinant or synthetic nucleic acid
22
molecules at that institution. The IBC assesses the safety of the research and identifies any potential risk to public health or the environment, and such review may result in some delay before initiation of a clinical trial. While the NIH Guidelines are not mandatory unless the research in question is being conducted at or sponsored by institutions receiving NIH funding of recombinant or synthetic nucleic acid molecule research, many companies and other institutions not otherwise subject to the NIH Guidelines voluntarily follow them.
Interim, topline and preliminary data that we announce or publish from time to time for any clinical trials that we initiate may change as more patient data become available or as additional analyses are conducted, and as the data are subject to audit and verification procedures that could result in material changes in the final data.
From time to time, we may publicly disclose interim, preliminary or topline data from our preclinical studies and clinical trials, which is based on a preliminary analysis of then-available data, and the results and related findings and conclusions are subject to change following a more comprehensive review of the data related to the particular trial. We also make assumptions, estimations, calculations and conclusions as part of our analyses of data, and we may not have received or had the opportunity to fully and carefully evaluate all data. As a result, the interim, preliminary or topline results that we report may differ from future results of the same trials, or different conclusions or considerations may qualify such results, once additional data have been received and fully evaluated. Topline data also remain subject to audit and verification procedures that may result in the final data being materially different from the preliminary data we previously published. As a result, topline data should be viewed with caution until the final data are available. From time to time, we may also disclose interim, preliminary or topline data from our clinical studies. Interim, topline or preliminary data from clinical trials that we may complete are subject to the risk that one or more of the clinical outcomes may materially change as patient enrollment continues and more patient data become available. Adverse differences between preliminary, topline or interim data and final data could significantly harm our business prospects.
Further, others, including regulatory agencies, may not accept or agree with our assumptions, estimates, calculations, conclusions or analyses or may interpret or weigh the importance of data differently, which could impact the value of the particular program, the approvability or commercialization of the particular product candidate or product and the value of our company in general. In addition, the information we choose to publicly disclose regarding a particular study or clinical trial is based on what is typically extensive information, and you or others may not agree with what we determine is the material or otherwise appropriate information to include in our disclosure, and any information we determine not to disclose may ultimately be deemed significant with respect to future decisions, conclusions, views, activities or otherwise regarding a particular product, product candidate or our business. If the topline data that we report differ from actual results, or if others, including regulatory authorities, disagree with the conclusions reached, our ability to obtain approval for, and commercialize, our product candidates may be harmed, which could harm our business, operating results, prospects or financial condition.
We and our collaborators may not achieve projected discovery and development milestones and other anticipated key events in the time frames that we or they announce, which could have an adverse impact on our business and could cause our stock price to decline.
From time to time, we expect that we will make public statements regarding the expected timing of certain milestones and key events, such as the commencement and completion of preclinical and IND-enabling studies in our product candidate discovery programs with collaborators as well as the commencement and completion of planned clinical trials in those programs. The actual timing of these events can vary dramatically due to a number of factors such as delays or failures in our or any future collaborators’ product candidate discovery and development programs, the amount of time, effort and resources committed by us and any future collaborators, and the numerous uncertainties inherent in the development of therapies. As a result, there can be no assurance that our or any future collaborators’ programs will advance or be completed in the time frames we or they announce or expect. If we or any collaborators fail to achieve one or more of these milestones or other key events
23
as planned, our business could be materially adversely affected, and the price of our common stock could decline.
Clinical trials are expensive, time-consuming and difficult to design and implement.
Human clinical trials are expensive and difficult to design and implement, in part because they are subject to rigorous regulatory requirements. Because our current and potential future product candidates are based on new technologies and discovery approaches, we expect that they will require extensive research and development and have substantial manufacturing and processing costs. In addition, the FDA or other regulatory authorities may require us to perform additional testing before commencing clinical trials and be hesitant to allow us to enroll patients impacted with our targeted disease indications in our future clinical trials. If we are unable to enroll patients impacted by our targeted disease indications in our future clinical trials, we would be delayed in obtaining potential proof-of-concept data in humans, which could extend our development timelines. In addition, costs to treat patients and to treat potential side effects that may result from our product candidates may be significant. Accordingly, our clinical trial costs are likely to be high and could have a material adverse effect on our business, financial condition, results of operations and prospects.
If we encounter difficulties enrolling patients in our clinical trials, our clinical development activities could be delayed or otherwise adversely affected.
We may not be able to initiate or continue any clinical trials for our current or potential future product candidates if we are unable to locate and enroll a sufficient number of eligible patients to participate in these trials as required by the FDA or other regulatory authorities. We cannot predict how difficult it will be to enroll patients for trials in the indications we are studying. We may experience difficulties in patient enrollment in our clinical trials for a variety of reasons. The enrollment of patients depends on many factors, including:
| • | the severity of the disease under investigation; |
| • | the patient eligibility criteria defined in the clinical trial protocol; |
| • | the size of the patient population required for analysis of the trial’s primary endpoints; |
| • | the proximity and availability of clinical trial sites for prospective patients; |
| • | willingness of physicians to refer their patients to our clinical trials; |
| • | our ability to recruit clinical trial investigators with the appropriate competencies and experience; |
| • | clinicians’ and patients’ perceptions as to the potential advantages of the product candidate being studied in relation to other available therapies, including any new drugs that may be approved for the indications we are investigating; |
| • | our ability to obtain and maintain patient consents; |
| • | the risk that patients enrolled in clinical trials will drop out of the trials before completion; and |
| • | factors we may not be able to control, such as current or potential pandemics, including the ongoing COVID-19 pandemic, that may limit the availability of patients, principal investigators or staff or clinical sites to participate in our clinical trials. |
In addition, our future clinical trials will compete with other clinical trials for product candidates that are in the same therapeutic areas as our product candidates, and this competition will reduce the number and types of patients available to us, because some patients who might have opted to enroll in our trials may instead opt to enroll in a trial being conducted by one of our competitors. Since the number of qualified clinical investigators is limited, we expect to conduct some of our clinical trials at the same clinical trial sites that some of our competitors use, which will reduce the number of patients who are available for our clinical trials at such clinical
24
trial sites. Additionally, because some of our clinical trials will be in patients with advanced disease who may experience disease progression or adverse events independent from our product candidates, such patients may be unevaluable for purposes of the trial and, as a result, we may require additional enrollment. Delays in patient enrollment may result in increased costs or may affect the timing or outcome of the planned clinical trials, which could prevent completion of these trials and adversely affect our ability to advance the development of our product candidates.
If clinical trials for our product candidates are prolonged, delayed or stopped, we may be unable to seek or obtain regulatory approval and commercialize our product candidates on a timely basis, or at all, which would require us to incur additional costs and delay our receipt of any product revenue.
We may experience delays in our ongoing or future preclinical studies or clinical trials, and we do not know whether future preclinical studies or clinical trials will begin on time, need to be redesigned, enroll an adequate number of patients on time or be completed on schedule, if at all. The commencement or completion of these clinical trials could be substantially delayed or prevented by many factors, including:
| • | further discussions with the FDA or comparable foreign regulatory authorities regarding the scope or design of our clinical trials, including the endpoint measures required for regulatory approval and our statistical plan; |
| • | the limited number of, and competition for, suitable study sites and investigators to conduct our clinical trials, many of which may already be engaged in other clinical trial programs with similar patients, including some that may be for the same indications as our product candidates; |
| • | any delay or failure to obtain timely approval or agreement to commence a clinical trial in any of the countries where enrollment is planned; |
| • | inability to obtain sufficient funds required for a clinical trial; |
| • | clinical holds on, or other regulatory objections to, a new or ongoing clinical trial; |
| • | delay or failure to manufacture sufficient quantities or inability to produce quantities of consistent quality, purity and potency of the product candidate for our clinical trials; |
| • | delay or failure to reach agreement on acceptable clinical trial agreement terms or clinical trial protocols with prospective sites or CROs, the terms of which can be subject to extensive negotiation and may vary significantly among different sites or CROs; |
| • | delay or failure to obtain institutional review board (“IRB”) or ethics committee approval to conduct a clinical trial at a prospective site; |
| • | the FDA or other comparable foreign regulatory authorities may require us to submit additional data or impose other requirements before permitting us to initiate a clinical trial; |
| • | slower than expected rates of patient recruitment and enrollment; |
| • | failure of patients to complete the clinical trial; |
| • | the inability to enroll a sufficient number of patients in studies to ensure adequate statistical power to detect statistically significant treatment effects; |
| • | unforeseen safety issues, including severe or unexpected drug-related adverse effects experienced by patients, including possible deaths; |
| • | lack of efficacy or failure to measure a statistically significant clinical benefit within the dose range with an acceptable safety margin during clinical trials; |
| • | termination of our clinical trials by one or more clinical trial sites; |
| • | inability or unwillingness of patients or clinical investigators to follow our clinical trial protocols; |
25
| • | inability to monitor patients adequately during or after treatment by us or our CROs; |
| • | our CROs or clinical study sites failing to comply with regulatory requirements or meet their contractual obligations to us in a timely manner, or at all, deviating from the protocol or dropping out of a study; |
| • | inability to address any noncompliance with regulatory requirements or safety concerns that arise during the course of a clinical trial; |
| • | the impact of, and delays related to, health epidemics such as the COVID-19 pandemic; |
| • | the need to suspend, repeat or terminate clinical trials as a result of non-compliance with regulatory requirements, inconclusive or negative results or unforeseen complications in testing; and |
| • | the suspension or termination of our clinical trials upon a breach or pursuant to the terms of any agreement with, or for any other reason by, any future strategic collaborator that has responsibility for the clinical development of any of our product candidates. |
Changes in regulatory requirements, policies and guidelines may also occur and we may need to significantly modify our clinical development plans to reflect these changes with appropriate regulatory authorities. These changes may require us to renegotiate terms with CROs or resubmit clinical trial protocols to IRBs for re-examination, which may impact the costs, timing or successful completion of a clinical trial. Our clinical trials may be suspended or terminated at any time by us, the FDA, other regulatory authorities, the IRB overseeing the clinical trial at issue, any of our clinical trial sites with respect to that site, or us.
Any failure or significant delay in commencing or completing clinical trials for our product candidates, any failure to obtain positive results from clinical trials, any safety concerns related to our product candidates, or any requirement to conduct additional clinical trials or other testing of our product candidates beyond those that we currently contemplate would adversely affect our ability to obtain regulatory approval and our commercial prospects and ability to generate product revenue will be diminished.
If we decide to seek orphan drug designation for one or more of our product candidates, we may be unsuccessful or may be unable to maintain the benefits associated with orphan drug designation for our current or future product candidates that we may develop.
Under the Orphan Drug Act, the FDA may designate a product candidate as an orphan drug if it is a drug or biologic product intended to treat a rare disease or condition, which is generally defined as a patient population of fewer than 200,000 individuals annually in the United States, or where there is no reasonable expectation that the cost of developing the product will be recovered from sales in the United States. We may seek orphan drug designation for certain indications for our product candidates in the future. Orphan drug designation neither shortens the development time or regulatory review time of a drug nor gives the drug any advantage in the regulatory review or approval process. Orphan drug designation can entitle a party to financial incentives such as opportunities for grant funding towards clinical trial costs, tax advantages and user-fee waivers.
In addition, if a product candidate with an orphan drug designation receives the first marketing approval for the indication for which it has such designation, the product is entitled to a period of marketing exclusivity, which precludes the FDA from approving another marketing application for the same drug for the same indication for seven years. The FDA may reduce the seven-year exclusivity if the same drug from a competitor demonstrates clinical superiority to the product with orphan exclusivity or if the FDA finds that the holder of the orphan exclusivity has not shown that it can assure the availability of sufficient quantities of the orphan product to meet the needs of patients with the disease or condition for which the drug was designated. Even if one of our product candidates receives orphan exclusivity, the FDA can still approve other drugs that have a different active ingredient for use in treating the same indication or disease.
In addition, exclusive marketing rights in the United States may be limited if we seek approval for an indication broader than the orphan-designated indication or may be lost if the FDA later determines that the
26
request for designation was materially defective or if the manufacturer is unable to assure sufficient quantities of the product to meet the needs of patients with the rare disease or condition. Further, even if we obtain orphan drug exclusivity for a product, that exclusivity may not effectively protect the product from competition because different drugs with different active moieties can be approved for the same condition, and while we may seek orphan drug designation for our product candidates, we may never receive such designations. In addition, the FDA may reevaluate the Orphan Drug Act and its regulations and policies. We do not know if, when, or how the FDA may change the orphan drug regulations and policies in the future, and it is uncertain how any changes might affect our business. Depending on what changes the FDA may make to its orphan drug regulations and policies, our business could be adversely impacted.
We may not be able to conduct, or contract with others to conduct, animal testing in the future, which could harm our research and development activities.
Certain laws and regulations relating to drug development require us to test our product candidates on animals before initiating clinical trials involving humans. Animal testing activities have been the subject of controversy and adverse publicity. Animal rights groups and other organizations and individuals have attempted to stop animal testing activities by pressing for legislation and regulation in these areas and by disrupting these activities through protests and other means. To the extent the activities of these groups are successful, our research and development activities may be interrupted or delayed.
Risks Related to Third Parties
We rely on third parties to conduct our preclinical studies, and plan to rely on third parties to conduct clinical trials, and those third parties may not perform satisfactorily.
We expect to rely on third-party clinical investigators, CROs, clinical data management organizations and consultants to design, conduct, supervise and monitor certain preclinical studies and any clinical trials. Because we intend to rely on these third parties and will not have the ability to conduct certain preclinical studies or clinical trials independently, we will have less control over the timing, quality and other aspects of such preclinical studies and clinical trials than we would have had we conducted them on our own. These investigators, CROs and consultants will not be our employees and we will have limited control over the amount of time and resources that they dedicate to our programs. Some of these third parties may terminate their engagements with us at any time. We also expect to have to negotiate budgets and contracts with CROs, clinical trial sites and contract manufacturing organizations and we may not be able to do so on favorable terms, which may result in delays to our development timelines and increased costs. If we need to enter into alternative arrangements with, or replace or add any third parties, it would involve substantial cost and require extensive management time and focus, or involve a transition period, and may delay our drug development activities, as well as materially impact our ability to meet our desired clinical development timelines. These third parties may have contractual relationships with other entities, some of which may be our competitors, which may draw time and resources from our programs. The third parties with which we may contract might not be diligent, careful or timely in conducting our preclinical studies or clinical trials, resulting in the preclinical studies or clinical trials being delayed or unsuccessful.
Our reliance on these third parties for such drug development activities will reduce our control over these activities. As a result, we will have less direct control over the conduct, timing and completion of preclinical studies and clinical trials and the management of data developed through preclinical studies and clinical trials than would be the case if we were relying entirely upon our own staff. Nevertheless, we will be responsible for ensuring that each of our studies and trials is conducted in accordance with applicable protocol, legal and regulatory requirements and scientific standards, including good laboratory practice (“GLP”), good clinical practice (“ GCP”), cGMP, and cGTP and our reliance on third parties does not relieve us of our regulatory responsibilities. For example, we will remain responsible for ensuring that each of our clinical trials is conducted in accordance with the general investigational plan and protocols for the trial. Moreover, the FDA and other
27
regulatory authorities require us to comply with GCP standards, regulations for conducting, recording and reporting the results of clinical trials to assure that data and reported results are reliable and accurate and that the rights, integrity and confidentiality of trial participants are protected. Regulatory authorities enforce these GCP requirements through periodic inspections of trial sponsors, principal investigators and trial sites. If we or any of our CROs, clinical sites and investigators fail to comply with applicable GCP requirements, the clinical data generated in our clinical trials may be deemed unreliable and the FDA, European Medicines Agency (“EMA”), or other regulatory authorities may require us to perform additional clinical trials before approving our marketing applications. There can be no assurance that upon inspection by a given regulatory authority, such regulatory authority will determine that any of our clinical trials substantially comply with GCP regulations. In addition, our clinical trials must be conducted with product candidates produced under cGMP regulations and will require a large number of test patients. Our failure or any failure by these third parties to comply with these regulations or to recruit a sufficient number of patients, may require us to repeat clinical trials, which would delay the regulatory approval process. Moreover, our business may be implicated if any of these third parties violates FDA regulatory requirements as well as federal or state healthcare laws and regulations or healthcare privacy and security laws.
If these third parties do not successfully carry out their contractual duties, meet expected deadlines or conduct our clinical trials in accordance with regulatory requirements or our stated protocols, or if these third parties need to be replaced, we will not be able to obtain, or may be delayed in obtaining, marketing approvals for our product candidates and will not be able to, or may be delayed in our efforts to, successfully commercialize our product candidates. As a result, our financial results and the commercial prospects for our product candidates would be harmed, our costs could increase and our ability to generate revenue could be delayed.
We depend on strategic partnerships and collaboration arrangements, such as our collaboration arrangements with Spark Therapeutics, Inc. (“Spark”), and Bluerock Therapeutics, Inc. (“Bluerock”), for the application of our gene circuit platform technology to the development and commercialization of potential product candidates in certain indications, and if these arrangements are unsuccessful, this could impair our ability to generate revenues and materially harm our results of operations.
Our business strategy for exploiting the potential of our gene circuit platform technology is dependent upon maintaining our current arrangements and establishing new arrangements with strategic partners, research collaborators and other third parties. We currently have collaboration agreements with Spark and Bluerock. These collaboration agreements provide for, among other things, research funding and significant future payments should certain development, regulatory and commercial milestones be achieved. Under these arrangements, our collaborators are typically responsible for:
| • | electing to advance product candidates through preclinical and into clinical development; |
| • | conducting clinical development and obtaining required regulatory approvals for product candidates; and |
| • | commercializing any resulting products. |
As a result, we may not be able to conduct these collaborations in the manner or on the time schedule we currently contemplate, which may negatively impact our business operations.
Additionally, the development and commercialization of potential product candidates under our collaboration agreements could be substantially delayed, and our ability to receive future funding could be substantially impaired if one or more of our collaborators:
| • | shifts its priorities and resources away from our collaborations due to a change in business strategies, or a merger, acquisition, sale or downsizing of its company or business unit; |
| • | ceases development in therapeutic areas which are the subject of our collaboration; |
28
| • | fails to select a product candidate for advancement into preclinical development, clinical development, or subsequent clinical development into a marketed product; |
| • | changes the success criteria for a particular product candidate, thereby delaying or ceasing development of such product candidate; |
| • | significantly delays the initiation or conduct of certain activities which could delay our receipt of milestone payments tied to such activities, thereby impacting our ability to fund our own activities; |
| • | develops a product candidate that competes, either directly or indirectly, with our product candidates; |
| • | does not obtain the requisite regulatory approval of a product candidate; |
| • | does not successfully commercialize a product candidate; |
| • | encounters regulatory, resource or quality issues and is unable to meet demand requirements; |
| • | exercises its rights under the agreement to terminate the collaboration, or otherwise withdraws support for, or otherwise impairs development under the collaboration; |
| • | disagrees on the research, development or commercialization of a product candidate resulting in a delay in milestones, royalty payments or termination of research and development activities for such product candidate; and |
| • | uses our proprietary information or intellectual property in such a way as to jeopardize our rights in such property. |
In addition, the termination of our existing collaborations or any future strategic partnership or collaboration arrangement that we enter into may prevent us from receiving any milestone, royalty payment, sharing of profits, and other benefits under such agreement. Furthermore, disagreements with these parties could require or result in litigation or arbitration, which would be time-consuming and expensive. Any of these events could have a material adverse effect on our ability to develop and commercialize any of our product candidates and may adversely impact our business, prospects, financial condition, and results of operations.
We may not be able to enter into additional strategic transactions on acceptable terms, if at all, which could adversely affect our ability to develop and commercialize current and potential future product candidates and technologies, impact our cash position, increase our expenses and present significant distractions to our management.
From time to time, we consider strategic transactions, such as collaborations, regional partnerships for the co-development and/or co-commercialization of our product candidates in selected territories, acquisitions of companies, asset purchases, joint ventures, out- or in-licensing of product candidates or technologies and biomanufacturing partnerships involving our manufacturing facilities and gene circuit platform technology. For example, we will evaluate and, if strategically attractive, seek to enter into collaborations, including with biotechnology or biopharmaceutical companies, contract development manufacturing organizations or hospitals. The competition for collaborators is intense, and the negotiation process is time-consuming and complex. If we are not able to enter into strategic transactions, we may not have access to required liquidity or expertise to further develop our potential future product candidates or our gene circuit platform. Any such collaboration, or other strategic transaction, may require us to incur non-recurring or other charges, increase our near- and long-term expenditures and pose significant integration or implementation challenges or disrupt our management or business.
We also may acquire additional technologies and assets, form strategic alliances or create joint ventures with third parties that we believe will complement or augment our existing business, but we may not be able to realize the benefit of acquiring such assets. Conversely, any new collaboration that we do enter into may be on
29
terms that are not optimal for us, our product candidates or our technologies. These transactions would entail numerous operational and financial risks, including:
| • | exposure to unknown liabilities; |
| • | disruption of our business and diversion of our management’s time and attention in order to negotiate and manage a collaboration or develop acquired products, product candidates or technologies; |
| • | incurrence of substantial debt or dilutive issuances of equity securities to pay transaction consideration or costs; |
| • | higher-than-expected collaboration, acquisition or integration costs, write-downs of assets or goodwill or impairment charges, increased amortization expenses; |
| • | difficulty and cost in facilitating the collaboration or combining the operations and personnel of any acquired business; |
| • | impairment of relationships with key suppliers, manufacturers or customers of any acquired business due to changes in management and ownership; and |
| • | the inability to retain key employees of any acquired business. |
Accordingly, although there can be no assurance that we will undertake or successfully complete any transactions of the nature described above, any transactions that we do complete may be subject to the foregoing or other risks and our business could be materially harmed by such transactions. Conversely, any failure to enter any collaboration or other strategic transaction that would be beneficial to us could delay the development and potential commercialization of our product candidates and technologies and have a negative impact on the competitiveness of any product candidate or technology that reaches market.
In addition, to the extent that any future collaborators terminate a collaboration agreement, we may be forced to independently develop our current and future product candidates and technologies, including funding preclinical studies or clinical trials, assuming marketing and distribution costs and maintaining, enforcing and defending intellectual property rights, or, in certain instances, abandon product candidates and technologies altogether, any of which could result in a change to our business plan and have a material adverse effect on our business, financial condition, results of operations and prospects.
Risks Related to Manufacturing
The manufacturing of our product candidates is complex. We may encounter difficulties in production. If we encounter any such difficulties, our ability to supply our product candidates for clinical trials or, if approved, for commercial sale, could be delayed or halted entirely.
The manufacture of biopharmaceutical products is complex and requires significant expertise, including the development of advanced manufacturing techniques and process controls. The process of manufacturing our product candidates is also extremely susceptible to product loss due to contamination, equipment failure or improper installation or operation of equipment, operator error, contamination and inconsistency in yields, variability in product characteristics and difficulties in scaling the production process. Even minor deviations from normal manufacturing processes could result in reduced production yields, product defects and other supply disruptions. If microbial, viral or other contaminations are discovered in our product candidates or the manufacturing facilities in which they are made, the facilities may need to be closed for an extended period of time to investigate and remedy the contamination. As a result of the complexities, the cost to manufacture biologics in general, and our cell-based product candidates in particular, is generally higher than traditional small molecule chemical compounds, and the manufacturing process is less reliable and is more difficult to reproduce.
Any adverse developments affecting manufacturing operations for our product candidates, if any are approved, may result in shipment delays, inventory shortages, lot failures, product withdrawals or recalls, or
30
other interruptions in the supply of our products. We may also have to take inventory write-offs and incur other charges and expenses for products that fail to meet specifications, undertake costly remediation efforts or seek more costly manufacturing alternatives. Furthermore, it is too early to estimate our cost of goods sold. The actual cost to manufacture our product candidates could be greater than we expect because we are early in our development efforts.
Construction of our planned in-house manufacturing may be delayed or, even if completed, supply of our product candidates for preclinical and clinical development may become limited or interrupted or may not be of satisfactory quantity or quality, and we will experience delays if we are unable to operate our own manufacturing facility and are required to relay on third party back-up manufacturers.
A key to our strategy is operating our own manufacturing facility. We initiated construction in June 2021 of a dedicated in-house facility to support clinical and commercial-scale production of allogeneic NK cell product candidates in accordance with cGMP and cGTP requirements. We anticipate that this facility will become operational in time to support initial clinical trials for our lead product candidates. Initial manufacturing efforts at our planned facility will focus on product candidates from our two lead programs, SENTI-202 and SENTI-301.
The construction and commissioning of our planned facility may be delayed or may not be completed. As such, we cannot assure that our preclinical or future clinical development product supplies and commercial supplies will not be limited or interrupted. In particular, any change in our plans to construct and operate our own facility, including any decision to rely on third party back-up manufacturers, could require significant effort and expertise because there may be a limited number, if any, of qualified third-party replacements. We do not currently have arrangements in place for a redundant or second-source supply in the event our planned facility does not become operational. Any delays in manufacturing our product candidates could impede, delay, limit or prevent our drug development efforts, which could harm our business, results of operations, financial condition and prospects. Additionally, we may pursue a biomanufacturing partnership in which we grant a third party certain rights to use our manufacturing facility for the manufacture of third parties’ products or product candidates, which could divert our manufacturing capacity and management resources from the manufacture of our product candidates.
We do not currently produce our product candidates in quantities sufficient for preclinical and clinical development, and we do not currently have arrangements with any third parties to produce them for us. We cannot be sure that the manufacturing processes employed by us or the technologies that we incorporate for manufacturing will result in viable or scalable yields of our product candidates that will be safe, effective, and meet market demand.
The manufacturing process for a product candidate is subject to FDA and other regulatory authority review. We and any third-party manufacturers we may contract with must meet applicable manufacturing requirements and undergo rigorous facility and process validation tests required by regulatory authorities in order to comply with regulatory standards, such as cGMP and cGTP. In the event that we or any third-party manufacturer fails to comply with such requirements or to perform obligations in relation to quality, timing or otherwise, or if our supply of components or other materials becomes limited or interrupted for other reasons, we may be forced to or enter into an agreement with another third party, which we may not be able to do on reasonable terms, or at all. In some cases, the technical skills or technology required to manufacture our current and future product candidates may be difficult or impossible to transfer to a third party and a feasible alternative may not exist. If we are required to change manufacturing facilities or manufacturers for any reason, we will be required to verify that the new facilities and procedures comply with quality standards and with all applicable regulations and guidelines. We will also need to verify, such as through a manufacturing comparability study, that any new manufacturing process will produce our product candidate according to the specifications previously submitted to the FDA or another regulatory authority. The delays associated with the verification of a new manufacturing could negatively affect our ability to develop product candidates in a timely manner or within budget. In addition, changes in manufacturers often involve changes in manufacturing procedures and processes, which could require that we
31
conduct bridging studies between our prior clinical supply used in our clinical trials and that of any new manufacturer. We may be unsuccessful in demonstrating the comparability of clinical supplies which could require the conduct of additional clinical trials.
If we receive regulatory approval for any product candidate and we are unable to for any reason to produce sufficient quantities of the product in our own facility, and we are unable to obtain or maintain third-party manufacturing on commercially reasonable terms, we may not be able to commercialize the product candidate successfully. Our or a third party’s failure to execute on our manufacturing requirements and comply with cGMP and cGTP could adversely affect our business in a number of ways, including:
| • | an inability to initiate or continue clinical trials of product candidates under development; |
| • | delay in submitting regulatory applications, or receiving regulatory approvals, for product candidates; |
| • | loss of the cooperation of potential future collaborators; |
| • | subjecting third-party manufacturing facilities or our potential future manufacturing facilities to additional inspections by regulatory authorities; |
| • | requirements to cease distribution or to recall batches of product candidates; and |
| • | in the event of approval to market and commercialize a product candidate, an inability to meet commercial demands for our products. |
Our future in-house manufacturing facility and any third-party manufacturers that we use may be unable to successfully scale the manufacturing of our current or potential future product candidates in sufficient quality and quantity, which would delay or prevent us from developing our current and potential future product candidates and commercializing approved products candidates, if any. We have never operated a cGMP facility before.
In order to conduct clinical trials for our current and potential future product candidates or to commercialize any approved product candidates, we will need to manufacture large quantities of these product candidates. We expect to use our in-house manufacturing facility to produce required quantities of our product candidates upon its planned completion in 2022. We, or any manufacturing partners, may be unable to successfully increase the manufacturing capacity for any current or potential future product candidate in a timely or cost-effective manner, or at all. In addition, quality issues may arise during scale-up activities and may result in lower yields than initially expected. While we believe our planned cGMP facility will be sufficiently scalable to produce commercial quantities, any significant revisions to the manufacturing process may create delays, which could negatively impact our overall development timelines. In addition, we have never operated a cGMP facility before. We may encounter difficulties in operating the facility or meeting the requirements of the FDA or other regulatory authorities that we have not anticipated. If we cannot successfully scale the manufacture of any current or potential future product candidate in sufficient quality and quantity, the development, testing, clinical trials and commercialization of that product candidate may be delayed or infeasible and regulatory approval or commercial launch of any potential resulting product may be delayed or not obtained, which could significantly harm our business.
We are exposed to a number of risks related to our supply chain for the materials required to manufacture our product candidates.
Manufacturing our product candidates is highly complex and requires sourcing specialty materials. Many of the risks associated with the complexity of manufacturing our final products are applicable to the manufacture and supply of the raw materials. In particular, these starting materials are subject to inconsistency in yields, variability in characteristics, contamination, difficulties in scaling the production process and defects. Similar minor deviations in the manufacturing process for these starting materials could result in supply disruption and
32
reduced production yields for our final product. In addition, we rely on third parties for the supply of these materials exposing us to similar risks of reliance on third parties as described above with respect to the manufacturing and supply of our drug products.
Our manufacturing processes requires many reagents, some of which are drug substance intermediates used in our manufacturing processes to bring about chemical or biological reactions, and other specialty materials and equipment, some of which are manufactured or supplied by small companies with limited resources and experience to support commercial production. We currently depend on a limited number of vendors for certain materials and equipment used in the manufacture of our product candidates. Some of these suppliers may not have the capacity to support commercial products manufactured under cGMP by biopharmaceutical firms or may otherwise be ill-equipped to support our needs. Reagents and other key materials from these suppliers may have inconsistent attributes and introduce variability into our manufactured product candidates, which may contribute to variable patient outcomes and possible adverse events. We also do not have supply contracts with many of these suppliers and may not be able to obtain supply contracts with them on acceptable terms or at all. Accordingly, we may experience delays in receiving key materials and equipment to support clinical or commercial manufacturing.
For some of these reagents, equipment, and materials, we rely and may in the future rely on sole source vendors or a limited number of vendors. An inability to continue to source product from any of these suppliers, which could be due to regulatory actions or requirements affecting the supplier, adverse financial or other strategic developments experienced by a supplier, labor disputes or shortages, unexpected demands, or quality issues, could adversely affect our ability to satisfy demand for our product candidates, which could adversely and materially affect our product sales and operating results or our ability to conduct clinical trials, either of which could significantly harm our business. Additionally, in response to governmental shelter-in-place orders resulting from the ongoing COVID-19 pandemic, third-party suppliers and manufacturers on whom we rely may from time to time be required to limit their on-site staff’s availability to conduct activities at their respective facilities, and may encounter problems with shortages of qualified personnel and key contractors, and delays or pauses in the production and delivery of laboratory equipment, materials and supplies necessary for the manufacture of our product candidates. These problems may include workforce reductions, employee absenteeism and attrition, and supply chain failures or delays relating to the ongoing COVID-19 pandemic or other events affecting raw material supply or manufacturing capabilities.
As we continue to develop and scale our manufacturing process, we expect that we will need to obtain rights to and supplies of certain materials and equipment to be used as part of that process. We may not be able to obtain rights to such materials on commercially reasonable terms, or at all, and if we are unable to alter our process in a commercially viable manner to avoid the use of such materials or find a suitable substitute, it would have a material adverse effect on our business. Even if we are able to alter our process so as to use other materials or equipment, such a change may lead to a delay in our clinical development and/or commercialization plans. If such a change occurs for a product candidate that is already in clinical testing, the change may require us to perform both comparability studies and to collect additional data from patients prior to undertaking more advanced clinical trials.
Changes in methods of product candidate manufacturing or formulation may result in the need to perform new clinical trials, which would require additional costs and cause delay.
As product candidates are developed through preclinical to late-stage clinical trials towards approval and commercialization, it is common that various aspects of the development program, such as manufacturing methods and formulation, are altered along the way in an effort to optimize yield and manufacturing batch size, minimize costs and achieve consistent quality and results. Such changes carry the risk that they will not achieve these intended objectives. Any of these changes could cause our product candidates to perform differently and affect the results of ongoing, planned or future clinical trials conducted with the altered materials. This could delay completion of clinical trials, require the conduct of bridging clinical trials or the repetition of one or more
33
clinical trials, increase clinical trial costs, delay approval of our product candidates and jeopardize our ability to commence product sales and generate revenue.
Risks Related to Our Business and Operations
If the market opportunities for our current and potential future product candidates, including SENTI-202, SENTI-301 and SENTI-401, are smaller than we believe they are, our future product revenues may be adversely affected, and our business may suffer.
Our understanding of the number of people who suffer from diseases that our current product candidates may be able to treat are based on estimates. These estimates may prove to be incorrect, and new studies may reduce the estimated incidence or prevalence of these diseases. The number of patients in the United States or elsewhere may turn out to be lower than expected, may not be otherwise amenable to treatment with our current or potential future product candidates or patients may become increasingly difficult to identify and access, all of which would adversely affect our business prospects and financial condition. In particular, the treatable population for our candidates may further be reduced if our estimates of addressable populations are erroneous or sub-populations of patients do not derive benefit from our product candidates.
Further, there are several factors that could contribute to making the actual number of patients who receive our current or potential future product candidates less than the potentially addressable market. These include the lack of widespread availability of, and limited reimbursement for, new therapies in many underdeveloped markets.
We face competition from companies that have developed or may develop product candidates for the treatment of the diseases that we may target, including companies developing novel therapies and platform technologies. If these companies develop platform technologies or product candidates more rapidly than we do, or if their platform technologies or product candidates are more effective or have fewer side effects, our ability to develop and successfully commercialize product candidates may be adversely affected.
The development and commercialization of cell and gene therapies is highly competitive. We compete with a variety of large pharmaceutical companies, multinational biopharmaceutical companies, other biopharmaceutical companies and specialized biotechnology companies, as well as technology and/or therapeutics being developed at universities and other research institutions. Our competitors are often larger and better funded than we are. Our competitors have developed, are developing or will develop product candidates and processes competitive with ours. Competitive therapeutic treatments include those that have already been approved and accepted by the medical community and any new treatments that are currently in development or that enter the market. We believe that a significant number of product candidates are currently under development, and may become commercially available in the future, for the treatment of conditions for which we may try to develop product candidates. There is intense and rapidly evolving competition in the biotechnology and biopharmaceutical fields. We believe that while our gene circuit platform, its associated intellectual property, the characteristics of our current and potential future product candidates and our scientific and technical know-how together give us a competitive advantage in this space, competition from many sources remains.
Many of our competitors have significantly greater financial, technical, manufacturing, marketing, sales and supply resources or experience than we do. If we successfully obtain approval for any product candidate, we will face competition based on many different factors, including the safety and effectiveness of our product candidates, the ease with which our product candidates can be administered, the timing and scope of regulatory approvals for these product candidates, the availability and cost of manufacturing, marketing and sales capabilities, price, reimbursement coverage and patent position. Competing products and product candidates could present superior treatment alternatives, including by being more effective, safer, less expensive or marketed and sold more effectively than any products we may develop. Competitive products and product
34
candidates may make any product we develop obsolete or noncompetitive before we recover the expense of developing and commercializing such product. Such competitors could also recruit our employees, which could negatively impact our level of expertise and our ability to execute our business plan.
Any inability to attract and retain qualified key management, technical personnel and employees would impair our ability to implement our business plan.
Our success largely depends on the continued service of key executive management, advisors and other specialized personnel, including Timothy Lu, our Chief Executive Officer, Philip Lee, our Chief Technology Officer, Kanya Rajangam, our Chief Medical and Development Officer, and Deborah Knobelman, our Chief Financial Officer. Our senior management may terminate their employment with us at any time. For example, Senti’s former Chief Scientific Officer departed Senti in the first quarter of 2022, and our Chief Operating Officer notified us in July 2022 of his intent to resign from his employment with us in August 2022. We do not maintain “key person” insurance for any of our employees. The loss of one or more members of our executive team, management team or other key employees or advisors could delay our research and development programs and have a material adverse effect on our business, financial condition, results of operations and prospects.
Recruiting and retaining qualified scientific and clinical personnel and, if we progress the development of any of our product candidates, commercialization, manufacturing and sales and marketing personnel, will be critical to our success. The loss of the services of members of our senior management or other key employees could impede the achievement of our research, development and commercialization objectives and seriously harm our ability to successfully implement our business strategy. Furthermore, replacing members of our senior management and key employees may be difficult and may take an extended period of time because of the limited number of individuals in our industry with the breadth of skills and experience required to successfully develop, gain regulatory approval of and commercialize our product candidates. Our success also depends on our ability to continue to attract, retain and motivate highly skilled junior, mid-level and senior managers, as well as junior, mid-level and senior scientific and medical personnel. Competition to hire from this limited candidate pool is intense, and we may be unable to hire, train, retain or motivate these key personnel on acceptable terms given the competition among numerous pharmaceutical and biotechnology companies for similar personnel. We also experience competition for the hiring of scientific and clinical personnel from universities and research institutions. In addition, we rely on consultants and advisors, including scientific and clinical advisors, to assist us in formulating our research and development and commercialization strategy. Our consultants and advisors may have commitments under consulting or advisory contracts with other entities that may limit their availability to us. If we are unable to continue to attract and retain high-quality personnel, our ability to pursue our growth strategy will be limited.
We may experience difficulties in managing our growth and expanding our operations.
We have limited experience in therapeutic development. As our current and potential future product candidates enter and advance through preclinical studies and any clinical trials, we will need to expand our development, regulatory and manufacturing capabilities or contract with other organizations to provide these capabilities for us.
To manage our anticipated future growth, we will continue to implement and improve our managerial, operational, and financial systems, expand our facilities, and continue to recruit and train additional qualified personnel. Due to our limited financial resources and the complexity in managing a company with such anticipated growth, we may not be able to effectively manage the expansion of our operations or recruit and train additional qualified personnel. In addition, we have limited experience in managing the manufacturing processes necessary for making cell and gene therapies. The expansion of our operations may lead to significant costs and may divert our management and business development resources. Any inability to manage growth could delay the execution of our business plans or disrupt our operations.
In addition, future growth imposes significant added responsibilities on members of management, including: identifying, recruiting, integrating, maintaining, and motivating additional employees; managing our internal
35
development efforts effectively, including the clinical and FDA review process for our product candidates, while complying with our contractual obligations to contractors and other third parties; and improving our operational, financial and management controls, reporting systems and procedures.
We may also experience difficulties in the discovery and development of potential future product candidates using our gene circuit platform if we are unable to meet demand as we grow our operations. In the future, we also expect to have to manage additional relationships with collaborators, suppliers and other organizations. Our ability to manage our operations and future growth will require us to continue to improve our operational, financial and management controls, reporting systems and procedures and secure adequate facilities for our operational needs. We may not be able to implement improvements to our management information and control systems in an efficient or timely manner and may discover deficiencies in existing systems and controls.
If any of our product candidates is approved for marketing and commercialization in the future and we are unable to develop sales, marketing and distribution capabilities on our own or enter into agreements with third parties to perform these functions on acceptable terms, we will be unable to successfully commercialize any such future products.
We currently have no sales, marketing or distribution capabilities or experience. We will need to develop internal sales, marketing and distribution capabilities to commercialize each current and potential future product candidate that gains, if ever, FDA or other regulatory authority approval, which would be expensive and time-consuming, or enter into collaborations with third parties to perform these services. If we decide to market any approved products directly, we will need to commit significant financial and managerial resources to develop a marketing and sales force with technical expertise and supporting distribution, administration and compliance capabilities. If we rely on third parties with such capabilities to market any approved products or decide to co-promote products with third parties, we will need to establish and maintain marketing and distribution arrangements with third parties, and there can be no assurance that we will be able to enter into such arrangements on acceptable terms or at all. In entering into third-party marketing or distribution arrangements, any revenue we receive will depend upon the efforts of the third parties and we cannot assure you that such third parties will establish adequate sales and distribution capabilities or be successful in gaining market acceptance for any approved product. If we are not successful in commercializing any product approved in the future, either on our own or through third parties, our business and results of operations could be materially and adversely affected.
Our potential future international operations may expose us to business, political, operational and financial risks associated with doing business outside of the United States.
Our business is subject to risks associated with conducting business internationally. Some of our future clinical trials may be conducted outside of the United States and we may enter into key supply arrangements or do other business with persons outside of the United States. Furthermore, if we or any future collaborator succeeds in developing any products, we anticipate marketing them in the European Union and other jurisdictions in addition to the United States. If approved, we or any future collaborator may hire sales representatives and conduct physician and patient association outreach activities outside of the United States. Doing business internationally involves a number of risks, including but not limited to:
| • | multiple, conflicting and changing laws and regulations such as those relating to privacy, data protection and cybersecurity, tax laws, export and import restrictions, employment laws, regulatory requirements and other governmental approvals, permits and licenses; |
| • | failure by us to obtain and maintain regulatory approvals for the commercialization of our product candidates in various countries; |
| • | rejection or qualification of foreign clinical trial data by the competent authorities of other countries; |
| • | additional potentially relevant third-party patent rights; |
36
| • | complexities and difficulties in obtaining, maintaining, protecting and enforcing our intellectual property rights; |
| • | difficulties in staffing and managing foreign operations; |
| • | complexities associated with managing multiple payor reimbursement regimes, government payors or patient self-pay systems; |
| • | limits in our ability to penetrate international markets; |
| • | financial risks, such as longer payment cycles, difficulty collecting accounts receivable, the impact of local and regional financial crises on demand and payment for our products and exposure to foreign currency exchange rate fluctuations; |
| • | natural disasters, political and economic instability, including wars, terrorism and political unrest, outbreak of disease (including the COVID-19 pandemic), boycotts, curtailment of trade and other business restrictions; |
| • | certain expenses including, among others, expenses for travel, translation and insurance; and |
| • | regulatory and compliance risks that relate to anti-corruption compliance and record-keeping that may fall within the purview of the U.S. Foreign Corrupt Practices Act, its accounting provisions or its anti-bribery provisions or provisions of anti-corruption or anti-bribery laws in other countries. |
Any of these factors could harm our ongoing international operations and supply chain, as well as any future international expansion and operations and, consequently, our business, financial condition, prospects and results of operations.
Our business entails a significant risk of product liability, and our inability to obtain sufficient insurance coverage could have a material adverse effect on our business, financial condition, results of operations and prospects.
As we conduct preclinical studies and future clinical trials of our current and potential future product candidates, we will be exposed to significant product liability risks inherent in the development, testing, manufacturing and marketing of these product candidates. Product liability claims could delay or prevent completion of our development programs. If we succeed in marketing products, such claims could result in an FDA investigation of the safety and effectiveness of our products, our manufacturing processes and facilities or our marketing programs and potentially a recall of our products or more serious enforcement action, limitations on the approved indications for which they may be used or suspension or withdrawal of approvals. Regardless of the merits or eventual outcome, liability claims may also result in decreased demand for our products, injury to our reputation, costs to defend the related litigation, a diversion of management’s time and our resources, substantial monetary awards to trial participants or patients and a decline in our stock price. Any insurance we have or may obtain may not provide sufficient coverage against potential liabilities. Furthermore, clinical trial and product liability insurance is becoming increasingly expensive. As a result, we or any future collaborators may be unable to obtain sufficient insurance at a reasonable cost to protect us against losses caused by product liability claims that could have a material adverse effect on our business, financial condition, results of operations and prospects.
Our employees, principal investigators, consultants and commercial collaborators may engage in misconduct or other improper activities, including noncompliance with regulatory standards and requirements.
We are exposed to the risk of fraud or other misconduct by our employees, principal investigators, consultants and commercial collaborators. Misconduct by employees could include intentional failures to comply with FDA regulations, provide accurate information to the FDA, comply with manufacturing standards we may establish, comply with federal and state healthcare fraud and abuse laws and regulations, report financial
37
information or data accurately or disclose unauthorized activities to us. In particular, sales, marketing and business arrangements in the healthcare industry are subject to extensive laws and regulations intended to prevent fraud, kickbacks, self-dealing and other abusive practices. These laws and regulations may restrict or prohibit a wide range of pricing, discounting, marketing and promotion, sales commission, customer incentive programs and other business arrangements. Such misconduct could also involve the improper use of information obtained in the course of clinical trials, which could result in regulatory sanctions and serious harm to our reputation. It is not always possible to identify and deter misconduct, and the precautions we take to detect and prevent this activity may not be effective in controlling unknown or unmanaged risks or losses or in protecting us from governmental investigations or other actions or lawsuits stemming from a failure to be in compliance with such laws or regulations. If any such actions are instituted against us, and we are not successful in defending ourselves or asserting our rights, those actions could have a material adverse effect on our business and financial condition, including the imposition of significant criminal, civil and administrative fines or other sanctions, such as monetary penalties, damages, fines, disgorgement, imprisonment, exclusion from participation in government-funded healthcare programs, such as Medicare and Medicaid, integrity obligations, reputational harm and the curtailment or restructuring of our operations.
We depend on sophisticated information technology systems and data processing to operate our business. If we experience security or data privacy breaches or other unauthorized or improper access to, use of, or destruction of our proprietary or confidential data, employee data or personal data, we may face costs, significant liabilities, harm to our brand and business disruption.
We rely on information technology systems and data processing that we or our service providers, collaborators, consultants, contractors or partners operate to collect, process, transmit and store electronic information in our day-to-day operations, including a variety of personal data, such as name, mailing address, email addresses, phone number and potentially clinical trial information. Additionally, we, and our service providers, collaborators, consultants, contractors or partners, do or will collect, receive, store, process, generate, use, transfer, disclose, make accessible, protect and share personal information, health information and other information to host or otherwise process some of our anticipated future clinical data and that of users, develop our products, to operate our business, for clinical trial purposes, for legal and marketing purposes, and for other business-related purposes. Our internal computer systems and data processing and those of our third-party vendors, consultants, collaborators, contractors or partners, including future CROs may be vulnerable to a cyber-attack (including supply chain cyber-attacks), malicious intrusion, breakdown, destruction, loss of data privacy, actions or inactions by our employees or contractors that expose security vulnerabilities, theft or destruction of intellectual property or other confidential or proprietary information, business interruption or other significant security incidents. As the cyber-threat landscape evolves, these attacks are growing in frequency, level of persistence, sophistication and intensity, and are becoming increasingly difficult to detect. In addition to traditional computer “hackers,” threat actors, software bugs, malicious code (such as viruses and worms), employee theft or misuse, denial-of-service attacks (such as credential stuffing), phishing and ransomware attacks, sophisticated nation-state and nation-state supported actors now engage in attacks (including advanced persistent threat intrusions). These risks may be increased as a result of COVID-19, owing to an increase in personnel working remotely and higher reliance on internet technology. Furthermore, because the techniques used to obtain unauthorized access to, or to sabotage, systems change frequently and often are not recognized until launched against a target, we may be unable to anticipate these techniques or implement adequate preventative measures. We may also experience security breaches that may remain undetected for an extended period.
There can be no assurance that we, our service providers, collaborators, consultants, contractors or partners will be successful in efforts to detect, prevent or fully recover systems or data from all breakdowns, service interruptions, attacks or breaches of systems that could adversely affect our business and operations and/or result in the loss of critical or sensitive data. Any failure by us or our service providers, collaborators, consultants, contractors or partners to detect, prevent, respond to or mitigate security breaches or improper access to, use of, or inappropriate disclosure of any of this information or other confidential or sensitive information, including
38
patients’ personal data, or the perception that any such failure has occurred, could result in claims, litigation, regulatory investigations and other proceedings, significant liability under state, federal and international law, and other financial, legal or reputational harm to us. Further, such failures or perceived failures could result in liability and a material disruption of our development programs and our business operations, which could lead to significant delays or setbacks in our research, delays to commercialization of our product candidates, lost revenues or other adverse consequences, any of which could have a material adverse effect on our business, results of operations, financial condition, prospects and cashflow. For example, the loss or alteration of clinical trial data from future clinical trials could result in delays in our regulatory approval efforts and significantly increase our costs to recover or reproduce the data.
Additionally, applicable laws and regulations relating to privacy, data protection or cybersecurity, external contractual commitments and internal privacy and security policies may require us to notify relevant stakeholders if there has been a security breach, including affected individuals, business partners and regulators. Such disclosures are costly, and the disclosures or any actual or alleged failure to comply with such requirements could lead to a materially adverse impact on the business, including negative publicity, a loss of confidence in our services or security measures by our business partners or breach of contract claims. There can be no assurance that the limitations of liability in our contracts would be enforceable or adequate or would otherwise protect us from liabilities or damages if we fail to comply with applicable data protection laws, privacy policies or other data protection obligations related to information security or security breaches.
If we do not comply with laws regulating the protection of the environment and health and human safety, our business could be adversely affected.
Our research, development and manufacturing involve the use of hazardous materials and various chemicals. We maintain quantities of various flammable and toxic chemicals in our facilities that are required for our research, development and manufacturing activities. We are subject to federal, state and local laws and regulations governing the use, manufacture, storage, handling and disposal of these hazardous materials. We believe our procedures for storing, handling and disposing of these materials in our facilities comply with the relevant guidelines of the state of California and the Occupational Safety and Health Administration of the U.S. Department of Labor. Although we believe that our safety procedures for handling and disposing of these materials comply with the standards mandated by applicable regulations, the risk of accidental contamination or injury from these materials cannot be eliminated. If an accident occurs, we could be held liable for resulting damages, which could be substantial. We are also subject to numerous environmental, health and workplace safety laws and regulations, including those governing laboratory procedures, exposure to blood-borne pathogens and the handling of animals and biohazardous materials. Although we maintain workers’ compensation insurance to cover us for costs and expenses we may incur due to injuries to our employees resulting from the use of these materials, this insurance may not provide adequate coverage against potential liabilities. Although we have some environmental liability insurance covering certain of our facilities, we may not maintain adequate insurance for all environmental liability or toxic tort claims that may be asserted against us in connection with our storage or disposal of biological or hazardous materials. Additional federal, state and local laws and regulations affecting our operations may be adopted in the future. We may incur substantial costs to comply with, and substantial fines or penalties if we violate, any of these laws or regulations.
Our business, operations and clinical development plans and timelines could be adversely affected by the effects of health epidemics, including the ongoing COVID-19 pandemic, on the manufacturing, clinical trial and other business activities performed by us or by third parties with whom we may conduct business, including our anticipated contract manufacturers, CROs, shippers and others.
Health epidemics could cause significant disruption in our operations and the operations of third-party manufacturers, CROs and other third parties upon whom we rely. For example, in March 2020, the World Health Organization declared the COVID-19 outbreak a pandemic. Since then, COVID-19 has spread to most countries and all 50 states within the United States, and the U.S. government has, at various times, ordered the closure of
39
all non-essential businesses, imposed social distancing measures, “shelter-in-place” orders and restrictions on travel between the United States, Europe and certain other countries. The global pandemic and government measures taken in response have also had a significant impact on businesses and commerce worldwide, as worker shortages have occurred, supply chains have been disrupted, facilities and production have been suspended across a variety of industries, and demand for certain goods and services, such as medical services and supplies, has spiked, while demand for other goods and services, such as travel, has fallen. In connection with COVID-19, we implemented work-from-home policies for most employees. The effects of government orders and our work-from-home policies may negatively impact productivity, disrupt our business and delay our clinical programs and timelines, the magnitude of which will depend, in part, on the length and severity of the restrictions and other limitations on our ability to conduct our business in the ordinary course.
If our relationships with our suppliers or other vendors are terminated or scaled back as a result of the COVID-19 pandemic or other health epidemics, we may not be able to enter into arrangements with alternative suppliers or vendors or do so on commercially reasonable terms or in a timely manner. Switching or adding additional suppliers or vendors involves substantial cost and requires management time and focus. In addition, there is a natural transition period when a new supplier or vendor commences work. As a result, delays may occur, which could adversely impact our ability to meet our desired clinical development and any future commercialization timelines. Although we carefully manage our relationships with our suppliers and vendors, there can be no assurance that we will not encounter challenges or delays in the future or that these delays or challenges will not harm our business.
In addition, our preclinical studies and future clinical trials may be affected by the COVID-19 pandemic. Clinical site initiation, patient enrollment and activities that require visits to clinical sites, including data monitoring, may be delayed due to prioritization of hospital resources toward the COVID-19 pandemic or concerns among patients about participating in clinical trials during a pandemic. Some patients may have difficulty following certain aspects of clinical trial protocols if quarantines impede patient movement or interrupt healthcare services. These challenges may also increase the costs of completing our clinical trials. Similarly, if we are unable to successfully recruit and retain patients and principal investigators and site staff who, as healthcare providers, may have heightened exposure to COVID-19 or experience additional restrictions by their institutions, city or state, our preclinical studies and future clinical trial operations could be adversely impacted.
The spread of COVID-19, which has caused a broad impact globally, may materially affect us economically. While the potential economic impact brought by, and the duration of, COVID-19 may be difficult to assess or predict, a widespread pandemic has resulted in significant volatility for global financial markets, resulting in economic uncertainty that could continue to significantly impact our business and operations and may reduce our ability to access capital, which could in the future negatively affect our liquidity. In addition, a recession or market correction resulting from the spread of COVID-19 could materially affect our business and the value of our common stock. In addition, any recurrence or new increases in the rates and severity of COVID-19 infection could cause other widespread or more severe impacts depending on where infection rates are highest.
Further, we may experience additional disruptions that could severely impact our business and future clinical trials, including:
| • | diversion of healthcare resources away from the conduct of clinical trials, including the diversion of hospitals serving as our clinical trial sites and hospital staff supporting the conduct of our clinical trials; |
| • | interruption or delays in the operations of the FDA or other regulatory authorities, which may impact review and approval timelines; |
| • | limitations on employee resources that would otherwise be focused on the conduct of our preclinical studies and clinical trials, including because of sickness of employees or their families or the desire of employees to avoid contact with large groups of people; |
40
| • | risk that participants enrolled in our clinical trials will acquire COVID-19 while the clinical trial is ongoing, which could impact the results of the clinical trial, including by increasing the number of observed adverse events; and |
| • | refusal of the FDA or other regulatory authorities to accept data from clinical trials in these affected geographies. |
In particular, three vaccines for COVID-19 have been granted Emergency Use Authorization by the FDA, and two of those later received marketing approval. Additional vaccines may be authorized or approved in the future. The resultant demand for vaccines and potential for manufacturing facilities and materials to be commandeered under the Defense Production Act of 1950, or equivalent foreign legislation, may make it more difficult to obtain materials or manufacturing slots for the product candidates needed for our clinical trials, which could lead to delays in these trials. These and similar, and perhaps more severe, disruptions in our operations could have a material adverse effect on our business, results of operations, cash flows, financial condition and/or prospects.
As a result of the COVID-19 public health emergency, we may be required to develop and implement additional clinical trial policies and procedures designed to help protect subjects from the COVID-19 virus. The ultimate impact of the COVID-19 pandemic on our business operations is highly uncertain and subject to change and will depend on future developments, including new regulatory requirements and changes to existing regulations.
The global pandemic of COVID-19 continues to evolve rapidly. We do not yet know the full extent of potential delays or impacts on our business, our future clinical trials, healthcare systems or the global economy as a whole that may result from the ongoing COVID-19 pandemic. However, these effects could have a material impact on our operations, and we continue to monitor the COVID-19 situation closely. To the extent the COVID-19 pandemic adversely affects our business, results of operations, cash flows, financial condition and/or prospects, it may also have the effect of heightening many of the other risks described in this “Risk Factors” section.
Our business, operations, financial position and clinical development plans and timelines could be materially adversely affected by the continuing military action in Ukraine.
As a result of the military action commenced in February 2022 by the Russian Federation and Belarus in Ukraine, and related economic sanctions imposed by certain governments and our financial position and operations may be materially and adversely affected. As our ability to continue to operate will be dependent on raising debt and equity finance, any adverse impact to those markets as a result of this military action, including due to increased market volatility, decreased availability in third-party financing and/or a deterioration in the terms on which it is available (if at all), could negatively impact our business, operations or financial position. The extent of any potential impact is not yet determinable, however.
The current economic downturn may harm our business and results of operations.
Our overall performance depends, in part, on worldwide economic conditions. In recent months, we have observed increased economic uncertainty in the United States and abroad. Impacts of such economic weakness include:
| • | declining overall demand for goods and services, leading to reduced profitability; |
| • | reduced credit availability; |
| • | higher borrowing costs; |
| • | reduced liquidity; |
41
| • | volatility in credit, equity and foreign exchange markets; and |
| • | bankruptcies. |
These developments could lead to supply chain disruption, inflation, higher interest rates, and uncertainty about business continuity, which may adversely affect our business and our results of operations.
Recent volatility in capital markets and lower market prices for our securities may affect our ability to access new capital through sales of shares of our common stock or issuance of indebtedness, which may harm our liquidity, limit our ability to grow our business, pursue acquisitions or improve our operating infrastructure and restrict our ability to compete in our markets.
Our operations consume substantial amounts of cash, and we intend to continue to make significant investments to support our business growth, respond to business challenges or opportunities, develop new solutions, retain or expand our current levels of personnel, improve our existing solutions, enhance our operating infrastructure, and potentially acquire complementary businesses and technologies. Our future capital requirements may be significantly different from our current estimates and will depend on many factors, including the need to:
| • | finance unanticipated working capital requirements; |
| • | develop or enhance our technological infrastructure and our existing solutions; |
| • | pursue acquisitions or other strategic relationships; and |
| • | respond to competitive pressures. |
Accordingly, we may need to pursue equity or debt financings to meet our capital needs. With uncertainty in the capital markets and other factors, such financing may not be available on terms favorable to us or at all. If we raise additional funds through further issuances of equity or convertible debt securities, our existing stockholders could suffer significant dilution, and any new equity securities we issue could have rights, preferences, and privileges superior to those of holders of our common stock. Any debt financing secured by us in the future could involve additional restrictive covenants relating to our capital-raising activities and other financial and operational matters, which may make it more difficult for us to obtain additional capital and to pursue business opportunities, including potential acquisitions. If we are unable to obtain adequate financing or financing on terms satisfactory to us, we could face significant limitations on our ability to invest in our operations and otherwise suffer harm to our business.
Rising inflation rates could negatively impact our revenues and profitability if increases in the prices of our products or a decrease in consumer spending results in lower sales. In addition, if our costs increase and we are not able to pass along these price increases to our customers, our net income would be adversely affected, and the adverse impact may be material.
Inflation rates, particularly in the United States, have increased recently to levels not seen in years. Increased inflation may result in decreased demand for our products and services, increased operating costs (including our labor costs), reduced liquidity, and limitations on our ability to access credit or otherwise raise debt and equity capital. In addition, the United States Federal Reserve has raised, and may again raise, interest rates in response to concerns about inflation. Increases in interest rates, especially if coupled with reduced government spending and volatility in financial markets, may have the effect of further increasing economic uncertainty and heightening these risks.
42
Risks Related to Our Intellectual Property
If we are unable to obtain or protect intellectual property rights related to our technology and current or future product candidates, or if our intellectual property rights are inadequate, our competitors could develop and commercialize products and technology similar or identical to ours, and we may not be able to compete effectively in our market or successfully commercialize any product candidates we may develop.
Our success depends in part on our ability to obtain and maintain protection for our owned and in-licensed intellectual property rights and proprietary technology. We rely on a combination of patents, trademarks, trade secret protection and confidentiality agreements, including in-licenses of intellectual property rights and biologic materials of others, to protect our current or future platform technologies, product candidates, methods used to manufacture our current or future product candidates and methods for treating patients using our current or future product candidates.
We own or in-license patents and patent applications relating to our platform technologies and product candidates. There is no guarantee that any patents covering our platform technologies or product candidates will issue from the patent applications we own, in-license or may file in the future, or, if they do, that the issued claims will provide adequate protection for our platform technologies or product candidates, or any meaningful competitive advantage. Further, there cannot be any assurance that such patents issued will not be infringed, designed around, invalidated by third parties or effectively prevent others from commercializing competitive technologies, products or product candidates.
The patent prosecution process is expensive, complex and time-consuming. Patent license negotiations also can be complex and protracted, with uncertain results. We may not be able to file, prosecute, maintain, enforce or license all necessary or desirable patents and patent applications at a reasonable cost or in a timely manner. It is also possible that we will fail to identify patentable aspects of our research and development output before it is too late to obtain patent protection. The patent applications that we own or in-license may fail to result in issued patents, and, even if they do issue as patents, such patents may not cover our current or future technologies or product candidates in the United States or in other countries or provide sufficient protection from competitors. In addition, the coverage claimed in a patent application can be significantly reduced before the patent is issued, and its scope can be reinterpreted after issuance. We do not have exclusive control over the preparation, filing and prosecution of patent applications under certain of our in-license agreements, and we may not have the right to control the preparation, filing and prosecution of patent applications, or to maintain the rights to patents, that we out-license to third parties. Therefore, these patents and applications may not be prosecuted and enforced in a manner consistent with the best interests of our business. Even if our owned or in-licensed patent applications issue as patents, they may not issue in a form that will provide us with any meaningful protection, prevent competitors from competing with us or otherwise provide us with any competitive advantage. Our competitors may be able to circumvent our patents by developing similar or alternative product candidates in a non-infringing manner.
Further, although we make reasonable efforts to ensure patentability of our inventions, we cannot guarantee that all of the potentially relevant prior art relating to our owned or in-licensed patents and patent applications has been found. For example, publications of discoveries in scientific literature often lag behind the actual discoveries, and patent applications in the United States and other jurisdictions are typically not published until 18 months after filing, and in some cases not at all. Additionally, pending patent applications that have been published can, subject to certain limitations, be later amended in a manner that could cover our platform technologies, our product candidates, or the use of our technologies. We thus cannot know with certainty whether we or our licensors were the first to file for patent protection of such inventions. In addition, the United States Patent and Trademark Office (“USPTO”) might require that the term of a patent issuing from a pending patent application be disclaimed and limited to the term of another patent that is commonly owned or names a common inventor. There is no assurance that all potentially relevant prior art relating to our owned or in-licensed patent applications has been found. For this reason, and because there is no guarantee that any prior art search is absolutely correct and comprehensive, we may be unaware of prior art that could be used to invalidate an issued
43
patent or to prevent our owned or in-licensed patent applications from issuing as patents. Invalidation of any of our patent rights, including in-licensed patent rights, could materially harm our business.
Moreover, the patent positions of biotechnology companies like ours are generally uncertain because they may involve complex legal and factual considerations that have, in recent years, been the subject of legal development and change. The relevant patent laws and their interpretation, both inside and outside of the United States, is also uncertain. Changes in either the patent laws or their interpretation in the United States and other jurisdictions may diminish our ability to protect our platform technology or product candidates and could affect the value of such intellectual property. In particular, our ability to stop third parties from making, using, selling, offering to sell or importing products that infringe, misappropriate or otherwise violate our intellectual property will depend in part on our success in obtaining and enforcing patent claims that cover our platform technology, product candidates, inventions and improvements. We cannot guarantee that patents will be granted with respect to any of our owned or licensed pending patent applications or with respect to any patent applications we may file or license in the future, nor can we be sure that any patents that may be granted to us or our licensors in the future will be commercially useful in protecting our products, the methods of use or manufacture of those products. Additionally, third parties, including our former employees and collaborators, may challenge the ownership or inventorship of our patent rights to claim that they are entitled to ownership and inventorship interest, and we may not be successful in defending against such claims. However, we are not currently facing any such challenges. Moreover, issued patents do not guarantee the right to practice our technology in relation to the commercialization of our products. Issued patents only allow us to block—in some cases—potential competitors from practicing the claimed inventions of the issued patents.
The issuance, scope, validity, enforceability and commercial value of our pending patent rights are uncertain. The standards applied by the USPTO and foreign patent offices in granting patents are not always certain and moreover, are not always applied uniformly or predictably. For example, there is no uniform worldwide policy regarding patentable subject matter or the scope of claims allowable in patents. Our pending and future patent applications may not result in patents being issued in the United States or in other jurisdictions which protect our technology or products or which effectively prevent others from commercializing competitive technologies and products. Changes in either the patent laws or interpretation of the patent laws in the United States and other countries may diminish the value of our owned or in-licensed patent applications or narrow the scope of any patent protection we may obtain from our owned or in-licensed patent applications. In addition, the laws of foreign countries may not protect our rights to the same extent as the laws of the United States.
Further, patents and other intellectual property rights in the pharmaceutical and biotechnology space are evolving and involve many risks and uncertainties. For example, third parties may have blocking patents that could be used to prevent us from commercializing our product candidates and any future product candidates and practicing our proprietary technology, and any issued patents may be challenged, invalidated or circumvented, which could limit our ability to stop competitors from marketing related products or could limit the term of patent protection that otherwise may exist for our product candidate and any future product candidates. In addition, the scope of the rights granted under any issued patents may not provide us with protection or competitive advantages against competitors or other parties with similar technology. Additionally, our competitors may initiate legal proceedings, such as declaratory judgment actions in federal court or reexaminations or an inter partes review at the USPTO in an attempt to invalidate or narrow the scope of our patents. However, we are not currently facing any such proceedings. Furthermore, our competitors or other parties may independently develop similar technologies that are outside the scope of the rights granted under any issued patents. For these reasons, we may face competition with respect to our product candidates and any future product candidates. Moreover, because of the extensive time required for development, testing and regulatory review of a potential product, it is possible that, before any particular product candidate can be commercialized, any patent protection for such product candidate may expire or remain in force for only a short period following commercialization, thereby reducing the commercial advantage the patent provides.
Even if patents do successfully issue from our owned or in-licensed patent application, and even if such patents cover our current or any future technologies or product candidates, third parties may challenge their
44
validity, enforceability or scope, which may result in such patents being narrowed, invalidated, or held unenforceable. Any successful challenge to these patents or any other patents owned by or licensed to us could deprive us of rights necessary for the successful commercialization of any current or future technologies or product candidates that we may develop. Likewise, if patent applications we own or have in-licensed with respect to our development programs and current or future technologies or product candidates fail to issue, if their breadth or strength is threatened, or if they fail to provide meaningful exclusivity, other companies could be dissuaded from collaborating with us to develop current or future technologies or product candidates. Lack of valid and enforceable patent protection could threaten our ability to commercialize current or future products and could prevent us from maintaining exclusivity with respect to the invention or feature claimed in the patent applications. Any failure to obtain or any loss of patent protection could have a material adverse impact on our business and ability to achieve profitability. We may be unable to prevent competitors from entering the market with a product that is similar or identical to any of our current or potential future product candidates or from utilizing technologies similar to those in our gene circuit platform technologies.
The filing of a patent application or the issuance of a patent is not conclusive as to its ownership, inventorship, scope, patentability, validity or enforceability. Issued patents and patent applications may be challenged in the courts and in the patent office in the United States and abroad. For example, our patent applications or patent applications filed by our licensors, or any patents that grant therefrom, may be challenged through third-party submissions, opposition or derivation proceedings. By further example, any issued patents that may result from our owned or in-licensed patent applications may be challenged through reexamination, inter partes review or post-grant review proceedings before the USPTO, or in declaratory judgment actions or counterclaims. An adverse determination in any such submission, proceeding or litigation could prevent the issuance of, reduce the scope of, invalidate or render unenforceable our owned or in-licensed patent rights, result in the loss of exclusivity, limit our ability to stop others from using or commercializing similar or identical platforms and product candidates, or allow third parties to compete directly with us without payment to us. In addition, if the breadth or strength of protection provided by any patents that might result from our owned or in-licensed patent applications is threatened, it could dissuade companies from collaborating with us to license, develop or commercialize current or future platforms or product candidates. Any of the foregoing could have a material adverse effect on our business, financial condition, results of operations and prospects.
Moreover, we currently co-own certain patent applications with third parties and may in the future co-own additional patents and patent applications with third parties. If we are unable to obtain an exclusive license to any such third-party co-owners’ interest in such patents or patent application, such co-owners may be able to license their rights to other third parties, including our competitors, and our competitors could market competing products and technology. We may need the cooperation of any such co-owners to enforce such patents against third parties, and such cooperation may not be provided to us. Any of the foregoing could have a material adverse effect on our competitive position, business prospects and financial conditions.
Our in-licensed patent rights may be subject to a reservation of rights by one or more third parties, such as the U.S. government. In addition, our rights in such inventions may be subject to certain requirements to manufacture product candidates embodying such inventions in the United States. Any exercise by the U.S. government of such rights could harm our competitive position, business, financial condition, results of operations and prospects.
The patent protection and patent prosecution for some of our product candidates and technologies may be dependent on third parties.
While we normally seek to obtain the right to control prosecution, maintenance and enforcement of the patents relating to our product candidates and technologies, there may be times when the filing and prosecution activities for patents and patent applications relating to our product candidates and technologies are controlled by our licensors or collaborators. Our licensors may not successfully prosecute the patent applications to which we
45
are licensed. Even if patents are issued in respect of these patent applications, our licensors may fail to maintain these patents, may determine not to pursue litigation against other companies that are infringing these patents, or may pursue such litigation less aggressively than we would.
If any of our licensors or collaborators fail to prosecute, maintain and enforce such patents and patent applications in a manner consistent with the best interests of our business, including by payment of all applicable fees for patents covering our product candidates and technologies, we could lose our rights to the intellectual property or our exclusivity with respect to those rights, our ability to develop and commercialize those product candidates and technologies may be adversely affected and we may not be able to prevent competitors from making, using and selling competing product candidates. In addition, even where we have the right to control patent prosecution of patents and patent applications we have licensed to and from third parties, we may still be adversely affected or prejudiced by actions or inactions of our licensees, our current and future licensors and their counsel that took place prior to the date upon which we assumed control over patent prosecution.
Further, we may have limited control over the manner in which our licensors initiate an infringement proceeding against a third-party infringer of the intellectual property rights, or defend certain of the intellectual property that is licensed to us. It is possible that the licensors’ infringement proceeding(s) or defense activities may be less vigorous than had we conducted them ourselves.
We may be unable to acquire or in-license any relevant third-party intellectual property rights that we identify as necessary or important to our business operations.
Because our development programs may in the future require the use of proprietary rights held by third parties, the growth of our business may depend in part on our ability to acquire, in-license or use these third-party proprietary rights. We may be unable to acquire or in-license any compositions, methods of use, processes or other third-party intellectual property rights from third parties that we identify as necessary for our product candidates. The licensing of third-party intellectual property rights is a competitive area, and more established companies may pursue strategies to license or acquire third-party intellectual property rights that we may consider attractive or necessary. More established companies may have a competitive advantage over us due to their size, capital resources and greater clinical development and commercialization capabilities. In addition, companies that perceive us to be a competitor may be unwilling to assign or license rights to us. We also may be unable to license or acquire third-party intellectual property rights on terms that would allow us to make an appropriate return on our investment or at all. Even if we are able to obtain a license, it may be non-exclusive, thereby giving our competitors access to the same technologies licensed to us. If we are unable to license such technology, or if we are forced to license such technology on unfavorable terms, our business could be materially harmed. If we are unable to obtain a necessary license, we may be unable to develop or commercialize the affected current or future product candidates, which could materially harm our business, and the third parties owning such intellectual property rights could seek either an injunction prohibiting our sales, or, with respect to our sales, an obligation on our part to pay royalties or other forms of compensation. Any of the foregoing could harm our competitive position, business, financial condition, results of operations and prospects.
Further, our licensors may retain certain rights under their agreements with us, including the right to use the underlying technology for noncommercial academic and research use, to publish general scientific findings from research related to the technology, and to make customary scientific and scholarly disclosures of information relating to the technology. It is difficult to monitor whether our licensors limit their use of the technology to these uses, and we could incur substantial expenses to enforce our rights to our licensed technology in the event of misuse.
Additionally, some intellectual property that we have in-licensed or that we own may have been discovered through government funded programs and thus may be subject to federal regulations such as “march-in” rights, certain reporting requirements and a preference for U.S.-based companies. Compliance with such regulations may limit our exclusive rights, and limit our ability to contract with non-U.S. manufacturers. As a result, the U.S.
46
government may have certain rights to intellectual property embodied in our current or future product candidates pursuant to the Bayh-Dole Act of 1980 (“Bayh-Dole Act”) and implementing regulations. These U.S. government rights in certain inventions developed under a government-funded program include a non-exclusive, non-transferable, irrevocable worldwide license to use inventions for any governmental purpose. In addition, the U.S. government may have the right to require us or our licensors to grant exclusive, partially exclusive, or non-exclusive licenses to any of these inventions to a third party if it determines that: (i) adequate steps have not been taken to commercialize the invention; (ii) government action is necessary to meet public health or safety needs; or (iii) government action is necessary to meet requirements for public use under federal regulations (also referred to as “march-in rights”). More specifically, certain currently in-licensed patents that cover certain split, universal and programmable chimeric antigen receptor technology may be subject to march-in-rights. This technology is not embodied in any of our current product candidates. In addition, certain currently in-licensed patents that cover certain components and process for regulating the expression of a fusion protein with the use of a protease inhibitor are subject to march-in-rights, which technology can be embodied in certain regulator dial gene circuits. We also own a patent family claiming an invention made under research partially funded by the federal government. Such invention covers mesenchymal stem cells that express combinations of immune effectors for autoimmunity. While the foregoing invention is not embodied in any current product candidates, it is subject to march-in-rights. The U.S. government also has the right to take title to these inventions made through government funded programs if we, or the applicable licensor, fail to disclose the invention to the government and fail to file an application to register the intellectual property within specified time limits. These time limits have recently been changed by regulation, and may change in the future. Intellectual property generated under a government-funded program is also subject to certain reporting requirements, compliance with which may require us or the applicable licensor to expend substantial resources. In addition, the U.S. government requires that any products embodying the subject invention or produced through the use of the subject invention be manufactured substantially in the United States. The manufacturing preference requirement can be waived if the owner of the intellectual property can show that reasonable but unsuccessful efforts have been made to grant licenses on similar terms to potential licensees that would be likely to manufacture substantially in the United States or that under the circumstances domestic manufacture is not commercially feasible. This preference for U.S. manufacturers may limit our ability to contract with non-U.S. product manufacturers for products covered by such intellectual property. To the extent any of our current or future intellectual property is generated through the use of U.S. government funding, the provisions of the Bayh-Dole Act may similarly apply.
We currently, and in the future may continue to, enter into agreements involving licenses or collaborations that provide for access or sharing of intellectual property. These intellectual property-related agreements may impose certain obligations and restrictions on our ability to develop and commercialize our product candidates and technologies that are the subject of such licenses.
We license rights from third parties to use certain intellectual property relevant to one or more of our current and future product candidates. In the future, we may need to obtain additional licenses from others to advance our research and development activities or allow the commercialization of our current and future product candidates we may identify and pursue. These existing license agreements impose, and any future license agreements we enter into are likely to impose, various development, commercialization, funding, milestone, royalty, diligence, sublicensing, insurance, patent prosecution and enforcement or other obligations on us. For example, we are a party to three license agreements with the U.S. Department of Health and Human Services, as represented by the National Cancer Institute (“NCI”), for intellectual property relevant to our product candidates. For a more detailed description of the license agreements with NCI, see the section titled “Business—Material License and Collaboration Agreements.”
In addition, certain of our future agreements with third parties may limit or delay our ability to consummate certain transactions, may impact the value of those transactions, or may limit our ability to pursue certain activities. For example, we may in the future enter into license agreements that are not assignable or transferable, or that require the licensor’s express consent in order for an assignment or transfer to take place.
47
Further, we or our licensors, if any, may fail to identify patentable aspects of inventions made in the course of development and commercialization activities before it is too late to obtain patent protection on them. Therefore, we may miss potential opportunities to strengthen our patent position. It is possible that defects of form in the preparation or filing of our patents or patent applications may exist, or may arise in the future, for example with respect to proper priority claims, inventorship, claim scope, or requests for patent term adjustments. If we or our licensors fail to establish, maintain or protect such patents and other intellectual property rights, such rights may be reduced or eliminated. If our licensors are not fully cooperative or disagree with us as to the prosecution, maintenance or enforcement of any patent rights, such patent rights could be compromised. If there are material defects in the form, preparation, prosecution, or enforcement of our patents or patent applications, such patents may be invalid and/or unenforceable, and such applications may never result in valid, enforceable patents. Any of these outcomes could impair our ability to prevent competition from third parties, which may have an adverse impact on our business, financial conditions, results of operations and prospects.
Furthermore, we may not have the right to control the preparation, filing, prosecution, maintenance, enforcement and defense of patents and patent applications that we license from third parties. In certain circumstances, our licensed patent rights are subject to our reimbursing our licensors for their patent prosecution and maintenance costs. If our licensors and future licensors fail to prosecute, maintain, enforce and defend patents we may license, or lose rights to licensed patents or patent applications, our licensed rights may be reduced or eliminated. In such circumstances, our right to develop and commercialize any of our products or product candidates that is the subject of such licensed rights could be materially adversely affected. Even where we have the right to control prosecution of patents and patent applications under license from third parties, we may still be adversely affected or prejudiced by actions or inactions of our predecessors or licensors and their counsel that took place prior to us assuming control over patent prosecution.
Our technology acquired or licensed currently or in the future from various third parties is or may be subject to retained rights. Our predecessors or licensors do and may retain certain rights under their agreements with us, including the right to use the underlying technology for non-commercial academic and research use, to publish general scientific findings from research related to the technology, and to make customary scientific and scholarly disclosures of information relating to the technology. It is difficult to monitor whether our predecessors or licensors limit their use of the technology to these uses, and we could incur substantial expenses to enforce our rights to our licensed technology in the event of misuse.
If we are limited in our ability to utilize acquired or licensed technologies, or if we lose our rights to critical in-licensed technology, we may be unable to successfully develop, out-license, market and sell our product candidates, which could prevent or delay new product introductions. Our business strategy depends on the successful development of acquired technologies and licensed technology into commercial product candidates. Therefore, any limitations on our ability to utilize these technologies may impair our ability to develop, out-license or market and sell our product candidates.
If we fail to comply with our obligations under any existing or future license, collaboration or other intellectual property-related agreements, we may be required to pay damages and could lose intellectual property rights that may be necessary for developing, commercializing and protecting our current or future technologies or product candidates or we could lose certain rights to grant sublicenses.
We have certain obligations to third-party licensors from whom we license certain patent rights that are relevant to one or more current and future product candidates. In the future, we may need to obtain additional licenses from other third parties to advance our research and development activities or allow the commercialization of our current and future product candidates. Our existing license agreements impose, and any future license agreements we enter into are likely to impose, various development, commercialization, funding, milestone, royalty, diligence, sublicensing, insurance, patent prosecution and enforcement or other obligations on us. For a more detailed description of our existing license agreements, see the section titled “Business—Material
48
License and Collaboration Agreements.” If we breach any of these obligations, including diligence obligations with respect to development and commercialization of product candidates covered by the intellectual property licensed to us, or use the intellectual property licensed to us in an unauthorized manner or we are subject to bankruptcy-related proceedings, we may be required to pay damages and the licensor may have the right to terminate the respective agreement or materially modify the terms of the license, such as by rendering currently exclusive licenses non-exclusive. License termination or modification could result in our inability to develop, manufacture and sell products that are covered by the licensed intellectual property or could enable a competitor to gain access to the licensed intellectual property.
In certain circumstances, our licensed patent rights are subject to our reimbursing our licensors for their patent prosecution and maintenance costs. If our licensors and future licensors fail to prosecute, maintain, enforce and defend patents we may license, or lose rights to licensed patents or patent applications, our licensed rights may be reduced or eliminated. In such circumstances, our right to develop and commercialize any of our products or product candidates that are the subject of such licensed rights could be materially adversely affected.
Our current or future licensors may own or control intellectual property that has not been licensed to us and, as a result, we may be subject to claims, regardless of their merit, that we are infringing, misappropriating or otherwise violating the licensor’s intellectual property rights. In addition, while we cannot currently determine the amount of the royalty obligations we would be required to pay on sales of future products if infringement or misappropriation were found, those amounts could be significant. The amount of our future royalty obligations will depend on the technology and intellectual property we use in products that we successfully develop and commercialize, if any. Therefore, even if we successfully develop and commercialize products, we may be unable to achieve or maintain profitability.
Disputes may arise between us and our present and future licensors regarding intellectual property subject to a licensing agreement, including:
| • | the scope of rights granted under the license agreement and other interpretation-related issues, including but not limited to our right to transfer or assign the license; |
| • | whether and the extent to which our product candidates, technology and processes infringe on intellectual property of the licensor that is not subject to the licensing agreement; |
| • | our right to sublicense patents and other rights to third parties, including the terms and conditions thereof; |
| • | our diligence obligations with respect to the development and commercialization of our product candidates that are covered by the license agreement, and what activities satisfy those diligence obligations; |
| • | our right to transfer or assign the license; |
| • | the inventorship and ownership of inventions and know-how resulting from the joint creation or use of intellectual property by our licensors and us and our collaborators; and |
| • | the priority of invention of patented technology. |
If disputes over intellectual property that we license in the future prevent or impair our ability to maintain our licensing arrangements on acceptable terms, we may not be able to successfully develop and commercialize the affected product candidates, which would have a material adverse effect on our business, financial condition, results of operations and prospects.
In addition, the agreements under which we currently license intellectual property or technology from the National Cancer Institute (“NCI”) and other third parties are complex, and certain provisions in such agreements may be susceptible to multiple interpretations. The resolution of any contract interpretation disagreement that
49
may arise could narrow what we believe to be the scope of our rights to the relevant intellectual property or technology, or increase what we believe to be our financial or other obligations under the relevant agreement, either of which could have a material adverse effect on our business, financial condition, results of operations and prospects. Moreover, if disputes over intellectual property that we have licensed prevent or impair our ability to maintain our current licensing arrangements on commercially acceptable terms, we may be unable to successfully develop and commercialize the affected product candidates, which could have a material adverse effect on our business, financial condition, results of operations and prospects.
In addition, while we currently do not have any liens, security interests, or other encumbrances on the intellectual property that we own, we may, in the future, need to obtain a loan or a line of credit that will require that we put up our intellectual property as collateral to our lenders or creditors. If we do so, and we violate the terms of any such loan or credit agreement, our lenders or creditors may take possession of such intellectual property, including the rights to receive proceeds derived from such intellectual property.
Patent terms may not be able to protect our competitive position for an adequate period of time with respect to our current or future technologies or product candidates.
Patents have a limited lifespan. The term of individual patents and applications in our portfolio depends upon the legal term of patents in the countries in which they are obtained. In most countries in which we file, including the United States, the patent term is 20 years from the earliest date of filing a non-provisional patent application. Extensions of patent term may be available, but there is no guarantee that we would have patents eligible for extension, or that we would succeed in obtaining any particular extension, and no guarantee any such extension would confer a patent term for a sufficient period of time to exclude others from commercializing product candidates similar or identical to ours. In the United States, the term of a patent may be eligible for patent term adjustment, which permits patent term restoration as compensation for delays incurred at the USPTO during the patent prosecution process. In addition, for patents that cover an FDA-approved drug, the Drug Price Competition and Patent Term Restoration Act of 1984 (the “Hatch-Waxman Act”) permits a patent term extension of up to five years beyond the expiration of the patent. While the length of the patent term extension is related to the length of time the drug is under regulatory review, patent term extension cannot extend the remaining term of a patent beyond a total of 14 years from the date of product approval, and only one patent per approved drug—and only those claims covering the approved drug, a method for using it or a method for manufacturing it—may be extended under the Hatch-Waxman Act. Similar provisions are available in Europe and other foreign jurisdictions to extend the term of a patent that covers an approved drug. In the future, if and when our products receive FDA approval or applicable approval in other jurisdictions, we expect to apply for patent term extensions on issued patents covering those products in the United States and other jurisdiction where such extensions are available; however, there is no guarantee that the applicable authorities, including the FDA in the United States, will agree with our assessment of whether such extensions should be granted, and if granted, the length of such extensions. We also may not be granted an extension because of, for example, failing to exercise due diligence during the testing phase or regulatory review process, failing to apply within applicable deadlines, failing to apply prior to expiration of relevant patents or otherwise failing to satisfy applicable requirements. If we are unable to obtain patent term extension or the term of any such extension is less than we request, the period during which we can enforce our patent rights for the applicable product candidate will be shortened and our competitors may obtain approval to market competing products sooner. As a result, our revenue from applicable products could be reduced. Further, if this occurs, our competitors may be able to launch their products earlier by taking advantage of our investment in development and clinical trials along with our clinical and preclinical data. This could have a material adverse effect on our business and ability to achieve profitability.
The life of a patent and the protection it affords are limited. As a result, our owned and in-licensed patent portfolio provides us with limited rights that may not last for a sufficient period of time to exclude others from commercializing product candidates similar or identical to ours. Even if patents covering our product candidates are obtained, once the patent life has expired, we may be open to competition from competitive products,
50
including generics or biosimilars. For example, given the large amount of time required for the research, development, testing and regulatory review of new product candidates, patents protecting such candidates might expire before or shortly after such candidates are commercialized. As a result, our owned and licensed patent portfolio may not provide us with sufficient rights to exclude others from commercializing products similar or identical to ours.
Changes in U.S. patent law or the patent law of other countries or jurisdictions could diminish the value of patents in general, thereby impairing our ability to protect our current or any future technologies or product candidates.
Changes in either the patent laws or interpretation of the patent laws in the United States or elsewhere could increase the uncertainties and costs surrounding the prosecution of patent applications and the enforcement or defense of issued patents. The United States has enacted and implemented wide-ranging patent reform legislation. On September 16, 2011, the Leahy-Smith America Invents Act (the “Leahy-Smith Act”) was signed into law, which could increase the uncertainties and costs surrounding the prosecution of our owned or in-licensed patent applications and the enforcement or defense of any future owned or in-licensed issued patents. The Leahy-Smith Act includes a number of significant changes to U.S. patent law. These include provisions that affect the way patent applications are prosecuted, redefine prior art, may affect patent litigation and switch the U.S. patent system from a “first-to-invent” system to a “first-to-file” system. Under a first-to-file system, assuming the other requirements for patentability are met, the first inventor to file a patent application generally will be entitled to the patent on an invention regardless of whether another inventor had made the invention earlier. A third party that files a patent application in the USPTO after March 16, 2013, but before us, could therefore be awarded a patent covering an invention of ours even if we had made the invention before it was made by such third party. This will require us to be cognizant of the time from invention to filing of a patent application. Since patent applications in the United States and most other countries are confidential for a period of time after filing or until issuance, we cannot be certain that we or our licensors were the first to either (i) file any patent application related to our product candidates or (ii) invent any of the inventions claimed in our or our licensor’s patents or patent applications. The Leahy-Smith Act also allows third-party submission of prior art to the USPTO during patent prosecution and sets forth additional procedures to challenge the validity of a patent by USPTO-administered post-grant proceedings, including derivation, reexamination, inter partes review, post-grant review and interference proceedings. The USPTO developed additional regulations and procedures to govern administration of the Leahy-Smith Act, and many of the substantive changes to patent law associated with the Leahy-Smith Act, and, in particular, the first-to-file provisions, became effective on March 16, 2013. Accordingly, it is not clear what, if any, impact the Leahy-Smith Act will have on the operation of our business. The Leahy-Smith Act and its implementation could increase the uncertainties and costs surrounding the prosecution of our owned or in-licensed patent applications and the enforcement or defense of our issued owned or in-licensed patents, all of which could have a material adverse impact on our business prospects and financial condition.
As referenced above, for example, courts in the U.S. continue to refine the heavily fact-and-circumstance-dependent jurisprudence defining the scope of patent protection available for therapeutics, narrowing the scope of patent protection available in certain circumstances or weakening the rights of patent owners in certain situations. This creates uncertainty about our ability to obtain patents in the future and the value of such patents. In addition, the patent positions of companies in the development and commercialization of pharmaceuticals are particularly uncertain. Recent U.S. Supreme Court rulings have narrowed the scope of patent protection available in certain circumstances and weakened the rights of patent owners in certain situations. This combination of events has created uncertainty with respect to the validity and enforceability of patents, once obtained. Depending on future actions by the U.S. Congress, the federal courts and the USPTO, the laws and regulations governing patents could change in unpredictable ways that could have a material adverse effect on our existing patent portfolio and our ability to protect and enforce our intellectual property in the future. We cannot provide assurance that future developments in U.S. Congress, the federal courts and the USPTO will not adversely impact our owned or in-licensed patents or patent applications. The laws and regulations governing patents could change
51
in unpredictable ways that could weaken our and our licensors’ ability to obtain new patents or to enforce our existing owned or in-licensed patents and patents that we might obtain or in-license in the future. Similarly, changes in patent law and regulations in other countries or jurisdictions or changes in the governmental bodies that enforce them or changes in how the relevant governmental authority enforces patent laws or regulations may have a material adverse effect on our and our licensors’ ability to obtain new patents or to protect and enforce our owned or in-licensed patents or patents that we may obtain or in-license in the future.
We may be subject to lawsuits or litigation to protect or enforce our patents or other intellectual property, which could result in substantial costs and liability and prevent us from commercializing our potential products.
Third parties may attempt to invalidate our or our licensors’ intellectual property rights via procedures including but not limited to patent infringement lawsuits, declaratory judgment actions, interferences, oppositions and inter partes reexamination proceedings before the USPTO, U.S. courts and foreign patent offices or foreign courts. An adverse determination in any such submission or proceeding could reduce the scope or enforceability of, or invalidate, our patent rights, which could adversely affect our competitive position. Because of a lower evidentiary standard in USPTO proceedings compared to the evidentiary standard in United States federal courts necessary to invalidate a patent claim, a third party could potentially provide evidence in a USPTO proceeding sufficient for the USPTO to hold a claim invalid even though the same evidence would be insufficient to invalidate the claim if first presented in a district court action. Accordingly, a third party may attempt to use the USPTO procedures to invalidate our patent claims that would not have been invalidated if first challenged by the third party in a district court action. Even if such rights are not directly challenged, disputes could lead to the weakening of our or our licensors’ intellectual property rights. Our defense against any attempt by third parties to circumvent or invalidate our intellectual property rights could be costly to us, could require significant time and attention of our management, and could have a material and adverse impact on our profitability, financial condition and prospects or ability to successfully compete.
We or our licensors may find it necessary to pursue claims or to initiate lawsuits to protect or enforce our owned or in-licensed patent or other intellectual property rights. The cost to us in defending or initiating any litigation or other proceeding relating to our owned or in-licensed patent or other intellectual property rights, even if resolved in our favor, could be substantial, particularly in a foreign jurisdiction, and any litigation or other proceeding would divert our management’s attention. Such litigation or proceedings could materially increase our operating losses and reduce the resources available for development activities or any future sales, marketing or distribution activities. Some of our competitors may be able to more effectively sustain the costs of complex patent litigation because they have substantially greater resources. Uncertainties resulting from the initiation and continuation of patent litigation or other proceedings could delay our research and development efforts and materially limit our ability to continue our operations.
If we or our licensors were to initiate legal proceedings against a third party to enforce a patent covering one of our product candidates or our technology, the defendant could counterclaim that such patent is invalid or unenforceable. In patent litigation in the United States, defendant counterclaims alleging invalidity or unenforceability are commonplace. Grounds for a validity challenge could be an alleged failure to meet any of several statutory requirements, for example, claiming patent-ineligible subject matter, lack of novelty, indefiniteness, lack of written description, non-enablement, anticipation or obviousness. Grounds for an unenforceability assertion could be an allegation that someone connected with prosecution of the patent withheld relevant information from the USPTO or made a misleading statement during prosecution. The outcome of such invalidity and unenforceability claims is unpredictable. With respect to the validity question, for example, we cannot be certain that there is no invalidating prior art of which we or our licensors and the patent examiner were unaware during prosecution. If a defendant were to prevail on a legal assertion of invalidity or unenforceability, we could lose at least part, and perhaps all, of the patent protection for one or more of our product candidates or certain aspects of our platform technologies. Such a loss of patent protection could have a material adverse effect on our business, financial condition, results of operations and prospects. Patents and other intellectual property
52
rights also will not protect our product candidates and technologies if competitors or third parties design around such product candidates and technologies without legally infringing, misappropriating or violating our owned or in-licensed patents or other intellectual property rights.
We may not be able to protect our intellectual property rights throughout the world, which could negatively impact our business.
Filing, prosecuting and defending patents on current or future technologies or product candidates in all countries throughout the world would be prohibitively expensive, and our intellectual property rights in some countries outside the United States can be less extensive than those in the United States. In addition, the laws of some countries do not protect intellectual property rights to the same extent as laws in the United States. Consequently, we may not be able to prevent third parties from practicing our inventions in all countries outside the United States, or from selling or importing products made using our inventions in and into the United States or other countries. Competitors or other third parties may use our technologies in jurisdictions where we have not obtained patent protection to develop their own products and, further, may export infringing product candidates to territories where we have patent protection or licenses, but enforcement is not as strong as that in the United States. These product candidates may compete with our products, and our patents or other intellectual property rights may not be effective or sufficient to prevent them from competing.
Many companies have encountered significant difficulties in protecting and defending such rights in such jurisdictions. The legal systems of certain countries, including certain developing countries, do not favor the enforcement of patents and other intellectual property protection, particularly those relating to biotechnology, which could make it difficult for us to stop the infringement of any owned and in-licensed patents we may obtain in other countries, or the marketing of competing products in violation of our intellectual property and proprietary rights generally. Proceedings to enforce our owned or in-licensed intellectual property and proprietary rights in foreign jurisdictions could result in substantial costs and could divert our efforts and attention from other aspects of our business. Such proceedings could also put any owned or in-licensed patents at risk of being invalidated or interpreted narrowly, could put our owned or in-licensed patent applications at risk of not issuing, and could provoke third parties to assert claims against us or our licensors. We or our licensors may not prevail in any lawsuits or other adversarial proceedings that we or our licensors initiate, and the damages or other remedies awarded, if any, may not be commercially meaningful. Accordingly, our and our licensors’ efforts to enforce such intellectual property and proprietary rights around the world may be inadequate to obtain a significant commercial advantage from the intellectual property that we develop or in-license.
Further, many countries have compulsory licensing laws under which a patent owner may be compelled to grant licenses to third parties. In addition, many countries limit the enforceability of patents against government agencies or government contractors. In these countries, the patent owner may have limited remedies, which could materially diminish the value of its patents. If we or any of our licensors are forced to grant a license to third parties with respect to any patents relevant to our business, our competitive position in the relevant jurisdiction may be impaired and our business prospects may be materially adversely affected.
Third parties may initiate legal proceedings alleging that we are infringing, misappropriating or violating their intellectual property rights, the outcome of which would be uncertain and could have a material adverse impact on the success of our business.
Our commercial success depends, in part, upon our ability or the ability of our potential future collaborators to develop, manufacture, market and sell our current or any future product candidates and to use our proprietary technologies without infringing, misappropriating or violating the proprietary and intellectual property rights of third parties. There is a substantial amount of litigation, both within and outside the United States, involving patent and other intellectual property rights in the biotechnology and pharmaceutical industries, including patent infringement lawsuits, interferences, oppositions and inter partes review proceedings before the USPTO, U.S. courts, foreign patent offices or foreign courts. As the field of gene and cell therapies advances, patent applications are being processed by national patent offices around the world. There is uncertainty about which
53
patents will issue, and, if they do, there is uncertainty as to when, to whom, and with what claims. Any claims of patent infringement asserted by third parties would be time consuming and could:
| • | result in costly litigation that may cause negative publicity; |
| • | divert the time and attention of our technical personnel and management; |
| • | cause development delays; |
| • | prevent us from commercializing any of our product candidates until the asserted patent expires or is held finally invalid or not infringed in a court of law; |
| • | require us to develop non-infringing technology, which may not be possible on a cost-effective basis; |
| • | subject us to substantial damages for infringement, which we may have to pay if a court decides that the product candidate or technology at issue infringes on or violates the third party’s rights, and, if the court finds that the infringement was willful, we could be ordered to pay treble damages and the patent owner’s attorneys’ fees; or |
| • | require us to enter into royalty or licensing agreements, which may not be available on commercially reasonable terms, or at all, or which might be non-exclusive, which could result in our competitors gaining access to the same technology. |
Some of our competitors may be able to sustain the costs of complex patent litigation more effectively than we can because they have substantially greater resources. In addition, any uncertainties resulting from the initiation and continuation of any litigation could have a material adverse effect on our ability to raise the funds necessary to continue our operations or could otherwise have a material adverse effect on our business, results of operations, financial condition and prospects.
Numerous U.S. and foreign issued patents and pending patent applications, which are owned by third parties, exist in the fields in which we are pursuing development candidates. As the biotechnology and pharmaceutical industries expand and more patents are issued, the risk increases that we may be subject to claims of infringement of the patent rights of third parties. Because patent applications can take many years to issue, there may also be currently pending patent applications that may later result in issued patents that our technology or product candidates may infringe. Further, we cannot guarantee that we are aware of all patents and patent applications potentially relevant to our technology or products. We may not be aware of potentially relevant third-party patents or applications for several reasons. For example, U.S. applications filed before November 29, 2000, and certain U.S. applications filed after that date that will not be filed outside the U.S. remain confidential until a patent issues. Patent applications filed in the United States (after November 29, 2000) and elsewhere are published approximately 18 months after the earliest filing for which priority is claimed, with such earliest filing date being commonly referred to as the priority date. Therefore, patent applications covering our product candidates or platform technologies could have been filed by others without our knowledge. Any such patent application may have priority over our patent applications or patents, which could require us to obtain rights to issued patents covering such technologies. Additionally, claims pending in patent applications that have been published can, subject to certain limitations, be later amended in a manner that could cover our platform, our product candidates or the use of our technologies.
Although no third party has asserted a claim of patent infringement against us as of the date of this prospectus, others may hold proprietary rights that could prevent our product candidates from being marketed. We or our licensors, or any future strategic collaborator, may be party to, or be threatened with, adversarial proceedings or litigation regarding intellectual property rights with respect to our current or any potential future product candidates and technologies, including derivation, reexamination, inter partes review or post-grant review before the USPTO and similar proceedings in jurisdictions outside of the United States such as opposition proceedings. In some instances, we may be required to indemnify our licensors for the costs associated with any such adversarial proceedings or litigation. Third parties may assert infringement claims against us, our licensors or our strategic collaborators based on existing patents or patents that may be granted in the future, regardless of
54
their merit. There is a risk that third parties may choose to engage in litigation or other adversarial proceedings with us, our licensors or our strategic collaborators to enforce or otherwise assert their patent rights. Even if we believe such claims are without merit, a court of competent jurisdiction could hold that these third-party patents are not invalid, enforceable and infringed, which could have a material adverse impact on our ability to utilize our platform technologies or to commercialize our current or any future product candidates. In order to successfully challenge the validity of any such U.S. patent in federal court, we would need to overcome a presumption of validity by presenting clear and convincing evidence of invalidity. There is no assurance that a court of competent jurisdiction, even if presented with evidence we believe to be clear and convincing, would invalidate the claims of any such U.S. patent.
Further, we cannot guarantee that we will be able to successfully settle or otherwise resolve such adversarial proceedings or litigation. If we are unable to successfully settle future claims on terms acceptable to us, we may be required to engage in or to continue costly, unpredictable and time-consuming litigation and may be prevented from or experience substantial delays in marketing our product candidates. If we, or our licensors, or any future strategic collaborators are found to infringe, misappropriate or violate a third-party patent or other intellectual property rights, we could be required to pay damages, including treble damages and attorney’s fees, if we are found to have willfully infringed. In addition, we, or our licensors, or any future strategic collaborators may choose to seek, or be required to seek, a license from a third party, which may not be available on commercially reasonable terms, if at all. Even if a license can be obtained on commercially reasonable terms, the rights may be non-exclusive, which could give our competitors access to the same technology or intellectual property rights licensed to us, and we could be required to make substantial licensing and royalty payments. Parties making claims against us may obtain injunctive or other equitable relief, which could effectively block our ability to further develop and commercialize our current or future product candidates. We could be forced, including by court order, to cease utilizing, developing, manufacturing and commercializing our platform technologies or product candidates deemed to be infringing. We may be forced to redesign current or future technologies or products. Defense of these claims, regardless of their merit, would involve substantial litigation expense and would be a substantial diversion of employee resources from our business. Any of the foregoing could have a material adverse effect on our ability to generate revenue or achieve profitability and possibly prevent us from generating revenue sufficient to sustain our operations.
Thus, it is possible that one or more third parties will hold patent rights to which we will need a license, which may not be available on reasonable terms or at all. If such third parties refuse to grant us a license to such patent rights on reasonable terms or at all, we may be required to expend significant time and resources to redesign our technology, product candidates or the methods for manufacturing our product candidates, or to develop or license replacement technology, all of which may not be commercially or technically feasible. In such case, we may not be able to market such technology or product candidates and may not be able to perform research and development or other activities covered by these patents. This could have a material adverse effect on our ability to commercialize our product candidates and our business and financial condition.
Lastly, if our technology or products are found to infringe the intellectual property rights of third parties, these third parties may assert infringement claims against our licensees and other parties with whom we have business relationships, and we may be required to indemnify those parties for any damages they suffer as a result of these claims. The claims may require us to initiate or defend protracted and costly litigation on behalf of licensees and other parties regardless of the merits of these claims. If any of these claims succeed, we may be forced to pay damages on behalf of those parties or may be required to obtain licenses for the products they use.
Intellectual property litigation may lead to unfavorable publicity that harms our reputation and causes the market price of Senti Common Shares to decline.
During the course of any intellectual property litigation, there could be public announcements of the initiation of the litigation as well as results of hearings, rulings on motions and other interim proceedings or developments in the litigation. If securities analysts or investors regard these announcements as negative, the
55
perceived value of our existing product candidates, approved products, programs or intellectual property could be diminished. Accordingly, the market price of Senti Common Shares may decline. Such announcements could also harm our reputation or the market for our future products, which could have a material adverse effect on our business.
Intellectual property rights of third parties could adversely affect our ability to commercialize our current or future technologies or product candidates, and we might be required to litigate or obtain licenses from third parties to develop or market our current or future technologies or product candidates, which may not be available on commercially reasonable terms or at all.
Because the gene and cell therapy landscape is still evolving, it is difficult to conclusively assess our freedom to operate without infringing, misappropriating or violating third-party rights. The scope of a patent claim is determined by an interpretation of the law, the written disclosure in a patent and the patent’s prosecution history. Our interpretation of the relevance or the scope of a patent or a pending application may be incorrect. For example, we may incorrectly determine that our products are not covered by a third-party patent or may incorrectly predict whether a third-party’s pending application will issue with claims of relevant scope. Also, our determination of the expiration date of any patent in the United States or abroad that we consider relevant may be incorrect.
There are numerous companies that have pending patent applications and issued patents broadly covering gene and cell therapy generally or covering related inventions that may be relevant for product candidates that we wish to develop. We are aware of third-party patents and patent applications that claim aspects of our current or potential future product candidates and modifications that we may need to apply to our current or potential future product candidates. There are also many issued patents that claim inventions that may be relevant to products we wish to develop. The holders of such patents may be able to block our ability to develop and commercialize the applicable product candidate unless we obtain a license or until such patent expires. In either case, such a license may not be available on commercially reasonable terms or at all, or it may be non-exclusive, which could result in our competitors gaining access to the same intellectual property.
Our competitive position may materially suffer if patents issued to third parties or other third-party intellectual property rights cover our current or future technologies, product candidates or elements thereof or our manufacture or uses relevant to our development plans. In such cases, we may not be in a position to develop or commercialize current or future technologies or product candidates unless we successfully pursue litigation to narrow or invalidate the third-party intellectual property right concerned, or enter into a license agreement with the intellectual property right holder, if available on commercially reasonable terms. There may be issued patents of which we are not aware, held by third parties that, if found to be valid and enforceable, could be alleged to be infringed by our current or future technologies or product candidates. There also may be pending patent applications of which we are not aware that may result in issued patents, which could be alleged to be infringed by our current or future technologies or product candidates. If such an infringement claim should successfully be brought, we may be required to pay substantial damages or be forced to abandon our current or future technologies or product candidates or to seek a license from any patent holders. No assurances can be given that a license will be available on commercially reasonable terms, if at all.
Third-party intellectual property right holders may also actively bring infringement, misappropriation, or other claims alleging violations of intellectual property rights against us. We cannot guarantee that we will be able to successfully settle or otherwise resolve such claims. If we are unable to successfully settle future claims on terms acceptable to us, we may be required to engage in or to continue costly, unpredictable and time-consuming litigation and may be prevented from or experience substantial delays in marketing our product candidates. If we fail in any such dispute, in addition to being forced to pay damages, we may be temporarily or permanently prohibited from commercializing any of our current or future technologies or product candidates that are held to be infringing, misappropriating or otherwise violating third-party intellectual property rights. We might, if possible, also be forced to redesign current or future technologies or product candidates so that we no
56
longer infringe, misappropriate or violate the third-party intellectual property rights. Any of these events, even if we were ultimately to prevail, could require us to divert substantial financial and management resources that we would otherwise be able to devote to our business, which could have a material adverse effect on our financial condition and results of operations.
If we are unable to protect the confidentiality of our trade secrets, our business and competitive position would be harmed.
In addition to seeking patent protection for certain aspects of our current or future technologies and product candidates, we rely on trade secrets, including confidential and unpatented know-how, technology and other proprietary information, to maintain our competitive position and to protect aspects of our business that are not amenable to, or that we do not consider appropriate for, patent protection. Elements of our product candidates, including processes for their preparation and manufacture, may involve proprietary know-how, information, or technology that is not covered by patents, and thus for these aspects we may consider trade secrets and know-how to be our primary intellectual property. Our trade secrets include, for example, certain program specific synthesis, formulations, patient selection strategies and certain aspects of our research.
Trade secrets and know-how can be difficult to protect. We seek to protect trade secrets and confidential and unpatented know-how, in part, by entering into non-disclosure and confidentiality agreements with parties who have access to such knowledge, such as our employees, corporate collaborators, outside scientific collaborators, contract research organizations, contract manufacturers, consultants, advisors and other third parties. We also enter into confidentiality and invention or patent assignment agreements with our employees and consultants under which they are obligated to maintain confidentiality and to assign their inventions to us. However, we cannot be certain that such agreements have been entered into with all relevant parties, and we cannot be certain that our trade secrets and other confidential proprietary information will not be disclosed or that competitors will not otherwise gain access (such as through a cybersecurity breach) to our trade secrets or independently develop substantially equivalent information and techniques. Moreover, individuals with whom we have such agreements may not comply with their terms. Any of these parties may breach such agreements and disclose our proprietary information, including our trade secrets, and we may not be able to obtain adequate remedies for any such breaches. In addition, we take other appropriate precautions, such as physical and technological security measures, to guard against misappropriation of our proprietary technology by third parties.
We may also become involved in inventorship disputes relating to inventions and patents developed by our employees or consultants under such agreements. Enforcing a claim that a party illegally disclosed or misappropriated a trade secret, or securing title to an employee- or consultant-developed invention if a dispute arises, is difficult, expensive and time-consuming, and the outcome is unpredictable. In addition, some courts in the United States and certain foreign jurisdictions disfavor or are unwilling to protect trade secrets. We may need to share our proprietary information, including trade secrets, with future business partners, collaborators, contractors and others located in countries at heightened risk of theft of trade secrets, including through direct intrusion by private parties or foreign actors, and those affiliated with or controlled by state actors. Further, if any of our trade secrets were to be lawfully obtained or independently developed by a competitor, we would have no right to prevent that competitor from using the technology or information to compete with us. If, in the future, any of our trade secrets were to be disclosed to or independently developed by a competitor, our competitive position would be materially and adversely harmed.
We may be subject to claims that we or our employees or consultants have wrongfully used or disclosed alleged trade secrets or other proprietary information of third parties, including our employees’ or consultants’ former employers or their clients.
We are party to various contracts under which we are obligated to maintain the confidentiality of trade secrets or other confidential and proprietary information of third parties, including our licensors and strategic partners. In addition, many of our employees or consultants and our licensors’ employees or consultants were
57
previously employed at universities or biotechnology or biopharmaceutical companies, including our competitors or potential competitors. We may be subject to claims that one or more of these employees or consultants or we have inadvertently or otherwise used or disclosed trade secrets or other proprietary information of third parties, including former employers of our employees and consultants. Litigation or arbitration may be necessary to defend against these claims. If we fail in defending such claims, in addition to paying monetary damages, we may lose valuable intellectual property rights or personnel or may be enjoined from using such intellectual property. Any such proceedings and possible aftermath would likely divert significant resources from our core business, including distracting our technical and management personnel from their normal responsibilities. A loss of key research personnel or their work product could limit our ability to commercialize, or prevent us from commercializing, our current or future technologies or product candidates, which could materially harm our business. Even if we are successful in defending against any such claims, litigation or arbitration could result in substantial costs and could be a distraction to management.
We may be subject to claims challenging the inventorship of our patents and other intellectual property.
We or our licensors may be subject to claims that former employees, collaborators or other third parties have an interest in our owned or in-licensed patents as an inventor or co-inventor, or in our trade secrets or other intellectual property as a contributor to its development. The failure to name the proper inventors on a patent application can result in the patents issuing thereon being unenforceable. Inventorship disputes may arise from conflicting views regarding the contributions of different individuals named as inventors, the effects of foreign laws where foreign nationals are involved in the development of the subject matter of the patent, conflicting obligations of third parties involved in developing our product candidates or as a result of questions regarding co-ownership of potential joint inventions. For example, we or our licensors may have inventorship disputes arise from conflicting obligations of employees, consultants or others who are involved in developing our product candidates. Litigation may be necessary to defend against these and other claims challenging inventorship or our or our licensors’ ownership of our owned or in-licensed patents, trade secrets or other intellectual property. Alternatively, or additionally, we may enter into agreements to clarify the scope of our rights in such intellectual property. If we or our licensors fail in defending any such claims, in addition to paying monetary damages, we may lose valuable intellectual property rights, such as exclusive ownership of, or right to use, intellectual property that is important to our product candidates. Even if we are successful in defending against such claims, litigation could result in substantial costs and be a distraction to management and other employees.
Also, our licensors may have relied on third-party consultants or collaborators or on funds from third parties, such as the U.S. government, such that our licensors are not the sole and exclusive owners of the patents we in-licensed. If other third parties have ownership rights or other rights to our in-licensed patents, they may be able to license such patents to our competitors, and our competitors could market competing products and technology. This could have a material adverse effect on our competitive position, business, financial condition, results of operations and prospects.
Further, while it is our policy to require our employees and contractors who may be involved in the conception or development of intellectual property to execute agreements assigning such intellectual property to us, we may be unsuccessful in executing such an agreement with each party who, in fact, conceives or develops intellectual property that we regard as our own. The assignment of intellectual property rights may not be self-executing, or the assignment agreements may be breached, and we may be forced to bring claims against third parties, or defend claims that they may bring against us, to determine the ownership of what we regard as our intellectual property. Such claims could have a material adverse effect on our business, financial condition, results of operations and prospects.
58
Obtaining and maintaining our patent protection depends on compliance with various procedural, document submission, fee payment and other requirements imposed by government patent agencies, and our patent protection could be reduced or eliminated for non-compliance with these requirements.
Periodic maintenance fees, renewal fees, annuity fees and various other government fees on patents or applications will be due to be paid to the USPTO and various government patent agencies outside of the United States over the lifetime of our owned and in-licensed patents or applications and any patent rights we may own or in-license in the future. The USPTO and various non-U.S. patent offices require compliance with several procedural, documentary, fee payment and other similar provisions during the patent application process. We employ reputable law firms and other professionals to help us comply with these requirements, and we are also dependent on our licensors to take the necessary action to comply with these requirements with respect to our in-licensed intellectual property. In many cases, an inadvertent lapse, including due to the effect of the COVID-19 on us, our patent counsel or other applicable patent maintenance vendors, can be cured by payment of a late fee or by other means in accordance with the applicable rules. There are situations, however, in which non-compliance can result in abandonment or lapse of the patent or patent application, resulting in partial or complete loss of patent rights in the relevant jurisdiction. Non-compliance events that could result in abandonment or lapse of a patent or patent application include, but are not limited to, failure to respond to official actions within prescribed time limits, non-payment of fees and failure to properly legalize and submit formal documents. In such an event, potential competitors might be able to enter the market with similar or identical product candidates or platforms, which could have a material adverse effect on our business prospects and financial condition.
If our trademarks and trade names are not adequately protected, then we may not be able to build name recognition in our markets of interest and our business may be adversely affected.
We use and will continue to use registered and/or unregistered trademarks or trade names to brand and market ourselves and our products. Our trademarks or trade names may be challenged, infringed, circumvented, declared generic or determined to be infringing on other marks. We may not be able to protect our rights to these trademarks and trade names or may be forced to stop using these names, which we use for name recognition by potential collaborators or customers in our markets of interest. At times, competitors may adopt trade names or trademarks similar to ours, thereby impeding our ability to build brand identity and possibly leading to market confusion. In addition, there could be potential trade name or trademark infringement claims brought by owners of other trademarks or trademarks that incorporate variations of our registered or unregistered trademarks or trade names. Over the long term, if we are unable to establish name recognition based on our trademarks and trade names, we may not be able to compete effectively, and our business may be materially adversely affected.
We may also license our trademarks and trade names to third parties, such as distributors. Though these license agreements may provide guidelines for how our trademarks and trade names may be used, a breach of these agreements or misuse of our trademarks and trade names by our licensees may jeopardize our rights in or diminish the goodwill associated with our trademarks and trade names.
Intellectual property rights do not necessarily address all potential threats to our business.
The degree of future protection afforded by our intellectual property rights is uncertain because intellectual property rights have limitations and may not adequately protect our business. The following examples are illustrative:
| • | others may be able to create gene circuit technologies that are similar to our technologies or our product candidates, but that are not covered by the claims of any patents that we own, license or control; |
| • | we or any strategic collaborators might not have been the first to make the inventions covered by the issued patents or pending patent applications that we own, license or control; |
59
| • | we or our licensors might not have been the first to file patent applications covering certain of our owned and in-licensed inventions; |
| • | others may independently develop the same, similar, or alternative technologies without infringing, misappropriating or violating our owned or in-licensed intellectual property rights; |
| • | it is possible that our owned or in-licensed pending patent applications will not lead to issued patents; |
| • | issued patents that we own, in-license, or control may not provide us with any competitive advantages, or may be narrowed or held invalid or unenforceable, including as a result of legal challenges; |
| • | our competitors might conduct research and development activities in the United States and other countries that provide a safe harbor from patent infringement claims for certain research and development activities, as well as in countries where we do not have patent rights, and may then use the information learned from such activities to develop competitive products for sale in our major commercial markets; |
| • | we may choose not to file a patent application in order to maintain certain trade secrets or know-how, and a third party may subsequently file a patent application covering such trade secrets or know-how; and |
| • | the patents of others may have an adverse effect on our business. |
Should any of these events occur, they could have a material adverse impact on our business, financial condition, results of operations and prospects.
Risks Related to Government Regulation
Clinical development includes a lengthy and expensive process with an uncertain outcome, and results of earlier studies and trials may not be predictive of future trial results.
All of our current product candidates are in preclinical development and their risk of failure is high. It is impossible to predict when or if our candidates or any potential future product candidates will prove effective in humans or will receive regulatory approval. Before obtaining marketing approval from regulatory authorities for the sale of any product candidate, we must complete preclinical studies for our current product candidates and then conduct extensive clinical trials to demonstrate the safety, purity and potency, or efficacy of that product candidate in humans. Clinical testing is expensive and can take many years to complete, and its outcome is inherently uncertain. Failure can occur at any time during the development process. The results of preclinical studies and clinical trials of any of our current or potential future product candidates may not be predictive of the results of later-stage clinical trials. Product candidates in later stages of clinical trials may fail to show the desired safety and efficacy traits despite having progressed through preclinical studies and initial clinical trials. A number of companies in the pharmaceutical industry have suffered significant setbacks in advanced clinical trials due to lack of efficacy or safety profiles, notwithstanding promising results in earlier trials.
We are currently conducting IND-enabling studies for our current product candidates. We may experience delays in completing our preclinical studies and initiating or completing our clinical studies. We do not know whether planned preclinical studies and clinical trials will be completed on schedule or at all, or whether planned clinical trials will begin on time, need to be redesigned, enroll patients on time or be completed on schedule, if at all. Our development programs may be delayed for a variety of reasons, including delays related to:
| • | the FDA or other regulatory authorities requiring us to submit additional data or imposing other requirements before permitting us to initiate a clinical trial; |
| • | obtaining regulatory approval to commence a clinical trial; |
| • | reaching agreement on acceptable terms with prospective CROs and clinical trial sites, the terms of which can be subject to extensive negotiation and may vary significantly among different CROs and clinical trial sites; |
60
| • | obtaining IRB or ethics committee approval at each clinical trial site; |
| • | recruiting suitable patients to participate in a clinical trial; |
| • | having patients complete a clinical trial or return for post-treatment follow-up; |
| • | clinical trial sites deviating from trial protocol or dropping out of a trial; |
| • | the FDA placing the clinical trial on hold; |
| • | subjects failing to enroll or remain in our trial at the rate we expect; |
| • | subjects choosing an alternative treatment for the indication for which we are developing or other product candidates, or participating in competing clinical trials; |
| • | lack of adequate funding to continue the clinical trial; |
| • | subjects experiencing severe or unexpected drug-related adverse events; |
| • | any changes to our manufacturing process that may be necessary or desired; |
| • | adding new clinical trial sites; and |
| • | manufacturing sufficient quantities of our product candidates for use in clinical trials. |
Furthermore, we expect to rely on our CROs and clinical trial sites to ensure the proper and timely conduct of our clinical trials and, while we expect to enter into agreements governing their committed activities, we have limited influence over their actual performance.
We could encounter delays if prescribing physicians encounter unresolved ethical issues associated with enrolling patients in clinical trials of our current or potential future product candidates in lieu of prescribing existing treatments that have established safety and efficacy profiles. Further, a clinical trial may be suspended or terminated by us, our collaborators, the IRBs of the institutions in which such trials are being conducted, the Data Safety Monitoring Board for such trial or by the FDA or other regulatory authorities due to a number of factors, including failure to conduct the clinical trial in accordance with regulatory requirements or our clinical protocols, inspection of the clinical trial operations or trial site by the FDA or other regulatory authorities resulting in the imposition of a clinical hold, unforeseen safety issues or adverse side effects, failure to demonstrate a benefit from using a drug or therapeutic biologic, changes in governmental regulations or administrative actions or lack of adequate funding to continue the clinical trial.
Moreover, principal investigators for our clinical trials may serve as scientific advisors or consultants to us from time to time and receive cash or equity compensation in connection with such services. If these relationships and any related compensation result in perceived or actual conflicts of interest, or a regulatory authority concludes that the financial relationship may have affected the interpretation of the trial, the integrity of the data generated at the applicable clinical trial site may be questioned and the utility of the clinical trial itself may be jeopardized, which could result in the delay or rejection of the marketing application we submit. Any such delay or rejection could prevent or delay us from commercializing our current or future product candidates.
If we experience delays in the completion of, or termination of, any clinical trial of any of our current or potential future product candidates, the commercial prospects of such product candidate will be harmed, and our ability to generate product revenue from such product candidates will be delayed. In addition, any delays in completing our clinical trials will increase our costs, slow our product development and approval process and jeopardize our ability to commence product sales and generate revenue. Any of these occurrences may have a material adverse effect on our business, financial condition, results of operations and prospects. In addition, many of the factors that cause, or lead to, a delay in the commencement or completion of clinical trials may also ultimately lead to the denial of regulatory approval of our current or potential future product candidates.
61
We may be unable to obtain U.S. or foreign regulatory approval and, as a result, be unable to commercialize our current or potential future product candidates.
Our current and any potential future product candidates are subject to extensive governmental regulations relating to, among other things, research, testing, development, manufacturing, safety, efficacy, approval, recordkeeping, reporting, labeling, storage, packaging, advertising and promotion, pricing, marketing and distribution of therapeutic biologics. Rigorous preclinical testing and clinical trials and an extensive regulatory approval process are required to be successfully completed in the U.S. and in many foreign jurisdictions before a new drug or therapeutic biologic can be marketed. Satisfaction of these and other regulatory requirements is costly, time-consuming, uncertain and subject to unanticipated delays. It is possible that none of the product candidates we may develop will obtain the regulatory approvals necessary for us or our potential future collaborators to begin selling them.
We have very limited experience in conducting and managing the clinical trials necessary to obtain regulatory approvals, including approval by the FDA and other regulatory authorities. The time required to obtain FDA and other approvals is unpredictable but typically takes many years following the commencement of clinical trials, depending upon the type, complexity and novelty of the product candidate. The standards that the FDA and its foreign counterparts use when regulating us require judgment and can change, which makes it difficult to predict with certainty how they will be applied. Any analysis we perform of data from preclinical and clinical activities is subject to confirmation and interpretation by regulatory authorities, which could delay, limit or prevent regulatory approval. We may also encounter unexpected delays or increased costs due to new government regulations, for example, from future legislation or administrative action, or from changes in regulatory policy during the period of product development, clinical trials and FDA regulatory review in the United States and other jurisdictions. It is impossible to predict whether legislative changes will be enacted, or whether FDA or foreign regulations, guidance or interpretations will be changed, or what the impact of such changes, if any, may be.
Any delay or failure in obtaining required approvals could have a material adverse effect on our ability to generate revenue from the particular product candidate for which we are seeking approval. Further, we and our potential future collaborators may never receive approval to market and commercialize any product candidate. Even if we or a potential future collaborator obtains regulatory approval, the approval may be for targets, disease indications or patient populations that are not as broad as we intended or desired or may require labeling that includes significant use or distribution restrictions or safety warnings.
Once a product obtains regulatory approval, numerous post approval requirements apply, including periodic monitoring and reporting obligations, review of promotional material, reports on ongoing clinical trials and adverse events and inspections of manufacturing facilities. In addition, material changes to approved products, including any changes to the manufacturing process or labeling, require further review by the appropriate authorities before marketing. Approvals may also be withdrawn or revoked due to safety, effectiveness or potency concerns, including as a result of adverse events reported in patients or ongoing clinical trials, or failure to comply with cGMP. In addition to revocation or withdrawal of approvals, we and our partners may be subject to warnings, fines, recalls, criminal prosecution or other sanctions if we fail to comply with regulatory requirements. If we or our partners are unable to obtain or maintain regulatory approvals for our products and product candidates, our business, financial position, results of operations and future growth prospects will be negatively impacted and we or our partners may be subject to sanctions. If any of our product candidates prove to be ineffective, unsafe or commercially unviable, we may have to re-engineer our current or potential future product candidates, and our entire pipeline could have little, if any, value, which could require us to change our focus and approach to product candidate discovery and therapeutic development, which would have a material adverse effect on our business, financial condition, results of operations and prospects.
We will also be subject to numerous foreign regulatory requirements governing, among other things, the conduct of clinical trials, manufacturing and marketing authorization, pricing and third-party reimbursement. The foreign regulatory approval process varies among countries and may include all of the risks associated with FDA
62
approval described above as well as risks attributable to the satisfaction of local regulations in foreign jurisdictions. Moreover, the time required to obtain approval may differ from that required to obtain FDA approval.
Obtaining and maintaining regulatory approval of our product candidates in one jurisdiction does not mean that we will be successful in obtaining regulatory approval of our product candidates in other jurisdictions.
If we succeed in developing any products, we intend to market them in the United States as well as the European Union and other foreign jurisdictions. In order to market and sell our products in other jurisdictions, we must obtain separate marketing approvals and comply with numerous and varying regulatory requirements.
Obtaining and maintaining regulatory approval of our product candidates in one jurisdiction does not guarantee that we will be able to obtain or maintain regulatory approval in any other jurisdiction, but a failure or delay in obtaining regulatory approval in one jurisdiction may have a negative effect on the regulatory approval process in others. For example, even if the FDA or EMA grants marketing approval of a product candidate, comparable regulatory authorities in foreign jurisdictions must also approve the manufacturing, marketing and promotion of the product candidate in those countries. Approval procedures vary among jurisdictions and can involve requirements and administrative review periods different from those in the United States, including additional preclinical studies or clinical trials as clinical trials conducted in one jurisdiction may not be accepted by regulatory authorities in other jurisdictions. In many jurisdictions outside the United States, a product candidate must be approved for reimbursement before it can be approved for sale in that jurisdiction. In some cases, the price that we intend to charge for our products is also subject to approval.
Obtaining foreign regulatory approvals and compliance with foreign regulatory requirements could result in significant delays, difficulties and costs for us and could delay or prevent the introduction of our products in certain countries. If we or any partner we work with fail to comply with the regulatory requirements in international markets or fail to receive applicable marketing approvals, our target market will be reduced, and our ability to realize the full market potential of our product candidates will be harmed.
We may in the future conduct certain of our clinical trials for our product candidates outside of the United States. However, the FDA and other foreign equivalents may not accept data from such trials, in which case our development plans will be delayed, which could materially harm our business.
We may in the future choose to conduct one or more of our clinical trials for our product candidates outside the United States. Although the FDA may accept data from clinical trials conducted outside the United States, acceptance of this data is subject to certain conditions imposed by the FDA. In cases where data from foreign clinical trials are intended to serve as the basis for marketing approval in the United States, the FDA will not approve the application on the basis of foreign data alone unless (i) those data are applicable to the U.S. population and U.S. medical practice; (ii) the studies were performed by clinical investigators of recognized competence; and (iii) the data are considered valid without the need for an on-site inspection by the FDA or, if the FDA considers such an inspection to be necessary, the FDA is able to validate the data through an on-site inspection or other appropriate means. For studies that are conducted only at sites outside of the United States and not subject to an IND, the FDA requires the clinical trial to have been conducted in accordance with GCPs, and the FDA must be able to validate the data from the clinical trial through an on-site inspection if it deems such inspection necessary. For such studies not subject to an IND, the FDA generally does not provide advance comment on the clinical protocols for the studies, and therefore there is an additional potential risk that the FDA could determine that the study design or protocol for a non-U.S. clinical trial was inadequate, which could require us to conduct additional clinical trials. There can be no assurance the FDA will accept data from clinical trials conducted outside of the United States. If the FDA does not accept data from our clinical trials of our product candidates, it would likely result in the need for additional clinical trials, which would be costly and time consuming and delay or permanently halt our development of our product candidates.
63
Many foreign regulatory bodies have similar approval requirements. In addition, such foreign trials would be subject to the applicable local laws of the foreign jurisdictions where the trials are conducted. There can be no assurance that the FDA or any similar foreign regulatory authority will accept data from trials conducted outside of the United States or the applicable jurisdiction. If the FDA or any similar foreign regulatory authority does not accept such data, it would result in the need for additional trials, which would be costly and time-consuming and delay aspects of our business plan, and which may result in our product candidates not receiving approval or clearance for commercialization in the applicable jurisdiction.
Conducting clinical trials outside the United States also exposes us to additional risks, including risks associated with:
| • | additional foreign regulatory requirements; |
| • | foreign exchange fluctuations; |
| • | compliance with foreign manufacturing, customs, shipment and storage requirements; |
| • | cultural differences in medical practice and clinical research; and |
| • | diminished protection of intellectual property in some countries. |
Even if we receive regulatory approval for any of our current or potential future product candidates, we will be subject to ongoing regulatory obligations and continued regulatory review, which may result in significant additional expense. Additionally, our current or potential future product candidates, if approved, could be subject to labeling and other restrictions and market withdrawal and we may be subject to penalties if we fail to comply with regulatory requirements or experience unanticipated problems with our products.
Any regulatory approvals that we or potential future collaborators obtain for any of our current or potential future product candidates will be subject to limitations on the approved indicated uses for which a product may be marketed or may be subject to the conditions of approval, or contain requirements for potentially costly post-marketing testing, and surveillance to monitor the safety and efficacy of such product candidate. In addition, if the FDA or any other regulatory authority approves any of our current or potential future product candidates, the manufacturing processes, labeling, packaging, distribution, adverse event reporting, storage, import, export, advertising, promotion and recordkeeping for such product will be subject to extensive and ongoing regulatory requirements. These requirements include submissions of safety and other post-marketing information and reports, registration, as well as continued compliance with cGMP and good clinical practices for any clinical trials that we conduct post-approval. In addition, manufacturers and manufacturers’ facilities are required to comply with extensive FDA and comparable foreign regulatory authority requirements, including ensuring that quality control and manufacturing procedures conform to cGMP and cGTP regulations and applicable product tracking and tracing requirements.
Later discovery of previously unknown problems with a product candidate, including adverse events of unanticipated severity or frequency, or with our third-party manufacturers or manufacturing processes, or failure to comply with regulatory requirements, may result in, among other things:
| • | restrictions on the marketing or manufacturing of the product candidate, withdrawal of the product candidate from the market or voluntary or mandatory product recalls; |
| • | fines, warning letters, untitled letters or holds on clinical trials; |
| • | refusal by the FDA to approve pending applications or supplements to approved applications filed by us or our strategic collaborators; |
| • | suspension or revocation of product approvals; |
| • | suspension of any ongoing clinical trials; |
64
| • | product seizure or detention or refusal to permit the import or export of products; and |
| • | injunctions or the imposition of civil or criminal penalties or monetary fines. |
The occurrence of any event or penalty described above may inhibit our ability to commercialize our product candidates and generate revenue.
The FDA has the authority to require a risk evaluation and mitigation strategy (“REMS”) as part of a biologics license application (“BLA”) or after approval, which may impose further requirements or restrictions on the distribution or use of an approved product, such as limiting prescribing to certain physicians or medical centers that have undergone specialized training, limiting treatment to patients who meet certain safe-use criteria and requiring treated patients to enroll in a registry.
Furthermore, the FDA strictly regulates marketing, labeling, advertising and promotion of products that are placed on the market. Products may be promoted only for the approved indications and in accordance with the provisions of the approved label. While physicians may prescribe, in their independent professional medical judgment, products for off-label uses as the FDA does not regulate the behavior of physicians in their choice of drug treatments, the FDA does restrict a manufacturer’s communications on the subject of off-label use of their products. Companies may only share truthful and not misleading information that is otherwise consistent with a product’s FDA approved labeling. The FDA and other authorities actively enforce the laws and regulations prohibiting the promotion of off-label uses and a company that is found to have improperly promoted off-label uses may be subject to significant liability including, among other things, adverse publicity, warning letters, corrective advertising and potential civil and criminal penalties. The federal government has levied large civil and criminal fines against companies for alleged improper promotion of off-label use and has enjoined companies from engaging in off-label promotion. The FDA and other regulatory authorities have also required that companies enter into consent decrees or permanent injunctions under which specified promotional conduct is changed or curtailed.
Occurrence of any of the foregoing could have a material adverse effect on our business and results of operations. The FDA’s and other regulatory authorities’ policies may change, and additional government regulations may be enacted that could prevent, limit or delay regulatory approval of our product candidates. We cannot predict the likelihood, nature or extent of government regulation that may arise from future legislation or administrative action, either in the United States or abroad. If we are slow or unable to adapt to changes in existing requirements or the adoption of new requirements or policies, or if we are not able to maintain regulatory compliance, we may lose any marketing approval that we may have obtained and we may not achieve or sustain profitability, which would adversely affect our business.
Any product candidates for which we intend to seek approval as biologic products may face competition sooner than anticipated.
The Affordable Care Act includes a subtitle called the Biologics Price Competition and Innovation Act of 2009 (“BPCIA”) which created an abbreviated approval pathway for biological products that are biosimilar to or interchangeable with an FDA-licensed reference biological product. Under the BPCIA, an application for a biosimilar product may not be submitted to the FDA until four years following the date that the reference product was first licensed by the FDA. In addition, the approval of a biosimilar product may not be made effective by the FDA until twelve years from the date on which the reference product was first licensed. During this twelve-year period of exclusivity, another company may still market a competing version of the reference product if the FDA approves a full BLA for the competing product containing the sponsor’s own preclinical data and data from adequate and well-controlled clinical trials to demonstrate the safety, purity and potency of its product. The law is complex. The BPCIA could have a material adverse effect on the future commercial prospects for our biological products.
We believe that any of our future product candidates approved as a biological product under a BLA should qualify for the twelve-year period of exclusivity. However, there is a risk that this exclusivity could be shortened
65
due to Congressional action or otherwise, or that the FDA will not consider our product candidates to be reference products for competing products, potentially creating the opportunity for generic competition sooner than anticipated. Other aspects of the BPCIA, some of which may impact the BPCIA exclusivity provisions, have also been the subject of recent litigation. Moreover, the extent to which a biosimilar, once approved, could be substituted for any one of our reference products in a way that is similar to traditional generic substitution for non-biological products will depend on a number of marketplace and regulatory factors that are still developing.
Healthcare legislative reform measures may have a material adverse effect on our business and results of operations.
In the United States, there have been and continue to be a number of legislative initiatives to contain healthcare costs. For example, in March 2010, the Patient Protection and Affordable Care Act (the “ACA”) was enacted, which substantially changed the way healthcare is financed by both governmental and private insurers, and significantly impacted the U.S. pharmaceutical industry. Among the provisions of the ACA, of greatest importance to the pharmaceutical and biotechnology industry are the following:
| • | an annual, nondeductible fee on any entity that manufactures or imports certain specified branded prescription drugs and biologic agents apportioned among these entities according to their market share in some government healthcare programs; |
| • | an increase in the statutory minimum rebates a manufacturer must pay under the Medicaid Drug Rebate Program to 23.1% and 13% of the average manufacturer price for most branded and generic drugs, respectively, and a cap on the total rebate amount for innovator drugs at 100% of the Average Manufacturer Price; |
| • | a new methodology by which rebates owed by manufacturers under the Medicaid Drug Rebate Program are calculated for certain drugs and biologics that are inhaled, infused, instilled, implanted or injected; |
| • | extension of manufacturers’ Medicaid rebate liability to covered drugs dispensed to individuals who are enrolled in Medicaid managed care organizations; |
| • | expansion of eligibility criteria for Medicaid programs by, among other things, allowing states to offer Medicaid coverage to additional individuals and by adding new mandatory eligibility categories for individuals with income at or below 133% of the federal poverty level, thereby potentially increasing manufacturers’ Medicaid rebate liability; |
| • | a new Medicare Part D coverage gap discount program, in which manufacturers must agree to offer 50% (and 70% as of January 1, 2019) point-of-sale discounts off negotiated prices of applicable brand drugs to eligible beneficiaries during their coverage gap period, as a condition for the manufacturer’s outpatient drugs to be covered under Medicare Part D; |
| • | expansion of the entities eligible for discounts under the Public Health program; |
| • | a new Patient-Centered Outcomes Research Institute to oversee, identify priorities in, and conduct comparative clinical effectiveness research, along with funding for such research; |
| • | establishment of a Center for Medicare Innovation at the Centers for Medicare & Medicaid Services (“CMS”) to test innovative payment and service delivery models to lower Medicare and Medicaid spending; and |
| • | implementation of the federal physician payment transparency requirements, sometimes referred to as the “Physician Payments Sunshine Act.” |
Since its enactment, there have been judicial, Congressional and executive challenges to certain aspects of the ACA. On June 17, 2021, the U.S. Supreme Court dismissed the most recent judicial challenge to the ACA
66
brought by several states without specifically ruling on the constitutionality of the ACA. Prior to the Supreme Court’s decision, President Biden issued an executive order to initiate a special enrollment period from February 15, 2021 through August 15, 2021 for purposes of obtaining health insurance coverage through the ACA marketplace. The executive order also instructed certain governmental agencies to review and reconsider their existing policies and rules that limit access to healthcare, including among others, reexamining Medicaid demonstration projects and waiver programs that include work requirements, and policies that create unnecessary barriers to obtaining access to health insurance coverage through Medicaid or the ACA. It is unclear how other healthcare reform measures of the Biden administration or other efforts, if any, to challenge, repeal or replace the ACA will impact our business. In addition, other legislative changes have been proposed and adopted in the United States since the ACA was enacted.
| • | On August 2, 2011, the Budget Control Act of 2011 among other things, included aggregate reductions of Medicare payments to providers of 2% per fiscal year. These reductions went into effect on April 1, 2013 and will remain in effect through 2030. |
| • | On January 2, 2013, the American Taxpayer Relief Act of 2012 among other things, reduced Medicare payments to several providers, including hospitals and increased the statute of limitations period for the government to recover overpayments to providers from three to five years. |
| • | On April 13, 2017, CMS published a final rule that gives states greater flexibility in setting benchmarks for insurers in the individual and small group marketplaces, which may have the effect of relaxing the essential health benefits required under the ACA for plans sold through such marketplaces. |
| • | On May 30, 2018, the Right to Try Act was signed into law. The law, among other things, provides a federal framework for certain patients to access certain investigational new drug products that have completed a Phase 1 clinical trial and that are undergoing investigation for FDA approval. Under certain circumstances, eligible patients can seek treatment without enrolling in clinical trials and without obtaining FDA permission under the FDA expanded access program. There is no obligation for a pharmaceutical manufacturer to make its drug products available to eligible patients as a result of the Right to Try Act. |
| • | On May 23, 2019, CMS published a final rule to allow Medicare Advantage Plans the option of using step therapy for Part B drugs beginning January 1, 2020. |
| • | On December 20, 2019, former President Trump signed into law the Further Consolidated Appropriations Act (H.R. 1865), which repealed the Cadillac tax, the health insurance provider tax, and the medical device excise tax. It is impossible to determine whether similar taxes could be instated in the future. |
Additionally, there has been heightened governmental scrutiny recently over the manner in which manufacturers set prices for their marketed products. For example, there have been several recent Congressional inquiries and proposed and enacted federal and state legislation designed to, among other things, bring more transparency to drug pricing, review the relationship between pricing and manufacturer patient programs, and reform government program reimbursement methodologies for drug products.
At the state level, individual states are increasingly aggressive in passing legislation and implementing regulations designed to control pharmaceutical and biological product pricing, including price or patient reimbursement constraints, discounts, restrictions on certain product access and marketing cost disclosure and transparency measures, and, in some cases, designed to encourage importation from other countries and bulk purchasing. In addition, regional health care authorities and individual hospitals are increasingly using bidding procedures to determine what pharmaceutical products and which suppliers will be included in their prescription drug and other health care programs. These measures could reduce the ultimate demand for our products, once approved, or put pressure on our product pricing, which could negatively affect our business, financial conditions, results of operation and prospects.
67
We expect that additional state and federal healthcare reform measures will be adopted in the future, any of which could limit the amounts that federal and state governments will pay for healthcare products and services, which could result in reduced demand for our current or future product candidates or additional pricing pressures. Further, it is possible that additional governmental action is taken in response to the COVID-19 pandemic. Any denial in coverage or reduction in reimbursement from Medicare or other government-funded programs may result in a similar denial or reduction in payments from private payors, which may prevent us from being able to generate sufficient revenue, attain profitability or commercialize our products. It is not clear how other future potential changes to the ACA will change the reimbursement model and market outlook for our current and future product candidates.
Failure to comply with health and data protection laws and regulations could lead to government enforcement actions (which could include civil or criminal penalties), private litigation or adverse publicity and could negatively affect our operating results and business.
We may collect, receive, store, process, generate, use, transfer, disclose, make accessible, protect and share personal information, health information and other sensitive information to develop our products, to operate our business, for clinical trial purposes, for legal and marketing purposes, and for other business-related purposes.
We and any potential future collaborators, partners or service providers may be subject to federal, state and foreign data protection laws, regulations and regulatory guidance, the number and scope of which is changing, subject to differing applications and interpretations, and which may be inconsistent among jurisdictions, or in conflict with other rules, laws or contractual obligations. In the United States, numerous federal and state laws and regulations, including federal health information privacy laws, such as the Health Insurance Portability and Accountability Act (“HIPAA”), state data breach notification laws, state health information privacy laws and federal and state consumer protection laws, that govern the collection, use, disclosure and protection of health-related and other personal information could apply to our operations or the operations of any future potential collaborators or service providers. In addition, we may obtain health information from third parties (including research institutions from which we obtain clinical trial data) that are subject to privacy and security requirements under HIPAA, or other privacy and data security laws. Depending on the facts and circumstances, we could be subject to civil or criminal penalties if we obtain, use, or disclose individually identifiable health information maintained by a HIPAA-covered entity in a manner that is not authorized or permitted by HIPAA, or if we otherwise violate applicable privacy and data security laws.
International data protection laws, including the EU’s General Data Protection Regulation (“GDPR”), may also apply to health-related and other personal information obtained outside of the United States. The GDPR went into effect on May 25, 2018, and imposes stringent data protection requirements for processing of personal data of individuals within the European Economic Area (“EEA”) as well as potential fines for noncompliant companies of up to the greater of €20 million or 4% of annual global revenue. The GDPR imposes numerous requirements for the collection, use and disclosure of personal data, including stringent requirements relating to consent and the information that must be shared with data subjects about how their personal information is used, the obligation to notify regulators and affected individuals of personal data breaches, extensive internal privacy governance obligations and obligations to honor expanded rights of individuals in relation to their personal information.
In addition, the GDPR places restrictions on cross-border data transfers. A decision by the Court of Justice of the European Union (“CJEU”) in 2020 invalidated the EU-U.S. Privacy Shield Framework, which was one of the primary mechanisms used by U.S. companies to import personal information from Europe in compliance with the GDPR’s cross-border data transfer restrictions, and raised questions about whether the European Commission’s Standard Contractual Clauses, one of the primary alternatives to the Privacy Shield, can lawfully be used for personal information transfers from Europe to the United States or most other countries. Similarly, the Swiss Federal Data Protection and Information Commissioner has opined that the Swiss-U.S. Privacy Shield is inadequate for transfers of data from Switzerland to the U.S. Furthermore, on June 4, 2021, the European
68
Commission issued new forms of standard contractual clauses for data transfers from controllers or processors in the EEA (or otherwise subject to the GDPR) to controllers or processors established outside the EEA (and not subject to the GDPR). The new forms of standard contractual clauses have replaced the standard contractual clauses that were adopted previously under the Data Protection Directive. We will be required to transition to the new forms of standard contractual clauses and doing so will require significant effort and cost. The new standard contractual clauses may also impact our business as companies based in Europe may be reluctant to utilize the new clauses to legitimize transfers of personal information to third countries given the burdensome requirements of transfer impact assessments and the substantial obligations that the new standard contractual clauses impose upon exporters. If we are investigated by a European data protection authority, we may face fines and other penalties. Any such investigation or charges by European data protection authorities could have a negative effect on our existing business and on our ability to attract and retain new clients or pharmaceutical partners. We may also experience hesitancy, reluctance, or refusal by European or multi-national clients or pharmaceutical partners to continue to use our products due to the potential risk exposure as a result of the current (and, in particular, future) data protection obligations imposed on them by certain data protection authorities in interpretation of current law, including the GDPR. Such clients or pharmaceutical partners may also view any alternative approaches to compliance as being too costly, too burdensome, too legally uncertain, or otherwise objectionable and therefore decide not to do business with us. Any of the foregoing could materially harm our business, prospects, financial condition, and results of operations.
The GDPR has increased our responsibilities and potential liability in relation to personal data processed subject to the GDPR, and we may be required to put in place additional mechanisms to ensure compliance with the GDPR, including as implemented by individual countries. Companies now have to comply with the GDPR and also the United Kingdom GDPR (“UK GDPR”), which, together with the amended UK Data Protection Act 2018, retains the GDPR in UK national law. The UK GDPR mirrors the fines under the GDPR, i.e., fines up to the greater of €20 million (£17.5 million) or 4% of global turnover. In addition, on June 28, 2021, the European Commission adopted an adequacy decision in respect of transfers of personal data to the UK for a four-year period (until June 27, 2025). Similarly, the UK has determined that it considers all of the EEA to be adequate for the purposes of data protection. This ensures that data flows between the UK and the EEA remain unaffected. Compliance with the GDPR and applicable laws and regulations relating to privacy and data protection of EEA Member States and the UK is a rigorous and time-intensive process that may increase our cost of doing business or require us to change our business practices, and despite those efforts, there is a risk that we may be subject to fines and penalties, litigation and reputational harm in connection with our European activities. In addition, any failure by us (or our business partners who handle personal data) to comply with GDPR and applicable laws and regulations relating to privacy and data protection of EEA member states and the UK may result in regulators prohibiting our processing of the personal data of EEA data subjects, which could impact our operations and ability to develop our products and provide our services, including interrupting or ending EEA clinical trials.
In addition, states are constantly adopting new laws or amending existing laws, requiring attention to frequently changing regulatory requirements. For example, California enacted the California Consumer Privacy Act (the “CCPA”) on June 28, 2018, which took effect on January 1, 2020. The CCPA gives California residents expanded rights to access and delete their personal information, opt out of certain personal information sharing and receive detailed information about how their personal information is used by requiring covered companies to provide new disclosures to California consumers (as that term is broadly defined and can include any of our current or future employees who may be California residents) and provide such residents new ways to opt-out of certain sales of personal information. The CCPA provides for civil penalties for violations, as well as a private right of action for data breaches and statutory damages, which is expected to increase data breach class action litigation and result in significant exposure to costly legal judgments and settlements. Although the law includes limited exceptions for health-related information, including clinical trial data, such exceptions may not apply to all of our operations and processing activities. As we expand our operations and trials (both preclinical and clinical), the CCPA may increase our compliance costs and potential liability. Some observers have noted that the CCPA could mark the beginning of a trend toward more stringent privacy legislation in the United States. In November 2020, California passed the California Privacy Rights Act (the “CPRA”) which amends and expands
69
the CCPA. The CPRA will impose additional data protection obligations on covered businesses, including additional consumer rights processes, limitations on data uses, new audit requirements for higher risk data, and opt outs for certain uses of sensitive data. It will also create a new California data protection agency authorized to issue substantive regulations and could result in increased privacy and information security enforcement. The majority of the provisions will go into effect on January 1, 2023, and additional compliance investment and potential business process changes may be required. The CPRA has created additional uncertainty and may increase our cost of compliance. Other states are beginning to pass similar laws. In the event that we are subject to or affected by HIPAA, the GDPR, the CCPA, the CPRA or other domestic privacy and data protection laws, any liability from failure to comply with the requirements of these laws could adversely affect our financial condition.
Compliance with U.S. and international data protection laws and regulations could require us to take on more onerous obligations in our contracts, restrict our ability to collect, use and disclose data, or in some cases, impact our ability to operate in certain jurisdictions. Laws and regulations worldwide relating to privacy, data protection and cybersecurity are, and are likely to remain, uncertain for the foreseeable future. While we strive to comply with applicable laws and regulations relating to privacy, data protection and cybersecurity, external and internal privacy and security policies and contractual obligations relating to privacy, data protection and cybersecurity to the extent possible, we may at times fail to do so, or may be perceived to have failed to do so. Moreover, despite our efforts, we may not be successful in achieving compliance if our personnel, collaborators, partners or vendors do not comply with applicable laws and regulations relating to privacy, data protection and cybersecurity, external and internal privacy and security policies and contractual obligations relating to privacy, data protection and cybersecurity. Actual or perceived failure to comply with any laws and regulations relating to privacy, data protection or cybersecurity in the U.S. or foreign jurisdictions could result in government enforcement actions (which could include civil or criminal penalties), private litigation or adverse publicity and could negatively affect our operating results and business. Moreover, clinical trial subjects about whom we or our potential collaborators or service providers obtain information, as well as the providers who share this information with us, may contractually limit our ability to use and disclose the information. Claims that we have violated individuals’ privacy rights, failed to comply with applicable laws or regulations, or breached our contractual obligations, even if we are not found liable, could be expensive and time consuming to defend, result in regulatory actions and proceedings, in addition to private claims and litigation, and could result in adverse publicity that could harm our business.
We also are, or may be asserted to be, subject to the terms of our external and internal privacy and security policies, representations, certifications, publications and frameworks and contractual obligations to third parties related to privacy, data protection, information security and processing. Failure to comply or the perceived failure to comply with any of these, or if any of these policies or any of our representations, certifications, publications or frameworks are, in whole or part, found or perceived to be inaccurate, incomplete, deceptive, unfair or misrepresentative of our actual practices, could result in reputational harm, result in litigation, cause a material adverse impact to business operations or financial results and otherwise result in other material harm to our business.
If we or our existing or potential future collaborators, manufacturers or service providers fail to comply with healthcare laws and regulations, we or they could be subject to enforcement actions, which could affect our ability to develop, market and sell our product candidates and may harm our reputation.
Healthcare providers, physicians and third-party payors, among others, will play a primary role in the prescription and recommendation of any product candidates for which we obtain marketing approval. Our current and future arrangements with third-party payors, providers and customers, among others, may expose us to broadly applicable fraud and abuse and other healthcare laws and regulations that may constrain the business or financial arrangements and relationships through which we market, sell and distribute our product candidates for
70
which we obtain marketing approval. Restrictions under applicable federal and state healthcare laws and regulations in the United States and other countries, include the following:
| • | the federal Anti-Kickback Statute, which prohibits, among other things, a person or entity from knowingly and willfully soliciting, offering, paying, receiving or providing remuneration, directly or indirectly, in cash or in kind, to induce or reward either the referral of an individual for, or the purchase, lease order, arranging for or recommendation of, any good, facility, item or service, for which payment may be made, in whole or in part, by a federal healthcare program, such as Medicare or Medicaid. A person or entity does not need to have actual knowledge of the statute or specific intent to violate it in order to have committed a violation; |
| • | federal civil and criminal false claims laws, including the federal False Claims Act, which provides for civil whistleblower or qui tam actions, and civil monetary penalties laws, that impose penalties against individuals or entities for knowingly presenting, or causing to be presented, to the federal government, claims for payment that are false or fraudulent or making a false statement to avoid, decrease or conceal an obligation to pay money to the federal government. In addition, the government may assert that a claim including items and services resulting from a referral made in violation of the federal Anti-Kickback Statute constitutes a false or fraudulent claim for purposes of the False Claims Act; |
| • | HIPAA, which imposes criminal and civil liability for executing a scheme to defraud any healthcare benefit program, or knowingly and willfully falsifying, concealing or covering up a material fact or making any materially false statement in connection with the delivery of or payment for healthcare benefits, items or services. Similar to the federal Anti-Kickback Statute, a person or entity does not need to have actual knowledge of the statute or specific intent to violate it in order to have committed a violation; |
| • | HIPAA, as amended by the Health Information Technology for Economic and Clinical Health Act (“HITECH”) and its implementing regulations, including the Final Omnibus Rule published in January 2013, which impose obligations on certain covered entity healthcare providers, health plans and healthcare clearinghouses as well as their business associates and their subcontractors that perform certain services involving the use or disclosure of individually identifiable health information, including mandatory contractual terms, with respect to safeguarding the privacy, security and transmission of individually identifiable health information, and require notification to affected individuals and regulatory authorities of certain breaches of security of individually identifiable health information. HITECH also created new tiers of civil monetary penalties, amended HIPAA to make civil and criminal penalties directly applicable to business associates, and gave state attorneys general new authority to file civil actions for damages or injunctions in federal courts to enforce the federal HIPAA laws and seek attorneys’ fees and costs associated with pursuing federal civil actions. In addition, there may be additional federal, state, and non-U.S. laws which govern the privacy and security of health and other personal information in certain circumstances, many of which differ from each other in significant ways and may not have the same effect, thus complicating compliance efforts; |
| • | the federal false statements statute, which prohibits knowingly and willfully falsifying, concealing or covering up a material fact or making any materially false statement in connection with the delivery of or payment for healthcare benefits, items or services; |
| • | the federal physician payment transparency requirements, sometimes referred to as the “Sunshine Act” under the Affordable Care Act, require certain manufacturers of drugs, devices, biologics and medical supplies that are reimbursable under Medicare, Medicaid, or the Children’s Health Insurance Program to report to the CMS information related to transfers of value made to physicians (currently defined to include doctors, dentists, optometrists, podiatrists and chiropractors) and teaching hospitals, as well as ownership and investment interests of such physicians and their immediate family members. Effective January 1, 2022, these reporting obligations extend to include payments and transfers of value, made during the previous year to certain non-physician providers, including physician assistants, nurse |
71
practitioners, clinical nurse specialists, certified registered nurse anesthetists, anesthesiologist assistants and certified nurse midwives; and |
| • | analogous local, state and foreign laws and regulations, such as state anti-kickback and false claims laws that may apply to healthcare items or services reimbursed by third party payors, including private insurers, local, state and foreign transparency laws that require manufacturers to report information related to payments and transfers of value to other healthcare providers and healthcare entities, marketing expenditures, or drug pricing, state laws that require pharmaceutical companies to register certain employees engaged in marketing activities in the location and comply with the pharmaceutical industry’s voluntary compliance guidelines and the relevant compliance guidance promulgated by the federal government, and state and foreign laws governing the privacy and security of health information in certain circumstances, many of which differ from each other in significant ways and often are not preempted by HIPAA, thus complicating compliance efforts. |
Ensuring that our future business arrangements with third parties comply with applicable healthcare laws and regulations could involve substantial costs. It is possible that governmental authorities will conclude that our business practices, including our relationships with physicians and other healthcare providers, some of whom are compensated in the form of stock options for consulting services provided, may not comply with current or future statutes, regulations, agency guidance or case law involving applicable fraud and abuse or other healthcare laws and regulations. If our operations are found to be in violation of any such requirements, we may be subject to penalties, including criminal and significant civil monetary penalties, damages, fines, imprisonment, disgorgement, contractual damages, reputational harm, exclusion from participation in government healthcare programs, integrity obligations, injunctions, recall or seizure of products, total or partial suspension of production, denial or withdrawal of pre-marketing product approvals, private qui tam actions brought by individual whistleblowers in the name of the government, refusal to allow us to enter into supply contracts, including government contracts, additional reporting requirements and oversight if subject to a corporate integrity agreement or similar agreement to resolve allegations of non-compliance with these laws, and the curtailment or restructuring of our operations, any of which could adversely affect our ability to operate our business and our results of operations. Although effective compliance programs can mitigate the risk of investigation and prosecution for violations of these laws, these risks cannot be entirely eliminated. Any action against us for an alleged or suspected violation could cause us to incur significant legal expenses and could divert our management’s attention from the operation of our business, even if our defense is successful. Therefore, even if we are successful in defending against any such actions that may be brought against us, our business may be impaired. If any of the above occur, our ability to operate our business and our results of operations could be adversely affected. In addition, achieving and sustaining compliance with applicable laws and regulations may be costly to us in terms of money, time and resources.
If we fail to comply with U.S. and foreign regulatory requirements, regulatory authorities could limit or withdraw any marketing or commercialization approvals we may receive and subject us to other penalties that could materially harm our business.
Even if we receive marketing and commercialization approval of a product candidate, we will be subject to continuing regulatory requirements, including in relation to adverse patient experiences with the product and clinical results that are reported after a product is made commercially available, both in the United States and any foreign jurisdiction in which we seek regulatory approval. The FDA and other regulatory authorities have significant post- market authority, including the authority to require labeling changes based on new safety information and to require post-market studies or clinical trials to evaluate safety risks related to the use of a product or to require withdrawal of the product candidate from the market. The FDA and other regulatory authorities also have the authority to require a REMS after approval, which may impose further requirements or restrictions on the distribution or use of an approved drug or therapeutic biologic. The manufacturer and manufacturing facilities we use to make a future product, if any, will also be subject to periodic review and inspection by the FDA and other regulatory authorities, including for continued compliance with cGMP and
72
cGTP requirements. The discovery of any new or previously unknown problems with our third-party manufacturers, manufacturing processes or facilities may result in restrictions on the product candidate, manufacturer or facility, including withdrawal of the product candidate from the market. We intend to rely on third-party manufacturers and we will not have control over compliance with applicable rules and regulations by such manufacturers. Any product promotion and advertising will also be subject to regulatory requirements and continuing regulatory review. If we or our existing or future collaborators, manufacturers or service providers fail to comply with applicable continuing regulatory requirements in the U.S. or foreign jurisdictions in which we seek to market our products, we or they may be subject to, among other things, fines, warning letters, holds on clinical trials, delay of approval or refusal by the FDA or other regulatory authorities to approve pending applications or supplements to approved applications, suspension or withdrawal of regulatory approval, product recalls and seizures, administrative detention of products, refusal to permit the import or export of products, operating restrictions, injunction, civil penalties and criminal prosecution.
Even if we are able to commercialize any product candidate, such product candidate may become subject to unfavorable pricing regulations or third-party coverage and reimbursement policies, which would harm our business.
In the United States and markets in other countries, patients generally rely on third-party payors to reimburse all or part of the costs associated with their treatment. Adequate coverage and reimbursement from governmental healthcare programs, such as Medicare and Medicaid, and commercial payors is critical to new product acceptance. Further, due to the COVID-19 pandemic, millions of individuals have lost/will be losing employer-based insurance coverage, which may adversely affect our ability to commercialize our products. It is unclear what effect, if any, the American Rescue Plan will have on the number of covered individuals.
There is also significant uncertainty related to the insurance coverage and reimbursement of newly approved products and coverage may be more limited than the purposes for which the medicine is approved by the FDA or comparable foreign regulatory authorities. In the United States, the principal decisions about reimbursement for new medicines are typically made by the CMS, an agency within the U.S. Department of Health and Human Services. CMS decides whether and to what extent a new medicine will be covered and reimbursed under Medicare and private payors tend to follow CMS to a substantial degree.
Our ability to commercialize any products successfully will depend, in part, on the extent to which coverage and adequate reimbursement for these products and related treatments will be available from third-party payors, such as government authorities, private health insurers and health maintenance organizations. Patients who are prescribed medications for the treatment of their conditions generally rely on third-party payors to reimburse all or part of the costs associated with their prescription drugs. Coverage and adequate reimbursement from government healthcare programs, such as Medicare and Medicaid, and private health insurers are critical to new product acceptance. Patients are unlikely to use our future products, if any, unless coverage is provided and reimbursement is adequate to cover a significant portion of the cost. Obtaining coverage and adequate reimbursement for our product candidates may be particularly difficult because of the higher prices often associated with drugs administered under the supervision of a physician. Similarly, because our product candidates are physician-administered, separate reimbursement for the product itself may or may not be available. Instead, the administering physician may or may not be reimbursed for providing the treatment or procedure in which our product is used.
Cost-containment is a priority in the U.S. healthcare industry and elsewhere. As a result, government authorities and other third-party payors have attempted to control costs by limiting coverage and the amount of reimbursement for particular medications. Increasingly, third-party payors are requiring that drug companies provide them with predetermined discounts from list prices and are challenging the prices charged for medical products. Third-party payors also may request additional clinical evidence beyond the data required to obtain marketing approval, requiring a company to conduct expensive pharmacoeconomic studies in order to demonstrate the medical necessity and cost-effectiveness of its product. Commercial third-party payors often rely
73
upon Medicare coverage policy and payment limitations in setting their reimbursement rates, but also have their own methods and approval process apart from Medicare determinations. Therefore, coverage and reimbursement for pharmaceutical products in the U.S. can differ significantly from payor to payor. We cannot be sure that coverage and adequate reimbursement will be available for any product that we commercialize and, if reimbursement is available, that the level of reimbursement will be adequate. Coverage and reimbursement may impact the demand for, or the price of, any product candidate for which we obtain marketing approval. If coverage and reimbursement are not available or are available only at limited levels, we may not be able to successfully commercialize any product candidate for which we obtain marketing approval.
Additionally, the regulations that govern regulatory approvals, pricing and reimbursement for new drugs and therapeutic biologics vary widely from country to country. Some countries require approval of the sale price of a drug or therapeutic biologic before it can be marketed. In many countries, the pricing review period begins after marketing approval is granted. In some foreign markets, prescription pharmaceutical pricing remains subject to continuing governmental control even after initial approval is granted. As a result, we might obtain regulatory approval for a product in a particular country, but then be subject to price regulations that delay our commercial launch of the product, possibly for lengthy time periods, and negatively impact the revenues we are able to generate from the sale of the product in that country. Adverse pricing limitations may hinder our ability to recoup our investment in one or more product candidates, even if our product candidates obtain regulatory approval.
We are subject to U.S. and foreign anti-corruption and anti-money laundering laws with respect to our operations and non-compliance with such laws can subject us to criminal or civil liability and harm our business.
We are subject to the U.S. Foreign Corrupt Practices Act of 1977, as amended (the “FCPA”), the U.S. domestic bribery statute contained in 18 U.S.C. § 201, the U.S. Travel Act, the USA PATRIOT Act, and possibly other state and national anti-bribery and anti-money laundering laws in countries in which we conduct activities. Anti-corruption laws are interpreted broadly and prohibit companies and their employees, agents, third-party intermediaries, joint venture partners and collaborators from authorizing, promising, offering or providing, directly or indirectly, improper payments or benefits to recipients in the public or private sector. We interact with officials and employees of government agencies and government-affiliated hospitals, universities and other organizations. In addition, we may engage third-party intermediaries to promote our clinical research activities abroad or to obtain necessary permits, licenses and other regulatory approvals. We can be held liable for the corrupt or other illegal activities of these third-party intermediaries, our employees, representatives, contractors, collaborators and agents, even if we do not explicitly authorize or have actual knowledge of such activities.
We adopted a Code of Business Conduct and Ethics and we expect to prepare and implement policies and procedures to ensure compliance with such code. The Code of Business Conduct and Ethics mandates compliance with the FCPA and other anti-corruption laws applicable to our business throughout the world. However, we cannot assure you that our employees and third-party intermediaries will comply with this code or such anti-corruption laws. Noncompliance with anti-corruption and anti-money laundering laws could subject us to whistleblower complaints, investigations, sanctions, settlements, prosecution, other enforcement actions, disgorgement of profits, significant fines, damages, other civil and criminal penalties or injunctions, suspension or debarment from contracting with certain persons, the loss of export privileges, reputational harm, adverse media coverage and other collateral consequences. If any subpoenas, investigations or other enforcement actions are launched, or governmental or other sanctions are imposed, or if we do not prevail in any possible civil or criminal litigation, our business, results of operations and financial condition could be materially harmed. In addition, responding to any action will likely result in a materially significant diversion of management’s attention and resources and significant defense and compliance costs and other professional fees. In certain cases, enforcement authorities may even cause us to appoint an independent compliance monitor which can result in added costs and administrative burdens.
74
Risks Related to Senti and the Senti Common Shares
The Senti stock price may be volatile.
The Senti stock price is likely to be volatile. The market price for Senti Common Shares may be influenced by many factors, including the other risks described in this section of the prospectus entitled “Risk Factors” and the following:
| • | our ability to advance our current or potential future product candidates into the clinic; |
| • | results of preclinical studies for our current or potential future product candidates, or those of our competitors or potential future collaborators; |
| • | the impact of the ongoing COVID-19 pandemic on our business; |
| • | regulatory or legal developments in the United States and other countries, especially changes in laws or regulations applicable to our future products; |
| • | our ability to successfully construct and operate our planned cGMP and cGTP facility; |
| • | the success of competitive products or technologies; |
| • | introductions and announcements of new products by us, our future commercialization collaborators, or our competitors, and the timing of these introductions or announcements; |
| • | actions taken by regulatory authorities with respect to our future products, clinical trials, manufacturing process or sales and marketing terms; |
| • | actual or anticipated variations in our financial results or those of companies that are perceived to be similar to us; |
| • | the success of our efforts to acquire or in-license additional technologies, products or product candidates; |
| • | developments concerning any future collaborations, including, but not limited to, those with any sources of manufacturing supply and future commercialization collaborators; |
| • | market conditions in the pharmaceutical and biotechnology sectors; |
| • | market conditions and sentiment involving companies that have recently completed a business combination with a special purpose acquisition company (“SPAC”); |
| • | announcements by us or our competitors of significant acquisitions, strategic alliances, joint ventures or capital commitments; |
| • | developments or disputes concerning patents or other proprietary rights, including patents, litigation matters and our ability to obtain patent protection for our products; |
| • | our ability or inability to raise additional capital and the terms on which it is raised; |
| • | the recruitment or departure of key personnel; |
| • | changes in the structure of healthcare payment systems; |
| • | actual or anticipated changes in earnings estimates or changes in stock market analyst recommendations regarding Senti Common Shares, other comparable companies or the industry generally; |
| • | our failure or the failure of our competitors to meet analysts’ projections or guidance that we or our competitors may give to the market; |
| • | fluctuations in the valuation of companies perceived by investors to be comparable to us; |
| • | announcement and expectation of additional financing efforts; |
75
| • | speculation in the press or investment community; |
| • | trading volume of Senti Common Shares; |
| • | sales of Senti Common Shares by us or our stockholders; |
| • | the concentrated ownership of Senti Common Shares; |
| • | changes in accounting principles; |
| • | terrorist acts, acts of war or periods of widespread civil unrest; |
| • | natural disasters, public health crises and other calamities; and |
| • | general economic, industry and market conditions. |
In addition, the stock markets in general, and the markets for SPAC post-business combination businesses, pharmaceutical, biopharmaceutical and biotechnology stocks in particular, have experienced extreme volatility, including since the public announcement of the Business Combination Agreement in December 2021. This volatility can often be unrelated to the operating performance of the underlying business. These broad market and industry factors may seriously harm the market price of Senti Common Shares, regardless of our operating performance.
We may incur significant costs from class action litigation due to the expected stock volatility.
Our stock price may fluctuate for many reasons, including as a result of public announcements regarding the progress of development efforts for our platform and product candidates, the development efforts of future collaborators or competitors, the addition or departure of key personnel, variations in quarterly operating results and changes in market valuations of biopharmaceutical and biotechnology companies. This risk is especially relevant to us because biopharmaceutical and biotechnology companies have experienced significant stock price volatility in recent years, including since the public announcement of the Business Combination Agreement in December 2021. In addition, recently there has been significant stock price volatility involving the shares of companies that have recently completed a business combination with a SPAC. When the market price of a stock has been volatile as our stock price may be, holders of that stock have occasionally brought securities class action litigation against the company that issued the stock. Additionally, there has recently been a general increase in litigation against companies that have recently completed a business combination with a SPAC alleging fraud and other claims based on inaccurate or misleading disclosures. If any of our stockholders were to bring a lawsuit of this type against us, even if the lawsuit is without merit, we could incur substantial costs defending the lawsuit. The lawsuit could also divert the time and attention of management.
We are an “emerging growth company” and it cannot be certain if the reduced disclosure requirements applicable to emerging growth companies will make the Senti Common Shares less attractive to investors and may make it more difficult to compare performance with other public companies.
We are an emerging growth company as defined in the JOBS Act, and we intend to continue to take advantage of certain exemptions from various reporting requirements that are applicable to other public companies that are not emerging growth companies, including not being required to comply with the auditor attestation requirements of Section 404 of the Sarbanes-Oxley Act, reduced disclosure obligations regarding executive compensation in periodic reports and proxy statements, and exemptions from the requirements of holding a nonbinding advisory vote on executive compensation and stockholder approval of any golden parachute payments not previously approved. Investors may find the Senti Common Shares less attractive because we will continue to rely on these exemptions. If some investors find the Senti Common Shares less attractive as a result, there may be a less active trading market for their common stock, and the stock price may be more volatile.
An emerging growth company may elect to delay the adoption of new or revised accounting standards. With DYNS making this election, Section 102(b)(2) of the JOBS Act allows us to delay adoption of new or revised
76
accounting standards until those standards apply to non-public business entities. As a result, the financial statements contained in this prospectus and those that we will file in the future may not be comparable to companies that comply with public business entities revised accounting standards effective dates.
If certain holders of our common stock sell a significant portion of their securities, it may negatively impact the market price of the shares of our common stock and such holders still may receive significant proceeds.
As of the date of this prospectus, the market price of our common stock is below $10.00 per share, which was the price per share of Class A Common Stock sold in the initial public offering of our predecessor, DYNS, the per share price of the 5,060,000 Senti Common Shares sold to certain investors in connection with our PIPE financing and also the per share value of the consideration issued to former stockholders of Senti Sub I, Inc. (formerly Senti Biosciences, Inc.) upon consummation of our Business Combination. However, certain of our stockholders who hold shares of our common stock that were (i) originally purchased by our predecessor’s sponsor, Dynamics Sponsor LLC, in a private placement prior to our predecessor’s initial public offering (the “Founder Shares”) or (ii) issued to the Anchor Investors in consideration for their agreement not to redeem their shares of Class A Common Stock of DYNS in connection with the Business Combination. In particular, 4,878,972 of the currently outstanding Founder Shares registered for resale in this prospectus were purchased at an effective price of $0.004 per share, and 871,028 of the currently outstanding Senti Common Shares held by the Anchor Investors and registered for resale in this prospectus were issued solely in consideration for the Anchor Investors’ agreement not to redeem their shares of Class A Common Stock as described above. Accordingly, holders of these 5,750,000 Senti Common Shares could sell their securities at a per share price that is less than $10.00 and still realize a significant return from the sale of those securities that could not be realized by our other stockholders. On July 28, 2022, the closing price of our common stock as reported on the Nasdaq Global Market was $1.86 per share. Based on this closing price, the aggregate sales price of the Founder Shares would be approximately $9.07 million and the aggregate sales price of the Senti Common Shares held by the Anchor Investors would be approximately $1.62 million.
Future sales and issuances of our common stock or rights to purchase common stock could result in additional dilution of the percentage ownership of our stockholders and could cause our stock price to fall.
Significant additional capital will be needed in the future to continue our planned operations, including further development of our gene circuit platform, preparing IND or equivalent filings, conducting preclinical studies and clinical trials, commercialization efforts, expanded research and development activities and costs associated with operating a public company. To raise capital, we may sell common stock, convertible securities or other equity securities in one or more transactions at prices and in a manner as determined from time to time. If we sell common stock, convertible securities or other equity securities, investors may be materially diluted by subsequent sales. Such sales may also result in material dilution to existing stockholders, and new investors could gain rights, preferences and privileges senior to the holders of Senti Common Shares.
Pursuant to the Incentive Plan, our board of directors or compensation committee is authorized to grant stock options to our employees, directors and consultants. Initially, the maximum aggregate number of Senti Common Shares that may be issued pursuant to stock awards under the Incentive Plan is 2,492,735 Senti Common Shares. Additionally, the number of Senti Common Shares reserved for issuance under the Incentive Plan will automatically increase on January 1 of each year, beginning on January 1, 2023 and continuing through and including January 1, 2032, by 5% of the total number of Senti Common Shares outstanding on December 31 of the preceding calendar year, or a lesser number of shares determined by our board of directors. Unless our board of directors elects not to increase the number of shares available for future grant each year, our stockholders may experience additional dilution, which could cause our stock price to fall. Our issuance of additional shares of common stock or other equity securities of equal or senior rank would, all else being equal, have the following effects:
| • | the amount of cash available per share, including for payment of dividends in the future, may decrease; |
77
| • | the relative voting strength of each previously outstanding share of common stock would be diminished; and |
| • | the market price of shares of Senti Common Shares may decline. |
Our disclosure controls and procedures may not prevent or detect all errors or acts of fraud.
We must design our disclosure controls and procedures to reasonably assure that information we must disclose in reports we file or submit under the Exchange Act is accumulated and communicated to management, and recorded, processed, summarized, and reported within the time periods specified in the rules and forms of the SEC. We believe that any disclosure controls and procedures or internal controls and procedures, no matter how well-conceived and operated, can provide only reasonable, not absolute, assurance that the objectives of the control system are met. These inherent limitations include the realities that judgments in decision-making can be faulty, and that breakdowns can occur because of simple error or mistake. For example, our directors or executive officers could inadvertently fail to disclose a new relationship or arrangement causing us to fail to make a required related party transaction disclosure. Additionally, controls can be circumvented by the individual acts of some persons, by collusion of two or more people or by an unauthorized override of the controls. Accordingly, because of the inherent limitations in our control system, misstatements due to error or fraud may occur and not be detected.
Reports published by analysts, including projections in those reports that differ from our actual results, could adversely affect the price and trading volume of Senti Common Shares.
We currently expect that securities research analysts will establish and publish their own periodic financial projections for our business. These projections may vary widely and may not accurately predict the results we actually achieve. Our stock price may decline if our actual results do not match the projections of these securities research analysts. Similarly, if one or more of the analysts who write reports on us downgrades our stock or publishes inaccurate or unfavorable research about our business, our stock price could decline. If one or more of these analysts ceases coverage of us or fails to publish reports on us regularly, our stock price or trading volume could decline. While we expect research analyst coverage, if no analysts commence coverage of us, the trading price and volume for Senti Common Shares could be adversely affected.
Our actual financial position and results of operations may differ materially from the unaudited pro forma condensed combined financial information included in this prospectus, which may not be indicative of what our actual financial position or results of operations would have been.
The unaudited pro forma condensed combined financial information in this prospectus is presented for illustrative purposes only and is not necessarily indicative of what our actual financial position or results of operations would have been. See the section titled “Unaudited Pro Forma Condensed Combined Financial Information” for more information.
The obligations associated with being a public company will involve significant expenses and will require significant resources and management attention, which may divert from our business operations.
As a public company, we are subject to the reporting requirements of the Exchange Act and the Sarbanes-Oxley Act. The Exchange Act requires the filing of annual, quarterly and current reports with respect to a public company’s business and financial condition. The Sarbanes-Oxley Act requires, among other things, that a public company establish and maintain effective internal control over financial reporting. As a result, we will incur significant legal, accounting and other expenses that we did not previously incur. Our entire management team and many of our other employees will need to devote substantial time to compliance, and may not effectively or efficiently manage our transition into a public company.
These rules and regulations will result in us incurring substantial legal and financial compliance costs and will make some activities more time-consuming and costly. For example, these rules and regulations will likely
78
make it more difficult and more expensive for us to obtain director and officer liability insurance, and we may be required to accept reduced policy limits and coverage or incur substantially higher costs to obtain the same or similar coverage. As a result, it may be difficult for us to attract and retain qualified people to serve on our board of directors, our board committees or as executive officers.
Provisions in our second amended and restated certificate of incorporation (“Charter”), our amended and restated bylaws (“Bylaws”) and Delaware law may have anti-takeover effects that could discourage an acquisition of us by others, even if an acquisition would be beneficial to our stockholders, and may prevent attempts by our stockholders to replace or remove our current management, which could depress the trading price of Senti Common Shares.
Our Charter, Bylaws and Delaware law contain provisions that may have the effect of discouraging, delaying or preventing a change in control of us or changes in our management that stockholders may consider favorable, including transactions in which you might otherwise receive a premium for your shares. Our Charter and Bylaws include provisions that:
| • | authorize “blank check” preferred stock, which could be issued by our board of directors without stockholder approval and may contain voting, liquidation, dividend and other rights superior to our common stock; |
| • | create a classified board of directors whose members serve staggered three-year terms; |
| • | specify that special meetings of our stockholders can be called only by our board of directors; |
| • | prohibit stockholder action by written consent; |
| • | establish an advance notice procedure for stockholder approvals to be brought before an annual meeting of our stockholders, including proposed nominations of persons for election to our board of directors; |
| • | specify that no stockholder is permitted to cumulate votes at any election of directors; |
| • | expressly authorize our board of directors to make, alter, amend or repeal our Bylaws; and |
| • | require supermajority votes of the holders of our common stock to amend specified provisions of our Charter and Bylaws. |
These provisions, alone or together, could delay or prevent hostile takeovers and changes in control or changes in our management. These provisions could also limit the price that investors might be willing to pay in the future for shares of our common stock, thereby depressing the market price of Senti Common Shares.
In addition, because we are incorporated in the State of Delaware, we are governed by the provisions of Section 203 of the General Corporation Law of the State of Delaware, which prohibits a person who owns in excess of 15% of our outstanding voting stock from merging or combining with us for a period of three years after the date of the transaction in which the person acquired in excess of 15% of our outstanding voting stock, unless the merger or combination is approved in a prescribed manner.
Any provision of our Charter, Bylaws or Delaware law that has the effect of delaying or deterring a change in control could limit the opportunity for our stockholders to receive a premium for their Senti Common Shares, and could also affect the price that some investors are willing to pay for Senti Common Shares.
Our Bylaws designate the Court of Chancery of the State of Delaware as the exclusive forum for certain state law litigation that may be initiated by our stockholders and the U.S. federal district courts as the exclusive forum for certain securities law actions, which could limit our stockholders’ ability to litigate disputes with us in a different judicial forum and increase the costs for our stockholders to pursue certain claims against us.
Pursuant to our Bylaws, unless we consent in writing to the selection of an alternative forum, the Court of Chancery of the State of Delaware will be the sole and exclusive forum for the following types of actions or
79
proceedings under Delaware statutory or common law: (i) any derivative action or proceeding brought on our behalf; (ii) any action asserting a claim of breach of a fiduciary duty owed by any of our current or former directors, officers or employees to us or our stockholders; (iii) any action asserting a claim arising pursuant to any provision of the General Corporation Law of the State of Delaware, our Charter or our Bylaws (including their interpretation, validity or enforceability); or (iv) any action asserting a claim governed by the internal affairs doctrine. This exclusive forum provision will not apply to any causes of action arising under the Securities Act or the Exchange Act or any other claim for which the federal courts have exclusive jurisdiction. Stockholders cannot waive compliance with the Securities Act, the Exchange Act or any other federal securities laws or the rules and regulations thereunder. Unless we consent in writing to the selection of an alternate forum, the United States federal district courts shall be the sole and exclusive forum for resolving any complaint asserting a cause of action arising under the Securities Act. In addition, our Bylaws provide that any person or entity purchasing or otherwise acquiring any interest in shares of our capital stock is deemed to have notice of and consented to these exclusive forum provisions. The forum selection provisions in our Bylaws may limit our stockholders’ ability to litigate disputes with us in a judicial forum that they find favorable for disputes with us or our directors, officers or employees, which may discourage the filing of lawsuits against us and our directors, officers and employees, even though an action, if successful, might benefit our stockholders. In addition, these forum selection provisions may impose additional litigation costs for stockholders who determine to pursue any such lawsuits against us.
Our failure to meet the continued listing requirements of Nasdaq could result in a delisting of our securities.
If we fail to satisfy the continued listing requirements of Nasdaq such as the corporate governance requirements or the minimum closing bid price requirement, Nasdaq may take steps to delist our securities. Such a delisting would likely have a negative effect on the price of the securities and would impair your ability to sell or purchase the securities when you wish to do so. In the event of a delisting, we can provide no assurance that any action taken by us to restore compliance with listing requirements would allow our securities to become listed again, stabilize the market price or improve the liquidity of our securities, prevent our securities from dropping below the Nasdaq minimum bid price requirement or prevent future non-compliance with Nasdaq’s listing requirements. Additionally, if our securities are not listed on, or become delisted from, Nasdaq for any reason, and are quoted on the OTC Bulletin Board, an inter-dealer automated quotation system for equity securities that is not a national securities exchange, the liquidity and price of our securities may be more limited than if we were quoted or listed on Nasdaq or another national securities exchange. You may be unable to sell your securities unless a market can be established or sustained.
General Risk Factors
Disruptions at the FDA and other government agencies caused by funding shortages or global health concerns could hinder their ability to hire, retain or deploy key leadership and other personnel, or otherwise prevent new or modified products from being developed, approved or commercialized in a timely manner or at all, which could negatively impact our business.
The ability of the FDA to review and approve new products can be affected by a variety of factors, including government budget and funding levels, statutory, regulatory and policy changes, the FDA’s ability to hire and retain key personnel and accept the payment of user fees, and other events that may otherwise affect the FDA’s ability to perform routine functions. Average review times at the FDA have fluctuated in recent years as a result. In addition, government funding of other government agencies that fund research and development activities is subject to the political process, which is inherently fluid and unpredictable. Disruptions at the FDA and other agencies may also slow the time necessary for new drugs and biologics or modifications to approved drugs and biologics to be reviewed and/or approved by necessary government agencies, which would adversely affect our business. For example, over the last several years, including for 35 days beginning on December 22, 2018, the U.S. government has shut down several times and certain regulatory agencies, such as the FDA, have had to furlough critical FDA employees and stop critical activities.
80
Since March 2020 when foreign and domestic inspections of facilities were largely placed on hold, the FDA has been working to resume routine surveillance, bioresearch monitoring and pre-approval inspections on a prioritized basis. Since April 2021, the FDA has conducted limited inspections and has employed remote interactive evaluations, using risk management methods, to meet user fee commitments and goal dates. Ongoing travel restrictions and other uncertainties continue to impact oversight operations both domestic and abroad and it is unclear when standard operational levels will resume. The FDA is continuing to complete mission-critical work, prioritize other higher-tiered inspectional needs (e.g., for-cause inspections), and carry out surveillance inspections using risk-based approaches for evaluating public health. Should FDA determine that an inspection is necessary for approval and an inspection cannot be completed during the review cycle due to restrictions on travel, and the FDA does not determine a remote interactive evaluation to be adequate, the agency has stated that it generally intends to issue, depending on the circumstances, a complete response letter or defer action on the application until an inspection can be completed. During the COVID-19 public health emergency, a number of companies announced receipt of complete response letters due to the FDA’s inability to complete required inspections for their applications. Regulatory authorities outside the U.S. may adopt similar restrictions or other policy measures in response to the ongoing COVID-19 pandemic and may experience delays in their regulatory activities.
We or the third parties upon whom we depend may be adversely affected by natural disasters and our business continuity and disaster recovery plans may not adequately protect us from a serious disaster.
Our current operations are located in the San Francisco Bay Area. Any unplanned event, such as earthquake, flood, fire, explosion, extreme weather condition, medical epidemics, including any potential effects from the current global spread of COVID-19, power shortage, telecommunication failure or other natural or man-made accidents or incidents that result in us being unable to fully utilize our facilities, or the manufacturing facilities of our third-party contract manufacturers, may have a material adverse effect on our ability to operate our business, particularly on a daily basis and have significant negative consequences on our financial and operating conditions. Loss of access to these facilities may result in increased costs, delays in the development of our product candidates or interruption of our business operations. Natural disasters or pandemics such as the COVID-19 outbreak could further disrupt our operations and have a material adverse effect on our business, financial condition, results of operations and prospects. If a natural disaster, power outage or other event occurred that prevented us from using all or a significant portion of our headquarters, that damaged critical infrastructure, such as our research facilities or the manufacturing facilities of our third-party contract manufacturers, or that otherwise disrupted operations, it may be difficult or, in certain cases, impossible, for us to continue our business for a substantial period of time. The disaster recovery and business continuity plans we have in place may prove inadequate in the event of a serious disaster or similar event. We may incur substantial expenses as a result of the limited nature of our disaster recovery and business continuity plans, which could have a material adverse effect on our business. As part of our risk management policy, we maintain insurance coverage at levels that we believe are appropriate for our business. However, in the event of an accident or incident at these facilities, we cannot assure our investors that the amounts of insurance will be sufficient to satisfy any damages and losses. If our facilities or the manufacturing facilities of our third-party contract manufacturers are unable to operate because of an accident or incident or for any other reason, even for a short period of time, any or all of our research and development programs may be harmed. Any business interruption may have a material adverse effect on our business, financial condition, results of operations and prospects.
Our quarterly operating results may fluctuate significantly or may fall below the expectations of investors or securities analysts, each of which may cause our stock price to fluctuate or decline.
We expect our operating results to be subject to quarterly fluctuations. Our net loss and other operating results will be affected by numerous factors, including:
| • | variations in the level of expense related to the ongoing development of our product candidates or future development programs; |
81
| • | results of preclinical studies and clinical trials, or the addition or termination of preclinical studies and clinical trials or funding support by us or potential future collaborators; |
| • | our execution of any collaboration, licensing or similar arrangements, and the timing of payments we may make or receive under potential future arrangements or the termination or modification of any of our existing or potential future collaboration, licensing or similar arrangements; |
| • | any intellectual property infringement, misappropriation or violation lawsuit or opposition, interference or cancellation proceeding in which we may become involved; |
| • | additions and departures of key personnel; |
| • | strategic decisions by us or our competitors, such as acquisitions, divestitures, spin-offs, joint ventures, strategic investments or changes in business strategy; |
| • | if any of our product candidates receives regulatory approval, the terms of such approval and market acceptance and demand for such product candidates; |
| • | regulatory developments affecting our product candidates or those of our competitors; and |
| • | changes in general market and economic conditions. |
If our quarterly operating results fall below the expectations of investors or securities analysts, the price of our common stock could decline substantially. Furthermore, any quarterly fluctuations in our operating results may, in turn, cause the price of our stock to fluctuate substantially. We believe that quarterly comparisons of our financial results are not necessarily meaningful and should not be relied upon as an indication of our future performance.
We may be subject to claims that our employees, consultants, or independent contractors have wrongfully used or disclosed confidential information of third parties.
We have received confidential and proprietary information from third parties. In addition, we employ individuals who were previously employed at other biotechnology or pharmaceutical companies. We may be subject to claims that we or our employees, consultants, or independent contractors have inadvertently or otherwise used or disclosed confidential information of these third parties or our employees’ former employers, or that we caused an employee to breach the terms of his or her non-competition or non-solicitation agreement. Litigation may be necessary to defend against these claims. Even if we are successful in defending against these claims, litigation could result in substantial cost and be a distraction to our management and employees. If our defenses to these claims fail, in addition to requiring us to pay monetary damages, a court could prohibit us from using technologies or features that are essential to our product candidates, if such technologies or features are found to incorporate or be derived from the trade secrets or other proprietary information of the former employers. Moreover, any such litigation or the threat thereof may adversely affect our reputation, our ability to form strategic alliances or sublicense our rights to collaborators, engage with scientific advisors or hire employees or consultants, each of which would have an adverse effect on our business, results of operations, financial condition and prospects. Even if we are successful in defending against such claims, litigation could result in substantial costs and be a distraction to management.
82
All of the Senti Common Shares offered by the Selling Securityholders pursuant to this prospectus will be sold by the Selling Securityholders for their respective accounts. We will not receive any of the proceeds from the sale of the Senti Common Shares hereunder.
With respect to the registration of all Senti Common Shares offered by the Selling Securityholders pursuant to this prospectus, the Selling Securityholders will pay any underwriting discounts and commissions and expenses incurred by them for brokerage, accounting, tax or legal services or any other expenses incurred by them in disposing of the Securities. We will bear the costs, fees and expenses incurred in effecting the registration of the securities covered by this prospectus, including all registration and filing fees and fees and expenses of our counsel and our independent registered public accounting firm.
DETERMINATION OF OFFERING PRICE
We cannot currently determine the price or prices at which the Senti Common Shares may be sold by the Selling Securityholders under this prospectus. Our Common Shares are listed on Nasdaq under the symbol “SNTI.”
83
MARKET PRICE AND DIVIDEND INFORMATION
Market Price
Senti Common Shares are listed on Nasdaq under the symbol “SNTI”. Prior to the consummation of the Business Combination our common shares were traded on Nasdaq under the symbol “DYNS”.
The closing price of the Senti Common Shares on July 28, 2022 was $1.86 per share.
Holders
As of July 28, 2022, there were 156 holders of record of the Senti Common Shares. The number of holders of record does not include for example a substantially greater number of “street name” holders or beneficial holders whose Senti Common Shares are held of record by banks, brokers and other financial institutions.
Dividend Policy
We have not paid any cash dividends to date. The payment of cash dividends in the future will be dependent upon our revenues and earnings, if any, capital requirements and general financial condition. The payment of any cash dividends will be within the discretion of our Board at such time. Our ability to declare dividends may also be limited by restrictive covenants pursuant to any future debt financing agreements.
84
UNAUDITED PRO FORMA CONDENSED COMBINED FINANCIAL INFORMATION
The following unaudited pro forma condensed combined financial statements present the combination of the financial information of DYNS and Senti after giving effect to the Business Combination.
On the Closing Date of the Business Combination, the following transactions (collectively, the “Transactions”) were completed, and the unaudited pro forma condensed combined financial information gives effect to the following:
| • | Merger Sub merged with and into Senti, with Senti surviving as a wholly-owned subsidiary of the Combined Company; |
| • | each outstanding share of Senti Common Stock was cancelled and converted into the right to receive a number of shares of Class A Common Stock of DYNS, rounded down to the nearest whole share, equal to the number of shares of Senti Common Stock multiplied by the Exchange Ratio; |
| • | each outstanding share of Senti Preferred Stock was cancelled and converted into the right to receive a number of shares of Class A Common Stock, rounded down to the nearest whole share, equal to (A) the aggregate number of shares of Senti Common Stock issuable upon conversion of the shares of Senti Preferred Stock based on the applicable conversion ratio immediately prior to the Effective Time, which was 1:1, multiplied by (B) the Exchange Ratio; |
| • | each outstanding Senti option (whether vested or unvested) was converted into an option to purchase a number of shares of Class A Common Stock (rounded down to the nearest whole share) equal to (A) the number of shares of Senti Common Stock subject to such option immediately prior to the Effective Time, multiplied by (B) the Exchange Ratio, at an exercise price per share equal to the current exercise price per share for such option divided by the Exchange Ratio, rounded up to the nearest whole cent; |
| • | the Combined Company issued an aggregate of 5,060,000 shares of Class A Common Stock to the PIPE Investors; |
| • | the Combined Company issued 517,500 shares of Class A Common Stock in connection with the Convertible Note Exchange; and |
| • | all shares of Class A Common Stock were redesignated as common stock, par value $0.0001 per share, of the Combined Company (“New Senti Common Stock”). |
The unaudited pro forma condensed combined financial statements are based on the DYNS historical consolidated financial statements and the Senti historical consolidated financial statements as adjusted to give effect to the Transactions. The unaudited pro forma condensed combined balance sheet gives pro forma effect to the Transactions as if they had been consummated on March 31, 2022. The unaudited pro forma condensed combined statements of operations for the three months ended March 31, 2022 and for the year ended December 31, 2021 give effect to the Transactions as if they had occurred on January 1, 2021.
The unaudited pro forma condensed combined financial statements have been derived from and should be read in conjunction with:
| • | the accompanying notes to the unaudited pro forma condensed combined financial statements; |
| • | the historical unaudited condensed consolidated financial statements of DYNS as of and for the three months ended March 31, 2022 and the related notes included in its Quarterly Report on Form 10-Q for the quarterly period ended March 31, 2022, as filed on May 16, 2022; |
| • | the historical audited consolidated financial statements of DYNS as of December 31, 2021 and for the period from March 1, 2021 (inception) through December 31, 2021 and the related notes included in the Proxy Statement/Prospectus, beginning on page F-2, as filed on May 13, 2022; |
85
| • | the historical unaudited condensed consolidated financial statements of Senti as of and for the three months ended March 31, 2021 and the related notes included in this prospectus; |
| • | the historical audited consolidated financial statements of Senti as of and for the year ended December 31, 2021 and the related notes included in the Proxy Statement/Prospectus, beginning on page F-26, as filed on May 13, 2022; |
| • | the “DYNS Management’s Discussion and Analysis of Financial Condition and Results of Operations,” included in its Quarterly Report on Form 10-Q for the quarterly period ended March 31, 2022, as filed on May 16, 2022, and for the year ended December 31, 2021 included in the Proxy Statement/Prospectus, beginning on page 206, as filed on May 13, 2022; and |
| • | the “Senti Management’s Discussion and Analysis of Financial Condition and Results of Operations,” for the three months ended March 31, 2022 and 2021 included in this prospectus and for the years ended December 31, 2021 and 2020 included in the Proxy Statement/Prospectus, beginning on page 307, as filed on May 13, 2022. |
The unaudited pro forma condensed combined financial statements are provided for illustrative purposes only and are not necessarily indicative of what the actual results of operations and financial position would have been had the Transactions taken place on the dates indicated, nor are they indicative of the future consolidated results of operations or financial position of the combined company.
86
UNAUDITED PRO FORMA CONDENSED COMBINED BALANCE SHEET
AS OF MARCH 31, 2022
(in thousands, except share and per share information)
| Historical | Historical | Actual Redemptions | ||||||||||||||||||||||||||
| 5(A) | 5(B) | |||||||||||||||||||||||||||
| DYNS | Senti | Convertible Note | Transaction Accounting Adjustments | Pro Forma Balance Sheet | ||||||||||||||||||||||||
Assets | ||||||||||||||||||||||||||||
Current assets: | ||||||||||||||||||||||||||||
Cash and cash equivalents | $ | 397 | $ | 38,140 | $ | 5,175 | 5(aa) | $ | 230,032 | 5(a) | $ | 155,660 | ||||||||||||||||
| (7,050 | ) | 5(b) | ||||||||||||||||||||||||||
| (4,051 | ) | 5(c) | ||||||||||||||||||||||||||
| (5,116 | ) | 5(d) | ||||||||||||||||||||||||||
| (5,383 | ) | 5(e) | ||||||||||||||||||||||||||
| 50,600 | 5(f) | |||||||||||||||||||||||||||
| (1,664 | ) | 5(f) | ||||||||||||||||||||||||||
| 74 | 5(h) | |||||||||||||||||||||||||||
| (145,495 | ) | 5(g) | ||||||||||||||||||||||||||
Trade and other receivables | — | 430 | 430 | |||||||||||||||||||||||||
Prepaid expenses and other current assets | 430 | 6,048 | (430 | ) | 5(c) | 2,974 | ||||||||||||||||||||||
| (3,074 | ) | 5(e) | ||||||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||||||
Total current assets | 827 | 44,618 | 5,175 | 108,444 | 159,064 | |||||||||||||||||||||||
Restricted cash | — | 3,257 | 3,257 | |||||||||||||||||||||||||
Investments held in Trust Account | 230,032 | — | (230,032 | ) | 5(a) | — | ||||||||||||||||||||||
Property and equipment, net | — | 24,067 | 24,067 | |||||||||||||||||||||||||
Operating lease right-of-use assets | — | 20,178 | 20,178 | |||||||||||||||||||||||||
Other long term assets | 57 | 186 | (57 | ) | 5(c) | 186 | ||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||||||
Total assets | $ | 230,916 | $ | 92,306 | $ | 5,175 | $ | (121,646 | ) | $ | 206,752 | |||||||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||||||
Liabilities, redeemable convertible preferred stock and stockholders’ deficit | ||||||||||||||||||||||||||||
Current liabilities: | ||||||||||||||||||||||||||||
Accounts payable | 33 | 5,657 | (33 | ) | 5(c) | 5,598 | ||||||||||||||||||||||
| (59 | ) | 5(e) | ||||||||||||||||||||||||||
Early exercise liability, current portion | — | 325 | 325 | |||||||||||||||||||||||||
Deferred revenue | — | 1,379 | 1,379 | |||||||||||||||||||||||||
Accrued expenses and other current liabilities | 3,968 | 8,979 | — | (3,968 | ) | 5(c) | 6,576 | |||||||||||||||||||||
| (2,403 | ) | 5(e) | ||||||||||||||||||||||||||
Franchise tax payable | 50 | — | (50 | ) | 5(c) | — | ||||||||||||||||||||||
Operating lease liabilities | — | 1,799 | 1,799 | |||||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||||||
Total current liabilities | 4,051 | 18,139 | — | (6,513 | ) | 15,677 | ||||||||||||||||||||||
Operating lease liabilities, net of current portion | — | 23,596 | 23,596 | |||||||||||||||||||||||||
Deferred underwriting fee payable | 7,050 | — | (7,050 | ) | 5(b) | — | ||||||||||||||||||||||
Convertible note | — | — | 5,175 | 5(aa) | (5,175 | ) | 5(n) | — | ||||||||||||||||||||
Early exercise liability, net of current portion | — | 545 | 545 | |||||||||||||||||||||||||
Deferred revenue, net of current portion | — | — | ||||||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||||||
Total liabilities | $ | 11,101 | $ | 42,280 | $ | 5,175 | $ | (18,738 | ) | $ | 39,818 | |||||||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||||||
See accompanying notes to the unaudited pro forma condensed combined financial statements.
87
UNAUDITED PRO FORMA CONDENSED COMBINED BALANCE SHEET
AS OF MARCH 31, 2022
(in thousands, except share and per share information)
| Historical | Historical | Actual Redemptions | ||||||||||||||||||||||
| 5(A) | 5(B) | |||||||||||||||||||||||
| DYNS | Senti Biosciences, Inc. | Convertible Note | Transaction Accounting Adjustments | Pro Forma Balance Sheet | ||||||||||||||||||||
Class A common stock subject to possible redemption, 23,000,000 shares at redemption value | $ | 230,000 | $ | — | $ | (230,000 | ) | 5(g) | $ | — | ||||||||||||||
Stockholders’ Equity | ||||||||||||||||||||||||
DYNS Class A common stock | — | — | — | 5(k) | — | |||||||||||||||||||
| 1 | 5(l) | |||||||||||||||||||||||
| (1 | ) | 5(m) | ||||||||||||||||||||||
DYNS Class B common stock | 1 | — | — | 5(j) | — | |||||||||||||||||||
| (1 | ) | 5(l) | ||||||||||||||||||||||
New Senti Class A common stock | 1 | 5(f) | 5 | |||||||||||||||||||||
| 1 | 5(g) | |||||||||||||||||||||||
| 2 | 5(i) | |||||||||||||||||||||||
| 1 | 5(m) | |||||||||||||||||||||||
| — | 5(n) | |||||||||||||||||||||||
Redeemable convertible preferred stock: | ||||||||||||||||||||||||
Redeemable convertible preferred stock (A and B), $0.0001 par value; 99,734,554 shares authorized at March 31, 2022 (unaudited); 99,734,543 issued and outstanding at March 31, 2022 | — | 171,833 | (171,833 | ) | 5(i) | — | ||||||||||||||||||
Stockholder’s deficit | ||||||||||||||||||||||||
Common stock, $0.0001 par value; 138,000,000 shares authorized as of March 31, 2022 (unaudited); 16,804,476 issued and outstanding at March 31, 2022 (unaudited) | — | 1 | (1 | ) | 5(i) | — | ||||||||||||||||||
| — | 5(h) | |||||||||||||||||||||||
Additional paid-in capital | — | 5,076 | (487 | ) | 5(c) | 293,813 | ||||||||||||||||||
| (200 | ) | 5(d) | ||||||||||||||||||||||
| (5,995 | ) | 5(e) | ||||||||||||||||||||||
| 50,599 | 5(f) | |||||||||||||||||||||||
| (1,664 | ) | 5(f) | ||||||||||||||||||||||
| 84,504 | 5(g) | |||||||||||||||||||||||
| 148,021 | 5(i) | |||||||||||||||||||||||
| — | 5(j) | |||||||||||||||||||||||
| 8,710 | 5(k) | |||||||||||||||||||||||
| 74 | 5(h) | |||||||||||||||||||||||
| 5,175 | 5(n) | |||||||||||||||||||||||
Accumulated deficit | (10,186 | ) | (126,884 | ) | (4,916 | ) | 5(d) | (126,884 | ) | |||||||||||||||
| 23,812 | 5(i) | |||||||||||||||||||||||
| (8,710 | ) | 5(k) | ||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||
Total stockholders’ (deficit) / equity | $ | (10,185 | ) | $ | (121,807 | ) | $ | — | $ | 298,926 | $ | 166,934 | ||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||
Total liabilities, redeemable convertible preferred stock and stockholders’ (deficit) / equity | $ | 230,916 | $ | 92,306 | $ | 5,175 | $ | (121,646 | ) | $ | 206,752 | |||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||
See accompanying notes to the unaudited pro forma condensed combined financial statements.
88
UNAUDITED PRO FORMA CONDENSED COMBINED STATEMENT OF OPERATIONS FOR THE
THREE MONTHS ENDED MARCH 31, 2022
(in thousands, except share and per share amounts)
| Historical | Actual Redemptions | |||||||||||||||||||
| 6(A) | 6(B) | |||||||||||||||||||
| DYNS | Senti | Transaction Accounting Adjustments | Pro Forma Statement of Operations | |||||||||||||||||
Revenue | ||||||||||||||||||||
Contract revenue | 854 | 854 | ||||||||||||||||||
Grant Income | 250 | 250 | ||||||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Total revenue | — | 1,104 | — | 1,104 | ||||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Operating expenses: | ||||||||||||||||||||
Research and development | 7,603 | 402 | 6(d) | 8,005 | ||||||||||||||||
Professional fees and other expenses | 1,283 | — | 1,283 | |||||||||||||||||
Franchise tax expense | 50 | — | 50 | |||||||||||||||||
General and administrative | 5,259 | 3,173 | 6(d) | 8,432 | ||||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Total operating expenses | 1,333 | 12,862 | 3,575 | 17,770 | ||||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Loss from operations | (1,333 | ) | (11,758 | ) | (3,575 | ) | (16,666 | ) | ||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Other income (expense): | ||||||||||||||||||||
Interest income, net | 4 | 4 | ||||||||||||||||||
Interest and dividend income on investments held in Trust Account | 23 | — | (23 | ) | 6(a) |
| — |
| ||||||||||||
Other expense | — | (54 | ) | — | (54 | ) | ||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Total other income (expense), net | 23 | (50 | ) | (23 | ) | (50 | ) | |||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Net loss | (1,310 | ) | (11,808 | ) | (3,598 | ) | (16,716 | ) | ||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Basic and diluted net loss per share, Class B common stock | $ | (0.04 | ) | |||||||||||||||||
|
| |||||||||||||||||||
Basic and diluted weighted average shares outstanding, Class B common stock | 5,750,000 | |||||||||||||||||||
|
| |||||||||||||||||||
Basic and diluted net loss per share, Class A common stock | $ | (0.04 | ) | $ | (0.73 | ) | $ | (0.39 | ) | |||||||||||
|
|
|
|
|
| |||||||||||||||
Basic and diluted weighted average shares outstanding, Class A common stock | 23,715,500 | 16,204,614 | 43,368,276 | 6(f) | ||||||||||||||||
|
|
|
|
|
| |||||||||||||||
See accompanying notes to the unaudited pro forma condensed combined financial statements.
89
UNAUDITED PRO FORMA CONDENSED COMBINED STATEMENT OF OPERATIONS FOR THE
YEAR ENDED DECEMBER 31, 2021
(in thousands, except share and per share amounts)
| Historical | Actual Redemptions | |||||||||||||||||||
| 6(C) | 6(D) | |||||||||||||||||||
| DYNS | Senti | Transaction Accounting Adjustments | Pro Forma Statement of Operations | |||||||||||||||||
Revenue | ||||||||||||||||||||
Contract revenue | — | 2,291 | 2,291 | |||||||||||||||||
Grant Income | — | 470 | 470 | |||||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Total revenue | — | 2,761 | — | 2,761 | ||||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Operating expenses: | ||||||||||||||||||||
Research and development | — | 21,957 | 2,991 | 6(d) | 24,948 | |||||||||||||||
Professional fees and other expenses | 3,702 | — | 3,702 | |||||||||||||||||
Franchise tax expense | 164 | — | 164 | |||||||||||||||||
General and administrative | — | 21,250 | 23,048 | 6(d) | 49,214 | |||||||||||||||
| 4,916 | 6(e) | |||||||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Total operating expenses | 3,866 | 43,207 | 30,955 | 78,028 | ||||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Loss from operations | (3,866 | ) | (40,446 | ) | (30,955 | ) | (75,267 | ) | ||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Other income (expense): | ||||||||||||||||||||
Interest income, net | — | 11 | 11 | |||||||||||||||||
Interest and dividend income on investments held in Trust Account | 9 | — | (9 | ) | 6(a) | — | ||||||||||||||
Change in preferred stock tranche liability | — | (14,742 | ) | 14,742 | 6(c) | — | ||||||||||||||
Loss on impairment of fixed assets | — | (22 | ) | (22 | ) | |||||||||||||||
Other expense | — | (120 | ) | (8,710 | ) | 6(b) | (8,830 | ) | ||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Total other income (expense), net | 9 | (14,873 | ) | 6,023 | (8,841 | ) | ||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Net loss | (3,857 | ) | (55,319 | ) | (24,932 | ) | (84,108 | ) | ||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Basic and diluted net loss per share, Class B common stock | $ | (0.17 | ) | |||||||||||||||||
|
| |||||||||||||||||||
Basic and diluted weighted average shares outstanding, Class B common stock | 5,418,853 | |||||||||||||||||||
|
| |||||||||||||||||||
Basic and diluted net loss per share, Class A common stock | $ | (0.17 | ) | $ | (3.72 | ) | $ | (1.94 | ) | |||||||||||
|
|
|
|
|
| |||||||||||||||
Basic and diluted weighted average shares outstanding, Class A common stock | 16,872,995 | 14,881,325 | 43,368,276 | 6(f) | ||||||||||||||||
|
|
|
|
|
| |||||||||||||||
See accompanying notes to the unaudited pro forma condensed combined financial statements.
90
NOTES TO UNAUDITED PRO FORMA CONDENSED COMBINED FINANCIAL STATEMENTS
1. Description of the Transactions
On December 19, 2021, Senti entered into a definitive merger agreement with DYNS, a publicly traded special purpose acquisition company (“SPAC”). On June 8, 2022, DYNS consummated the business combination with Senti. Pursuant to the terms of the Business Combination Agreement, Merger Sub merged with and into Senti, with Senti surviving the merger as a wholly-owned subsidiary of DYNS (the “Business Combination”). The cash components of the Business Combination were funded by DYNS cash in trust of $84.5 million, $50.6 million of the expected $66.8 million from a private placement of common stock at $10.00 per share sold to various accredited investors (the “PIPE Investment”) and $5.2 million in principal from the Convertible Note (as defined below), which was exchanged for common stock at $10.00 per share concurrently with the PIPE Investment.
Non-Redemption Agreements
Funds and accounts managed by the Anchor Investors, in exchange for 871,028 shares of new securities in DYNS, entered into the Non-Redemption Agreements, pursuant to which they agreed not to redeem, in aggregate, 7,839,337 shares of Class A Common Stock. The new securities issued to the Anchor Investors at the closing of the Business Combination were shares of Class A Common Stock, and the issuance of such shares corresponded with a simultaneous cancellation/forfeiture of an equivalent aggregate amount of Founder Shares held by the Sponsor, such that there was no net effect on the aggregate issued share capital of DYNS. New securities were issued to the Anchor Investors on the basis that they received, in shares of Class A Common Stock, 11.111% of the number of shares of Class A Common Stock which they held at the time the Business Combination was consummated. On May 9, 2022, DYNS, the Sponsor and the Anchor Investors agreed to amend the Non-Redemption Agreements such that the number of shares of Class A Common Stock to which each Anchor Investor may be entitled (as described above) would be determined based on how many Public Shares such Anchor Investor holds at the time the Business Combination is consummated (as opposed to when the Non-Redemption Agreement was signed). The issuance of such shares of Class A Common Stock to the Anchor Investors is the only consideration which they received in connection with their agreement not to redeem their Public Shares.
The Convertible Note
On May 19, 2022, Senti issued an unsecured convertible promissory note to Bayer HealthCare, LLC, a Senti related party, in the principal amount of $5.2 million, bearing a 3.00% annual interest rate, with a maturity date of May 19, 2024 (the “Convertible Note”). On June 8, 2022, in conjunction with the closing of the Business Combination, the outstanding principal amount on the Convertible Note of $5.2 million was cancelled and exchanged for 517,500 shares of the New Senti Common Stock at a price of $10.00 per share. An immaterial amount of accrued interest was forfeited in accordance with the terms of the Convertible Note.
2. Basis of Pro Forma Presentation
The unaudited pro forma condensed combined financial statements were prepared in accordance with Article 11 of SEC Regulation S-X, as amended by the final rule, Release No. 33-10786, Amendments to Financial Disclosures about Acquired and Disposed Businesses. Release No. 33-10786 replaced the previous pro forma adjustment criteria with simplified requirements to depict the accounting for the Transactions (“Transaction Accounting Adjustments”) and present the reasonably estimable synergies and other transaction effects that have occurred or are reasonably expected to occur (“Management’s Adjustments”). Management has elected not to present Management’s Adjustments and will only be presenting Transaction Accounting Adjustments in the unaudited pro forma condensed combined financial information. The adjustments presented in the unaudited pro forma condensed combined financial statements have been identified and presented to provide relevant information necessary for an understanding of the combined company reflecting the Transactions.
91
The unaudited pro forma condensed combined financial statements are based on the DYNS historical consolidated financial statements, and the Senti historical consolidated financial statements as adjusted to give effect to the Transactions. The unaudited pro forma condensed combined balance sheet gives pro forma effect to the Transactions as if they had been consummated on March 31, 2022. The unaudited pro forma condensed combined statements of operations for three months ended March 31, 2022 and for the year ended December 31, 2021 give effect to the Transactions as if they had occurred on January 1, 2021.
Management has made significant estimates and assumptions in its determination of the pro forma adjustments. The pro forma adjustments reflecting the Transactions are based on certain currently available information and certain assumptions and methodologies that management believes are reasonable under the circumstances. The pro forma adjustments, which are described in the accompanying notes, may be revised as additional information becomes available and is evaluated. Therefore, it is likely that the actual adjustments will differ from the pro forma adjustments, and it is possible the difference may be material. Management believes that its assumptions and methodologies provide a reasonable basis for presenting all of the significant effects of the Transactions based on information available at this time and that the pro forma adjustments give appropriate effect to those assumptions and are properly applied in the unaudited pro forma condensed combined financial statements.
The unaudited pro forma condensed combined financial statements do not give effect to any anticipated synergies, operating efficiencies, tax savings, or cost savings that may be associated with the Business Combination. DYNS and Senti have not had any historical relationship prior to the Business Combination. Accordingly, no pro forma adjustments were required to eliminate activities between the companies.
The unaudited pro forma condensed combined financial information has been prepared based on actual redemptions of 14,549,537 outstanding shares of DYNS Common Stock for aggregate redemption payments of $145.5 million out of the trust account on the Closing Date. No other shares of DYNS Common Stock were subject to redemption.
Shares outstanding as presented in the unaudited pro forma condensed combined financial statements include 23,163,614 shares of New Senti Common Stock issued to Senti stockholders, 14,915,963 shares of New Senti Common Stock issued to DYNS stockholders (reflecting actual redemptions by DYNS public stockholders), 5,060,000 shares of New Senti Common Stock issued in connection with the PIPE Investment and 517,500 shares of New Senti Common Stock issued in connection with the exchange of the Convertible Note.
As a result of the Transactions, Senti stockholders own approximately 54.2% of the shares of New Senti Common Stock, DYNS public stockholders own approximately 21.4% of the shares of New Senti Common Stock, the PIPE Investors own approximately 11.6% of the shares of New Senti Common Stock and the Sponsor owns approximately 12.8% of the shares of New Senti Common Stock, based on the number of shares of New Senti Common Stock outstanding as of March 31, 2022 (before the distribution from the Sponsor LLC to its members in connection with the Closing).
These unaudited pro forma condensed combined financial statements and related notes have been derived from and should be read in conjunction with:
| • | the accompanying notes to the unaudited pro forma condensed combined financial statements; |
| • | the historical unaudited condensed consolidated financial statements of DYNS as of and for the three months ended March 31, 2022 and the related notes included in its Quarterly Report on Form 10-Q for the quarterly period ended March 31, 2022, as filed on May 16, 2022; |
| • | the historical audited consolidated financial statements of DYNS as of December 31, 2021 and for the period from March 1, 2021 (inception) through December 31, 2021 and the related notes included in the Proxy Statement/Prospectus, beginning on page F-2, as filed on May 13, 2022; |
| • | the historical unaudited condensed consolidated financial statements of Senti as of and for the three months ended March 31, 2021 and the related notes included in this prospectus; |
| • | the historical audited consolidated financial statements of Senti as of and for the year ended December 31, 2021 and the related notes included in the Proxy Statement/Prospectus, beginning on page F-26, as filed on May 13, 2022; |
92
| • | the “DYNS Management’s Discussion and Analysis of Financial Condition and Results of Operations,” included in its Quarterly Report on Form 10-Q for the quarterly period ended March 31, 2022, as filed on May 16, 2022, and included in the Proxy Statement/Prospectus, beginning on page 206, as filed on May 13, 2022; and |
| • | the “Senti Management’s Discussion and Analysis of Financial Condition and Results of Operations,” for the three months ended March 31, 2022 and 2021 included in this prospectus and for the years ended December 31, 2021 and 2020 included in the Proxy Statement/Prospectus, beginning on page 307, as filed on May 13, 2022. |
The unaudited pro forma condensed combined financial statements are provided for illustrative purposes only and are not necessarily indicative of what the actual results of operations and financial position would have been had the Transactions taken place on the dates indicated, nor are they indicative of the future consolidated results of operations or financial position of the combined company.
3. Accounting for the Merger
Notwithstanding the legal form, the Business Combination will be accounted for as a reverse recapitalization in accordance with U.S. generally accepted accounting principles (“U.S. GAAP”). Under this method of accounting, DYNS will be treated as the acquired company for financial reporting purposes, whereas Senti will be treated as the accounting acquiror. In accordance with this accounting method, the Business Combination will be treated as the equivalent of Senti issuing stock for the net assets of DYNS, accompanied by a recapitalization. The net assets of Senti will be stated at historical cost, with no goodwill or other intangible assets recorded, and operations prior to the Business Combination will be those of Senti. Senti has been determined to be the accounting acquiror for purposes of the Business Combination based on an evaluation of the following facts and circumstances:
| • | Persons affiliated with Senti control a majority of the governing body of New Senti; |
| • | Senti’s operations prior to the Business Combination will comprise the ongoing operations of New Senti; and |
| • | Senti’s existing senior management team comprise the senior management team of the Combined Company. |
93
4. DYNS Class A Common Stock Issued to Senti Stockholders upon Closing of the Business Combination and the consummation of the PIPE Investment
Based on 118,363,753 shares of Senti Common Stock outstanding after conversion of the preferred stock into common stock and immediately prior to the closing of the Transactions, the estimated Exchange Ratio (as defined in the section of this Proxy Statement /Prospectus entitled “Frequently Used Terms”) determined in accordance with the terms of the Business Combination Agreement is approximately 0.19571, which means New Senti issued 23,163,614 shares of New Senti Common Stock in the Business Combination, determined as follows:
| Number of Senti shares as of March 31, 2022 | Unvested restricted common stock subject to repurchase reclassed to Common Stock from April 1 to June 8, 2022 | Vested options exercised into common stock from April 1 to June 8, 2022 | Senti common and preferred stock assumed outstanding prior to the closing of the Business Combination, Non- Redemption Agreement and the PIPE Investment | |||||||||||||
Common stock | 16,804,476 | 209,748 | 139,255 | 17,153,479 | ||||||||||||
Unvested restricted common stock subject to repurchase | 1,685,479 | (209,748 | ) | 1,475,731 | ||||||||||||
Preferred stock | 99,734,543 | 99,734,543 | ||||||||||||||
|
|
|
|
|
|
|
| |||||||||
Total | 118,224,498 | — | 139,255 | 118,363,753 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Senti common and preferred stock outstanding prior to the closing of the Transactions | 118,363,753 | |||||||||||||||
Assumed Exchange Ratio | 0.1957 | |||||||||||||||
|
| |||||||||||||||
Estimated shares of New Senti common stock issued to Senti Stockholders upon closing of the Transactions(2) | 23,163,614 | |||||||||||||||
|
| |||||||||||||||
| 1 | Exchange Ratio is calculated pursuant to the Business Combination Agreement by dividing the Equity Value Per Share by the DYNS Share Value, as each of those terms is defined in the Business Combination Agreement. DYNS Share Value is equal to $10.00. Equity Value Per Share is determined by dividing the Equity Value by the Fully Diluted Company Capitalization, again, as each of those terms is defined in the Business Combination Agreement. The Equity Value is $240,000,000. The Fully Diluted Company Capitalization is the sum of (x) the aggregate number of shares of Senti common stock outstanding as of immediately prior to the Effective Time (including the Senti preferred stock on an as-converted basis), or 118,363,753 shares, and (y) the aggregate number of shares of Senti common stock subject to Senti options (on a net exercise basis) as of immediately prior to the Effective Time (excluding any shares of Senti common stock subject to options issued under the Incentive Plan at or prior to Closing), or 4,243,163 shares, giving a total of 122,606,916 shares. Therefore, the Equity Value Per Share is approximately $1.957 (i.e. $240,000,000/ 122,606,916) and the Exchange Ratio is approximately 0.1957 (i.e. $1.957 / $10.00). |
| (2) | Calculated by multiplying the “Senti preferred and common stock outstanding prior to the closing of the Transactions,” or 118,363,753 shares, by the assumed Exchange Ratio of 0.1957. |
94
5. Adjustments to Unaudited Pro Forma Condensed Combined Balance Sheet
The pro forma notes and adjustments, based on preliminary estimates that could change materially as additional information is obtained, are as follows:
Pro forma notes:
| (A) | Derived from the unaudited condensed consolidated balance sheet of DYNS as of March 31, 2022. |
| (B) | Derived from the unaudited condensed consolidated balance sheet of Senti as of March 31, 2022. |
Issuance of the Convertible Note:
| aa) | To reflect the issuance of the Convertible Note in the amount of $5.2 million on May 19, 2022. Senti accrued an immaterial amount of interest from May 19 through June 8, 2022, which is not reflected herein. The Convertible Note was exchanged for shares of New Senti Common Stock upon the closing of the Business Combination with identical rights as the PIPE Investment (see Notes 1 and 5(n)). |
Pro forma Transaction Accounting Adjustments:
| a) | To reflect the release of investments from the trust account to cash and cash equivalents at the closing of the Business Combination. |
| b) | To reflect the payment of DYNS’s deferred underwriting fee payable of $7.1 million of costs incurred in connection with the DYNS initial public offering and payable upon completion of the Business Combination. The payment of $7.1 million has been recorded as a reduction of $7.1 million to deferred underwriting fee payable. |
| c) | To reflect the payment of DYNS’s accrued expenses and other current liabilities of $4.0 million, accounts payable of $33 thousand, franchise taxes of $50 thousand and a reclassification of deferred transaction cost of $0.5 million that are deemed to be direct and incremental costs of the Business Combination from prepaid expenses and other current assets and other long-term assets to additional paid-in capital. |
| d) | To reflect the payment of DYNS total estimated advisory, legal, accounting and auditing fees and other professional fees of $0.2 million that are deemed to be direct and incremental costs of the Business Combination, which is reflected as a reduction to additional paid-in capital. Also, to reflect the payment of $4.9 million of DYNS’s additional transaction costs that are not directly attributable to the Business Combination and are non-recurring items. The payment of $4.9 million of additional transaction costs has been recorded as an increase to accumulated deficit (see Note 6(e)). |
| e) | To reflect the payment of Senti total estimated advisory, legal, accounting and auditing fees and other professional fees of $5.4 million that are deemed to be direct and incremental costs of the Business Combination. The payment of $5.4 million of costs directly attributable to the Business Combination have been recorded as a reduction of $6.0 million to additional paid-in capital, a reduction of $2.4 million to accrued expenses and other current liabilities, a reduction of $59 thousand to accounts payable and a reduction of $3.1 million to prepaid expenses and other current assets. |
| f) | To reflect the issuance of an aggregate of 5,060,000 shares of New Senti Common Stock in the PIPE Investment at a price of $10.00 per share, for proceeds of $50.6 million and to record the fees associated with the consummation of the PIPE Investment in the amount of $1.7 million. The issuance of 5,060,000 shares was recorded as an increase of $50.6 million to cash and cash equivalents, an increase to common stock of $1 thousand and an increase to additional paid-in capital in amount of $50.6 million. The PIPE fees in the amount of $1.7 million were recorded as a decrease to cash and cash equivalents and a decrease to additional paid-in capital. |
| g) | To reflect the actual redemption of 14,549,537 shares of DYNS Class A Common Stock resulting in a reduction of $145.5 million in cash and cash equivalents and a reclassification of 8,450,463 shares of |
95
| DYNS Class A Common Stock that were not redeemed to New Senti Class A Common Stock of $1 thousand and additional paid-in capital of $84.5 million. |
| h) | To reflect an increase of 139,255 shares of Senti Common Stock due to the exercise of vested options in the period from April 1 to June 8, 2022, resulting in an increase of $74 thousand to cash and cash equivalents, an increase of $14 to common stock and an increase of $74 thousand to additional paid-in capital (see Note 4). |
| i) | To reflect the recapitalization of Senti through the contribution of all outstanding common stock and preferred stock of Senti to DYNS and the issuance of 23,163,614 shares of New Senti Common Stock and the elimination of the accumulated deficit of DYNS, the accounting acquiree. As a result of the recapitalization, Senti Common Stock of $1 thousand, Senti redeemable convertible preferred stock of $171.8 million and DYNS accumulated deficit of $23.8 million including the transaction adjustment of $8.7 million described in Note 5(k) were derecognized. The shares of New Senti Common Stock issued in exchange for Senti’s capital were recorded as increase to common stock of $2 thousand and increase to additional paid-in capital in amount of $148 million. |
| j) | To reflect the cancellation of 871,028 shares of Class B common stock of DYNS in order to issue 871,028 shares of Class A common stock of DYNS to the Anchor Investors as discussed in Notes 1 and 5(k). |
| k) | To reflect the issuance of 871,028 shares of Class A Common Stock of DYNS to the Anchor Investors. To induce Anchor Investors, to not exercise their redemption rights in respect of the Class A Common Stock in connection with the pending merger with Senti, DYNS entered into the non-redemption agreements with Anchor Investors. Pursuant to the non-redemption agreements, concurrently with the execution of the Business Combination Agreement, the Sponsor agreed to forfeit to DYNS certain Class B Common Stock which it held, and DYNS agreed to cancel such shares of Class B Common Stock of the Sponsor and concurrently issue to the Anchor Investors an equivalent number of shares of Class A Common Stock, thereby increasing the Anchor Investors’ ownership interest in New Senti. The issuance of such shares of Class A Common Stock to the Anchor Investors is the only consideration which they received in connection with their agreement not to redeem their Public Shares. Based on the price of $10.00 per share this transaction results in an increase to common stock of $87, increase to additional paid-in capital of $8.7 million and increase to accumulated deficit of $8.7 million (see Note 6(b)). |
| l) | To reflect the conversion of the remaining shares of DYNS Class B Common Stock (after the cancellation of 871,028 shares of DYNS Class B Common Stock as discussed in Note 5(j)) to DYNS Class A Common Stock. |
| m) | To reflect the reclassification of DYNS Class A Common Stock including amounts discussed in Note 5(k) to New Senti Class A Common Stock. |
| n) | On June 8, 2022, in conjunction with the closing of the Business Combination, the $5.2 million outstanding principal amount of the Convertible Note was exchanged into 517,500 shares of New Senti Common Stock at a price of $10.00 per share with identical rights to the PIPE Investment. An immaterial amount of accrued interest was forfeited in accordance with the terms of the Convertible Note (see Notes 1 and 5(aa)). |
6. Adjustments to Unaudited Pro Forma Condensed Combined Statement of Operations
The pro forma notes and adjustments, based on preliminary estimates that could change materially as additional information is obtained, are as follows:
Pro forma notes:
| (A) | Derived from the unaudited condensed consolidated statement of operations of DYNS for the three months ended March 31, 2022. |
96
| (B) | Derived from the unaudited condensed consolidated statement of operations of Senti for the three months ended March 31, 2022. |
| (C) | Derived from the audited consolidated statement of operations of DYNS for the period from March 1, 2021 (inception) through December 31, 2021. |
| (D) | Derived from the audited consolidated statement of operations of Senti for the year ended December 31, 2021. |
Pro forma Transaction Accounting Adjustments:
| a) | To reflect an adjustment to eliminate interest and dividend income earned on investments held in the trust account as if the Business Combination had occurred on January 1, 2021. |
| b) | To reflect expense associated with the issuance of the Class A Common Stock equal to $8.7 million in accordance with the non-redemption agreements (see Notes 5(j) and 5(k)). |
| c) | To reflect an adjustment to eliminate the change in preferred stock tranche liability as it is assumed that the preferred stock would have been converted to Senti Common Stock and then to shares of New Senti Common Stock as if the Business Combination had occurred on January 1, 2021. |
| d) | To reflect an estimated compensation expense associated with the stock options that were granted under the equity incentive plan as if the Business Combination had occurred on January 1, 2021. The compensation expense was estimated on a tranche-by-tranche basis. The estimated grant date fair value was determined as of February 12, 2022. The number of shares that become exercisable for certain key executives decreased based on the number of redeemed DYNS Class A Common Stock as of the Closing (see note 5(g)). The number of stock options granted under the equity incentive plan are presented as follows: |
Stock options that are contingent on the consummation of the Business Combination and a four years service period | 34,727,225 | |||
Stock options that are contingent on the consummation of the Business Combination, market conditions, and an estimated two years service period | 1,613,430 |
| e) | To reflect additional transaction costs of $4.9 million within general and administrative expense of DYNS (see Note 5(d)). |
| f) | The pro forma basic and diluted net loss per share amounts presented in the unaudited pro forma condensed combined statements of operations are based upon the number of New Senti shares outstanding as if the Transactions occurred on January 1, 2021. The calculation of weighted-average shares outstanding for pro forma basic and diluted net loss per share assumes that the shares issuable in connection with the Transactions have been outstanding for the entirety of the period presented. |
97
Pro forma weighted-average common shares outstanding—basic and diluted is calculated as follows:
| Three Months Ended March 31, 2022 | ||||
Weighted-average shares calculation—basic and diluted | ||||
New Senti Class A common stock owned by Sponsors(1)(2) | 5,594,472 | |||
New Senti Class A common stock owned by public stockholders(1) | 9,321,491 | |||
Issuance of New Senti Class A common stock in connection with closing of the PIPE Investment (Note 5(f)) | 5,060,000 | |||
Issuance of New Senti Class A common stock to Convertible Note holders in connection with the Business Combination (Note 5(n)) | 517,500 | |||
Issuance of New Senti Class A common stock to Senti stockholders in connection with Business Combination(3) | 23,163,614 | |||
New Senti Class A common stock issued for Senti unvested restricted common stock subject to repurchase(3) | (288,801 | ) | ||
|
| |||
Pro forma weighted-average shares outstanding—basic and diluted | 43,368,276 | |||
|
| |||
| (1) | The New Senti Common Stock owned by Sponsors and public stockholders are derived as follows: |
| Note | DYNS Class A Common Stock subject to possible redemption | DYNS Class A Common Stock | DYNS Class B Common Stock | New Senti Class A Common Stock owned by public stockholders | New Senti Class A Common Stock owned by Sponsors | |||||||||||||||||||||||||||
DYNS historical common stock outstanding as of March 31, 2022 | 23,000,000 | 715,500 | 5,750,000 | |||||||||||||||||||||||||||||
Cancellation of 871,028 Class B Common Stock of DYNS and issuance of 871,028 Class A Common Stock of DYNS to the Anchor Investors | Notes 5(j) and 5(k) | (871,028 | ) | 871,028 | ||||||||||||||||||||||||||||
Reclassification to reflect shares of DYNS Class A Stock that were not redeemed to New Senti Class A Common Stock | Note 5(g) | (8,450,463 | ) | 8,450,463 | ||||||||||||||||||||||||||||
Conversion of the remaining DYNS Class B Common Stock (after the cancellation of 871,028 DYNS Class B Common Stock) to DYNS Class A Common Stock | Note 5(l) | 4,878,972 | (4,878,972 | ) | ||||||||||||||||||||||||||||
Reclassification of DYNS Class A Common Stock to New Senti Class A Common Stock. | Note 5(m) | (5,594,472 | ) | 5,594,472 | ||||||||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||||||||||
Total | 14,549,537 | — | — | 9,321,491 | 5,594,472 | |||||||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
| |||||||||||||||||||||||
98
| (2) | Shares of New Senti Class A common stock owned by the Sponsor does not take into account any distributions from the Sponsor that occurred in connection with the Closing. |
| (3) | New Senti Common Stock issued for Senti’s 1,475,731 shares of unvested restricted common stock subject to repurchase are excluded from the computation of basic and diluted earnings per share until the shares are no longer contingently returnable. |
99
Unless the context otherwise requires, for purposes of this section, the terms “we,” “us,” “the Company” or “Senti” refer to Senti and its subsidiaries.
Overview
We are a preclinical biotechnology company developing next-generation cell and gene therapies engineered with our gene circuit platform technologies to fight challenging diseases. Our mission is to create a new generation of smarter medicines that outmaneuver complex diseases using novel and unprecedented approaches. To accomplish this mission, we have built a synthetic biology platform that we believe may enable us to program next-generation cell and gene therapies with what we refer to as “gene circuits.” These gene circuits, which we created from novel and proprietary combinations of genetic parts, are designed to reprogram cells with biological logic to sense inputs, compute decisions and respond to their respective cellular environments. We aim to design and optimize gene circuits through our Design-Build-Test-Learn Engine, or DBTL Engine, to improve the “intelligence” of cell and gene therapies in order to enhance their therapeutic effectiveness against a broad range of diseases that conventional medicines are unable to address. Our gene circuit platform technologies are designed to be applied in a modality-agnostic manner, with applicability to natural killer (NK) cells, T cells, tumor infiltrating lymphocytes (TILs), stem cells including Hematopoietic Stem Cells (HSCs), in vivo gene therapy and messenger ribonucleic acid (mRNA). All of our current product candidates are in preclinical development. Our lead product candidates utilize off-the-shelf chimeric antigen receptor (CAR) NK cells outfitted with our gene circuit technologies in several oncology indications with currently high unmet need. Subject to the successful completion of IND- enabling studies, we expect to file investigational new drug applications, or INDs, for multiple product candidates starting in 2023.
The field of synthetic biology has evolved rapidly over the past few decades, and we believe that we are uniquely positioned to harness its potential to drive significant advances in medicine. Our scientific team is comprised of leaders in the space, and we have leveraged their expertise to create our scalable DBTL Engine and develop a proprietary knowledge database for therapeutic gene circuits. Our founders, Dr. Tim Lu, Dr. Philip Lee, Prof. James Collins, and Prof. Wilson Wong are pioneers in synthetic biology, gene circuits and cell and gene therapy, each having spent over twenty years advancing next-generation technologies in these areas. Our scientific founders and advisors are among the foremost leaders in their respective fields, having collectively published many of the seminal scientific papers in synthetic biology in top journals such as Nature, Science and Cell. Integrating disciplines from biology, chemistry and computer science, we have leveraged recent advances in DNA sequencing and synthesis, high-throughput experimentation and computational design, together with our intellectual property, to design, build and test gene circuits. We believe these are novel technologies, and we are not aware of U.S. Food and Drug Administration, or FDA, approved therapeutics utilizing similar technologies. As a result, these technologies may require significant resources in order to achieve regulatory approval. In preclinical studies, we have shown that our gene circuits are capable of carrying out sophisticated biological functions in a variety of disease models and we are preparing to advance our product candidates to clinical studies. We believe in the potential of gene circuits to enhance efficacy, precision and control of numerous cell and gene therapy products. Ultimately, we envision that cells running computations using our gene circuits in the human body will be able to outsmart a myriad of complex diseases.
100
The following figure illustrates how our gene circuit platform technologies may enable the creation of smarter medicines that can “sense inputs,” “compute decisions” and “respond with outputs” to impact diseases:
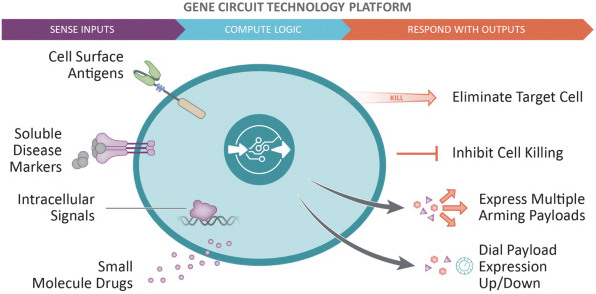
Key Challenges to Existing Disease Treatments and Our Gene Circuit Solutions
Key Challenges to Existing Disease Treatments
Diseases often involve complex biological interactions, which limit the effectiveness of existing therapeutics that only have single mechanisms of action and are unable to adapt to dynamic disease states. We characterize these key challenges in the following four categories:
 | Target Heterogeneity: Many diseases are heterogeneous and express antigens that are also present on healthy cells. The overlap of antigen expression on diseased and healthy cells limits the ability of existing therapies to target diseased cells at therapeutically relevant doses due to undesirable effects against healthy cells. For example, most cancers do not have a single antigen target that is uniformly expressed on all cancer cells with limited to no expression on non-cancerous cells. Thus, the ability to precisely distinguish between diseased cells and healthy cells has been a central challenge to date with current therapeutic approaches that do not encode logic, such as monoclonal antibodies, antibody-drug conjugates and single-target CAR therapies. Modalities that can respond to multiple biomarkers, rather than just a single one, have the potential to open up the opportunity for more precise and efficacious medicines. | |
 | Disease Evasion: Disease pathologies are multifaceted. For example, diseases can evade the immune system or acquire resistance to single-target treatments by activating other biological pathways. The tumor microenvironment (TME) of many solid tumors suppresses cancer-fighting immune cells via multiple pathways. To overcome these complex barriers, combination therapies that utilize multiple individual drugs are being explored clinically. However, manufacturing issues, regulatory aspects, pharmacology complexities and clinical challenges of using multiple individual drugs together can be difficult. A gene or cell therapy with the ability to activate multiple anti-tumor pathways within a single product could help limit disease evasion and may improve the durability of responses to treatment, while simplifying the translational path. | |
101
 | Narrow Therapeutic Window: Once administered to a patient, conventional medicines, including cell and gene therapies, cannot be tuned up or down, which makes it difficult to find the optimal dose, especially for diseases that have a narrow therapeutic window. The ability to create therapeutics that can be titrated or regulated in vivo in the patient may lead to enhanced efficacy and safety. | |
 | Dynamic Disease Conditions: Disease conditions are dynamic and vary in space and time. For example, diseases may manifest only in certain tissues, or have a waxing and waning progression over time. Conventional therapies are (i) static, (ii) have a predefined activity around a single mechanism of action that cannot be modified post-administration and (iii) do not adapt to these dynamic conditions, thus limiting their efficacy, specificity and safety. For example, current cell and gene therapies are not dynamic or highly specific, thus limiting the indications that they can address. Developing dynamic therapeutics that are able to sense, and respond to, these spatially or temporally varying conditions would address this challenge. | |
Our Gene Circuit Solutions
We believe that our core gene circuit platform technologies may enable us to engineer smarter medicines. These technologies can be categorized as follows.
 | Logic Gating: Logic Gating gene circuits are designed to enable cell and gene therapies to control their therapeutic activity in response to the presence or absence of multiple disease biomarkers. Below are examples of Logic Gates applied to cancer, although Logic Gating may also be applied to various other disease indications. | |||
| NOT GATE: NOT GATE gene circuits are designed to widen the therapeutic window by enabling effective killing of cancer cells while preserving healthy cells. The NOT GATE functions by recognizing Safety Antigens (SAs), or antigens that are selectively expressed on healthy cells and not on cancer cells, thus limiting on-target, off-tumor killing. By protecting healthy cells, the NOT GATE has the potential to enable more effective on-target, on-tumor killing of tumor cells that express Tumor-Associated Antigens (TAAs). Generally, existing cancer drugs target only a single antigen, which means they can only be effectively and safely used in situations where that antigen is uniquely expressed on tumors and not in healthy cells, or where the on-target, off-tumor effects are tolerable. | |||
 | OR GATE: OR GATE gene circuits are designed to address tumor heterogeneity and limit antigen escape. The OR GATE functions by killing tumor cells that express any one of multiple antigens. Generally, current medicines are unable to address more than one target at a time and are thus susceptible to tumor evasion. | |||
 | AND GATE: AND GATE gene circuits require that multiple targets be present at the same time to trigger killing of cancer cells, which may enhance the specificity of on-target, on-tumor activity. Generally, conventional therapies only recognize a single antigen for their activity, which can result in a lack of specificity. | |||
| Multi-Arming: Multi-Arming gene circuits are designed to incorporate multiple payloads into a single cell or gene therapy product. These gene circuits are intended to activate various biological pathways in complementary ways to prevent diseases from evading single-target treatments, and thereby potentially improve treatment efficacy. Existing combination therapies that target complex diseases require the application of multiple individual drugs, which is difficult due to research, clinical development, regulatory and pharmacology barriers. | |||
102
| Regulator Dial: Regulator Dial gene circuits are designed to enable the precise tuning of therapeutic activity from a cell or gene therapy product. For example, this can be implemented by regulating therapeutic payload expression in response to varying concentrations of FDA-approved drugs. Regulator Dials are expected to enable the exogenous regulation of next-generation cell and gene therapies even after they have been delivered in vivo. Existing cell and gene therapies cannot be modulated once they have been delivered into patients. | |||
| Smart Sensor: A Smart Sensor is a gene circuit, or combination of gene circuits, designed to precisely detect distinct cell types or disease environments, and thus distinguish between the “disease state” and “healthy state.” For example, Smart Sensors can be engineered to detect whether certain conditions, or disease biomarkers, are present before responding with a specific therapeutic response. Conventional medicines are generally unable to dynamically change their behavior in response to cell or disease specific conditions. | |||
We believe we can rationally combine any of these four gene circuit platform technologies to strategically customize therapeutics to outmaneuver complex diseases. The following figure maps how our gene circuit platform technologies are designed to address specific challenges facing existing medicines:
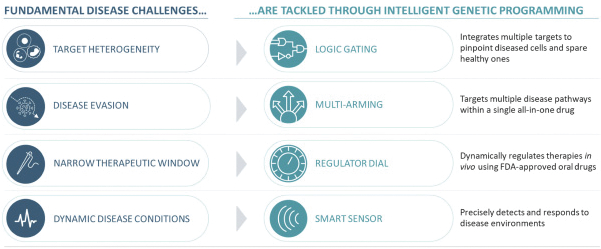
We Believe Our Gene Circuits May Have Broad Applicability in Multiple Treatment Modalities and Disease Areas
Treatment Modalities: Our gene circuit biological “software” can be used to program numerous cell and gene therapy products, or “hardware.” Specifically, these modalities include NK cells, T cells, TILs, stem cells including HSCs, in vivo gene therapy and mRNA.
We have conducted research in multiple cell types and vector types, and the initial focus of our internal pipeline is implementing gene circuits within off-the-shelf CAR-NK cells in oncology.
Disease Areas: We believe our gene circuits can be customized to address many aspects of disease biology. We have demonstrated and published on applications of gene circuits across many different in vivo disease models. Thus, we believe that our gene circuit platform technologies have the potential to be used for a broad range of diseases that span therapeutic areas such as oncology, immunology, genetic diseases, neurology, cardiology, metabolic diseases, ophthalmology and regenerative medicine.
103
The following figure presents our perspective on how our gene circuit technologies can be utilized across modalities and corresponding therapeutic areas:
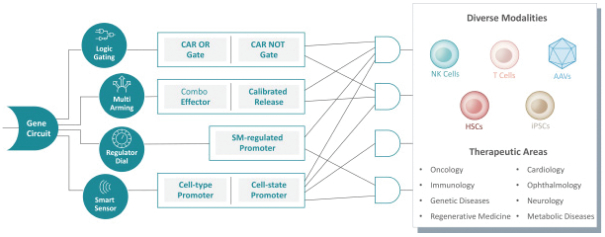
We Utilize Our Design-Build-Test-Learn Engine to Optimize Our Gene Circuits
We have established, and continue to scale, our powerful DBTL Engine to generate our therapeutic gene circuits. We believe the speed, quantity and quality by which we can design multiple types of gene circuits, resulting in thousands of functional gene circuits engineered to date, is unique to our platform. Our gene circuits are engineered by an expert team of synthetic biologists informed by proprietary bioinformatics and our internal gene circuits knowledge database. This proprietary knowledge database contains quantitative characterization data on gene circuits we have previously built, including those that are functional and those that are not. Thus, this database helps inform the design of future gene circuits guided by our past experiences. Furthermore, we leverage machine learning approaches to continually enhance the design of such gene circuits based on data generated through testing in our in vitro and in vivo disease models. The breadth and scale of our DBTL Engine allows us to learn from each cycle of design to improve the speed and quality of future designs—even across projects and modalities. This approach leverages and reinforces our position as leaders and innovators in the field of synthetic biology for the development of human therapeutics. Based on decades of experience among our founders as well as the accumulated data from our DBTL Engine, we believe that our approach to programming gene circuits is broadly applicable toward engineering optimal efficacy, precision and control into many cell or gene-based medicines.
104
The following figure provides an overview of the key steps in our DBTL Engine process:
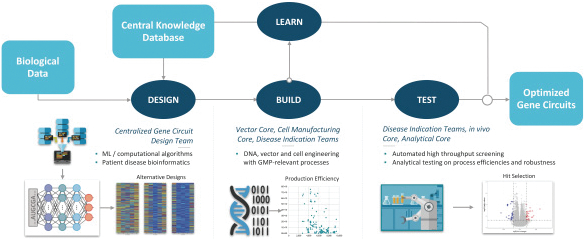
Our Pipeline and Product Candidates
We believe that our gene circuits will enable us to better address indications that conventional small molecule, protein and cell and gene therapies cannot. We intend to seek feedback from the FDA and comparable regulatory authorities given the novelty of our technologies, which could make the regulatory pathway more complex and potentially time-consuming than for more well-known therapeutics. Our most advanced gene-circuit product candidates are directed at off-the-shelf CAR-NK cells for oncology. In addition to these product candidates, we have discovery stage product candidates focused on gene therapies for tissue-directed targets and cell therapies for regenerative medicines. The following pipeline chart depicts our preclinical stage product candidates.
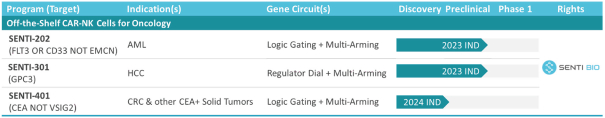
SENTI-202
We are developing our SENTI-202 product candidate as a Logic Gated (OR + NOT) off-the-shelf CAR-NK cell therapy designed to target and eliminate acute myeloid leukemia, or AML, cells while sparing the healthy hematopoietic stem cells. We are engineering SENTI-202 to express a bivalent CAR as an OR GATE directed against the Tumor-Associated Antigens, Fms-like tyrosine kinase 3 (FLT3) and/or Cluster of Differentiation 33 (CD33), where one or both are expressed in 95% of AML patients. FLT3 is robustly expressed on leukemic stem cells, or LSCs, while CD33 is highly expressed on AML blasts. AML is a heterogeneous disease composed of both AML LSCs and blasts. Thus, we believe that targeting FLT3 OR CD33 will enhance the overall killing activity against diseased cells in AML. However, FLT3 is also expressed on healthy hematopoietic stem cells, or HSCs, in the bone marrow. In order to spare FLT3-expressing healthy HSCs, we have further engineered SENTI-202 with a NOT GATE gene circuit comprised of an inhibitory CAR, or iCAR, targeted against endomucin, or EMCN. EMCN is a Safety Antigen with robust expression on HSCs and no or low expression on AML LSCs and
105
blasts. We believe this NOT GATE gene circuit could allow SENTI-202 to eliminate LSCs that cause relapse while preserving the patient’s own healthy HSCs. This proprietary product profile has the potential to drive towards deeper and longer remissions for AML by enabling killing of diverse AML cells while sparing HSCs that regenerate the blood and the immune systems. We are also engineering SENTI-202 with an aim to express our proprietary calibrated release interleukin 15, or crIL-15. Our crIL-15 construct is being designed to simultaneously produce both membrane-associated and fully-secreted IL-15 proteins in order to simultaneously stimulate surrounding immune cells and promote NK cell expansion, persistence and tumor killing.
In 2022, we plan to present IND-enabling pharmacological data at key scientific conferences. In 2023, we plan to submit an IND application to support the clinical evaluation of SENTI-202.
SENTI-301
Our SENTI-301 product candidate is a Multi-Armed off-the-shelf CAR-NK cell therapy that we are developing for the treatment of advanced hepatocellular carcinoma, or HCC. We are engineering NK cells to target glypican 3, or GPC3, which is highly expressed in 70% to 90% of HCCs and has low or no expression on normal adult tissues. SENTI-301 is armed with a combination of immuno-stimulatory payloads intended to promote expansion and persistence of our CAR NK cells, as well as activation and recruitment of endogenous immune cells into the solid tumor microenvironment for enhanced anti-tumor activity. One of the immuno-stimulatory payloads is our proprietary crIL-15 protein. crIL-15 is designed to simultaneously stimulate surrounding immune cells and promote NK cell expansion, persistence and tumor killing.Expression of our proprietary calibrated release interleukin 12, or crIL-12, is modulated via a small-molecule Regulator Dial gene circuit, and has the potential to stimulate the immune system and overcome the challenges of the immunosuppressive TME in HCC.
In 2022, we plan to present IND-enabling pharmacological data at key scientific conferences. In 2023, we plan to submit an IND application to support the clinical evaluation of SENTI-301.
SENTI-401
Our SENTI-401 product candidate is a Logic Gated off-the-shelf CAR-NK cell therapy that we are developing to more precisely target and eliminate colorectal cancer, or CRC, cells while sparing healthy cells elsewhere in the body. We are engineering NK cells to express a CAR directed against carcinoembryonic antigen, or CEA, which is highly overexpressed in 85% to 90% of colorectal cancer but is also expressed in epithelial cells in healthy tissues. CEA is also expressed in other solid tumors, including lung, breast and gastric cancers. The expression profile of CEA in both tumor and healthy cells has resulted in on-target, off-tumor toxicities with conventional CEA-targeted therapies, thus limiting their clinical success. To address this challenge, we are engineering SENTI-401 with a NOT GATE implemented via an iCAR targeted against an epithelial cell Safety Antigen called V-set and Immunoglobulin Domain Containing 2, or VSIG2. Thus, the SENTI-401 product candidate’s Logic Gating is intended to more effectively treat CRC patients by targeting a well-known Tumor-Associated Antigen, CEA, and widen the therapeutic window by preventing killing when CEA appears on healthy cells that also express the VSIG2 Safety Antigen. We are also engineering SENTI-401 to express a combination of potent immune effectors, including our proprietary crIL-15 protein to simultaneously stimulate surrounding immune cells and promote NK cell expansion, persistence and tumor killing, and an additional undisclosed potent immune effector to potentially enhance therapeutic function in solid tumors.
In 2023, we plan to present IND-enabling pharmacological data at key scientific conferences. In 2024, we plan to submit an IND application to support the clinical evaluation of SENTI-401.
106
Our Discovery Stage Programs
Our current discovery stage programs are as follows:
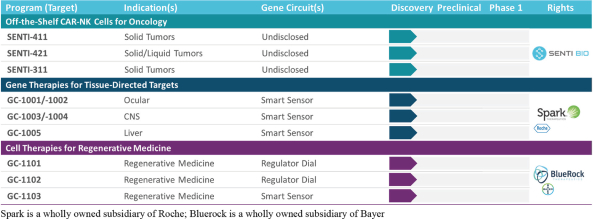
We believe our gene circuits can be readily adapted to new disease contexts to enable a variety of additional CAR-NK product candidates that address important cancers. Our SENTI-411, SENTI-421, and SENTI-311 product candidates are additional off-the-shelf CAR-NK cell therapies for solid and liquid tumors. These product candidates may leverage the gene circuits being developed for our SENTI-202, SENTI-301, and SENTI-401 CAR-NK cells, along with the learnings from our DBTL Engine, to tackle key challenges in oncology, such as Target Heterogeneity and Disease Evasion.
Furthermore, we are actively pursuing the nomination and development of multiple product candidates that harness the full breadth of our gene circuit platform beyond Logic Gating and Multi-Arming of off-the-shelf CAR-NK cells within oncology. In particular, we have entered into collaborations with Spark Therapeutics, Inc. (acquired by Roche Holding AG) for the design of Smart Sensors for disease- and tissue-specific gene therapy, and with Bluerock Therapeutics LP (acquired by Bayer AG) for the use of Smart Sensors and Regulator Dials for regenerative medicines.
Our Gene Circuit Application to Off-the-Shelf NK Cells for Oncology
Our initial pipeline focus is on the application of our gene circuit platform technologies towards improving the treatment of specific oncology indications. Our most advanced product candidates are off-the-shelf, gene circuit-engineered CAR-NK cells. We have chosen to engineer NK cells with our gene circuits based on our belief that NK cells confer the following advantages in relation to other potential immune cell types in oncology:
| • | Innate Killing: NK cells naturally carry multiple activating and inhibitory receptors that enable them to innately kill tumor cells while sparing healthy tissues. Furthermore, NK cells have been engineered with CARs to enhance their targeted killing activity. We leverage these features to create Logic Gated CAR-NKs, such as OR GATE CAR-NKs that enhance the killing of heterogeneous tumors and NOT GATE CAR-NKs that spare healthy cells from undesired toxicity and thereby potentially improve on-target, on-tumor killing. |
107
| • | Immune Activation: NK cells have been shown to support robust activation of anti-tumor immune pathways via proinflammatory cytokine and chemokine secretion. We leverage this feature with our Multi-Arming gene circuits to further improve their ability to trigger endogenous, complementary anti-tumor activity by engaging the rest of the tumor immunity cycle. |
| • | Validated Clinical Activity and Tolerability: Off-the-shelf, as in healthy donor-derived, CAR-NK cells have been recently shown in the clinical setting to have the potential to promote effective anti-tumor activity along with low risks of graft versus host disease, or GvHD, severe cytokine release syndrome, or CRS, and neurotoxicity. |
| • | Off-the-Shelf Manufacturing for Broad Patient Access: We have established proprietary protocols to derive NK cells from healthy donors, manufacture them at scale with a projected low cost, and cryopreserve them with high retained viability post-thaw. As a result, we believe that CAR-NK cells have the potential to be broadly accessible to patients as they may be delivered rapidly to patients in an off-the-shelf manner and in an outpatient setting. |
Our Calibrated Release (cr) Technology
Current technologies for arming immune cells with cytokines are limited to either expressing the fully secreted natural form of the protein to support trans- or paracrine signaling, or expressing a membrane-tethered version to promote cis- or autocrine signaling. As a result, we believe these first-generation constructs are unable to efficiently stimulate the engineered cell product and surrounding immune cells, such as those cells from the endogenous immune system, at the same time.
We have created a novel engineered protein technology called calibrated release (cr). We are using this approach to improve IL-15 and IL-12 signaling in our CAR-NK platform. Our crIL-15 engineered cytokine is tethered to the NK cell surface via a cleavable linker that can be cut off by a ubiquitously expressed protease on the cell surface of NK cells. The rate of linker cleavage can be calibrated by engineering the sensitivity of the cleavable linker sequence to the cell surface protease, enabling us to tune the ratio of membrane-tethered versus fully secreted protein. Our current CAR -NK products utilize crIL-15 to simultaneously stimulate surrounding immune cells and promote NK cell expansion, persistence and tumor killing. crIL-12 is utilized in the SENTI-301 product candidate to potentially stimulate the immune system and overcome the challenges of immunosuppressive TME in HCC.
We Are Building Manufacturing Capabilities That May Enable Production of Off-The-Shelf Cell Therapies
Capitalize manufacturing capabilities are central to our business strategy, since they can enable us to control the quality and supply of our off-the-shelf CAR-NK cell therapies for clinical studies and ultimately commercialization. A key advantage of off-the-shelf cell therapies, versus autologous products that use each patient’s own cells, is the ability to manufacture large batches of drug product from healthy donor cells that can be produced in advance of clinical use, and then stored in frozen vials. Upon commercialization, we expect to be able to make our cell therapies, if approved, broadly accessible in an off-the-shelf manner to cancer patients.
Our corporate headquarters is located in South San Francisco, CA, where we lease approximately 40,000 square feet of research and development and corporate office space. In this location, we have approximately 10,000 square feet dedicated to manufacturing development labs. We have established research and development teams with extensive experience in cell and gene therapy manufacturing operations, including vector process development, cell process development, analytical development, quality control and quality assurance. In June 2021, we signed a lease agreement for approximately 92,000 square feet in Alameda, California and have commenced construction of a Current Good Manufacturing Practices, or cGMP, facility to support clinical and commercial-scale manufacturing of multiple off-the-shelf CAR-NK cell product candidates.
This manufacturing facility is being designed as a customized end-to-end manufacturing solution to give us the ability to isolate NK cells, engineer these cells with proprietary gene circuits, perform cell culture expansion
108
in large batches, and cryopreserve and store the final cGMP products. We anticipate that this facility will become operational in time to support initial clinical trials for our lead product candidates. We plan to leverage the latest cell therapy manufacturing technologies as we strive to optimize quality, maximize scalability and minimize cost. Our initial manufacturing efforts will focus on our two lead product candidates, SENTI-202 and SENTI-301.
We expect cGMP manufacturing facility startup by the end of 2022 and to present an overview of our clinical-scale GMP manufacturing process for gene-circuit-engineered NK cells at key technical conferences in 2022.
We may also leverage our manufacturing facility to expand the application of our gene circuit technology to biomanufacturing in partnership with one or more third parties.
Our experienced manufacturing and technical operations team has established an innovative process with the potential for efficient and scalable production of our off-the-shelf CAR-NK cell product candidates. Critical aspects of the cell manufacturing process include the ability to perform the four key steps in the CAR-NK cell manufacturing process as outlined below:
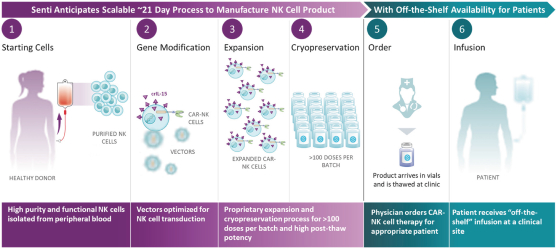
Step 1: Source, Isolate and Bank Purified NK Cells as Starting Cells: Starting Cells are obtained from enriching and isolating NK cells from qualified healthy donors.
Step 2: Genetically Engineer Starting Cells with Gene Circuits: We genetically modify our NK cells through a viral vector transduction process focused on enhancing gene circuit expression while minimizing impacts on compromising cell viability or cell expansion.
Step 3: Expand and Scale CAR-NK Cells: Our expansion process is designed to generate large numbers of final product doses per manufacturing batch.
Step 4: Formulate and Cryopreserve CAR-NK Cells: For storage and distribution, we will formulate and cryopreserve our final product to retain viability, persistence and cytotoxic function post-thaw for off-the-shelf use.
Our Team and Investors
Since our founding in 2016, we have built a team of industry-leading experts, including scientists, engineers, advisors and company-builders—all with a deep knowledge of synthetic biology, gene circuits and cell and gene therapy.
109
Technology Experts and Company Builders. Our founders, Dr. Tim Lu and Dr. Philip Lee are seasoned experts at identifying and building transformative technologies and companies. Dr. Lu is a pioneer in synthetic biology with strong ties to Harvard University, where he received his M.D., and the Massachusetts Institute of Technology, or MIT, where he received his Ph.D. in Electrical and Biomedical Engineering and started his academic lab in 2010. Dr. Lu is a co-founder of multiple therapeutics platform companies including Synlogic, Tango Therapeutics, Eligo Bioscience, BiomX, and Engine Biosciences. Dr. Philip Lee is an entrepreneur and technology platform builder specializing in cellular systems. He received his Ph.D. in Bioengineering from the University of California, Berkeley and the University of California, San Francisco, and Bachelor of Science, or BS, degrees in Chemical Engineering and Biology from MIT. Dr. Philip Lee was a co-founder of CellASIC, which was acquired by MilliporeSigma, division of Merck KGaA, where he subsequently served as the Head of Cell Culture Systems.
Groundbreaking Scientists, Clinicians and Drug Developers. Throughout our company are passionate individuals with deep R&D, translational, regulatory and manufacturing knowledge in the fields of synthetic biology, gene circuits and cell and gene therapy. We have numerous scientists and scientific advisors who have made critical discoveries and contributions to the fields of cell and gene therapy. As of June 23, 2022, 33 of our employees hold Ph.D. or M.D. degrees. Our scientific co-founders include Dr. Jim Collins of MIT, one of the founders of the field of synthetic biology, who has the rare distinction of being elected to all three national academies—the National Academy of Sciences, National Academy of Engineering and National Academy of Medicine—and has received a number of major awards recognizing his work, including the Dickson Prize in Medicine. Additionally, we are also advised by our scientific co-founder, Dr. Wilson Wong of Boston University, who is considered an expert in immune cell engineering and synthetic biology for therapeutic applications, and Dr. Ahmad Khalil of Boston University, who is considered an expert in transcription factor engineering for mammalian synthetic biology applications. We are also advised by Dr. Martin Fussenegger of ETH Zurich, who is considered a pioneer in therapeutic synthetic biology and a member of the National Academy of Engineering, and who is the recipient of numerous honors including the AIChE Bailey Award and the Merck Cell Culture Engineering Award. Our Chief Medical Advisor, Dr. Jose Iglesias, has over 30 years of experience in cancer drug clinical development. We are advised by experienced oncology clinicians, including Dr. Lawrence Fong of UCSF, who has been focused on cancer immunotherapy for two decades and has been involved in both preclinical and clinical studies of FDA-approved immunotherapies including sipuleucel-T and immune checkpoint inhibitors, and Dr. Michael Andreeff of M.D. Anderson Cancer Center, who has worked extensively on drug resistance in hematopoietic malignancies, such as AML, and developed or co-developed several new therapeutic agents. Additionally, in 2021, we added three more advisors who are leaders in the fields of immunotherapy drug discovery and development, and commercial oncology therapeutics. Dr. Michael Kalos, an independent consultant, is an internationally recognized expert in T cell therapy, oncology vaccines and immuno-oncology with experience in both industry and academia. Dr. Robin Taylor, an independent consultant, has two decades of biopharma experience in global development and commercialization of oncology drugs. Dr. Michael Varney, an independent consultant, is a pioneer drug discoverer and biotech leader who has led research and early drug development efforts at Genentech, Pfizer and Agouron.
Our Strategy
Our goal is to become an industry leader in the cell and gene therapy landscape. We are pursuing this goal by advancing our gene circuit platform to discover, develop, manufacture and globally commercialize new classes of cell and gene therapies across therapeutic areas and modalities. To achieve this, we have strategically focused on designing therapeutics to address specific challenges that confound existing disease treatments. We aim to provide smarter medicines to patients, and to execute on this strategy we will continue to build on our extensive capabilities by:
| • | Advancing our portfolio of off-the-shelf CAR-NK cell product candidates into clinical development. |
| • | Expanding our discovery stage pipeline and advancing select product candidates into the clinic. |
110
| • | Driving innovation in our leading gene circuit platform and expanding the breadth of our technology and capabilities. |
| • | Building clinical and commercial-scale manufacturing capabilities for our CAR-NK cell product candidates. |
| • | Maximizing the commercial potential of our gene circuit platform technologies via strategic collaborations. |
The Need for Synthetic Biology-Based Gene Circuits
For the human body to maintain proper function, cells constantly sense and interpret a variety of inputs, or biological signals, to produce outputs, or biological responses. Diseases emerge when the balance between these biological inputs and outputs become inadequate or inappropriate to maintain a healthy state. Furthermore, diseases can evolve or mutate to evade the human body’s natural defense mechanisms that normally serve as a check against these imbalances. Thus, many diseases progress when the intrinsic ability of cells in the human body to rebalance healthy physiology is insufficient or becomes overactive. We believe that programming cells to better sense and react to disease environments has the potential to enhance our ability to treat diseases and restore healthy phenotypes.
Traditional medicines, such as small molecules and biologics, typically target proteins and block their function. We consider these medicines to be static because they have a predefined activity around a single mechanism of action that cannot be modulated once administered. With some exceptions, most traditional medicines primarily treat disease symptoms or sub-optimally address the underlying disease biology, thus failing to achieve durable cures. In addition, some traditional medicines have on-target, off-tissue effects that limit therapeutic windows and cause safety concerns.
There have been remarkable advances in technologies for reading (sequencing) and writing (synthesizing) DNA over the past few decades. These technologies have aided the biopharmaceutical industry in identifying disease mechanisms and have enabled the programming of cell and gene therapies.
As transformative as the early generations of cell and gene therapies have been, they are currently confined to narrow applications and have been proven effective against only a few monogenic diseases and hematological malignancies. These current approaches are limited to sensing and correcting single disease signatures while providing little control over their dosage, timing or localization. Thus, diseases that are dynamic or multifactorial cannot be readily addressed by existing cell and gene therapy products.
Using our gene circuits, we believe we can design more intelligent cell and gene therapies that (i) can precisely target heterogeneous diseases using Logic Gating, (ii) can be Multi-Armed with complementary payloads to overcome disease evasion, (iii) can be controlled in vivo using Regulator Dials to overcome narrow therapeutic windows and (iv) are equipped with Smart Sensors that dynamically detect disease environments.
We believe that by leveraging synthetic biology to engineer gene circuit-enabled cell and gene therapies, we will be able to overcome the shortcomings of the early generations of these genetic medicines.
Our Platform: The Opportunity for Gene Circuits
We believe that our gene circuit platform technologies are modality-agnostic and can be deployed in any cell and gene therapy product candidate to improve efficacy, safety and control. Fundamentally, gene circuits reprogram cells to sense key biological signals, compute based on this information and dynamically respond with multiple therapeutic outputs. In contrast to existing single-target or static medicines, this sense-compute-respond paradigm has the potential to enable precise and highly active medicines that can address the complex and dynamic mechanisms underlying important diseases.
111
Our Gene Circuit Platform Technologies
In our pursuit to create a new generation of smarter medicines, we have built a toolbox of proprietary gene circuit platform technologies that we believe may enhance the risk benefit paradigm of cell and gene therapy products. We are initially focused on four core categories of gene circuits to develop our current and future programs: (i) Logic Gating, (ii) Multi-Arming, (iii) Regulator Dials and (iv) Smart Sensors. Each of our gene circuit platform technologies is designed to confer greater clinical and therapeutic activity, precision and control to cell and gene therapies.
We believe that our core gene circuit platform technologies may enable us to engineer smarter medicines and can be categorized as follows:
 | Logic Gating: Logic Gating gene circuits are designed to enable cell and gene therapies to control their therapeutic activity in response to the presence or absence of multiple disease biomarkers. Below are examples of Logic Gates applied to cancer, although Logic Gating may be applied to various other disease indications as well. | |||
| NOT GATE: NOT GATE gene circuits are designed to widen the therapeutic window by enabling effective killing of cancer cells while preserving healthy cells. The NOT GATE functions by recognizing Safety Antigens, or antigens that are selectively expressed on healthy cells and not on cancer cells, thus limiting on-target, off-tumor killing. By protecting healthy cells, the NOT GATE has the potential to enable more effective on-target, on-tumor killing of tumor cells that express Tumor-Associated Antigens. Generally, existing cancer drugs target only a single antigen, which means they can only be effectively and safely used in situations where that antigen is uniquely expressed on tumors and not in healthy cells, or where the on-target, off-tumor effects are tolerable. | |||
 | OR GATE: OR GATE gene circuits are designed to address tumor heterogeneity and limit antigen escape. The OR GATE functions by killing tumor cells that express any one of multiple antigens. Generally, current medicines are unable to address more than one target at a time and are thus susceptible to tumor evasion. | |||
 | AND GATE: AND GATE gene circuits require that multiple targets be present at the same time to trigger killing of cancer cells, which may enhance the specificity of on-target, on-tumor activity. Generally, conventional therapies only recognize a single antigen for their activity, which can result in a lack of specificity. | |||
| Multi-Arming: Multi-Arming gene circuits are designed to incorporate multiple potent immune effectors into a single cell or gene therapy product. These gene circuits are intended to activate various biological pathways in complementary ways to prevent diseases from evading single-target treatments, and thereby potentially improve treatment efficacy. Existing combination therapies that target complex diseases require the application of multiple individual drugs, which is difficult due to research, clinical development, regulatory and pharmacology barriers. | |||
| Regulator Dial: Regulator Dial gene circuits are designed to enable the precise tuning of therapeutic activity from a cell or gene therapy product. For example, this can be implemented by regulating therapeutic immune effector expression in response to varying concentrations of FDA-approved drugs. Regulator Dials are expected to enable the exogenous regulation of next- generation cell and gene therapies even after they have been delivered in vivo. Existing cell and gene therapies cannot be modulated once they have been delivered into patients. | |||
| Smart Sensor: A Smart Sensor is a gene circuit, or combination of gene circuits, designed to precisely detect cell type or disease environments, and thus distinguish between the “disease state” and “healthy state.” For example, Smart Sensors can be engineered to detect whether certain conditions, or disease biomarkers, are present before responding with a specific therapeutic response. Conventional medicines are generally unable to dynamically change their behavior in response to cell or disease specific conditions. | |||
112
We believe we can rationally combine any one of these four gene circuit platform technologies to strategically customize therapeutics to outmaneuver complex diseases.
 | Logic Gating |
Logic Gating gene circuits are designed to enable cell and gene therapies to control their therapeutic activity in response to the presence or absence of multiple disease biomarkers. This capability has the potential to enable more accurate and efficient targeting of heterogeneous diseased cells while sparing healthy ones. Our initial product candidates for oncology will utilize our NOT GATE and OR GATE gene circuit technology. Furthermore, we believe this technology can be utilized across a broad range of oncology indications. To this end, we have established a proprietary Tumor-Associated Antigen and Safety Antigen Paired Discovery Platform that enables the expansion of our Logic Gating approach against novel Tumor-Associated Antigen and Safety Antigen pairs across multiple cancer indications.
The figure below illustrates the behavior of our Logic Gating gene circuit technologies in CAR-NK cells:
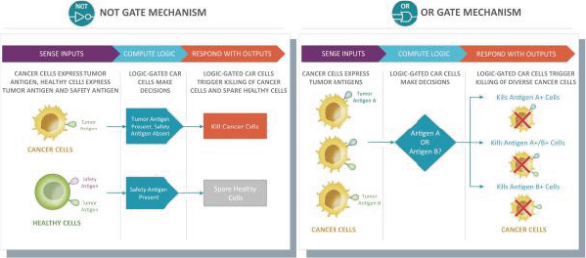
 | NOT GATE |
Background: The Need for Precision Targeting
The expression of a single CAR in T cells or NK cells can redirect them to kill cancer cells that express a specific surface antigen. This technology has led to breakthrough therapies for B cell malignancies and multiple myeloma, where targeting of tissue-lineage antigens – CD19 or B Cell Maturation Antigen, or BCMA – rather than Tumor-Associated Antigens, is tolerated. Beyond these initial applications, the lack of uniquely specific tumor antigens presents a great challenge since on-target, off-tumor toxicity to vital tissues significantly limits the cancer indications addressable by single-target CAR-NK or CAR-T therapies. Similar limitations are faced by monoclonal antibodies and antibody-drug conjugates that rely on a single target to discriminate cancer cells from healthy ones.
113
Our Logic Gating Solution: NOT GATE
The application of CAR-immune cells may be broadened to many cancer types if recognition of a Safety Antigen that is selectively expressed on healthy cells, but not on cancer cells, could selectively block killing against the healthy cells. We believe this feature enables a widened therapeutic window and aggressive treatment of cancers with the potential for enhanced efficacy and reduced risk of undesirable side effects, as well as the expansion of cell therapies into cancer indications where there are no ideal Tumor-Associated Antigens.
As shown in the figure below, we have engineered NK cells with a synthetic NOT GATE gene circuit, where an activating CAR, or aCAR, can drive the killing of cancer cells presenting an activating, Tumor-Associated Antigen, shown in green, while an inhibitory CAR, or iCAR, can suppress cytotoxicity against normal healthy cells that express both the activating Tumor-Associated Antigen and a Safety Antigen, shown in purple.

Selected NOT GATE Proof-of-Concept Data
Our NOT GATE is implemented with iCARs, which consist of a Safety Antigen-binding domain and a functional intracellular domain derived from the cytoplasmic tails of inhibitory co-receptors containing immunoreceptor tyrosine-based inhibitory motifs, or ITIMs, which are selected from a library of ITIMs upon testing and evaluation. When a Logic Gated CAR-NK cell encounters a target cell and associates with its cell surface antigens, the aCAR and iCAR “sense” these inputs and provide activating or inhibitory signals into the Logic Gated CAR-NK cell, respectively. Specifically, engagement of the aCAR alone with an activating, Tumor-Associated Antigen triggers an activating signal cascade in the CAR-NK cells that release cytotoxic mediators to kill the cancer cells. When the iCAR recognizes a certain Safety Antigen that is preferentially expressed on healthy cells, an inhibitory signal cascade is triggered in the CAR-NK cells to block the cytotoxic response, thus sparing the healthy cells.
In vivo functional demonstration of our NOT GATE gene circuit is illustrated in the figure below. A group of mice that received xenotransplantation of model Healthy Cells and model Cancer Cells at a ratio of 50:50 were treated with NOT GATE CAR-NK cells that contained an aCAR that recognizes the tumor-associated antigen on the model Healthy Cells and the model Cancer Cells, and that also contain an iCAR that recognizes the Safety Antigen on the model Healthy Cells. These mice were also treated with Control CAR-NK cells, which contain an aCAR that recognizes the tumor-associated antigen but do not contain an iCAR that recognizes the Safety Antigen on the model Healthy Cells. The Control CAR-NK cells indiscriminately killed both the model Healthy Cells and model Cancer Cells in mice. Conversely, the NOT GATE CAR-NK cells selectively killed the model Cancer Cells, while sparing the model Healthy Cells. Further analysis showed that treatment with NOT GATE
114
CAR-NK cells resulted in significant enrichment of model Healthy Cells in these mice, up from 50% at baseline to approximately 95% after treatment. This data demonstrates that NOT GATE CAR-NK cells can spare model Healthy Cells while maintaining killing of model Cancer Cells in vivo.
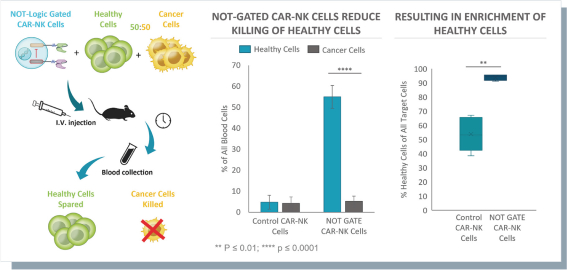
Future Areas of Applications and Alternate Gene Circuits
We believe the enhanced precision enabled by our NOT GATE gene circuit may improve the therapeutic window, and thus the potential efficacy and safety, of our product candidates against the cancer types in our pipeline. Furthermore, the NOT GATE has the potential to significantly increase the applicability of CAR-NK cells against a wide range of liquid and solid tumors that currently do not have ideal Tumor-Associated Antigen targets and are thus currently unaddressed.
 | OR GATE |
Background: The Need for Targeting Multiple Antigens
Many cancers are heterogeneous, making it difficult to treat them by only targeting a single antigen. For example, the development of targeted AML treatments is difficult due to more than 200 types of chromosome translocations and mutations having been identified in patients. Thus, therapies targeting a single AML-associated antigen are often insufficient to kill all of the tumor subsets, including both AML LSCs and blasts. Consequently, most AML patients treated with these therapies die from disease relapse and progression due to incomplete therapeutic activity. Additionally, due to the highly mutagenic nature of cancer cells, targeting single antigens allows for cancers to more easily escape or acquire resistance to treatment. For example, while recent triumphs of CD19-directed autologous CAR-T therapies have brought renewed hope to patients with relapsed/refractory B cell malignancies, up to 50% of patients with pre-B cell acute lymphoblastic leukemia, or ALL, suffer disease relapse within twelve months after treatment. Many of those patients who relapse toward the latter end of the twelve-month period have cancers that have been associated with loss of the CD19 epitope.
These clinical observations demonstrate the potential benefit of developing therapeutics that are capable of simultaneously targeting multiple Tumor-Associated Antigens across heterogeneous cancers using OR GATE gene circuit technology.
115
Our Solution and Selected Proof-of-Concept Data: OR GATE
OR GATE gene circuits are designed to simultaneously target multiple Tumor-Associated Antigens. As an example of our OR GATE gene circuits, we have evaluated two forms of OR GATE gene circuits to support our SENTI-202 product candidate, a bicistronic dual CAR architecture and a bivalent CAR architecture.
Bicistronic dual CAR: The bicistronic dual CAR is designed to express two CAR molecules directed against FLT3 and CD33, respectively, two Tumor-Associated Antigens where one or both are expressed in 95% of AML patients. Because CD33 is highly expressed on AML blasts, and FLT3 is highly expressed on LSCs, SENTI-202 offers the potential for elimination of both AML tumor subsets. Using our DBTL Engine, we systematically optimized our OR GATE gene circuit to achieve highly efficient expression of both CAR constructs, as shown in the figures below from top to bottom. Functional proof-of-concept of the OR GATED CAR-NK cells targeting AML is shown in the SENTI-202 pipeline discussion.
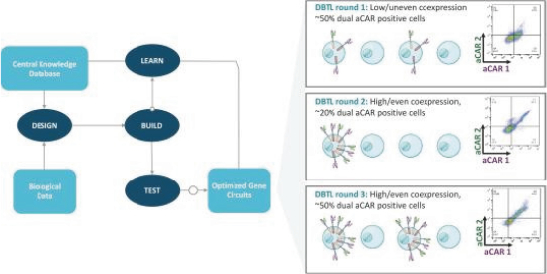
Bivalent CAR: Bivalent CARs are directed against FLT3 and CD33. The bivalent CAR is a single-chain molecule containing two extracellular binding domains, thus allowing for increased OR GATE expression and targeting with a single construct. In preclinical mouse models, our FLT3/CD33 bivalent CAR constructs demonstrated significant tumor killing across multiple leukemic cell lines, such as MV4-11, SEM, and HL-60, possessing differential expression levels of FLT3 and CD33 on their cell surfaces.
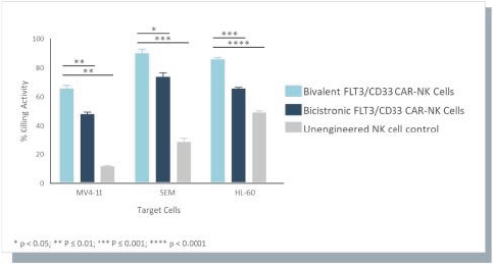
116
 | AND GATE |
Our third Logic Gate gene circuit technology is the AND GATE. AND GATE gene circuits require that multiple targets be present at the same time to trigger killing of cancer cells, which may enhance the specificity of on-target, on-tumor activity. Generally, conventional therapies only recognize a single antigen for their activity. We can implement AND GATE gene circuits in multiple formats, including multiple CARs that activate cancer cell killing when two Tumor-Associated Antigen targets are present simultaneously or multiple Smart Sensors that activate gene therapies when two disease-specific promoters are active simultaneously. For example, we have designed cancer gene therapy product candidates that integrate two cancer-specific promoters with an AND GATE to express cytokines, T cell engagers, chemokines and anti-PD1 antibodies in order to trigger powerful and specific anti-cancer responses in mouse models of cancer.
 | Multi-Arming |
Multi-Arming gene circuits incorporate multiple payloads into a single cell or gene therapy product. These gene circuits are intended to activate various biological pathways in complementary ways to prevent diseases from evading single-target treatments, and thereby improve treatment efficacy. Existing combination therapies that target complex diseases require the application of multiple individual drugs, which is difficult due to research, clinical development, regulatory and pharmacology barriers.
Background: The Need for Targeting Multiple Biological Pathways
Many diseases are difficult to treat since they result from the dysfunction of numerous biological pathways, or they evolve strategies to evade single-target therapies. Combination therapies involving multiple distinct drugs are being used to tackle this problem, but manufacturing, developing and delivering multiple individual drugs into the body is challenging.
Our Gene Circuit Solution: Multi-Arming
We believe our Multi-Arming gene circuits can be used to create a single cell or gene therapy product candidate that includes multiple payloads capable of combating multiple disease pathways more effectively. These Multi-Arming gene circuits have the potential to simplify the manufacturing, regulatory and delivery challenges associated with conventional combination therapies. Multi-Arming gene circuits can be controlled by any of our other gene circuit technologies, including Regulator Dials and Logic Gates, to achieve conditional therapeutic activity.
117
Selected Multi-Arming Proof-of-Concept Data
We have assembled a library of immune-stimulatory payloads—such as cytokines, chemokines and enzymes—that have the potential to trigger anti-tumor responses. As illustrated by the figure below, we leveraged our DBTL Engine to improve the expression of various immune stimulatory payloads in CAR-NK cells, and test the effects of single-armed versus multi-armed CAR-NK cells for their anti-cancer activity.
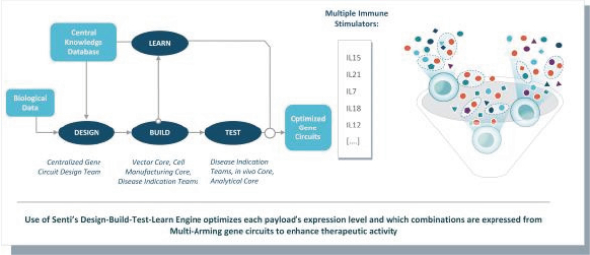
The figure below illustrates an example of the benefits of multi-arming. CAR-NK cells were engineered to express either a single cytokine, IL-15 or IL-21, or multi-armed with both IL-15 and IL-21. These engineered CAR-NK cells were co-cultured with fluorescently labeled tumor cells, and in vitro tumor cell killing was measured over 5 days. While unarmed CAR-NK cells, and single-armed CAR-NK cells, shown by the purple and red lines in the figure, were able to control and reduce tumor cell growth, the multi-armed CAR-N ells, shown by the teal line in the figure, had greater anti-tumor activity. These results can also be observed by representative fluorescent tumor cell images, shown on the right hand side of the figure, where enhanced tumor killing by the multi-armed CAR-NK cells led to reduced number of tumor cells.
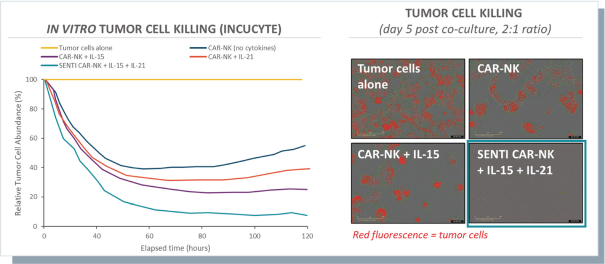
 | Regulator Dial |
118
Regulator Dial gene circuits are designed to enable the precise tuning of therapeutic activity from a cell or gene therapy product. For example, this can be implemented by regulating therapeutic payload expression in response to varying concentrations of FDA-approved drugs. Regulator Dials are expected to enable the exogenous regulation of next-generation cell and gene therapies in vivo even after they have been delivered. We have generated numerous Regulator Dial gene circuits that can be controlled by a variety of FDA-approved small molecule oral drugs, and that can implement various control behaviors, such as ON switches, OFF switches and rheostats.
Background: The Need for Dynamic Regulation
Existing cell and gene therapies cannot be regulated once they are delivered into the patient. This lack of in vivo control makes it difficult to control dosing within the ideal therapeutic window. This problem makes it challenging to expand cell and gene therapies to many disease indications and to engineer these products to have increased potency and safety. As a result, gene therapies have focused on indications where constitutive expression is acceptable, rather than diseases where expression of the therapeutic payload must be regulated within a specific range or be toggled on and off over a period of time. As another example, CAR-T cell therapies for oncology have exhibited clinical toxicity due to lack of control post-infusion.
The efficacy of adoptive cell therapies in solid tumors is hampered by the poor persistence and dysfunction of these cell therapies in the immunosuppressive tumor microenvironment. Inflammatory cytokines, such as IL-12, have been shown in preclinical studies to enhance CAR-mediated effector functions and stimulate the innate immune response to further support tumor killing. However, clinical trials involving systemic use of IL-12 have shown severe unexpected toxicity, limiting its clinical application. Overexpressing IL-12 from adoptive T cell therapies using a poorly regulated promoter has also resulted in significant clinical toxicities. Beyond toxicity issues, persistent stimulation by inflammatory cytokines has been associated with cell exhaustion and may limit anti-tumor efficacy. Thus, a mechanism to dynamically regulate cytokine production by armored CAR-immune cells could enable enhanced anti-tumor activity without triggering unacceptable levels of toxicity in patients.
Our Gene Circuit Solution: Regulator Dial
One example of our Regulator Dial gene circuit technology is a system designed to regulate gene expression via FDA-approved orally dosed nonstructural protein 3, or NS3, inhibitors. As shown in the figure below, this Regulator Dial consists of a synthetic drug-regulated transcription factor and a synthetic promoter responsive to this regulated transcription factor. In the absence of the drug, the transcription factor is inactive, and no therapeutic protein is produced from the engineered cells. In the presence of the drug, the small molecule triggers expression of the therapeutic protein in a dose-dependent manner—effectively, the Regulator Dial “computes”
119
the level of induction based on the concentration of the drug. Key features of the Regulator Dial, such as (i) basal and maximal expression levels, (ii) thresholds for activation and (iii) input-output gain, can be tuned by our DBTL Engine.
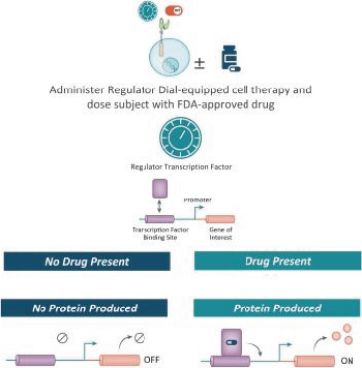
Selected Regulator Dial Proof-of-Concept Data
Leveraging our DBTL Engine, our NS3-based Regulator Dial was systematically engineered to improve its sensitivity to drug concentration. Optimization of various elements in the Regulator Dial improved the drug sensitivity by more than 100-fold. As illustrated by the figure below, we evaluated the drug sensitivity of our Regulator Dial gene circuit to control the expression of the calibrated release version of the potent immune effector IL-12. Specifically, this enhanced Regulator Dial gene circuit was triggered at concentrations as low as 0.01 µM of the NS3 inhibitor, grazoprevir, and achieved at least 100-fold induction around the known drug Cmax in humans of 0.23 µM. Thus, we believe that this system could enable precise and tunable control of timing and duration of crIL12 expression at clinically achievable drug concentrations in a dose-dependent fashion.
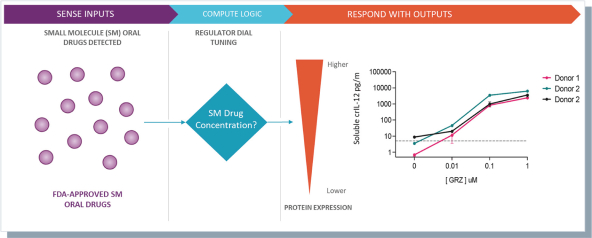
120
We have also examined the potential of our Regulator Dial gene circuits in vivo. Using a mouse model to evaluate the ON/OFF/ON induction kinetics of crIL-12 production. Regulator Dial gene circuit-engineered NK cells were injected intravenously into immunodeficient mice on Day 0. Induction of crIL-12 expression in mice was evaluated by treatment with either vehicle control or grazoprevir (GRZ in the figure below). Significant crIL-12 induction was observed in mice treated with grazoprevir on Day 2 post GRZ-treatment in a GRZ-dose dependent manner. crIL-12 returned to basal level eight days upon withdrawal of grazoprevir, and was significantly induced again two days after GRZ-treatment.
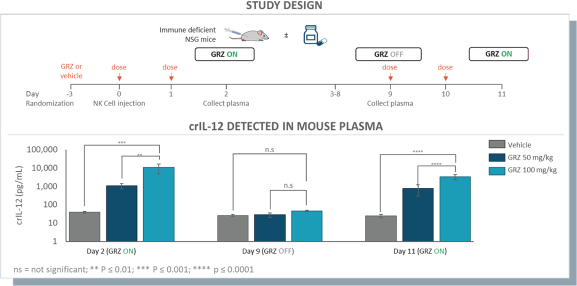
Future Areas of Applications and Alternate Gene Circuits
Beyond the NS3-based Regulator Dial, we have developed and continue to optimize other Regulator Dials. These include Regulator Dials that are controlled by other orally dosed compounds that are FDA-approved or chemicals that are otherwise known as safe, which have differing pharmacology profiles and tissue biodistribution, such as into the central nervous system. These different Regulator Dials can be customized for a variety of cell and gene therapy applications. Conversely, we have created Regulator Dials that are dialed down in response to increasing concentrations of the drug. For example, we have conceptualized and designed various
121
versions of Regulator Dials that have the potential to be regulated by different small molecule drugs, such as Hepatitis C Virus (HCV) protease inhibitors, Immunomodulatory imide drugs, or IMiDs, such as thalidomide and its analogs, and tamoxifen.
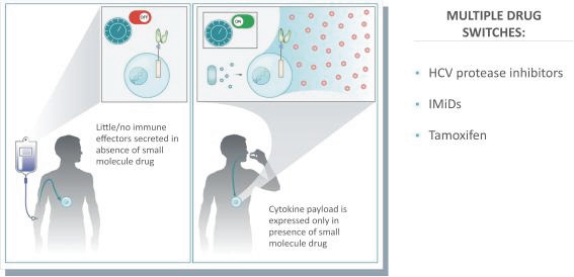
 | Smart Sensor |
A Smart Sensor is a gene circuit, or combination of gene circuits, designed to precisely detect cell type or disease environments, and thus distinguish between the “disease state” and “healthy state.” For example, Smart Sensors can be engineered to detect whether certain conditions, or disease biomarkers, are present before responding with a specific therapeutic response. Conventional medicines are generally unable to dynamically change their behavior in response to cell or disease specific conditions.
Diseases change over time and location in the body. Existing therapies are often unable to dynamically change their behavior in response to disease conditions or concentrate their activity only to specific places. Smart Sensors can be designed to sense diverse biomarkers that are specific to disease or cell states, including cell-surface antigens, soluble disease markers, metabolites, transcription factors, microRNAs and others. For example, we have created artificial receptors that are displayed on the surface of engineered cells and activate gene expression within these cells when they encounter specific cytokines or small molecule chemicals. We have also designed gene regulatory elements such as promoters and RNA elements that respond to specific intracellular signals, such as transcription factors and microRNAs.
122
The figure below illustrates how our Smart Sensor gene circuit technology can be used to design synthetic promoters to enable gene therapies that are selectively activated in diseased cells by detecting disease-specific transcription factors:
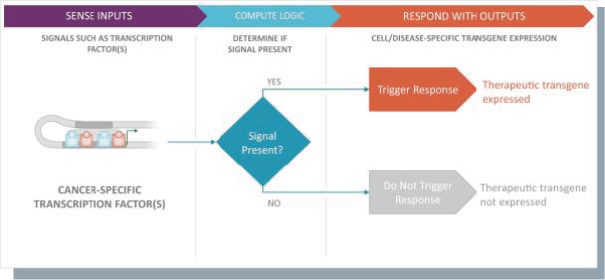
Background: The Need for Novel Sensors in Smart Medicine
Cell and gene therapies have long held out the promise of curing a myriad of diseases, including cancer and genetic disorders. These therapies are generally comprised of three components: (i) the vector, which is used to deliver the transgene into cells; (ii) the promoter, which is a regulatory DNA sequence that drives expression of the transgene; and (iii) a transgene, which is the therapeutic payload.
While early successes in the field have led to recently approved gene therapies, it remains challenging to precisely target gene expression only in diseased cells. This is an important limitation since many genetic disorders require controlled or targeted activity in certain cell types in order to correct diseases while preventing undesirable side effects. Similarly, in cancer gene therapy, it is important to achieve selective killing in cancer cells while sparing healthy tissues. Engineering viral vectors that are biased toward specific cell types is limited by the availability of a unique feature on the outside of the target cell that a viral vector can harness. Additionally, many of the promoters used in current gene therapies are not disease, cell or tissue specific and thus lack the ability to dynamically regulate therapeutic protein production in response to the disease state or location.
Our Smart Sensors Solution: Cell Type or Cell State Specific Conditional Synthetic Promoters
Our solution to address these limitations is to construct Smart Sensors that are selectively activated by cell type or cell state. For example, these Smart Sensors are synthetic promoters that sense internal control mechanisms that cells already possess, such as transcription factors. Transcription factors modulate regulatory elements encoded in the DNA sequence of promoters to direct gene transcription to occur in a specific cell type, or even a specific cell state.
123
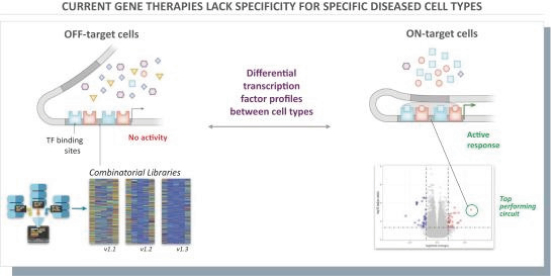
We have established, and continue to scale, our powerful DBTL Engine to discover highly potent and selective synthetic promoters. As shown in the figure below, our iterative high-throughput process utilizes advanced computational approaches, such as machine learning, to discover these promoters. In the first stage, we perform computational analyses of public and proprietary gene expression datasets to identify transcriptional regulatory elements that are active in a desired, or on-target, cell type and inactive in one or more undesired, or off-target, cell types. Based on these analyses, we computationally design diverse libraries of synthetic, compact promoters that can be synthesized in parallel. For example, we can design libraries containing more than 10,000 promoters that are 200 to 400 base pairs in size, which is significantly smaller than currently used promoters in gene therapies. In the second stage, we perform high-throughput assays to quantify the activities of these promoters in the on-target cell types versus the off-target cell types using next-generation sequencing. This enables us to identify synthetic promoters that are both highly active and specific for the on-target cells. If further optimization is needed, the output of these screens provides a rich source of proprietary data for the machine-learning-enhanced design of additional synthetic promoter libraries, representing the third stage of the process.
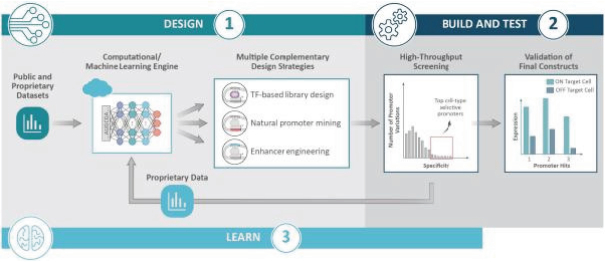
124
Selected Smart Sensor Proof-of-Concept Data
We have used this high-throughput design platform to generate synthetic promoters for diverse gene and cell therapies. For example, we designed and evaluated, in a high-throughput manner, thousands of synthetic promoters to identify candidates that achieve strong differential expression in breast cancer cells versus healthy breast cells. As shown in the figure below, we were able to validate promoters with very strong selectivity for human breast cancer cells, labeled as Cancer Cell Synthetic Promoter in the figure, versus the healthy breast cells, by up to ~1,000-fold. This level of selectivity is much greater than what we have observed from other cancer-specific promoters of which we are aware. In addition, we also identified healthy-cell-specific promoters, labeled as Healthy Cell Synthetic Promoter in the figure, that are highly selective for healthy breast cells compared to breast cancer cells.
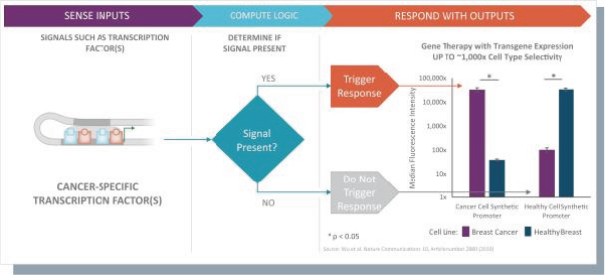
Future Areas of Applications and Alternate Gene Circuits
The concept of Smart Sensors that sense disease-specific or tissue-specific transcriptional states is broadly applicable across various therapeutic areas outside of oncology. For example, we believe we can apply our Smart Sensor design platform to create promoters that are selectively activated in certain cells and tissues, such as neurons and muscle. We have also designed microRNA-responsive Smart Sensor elements into mRNA sequences that achieve selective gene expression in desired cells. These Smart Sensors have the potential to enable gene therapies with maximal on-target activity and minimal off-target side effects, thus increasing the therapeutic window of our product candidates.
We have also created artificial receptor architectures that can detect extracellular or cell-surface proteins beyond traditional CARs. These artificial receptor Smart Sensors can be programmed to bind to soluble disease markers, such as cytokines, metabolites, hormones and others, and then modulate gene transcription within cells to drive the appropriate therapeutic response.
We Believe Our Gene Circuits May Have Broad Applicability in Multiple Treatment Modalities and Disease Areas
We believe that our gene circuit platform may have broad applicability across treatment modalities and disease areas.
Treatment Modalities: Our gene circuit biological “software” can be used to program numerous cell and gene therapy products, or “hardware.” Specifically, these modalities include NK cells, T cells, TILs, stem cells
125
including HSCs, in vivo gene therapy and mRNA. We have conducted research in multiple cell types and vector types, and the initial focus of our internal pipeline is implementing gene circuits within off-the-shelf CAR-NK cells.
Disease Areas: Our gene circuits can be customized to address many aspects of disease biology. We have demonstrated and published on applications of gene circuits across many different in vivo disease models. Thus, we believe that our gene circuit platform technologies can be used against a broad range of diseases that span therapeutic areas such as oncology, immunology, genetic diseases, neurology, cardiology, metabolic diseases, ophthalmology and regenerative medicine.
The following figure presents our perspective on how our gene circuit technologies can be utilized across modalities and corresponding therapeutic areas:
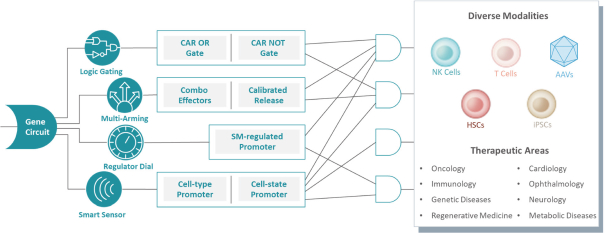
We Utilize Our Design-Build-Test-Learn Engine to Optimize Our Gene Circuits
We have established, and continue to scale, our DBTL Engine to generate our therapeutic gene circuits. We believe the speed, quantity and quality by which we can design multiple types of gene circuits, resulting in thousands of functional gene circuits engineered to date, is unique to our platform. Our gene circuits are engineered by an expert team of synthetic biologists informed by proprietary bioinformatics and our internal gene circuits knowledge database. We also leverage machine learning approaches to continually enhance the design of such gene circuits based on data generated through testing in our in vitro and in vivo disease models. The breadth and scale of our DBTL Engine allows us to learn from each cycle of design to improve the speed and quality of future designs—even across projects and modalities. This approach leverages and reinforces our position as leaders and innovators in the field of synthetic biology for the development of human therapeutics. Based on decades of experience among our founders as well as the accumulated data from our DBTL Engine, we believe that our approach to programming gene circuits is broadly applicable toward engineering optimal efficacy, precision and control into many cell or gene based medicines.
126
The following figure provides an overview of the key steps in our DBTL Engine process:
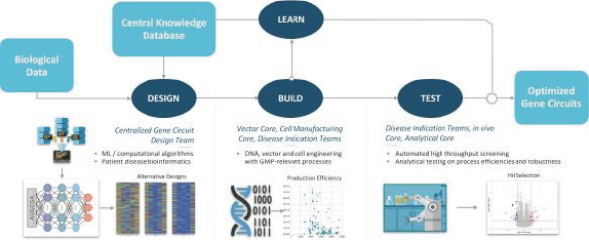
Our Calibrated Release (cr) Technology
Cytokines and other immune stimulatory proteins may be useful in overcoming the immunosuppressive TME in solid tumors by activating endogenous anti-tumor immune cells and to provide support for adoptive cell therapies. For example, in clinical trials run by other parties unaffiliated with Senti Bio, IL-15 has been shown to improve persistence and maintain a cytotoxic phenotype in NK cells. A clinical trial of CAR-NK cells with IL-15 reported clinical efficacy without significant toxicity at assessed doses and time points. Previously published studies of tumor resident NK cells collected from HCC patients have also shown that IL-15 can restore NK cell dysfunction.
However, traditional approaches to use cytokines in combination with adoptive cell therapies have relied on systemic injection of cytokines or engineering the cell therapies themselves to secrete the cytokines or to display them on the cell surface. Systemic injection of cytokines has been challenging due to poor tumor penetration and the risk of systemic immune toxicity. Engineering cell therapies to secrete cytokines can activate endogenous immune cells in a paracrine manner but these secreted cytokines may not provide optimal stimulation of the cell therapies themselves. Engineering cell therapies to display cytokines on the cell surface can stimulate the cell therapies themselves in an autocrine fashion but may not provide optimal activation of endogenous immune cells.
To overcome these limitations, we have created a novel engineered protein technology called calibrated release (cr). Our calibrated release engineered cytokines are expressed by our engineered cells and are tethered to the NK cell surface via a cleavable linker that can be cut off by a ubiquitously expressed protease on the cell surface of NK cells. The rate of linker cleavage can be calibrated by engineering the sensitivity of the cleavable linker sequence to the cell surface protease, enabling us to tune the ratio of membrane-tethered versus fully secreted protein. We believe this platform is generalizable to various proteins, including IL-15 and IL-12.
127
We are using this approach to optimize IL-15 and IL-12 signaling in our CAR-NK platform. All of our current CAR–NK product candidates utilize crIL-15 to simultaneously stimulate surrounding immune cells (paracrine) and promote CAR-NK cell expansion, persistence and tumor killing (autocrine). We have also developed crIL-12 for our SENTI301 product candidate for advanced HCC to potentially stimulate the immune system and overcome the challenges of immunosuppressive TME. This concept is illustrated in the figure below.
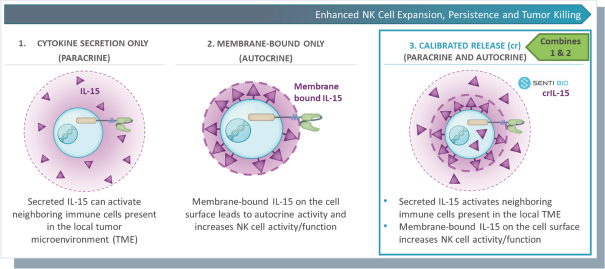
As shown in the figure below, crIL-15 is functional when cleaved and released into the supernatant, resulting in activation of pSTAT5 signaling in T cells from resting PBMCs. In this experiment, engineered CAR-NK cells that expressed crIL-15 were cultured in the absence of any additional cytokines in the media for 72 hours. That media was then collected and used to stimulate resting PBMCs that were thawed. The levels of pSTAT5 were quantified using flow cytometry on the CD3+ T cell fraction and mean fluorescence intensity (MFI) was measured (Y axis). As shown in the left panel, media from SENTI CAR-NK cells that expressed crIL-15 (teal bar) resulted in pSTAT5 induction that was comparable to CAR-NK expressing wtIL-15 (wild-type IL-15, fully secreted, pink bar), demonstrating the paracrine benefits of crIL-15 in activating other immune cells.
Furthermore, crIL-15 was shown to improve CAR-NK persistence and cancer cell killing with a 3-round serial killing assay. Engineered SENTI CAR-NK cells armed with our crIL-15 or CAR-NK cells secreting wtIL-15 were co-cultured with tumor cells, which were added at hour 0, hour 96, and hour 168, to repeatedly challenge the CARNK cells with new cancer target cells. Tumor cell samples without NK cells, shown as the yellow lines, continued to grow. In the first round of tumor killing, CAR-NK cells containing crIL-15, shown in teal, as well as CAR-NK cells containing wtIL-15, shown in pink, effectively killed tumor cells. At 96 and 168 hours, CAR-NK cells were rechallenged with fresh tumor cells. In the second and third rounds of cancer cell killing, which commenced with fresh cancer cells being added at hour 96 and hour 168, only SENTI CAR-NK cells armed with crIL-15, shown in teal, maintained their ability to effectively kill tumor cells. This data shows the potential of our calibrated release technology platform to functionally enhance the killing activity of CAR-NK cells in challenging conditions.
128
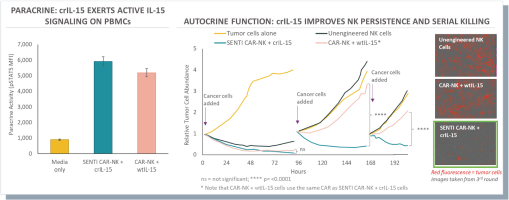
We are also leveraging the calibrated release technology for IL-12 in SENTI-301, where crIL-12 expression is modulated via a small molecule Regulator Dial gene circuit to control crIL-12 expression levels, in order to stimulate the immune system and overcome the challenges of immunosuppressive TME while potentially avoiding safety issues. We will discuss crIL-12 data in detail in the SENTI-301 product section.
Our Pipeline and Product Candidates
We are advancing a broad pipeline of gene circuit-enabled product candidates focused on three distinct categories: (i) off-the-shelf CAR-NK cells for oncology, (ii) gene therapies for tissue-directed targets and (iii) cell therapies for regenerative medicines. Our most advanced programs are off-the-shelf CAR-NK product candidates designed to improve the therapeutic outcome of certain oncology indications: SENTI-202, SENTI-301 and SENTI-401.
Our pipeline chart is as follows:
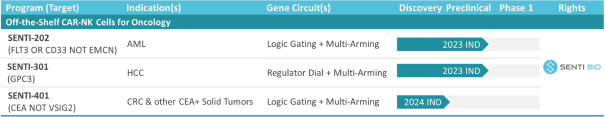
SENTI-202 for the Potential Treatment of Acute Myeloid Leukemia
Overview
We are developing our SENTI-202 product candidate as a Logic Gated (OR + NOT) off-the-shelf CAR-NK cell therapy designed to target and eliminate AML cells while sparing the healthy bone marrow. We are engineering SENTI-202 to express a bivalent CAR as an OR GATE directed against the Tumor-Associated Antigens, FLT3 and CD33, where one or both are expressed in 95% of AML patients. FLT3 is highly expressed on LSCs, while CD33 is highly expressed on AML blasts. AML is a heterogeneous disease composed of both AML LSCs and blasts. Thus, we believe that targeting FLT3 OR CD33 will enhance the overall killing activity against diseased cells in AML. However, FLT3 is also expressed on HSCs in the bone marrow. In order to spare FLT3-expressing healthy HSCs, we have further engineered SENTI-202 with a NOT GATE gene circuit comprised of an iCAR targeted against EMCN. EMCN is a Safety Antigen with high expression on HSCs and no or low expression on AML LSCs and blasts. We believe this NOT GATE gene circuit could allow SENTI-202 to eliminate LSCs that cause relapse while preserving the patient’s healthy HSCs. Further, SENTI-202 is engineered to express our proprietary crIL-15 to simultaneously stimulate surrounding immune cells and promote
129
NK cell expansion, persistence and tumor killing. This proprietary product profile has the potential to drive towards deeper and longer remissions for AML by enabling killing of diverse AML cells while sparing HSCs that regenerate the blood and the immune systems.
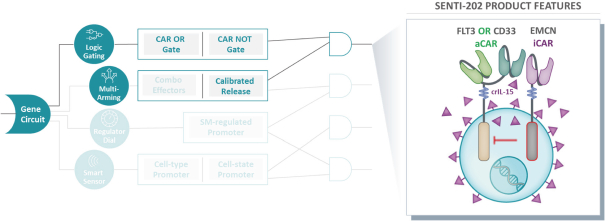
In 2022, we plan to present IND-enabling pharmacological data at key scientific conferences. In 2023, we plan to submit an IND application to support the clinical evaluation of SENTI-202.
Acute Myeloid Leukemia: an Unmet Medical Need
Almost 10% of new cancer cases in the United States each year are hematologic malignancies, including leukemia, lymphoma and myeloma. AML is a type of acute leukemia characterized by an accumulation of malignant immature white blood cells. It is the most common type of acute leukemia in adults, constituting 80% to 85% of cases, and is the second most common—as well as the deadliest—in children. Due to the absence of highly efficacious therapies, AML has the lowest five-year survival rate among all leukemias at just 29.5%. Since the incidence is highest among the elderly, we expect cases and economic burden will continue to rise as the general population ages. According to Dieguez et al., costs for the three years following AML diagnosis can reach $800,000 per patient.
Conventional therapy for AML generally involves remission induction therapy, followed by consolidation (post-remission) therapy, in which chemotherapy is used with stem cell transplantation to prevent disease recurrence. For remission induction, treatment options include cytotoxic chemotherapy, radiation therapy and targeted therapies, such as monoclonal antibodies and small molecule inhibitors of disease pathways, with the aim of achieving fewer than 5% blast cells in the bone marrow, blood cell counts within normal limits and no signs or symptoms of disease. Unfortunately, 10% to 40% of patients are unable to achieve these complete remission targets despite intensive induction therapy, and conventional therapies have failed to significantly improve the long-term survival of patients for decades. Moreover, relapse of disease in patients with AML is a major issue and remains a difficult clinical challenge, with approximately 70% of patients relapsing within three years.
Development of targeted AML treatments is difficult due to the fact that the disease is highly heterogeneous, with more than 200 types of chromosome translocations and mutations having been identified in AML patients. Therapies targeting a single Tumor-Associated Antigen are therefore often insufficient to kill all of the cancer cell subsets in AML, leading to eventual disease relapse. To drive patients into deeper remissions and prevent relapses, therapies designed to target multiple AML antigens are needed. Additionally, recent studies suggest relapse is associated with the less targeted AML subpopulation of LSCs. Thus, the development of therapies targeting AML LSCs is sorely needed, but this has been challenging since LSC targets are often expressed on healthy cells, such as HSCs, leading to on-target, off-tumor treatment-induced toxicities.
130
CAR Cell Therapy for AML
The therapeutic administration of CAR cell therapies has considerably advanced the treatment of certain cancers, such as ALL. However, the successes of CAR cell therapies have not yet translated to successful treatment of AML, in part due to the absence of AML-specific target antigens. Due to their nonrestrictive expression, most AML antigens are also expressed on healthy HSCs or myeloid cells. Thus, on-target, off-tumor killing effects of the therapy may lead to the ablation of hematopoietic stem, progenitor or myeloid cells. While the B cell depletion that results from off-tumor killing of normal healthy cells in CAR-T therapy of ALL can be clinically managed, off-tumor killing of HSCs is unlikely to be tolerated in the case of AML treatment. Thus, the identification of antigens that enable more robust targeting of AML cells, including LSCs, along with new strategies to reduce off-target killing of HSCs, are critically needed to realize the promise of CAR cell therapies for AML treatment. These described challenges also extend to other potential AML therapeutic modalities, such as antibodies and bispecific T cell engagers.
SENTI-202 Approach to AML
SENTI-202 off-the-shelf CAR-NK cells are engineered with gene circuits that enable identification of cancerous versus healthy cells using NOT GATE + OR GATE logic decisions, and potentially improved persistence and more durable antitumor functions. SENTI-202 combines two different Logic Gates, and crIL-15 expression, as follows:
| 1. | An iCAR NOT GATE gene circuit to prevent CAR-mediated killing of cells expressing either FLT3 or CD33 and a Safety Antigen, EMCN. The EMCN iCAR is intended to suppress CAR-NK cell cytotoxicity against healthy HSCs, reducing the risk of potential life-threatening bone marrow toxicity and potentially increasing the therapeutic window and on-target, on-tumor activity. |
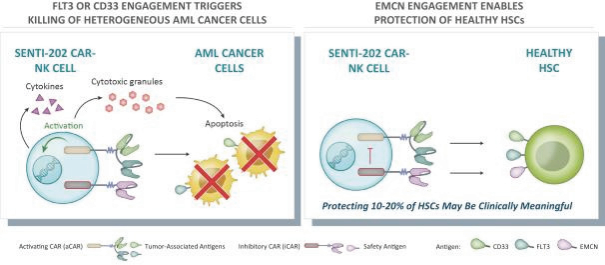
| 2. | An aCAR OR GATE gene circuit to activate CAR-mediated killing of AML cells expressing either or both of the Tumor-Associated Antigens FLT3 and CD33, thus increasing the targeting of both AML LSCs and blasts. |
| 3. | A crIL-15 gene circuit to simultaneously provide both autocrine and paracrine IL-15 signaling in order to simultaneously stimulate surrounding immune cells and promote NK cell expansion, persistence and tumor killing. |
131
The following figure illustrates the design of SENTI-202 Logic Gating gene circuits to kill AML LSCs and blasts, while sparing healthy HSCs via (FLT3 OR CD33) NOT EMCN logic. Based on the medical community’s substantial clinical experience from autologous and allogeneic-bone marrow transplantations, we believe that protecting 10% to 20% of HSCs would be sufficient to enable hematopoietic recovery and provide clinical benefits to patients.
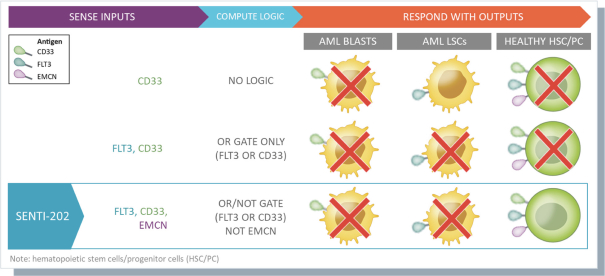
We have established a proprietary Tumor-Associated Antigen and Safety Antigen Paired Discovery Platform to identify complementary Tumor-Associated Antigens for the OR GATE and selective Safety Antigens for the NOT GATE. For SENTI-202, we applied this platform to discover the combination of the Tumor-Associated Antigens, FLT3 and CD33, and the corresponding Safety Antigen, EMCN, for application in AML.
132
In order to select the AML target antigens for the OR GATE gene circuit, we first established criteria for success, including: (i) expression on cell surface targetable by CAR, (ii) high expression across different AML subtypes, (iii) little to no expression in non-hematopoietic tissues and (iv) target combinations that yield broad coverage of AML LSCs and blast cells both among different patients and within individual patients. We utilized our Tumor-Associated Antigen and Safety Antigen Paired Discovery Platform, which leverages an internal bioinformatics database comprising greater than 10 published studies and greater than 1,300 AML patient sample datasets. Using our proprietary transcriptomics- and proteomics-based bioinformatics pipeline, we identified FLT3 and CD33 as desirable Tumor-Associated Antigens for an OR GATE gene circuit to have the potential for comprehensive CAR-mediated killing of AML, including AML LSCs and blasts.
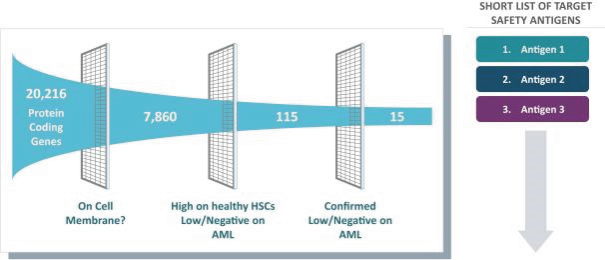
As shown in the left panels of the two transcriptomic analysis figures below, our bioinformatics analyses concluded that FLT3 and CD33 are Tumor-Associated Antigens that are more highly expressed among AML LSCs and blast cells, respectively, relative to most healthy hematopoietic lineages.
133
As shown in the right panels of the two transcriptomic analysis figures below, these antigens are generally not expressed in normal healthy solid organ tissues. An important exception is that high-level expression of FLT3 is observed in healthy HSCs, as shown in the green box in the figure below, which is an observation consistent with published literature. In support of this observation, FLT3-directed bispecific antibodies and CAR-T have demonstrated bone marrow suppression and toxicity against hematopoietic stem and pregenitor in preclinical models previously described in literature. Accordingly, we believe preserving these HSCs through a NOT GATE is important to prevent bone marrow suppression during LSC-directed AML treatment.
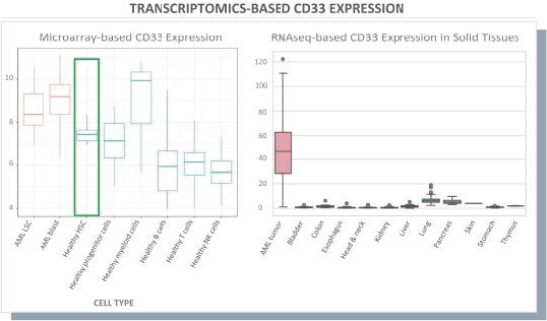
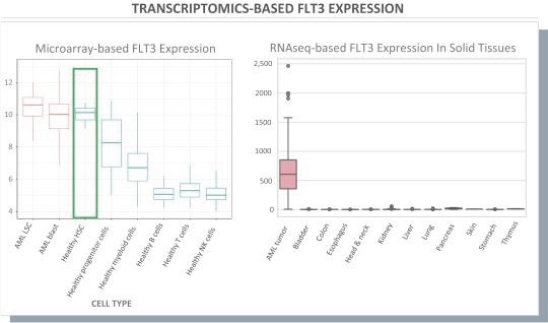
Further, our internal evaluations of primary AML samples also indicated that FLT3 and CD33 were highly expressed at the protein level, in both the AML blast and LSC subsets. A representative flow cytometric analysis
134
is shown in the figure below. The green-shaded quadrants in the figure below represent AML cells that were either FLT3 positive, CD33 positive, or both, demonstrating that the OR GATE approach could limit the number of AML cells that are not targeted by our product candidate.

SENTI-202 Preclinical Proof-of-Concept Data
Leveraging our DBTL Engine, we optimized the expression of the OR GATE FLT3 and CD33 CAR constructs, as shown above in the section titled “Our Platform: The Opportunity for Gene Circuits—Logic Gating—OR GATE”. We then evaluated the ability of these OR GATE CAR-NK cells to kill different leukemia cell lines, including ones that have differential expression levels of the FLT3 and CD33 antigens. As shown in the figure below, our FLT3 OR CD33 CAR-NK cells exhibited increased killing over that of the single-target CAR-NK cells, such as FLT3 only CAR-NK and CD33 only CAR-NK cells. Specifically, they demonstrated significantly improved killing across FLT3++ (p < 0.05) and CD33++ (p < 0.01) expressing leukemia cell lines in vitro, shown as FLT3++ and CD33++ bars in the figure below.
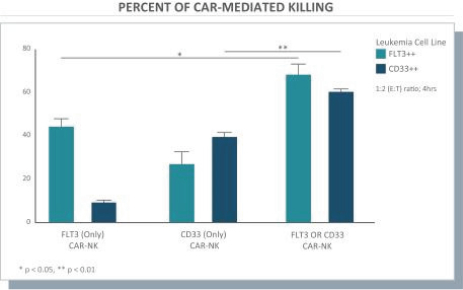
We further confirmed in vitro that our OR GATE CAR-NK cells were capable of killing primary AML cells. As shown in the right panel in the figure below, we identified primary AML samples, labeled AML#770,
135
#857, #847, #837 and #846, with expanded blast populations by flow cytometry, then performed co-culture in vitro cytotoxicity assays. Both of our versions of OR GATE CAR-NK cells, bivalent and bicistronic, showed significant cytotoxicity against the primary AML cells (p < 0.01) in comparison to unengineered NK controls.
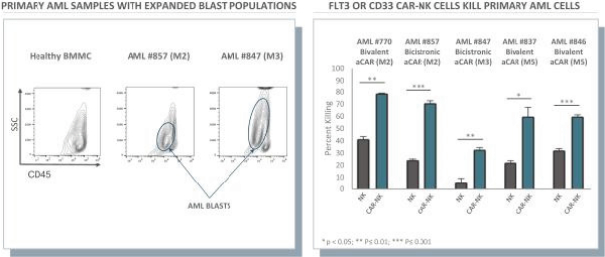
Furthermore, we evaluated the OR GATE CAR-NK cells in vivo in two AML xenotransplantation tumor models using MV4-11 and MOLM-13 AML cell lines. As shown in the figures below, in each of the mouse models, our FLT3 OR CD33 CAR-NK cells achieved statistically significantly greater anti-tumor activity compared to untreated control mice and mice treated with unengineered NK cells. Treatment with the OR GATE CAR-NK cells also improved survival compared to the control groups.
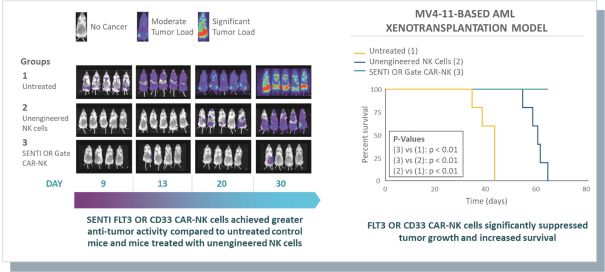
136
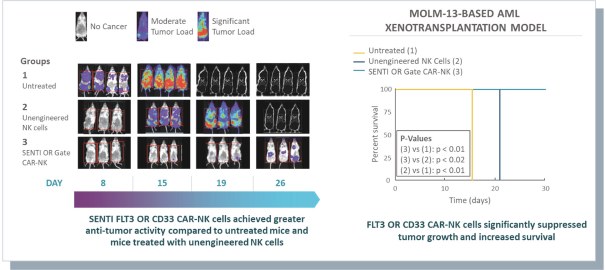
As shown in the figure below, using the same proprietary transcriptomics and proteomics-based bioinformatics methodology discussed earlier, we identified EMCN as a target antigen that is highly expressed on healthy HSCs but not on AML LSCs or blasts. This validates EMCN’s potential as a Safety Antigen to protect HSCs from potential on-target, off-tumor CAR-NK mediated toxicity. The rationale for utilizing EMCN as the Safety Antigen is further bolstered by a previous finding in the literature that identified EMCN as a marker of the key cell type for repopulating the blood and immune systems.
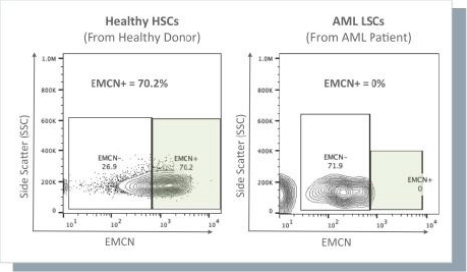
Upon selection of EMCN as our primary Safety Antigen target, we next incorporated binders for the FLT3 activating CAR (aCAR) and the EMCN safety antigen into our internal NOT GATE (iCAR) discovery and development platform in order to best identify the optimal iCAR architecture for the SENTI-202 program. Using different FLT3 NOT EMCN CAR-NK cells (primary NK cells engineered to co-express the same FLT3 aCAR with one of dozens or different proprietary EMCN iCARs), we performed an in vitro cytotoxicity protection assay screen using target cells that expressed only the FLT3 Tumor-Associated Antigen and not the EMCN SA (gray bars - model cancer cells) or target cells that expressed both the FLT3 Tumor-Associated Antigen and the EMCN SA (teal bars - model healthy cells). This latter target cell population should be protected from aCAR-mediated killing if the particular iCAR is functional. Using this approach, we identified multiple functional EMCN iCAR architectures that
137
enabled robust target cell killing in the absence of the SA (model cancer cells) and provided significant antigen-dependent target cell protection in the presence of the EMCN SA (model healthy cells).
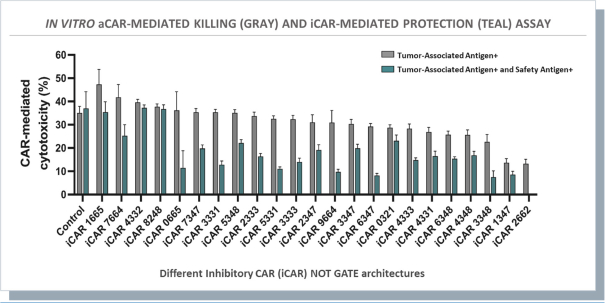
Upon identifying several different EMCN iCARs possessing potent antigen-dependent protection activity, we further tested two of our top EMCN iCAR candidates (v1, v2) within another in vitro cytotoxicity protection assay in which we co-cultured FLT3 NOT EMCN CAR-NK cells (NK cells engineered to express the same FLT3 aCAR with v1 or v2 EMCN iCAR) with target cells that only expressed the FLT3 Tumor-Associated Antigen but did not express the EMCN SA (gray bars - model cancer cells) or target cells that expressed both the FLT3 Tumor-Associated Antigen and the EMCN SA (teal bars - model healthy cells). This latter target cell population should be protected from aCAR-mediated killing if the iCAR (v1 or v2) is functional. As shown in the figure below, we confirmed that the NOT GATE (with multiple EMCN iCAR designs) enables significant antigen-dependent protection of EMCN-expressing cells from CAR-mediated toxicity. Within this experiment, the v1 EMCN iCAR provided 67% protection and the v2 EMCN iCAR provided 50% safety antigen-dependent protection from aCAR-mediated toxicity.
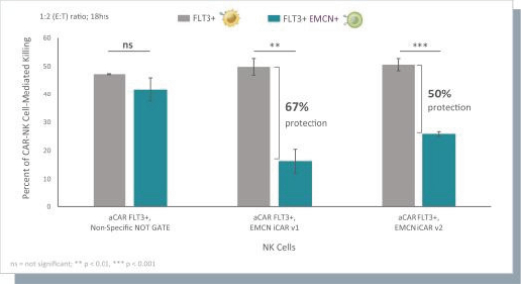
138
We further evaluated the full FLT3 OR CD33 NOT EMCN gene circuit-equipped NK cells in a cytotoxicity protection assay using the more clinically-relevant donor-derived primary healthy HSCs. Unlike the model Healthy Cell line shown above, bone marrow-derived CD34 enriched primary HSCs have natural levels of both the Tumor-Associated Antigens, FLT3 and CD33, as well as EMCN, expressed on the cell surface and represent a more realistic model to evaluate our proprietary AML NOT GATE gene circuit. As shown below, while FLT3 OR CD33 NOT EMCN CAR-NK cells demonstrated killing of leukemia cell lines comparable to that of the control that does not express the EMCN iCAR, labeled as FLT3 OR CD33 CAR-NK cells (see left data), our NOT GATE enabled significant protection of primary HSCs (see right data), exceeding the 10% to 20% protection target we anticipate would provide clinical benefits to patients.
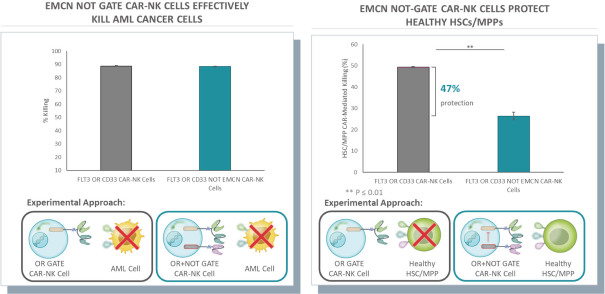
Development Plan and Key Next Steps for SENTI-202
We have demonstrated, preclinically, the functionality of the key gene circuit components of SENTI-202, namely our FLT3 aCAR, CD33 aCAR and EMCN iCAR constructs. In 2022, we plan to present IND-enabling data at key scientific conferences. In 2023, we plan to submit an IND application to support the clinical evaluation of SENTI-202.
National Cancer Institute (NCI) Contract to Support Development of SENTI-202
In September 2021, we were awarded funding from the National Cancer Institute of the National Institutes of Health in the form of a Small Business Innovation Research (SBIR) contract to support further development of SENTI-202 for AML towards clinical development. The Direct to Phase II SBIR contract will provide us with approximately $1.9 million in federal funding for the SENTI-202 program over two years.
SENTI-301 for the Potential Treatment of HCC
Overview
Our SENTI-301 product candidate is a Multi-Armed off-the-shelf CAR-NK cell therapy that we are developing for the treatment of advanced HCC. We are engineering NK cells to target GPC3, which is highly expressed in 70% to 90% of HCCs and has low or no expression on normal adult tissues. SENTI-301 is armed with a combination of potent immune effectors, including our proprietary crIL-15 gene circuit, intended to simultaneously stimulate surrounding immune cells and promote NK cell expansion, persistence, and tumor killing, as well as our proprietary crIL-12, where expression is modulated via a small molecule Regulator Dial
139
gene circuit, to stimulate the immune system and potentially overcome the challenges of immunosuppressive TME in advanced HCC.
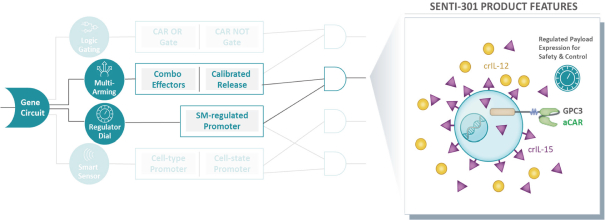
In 2022, we plan to present IND-enabling pharmacological data at key scientific conferences. In 2023, we plan to submit an IND application to support the evaluation of SENTI-301.
Hepatocellular Carcinoma: an Unmet Medical Need
HCC accounts for approximately 90% of primary liver cancers and represents a large unmet medical need due to the lack of effective treatment options. Globally, it is the sixth most commonly diagnosed cancer, and the fourth leading cause of cancer deaths. In the United States, the rate of death from liver cancer increased by 43% from 7.2 to 10.3 deaths per 100,000 people between 2000 and 2016. Frequently, HCC develops in patients with liver disease such as hepatitis C virus, alcoholic liver disease or non-alcoholic steatohepatitis.
Available therapies are only modestly efficacious and mortality rate in advanced HCC remains high despite recent improvements in treatment options. The most effective therapy currently available for advanced HCC is atezolizumab plus bevacizumab combination therapy for first line treatment with a 28% objective response rate and a 7% complete response rate.
SENTI-301 Approach to Advanced HCC
As shown in the figure below, SENTI-301 off-the-shelf NK cells are engineered with multiple anti-tumor activities to achieve a Multi-Armed attack on solid tumors.
Specifically, SENTI-301 includes:
| 1. | An aCAR that targets GPC3, a highly expressed antigen in HCC and that has low or no expression on normal adult tissues. |
| 2. | crIL-15 for simultaneous paracrine and autocrine signaling in order to simultaneously stimulate surrounding immune cells and promote NK cell expansion, and persistence, and tumor killing. |
| 3. | crIL-12, where expression is modulated via a small molecule Regulator Dial gene circuit, to stimulate the immune system and potentially overcome the challenges of immunosuppressive TME in advanced HCC. |
140
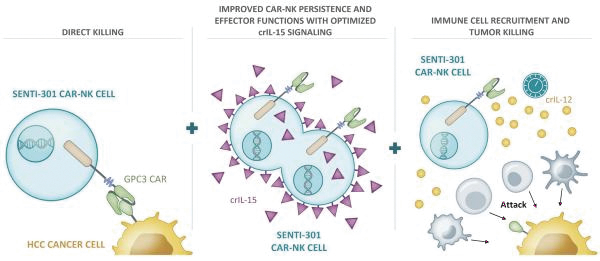
GPC3 is a Tumor-Associated Antigen expressed in approximately 70% to 90% of human HCCs, but not expressed in healthy liver tissue or other human organs after birth. GPC3 has previously been clinically evaluated as a therapeutic target for immunotherapy in HCC. GPC3 is also a histologic and serum clinical marker for HCC and its expression has been associated with poor prognosis. Functionally, GPC3 is associated with the control of cell division and growth regulation. We built GPC3 CAR constructs to redirect NK-mediated cytotoxicity against advanced HCC using a GPC3 binder that associates to the membrane proximal region of the GPC3 protein.
As recombinant proteins, the IL-15 and IL-12 pleiotropic cytokines have previously demonstrated anti-tumor activity in several preclinical studies. IL-15 has been shown to improve NK cell persistence in vivo and maintain cytotoxicity. Functionally, IL-12 promotes the secretion of Th1 cytokines from other immune cells, potentiating the recruitment and activation of the endogenous innate and adaptive immune systems, which leads to subsequent induction of an anti-tumor immune response.
Our proprietary crIL-15 gene circuit is designed to simultaneously produce both membrane-associated and fully secreted IL-15 to support both autocrine- and paracrine-like signaling. We believe that the ability of crIL-15 to also secrete active IL-15 into the tumor microenvironment should enable stimulation of endogenous immune cells within the tumor microenvironment in solid tumor settings. Our proprietary crIL-12 is designed to potentially induce a potent immune response and overcome the challenges of immunosuppressive TME in advanced HCC.
Previous clinical experiences with adoptive cell transfer of engineered immune cells expressing IL-12 have demonstrated the feasibility of IL-12-secreting cell therapies. However, systemic immunotoxicity has been observed in patients when IL-12 is expressed without tight regulation from adoptive cell therapies. Thus, the narrow therapeutic window associated with IL-12 has limited its success to date.
We believe our gene circuit technologies may address these previously observed therapeutic window limitations from clinical studies by modulating the expression of crIL-12 using our Regulator Dial gene circuit. For example, a NS3-based Regulator Dial can be utilized to modulate crIL-12 expression in vivo after infusion of the SENTI-301 product candidate via FDA-approved, orally dosed NS3 inhibitors. The NS3 Regulator Dial consists of a synthetic drug-regulated transcription factor and a synthetic promoter responsive to this regulated transcription factor. In the absence of the drug, the transcription factor is inactive, and no therapeutic protein (such as IL-12) is produced from the engineered cells. In the presence of the drug, the transcription factor is activated, leading to production of the IL-12 payload.
A potential clinical application of the NS3-based Regulator Dial is illustrated in the figure below. Upon infusion of SENTI-301, the crIL-12 regulated gene circuit remains in the off state, thus limiting the potential of
141
systemic immunotoxicity in patients. As infused CAR-NK cells survey the body, we expect local enrichment, activation and expansion of SENTI-301 in GPC3-positive tumors. The antigen-driven anti-tumor response is further supported by the expression of crIL-15. Once local infiltration and engraftment of SENTI-301 is established, NS3 inhibitors may be given to patients in order to induce crIL-12 expression and promote recruitment of endogenous immune cells to help further mount an anti-tumor response. By incorporating multiple therapeutic mechanisms, such as GPC3 CAR, crIL-15 and regulated crIL-12, into the off-the-shelf NK cells, we believe our SENTI-301 product candidate would be armed with the necessary tools to activate multiple pathways in the tumor-immunity cycle in complementary ways in order to combat advanced HCC and its hostile tumor microenvironment.
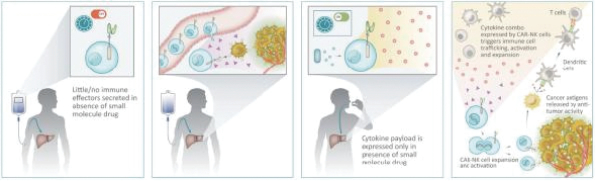
SENTI-301 Supporting Data
GPC3 CAR Expression and Function
We have designed and built hundreds of crIL-15 GPC3 CAR constructs, with the aim to identify and select our lead GPC3 CAR construct based on its expression profile and cytotoxic functions. These GPC3 CAR constructs were delivered into NK cells and evaluated. Anti-tumor cytotoxic functions were evaluated in co-culture assays against the HCC cell lines, HepG2 and HuH7. The figure below shows a representative experiment demonstrating that NK cells engineered to express several GPC3 CAR and crIL-15, constructs, have enhanced levels of killing activity against HCC target cells (GPC3-positive) compared to unengineered NK cells in an Incucyte assay.
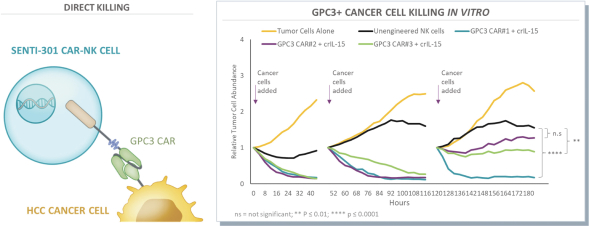
NK cells engineered to GPC3 CAR-crIL15 showed statically significant in vivo anti-tumor activity compared to unengineered NK cells in an IP HCC (HepG2+luciferase)xenotransplantation model. As shown in the figure below, groups treated with SENTI CAR NK #1 +crIL15 and CAR NK #2 +crIL15 (purple and light
142
blue) engineered NK cells exhibited significantly increased survival (p< 0.01 and p<0.001 respectively) over untreated (PBS) and unengineered NK cell-treated groups.
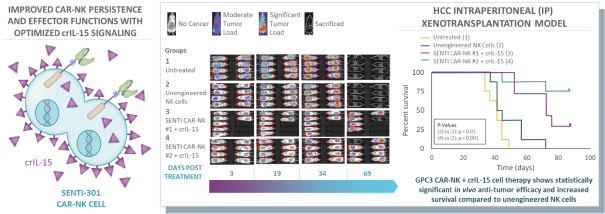
Regulated crIL-12 Expression
SENTI-301 is engineered with our proprietary crIL-12, where expression is modulated via a small molecule Regulator Dial gene circuit, to stimulate the immune system and potentially overcome the challenges of immunosuppressive TME in advanced HCC. We optimized the Regulator Dial gene circuit in immune cells to minimize basal expression, resulting in minimal production of crIL-12 in the absence of NS3 inhibitors, while maintaining high induced expression in a drug-dose dependent manner. As shown in the figure below, NK cells engineered with the crIL-12 regulated gene circuit were evaluated for induction of crIL-12 expression in the presence of the small molecule NS3 inhibitor, grazoprevir (GRZ). We achieved a basal crIL-12 of <100 pg/ml/1e6 cells while induction with a clinically relevant dose of GRZ (10nM) led to an increased crIL-12 expression by ~390- fold (30,000 pg/1e6 cells<0.0001) in 24 hours.
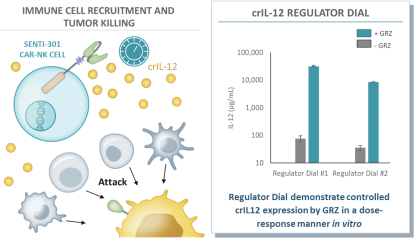
Repeated crIL-12 induction using this Regulator Dial gene circuit was evaluated in vivo. As shown in the figure below, immune-deficient NSG mice received 20×106 engineered NK cells on day 0 and were dosed twice with 50 or 100 mg/kg of GRZ on day 0 and day 1. Blood samples were drawn 1 day (day 2) and 8 days (day 9) posttreatment to assess secreted crIL-12 levels during the small molecule-induced state (ON) and post-small molecule withdrawal (OFF), respectively. We found that on day 2, crIL-12 was detected at ~1,000 and ~10,700 pg/mL in the plasma of mice that received 50 mg/kg or 10 0mg/kg of GRZ respectively, whereas in vehicle-treated mice, crIL-12 remained <40 pg/ml, demonstrating a significant upregulation of crIL-12 production. On
143
day 9, both the GRZ- and vehicle-treated mice exhibited only background levels (<50 pg/mL) of crIL-12, demonstrating that crIL-12 production was switched off in the absence of GRZ. A second round of crIL-12 induction was assessed by treating mice again at day 9 and day 10 with GRZ. Blood samples were drawn 1 day after the second dose (day 11). We observed that crIL-12 was induced again (~700 and 3000 pg/ml) in response to 50 mg/kg or 100 mg/kg of GRZ. This data validates that crIL-12 expression from engineered NK cells can be regulated in a repeated ON/OFF/ON fashion via the GRZ small molecule.
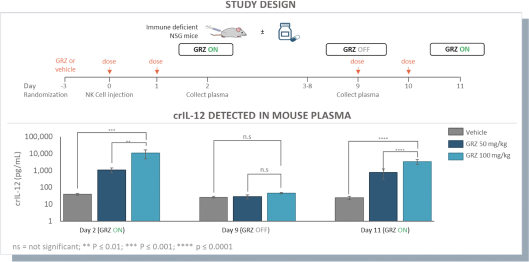
This Regulator Dial gene circuit for IL-12 was evaluated in vivo. As shown in the figure below, immune-deficient NSG mice were dosed with 37.5 mg/kg of GRZ on day 0 and subsequently 75 mg/kg GRZ from day 1 through day 4. These mice received 20×106 engineered cells on day 2. Blood samples were drawn on day 4 and day 8 to assess IL-12 levels during the small molecule-induced state and post-small molecule withdrawal, respectively. We found that on day 4, IL-12 was detected at 1,642 pg/mL in the plasma of mice that received GRZ versus 19 pg/mL in vehicle-treated mice (p < 0.01), a greater than 80-fold upregulation of IL-12 production. On day 8, 4 days after the final GRZ dose, both the GRZ- and vehicle-treated mice exhibited only background levels (20 – 30 pg/mL) of IL-12, demonstrating that IL-12 production was switched off in the absence of GRZ.
Development Plan and Key Next Steps for SENTI-301
We have demonstrated, preclinically, the key gene circuit components of SENTI-301, namely our GPC3 aCAR, our engineered crIL-15 and crIL-12 constructs, and our NS3-based Regulator Dial constructs. In 2022, we plan to present IND-enabling data at key scientific conference . In 2023, we plan to submit an IND application to support the clinical evaluation of our SENTI-301 product candidate.
SENTI-401 for the Potential Treatment of CRC
Overview
Our SENTI-401 product candidate is a Logic Gated off-the-shelf CAR-NK cell therapy that we are developing to more precisely target and eliminate CRC cells while sparing healthy cells elsewhere in the body. We are engineering NK cells to express a CAR directed against CEA, which is highly overexpressed in 85% to 90% of colorectal cancer samples but is also expressed in epithelial cells in healthy tissues. CEA is also expressed in other solid tumors, including lung, breast and gastric cancers. The expression profile of CEA in both tumor and healthy cells has resulted in on-target, off-tumor toxicities by conventional CEA-targeted therapies, thus limiting their clinical success. To address this challenge, we are engineering NK cells with a NOT GATE implemented via an iCAR targeted against an epithelial cell Safety Antigen called VSIG2. Thus, the SENTI-401
144
product candidate’s logic gating is intended to more effectively treat CRC patients by targeting a well-known Tumor-Associated Antigen, CEA, and widen the therapeutic window by preventing killing when CEA appears on healthy cells that also express the VSIG2 Safety Antigen. We are also engineering SENTI-401 to express a combination of potent immune effectors, including our proprietary crIL-15 protein to simultaneously stimulate surrounding immune cells and promote NK cell expansion, persistence and tumor killing, and an additional undisclosed potent immune effector to potentially enhance therapeutic function in solid tumors.
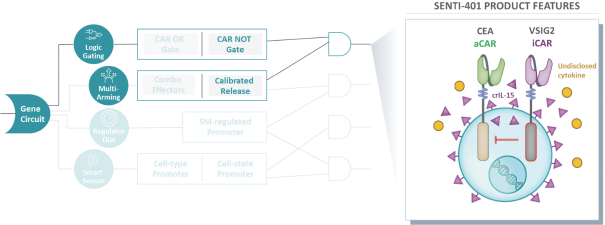
In 2023, we plan to present IND-enabling pharmacological data at key scientific conferences. In 2024, we plan to submit an IND application to support the clinical evaluation of SENTI-401.
Colorectal Cancer: an Unmet Medical Need
CRC accounts for approximately 10% of all annually diagnosed cancers and cancer-related deaths worldwide and is the second and third most commonly diagnosed cancer in women and men, respectively. The incidence of CRC worldwide is predicted to increase to 2.5 million new cases in 2035. Of new colorectal cancer diagnoses, 20% of patients present with metastatic disease and another 25% who present with localized disease will later develop metastases. Among patients with metastatic colorectal cancer, approximately 70% to 75% of patients survive after one year of their initial diagnosis; however, the five-year survival rate is less than 20% despite multiple lines of treatment, including combinations of chemotherapy and targeted therapies.
SENTI-401 Approach to CRC
CEA is a tumor-associated protein overexpressed in many epithelial cancers, most notably in colorectal cancer. However, it is also expressed in a variety of normal epithelial cells throughout the gastrointestinal tract. As shown in the figure below, bioinformatics analyses of RNA sequencing data collected from over 9,500 tumor and 8,500 healthy tissue samples showed that CEACAM5, one of the main isoforms of CEA, is overexpressed across many cancer types, especially colorectal cancer. CEACAM5 expression is also found in healthy organs, including tissues in the GI tract and lungs. Cancer immunotherapies using vaccines and antibodies targeting CEA are actively being investigated in the clinical setting. However, recent clinical studies have shown dose-limiting on-target, off-tumor toxicities in these healthy tissues that also express CEA.
145
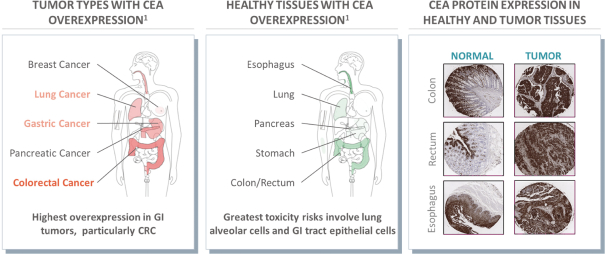
We are developing our SENTI-401 product candidate to overcome the challenges associated with targeting the CEA Tumor-Associated Antigen that is present on both tumor and healthy cells. To mitigate the potential risk of on-target, off-tumor toxicity, we are designing SENTI-401 with a NOT GATE gene circuit to differentiate between cancerous and healthy cells. Specifically, SENTI-401 incorporates the following gene circuit:
| 1. | An iCAR with a NOT GATE gene circuit that restricts CAR-mediated cell killing to CRC cells that express CEA but not healthy cells that express an epithelial cell Safety Antigen, VSIG2. This NOT gate is designed to potentially reduce on-target, off-tumor toxicity, thus potentially enabling more effective treatment of CEA-expressing cancers. |
| 2. | An aCAR that targets CEA, a well-characterized antigen that is overexpressed in many cancers, including CRC. |
| 3. | A crIL-15 gene circuit to simultaneously provide both autocrine and paracrine-like IL-15 signaling in order to simultaneously stimulate surrounding immune cells and promote NK cell expansion, persistence and tumor killing. |
| 4. | An undisclosed potent immune effector to potentially enhance therapeutic function in solid tumors. |
SENTI-401 Supporting Data
Our CEA aCAR-NK cells kill CRC cells in an antigen-dependent manner
We have designed, built and evaluated hundreds of CEA aCAR constructs by varying the antigen binders, co-stimulatory domains, and other parameters. We screened these CEA aCAR constructs for robust and durable expression on NK cells, and cytotoxicity against CEA-positive tumor cell lines. As shown in the figure below, we evaluated our CEA aCAR-transduced NK cells, labeled as CEA aCAR #1 and CEA aCAR #2, for anti-tumor cytotoxic functions against a CEA-positive CRC tumor cell line, Ls174t. Both of these CEA aCAR constructs, in comparison to unengineered NK cells or NK cells engineered with a non-specific aCAR construct, mediated statistically significant cytotoxicity against Ls174t and released cytokines in an antigen-specific manner.
146
Our CEA aCAR-NK cells significantly reduced tumor burden in a human CRC xenograft tumor model in vivo
To assess the in vivo activity of our CAR-NK cells, we developed human xenograft mouse models of CEA-positive CRC tumors. We implanted Ls174t CRC cells in the peritoneal cavity of NSG mice and measured tumor burden and disease progression using a bioluminescent reporter. Mice were treated with PBS, or with one single dose of unengineered NK cells or CEA aCAR-NK cells. CEA aCAR-NK cells resulted in significant reduction (p < 0.05) in tumor burden in mice compared to control mice treated with unengineered NK cells, as shown in the figure below.
147
Utilization of the VISG2 protein as our NOT GATE gene circuit Safety Antigen
We have developed a robust Tumor-Associated Antigen and Safety Antigen Paired Discovery Platform for the development of NOT GATE CAR-NK therapies. Using this approach, we have identified genes that are differentially expressed in healthy versus tumor tissues and selected antigen candidates based on-target expression in tissues, subcellular localization, antigen topology or presence of extracellular domains and antibody availability. To protect healthy epithelial cells that also express CEA, we discovered VSIG2 as a Safety Antigen candidate. VSIG2 exhibits a favorable pattern of expression in the membrane of epithelial cells of the gastrointestinal tract and lungs, which are CEA-positive tissues that are most at risk of on-target, off-tumor toxicity. We further validated the expression of VSIG2 using immunohistochemistry, or IHC, in healthy tissues and confirmed the lack of expression in primary CRC tumor tissue samples. Specifically, IHC analyses of colorectal tumor tissues and healthy colon epithelium demonstrated that CEA is expressed in both healthy samples, as shown in the upper left of the figure below, and tumor samples, as shown in the lower left of the figure below. In addition, the Safety Antigen VSIG2 is only expressed in healthy colon epithelium, as shown in the upper right of the figure below, and not in tumor samples, as shown in the lower right of the figure below.

148
Leveraging these findings, we have constructed VISG2-iCARs that showed selective NOT gate functions in vitro. As shown in the figure below, we engineered NK cells to express both our CEA-aCAR and two different VSIG2-iCARs, each with a different intracellular inhibitory domain, at greater than 70% efficiency. These NOT gated CAR NK cells showed equivalent tumor killing relative to CEA aCAR only control NK cells, but were observed to significantly reduce cytotoxicity against a Model Healthy cell line, labelled CEACAM5+VSIG2+ below, by up to 43%.
149
To study the benefits of crIL-15 armed CAR-NK cells over unarmed CAR-NK cells, NSG mice with established Ls174t CEA+ tumor cells were treated with engineered NK cells. Mice received a supplement of recombinant human IL-2 (10,000 IU, 2x week) but no additional IL-15. Tumor burden was measured using bioluminescence of the tumor cells expressing fLuciferase reporter. Representative images taken at day 15 post tumor implantation (11 days after NK treatment) show that tumor burden was reduced in mice that were treated with CAR-NK cells armed with crIL-15 compared toCAR-NK cells with the CAR alone and no IL-15 (without any IL-15) and unengineered NK cells. This experiment demonstrates the advantage of crIL-15 in CEA-CAR-NK cells.
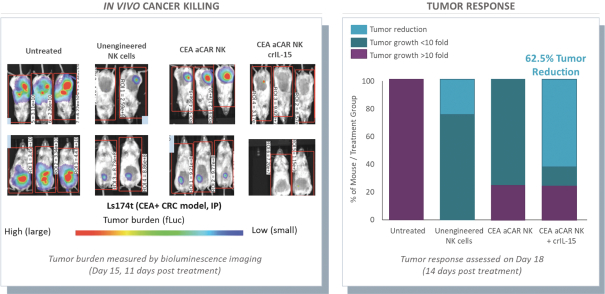
Development Plan and Key Next Steps for SENTI-401
In 2022, we intend to further evaluate different variants of the CEA aCAR and VSIG2 iCAR constructs, for example different aCAR co-stimulatory domains and iCAR inhibitory domains etc., in vitro and in vivo to determine the exact final coding sequences of these individual components. These finalized key gene circuit components would then be incorporated into an optimized vector backbone for cGMP manufacturing. Concurrent with anticipated cGMP manufacturing activities in 2022 and 2023, we anticipate that IND-enabling pharmacology and toxicology studies will be executed to support future submission of an IND application.
Portfolio Expansion Opportunities
Our Discovery Stage Programs
We believe our gene circuits can be readily adapted to new disease contexts to enable a variety of additional CAR-NK product candidates that address important cancers. For example, there are additional opportunities for the application of the NOT GATE gene circuit toward other solid and/or liquid tumor indications beyond SENTI-401. Toward that end, we have developed a Tumor-Associated Antigen and Safety Antigen Paired Discovery Platform to identify future opportunities.
Starting in 2024, we anticipate submitting approximately one IND application per year. Furthermore, we are actively pursuing the nomination and development of multiple product candidates that harness the full breadth of our gene circuit platform beyond Logic Gating and Multi-Arming of off-the-shelf CAR-NK cells within oncology. Our additional discovery efforts are focused on a diverse set of cell and gene therapy applications
150
outside of oncology. In particular, we have entered into collaborations with Spark Therapeutics, Inc. (acquired by Roche Holding AG) for the design of Smart Sensors for disease- and tissue-specific gene therapy, and with Bluerock Therapeutics, Inc. (acquired by Bayer AG) for the use of Smart Sensors and Regulator Dials for regenerative medicines.
Tumor-Associated Antigen and Safety Antigen Paired Discovery Platform
We have developed a proprietary Tumor-Associated Antigen and Safety Antigen Paired Discovery Platform to select and validate NOT GATE antigen candidates, as shown in the figure below. We have built a generalizable bioinformatics pipeline that uses RNA transcriptomics data to discover and prioritize tumor and healthy tissue Safety Antigens. We identify Tumor-Associated Antigens that are highly expressed in cancer cells with as little healthy tissue expression as possible, for example Tumor-Associated Antigen A in the figure below. We then discover healthy tissue selective Safety Antigens, for example Safety Antigen E in the figure below, that can protect those healthy tissues that express the Tumor-Associated Antigens, for example Tissues 2 and 5 in the figure below. This process looks at differences in Safety Antigen gene expression in healthy versus tumor tissue. Leads are selected based on the co-expression of Tumor-Associated Antigens and Safety Antigens in healthy tissues, the localization of the Safety Antigens to the cell surface, Safety Antigen topology (presence of extracellular domain) and Safety Antigen-specific antibody availability. Prioritized Tumor-Associated Antigen and Safety Antigen pairs are further validated in primary cancer and primary healthy tissue samples. We leveraged this platform to identify the Safety Antigen targets for the SENTI-202 and SENTI-401 programs, thus demonstrating our ability to target both liquid and solid tumors. This approach allows us to potentially expand our NOT GATE approach to additional cancer indications in which existing single-target approaches, such as monoclonal antibodies, antibody-drug conjugates and single-target CAR cells, are inadequate due to a lack of specificity for cancer cells.
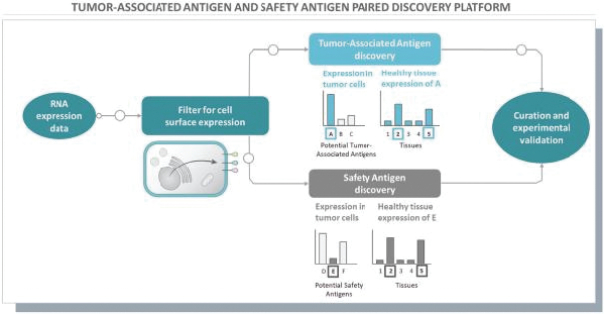
151
Portfolio Expansion Opportunities Outside of Oncology
Our additional discovery efforts are focused on cell and gene therapy applications that utilize other facets of our synthetic biology platform, including Smart Sensors and Regulator Dials in therapeutic areas beyond oncology.
Manufacturing
Manufacturing capabilities are central to our business strategy, since they can enable us to control the quality and supply of our off-the-shelf CAR-NK cell therapies for clinical studies and ultimately commercialization. A key advantage of off-the-shelf cell therapies, versus autologous products that use each patient’s own cells, is the ability to manufacture large batches of drug product from healthy donor cells that can be produced in advance of clinical use, and then stored in frozen vials. Upon commercialization, we expect to be able to make our cell therapies, if approved, broadly accessible in an off-the-shelf manner to cancer patients.
Our experienced manufacturing and technical operations team has established an innovative process for efficient production of our off-the-shelf CAR-NK cell product candidates. Critical aspects of the cell manufacturing process include the ability to perform four key steps in the CAR-NK cell manufacturing process:
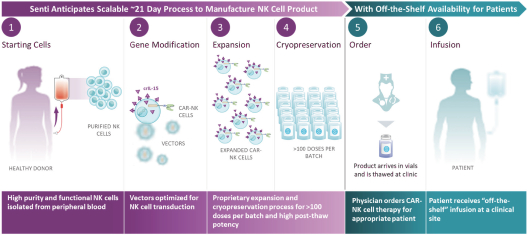
152
Step 1: Source, Isolate and Bank Purified NK Cells as Starting Cells.
Starting Cells are obtained from enriching and isolating NK cells from qualified healthy donors. Purified NK cells are subsequently cryopreserved and characterized for consistent performance, including assays for cell phenotype, transduction efficiency, cell expansion capability and anti-tumor cytotoxicity. For our initial SENTI-202 and SENTI-301 product candidates, we plan to derive Starting Cells from leukapheresis products collected from qualified healthy donors. From each leukapheresis collection, we will isolate and cryopreserve hundreds of millions of Starting Cells to support multiple product production batches. We believe that peripheral blood derived leukapheresis products are an attractive starting material source due to (i) a mature and validated commercial supply chain, (ii) the large number of purified NK cells per collection and (iii) our ability to characterize the NK cells prior to initiation of manufacturing. An analysis of over a dozen recent isolations performed from different healthy donors demonstrated that our process achieved greater than 95% NK cell purity, greater than 90% viability and up to 500 million NK cells per collection, as shown in the figure below:
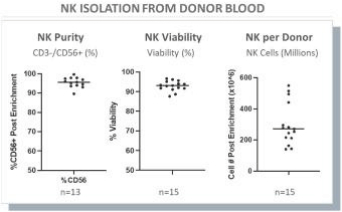
Step 2: Genetically Engineer Starting Cells with Gene Circuits.
We genetically modify our NK cells through a viral vector transduction process focused on enhancing gene circuit expression while minimizing impacts on compromising cell viability or cell expansion. To generate
our CAR-NK products, the Starting Cells are first thawed and activated. On a specific day post activation, the activated cells undergo our vector transduction process to genetically incorporate our gene circuits. The figure below shows transduction of our activated Starting Cells successfully reached approximately 50% transduction efficiency using a potentially clinically appropriate manufacturing process. Gene circuit-enabled CAR-NK cells were expanded over a total of 21 days. As shown in the center panel of the figure below, our transduction process was shown to have minimal impact on the cell expansion capability when comparing transduced CAR-NK cells versus unengineered NK cells. The transduced cells retained >90% viability with similar growth rate to unengineered NK cells through the 21st day.
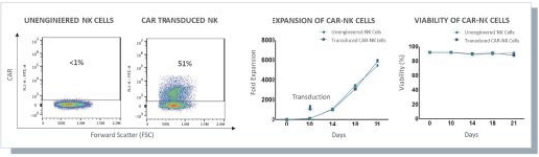
153
Step 3: Expand and Scale CAR-NK Cells.
Our expansion process is designed to generate large numbers of final product doses per manufacturing batch. This production process has resulted in high purity of NK cells (>98%) with minimal (<1%) detectable residual T cells. As shown in the figure below, our current process has produced greater than 6,000-fold expansion of CAR-NK cells in a 21 day process, achieving a planned clinical manufacturing scale of hundreds of patient doses per a single manufacturing batch. We are developing additional technologies and processes to further enhance NK cell expansion for commercial manufacturing, including alternative methods for cell activation and expansion and utilization of large-scale cell culture systems.
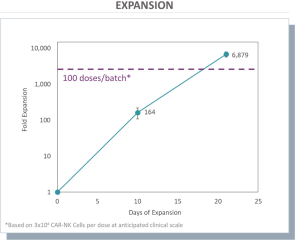
Step 4: Formulate and Cryopreserve CAR-NK Cells.
For freezing and distribution, we intend to formulate and cryopreserve our final product to retain viability, persistence and cytotoxic function post-thaw for off-the-shelf use. Each batch of CAR-NK cells will be filled into vials and cryopreserved for long term storage. The CAR-NK cell product candidates will be shipped in vials to clinical sites, where they will be thawed and infused on demand. We have demonstrated that cryopreserved CAR-NK cells can retain key functional properties required for cancer treatment, including stable transgene expression >44 days. As shown below, our cryopreserved CAR-NK cells retained viability and anti-tumor functions in both in vitro and in vivo models of AML:
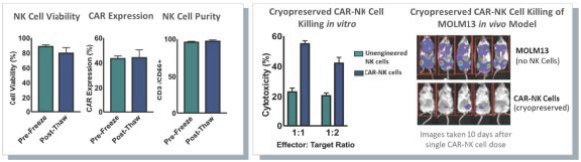
Technical Expertise and Facilities for Clinical and Commercial Manufacturing
Our corporate headquarters is located in South San Francisco, CA, where we lease approximately 40,000 square feet of research and development and corporate office space. In this location, we have approximately 10,000 square feet dedicated to manufacturing development labs. We have established research and development
154
teams with extensive experience in cell and gene therapy manufacturing operations, including vector process development, cell process development, analytical development, quality control and quality assurance. In June 2021, we signed a lease agreement for a property in Alameda, California with approximately 92,000 square feet and have begun construction on a state-of-the-art cGMP facility to support clinical and commercial-scale manufacturing of multiple off-the-shelf CAR-NK cell product candidates. This manufacturing facility is being designed as a customized end-to-end manufacturing solution to give us the ability to isolate NK cells, engineer these cells with proprietary gene circuits, perform cell culture expansion in large batches, and cryopreserve and store the final cGMP products.
We expect cGMP manufacturing facility startup by end of 2022 and present an overview of our clinical-scale GMP manufacturing process for gene-circuit-engineered NK cells at key technical conferences in 2022.
Our off-the-shelf production process and proprietary manufacturing capabilities are central to our business strategy of maintaining control over the quality and supply of our present and future candidates for off-the-shelf CAR-NK cell therapies. In addition, we believe that our proprietary manufacturing process enables an anticipated cost in line with competitive off-the-shelf production process estimates. Continued advancements in cell culture scale and process efficiencies may further reduce this cost over time.
In addition, we may also leverage our manufacturing facility to expand the application of our gene circuit technology to biomanufacturing in partnership with one or more third parties. See the section titled “Potential Collaboration Around Gene Circuits and GMP Manufacturing.”
Material License and Collaboration Agreements
Exclusive/Co-Exclusive Patent License Agreement with the National Cancer Institute for FLT3 Technology
In July 2020, we entered into an Exclusive/Co-Exclusive Patent License Agreement, as amended, or the NCI FLT3 Agreement, with the U.S. Department of Health and Human Services, as represented by the National Cancer Institute, or the NCI, under which the NCI granted us a worldwide, royalty-bearing, sublicensable license under the NCI’s patent rights related to FLT3-targeting chimeric antigen receptor, or CAR, technology (i) exclusively for the development of a universal or split CAR-based immunotherapy using T-cells or NK cells transduced with lentiviral vectors or other retroviral vectors, depending on the cell type, for the prophylaxis or treatment of cancers expressing FMS-like tyrosine kinase 3, or FLT3, where the CAR construct binds to specific domains and (ii) co-exclusively, with a third party, for the development of a multi-specific FLT3 CAR-based immunotherapy or FLT3-specific regulated or switch or Logic Gated CAR-based immunotherapy using T-cells or NK cells transduced with lentiviral vectors or other retroviral vectors, depending on the cell type, for the prophylaxis or treatment of FLT3-expressing cancers, where the CAR construct contains specific domains, in each case of (i) and (ii), to make and have made, use and have used, sell and have sold, offer to sell and import products covered by the licensed patent rights and to practice and have practiced processes covered by the licensed patent rights. In addition to the co-exclusive rights held by a third party, the foregoing license is subject to (a) certain rights of the United States government, including an irrevocable, non-exclusive, non-transferable, royalty-free license for the government to practice all licensed patent rights throughout the world and (b) the NCI’s reserved rights to grant a non-exclusive license to practice the licensed patent rights for purposes of internal research (and not for purposes of commercial manufacture or distribution) at an academic or corporate facility.
Pursuant to the NCI FLT3 Agreement, we must use commercially reasonable efforts to adhere to a commercial development plan, including by achieving certain specified development and regulatory milestones by certain dates, provided that we may request to extend the timelines of such milestones, which the NCI shall not unreasonably deny if the request is supported by a reasonable showing of our diligent performance under the commercial development plan. Upon the first commercial sale of a licensed product or process, we must also use commercially reasonable efforts to make the licensed product or process reasonably accessible to the United States public.
155
In consideration for the rights granted to us under the NCI FLT3 Agreement, we paid the NCI a one-time, non-refundable license issue fee of $75,000, and are required to pay the NCI a minimum flat annual royalty fee of a dollar amount in the low five digits. We are also obligated to pay the NCI certain development, regulatory and commercial milestone payments of up to an aggregate of $4.6 million for the first licensed product to achieve the applicable event. We will also be required to pay the NCI a tiered royalty in the low-single digit percentages on net sales of each licensed product by us and our sublicensees, subject to specified reductions and offsets, including against the minimum annual royalty payments. Further, the NCI is entitled to receive a portion of the amounts – excluding royalties and certain payments – we receive as a result of the grant of a sublicense under the rights granted under the NCI FLT3 Agreement at a percentage ranging from the low-single digits to low-double digits, depending on the stage of development at which the sublicense is granted. Additionally, we are obligated to pay for a portion of patent expenses that NCI incurred with respect to the licensed patent rights.
The NCI FLT3 Agreement will expire, on a licensed product-by-licensed product and country-by-country basis, on the expiration of all licensed patent rights that claim the applicable licensed product in the applicable country. Licensed patent rights are currently expected to expire in 2037, absent patent term extension or adjustment. We may terminate the NCI FLT3 Agreement in its entirety or with respect to a country for any reason by providing 60 days’ prior written notice to the NCI. The NCI may terminate the NCI FLT3 Agreement if (i) we breach any material obligations under the NCI FLT3 Agreement and fail to cure such breach within 90 days after receiving written notice thereof, or (ii) if the NCI reasonably determines that (a) we are not using commercially reasonable efforts to execute the commercial development plan, including the milestones specified therein, (b) we have willfully made a false statement or omitted a material fact in our license application or any report to the NCI, (c) we have committed a material breach of a covenant or agreement to the NCI, (d) we are not keeping the licensed products or licensed services reasonably available to the public after commercial use commences, or (e) we cannot reasonably justify a failure to comply with the domestic production requirement, in each case of (a) through (e), where we fail to alleviate the NCI’s concerns in 90 days. Additionally, the NCI reserves the right to terminate or modify the NCI FLT3 Agreement if the NCI determines that such action is necessary to meet the requirements for public use specified by federal regulations issued after the date of the license and these requirements are not reasonably satisfied by us.
Exclusive Patent License Agreement with the National Cancer Institute for GPC3 Technology
In February 2021, we entered into an Exclusive Patent License Agreement, or the NCI GPC3 Agreement, with the U.S. Department of Health and Human Services, as represented by the NCI, under which the NCI granted us an exclusive, royalty-bearing, sublicensable, worldwide license under the NCI’s patent rights related to glypican-3, or GPC3, targeting CAR technology to make and have made, use and have used, sell and have sold, offer to sell and import products covered by the licensed patent rights and to practice and have practiced processes covered by the licensed patent rights, for the development, production and commercialization of a monospecific CAR-based immunotherapy for the prophylaxis and treatment of GPC3 expressing human cancers using unmodified, off-the-shelf natural killer cells transduced with a viral vector that expresses a CAR, and a gene circuit regulating the expression of one or more armoring payloads, specifically excluding the use of autologous T cells or T cells that have been genetically modified to become off-the-shelf. The foregoing license is subject to (i) certain rights of the United States government, including an irrevocable, non-exclusive, nontransferable, royalty-free license for the government to practice all licensed patent rights throughout the world and (ii) the NCI’s reserved rights to grant a non-exclusive license to practice the licensed patent rights for purposes of internal research (and not for purposes of commercial manufacture or distribution) at an academic or corporate facility.
Pursuant to the NCI GPC3 Agreement, we must use commercially reasonable efforts to adhere to a commercial development plan, including by achieving certain specified development and regulatory milestones by certain dates, provided that we may request to extend the timelines of such milestones, which the NCI shall not unreasonably deny if the request is supported by a reasonable showing of our diligent performance under the commercial development plan. Upon the first commercial sale of a licensed product or process, we must also use
156
commercially reasonable efforts to make the licensed product or process reasonably accessible to the United States public.
In consideration for the rights granted to us under the NCI GPC3 Agreement, we paid the NCI a one-time, non-refundable license issue fee of $250,000, and are required to pay the NCI a minimum flat annual royalty fee of a dollar amount in the low five digits. We are obligated to pay the NCI certain development, regulatory and commercial milestone payments of an aggregate of $2,575,000 for the first licensed product to achieve the applicable events. We will also be required to pay the NCI a flat royalty in the low-single digit percentages on net sales of each licensed product by us and our sublicensees, subject to specified reductions and offsets, including against the minimum annual royalty payments. Further, the NCI is entitled to receive a portion of the amounts—excluding royalties and certain payments—we receive as a result of the grant of a sublicense under the rights granted under the NCI GPC3 Agreement at a percentage ranging from the low-single digits to low-double digits, depending on the stage of development at which the sublicense is granted. Additionally, we are obligated to pay for patent expenses that NCI incurred with respect to the licensed patent rights.
The NCI GPC3 Agreement will expire, on a licensed product-by-licensed product and country-by-country basis, on the expiration of all licensed patent rights that claim the applicable licensed product in the applicable country. Licensed patent rights are currently expected to expire in 2033, absent any patent term extension or adjustment. We may terminate the NCI GPC3 Agreement in its entirety or with respect to a country for any reason by providing 60 days’ prior written notice to the NCI. The NCI may terminate the NCI GPC3 Agreement if (i) we breach any material obligations under the NCI GPC3 Agreement and fail to cure such breach within 90 days after receiving written notice thereof, or (ii) if the NCI reasonably determines that (a) we are not executing the commercial development plan, including the milestones specified therein, (b) we have willfully made a false statement or omitted a material fact in our license application or any report to the NCI, (c) we have committed a material breach of a covenant or agreement to the NCI, (d) we are not keeping the licensed products or licensed services reasonably available to the public after commercial use commences, (e) we cannot reasonably satisfy unmet health and safety needs, (f) we cannot reasonably justify a failure to comply with the domestic production requirement or (g) we have been found by a court to have violated antitrust laws in connection with our performance under the NCI GPC3 Agreement, in each case of (a) through (f), where we fail to alleviate the NCI’s concerns in 90 days. Additionally, the NCI reserves the right to terminate or modify the NCI GPC3 Agreement if the NCI determines that such action is necessary to meet the requirements for public use specified by federal regulations issued after the date of the license and these requirements are not reasonably satisfied by us.
Exclusive Patent License Agreement with the National Cancer Institute for CD33 Technology
In May 2021, we entered into an Exclusive Patent License Agreement, or the NCI CD33 Agreement, with the U.S. Department of Health and Human Services, as represented by the NCI, under which the NCI granted us an exclusive, royalty-bearing, sublicensable, worldwide license under the NCI’s patent rights related to CD33 targeting CAR technology to make and have made, use and have used, sell and have sold, offer to sell and import products covered by the licensed patent rights and to practice and have practiced processes covered by the licensed patent rights, for the development of a CD33-specific logic-gated CAR-based immunotherapy using autologous human T cells transduced with lentiviral vectors or off-the-shelf human NK cells transduced with retroviral vectors for the prophylaxis or treatment of CD33-expressing cancers. The foregoing license is subject to (i) certain rights of the United States government, including an irrevocable, non-exclusive, nontransferable, royalty-free license for the government to practice all licensed patent rights throughout the world and (ii) the NCI’s reserved rights to grant a non-exclusive license to practice the licensed patent rights for purposes of internal research (and not for purposes of commercial manufacture or distribution) at an academic or corporate facility.
Pursuant to the NCI CD33 Agreement, we must use commercially reasonable efforts to adhere to a commercial development plan, including by achieving certain specified development and regulatory milestones
157
by certain dates, provided that we may request to extend the timelines of such milestones, which the NCI shall not unreasonably deny if the request is supported by a reasonable showing of our diligent performance under the commercial development plan. Upon the first commercial sale of a licensed product or process, we must also use commercially reasonable efforts to make the licensed product or process reasonably accessible to the United States public.
In consideration for the rights granted to us under the NCI CD33 Agreement, we paid the NCI a one-time, non-refundable license issue fee of $150,000, and are required to pay the NCI a minimum flat annual royalty fee of a dollar amount in the low five digits. We are obligated to pay the NCI certain development, regulatory and commercial milestone payments of an aggregate of $3.5 million for the first licensed product to achieve the applicable events. We will also be required to pay the NCI a flat royalty in the low single-digit percentages on net sales of each licensed product by us and our sublicensees, subject to specified reductions and offsets, including against the minimum annual royalty payments. Further, the NCI is entitled to receive a portion of the amounts—excluding royalties and certain payments—we receive as a result of the grant of a sublicense under the rights granted under the NCI CD33 Agreement at a percentage ranging from the low-single digits to low-double digits, depending on the stage of development at which the sublicense is granted. Additionally, we are obligated to pay for patent expenses that NCI incurred with respect to the licensed patent rights.
The NCI CD33 Agreement will expire, on a licensed product-by-licensed product and country-by-country basis, on the expiration of all licensed patent rights that claim the applicable licensed product in the applicable country. Licensed patent rights are currently expected to expire in 2039, absent any patent term extension or adjustment. We may terminate the NCI CD33 Agreement in its entirety or with respect to a country for any reason by providing 60 days’ prior written notice to the NCI. The NCI may terminate the NCI CD33 Agreement if (i) we breach any material obligations under the NCI CD33 Agreement and fail to cure such breach within 90 days after receiving written notice thereof, or (ii) if the NCI reasonably determines that (a) we are not executing the commercial development plan, including the milestones specified therein, (b) we have willfully made a false statement or omitted a material fact in our license application or any report to the NCI, (c) we have committed a material breach of a covenant or agreement to the NCI, (d) we are not keeping the licensed products or licensed services reasonably available to the public after commercial use commences, (e) we cannot reasonably satisfy unmet health and safety needs, (f) we cannot reasonably justify a failure to comply with the domestic production requirement or (g) we have been found by a court to have violated antitrust laws in connection with our performance under the NCI CD33 Agreement, in each case of (a) through (f), where we fail to alleviate the NCI’s concerns in 90 days. Additionally, the NCI reserves the right to terminate or modify the NCI CD33 Agreement if the NCI determines that such action is necessary to meet the requirements for public use specified by federal regulations issued after the date of the license and these requirements are not reasonably satisfied by us.
Research Collaboration and License Agreement with Spark Therapeutics, Inc.
In April 2021, we entered into a Research Collaboration and License Agreement, or the Spark Agreement, with Spark Therapeutics, Inc., or Spark. Under the Spark Agreement, we engaged in a collaborative research program with Spark to design, build and test synthetic promoters that are intended to have each one of five sets of desired characteristics, or promoter profiles. Spark is obligated to reimburse us for our costs and expenses incurred in connection with the conduct of the research program. Upon completion of work under the research program for a particular promoter profile, Spark may select up to a specified number of synthetic promoters for such promoter profile on which it can conduct in vitro and in vivo evaluation activities.
We granted option rights to Spark, on a promoter profile-by-promoter profile basis, to obtain an exclusive, royalty-bearing, sublicensable, worldwide license under our intellectual property rights to develop, manufacture, commercialize and otherwise exploit, for the cure, treatment, palliation, prevention or diagnosis of specified indications, or a licensed field, in vivo gene therapy products incorporating an applicable synthetic promoter that is developed under the Spark Agreement with respect to such promoter profile and is directed towards specified cell types in the central nervous system, eye, or liver. Spark may exercise its option for a single synthetic
158
promoter per promoter profile together with certain related synthetic promoters, or licensed promoters, prior to the expiration of the applicable evaluation period. During the research program and until the expiration of the evaluation period for each promoter profile, we are obligated to work exclusively with Spark on the development, manufacture and commercialization of in vivo gene therapy products incorporating synthetic promoters intended to have the same cell type specificity as such promoter profile.
After exercise of an option, Spark will be responsible for all development, manufacture, commercialization and exploitation in the licensed field, at its own cost and expense, of all in vivo gene therapy products containing an applicable licensed promoter, and we will retain the right to develop, manufacture, commercialize and exploit other products that incorporate the licensed promoters as well as in vivo gene therapy products that incorporate the licensed promoters for uses outside the licensed field. If Spark does not exercise an option for a particular promoter profile prior to the expiration of the evaluation period for such promoter profile, we will retain all rights to the synthetic promoters developed under the Spark Agreement without any further obligations to Spark for such promoter profile.
Pursuant to the Spark Agreement, we received an upfront payment from Spark of $3 million. If Spark exercises an option for a particular promoter profile, it will be required to pay us an option exercise fee in the low to mid- single digit millions. For each licensed promoter-containing in vivo gene therapy product, or licensed product, developed and commercialized by Spark or its affiliates or sublicensees, we are eligible to receive development, regulatory and commercialization milestone payments from Spark up to an aggregate dollar amount in the mid teens millions, and sales milestone payments from Spark up to an aggregate dollar amount in the low hundred millions. In total, we are potentially eligible to receive upfront, opt-in and milestone payments exceeding $645 million if Spark exercises its options for all five promoter profiles and Spark, its affiliates and its sublicensees successfully develop and commercialize five licensed products; we will be eligible to receive additional milestone payments if additional licensed products are developed and commercialized by Spark, its affiliates and its sublicensees. Further, Spark will be obligated to pay us royalties in the low-single digits percentage on net sales of each licensed product sold by Spark, its affiliates and its sublicensees, subject to specified reductions and offsets. Spark’s obligation to pay royalties to us will expire for each licensed product when certain licensed patents and regulatory exclusivities have expired in the country of sale and a minimum number of years has elapsed since the first commercial sale of such licensed product in such country.
The Spark Agreement will expire at the end of the last evaluation period if Spark does not exercise any of its options. If Spark exercises at least one option, then the Spark Agreement will expire, on a licensed product-by-licensed product and country-by-country basis, upon the expiration of Spark’s royalty obligation for such licensed product in such country. Spark may terminate the Spark Agreement in its entirety, or on a promoter profile-by-promoter profile or licensed promoter-by-licensed promoter basis, following a specified notice period. Either party may terminate the Spark Agreement in its entirety or in part if the other party fails to cure its material breach of the Spark Agreement within a specified cure period, or immediately if the other party becomes bankrupt or insolvent. We may terminate the Spark Agreement if Spark or any of its affiliates commences any action challenging the validity or enforceability of the licensed patents, other than in certain specified circumstances, or if Spark’s sublicensee challenges our licensed patents, under certain specified circumstances.
Collaboration and Option Agreement with BlueRock Therapeutics LP
In May 2021, we entered into a Collaboration and Option Agreement, or the BlueRock Agreement, with BlueRock Therapeutics LP, or BlueRock. BlueRock is a wholly-owned subsidiary of Bayer Healthcare LLC. Bayer Healthcare LLC’s parent company is Bayer AG, which served as the lead investor in our Series B financing through its Leaps by Bayer unit. Under the BlueRock Agreement, we have engaged in three collaboration programs with BlueRock to research and develop gene circuits that have specified functions. We are responsible for up to $10 million in costs and expenses incurred in connection with our conduct of research activities under an agreed-upon research plan. If the parties mutually agree to add new research activities to the
159
research plan, then BlueRock will be obligated to reimburse us for the costs and expenses that we incur in connection with the agreed-upon additional research activities that, together with costs and expenses incurred under the initial research plan, exceed $10 million. We have not yet received any payment from BlueRock under the BlueRock Agreement and we do not have any obligations to make any payments to BlueRock under the BlueRock Agreement. We are obligated to use commercially reasonable efforts to conduct the research activities assigned to us under the research plan. If we materially breach that obligation and do not cure it within a specified period, BlueRock will have the right to receive a transfer of technology and perform the remainder of the research plan at its own expense.
Upon completion of work under a research plan for a collaboration program, the joint steering committee established by the parties will identify, subject to a specified maximum, a number of gene circuits per collaboration program, or option gene circuits, that have been successfully developed under such collaboration program. We have granted to BlueRock an option, on a collaboration program-by-collaboration program basis, to obtain an exclusive or non-exclusive license under our intellectual property rights to develop, manufacture and commercialize, for the prevention, treatment or palliation of specified indications, or a licensed field, cell therapy products that contain cells of specified types that incorporate an option gene circuit from such collaboration program or a closely related derivative gene circuit. For each collaboration program, BlueRock may conduct evaluation activities on the option gene circuits from such collaboration program to determine whether to exercise its option, and BlueRock may exercise its option to such option gene circuits together with certain closely related derivative gene circuits, or licensed gene circuits, prior to the expiration of a certain time period, or the option exercise period, which includes a minimum amount of time after the expiration of the three-year research term, delivery of a data package to BlueRock, and completion of a transfer of technology to enable BlueRock’s evaluation activities, whichever happens last. If BlueRock exercises its option for a collaboration program, the parties shall negotiate the financial terms, which will be within certain pre-agreed parameters and may be determined by baseball arbitration if the parties do not reach agreement within the specified negotiation period, and enter into an otherwise agreed-upon written license agreement, or a commercial license. If the parties enter into a commercial license, BlueRock will be responsible, at its sole expense, for the development, manufacture and commercialization, in the applicable licensed field, of cell therapy products containing cells of an applicable type that incorporate an applicable licensed gene circuit, and we will be eligible to receive from BlueRock development, regulatory and commercialization milestone payments, in amounts to be agreed-upon before entry into the commercial license, and royalties, subject to negotiation, equal to low single digit percentages of net sales of applicable cell therapy products sold by BlueRock, its affiliates and its sublicensees, subject to specified reductions and offsets. If BlueRock does not exercise its option for a collaboration program prior to the expiration of the applicable option exercise period, then we will retain all rights to the gene circuits developed under such collaboration program without any further obligations to BlueRock.
For each collaboration program, we are obligated to work exclusively with BlueRock on the development, manufacture and commercialization, in the applicable licensed field, of cell therapy products that contain cells of specified types that incorporate the specific type of gene circuit for such collaboration program. The end date for this exclusivity obligation for each collaboration program will depend upon whether BlueRock exercises its option for such collaboration program and, if it does, whether the parties enter into a commercial license for such collaboration program. If BlueRock does not exercise its option, then it will end on the expiration of the applicable option exercise period. If BlueRock exercises its option but the parties do not enter into a commercial license, then it will end after a specified time following expiration of the applicable negotiation or baseball arbitration period for the commercial license. If BlueRock exercises its option and the parties enter into a commercial license, then it will end a certain amount of time after the later of completion of research activities or execution of the commercial license.
In addition to the option described above, we granted a right of first negotiation to BlueRock, on a collaboration program-by-collaboration program basis, to obtain a license under our intellectual property rights to research, develop, manufacture and commercialize, for the prevention, treatment or palliation of a specified disease area, or the negotiation field, cell therapy products containing cells of a specified type, or the negotiation
160
cells, that incorporate an applicable efficacy gene circuit developed under such collaboration program. This right of first negotiation does not overlap with the option described above because it pertains to different combinations of indications, cell types and gene circuits. Starting from the effective date of the BlueRock Agreement and, on a collaboration program-by-collaboration program basis, continuing for twelve months or, if later, until the completion of a certain portion of the research plan for such collaboration program, we are obligated to work exclusively with BlueRock on the development, manufacture and commercialization, in the negotiation field, of cell therapy products containing negotiation cells that incorporate the specific type of gene circuit for such collaboration program.
The BlueRock Agreement will expire, on a collaboration program-by-collaboration program basis, upon the earliest of the expiration of the option exercise period for such collaboration program, the effective date of the commercial license, the expiration of the applicable negotiation or baseball arbitration period for the commercial license, or the date the parties mutually agree to cease negotiations for the commercial license. Such expiration shall occur no later than January 2026 unless the parties mutually agree to extend the research term. BlueRock may terminate the BlueRock Agreement in its entirety, or on a collaboration program-by-collaboration program basis, following a specified notice period. Either party may terminate the BlueRock Agreement if the other party fails to cure its material breach of the BlueRock Agreement within a specified cure period, or immediately if the other party becomes bankrupt or insolvent. We may terminate the BlueRock Agreement if BlueRock or any of its affiliates commences any action challenging the validity or enforceability of our patents, other than in certain specified circumstances, or if BlueRock’s sublicensee challenges our patents under certain specified circumstances.
Other Agreements
National Cancer Institute (NCI) Contract to Support Development of SENTI-202 in Acute Myeloid Leukemia
In September 2021, we were awarded funding from the National Cancer Institute in the form of a Small Business Innovation Research (SBIR) contract to support further development of SENTI-202 for acute myeloid leukemia (AML) towards clinical development. The Direct to Phase II SBIR contract will provide funding over two years from the NCI of the National Institutes of Health (NIH) and is titled: “Logic-Gated Chimeric Antigen Receptor-Natural Killer Cell Therapy for Acute Myeloid Leukemia.” With the award of this contract, the SENTI-202 program will be funded in part with Federal funds from the National Cancer Institute, National Institutes of Health, Department of Health and Human Services, under Contract No. 75N91021C00026.
161
Potential Collaboration Around Gene Circuits and GMP Manufacturing
We may seek to leverage our manufacturing capabilities and proposed cGMP facility to enable us to expand the application of our gene circuit technology through a partnership in the biomanufacturing space. While we intend to use our proprietary gene circuit technology and manufacturing facility primarily for therapeutic product development and commercialization, our technology and facility can also be applied to noncompetitive biomanufacturing applications, which we believe is an approach well-suited for partnering. A potential biomanufacturing partnership could involve retaining operational control and manufacturing supply of our therapeutic candidates, while our partner could control part of the facility for its own use. The following is an illustrative depiction of the framework for a potential biomanufacturing partnership:
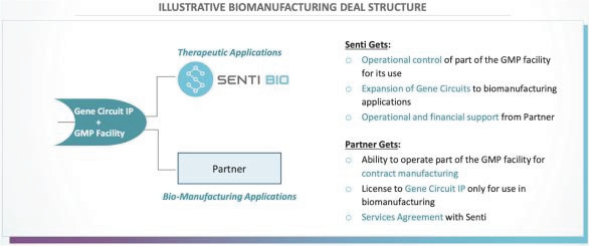
We currently have no agreements or commitments for a manufacturing partnership, and we could determine to advance our manufacturing plans without a partner.
Competition
We are aware of other companies that are developing technologies that may compete with elements of our gene circuit platform technologies, including A2 Biotherapeutics, Inc., Arsenal Biosciences, Inc., Beam Therapeutics Inc., CRISPR Therapeutics AG, Encoded Therapeutics, Inc., ImmPACT Bio USA, Inc., Intellia Therapeutics, Inc., MeiraGTx Holdings plc, Obsidian Therapeutics, Inc. and Strand Therapeutics Inc. We are also aware of other companies that are focused on the application of engineered CAR-based immune cell therapies, including NK cells, to oncology, and such competitors include Allogene Therapeutics, Inc., Artiva Biotherapeutics, Inc., Atara Biotherapeutics, Inc., Bristol-Myers Squibb Company, Century Therapeutics, Inc., Caribou Biosciences, Inc., Catamaran Bio, Inc., Cytovia Therapeutics, Inc., Editas Medicine, Inc., Fate Therapeutics, Inc., Gilead Sciences, Inc., Lyell Immunopharma, Inc., Nkarta, Inc., Sana Biotechnology, Inc., Shoreline Biosciences, Inc., Takeda Pharmaceutical Company and Vor Biopharma Inc. Some of these companies may have substantially greater financial and other resources than we have, such as larger research and development staff and well-established marketing and salesforces. Mergers and acquisitions in the biotechnology industry may result in even greater resource concentration among a smaller number of competitors. Smaller or early-stage companies may also prove to be significant competitors, either alone or through collaborative arrangements with large and established companies.
These companies compete with us in recruiting scientific and managerial talent. Our success will partially depend on our ability to obtain, maintain, enforce and defend patents and other intellectual property rights with respect to our product candidates. Our competitors may obtain FDA or other regulatory approval for their product candidates more rapidly than we may obtain approval for ours, which could result in our competitors establishing a strong market position before we are able to enter the market.
162
Our commercial opportunity could be reduced or eliminated if our competitors develop and commercialize products that are safer, more effective, have fewer or less severe side effects, are more convenient or are less expensive than any products that we may develop.
Intellectual Property
Intellectual property is the foundation of our company and not only defines who we are, but is the lens through which we implement our business strategy and research and development. Our overall strategy is to own and control all intellectual property related to our gene circuits. We protect our proprietary technology and intellectual property rights through a combination of wholly-owned patent rights, licensed patent rights in particular fields of use, trademark rights, trade secrets and know-how, contractual provisions and confidentiality procedures. Our general strategy includes protecting our proprietary technology and intellectual property rights domestically and in certain key foreign markets. We continually grow and supplement our intellectual property portfolio with new filings and applications not only to strengthen the protection of proprietary technology and intellectual property rights, but also to protect and support the development and commercialization of current and future product candidates. In addition, we always seek to protect our technological innovations and branding efforts by filing new patent and trademark applications at the appropriate time and strategically relevant jurisdictions.
Our patent portfolio relates to our ongoing research and development activities and includes a combination of patents and pending patent applications licensed from third parties, pending patent applications jointly owned with third parties, and patent applications solely owned by us. The patents and pending patent applications in our portfolio can be categorized as relating to our gene circuit platform technologies, including Logic Gating gene circuits, Multi-Arming gene circuits, Regulator Dial gene circuits and Smart Sensor gene circuits; our product candidates, including SENTI-202, SENTI-301 and SENTI-401, as well as other pipeline product candidates; and alternative technologies. Certain of our issued patents and pending patent applications are exclusively or co-exclusively licensed to us in certain therapeutic fields of use from third-party licensors. As of June 17, 2022, our patent portfolio includes four issued U.S. patents, four issued foreign patents, 25 pending U.S. provisional and utility patent applications, 95 pending foreign utility patent applications, and 14 Patent Cooperation Treaty, or PCT, applications, that have not entered national stage.
With respect to our issued patents, we own one issued U.S. patent and we license from the NCI two issued U.S. patents and four issued foreign patents. Further, we license from a third-party licensor one additional U.S. issued patent. With respect to our pending provisional and utility patent applications, we own or co-own 22 pending U.S. provisional and utility patent applications, 72 pending foreign utility patent applications and 14 PCT applications, that have not entered national stage, and we license from third parties (including the NCI) three pending U.S. utility patent applications and 23 pending foreign utility patent applications. The estimated expiration dates of the issued patents are between 2030 and 2039, and the estimated expiration dates of the pending provisional and utility patent applications, to the extent they issue, will be between 2036 and 2043, without accounting for any patent term adjustments or extensions.
We have one issued U.S. patent, two pending U.S. provisional and utility patent applications, and 18 pending foreign utility applications licensed from the NCI. In addition, we have four solely owned pending U.S. provisional and utility patent applications, 18 solely owned pending foreign utility applications, and five solely owned PCT applications that have not entered national stage related to our SENTI-202 product candidate. These patent applications relate to composition of matter, method of preparing and method of treatment. The estimated expiration date of the issued patent is 2038, and the estimated expiration dates of the pending provisional and utility patent applications, to the extent they issue, will be between 2037 and 2043, without accounting for any patent term adjustments or extensions.
We have one issued U.S. patent and four issued foreign patents licensed from the NCI, seven solely owned pending U.S. provisional and utility patent applications, 28 solely owned pending foreign utility applications, and
163
seven PCT applications that have not entered national stage related to our SENTI-301 product candidate. These patent applications relate to composition of matter, method of preparing and method of treatment. The issued patents are expected to expire in 2033, without accounting for any patent term adjustments or extensions. The estimated expiration dates of the pending provisional and utility patent applications, to the extent they issue, will be between 2039 and 2043, without accounting for any patent term adjustments or extensions.
We solely own or co-own six pending U.S. provisional and utility patent applications, 20 pending foreign utility applications and six PCT applications that have not entered national stage related to our SENTI-401 product candidate. These patent applications relate to composition of matter, method of preparing and method of treatment. The estimated expiration dates of the pending provisional and utility patent applications, to the extent they issue, will be between 2039 and 2043, without accounting for any patent term adjustments or extensions.
We also utilize trademark rights to protect our brand. As of June 17, 2022, we are listed as owners of one registered United States trademark, five United States pending and allowed trademarks, four foreign registered trademarks, and 12 foreign granted trademarks. We own the filed trademarks “SENTI,” “SENTI BIOSCIENCES,” “SENTI BIO,” Senti’s “S” logo, and “PRO-DIAL” in the United States and in certain foreign countries. We have also registered multiple internet domain names to further supplement the protection of our brand.
Government Regulation
The U.S. Food and Drug Administration, or FDA, and other regulatory authorities at federal, state and local levels, as well as in foreign countries, extensively regulate, among other things, the research, development, testing, manufacture, quality control, import, export, safety, effectiveness, labeling, packaging, storage, distribution, record keeping, approval, advertising, promotion, marketing, sampling post-approval monitoring and post-approval reporting of biologics such as those we are developing. Any product candidates that we develop must be approved by the FDA before they may be legally marketed in the United States and by the appropriate foreign regulatory agency before they may be legally marketed in those foreign countries. Generally, our activities in other countries will be subject to regulation that is similar in nature and scope as that imposed in the United States, although there can be important differences.
U.S. Biologics Regulation
In the United States, biological products are subject to regulation under the Federal Food, Drug, and Cosmetic Act, the Public Health Service Act, and other federal, state, local and foreign statutes and their implementing regulations. The process of obtaining regulatory approvals and the subsequent compliance with appropriate federal, state, local and foreign statutes and regulations require the expenditure of substantial time and financial resources. The process required by the FDA before biologics may be marketed in the United States generally involves the following:
| • | completion of preclinical laboratory tests and animal studies performed in accordance with the FDA’s Good Laboratory Practice requirements, or GLP; |
| • | submission to the FDA of an investigational new drug application, or IND, which must become effective before clinical trials may begin; |
| • | approval by an institutional review board, or IRB, or ethics committee at each clinical site before the trial is commenced; |
| • | performance of adequate and well-controlled human clinical trials according to the FDA’s regulations commonly referred to as good clinical practice, or GCP, regulations and any additional requirements for the protection of human research subjects and their health information to establish the safety, purity and potency of the proposed biologic product candidate for its intended purpose; |
| • | preparation of and submission to the FDA of a Biologics License Application, or BLA, after completion of all pivotal clinical trials; |
164
| • | satisfactory completion of an FDA Advisory Committee review, if applicable; |
| • | a determination by the FDA within 60 days of its receipt of a BLA to file the application for review; |
| • | satisfactory completion of an FDA pre-approval inspection of the manufacturing facility or facilities at which the proposed product is produced to assess compliance with cGMP, and to assure that the facilities, methods and controls are adequate to preserve the biological product’s continued safety, purity and potency and, if applicable, to assess compliance with the FDA’s current Good Tissue Practice, or cGTP, requirements for the use of human cellular and tissue products, and of selected clinical investigation sites to assess compliance with GCPs; |
| • | potential FDA audit of the nonclinical and clinical study sites that generated the data in support of the BLA; and |
| • | FDA review and approval of the BLA to permit commercial marketing of the product for particular indications for use in the United States. |
Before testing any biological product candidate in humans, the product candidate enters the preclinical testing stage. Preclinical tests, also referred to as nonclinical studies, include laboratory evaluations of product chemistry, toxicity and formulation, as well as animal studies to assess the potential safety and activity of the product candidate. The conduct of the preclinical tests must comply with federal regulations and requirements including GLPs.
Prior to beginning the first clinical trial with a product candidate in the United States, we must submit an IND to the FDA. An IND is a request for authorization from the FDA to administer an investigational new drug to humans. The central focus of an IND submission is on the general investigational plan and the protocol(s) for clinical studies. Some preclinical testing may continue even after the IND is submitted. The IND also includes results of animal and in vitro studies assessing the toxicology, pharmacokinetics, pharmacology and pharmacodynamic characteristics of the product; chemistry, manufacturing and controls information; and any available human data or literature to support the use of the investigational product. An IND must become effective before human clinical trials may begin. The IND automatically becomes effective 30 days after receipt by the FDA, unless the FDA, within the 30-day time period, raises safety concerns or questions about the proposed clinical trial. In such a case, the IND may be placed on clinical hold and the IND sponsor and the FDA must resolve any outstanding concerns or questions before the clinical trial can begin. Submission of an IND therefore may or may not result in FDA authorization to begin a clinical trial.
In addition to the submission of an IND to the FDA before initiation of a clinical trial in the United States, certain human clinical trials involving recombinant or synthetic nucleic acid molecules are subject to oversight of institutional biosafety committees, or IBCs, as set forth in the National Institutes of Health, or NIH, Guidelines for Research Involving Recombinant DNA Molecules, or the NIH Guidelines. Specifically, under the NIH Guidelines, supervision of human gene transfer trials includes evaluation and assessment by an IBC, a local institutional committee that reviews and oversees research utilizing recombinant or synthetic nucleic acid molecules at that institution. The IBC assesses the safety of the research and identifies any potential risk to public health or the environment, and such review may result in some delay before initiation of a clinical trial. While the NIH Guidelines are not mandatory unless the research in question is being conducted at or sponsored by institutions receiving NIH funding of recombinant or synthetic nucleic acid molecule research, many companies and other institutions not otherwise subject to the NIH Guidelines voluntarily follow them.
Clinical trials involve the administration of the investigational product to human subjects under the supervision of qualified investigators in accordance with GCPs, which include the requirement that all research subjects provide their informed consent for their participation in any clinical study. Clinical trials are conducted under protocols detailing, among other things, the objectives of the study, the parameters to be used in monitoring safety and the effectiveness criteria to be evaluated. A separate submission to the existing IND must be made for each successive clinical trial conducted during product development and for any subsequent protocol
165
amendments. Furthermore, an independent IRB for each site proposing to conduct the clinical trial must review and approve the plan for any clinical trial and its informed consent form before the clinical trial begins at that site, and must monitor the study until completed. An IRB is charged with protecting the welfare and rights of trial participants and considers such items as whether the risks to individuals participating in the clinical trials are minimized and are reasonable in relation to anticipated benefits. The IRB also approves the informed consent form that must be provided to each clinical trial subject or his or her legal representative and must monitor the clinical trial until completed. Regulatory authorities, the IRB or the sponsor may suspend a clinical trial at any time on various grounds, including a finding that the subjects are being exposed to an unacceptable health risk or that the trial is unlikely to meet its stated objectives. Some studies also include oversight by an independent group of qualified experts organized by the clinical study sponsor, known as a data safety monitoring board, which provides authorization for whether or not a study may move forward at designated check points based on access to certain data from the study and may halt the clinical trial if it determines that there is an unacceptable safety risk for subjects or other grounds, such as no demonstration of efficacy. There are also requirements governing the reporting of ongoing clinical studies and clinical study results to public registries.
For purposes of BLA approval, human clinical trials are typically conducted in three sequential phases that may overlap or be combined:
| • | Phase 1—The investigational product is initially introduced into healthy human subjects or patients with the target disease or condition. These studies are designed to test the safety, dosage tolerance, absorption, metabolism and distribution of the investigational product in humans, the side effects associated with increasing doses, and, if possible, to gain early evidence on effectiveness. In the case of some products for severe or life-threatening diseases, such as cancer, especially when the product may be too inherently toxic to ethically administer to healthy volunteers, the initial human testing is often conducted in patients. |
| • | Phase 2—The investigational product is administered to a limited patient population with a specified disease or condition to evaluate the preliminary efficacy, optimal dosages, dose tolerance and dosing schedule and to identify possible adverse side effects and safety risks. Multiple Phase 2 clinical trials may be conducted to obtain information prior to beginning larger and more expensive Phase 3 clinical trials. |
| • | Phase 3—The investigational product is administered to an expanded patient population to further evaluate dosage, to provide statistically significant evidence of clinical efficacy and to further test for safety, generally at multiple geographically dispersed clinical trial sites. These clinical trials are intended to establish the overall risk/benefit ratio of the investigational product and to provide an adequate basis for product approval. Generally, two adequate and well-controlled Phase 3 clinical trials are required by the FDA for approval of a BLA. |
In some cases, the FDA may require, or companies may voluntarily pursue, additional clinical trials after a product is approved to gain more information about the product in the intended therapeutic indication, particularly for long-term safety follow-up. Completion of these so-called Phase 4 studies may also be made a condition to approval of the BLA.
Concurrent with clinical trials, companies may complete additional animal studies and develop additional information about the biological characteristics of the product candidate, and must finalize a process for manufacturing the product in commercial quantities in accordance with cGMP requirements. The manufacturing process must be capable of consistently producing quality batches of the product candidate and, among other things, must develop methods for testing the safety, purity and potency of the final product. Additionally, appropriate packaging must be selected and tested, and stability studies must be conducted to demonstrate that the product candidate does not undergo unacceptable deterioration over its shelf life.
166
BLA Submission and Review by the FDA
Assuming successful completion of all required testing in accordance with all applicable regulatory requirements, the results of product development, nonclinical studies and clinical trials are submitted to the FDA as part of a BLA requesting approval to market the product for one or more indications. The BLA must include all relevant data available from preclinical and clinical studies, including negative or ambiguous results as well as positive findings, together with detailed information relating to the product’s chemistry, manufacturing, controls and proposed labeling, among other things. Data can come from company-sponsored clinical studies intended to test the safety and effectiveness of a use of the product, or from a number of alternative sources, including studies initiated by independent investigators. To support marketing approval, the data submitted must be sufficient in quality and quantity to establish the safety and effectiveness of the investigational drug product to the satisfaction of the FDA. The submission of a BLA requires payment of a substantial application user fee to the FDA, unless a waiver or exemption applies.
Within 60 days following submission of the application, the FDA reviews a BLA submitted to determine if it is substantially complete before the FDA accepts it for filing. The FDA may refuse to file any BLA that it deems incomplete or not properly reviewable at the time of submission and may request additional information. In this event, the BLA must be resubmitted with the additional information. The resubmitted application also is subject to review before the FDA accepts it for filing.
Once a BLA has been accepted for filing, the FDA’s goal is to review standard applications within ten months after the filing date, or, if the application qualifies for priority review, six months after the FDA accepts the application for filing. In both standard and priority reviews, the review process may also be extended by FDA requests for additional information or clarification. The FDA reviews a BLA to determine, among other things, whether a product is safe, pure and potent and the facility in which it is manufactured, processed, packed or held meets standards designed to assure the product’s continued safety, purity and potency. The FDA may also convene an advisory committee to provide clinical insight on application review questions. An advisory committee is a panel of independent experts, including clinicians and other scientific experts, that reviews, evaluates and provides a recommendation as to whether the application should be approved and under what conditions. The FDA is not bound by the recommendations of an advisory committee, but it considers such recommendations carefully when making decisions.
Before approving a BLA, the FDA will typically inspect the facility or facilities where the product is manufactured. The FDA will not approve an application unless it determines that the manufacturing processes and facilities are in compliance with cGMP and adequate to assure consistent production of the product within required specifications. For a product candidate that is also a human cellular or tissue product, the FDA also will not approve the application if the manufacturer is not in compliance with cGTPs. These are FDA regulations that govern the methods used in, and the facilities and controls used for, the manufacture of human cells, tissues, and cellular and tissue based products, or HCT/Ps, which are human cells or tissue intended for implantation, transplant, infusion, or transfer into a human recipient. The primary intent of the GTP requirements is to ensure that cell and tissue based products are manufactured in a manner designed to prevent the introduction, transmission and spread of communicable disease. FDA regulations also require tissue establishments to register and list their HCT/Ps with the FDA and, when applicable, to evaluate donors through screening and testing. Additionally, before approving a BLA, the FDA will typically inspect one or more clinical sites to assure compliance with GCP. If the FDA determines that the application, manufacturing process or manufacturing facilities are not acceptable, it will outline the deficiencies in the submission and often will request additional testing or information. Notwithstanding the submission of any requested additional information, the FDA ultimately may decide that the application does not satisfy the regulatory criteria for approval.
After the FDA evaluates a BLA and conducts inspections of manufacturing facilities where the investigational product and/or its drug substance will be produced, the FDA may issue an approval letter or a Complete Response Letter, or CRL. An approval letter authorizes commercial marketing of the product with
167
specific prescribing information for specific indications. A CRL indicates that the review cycle of the application is complete, and the application will not be approved in its present form. A CRL will describe all of the deficiencies that the FDA has identified in the BLA, except that where the FDA determines that the data supporting the application are inadequate to support approval, the FDA may issue the CRL without first conducting required inspections, testing submitted product lots, and/or reviewing proposed labeling. In issuing the CRL, the FDA may recommend actions that the applicant might take to place the BLA in condition for approval, including requests for additional information or clarification. The FDA may delay or refuse approval of a BLA if applicable regulatory criteria are not satisfied, require additional testing or information and/or require post-marketing testing and surveillance to monitor safety or efficacy of a product. If a CRL is issued, the sponsor must resubmit the BLA, addressing all of the deficiencies identified in the letter, or withdraw the application. Even if such data and information are submitted, the FDA may decide that the BLA does not satisfy the criteria for approval.
If regulatory approval of a product is granted, such approval will be granted for particular indications and may entail limitations on the indicated uses for which such product may be marketed. For example, the FDA may approve the BLA with a Risk Evaluation and Mitigation Strategy, or REMS, to ensure the benefits of the product outweigh its risks, or otherwise limit the scope of any approval. A REMS is a safety strategy implemented to manage a known or potential serious risk associated with a product and to enable patients to have continued access to such medicines by managing their safe use, and could include medication guides, physician communication plans or elements to assure safe use, such as restricted distribution methods, patient registries and other risk minimization tools. The FDA also may condition approval on, among other things, changes to proposed labeling or the development of adequate controls and specifications. Once approved, the FDA may withdraw the product approval if compliance with pre- and post-marketing requirements is not maintained or if problems occur after the product reaches the marketplace. The FDA may require one or more Phase 4 post-market studies and surveillance to further assess and monitor the product’s safety and effectiveness after commercialization, and may limit further marketing of the product based on the results of these post-marketing studies.
Expedited Development and Review Programs
The FDA offers a number of expedited development and review programs for qualifying product candidates. For example, new biological products are eligible for fast track designation if they are intended to treat a serious or life-threatening disease or condition and demonstrate the potential to address unmet medical needs for the disease or condition. Fast track designation applies to the combination of the product and the specific indication for which it is being studied. The sponsor of a new biologic may request that the FDA designate the biologic as a fast track product at any time during the clinical development of the product. The sponsor of a fast track product has opportunities for more frequent interactions with the applicable FDA review team during product development and, once a BLA is submitted, the product candidate may be eligible for priority review. A fast track product may also be eligible for rolling review, where the FDA may consider for review sections of the BLA on a rolling basis before the complete application is submitted, if the sponsor provides a schedule for the submission of the sections of the BLA, the FDA agrees to accept sections of the BLA and determines that the schedule is acceptable, and the sponsor pays any required user fees upon submission of the first section of the BLA.
A product candidate intended to treat a serious or life-threatening disease or condition may also be eligible for breakthrough therapy designation to expedite its development and review. A product candidate can receive breakthrough therapy designation if preliminary clinical evidence indicates that the product candidate, alone or in combination with one or more other drugs or biologics, may demonstrate substantial improvement over existing therapies on one or more clinically significant endpoints, such as substantial treatment effects observed early in clinical development. The designation includes all of the fast track program features, as well as more intensive FDA interaction and guidance beginning as early as Phase 1 and an organizational commitment to expedite the development and review of the product candidate, including involvement of senior managers.
168
Any marketing application for a biologic submitted to the FDA for approval, including a product candidate with a fast track designation and/or breakthrough therapy designation, may be eligible for other types of FDA programs intended to expedite development and review, such as priority review and accelerated approval. A product candidate is eligible for priority review if it has the potential to provide safe and effective therapy where no satisfactory alternative therapy exists or a significant improvement in the treatment, diagnosis or prevention of a disease compared to marketed products. The FDA will attempt to direct additional resources to the evaluation of an application for a new biological product designated for priority review in an effort to facilitate the review. For original BLAs, priority review designation means the FDA’s goal is to take action on the marketing application within six months of the 60-day filing date (as compared to ten months under standard review).
Additionally, product candidates studied for their safety and effectiveness in treating serious or life-threatening diseases or conditions may receive accelerated approval upon a determination that the product has an effect on a surrogate endpoint that is reasonably likely to predict clinical benefit, or on a clinical endpoint that can be measured earlier than irreversible morbidity or mortality, that is reasonably likely to predict an effect on irreversible morbidity or mortality or other clinical benefit, taking into account the severity, rarity or prevalence of the condition and the availability or lack of alternative treatments. As a condition of accelerated approval, the FDA will generally require the sponsor to perform adequate and well-controlled post-marketing clinical studies to verify and describe the anticipated effect on irreversible morbidity or mortality or other clinical benefit. Products receiving accelerated approval may be subject to expedited withdrawal procedures if the sponsor fails to conduct the required post-marketing studies or if such studies fail to verify the predicted clinical benefit. In addition, for products being considered for accelerated approval, the FDA generally requires, unless otherwise informed by FDA, that all advertising and promotional materials intended for dissemination or publication within 120 days of marketing approval be submitted to FDA for review during the pre-approval period.
In 2017, the FDA established a new regenerative medicine advanced therapy, or RMAT, designation, which is intended to facilitate an efficient development program for, and expedite review of, any biologic that meets the following criteria: (i) the biologic qualifies as a RMAT, which is defined as a cell therapy, therapeutic tissue engineering product, human cell and tissue product, or any combination product using such therapies or products, with limited exceptions; (ii) the biologic is intended to treat, modify, reverse, or cure a serious or life-threatening disease or condition; and (iii) preliminary clinical evidence indicates that the biologic has the potential to address unmet medical needs for such a disease or condition. RMAT designation provides all the benefits of breakthrough therapy designation, including more frequent meetings with the FDA to discuss the development plan for the product candidate and eligibility for rolling review and priority review. Product candidates granted RMAT designation may also be eligible for accelerated approval on the basis of a surrogate or intermediate endpoint reasonably likely to predict long-term clinical benefit, or reliance upon data obtained from a meaningful number of clinical trial sites, including through expansion of trials to additional sites. RMAT-designated products that receive accelerated approval may, as appropriate, fulfill their post-approval requirements through submission of clinical evidence, clinical studies, patient registries, or other sources of real-world evidence (such as electronic health records); through the collection of larger confirmatory data sets; or via post-approval monitoring of all patients treated with such therapy prior to approval of such therapy.
Fast track designation, breakthrough therapy designation, priority review, accelerated approval, and RMAT designation do not change the standards for approval but may expedite the development or approval process. Even if a product candidate qualifies for one or more of these programs, the FDA may later decide that the product no longer meets the conditions for qualification or decide that the time period for FDA review or approval will not be shortened.
Orphan Drug Designation and Exclusivity
Under the Orphan Drug Act, the FDA may grant orphan designation to a biologic intended to treat a rare disease or condition, defined as a disease or condition with a patient population of fewer than 200,000 individuals in the United States, or a patient population greater than 200,000 individuals in the United States and when there
169
is no reasonable expectation that the cost of developing and making available the drug or biologic in the United States will be recovered from sales in the United States for that biologic. Orphan drug designation must be requested before submitting a BLA. After the FDA grants orphan drug designation, the generic identity of the therapeutic agent and its potential orphan use are disclosed publicly by the FDA. Orphan drug designation does not convey any advantage in or shorten the duration of the regulatory review and approval process.
In the United States, orphan drug designation entitles a party to financial incentives such as opportunities for grant funding towards clinical trial costs, tax advantages and user-fee waivers. In addition, if a product that has orphan drug designation subsequently receives the first FDA approval for a particular drug or biologic for the disease for which it has such designation, the product is entitled to orphan product exclusivity, which means that the FDA may not approve any other applications, including a full BLA, to market the same biologic for the same indication for seven years, except in limited circumstances, such as a showing of clinical superiority to the product with orphan drug exclusivity or if the FDA finds that the holder of the orphan drug exclusivity has not shown that it can assure the availability of sufficient quantities of the orphan drug to meet the needs of patients with the disease or condition for which the drug was designated. Orphan drug exclusivity does not prevent the FDA from approving a different drug or biologic for the same disease or condition, or the same drug or biologic for a different disease or condition. Competitors may receive approval of different products for the indication for which the orphan product has exclusivity or obtain approval for the same product but for a different indication for which the orphan product has exclusivity. Orphan product exclusivity also could block the approval of one of our products for seven years if a competitor obtains approval of the same biological product as defined by the FDA or if our product candidate is determined to be contained within the competitor’s product for the same indication or disease.
A designated orphan drug may not receive orphan drug exclusivity if it is approved for a use that is broader than the indication for which it received orphan designation. In addition, orphan drug exclusive marketing rights in the United States may be lost if the FDA later determines that the request for designation was materially defective or, as noted above, if a second applicant demonstrates that its product is clinically superior to the approved product with orphan exclusivity or the manufacturer of the approved product is unable to assure sufficient quantities of the product to meet the needs of patients with the rare disease or condition.
Post-Approval Requirements
Biologics are subject to pervasive and continuing regulation by the FDA, including, among other things, requirements relating to record-keeping, reporting of adverse experiences, periodic reporting, product sampling and distribution, and advertising and promotion of the product. After approval, most changes to the approved product, such as adding new indications or other labeling claims, are subject to prior FDA review and approval. There also are continuing, annual program fees for any marketed products. Biologic manufacturers and other entities involved in the manufacture and distribution of approved biological products are required to register their establishments with the FDA and certain state agencies, and are subject to periodic unannounced inspections by the FDA and certain state agencies for compliance with cGMP requirements and other laws, which impose certain procedural and documentation requirements upon us and our third-party manufacturers. Manufacturers and other parties involved in the drug supply chain for prescription drug products must also comply with product tracking and tracing requirements and for notifying the FDA of counterfeit, diverted, stolen and intentionally adulterated products or products that are otherwise unfit for distribution in the United States. Accordingly, manufacturers must continue to expend time, money, and effort in the area of production and quality control to maintain GMP compliance. Changes to the manufacturing process or facility are strictly regulated, and, depending on the significance of the change, may require prior FDA approval before being implemented. FDA regulations also require investigation and correction of any deviations from cGMP and impose reporting requirements upon us and any third-party manufacturers that we may decide to use. Accordingly, manufacturers must continue to expend time, money and effort in the area of production and quality control to maintain compliance with cGMP and other aspects of regulatory compliance.
170
The FDA may withdraw approval if compliance with regulatory requirements and standards is not maintained or if problems occur after the product reaches the market. Later discovery of previously unknown problems with a product, including adverse events of unanticipated severity or frequency, or with manufacturing processes, or failure to comply with regulatory requirements, may result in revisions to the approved labeling to add new safety information; imposition of post-market studies or clinical studies to assess new safety risks; or imposition of distribution restrictions or other restrictions under a REMS program. Other potential consequences include, among other things:
| • | restrictions on the marketing or manufacturing of the product, complete withdrawal of the product from the market or product recalls; |
| • | fines, warning letters, or untitled letters; |
| • | clinical holds on clinical studies; |
| • | refusal of the FDA to approve pending applications or supplements to approved applications, or suspension or revocation of product license approvals; |
| • | product seizure or detention, or refusal to permit the import or export of products; |
| • | consent decrees, corporate integrity agreements, debarment or exclusion from federal healthcare programs; |
| • | mandated modification of promotional materials and labeling and the issuance of corrective information; |
| • | the issuance of safety alerts, Dear Healthcare Provider letters, press releases and other communications containing warnings or other safety information about the product; or |
| • | injunctions or the imposition of civil or criminal penalties. |
The FDA also may require post-marketing testing, known as Phase 4 testing, and surveillance to monitor the effects of an approved product. Discovery of previously unknown problems with a product or the failure to comply with applicable FDA requirements can have negative consequences, including adverse publicity, judicial or administrative enforcement, warning letters from the FDA, mandated corrective advertising or communications with doctors, and civil or criminal penalties, among others. Newly discovered or developed safety or effectiveness data may require changes to a product’s approved labeling, including the addition of new warnings and contraindications, and also may require the implementation of other risk management measures.
The FDA closely regulates the marketing, labeling, advertising and promotion of biologics. A company can make only those claims relating to safety and efficacy, purity and potency that are approved by the FDA and in accordance with the provisions of the approved label. The FDA and other agencies actively enforce the laws and regulations prohibiting the promotion of off-label uses. The federal government has levied large civil and criminal fines against companies for alleged improper promotion of off-label use and has enjoined companies from engaging in off-label promotion. The FDA and other regulatory agencies have also required that companies enter into consent decrees or permanent injunctions under which specified promotional conduct is changed or curtailed. Failure to comply with these requirements can result in, among other things, adverse publicity, warning letters, corrective advertising and potential civil and criminal penalties. FDA sanctions could include refusal to approve pending applications, withdrawal of an approval, clinical hold, warning or untitled letters, product recalls, product seizures, total or partial suspension of production or distribution, injunctions, fines, refusals of government contracts, mandated corrective advertising or communications with doctors, debarment, restitution, disgorgement of profits, or civil or criminal penalties. Physicians may prescribe, in their independent professional and medical judgment, legally available products for uses that are not described in the product’s labeling and that differ from those tested and approved by the FDA. Such off-label uses are common across medical specialties. Physicians may believe that such off-label uses are the best treatment for many patients in varied circumstances. The FDA does not regulate the behavior of physicians in their choice of treatments. The FDA does, however, restrict manufacturer’s communications on the subject of off-label use of their products.
171
Biosimilars and Reference Product Exclusivity
The Affordable Care Act, signed into law in 2010, includes a subtitle called the Biologics Price Competition and Innovation Act, or BPCIA, which created an abbreviated approval pathway for biological products that are biosimilar to or interchangeable with an FDA-licensed reference biological product. The FDA has issued several guidance documents outlining an approach to review and approval of biosimilars.
Biosimilarity, which requires that there be no clinically meaningful differences between the biological product and the reference product in terms of safety, purity and potency, can be shown through analytical studies, animal studies, and a clinical study or studies. Interchangeability requires that a product is biosimilar to the reference product and the product must demonstrate that it can be expected to produce the same clinical results as the reference product in any given patient and, for products that are administered multiple times to an individual, the biologic and the reference biologic may be alternated or switched after one has been previously administered without increasing safety risks or risks of diminished efficacy relative to exclusive use of the reference biologic. However, complexities associated with the larger, and often more complex, structures of biological products, as well as the processes by which such products are manufactured, pose significant hurdles to implementation of the abbreviated approval pathway that are still being worked out by the FDA.
Under the BPCIA, an application for a biosimilar product may not be submitted to the FDA until four years following the date that the reference product was first licensed by the FDA. In addition, the approval of a biosimilar product may not be made effective by the FDA until 12 years from the date on which the reference product was first licensed. During this 12-year period of exclusivity, another company may still market a competing version of the reference product if the FDA approves a full BLA for the competing product containing that applicant’s own preclinical data and data from adequate and well-controlled clinical trials to demonstrate the safety, purity and potency of its product. The BPCIA also created certain exclusivity periods for biosimilars approved as interchangeable products. At this juncture, it is unclear whether products deemed “interchangeable” by the FDA will, in fact, be readily substituted by pharmacies, which are governed by state pharmacy law.
A biological product can also obtain pediatric market exclusivity in the United States. Pediatric exclusivity, if granted, adds six months to existing exclusivity periods and patent terms. This six-month exclusivity, which runs from the end of other exclusivity protection or patent term, may be granted based on the voluntary completion of a pediatric study in accordance with an FDA-issued “Written Request” for such a study. The BPCIA is complex and continues to be interpreted and implemented by the FDA. In addition, government proposals have sought to reduce the 12-year reference product exclusivity period. Other aspects of the BPCIA, some of which may impact the BPCIA exclusivity provisions, have also been the subject of recent litigation. As a result, the ultimate impact, implementation, and impact of the BPCIA is subject to significant uncertainty.
Government Regulation Outside of the United States
In addition to regulations in the United States, we will be subject to a variety of regulations in other jurisdictions governing, among other things, clinical studies and any commercial sales and distribution of our products. Because biologically sourced raw materials are subject to unique contamination risks, their use may be restricted in some countries.
Whether or not we obtain FDA approval for a product, we must obtain the requisite approvals from regulatory authorities in foreign countries prior to the commencement of clinical studies or marketing of the product in those countries. Certain countries outside of the United States have a similar process that requires the submission of a clinical study application much like the IND prior to the commencement of human clinical studies. In the European Union, for example, a CTA must be submitted to each country’s national health authority and an independent ethics committee, much like the FDA and the IRB, respectively. Once the CTA is approved in accordance with a country’s requirements, clinical study development may proceed.
The requirements and process governing the conduct of clinical studies, product licensing, pricing and reimbursement vary from country to country. In all cases, the clinical studies are conducted in accordance with
172
GCP and the applicable regulatory requirements and the ethical principles that have their origin in the Declaration of Helsinki.
To obtain regulatory approval of an investigational biological product under European Union regulatory systems, we must submit a marketing authorization application. The application used to file the BLA in the United States is similar to that required in the European Union, with the exception of, among other things, country-specific document requirements. The European Union also provides opportunities for market exclusivity. For example, in the European Union, upon receiving marketing authorization, new chemical entities generally receive eight years of data exclusivity and an additional two years of market exclusivity. If granted, data exclusivity prevents regulatory authorities in the European Union from referencing the innovator’s data to assess a generic application. During the additional two-year period of market exclusivity, a generic marketing authorization can be submitted, and the innovator’s data may be referenced, but no generic product can be marketed until the expiration of the market exclusivity. However, there is no guarantee that a product will be considered by the European Union’s regulatory authorities to be a new chemical entity, and products may not qualify for data exclusivity. Products receiving orphan designation in the European Union can receive ten years of market exclusivity, during which time no similar medicinal product for the same indication may be placed on the market. An orphan product can also obtain an additional two years of market exclusivity in the European Union for pediatric studies. No extension to any supplementary protection certificate can be granted on the basis of pediatric studies for orphan indications.
The criteria for designating an “orphan medicinal product” in the European Union are similar in principle to those in the United States. Under Article 3 of Regulation (EC) 141/2000, a medicinal product may be designated as orphan if (1) it is intended for the diagnosis, prevention or treatment of a life-threatening or chronically debilitating condition; (2) either (a) such condition affects no more than five in 10,000 persons in the European Union when the application is made, or (b) the product, without the benefits derived from orphan status, would not generate sufficient return in the European Union to justify investment; and (3) there exists no satisfactory method of diagnosis, prevention or treatment of such condition authorized for marketing in the European Union, or if such a method exists, the product will be of significant benefit to those affected by the condition, as defined in Regulation (EC) 847/2000. Orphan medicinal products are eligible for financial incentives such as reduction of fees or fee waivers and are, upon grant of a marketing authorization, entitled to ten years of market exclusivity for the approved therapeutic indication. The application for orphan drug designation must be submitted before the application for marketing authorization. The applicant will receive a fee reduction for the marketing authorization application if the orphan drug designation has been granted, but not if the designation is still pending at the time the marketing authorization is submitted. Orphan drug designation does not convey any advantage in, or shorten the duration of, the regulatory review and approval process.
The 10-year market exclusivity may be reduced to six years if, at the end of the fifth year, it is established that the product no longer meets the criteria for orphan designation, for example, if the product is sufficiently profitable not to justify maintenance of market exclusivity. Additionally, marketing authorization may be granted to a similar product for the same indication at any time if:
| • | The second applicant can establish that its product, although similar, is safer, more effective or otherwise clinically superior; |
| • | The applicant consents to a second orphan medicinal product application; or |
| • | The applicant cannot supply enough orphan medicinal product. |
For other countries outside of the European Union, such as countries in Eastern Europe, Latin America or Asia, the requirements governing the conduct of clinical studies, product licensing, pricing and reimbursement vary from country to country. In all cases, again, the clinical studies are conducted in accordance with GCP and the applicable regulatory requirements and the ethical principles that have their origin in the Declaration of Helsinki.
173
If we fail to comply with applicable foreign regulatory requirements, we may be subject to, among other things, fines, suspension or withdrawal of regulatory approvals, product recalls, seizure of products, operating restrictions and criminal prosecution.
Other Healthcare Laws
Pharmaceutical companies are subject to additional healthcare regulation and enforcement by the federal government and by authorities in the states and foreign jurisdictions in which they conduct their business and may constrain the financial arrangements and relationships through which we research, as well as, sell, market and distribute any products for which we obtain marketing approval. Such laws include, without limitation, federal and state anti-kickback, fraud and abuse, false claims, data privacy and security and physician and other health care provider transparency laws and regulations.
In order to distribute products commercially, we must also comply with state laws that require the registration of manufacturers and wholesale distributors of pharmaceutical products in a state, including, in certain states, manufacturers and distributors who ship products into the state even if such manufacturers or distributors have no place of business within the state. Some states also impose requirements on manufacturers and distributors to establish the pedigree of product in the chain of distribution, including some states that require manufacturers and others to adopt new technology capable of tracking and tracing product as it moves through the distribution chain. Several states have enacted legislation requiring pharmaceutical companies to establish marketing compliance programs, file periodic reports with the state, make periodic public disclosures on sales, marketing, pricing, track and report gifts, compensation and other remuneration made to physicians and other healthcare providers, clinical trials and other activities, and/or register their sales representatives, as well as to prohibit pharmacies and other healthcare entities from providing certain physician prescribing data to pharmaceutical companies for use in sales and marketing, and to prohibit certain other sales and marketing practices. All of our activities are potentially subject to federal and state consumer protection and unfair competition laws.
If our operations are found to be in violation of any of the federal and state healthcare laws described above or any other governmental regulations that apply to us, we may be subject to penalties, including without limitation, civil, criminal and/or administrative penalties, damages, fines, disgorgement, imprisonment, exclusion from participation in government programs, such as Medicare and Medicaid, injunctions, private “qui tam” actions brought by individual whistleblowers in the name of the government, or refusal to allow us to enter into government contracts, contractual damages, reputational harm, administrative burdens, diminished profits and future earnings, and the curtailment or restructuring of our operations, any of which could adversely affect our ability to operate our business and our results of operations. For information regarding risks related to these compliance requirements, see the section titled “Risk Factors—Risks Related to Government Regulations.”
Coverage and Reimbursement
Sales of any product depend, in part, on the extent to which such product will be covered by third-party payors, such as federal, state, and foreign government healthcare programs, commercial insurance and managed healthcare organizations, and the level of reimbursement for such product by third-party payors. Decisions regarding the extent of coverage and amount of reimbursement to be provided are made on a plan-by-plan basis. These third-party payors are increasingly reducing coverage and reimbursement for medical products, drugs and services. Obtaining coverage and adequate reimbursement for our product candidates may be particularly difficult because of the higher prices often associated with drugs administered under the supervision of a physician. Similarly, because our product candidates are physician-administered, separate reimbursement for the product itself may or may not be available. Instead, the administering physician may or may not be reimbursed for providing the treatment or procedure in which our product is used.
In addition, the U.S. government, state legislatures and foreign governments have continued implementing cost-containment programs, including price controls, restrictions on coverage and reimbursement and
174
requirements for substitution of generic products. Adoption of price controls and cost-containment measures, and adoption of more restrictive policies in jurisdictions with existing controls and measures, could further limit sales of any product. Decreases in third-party reimbursement for any product or a decision by a third-party payor not to cover a product could reduce physician usage and patient demand for the product and also have a material adverse effect on sales.
Healthcare Reform
Payors, whether domestic or foreign, or governmental or private, are developing increasingly sophisticated methods of controlling healthcare costs and those methods are not always specifically adapted for new technologies such as gene therapy and therapies addressing rare diseases such as those we are developing. In both the United States and certain foreign jurisdictions, there have been a number of legislative and regulatory changes to the health care system that could impact our ability to sell our products profitably.
In the United States, in March 2010, the Patient Protection and Affordable Care Act, as amended by the Health Care and Education Reconciliation Act, each as amended, collectively known as the ACA, was enacted, which substantially changed the way healthcare is financed by both governmental and private insurers, and significantly affected the pharmaceutical industry. The ACA contained a number of provisions, including those governing enrollment in federal healthcare programs, reimbursement adjustments and changes to fraud and abuse laws. For example, the ACA:
| • | increased the minimum level of Medicaid rebates payable by manufacturers of brand name drugs from 15.1% to 23.1% of the average manufacturer price; |
| • | required collection of rebates for drugs paid by Medicaid managed care organizations; |
| • | required manufacturers to participate in a coverage gap discount program, under which they must now agree to offer 70 percent point-of-sale discounts off negotiated prices of applicable brand drugs to eligible beneficiaries during their coverage gap period, as a condition for the manufacturer’s outpatient drugs to be covered under Medicare Part D; and |
| • | imposed a non-deductible annual fee on pharmaceutical manufacturers or importers who sell “branded prescription drugs” to specified federal government programs. |
On June 17, 2021, the U.S. Supreme Court dismissed the most recent judicial challenge to the ACA brought by several states without specifically ruling on the constitutionality of the ACA. Prior to the Supreme Court’s decision, President Biden issued an Executive Order to initiate a special enrollment period from February 15, 2021 through August 15, 2021 for purposes of obtaining health insurance coverage through the ACA marketplace. The Executive Order also instructed certain governmental agencies to review and reconsider their existing policies and rules that limit access to healthcare, including among others, reexamining Medicaid demonstration projects and waiver programs that include work requirements, and policies that create unnecessary barriers to obtaining access to health insurance coverage through Medicaid or the ACA. It is unclear how other healthcare reform measures of the Biden administrations or other efforts, if any, to challenge repeal or replace the ACA, will impact our business.
Other legislative changes have been proposed and adopted in the United States since the Affordable Care Act was enacted. For example, on March 11, 2021, President Biden signed the American Rescue Plan Act of 2021 into law, which eliminates the statutory Medicaid drug rebate cap, currently set at 100% of a drug’s average manufacturer price, for single source and innovator multiple source drugs, beginning January 1, 2024. Further, in August 2011, the Budget Control Act of 2011, among other things, created measures for spending reductions by Congress. A Joint Select Committee on Deficit Reduction, tasked with recommending a targeted deficit reduction of at least $1.2 trillion for the years 2013 through 2021, was unable to reach required goals, thereby triggering the legislation’s automatic reduction to several government programs, including aggregate reductions of Medicare payments to providers of 2% per fiscal year. These reductions went into effect in April 2013 and, due to
175
subsequent legislative amendments to the statute, will remain in effect through 2030 unless additional action is taken by Congress. Pursuant to the Coronavirus Aid, Relief, and Economic Security Act, also known as the CARES Act, as well as subsequent legislation, these reductions have been suspended from May 1, 2020 through December 31, 2021 due to the COVID-19 pandemic.
Further, on May 30, 2018, the Right to Try Act was signed into law. The law, among other things, provides a federal framework for certain patients to access certain investigational new drug products that have completed a Phase 1 clinical trial and that are undergoing investigation for FDA approval. Under certain circumstances, eligible patients can seek treatment without enrolling in clinical trials and without obtaining FDA permission under the FDA expanded access program. There is no obligation for a pharmaceutical manufacturer to make its drug products available to eligible patients as a result of the Right to Try Act.
Moreover, there has recently been heightened governmental scrutiny over the manner in which manufacturers set prices for their marketed products, which has resulted in several Congressional inquiries, proposed and enacted legislation and executive orders issued by the previous administration designed to, among other things, bring more transparency to product pricing, review the relationship between pricing and manufacturer patient programs, and reform government program reimbursement methodologies for drug products. The likelihood of success of these and other measures initiated by the previous administration is uncertain, particularly in light of the new Biden administration. It is also possible that additional governmental action is taken in response to the COVID-19 pandemic. Individual states in the United States have also become increasingly active in implementing regulations designed to control pharmaceutical product pricing, including price or patient reimbursement constraints, discounts, restrictions on certain product access and marketing cost disclosure and transparency measures, and, in some cases, designed to encourage importation from other countries and bulk purchasing.
Data Privacy and Security Laws
We also are or will become subject to privacy laws in the jurisdictions in which we are established or in which we sell or market our products or run clinical trials. For example, in Europe we are subject to the GDPR in relation to our collection, control, processing and other use of personal data (i.e., data relating to an identifiable living individual). We process personal data in relation to participants in our clinical trials in the EEA, including health and medical information of these participants. The GDPR also provides that individual EEA countries may introduce further conditions of their own, including limitations which could limit our ability to collect, use and share personal data.
The GDPR imposes onerous accountability obligations requiring data controllers and processors to maintain a record of their data processing and implement policies as part of its mandated privacy governance framework. It also requires data controllers to be transparent and disclose to data subjects (in a concise, intelligible and easily accessible form) how their personal information is to be used; imposes limitations on retention of personal data; defines pseudonymized (i.e., key-coded) data; introduces mandatory data breach notification requirements; and sets higher standards for data controllers to demonstrate that they have obtained valid consent for certain data processing activities. Fines for certain breaches of the GDPR are significant: up to the greater of €20 million or 4% of total global annual turnover. A breach of the GDPR or other applicable privacy and data protection laws and regulations could also result in regulatory investigations, reputational damage, orders to cease/change our use of data, enforcement notices, or potential civil claims including class action type litigation. Further, from January 1, 2021, we have to comply with the GDPR and separately the UK GDPR, which, together with the amended UK Data Protection Act 2018, retains the GDPR in UK national law. The GDPR and the UK GDPR each have the ability to fine up to the greater of €20 million/ £17 million or 4% of global turnover. Further, the relationship between the United Kingdom and the European Union in relation to certain aspects of data protection law remains unclear, including how data transfers between European Union member states and the United Kingdom will be treated and how United Kingdom data protection laws and regulations will develop in the medium to longer term. Currently there is a four to six-month grace period agreed in the European Union and
176
United Kingdom Trade and Cooperation Agreement, ending June 30, 2021 at the latest, whilst the parties discuss an adequacy decision. The European Commission published a draft adequacy decision on February 19, 2021. If adopted, the decision will enable data transfers from European Union member states to the United Kingdom for a four-year period, subject to subsequent extensions. These changes may lead to additional compliance costs and could increase our overall risk.
In addition, the GDPR places restrictions on cross-border data transfers. Certain aspects of cross-border data transfers under the GDPR are uncertain as the result of legal proceedings in the European Union, including a recent decision by the Court of Justice for the European Union that invalidated the EU-U.S. Privacy Shield and, to some extent, called into question the efficacy and legality of using standard contractual clauses. This may increase the complexity of transferring personal data across borders. The GDPR will increase our responsibility and liability in relation to personal data that we process where such processing is subject to the GDPR, and we may be required to put in place additional mechanisms to ensure compliance with the GDPR, including as implemented by individual countries. We are also subject to European Union rules with respect to cross-border transfers of personal data out of the EEA. Recent legal developments in the European Union have created complexity and uncertainty regarding transfers of personal data from the EEA to other countries whose data protection standards have not been deemed “adequate” by the European Commission (including the United States). On July 16, 2020, the Court of Justice of the European Union, or CJEU, invalidated the EU-US Privacy Shield Framework, or Privacy Shield, under which personal data could be transferred from the EEA to US entities who had self-certified under the Privacy Shield scheme. While the CJEU upheld the adequacy, subject to certain conditions, of the standard contractual clauses (a standard form of contract approved by the European Commission as an adequate personal data transfer mechanism), future regulatory guidance could result in changes to the use of standard contractual clauses. As supervisory authorities issue further guidance on personal data export mechanisms, including circumstances where the standard contractual clauses cannot be used, and/or start taking enforcement action, we could suffer additional costs, complaints and/or regulatory investigations or fines, and/or if we are otherwise unable to transfer personal data between and among countries and regions in which we operate, it could affect the manner in which we provide our services, the geographical location or segregation of our relevant systems and operations, and could adversely affect our financial results.
Further, the exit of the United Kingdom, or UK, from the European Union, often referred to as Brexit, has created uncertainty with regard to data protection regulation in the UK. Specifically, the UK exited the European Union on January 1, 2020, subject to a transition period that ended December 31, 2020. Under the post-Brexit Trade and Cooperation Agreement between the European Union and the UK, the UK and European Union have agreed that transfers of personal data to the UK from EEA member states will not be treated as ‘restricted transfers’ to a non-EEA country for a period of up to four months from January 1, 2021, plus a potential further two months extension, or the Extended Adequacy Assessment Period. Although the current maximum duration of the Extended Adequacy Assessment Period is six months, it may end sooner, for example, in the event that the European Commission adopts an adequacy decision in respect of the UK, or the UK amends the UK GDPR and/or makes certain changes regarding data transfers under the UK GDPR/Data Protection Act 2018 without the consent of the European Union (unless those amendments or decisions are made simply to keep relevant UK laws aligned with the European Union’s data protection regime). If the European Commission does not adopt an ‘adequacy decision’ in respect of the UK prior to the expiry of the Extended Adequacy Assessment Period, from that point onwards the UK will be an ‘inadequate third country’ under the GDPR and transfers of personal data from the EEA to the UK will require a ‘transfer mechanism’ such as the Standard Contractual Clauses.
In the United States, numerous federal and state laws and regulations, including data breach notification laws, health information privacy and security laws, including HIPAA, and federal and state consumer protection laws and regulations (e.g., Section 5 of the Federal Trade Commission Act) that govern the collection, use, disclosure, and protection of health-related and other personal information could apply to our operations or the operations of our partners. In addition, certain state laws govern the privacy and security of personal information, including health-related information in certain circumstances, some of which are more stringent than HIPAA and many of which differ from each other in significant ways and may not have the same effect, thus complicating
177
compliance efforts. For example, California enacted the CCPA, which creates individual privacy rights for California consumers (as defined in the law) and places increased privacy and security obligations on entities handling certain personal data of consumers or households. The CCPA requires covered companies to provide new disclosure to consumers about such companies’ data collection, use and sharing practices, provide such consumers new ways to opt-out of certain sales or transfers of personal information, and provide consumers with additional causes of action. The CCPA provides for civil penalties for violations, as well as a private right of action for certain data breaches that result in the loss of personal information. This private right of action may increase the likelihood of, and risks associated with, data breach litigation. The CCPA became effective on January 1, 2020, and (a) allows the California Attorney General to impose civil penalties for violations and (b) authorizes private lawsuits to recover statutory damages for certain data breaches. In addition, laws in all 50 U.S. states require businesses to provide notice to consumers whose personal information has been disclosed as a result of a data breach. State laws are changing rapidly and there is discussion in the U.S. Congress of a new comprehensive federal data privacy law to which we would become subject if it is enacted. The CCPA may impact our business activities and exemplifies the vulnerability of our business to the evolving regulatory environment related to personal data and protected health information. Additionally, a new privacy law, the California Privacy Rights Act, or CPRA, recently passed in California. The CPRA significantly modifies the CCPA and imposes additional data protection obligations on covered businesses, including additional consumer rights processes, limitations on data uses, new audit requirements for higher risk data, and opt outs for certain uses of sensitive data. It will also expand the types of data breaches subject to the CCPA’s private right of action, provide for increased penalties for CPRA violations concerning California residents under the age of 16 and create a new California data protection agency authorized to issue substantive regulations, and could result in increased privacy and information security enforcement. The majority of the provisions will go into effect on January 1, 2023, and additional compliance investment and potential business process changes may be required. Ensuring compliance with the CPRA could require us to incur additional costs and expenses.
In order to distribute products commercially, we must comply with state laws that require the registration of manufacturers and wholesale distributors of pharmaceutical products in a state, including, in certain states, manufacturers and distributors who ship products into the state even if such manufacturers or distributors have no place of business within the state. Some states also impose requirements on manufacturers and distributors to establish the pedigree of product in the chain of distribution, including some states that require manufacturers and others to adopt new technology capable of tracking and tracing product as it moves through the distribution chain. Several states have enacted legislation requiring pharmaceutical companies to establish marketing compliance programs, file periodic reports with the state, make periodic public disclosures on sales, marketing, pricing, track and report gifts, compensation and other remuneration made to physicians and other healthcare providers, clinical trials and other activities, and/or register their sales representatives, as well as to prohibit pharmacies and other healthcare entities from providing certain physician prescribing data to pharmaceutical companies for use in sales and marketing, and to prohibit certain other sales and marketing practices. All of our activities are potentially subject to federal and state consumer protection and unfair competition laws.
If our operations are found to be in violation of any of the federal and state healthcare and privacy laws described above or any other governmental regulations that apply to us, we may be subject to penalties, including without limitation, civil, criminal and/or administrative penalties, damages, fines, disgorgement, imprisonment, exclusion from participation in government programs, such as Medicare and Medicaid, injunctions, private “qui tam” actions brought by individual whistleblowers in the name of the government, or refusal to allow us to enter into government contracts, contractual damages, reputational harm, administrative burdens, diminished profits and future earnings, and the curtailment or restructuring of our operations, any of which could adversely affect our ability to operate our business and our results of operations. For information regarding risks related to these compliance requirements, see the section titled “Risk Factors—Risks Related to Government Regulation.”
178
Facilities
Our corporate headquarters are located in South San Francisco, California, where we lease approximately 40,000 square feet of office and research and development space pursuant to a lease agreement which commenced on April 25, 2019 and expires on April 30, 2027, with an option to extend for eight years. In Alameda, California, we lease approximately 92,000 square feet of space pursuant to a lease agreement which initiated on June 3, 2021 and expires on September 30, 2032, with two options to extend for five years each. Within this space, we have begun the build-out of a cell therapy manufacturing facility designed to meet Current Good Manufacturing Practices (cGMP) with the goal of providing clinical and commercial-scale manufacturing for multiple off-the-shelf chimeric antigen receptor (CAR) natural killer (NK) cell product candidates. We believe that our existing facilities are suitable and adequate for our needs.
Employees and Human Capital Resources
As of June 23, 2022, we had 105 employees, all of whom were full-time, consisting of clinical, research, operations, regulatory, finance and business development personnel. 33 of our employees hold Ph.D. or M.D. degrees. None of our employees are subject to a collective bargaining agreement. We consider our relationship with our employees to be good.
Our human capital resources objectives include, as applicable, identifying, recruiting, retaining, incentivizing and integrating our existing and additional employees. The principal purposes of our equity incentive plans are to attract, retain and motivate selected employees, consultants and directors through the granting of stock-based compensation awards, in order to increase stockholder value and the success of our company by motivating such individuals to perform to the best of their abilities and achieve our objectives.
Periodic Reporting and Financial Information
Upon consummation of the Business Combination, we expect to be a “smaller reporting company” as defined in Item 10(f)(1) of Regulation S-K. Smaller reporting companies may take advantage of certain reduced disclosure obligations, including, among other things, providing only two years of audited financial statements. We will remain a smaller reporting company if (1) the market value of our common stock held by non-affiliates is less than $250 million as of the last business day of the second fiscal quarter, or (2) our annual revenues in our most recent fiscal year completed before the last business day of our second fiscal quarter are less than $100 million and the market value of our common stock held by non-affiliates is less than $700 million as of the last business day of the second fiscal quarter.
Legal Proceedings
From time to time, we may become involved in legal proceedings or be subject to claims arising in the ordinary course of our business. Although we are not currently a party to any material legal proceedings, as disclosed in our Current Report on Form 8-K filed on June 9, 2022, LifeForce Capital has not funded its commitment of $16.2 million pursuant to a subscription agreement entered into concurrently with the execution of the Business Combination Agreement in December 2021, and we are exploring available avenues and presently intend to enforce LifeForce Capital’s legal obligations under its subscription agreement. Regardless of outcome, any such proceedings or claims can have an adverse impact on us because of defense and settlement costs, diversion of resources and other factors, and there can be no assurances that favorable outcomes will be obtained.
179
SENTI MANAGEMENT’S DISCUSSION AND ANALYSIS OF FINANCIAL CONDITIONS AND RESULTS OF OPERATIONS
On June 6, 2022, Senti Biosciences, Inc. changed its name to Senti Sub I, Inc. For purposes of this section, all references to “we,” “us,” “our,” “Senti” or the “Company” refer to Senti Sub I, Inc. and its subsidiary.
You should read the following discussion and analysis of our financial condition and results of operations together with our unaudited interim consolidated financial statements as of March 31, 2022 and related notes included elsewhere in this prospectus. The discussion and analysis should also be read together with the pro forma financial information as of and for the three months ended March 31, 2022, and for the year ended December 31, 2021, which is included elsewhere in this prospectus.
Cautionary Statement Regarding Forward-Looking Statements
Some of the information contained in this discussion and analysis includes forward-looking statements that involve risks and uncertainties, including information with respect to our plans and strategy for our business, future financial performance, expense levels and liquidity sources. As a result of many factors, including those factors set forth in the section of this titled “Risk Factors,” or in other parts of this prospectus, our actual results could differ materially from the results described in or implied by the forward-looking statements contained in the following discussion and analysis.
Overview
Senti is a preclinical biotechnology company developing next-generation cell and gene therapies engineered with its gene circuit platform technologies to fight challenging diseases. Senti’s mission is to create a new generation of smarter therapies that can outmaneuver complex diseases in ways previously not implemented by conventional medicines. To accomplish this mission, Senti has built a synthetic biology platform that it believes may enable it to program next-generation cell and gene therapies with what it refers to as “gene circuits.” These gene circuits, which Senti created from novel and proprietary combinations of genetic parts, are designed to reprogram cells with biological logic to sense inputs, compute decisions and respond to their respective cellular environments. Senti aims to design and optimize gene circuits through its Design-Build-Test-Learn Engine or DBTL Engine, to improve the “intelligence” of cell and gene therapies in order to enhance their therapeutic effectiveness against a broad range of diseases that conventional medicines are unable to address. Senti’s gene circuit platform technologies can be applied in a modality-agnostic manner, with applicability to natural killer (NK) cells, T cells, tumor-infiltrating lymphocytes (“TILs”), stem cells including Hematopoietic Stem Cells (“HSCs”), in vivo gene therapy and messenger ribonucleic acid (mRNA). All of Senti’s current product candidates are in preclinical development. Senti’s lead product candidates utilize allogeneic chimeric antigen receptor (“CAR”) NK cells outfitted with its gene circuit technologies in several oncology indications with currently high unmet needs. Senti expects to file investigational new drug applications (“INDs”) for multiple product candidates starting in 2023.
Since our inception, we have funded our operations almost exclusively with proceeds from the sale and issuance of shares of our redeemable convertible preferred stock and debt financings, and we have devoted substantially all of our resources to organizing and staffing our company, business planning, raising capital, developing and optimizing our platform technologies, identifying potential product candidates, undertaking research and preclinical studies and clinical trial planning activities, engaging in manufacturing for our development programs, establishing and enhancing our intellectual property portfolio, and providing general and administrative support for these operations. Through March 31, 2022, we have received gross proceeds of $158.1 million from sales of our redeemable convertible preferred stock including borrowings under convertible notes, which converted into redeemable convertible preferred stock in 2018 and 2020.
We have incurred net losses of $11.8 million and $21.0 million for the three months ended March 31, 2022 and 2021, respectively. We expect to continue to incur significant losses for the foreseeable future. As of
180
March 31, 2022, we had cash and cash equivalents of $38.1 million, and an accumulated deficit of $126.9 million.
We anticipate that our expenses and operating losses will increase substantially over the foreseeable future. The expected increase in expenses will be driven in large part by our ongoing activities, if and as we:
| • | continue to advance our gene circuit platform technologies; |
| • | continue preclinical development of our current and future product candidates and initiate additional preclinical studies; |
| • | commence clinical trials of our current and future product candidates; |
| • | establish our manufacturing capability, including developing our contract development and manufacturing relationships, and building our internal manufacturing facilities; |
| • | acquire and license technologies aligned with our gene circuit platform technologies; |
| • | seek regulatory approval of our current and future product candidates; |
| • | expand our operational, financial, and management systems and increase personnel, including personnel to support our preclinical and clinical development, manufacturing and commercialization efforts; |
| • | continue to develop, grow, perfect, and defend our intellectual property portfolio; and |
| • | incur additional legal, accounting, or other expenses in operating our business, including the additional costs associated with operating as a public company. |
In addition, in 2021, we began construction on a dedicated in-house, state-of-the-art current good manufacturing practices (“cGMP”) facility to support clinical and commercial-scale production of multiple allogeneic NK cell product candidates. We anticipate that this facility will become operational in time to support initial clinical trials for our lead product candidates. Our manufacturing facility is designed to leverage the latest cell therapy process technologies as we strive to maximize scalability and minimize cost of goods.
As of April 1, 2022, the issuance date of the consolidated financial statements for the year ended December 31, 2021, the Company concluded that substantial doubt existed about the Company’s ability to continue as a going concern for one year from the issuance date of the annual consolidated financial statements. In light of these concerns, our independent registered public accounting firm included in its opinion for the year ended December 31, 2021 an explanatory paragraph expressing substantial doubt about our ability to continue as a going concern within one year from April 1, 2022.
We believe that our cash and cash equivalents on hand as of May 20, 2022, the issuance date of the quarterly unaudited financial statements, were not sufficient to fund our operations for the next twelve months from that date.
During 2021, widespread availability of COVID-19 vaccines in the United States and elsewhere in the world, combined with government assistance programs, fiscal policies and other factors, led to a rebound in the global economy as several states and countries began to re-open and loosen many COVID-19 related restrictions. Nonetheless, the COVID-19 pandemic remains a global health crisis and continues to evolve. We are unable to predict the full impact that the COVID-19 pandemic will have on our future results of operations, liquidity and financial condition due to numerous uncertainties, including the duration of the pandemic and the actions that may be taken by government authorities across the United States. However, as of March 31, 2022, we were operating at pre-pandemic levels. We will continue to monitor the performance of our business and assess the impacts of COVID-19.
181
Recent Developments
Business Combination with Dynamics Special Purpose Corp.
On December 19, 2021, we entered into a definitive Business Combination Agreement (the “Business Combination Agreement”) with Dynamics Special Purpose Corp. (“DYNS”), a publicly-traded special purpose acquisition company (“SPAC”), and Explore Merger Sub, Inc. (“Merger Sub”), a wholly-owned subsidiary of DYNS. On February 12, 2022, we entered into Amendment No. 1 to the Business Combination Agreement to restructure certain option grants made at the time the Business Combination Agreement was signed. On May 19, 2022, we entered into Amendment No. 2 to the Business Combination Agreement to provide for the subscription agreement and promissory note entered into with a certain investor. On June 8, 2022, pursuant to the terms of the Business Combination Agreement, as amended to date, Merger Sub merged with and into Senti, with Senti surviving the merger as a wholly-owned subsidiary of DYNS (the “Closing”). DYNS was immediately renamed “Senti Biosciences, Inc.” upon the Closing, and its shares of common stock began trading on the Nasdaq Global Market under the symbol “SNTI” on June 9, 2022.
Under the terms of the transaction, the estimated combined enterprise value of the combined company was approximately $280.9 million. The cash components of the transaction were funded by DYNS’ cash in trust of $84.5 million (net of redemptions), as well as $50.6 million funded as of the Closing out of $66.8 million in expected cash proceeds from a private placement of common stock at $10.00 per share from various accredited investors and $5.2 million in cash proceeds from the issuance of a convertible note (the “Note”) to Bayer HealthCare LLC on May 19, 2022, the principal amount of which was automatically cancelled and exchanged for shares of DYNS Class A Common Stock upon the Closing at a conversion price of $10.00 per share. All accrued interest under the Note was canceled and forgiven at the Closing.
Components of Results of Operations
Total Revenue
We currently have no therapeutic products approved for sale, and we have never generated any revenue from the sale of any therapeutic products. Total revenue consists of contract revenue related to research services provided to customers and grant income which is research funding received from grants.
Our ability to generate product revenues will depend on our partners’ ability to replicate our results and the successful development and eventual commercialization of our product candidates, which we do not expect for the foreseeable future, if ever. We may also look to generate revenue from collaboration and license agreements in the future.
Operating Expenses
Our operating expenses consist of research and development expense and general and administrative expenses.
Research and Development Expenses
Research and development costs consist primarily of costs incurred for the discovery and preclinical development of our product candidates, which include:
| • | employee-related expenses, including salaries, related benefits, and stock-based compensation expenses for employees engaged in research and development functions; |
| • | expenses incurred in connection with research, laboratory consumables and preclinical studies; |
| • | the cost of consultants engaged in research and development related services and the cost to manufacture drug products for use in our preclinical studies and trials; |
182
| • | facilities, depreciation and other expenses, which include allocated expenses for rent and maintenance of facilities, insurance and supplies; |
| • | costs related to regulatory compliance; and |
| • | the cost of annual license fees. |
We have not historically tracked research and development expenses by program, with the exception of third-party research projects. We have various ongoing early-stage research and product candidate discovery projects and going forward, we expect to have various products undergoing clinical trials. Our internal resources, employees and infrastructure are not directly tied to any one research or product candidate discovery project and are typically deployed across multiple projects. As such, we do not maintain information regarding these costs incurred for these early-stage research and product candidate discovery programs on a project-specific basis.
Our direct external development program expenses reflect external costs attributable to our preclinical development candidates selected for further development as well as Investigational New Drug applications (“INDs”) and clinical development. Such expenses include third-party contract costs relating to manufacturing, clinical trial activities, translational medicine and toxicology activities. We do not allocate internal research and development costs which include personnel, facility costs, laboratory consumables and discovery and research related activities associated with our pipeline because these costs are deployed across multiple programs and our platform, and, as such, are not separately classified.
Research and development expenses consisted of the following (in thousands):
| Three Months Ended March, 31 | ||||||||
| 2022 | 2021 | |||||||
| (unaudited) | (unaudited) | |||||||
Personnel-related expenses including share-based compensation | $ | 2,799 | $ | 1,738 | ||||
External services and supplies | 2,886 | 2,132 | ||||||
Office and facilities | 1,747 | 931 | ||||||
Other | 171 | 102 | ||||||
|
|
|
| |||||
Total | $ | 7,603 | $ | 4,903 | ||||
|
|
|
| |||||
Research and development activities are central to our business model. There are numerous factors associated with the successful commercialization of any of our product candidates, including future trial design and various regulatory requirements, many of which cannot be determined with accuracy at this time based on our stage of development. In addition, future regulatory factors beyond our control may impact our preclinical development programs. Product candidates in clinical development generally have higher development costs than those in preclinical stages of development, primarily due to the increased size and duration of clinical trials. At this time, we cannot reasonably estimate or know the nature, timing and costs of the efforts that will be necessary to complete the preclinical development of any of our product candidates. However, we expect that our research and development expenses and manufacturing costs will increase substantially in connection with our planned preclinical and clinical development activities in the near term and in the future.
The successful development of our current and future product candidates is highly uncertain. This is due to numerous risks and uncertainties, including the following:
| • | negative or inconclusive results from our preclinical or clinical trials or the clinical trials of others for product candidates similar to ours, leading to a decision or requirement to conduct additional preclinical studies or clinical trials or abandon any or all of our programs; |
| • | product-related adverse events or side effects experienced by participants in our clinical trials or by individuals using therapeutics similar to our product candidates; |
183
| • | delays in submitting IND applications or comparable foreign applications, or delays or failures to obtain the necessary approvals from regulators to commence a clinical trial, or a suspension or termination of a clinical trial once commenced; |
| • | conditions imposed by the FDA or other regulatory authorities regarding the scope or design of our clinical trials; |
| • | delays in enrolling research subjects in clinical trials; |
| • | high drop-out rates of research subjects; |
| • | inadequate supply or quality of product candidate components or materials or other supplies necessary for the conduct of our clinical trials; |
| • | CMC challenges associated with manufacturing and scaling up biologic product candidates to ensure consistent quality, stability, purity and potency among different batches used in clinical trials; |
| • | greater-than-anticipated clinical trial costs; |
| • | poor potency or effectiveness of our product candidates during clinical trials; |
| • | unfavorable FDA or other regulatory authority inspection and review of a clinical trial or manufacturing site; |
| • | delays as a result of the COVID-19 pandemic or events associated with the pandemic; |
| • | failure of our third-party contractors or investigators to comply with regulatory requirements or otherwise meet their contractual obligations in a timely manner, or at all; |
| • | delays and changes in regulatory requirements, policies and guidelines; and |
| • | the FDA or other regulatory authorities interpret our data differently than we do. |
A change in the outcome of any of these variables may significantly impact the costs and timing associated with the development of our product candidates. We may never succeed in obtaining regulatory approval for any of our product candidates.
General and Administrative Expenses
General and administrative expenses consist primarily of salaries and employee-related costs, including stock-based compensation, for personnel in executive, finance and other administrative functions. Other significant costs include legal fees relating to corporate matters, professional fees for accounting and consulting services and an allocation of facility-related costs.
We expect our general and administrative expenses will increase for the foreseeable future to support our increased research and development, manufacturing activities, and preclinical and clinical activities and to reflect increased costs associated with operating as a public company. These increased costs will likely include increased expenses for audit, legal, regulatory, tax and related services associated with maintaining compliance with exchange listing and SEC requirements, director and officer insurance premiums and investor relations costs.
Other Income (Expense)
Interest Income, net
Interest income, net consists of interest earned on our cash and cash equivalents, and short-term investments, if any, held during the year, net of interest expense.
184
Change in Fair Value of Convertible Notes
Our convertible notes have been accounted for at fair value with changes in fair value recorded in earnings at each reporting period through settlement.
Change in Preferred Stock Tranche Liability
Our preferred stock tranche liability has been accounted for at fair value with changes in the fair value recorded in earnings at each reporting period through settlement.
Results of Operations
Comparison of the Three Months Ended March 31, 2022 and 2021
The following table summarizes our results of operations for the three months ended March 31, 2022 and 2021 (in thousands):
| Three Months Ended March 31, | ||||||||||||
| 2022 | 2021 | Change | ||||||||||
Revenue: | ||||||||||||
Contract revenue | $ | 854 | $ | 44 | $ | 810 | ||||||
Grant income | 250 | 28 | 222 | |||||||||
|
|
|
|
|
| |||||||
Total revenue | 1,104 | 72 | 1,032 | |||||||||
|
|
|
|
|
| |||||||
Operating expenses: | ||||||||||||
Research and development | 7,603 | 4,903 | 2,700 | |||||||||
General and administrative | 5,259 | 4,311 | 948 | |||||||||
|
|
|
|
|
| |||||||
Total operating expenses | 12,862 | 9,214 | 3,648 | |||||||||
|
|
|
|
|
| |||||||
Loss from operations | (11,758 | ) | (9,142 | ) | (2,616 | ) | ||||||
|
|
|
|
|
| |||||||
Other income (expense): | ||||||||||||
Interest income, net | 4 | 1 | 3 | |||||||||
Change in preferred stock tranche liability | — | (11,824 | ) | 11,824 | ||||||||
Other expense | (54 | ) | (37 | ) | (17 | ) | ||||||
|
|
|
|
|
| |||||||
Total other income (expense), net | (50 | ) | (11,860 | ) | 11,810 | |||||||
|
|
|
|
|
| |||||||
Net loss | $ | (11,808 | ) | $ | (21,002 | ) | $ | 9,194 | ||||
|
|
|
|
|
| |||||||
Contract revenue. For the three months ended March 31, 2022 and 2021, we generated revenue from contracts and license agreements of $0.9 million and less than $0.1 million, respectively. The increase of $0.8 million was due primarily to a new collaboration agreement entered into in 2021.
Grant income. For the three months ended March 31, 2022 and 2021, we generated revenue from grants of $0.3 million and less than $0.1 million, respectively. The increase of $0.2 million was primarily due to the recognition of revenue related to the Small Business Innovation Research (“SBIR”) SENTI-202 grant funding.
Research and development expenses. Research and development expenses were $7.6 million and $4.9 million for the three months ended March 31, 2022 and 2021, respectively. The increase of $2.7 million was primarily due to an increase of $1.1 million in personnel-related expenses, $0.8 million in facility costs and $0.8 million in professional services costs.
General and administrative expenses. General and administrative expenses were $5.3 million and $4.3 million for the three months ended March 31, 2022 and 2021, respectively. The increase of $0.9 million was
185
primarily due to increases of $1.8 million in personnel-related expenses, partially offset by a decrease of $0.9 million related to professional, legal and accounting services expenses.
Change in preferred stock tranche liability. For the three months ended March 31, 2021, we recognized a loss of $11.8 million as an adjustment to the preferred stock tranche liability. The adjustment stems primarily from the increase, since the December 31, 2020 measurement date, in management’s estimate of the fair value of our Series B redeemable convertible preferred stock resulting from a decrease in time to liquidity as we drew nearer to completing an initial public offering. In addition, the probability of calling Tranche 2 increased as we considered related research milestones achieved. These increases in value were offset by the decline in value resulting from the decrease in the likelihood of Tranche 3 due to new uncertainty around future investments from a key shareholder. For the three months ended March 31, 2022, there was no activity as the preferred stock tranches were issued on May 14, 2021.
Liquidity and Capital Resources
Sources of Liquidity
From inception to March 31, 2022, we raised aggregate gross proceeds of $158.1 million from the issuance of shares of our redeemable convertible preferred stock and the issuance of convertible notes.
We do not have any products approved for sale and have not generated any revenue from product sales or otherwise. We have incurred net losses and negative cash flows from operations since our inception and anticipate we will continue to incur net losses for the foreseeable future. As of March 31, 2022, we had $38.1 million in cash and cash equivalents, and an accumulated deficit of $126.9 million.
We will need substantial additional funding to support our continuing operations and pursue our development strategy. Until such time as we can generate significant revenue from sales of our product candidates, if ever, we expect to finance our operations through the sale of equity, debt financings or other capital sources, including potential collaborations with other companies or other strategic transactions. Adequate funding may not be available to us on acceptable terms, if at all. Should we fail to raise capital or enter into such agreements as, and when, needed, we may have to significantly delay, scale back, or discontinue the development and commercialization of our product candidates or delay our efforts to expand our product pipeline. We may also be required to sell or license to other parties’ rights to develop or commercialize our product candidates that we would prefer to retain.
Cash Flows
The following table sets forth a summary of our cash flows for each of the periods indicated (in thousands):
| Three Months Ended March 31, | ||||||||
| 2022 | 2021 | |||||||
Net cash from operating activities | $ | (10,059 | ) | $ | (8,365 | ) | ||
Net cash from investing activities | (7,380 | ) | (206 | ) | ||||
Net cash from financing activities | (455 | ) | 3,558 | |||||
|
|
|
| |||||
Net change in cash and cash equivalents | $ | (17,894 | ) | $ | (5,013 | ) | ||
|
|
|
| |||||
Operating Activities
For the three months ended March 31, 2022, net cash used in operating activities of $10.1 million was primarily due to our loss of $11.8 million with non-cash adjustments of $1.0 million for depreciation and
186
amortization of operating lease right-of-use-assets and $0.7 million for stock-based compensation expense, as well as a $1.6 million decrease in accounts payable and accrued and other current liabilities and a $0.5 million decrease in deferred revenue, offset by a $2.4 million increase in operating lease liabilities.
For the three months ended March 31, 2021, net cash used in operating activities of $8.4 million was primarily due to our net loss of $21.0 million with non-cash adjustments of $11.8 million for an increase in our preferred stock tranche liability, and $0.7 million for an increase in accounts payable.
Investing Activities
For the three months ended March 31, 2022 and 2021, net cash used in investing activities of $7.4 million and $0.2 million, respectively, was due entirely to purchases of property and equipment.
Financing Activities
For the three months ended March 31, 2022, net cash used in financing activities of $0.5 million was primarily due to payment of deferred transaction costs relating to a pending business combination of $0.6 million partially offset by $0.1 million proceeds from the issuance of common stock upon exercise of stock options.
For the three months ended March 31, 2021, net cash provided by financing activities of $3.6 million was primarily due to proceeds received of $2.3 million from the issuance of our Series B redeemable convertible preferred stock, $1.4 million from the issuance of common stock upon exercise of stock options and $0.2 million from the payment of prior-year issuance costs related to Series B redeemable convertible preferred stock.
Funding Requirements
Based upon our current operating plans, we believe that our existing cash and cash equivalents as of May 20, 2022, the issuance date of the quarterly unaudited financial statements, were not sufficient to fund our operations for the next twelve months from that date. However, as noted in the Recent Developments section above, on June 8, 2022, we completed a business combination with DYNS that provides further liquidity and resulted in the funding of $84.5 million (net of redemptions) from DYNS’s cash in trust, as well as $50.6 million funded as of the Closing out of $66.8 million in expected cash proceeds from a private placement of common stock at $10.00 per share from various accredited investors and $5.2 million in cash proceeds from our issuance of the Note, which was cancelled and exchanged for shares of common stock at $10.00 per share upon the completion of the business combination. We anticipate that we will require additional funding to support our ongoing operations, although the precise timing of such needs may prove uncertain as our forecast of the period of time through which our financial resources will be adequate to support our operations is a forward-looking statement that involves risks and uncertainties, and actual results could vary materially. Our assumptions may prove to be inaccurate, and we could deplete our capital resources sooner than we expect. Additionally, the process of testing and manufacturing product candidates in preclinical studies and clinical trials is costly and the timing and expenses in these trials are uncertain.
Our future capital requirements will depend on many factors, including:
| • | the scope, rate of progress, results and costs of drug discovery, preclinical development, laboratory testing and clinical trials for our product candidates; |
| • | the number and development requirements of product candidates that we may pursue, and other indications for our current product candidates that we may pursue; |
| • | the costs, timing and outcome of regulatory review of our product candidates; |
| • | the scope and costs of constructing and operating our planned cGMP facility and any commercial manufacturing activities; |
187
| • | the cost associated with commercializing any approved product candidates; |
| • | the cost and timing of developing our ability to establish sales and marketing capabilities, if any; |
| • | the costs of preparing, filing and prosecuting patent applications, maintaining, enforcing and protecting our intellectual property rights, defending intellectual property-related claims and obtaining licenses to third-party intellectual property; |
| • | the timing and amount of any milestone and royalty payments we are required to make under our present or future license agreements; |
| • | our ability to establish and maintain collaborations on favorable terms, if at all; and |
| • | the extent to which we acquire or in-license other product candidates and technologies and associated intellectual property. |
In order to improve our liquidity, management is actively pursuing additional financing. We expect our expenses to increase substantially in connection with ongoing activities, particularly as we advance our preclinical activities and clinical trials for our product candidates in development. Accordingly, we will need to obtain substantial additional funding for continuing operations. If we are unable to raise capital when needed, or on attractive terms, we could be forced to delay, reduce or eliminate our research or drug development programs or any future commercialization efforts. Although management continues to pursue these plans, there is no assurance that we will be successful in obtaining sufficient funding on terms acceptable to us to fund continuing operations, if at all.
Accounting standards require that management evaluate whether we have adequate financial resources to continue as a going concern for one year after the date that these consolidated financial statements are available to be issued. Management has determined that additional funds will be needed to continue as a going concern for the period defined in the accounting standards.
Contractual Obligations and Commitments
On June 3, 2021, we entered into a lease agreement for a new cGMP facility in Alameda, California to support planned initial clinical trials for our product candidates. The lease will expire in 2032 with future undiscounted operating lease payments of $46.0 million over an initial lease period of eleven years. See Note 9—Operating Leases for details on our lease obligations.
In 2021, we began construction of the cGMP facility. As of March 31, 2022, we have paid $8.2 million in construction costs and the purchase commitments amounted to approximately $35.5 million. The agreements with the construction company provide for termination following a certain period after notice. Upon termination we will be responsible for payment for work performed to date.
During the year ended December 31, 2021, we entered into a three-year collaboration and option agreement with BlueRock Therapeutics LP (“BlueRock”) under which the Company granted BlueRock an option to execute an exclusive or non-exclusive license to develop, manufacture and commercialize cell therapy products (See Note 12—Related Parties for details into the BlueRock agreement). In consideration for the option, the Company is responsible for up to $10.0 million in research and development costs and expenses associated with the collaboration plan incurred over the three-year term.
We have also entered into license agreements under which we are obligated to make annual maintenance payments of $0.1 million and specified milestone and royalty payments. Milestone and royalty payment obligations under these agreements are contingent upon future events, such as our achievement of specified development, regulatory, and sales milestones, or generating product sales. As of March 31, 2022, we were unable to estimate the timing or likelihood of achieving these milestones or generating future product sales.
188
We have entered into sponsored research agreements under which we are obligated to pay $1.0 million, $0.8 million and $0.2 million in 2022, 2023 and 2024, respectively.
Off-Balance Sheet Arrangements
During the periods presented, we did not have, nor do we currently have, any off-balance sheet arrangements as defined under the rules and regulations of the SEC.
Critical Accounting Policies and Significant Judgments and Estimates
Our management’s discussion and analysis of our financial condition and results of operations are based on our consolidated financial statements, which have been prepared in accordance with U.S. generally accepted accounting principles, or GAAP. The preparation of these consolidated financial statements requires us to make estimates and judgments that affect the reported amounts of assets, liabilities and expenses and the disclosure of contingent assets and liabilities in our consolidated financial statements and accompanying notes. On an ongoing basis, we evaluate our estimates and judgments. We base our estimates and assumptions on historical experience, known trends and events, and various other factors that are believed to be reasonable and appropriate under the circumstances, the results of which form the basis for making judgments about the carrying values of assets and liabilities that are not readily apparent from other sources. Actual results may differ from these estimates under different assumptions or conditions.
While our significant accounting policies are described in more detail in Note 2 to our condensed consolidated financial statements included elsewhere in this prospectus, we believe the following accounting policies and estimates to be most critical to the preparation of our consolidated financial statements. We define our critical accounting policies as those under U.S. GAAP that require us to make subjective estimates and judgments about matters that are inherently uncertain and are likely to have a material impact on our financial condition and results of operations, as well as the specific manner in which we apply those principles.
Determination of the Fair Value of Common Stock
We are required to estimate the fair value of our common stock underlying our share-based awards when performing the fair value calculations using the Black-Scholes option pricing model. Because our common stock is not currently publicly traded, the fair value of our common stock underlying our share-based awards has been determined on each grant date by our board of directors, with input from management, considering our most recently available third-party valuation of our common stock.
In the absence of a public trading market for our common stock, on each grant date, our board of directors has made a reasonable determination of the fair value of our common stock based on the information known to us on the date of grant, upon a review of any recent events and their potential impact on the estimated fair value per share of the common stock, and timely valuations from an independent third-party valuation in accordance with guidance provided by the American Institute of Certified Public Accountants, Inc. Practice Aid: Valuation of Privately-Held-Company Equity Securities Issued as Compensation, 2013. In addition, our board of directors considered various objective and subjective factors to determine the fair value of our common stock, including:
| • | the estimated value of each security both outstanding and anticipated; |
| • | the anticipated capital structure that will directly impact the value of the currently outstanding securities; |
| • | our results of operations and financial position; |
| • | the status of our research and development efforts; |
| • | the composition of, and changes to, our management team and board of directors; |
189
| • | the lack of liquidity of our common stock as a private company; |
| • | our stage of development and business strategy and the material risks related to our business and industry; |
| • | external market conditions affecting the life sciences and biotechnology industry sectors; |
| • | U.S. and global economic conditions; |
| • | the results of independent third-party valuations of our common stock; |
| • | the likelihood of achieving a liquidity event for the holders of our common stock, such as an initial public offering or a sale of our company, given prevailing market conditions; and |
| • | the market value and volatility of comparable companies. |
The Practice Aid identifies various available methods for allocating enterprise value across classes and series of capital stock to determine the estimated fair value of common stock at each valuation date. In accordance with the Practice Aid, we considered various income, market or asset valuation methods.
Based on our early stage of development and other relevant factors, we appropriately used different valuation methods including a hybrid of the option pricing method, or OPM, and guideline transactions Backsolve method, a hybrid of the OPM and guideline public company methods or a hybrid of OPM, Backsolve method, and Monte Carlo simulation to determine the estimated fair value of our common stock for valuations performed through March 31, 2022. In determining the estimated fair value of our common stock, our Board of Directors also considered the fact that our stockholders could not freely trade our common stock in the public markets. Accordingly, we applied discounts to reflect the lack of marketability of our common stock based on the weighted-average expected time to liquidity.
Our Board of Directors and management develop best estimates based on the application of these approaches and the assumptions underlying these valuations, giving careful consideration to the advice from our third-party valuation expert. Such estimates involve inherent uncertainties and the application of significant judgment. As a result, if factors or expected outcomes change and we use significantly different assumptions or estimates, our equity-based compensation could be materially different.
Valuation of Preferred Stock Tranche Liability
Our Series B redeemable convertible preferred stock included an obligation whereby the investors agreed to buy, and the Company agreed to sell, additional shares at a fixed price if certain agreed-upon milestones were achieved or at the election of investors. This obligation was determined to be a freestanding financial instrument that should be accounted for as a liability at fair value, and until settlement, the preferred stock tranche liability was revalued at each reporting period with changes in the fair value recorded in earnings. Upon achieving specific milestones, and obtaining Board and stockholder approval, the tranches were called and settled on May 14, 2021. The liability was then extinguished and the fair value was reclassified to redeemable convertible preferred stock.
We utilized the Monte Carlo valuation model and/or Black-Scholes option pricing model which incorporated assumptions and estimates, to value the preferred stock tranche feature prior to its settlement. Significant estimates and assumptions impacting the fair value measurement included the estimated fair value per share of the underlying Series B redeemable convertible preferred stock, risk-free rate, expected dividend yield, time to liquidity, expected volatility of the price of the underlying preferred stock and determining the type of option (call option and/or forward contract) and associated probabilities. The most significant assumptions impacting the fair value of the preferred stock tranche feature included the estimated fair value of our Series B redeemable convertible preferred stock, the estimated probability of and time to liquidity for going public and staying-private, and the determination of the type of option (call option and/or forward contract) and associated probability.
190
We determined the estimated fair value per share of the underlying redeemable convertible preferred stock by taking into consideration the most recent sales of our redeemable convertible preferred stock as well as additional factors that we deemed relevant. We assessed these assumptions and estimates on a quarterly basis as additional information impacting the assumptions became available. The risk-free rate was determined by reference to the U.S. Treasury yield curve for time periods approximately equal to the expected term of the preferred stock tranche feature. We estimated a 0% dividend yield based on the expected dividend yield and the fact that we have never paid or declared dividends. We estimated the time to liquidity by weighting potential timelines associated with reaching various pipeline milestones and completing an initial public offering. Historically, we have been a private company and lack company-specific and implied volatility information of our stock. Therefore, we estimated our expected stock volatility based on the historical volatility of a representative group of public companies in the biotechnology industry for the expected terms. The determination of the type of option is based on the payouts available to the holders of the tranche rights and the level of control the investors had over-exercising these rights.
These estimates involved inherent uncertainties and the application of significant judgment. As a result, if factors or expected outcomes change and we used significantly different assumptions or estimates, our preferred stock tranche liability could be materially different.
Fair Value Option for Convertible Notes
We elected to account for our convertible notes at fair value in order to measure those liabilities at amounts that more accurately reflect the current economic environment in which the Company operates. We recorded the convertible notes at fair value with changes in fair value recorded in earnings at each reporting period through settlement. The fair value of the convertible notes was determined using a probability-weighted income approach as the convertible notes contained various settlement outcomes. The significant assumptions used to estimate the fair value of the convertible notes involved inherent uncertainties and the application of significant judgment and included the time to maturity and the probability of the various settlement outcomes.
Revenue from Contracts
We recognize revenue from contracts when our customer obtains control of the promised goods or services, in an amount that reflects the consideration which we have received or expect to receive in exchange for those goods or services.
Our revenues are primarily derived through our collaborative research, development and license agreements. The terms of these types of agreements may include (i) research and development services, (ii) licenses for our technology or programs, and (iii) services or obligations in connection with participation in research or steering committees. Payments to us under these arrangements typically include one or more of the following: nonrefundable upfront and license fees, research funding, milestone and other contingent payments for the achievement of defined research, development and commercial-based events, as well as royalties on sales of any commercialized products. We assess whether the promises in its arrangements with customers are considered distinct performance obligations that should be accounted for separately. Judgment may be required to determine whether the research and development services are distinct from the license to our intellectual property or participation on steering committees.
Arrangements that include rights to additional goods or services that are exercisable at a customer’s discretion are generally considered options. If these options provide a material right to the customer, they are considered performance obligations. The identification of material rights requires judgments related to the determination of the value of the underlying license relative to the option exercise price, including assumptions about the technical feasibility and the probability of developing a candidate that would be subject to the option rights.
191
The transaction price in each arrangement is allocated based on the relative standalone selling price (“SSP”) of each distinct performance obligation, which requires judgment. In instances where SSP is not directly observable, such as when a license or service is not sold separately, SSP is determined using information that may include market conditions and other observable inputs. Due to the early stage of our licensed technology, the license of such technology is typically combined with research and development services and steering committee participation as one performance obligation. Changes in the key assumptions used to determine the SSP could have a significant effect on the allocation of arrangement consideration between multiple performance obligations.
Recently Issued Accounting Pronouncements
See Note 2 to our condensed consolidated financial statements included elsewhere in this prospectus for recently issued accounting pronouncements.
Emerging Growth Company Status
The JOBS Act permits an emerging growth company to take advantage of an extended transition to comply with new or revised accounting standards applicable to public companies until those standards would otherwise apply to private companies. Immediately prior to the consummation of the Business Combination, DYNS was an “emerging growth company” as defined in Section 2(a) of the Securities Act, and elected to take advantage of the benefits of this extended transition period, which means that when an accounting standard is issued or revised and has different application dates for public or private companies, DYNS may adopt the new or revised standard only at the time private companies are required or permitted to adopt the new or revised standard. Senti has elected not to take advantage of the extended transition period.
Following the consummation of the Business Combination, we expect to remain an emerging growth company until the earlier of: (1) the last day of the fiscal year (a) following the fifth anniversary of the closing of the DYNS IPO (which occurred on May 25, 2021), (b) in which we have total annual revenue of at least $1.07 billion, or (c) in which we are deemed to be a large accelerated filer, which means the market value of our common equity that is held by non-affiliates exceeds $700 million as of the end of that fiscal year’s second fiscal quarter and our net sales for the year exceed $100 million; and (2) the date on which we have issued more than $1.0 billion in non-convertible debt securities during the preceding, rolling three-year period. As a result, following the Business Combination, our consolidated financial statements may not be comparable to the financial statements of companies that are required to comply with the effective dates for new or revised accounting standards that are applicable to public companies.
Smaller Reporting Company Status
Upon consummation of the Business Combination, we expect to be a “smaller reporting company” as defined in Item 10(f)(1) of Regulation S-K. Smaller reporting companies may take advantage of certain reduced disclosure obligations, including, among other things, providing only two years of audited financial statements. We will remain a smaller reporting company if (1) the market value of our common stock held by non-affiliates is less than $250 million as of the last business day of the second fiscal quarter, or (2) our annual revenues in our most recent fiscal year completed before the last business day of our second fiscal quarter are less than $100 million and the market value of our common stock held by non-affiliates is less than $700 million as of the last business day of the second fiscal quarter.
Segment Information
We have one business activity and operate in one reportable segment.
192
DYNS MANAGEMENT’S DISCUSSION AND ANALYSIS OF FINANCIAL CONDITION AND RESULTS OF OPERATIONS
References in this “DYNS Management’s Discussion and Analysis of Financial Condition and Results of Operations” section of this prospectus to “we,” “us” or the “Company” refer to Dynamics Special Purpose Corp. References to our “management” or our “management team” refer to our officers and directors, and references to the “Sponsor” refer to Dynamics Sponsor LLC. The following discussion and analysis of the Company’s financial condition and results of operations should be read in conjunction with the unaudited condensed consolidated financial statements and the notes thereto contained elsewhere in this prospectus. Certain information contained in the discussion and analysis set forth below includes forward-looking statements that involve risks and uncertainties.
Special Note Regarding Forward-Looking Statements
This prospectus includes “forward-looking statements” that are not historical facts and involve risks and uncertainties that could cause actual results to differ materially from those expected and projected. All statements, other than statements of historical fact included in this prospectus including, without limitation, statements regarding the Company’s financial position, business strategy and the plans and objectives of management for future operations, are forward-looking statements. Words such as “expect,” “believe,” “anticipate,” “intend,” “estimate,” “seek” and variations and similar words and expressions are intended to identify such forward-looking statements. Such forward-looking statements relate to future events or future performance, but reflect management’s current beliefs, based on information currently available. A number of factors could cause actual events, performance or results to differ materially from the events, performance and results discussed in the forward-looking statements. For information identifying important factors that could cause actual results to differ materially from those anticipated in the forward-looking statements, please refer to the “Risk Factors” section of the Company’s most recent Annual Report on 10-K, filed with the U.S. Securities and Exchange Commission (the “SEC”) on March 7, 2022. The Company’s securities filings can be accessed on the EDGAR section of the SEC’s website at www.sec.gov. Except as expressly required by applicable securities law, the Company disclaims any intention or obligation to update or revise any forward-looking statements whether as a result of new information, future events or otherwise.
Overview
We are a blank check company incorporated on March 1, 2021 as a Delaware corporation and formed for the purpose of effecting a merger, capital stock exchange, asset acquisition, stock purchase, reorganization or similar business combination with one or more businesses. We expect to continue to incur significant costs in the pursuit of our initial business combination, including our proposed initial business combination with Senti. We cannot assure you that our plans to complete our initial business combination, including our proposed initial business combination with Senti, will be successful.
Recent Developments
On December 19, 2021, we entered into the Business Combination Agreement with Merger Sub and Senti. The Business Combination Agreement provides, among other things, that on the terms and subject to the conditions set forth therein, Merger Sub will merge with and into Senti, with Senti surviving as a wholly-owned subsidiary of the Company. Upon the Closing, the Company will change its name to “Senti Biosciences, Inc.” and its ticker symbol on the Nasdaq Global Market, where it expects to be listed, is expected to change to “SNTI.”
The Business Combination Agreement and the transactions contemplated thereby were approved by the boards of directors of each of the Company and Senti. We intend to effectuate our proposed initial business combination with Senti using a combination of cash from the proceeds of our Initial Public Offering (and the concurrent private placement of shares to our Sponsor), the proceeds of the sale of our shares to private investors in connection with our initial business combination (the Subscriptions) and shares issued to the current owners of Senti.
193
For further information regarding the Business Combination Agreement and our proposed initial business combination with Senti, please refer to “Part I, Item 1. Business ” of our Annual Report on Form 10-K, which was filed with the SEC on March 7, 2022, and the Current Report on Form 8-K announcing the proposed business combination, which was filed with the SEC on December 20, 2021.
Results of Operations
We have neither engaged in any operations nor generated any operating revenues to date. Our only activities to date were organizational activities, those necessary to prepare for our Initial Public Offering, and, after our Initial Public Offering, identifying target companies for a business combination, conducting due diligence on such target companies and negotiating the Business Combination Agreement with Senti, which we anticipate will give effect to our initial business combination. We do not expect to generate any operating revenues (if any) until after the completion of our initial business combination. We generate non-operating income in the form of interest income on cash and cash equivalents held following our Initial Public Offering. We incur expenses as a result of being a public company (for legal, financial reporting, accounting and auditing compliance) and we incurred expenses for due diligence in connection with identifying Senti as the target company for our initial business combination.
For the three months ended March 31, 2022, we had a net loss of $1,309,849, which resulted from professional fees and other expenses of $1,282,742 and franchise tax expense of $50,269, partially offset by interest and dividend income on investments in the Trust Account of $23,162.
For the period from March 1, 2021 (inception) through March 31, 2021, we had a net loss of $1,178, which resulted from operating and formation costs of $1,178.
Liquidity and Capital Resources
On May 28, 2021, we consummated our Initial Public Offering of 23,000,000 shares of Class A Common Stock, including 3,000,000 public shares that were issued pursuant to the underwriter’s exercise, in full, of its over-allotment option, at $10.00 per share, generating gross proceeds of $230,000,000.
Simultaneously with the closing of our Initial Public Offering, our Sponsor purchased an aggregate of 715,500 shares of Class A Common Stock at a price of $10.00 per share (i.e. the Private Placement Shares), generating gross proceeds of $7,155,000. A portion of the proceeds from the sale of the Private Placement Shares was added to the net proceeds from our Initial Public Offering held in the Trust Account. If we do not complete our initial business combination within 24 months of the closing of our Initial Public Offering, the proceeds from the sale of the Private Placement Shares held in the Trust Account will be used to fund the redemption of our Public Shares (subject to the requirements of applicable law).
For the three months ended March 31, 2022, net cash used in operating activities was $492,630, which was primarily due to our net loss of $1,309,849, and non-cash interest and dividend income on investments held in the trust account of $23,162 offset in part by a changes in working capital accounts of $840,381.
For the period from March 1, 2021 (inception) through March 31, 2021, net cash used in operating activities was $0, which was due to our net loss of $1,178, offset in part by the payment of operating and formation costs by an affiliate of our Sponsor of $150 and changes in working capital of $1,028.
As of March 31, 2022, we had cash of $396,693 held outside the Trust Account. We intend to use the funds held outside the Trust Account primarily to complete our proposed initial business combination with Senti.
We intend to use substantially all of the funds held in the Trust Account, including any amounts representing interest earned on the Trust Account (less taxes payable and deferred underwriting fees), to complete our initial
194
business combination with Senti. We may withdraw interest income (if any) to pay franchise and income taxes, if any. Our annual income tax obligations will depend on the amount of interest and other income earned on the amount held in the Trust Account. We expect the interest income earned on the amount in the Trust Account (if any) will be sufficient to pay our income taxes. To the extent that our equity or debt is used, in whole or in part, as consideration to complete our proposed initial business combination with Senti, the remaining amount held in the Trust Account will be used as working capital to finance the operations of Senti, to make other acquisitions and to pursue our growth strategies.
We do not believe we will need to raise additional funds in order to meet the expenditures required for operating our business while our initial business combination with Senti is completed. However, if our estimates of the costs of operating our business during this period are less than the actual amount necessary to do so, we may have insufficient funds available to operate our business prior to our initial business combination. In order to fund working capital deficiencies or finance transaction costs in connection with our proposed initial business combination with Senti, our sponsor, or an affiliate of our sponsor, or certain of our officers or directors may, but are not obligated to, loan us funds as may be required. If we complete our initial business combination, we would repay such loaned amounts. In the event that our initial business combination does not close, we may use a portion of the working capital held outside the Trust Account to repay such loaned amounts, but no proceeds from our Trust Account would be used for such repayment. Up to $2,000,000 of such loans, if made, may be convertible into shares of the post-business combination entity at a price of $10.00 per share at the option of the lender. The shares would be identical to the Private Placement Shares. The terms of such loans, if any, have not been determined and no written agreements exist with respect to such loans. We do not expect to seek loans from parties other than our Sponsor, affiliates of our Sponsor or our officers or directors as we do not believe third parties would be willing to loan such funds and provide a waiver against any and all rights to seek access to funds in our Trust Account.
Off-Balance Sheet Arrangements
We did not have any off-balance sheet arrangements as of March 31, 2022 and December 31, 2021.
Contractual Obligations
Underwriters Agreement
In connection with our Initial Public Offering, the Company granted the underwriter a 45-day option to purchase up to 3,000,000 additional shares of Class A Common Stock to cover over-allotments at the Initial Public Offering price, less the underwriting discounts and fees. The underwriter exercised its over-allotment option in full on May 28, 2021.
The underwriter was paid a cash underwriting fee of $0.20 per share, or $4,600,000 in the aggregate, upon the closing of our Initial Public Offering. In addition, approximately $0.306 per share, or $7,050,000 in the aggregate, may be payable to the underwriter for deferred underwriting fees (this amount having being reduced from $8,050,000 by $1,000,000 by agreement with the underwriter on December 17, 2021). The deferred underwriting fee will become payable to the underwriter from the amount held in the Trust Account solely in the event that the Company completes its initial business combination, subject to the terms of the underwriting agreement.
Financial Advisor Agreement
On December 16, 2021, the Company entered into an agreement (the “Financial Advisor Agreement”) with Morgan Stanley & Co. LLC (“Morgan Stanley”) for financial advisory services in connection with our potential initial business combination with Senti, which services Morgan Stanley had been engaged to provide, and which services Morgan Stanley had provided, since August 4, 2021. The Financial Advisor Agreement shall terminate automatically on December 16, 2022 unless terminated earlier, with or without cause, by either the Company or Morgan Stanley. The Company will pay Morgan Stanley a fee of $1,000,000 upon the consummation of our proposed initial business combination with Senti.
195
Placement Agent Agreement
On September 21, 2021, the Company entered into an agreement (the “Placement Agent Agreement”) with Morgan Stanley, J.P. Morgan Securities LLC and BofA Securities, Inc. (together, the “Placement Agents”) for services in connection with the placement of shares of our Class A Common Stock to certain private investors which is anticipated to occur concurrently with the completion our potential initial business combination with Senti. The Placement Agent Agreement shall terminate automatically on August 28, 2022 unless terminated earlier, with or without cause, by either the Company or any Placement Agent (as to itself only). The Company will pay to the Placement Agents a total fee equal to 4.0% of the aggregate price at which the shares of our Class A Common Stock are sold to the private investors, which fee shall be payable upon the consummation of the placement of the shares. Each of the Placement Agents will receive 33.3% of the fee.
Registration Rights
The holders of the Founder Shares, Private Placement Shares and any Class A Common Stock issuable upon conversion of any working capital loans from our Sponsor, officers or directors have registration rights pursuant to a registration and stockholder rights agreement signed in connection with our Initial Public Offering. The holders of these securities are entitled to make up to three demands, excluding short form demands, that the Company register such securities. In addition, the holders have certain “piggy-back” registration rights with respect to registration statements filed subsequent to the completion of our initial business combination. The Company will bear the expenses incurred in connection with the filing of any such registration statements.
In addition, it is anticipated that each signatory to the Investor Rights Agreement, other than the Company, will be granted certain registration rights with respect to their respective shares of Class A Common Stock. Further, shares of Class A Common Stock issued to the private investors making Subscriptions will have registration rights pursuant to the Subscription Agreements following the consummation of the proposed business combination with Senti.
Business Combination Agreement
As set forth in Note 1 of the accompanying financial statements, we have entered into the Business Combination Agreement with Merger Sub and Senti pursuant to which, among other things, Merger Sub will merge with and into Senti, with Senti surviving as a wholly-owned subsidiary of the Company. We have also entered into various ancillary transaction documents to give effect to the Merger, which are described throughout this prospectus and in our other public filings with the SEC.
Critical Accounting Policies
The preparation of unaudited condensed consolidated financial statements and related disclosures in conformity with accounting principles generally accepted in the United States of America requires management to make estimates and assumptions that affect the reported amounts of assets and liabilities, disclosure of contingent assets and liabilities at the date of the unaudited condensed consolidated financial statements, and income and expenses during the periods reported. Actual results could materially differ from those estimates. We have identified the following critical accounting policies:
Net Loss Per Common Share
Net loss per common share is computed by dividing net loss by the weighted-average number of shares of common stock outstanding during the period.
Class A Common Stock Subject to Possible Redemption
We account for our Class A Common Stock subject to possible redemption in accordance with the guidance in Accounting Standards Codification (“ASC”) 480, Distinguishing Liabilities from Equity. Shares of Class A
196
Common Stock subject to mandatory redemption are classified as a liability instrument and measured at fair value. Conditionally redeemable common stock (including common stock that features redemption rights that are either within the control of the holder or subject to redemption upon the occurrence of uncertain events not solely within our control) is classified as temporary equity. At all other times, common stock is classified as stockholders’ equity. Our Class A Common Stock features certain redemption rights that are considered to be outside of our control and subject to occurrence of uncertain future events. Accordingly, Class A Common Stock subject to possible redemption is presented at redemption value as temporary equity, outside of the stockholders’ equity section of our unaudited condensed consolidated balance sheet. Immediately upon the closing of the Initial Public Offering, the Company recognized the remeasurement from initial book value to redemption amount value. The change in the carrying value of the redeemable Class A Common Stock subject to possible redemption resulted in charges against additional paid-in capital and accumulated deficit.
Recent Accounting Standards
Management does not believe that any recently issued, but not yet effective, accounting standards, if currently adopted, would have a material effect on our unaudited condensed consolidated financial statements.
JOBS Act
The JOBS Act contains provisions that, among other things, relax certain reporting requirements for qualifying public companies. We qualify as an “emerging growth company” and under the JOBS Act will be allowed to comply with new or revised accounting pronouncements based on the effective date for private (not publicly traded) companies. We are electing to delay the adoption of new or revised accounting standards, and as a result, we may not comply with new or revised accounting standards on the relevant dates on which adoption of such standards is required for non-emerging growth companies. As a result, our financial statements may not be comparable to companies that comply with new or revised accounting pronouncements as of public company effective dates.
Additionally, we are in the process of evaluating the benefits of relying on the other reduced reporting requirements provided by the JOBS Act. Subject to certain conditions set forth in the JOBS Act, if, as an “emerging growth company,” we choose to rely on such exemptions we may not be required to, among other things, (i) provide an auditor’s attestation report on our system of internal control over financial reporting pursuant to Section 404, (ii) provide all of the compensation disclosure that may be required of non-emerging growth public companies under the Dodd-Frank Wall Street Reform and Consumer Protection Act, (iii) comply with any requirement that may be adopted by the PCAOB regarding mandatory audit firm rotation or a supplement to the auditor’s report providing additional information about the audit and the financial statements (auditor discussion and analysis) and (iv) disclose certain executive compensation related items such as the correlation between executive compensation and performance and comparisons of the CEO’s compensation to median employee compensation. These exemptions will apply for a period of five years following the completion of our Initial Public Offering or until we are no longer an “emerging growth company,” whichever is earlier.
Quantitative and Qualitative Disclosures about Market Risk
We are a smaller reporting company as defined by Rule 12b-2 of the Exchange Act and are not required to provide the information otherwise required under this item.
197
Directors and Executive Officers
Senti’s current directors and executive officers are as follows (ages as of June 23, 2022):
Name | Age | Position(s) Held | ||||
Executive Officers | ||||||
Timothy Lu, M.D., Ph.D. | 41 | Chief Executive Officer, President and Director | ||||
Curt Herberts III* | 41 | Chief Operating Officer | ||||
Deborah Knobelman, Ph.D. | 49 | Chief Financial Officer | ||||
Philip Lee, Ph.D. | 41 | Chief Technology Officer | ||||
Kanya Rajangam, M.D., Ph.D. | 49 | Chief Medical and Development Officer | ||||
Non-Employee Directors | ||||||
Susan Berland(a)(b) | 68 | Director | ||||
Brenda Cooperstone, M.D.(b) | 57 | Director | ||||
Edward Mathers(a)(c) | 62 | Director | ||||
James J. (Jim) Collins(c) | 56 | Director | ||||
Omid Farokhzad(a) | 52 | Director | ||||
David Epstein(b)(c) | 60 | Director | ||||
| (a) | Member of the audit committee |
| (b) | Member of the compensation committee |
| (c) | Member of the nominating and corporate governance committee |
| * | On July 26, 2022, Mr. Herberts notified us of his decision to resign from employment with us as Chief Operating Officer, effective as of August 19, 2022. |
Executive Officers
Timothy Lu, M.D., Ph.D. has served as our Chief Executive Officer since July 2016, President since February 2018 and a member of our board of directors since June 2016, and is one of our co-founders. In June 2010, Dr. Lu joined Massachusetts Institute of Technology faculty in the departments of Biological Engineering
and Electrical Engineering and Computer Science. Dr. Lu has been a co-founder and a Scientific Advisory Board member to a number of biotechnology and biopharmaceutical companies, including BiomX Inc., Corvium, Inc., Eligo Bioscience S.A.S, Engine Biosciences Pte. Ltd., Synlogic, Inc. and Tango Therapeutics, Inc. He currently
serves on the board of directors of the Alliance for Regenerative Medicine. Dr. Lu earned his M.D. from Harvard Medical School and his Ph.D. in Electrical and Biomedical Engineering from Massachusetts Institute of Technology as part of the Harvard-MIT Health Sciences and Technology Medical Engineering and Medical Physics Program. We believe Dr. Lu is qualified to serve on our board of directors due to his extensive experience in the field of synthetic biology, as well as the perspective and experience he brings as our Chief Executive Officer.
Curt Herberts III has served as our Chief Operating Officer since January 2021 and as our Secretary since July 2018. From June 2018 to January 2021, he served as our Chief Financial Officer and Chief Business Officer, from January 2021 to May 2021, he served as our Acting Chief Financial Officer and from November 2020 to May 2021 he served as our Treasurer. Prior to joining us, Mr. Herberts held various positions at Sangamo Therapeutics, Inc., a public biotechnology company, including as Senior Vice President and Chief Business Officer from December 2016 to May 2018 and Vice President and Head of Corporate Development from July 2015 to December 2016. Prior to Sangamo Therapeutics, Inc., Mr. Herberts served in various positions at Campbell Alliance Group, Inc., which was acquired by inVentiv Health, Inc. Mr. Herberts earned his B.A. in Human Biology from Stanford University and his Master of Business and Science from the Keck Graduate Institute of Applied Life Sciences.
Deborah Knobelman, Ph.D. has served as our Chief Financial Officer and Treasurer since May 2021. Prior to joining us, Dr. Knobelman served in interim C-suite roles for several life sciences companies through her firm
198
Waverly BioConsulting LLC from April 2012 to May 2021. Dr. Knobelman served as a Chief Financial Officer at GeneriCo, LLC from April 2016 to July 2017 and prior to that as a Chief Business Officer at Ampio Pharmaceuticals, Inc. from September 2011 to April 2012. Dr. Knobelman previously served as Director of Commercial Strategy and Analytics at Pfizer, Inc. from June 2008 to August 2011. Earlier in her career, Dr. Knobelman was an Equity Research Analyst covering Specialty Pharmaceuticals and Biotech as a Senior Research Analyst for Piper Jaffray and as a Research Associate at JPMorgan. Dr. Knobelman earned her AB in Chemistry from Duke University and her Ph.D. in Pharmacology from the University of Pennsylvania School of Medicine.
Philip Lee, Ph.D. has served as our Chief Technology Officer since January 2021 and is one of our co-founders. Dr. Lee served as our Chief Operating Officer from February 2018 to February 2021, as our President from July 2016 to February 2018 and as our Treasurer from July 2016 to November 2020. Dr. Lee also served as a member of our board of directors from July 2016 to February 2018. Prior to joining us, Dr. Lee held various positions at MilliporeSigma, a division of Merck KGaA, including as the Head of Cell Culture Systems from November 2014 to May 2016 and Senior Manager of Science & Technology and New Business Initiatives Lead from 2012 to 2014. Dr. Lee co-founded CellASIC Corp. in September 2004 and served as its Chief Executive Officer until it was acquired by Merck KGaA in April 2012. Dr. Lee earned his B.S. in Chemical Engineering and Biology from the Massachusetts Institute of Technology and his Ph.D. in Bioengineering from the University of California, Berkeley and the University of California, San Francisco.
Kanya Rajangam, M.D., Ph.D. has served as our Chief Medical and Development Officer since July 2022. Previously, she served as Nkarta, Inc.’s Chief Medical Officer from September 2019 to June 2022 and as its Senior Vice President and Chief Medical Officer from December 2018 to September 2019. Dr. Rajangam also serves as an independent director at Turnstone Biologics, a privately held oncolytic virus/ TIL therapies company, and has since November 2021. Previously, Dr. Rajangam was Senior Vice President and Chief Medical Officer at Atara Biotherapeutics, Inc., a publicly held allogeneic T-cell immunotherapy company, from August 2017 to September 2018. She was Chief Medical Officer at Cleave Biosciences from December 2016 to July 2017 and Vice President of Clinical Development from June 2015 to December 2016. Previously, she was Executive Director at Nektar Therapeutics, a publicly held biopharmaceutical company, from March 2015 to May 2015. Prior to that, she held positions of increasing responsibility at Onyx Pharmaceuticals, Inc. from April 2011 to February 2015, including as Senior Medical Director. Before that, she served at Exelixis, Inc. from January 2008 to April 2011 in positions of increasing responsibility, including as Associate Medical Director. She was a research scientist at Baxter Healthcare, Inc. from November 2006 to December 2007. Dr. Rajangam earned a medical degree from St. John’s Medical College Bangalore University and subsequently completed her general surgical residency at PGIMER, Chandigarh, India. She received a Ph.D. in biomedical engineering from Northwestern University.
Non-Employee Directors
Susan Berland has served as a member of our board of directors since June 2021. Most recently, Ms. Berland served as Consulting Chief Financial Officer of Bluestar Genomics, Inc. from May 2000 through August 2021. Previously, Ms. Berland was Chief Financial Officer at Atreca, Inc. from February 2015 to April 2019 and Chief Financial Officer at Mendel Biotechnology from September 2011 to December 2014. Ms. Berland served as an independent consultant to various biotech companies from March 2006 to August 2011. Ms. Berland was also the Chief Financial Officer at Poniard Pharmaceuticals from September 2004 to August 2006, and Chief Financial Officer at DNA Sciences from September 2000 to May 2003. Ms. Berland held various leadership positions at Monsanto including Head of Financial Planning from June 1999 to August 2000 and Director, Mergers & Acquisitions from April 1996 to June 1999. Ms. Berland earned her B.A. in Finance and M.B.A. from the University of Wisconsin — Milwaukee. We believe Ms. Berland is qualified to serve on our board of directors because of her extensive financial experience and experience in the biotechnology industry.
Brenda Cooperstone, M.D. has served as a member of our board of directors since October 2019. Dr. Cooperstone has held various leadership positions at Pfizer, Inc., a public biopharmaceutical company,
199
including as Senior Vice President since May 2017, Chief Development Officer for Rare Disease in Global Product Development since May 2016 and Head of Development for Rare Disease in Global Product Development from November 2015 to May 2016. Dr. Cooperstone started her career in the pharmaceutical industry at Wyeth Pharmaceuticals in 1999 and joined Pfizer, Inc. in 2009. Dr. Cooperstone earned her M.D. from McGill University, and completed her residency in pediatrics at the Montreal Children’s Hospital, her clinical fellowship in pediatric nephrology at Children’s Hospital of Philadelphia and a research fellowship at the University of Pennsylvania’s Renal Electrolyte division. We believe Dr. Cooperstone is qualified to serve on our board of directors because of her extensive experience in the pharmaceutical industry.
Edward Mathers has served as a member of our board of directors since July 2016. Mr. Mathers has served as a General Partner at New Enterprise Associates, Inc. (NEA), a private venture capital firm focusing on technology and healthcare investments, since November 2019, and prior to that served as partner at NEA from August 2008 to October 2019. Prior to joining NEA, Mr. Mathers served as Executive Vice President, Corporate Development and Venture at MedImmune, Inc., a biopharmaceutical company, and led its venture capital subsidiary, MedImmune Ventures, Inc. Mr. Mathers currently serves on the board of directors of Affinia Therapeutics, Inc., Akouos, Inc. (NASDAQ: AKUS), Code Biotherapeutics, Inc., Inozyme Pharma, Inc. (NASDAQ: INZY), MBX Biosciences, Inc., Mirum Pharmaceuticals, Inc. (NASDAQ: MIRM), ObsEva SA (NASDAQ: OBSV), Reneo Pharmaceuticals, Inc. (NASDAQ: RPHM), Rhythm Pharmaceuticals, Inc. (NASDAQ: RYTM), Shape Therapeutics Inc., Sorriso Pharmaceuticals, Inc., Synlogic, Inc. (NASDAQ: SYBX) (formerly known as Mirna Therapeutics, Inc.) and Trevi Therapeutics, Inc. (NASDAQ: TRVI), all biopharmaceutical or pharmaceutical companies, and he previously served on the board of directors of Amplyx Pharmaceuticals, Inc. from October 2015 to April 2021, when it was acquired by Pfizer Inc., Liquidia Technologies, Inc., a public biopharmaceutical company, from April 2009 to May 2019 and Ra Pharmaceuticals, Inc. from February 2010 to April 2020 when it was acquired by UCB S.A. Mr. Mathers earned his B.S. in chemistry from North Carolina State University. We believe Mr. Mathers’ experience as a venture capitalist, as an executive and in business development and his experience in serving on the board of directors for several public and private biopharmaceutical and life sciences companies qualify him to serve on our board of directors.
James J. (Jim) Collins, Ph.D. has served as a member of our board of directors since June 2022. Dr. Collins has served as the Termeer Professor of Medical Engineering and Science in the Institute for Medical Engineering and Science and the Department of Biological Engineering at MIT since December 2014. Prior to his joining MIT, from October 1990 to November 2014, Dr. Collins served as a professor in biomedical engineering at Boston University. Dr. Collins currently serves as a member of the board of directors of Fulcrum Therapeutics, Inc. (NASDAQ: FULC) and the Orion Biotech Opportunities Corp (NASDAQ: ORIA). Dr. Collins received a B.S. in Physics from the College of the Holy Cross and a doctorate in Medical Engineering from the University of Oxford. From 1987 to 1990, he was a Rhodes Scholar. We believe Dr. Collins’ extensive industry expertise qualifies him to serve on our board of directors.
Omid Farokhzad, M.D. has served as a member of our board of directors since June 2022. Dr. Farokhzad is a physician-scientist, serial entrepreneur, company founder, company builder, executive and director — across multiple companies and technology platforms. He founded Seer, Inc. (Nasdaq: SEER) in 2017, which advances a transformative proteomics platform, and served as Founder, CEO and Chair of DYNS from March 2021 to June 2022. He previously co-founded BIND Therapeutics (acquired by Pfizer), Selecta Biosciences, Inc. (Nasdaq: SELB), which is developing a novel antigen-specific tolerance platform for biologics and gene therapy, and Tarveda Therapeutics, Inc., a privately held oncology biotherapeutics company. From September 2004 to February 2018, he was a Professor at Harvard Medical School and a director of the Center for Nanomedicine at Brigham and Women’s Hospital. He has authored over 180 papers and is an inventor on over 200 issued or pending patents. He is a Fellow of the National Academy of Inventors. He is also a recipient of the 2016 Ellis Island Medal of Honor; the 2014 Golden Door Award from the International Institute of New England, for his scientific, societal and economic contributions to America as an immigrant; The Worldview 100 by Scientific American in 2015, which recognized visionaries who shaped biotechnology around the world; the 2013 RUSNANOPRIZE, one of the largest international nanotechnology prizes, for his work on nanomaterial surface modification; and the 2012 Ernst & Young New England Entrepreneur of the Year Award. Dr. Farokhzad holds
200
an MA and M.D. from Boston University and an MBA from MIT Sloan School of Management.
David R. Epstein has served as a member of our board of directors since June 2022, and was previously a member of the DYNS board since March 2021. Mr. Epstein is the executive partner at Flagship Pioneering and Chairman of Axcella Therapeutics (Nasdaq: AXLA), Rubius Therapeutics, Inc. (Nasdaq: RUBY) and Evelo Biosciences, Inc. (Nasdaq: EVLO), and he is a director of OPY Acquisition Corp. I (Nasdaq: OHAA). Mr. Epstein is also a board member at four privately held biotherapeutics companies (Ring Therapeutics, Tarus Therapeutics, Valo Health and Woolsey Pharma). From 2010 to mid-2016, he served as CEO of Novartis Pharmaceuticals, a division of Novartis AG. Previously, he started and led Novartis’s Oncology and Molecular Diagnostic units. Under his leadership, Norvartis’s oncology business grew to the second largest in the world. Mr. Epstein has more than 25 years of extensive drug development, deal making, commercialization and leadership experience on a global scale. Over the course of his career, he led the development and commercialization of over 30 new molecular entities, including major breakthroughs such as Glivec®, Tasigna®, Gilenya®, Cosentyx® and Entresto®. His teams developed three Prix Galien award winners, and he has mentored several CEOs into their roles. In 2015, he was named by FierceBiotech as one of the “25 most influential people in biopharma.” Early in his career, he was an associate in the strategy practice of consulting firm Booz, Allen and Hamilton. Mr. Epstein holds a BS in pharmacy from Rutgers University College of Pharmacy and an MBA in finance and marketing from Columbia University Graduate School of Business.
Family Relationships
There are no family relationships among any of our executive officers or directors.
Board Composition
Our board of directors manages our business and affairs, as provided by Delaware law, and conducts its business through meetings of the board of directors and its standing committees. Our board of directors consists of seven members. The primary responsibilities of our board of directors is to provide risk oversight and strategic guidance and to counsel and direct management. Our board of directors meets on a regular basis and convenes additional meetings, as required.
Director Independence
We adhere to the rules of Nasdaq in determining whether a director is independent. Our board of directors has consulted with its counsel to ensure that the board of directors’ determinations are consistent with those rules and all relevant securities and other laws and regulations regarding the independence of directors. The Nasdaq listing standards generally define an “independent director” as a person who is not an executive officer or employee, or who does not have a relationship which, in the opinion of the company’s board of directors, would interfere with the exercise of independent judgment in carrying out his or her responsibilities as a director. Our board of directors has determined that Brenda Cooperstone, Susan Berland, Edward Mathers, Omid Farokhzad, David Epstein and James J. (Jim) Collins are considered independent directors. Our independent directors have regularly scheduled meetings at which only independent directors are present.
Committees of Our Board of Directors
Our board of directors has an audit committee, a compensation committee, and a nominating and corporate governance committee. In addition, from time to time, special committees may be established under the direction of our board of directors when necessary to address specific issues. Copies of each board committee’s charter are posted on our website. Our website and the information contained on, or that can be accessed through, such website are not deemed to be incorporated by reference in, and are not considered part of, this prospectus. The composition and responsibilities of each of the committees of our board of directors are described below. Members serve on these committees until their resignation or until otherwise determined by our board of directors.
201
Audit Committee
Our audit committee consists of Susan Berland, Edward Mathers and Omid Farokhzad. Our board of directors has determined that each member of the audit committee satisfies the independence requirements under the Nasdaq Listing Rules and Rule 10A-3(b)(1) of the Exchange Act. The chair of the audit committee is Susan Berland. Our board of directors has determined that Susan Berland is an “audit committee financial expert” within the meaning of SEC regulations. Each member of the audit committee can read and understand fundamental financial statements in accordance with applicable listing standards. In arriving at these determinations, our board of directors examined each audit committee member’s scope of experience and the nature of his or her employment. The primary purpose of the audit committee is to discharge the responsibilities of our board of directors with respect to corporate accounting and financial reporting processes, systems of internal control and financial statement audits, and to oversee our independent registered public accounting firm. Specific responsibilities of the audit committee include:
| • | helping our board of directors oversee the corporate accounting and financial reporting processes; |
| • | managing and/or assessing the selection, engagement, qualifications, independence and performance of a qualified firm to serve as the independent registered public accounting firm to audit our consolidated financial statements; |
| • | discussing the scope and results of the audit with the independent registered public accounting firm, and reviewing, with management and the independent accountants, our interim and year-end operating results; |
| • | developing procedures for employees to submit concerns anonymously about questionable accounting or audit matters; |
| • | reviewing related party transactions; |
| • | reviewing our policies on risk assessment and risk management; |
| • | reviewing, with the independent registered public accounting firm, our internal quality control procedures, any material issues with such procedures and any steps taken to deal with such issues; and |
| • | pre-approving audit and permissible non-audit services to be performed by the independent registered public accounting firm. |
Our audit committee operates under a written charter that satisfies the applicable Nasdaq Listing Rules.
Compensation Committee
Our compensation committee consists of Brenda Cooperstone, Susan Berland and David Epstein. The chair of the compensation committee is Brenda Cooperstone. The parties have determined that each member of the compensation committee satisfies the independence requirements under the Nasdaq Listing Rules, and is a “non-employee director” as defined in Rule 16b-3 promulgated under the Exchange Act. The primary purpose of our compensation committee is to discharge the responsibilities of our board of directors in overseeing our compensation policies, plans and programs and to review and determine the compensation to be paid to our executive officers, directors and other senior management, as appropriate. Specific responsibilities of the compensation committee include:
| • | reviewing and recommending to our board of directors the compensation of the chief executive officer and other executive officers; |
| • | reviewing and recommending to our board of directors the compensation of the directors; |
| • | administering our equity incentive plans and other benefit programs; |
| • | reviewing, adopting, amending and terminating incentive compensation and equity plans, severance agreements, profit sharing plans, bonus plans, change-of-control protections and any other compensatory arrangements for our executive officers and other senior management; and |
202
| • | reviewing and establishing general policies relating to compensation and benefits of our employees, including our overall compensation philosophy. |
Our compensation committee operates under a written charter that satisfies the applicable Nasdaq Listing Rules.
Nominating and Corporate Governance Committee
Our nominating and corporate governance committee consists of Edward Mathers, James J. (Jim) Collins and David Epstein. The chair of the nominating and corporate governance committee is Edward Mathers. Our board of directors has determined that each member of the nominating and corporate governance committee satisfies the independence requirements under the Nasdaq Listing Rules.
Specific responsibilities of our nominating and corporate governance committee include:
| • | identifying and evaluating candidates, including the nomination of incumbent directors for reelection and nominees recommended by stockholders, to serve on our board of directors; |
| • | considering and making recommendations to our board of directors regarding the composition and chairpersonship of the board of directors and committees of the board of directors; |
| • | reviewing developments in corporate governance practices; |
| • | developing and making recommendations to our board of directors regarding corporate governance guidelines and matters; and |
| • | overseeing periodic evaluations of our board of directors’ performance, including committees of our board of directors. |
Our nominating and corporate governance committee operates under a written charter that satisfies the applicable Nasdaq Listing Rules.
Code of Business Conduct and Ethics
We have adopted a code of business conduct and ethics, or the Code of Conduct, that applies to all directors, officers and employees, including the principal executive officer, principal financial officer, principal accounting officer or controller or persons performing similar functions, and is available on our website at www.sentibio.com. In addition, we intend to post on our website all disclosures that are required by law or the Nasdaq Listing Rules concerning any amendments to, or waivers from, any provision of the Code of Conduct. The reference to our website address does not constitute incorporation by reference of the information contained at or available through the website, and you should not consider it to be a part of this prospectus.
Compensation Committee Interlocks and Insider Participation
None of the members of the compensation committee is currently, or has been at any time, one of our executive officers or employees. None of our executive officers currently serves, or has served during the last calendar year, as a member of the board of directors or compensation committee of any entity that has one or more executive officers serving as a member of our board of directors or compensation committee.
203
References in this section to “we,” “our,” “us” and the “Company” generally refer to Senti and its subsidiaries prior to the Business Combination and to Senti and its subsidiaries after giving effect to the Business Combination.
This section provides an overview of Senti’s executive compensation program as it relates to the executive officers named below (the “named executive officers”), for the year ended December 31, 2021, which consist of our principal executive officer and our two most highly compensated executive officers:
| • | Timothy Lu, M.D., Ph.D., our Chief Executive Officer and President, referred to herein as Dr. Lu; |
| • | Curt Herberts III, our Chief Operating Officer, former Chief Financial Officer and former Chief Business Officer, referred to herein as Mr. Herberts; and |
| • | Philip Lee, Ph.D., our Chief Technology Officer and former Chief Operating Officer, referred to herein as Dr. Lee. |
Summary Compensation Table
The following table presents all of the compensation awarded to, earned by or paid to Senti’s named executive officers for the year ended December 31, 2021.
Name and Principal Position | Year | Salary ($) | Option Awards (1) | Non-Equity Incentive Plan Compensation ($)(2) | All Other Compensation ($)(3) | Total ($) | ||||||||||||||||||
Timothy Lu, M.D., Ph.D. | 2021 | 475,000 | 23,803,309 | 219,213 | — | 24,497,522 | ||||||||||||||||||
Chief Executive Officer and President | ||||||||||||||||||||||||
Curt Herberts III | 2021 | 410,000 | 10,416,683 | 151,372 | 15,345 | 10,993,400 | ||||||||||||||||||
Chief Operating Officer, | ||||||||||||||||||||||||
Philip Lee, Ph.D. | 2021 | 400,000 | 10,223,623 | 160,000 | 11,600 | 10,795,223 | ||||||||||||||||||
Chief Technology Officer | ||||||||||||||||||||||||
| (1) | The amounts reported represent the aggregate grant date fair value of the awards granted to the named executive officers during year 2021, calculated in accordance with ASC 718. Such grant date fair value does not take into account any estimated forfeitures. Certain of the assumptions used in calculating the grant date fair value of the awards reported in this column are set forth in Note 9 to Senti’s consolidated financial statements included elsewhere in this prospectus. The amounts reported in this column reflect the accounting cost for the stock options and stock awards, as applicable, and does not correspond to the actual economic value that may be received upon exercise of the stock option, issuance of shares of common stock, or any sale of any of the underlying shares of common stock. In addition, certain of the amounts reported in this column have not been audited and are subject to customary year-end audit adjustments. |
| (2) | Reflects performance-based cash bonuses awarded to Senti’s named executive officers. See “— Narrative to the Summary Compensation Table — Non-Equity Incentive Plan Compensation” below for a description of the material terms pursuant to which this compensation was awarded. |
| (3) | Represents: (i) for Dr. Lee, $11,600 in matching contributions made by Senti under Senti’s 401(k) plan; and (ii) for Mr. Herberts, $11,600 in matching contributions made by Senti under Senti’s 401(k) plan and $3,745 paid by us to cover taxes Mr. Herberts owed relating to a health savings account contribution. |
Narrative to the Summary Compensation Table
Senti’s compensation committee or board of directors reviews compensation annually for all employees, including named executive officers. In making compensation determinations, Senti considers compensation for
204
comparable positions in the market, the historical compensation levels of executives, individual performance as compared to Senti’s expectations and objectives, Senti’s desire to motivate employees to achieve short- and long-term results that are in the best interests of Senti’s stockholders and a long-term commitment to the company.
Either the compensation committee or the board of directors has historically determined the executive officers’ compensation and has typically reviewed and discussed management’s proposed compensation with the chief executive officer for all executives other than the chief executive officer. Based on those discussions and its discretion, either Senti’s board of directors or compensation committee then approved the compensation of each executive officer. Upon the closing of the Business Combination, the compensation committee will determine the executive officers’ compensation and follow this process, but generally the compensation committee itself, rather than the board of directors, will approve the compensation of each executive officer.
Annual Base Salary
Base salaries for the executive officers are initially established through arm’s-length negotiations at the time of the executive officer’s hiring, taking into account such executive officer’s qualifications, experience, the scope of his or her responsibilities and competitive market compensation paid by other companies for similar positions within the industry and geography. Base salaries are reviewed periodically, typically in connection with Senti’s annual performance review process, and adjusted from time to time to realign salaries with market levels after taking into account individual responsibilities, performance and experience. In making decisions regarding salary increases, Senti may also draw upon the experience of members of the board of directors with executives at other companies. The 2021 base salaries for the named executive officers were as follows: (a) $475,000 for Dr. Lu; (b) $410,000 for Mr. Herberts; and (c) $400,000 for Dr. Lee.
Non-Equity Incentive Plan Compensation
Senti’s named executive officers are each eligible to receive a discretionary annual bonus based on individual and company performance. In 2021, Dr. Lu was eligible to earn an annual target performance bonus equal to 50% of his 2021 base salary based on the achievement of corporate objectives. Mr. Herberts and Dr. Lee were eligible to earn an annual target performance bonus equal to 40% of their respective 2021 base salary based on the achievement of both individual and corporate objectives. Payment of 2021 annual bonuses was based in part on us achieving certain research and product development, capital raising and other target goals. The compensation committee determined that Dr. Lu, Mr. Herberts and Dr. Lee were entitled to approximately 92.3%, 92.3% and 100% respectively, of their target bonuses.
Equity-Based Incentive Awards
Senti’s equity-based incentive awards are designed to align our interests and those of Senti’s stockholders with those of Senti’s employees and consultants, including Senti’s named executive officers. As of December 31, 2021, stock option awards were the only form of equity award we granted to the named executive officers.
We have historically used stock options as incentives for long-term compensation to the named executive officers as the return on the awards is tied to an increase in our stock price. Senti may grant equity awards at such times as our board of directors or compensation committee determines appropriate in their discretion. Additional grants may occur periodically in order to incentivize executives with respect to achieving certain corporate goals or to reward them for exceptional performance.
Prior to the completion of the Business Combination, all of the equity incentive awards Senti granted were made pursuant to Senti’s 2016 Stock Incentive Plan, as amended, or the 2016 Plan. Following the completion of the Business Combination, Senti will grant equity incentive awards under the terms of our 2022 Equity Incentive Plan, or the Incentive Plan. The terms of Senti’s 2016 Plan are described below under “— Equity Benefit Plans.”
205
All stock options are granted with an exercise price per share that is no less than the fair market value of Senti’s common stock on the date of grant of such award. Senti’s stock option grants generally vest over a four-year period, and may be subject to acceleration of vesting and exercisability under certain termination and change in control events. See “— Outstanding Equity Awards at Fiscal Year-End” below for additional information.
Outstanding Equity Awards at Fiscal Year-End
The following table provides information regarding the outstanding equity awards held by the named executive officers as of December 31, 2021. All awards were granted pursuant to the 2016 Plan. See “— Equity Benefit Plans–2016 Stock Incentive Plan” below for additional information.
| Option Awards | Stock Awards | |||||||||||||||||||||||||||||||||||
Name and Principal | Grant Date | Vesting Commencement Date | Number of Securities Underlying Unexercised Options (#) (Exercisable) | Number of Securities Underlying Unexercised Options (#) (Unexercisable) | Equity Incentive Plan Awards: Number of Securities Underlying Unexercised Unearned Options (#) | Option Exercise Price ($) | Option Expiration Date | Number of Shares or Units of Stock that have not Vested (#) | Market Value of Shares or Units of Stock that have not Vested ($)(6) | |||||||||||||||||||||||||||
Timothy Lu, M.D., Ph.D. | 2/2/2021 | (1) | 1/1/2021 | 2,320,000 | 14,695,435 | 0.52 | 2/1/2031 | |||||||||||||||||||||||||||||
Chief Executive Officer and President | 12/19/2021 | (3) | 6/8/2022 | 3,093,776 | 1.94 | 12/18/2031 | ||||||||||||||||||||||||||||||
| 12/19/2021 | (4) | 6/8/2022 | 1.94 | 12/18/2031 | ||||||||||||||||||||||||||||||||
Curt Herberts III | 6/18/2018 | (1)(2) | 6/4/2018 | 133,871 | (5) | $ | 236,952 | |||||||||||||||||||||||||||||
Chief Operating Officer, | 2/2/2021 | (1) | 1/1/2021 | 1,250,000 | (5) | $ | 2,212,500 | |||||||||||||||||||||||||||||
| 12/19/2021 | (3) | 6/8/2022 | 7,734,440 | 1.94 | 12/18/2031 | |||||||||||||||||||||||||||||||
Philip Lee, Ph.D. | 2/2/2021 | (1) | 1/1/2021 | — | 1,035,000 | (5) | $ | 1,831,950 | ||||||||||||||||||||||||||||
Chief Technology Officer | 12/19/2021 | (3) | 6/8/2022 | 7,734,440 | 1.94 | 12/18/2031 | ||||||||||||||||||||||||||||||
| (1) | 25% of the shares underlying this option vest on the one-year anniversary of the vesting commencement date and the remainder vest in 36 equal monthly installments thereafter, subject to the named executive officer’s continued employment through the applicable vesting date. |
| (2) | This grant is eligible for accelerated vesting as described below under the section titled “Potential Payments and Benefits upon Termination or Change in Control.” |
| (3) | The shares underlying this option are subject to both time-based and performance-based vesting conditions, or the BCA Vesting Conditions. 100% of the shares underlying the option satisfy the performance-based vesting condition upon consummation of the transactions contemplated by the BCA subject to the named executive officer’s continued employment or other service relationship through such date. The shares underlying the option shall satisfy the time-based vesting condition as follows: 25% on the one-year anniversary of the vesting commencement date and the remainder vest in 36 equal monthly installments thereafter, subject to the named executive officer’s continued employment through the applicable vesting date. In February 2022, this option was amended to provide that the vesting commencement date would be the Closing Date, rather than December 19, 2021. |
| (4) | The shares underlying this option are subject to the BCA Vesting Conditions and additional market conditions based upon the attainment of certain share prices, or hurdle prices. 25% of the shares underlying the option satisfy the additional market condition on the date that the applicable hurdle price is reached for 20 out of 30 consecutive trading days. The hurdle prices are $2.90, $3.87, $4.84 and $5.81, respectively. In February 2022, this option was amended to provide that the vesting commencement date would be the Closing Date, rather than December 19, 2021. |
| (5) | The amount reflects the number of unvested shares issued upon the early exercise of a stock option grant that remain subject to Senti’s repurchase right. |
| (6) | The amounts reported in this column reflect the number of unvested shares multiplied by $1.77, which was the fair market value of Senti’s common stock as of December 20, 2021 as determined by an independent third-party valuation. |
Pension and retirement benefits
Senti’s named executive officers did not participate in, or otherwise receive any benefits under, any pension or defined benefit retirement plan sponsored by Senti during the fiscal year ended December 31, 2021.
206
Nonqualified deferred compensation
Senti’s named executive officers did not participate in, or earn any benefits under, any nonqualified deferred compensation plan sponsored by Senti during the fiscal year ended December 31, 2021. Senti’s board of directors may elect to provide the officers and other employees with nonqualified deferred compensation benefits in the future if it determines that doing so is in Senti’s best interests.
Employment Arrangements
Below are descriptions of Senti’s employment offer letters with Dr. Lu, Mr. Herberts and Dr. Lee. The letters generally provide for at-will employment without any specific term and set forth the named executive officer’s initial base salary and eligibility for employee benefits. Each of Senti’s named executive officers has executed a form of Senti’s standard confidential information and inventions assignment agreement.
Additionally, the named executive officers are entitled to certain severance benefits pursuant to their employment offer letters, the terms of which are described under the section titled “Potential Payments and Benefits upon Termination or Change in Control” below.
Agreement with Timothy Lu, M.D., Ph.D.
In December 2018, Senti entered into an employment letter agreement with Dr. Lu, Senti’s current Chief Executive Officer. Pursuant to his letter agreement, Dr. Lu was initially entitled to an annual base salary of $400,000, a signing bonus of $168,333.33, and a discretionary annual target bonus equal to 40% of his base salary, contingent upon the achievement of performance objectives established by Senti. In January 2021, Dr. Lu’s annual base salary was increased to $475,000. Prior to his employment, starting in July 2016, Dr. Lu provided services to Senti pursuant to a consulting agreement. In connection with such consulting services, Dr. Lu was issued 8,100,000 shares of Senti common stock pursuant to a restricted stock purchase agreement, which vested as follows: 25% on the date of issuance and the remainder in 36 equal monthly installments thereafter, subject to Dr. Lu’s continued service through each such date. Dr. Lu was also granted options to purchase 2,320,000 shares of Senti common stock in 2021 as described in “— Outstanding Equity Awards at Fiscal Year-End” above. Dr. Lu remains eligible for future equity awards as determined by our board of directors or its compensation committee.
Agreement with Curt Herberts III
In April 2018, Senti entered into an employment agreement with Mr. Herberts, Senti’s current Chief Operating Officer. Pursuant to his agreement, Mr. Herberts held the positions of Chief Financial Officer and Chief Business Officer, and was initially entitled to an annual base salary of $370,000, a signing bonus of $100,000, and a discretionary annual target bonus equal to 35% of his base salary, contingent upon the achievement of performance objectives established by Senti. In January 2021, Mr. Herberts’ annual base salary was increased to $410,000. Mr. Herberts’ agreement also provided that Mr. Herberts was entitled to the grant of a stock option to purchase 1,070,964 shares of Senti common stock, which was granted in June 2018 and vests as follows: 25% on the one- year anniversary of June 4, 2018 and the remainder in 36 equal monthly installments thereafter, subject to Mr. Herberts’ continued employment through each such date. Mr. Herberts was also granted “early exercise” options to purchase 1,250,000 shares of Senti common stock in 2021, which Mr. Herberts exercised in February 2021 and remain subject to vesting as described in “— Outstanding Equity Awards at Fiscal Year-End” above. Mr. Herberts remains eligible for future equity awards as determined by our board of directors or its compensation committee.
Agreement with Philip Lee, Ph.D.
In December 2018, Senti entered into an employment letter agreement with Dr. Lee, Senti’s current Chief Technology Officer. Pursuant to his letter agreement, Dr. Lee held the position of Chief Operating Officer, and
207
was initially entitled to an annual base salary of $350,000, a signing bonus of $126,666.67, and a discretionary annual target bonus equal to 35% of his base salary, contingent upon the achievement of performance objectives established by Senti. In January 2021, Dr. Lee’s annual base salary was increased to $400,000. Prior to his employment, starting in July 2016, Dr. Lee provided services to Senti pursuant to a consulting agreement. In connection with such consulting services, Dr. Lee was issued 3,750,000 shares of Senti common stock pursuant to a restricted stock purchase agreement, which vested as follows: 25% on the date of issuance and the remainder in 36 equal monthly installments thereafter, subject to Dr. Lee’s continued service through each such date. Dr. Lee was also granted options to purchase 1,035,000 shares of Senti common stock in 2021, which Dr. Lee exercised in February 2021 and remain subject to vesting as described in “—Outstanding Equity Awards at Fiscal Year-End” above. Dr. Lee remains eligible for future equity awards as determined by our board of directors or its compensation committee.
Potential Payments and Benefits upon Termination or Change in Control
Regardless of the manner in which a named executive officer’s employment with Senti terminates, the named executive officer is entitled to receive amounts earned during his term of service, including salary and accrued unused vacation pay.
Termination Payments and Benefits
Under the terms of their respective employment agreements, Dr. Lu, Mr. Herberts and Dr. Lee are each eligible to receive the following severance payments and benefits upon a termination without “cause” or upon “resignation for good reason,” each as defined below, contingent upon the named executive officer’s timely delivery to Senti of a satisfactory release of claims:
| • | For Dr. Lu, he is entitled to a cash severance equal to 12 months of his then current base salary, plus the prorated portion of his target annual bonus, and up to 12 months of payment for continued group health plan benefits. If such termination or resignation occurs within 3 months before or 12 months after a change of control, then all of his then remaining unvested shares of restricted common stock will become fully vested, although such restricted stock has already vested in full. |
| • | For Mr. Herberts, he is entitled to a cash severance equal to 9 months of his then current base salary, plus any unpaid bonus from a prior fiscal year, plus reimbursement for any unreimbursed expenses, and up to 9 months of payment for continued group health plan benefits. If such termination or resignation occurs within 3 months before or 12 months after a change of control, then all of the outstanding stock options granted to him in June 2018 will become fully vested. |
| • | For Dr. Lee, he is entitled to a cash severance equal to 9 months of his then current base salary, plus the prorated portion of his target annual bonus, and up to 9 months of payment for continued group health plan benefits. If such termination or resignation occurs within 3 months before or 12 months after a change of control, then all of his then remaining unvested shares of restricted common stock will become fully vested, although such restricted stock has already vested in full. |
For the purposes of Senti’s named executive officers’ severance benefits, the following definitions apply:
| • | “cause” means the occurrence of any of the following: (i) the employee’s material breach of their employment agreement; (ii) any act (other than retirement) or omission which has a material and adverse effect on our business, or on the employee’s ability to perform services for us, including the commission of any crime (other than minor traffic violations); or (iii) material misconduct or material neglect of the employee’s duties in connection with our business or affairs; provided, however, that before terminating the employee’s employment for cause, we will: (a) provide them with 30 days’ advance written notice with the event specifically set forth in the notice and the opportunity to cure the event (if curable); (b) provide them with a reasonable opportunity to present their case to our board of directors; and (c) require that to our board of directors determine, by majority vote, whether their employment should be terminated for cause. |
208
| • | “change of control” means the closing of: (i) a sale of all or substantially all of our assets; (ii) any consolidation or merger by us with or into any other corporation or other entity or person, or any other corporate reorganization, other than any such consolidation, merger or reorganization in which our stockholders immediately prior to such consolidation, merger or reorganization, continue to hold a majority of the voting power of the surviving entity (or, if the surviving entity is a wholly owned subsidiary, its parent) immediately after such consolidation, merger or reorganization; or (iii) a stock tender or a merger, consolidation or similar event pursuant to a transaction or series of related transactions in which a third party (which term shall include a current stockholder) acquires more than fifty percent (50%) of our equity voting securities outstanding immediately prior to the consummation of such transaction or series of related transactions, and our stockholders do not retain a majority of the equity voting securities of the surviving entity, other than (a) a merger, conversion or other transaction the principal goal of which is to change our jurisdiction of incorporation, or (b) an equity security financing for our account in which our capital stock is sold to one or more institutional investors. |
| • | “good reason” means the employee’s termination of their own employment because of any of the following: (i) our breach of any one or more of the material provisions of this Agreement; (ii) a material reduction by us of their annual base salary, unless they consent to such reduction or unless such reduction is applied equally, as a percentage of base salary, to all our senior executives; (iii) a relocation of our location such that their one-way commute as of the effective date of their employment agreement increases by more than 35 miles; or (iv) a material adverse change in their duties, authority, or responsibilities relative to their duties, authority, or responsibilities in effect immediately prior to such reduction (other than a change in title and provided that a change in title, reporting lines or position in connection with a change of control will not, in itself, be deemed to be a change in duties, authority or responsibility); provided, however, that any such termination by them shall only be deemed for good reason pursuant to this definition if: (a) they give us written notice of their intent to terminate for good reason within 90 days following the first occurrence of the condition that they believe constitutes good reason, which notice shall describe such condition; (b) we fail to remedy such condition within 30 days following receipt of the written notice (referred to as the cure period); and (c) they voluntarily terminate their employment within 30 days following the end of the cure period. |
Health and Welfare and Retirement Benefits; Perquisites
Health and Welfare Benefits and Perquisites
All of Senti’s current named executive officers are eligible to participate in Senti’s employee benefit plans, including Senti’s medical, dental, vision, disability and life insurance plans, in each case on the same basis as all of Senti’s other employees. Senti pays the premiums for the life, disability and accidental death and dismemberment insurance for all of its employees, including its named executive officers. Senti generally does not provide perquisites or personal benefits to its named executive officers, except in limited circumstances.
401(k) Plan
Senti currently maintains a 401(k) retirement savings plan for its employees, including its named executive officers, who satisfy certain eligibility requirements. The 401(k) plan is intended to qualify as a tax-qualified plan under the Code. Senti’s named executive officers are eligible to participate in the 401(k) plan on the same basis as its other employees. The Code allows eligible employees to defer a portion of their compensation, within prescribed limits, on a pre-tax basis through contributions to the 401(k) plan. Senti currently provides matching 401(k) contributions to its named executive officers.
Equity Benefit Plans
2016 Stock Incentive Plan
Senti’s board of directors adopted, and Senti’s stockholders approved the 2016 Stock Incentive Plan, or the 2016 Plan, in July 2016. As of December 31, 2021, under the 2016 Plan, options to purchase 57,732,604 shares
209
of common stock were outstanding, and 3,648,364 shares of common stock remained available for future issuance.
Awards. The 2016 Plan provides for the grant of ISOs to employees of Senti, any parent or certain subsidiary companies, and for the grant of NSOs and restricted shares to such employees, Senti’s directors, and to consultants engaged by Senti or any of its subsidiary companies.
Plan Administration. Senti’s board of directors administers and interprets the provisions of the 2016 Plan. Senti’s board of directors may delegate any or all its powers under the 2016 Plan to a committee appointed by the Board (to the extent permitted under applicable law and regulations), except that the Board retains control to amend or terminate the plan and to determine share issuances pursuant to the terms of the 2016 Plan. Under the 2016 Plan, Senti’s board of directors (or a committee delegated by Senti’s board of directors) has the authority to construe terms of awards granted under the 2016 Plan and to prescribe, amend and rescind rules and regulations relating to the 2016 Plan, to determine the terms and provisions of awards granted under the 2016 Plan and to make all other determinations in the judgment of the Senti board of directors necessary or desirable for the administration of the 2016 Plan.
Stock Options and Restricted Shares. Stock options and restricted shares granted under the 2016 Plan generally have terms similar to those described above with respect to stock options and restricted shares granted under the Incentive Plan, except the 2016 Plan provides that (unless otherwise provided for in a stock option agreement) stock options may be exercised for a period of 12 months in the case of an optionee’s death or permanent and total disability.
Changes to Capital Structure. If, through or as a result of Senti’s merger, consolidation, sale of all or substantially all of our assets, reorganization, recapitalization, reclassification, stock dividend, stock split, reverse stock split or other similar transaction, (i) the outstanding shares of common stock are increased, decreased or exchanged for a different number or kind of shares or other securities of Senti, or (ii) additional shares or new or different or other securities of Senti or other noncash assets are distributed with respect to such shares of Senti common stock or other securities, an appropriate and proportionate adjustment shall be made in (x) the maximum number and kind of shares reserved for issuance under the 2016 Plan, (y) the number and kind of shares or other securities subject to any then outstanding stock options, and (z) the price for each share or other security subject to any then outstanding stock options, so that upon exercise of such stock options, in lieu of the share of common stock for which such options were then exercisable, the relevant optionee shall be entitled to receive, for the same aggregate consideration, the same total number and kind of shares or other securities, cash or property that the owner of an equal number of outstanding shares of common stock immediately prior to the event requiring adjustment would own as a result of the event.
Corporate Transactions. If Senti is merged with or into or consolidated with another corporation under circumstances where Senti stockholders immediately prior to such merger or consolidation do not own after such merger or consolidation shares representing at least fifty percent (50%) of the voting power of Senti or the surviving or resulting corporation, as the case may be, or if shares representing fifty percent (50%) or more of the voting power of Senti are transferred to an unrelated third party, as hereinafter defined, or if Senti is liquidated, or sells or otherwise disposes of all or substantially all of its assets (each such transaction is referred to as a “change in control transaction”), Senti’s board of directors, or the board of directors of any corporation assuming the obligations of Senti, may, in its discretion, take any one or more of the following actions, as to some or all outstanding stock options or restricted stock awards (and need not take the same action as to each such option or restricted stock award): (i) provide that such stock options shall be assumed, or equivalent stock options will be substituted, by the acquiring or succeeding corporation (or an affiliate thereof), provided that any such stock options substituted for incentive stock options shall meet the requirements of Section 424(a) of the Code, (ii) upon written notice to the optionees, provide that all unexercised stock options (whether vested or unvested) will terminate immediately prior to the consummation of the change in control transaction unless exercised by the optionee to the extent otherwise then exercisable within a specified period following the date of such notice,
210
(iii) upon written notice to the grantees, provide that all unvested shares of restricted stock shall be repurchased at cost, (iv) make or provide for a cash payment to the optionees equal to the difference between (A) the fair market value of the per share consideration (whether cash, securities or other property or any combination of the above) the holder of a share of common stock will receive upon consummation of the change in control transaction (the “per share transaction price”) times the number of shares of common stock subject to outstanding vested stock options (to the extent then exercisable at prices not equal to or in excess of the per share transaction price) and (B) the aggregate exercise price of such outstanding vested stock options, in exchange for the termination of such stock options, or (v) provide that all or any outstanding stock options shall become exercisable and all or any outstanding restricted stock awards shall vest in part or in full immediately prior to such event. To the extent that any stock options are exercisable at a price equal to or in excess of the per share transaction price, the Senti board of directors may provide that such stock options shall terminate immediately upon the consummation of the change in control transaction without any payment being made to the holders of such stock options.
Senti Biosciences, Inc. 2022 Stock Option and Incentive Plan
Overview
On June 8, 2022, the Senti Biosciences, Inc. 2022 Equity Incentive Plan (the “Incentive Plan”) became effective. At the Special Meeting, the DYNS stockholders approved the Incentive Plan, which was recommended to them for approval by the DYNS board of directors. Our equity compensation program, as implemented under the Incentive Plan, allows us to grant stock options and other equity awards at levels it determines to be appropriate in order to attract new employees and other service providers, retain existing employees and service providers and to provide incentives for such persons to exert maximum efforts for our success and ultimately increase stockholder value. The Incentive Plan allows us to utilize a broad array of equity incentives with flexibility in designing equity incentives, including traditional stock option grants, stock appreciation rights, restricted stock awards, restricted stock unit awards, other stock awards and performance awards to offer competitive equity compensation packages in order to retain and motivate necessary talent .
2,492,735 Senti Common Shares are available for grant under the Incentive Plan. In addition, as further described below under “— Description of the Incentive Plan — Authorized Shares,” the share reserve is subject to annual increases each January 1 of up to 5% of the shares of our common stock (or a lesser number determined by our board of directors).
Description of the Incentive Plan
A summary description of the material features of the Incentive Plan is set forth below. The following summary does not purport to be a complete description of all the provisions of the Incentive Plan and is qualified by reference to the Incentive Plan, the form of which is included as an exhibit to this prospectus and is incorporated by reference in its entirety. Stockholders should refer to the Incentive Plan for more complete and detailed information about the terms and conditions of the Incentive Plan.
Eligibility. Any individual who is an employee of Senti or any of its affiliates, or any person who provides services to Senti or its affiliates, including members of the Senti board of directors, is eligible to receive awards under the Incentive Plan at the discretion of the plan administrator.
Awards. The Incentive Plan provides for the grant of ISOs, within the meaning of Section 422 of the Code, to employees, including employees of any parent or subsidiary, and for the grant of nonstatutory stock options (“NSOs”), stock appreciation rights, restricted stock awards, restricted stock unit awards, performance awards and other forms of awards to employees, directors and consultants, including employees and consultants of Senti’s affiliates.
Authorized Shares. Subject to adjustment as set forth in the Incentive Plan, the maximum number of Senti Common Shares that may be issued under the Incentive Plan is 2,492,735 shares. In addition, the number of Senti
211
Common Shares reserved for issuance under the Incentive Plan will automatically increase on January 1 of each year, starting on January 1, 2023 through January 1, 2032, in an amount equal to (1) 5% of the total number of Senti Common Shares on December 31 of the preceding year, or (2) a lesser number of Senti Common Shares determined by our board of directors prior to the date of the increase. The maximum number of Senti Common Shares that may be issued on the exercise of ISOs under the Incentive Plan is 2,492,735 shares.
Shares subject to stock awards granted under the Incentive Plan that expire or terminate without being exercised or otherwise issued in full or that are paid out in cash rather than in shares do not reduce the number of shares available for issuance under the Incentive Plan. Shares withheld under a stock award to satisfy the exercise, strike or purchase price of a stock award or to satisfy a tax withholding obligation do not reduce the number of shares available for issuance under the Incentive Plan. If any Senti Common Shares issued pursuant to a stock award or Rollover Option are forfeited back to or repurchased or reacquired by us (1) because of the failure to vest, (2) to satisfy the exercise, strike or purchase price, or (3) to satisfy a tax withholding obligation in connection with an award, the shares that are forfeited or repurchased or reacquired will revert to and again become available for issuance under the Incentive Plan.
Non-Employee Director Compensation Limit. The aggregate value of all compensation granted or paid to any non-employee director with respect to any calendar year, including awards granted and cash fees paid to such non-employee director, will not exceed (1) $750,000 in total value or (2) if such non-employee director is first appointed or elected to our board of directors during such calendar year, $1,000,000 in total value, in each case, calculating the value of any equity awards based on the grant date fair value of such equity awards for financial reporting purposes.
Plan Administration. Our board of directors, or a duly authorized committee thereof, administers the Incentive Plan and is referred to as the “plan administrator” herein. Our board of directors (or committee thereof) may also delegate to one or more of our officers the authority to (1) designate employees (other than officers) to receive specified stock awards and (2) determine the number of shares subject to such stock awards. Under the Incentive Plan, our board of directors (or an authorized delegate) has the authority to determine award recipients, grant dates, the numbers and types of stock awards to be granted, the applicable fair market value, and the provisions of each stock award, including the period of exercisability and the vesting schedule applicable to a stock award.
Under the Incentive Plan, our board of directors also generally has the authority to effect, without the approval of stockholders but with the consent of any materially adversely affected participant, (1) the reduction of the exercise, purchase, or strike price of any outstanding option or stock appreciation right; (2) the cancellation of any outstanding option or stock appreciation right and the grant in substitution therefore of other awards, cash, or other consideration; or (3) any other action that is treated as a repricing under GAAP.
Stock Options. ISOs and NSOs are granted under stock option agreements adopted by the plan administrator. The plan administrator determines the exercise price for stock options, within the terms and conditions of the Incentive Plan, provided that the exercise price of a stock option generally cannot be less than 100% of the fair market value of a share of our common stock on the date of grant. Options granted under the Incentive Plan vest at the rate specified in the stock option agreement as determined by the plan administrator.
The plan administrator determines the term of stock options granted under the Incentive Plan, up to a maximum of 10 years. Unless the terms of an optionholder’s stock option agreement provide otherwise or as otherwise provided by the plan administrator, if an optionholder’s service relationship with us or any of our affiliates ceases for any reason other than disability, death, or cause, the optionholder may generally exercise any vested options for a period of three months following the cessation of service. This period may be extended in the event that exercise of the option is prohibited by applicable securities laws. Unless the terms of an optionholder’s stock option agreement provide otherwise or as otherwise provided by the plan administrator, if an optionholder’s service relationship with us or any of our affiliates ceases due to death, or an optionholder dies
212
within a certain period following cessation of service, the optionholder or a beneficiary may generally exercise any vested options for a period of 18 months following the date of death. Unless the terms of an optionholder’s stock option agreement provide otherwise or as otherwise provided by the plan administrator, if an optionholder’s service relationship with us or any of our affiliates ceases due to disability, the optionholder may generally exercise any vested options for a period of 12 months following the cessation of service. In the event of a termination for cause, options generally terminate upon the termination date. In no event may an option be exercised beyond the expiration of its term.
Acceptable consideration for the purchase of Senti Common Shares issued upon the exercise of a stock option will be determined by the plan administrator and may include (1) cash, check, bank draft or money order, (2) a broker-assisted cashless exercise, (3) the tender of shares of our common stock previously owned by the optionholder, (4) a net exercise of the option if it is an NSO or (5) other legal consideration approved by the plan administrator.
Unless the plan administrator provides otherwise, options and stock appreciation rights generally are not transferable except by will or the laws of descent and distribution. Subject to approval of the plan administrator or a duly authorized officer, an option may be transferred pursuant to a domestic relations order.
Tax Limitations on ISOs. The aggregate fair market value, determined at the time of grant, of Senti Common Shares with respect to ISOs that are exercisable for the first time by an award holder during any calendar year under all of our stock plans may not exceed $100,000. Options or portions thereof that exceed such limit will generally be treated as NSOs. No ISO may be granted to any person who, at the time of the grant, owns or is deemed to own stock possessing more than 10% of our total combined voting power or that of any of our parent or subsidiary corporations unless (1) the option exercise price is at least 110% of the fair market value of the stock subject to the option on the date of grant and (2) the term of the ISO does not exceed five years from the date of grant.
Restricted Stock Unit Awards. Restricted stock unit awards are granted under restricted stock unit award agreements adopted by the plan administrator. Restricted stock unit awards may be granted in consideration for any form of legal consideration (including services) that may be acceptable to the plan administrator and permissible under applicable law. A restricted stock unit award may be settled by cash, delivery of Senti Common Shares, a combination of cash and Senti Common Shares as determined by the plan administrator, or in any other form of consideration set forth in the restricted stock unit award agreement. Additionally, dividend equivalents may be credited in respect of shares covered by a restricted stock unit award. Except as otherwise provided in the applicable award agreement or by the plan administrator, restricted stock unit awards that have not vested will be forfeited once the participant’s continuous service ends for any reason.
Restricted Stock Awards. Restricted stock awards are granted under restricted stock award agreements adopted by the plan administrator. A restricted stock award may be awarded in consideration for cash, check, bank draft or money order, services to us, or any other form of legal consideration that may be acceptable to the plan administrator and permissible under applicable law. The plan administrator determines the terms and conditions of restricted stock awards, including vesting and forfeiture terms. If a participant’s service relationship with us ends for any reason, we may receive any or all of the Senti Common Shares held by the participant that have not vested as of the date the participant terminates service with us through a forfeiture condition or a repurchase right.
Stock Appreciation Rights. Stock appreciation rights are granted under stock appreciation right agreements adopted by the plan administrator. The plan administrator determines the strike price for a stock appreciation right, which generally cannot be less than 100% of the fair market value of Senti Common Shares on the date of grant. A stock appreciation right granted under the Incentive Plan vests at the rate specified in the stock appreciation right agreement as determined by the plan administrator. Stock appreciation rights may be settled in cash or Senti Common Shares or in any other form of payment, as determined by the plan administrator and specified in the stock appreciation right agreement.
213
The plan administrator determines the term of stock appreciation rights granted under the Incentive Plan, up to a maximum of 10 years. Unless the terms of a participant’s stock appreciation rights agreement provide otherwise or as otherwise provided by the plan administrator, if a participant’s service relationship with us or any of our affiliates ceases for any reason other than cause, disability, or death, the participant may generally exercise any vested stock appreciation right for a period of three months following the cessation of service. This period may be further extended in the event that exercise of the stock appreciation right following such a termination of service is prohibited by applicable securities laws. Unless the terms of a participant’s stock appreciation rights agreement provide otherwise or as otherwise provided by the plan administrator, if a participant’s service relationship with us or any of our affiliates, ceases due to disability or death, or a participant dies within a certain period following cessation of service, the participant or a beneficiary may generally exercise any vested stock appreciation right for a period of 12 months in the event of disability and 18 months in the event of death. In the event of a termination for cause, stock appreciation rights generally terminate immediately upon the occurrence of the event giving rise to the termination of the individual for cause. In no event may a stock appreciation right be exercised beyond the expiration of its term.
Performance Awards. The Incentive Plan permits the grant of performance awards that may be settled in stock, cash or other property. Performance awards may be structured so that the stock or cash will be issued or paid only following the achievement of certain pre-established performance goals during a designated performance period. Performance awards that are settled in cash or other property are not required to be valued in whole or in part by reference to, or otherwise based on, Senti Common Shares.
The performance goals may be based on any measure of performance selected by the plan administrator. The performance goals may be based on company-wide performance or performance of one or more business units, divisions, affiliates, or business segments, and may be either absolute or relative to the performance of one or more comparable companies or the performance of one or more relevant indices. Unless specified otherwise by the plan administrator when the performance award is granted, the plan administrator will appropriately make adjustments in the method of calculating the attainment of performance goals as follows: (1) to exclude restructuring and/or other nonrecurring charges; (2) to exclude exchange rate effects; (3) to exclude the effects of changes to GAAP; (4) to exclude the effects of any statutory adjustments to corporate tax rates; (5) to exclude the effects of items that are “unusual” in nature or occur “infrequently” as determined under GAAP; (6) to exclude the dilutive effects of acquisitions or joint ventures; (7) to assume that any portion of our business which is divested achieved performance objectives at targeted levels during the balance of a performance period following such divestiture; (8) to exclude the effect of any change in the outstanding Senti Common Shares by reason of any stock dividend or split, stock repurchase, reorganization, recapitalization, merger, consolidation, spin-off, combination or exchange of shares or other similar corporate change, or any distributions to common stockholders other than regular cash dividends; (9) to exclude the effects of stock based compensation and the award of bonuses under our bonus plans; (10) to exclude costs incurred in connection with potential acquisitions or divestitures that are required to be expensed under GAAP; and (11) to exclude the goodwill and intangible asset impairment charges that are required to be recorded under GAAP. In addition, the our board of directors may establish or provide for other adjustment items in the award agreement at the time the award is granted or in such other document setting forth the performance goals at the time the performance goals are established.
Other Stock Awards. The plan administrator may grant other awards based in whole or in part by reference to Senti Common Shares. The plan administrator will set the number of shares under the stock award (or cash equivalent) and all other terms and conditions of such awards.
Changes to Capital Structure. In the event there is a specified type of change in our capital structure, such as a stock split, reverse stock split, or recapitalization, appropriate adjustments will be made to (1) the class and maximum number of shares reserved for issuance under the Incentive Plan, (2) the class of shares by which the share reserve may increase automatically each year, (3) the class and maximum number of shares that may be issued on the exercise of ISOs and (4) the class and number of shares and exercise price, strike price, or purchase price, if applicable, of all outstanding stock awards.
214
Corporate Transactions. The following applies to stock awards under the Incentive Plan in the event of a corporate transaction (as defined in the Incentive Plan), unless otherwise provided in a participant’s stock award agreement or other written agreement with us or one of its affiliates or unless otherwise expressly provided by the plan administrator at the time of grant.
In the event of a corporate transaction, any stock awards outstanding under the Incentive Plan may be assumed, continued or substituted for by any surviving or acquiring corporation (or its parent company), and any reacquisition or repurchase rights held by us with respect to the stock award may be assigned to our successor (or its parent company). If the surviving or acquiring corporation (or its parent company) does not assume, continue or substitute for such stock awards, then (i) with respect to any such stock awards that are held by participants whose continuous service has not terminated prior to the effective time of the corporate transaction, or current participants, the vesting (and exercisability, if applicable) of such stock awards will be accelerated in full (or, in the case of performance awards with multiple vesting levels depending on the level of performance, vesting will accelerate at 100% of the target level) to a date prior to the effective time of the corporate transaction (contingent upon the effectiveness of the corporate transaction), and such stock awards will terminate if not exercised (if applicable) at or prior to the effective time of the corporate transaction, and any reacquisition or repurchase rights held by us with respect to such stock awards will lapse (contingent upon the effectiveness of the corporate transaction), and (ii) any such stock awards that are held by persons other than current participants will terminate if not exercised (if applicable) prior to the effective time of the corporate transaction, except that any reacquisition or repurchase rights held by us with respect to such stock awards will not terminate and may continue to be exercised notwithstanding the corporate transaction.
In the event a stock award will terminate if not exercised prior to the effective time of a corporate transaction, the plan administrator may provide, in its sole discretion, that the holder of such stock award may not exercise such stock award but instead will receive a payment equal in value to the excess (if any) of (i) the per share amount payable to holders of Senti Common Shares in connection with the corporate transaction, over (ii) any per share exercise price payable by such holder, if applicable.
Plan Amendment or Termination. Our board of directors has the authority to amend, suspend, or terminate the Incentive Plan at any time, provided that such action does not materially impair the existing rights of any participant without such participant’s written consent. Certain material amendments also require approval of our stockholders. No ISOs may be granted after the tenth anniversary of the date the DYNS board of directors adopts the Incentive Plan. No stock awards may be granted under the Incentive Plan while it is suspended or after it is terminated.
U.S. Federal Income Tax Consequences
The following is a summary of the principal U.S. federal income tax consequences to participants and Senti with respect to participation in the Incentive Plan. This summary is not intended to be exhaustive and does not discuss the income tax laws of any local, state or foreign jurisdiction in which a participant may reside. The information is based upon current U.S. federal income tax rules and therefore is subject to change when those rules change. Because the tax consequences to any participant may depend on his or her particular situation, each participant should consult the participant’s tax adviser regarding the federal, state, local and other tax consequences of the grant or exercise of an award or the disposition of stock acquired under the Incentive Plan. The Incentive Plan is not qualified under the provisions of Section 401(a) of the Code and is not subject to any of the provisions of the Employee Retirement Income Security Act of 1974, as amended. Senti’s ability to realize the benefit of any tax deductions described below depends on Senti’s generation of taxable income as well as the requirement of reasonableness and the satisfaction of Senti’s tax reporting obligations.
Nonstatutory Stock Options. Generally, there is no taxation upon the grant of a NSO. Upon exercise, a participant will recognize ordinary income equal to the excess, if any, of the fair market value of the underlying stock on the date of exercise of the stock option over the exercise price. If the participant is employed by us or
215
one of our affiliates, that income will be subject to withholding taxes. The participant’s tax basis in those shares will be equal to their fair market value on the date of exercise of the stock option, and the participant’s capital gain holding period for those shares will begin on the day after they are transferred to the participant. Subject to the requirement of reasonableness, the deduction limits under Section 162(m) of the Code and the satisfaction of a tax reporting obligation, Senti will generally be entitled to a tax deduction equal to the taxable ordinary income realized by the participant.
Incentive Stock Options. The Incentive Plan provides for the grant of stock options that are intended to qualify as “incentive stock options,” as defined in Section 422 of the Code. Under the Code, a participant generally is not subject to ordinary income tax upon the grant or exercise of an ISO. If the participant holds a share received upon exercise of an ISO for more than two years from the date the stock option was granted and more than one year from the date the stock option was exercised, which is referred to as the required holding period, the difference, if any, between the amount realized on a sale or other taxable disposition of that share and the participant’s tax basis in that share will be long-term capital gain or loss. If, however, a participant disposes of a share acquired upon exercise of an ISO before the end of the required holding period, which is referred to as a disqualifying disposition, the participant generally will recognize ordinary income in the year of the disqualifying disposition equal to the excess, if any, of the fair market value of the share on the date of exercise of the stock option over the exercise price. However, if the sales proceeds are less than the fair market value of the share on the date of exercise of the stock option, the amount of ordinary income recognized by the participant will not exceed the gain, if any, realized on the sale. If the amount realized on a disqualifying disposition exceeds the fair market value of the share on the date of exercise of the stock option, that excess will be short-term or long-term capital gain, depending on whether the holding period for the share exceeds one year. For purposes of the alternative minimum tax, the amount by which the fair market value of a share of stock acquired upon exercise of an ISO exceeds the exercise price of the stock option generally will be an adjustment included in the participant’s alternative minimum taxable income for the year in which the stock option is exercised. If, however, there is a disqualifying disposition of the share in the year in which the stock option is exercised, there will be no adjustment for alternative minimum tax purposes with respect to that share. In computing alternative minimum taxable income, the tax basis of a share acquired upon exercise of an ISO is increased by the amount of the adjustment taken into account with respect to that share for alternative minimum tax purposes in the year the stock option is exercised. Senti is not allowed a tax deduction with respect to the grant or exercise of an ISO or the disposition of a share acquired upon exercise of an ISO after the required holding period. If there is a disqualifying disposition of a share, however, Senti will generally be entitled to a tax deduction equal to the taxable ordinary income realized by the participant, subject to the requirement of reasonableness, the deduction limits under Section 162(m) of the Code and provided that either the employee includes that amount in income or Senti timely satisfies its reporting requirements with respect to that amount.
Restricted Stock Awards. Generally, the recipient of a restricted stock award will recognize ordinary income at the time the stock is received equal to the excess, if any, of the fair market value of the stock received over any amount paid by the recipient in exchange for the stock. If, however, the stock is subject to restrictions constituting a substantial risk of forfeiture when it is received (for example, if the employee is required to work for a period of time in order to have the right to transfer or sell the stock), the recipient generally will not recognize income until the restrictions constituting a substantial risk of forfeiture lapse, at which time the recipient will recognize ordinary income equal to the excess, if any, of the fair market value of the stock on the date it becomes vested over any amount paid by the recipient in exchange for the stock. A recipient may, however, file an election with the IRS, within 30 days following the date of grant, to recognize ordinary income, as of the date of grant, equal to the excess, if any, of the fair market value of the stock on the date the award is granted over any amount paid by the recipient for the stock. The recipient’s basis for the determination of gain or loss upon the subsequent disposition of shares acquired from a restricted stock award will be the amount paid for such shares plus any ordinary income recognized either when the stock is received or when the restrictions constituting a substantial risk of forfeiture lapse. Subject to the requirement of reasonableness, the deduction limits under Section 162(m) of the Code and the satisfaction of a tax reporting obligation, Senti will generally be entitled to a tax deduction equal to the taxable ordinary income realized by the recipient of the restricted stock award.
216
Restricted Stock Unit Awards. Generally, the recipient of a restricted stock unit award will generally recognize ordinary income at the time the stock is delivered equal to the excess, if any, of (i) the fair market value of the stock received over any amount paid by the recipient in exchange for the stock or (ii) the amount of cash paid to the participant. The recipient’s basis for the determination of gain or loss upon the subsequent disposition of shares acquired from a restricted stock unit award will be the amount paid for such shares plus any ordinary income recognized when the stock is delivered, and the participant’s capital gain holding period for those shares will begin on the day after they are transferred to the participant. Subject to the requirement of reasonableness, the deduction limits under Section 162(m) of the Code and the satisfaction of a tax reporting obligation, Senti will generally be entitled to a tax deduction equal to the taxable ordinary income realized by the recipient of the restricted stock unit award.
Stock Appreciation Rights. Generally, the recipient of a stock appreciation right will recognize ordinary income equal to the fair market value of the stock or cash received upon exercise. Subject to the requirement of reasonableness, the deduction limits under Section 162(m) of the Code and the satisfaction of a tax reporting obligation, Senti will generally be entitled to a tax deduction equal to the taxable ordinary income realized by the recipient of the stock appreciation right.
Tax Consequences to Senti
Compensation of Covered Employees. The ability of Senti to obtain a deduction for amounts paid under the Incentive Plan could be limited by Section 162(m) of the Code. Section 162(m) of the Code limits Senti’s ability to deduct compensation, for U.S. federal income tax purposes, paid during any year to a “covered employee” (within the meaning of Section 162(m) of the Code) in excess of $1.0 million.
Golden Parachute Payments. The ability of Senti (or the ability of one of its subsidiaries) to obtain a deduction for future payments under the Incentive Plan could also be limited by the golden parachute rules of Section 280G of the Code, which prevent the deductibility of certain “excess parachute payments” made in connection with a change in control of an employer-corporation.
New Plan Benefits
No awards have been previously granted under the Incentive Plan and no awards have been granted that are contingent on stockholder approval of the Incentive Plan. The awards that are to be granted to any participant or group of participants are indeterminable at the date of this prospectus because participation and the types of awards that may be granted under the Incentive Plan are subject to the discretion of the plan administrator. Consequently, no new plan benefits table is included in this prospectus.
Senti Biosciences, Inc. 2022 Employee Stock Purchase Plan
Overview
On June 8, 2022, the Senti Biosciences, Inc. 2022 Employee Stock Purchase Plan (the “ESPP”) became effective. At the Special Meeting, the DYNS stockholders approved the ESPP, which was recommended to them for approval by the DYNS board of directors.
The purpose of the ESPP is to provide a means whereby we can align the long-term financial interests of our employees with the financial interests of our stockholders. In addition, the board of directors believes that the ability to allow our employees to purchase Senti Common Shares will help us to attract, retain, and motivate employees and encourages them to devote their best efforts to our business and financial success. The ESPP allows us to provide our employees with the opportunity to acquire an ownership interest in us through their participation in the ESPP, thereby encouraging them to remain in service and more closely aligning their interests with those of our stockholders.
217
Description of the ESPP
The material features of the ESPP are described below. The following description of the ESPP is a summary only. This summary is not a complete statement of the ESPP and is qualified in its entirety by reference to the complete text of the ESPP, a copy of which is attached as an exhibit to this prospectus. Stockholders should refer to the ESPP for more complete and detailed information about the terms and conditions of the ESPP.
Purpose. The purpose of the ESPP is to provide a means by which eligible employees of Senti and certain designated companies may be given an opportunity to purchase Senti Common Shares, to assist Senti in retaining the services of eligible employees, to secure and retain the services of new employees and to provide incentives for such persons to exert maximum efforts for our success.
Share Reserve. The maximum number of Senti Common Shares that may be issued under the ESPP is 592,584 shares. Additionally, the number of Senti Common Shares reserved for issuance under the ESPP will automatically increase on January 1st of each year, beginning on January 1, 2023 and continuing through and including January 1, 2032, by the lesser of 1% of the total number of Senti Common Shares on December 31st of the preceding calendar year or such lesser number of Senti Common Shares as determined by our board of directors. Shares subject to purchase rights granted under the ESPP that terminate without having been exercised in full will not reduce the number of shares available for issuance under the ESPP.
Administration. Our board of directors, or a duly authorized committee thereof, will administer the ESPP.
Limitations. Our employees and the employees of any of our designated affiliates, will be eligible to participate in the ESPP, provided they may have to satisfy one or more of the following service requirements before participating in the ESPP, as determined by the administrator: (1) customary employment with us or one of our affiliates for more than 20 hours per week and five or more months per calendar year or (2) continuous employment with us or one of our affiliates for a minimum period of time, not to exceed two years, prior to the first date of an offering. In addition, our board of directors may also exclude from participation in the ESPP or any offering, employees who are “highly compensated employees” (within the meaning of Section 423(b)(4)(D) of the Code) or a subset of such highly compensated employees. An employee may not be granted rights to purchase stock under the ESPP (a) if such employee immediately after the grant would own stock possessing 5% or more of the total combined voting power or value of all classes of our capital stock or (b) to the extent that such rights would accrue at a rate that exceeds $25,000 worth of our capital stock for each calendar year that the rights remain outstanding.
The ESPP is intended to qualify as an employee stock purchase plan under Section 423 of the Code. The administrator may specify offerings with a duration of not more than 27 months, and may specify one or more shorter purchase periods within each offering. Each offering will have one or more purchase dates on which shares of our common stock will be purchased for the employees who are participating in the offering. The administrator, in its discretion, will determine the terms of offerings under the ESPP. The administrator has the discretion to structure an offering so that if the fair market value of a share of our common stock on any purchase date during the offering period is less than or equal to the fair market value of a share of our common stock on the first day of the offering period, then that offering will terminate immediately, and the participants in such terminated offering will be automatically enrolled in a new offering that begins immediately after such purchase date.
A participant may not transfer purchase rights under the ESPP other than by will, the laws of descent and distribution, or as otherwise provided under the ESPP.
Payroll Deductions. The ESPP permits participants to purchase Senti Common Shares through payroll deductions. Unless otherwise determined by the administrator, the purchase price of the shares will be 85% of the lower of the fair market value of Senti Common Shares on the first day of an offering or on the date of purchase.
218
Withdrawal. Participants may withdraw from an offering by delivering a withdrawal form to us and terminating their contributions. Such withdrawal may be elected at any time prior to the end of an offering, except as otherwise provided by the plan administrator. Upon such withdrawal, we will distribute to the employee his or her accumulated but unused contributions without interest, and such employee’s right to participate in that offering will terminate. However, an employee’s withdrawal from an offering does not affect such employee’s eligibility to participate in any other offerings under the ESPP.
Termination of Employment. A participant’s rights under any offering under the ESPP will terminate immediately if the participant either (i) is no longer employed by us or any of our parent or subsidiary companies (subject to any post-employment participation period required by law) or (ii) is otherwise no longer eligible to participate. In such event, we will distribute to the participant his or her accumulated but unused contributions, without interest.
Corporate Transactions. In the event of certain specified significant corporate transactions, such as a merger or change in control, a successor corporation may assume, continue, or substitute each outstanding purchase right. If the successor corporation does not assume, continue, or substitute for the outstanding purchase rights, the offering in progress will be shortened and a new purchase date will be set. The participants’ purchase rights will be exercised on the new purchase date and such purchase rights will terminate immediately thereafter.
Amendment and Termination. Our board of directors has the authority to amend, suspend, or terminate the ESPP, at any time and for any reason, provided certain types of amendments will require the approval of our stockholders. Any benefits privileges, entitlements and obligations under any outstanding purchase rights granted before an amendment, suspension or termination of the ESPP will not be materially impaired by any such amendment, suspension or termination except (i) with the consent of the person to whom such purchase rights were granted, (ii) as necessary to facilitate compliance with any laws, listing requirements,or governmental regulations, or (iii) as necessary to obtain or maintain favorable tax, listing, or regulatory treatment. The ESPP will remain in effect until terminated by our board of directors in accordance with the terms of the ESPP.
U.S. Federal Income Tax Consequences
The following is a summary of the principal U.S. federal income tax consequences to participants and Senti with respect to participation in the ESPP. This summary is not intended to be exhaustive and does not discuss the income tax laws of any local, state or foreign jurisdiction in which a participant may reside. The information is based upon current U.S. federal income tax rules and therefore is subject to change when those rules change. Because the tax consequences to any participant may depend on his or her particular situation, each participant should consult the participant’s tax adviser regarding the federal, state, local, and other tax consequences of the grant or exercise of a purchase right or the sale or other disposition of Senti Common Shares acquired under the ESPP. The ESPP is not qualified under the provisions of Section 401(a) of the Code and is not subject to any of the provisions of the Employee Retirement Income Security Act of 1974, as amended.
Section 423 of the Code
Rights granted under the ESPP are intended to qualify for favorable U.S. federal income tax treatment associated with rights granted under an employee stock purchase plan which qualifies under the provisions of Section 423 of the Code.
A participant will be taxed on amounts withheld for the purchase of Senti Common Shares as if such amounts were actually received. Otherwise, no income will be taxable to a participant as a result of the granting or exercise of a purchase right until a sale or other disposition of the acquired shares. The taxation upon such sale or other disposition will depend upon the holding period of the acquired shares.
If the shares are sold or otherwise disposed of more than two years after the beginning of the offering period and more than one year after the shares are transferred to the participant, then the lesser of the following will be
219
treated as ordinary income: (i) the excess of the fair market value of the shares at the time of such sale or other disposition over the purchase price; or (ii) the excess of the fair market value of the shares as of the beginning of the offering period over the purchase price (determined as of the beginning of the offering period). Any further gain or any loss will be taxed as a long-term capital gain or loss.
If the shares are sold or otherwise disposed of before the expiration of either of the holding periods described above, then the excess of the fair market value of the shares on the purchase date over the purchase price will be treated as ordinary income at the time of such sale or other disposition. The balance of any gain will be treated as capital gain. Even if the shares are later sold or otherwise disposed of for less than their fair market value on the purchase date, the same amount of ordinary income is attributed to the participant, and a capital loss is recognized equal to the difference between the sales price and the fair market value of the shares on such purchase date. Any capital gain or loss will be short-term or long-term, depending on how long the shares have been held.
We are not allowed a deduction upon the grant or exercise of a purchase right or the disposition of a share acquired upon exercise of a purchase right after the required holding period. If the shares are sold or otherwise disposed of before the expiration of either holding period, we will generally be entitled to a tax deduction equal to the taxable ordinary income, realized by the participant.
New Plan Benefits
Participation in the ESPP is voluntary and each eligible employee will make his or her own decision regarding whether and to what extent to participate in the ESPP. Therefore, we cannot currently determine the benefits or number of shares subject to purchase rights and a new plan benefits table is thus not provided.
220
Non-Employee Director Compensation
During the year ended December 31, 2021, none of Senti’s non-employee directors, other than Ms. Berland who is not affiliated with any of our stockholders, earned compensation in connection with their service on our board of directors, except as described below. We have reimbursed and will continue to reimburse our non-employee directors for their reasonable out-of-pocket expenses incurred in connection with attending meetings of our board of directors or its committees.
2021 Director Compensation Table
The following table sets forth information regarding the compensation awarded to, earned by or paid to Senti’s non-employee directors for service on the Senti board of directors during the year ended December 31, 2021. Dr. Lu also served on the Senti board of directors, but did not receive any additional compensation for his service as a director and therefore is not included in the table below. The compensation for Dr. Lu, as a named executive officer, is set forth above under “Executive Compensation — Summary Compensation Table.”
Name | Fees Earned or Paid in Cash ($) | Option Awards(1)(2) ($) | All Other Compensation ($) | Total ($) | ||||||||||||
Susan Berland | 27,843 | 96,763 | — | 124,606 | ||||||||||||
Lee Cooper | — | — | — | — | ||||||||||||
Brenda Cooperstone, M.D. | — | — | — | — | ||||||||||||
Ran Geng | — | — | — | — | ||||||||||||
Alex Kolicich | — | — | — | — | ||||||||||||
Edward Mathers | — | — | — | — | ||||||||||||
| (1) | In accordance with SEC rules, this column reflects the aggregate grant date fair value of the option awards granted during fiscal year 2021 computed in accordance with ASC 718. Assumptions used in the calculation of these amounts are included in Note 9 to Senti’s consolidated financial statements included elsewhere in this prospectus. These amounts do not reflect the actual economic value that will be realized by our non-employee directors upon the vesting of the stock options, the exercise of the stock options or the sale of the common stock underlying such stock options. |
| (2) | The following table provides information regarding the number of shares of common stock underlying stock options granted to our non-employee directors that were outstanding as of December 31, 2021. |
Name | Option Awards Outstanding at Year-End (number of shares) | |||
Susan Berland | 90,000 | |||
Lee Cooper | — | |||
Brenda Cooperstone, M.D. | 160,645 | |||
Ran Geng | — | |||
Alex Kolicich | — | |||
Edward Mathers | — | |||
221
The following table sets forth information regarding the beneficial ownership of the Senti Common Shares as of June 8, 2022:
| • | each person known by Senti to be the beneficial owner of more than 5% of the Senti Common Shares; |
| • | each of Senti’s named executive officers and directors; and |
| • | all of Senti’s executive officers and directors as a group. |
Beneficial ownership is determined according to the rules of the SEC, which generally provide that a person has beneficial ownership of a security if he, she or it possesses sole or shared voting or investment power over that security, including options and restricted stock units that are currently exercisable or vested or that will become exercisable or vest within 60 days. Unless otherwise indicated, Senti believes that all persons named in the table below have sole voting and investment power with respect to the voting securities beneficially owned by them.
The beneficial ownership of the Senti Common Shares is based on 43,657,077 Senti Common Shares issued and outstanding as of the Closing Date.
Directors and Named Executive Officers: | Number of Shares of Common Stock | % | ||||||
Timothy Lu, M.D., Ph.D.(2) | 2,070,300 | 4.7 | % | |||||
Curt Herberts, M.B.S.(3) | 454,208 | 1.0 | % | |||||
Philip Lee, Ph. D.(4) | 936,424 | 2.1 | % | |||||
James J. (Jim) Collins(5) | 176,130 | * | ||||||
Omid Farokhzad(6)(7) | 1,947,403 | 4.5 | % | |||||
Brenda Cooperstone(8) | 21,613 | * | ||||||
Susan Berland(9) | 4,770 | * | ||||||
David Epstein | 123,252 | * | ||||||
Edward Mathers | — | * | ||||||
All executive officers and directors as a group (10 persons)(10) | 5,776,909 | 13.2 | % | |||||
Five Percent Holders: | Number of Shares of Common Stock | % | ||||||
Entities Affiliated with 8VC(11) | 2,537,558 | 5.8 | % | |||||
Entities Affiliated with NEA(12) | 4,429,725 | 10.1 | % | |||||
Bayer Healthcare LLC(13) | 5,878,488 | 13.5 | % | |||||
Accounts Advised or Sub Advised by T. Rowe Price Associates(14) | 3,916,551 | 9.0 | % | |||||
ARK Genomic Revolution EFT(15) | 2,410,394 | 5.5 | % | |||||
| * | Represents beneficial ownership of less than 1%. |
| (1) | Unless otherwise noted, the business address of each of the individuals and entities listed in the table above is c/o Senti Biosciences, Inc., 2 Corporate Drive, First Floor, South San Francisco, California 94080. |
| (2) | Consists of (i) 559,496 shares of Common Stock held directly by Dr. Lu, (ii) 528,390 shares of Common Stock held by Luminen Services, LLC, as trustee of the Luminen Trust, of which Dr. Lu is the settlor, (iii) 528,390 shares of Common Stock held by Dr. Lu’s wife, Sandy Shan Wang, and (iv) 454,024 shares of Common Stock issuable upon exercise of stock options held by Dr. Lu that are exercisable within 60 days of June 8, 2022. |
| (3) | Consists of 454,208 shares of Common Stock held by the C. and E. Herberts Revocable Trust dated July 17, 2013, over which Mr. Herberts and his wife share voting and investment power as trustees. |
222
| (4) | Consists of 936,424 shares of Common Stock held directly by Dr. Lee. |
| (5) | Consists of 176,130 shares of Common Stock held directly by Dr. Collins. |
| (6) | This reflects Omid Farokhzad’s ownership interests following the distribution of shares by Dynamics Sponsor LLC to its members upon Closing. |
| (7) | Omid Farokhzad’s beneficial ownership interest in the Sponsor was held indirectly through Dynamics Group, LLC. Mr. Farokhzad controls and is the sole member of Dynamics Group, LLC. |
| (8) | Consists of 21,613 shares of Common Stock issuable upon exercise of stock options held by Ms. Cooperstone that are exercisable within 60 days of June 8, 2022. |
| (9) | Consists of 4,770 shares of Common Stock issuable upon exercise of stock options held by Susan Berland that are exercisable within 60 days of June 8, 2022. |
| (10) | Consists of shares beneficially owned by the named executive officers and directors listed in the table above and 42,809 shares of Common Stock issuable upon exercise of stock options held by Deborah Knobelman that are exercisable within 60 days of June 8, 2022. Does not include any holdings of Kanya Rajangam, who joined Senti as an executive officer in July 2022 and does not beneficially own any shares of Common Stock. |
| (11) | Consists of (i) 2,498,277 shares of Common Stock held by 8VC Fund I, L.P. (“8VC”); and (ii) 39,281 shares of Common Stock held by 8VC Entrepreneurs Fund I, L.P. (“8VC Entrepreneurs” and, collectively with 8VC, the “8VC Entities”). 8VC GP I, LLC (“8VC GP I”), as general partner of each of the 8VC Entities, has sole voting and dispositive power with respect to the securities held by the 8VC Entities. Joe Lonsdale, in his capacity as the managing member of 8VC GP I, has sole voting and dispositive power with respect to the shares held by the 8VC Entities. Mr. Lonsdale and 8VC GP I disclaim beneficial ownership of the shares held by the 8VC Entities. The address of each of the 8VC Entities is 907 South Congress Avenue, Austin, Texas 78704. |
| (12) | Consists of (i) 4,426,151 shares of Common Stock held by New Enterprise Associates 15, L.P. (“NEA 15”); and (ii) 3,574 shares of Common Stock held by NEA Ventures 2018, L.P. (“Ven 2018”). The securities directly held by NEA 15 are indirectly held by NEA Partners 15, L.P. (“NEA Partners 15”), which is the sole general partner of NEA 15, NEA 15 GP, LLC (“NEA 15 LLC”), which is the sole general partner of NEA Partners 15, and each of the individual managers of NEA 15 LLC. The individual managers of NEA 15 LLC (collectively the “NEA 15 Managers”) are Forest Baskett, Anthony A. Florence, Mohamad Makhzoumi, Scott D. Sandell and Peter Sonsini. NEA 15, NEA Partners 15, NEA 15 LLC and the NEA 15 Managers share voting and dispositive power with regard to the shares directly held by NEA 15. The securities directly held by Ven 2018 are indirectly held by Karen P. Welsh, the general partner of Ven 2018. Mr. Edward Mathers, a member of the board of directors of the Combined Company, is a partner at New Enterprise Associates, Inc., which is affiliated with NEA 15 and Ven 2018, but does not have voting or investment power over the shares held by NEA 15 or Ven 2018. All indirect holders of the above referenced shares disclaim beneficial ownership of all applicable shares of Common Stock. The address for these entities and individuals is 1954 Greenspring Drive, Suite 600, Timonium, Maryland 21093. |
| (13) | Consists of 5,878,488 shares of Common Stock held by Bayer HealthCare LLC (“Bayer”). Bayer is an indirect wholly-owned subsidiary of Bayer AG, which may be deemed to be an indirect beneficial owner of the shares owned directly by Bayer. Kelly Gast, President of Bayer, and Brian Branca, Treasurer of Bayer, share voting and dispositive power over the shares held by Bayer. The address of Bayer is 100 Bayer Boulevard, Whippany, New Jersey 07981. |
| (14) | Consists of (i) 1,688,908 shares of common stock held by T. Rowe Price Health Sciences Fund, Inc., (ii) 75,977 shares of common stock held by T. Rowe Price Health Sciences Portfolio, (iii) 1,626,003 shares held by T. Rowe Price New Horizons Fund, Inc., (iv) 200,916 shares held by T. Rowe Price New Horizons Fund Trust, (v) 9,952 shares held by T. Rowe Price U.S. Equities Trust, (vi) 144,636 shares of common stock held by TD Mutual Funds—TD Health Sciences Fund, (vii) 1,761 shares of common stock held by Saint-Gobain Corporation, (viii) 38,709 shares of common stock held by New York City Deferred Compensation Plan, (ix) 16,675 shares of common stock held by Dow Retirement Group Trust, (x) 5,739 shares of common stock held by Master Trust Agreement Between Pfizer Inc. & The Northern Trust Company, (xi) 6,130 shares of common stock held by Bank of America Pension Plan, (xii) 6,069 shares of common stock held by MassMutual Select Funds - MassMutual Select T. Rowe Price Small and Mid Cap |
223
| Blend Fund, (xiii) 31,062 shares of common stock held by Johnson & Johnson Pension and Savings Plans Master Trust, (xiv) 13,193 shares of common stock held by EQ Advisors Trust – EQ/T. Rowe Health Sciences Portfolio, (xv) 2,934 shares of common stock held by Swarthmore College, (xvi) 18,789 shares of common stock held by John Hancock Variable Insurance Trust – Health Sciences Trust, (xvii) 26,772 shares of common stock held by John Hancock Funds II – Health Sciences Fund, and (xviii) 2,326 shares of common stock held by Johnson and Johnson Pension and Savings Plan Master Trust. T. Rowe Price Associates, Inc. (“TRPA”) serves as investment adviser or subadviser with power to direct investments and/or sole power to vote the securities. For purposes of reporting requirements of the Securities Exchange Act of 1934, TRPA may be deemed to be the beneficial owner of all of these shares; however, TRPA expressly disclaims that it is, in fact, the beneficial owner of such securities. TRPA is the wholly owned subsidiary of T. Rowe Price Group, Inc., which is a publicly traded financial services holding company. The address of each of these entities is 100 East Pratt Street, Baltimore, MD 21202. |
| (15) | The address of this entity is 200 Central Avenue, Suite 1850, Saint Petersburg, FL 33701. |
224
This prospectus relates to the possible offer and resale by the Selling Securityholders of up to 35,444,908 Senti Common Shares, consisting of up to (i) 15,168,616 Senti Common Shares originally issued to certain of our affiliates as consideration in connection with the Business Combination at a per share value of $10.00 per share, (ii) up to 6,233,292 Senti Common Shares issuable upon the exercise of stock options at exercise prices ranging from $2.66 to $9.92 per share, issued to certain of our affiliates upon the conversion of stock options in Senti Sub I, Inc. (formerly Senti Biosciences, Inc.) in connection with the Business Combination, (iii) 4,878,972 Senti Common Shares distributed by Sponsor to certain of its members who were affiliates of DYNS prior to the completion of the Business Combination, which shares were originally issued to Sponsor at a price per share of $0.004, (iv) 715,500 Senti Common Shares distributed by Sponsor to certain of its members who were affiliates of DYNS prior to the completion of the Business Combination, which shares were originally issued to Sponsor at a price per share of $10.00 in a private placement transaction completed concurrently with the initial public offering of DYNS, (v) 871,028 Senti Common Shares issued to the Anchor Investors in consideration for their agreement not to redeem their shares of Class A Common Stock of DYNS in connection with the Business Combination, (vi) 5,060,000 PIPE Shares originally purchased at a purchase price of $10.00 per share at the closing of the Business Combination and (vii) 517,500 Senti Common Shares issued to Bayer Healthcare LLC at an effective exchange price of $10.00 per share at the closing of the Business Combination upon the cancellation and exchange of the Convertible Note. Sales of the foregoing Senti Common Shares, which comprise a significant portion of our public float, by the Selling Securityholders, or the perception that such sales may occur, could have a significant negative impact on the trading price of our common stock.
The Selling Securityholders may from time to time offer and sell any or all of the Senti Common Shares set forth below pursuant to this prospectus. When we refer to the “Selling Securityholders” in this prospectus, we mean the persons listed in the table below, and the pledgees, donees, transferees, assignees, successors and others who later come to hold any of the Selling Securityholders’ interest in the Senti Common Shares after the date of this prospectus such that registration rights shall apply to those securities.
The following table is prepared based on information provided to us by the Selling Securityholders. It sets forth the name and address of the Selling Securityholders, the aggregate number of Senti Common Shares that the Selling Securityholders may offer pursuant to this prospectus, and the beneficial ownership of the Selling Securityholders both before and after the offering. We have based percentage ownership after this offering on 43,657,077 shares of common stock outstanding as of the Closing Date.
We cannot advise you as to whether the Selling Securityholders will in fact sell any or all of such Senti Common Shares. In addition, the Selling Securityholders may sell, transfer or otherwise dispose of, at any time and from time to time, the Senti Common Shares in transactions exempt from the registration requirements of the Securities Act after the date of this prospectus. For purposes of this table, we have assumed that the Selling Securityholders will have sold all of the securities covered by this prospectus upon the completion of the offering. Any changed or new information given to us by the Selling Securityholders, including regarding the identity of, and the securities held by, each Selling Securityholder, will be set forth in a prospectus supplement or amendments to the registration statement of which this prospectus is a part, if and when necessary.
Please see the section entitled “Plan of Distribution” for further information regarding the Selling Securityholders’ method of distributing these securities. For information regarding transactions between us and the Selling Securityholders, see the section entitled “Certain Relationships and Related Person Transactions.”
Unless otherwise indicated below, the address of each Selling Securityholder listed in the tables below is c/o Senti Biosciences, Inc., 2 Corporate Drive, First Floor South San Francisco, CA 94080.
225
| Common Stock Beneficially Owned Prior to this Offering | Common Stock to be Sold in this Offering | Common Stock Owned After this Offering | Percent | |||||||||||||
Name of Selling Securityholder | ||||||||||||||||
Entities Affiliated with 8VC(1) | 2,537,558 | 2,537,558 | — | — | ||||||||||||
Alexandria Venture Investments, LLC(2) | 338,263 | 100,000 | 238,263 | * | ||||||||||||
Amgen Ventures LLC(3) | 923,032 | 500,000 | 423,032 | * | ||||||||||||
Mark Afrasiabi(4) | 998,672 | 998,672 | — | — | ||||||||||||
Bayer Healthcare LLC(5) | 5,878,488 | 5,878,488 | — | — | ||||||||||||
Susan Berland(6) | 17,613 | 17,613 | — | — | ||||||||||||
Caspian Capital LLC(7) | 100,000 | 100,000 | — | — | ||||||||||||
Rowan Chapman(8) | 256,238 | 256,238 | — | — | ||||||||||||
James J. Collins(9) | 179,652 | 179,652 | ||||||||||||||
Brenda Cooperstone(10) | 31,438 | 31,438 | — | — | ||||||||||||
Dynamics Group LLC(11) | 1,947,403 | 1,947,403 | — | — | ||||||||||||
David Epstein | 123,252 | 123,252 | — | — | ||||||||||||
Jay Flatley(12) | 123,252 | 123,252 | — | — | ||||||||||||
GPK Group, Inc.(13) | 300,000 | 300,000 | — | — | ||||||||||||
Green Sands Fund Z, LLC(14) | 100,000 | 100,000 | — | — | ||||||||||||
Curt A. Herberts IIII(15) | 1,747,070 | 1,747,070 | — | — | ||||||||||||
Invus Public Equities, L.P.(16) | 1,055,555 | 555,555 | 500,000 | 1.15 | % | |||||||||||
KB Securities Co., Ltd.(17) | 40,000 | 40,000 | — | — | ||||||||||||
Deborah Knobelman(18) | 1,094,483 | 1,094,483 | — | — | ||||||||||||
Robert Langer(19) | 75,000 | 75,000 | — | — | ||||||||||||
Philip J. Lee(20) | 2,087,924 | 2,087,924 | — | — | ||||||||||||
LifeSci Venture Partners II, LP(21) | 293,327 | 50,000 | 243,327 | * | ||||||||||||
Timothy Lu(22) | 4,574,128 | 4,574,128 | — | — | ||||||||||||
Lux Ventures IV, L.P.(23) | 828,454 | 10,000 | 818,454 | 1.87 | % | |||||||||||
Matrix Partners China VI Hong Kong | 1,251,329 | 1,251,329 | — | — | ||||||||||||
Entities Affiliated with Morgan Stanley Investment Management(25) | 1,183,941 | 349,858 | 834,083 | 1.91 | % | |||||||||||
Entities Affiliated with NEA(26) | 4,429,725 | 4,429,725 | — | — | ||||||||||||
Dipchand (Deep) Nishar(27) | 123,252 | 123,252 | — | — | ||||||||||||
OCF 2014 Trust(28) | 250,000 | 250,000 | — | — | ||||||||||||
Parker Institute for Cancer | 250,000 | 250,000 | — | — | ||||||||||||
Mostafa Ronaghi(30) | 2,197,403 | 2,197,403 | — | — | ||||||||||||
Accounts Advised or Sub Advised by T. Rowe Price Associates(31) | 3,916,551 | 922,144 | 2,994,407 | 6.86 | % | |||||||||||
ARK Genomic Revolution ETF(32) | 2,410,394 | 243,471 | 2,166,923 | 4.96 | % | |||||||||||
| * | Indicates beneficial ownership less than 1%. |
| (1) | Consists of (i) 2,498,277 shares of common stock held by 8VC Fund I, L.P. (“8VC”) and (ii) 39,281 shares of common stock held by 8VC Entrepreneurs Fund I, L.P. (“8VC Entrepreneurs” and, collectively with 8VC, the “8VC Entities”). 8VC GP I, LLC (“8VC GP I”), as general partner of each of the 8VC Entities, has sole voting and dispositive power with respect to the securities held by the 8VC Entities. Joe Lonsdale, in his capacity as the managing member of 8VC GP I, has sole voting and dispositive power with respect to the shares held by the 8VC Entities. Mr. Lonsdale and 8VC GP I disclaim beneficial ownership of the shares held by the 8VC Entities. The address of each of the 8VC Entities is 907 South Congress Avenue, Austin, Texas 78704. |
| (2) | The address for this entity is 26 North Euclid Avenue, Pasadena, CA 91101. |
226
| (3) | Amgen Ventures LLC is a wholly-owned subsidiary of Amgen Inc. The address for these entities is One Amgen Center Drive, Thousand Oaks, CA 91320. |
| (4) | The address for this individual is 711 El Medio Avenue, Pacific Palisades, CA 90272. |
| (5) | Consists of 5,878,488 shares of common stock held by Bayer HealthCare LLC (“Bayer”). Bayer is an indirect wholly-owned subsidiary of Bayer AG, which may be deemed to be an indirect beneficial owner of the shares owned directly by Bayer. Kelly Gast, President of Bayer, and Brian Branca, Treasurer of Bayer, share voting and dispositive power over the shares held by Bayer. The address of Bayer is 100 Bayer Boulevard, Whippany, New Jersey 07981. |
| (6) | Consists of 17,613 shares of common stock issuable upon the exercise of stock options. |
| (7) | Jeffrey Huber and Angel Vossough Modarres exercise voting and dispositive power over these shares. The address for these individuals and this entity is 930 Tahoe Boulevard, Suite 802, #812, Incline Village, NV 89451. |
| (8) | The address for this individual is 2875 El Camino Real, Redwood City, CA 94061. |
| (9) | Consists of 176,130 shares of common stock held directly and 3,522 shares of common stock issuable upon the exercise of stock options. |
| (10) | Consists of 31,438 shares of common stock issuable upon the exercise of stock options. |
| (11) | Omid Farokhzad exercises voting and dispositive power over these shares. The address for this individual and this entity is 125 Yarmouth Road, Chestnut Hill, MA 02467. |
| (12) | The address for this individual is 6725 Calle Ponte Bella, Rancho Santa Fe, CA 92091. |
| (13) | S. Peter Lee exercises voting and dispositive power over these shares. The address for this individual and this entity is 17900 Ridgeway Road, Granada Hills, CA 91344. |
| (14) | Reema Khan exercises voting and dispositive power over these shares. The address for this individual and this entity is 548 Palmer Lange, Menlo Park, CA 94025. |
| (15) | Consists of 454,208 shares of common stock held by the C. and E. Herberts Revocable Trust dated July 17, 2013, over which Curt A. Herberts III and his spouse share voting and investment power as trustee, and 1,292,862 shares of common stock issuable upon the exercise of stock options. |
| (16) | Invus Public Equities, L.P. (“Invus PE”) directly holds 1,055,555 shares of common stock. Invus Public Equities Advisors, LLC (“Invus PE Advisors”) controls Invus PE, as its general partner and accordingly, may be deemed to beneficially own the shares held by Invus PE. The Geneva branch of Artal International S.C.A. (“Artal International”) controls Invus PE Advisors, as its managing member and accordingly, may be deemed to beneficially own the shares held by Invus PE. Artal International Management S.A. (“Artal International Management”) as the managing partner of Artal International, controls Artal International and accordingly, may be deemed to beneficially own shares that Artal International may be deemed to beneficially own. Artal Group S.A., as the sole stockholder of Artal International Management, controls Artal International Management and accordingly, may be deemed to beneficially own the Shares that Artal International Management may be deemed to beneficially own. Westend S.A. (“Westend”), as the parent company of Artal Group S.A.(“Artal Group”) controls Artal Group and accordingly, may be deemed to beneficially own the shares that Artal Group may be deemed to beneficially own. Stichting Administratiekantoor Westend (the “Stichting”), as majority shareholder of Westend controls Westend and accordingly, may be deemed to beneficially own the shares that Westend may be deemed to beneficially own. As of June 8, 2022 , Mr. Amaury Wittouck, as the sole member of the board of the Stichting, controls the Stichting and accordingly, may be deemed to beneficially own the shares that the Stichting may be deemed to beneficially own. The address for Invus PE and Invus PE Advisors is 750 Lexington Avenue, 30th Floor, New York, NY 10022. The address for Artal International, Artal International Management, Artal Group, Stichting and Mr. Amaury Wittouck is Valley Park, 44, Rue de la Vallée, L-2661, Luxembourg. |
| (17) | Consists of (i) 20,000 shares of common stock held by KB Securities Co., Ltd. not in its corporate capacity but solely in its capacity as trustee on behalf of Smilegate Bamboo Fund 2 and (ii) 20,000 shares of common stock held by KB Securities Co., Ltd. not in its corporate capacity but solely in its capacity as trustee on behalf of Smilegate Bamboo Shoot Fund. The address for these entities is 50, Yeouinaru-ro, Yeongdeungpo-gu, Seoul 07328, Korea. |
| (18) | Consists of 1,094,483 shares of common stock issuable upon the exercise of stock options. |
| (19) | The address for this individual is 98 Montvale Road, Newton, MA 02459. |
227
| (20) | Consists of 936,424 shares of common stock held directly and 1,151,500 shares of common stock issuable upon the exercise of stock options. |
| (21) | Paul Yook, as managing member of LifeSci Venture Partners II, LP exercises voting and dispositive power over the shares. The address for this entity and individual is 250 West 55th Street, Suite 3401, New York, NY 10019. |
| (22) | Consists of (i) 559,496 shares of common stock held directly, (ii) 528,390 shares of common stock held by the individual’s spouse, (iii) 528,390 shares of common stock held by Luminen Services, LLC, as trustee of the Luminen Trust, of which Timothy Lu is the settlor (and over which Dr. Lu disclaims beneficial ownership of, except to the extent of his pecuniary interest therein), and (iv) 2,957,852 shares of common stock issuable upon the exercise of stock options. |
| (23) | Lux Venture Partners IV, LLC (“LVP4”) is the general partner of Lux Ventures IV, L.P. (“LV4”) and exercises voting and dispositive power over the shares held by LV4. Peter James Hebert (“PH”) and Joshua Howard Wolfe (“JW”) are the sole managing members of LVP4 and may be deemed to share voting and dispositive power over the shares held by LV4. PH and JW disclaim beneficial ownership of the shares held by LV4 except to the extent of their pecuniary interests therein. The address for these entities and individuals is 920 Broadway, 11th Floor, New York, NY, 10010. |
| (24) | Matrix Partners China VI Hong Kong Limited is owned by Matrix Partners China VI, L.P. (“MPCVI”) and Matrix Partners China VI-A, L.P. (“MPCVI-A”). The general partner of MPCVI and MPCVI-A is Matrix China Management VI, L.P. (“MCM”). The general partner of MCM is Matrix China VI GP GP, Ltd. (“MCVI”). Timothy A. Barrows, David Ying Zhang, David Su and Harry Ho Kee Man are directors of MCVI and are deemed to have shared investment voting power over the shares held by MPCVI and MPCVI-A. The address of these entities is Flat 2807, 28/F, AIA Central, No.1 Connaught Road, Central, Hong Kong. The address of Timothy A. Barrows is 101 Main St., 17th Floor, Cambridge, MA 02142. The address of David Ying Zhang, Harry Ho Kee Man and David Su is c/o Matrix China Advisors, Suite 2601, Taikang Financial Tower, No. 38, East 3rd Ring Road North, Chaoyang District, Beijing, 100026, China. |
| (25) | Consists of (i) 697,602 shares of common stock held by Morgan Stanley Institutional Fund, Inc. — Inception Portfolio, (ii) 329,210 shares of common stock held by Inception Trust, (iii) 1,414 shares of common stock held by Morgan Stanley Institutional Fund, Inc. — Counterpoint Global Portfolio, (iv) 744 shares of common stock held by Morgan Stanley Investment Fund — Counterpoint Global Fund and (v) 154,971 shares of common stock held by EQ Advisors Trust — EQ/Morgan Stanley. The address for these entities is 522 Fifth Avenue, New York, NY 10036. |
| (26) | Consists of (i) 4,426,151 shares of common stock held by New Enterprise Associates 15, L.P. (“NEA 15”) and (ii) 3,574 shares of common stock held by NEA Ventures 2018, L.P. (“Ven 2018”). The securities directly held by NEA 15 are indirectly held by NEA Partners 15, L.P. (“NEA Partners 15”), which is the sole general partner of NEA 15, NEA 15 GP, LLC (“NEA 15 LLC”), which is the sole general partner of NEA Partners 15, and each of the individual managers of NEA 15 LLC. The individual managers of NEA 15 LLC (collectively the “NEA 15 Managers”) are Forest Baskett, Anthony A. Florence, Mohamad Makhzoumi, Scott D. Sandell and Peter Sonsini. NEA 15, NEA Partners 15, NEA 15 LLC and the NEA 15 Managers share voting and dispositive power with regard to the shares directly held by NEA 15. The securities directly held by Ven 2018 are indirectly held by Karen P. Welsh, the general partner of Ven 2018. Mr. Edward Mathers, a member of the board of directors of the Combined Company, is a partner at New Enterprise Associates, Inc., which is affiliated with NEA 15 and Ven 2018, but does not have voting or investment power over the shares held by NEA 15 or Ven 2018. All indirect holders of the above referenced shares disclaim beneficial ownership of all applicable shares of Common Stock. The address for these entities and individuals is 1954 Greenspring Drive, Suite 600, Timonium, Maryland 21093. |
| (27) | The address for this individual is c/o ICONIQ Capital, 394 Pacific Avenue, 2nd Floor, San Francisco, CA 94111. |
| (28) | Leela Ghaffari is the investment advisor with respect to these shares of common stock, with an address of 15 Central Park West #37A, New York, NY 10023. The address of OCF 2014 Trust is 500 Stanton Christiana Road, Newark, DE 19713. |
| (29) | The address for this entity is 1 Letterman Drive, D3500, San Francisco, CA 94129. |
228
| (30) | Consists of 1,947,403 shares of common stock held by Mostafa Ronaghi and 250,000 shares held by Ronaghi Revocable Trust. The address for these stockholders is 95 Stern Lange, Atherton, CA 94027. |
| (31) | Consists of (i) 1,688,908 shares of common stock held by T. Rowe Price Health Sciences Fund, Inc., (ii) 75,977 shares of common stock held by T. Rowe Price Health Sciences Portfolio, (iii) 1,626,003 shares held by T. Rowe Price New Horizons Fund, Inc., (iv) 200,916 shares held by T. Rowe Price New Horizons Fund Trust, (v) 9,952 shares held by T. Rowe Price U.S. Equities Trust, (vi) 144,636 shares of common stock held by TD Mutual Funds—TD Health Sciences Fund, (vii) 1,761 shares of common stock held by Saint-Gobain Corporation, (viii) 38,709 shares of common stock held by New York City Deferred Compensation Plan, (ix) 16,675 shares of common stock held by Dow Retirement Group Trust, (x) 5,739 shares of common stock held by Master Trust Agreement Between Pfizer Inc. & The Northern Trust Company, (xi) 6,130 shares of common stock held by Bank of America Pension Plan, (xii) 6,069 shares of common stock held by MassMutual Select Funds — MassMutual Select T. Rowe Price Small and Mid Cap Blend Fund, (xiii) 31,062 shares of common stock held by Johnson & Johnson Pension and Savings Plans Master Trust, (xiv) 13,193 shares of common stock held by EQ Advisors Trust — EQ/T. Rowe Health Sciences Portfolio, (xv) 2,934 shares of common stock held by Swarthmore College, (xvi) 18,789 shares of common stock held by John Hancock Variable Insurance Trust — Health Sciences Trust, (xvii) 26,772 shares of common stock held by John Hancock Funds II — Health Sciences Fund, and (xviii) 2,326 shares of common stock held by Johnson and Johnson Pension and Savings Plan Master Trust. T. Rowe Price Associates, Inc. (“TRPA”) serves as investment adviser or subadviser with power to direct investments and/or sole power to vote the securities. For purposes of reporting requirements of the Securities Exchange Act of 1934, TRPA may be deemed to be the beneficial owner of all of these shares; however, TRPA expressly disclaims that it is, in fact, the beneficial owner of such securities. TRPA is the wholly owned subsidiary of T. Rowe Price Group, Inc., which is a publicly traded financial services holding company. The address of each of these entities is 100 East Pratt Street, Baltimore, MD 21202. |
| (32) | The address of this entity is 200 Central Avenue, Suite 1850, Saint Petersburg, FL 33701. |
229
CERTAIN RELATIONSHIPS AND RELATED PARTY TRANSACTIONS
Senti Related Party Transactions
Convertible Note Exchange
On the closing of the Business Combination, an unsecured convertible promissory note (the “Note”) in the aggregate principal amount of $5,175,000 that was previously issued by Senti to Bayer Healthcare LLC (“Bayer”) for a purchase price of $5,175,000 on May 19, 2022 was automatically cancelled and exchanged for 517,500 shares of DYNS Class A Common Stock (the “Convertible Note Exchange”). All interest accrued on the Note was cancelled as part of the Convertible Note Exchange. The shares of DYNS Class A Common Stock issued in the Convertible Note Exchange are entitled to the same registration rights granted to the PIPE Investors with respect to the PIPE Shares.
Mr. Cooper, a former member of Senti’s board of directors, is employed as a Director of Venture Investments with Leaps by Bayer, an investment arm of Bayer AG, which is an affiliate of Bayer Healthcare LLC.
PIPE Investment
In connection with the Business Combination, DYNS entered into subscription agreements with the PIPE Investors, pursuant to which the PIPE Investors agreed to purchase, and DYNS agreed to sell to the PIPE Investors, an aggregate of 6,680,000 shares of DYNS Class A Common Stock, for a purchase price of $10.00 per share and an aggregate purchase price of $66.8 million, in the PIPE Investment.
The table below sets forth the number of shares of DYNS Class A Common Stock purchased by Senti’s related parties:
Related Person | Shares of DYNS Class A Common Stock | Cash Purchase Price | ||||||
S. Peter Lee(1) | 300,000 | $ | 3,000,000 | |||||
New Enterprise Associates 15, L.P.(2) | 1,250,000 | $ | 12,500,000 | |||||
Entities Affiliated with 8VC(3) | 600,000 | $ | 6,000,000 | |||||
Matrix Partners China VI Hong Kong Limited(4) | 60,000 | $ | 600,000 | |||||
| (1) | S. Peter Lee is the father of Philip Lee, Ph.D., Senti’s Chief Technology Officer. |
| (2) | Mr. Mathers, a member of Senti’s board of directors, is employed as a Partner at New Enterprise Associates, Inc., which is affiliated with New Enterprise Associates 15, L.P. |
| (3) | Mr. Kolicich, a former member of Senti’s board of directors, is employed as a Partner of Eight Partners VC, LLC, which is an affiliate of 8VC Fund I L.P., or 8VC, and 8VC Entrepreneurs Fund I, L.P., or 8VC Entrepreneurs. |
| (4) | Ms. Geng, is a former member of Senti’s board of directors and was a former Vice President of Matrix Partners China, which is an affiliate of Matrix Partners China VI Hong Kong Limited. |
Preferred Stock Financings
Series A Redeemable Convertible Preferred Stock Financing
In February 2018 and January 2019, Senti issued and sold to investors in a private placement an aggregate of 35,199,610 shares of its Series A redeemable convertible preferred stock at a purchase price of $1.6427 per share for an aggregate purchase price of approximately $53.4 million, through the payment of cash proceeds and the conversion of convertible promissory notes issued in 2016 and the interest accrued thereon. Each share of Series A redeemable convertible preferred stock automatically converted into one share of our common stock upon closing of the Business Combination.
230
The following table summarizes the Series A redeemable convertible preferred stock purchased by holders of more than 5% of Senti’s capital stock, Senti’s directors, executive officers and entities affiliated with Senti’s executive officers and directors in February 2018 and January 2019.
Participants | Series A Redeemable Convertible Preferred Stock Purchased for Cash | Series A Redeemable Convertible Preferred Stock Issued upon Conversion of Promissory Notes | Total Series A Redeemable Convertible Preferred Stock Purchased | Total Purchase Price | ||||||||||||
Timothy Lu(1) | — | 158,950 | 158,950 | $ | 129,941.92 | |||||||||||
Entities affiliated with NEA(2) | 12,168,990 | 1,336,045 | 13,505,035 | $ | 21,082,219.07 | |||||||||||
Entities affiliated with 8VC(3) | 8,370,366 | — | 8,370,366 | $ | 13,750,000.25 | |||||||||||
| (1) | Dr. Lu is Senti’s Chief Executive Officer and President and a member of Senti’s board of directors. |
| (2) | Mr. Mathers, a member of Senti’s board of directors, is employed as a Partner at New Enterprise Associates, Inc., which is affiliated with New Enterprise Associates 15, L.P., or NEA 15, and NEA Ventures 2018, L.P., or Ven 2018. |
| (3) | Mr. Kolicich, a former member of Senti’s board of directors, is employed as a Partner of Eight Partners VC, LLC, which is an affiliate of 8VC Fund I L.P., or 8VC, and 8VC Entrepreneurs Fund I, L.P., or 8VC Entrepreneurs. |
2020 Convertible Note Financing
In August 2020, Senti issued convertible promissory notes in the aggregate principal amount of $8.0 million, which are referred to as the 2020 Notes. The 2020 Notes accrued interest at the rate of 8% per annum. In October 2020, all of the 2020 Notes converted into 5,485,858 shares of Series B redeemable convertible preferred stock in connection with the issuance of Series B redeemable convertible preferred stock.
The following table summarizes the aggregate principal amount of 2020 Notes issued to holders of more than 5% of Senti’s capital stock, Senti’s directors, executive officers and entities affiliated with Senti’s executive officers and directors.
Noteholders | Aggregate Principal Amount | |||
Entities affiliated with NEA(1) | $ | 5,000,000.00 | ||
Entities affiliated with 8VC(2) | $ | 2,231,640.00 | ||
| (1) | Mr. Mathers, a member of Senti’s board of directors, is employed as a Partner at New Enterprise Associates, Inc., which is affiliated with NEA 15 and Ven 2018. |
| (2) | Mr. Kolicich, a former member of Senti’s board of directors, is employed as a Partner of Eight Partners VC, LLC, which is an affiliate of 8VC and 8VC Entrepreneurs. |
Series B Redeemable Convertible Preferred Stock Financing
Between October 2020 and May 2021, Senti issued and sold to investors in a private placement an aggregate of 64,534,933 shares of its Series B redeemable convertible preferred stock at a purchase price of $1.6427 per share for an aggregate purchase price of approximately $105.1 million, through the payment of cash proceeds and the conversion of the 2020 Notes and the interest accrued thereon. Each share of Series B redeemable convertible preferred stock automatically converted into one share of our common stock upon the closing of the Business Combination.
231
The following table summarizes the Series B redeemable convertible preferred stock purchased by holders of more than 5% of Senti’s capital stock, Senti’s directors, executive officers and entities affiliated with Senti’s executive officers and directors.
Participants | Series B Redeemable Convertible Preferred Stock Purchased for Cash | Series B Redeemable Convertible Preferred Stock Issued Upon Conversion of 2020 Notes | Total Series B Redeemable Convertible Preferred Stock Purchased | Total Purchase Price | ||||||||||||
Bayer Healthcare LLC(1) | 27,393,924 | — | 27,393,924 | $ | 44,999,998.98 | |||||||||||
Entities affiliated with NEA(2) | — | 2,742,931 | 2,742,931 | $ | 4,055,232.88 | |||||||||||
Entities affiliated with 8VC(3) | — | 1,530,308 | 1,530,308 | $ | 2,262,454.97 | |||||||||||
Matrix Partners China VI Hong Kong Limited | 6,087,537 | — | 6,087,537 | $ | 9,999,997.05 | |||||||||||
| (1) | Mr. Cooper, a former member of Senti’s board of directors, is employed as a Director of Venture Investments with Leaps by Bayer, an investment arm of Bayer AG, which is an affiliate of Bayer Healthcare LLC. |
| (2) | Mr. Mathers, a member of Senti’s board of directors, is employed as a Partner at New Enterprise Associates, Inc., which is affiliated with NEA 15 and Ven 2018. |
| (3) | Mr. Kolicich, a former member of Senti’s board of directors, is employed as a Partner of Eight Partners VC, LLC, which is an affiliate of 8VC and 8VC Entrepreneurs. |
Investors’ Rights Agreement
Senti is party to an amended and restated investors’ rights agreement, or the IRA, with certain holders of Senti’s capital stock, including the holders of more than 5% of Senti’s outstanding capital stock, such as Bayer Healthcare LLC, entities affiliated with NEA, entities affiliated with 8VC and Matrix Partners China VI Hong Kong Limited. The IRA provides the holders of Senti redeemable convertible preferred stock with certain registration rights, including the right to demand that Senti file a registration statement or request that their shares be covered by a registration statement that Senti is otherwise filing. In addition, the IRA also grants a right of first offer with respect to future sales of Senti equity, as well as certain information and inspection rights to each holder who holds at least 2,815,507 shares of Senti redeemable convertible preferred stock, which rights will terminate on the closing of the Business Combination. In connection with the closing of the Business Combination, the holders of up to 99,734,543 shares of Senti common stock issued on conversion of outstanding redeemable convertible preferred stock will be entitled to rights with respect to the registration of their shares under the Securities Act under the Investors’ Rights Agreement filed as an exhibit hereto and incorporated herein by reference, which superseded and replaced the IRA.
Right of First Refusal and Co-Sale Agreement
Senti was party to an amended and restated right of first refusal and co-sale agreement, or the ROFR Agreement, with certain holders of Senti capital stock including the holders of more than 5% of Senti’s outstanding capital stock, such as Bayer Healthcare LLC, entities affiliated with NEA, entities affiliated with 8VC, and Matrix Partners China VI Hong Kong Limited. The ROFR Agreement provided for rights of first refusal and co-sale relating to the shares of Senti capital stock held by certain parties to the agreement. The ROFR Agreement terminated upon the Closing of the Business Combination.
Voting Agreement
Senti was party to an amended and restated voting agreement, or the Voting Agreement, under which certain holders of Senti capital stock, including the holders of more than 5% of Senti’s outstanding capital stock, such as
232
Bayer Healthcare LLC, entities affiliated with NEA, entities affiliated with 8VC, and Matrix Partners China VI Hong Kong Limited, have agreed as to the manner in which they will vote their shares of Senti capital stock on certain matters, including with respect to the election of directors. The Voting Agreement terminated upon the closing of the Business Combination.
Collaboration with BlueRock Therapeutics
In May 2021, Senti entered into a collaboration and option agreement with BlueRock Therapeutics LP, or BlueRock, pursuant to which Senti granted to BlueRock an option, on a collaboration program-by-collaboration program basis, to obtain an exclusive or non-exclusive license under Senti’s intellectual property rights to develop, manufacture and commercialize, for the prevention, treatment or palliation of specified indications, or a licensed field, cell therapy products that contain cells of specified types that incorporate an option gene circuit from such collaboration program or a closely related derivative gene circuit. BlueRock is a wholly-owned subsidiary of Bayer Healthcare LLC, a holder of more than 5% of Senti’s common stock. Mr. Cooper, a member of Senti’s board of directors, is employed as a Director of Venture Investments with Leaps by Bayer, an investment arm of Bayer AG, which is the parent company of Bayer Healthcare LLC. For a description of the collaboration and option agreement, see the section titled “Business — Material License and Collaboration Agreements.”
Indemnification Agreements
The Charter contains provisions limiting the liability of directors, and the Bylaws provide that we will indemnify each of our directors and officers to the fullest extent permitted under Delaware law. The Charter and Bylaws also provide our board of directors with discretion to indemnify our employees and other agents when determined appropriate by the board of directors.
In addition, we have entered into or intend to enter into an indemnification agreement with each of our directors and executive officers, which will require us to indemnify them.
Stock Option Grants to Directors and Executive Officers
We have granted stock options to our directors and executive officers, as more fully described in the sections titled “Executive Compensation” and “Director Compensation.”
Related Person Transactions Policy
Our board of directors has adopted a related person transaction policy setting forth the policies and procedures for the identification, review and approval or ratification of related person transactions. This policy covers, with certain exceptions set forth in Item 404 of Regulation S-K under the Securities Act, any transaction, arrangement or relationship, or any series of similar transactions, arrangements or relationships, in which Senti and a related person were or will be participants and the amount involved exceeds $120,000, including purchases of goods or services by or from the related person or entities in which the related person has a material interest, indebtedness and guarantees of indebtedness. In reviewing and approving or rejecting any such transactions, our audit committee will consider all relevant facts and circumstances as appropriate, such as the purpose of the transaction, the availability of other sources of comparable products or services, whether the transaction is on terms comparable to those that could be obtained in an arm’s length transaction, management’s recommendation with respect to the proposed related person transaction, and the extent of the related person’s interest in the transaction.
233
DYNS Related Party Transactions
Founder Shares
On March 8, 2021, the Sponsor was issued 5,750,000 shares of DYNS Class B Common Stock (the Founder Shares) for an aggregate price of $25,000. The Founder Shares included an aggregate of up to 750,000 shares of Class B Common Stock subject to forfeiture by the Sponsor to the extent that the underwriter’s over-allotment option was not exercised in full or in part, so that the Sponsor would own, on an as-converted basis, 20% of DYNS’ issued and outstanding shares after its Initial Public Offering (excluding the Private Placement Shares) and assuming its Sponsor did not purchase any Public Shares in its Initial Public Offering). The underwriter fully exercised the over-allotment option on May 28, 2021; thus, these 750,000 Founder Shares are no longer subject to forfeiture.
Private Placement Shares
Simultaneously with the closing of the DYNS Initial Public Offering, DYNS consummated the sale of 715,500 shares of its Class A Common Stock (the “Private Placement Shares”) at a price of $10.00 per share in a private placement to its Sponsor, generating gross proceeds of $7,155,000. A portion of the proceeds from the sale of the Private Placement Shares was added to the net proceeds from its Initial Public Offering held in the Trust Account. If DYNS did not complete an initial business combination within 24 months from the closing of its Initial Public Offering, the proceeds from the sale of the Private Placement Shares held in the Trust Account would have been used to fund the redemption of Public Shares (subject to the requirements of applicable law).
Promissory Note — Related Party
On March 8, 2021, DYNS issued an unsecured promissory note to its Sponsor (the “Promissory Note”), pursuant to which DYNS could borrow up to an aggregate of $300,000 to cover expenses related to its Initial Public Offering. The Promissory Note was non-interest bearing and was payable on the earlier of December 31, 2021 or the consummation of its Initial Public Offering. In April 2021, DYNS borrowed $250,000 under the Promissory Note, which was repaid on May 26, 2021.
Administrative Support Agreement
DYNS entered into an agreement, commencing on the effective date of its Initial Public Offering, to pay the Sponsor up to a total of $10,000 per month for office space, administrative and support services. Upon the closing of the Business Combination, the agreement terminated. DYNS did not exercise its option to use such services and did not paid any fees to the Sponsor.
Sponsor Support Agreement
In connection with the execution of the Business Combination Agreement, the Sponsor and each of the DYNS officers and directors entered into the Sponsor Support Agreement with DYNS and Senti. Under the Sponsor Support Agreement, the Sponsor has agreed to vote, at any meeting of the stockholders of DYNS and in any action by written consent of the stockholders of DYNS, all of its shares of Class B Common Stock (together with any other equity securities of DYNS that it holds of record or beneficially, as of the date of the Sponsor Support Agreement, or of which it acquires record or beneficial ownership after the date thereof (the “Subject DYNS Equity Securities”)) (i) in favor of (a) the Business Combination Agreement and the transactions contemplated thereby and (b) the other proposals that DYNS and Senti agreed in the Business Combination Agreement shall be submitted at such meeting for approval by DYNS’s stockholders together with the proposal to obtain the DYNS stockholders’ approval for the Business Combination (the “Required Transaction Proposals”) and (ii) against any proposal that conflicts or materially impedes or interferes with any Required Transaction Proposals or that would adversely affect or delay the Business Combination. The Sponsor Support
234
Agreement also prohibits the Sponsor from, among other things and subject to certain exceptions, selling, assigning or transferring any Subject DYNS Equity Securities held by the Sponsor or taking any action that would have the effect of preventing or materially delaying the Sponsor from performing its obligations under the Sponsor Support Agreement. In addition, in the Sponsor Support Agreement, the Sponsor agrees to waive, and not to assert or perfect, among other things, any rights to adjustment or other anti-dilution protections with respect to the rate at which the shares of Class B Common Stock held by the Sponsor convert into shares of Class A Common Stock in connection with the transactions contemplated by the Business Combination Agreement.
Commitments and Contingencies
Registration Rights
The holders of the Founder Shares and Private Placement Shares are entitled to registration rights pursuant to the registration and stockholder rights agreement requiring us to register such securities for resale. As at the date of this prospectus, there are 5,750,000 Founder Shares, 871,028 of which were distributed to the Anchor Investors, and 715,500 Private Placement Shares outstanding. The holders of these securities are entitled to make up to three demands, excluding short form demands, that DYNS registers such securities. In addition, the holders have certain “piggy-back” registration rights with respect to registration statements filed subsequent to the completion of an initial business combination and rights to require us to register for resale such securities pursuant to Rule 415 under the Securities Act. The registration rights agreement does not contain liquidated damages or other cash settlement provisions resulting from delays in registering our securities. DYNS will bear the expenses incurred in connection with the filing of any such registration statements. Under the Investor Rights Agreement, the Anchor Investors will be entitled to registration rights in respect of these shares.
In addition, the PIPE Investors are entitled to registration rights pursuant to the subscription agreements they entered into with DYNS in connection with the PIPE Investment. The PIPE Investors subscribed for, in aggregate, 5,060,000 shares of Class A Common Stock concurrently with the consummation of the Business Combination, and all such shares will have registration rights.
In total, after the consummation of the Business Combination, an aggregate of 11,525,500 shares of Senti common stock held by stockholders of DYNS prior to the consummation of the Business Combination and by the PIPE Investors are subject to registration rights, comprising 715,500 Private Placement Shares, 4,878,972 Founder Shares, 871,028 shares of common stock issued to Anchor Investors and 5,060,000 shares of common stock issued to PIPE Investors.
Underwriting Agreement
In connection with its Initial Public Offering, DYNS granted the underwriter a 45-day option to purchase up to 3,000,000 additional shares of Class A Common Stock to cover over-allotments at the Initial Public Offering price, less the underwriting discounts and fees. The underwriter exercised its over-allotment option in full on May 28, 2021.
The underwriter was paid a cash underwriting fee of $0.20 per share, or $4,600,000 in the aggregate, upon the closing of the Initial Public Offering. In addition, approximately $0.306 per share, or $7,050,000 in the aggregate, may be payable to the underwriter for deferred underwriting fees (this amount having being reduced from $8,050,000 by $1,000,000 by agreement with the underwriter on December 17, 2021). The deferred underwriting fee became payable to the underwriter from the amounts held in the Trust Account upon the completion of the Business Combination, subject to the terms of the underwriting agreement.
Financial Advisor Agreement
On December 16, 2021, DYNS entered into an agreement (the “Financial Advisor Agreement”) with Morgan Stanley for financial advisory services in connection with the Business Combination, which services
235
Morgan Stanley had been engaged to provide, and which services Morgan Stanley had provided, since August 4, 2021. The Financial Advisor Agreement shall terminate automatically on December 16, 2022 unless terminated earlier, with or without cause, by either DYNS or Morgan Stanley. DYNS paid Morgan Stanley a fee of $1,000,000 upon the consummation of the Business Combination.
Placement Agent Agreement
On September 21, 2021, DYNS entered into an agreement (the “Placement Agent Agreement”) with Morgan Stanley, J.P. Morgan and BofA Securities (together, the “co-placement agents”) for services in connection with the placement of shares of our Class A Common Stock to the PIPE Investors. The Placement Agent Agreement shall terminate automatically on August 28, 2022 unless terminated earlier, with or without cause, by either DYNS or any co-placement agent (as to itself only). DYNS paid the co-placement agents a total fee equal to 4.0% of the aggregate price at which the shares of DYNS Class A Common Stock were sold to the PIPE Investors, which fee was payable upon the consummation of the placement of the shares. Each of the co-placement agents received 33.3% of the fee.
Business Combination Agreement
As described elsewhere in this prospectus, DYNS entered into the Business Combination Agreement with Merger Sub and Senti pursuant to which, among other things, Merger Sub merged with and into Senti, with Senti surviving as a wholly-owned subsidiary of DYNS. DYNS also entered into various ancillary transaction documents to give effect to the Business Combination.
236
The following description summarizes certain important terms of our capital stock as of the date of this prospectus as specified in our Charter and Bylaws. Because the following description is only a summary, it does not contain all the information that may be important to you. For a complete description of the matters set forth in this section titled “Description of Securities,” you should refer to the Charter, the Bylaws and the Registration Rights Agreement, which are included as exhibits to the registration statement of which this prospectus is a part, and to the applicable provisions of Delaware law.
Authorized and Outstanding Stock
The Charter authorizes the issuance of 510,000,000 shares, consisting of 500,000,000 shares of common stock, $0.0001 par value per share, and 10,000,000 shares of preferred stock, $0.0001 par value. As of June 8, 2022, the closing date of the Business Combination, there were 43,657,077 shares of common stock outstanding. No shares of preferred stock are currently outstanding.
Common Stock
The Charter provides the following with respect to the rights, powers, preferences and privileges of the Senti Common Shares.
Voting Power
Except as otherwise required by law or as otherwise provided in any certificate of designation for any series of preferred stock, the holders of Senti Common Shares possess all voting power for the election of the directors and all other matters requiring stockholder action. Holders of Senti Common Shares are entitled to one vote per share on matters to be voted on by stockholders.
Dividends
Holders of Senti Common Shares will be entitled to receive such dividends, if any, as may be declared from time to time by our board of directors in its discretion out of funds legally available therefor. We have not historically paid any cash dividends on our common stock to date and do not intend to pay cash dividends in the foreseeable future. Any payment of cash dividends in the future will be dependent upon our revenues and earnings, if any, capital requirements and general financial conditions. In no event will any stock dividends or stock splits or combinations of stock be declared or made on Senti Common Shares unless the Senti Common Shares at the time outstanding are treated equally and identically.
Liquidation, Dissolution and Winding Up
In the event of our voluntary or involuntary liquidation, dissolution or winding-up, the net assets of Senti will be distributed pro rata to the holders of Senti Common Shares, subject to the rights of the holders of the preferred stock, if any.
Preemptive or Other Rights
There are no sinking fund provisions applicable to the Senti Common Shares.
Preferred Stock
The Charter provides that shares of preferred stock may be issued from time to time in one or more series. Our board of directors will be authorized to fix designations, powers, including voting powers, full or limited, or no voting powers, preferences and the relative, participating, optional or other special rights of the shares of each series of preferred stock and any qualifications, limitations and restrictions thereof. Our board of directors will be able to, without stockholder approval, issue preferred stock with voting and other rights that could adversely
237
affect the voting power and other rights of the holders of the Senti Common Shares and could have anti-takeover effects. The ability of our board of directors to issue preferred stock without stockholder approval could have the effect of delaying, deferring or preventing a change of control of Senti or the removal of existing management. We have no preferred stock currently outstanding.
Registration Rights
We, DYNS, and certain of our stockholders entered into the Investor Rights Agreement, pursuant to which, among other things, such stockholders were granted certain registration rights with respect to certain shares of securities held by them. A copy of the Investor Rights Agreement is attached as an exhibit hereto and incorporated herein by reference.
Anti-Takeover Provisions
Charter and Bylaws
Among other things, the Charter and Bylaws (as amended from time to time):
| • | permit our board of directors to issue up to 10,000,000 shares of preferred stock, with any rights, preferences and privileges as they may designate, including the right to approve an acquisition or other change of control; |
| • | provide that our number of directors may be changed only by resolution of our board of directors; |
| • | provide that, subject to the rights of any series of preferred stock to elect directors, directors may be removed only with cause by the holders of at least 75% of all of our then-outstanding shares of the capital stock entitled to vote generally at an election of directors; |
| • | provide that all vacancies, subject to the rights of any series of preferred stock, including newly created directorships, may, except as otherwise required by law, be filled by the affirmative vote of a majority of directors then in office, even if less than a quorum; |
| • | provide that stockholders seeking to present proposals before a meeting of stockholders or to nominate candidates for election as directors at a meeting of stockholders must provide advance notice in writing, and also specify requirements as to the form and content of a stockholder’s notice; |
| • | provide that special meetings of our stockholders may be called by our board of directors pursuant to a resolution adopted by a majority of the board; |
| • | provide that our board of directors will be divided into three classes of directors, with the directors serving three-year terms, therefore making it more difficult for stockholders to change the composition of the board of directors; and |
| • | not provide for cumulative voting rights, therefore allowing the holders of a majority of the Senti Common Shares entitled to vote in any election of directors to elect all of the directors standing for election, if they should so choose. |
The combination of these provisions make it more difficult for the existing stockholders to replace our board of directors as well as for another party to obtain control of us by replacing our board of directors. Because our board of directors will have the power to retain and discharge its officers, these provisions could also make it more difficult for existing stockholders or another party to effect a change in management. In addition, the authorization of undesignated preferred stock will make it possible for our board of directors to issue preferred stock with voting or other rights or preferences that could impede the success of any attempt to change the control of Senti.
These provisions are intended to enhance the likelihood of continued stability in the composition of our board of directors and its policies and to discourage coercive takeover practices and inadequate takeover bids. These provisions are also designed to reduce our vulnerability to hostile takeovers and to discourage certain
238
tactics that may be used in proxy fights. However, such provisions could have the effect of discouraging others from making tender offers for our shares and may have the effect of delaying changes in our control or management. As a consequence, these provisions may also inhibit fluctuations in the market price of the our stock.
Certain Anti-Takeover Provisions of Delaware Law
We are subject to the provisions of Section 203 of the DGCL. This statute prevents certain Delaware corporations, under certain circumstances, from engaging in a “business combination” with:
| • | a stockholder who owns 15% or more of our outstanding voting stock (otherwise known as an “interested stockholder”); |
| • | an affiliate of an interested stockholder; or |
| • | an associate of an interested stockholder, for three years following the date that the stockholder became an interested stockholder. |
A “business combination” includes a merger or sale of more than 10% of a corporation’s assets. However, the above provisions of Section 203 would not apply if:
| • | the relevant board of directors approves the transaction that made the stockholder an “interested stockholder,” prior to the date of the transaction; |
| • | after the completion of the transaction that resulted in the stockholder becoming an interested stockholder, that stockholder owned at least 85% of the corporation’s voting stock outstanding at the time the transaction commenced, other than statutorily excluded shares of common stock; or |
| • | on or subsequent to the date of the transaction, the initial business combination is approved by the board of directors and authorized at a meeting of the corporation’s stockholders, and not by written consent, by an affirmative vote of at least two-thirds of the outstanding voting stock not owned by the interested stockholder. |
These provisions may have the effect of delaying, deferring, or preventing changes in control of Senti.
Transfer Agent
Continental Stock Transfer & Trust Company is the transfer agent for the Senti Common Shares.
Trading Symbol and Market
Senti Common Shares are listed on Nasdaq under the symbol “SNTI”.
239
SECURITIES ACT RESTRICTIONS ON RESALE OF OUR SECURITIES
Rule 144
Pursuant to Rule 144 under the Securities Act (“Rule 144”), a person who has beneficially owned restricted Senti Common Shares for at least six months would be entitled to sell their securities provided that (i) such person is not deemed to have been our affiliate at the time of, or at any time during the three months preceding, a sale and (ii) we are subject to the Exchange Act periodic reporting requirements for at least three months before the sale and has filed all required reports under Section 13 or 15(d) of the Exchange Act during the 12 months (or such shorter period as it was required to file reports) preceding the sale.
Persons who have beneficially owned restricted Senti Common Shares for at least six months but who are our affiliates at the time of, or at any time during the three months preceding, a sale, would be subject to additional restrictions, by which such person would be entitled to sell within any three-month period only a number of securities that does not exceed the greater of:
| • | 1% of the total number of Senti Common Shares then outstanding; or |
| • | the average weekly reported trading volume of Senti Common Shares during the four calendar weeks preceding the date on which notice of the sale if filed with the SEC. |
Sales by affiliates of Senti Common Shares under Rule 144 are also limited by manner of sale provisions and notice requirements and by the availability of current public information about Senti.
Restrictions on the Use of Rule 144 by Shell Companies or Former Shell Companies
Rule 144 is not available for the resale of securities initially issued by shell companies (other than business-combination related shell companies) or issuers that have been at any time previously a shell company. However, Rule 144 also includes an important exception to this prohibition if the following conditions are met:
| • | the issuer of the securities that was formerly a shell company has ceased to be a shell company; |
| • | the issuer of the securities is subject to the reporting requirements of Section 13 or 15(d) of the Exchange Act; |
| • | the issuer of the securities has filed all Exchange Act reports and material required to be filed, as applicable, during the preceding 12 months (or such shorter period that the issuer was required to file such reports and materials) other than Form 8-K reports; and |
| • | at least one year has elapsed from the time that the issuer filed current Form 10-type information with the SEC reflecting its status as an entity that is not a shell company. |
We are no longer a shell company, and so, once the conditions listed above are satisfied, Rule 144 will become available for the resale of the above-noted restricted securities.
Investor Rights and Lock-Up Agreement
In connection with the Closing, DYNS, certain stockholders of DYNS (including the Sponsor) and certain stockholders of Senti entered into an Investor Rights and Lock-up Agreement (the “Investor Rights Agreement”). Pursuant to the Investor Rights Agreement, each signatory thereto (other than DYNS) was granted certain registration rights with respect to their respective Senti Common Shares.
The Investor Rights Agreement also restricts the ability of each stockholder who is a party thereto (other than DYNS) to transfer its Senti Common Shares (or any securities convertible into or exercisable or exchangeable for Senti Common Shares), subject to certain permitted transfers, for a period of one year following the Closing Date (the “Lock-Up Period”); provided that (i) the foregoing restrictions shall not apply to any Senti Common Shares purchased pursuant to the subscription agreements, and (ii) if the last reported sale
240
price of the Senti Common Shares on Nasdaq, or any other national securities exchange on which the Senti Common Shares are then traded, is greater than or equal to $12.00 per share over any 20 trading days within any consecutive 30 trading day period following the Closing Date, then, commencing at least 150 days after the Closing Date, the Lock-Up Period shall be deemed to have expired with respect to each stockholder’s Senti Common Shares subject to the Lock-Up Period.
The foregoing description of the Investor Rights Agreement does not purport to be complete and is qualified in its entirety by the terms and conditions of the Investor Rights Agreement, a form of which is included as an exhibit to this registration statement.
241
UNITED STATES FEDERAL INCOME TAX CONSIDERATIONS
The following is a discussion of certain material U.S. federal income tax consequences relating to the purchase, ownership and disposition of Senti Common Shares, which we also refer to as Senti “securities.” This discussion is limited to certain U.S. federal income tax considerations to investors that will hold securities as capital assets within the meaning of Section 1221 of the U.S. Internal Revenue Code of 1986, as amended (the “Code”) and that purchased such securities from the Selling Securityholders pursuant to this offering.
This discussion is a summary only and does not describe all of the tax consequences that may be relevant to you in light of your particular circumstances, including but not limited to the alternative minimum tax, the Medicare tax on certain net investment income and the different consequences that may apply if you are subject to special rules that apply to certain types of investors, including but not limited to:
| • | banks, financial institutions or financial services entities; |
| • | broker-dealers; |
| • | governments or agencies or instrumentalities thereof; |
| • | regulated investment companies; |
| • | real estate investment trusts; |
| • | expatriates or former long-term residents of the United States; |
| • | persons that actually or constructively own five percent or more (by vote or value) of our shares; |
| • | persons that acquired our securities pursuant to an exercise of employee share options, in connection with employee share incentive plans or otherwise as compensation; |
| • | insurance companies; |
| • | dealers or traders subject to a mark-to-market method of accounting with respect to our securities; |
| • | persons holding our securities as part of a “straddle,” “constructive sale”, “hedge”, “wash sale”, “conversion” or other integrated or similar transaction; |
| • | U.S. holders (as defined below) whose functional currency is not the U.S. dollar; |
| • | partnerships (or entities or arrangements classified as partnerships or other pass-through entities for U.S. federal income tax purposes) and any beneficial owners of such partnerships; |
| • | tax-exempt entities; |
| • | controlled foreign corporations; and |
| • | passive foreign investment companies. |
If a partnership (including an entity or arrangement treated as a partnership or other pass-thru entity for U.S. federal income tax purposes) holds our securities, the tax treatment of a partner, member or other beneficial owner in such partnership will generally depend upon the status of the partner, member or other beneficial owner, the activities of the partnership and certain determinations made at the partner, member or other beneficial owner level. If you are a partner, member or other beneficial owner of a partnership holding our securities, you are urged to consult your tax advisor regarding the tax consequences of the purchase, ownership and disposition of our securities.
This discussion is based on the Code, and administrative pronouncements, judicial decisions and final, temporary and proposed Treasury Regulations as of the date hereof, which are subject to change, possibly on a retroactive basis, and changes to any of which subsequent to the date of this prospectus may affect the tax
242
consequences described herein. This discussion does not address any aspect of state, local or non-U.S. taxation, or any U.S. federal taxes other than income taxes (such as gift and estate taxes).
We have not sought, and do not expect to seek, a ruling from the U.S. Internal Revenue Service (the “IRS”) as to any U.S. federal income tax consequence described herein. The IRS may disagree with the discussion herein, and its determination may be upheld by a court. Moreover, there can be no assurance that future legislation, regulations, administrative rulings or court decisions will not adversely affect the accuracy of the statements in this discussion. You are urged to consult your tax advisor with respect to the application of U.S. federal tax laws to your particular situation, as well as any tax consequences arising under the laws of any state, local or foreign jurisdiction.
THIS DISCUSSION IS ONLY A SUMMARY OF CERTAIN U.S. FEDERAL INCOME TAX CONSIDERATIONS ASSOCIATED WITH THE PURCHASE, OWNERSHIP AND DISPOSITION OF SENTI SECURITIES ACQUIRED PURSUANT TO THIS OFFERING. EACH PROSPECTIVE INVESTOR IN SENTI SECURITIES IS URGED TO CONSULT ITS TAX ADVISOR WITH RESPECT TO THE PARTICULAR TAX CONSEQUENCES TO SUCH INVESTOR OF THE PURCHASE, OWNERSHIP AND DISPOSITION OF SENTI SECURITIES, INCLUDING THE APPLICABILITY AND EFFECT OF ANY U.S. FEDERAL NON-INCOME, STATE, LOCAL, AND NON-U.S. TAX LAWS OR ANY APPLICABLE INCOME TAX TREATY.
U.S. Holders
This section applies to you if you are a “U.S. holder.” A U.S. holder is a beneficial owner of Senti Common Shares who or that is, for U.S. federal income tax purposes:
| • | an individual who is a citizen or resident of the United States; |
| • | a corporation (or other entity taxable as a corporation) organized in or under the laws of the United States, any state thereof or the District of Columbia; |
| • | an estate the income of which is includible in gross income for U.S. federal income tax purposes regardless of its source; or |
| • | a trust, if (i) a court within the United States is able to exercise primary supervision over the administration of the trust and one or more United States persons (as defined in the Code) have authority to control all substantial decisions of the trust or (ii) it has a valid election in effect under Treasury Regulations to be treated as a United States person. |
Taxation of Distributions. If we pay distributions in cash or other property (other than certain distributions of Senti Common Shares or rights to acquire Senti Common Shares) to U.S. holders of Senti Common Shares, such distributions generally will constitute dividends for U.S. federal income tax purposes to the extent paid from our current or accumulated earnings and profits, as determined under U.S. federal income tax principles. Distributions in excess of current and accumulated earnings and profits will constitute a return of capital that will be applied against and reduce (but not below zero) the U.S. holder’s adjusted tax basis in its Senti Common Shares. Any remaining excess will be treated as gain realized on the sale or other disposition of its Senti Common Shares and will be treated as described under “U.S. Holders—Gain or Loss on Sale, Taxable Exchange or Other Taxable Disposition of Senti Common Shares” below.
Dividends we pay to a U.S. holder that is treated as a taxable corporation generally will qualify for the dividends received deduction if the requisite holding period is satisfied. With certain exceptions (including, but not limited to, dividends treated as investment income for purposes of investment interest deduction limitations), and provided certain holding period requirements are met, dividends we pay to a non-corporate U.S. holder may constitute “qualified dividend income” that will be subject to tax at the applicable maximum tax rate accorded to long-term capital gains. If the applicable holding period requirements are not satisfied, then a U.S. holder that is a
243
corporation may not be able to qualify for the dividends received deduction and would have taxable income equal to the entire dividend amount, and non-corporate U.S. holders may be subject to tax on such dividend at regular ordinary income tax rates instead of the preferential rate that applies to qualified dividend income.
Gain or Loss on Sale, Taxable Exchange or Other Taxable Disposition of Senti Common Shares.
Upon a sale or other taxable disposition of Senti Common Shares, a U.S. holder generally will recognize capital gain or loss in an amount equal to the difference between the amount realized and the U.S. holder’s adjusted tax basis in its Senti Common Shares. Any such capital gain or loss generally will be long-term capital gain or loss if the U.S. holder’s holding period for its Senti Common Shares so disposed of exceeds one year. Long-term capital gains recognized by non-corporate U.S. holders may be eligible to be taxed at reduced rates. The deductibility of capital losses is subject to limitations.
Generally, the amount of gain or loss recognized by a U.S. holder is an amount equal to the difference between (i) the sum of the amount of cash and the fair market value of any property received in such disposition and (ii) the U.S. holder’s adjusted tax basis in its Senti Common Shares so disposed of. A U.S. holder’s adjusted tax basis in its Senti Common Shares generally will equal the U.S. holder’s acquisition cost less, in the case of Senti Common Shares, any prior distributions treated as a return of capital.
Information Reporting and Backup Withholding. In general, information reporting requirements may apply to distributions paid to a U.S. holder and to the proceeds of the sale or other disposition of Senti Common Shares, unless the U.S. holder is an exempt recipient. Backup withholding may apply to such payments if the U.S. holder fails to provide a taxpayer identification number, a certification of exempt status or has been notified by the IRS that it is subject to backup withholding (and such notification has not been withdrawn).
Backup withholding is not an additional tax. Any amounts withheld under the backup withholding rules will be allowed as a credit against a U.S. holder’s U.S. federal income tax liability and may entitle such holder to a refund, provided the required information is timely furnished to the IRS.
Non-U.S. Holders
This section applies to you if you are a “Non-U.S. holder.” As used herein, the term “Non-U.S. holder” means a beneficial owner of Senti Common Shares who or that is for U.S. federal income tax purposes:
| • | a non-resident alien individual (other than certain former citizens and residents of the United States subject to U.S. tax as expatriates); |
| • | a foreign corporation; or |
| • | an estate or trust that is not a U.S. holder; |
but generally does not include an individual who is present in the United States for 183 days or more in the taxable year of the disposition of their securities. If you are such an individual, you should consult your tax advisor regarding the U.S. federal income tax consequences of the purchase, ownership or sale or other disposition of our securities.
Taxation of Distributions. In general, any distributions (other than certain distributions of Senti stock or rights to acquire Senti stock) we make to a Non-U.S. holder of Senti Common Shares, to the extent paid out of our current or accumulated earnings and profits (as determined under U.S. federal income tax principles), will constitute dividends for U.S. federal income tax purposes and, provided such dividends are not effectively connected with the Non-U.S. holder’s conduct of a trade or business within the United States, we will be required to withhold tax from the gross amount of the dividend at a rate of 30%, unless such Non-U.S. holder is eligible for a reduced rate of withholding tax under an applicable income tax treaty and provides proper certification of
244
its eligibility for such reduced rate (usually on an IRS Form W-8BEN or W-8BEN-E). Any distribution not constituting a dividend will be treated first as reducing (but not below zero) the Non-U.S. holder’s adjusted tax basis in its Senti Common Shares and, to the extent such distribution exceeds the Non-U.S. holder’s adjusted tax basis, as gain realized from the sale or other disposition of its Senti Common Shares, which will be treated as described under “Non-U.S. Holders—Gain on Sale, Taxable Exchange or Other Taxable Disposition of Senti Common Shares” below. In addition, if we determine that we are likely to be classified as a “United States real property holding corporation” (see “Non-U.S. Holders—Gain on Sale, Taxable Exchange or Other Taxable Disposition of Senti Common Shares” below), we may withhold 15% of any distribution that exceeds our current and accumulated earnings and profits.
The withholding tax generally does not apply to dividends paid to a Non-U.S. holder who provides an IRS Form W-8ECI, certifying that the dividends are effectively connected with the Non-U.S. holder’s conduct of a trade or business within the United States. Instead, the effectively connected dividends will be subject to regular U.S. federal income tax as if the Non-U.S. holder were a U.S. resident, subject to an applicable income tax treaty providing otherwise. A corporate Non-U.S. holder receiving effectively connected dividends may also be subject to an additional “branch profits tax” imposed at a rate of 30% (or a lower applicable treaty rate).
Gain on Sale, Taxable Exchange or Other Taxable Disposition of Senti Common Shares. A Non-U.S. holder generally will not be subject to U.S. federal income or withholding tax in respect of gain recognized on a sale, taxable exchange or other taxable disposition of its Senti Common Shares unless:
| • | the gain is effectively connected with the conduct by the Non-U.S. holder of a trade or business within the United States (and, under certain income tax treaties, is attributable to a United States permanent establishment or fixed base maintained by the Non-U.S. holder); or |
| • | we are or have been a “United States real property holding corporation” (a “USRPHC”) for U.S. federal income tax purposes at any time during the shorter of the five-year period ending on the date of disposition or the Non-U.S. holder’s holding period for its Senti Common Shares, except, in the case where Senti Common Shares are regularly traded on an established securities market, the Non-U.S. holder has owned, directly or constructively, at all times within the shorter of the five-year period preceding the disposition of its Senti Common Shares or such Non-U.S. holder’s holding period for such Senti Common Shares, 5% or less of Senti Common Shares. There can be no assurance that our Senti Common Shares will be treated as regularly traded on an established securities market for this purpose. Non-U.S. holders should consult their own tax advisors regarding the application of the foregoing rules in light of their particular facts and circumstances. |
Unless an applicable treaty provides otherwise, gain described in the first bullet point above will be subject to tax at generally applicable U.S. federal income tax rates as if the Non-U.S. holder were a U.S. resident. Any gains described in the first bullet point above of a Non-U.S. holder that is treated as a foreign corporation for U.S. federal income tax purposes may also be subject to an additional “branch profits tax” imposed at a 30% rate (or lower treaty rate).
If the second bullet point above applies to a Non-U.S. holder, gain recognized by such holder on the sale, exchange or other disposition of its securities will be subject to tax at generally applicable U.S. federal income tax rates. In addition, a buyer of our securities from such holder may be required to withhold U.S. federal income tax at a rate of 15% of the amount realized upon such disposition if our Senti Common Shares are not treated as regularly traded on an established securities market. We will be classified as a USRPHC if the fair market value of our “United States real property interests” equals or exceeds 50% of the sum of the fair market value of our worldwide real property interests plus our other assets used or held for use in a trade or business, as determined for U.S. federal income tax purposes.
Information Reporting and Backup Withholding. Information returns generally will be filed with the IRS in connection with payments to a Non-U.S. holder of distributions on Senti Common Shares. Proceeds from a sale
245
or other taxable disposition of our securities within the United States or conducted through certain U.S.-related brokers may be subject to backup withholding or information reporting unless a Non-U.S. holder complies with certification procedures to establish that it is not a United States person. The certification procedures required to claim a reduced rate of withholding under a treaty generally will satisfy such certification requirements. Proceeds of a disposition of our securities conducted through a non-U.S. office of a non-U.S. broker generally will not be subject to backup withholding or information reporting. Backup withholding is not an additional tax. The amount of any backup withholding from a payment to a Non-U.S. holder will be allowed as a credit against such holder’s U.S. federal income tax liability and may entitle such holder to a refund, provided that the required information is timely furnished to the IRS.
FATCA Withholding Taxes. Provisions commonly referred to as “FATCA” impose withholding of 30% on payments of dividends on Senti Common Shares, or (subject to the proposed Treasury Regulations discussed below) gross proceeds from the sale or other disposition of, our securities paid (or deemed paid) to “foreign financial institutions” (which is broadly defined for this purpose and in general includes investment vehicles) and certain other non-U.S. entities unless various U.S. information reporting and due diligence requirements (generally relating to ownership by United States persons of interests in or accounts with those entities) have been satisfied by, or an exemption applies to, the payee (typically certified as to by the delivery of a properly completed IRS Form W-8BEN-E). Foreign financial institutions located in jurisdictions that have an intergovernmental agreement with the United States governing FATCA may be subject to different rules. Under certain circumstances, a Non-U.S. holder might be eligible for refunds or credits of such withholding taxes, and a Non-U.S. holder might be required to file a U.S. federal income tax return to claim such refunds or credits. Thirty percent withholding under FATCA was scheduled to apply to payments of gross proceeds from the sale or other disposition of property that produces U.S.-source interest or dividends beginning on January 1, 2019, but on December 13, 2018, the IRS released proposed regulations that, if finalized in their proposed form, would eliminate the obligation to withhold on gross proceeds. Such proposed regulations also delayed withholding on certain other payments received from other foreign financial institutions that are allocable, as provided for under final Treasury Regulations, to payments of U.S.-source dividends, and other fixed or determinable annual or periodic income. Although these proposed Treasury Regulations are not final, taxpayers generally may rely on them until final Treasury Regulations are issued. However, there can be no assurance that final Treasury Regulations will provide the same exceptions from FATCA withholding as the proposed Treasury Regulations. Prospective investors should consult their tax advisors regarding the effects of FATCA on their investment in securities.
246
We are registering the issuance by us of 2,000,000 Senti Common Shares that may be issued from time to time upon achievement of certain stock price thresholds (the “Earn-Out Shares”). We are also registering the resale by the Selling Securityholders of up to 33,444,908 additional Senti Common Shares.
Once issued and upon effectiveness of the registration statement of which this prospectus forms a part, the securities beneficially owned by the Selling Securityholders covered by this prospectus may be offered and sold from time to time by the Selling Securityholders. The term “Selling Securityholders” includes donees, pledgees, transferees or other successors in interest selling securities received after the date of this prospectus from a Selling Securityholder as a gift, pledge, partnership distribution or other transfer. The Selling Securityholders will act independently of us in making decisions with respect to the timing, manner and size of each sale. Such sales may be made on one or more exchanges or in the over-the-counter market or otherwise, at prices and under terms then prevailing or at prices related to the then current market price or in negotiated transactions. Each Selling Securityholder reserves the right to accept and, together with its respective agents, to reject, any proposed purchase of securities to be made directly or through agents. The Selling Securityholders and any of their permitted transferees may sell their securities offered by this prospectus on any stock exchange, market or trading facility on which the securities are traded or in private transactions.
Subject to any limitations set forth in any applicable agreement that provides for registration rights, the Selling Securityholders may use any one or more of the following methods when selling the securities offered by this prospectus:
| • | purchases by a broker-dealer as principal and resale by such broker-dealer for its own account pursuant to this prospectus; |
| • | ordinary brokerage transactions and transactions in which the broker solicits purchasers; |
| • | one or more underwritten offerings; |
| • | block trades in which the broker-dealer so engaged will attempt to sell the securities as agent, but may position and resell a portion of the block as principal to facilitate the transaction; |
| • | an exchange distribution in accordance with the rules of the applicable exchange; |
| • | in market transactions, including transactions on a national securities exchange or quotations service or over-the-counter market; |
| • | distributions to their members, partners or stockholders; |
| • | settlement of short sales entered into after the date of the registration statement of which this prospectus is a part is declared effective by the SEC; |
| • | agreements with broker-dealers to sell a specified number of the securities at a stipulated price per share; |
| • | in “at the market” offerings, as defined in Rule 415 under the Securities Act, at negotiated prices, at prices prevailing at the time of sale or at prices related to such prevailing market prices, including sales made directly on a national securities exchange or sales made through a market maker other than on an exchange or other similar offerings through sales agents; |
| • | directly to purchasers, including through a specific bidding, auction or other process or in privately negotiated transactions; |
| • | through the writing or settlement of options or other hedging transactions, whether through an options exchange or otherwise; |
| • | through a combination of any of the above methods of sale; or |
| • | any other method permitted pursuant to applicable law. |
247
In addition, a Selling Securityholder that is an entity may elect to make an in-kind distribution of securities to its members, partners, stockholders or other equityholders pursuant to the registration statement of which this prospectus is a part by delivering a prospectus. Such members, partners, stockholders or other equityholders that are not affiliates of ours would thereby receive freely tradeable securities pursuant to the distribution through a registration statement. To the extent a distributee is an affiliate of ours (or to the extent otherwise required by law), we may file a prospectus supplement in order to permit the distributees to use the prospectus to resell the securities acquired in the distribution.
The Selling Securityholders also may transfer the securities in other circumstances, in which case the transferees, pledgees or other successors-in-interest will be the selling beneficial owners for purposes of this prospectus. Upon being notified by a Selling Securityholder that a donee, pledgee, transferee, other successor-in-interest intends to sell our securities, we will, to the extent required, promptly file a supplement to this prospectus to name specifically such person as a Selling Securityholder.
To the extent required, the Senti Common Shares to be sold, the names of the Selling Securityholders, the respective purchase prices and public offering prices, the names of any agents, dealer or underwriter, any applicable commissions or discounts with respect to a particular offer will be set forth in an accompanying prospectus supplement or, if appropriate, a post-effective amendment to the registration statement that includes this prospectus.
The Selling Securityholders may enter into hedging transactions with broker-dealers or other financial institutions, which may in turn engage in short sales of the Senti Common Shares in the course of hedging the positions they assume. The Selling Securityholders may also sell the Senti Common Shares short and deliver these securities to close out their short positions, or loan or pledge the Senti Common Shares to broker-dealers that in turn may sell these shares. The Selling Securityholders may also enter into option or other transactions with broker-dealers or other financial institutions or the creation of one or more derivative securities which require the delivery to such broker-dealer or other financial institution of shares offered by this prospectus, which shares such broker-dealer or other financial institution may resell pursuant to this prospectus (as supplemented or amended to reflect such transaction).
The Selling Securityholders also may in the future resell a portion or all of the Senti Common Shares in open market transactions in reliance upon Rule 144 under the Securities Act, provided that they meet the criteria and conform to the requirements of that rule, or pursuant to other available exemptions from the registration requirements of the Securities Act.
Selling Securityholders may use this prospectus in connection with resales of the Senti Common Shares. This prospectus and any accompanying prospectus supplement will identify the Selling Securityholders, the terms of the Senti Common Shares and any material relationships between us and the Selling Securityholders. In offering the securities covered by this prospectus, the Selling Securityholders and any underwriters, broker-dealers or agents who execute sales for the Selling Securityholders may be deemed to be “underwriters” within the meaning of the Securities Act in connection with such sales. Any discounts, commissions, concessions or profit they earn on any resale of those securities may be underwriting discounts and commissions under the Securities Act. Unless otherwise set forth in a prospectus supplement, the Selling Securityholders will receive all the net proceeds from the resale of the Senti Common Shares. If any Selling Securityholder is an “underwriter” within the meaning of Section 2(11) of the Securities Act, then the Selling Securityholder will be subject to the prospectus delivery requirements of the Securities Act. Underwriters and their controlling persons, dealers and agents may be entitled, under agreements entered into with us and the Selling Securityholder, to indemnification against and contribution toward specific civil liabilities, including liabilities under the Securities Act.
In order to comply with the securities laws of certain states, if applicable, the securities must be sold in such jurisdictions only through registered or licensed brokers or dealers. In addition, in certain states the securities may not be sold unless they have been registered or qualified for sale in the applicable state or an exemption from the registration or qualification requirement is available and is complied with.
248
We have advised the Selling Securityholders that the anti-manipulation rules of Regulation M under the Exchange Act may apply to sales of shares in the market and to the activities of the Selling Securityholders and their affiliates. In addition, to the extent applicable we will make copies of this prospectus (as it may be supplemented or amended from time to time) available to the Selling Securityholders for the purpose of satisfying the prospectus delivery requirements of the Securities Act. The Selling Securityholders may indemnify any broker-dealer that participates in transactions involving the sale of the Senti Common Shares against certain liabilities, including liabilities arising under the Securities Act.
We are required to pay all fees and expenses incident to the registration of shares of the Senti Common Shares to be offered and sold pursuant to this prospectus.
249
Goodwin Procter LLP has passed upon the validity of the Senti Common Shares offered by this prospectus and certain other legal matters related to this prospectus.
The consolidated financial statements of Dynamics Special Purpose Corp. as of December 31, 2021, and for the period from March 1, 2021 (inception) through December 31, 2021, included in this prospectus have been audited by Marcum LLP, independent registered public accounting firm, as stated in their report herein (which contains an explanatory paragraph relating to substantial doubt about the ability of Dynamics Special Purpose Corp. to continue as going concern, as described in Note 1 to the consolidated financial statements), appearing elsewhere in this prospectus, and are included in reliance upon such report given on the authority of such firm as experts in accounting and auditing.
The consolidated financial statements of Senti Biosciences, Inc. and subsidiary as of December 31, 2021 and 2020, and for each of the years in the two-year period ended December 31, 2021, have been included herein and elsewhere in the registration statement in reliance upon the report of KPMG LLP, independent registered public accounting firm, appearing elsewhere herein, and upon authority of said firm as experts in accounting and auditing. The audit report covering the December 31, 2021 consolidated financial statements contains an explanatory paragraph that states that Senti Biosciences, Inc. and subsidiary’s recurring losses, negative cash flows from operations and accumulated deficit raise substantial doubt about the entity’s ability to continue as a going concern. The consolidated financial statements do not include any adjustments that might result from the outcome of that uncertainty.
250
CHANGES IN REGISTRANT’S CERTIFYING ACCOUNTANT
(a)Dismissal of independent registered public accounting firm
On June 8, 2022, our board of directors approved the engagement of KPMG LLP (“KPMG”) as Senti’s independent registered public accounting firm to audit Senti’s consolidated financial statements as of and for the year ending December 31, 2022. Marcum LLP (“Marcum”) served as independent registered public accounting firm of DYNS prior to the Business Combination. Accordingly, Marcum was informed that they have been dismissed as Senti’s independent registered public accounting firm.
The report of Marcum on DYNS’s balance sheet as of December 31, 2021, and for the period from March 1, 2021 (inception) through December 31, 2021, and the related notes to the financial statements, did not contain an adverse opinion or a disclaimer of opinion, and were not qualified or modified as to audit scope or accounting principles. However, the opinion was modified as management of DYNS concluded that DYNS has a working capital deficiency as of December 31, 2021 and lacks the financial resources it needs to sustain operations for a reasonable period of time, which is considered to be one year from the issuance date of the financial statements. These conditions raise substantial doubt about DYNS’s ability to continue as a going concern.
During the period from March 1, 2021 (DYNS inception) through December 31, 2021, and the subsequent interim period through June 8, 2022, there were no “disagreements” (as such term is defined in Item 304(a)(1)(iv) of Regulation S-K under the Exchange Act) between Senti and Marcum on any matter of accounting principles or practices, financial statement disclosure or auditing scope or procedure, which disagreements, if not resolved to the satisfaction of Marcum, would have caused it to make reference to the subject matter of the disagreements in its reports on DYNS’s financial statements for such period.
During the period from March 1, 2021 (DYNS inception) to December 31, 2021 and the subsequent interim period preceding Marcum’s dismissal, there was one “reportable event” (as defined in Item 304(a)(1)(v) of Regulation S-K under the Exchange Act). As previously disclosed in DYNS’s quarterly report for the period ended March 31, 2022, management determined that a material weakness in internal control over financial reporting existed relating to the accounting treatment for complex financial instruments.
Senti provided Marcum with a copy of the foregoing disclosures and requested that Marcum furnish Senti with a letter addressed to the Commission stating whether it agrees with the statements made by Senti set forth above. A copy of Marcum’s letter, dated June 14, 2022, is filed as Exhibit 16.1 hereto.
(b)Disclosures regarding the new independent auditor
As described above, on June 8, 2022, our board of directors approved the engagement of KPMG as Senti’s independent registered public accounting firm to audit Senti’s consolidated financial statements as of and for the year ending December 31, 2022. KPMG served as the independent registered public accounting firm of Senti prior to the Business Combination. During the period from March 1, 2021 (inception) through December 31, 2021, and the subsequent interim period through June 8, 2022, Senti did not consult with KPMG with respect to (i) the application of accounting principles to a specified transaction, either completed or proposed, the type of audit opinion that might be rendered on Senti’s financial statements, and neither a written report nor oral advice was provided to Senti that KPMG concluded was an important factor considered by Senti in reaching a decision as to any accounting, auditing or financial reporting issue, or (ii) any other matter that was the subject of a disagreement or a reportable event (as defined above).
251
WHERE YOU CAN FIND MORE INFORMATION
We have filed a registration statement on Form S-1, including exhibits, under the Securities Act of 1933, as amended, with respect to the Senti Common Shares offered by this prospectus. This prospectus constitutes only a part of the registration statement. Some items are contained in exhibits to the registration statement as permitted by the rules and regulations of the SEC. For further information with respect to us and our securities, we refer you to the registration statement, including the exhibits filed as a part of the registration statement. Statements contained in this prospectus concerning the contents of any contract or document referred to are not necessarily complete. If a contract or document has been filed as an exhibit to the registration statement, please see the copy of the contract or document that has been filed. Each statement in this prospectus relating to a contract or document filed as an exhibit is qualified in all respects by the filed exhibit.
In addition, we file annual, quarterly and current reports, proxy statements and other information with the SEC. Our SEC filings are available to the public on a website maintained by the SEC located at www.sec.gov. We also maintain a website at https://sentibio.com/. Through our website, we make available, free of charge, annual, quarterly and current reports, proxy statements and other information as soon as reasonably practicable after they are electronically filed with, or furnished to, the SEC. The information contained on, or that may be accessed through, our website is not part of, and is not incorporated into, this prospectus. Information contained on our website is not a part of or incorporated by reference into this prospectus and the inclusion of our website and investor relations website addresses in this prospectus is an inactive textual reference only.
252
FINANCIAL STATEMENTS AND SUPPLEMENTARY DATA INDEX TO FINANCIAL STATEMENTS
DYNAMICS SPECIAL PURPOSE CORP.
| Page | ||||
Financial Statements (Audited) for the period from March 1, 2021 (inception) to December 31, 2021 | ||||
| F-2 | ||||
| F-3 | ||||
| F-4 | ||||
| F-5 | ||||
| F-6 | ||||
| F-7 | ||||
Financial Statements (Unaudited) for the three months ended March 31, 2022 | ||||
Condensed Consolidated Balance Sheets as of March 31, 2022 and December 31, 2021 | F-25 | |||
| F-26 | ||||
| F-27 | ||||
| F-28 | ||||
Notes to Unaudited Condensed Consolidated Financial Statements | F-29 | |||
SENTI BIOSCIENCES, INC.
| Page | ||||
Financial Statements (Audited) for the years ended December 31, 2020 and December 31, 2021 | ||||
| F-46 | ||||
| F-47 | ||||
Consolidated Statements of Operations and Comprehensive Loss | F-48 | |||
Consolidated Statements of Redeemable Convertible Preferred Stock and Stockholders’ Deficit | F-49 | |||
| F-50 | ||||
| F-51 | ||||
Financial Statements (Unaudited) for the three months ended March 31, 2022 | ||||
| F-81 | ||||
Condensed Consolidated Statements of Operations and Comprehensive Loss | F-82 | |||
Condensed Consolidated Statement of Redeemable Convertible Preferred Stock and Stockholders’ Deficit | F-83 | |||
| F-84 | ||||
| F-85 | ||||
F-1
REPORT OF INDEPENDENT REGISTERED PUBLIC ACCOUNTING FIRM
To the Stockholders and Board of Directors of
Dynamics Special Purpose Corp.
Redwood City, California
Opinion on the Financial Statements
We have audited the accompanying consolidated balance sheet of Dynamics Special Purpose Corp.(the “Company”) as of December 31, 2021, the related consolidated statements of operations, changes in stockholders’ deficit and cash flows for the period from March 1, 2021 (inception) through December 31, 2021, and the related notes (collectively referred to as the “financial statements”). In our opinion, the financial statements present fairly, in all material respects, the financial position of the Company as of December 31, 2021, and the results of its operations and its cash flows for the period from March 1, 2021 (inception) through December 31, 2021, in conformity with accounting principles generally accepted in the United States of America.
Explanatory Paragraph – Going Concern
The accompanying financial statements have been prepared assuming that the Company will continue as a going concern. As more fully described in Note 1 to the financial statements, the Company’s business plan is dependent on the completion of a business combination and the Company’s cash and working capital as of December 31, 2021 are not sufficient to complete its planned activities. These conditions raise substantial doubt about the Company’s ability to continue as a going concern. Management’s plans in regard to these matters are also described in Note 1. The financial statements do not include any adjustments that might result from the outcome of this uncertainty.
Basis for Opinion
These financial statements are the responsibility of the Company’s management. Our responsibility is to express an opinion on the Company’s financial statements based on our audit. We are a public accounting firm registered with the Public Company Accounting Oversight Board (United States) (“PCAOB”) and are required to be independent with respect to the Company in accordance with the U.S. federal securities laws and the applicable rules and regulations of the Securities and Exchange Commission and the PCAOB.
We conducted our audit in accordance with the standards of the PCAOB. Those standards require that we plan and perform the audit to obtain reasonable assurance about whether the financial statements are free of material misstatement, whether due to error or fraud. The Company is not required to have, nor were we engaged to perform, an audit of its internal control over financial reporting. As part of our audit we are required to obtain an understanding of internal control over financial reporting but not for the purpose of expressing an opinion on the effectiveness of the Company’s internal control over financial reporting. Accordingly, we express no such opinion.
Our audit included performing procedures to assess the risks of material misstatement of the financial statements, whether due to error or fraud, and performing procedures that respond to those risks. Such procedures included examining, on a test basis, evidence regarding the amounts and disclosures in the financial statements. Our audit also included evaluating the accounting principles used and significant estimates made by management, as well as evaluating the overall presentation of the financial statements. We believe that our audit provides a reasonable basis for our opinion.
/s/ MarcumLLP |
Marcum LLP |
We have served as the Company’s auditor from 2021 to 2022. |
Houston, Texas |
March 7, 2022 |
F-2
DYNAMICS SPECIAL PURPOSE CORP.
DECEMBER 31, 2021
ASSETS | ||||
Current assets: | ||||
Cash | $ | 889,323 | ||
Prepaid expenses | 408,042 | |||
|
| |||
Total current assets | 1,297,365 | |||
Prepaid expenses—noncurrent | 150,514 | |||
Investments held in Trust Account | 230,008,784 | |||
|
| |||
TOTAL ASSETS | $ | 231,456,663 | ||
|
| |||
LIABILITIES AND STOCKHOLDERS’ DEFICIT | ||||
Current liabilities: | ||||
Accounts payable and other current liabilities | $ | 39,520 | ||
Accrued professional fees and other expenses | 3,078,822 | |||
Franchise tax payable | 163,839 | |||
|
| |||
Total current liabilities | 3,282,181 | |||
Deferred underwriting fee payable | 7,050,000 | |||
|
| |||
Total Liabilities | 10,332,181 | |||
|
| |||
Commitments and Contingencies (Note 6) | ||||
Class A common stock subject to possible redemption, 23,000,000 shares at redemption value (assumed to be $10.00 per share) | 230,000,000 | |||
Stockholders’ Deficit | ||||
Preferred stock, $0.0001 par value; 1,000,000 shares authorized; none issued and outstanding | 0 | |||
Class A common stock, $0.0001 par value; 100,000,000 shares authorized; 23,715,500 shares issued; 715,500 shares outstanding (excluding 23,000,000 shares subject to possible redemption) | 72 | |||
Class B common stock, $0.0001 par value; 10,000,000 shares authorized; 5,750,000 shares issued and outstanding | 575 | |||
Additionalpaid-incapital | 0 | |||
Accumulated deficit | (8,876,165 | ) | ||
|
| |||
Total Stockholders’ Deficit | (8,875,518 | ) | ||
|
| |||
Total Liabilities and Stockholders’ Deficit | $ | 231,456,663 | ||
|
|
The accompanying notes are an integral part of the consolidated financial statements.
F-3
DYNAMICS SPECIAL PURPOSE CORP.
CONSOLIDATED STATEMENT OF OPERATIONS
FOR THE PERIOD FROM MARCH 1, 2021 (INCEPTION) THROUGH DECEMBER 31, 2021
Professional fees and other expenses | $ | 3,702,033 | ||
Franchise tax expense | 163,839 | �� | ||
|
| |||
Loss from operations | (3,865,872 | ) | ||
Interest and dividend income on investments held in Trust Account | 8,784 | |||
|
| |||
Net loss | $ | (3,857,088 | ) | |
|
| |||
Basic and diluted weighted average shares outstanding, Class A common stock | 16,872,995 | |||
|
| |||
Basic and diluted net loss per share, Class A common stock | $ | (0.17 | ) | |
|
| |||
Basic and diluted weighted average shares outstanding, Class B common stock | 5,418,853 | |||
|
| |||
Basic and diluted net loss per share, Class B common stock | $ | (0.17 | ) | |
|
|
The accompanying notes are an integral part of the consolidated financial statements.
F-4
DYNAMICS SPECIAL PURPOSE CORP.
CONSOLIDATED STATEMENT OF CHANGES IN STOCKHOLDERS’ DEFICIT
FOR THE PERIOD FROM MARCH 1, 2021 (INCEPTION) THROUGH DECEMBER 31, 2021
| Class A Common Stock | Class B Common Stock | Additional Paid-in Capital | Accumulated Deficit | Total Stockholders’ Deficit | ||||||||||||||||||||||||
| Shares | Amount | Shares | Amount | |||||||||||||||||||||||||
Balance—March 1, 2021 (Inception) | 0 | $ | 0 | 0 | $ | 0 | $ | 0 | $ | 0 | $ | 0 | ||||||||||||||||
Issuance of Class B common stock to Sponsor | 0 | 0 | 5,750,000 | 575 | 24,425 | 0 | 25,000 | |||||||||||||||||||||
Sale of 715,500 shares of Class A common stock in private placement to Sponsor, net of offering costs | 715,500 | 72 | 0 | 0 | 7,138,365 | 0 | 7,138,437 | |||||||||||||||||||||
Remeasurement of redeemable Class A common stock to redemption amount | 0 | 0 | 0 | 0 | (7,162,790 | ) | (6,019,077 | ) | (13,181,867 | ) | ||||||||||||||||||
Waiver of deferred underwriting commissions by underwriter (see Note 6) | 0 | 0 | 0 | 0 | 0 | 1,000,000 | 1,000,000 | |||||||||||||||||||||
Net loss | 0 | 0 | 0 | 0 | 0 | (3,857,088 | ) | (3,857,088 | ) | |||||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||||||||||
Balance—December 31, 2021 | 715,500 | $ | 72 | 5,750,000 | $ | 575 | $ | 0 | $ | (8,876,165 | ) | $ | (8,875,518 | ) | ||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||||||||||
The accompanying notes are an integral part of the consolidated financial statements.
F-5
DYNAMICS SPECIAL PURPOSE CORP.
CONSOLIDATED STATEMENT OF CASH FLOWS
FOR THE PERIOD FROM MARCH 1, 2021 (INCEPTION) THROUGH DECEMBER 31, 2021
Cash Flows from Operating Activities: | ||||
Net loss | $ | (3,857,088 | ) | |
Adjustments to reconcile net loss to net cash used in operating activities: | ||||
Interest and dividend income on investments held in Trust Account | (8,784 | ) | ||
Changes in operating assets and liabilities: | ||||
Prepaid expenses | (558,556 | ) | ||
Accounts payable and other current liabilities | 39,520 | |||
Accrued professional fees and other expenses | 3,078,822 | |||
Franchise tax payable | 163,839 | |||
|
| |||
Net cash used in operating activities | (1,142,247 | ) | ||
|
| |||
Cash Flows from Investing Activities: | ||||
Cash deposited into Trust Account | (230,000,000 | ) | ||
|
| |||
Net cash used in investing activities | (230,000,000 | ) | ||
|
| |||
Cash Flows from Financing Activities: | ||||
Proceeds from promissory note—related party | 250,000 | |||
Repayment of promissory note—related party | (250,000 | ) | ||
Proceeds from initial public offering, net of underwriting discount paid | 225,400,000 | |||
Proceeds from sale of private placement shares | 7,155,000 | |||
Payment of offering costs | (523,430 | ) | ||
|
| |||
Net cash provided by financing activities | 232,031,570 | |||
|
| |||
Net Change in Cash | 889,323 | |||
Cash—Beginning of period | — | |||
|
| |||
Cash—End of period | $ | 889,323 | ||
|
| |||
Supplemental disclosures of non-cash investing and financing activities: | ||||
Remeasurement of Class A common stock subject to redemption to redemption value | $ | 13,181,867 | ||
|
| |||
Deferred underwriting fee payable | $ | 8,050,000 | ||
|
| |||
Offering costs paid in exchange for issuance of Class B common stock to Sponsor | $ | 25,000 | ||
|
| |||
Waiver of deferred underwriting commissions by underwriter | $ | 1,000,000 | ||
|
|
The accompanying notes are an integral part of the consolidated financial statements.
F-6
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
NOTE 1. DESCRIPTION OF ORGANIZATION AND BUSINESS OPERATIONS
Dynamics Special Purpose Corp. (the “Company”) is a blank check company incorporated in Delaware on March 1, 2021. As used herein, “the Company” refers to Dynamics Special Purpose Corp. and its wholly-owned andcontrolled subsidiary, Explore Merger Sub, Inc. (“Merger Sub”), unless the context indicates otherwise. The Company was formed for the purpose of entering into a merger, capital stock exchange, asset acquisition, stock purchase, reorganization or similar business combination with one or more businesses (a “Business Combination”). The Company is not limited to a particular industry or geographic region for purposes of consummating a Business Combination. The Company is an early stage and emerging growth company and, as such, the Company is subject to all of the risks associated with early stage and emerging growth companies.
As of December 31, 2021, the Company had not commenced any operations. All activity for the period from March 1, 2021 (inception) through December 31, 2021 relates to the Company’s formation, the initial public offering (“Initial Public Offering”), which is described below, and identifying a target company for a Business Combination and negotiating and entering into binding agreements in respect of such Business Combination. The Company will not generate any operating revenues until after the completion of a Business Combination, at the earliest. The Company will generatenon-operatingincome in the form of interest income on the proceeds derived from the Initial Public Offering. The Company has selected December 31 as its fiscal year end.
The registration statement for the Initial Public Offering was declared effective on May 25, 2021. On May 28, 2021, the Company consummated the Initial Public Offering of 23,000,000 shares of Class A common stock (the “Public Shares”), including 3,000,000 shares of Class A common stock that were issued pursuant to the underwriter’s exercise ofitsover-allotment option in full, at $10.00 per Public Share, generating gross proceeds of $230,000,000, which is discussed in Note 3.
Simultaneously with the closing of the Initial Public Offering, the Company consummated the sale of 715,500 shares of Class A common stock (the “Private Placement Shares”) at a price of $10.00 per Private Placement Share in a private placement to Dynamics Sponsor LLC (the “Sponsor”), generating gross proceeds of $7,155,000, which is described in Note 4.
Transaction costs for the Initial Public Offering amounted to $13,198,430 consisting of $4,600,000 of underwriting fees, $8,050,000 of deferred underwriting fees, and $548,430 of other offering costs. Subsequent to the Initial Public Offering, the underwriter agreed on December 17, 2021 to waive $1,000,000 of its deferred underwriting fees of $8,050,000, thereby reducing those fees to $7,050,000; thus, the transaction costs related to our Initial Public Offering amounted to $12,198,430.
Following the closing of the Initial Public Offering on May 28, 2021, an amount of $230,000,000 ($10.00 per Public Share) from the net proceeds of the sale of the Public Shares in the Initial Public Offering and the sale of the Private Placement Shares was placed in a trust account (the “Trust Account”), and will be invested only in U.S. government securities with maturities of 185 days or less,or in money market funds meeting certain conditions under Rule2a-7under the Investment Company Act which invest only in direct U.S. government treasury obligations, as determined by the Company, until the earlier of: (i) the completion of a Business Combination,and (ii) the distribution of the funds held in the Trust Account, as described below.
The Company’s management has broad discretion with respect to the specific application of the net proceeds of the Initial Public Offering and the sale of the Private Placement Shares, although substantially all of the net proceeds are intended to be applied generally toward consummating a Business Combination. There is no assurance that the Company will be able to complete a Business Combination successfully. The Company must
F-7
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
complete a Business Combination with one or more target businesses that together have an aggregate fair market value of at least 80% of the value of the Trust Account (excluding the deferred underwritingfeesand taxes payable on income earned on the Trust Account) at the time of the agreement to enter into an initial Business Combination. The Company will only complete a Business Combination if the post-transaction company owns or acquires 50% or more of the outstanding voting securities of the target or otherwise acquires a controlling interest in the target sufficient for it not to be required to register as an investment company under the Investment Company Act of 1940, as amended (the “Investment Company Act”).
The Company will provide its stockholders with the opportunity to redeem all or a portion of their Public Shares upon the completion of a Business Combination either (i) in connection with a stockholder meeting called to approve the Business Combination or (ii) by means of a tender offer. The decision as to whether the Company will seek stockholder approval of a Business Combination or conduct a tender offer will be made by the Company, solely in its discretion, subject to applicable law and stock exchange listing requirements. The stockholders will be entitled to redeem their Public Shares for a pro rata portion of the amount held in the Trust Account (initially anticipated to be $10.00 per share), calculated as of two business days prior to the completion of a Business Combination, including any pro rata interest earned on the funds held in the Trust Account and not previously released to the Company to pay its tax obligations.
The Company will proceed with a Business Combination if the Company has net tangible assets of at least $5,000,001 upon consummation of such Business Combination and a majority of the shares voted are voted in favor of the Business Combination. If a stockholder vote is not required under applicable law or stock exchange listing requirements and the Company does not decide to hold a stockholder vote for business or other reasons, the Company will, pursuant to its amended and restated certificate of incorporation (the “Amended and Restated Certificate of Incorporation”), conduct the redemptions pursuant to the tender offer rules of the Securities and Exchange Commission (“SEC”), and file tender offer documents with the SEC prior to completing a Business Combination. If the Company seeks stockholder approval in connection with a Business Combination, the holders of the Founder Shares (as defined in Note 5) have agreed to vote their Founder Shares, Private Placement Shares and any Public Shares purchased in or after the Initial Public Offering in favor of approving a Business Combination and to waive their redemption rights with respect to any such shares in connection with a stockholder vote to approve a Business Combination. Additionally, each public stockholder may elect to redeem their Public Shares without voting, and if they do vote, irrespective of whether they vote for or against the proposed Business Combination.
Notwithstanding the foregoing, if the Company seeks stockholder approval of a Business Combination and it does not conduct redemptions pursuant to the tender offer rules, the Company’s Amended and Restated Certificate of Incorporation provides that a public stockholder, together with any affiliate of such stockholder or any other person with whom such stockholder is acting in concert or as a “group” (as defined under Section 13 of the Securities Exchange Act of 1934, as amended (the “Exchange Act”)), will be restricted from redeeming its shares with respect to more than an aggregate of 15% of the Public Shares without the Company’s prior written consent.
The initial stockholders have agreed to waive (a) their redemption rights with respect to any Founder Shares, Private Placement Shares and Public Shares they hold in connection with the completion of an initial Business Combination, (b) their redemption rights with respect to any Founder Shares, Private Placement Shares and Public Shares they hold in connection with a stockholder vote to approve an amendment to the Amended and Restated Certificate of Incorporation to modify the substance or timing of the Company’s obligation to allow redemption in connection with an initial Business Combination or to redeem 100%of the Public Shares if the Company has not consummated an initial Business Combination within 24months from the closing of the Initial
F-8
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
Public Offering or with respect to any material provision relating to the rights of holders of Public Shares, and (c) their rights to liquidating distributions from the Trust Account with respect to any Founder Shares and Private Placement Shares they hold if the Company fails to complete an initial Business Combination within 24 months from the closing of the Initial Public Offering. However, if the initial stockholders acquire Public Shares in or after the Initial Public Offering, such Public Shares will be entitled to liquidating distributions from the Trust Account if the Company fails to complete a Business Combination within the Combination Period (as defined below).
The Company will have until May 28, 2023 to complete a Business Combination (the “Combination Period”). If the Company is unable to complete a Business Combination within the Combination Period, the Company will (i) cease all operations except for the purpose of winding up, (ii) as promptly as reasonably possible but no more than ten business days thereafter, subject to lawfully available funds therefor, redeem the Public Shares at aper-shareprice, payable in cash, equal to the aggregate amount then on deposit in the Trust Account,including interest earned on the funds held in the Trust Account and not previously released to the Company to pay its franchise and income taxes (less up to $100,000 ofinterest to pay dissolution expenses), divided by the number of then-outstanding Public Shares, which redemption will completely extinguish public stockholders’ rights as stockholders (including the right to receive further liquidating distributions, if any), subject to applicable law, and (iii) as promptly as reasonably possible following such redemption, subject to the approval of the Company’s remaining stockholders and board of directors, dissolve and liquidate, subject in each case to the Company’s obligations under Delaware law to provide for claims of creditors and the requirements of other applicable law.
The underwriter has agreed to waive its rights to its deferred underwriting commission (see Note 6) held in the Trust Account in the event the Company does not complete a Business Combination within in the Combination Period and, in such event, such amounts will be included with the other funds held in the Trust Account that will be available to fund the redemption of the Public Shares. In the event of such distribution, it is possible that the per share value of the assets remaining available for distribution will be less than the Initial Public Offering price per Public Share ($10.00).
In order to protect the amounts in the Trust Account, the Sponsor has agreed that it will be liable to the Company if and to the extent any claims by a third party for services rendered or products sold to the Company, or a prospective target business with which the Company has discussed entering into a transaction agreement, reduce the amount of funds in the Trust Account to below (i) $10.00 per Public Share, or (ii) the actual amount per Public Share held in the Trust Account as of the date of the liquidation of the Trust Account, if less than$10.00per Public Share due to reductions in the value of the Trust Account assets, less taxes payable, provided that such liability will not apply to any claims by a third party or prospective target business who executed a waiver of any and all rights to the monies held in the Trust Account (whether or not such waiver is enforceable), nor will it apply to any claims under the Company’s indemnity of the underwriter of the Initial Public Offering against certain liabilities, including liabilities under the Securities Act of 1933, as amended (the “Securities Act”). The Company will seek to reduce the possibility that the Sponsor will have to indemnify the Trust Account due to claims of creditors by endeavoring to have all vendors, service providers (other than the Company’s independent registered accounting firm), prospective target businesses or other entities with which the Company does business, execute agreements with the Company waiving any right, title, interest or claim of any kind in or to monies held in the Trust Account.
Business Combination Agreement
On December 19, 2021, the Company entered into a business combination agreement (the “Business Combination Agreement”) by and among the Company, Merger Sub and Senti Biosciences, Inc., a Delaware
F-9
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
corporation (“Senti”). The Business Combination Agreement provides, among other things, that on the terms and subject to the conditions set forth therein, Merger Sub will merge with and into Senti, with Senti surviving as a wholly-owned subsidiary of the Company (the “Merger”). Upon the closing of the Merger (the “Closing”), the Company will change its name to “Senti Biosciences, Inc.” The date on which the Closing actually occurs is hereinafter referred to as the “Closing Date.”
The Business Combination Agreement and the transactions contemplated thereby are referred to in theseNotes to Consolidated Financial Statementsas the “Senti Business Combination.” The Senti Business Combination was approved by the boards of directors of each of the Company and Senti.
Under the Business Combination Agreement, the Company will acquire all of the outstanding equity interests of Senti in exchange for shares of the Company’s Class A common stock, par value $0.0001 per share (the “Class A Common Stock”), based on an implied Senti equity value of $240,000,000, to be paid to Senti stockholders at the effective time of the Merger (the “Effective Time”). In addition, Senti stockholders will have the right to receive (i) an aggregateof 1,000,000 shares of Class A Common Stock if, after Closing, the volume weighted average price of the Class A Common Stock on the Nasdaq Capital Market (“Nasdaq”), or any other national securities exchange on which the shares of Class A Common Stock are then traded (“VWAP”), is greater thanor equal to $15.00 over any 20 trading days within any consecutive 30 trading day period, in the period that ends on the second anniversary of the Closing, and (ii) an additional 1,000,000 shares of Class A Common Stock in the aggregate if, after Closing, the VWAP of Class A Common Stock is greater than or equal to $20.00 over any 20 trading days within any consecutive 30 trading day period, in the period that ends on the third anniversary of the Closing.
Pursuant to the Business Combination Agreement, at or prior to the Effective Time, each option exercisable for Senti equity that is outstanding immediately prior to the Effective Time shall be assumed by the Company and continue in full force and effect on the same terms and conditions as are currently applicable to such options, subject to adjustments to exercise price and number of shares of Class A Common Stock issued upon exercise.
The parties to the Business Combination Agreement have agreed to customary representations and warranties for transactions of this type. In addition, the parties to the Business Combination Agreement agreed to be bound by certain customary covenants for transactions of this type, including, among others, covenants with respect to the conduct of Senti, the Company and their respective subsidiaries during the period between execution of the Business Combination Agreement and Closing. The representations, warranties, agreements and covenants of the parties set forth in the Business Combination Agreement will terminate at Closing, except for those covenants and agreements that, by their terms, contemplate performance after Closing. Each of the parties to the Business Combination Agreement has agreed to use its reasonable best efforts to take or cause to be taken all actions, and to do or cause to be done all things, reasonably necessary to consummate and expeditiously implement the Merger.
Under the Business Combination Agreement, the obligations of the parties to consummate the Merger are subject to the satisfaction or waiver of certain customary closing conditions of the respective parties, including, without limitation: (i) the approval and adoption of the Business Combination Agreement and transactions contemplated thereby by requisite vote of the Company’s stockholders (the “Company Stockholder Approval”) and Senti’s stockholders (the “Senti Stockholder Approval”); (ii) the expiration or termination of the applicable waiting period under the Hart-Scott-Rodino Antitrust Improvements Act of 1976, as amended; (iii) the absence of a Company Material Adverse Effect or DYNS Material Adverse Effect (each, as defined in the Business Combination Agreement) since the date of the Business Combination Agreement that is continuing; (iv) after giving effect to the transactions contemplated by the Business Combination Agreement, the Company has net
F-10
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
tangible assets of at least $5,000,001 upon consummation of the Merger; (v) the Company’s initial listing application with Nasdaq in connection with the Merger has been approved and, immediately following the Effective Time, the Company has satisfied any applicable initial and continuing listing requirements of Nasdaq and the shares of the Company’s Class A Common Stock have been approved for listing on Nasdaq, subject only to official notice of the issuance thereof; and (vi) the registration statement filed with the SEC on Form S-4 (the “Registration Statement”) has become effective, no stop order has been issued by the SEC and remains in effect with respect to the Registration Statement, and no proceeding seeking such a stop order has been threatened or initiated by the SEC and remains pending. In addition, Senti’s obligation to consummate the Merger is subject to the condition that the Available Closing Cash (as defined in the Business Combination Agreement) shall be greater than or equal to $150,000,000 (after reduction for the aggregate amount of payments made or required to be made in connection with the DYNS Stockholder Redemption (as defined in the Business Combination Agreement)) and the amount of funds available pursuant to the PIPE Financing (as defined in the Business Combination Agreement).
On February 12, 2022, following the period to which these consolidated financial statements relate, the Business Combination Agreement was amended by the parties thereto to reflect, among other things, (i) a correction to section 5.7 of the Business Combination Agreement, and (ii) changes to the options Senti granted to certain persons at the time the Business Combination Agreement was signed.
Other Agreements
The Business Combination Agreement contemplates the execution of various additional agreements and instruments, on or before the Closing, including, among others, the following:
Sponsor Support Agreement
In connection with the execution of the Business Combination Agreement, the Sponsor, as the sole holder of the Company’s Class B common stock, par value$0.0001per share (the “Class B Common Stock”, and also referred to herein as the Founder Shares (as defined in Note 5)) and other persons party thereto (“Other Company Insiders,” and together with the Sponsor, collectively, the “Company Insiders”), entered into a support agreement with the Company and Senti (the “Sponsor Support Agreement”). Under the Sponsor Support Agreement, the Sponsor agreed to vote, at any meeting of the stockholders of the Company and in any action by written consent of the stockholders of the Company, all of such Sponsor’s Class A Common Stock and Class B Common Stock (i) in favor of (a) the Business Combination Agreement and the transactions contemplated thereby, and (b) the other proposals that the Company and Senti agreed in the Business Combination Agreement shall be submitted at such meeting for approval by the Company’s stockholders together with the proposal to obtain the Company Stockholder Approval (together with the Company Stockholder Approval, these proposals are the Required Transaction Proposals (as defined in the Business Combination Agreement)), and (ii) against any proposal that conflicts with, or materially impedes or interferes with, any such proposal or that would adversely affect or delay the Merger. The Sponsor Support Agreement also prohibits the Sponsor from, among other things and subject to certain exceptions, selling, assigning or transferring any Class A Common Stock or Class B Common Stock held by the Sponsor prior to the Closing or taking any action that would have the effect of preventing or materially delaying the Sponsor from performing its obligations under the Sponsor Support Agreement. In addition, in the Sponsor Support Agreement, the Sponsor agreed to waive, and not to assert or perfect, among other things, any rights to adjustment or other anti-dilution protections with respect to the rate at which the shares of Class B Common Stock held by the Sponsor convert into shares of Class A Common Stock in connection with the transactions contemplated by the Business Combination Agreement.
F-11
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
The Sponsor Support Agreement also includes a lock-up in respect of the Sponsor’s equity interests in the Company. Pursuant to the Sponsor Support Agreement, the Sponsor agreed that, subject to limited exceptions, it would not sell, assign or transfer any Class A Common Stock or Class B Common Stock until the earlier of (i) the one year anniversary of the Closing, and (ii) subsequent to the Closing, (x) if the last reported sale price of the Class A Common Stock equals or exceeds $12.00 per share (as adjusted for stock splits, stock dividends, reorganizations, recapitalizations and the like) for any 20 trading days within any 30 consecutive trading day period commencing at least 150 days after the Closing, or (y) the date upon completion of a liquidation, merger, stock exchange, reorganization or other similar transaction that results in all of the public stockholders having the right to exchange their common stock for cash, securities or other property.
Senti Support Agreement
In connection with the execution of the Business Combination Agreement, certain Senti stockholders (the “Senti Supporting Stockholders”) entered into support agreements with the Company (the “Senti Support Agreements”). Under the Senti Support Agreements, each Senti Supporting Stockholder agreed, within forty-eight hoursfollowing the effectiveness of the Registration Statement, to execute and deliver a written consent with respect to all outstanding shares of Senti common stock and preferred stock held by such Senti Supporting Stockholder (the “Subject Senti Shares”) approving the Business Combination Agreement and the transactions contemplated thereby. In addition to the foregoing, each Senti Supporting Stockholder agreed that, at any meeting of the holders of Senti capital stock, each such Senti Supporting Stockholder will appear at the meeting, in person or by proxy, and cause its Subject Senti Shares to be voted (i) to approve and adopt the Business Combination Agreement, the transactions contemplated thereby, and any other matters necessary or reasonably requested by Senti for consummation of the Merger, and (ii) against any proposal that conflicts or materially impedes or interferes with, or would adversely affect or delay, the consummation of the transactions contemplated by the Business Combination Agreement.
The Senti Support Agreement also prohibits the Senti Supporting Stockholders from, among other things, (i) transferring any of the Subject Senti Shares prior to the Closing, (ii) entering into (a) any option, commitment or other arrangement that would require the Senti Supporting Stockholders to transfer the Subject Senti Shares, or (b) any voting trust, proxy or other contract with respect to the voting of the Subject Senti Shares, or (iii) taking any action in furtherance of the foregoing. In addition, under the Senti Support Agreement, each Senti Supporting Stockholder agreed (i) not to exercise any rights of appraisal or dissenter’s rights relating to the Business Combination Agreement and the transactions contemplated thereby, and (ii) not to commence or participate in any claim or action against Senti, the Company or any of their affiliates relating to the negotiation, execution or delivery of the Senti Support Agreement or the Business Combination Agreement or the consummation of the Merger.
Additionally, (i) certain Senti Support Agreements prohibit the applicable Senti Supporting Stockholders from transferring the shares of Class A Common Stock which they will receive in the Merger for, subject to certain permitted transfers, up to 18months following the Closing, which may be reducedto 12months upon the meeting of certain criteria (such period, the “ExtendedLock-Up”),and (ii) certain other Senti Support Agreements prohibit the applicable Senti Supporting Stockholders from transferring the shares of Class A Common Stock which they will receive in the Merger for, subject to certain permitted transfers,12months following the Closing (such period, the “GeneralLock-Up”);provided that, (a) with respect to the ExtendedLock-Up,if the last reported sale price of the Class A Common Stock on Nasdaq, or any other national securities exchange on which the Class A Common Stock is then traded, is greater than or equal to$12.00per share over any20trading days within any consecutive 30trading day commencing at least330days after the Closing Date, then the ExtendedLock-Upshall be deemed to have expired with respect to each stockholder’s Class A Common Stock subject to that lock-up,
F-12
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
and (b) with respect to the GeneralLock-Up,if the last reported sale price of the Class A Common Stock on Nasdaq, or any other national securities exchange on which the Class A Common Stock is then traded, is greater than or equal to$12.00 per share over any 20 trading days within any consecutive 30trading day period commencing at least150days after the Closing Date, then the GeneralLock-Upshall be deemed to have expired with respect to each stockholder’s Class A Common Stock subject to that lock-up.
On February 12, 2022, following the period to which these consolidated financial statements relate, the Company entered into amendments to certain Senti Support Agreements to amend those agreements such that, among other things, the shares of Class A Common Stock of the relevant Senti Supporting Stockholders may not be transferred, subject to certain permitted transfers, for three years following the Closing (such period, “the Three Year Lock-Up”). Unlike the Extended Lock-Up and the General Lock-Up described above, the Three Year Lock-Up does not terminate early based on the share price performance of Class A Common Stock.
PIPE Subscription Agreements
In connection with the execution of the Business Combination Agreement, the Company entered into subscription agreements with certain private investors (the “Subscription Agreements”), pursuant to which, among other things, such investors have subscribed to purchase an aggregate of6,680,000shares of Class A Common Stock (together, the “Subscriptions”) for a purchase priceof $10.00per share, or an aggregate purchase price of $66,800,000, which shares are to be issued at the Closing; provided that the Subscription Agreements permit the Company to accept additional subscriptions for a purchase price of$10.00per share to be issued at the Closing, following the execution of the Business Combination Agreement. The obligations of each party to consummate the Subscriptions are conditioned upon, among other things, customary closing conditions and the consummation of the transactions contemplated by the Business Combination Agreement.
Non-Redemption Agreements
In connection with the execution of the Business Combination Agreement, the Sponsor, as the holder of 5,750,000 shares of Class B Common Stock (the Founder Shares (as defined in Note 5)), the Company and each of Morgan Stanley Investment Management Inc., T. Rowe Price Group, Inc., The Invus Group, LLC and ARK Investment Management LLC and/or their respective investment funds (each, an “Investor”, and collectively, the “Investors”) entered into non-redemption agreements in respect of the Public Shares held by the Investors (the “Non-Redemption Agreements”).
Pursuant to the Non-Redemption Agreements, each Investor agreed for the benefit of the Company (a) to not redeem the shares of Class A Common Stock beneficially owned by it, or any other shares, capital stock or other equity interests, as applicable, of the Company, which it held on the date of the Non-Redemption Agreement, representing 8,691,655 shares of Class A Common Stock, in the aggregate (the “Investor Shares”), and (b) to not, among other things, sell, encumber or otherwise transfer the Investor Shares other than in connection with non-discretionary ETF or mutual fund pro rata rebalancing transfers. In connection with these commitments from the Investors, the Sponsor agreed to forfeit 965,728 shares of its Class B Common Stock and the Company has agreed to cancel such shares and concurrently issue to the Investors an equivalent number of shares of Class A Common Stock, in each case, at or promptly following the consummation of the Merger.
Investor Rights Agreement
In connection with the Closing, the Company, certain stockholders of the Company (including the Sponsor) and certain stockholders of Senti will enter into an investor rights and lock-up agreement (the “Investor Rights Agreement”). Pursuant to the Investor Rights Agreement, each signatory thereto (other than the Company) will be granted certain registration rights with respect to their respective shares of Class A Common Stock.
F-13
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
The Investor Rights Agreement will also restrict the ability of each stockholder who is a party thereto (other than the Company) to transfer its shares of Class A Common Stock (or any securities convertible into or exercisable or exchangeable for shares of Class A Common Stock) for, subject to certain permitted transfers and depending on the stockholder, a period of one year following the Closing Date (the “12 Month Lock-Up”) or a period of 18 months following the Closing Date (the “18 Month Lock-Up”); provided that (i) the foregoing restrictions shall not apply to any shares of Class A Common Stock purchased pursuant to the Subscription Agreements and (ii)(A) in respect of the 12 Month Lock-Up, if the last reported sale price of the Class A Common Stock on Nasdaq, or any other national securities exchange on which the Class A Common Stock is then traded, is greater than or equal to $12.00 per share over any 20 trading days within any consecutive 30 trading day period commencing at least 150 days after the Closing Date, then the 12 Month Lock-Up shall be deemed to have expired with respect to each stockholder’s Class A Common Stock subject to that lock-up; and (B) in respect of the 18 Month Lock-Up, if the last reported sale price of the Class A Common Stock on Nasdaq, or any other national securities exchange on which the Class A Common Stock is then traded, is greater than or equal to $12.00 per share over any 20 trading days within any consecutive 30 trading day period commencing at least 330 days after the Closing Date, then the 18 Month Lock-Up shall be deemed to have expired with respect to each stockholder’s Class A Common Stock subject to that lock-up.
Going Concern
As of December 31, 2021, the Company had $889,323 in cash held outside of the Trust Account and a working capital deficit of $1,984,816. The Company has incurred and expects to continue to incur significant costs in pursuit of its acquisition plans (including in respect of the Senti Business Combination). These conditions raise substantial doubt about the Company’s ability to continue as a going concern for a period of time within one year after the date that the consolidated financial statements are issued. Management plans to address this uncertainty through the Senti Business Combination, as discussed above. There is no assurance that the Company’s plans to consummate the Senti Business Combination (or any other Business Combination) will be successful or successful within the Combination Period. The consolidated financial statements do not include any adjustments that might result from the outcome of this uncertainty.
Risks and Uncertainties
Management continues to evaluate the impact of the COVID-19 pandemic on the industry and has concluded that while it is reasonably possible that the virus could have a negative effect on the Company’s financial position, results of its operations, and/or search for a target company, the specific impact is not readily determinable as of the date of these consolidated financial statements. The consolidated financial statements do not include any adjustments that might result from the outcome of this uncertainty.
NOTE 2. SUMMARY OF SIGNIFICANT ACCOUNTING POLICIES
Principles of Consolidation and Financial Statement Presentation
The accompanying consolidated financial statements of the Company are presented in conformity with accounting principles generally accepted in the United States of America (“GAAP”) and pursuant to the rules and regulations of the SEC.
The consolidated financial statements include the accounts of the Company and its wholly-owned and controlled subsidiary, Merger Sub, after elimination of any intercompany transactions and balances as of December 31, 2021.
F-14
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
Emerging Growth Company
The Company is an “emerging growth company,” as defined in Section 2(a) of the Securities Act, as modified by the Jumpstart Our Business Startups Act of 2012 (the “JOBS Act”), and it may take advantage of certain exemptions from various reporting requirements that are applicable to other public companies that are not emerging growth companies including, but not limited to, not being required to comply with the independent registered public accounting firm attestation requirements of Section 404 of the Sarbanes-Oxley Act, reduced disclosure obligations regarding executive compensation in its periodic reports and proxy statements, and exemptions from the requirements of holding a nonbinding advisory vote on executive compensation and stockholder approval of any golden parachute payments not previously approved.
Further, Section 102(b)(1) of the JOBS Act exempts emerging growth companies from being required to comply with new or revised financial accounting standards until private companies (that is, those that have not had a Securities Act registration statement declared effective or do not have a class of securities registered under the Exchange Act) are required to comply with the new or revised financial accounting standards. The JOBS Act provides that a company can elect to opt out of the extended transition period and comply with the requirements that apply to non-emerging growth companies but any such election to opt out is irrevocable. The Company has elected not to opt out of such extended transition period which means that when a standard is issued or revised and it has different application dates for public or private companies, the Company, as an emerging growth company, can adopt the new or revised standard at the time private companies adopt the new or revised standard. This may make comparison of the Company’s consolidated financial statements with another public company which is neither an emerging growth company nor an emerging growth company which has opted out of using the extended transition period difficult or impossible because of the potential differences in accounting standards used.
Use of Estimates
The preparation of consolidated financial statements in conformity with U.S. GAAP requires the Company’s management to make estimates and assumptions that affect the reported amounts of assets and liabilities and disclosure of contingent assets and liabilities at the date of the consolidated financial statements and the reported amounts of expenses during the reporting period.
Making estimates requires management to exercise significant judgment. It is at least reasonably possible that the estimate of the effect of a condition, situation or set of circumstances that existed at the date of the consolidated financial statements, which management considered in formulating its estimate, could change in the near term due to one or more future confirming events. Accordingly, the actual results could differ from those estimates.
Cash and Cash Equivalents
The Company considers all short-term investments with an original maturity of three months or less when purchased to be cash equivalents. The Company did not have any cash equivalents as of December 31, 2021. As of December 31, 2021, we had operating cash (i.e. cash held outside the Trust Account) of $889,323.
Investments Held in Trust Account
As of December 31, 2021, the assets held in the Trust Account were comprised of U.S. government securities, within the meaning set forth in Section 2(a) (16) of the Investment Company Act, with maturities of 185 days or less, or investments in money market funds that invest in U.S. government securities and generally have a readily determinable fair value, or a combination thereof. When the Company’s investments held in the Trust Account
F-15
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
are comprised of U.S. government securities, the investments are classified as trading securities. When the Company’s investments held in the Trust Account are comprised of money market funds, the investments are recognized at fair value. Trading securities and investments in money market funds are presented on the consolidated balance sheet at fair value at the end of each reporting period. Gains and losses resulting from the change in fair value of these securities are reported in the statements of operations. The estimated fair values of investments held in the Trust Account are determined using available market information.
Class A Common Stock Subject to Possible Redemption
The Public Shares sold in the Initial Public Offering contain a redemption feature which allows for the redemption of such Public Shares in connection with the Company’s liquidation, if there is a stockholder vote or tender offer in connection with the Business Combination and in connection with certain amendments to the Company’s Amended and Restated Certificate of Incorporation. In accordance with SEC and its staff’s guidance on redeemable equity instruments, which has been codified in Accounting Standards Codification (“ASC”) Topic 480, Distinguishing Liabilities from Equity, redemption provisions not solely within the control of the Company require common stock subject to redemption to be classified outside of permanent equity. Therefore, all Class A Common Stock has been classified outside of permanent equity.
The Company recognizes changes in redemption value immediately as they occur and adjusts the carrying value of redeemable common stock to equal the redemption value at the end of each reporting period. Increases or decreases in the carrying amount of redeemable common stock are affected by charges against additional paid in capital and accumulated deficit.
As of December 31, 2021, the Investor Shares (see Note 1) are classified as temporary equity within Class A Common Stock subject to redemption in the Company’s consolidated balance sheet. The Non-Redemption Agreements are terminated in the event that the Business Combination Agreement as described above is terminated. As such, the Company determined that the Non-Redemption Agreements are contingent upon the successful completion of the Senti Business Combination. In the event that the Senti Business Combination is not successful, the Non-Redemption Agreements are terminated, and the Investors would again have the right to redeem the Investor Shares. As such, the Company determined that the Non-Redemption Agreements would not change the nature of the underlying shares as redeemable.
As of December 31, 2021, the Class A Common Stock subject to redemption reflected in the consolidated balance sheet is reconciled in the following table:
Gross proceeds | $ | 230,000,000 | ||
Less: | ||||
Issuance costs allocated to Class A Common Stock | (13,181,867 | ) | ||
Plus: | ||||
Remeasurement of carrying value to redemption value | 13,181,867 | |||
|
| |||
Class A Common Stock subject to possible redemption | $ | 230,000,000 | ||
|
|
Offering Costs Associated with the Initial Public Offering
The Company complies with the requirements of ASC 340-10-S99-1 and SEC Staff Accounting Bulletin Topic 5A—Expenses of Offering. Offering costs consist principally of professional and registration fees incurred
F-16
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
related to the Initial Public Offering. Offering costs directly attributable to the issuance of an equity contract to be classified in equity are recorded as a reduction in equity. Offering costs for equity contracts that are classified as assets and liabilities are expensed immediately. The Company incurred offering costs amounting to $13,198,430 as a result of the Initial Public Offering (consisting of a $4,600,000 underwriting fee, $8,050,000 of deferred underwriting fees, and $548,430 of other offering costs). The Company recorded $13,181,867 of offering costs as a reduction of temporary equity in connection with the issuance of the Public Shares. The Company recorded $16,563 of offering costs as a reduction of permanent equity in connection with the issuance of the Private Placement Shares.
Income Taxes
The Company follows the asset and liability method of accounting for income taxes under ASC Topic 740, Income Taxes (“ASC 740”). Deferred tax assets and liabilities are recognized for the estimated future tax consequences attributable to differences between the consolidated financial statements carrying amounts of existing assets and liabilities and their respective tax bases. Deferred tax assets and liabilities are measured using enacted tax rates expected to apply to taxable income in the years in which those temporary differences are expected to be recovered or settled. The effect on deferred tax assets and liabilities of a change in tax rates is recognized in income in the period that included the enactment date. Valuation allowances are established, when necessary, to reduce deferred tax assets to the amount expected to be realized.
ASC 740 prescribes a recognition threshold and a measurement attribute for the financial statement recognition and measurement of tax positions taken or expected to be taken in a tax return. For those benefits to be recognized, a tax position must be more likely than not to be sustained upon examination by taxing authorities. The Company recognizes accrued interest and penalties related to unrecognized tax benefits as income tax expense. There were no unrecognized tax benefits and no amounts accrued for interest and penalties as of December 31, 2021. The Company is currently not aware of any issues under review that could result in significant payments, accruals or material deviation from its position. The Company is subject to income tax examinations by major taxing authorities since inception.
Net Loss Per Share of Common Stock
Net loss per common share is computed by dividing net loss by the weighted-average number of shares of common stock outstanding during the period. As the Public Shares are considered to be redeemable at fair value, and a redemption at fair value does not amount to a distribution different than other stockholders, Class A Common Stock and Class B Common Stock are presented as one class of stock in calculating net loss per share. As a result, the calculated net loss per share is the same for Class A Common Stock and Class B Common Stock. As of December 31, 2021, the Company did not have any dilutive securities and other contracts that could, potentially, be exercised or converted into shares of common stock and then share in the earnings of the Company. As a result, diluted loss per share is the same as basic loss per share for the periods presented.
F-17
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
The following table reflects the calculation of basic and diluted net loss per common share (in dollars, except per share amounts):
| For the Period from March 1, 2021 (Inception) Through December 31, 2021 | ||||||||
| Class A | Class B | |||||||
Basic and diluted net loss per share: | ||||||||
Numerator: | ||||||||
Net loss | $ | (2,919,481 | ) | $ | (937,607 | ) | ||
|
|
|
| |||||
Denominator: | ||||||||
Basic and diluted weighted average shares outstanding | 16,872,995 | 5,418,853 | ||||||
Basic and diluted net loss per share | $ | (0.17 | ) | $ | (0.17 | ) | ||
Concentration of Credit Risk
Financial instruments that potentially subject the Company to concentrations of credit risk consist of a cash account in a financial institution, which, at times, may exceed the Federal Depository Insurance Coverage of $250,000. The Company has not experienced losses on this account and management believes the Company is not exposed to significant risks on such account.
Fair Value of Financial Instruments
The Company applies ASC Topic 820, Fair Value Measurement (“ASC 820”), which establishes a framework for measuring fair value and clarifies the definition of fair value within that framework. ASC 820 defines fair value as an exit price, which is the price that would be received for an asset or paid to transfer a liability in the Company’s principal or most advantageous market in an orderly transaction between market participants on the measurement date. The fair value hierarchy established in ASC 820 generally requires an entity to maximize the use of observable inputs and minimize the use of unobservable inputs when measuring fair value. Observable inputs reflect the assumptions that market participants would use in pricing the asset or liability and are developed based on market data obtained from sources independent of the reporting entity. Unobservable inputs reflect the entity’s own assumptions based on market data and the entity’s judgments about the assumptions that market participants would use in pricing the asset or liability and are to be developed based on the best information available in the circumstances.
The carrying amounts reflected in the consolidated balance sheet for current assets and current liabilities approximate fair value due to their short-term nature.
Level 1 — Assets and liabilities with unadjusted, quoted prices listed on active market exchanges. Inputs to the fair value measurement are observable inputs, such as quoted prices in active markets for identical assets or liabilities.
Level 2 — Inputs to the fair value measurement are determined using prices for recently traded assets and liabilities with similar underlying terms, as well as direct or indirect observable inputs, such as interest rates and yield curves that are observable at commonly quoted intervals.
Level 3 — Inputs to the fair value measurement are unobservable inputs, such as estimates, assumptions, and valuation techniques when little or no market data exists for the assets or liabilities.
See Note 9 for additional information on assets and liabilities measured at fair value.
F-18
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
Recent Accounting Standards
In August 2020, the Financial Accounting Standards Board (“FASB”) issued Accounting Standards Update (“ASU”) 2020-06, Debt — Debt with Conversion and Other Options (Subtopic 470-20) and Derivatives and Hedging — Contracts in Entity’s Own Equity (Subtopic 815-40) (“ASU 2020-06”) to simplify accounting for certain financial instruments. ASU 2020-06 eliminates the current models that require separation of beneficial conversion and cash conversion features from convertible instruments and simplifies the derivative scope exception guidance pertaining to equity classification of contracts in an entity’s own equity. The new standard also introduces additional disclosures for convertible debt and freestanding instruments that are indexed to and settled in an entity’s own equity. ASU 2020-06 amends the diluted earnings per share guidance, including the requirement to use the if-converted method for all convertible instruments. ASU 2020-06 is effective January 1, 2022 and should be applied on a full or modified retrospective basis, with early adoption permitted beginning on January 1, 2021. The Company adopted ASU 2020-06 effective January 1, 2021 using the modified retrospective method of transition. The adoption of ASU 2020-06 did not have a material impact on the consolidated financial statements for the fiscal year ended December 31, 2021.
Management does not believe that any other recently issued, but not yet effective, accounting standards, if currently adopted, would have a material effect on the Company’s consolidated financial statements.
NOTE 3. INITIAL PUBLIC OFFERING
The registration statement for the Company’s Initial Public Offering was declared effective on May 25, 2021. On May 28, 2021, the Company completed its Initial Public Offering of 23,000,000 shares of Class A Common Stock, including 3,000,000 shares of Class A Common Stock that were issued pursuant to the underwriter’s exercise of its over-allotment option in full, at $10.00 per Public Share, generating gross proceeds of $230,000,000.
NOTE 4. PRIVATE PLACEMENT
Simultaneously with the closing of the Initial Public Offering, the Sponsor purchased an aggregate of 715,500 Private Placement Shares at a price of $10.00 per Private Placement Share, generating gross proceeds of $7,155,000. A portion of the proceeds from the sale of the Private Placement Shares was added to the net proceeds from the Initial Public Offering held in the Trust Account. If the Company does not complete a Business Combination within the Combination Period, the proceeds from the sale of the Private Placement Shares held in the Trust Account will be used to fund the redemption of the Public Shares (subject to the requirements of applicable law).
NOTE 5. RELATED PARTY TRANSACTIONS
Founder Shares
On March 8, 2021, the Sponsor was issued 5,750,000 shares (the “Founder Shares”) of Class B Common Stock for an aggregate price of $25,000. The Founder Shares included an aggregate of up to 750,000 shares of Class B Common Stock subject to forfeiture by the Sponsor to the extent that the underwriter’s over-allotment option was not exercised in full or in part, so that the Sponsor would own, on an as-converted basis, 20% of the Company’s issued and outstanding shares after the Initial Public Offering (excluding the Private Placement Shares) (assuming the Sponsor did not purchase any Public Shares in the Initial Public Offering, which it did not). The underwriter fully exercised the over-allotment option on May 28, 2021; thus, these 750,000 Founder Shares are no longer subject to forfeiture.
F-19
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
In connection with the Non-Redemption Agreements (see Note 1), the Sponsor has agreed to forfeit 965,728 Founder Shares and the Company has agreed to cancel such Founder Shares and concurrently issue to the Investors an equivalent number of shares of Class A Common Stock, in each case, at or promptly following the consummation of the Merger. The Company evaluated the forfeiture and cancellation of the Founder Shares by the Sponsor and concurrent issuance of an equivalent number of shares of Class A Common Stock to the Investors in accordance with Staff Accounting Bulletin Topic5A. The forfeiture and cancellation of the Founder Shares by the Sponsor and concurrent issuance of an equivalent number of shares of Class A Common Stock to the Investors has not been transacted as of December 31, 2021 and will not occur until at or promptly following the consummation of the Merger. As such, any expense associated with the issuance of the shares of Class A Common Stock to the Investors would be recognized at the date of issuance (i.e., upon consummation of the Merger).
Promissory Note—Related Party
On March 8, 2021, the Company issued an unsecured promissory note to the Sponsor (the “Promissory Note”), pursuant to which the Company could borrow an aggregate of up to $300,000 to cover expenses related to the Initial Public Offering. The Promissory Note was non-interest bearing and was payable on the earlier of December 31, 2021 or the consummation of the Initial Public Offering. In April 2021, the Company borrowed $250,000 under the Promissory Note which was repaid in full on May 26, 2021.
Related Party Loans
In addition, in order to finance transaction costs in connection with a Business Combination, the Sponsor or an affiliate of the Sponsor, or certain of the Company’s officers and directors may, but are not obligated to, loan the Company funds as may be required (“Working Capital Loans”). If the Company completes a Business Combination, the Company would repay the Working Capital Loans out of the proceeds held in the Trust Account released to the Company. Otherwise, the Working Capital Loans would be repaid only out of funds held outside the Trust Account. In the event that a Business Combination is not completed, the Company may use a portion of the proceeds held outside the Trust Account to repay the Working Capital Loans, but no proceeds held in the Trust Account would be used to repay the Working Capital Loans. Except for the foregoing, the terms of such Working Capital Loans, if any, have not been determined and no written agreements exist with respect to such loans. Up to $2,000,000 of such Working Capital Loans may be convertible into shares at a price of $10.00 per share at the option of the lender. The shares would be identical to the Private Placement Shares.
Administrative Support Agreement
The Company entered into an agreement, commencing on the effective date of the Initial Public Offering, to pay the Sponsor up to a total of $10,000 per month for office space, administrative and support services. Upon the completion of an initial Business Combination, the Company will cease paying these monthly fees (if any). To date, the Company has not exercised its option to use such services.
NOTE 6. COMMITMENTS AND CONTINGENCIES
Registration Rights
The holders of the Founder Shares, Private Placement Shares and any Class A Common Stock issuable upon conversion of any Working Capital Loans have registration rights pursuant to a registration and stockholder rights agreement signed in connection with our Initial Public Offering. The holders of these securities are entitled
F-20
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
to make up to three demands, excluding short form demands, that the Company register such securities. In addition, the holders have certain “piggy-back” registration rights with respect to registration statements filed subsequent to the completion of an initial Business Combination. The Company will bear the expenses incurred in connection with the filing of any such registration statements.
In addition, it is anticipated that each signatory to the Investor Rights Agreement (see Note 1), other than the Company, will be granted certain registration rights with respect to their respective shares of Class A Common Stock when that agreement is signed (which is expected to occur at Closing).
Underwriting Agreement
The Company granted the underwriter of its Initial Public Offering a 45-day option to purchase up to 3,000,000 additional shares of Class A Common Stock to cover over-allotments at the Initial Public Offering price, less the underwriting discounts and commissions. The underwriter exercised the over-allotment option in full on May 28, 2021.
The underwriter was paid a cash underwriting fee of $0.20 per share, or $4,600,000 in the aggregate, upon the closing of the Initial Public Offering. In addition, $0.35 per share, or $8,050,000 in the aggregate was payable to the underwriter for deferred underwriting commissions. On December 17, 2021, the underwriter agreed to waive its right to $1,000,000 of the fee payable by the Company for deferred underwriting commissions. The waived fee was recorded to accumulated deficit. The revised deferred underwriting fee of $7,050,000 will become payable to the underwriter from the amount held in the Trust Account solely in the event that the Company completes a Business Combination, subject to the terms of the underwriting agreement.
Financial Advisor Agreement
On December 16, 2021, the Company entered into an agreement (the “Financial Advisor Agreement”) with Morgan Stanley & Co. LLC (“Morgan Stanley”) for financial advisory services in connection with the Senti Business Combination, which services Morgan Stanley had been engaged to provide, and which services Morgan Stanley had provided, since August 4, 2021. The Financial Advisor Agreement shall terminate automatically on December 16, 2022 unless terminated earlier, with or without cause, by either the Company or Morgan Stanley. The Company will pay Morgan Stanley a fee of $1,000,000 upon the consummation of our proposed initial business combination with Senti.
Placement Agent Agreement
On September 21, 2021, the Company entered into an agreement (the “Placement Agent Agreement”) with Morgan Stanley, J.P. Morgan Securities LLC and BofA Securities, Inc. (together, the “Placement Agents”) for services in connection with the placement of shares of our Class A Common Stock to certain private investors which is anticipated to occur concurrently with the completion the Senti Business Combination (i.e. the Subscriptions – see Note 1). The Placement Agent Agreement shall terminate automatically on August 28, 2022 unless terminated earlier, with or without cause, by either the Company or any Placement Agent (as to itself only). The Company will pay to the Placement Agents a total fee equal to 4.0% of the aggregate price at which the shares of our Class A Common Stock are sold to the private investors in the Subscriptions, which fee shall be payable upon the consummation of the placement of the shares. Each of the Placement Agents will receive 33.3% of the fee.
F-21
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
Business Combination Agreement
As set forth in “Part I, Item 1. Business” of this Report, we have entered into the Business Combination Agreement with Merger Sub and Senti pursuant to which, among other things, Merger Sub will merge with and into Senti, with Senti surviving as a wholly-owned subsidiary of the Company. We have also entered into various ancillary transaction documents to give effect to the Merger, which are described throughout this Report.
NOTE 7. STOCKHOLDERS’ DEFICIT
Preferred stock — The Company is authorized to issue 1,000,000 shares of preferred stock with a par value of $0.0001 per share with such designations, voting and other rights and preferences as may be determined from time to time by the Company’s board of directors. As of December 31, 2021, there were no shares of preferred stock issued or outstanding.
Class A Common Stock — The Company is authorized to issue 100,000,000 shares of Class A Common Stockwith a par value of $0.0001 per share. Holders of Class A Common Stockare entitled to one vote for each share. As of December 31, 2021, there were 23,715,500 shares of Class A Common Stock issued and outstanding, including 23,000,000 shares of Class A common stock subject to possible redemption. Despite the Non-Redemption Agreements discussed in Note 1, it is possible, in certain limited circumstances, for the Investors to transfer their Public Shares, and a transfer of such shares to a third party who is not bound by a Non-Redemption Agreement would render such shares subject to possible redemption.
Class B Common Stock — The Company is authorized to issue 10,000,000 shares of Class B Common Stock with a par value of $0.0001 per share. Holders of Class B Common Stock are entitled to one vote for each share. As of December 31, 2021, there were 5,750,000 shares of Class BCommon Stock issued and outstanding. Of the 5,750,000 shares of Class B Common Stock initially issued and outstanding, up to 750,000 shares were subject to forfeiture to the Company by the Sponsor for no consideration to the extent that the underwriter’s over-allotment option was not exercised in full or in part, so that the initial stockholders would collectively own 20% of the Company’s issued and outstanding common stock after the Initial Public Offering (excluding the Private Placement Shares). The over-allotment option was exercised in full on May 28, 2021; thus, these shares are no longer subject to forfeiture.
Common stockholders of record are entitled to one vote for each share held on all matters to be voted on by stockholders. Holders of the Class A Common Stock and holders of the Class B Common Stock will vote together as a single class on all matters submitted to a vote of stockholders, including any vote in connection with an initial Business Combination, except where a vote of each class is required by law.
The shares of Class B Common Stock are convertible into shares of Class A Common Stock at the option of the holder and will automatically convert into shares of Class A Common Stock at the time of an initial Business Combination on a one-for-one basis (subject to adjustment for stock splits, stock dividends, reorganizations, recapitalizations and the like). In the case that additional shares of Class A Common Stock, or equity-linked securities, are issued or deemed issued in excess of the amounts offered in the Initial Public Offering and related to the closing of an initial Business Combination, the ratio at which shares of Class B Common Stock shall convert into shares of Class A Common Stock will be adjusted (unless the holders of a majority of the outstanding shares of Class B Common Stock agree to waive such adjustment with respect to any such issuance or deemed issuance, as is the case for the proposed Senti Business Combination) so that the number of shares of Class A Common Stock issuable upon conversion of all shares of Class B Common Stock will equal, in the aggregate, on an as-converted basis, 20% of the sum of (i) the total number of all shares of common stock
F-22
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
outstanding upon the completion of the Initial Public Offering (excluding the Private Placement Shares), plus (ii) all shares of Class A Common Stock and equity-linked securities issued or deemed issued in connection with an initial Business Combination (excluding any shares of Class A Common Stock or equity-linked securities issued, or to be issued, to any seller in an initial Business Combination and any Private Placement Shares issued to the Sponsor or its affiliates upon conversion of any Working Capital Loans).
NOTE 8. INCOME TAX
The Company’s net deferred tax assets (liabilities) as of December 31, 2021 is as follows:
Deferred tax assets: | ||||
Start-upcosts | $ | 551,466 | ||
Net operating loss carryforwards | 32,562 | |||
|
| |||
Total deferred tax assets | 584,028 | |||
Valuation allowance | (584,028 | ) | ||
|
| |||
Deferred tax assets, net of allowance | $ | 0 | ||
|
|
The income tax provision for the period from March 1, 2021 (inception) through December 31, 2021 consists of the following:
Federal | ||||
Current | $ | 0 | ||
Deferred | (584,028 | ) | ||
State | ||||
Current | 0 | |||
Deferred | 0 | |||
Change in valuation allowance | 584,028 | |||
|
| |||
Income tax provision | $ | 0 | ||
|
|
As of December 31, 2021, the Company has available U.S. federal operating loss carry forwards of approximately $155,000 that may be carried forward indefinitely.
In assessing the realization of deferred tax assets, management considers whether it is more likely than not that some portion or all of the deferred tax assets will not be realized. The ultimate realization of deferred tax assets is dependent upon the generation of future taxable income during the periods in which temporary differences representing future deductible amounts become deductible. Management considers the scheduled reversal of deferred tax assets, projected future taxable income and tax planning strategies in making this assessment. After consideration of all the information available, management believes that significant uncertainty exists with respect to future realization of the deferred tax assets and has therefore established a full valuation allowance. For the period ended December 31, 2021, the valuation allowance was $584,028.
F-23
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO CONSOLIDATED FINANCIAL STATEMENTS
DECEMBER 31, 2021
A reconciliation of the federal income tax rate to the Company’s effective tax rate as of December 31, 2021 is as follows:
Statutory federal income tax rate | 21.0 | % | ||
State taxes, net of federal tax benefit | 0.0 | % | ||
Other | 0.0 | % | ||
Change in valuation allowance | (15.1 | )% | ||
Business Combination transaction costs | (5.9 | )% | ||
|
| |||
Income tax provision | 0.0 | % | ||
|
|
The Company’s effective tax rates for the period presented differ from the expected (statutory) rates due to the recording of full valuation allowances on deferred tax assets and permanent differences.
The Company files income tax returns in the U.S. federal jurisdiction and California which remain open and subject to examination.
NOTE 9. FAIR VALUE MEASUREMENTS
The following table presents information about the Company’s financial assets that are measured at fair value on a recurring basis as of December 31, 2021, and indicates the fair value hierarchy of the valuation inputs the Company utilized to determine such fair value:
| Description | Amount at Fair Value | Level 1 | Level 2 | Level 3 | ||||||||||||||||
December 31, 2021 | ||||||||||||||||||||
Assets | ||||||||||||||||||||
Investments held in Trust Account: | ||||||||||||||||||||
U.S. Treasury Securities | $ | 230,008,784 | $ | 230,008,784 | $ | 0 | $ | 0 | ||||||||||||
NOTE 10. SUBSEQUENT EVENTS
The Company evaluated subsequent events and transactions that occurred after the consolidated balance sheet date up to the date that the consolidated financial statements were issued. Based upon this review, other than the amendments to the Business Combination Agreement and Senti Support Agreements as discussed in Note 1, the Company did not identify any subsequent events that would have required adjustment or disclosure in the consolidated financial statements.
F-24
DYNAMICS SPECIAL PURPOSE CORP.
CONDENSED CONSOLIDATED BALANCE SHEETS
| March 31, 2022 | December 31, 2021 | |||||||
| (Unaudited) | ||||||||
ASSETS | ||||||||
Current assets: | ||||||||
Cash | $ | 396,693 | $ | 889,323 | ||||
Prepaid expenses and other current assets | 430,459 | 408,042 | ||||||
|
|
|
| |||||
Total current assets | 827,152 | 1,297,365 | ||||||
Prepaid expenses - noncurrent | 56,764 | 150,514 | ||||||
Investments held in Trust Account | 230,031,946 | 230,008,784 | ||||||
|
|
|
| |||||
TOTAL ASSETS | $ | 230,915,862 | $ | 231,456,663 | ||||
|
|
|
| |||||
LIABILITIES AND STOCKHOLDERS’ DEFICIT | ||||||||
Current liabilities: | ||||||||
Accounts payable and other current liabilities | $ | 32,861 | $ | 39,520 | ||||
Accrued professional fees and other expenses | 3,968,324 | 3,078,822 | ||||||
Franchise tax payable | 50,044 | 163,839 | ||||||
|
|
|
| |||||
Total current liabilities | 4,051,229 | 3,282,181 | ||||||
Deferred underwriting fee payable | 7,050,000 | 7,050,000 | ||||||
|
|
|
| |||||
Total Liabilities | 11,101,229 | 10,332,181 | ||||||
|
|
|
| |||||
Commitments and Contingencies (Note 6) | ||||||||
Class A common stock subject to possible redemption, 23,000,000 shares at redemption value (assumed to be $10.00 per share) | 230,000,000 | 230,000,000 | ||||||
Stockholders’ Deficit | ||||||||
Preferred stock, $0.0001 par value; 1,000,000 shares authorized; none issued and outstanding | — | — | ||||||
Class A common stock, $0.0001 par value; 100,000,000 shares authorized; 23,715,500 shares issued; 715,500 shares outstanding (excluding 23,000,000 shares subject to possible redemption) | 72 | 72 | ||||||
Class B common stock, $0.0001 par value; 10,000,000 shares authorized; 5,750,000 shares issued and outstanding | 575 | 575 | ||||||
Additional paid-in capital | — | — | ||||||
Accumulated deficit | (10,186,014 | ) | (8,876,165 | ) | ||||
|
|
|
| |||||
Total Stockholders’ Deficit | (10,185,367 | ) | (8,875,518 | ) | ||||
|
|
|
| |||||
TOTAL LIABILITIES AND STOCKHOLDERS’ DEFICIT | $ | 230,915,862 | $ | 231,456,663 | ||||
|
|
|
| |||||
The accompanying notes are an integral part of the unaudited condensed consolidated financial statements.
F-25
DYNAMICS SPECIAL PURPOSE CORP.
CONDENSED CONSOLIDATED STATEMENTS OF OPERATIONS
(UNAUDITED)
| Three Months Ended March 31, 2022 | For the Period from March 1, 2021 (Inception) Through March 31, 2021 | |||||||
Professional fees and other expenses | $ | 1,282,742 | $ | — | ||||
Franchise tax expense | 50,269 | — | ||||||
Operating and formation costs | — | 1,178 | ||||||
|
|
|
| |||||
Loss from operations | (1,333,011 | ) | (1,178 | ) | ||||
Interest and dividend income on investments held in Trust Account | 23,162 | — | ||||||
|
|
|
| |||||
Net loss | $ | (1,309,849 | ) | $ | (1,178 | ) | ||
|
|
|
| |||||
Basic and diluted weighted average shares outstanding, Class A common stock | 23,715,500 | — | ||||||
|
|
|
| |||||
Basic and diluted net loss per share, Class A common stock | $ | (0.04 | ) | $ | — | |||
|
|
|
| |||||
Basic and diluted weighted average shares outstanding, Class B common stock(1) | 5,750,000 | 5,000,000 | ||||||
|
|
|
| |||||
Basic and diluted net loss per share, Class B common stock | $ | (0.04 | ) | $ | (0.00 | ) | ||
|
|
|
| |||||
| (1) | The period from March 1, 2021 (inception) through March 31, 2021 excludes up to 750,000 shares of Class B common stock which were subject to forfeiture if the over-allotment option was not exercised in full or in part by the underwriter. The over-allotment option was exercised in full on May 28, 2021; thus, these shares are no longer subject to forfeiture (see Notes 5 and 7). |
The accompanying notes are an integral part of the unaudited condensed consolidated financial statements.
F-26
| (1) | The period from March 1, 2021 (inception) through March 31, 2021 includes up to 750,000 shares of Class B common stock which were subject to forfeiture if the over-allotment option was not exercised in full or in part by the underwriter. The over-allotment option was exercised in full on May 28, 2021; thus, these shares are no longer subject to forfeiture (see Notes 5 and 7). |
The accompanying notes are an integral part of the unaudited condensed consolidated financial statements.
F-27
DYNAMICS SPECIAL PURPOSE CORP.
CONDENSED CONSOLIDATED STATEMENTS OF CASH FLOWS
(UNAUDITED)
| Three Months Ended March 31, 2022 | For the Period from March 1, 2021 (Inception) Through March 31, 2021 | |||||||
Cash Flows from Operating Activities: | ||||||||
Net loss | $ | (1,309,849 | ) | $ | (1,178 | ) | ||
Adjustments to reconcile net loss to net cash used in operating activities: | ||||||||
Interest and dividend income on investments held in Trust Account | (23,162 | ) | — | |||||
Payment of operating and formation costs by related party | — | 150 | ||||||
Changes in operating assets and liabilities: | ||||||||
Prepaid expenses and other current assets | 71,333 | — | ||||||
Accounts payable and other current liabilities | (6,659 | ) | 1,028 | |||||
Accrued professional fees and other expenses | 889,502 | — | ||||||
Franchise tax payable | (113,795 | ) | — | |||||
|
|
|
| |||||
Net cash used in operating activities | (492,630 | ) | — | |||||
|
|
|
| |||||
Net Change in Cash | (492,630 | ) | — | |||||
Cash - Beginning of period | 889,323 | — | ||||||
|
|
|
| |||||
Cash - End of period | $ | 396,693 | $ | — | ||||
|
|
|
| |||||
Supplemental disclosures of non-cash investing and financing activities: | ||||||||
Deferred offering costs included in accrued offering costs | $ | — | $ | 337,157 | ||||
|
|
|
| |||||
Deferred offering costs included in due to related party | $ | — | $ | 11,500 | ||||
|
|
|
| |||||
Offering costs paid in exchange for issuance of Class B common stock to Sponsor | $ | — | $ | 25,000 | ||||
|
|
|
| |||||
The accompanying notes are an integral part of the unaudited condensed consolidated financial statements.
F-28
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
NOTE 1. DESCRIPTION OF ORGANIZATION, BUSINESS OPERATIONS, AND GOING CONCERN
Dynamics Special Purpose Corp. (the “Company”) is a blank check company incorporated in Delaware on March 1, 2021. As used herein, “the Company” refers to Dynamics Special Purpose Corp. and its wholly-owned and controlled subsidiary, Explore Merger Sub, Inc. (“Merger Sub”), unless the context indicates otherwise. The Company was formed for the purpose of entering into a merger, capital stock exchange, asset acquisition, stock purchase, reorganization or similar business combination with one or more businesses (a “Business Combination”). The Company is not limited to a particular industry or geographic region for purposes of consummating a Business Combination. The Company is an early stage and emerging growth company and, as such, the Company is subject to all of the risks associated with early stage and emerging growth companies.
As of March 31, 2022, the Company had not commenced any operations. All activity for the period from March 1, 2021 (inception) through March 31, 2022 related to the Company’s formation, its initial public offering (“Initial Public Offering”), which is described below, and identifying a target company for a Business Combination and negotiating and entering into binding agreements in respect of such Business Combination. The Company will not generate any operating revenues until after the completion of a Business Combination, at the earliest. The Company generates non-operating income in the form of interest income on the proceeds derived from the Initial Public Offering. The Company has selected December 31 as its fiscal year end.
The registration statement for the Initial Public Offering was declared effective on May 25, 2021. On May 28, 2021, the Company consummated the Initial Public Offering of 23,000,000 shares of Class A common stock (the “Public Shares”), including 3,000,000 shares of Class A common stock that were issued pursuant to the underwriter’s exercise of its over-allotment option in full, at $10.00 per Public Share, generating gross proceeds of $230,000,000, which is discussed in Note 3.
Simultaneously with the closing of the Initial Public Offering, the Company consummated the sale of 715,500 shares of Class A common stock (the “Private Placement Shares”) at a price of $10.00 per Private Placement Share in a private placement to Dynamics Sponsor LLC (the “Sponsor”), generating gross proceeds of $7,155,000, which is described in Note 4.
Transaction costs amounted to $13,198,430 consisting of $4,600,000 of underwriting fees, $8,050,000 of deferred underwriting fees, and $548,430 of other offering costs. Subsequent to the Initial Public Offering, the underwriter agreed on December 17, 2021 to waive $1,000,000 of its deferred underwriting fees of $8,050,000, thereby reducing those fees to $7,050,000; thus, the transaction costs related to the Company’s Initial Public Offering amounted to $12,198,430.
Following the closing of the Initial Public Offering on May 28, 2021, an amount of $230,000,000 ($10.00 per Public Share) from the net proceeds of the sale of the Public Shares in the Initial Public Offering and the sale of the Private Placement Shares was placed in a trust account (the “Trust Account”), and is invested only in U.S. government securities with maturities of 185 days or less, or in money market funds meeting certain conditions under Rule 2a-7 under the Investment Company Act which invest only in direct U.S. government treasury obligations, as determined by the Company, until the earlier of: (i) the completion of a Business Combination, and (ii) the distribution of the funds held in the Trust Account, as described below.
The Company’s management has broad discretion with respect to the specific application of the net proceeds of the Initial Public Offering and the sale of the Private Placement Shares, although substantially all of the net proceeds are intended to be applied generally toward consummating a Business Combination. There is no assurance that the Company will be able to complete a Business Combination, including the proposed Business Combination with Senti (as defined and discussed below) successfully. The Company must complete a Business
F-29
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
Combination with one or more target businesses that together have an aggregate fair market value of at least 80% of the value of the Trust Account (excluding the deferred underwriting fees and taxes payable on income earned on the Trust Account) at the time of the agreement to enter into an initial Business Combination. The Company will only complete a Business Combination if the post-transaction company owns or acquires 50% or more of the outstanding voting securities of the target or otherwise acquires a controlling interest in the target sufficient for it not to be required to register as an investment company under the Investment Company Act of 1940, as amended (the “Investment Company Act”).
The Company will provide its stockholders with the opportunity to redeem all or a portion of their Public Shares upon the completion of a Business Combination either (i) in connection with a stockholder meeting called to approve the Business Combination or (ii) by means of a tender offer. The decision as to whether the Company will seek stockholder approval of a Business Combination or conduct a tender offer will be made by the Company, solely in its discretion, subject to applicable law and stock exchange listing requirements. The stockholders will be entitled to redeem their Public Shares for a pro rata portion of the amount held in the Trust Account, calculated as of two business days prior to the completion of a Business Combination, including any pro rata interest earned on the funds held in the Trust Account and not previously released to the Company to pay its tax obligations.
The Company will proceed with a Business Combination if the Company has net tangible assets of at least $5,000,001 upon consummation of such Business Combination and a majority of the shares voted are voted in favor of the Business Combination. If a stockholder vote is not required under applicable law or stock exchange listing requirements and the Company does not decide to hold a stockholder vote for business or other reasons, the Company will, pursuant to its amended and restated certificate of incorporation (the “Amended and Restated Certificate of Incorporation”), conduct the redemptions pursuant to the tender offer rules of the Securities and Exchange Commission (“SEC”), and file tender offer documents with the SEC prior to completing a Business Combination. If the Company seeks stockholder approval in connection with a Business Combination, the holders of the Founder Shares (as defined in Note 5) have agreed to vote their Founder Shares, Private Placement Shares and any Public Shares purchased in or after the Initial Public Offering in favor of approving a Business Combination and to waive their redemption rights with respect to any such shares in connection with a stockholder vote to approve a Business Combination. Additionally, each public stockholder may elect to redeem their Public Shares without voting, and if they do vote, irrespective of whether they vote for or against the proposed Business Combination.
Notwithstanding the foregoing, if the Company seeks stockholder approval of a Business Combination and it does not conduct redemptions pursuant to the tender offer rules, the Company’s Amended and Restated Certificate of Incorporation provides that a public stockholder, together with any affiliate of such stockholder or any other person with whom such stockholder is acting in concert or as a “group” (as defined under Section 13 of the Securities Exchange Act of 1934, as amended (the “Exchange Act”)), will be restricted from redeeming its shares with respect to more than an aggregate of 15% of the Public Shares without the Company’s prior written consent.
The initial stockholders have agreed to waive (a) their redemption rights with respect to any Founder Shares, Private Placement Shares and Public Shares they hold in connection with the completion of an initial Business Combination, (b) their redemption rights with respect to any Founder Shares, Private Placement Shares and Public Shares they hold in connection with a stockholder vote to approve an amendment to the Amended and Restated Certificate of Incorporation to modify the substance or timing of the Company’s obligation to allow redemption in connection with an initial Business Combination or to redeem 100% of the Public Shares if the Company has not consummated an initial Business Combination within 24 months from the closing of the Initial Public Offering or with respect to any material provision relating to the rights of holders of Public Shares, and
F-30
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
(c) their rights to liquidating distributions from the Trust Account with respect to any Founder Shares and Private Placement Shares they hold if the Company fails to complete an initial Business Combination within 24 months from the closing of the Initial Public Offering. However, if the initial stockholders acquired Public Shares in or after the Initial Public Offering, such Public Shares would be entitled to liquidating distributions from the Trust Account if the Company failed to complete a Business Combination within the Combination Period (as defined below).
The Company will have until May 28, 2023 to complete a Business Combination (the “Combination Period”). If the Company is unable to complete a Business Combination within the Combination Period, the Company will (i) cease all operations except for the purpose of winding up, (ii) as promptly as reasonably possible but no more than ten business days thereafter, subject to lawfully available funds therefor, redeem the Public Shares at a per-share price, payable in cash, equal to the aggregate amount then on deposit in the Trust Account, including interest earned on the funds held in the Trust Account and not previously released to the Company to pay its franchise and income taxes (less up to $100,000 of interest to pay dissolution expenses), divided by the number of then-outstanding Public Shares, which redemption will completely extinguish public stockholders’ rights as stockholders (including the right to receive further liquidating distributions, if any), subject to applicable law, and (iii) as promptly as reasonably possible following such redemption, subject to the approval of the Company’s remaining stockholders and board of directors, dissolve and liquidate, subject in each case to the Company’s obligations under Delaware law to provide for claims of creditors and the requirements of other applicable law.
The underwriter has agreed to waive its rights to its deferred underwriting fees (see Note 6) held in the Trust Account in the event the Company does not complete a Business Combination within in the Combination Period and, in such event, such amounts will be included with the other funds held in the Trust Account that will be available to fund the redemption of the Public Shares. In the event of such distribution, it is possible that the per share value of the assets remaining available for distribution will be less than the Initial Public Offering price per Public Share ($10.00).
In order to protect the amounts in the Trust Account, the Sponsor has agreed that it will be liable to the Company if and to the extent any claims by a third party for services rendered or products sold to the Company, or a prospective target business with which the Company has discussed entering into a transaction agreement, reduce the amount of funds in the Trust Account to below (i) $10.00 per Public Share, or (ii) the actual amount per Public Share held in the Trust Account as of the date of the liquidation of the Trust Account, if less than $10.00 per Public Share due to reductions in the value of the Trust Account assets, less taxes payable, provided that such liability will not apply to any claims by a third party or prospective target business who executed a waiver of any and all rights to the monies held in the Trust Account (whether or not such waiver is enforceable), nor will it apply to any claims under the Company’s indemnity of the underwriter of the Initial Public Offering against certain liabilities, including liabilities under the Securities Act of 1933, as amended (the “Securities Act”). The Company will seek to reduce the possibility that the Sponsor will have to indemnify the Trust Account due to claims of creditors by endeavoring to have all vendors, service providers (other than the Company’s independent registered accounting firm), prospective target businesses or other entities with which the Company does business, execute agreements with the Company waiving any right, title, interest or claim of any kind in or to monies held in the Trust Account.
Business Combination Agreement
On December 19, 2021, we entered into a business combination agreement (as amended from time to time, the “Business Combination Agreement”) with Merger Sub and Senti Biosciences, Inc., a Delaware corporation (“Senti”). The Business Combination Agreement provides, among other things, that on the terms and subject to the conditions set forth therein, Merger Sub will merge with and into Senti, with Senti surviving as a wholly-
F-31
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
owned subsidiary of the Company (the “Merger”). Upon the closing of the Merger (the “Closing”), the Company will change its name to “Senti Biosciences, Inc.” The date on which the Closing actually occurs is hereinafter referred to as the “Closing Date.”
The Business Combination Agreement and the transactions contemplated thereby (and contemplated in the Ancillary Documents, as defined in the Business Combination Agreement) are referred to in these Notes to unaudited condensed consolidated financial statements as the “Senti Business Combination.” The Senti Business Combination was approved by the boards of directors of each of the Company and Senti.
Under the Business Combination Agreement, the Company will acquire all of the outstanding equity interests of Senti in exchange for shares of the Company’s Class A common stock, par value $0.0001 per share (the “Class A Common Stock”), based on an implied Senti equity value of $240,000,000, to be paid to Senti stockholders at the effective time of the Merger (the “Effective Time”). In addition, Senti stockholders will have the right to receive (i) an aggregate of 1,000,000 shares of Class A Common Stock if, after Closing, the volume weighted average price of the Class A Common Stock on the Nasdaq Capital Market (“Nasdaq”), or any other national securities exchange on which the shares of Class A Common Stock are then traded (“VWAP”), is greater than or equal to $15.00 over any 20 trading days within any consecutive 30 trading day period, in the period that ends on the second anniversary of the Closing Date, and (ii) an additional 1,000,000 shares of Class A Common Stock in the aggregate if, after Closing, the VWAP of Class A Common Stock is greater than or equal to $20.00 over any 20 trading days within any consecutive 30 trading day period, in the period that ends on the third anniversary of the Closing Date.
Pursuant to the Business Combination Agreement, at or prior to the Effective Time, each option exercisable for Senti equity that is outstanding immediately prior to the Effective Time shall be converted into an option to purchase a number of shares of Class A Common Stock equal to the number of shares of Senti common stock subject to such option immediately prior to the Effective time multiplied by the exchange ratio derived under the Business Combination Agreement.
The parties to the Business Combination Agreement have agreed to customary representations and warranties for transactions of this type. In addition, the parties to the Business Combination Agreement agreed to be bound by certain customary covenants for transactions of this type, including, among others, covenants with respect to the conduct of Senti, the Company and their respective subsidiaries during the period between execution of the Business Combination Agreement and Closing. The representations, warranties, agreements and covenants of the parties set forth in the Business Combination Agreement will terminate at Closing, except for a limited number of representations and warranties and those covenants and agreements that, by their terms, contemplate performance after Closing. Each of the parties to the Business Combination Agreement has agreed to use its reasonable best efforts to take or cause to be taken all actions, and to do or cause to be done all things, reasonably necessary to consummate and expeditiously implement the Merger.
Under the Business Combination Agreement, the obligations of the parties to consummate the Merger are subject to the satisfaction or waiver of certain customary closing conditions of the respective parties, including, without limitation: (i) the approval and adoption of the Business Combination Agreement and transactions contemplated thereby by requisite vote of the Company’s stockholders (the “Company Stockholder Approval”) and Senti’s stockholders (the “Senti Stockholder Approval”); (ii) the expiration or termination of the applicable waiting period under the Hart-Scott-Rodino Antitrust Improvements Act of 1976, as amended; (iii) the absence of a Company Material Adverse Effect or DYNS Material Adverse Effect (each, as defined in the Business Combination Agreement) since the date of the Business Combination Agreement that is continuing; (iv) after giving effect to the transactions contemplated by the Business Combination Agreement, the Company has net tangible assets of at least $5,000,001 upon consummation of the Merger; (v) the Company’s initial listing
F-32
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
application with Nasdaq in connection with the Merger has been approved and, immediately following the Effective Time, the Company has satisfied any applicable initial and continuing listing requirements of Nasdaq and the shares of the Company’s Class A Common Stock have been approved for listing on Nasdaq, subject only to official notice of the issuance thereof; and (vi) the registration statement filed with the SEC on Form S-4 (the “Registration Statement”) has become effective, no stop order has been issued by the SEC and remains in effect with respect to the Registration Statement, and no proceeding seeking such a stop order has been threatened or initiated by the SEC and remains pending. In addition, Senti’s obligation to consummate the Merger is subject to the condition that the Available Closing Cash (as defined in the Business Combination Agreement) shall be greater than or equal to $150,000,000 (after reduction for the aggregate amount of payments made or required to be made in connection with the DYNS Stockholder Redemption (as defined in the Business Combination Agreement)).
On February 12, 2022, the Business Combination Agreement was amended by the parties thereto to reflect, among other things, (i) corrections to certain aspects section 5.7 of the Business Combination Agreement, and (ii) changes to certain terms of the options Senti granted to certain persons at the time the Business Combination Agreement was signed.
Other Agreements
The Business Combination Agreement contemplates the execution of various additional agreements and instruments, on or before the Closing, including, among others, the following:
Sponsor Support Agreement
In connection with the execution of the Business Combination Agreement, the Sponsor, as the sole holder of the Company’s Class B common stock, par value $0.0001 per share (the “Class B Common Stock”, and also referred to herein as the Founder Shares (as defined in Note 5)) and other persons party thereto (“Other Company Insiders,” and together with the Sponsor, collectively, the “Company Insiders”), entered into a support agreement with the Company and Senti (the “Sponsor Support Agreement”). Under the Sponsor Support Agreement, the Sponsor agreed to vote, at any meeting of the stockholders of the Company and in any action by written consent of the stockholders of the Company, all of such Sponsor’s Class A Common Stock and Class B Common Stock (i) in favor of (a) the Business Combination Agreement and the transactions contemplated thereby, and (b) the other proposals that the Company and Senti agreed in the Business Combination Agreement shall be submitted at such meeting for approval by the Company’s stockholders together with the proposal to obtain the Company Stockholder Approval (together with the Company Stockholder Approval, these proposals are the Required Transaction Proposals (as defined in the Business Combination Agreement)), and (ii) against any proposal that conflicts with, or materially impedes or interferes with, any such proposal or that would adversely affect or delay the Merger. The Sponsor Support Agreement also prohibits the Sponsor from, among other things and subject to certain exceptions, selling, assigning or transferring any Class A Common Stock or Class B Common Stock held by the Sponsor prior to the Closing or taking any action that would have the effect of preventing or materially delaying the Sponsor from performing its obligations under the Sponsor Support Agreement. In addition, in the Sponsor Support Agreement, the Sponsor agreed to waive, and not to assert or perfect, among other things, any rights to adjustment or other anti-dilution protections with respect to the rate at which the shares of Class B Common Stock held by the Sponsor convert into shares of Class A Common Stock in connection with the transactions contemplated by the Business Combination Agreement.
The Sponsor Support Agreement also includes a lock-up in respect of the Sponsor’s equity interests in the Company. Pursuant to the Sponsor Support Agreement, the Sponsor agreed that, subject to limited exceptions, it would not sell, assign or transfer any Class A Common Stock or Class B Common Stock until the earlier of
F-33
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
(i) the one year anniversary of the Closing, and (ii) subsequent to the Closing, (x) if the last reported sale price of the Class A Common Stock equals or exceeds $12.00 per share (as adjusted for stock splits, stock dividends, reorganizations, recapitalizations and the like) for any 20 trading days within any 30 consecutive trading day period commencing at least 150 days after the Closing, or (y) the date upon completion of a liquidation, merger, stock exchange, reorganization or other similar transaction that results in all of the public stockholders having the right to exchange their common stock for cash, securities or other property.
Senti Support Agreement
In connection with the execution of the Business Combination Agreement, certain Senti stockholders (the “Senti Supporting Stockholders”) entered into support agreements with the Company (the “Senti Support Agreements”). Under the Senti Support Agreements, each Senti Supporting Stockholder agreed, within forty-eight hours following the effectiveness of the Registration Statement, to execute and deliver a written consent with respect to all outstanding shares of Senti common stock and preferred stock held by such Senti Supporting Stockholder (the “Subject Senti Shares”) approving the Business Combination Agreement and the transactions contemplated thereby. In addition to the foregoing, each Senti Supporting Stockholder agreed that, at any meeting of the holders of Senti capital stock, each such Senti Supporting Stockholder will appear at the meeting, in person or by proxy, and cause its Subject Senti Shares to be voted (i) to approve and adopt the Business Combination Agreement, the transactions contemplated thereby, and any other matters necessary or reasonably requested by Senti for consummation of the Merger, and (ii) against any proposal that conflicts or materially impedes or interferes with, or would adversely affect or delay, the consummation of the transactions contemplated by the Business Combination Agreement.
The Senti Support Agreements also prohibit the Senti Supporting Stockholders from, among other things, (i) transferring any of the Subject Senti Shares prior to the Closing, (ii) entering into (a) any option, commitment or other arrangement that would require the Senti Supporting Stockholders to transfer the Subject Senti Shares, or (b) any voting trust, proxy or other contract with respect to the voting of the Subject Senti Shares, or (iii) taking any action in furtherance of the foregoing. In addition, under the Senti Support Agreement, each Senti Supporting Stockholder agreed (i) not to exercise any rights of appraisal or dissenter’s rights relating to the Business Combination Agreement and the transactions contemplated thereby, and (ii) not to commence or participate in any claim or action against Senti, the Company or any of their affiliates relating to the negotiation, execution or delivery of the Senti Support Agreement or the Business Combination Agreement or the consummation of the Merger.
Additionally, (i) certain Senti Support Agreements prohibit the applicable Senti Supporting Stockholders from transferring the shares of Class A Common Stock which they will receive in the Merger for, subject to certain permitted transfers, up to 18 months following the Closing, which may be reduced to 12 months upon the meeting of certain criteria (such period, the “Extended Lock-Up”), and (ii) certain other Senti Support Agreements prohibit the applicable Senti Supporting Stockholders from transferring the shares of Class A Common Stock which they will receive in the Merger for, subject to certain permitted transfers, 12 months following the Closing (such period, the “General Lock-Up”); provided that, (a) with respect to the Extended Lock-Up, if the last reported sale price of the Class A Common Stock on Nasdaq, or any other national securities exchange on which the Class A Common Stock is then traded, is greater than or equal to $12.00 per share over any 20 trading days within any consecutive 30 trading day period commencing at least 330 days after the Closing Date, then the Extended Lock-Up shall be deemed to have expired with respect to each stockholder’s Class A Common Stock subject to that lock-up, and (b) with respect to the General Lock-Up, if the last reported sale price of the Class A Common Stock on Nasdaq, or any other national securities exchange on which the Class A Common Stock is then traded, is greater than or equal to $12.00 per share over any 20 trading days within any consecutive 30 trading day period commencing at least 150 days after the Closing Date, then the General Lock-Up shall be deemed to have expired with respect to each stockholder’s Class A Common Stock subject to that lock-up.
F-34
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
On February 12, 2022, the Company entered into amendments to certain Senti Support Agreements to amend those agreements such that, among other things, the shares of Class A Common Stock of the relevant Senti Supporting Stockholders may not be transferred, subject to certain permitted transfers, for three years following the Closing (such period, “the Three Year Lock-Up”). Unlike the Extended Lock-Up and the General Lock-Up described above, the Three Year Lock-Up does not terminate early based on the share price performance of Class A Common Stock.
PIPE Subscription Agreements
In connection with the execution of the Business Combination Agreement, the Company entered into subscription agreements with certain private investors (the “Subscription Agreements”), pursuant to which, among other things, such investors have subscribed to purchase an aggregate of 6,680,000 shares of Class A Common Stock (together, the “Subscriptions”) for a purchase price of $10.00 per share, or an aggregate purchase price of $66,800,000, which shares are to be issued at the Closing; provided that the Subscription Agreements permit the Company to accept additional subscriptions for a purchase price of $10.00 per share to be issued at the Closing, following the execution of the Business Combination Agreement. The obligations of each party to consummate the Subscriptions are conditioned upon, among other things, customary closing conditions and the consummation of the transactions contemplated by the Business Combination Agreement.
Non-Redemption Agreements
In connection with the execution of the Business Combination Agreement, the Sponsor, as the holder of 5,750,000 shares of Class B Common Stock (the Founder Shares (as defined in Note 5)), the Company and each of certain funds and accounts managed by Morgan Stanley Investment Management Inc., T. Rowe Price Group, Inc., The Invus Group, LLC and ARK Investment Management LLC and/or their respective investment funds (each, an “Investor”, and collectively, the “Investors”) entered into non-redemption agreements in respect of the Public Shares held by the Investors (the “Non-Redemption Agreements”).
Pursuant to the Non-Redemption Agreements, each Investor agreed for the benefit of the Company (a) to not redeem the shares of Class A Common Stock beneficially owned by it, or any other shares, capital stock or other equity interests, as applicable, of the Company, which it held on the date of the Non-Redemption Agreement (the “Investor Shares”), and (b) to not, among other things, sell, encumber or otherwise transfer the Investor Shares other than in connection with non-discretionary ETF or mutual fund pro rata rebalancing transfers. In connection with these commitments from the Investors, the Sponsor agreed to forfeit 965,728 shares of its Class B Common Stock and the Company agreed to cancel such shares and concurrently issue to the Investors an equivalent number of shares of Class A Common Stock, in each case, at or promptly following the consummation of the Merger. The shares of Class A Common Stock to which the Investors were entitled as at the date the Non-Redemption Agreements were signed represented approximately 11.111% of the Investors’ aggregate holdings of Public Shares as at such date.
On May 9, 2022, the Company, the Sponsor and the Investors agreed to amend the Non-Redemption Agreements such that the number of shares of Class A Common Stock to which each Investor may be entitled equals 11.111% of the number of Public Shares held by the Investor at the time the Merger is consummated (as opposed to when the Non-Redemption Agreement was signed). As at April 29, 2022, 7,968,483 shares of Class A Common Stock, in the aggregate, were subject to Non-Redemption Agreements. Accordingly, as at April 29, 2022, it is anticipated that 885,377 shares of Class A Common Stock will be issued to Investors and an equivalent number of shares of Class B Common Stock will be forfeited by the Sponsor and canceled by the Company (as opposed to 965,728 shares, as was the case prior to such amendments to the Non-Redemption Agreements).
F-35
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
Investor Rights Agreement
In connection with the Closing, the Company, certain stockholders of the Company (including the Sponsor) and certain stockholders of Senti will enter into an investor rights and lock-up agreement (the “Investor Rights Agreement”). Pursuant to the Investor Rights Agreement, each signatory thereto (other than the Company) will be granted certain registration rights with respect to their respective shares of Class A Common Stock.
The Investor Rights Agreement will also restrict the ability of each stockholder who is a party thereto (other than the Company) to transfer its shares of Class A Common Stock (or any securities convertible into or exercisable or exchangeable for shares of Class A Common Stock) for, subject to certain permitted transfers and depending on the stockholder, a period of one year following the Closing Date (the “12 Month Lock-Up”) or a period of 18 months following the Closing Date (the “18 Month Lock-Up”); provided that (i) the foregoing restrictions shall not apply to any shares of Class A Common Stock purchased pursuant to the Subscription Agreements and (ii)(A) in respect of the 12 Month Lock-Up, if the last reported sale price of the Class A Common Stock on Nasdaq, or any other national securities exchange on which the Class A Common Stock is then traded, is greater than or equal to $12.00 per share over any 20 trading days within any consecutive 30 trading day period commencing at least 150 days after the Closing Date, then the 12 Month Lock-Up shall be deemed to have expired with respect to each stockholder’s Class A Common Stock subject to that lock-up; and (B) in respect of the 18 Month Lock-Up, if the last reported sale price of the Class A Common Stock on Nasdaq, or any other national securities exchange on which the Class A Common Stock is then traded, is greater than or equal to $12.00 per share over any 20 trading days within any consecutive 30 trading day period commencing at least 330 days after the Closing Date, then the 18 Month Lock-Up shall be deemed to have expired with respect to each stockholder’s Class A Common Stock subject to that lock-up.
Going Concern
As of March 31, 2022, the Company had $396,693 in cash held outside of the Trust Account and a working capital deficit of $3,224,077. The Company has incurred and expects to continue to incur significant costs in pursuit of its acquisition plans (including in respect of the Senti Business Combination). These conditions raise substantial doubt about the Company’s ability to continue as a going concern for a period of time within one year after the date that the unaudited condensed consolidated financial statements are issued. Management plans to address this uncertainty through the Senti Business Combination, as discussed above. There is no assurance that the Company’s plans to consummate the Senti Business Combination (or any other Business Combination) will be successful or successful within the Combination Period. The unaudited condensed consolidated financial statements do not include any adjustments that might result from the outcome of this uncertainty.
Risks and Uncertainties
Management continues to evaluate the impact of the COVID-19 pandemic on the industry and has concluded that while it is reasonably possible that the virus could have a negative effect on the Company’s financial position, results of its operations, and/or search for a target company, the specific impact is not readily determinable as of the date of these unaudited condensed consolidated financial statements. The unaudited condensed consolidated financial statements do not include any adjustments that might result from the outcome of this uncertainty.
Additionally, as a result of the military action commenced in February 2022 by the Russian Federation and Belarus in the country of Ukraine and related economic sanctions, the Company’s ability to consummate a Business Combination, or the operations of a target business with which the Company ultimately consummates a Business Combination, may be materially and adversely affected. In addition, the Company’s ability to consummate a transaction may be dependent on the ability to raise equity and debt financing which may be
F-36
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
impacted by these events, including as a result of increased market volatility, or decreased market liquidity in third-party financing being unavailable on terms acceptable to the Company or at all. The impact of this action and related sanctions on the world economy and the specific impact on the Company’s financial position, results of operations and/or ability to consummate a Business Combination are not yet determinable. The financial statements do not include any adjustments that might result from the outcome of this uncertainty.
NOTE 2. SUMMARY OF SIGNIFICANT ACCOUNTING POLICIES
Principles of Consolidation and Financial Statement Presentation
The accompanying unaudited condensed consolidated financial statements of the Company are presented in conformity with accounting principles generally accepted in the United States of America (“GAAP”) and pursuant to the rules and regulations of the SEC. The unaudited condensed consolidated financial statements include the accounts of the Company and its wholly-owned and controlled subsidiary, Merger Sub, after elimination of any intercompany transactions and balances as of March 31, 2022 and December 31, 2021.
Certain information or footnote disclosures normally included in financial statements prepared in accordance with GAAP have been condensed or omitted, pursuant to the rules and regulations of the SEC for interim financial reporting. Accordingly, they do not include all the information and footnotes necessary for a comprehensive presentation of financial position, results of operations, or cash flows. In the opinion of management, the accompanying unaudited condensed consolidated financial statements include all adjustments, consisting of a normal recurring nature, which are necessary for a fair presentation of the financial position, operating results and cash flows for the periods presented. The accompanying unaudited condensed consolidated financial statements should be read in conjunction with the Company’s annual report on Form 10-K as filed with the SEC on March 7, 2022. The interim results for the three months ended March 31, 2022 are not necessarily indicative of the results to be expected for the year ending December 31, 2022 or for any future periods.
Emerging Growth Company
The Company is an “emerging growth company,” as defined in Section 2(a) of the Securities Act, as modified by the Jumpstart Our Business Startups Act of 2012 (the “JOBS Act”), and it may take advantage of certain exemptions from various reporting requirements that are applicable to other public companies that are not emerging growth companies including, but not limited to, not being required to comply with the independent registered public accounting firm attestation requirements of Section 404 of the Sarbanes-Oxley Act, reduced disclosure obligations regarding executive compensation in its periodic reports and proxy statements, and exemptions from the requirements of holding a nonbinding advisory vote on executive compensation and stockholder approval of any golden parachute payments not previously approved.
Further, Section 102(b)(1) of the JOBS Act exempts emerging growth companies from being required to comply with new or revised financial accounting standards until private companies (that is, those that have not had a Securities Act registration statement declared effective or do not have a class of securities registered under the Exchange Act) are required to comply with the new or revised financial accounting standards. The JOBS Act provides that a company can elect to opt out of the extended transition period and comply with the requirements that apply to non-emerging growth companies but any such election to opt out is irrevocable. The Company has elected not to opt out of such extended transition period which means that when a standard is issued or revised and it has different application dates for public or private companies, the Company, as an emerging growth company, can adopt the new or revised standard at the time private companies adopt the new or revised standard. This may make comparison of the Company’s unaudited condensed consolidated financial statements with another public company which is neither an emerging growth company nor an emerging growth company which has opted out of using the extended transition period difficult or impossible because of the potential differences in accounting standards used.
F-37
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
Use of Estimates
The preparation of unaudited condensed consolidated financial statements in conformity with U.S. GAAP requires the Company’s management to make estimates and assumptions that affect the reported amounts of assets and liabilities and disclosure of contingent assets and liabilities at the date of the unaudited condensed consolidated financial statements and the reported amounts of expenses during the reporting period.
Making estimates requires management to exercise significant judgment. It is at least reasonably possible that the estimate of the effect of a condition, situation or set of circumstances that existed at the date of the unaudited condensed consolidated financial statements, which management considered in formulating its estimate, could change in the near term due to one or more future confirming events. Accordingly, the actual results could differ from those estimates.
Cash and Cash Equivalents
The Company considers all short-term investments with an original maturity of three months or less when purchased to be cash equivalents. The Company did not have any cash equivalents as of March 31, 2022 and December 31, 2021. As of March 31, 2022 and December 31, 2021, the Company had operating cash (i.e. cash held outside the Trust Account) of $396,693 and $889,323, respectively.
Investments Held in Trust Account
As of March 31, 2022 and December 31, 2021, the assets held in the Trust Account were comprised of U.S. government securities, within the meaning set forth in Section 2(a) (16) of the Investment Company Act, with maturities of 185 days or less, or investments in money market funds that invest in U.S. government securities and generally have a readily determinable fair value, or a combination thereof. When the Company’s investments held in the Trust Account are comprised of U.S. government securities, the investments are classified as trading securities. When the Company’s investments held in the Trust Account are comprised of money market funds, the investments are recognized at fair value. Trading securities and investments in money market funds are presented on the unaudited condensed consolidated balance sheet at fair value at the end of each reporting period. Gains and losses resulting from the change in fair value of these securities are reported in the statements of operations. The estimated fair values of investments held in the Trust Account are determined using available market information.
Class A Common Stock Subject to Possible Redemption
The Public Shares sold in the Initial Public Offering contain a redemption feature which allows for the redemption of such Public Shares in connection with the Company’s liquidation, if there is a stockholder vote or tender offer in connection with the Business Combination and in connection with certain amendments to the Company’s Amended and Restated Certificate of Incorporation. In accordance with SEC and its staff’s guidance on redeemable equity instruments, which has been codified in Accounting Standards Codification (“ASC”) Topic 480, Distinguishing Liabilities from Equity, redemption provisions not solely within the control of the Company require common stock subject to redemption to be classified outside of permanent equity. Therefore, all Class A Common Stock has been classified outside of permanent equity.
The Company recognizes changes in redemption value immediately as they occur and adjusts the carrying value of redeemable common stock to equal the redemption value at the end of each reporting period. Increases or decreases in the carrying amount of redeemable common stock are affected by charges against additional paid in capital and accumulated deficit.
F-38
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
As of March 31, 2022 and December 31, 2021, the Investor Shares (see Note 1) are classified as temporary equity within Class A Common Stock subject to redemption in the Company’s unaudited condensed consolidated balance sheet. The Non-Redemption Agreements are terminated in the event that the Business Combination Agreement as described above is terminated. As such, the Company determined that the Non-Redemption Agreements are contingent upon the successful completion of the Senti Business Combination. In the event that the Senti Business Combination is not successful, the Non-Redemption Agreements are terminated, and the Investors would again have the right to redeem the Investor Shares. As such, the Company determined that the Non-Redemption Agreements would not change the nature of the underlying shares as redeemable.
As of March 31, 2022 and December 31, 2021, the Class A common stock subject to redemption reflected in the balance sheet are reconciled in the following table:
Gross proceeds | $ | 230,000,000 | ||
Less: | ||||
Issuance costs allocated to Class A common stock | (13,181,867 | ) | ||
Plus: | ||||
Accretion of carrying value to redemption value | 13,181,867 | |||
|
| |||
Class A common stock subject to possible redemption | $ | 230,000,000 | ||
|
|
Offering Costs Associated with the Initial Public Offering
The Company complies with the requirements of ASC 340-10-S99-1 and SEC Staff Accounting Bulletin Topic 5A - Expenses of Offering. Offering costs consist principally of professional and registration fees incurred related to the Initial Public Offering. Offering costs directly attributable to the issuance of an equity contract to be classified in equity are recorded as a reduction in equity. Offering costs for equity contracts that are classified as assets and liabilities are expensed immediately. The Company incurred offering costs amounting to $13,198,430 as a result of the Initial Public Offering (consisting of a $4,600,000 underwriting fee, $8,050,000 of deferred underwriting fees, and $548,430 of other offering costs). The Company recorded $13,181,867 of offering costs as a reduction of temporary equity in connection with the issuance of the Public Shares. The Company recorded $16,563 of offering costs as a reduction of permanent equity in connection with the issuance of the Private Placement Shares.
As noted in Note 1, subsequent to the Initial Public Offering, the underwriter agreed on December 17, 2021 to waive $1,000,000 of its deferred underwriting fees of $8,050,000, thereby reducing those fees to $7,050,000; thus, the offering costs related to the Company’s Initial Public Offering amounted to $12,198,430.
Income Taxes
The Company follows the asset and liability method of accounting for income taxes under ASC Topic 740, Income Taxes (“ASC 740”). Deferred tax assets and liabilities are recognized for the estimated future tax consequences attributable to differences between the financial statements carrying amounts of existing assets and liabilities and their respective tax bases. Deferred tax assets and liabilities are measured using enacted tax rates expected to apply to taxable income in the years in which those temporary differences are expected to be recovered or settled. The effect on deferred tax assets and liabilities of a change in tax rates is recognized in income in the period that included the enactment date. Valuation allowances are established, when necessary, to reduce deferred tax assets to the amount expected to be realized.
F-39
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
ASC 740 prescribes a recognition threshold and a measurement attribute for the financial statement recognition and measurement of tax positions taken or expected to be taken in a tax return. For those benefits to be recognized, a tax position must be more likely than not to be sustained upon examination by taxing authorities. The Company recognizes accrued interest and penalties related to unrecognized tax benefits as income tax expense. There were no unrecognized tax benefits and no amounts accrued for interest and penalties as of March 31, 2022 and December 31, 2021. The Company is currently not aware of any issues under review that could result in significant payments, accruals or material deviation from its position. The Company is subject to income tax examinations by major taxing authorities since inception.
Net Loss Per Share of Common Stock
Net loss per common share is computed by dividing net loss by the weighted-average number of shares of common stock outstanding during the period. As the Public Shares are considered to be redeemable at fair value, and a redemption at fair value does not amount to a distribution different than other stockholders, Class A and Class B common stock are presented as one class of stock in calculating net loss per share. As a result, the calculated net loss per share is the same for Class A and Class B shares of common stock. As of March 31, 2022 and December 31, 2021, the Company did not have any dilutive securities and other contracts that could, potentially, be exercised or converted into shares of common stock and then share in the earnings of the Company. As a result, diluted loss per share is the same as basic loss per share for the periods presented.
The following table reflects the calculation of basic and diluted net loss per common share (in dollars, except per share amounts):
| For the three months ended March 31, 2022 | For the period from March 1, 2021 (inception) through March 31, 2021 | |||||||||||||||
| Class A | Class B | Class A | Class B | |||||||||||||
Basic and diluted net income (loss) per share: | ||||||||||||||||
Numerator: | ||||||||||||||||
Net loss | $ | (1,054,241 | ) | $ | (255,608 | ) | $ | — | $ | (1,178 | ) | |||||
|
|
|
|
|
|
|
| |||||||||
Denominator: | ||||||||||||||||
Basic and diluted weighted average shares outstanding | 23,715,500 | 5,750,000 | — | 5,000,000 | ||||||||||||
Basic and diluted net loss per share | $ | (0.04 | ) | $ | (0.04 | ) | $ | — | $ | (0.00 | ) | |||||
Concentration of Credit Risk
Financial instruments that potentially subject the Company to concentrations of credit risk consist of a cash account in a financial institution, which, at times, may exceed the Federal Depository Insurance Coverage of $250,000. The Company has not experienced losses on this account and management believes the Company is not exposed to significant risks on such account.
Fair Value of Financial Instruments
The Company applies ASC Topic 820, Fair Value Measurement (“ASC 820”), which establishes a framework for measuring fair value and clarifies the definition of fair value within that framework. ASC 820 defines fair value as an exit price, which is the price that would be received for an asset or paid to transfer a liability in the Company’s principal or most advantageous market in an orderly transaction between market participants on the
F-40
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
measurement date. The fair value hierarchy established in ASC 820 generally requires an entity to maximize the use of observable inputs and minimize the use of unobservable inputs when measuring fair value. Observable inputs reflect the assumptions that market participants would use in pricing the asset or liability and are developed based on market data obtained from sources independent of the reporting entity. Unobservable inputs reflect the entity’s own assumptions based on market data and the entity’s judgments about the assumptions that market participants would use in pricing the asset or liability and are to be developed based on the best information available in the circumstances.
The carrying amounts reflected in the unaudited condensed consolidated balance sheet for current assets and current liabilities approximate fair value due to their short-term nature.
Level 1 — Assets and liabilities with unadjusted, quoted prices listed on active market exchanges. Inputs to the fair value measurement are observable inputs, such as quoted prices in active markets for identical assets or liabilities.
Level 2 — Inputs to the fair value measurement are determined using prices for recently traded assets and liabilities with similar underlying terms, as well as direct or indirect observable inputs, such as interest rates and yield curves that are observable at commonly quoted intervals.
Level 3 — Inputs to the fair value measurement are unobservable inputs, such as estimates, assumptions, and valuation techniques when little or no market data exists for the assets or liabilities.
See Note 8 for additional information on assets and liabilities measured at fair value.
Recent Accounting Standards
Management does not believe that any recently issued, but not yet effective, accounting standards, if currently adopted, would have a material effect on the Company’s financial statements.
NOTE 3. INITIAL PUBLIC OFFERING
The registration statement for the Company’s Initial Public Offering was declared effective on May 25, 2021. On May 28, 2021, the Company completed its Initial Public Offering of 23,000,000 shares of Class A common stock, including 3,000,000 shares of Class A common stock that were issued pursuant to the underwriter’s exercise of its over-allotment option in full, at $10.00 per Public Share, generating gross proceeds of $230,000,000.
NOTE 4. PRIVATE PLACEMENT
Simultaneously with the closing of the Initial Public Offering, the Sponsor purchased an aggregate of 715,500 Private Placement Shares at a price of $10.00 per Private Placement Share, generating gross proceeds of $7,155,000. A portion of the proceeds from the sale of the Private Placement Shares was added to the net proceeds from the Initial Public Offering held in the Trust Account. If the Company does not complete a Business Combination within the Combination Period, the proceeds from the sale of the Private Placement Shares held in the Trust Account will be used to fund the redemption of the Public Shares (subject to the requirements of applicable law).
F-41
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
NOTE 5. RELATED PARTY TRANSACTIONS
Founder Shares
On March 8, 2021, the Sponsor was issued 5,750,000 shares (the “Founder Shares”) of Class B Common Stock for an aggregate price of $25,000. The Founder Shares included an aggregate of up to 750,000 shares of Class B Common Stock subject to forfeiture by the Sponsor to the extent that the underwriter’s over-allotment option was not exercised in full or in part, so that the Sponsor would own, on an as-converted basis, 20% of the Company’s issued and outstanding shares after the Initial Public Offering (excluding the Private Placement Shares) (assuming the Sponsor did not purchase any Public Shares in the Initial Public Offering, which it did not). The underwriter fully exercised the over-allotment option on May 28, 2021; thus, these 750,000 Founder Shares are no longer subject to forfeiture.
In connection with the Non-Redemption Agreements (see Note 1), it is anticipated that the Sponsor will forfeit 885,377 Founder Shares and the Company will cancel such Founder Shares and concurrently issue to the Investors an equivalent number of shares of Class A Common Stock, in each case, at or promptly following the consummation of the Merger. The Company evaluated the forfeiture and cancellation of the Founder Shares by the Sponsor and concurrent issuance of an equivalent number of shares of Class A Common Stock to the Investors in accordance with Staff Accounting Bulletin Topic 5A. The forfeiture and cancellation of the Founder Shares by the Sponsor and concurrent issuance of an equivalent number of shares of Class A Common Stock to the Investors has not been transacted as of March 31, 2022 and will not occur until at or promptly following the consummation of the Merger. As such, any expense associated with the issuance of the shares of Class A Common Stock to the Investors would be recognized at the date of issuance (i.e., upon consummation of the Merger).
Promissory Note - Related Party
On March 8, 2021, the Company issued an unsecured promissory note to the Sponsor (the “Promissory Note”), pursuant to which the Company could borrow an aggregate of up to $300,000 to cover expenses related to the Initial Public Offering. The Promissory Note was non-interest bearing and was payable on the earlier of December 31, 2021 or the consummation of the Initial Public Offering. In April 2021, the Company borrowed $250,000 under the Promissory Note which was repaid in full on May 26, 2021.
Related Party Loans
In addition, in order to finance transaction costs in connection with a Business Combination, the Sponsor or an affiliate of the Sponsor, or certain of the Company’s officers and directors may, but are not obligated to, loan the Company funds as may be required (“Working Capital Loans”). If the Company completes a Business Combination, the Company would repay the Working Capital Loans out of the proceeds held in the Trust Account released to the Company. Otherwise, the Working Capital Loans would be repaid only out of funds held outside the Trust Account. In the event that a Business Combination is not completed, the Company may use a portion of the proceeds held outside the Trust Account to repay the Working Capital Loans, but no proceeds held in the Trust Account would be used to repay the Working Capital Loans. Except for the foregoing, the terms of such Working Capital Loans, if any, have not been determined and no written agreements exist with respect to such loans. Up to $2,000,000 of such Working Capital Loans may be convertible into shares at a price of $10.00 per share at the option of the lender. The shares would be identical to the Private Placement Shares. There was no outstanding balance of Working Capital Loans as of March 31, 2022 and December 31, 2021.
Administrative Support Agreement
The Company entered into an agreement, commencing on the effective date of the Initial Public Offering, to pay the Sponsor up to a total of $10,000 per month for office space, administrative and support services. Upon the
F-42
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
completion of an initial Business Combination, the Company will cease paying these monthly fees (if any). To date, the Company has not exercised its option to use such services.
NOTE 6. COMMITMENTS AND CONTINGENCIES
Registration Rights
The holders of the Founder Shares, Private Placement Shares and any Class A Common Stock issuable upon conversion of any Working Capital Loans have registration rights pursuant to a registration and stockholder rights agreement signed in connection with the Company’s Initial Public Offering. The holders of these securities are entitled to make up to three demands, excluding short form demands, that the Company register such securities. In addition, the holders have certain “piggy-back” registration rights with respect to registration statements filed subsequent to the completion of an initial Business Combination. The Company will bear the expenses incurred in connection with the filing of any such registration statements.
In addition, it is anticipated that each signatory to the Investor Rights Agreement (see Note 1), other than the Company, will be granted certain registration rights with respect to their respective shares of Class A Common Stock when that agreement is signed (which is expected to occur at Closing). Further, shares of Class A Common Stock issued to the private investors making Subscriptions will have registration rights pursuant to the Subscription Agreements following the consummation of the Business Combination.
Underwriters Agreement
The Company granted the underwriter of its Initial Public Offering a 45-day option to purchase up to 3,000,000 additional shares of Class A Common Stock to cover over-allotments at the Initial Public Offering price, less the underwriting discounts and commissions. The underwriter exercised the over-allotment option in full on May 28, 2021.
The underwriter was paid a cash underwriting fee of $0.20 per share, or $4,600,000 in the aggregate, upon the closing of the Initial Public Offering. In addition, $0.35 per share, or $8,050,000 in the aggregate was payable to the underwriter for deferred underwriting commissions. On December 17, 2021, the underwriter agreed to waive its right to $1,000,000 of the fee payable by the Company for deferred underwriting commissions. The waived fee was recorded to accumulated deficit. The revised deferred underwriting fee of $7,050,000 will become payable to the underwriter from the amount held in the Trust Account solely in the event that the Company completes a Business Combination, subject to the terms of the underwriting agreement.
Financial Advisor Agreement
On December 16, 2021, the Company entered into an agreement (the “Financial Advisor Agreement”) with Morgan Stanley & Co. LLC (“Morgan Stanley”) for financial advisory services in connection with the Senti Business Combination, which services Morgan Stanley had been engaged to provide, and which services Morgan Stanley had provided, since August 4, 2021. The Financial Advisor Agreement shall terminate automatically on December 16, 2022 unless terminated earlier, with or without cause, by either the Company or Morgan Stanley. The Company will pay Morgan Stanley a fee of $1,000,000 upon the consummation of the Company’s proposed initial business combination with Senti.
Placement Agent Agreement
On September 21, 2021, the Company entered into an agreement (the “Placement Agent Agreement”) with Morgan Stanley, J.P. Morgan Securities LLC and BofA Securities, Inc. (together, the “Placement Agents”) for
F-43
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
services in connection with the placement of shares of the Company’s Class A Common Stock to certain private investors which is anticipated to occur concurrently with the completion the Senti Business Combination (i.e. the Subscriptions – see Note 1). The Placement Agent Agreement shall terminate automatically on August 28, 2022 unless terminated earlier, with or without cause, by either the Company or any Placement Agent (as to itself only). The Company will pay to the Placement Agents a total fee equal to 4.0% of the aggregate price at which the shares of the Company’s Class A Common Stock are sold to the private investors in the Subscriptions, which fee shall be payable upon the consummation of the placement of the shares. Each of the Placement Agents will receive 33.3% of the fee.
Business Combination Agreement
As set forth in Note 1, the Company has entered into the Business Combination Agreement with Merger Sub and Senti pursuant to which, among other things, Merger Sub will merge with and into Senti, with Senti surviving as a wholly-owned subsidiary of the Company. The Company has also entered into various ancillary transaction documents to give effect to the Merger, which are described throughout this Quarterly Report.
NOTE 7. STOCKHOLDERS’ EQUITY (DEFICIT)
Preferred stock — The Company is authorized to issue 1,000,000 shares of preferred stock with a par value of $0.0001 per share with such designations, voting and other rights and preferences as may be determined from time to time by the Company’s board of directors. As of March 31, 2022 and December 31, 2021, there were no shares of preferred stock issued or outstanding.
Class A common stock — The Company is authorized to issue 100,000,000 shares of Class A common stock with a par value of $0.0001 per share. Holders of Class A common stock are entitled to one vote for each share. As of March 31, 2022 and December 31, 2021, there were 23,715,500 shares of Class A common stock issued and outstanding, including 23,000,000 shares of Class A common stock subject to possible redemption. Despite the Non-Redemption Agreements discussed in Note 1, it is possible, in certain limited circumstances, for the Investors to transfer their Public Shares, and a transfer of such shares to a third party who is not bound by a Non-Redemption Agreement would render such shares subject to possible redemption.
Class B common stock — The Company is authorized to issue 10,000,000 shares of Class B common stock with a par value of $0.0001 per share. Holders of Class B common stock are entitled to one vote for each share. As of March 31, 2022 and December 31, 2021, there were 5,750,000 shares of Class B common stock issued and outstanding. Of the 5,750,000 shares of Class B common stock originally issued, up to 750,000 shares were subject to forfeiture to the Company by the Sponsor for no consideration to the extent that the underwriter’s over-allotment option was not exercised in full or in part, so that the initial stockholders would collectively own 20% of the Company’s issued and outstanding common stock after the Initial Public Offering (excluding the Private Placement Shares). The over-allotment option was exercised in full on May 28, 2021; thus, these shares are no longer subject to forfeiture.
Common stockholders of record are entitled to one vote for each share held on all matters to be voted on by stockholders. Holders of the Class A common stock and holders of the Class B common stock will vote together as a single class on all matters submitted to a vote of stockholders, including any vote in connection with an initial Business Combination, except where a vote of each class is required by law.
The shares of Class B common stock are convertible into shares of Class A common stock at the option of the holder and will automatically convert into shares of Class A common stock at the time of an initial Business Combination on a one-for-one basis (subject to adjustment for stock splits, stock dividends, reorganizations,
F-44
DYNAMICS SPECIAL PURPOSE CORP.
NOTES TO UNAUDITED CONDENSED CONSOLIDATED FINANCIAL STATEMENTS
recapitalizations and the like). In the case that additional shares of Class A common stock, or equity-linked securities, are issued or deemed issued in excess of the amounts offered in the Initial Public Offering and related to the closing of an initial Business Combination, the ratio at which shares of Class B common stock shall convert into shares of Class A common stock will be adjusted (unless the holders of a majority of the outstanding shares of Class B common stock agree to waive such adjustment with respect to any such issuance or deemed issuance, as is the case for the proposed Senti Business Combination) so that the number of shares of Class A common stock issuable upon conversion of all shares of Class B common stock will equal, in the aggregate, on an as-converted basis, 20% of the sum of (i) the total number of all shares of common stock outstanding upon the completion of the Initial Public Offering (excluding the Private Placement Shares), plus (ii) all shares of Class A common stock and equity-linked securities issued or deemed issued in connection with an initial Business Combination (excluding any shares of Class A common stock or equity-linked securities issued, or to be issued, to any seller in an initial Business Combination and any Private Placement Shares issued to the Sponsor or its affiliates upon conversion of any Working Capital Loans).
NOTE 8. FAIR VALUE MEASUREMENTS
The following table presents information about the Company’s financial assets that are measured at fair value on a recurring basis as of March 31, 2022 and December 31, 2021, and indicates the fair value hierarchy of the valuation inputs the Company utilized to determine such fair value:
Description | Amount at Fair Value | Level 1 | Level 2 | Level 3 | ||||||||||||
March 31, 2022 | ||||||||||||||||
Assets | ||||||||||||||||
Investments held in Trust Account: | ||||||||||||||||
U.S. Treasury Securities | $ | 230,031,946 | $ | 230,031,946 | $ | — | $ | — | ||||||||
December 31, 2021 | ||||||||||||||||
Assets | ||||||||||||||||
Investments held in Trust Account: | ||||||||||||||||
U.S. Treasury Securities | $ | 230,008,784 | $ | 230,008,784 | $ | — | $ | — | ||||||||
NOTE 9. SUBSEQUENT EVENTS
The Company evaluated subsequent events and transactions that occurred after the balance sheet date up to the date that the financial statements were issued. Based upon this review, other than the amendments to the Non-Redemption Agreements discussed in Note 1, the Company did not identify any subsequent events that would have required adjustment or disclosure in the financial statements.
F-45
Report of Independent Registered Public Accounting Firm
To the Stockholders and Board of Directors
Senti Biosciences, Inc.:
Opinion on the Consolidated Financial Statements
We have audited the accompanying consolidated balance sheets of Senti Biosciences, Inc. and subsidiary (the Company) as of December 31, 2021 and 2020, the related consolidated statements of operations and comprehensive loss, redeemable convertible preferred stock and stockholders’ deficit, and cash flows for the years then ended, and the related notes (collectively, the consolidated financial statements). In our opinion, the consolidated financial statements present fairly, in all material respects, the financial position of the Company as of December 31, 2021 and 2020, and the results of its operations and its cash flows for the years then ended, in conformity with U.S. generally accepted accounting principles.
Going Concern
The accompanying consolidated financial statements have been prepared assuming that the Company will continue as a going concern. As discussed in Note 1 to the consolidated financial statements, the Company has incurred recurring losses and negative cash flows from operations, and has an accumulated deficit that raise substantial doubt about its ability to continue as a going concern. Management’s plans in regard to these matters are also described in Note 1. The consolidated financial statements do not include any adjustments that might result from the outcome of this uncertainty.
Basis for Opinion
These consolidated financial statements are the responsibility of the Company’s management. Our responsibility is to express an opinion on these consolidated financial statements based on our audits. We are a public accounting firm registered with the Public Company Accounting Oversight Board (United States) (PCAOB) and are required to be independent with respect to the Company in accordance with the U.S. federal securities laws and the applicable rules and regulations of the Securities and Exchange Commission and the PCAOB.
We conducted our audits in accordance with the standards of the PCAOB and in accordance with auditing standards generally accepted in the United States of America. Those standards require that we plan and perform the audit to obtain reasonable assurance about whether the consolidated financial statements are free of material misstatement, whether due to error or fraud. Our audits included performing procedures to assess the risks of material misstatement of the consolidated financial statements, whether due to error or fraud, and performing procedures that respond to those risks. Such procedures included examining, on a test basis, evidence regarding the amounts and disclosures in the consolidated financial statements. Our audits also included evaluating the accounting principles used and significant estimates made by management, as well as evaluating the overall presentation of the consolidated financial statements. We believe that our audits provide a reasonable basis for our opinion.
/s/ KPMG LLP
We have served as the Company’s auditor since 2019.
San Francisco, California
April 1, 2022
F-46
SENTI BIOSCIENCES, INC.
(in thousands, except share and per share data)
| December 31, | ||||||||
| 2021 | 2020 | |||||||
Assets | ||||||||
Current assets: | ||||||||
Cash and cash equivalents | $ | 56,034 | $ | 30,537 | ||||
Trade and other receivables | 483 | 88 | ||||||
Prepaid expenses and other current assets | 3,676 | 1,084 | ||||||
|
|
|
| |||||
Total current assets | 60,193 | 31,709 | ||||||
|
|
|
| |||||
Restricted cash | 3,257 | 497 | ||||||
Property and equipment, net | 12,368 | 3,312 | ||||||
Operating lease right-of-use assets | 20,708 | 12,827 | ||||||
Other long-term assets | 176 | — | ||||||
|
|
|
| |||||
Total assets | $ | 96,702 | $ | 48,345 | ||||
|
|
|
| |||||
Liabilities and Stockholders’ Deficit | ||||||||
Current liabilities: | ||||||||
Accounts payable | $ | 5,187 | $ | 914 | ||||
Early exercise liability, current portion | 626 | — | ||||||
Preferred stock tranche liability | — | 435 | ||||||
Deferred revenue | 1,656 | — | ||||||
Accrued expenses and other current liabilities | 5,331 | 1,998 | ||||||
Operating lease liabilities | 1,743 | 1,519 | ||||||
|
|
|
| |||||
Total current liabilities | 14,543 | 4,866 | ||||||
Operating lease liabilities, net of current portion | 20,988 | 12,530 | ||||||
Deferred revenue, net of current portion | 176 | — | ||||||
Early exercise liability, net of current portion | 619 | — | ||||||
|
|
|
| |||||
Total liabilities | 36,326 | 17,396 | ||||||
|
|
|
| |||||
Commitments and contingencies (Note 13) | ||||||||
Redeemable convertible preferred stock (A and B), $0.0001 par value; 99,734,554 shares authorized at December 31, 2021 and 2020; 99,734,543 and 58,948,067 shares issued and outstanding at December 31, 2021 and 2020, respectively; aggregate liquidation preference of $163.8 million and $96.8 million at December 31, 2021 and 2020, respectively | 171,833 | 89,662 | ||||||
Stockholders’ deficit: | ||||||||
Common stock, $0.0001 par value; 138,000,000 shares authorized at December 31, 2021 and 2020; 15,189,091 and 14,504,193 shares issued and outstanding at December 31, 2021 and 2020, respectively | 1 | 1 | ||||||
Additional paid-in capital | 3,618 | 1,043 | ||||||
Other comprehensive income | — | — | ||||||
Accumulated deficit | (115,076 | ) | (59,757 | ) | ||||
|
|
|
| |||||
Total stockholders’ deficit | (111,457 | ) | (58,713 | ) | ||||
|
|
|
| |||||
Total liabilities, redeemable convertible preferred stock and stockholders’ deficit | $ | 96,702 | $ | 48,345 | ||||
|
|
|
| |||||
The accompanying notes are an integral part of these consolidated financial statements.
F-47
SENTI BIOSCIENCES, INC.
Consolidated Statements of Operations and Comprehensive Loss
(in thousands)
| Year Ended December 31, | ||||||||
| 2021 | 2020 | |||||||
Revenue: | ||||||||
Contract revenue | $ | 2,291 | $ | 394 | ||||
Grant income | 470 | 172 | ||||||
|
|
|
| |||||
Total revenue | 2,761 | 566 | ||||||
Operating expenses: | ||||||||
Research and development | 21,957 | 15,956 | ||||||
General and administrative | 21,250 | 9,304 | ||||||
|
|
|
| |||||
Total operating expenses | 43,207 | 25,260 | ||||||
|
|
|
| |||||
Loss from operations | (40,446 | ) | (24,694 | ) | ||||
Other income (expense): | ||||||||
Interest income, net | 11 | 88 | ||||||
Change in fair value of convertible notes | — | (720 | ) | |||||
Change in preferred stock tranche liability | (14,742 | ) | 5,748 | |||||
Loss on impairment of fixed assets | (22 | ) | (238 | ) | ||||
Other expense | (120 | ) | (46 | ) | ||||
|
|
|
| |||||
Total other income (expense), net | (14,873 | ) | 4,832 | |||||
|
|
|
| |||||
Net loss | $ | (55,319 | ) | $ | (19,862 | ) | ||
|
|
|
| |||||
Other comprehensive gain (loss): | ||||||||
Unrealized gain (loss) on investments | $ | — | $ | (13 | ) | |||
|
|
|
| |||||
Comprehensive loss | $ | (55,319 | ) | $ | (19,875 | ) | ||
|
|
|
| |||||
Net loss per share, basic and diluted | $ | (3.72 | ) | $ | (1.43 | ) | ||
|
|
|
| |||||
Weighted-average shares outstanding, basic and diluted | 14,881,325 | 13,862,582 | ||||||
|
|
|
| |||||
The accompanying notes are an integral part of these consolidated financial statements.
F-48
SENTI BIOSCIENCES, INC.
Consolidated Statements of Redeemable Convertible Preferred Stock and Stockholders’ Deficit
(in thousands, except share data)
| Redeemable Convertible Preferred Stock | Common Stock | Additional Paid-in Capital | Accumulated Deficit | Other Comprehensive Income | Total Stockholders’ Deficit | |||||||||||||||||||||||||||
| Shares | Amount | Shares | Amount | |||||||||||||||||||||||||||||
Balance as of January 1, 2020 | 35,199,610 | $ | 57,408 | 13,679,638 | $ | 1 | $ | 438 | $ | (39,895 | ) | $ | 13 | $ | (39,443 | ) | ||||||||||||||||
Issuance of Series B redeemable convertible preferred stock, net of preferred stock tranche liability of $5.4 million and issuance costs of $0.3 million | 18,262,599 | $ | 24,314 | — | — | — | — | — | — | |||||||||||||||||||||||
Issuance of Series B redeemable convertible preferred stock, upon conversion of notes, net of preferred stock tranche liability of $0.8 million. | 5,485,858 | 7,940 | — | — | — | — | — | — | ||||||||||||||||||||||||
Issuance of common stock | — | — | 824,555 | — | 333 | — | — | 333 | ||||||||||||||||||||||||
Stock-based compensation | — | — | — | — | 272 | — | — | 272 | ||||||||||||||||||||||||
Unrealized loss on investments | — | — | — | — | — | — | (13 | ) | (13 | ) | ||||||||||||||||||||||
Net loss | — | — | — | — | — | (19,862 | ) | — | (19,862 | ) | ||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||||||||||||
Balance as of December 31, 2020 | 58,948,067 | $ | 89,662 | 14,504,193 | $ | 1 | $ | 1,043 | $ | (59,757 | ) | $ | — | $ | (58,713 | ) | ||||||||||||||||
Issuance of Series B redeemable convertible preferred stock, including extinguishment of preferred stock tranche liability of $15.2 million, net of issuance costs of $6 thousand | 40,786,476 | 82,171 | — | — | — | — | — | — | ||||||||||||||||||||||||
Issuance of common stock | — | — | 3,103,769 | — | 1,525 | — | — | 1,525 | ||||||||||||||||||||||||
Early exercise of common stock options | — | — | (2,619,677 | ) | — | (1,329 | ) | — | — | (1,329 | ) | |||||||||||||||||||||
Vesting of early exercise of common stock options | — | — | 200,806 | — | 84 | — | — | 84 | ||||||||||||||||||||||||
Stock-based compensation | — | — | — | — | 2,295 | — | — | 2,295 | ||||||||||||||||||||||||
Net loss | — | — | — | — | — | (55,319 | ) | — | (55,319 | ) | ||||||||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||||||||||||
Balance as of December 31, 2021 | 99,734,543 | $ | 171,833 | 15,189,091 | $ | 1 | $ | 3,618 | $ | (115,076 | ) | $ | — | $ | (111,457 | ) | ||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||||||||||||
The accompanying notes are an integral part of these consolidated financial statements.
F-49
SENTI BIOSCIENCES, INC.
Consolidated Statements of Cash Flows
(in thousands)
| Year Ended December 31, | ||||||||
| 2021 | 2020 | |||||||
Cash flows from operating activities | ||||||||
Net loss | $ | (55,319 | ) | $ | (19,862 | ) | ||
Adjustments to reconcile net loss to net cash from operating activities: | ||||||||
Depreciation | 769 | 564 | ||||||
Amortization of operating lease right-of-use assets | 2,241 | 1,421 | ||||||
Accretion of discount on short-term investments | — | (3 | ) | |||||
Change in fair value of convertible notes | — | 720 | ||||||
Change in preferred stock tranche liability | 14,742 | (5,748 | ) | |||||
Stock-based compensation expense | 2,295 | 272 | ||||||
Loss on impairment of fixed assets | 22 | 238 | ||||||
Changes in assets and liabilities: | ||||||||
Accounts receivable | (395 | ) | (10 | ) | ||||
Prepaid expenses and other assets | (1,642 | ) | (231 | ) | ||||
Accounts payable | (617 | ) | (324 | ) | ||||
Accrued expenses and other current liabilities | 2,574 | (37 | ) | |||||
Deferred revenue | 1,832 | 165 | ||||||
Operating lease liabilities | (1,137 | ) | (1,338 | ) | ||||
|
|
|
| |||||
Net cash from operating activities | (34,635 | ) | (24,173 | ) | ||||
|
|
|
| |||||
Cash flows from investing activities | ||||||||
Purchase of short-term investments | — | (446 | ) | |||||
Maturity of short-term investments | — | 12,965 | ||||||
Purchases of property and equipment | (5,543 | ) | (1,161 | ) | ||||
|
|
|
| |||||
Net cash from investing activities | (5,543 | ) | 11,358 | |||||
|
|
|
| |||||
Cash flows from financing activities | ||||||||
Proceeds from issuance of common stock upon exercise of stock options | 1,500 | 333 | ||||||
Proceeds from issuance of notes converted to Series B redeemable convertible preferred stock | — | 8,000 | ||||||
Proceeds from issuance of Series B redeemable convertible preferred stock | 67,000 | 30,000 | ||||||
Payment of redeemable convertible preferred stock issuance costs | (48 | ) | (282 | ) | ||||
|
|
|
| |||||
Net cash from financing activities | $ | 68,435 | $ | 38,051 | ||||
|
|
|
| |||||
Net change in cash and cash equivalents | 28,257 | 25,236 | ||||||
Cash, cash equivalents, and restricted cash, beginning of the year | 31,034 | 5,798 | ||||||
|
|
|
| |||||
Cash, cash equivalents, and restricted cash, end of the year | $ | 59,291 | $ | 31,034 | ||||
|
|
|
| |||||
Supplemental disclosures of noncash financing and investing items | ||||||||
Purchase of property and equipment in accounts payable and accrued expenses | $ | 4,439 | $ | 39 | ||||
Conversion of convertible notes to Series B redeemable convertible preferred stock and Series B preferred stock tranche liability | — | 8,720 | ||||||
Recognition of Series B preferred stock tranche liability | 33 | 6,183 | ||||||
Extinguishment of Series B preferred stock tranche liability | 15,210 | — | ||||||
Deferred transaction costs related to pending business combination in accounts payable and accrued expenses | 1,429 | — | ||||||
Receivables in transit from issuance of common stock upon exercise of stock options | 25 | — | ||||||
The accompanying notes are an integral part of these consolidated financial statements.
F-50
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
1. Organization and Description of Business
Senti Biosciences, Inc. or (the “Company”), was incorporated under the laws of the State of Delaware in June 2016, and is a biotechnology company that programs next-generation cell and gene therapies with what we refer to as “gene circuits.” The Company is headquartered in South San Francisco, California.
Liquidity and Going Concern
The Company has devoted substantially all of its efforts to organizing and staffing, business planning, raising capital, and conducting preclinical studies and has not realized substantial revenues from its planned principal operations. In addition, the Company has a limited operating history, has incurred recurring operating losses and negative cash flows from operations since inception, has an accumulated deficit, has funded its operations primarily with proceeds from sale of redeemable convertible preferred stock and the issuance of convertible notes, and expects that it will continue to incur net losses and negative cash flows from operations into the foreseeable future, particularly as the Company advances its preclinical activities and clinical trials for its product candidates in development.
The Company’s continued existence is dependent upon management’s ability to develop profitable operations. Management is devoting substantially all of its efforts to developing its business and raising capital and there can be no assurance that the Company’s efforts will be successful. No assurance can be given that management’s actions will result in profitable operations or the meeting of ongoing liquidity needs.
The accompanying consolidated financial statements have been prepared on a going concern basis, which contemplates the realization of assets and satisfaction of liabilities in the normal course of business. In 2021 and 2020, the Company received aggregate proceeds of $67.0 million and $30.0 million, respectively, (Note 6) from the issuance of its Series B redeemable convertible preferred stock. Additionally, in 2020, the Company received $8.0 million from the issuance of promissory notes (Note 5). As of December 31, 2021, the Company had an accumulated deficit of $115.1 million, and cash, cash equivalents and restricted cash of $59.3 million. As of December 31, 2020, the Company had an accumulated deficit of $59.8 million, and cash, cash equivalents and restricted cash of $31.0 million.
As of April 1, 2022, the issuance date of the consolidated financial statements as of and for the year ended December 31, 2021, the Company expects that its cash and cash equivalents will not be sufficient to fund its operating expenses and capital expenditure requirements for at least one year from the issuance date of the consolidated financial statements and therefore the Company concluded that substantial doubt existed about the Company’s ability to continue as a going concern.
The Company is seeking to complete a liquidity event via a special purpose acquisition company (“SPAC”) (see pending merger with Dynamics Special Purpose Corp. below). Upon the completion of a qualified public offering on specified terms (Note 6), the Company’s outstanding convertible preferred stock will automatically convert into shares of common stock. These plans are intended to mitigate the relevant conditions or events that raise substantial doubt about the Company’s ability to continue as a going concern; however, as the plans are not entirely within the Company’s control, management cannot assure they will be effectively implemented. In the event the Company does not complete a SPAC merger, the Company expects to seek additional funding through private equity financings, debt financings, collaborations, licensing arrangements, and/or strategic alliances. The Company may not be able to obtain financing on acceptable terms, or at all, and the Company may not be able to enter into collaborations or other such arrangements. The terms of any financing may adversely affect the holdings or the rights of the Company’s stockholders. If the Company is unable to raise capital when needed, or on attractive terms, it could be forced to delay, reduce or eliminate its research or drug development programs or any future commercialization efforts.
F-51
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
Pending Merger with Dynamics Special Purpose Corp.
On December 19, 2021, the Company entered into a Business Combination Agreement with Dynamics Special Purpose Corp. (“DYNS”), a publicly traded SPAC. Under the terms of the proposed transaction, DYNS will merge with the Company at an estimated combined enterprise value of approximately $276.0 million. The cash components of the transaction will be funded by DYNS’ cash in trust of $230.0 million (assuming no redemptions) as well as a $66.8 million private placement of common stock at $10.00 per share from various accredited investors.
2. Summary of Significant Accounting Policies and Basis of Presentation
Basis of Presentation
The accompanying consolidated financial statements have been prepared in conformity with generally accepted accounting principles in the United States of America (“U.S. GAAP”) and the rules and regulations of the Securities and Exchange Commission (“SEC”). Any reference in these notes to applicable guidance is meant to refer to the authoritative U.S. GAAP as found in the Accounting Standards Codification (“ASC”) and as amended by Accounting Standards Updates (“ASU”) of the Financial Accounting Standards Board (“FASB”). The consolidated financial statements include the accounts of Senti Biosciences, Inc., and its wholly-owned subsidiary. All intercompany balances and transactions have been eliminated in consolidation. We have one business activity and operate in one reportable segment.
Use of Estimates
The preparation of consolidated financial statements in conformity with U.S. GAAP requires management to make certain estimates, judgments, and assumptions that affect the reported amounts of assets and liabilities, the disclosure of contingent assets and liabilities at the date of the consolidated financial statements and the reported amounts of revenues and expenses during the reporting period. Significant estimates and assumptions reflected in these consolidated financial statements include, but are not limited to, the accrual for research and development expenses, the valuation of stock-based awards, the valuation of convertible notes, the valuation of common and redeemable convertible preferred stock, the valuation of preferred stock tranche liability, standalone selling price (“SSP”) and the determination of the incremental borrowing rate. Actual results could differ from those estimates, and such differences could be material to the financial position and consolidated statements of operations and comprehensive loss.
Impact of the COVID-19 Coronavirus
During 2021, widespread availability of COVID-19 vaccines in the United States and elsewhere in the world, combined with government assistance programs, fiscal policies and other factors, led to a rebound in the global economy as several states and countries began to re-open and loosen many COVID-19 related restrictions. Nonetheless, the COVID-19 pandemic remains a global health crisis and continues to evolve. Despite the emergence of new variants, increased public safety measures and deployment of vaccines, including vaccine boosters, to slow the spread of the virus have resulted in substantial improvements in the global economy throughout 2021 and into early 2022. As of December 31, 2021, we were operating at pre-pandemic levels.
Concentration of Credit Risk
Financial instruments that potentially subject the Company to a significant concentration of credit risk consist of cash, cash equivalents, and short-term investments that are maintained in checking and money market
F-52
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
accounts at one financial institution, which at times, may exceed federally insured limits. The Company’s short-term investments, if any, are limited to certain types of debt securities issued by the U.S. government, its agencies, and institutions with investment-grade credit ratings, and places restrictions on maturities and concentration by type and issuer. The Company believes that it is not exposed to significant credit risk due to the financial position of the institutions in which those deposits and short-term investments are held. As of December 31, 2021 and 2020, the Company has not experienced any credit losses in such accounts or investments.
Cash, Cash Equivalents, and Restricted Cash
Cash equivalents consist of amounts deposited in money market funds and securities with original maturity dates of three months or less, which are stated at fair value.
The Company’s restricted cash consists of cash deposited with a financial institution as collateral for a letter of credit required under the Company’s headquarters and research facility leases. The restricted cash is presented separately from cash and cash equivalents and classified as non-current on the balance sheet, as the Company expects the cash to remain restricted for a period greater than one year.
The following table provides a reconciliation of cash and cash equivalents and restricted cash reported within the consolidated balance sheets that total to the amounts shown in the consolidated statements of cash flows for the Company:
| December 31, | ||||||||
| 2021 | 2020 | |||||||
Cash and cash equivalents | 56,034 | 30,537 | ||||||
Restricted cash | 3,257 | 497 | ||||||
|
|
|
| |||||
Total | $ | 59,291 | $ | 31,034 | ||||
|
|
|
| |||||
Short-term Investments
Investments in marketable securities with original maturities less than 12 months from the balance sheet date, if any, are classified as short-term investments. Investments with original maturities of greater than 12 months from the balance sheet date, if any, are classified as long-term. The Company classifies all of its investments as available-for-sale and records such assets at estimated fair value in the balance sheet, with unrealized gains and losses, if any, reported as a component of other comprehensive loss within the consolidated statement of operations and comprehensive loss, and as a separate component of stockholders’ equity. These investments consist of corporate debt securities, U.S. Government securities, asset-based securities, and commercial paper, which are subject to minimal credit and market risk. The Company uses the specific identification method to determine the amount of realized gains or losses on sales of marketable securities. Realized gains and losses on sales of securities and declines in the fair value of securities judged to be other than temporary are included in other income or expense. Unrealized gains and losses are included in other comprehensive loss. Interest on available-for-sale securities is included in interest income in the consolidated statements of operations and comprehensive loss.
Fair Value Measurements
Certain assets and liabilities of the Company are carried at fair value under U.S. GAAP. Fair value is defined as the exchange price that would be received for an asset or the exit price that would be paid to transfer a
F-53
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
liability in the principal or most advantageous market for the asset or liability in an orderly transaction between market participants on the measurement date. Valuation techniques used to measure fair value must maximize the use of observable inputs and minimize the use of unobservable inputs. The authoritative guidance on fair value measurements establishes a three-tier fair value hierarchy for disclosure of fair value measurements as follows:
| • | Level 1 – Quoted prices in active markets for identical assets or liabilities. |
| • | Level 2 – Observable inputs (other than Level 1 quoted prices), such as quoted prices in active markets for similar assets or liabilities, quoted prices in markets that are not active for identical or similar assets or liabilities, or other inputs that are observable or can be corroborated by observable market data. |
| • | Level 3 – Unobservable inputs that are supported by little or no market activity that are significant to determining the fair value of the assets or liabilities, including pricing models, discounted cash flow methodologies, and similar techniques. |
To the extent that the valuation is based on models or inputs that are less observable or unobservable in the market, the determination of fair value requires more judgment. Accordingly, the degree of judgment exercised by the Company in determining fair value is greatest for instruments categorized in Level 3. Financial assets and liabilities are classified in their entirety based on the lowest level of input that is significant to the fair value measurement.
The estimated fair values of the Company’s cash and cash equivalents, restricted cash, trade, and other receivables and accounts payable approximate their carrying values given their short-term nature.
The Company’s convertible notes and preferred stock tranche liability were carried at fair value from the date of issuance through their respective extinguishment in October 2020 and May 2021, and were determined using Level 3 inputs in the fair value hierarchy described above.
Property and Equipment, Net
Property and equipment, net is stated at cost, net of accumulated depreciation. Depreciation is calculated using the straight-line method over the estimated useful lives of the assets, which are as follows:
Small equipment | 2 years | |||
Computer equipment and software | 3 years | |||
Laboratory equipment | 5-7 years | |||
Furniture and fixtures | 5-7 years | |||
Leasehold improvements | Shorter of the lease term and the useful life |
The Company capitalizes certain costs incurred during the construction phase of a project or asset into construction-in-progress. Once the construction is complete and the asset is placed into service, we transfer its carrying value into the appropriate fixed asset category and begin depreciating the value over its useful life.
When assets are retired or disposed of, any resulting gain or loss is included in net loss. Expenditures for maintenance and repairs are expensed as incurred.
Impairment of Long-Lived Assets
The Company evaluates its long-lived assets, such as property and equipment, net, for impairment whenever events or changes in circumstances indicate that the carrying value of assets may not be recoverable.
F-54
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
Recoverability of these assets is measured by comparing their carrying value to the future net undiscounted cash flows the assets are expected to generate over their remaining economic life. If such assets are considered to be impaired, the amount of any impairment is measured as the difference between their carrying value and their fair value. If the useful life is shorter than originally estimated, the Company amortizes the remaining carrying value over the revised shorter useful life.
Leases
The Company determines if an arrangement is or contains a lease at inception. Operating leases are recorded on the consolidated balance sheets with right-of-use assets (“ROU”) representing the Company’s right to use an underlying asset for the lease term and lease liabilities representing the Company’s obligation to make lease payments. Operating lease ROU assets and liabilities are recognized at the lease commencement date based on the present value of lease payments over the lease term. Operating lease ROU assets also include the effect of any lease payments made prior to or on lease commencement and excludes lease incentives and initial direct costs incurred, as applicable. As the implicit rate in the Company’s leases is typically unknown, the Company uses its incremental borrowing rate based on the information available at the lease commencement date in determining the present value of future lease payments. The Company gives consideration to its credit risk, the term of the lease, and total lease payments and adjusts for the impacts of collateral as necessary when calculating its incremental borrowing rates. The lease terms may include options to extend or terminate the lease when it is reasonably certain that the Company will exercise that option. Operating lease expense is recognized on a straight-line basis over the lease term. Variable lease payments are recorded as an expense in the period incurred.
The Company has elected to not separate lease and non-lease components for any leases within its existing classes of assets and, as a result, accounts for any lease and non-lease components as a single lease component. The Company has also elected not to apply the recognition requirement for leases with a term of 12 months or less.
Revenue Recognition
Contract Revenue
Revenue is recognized when a customer obtains control of promised goods or services. The Company applies the following five steps to recognize revenue: (i) identify the contract with a customer; (ii) identify the performance obligations in the contract; (iii) determine the transaction price; (iv) allocate the transaction price to performance obligations in the contract; and (v) recognize revenue when (or as) the performance obligations are satisfied.
A performance obligation is defined as a promise to transfer a product or a service to a customer that is distinct. A product or a service is distinct if both (i) the customer can benefit from the product or the service either on its own or together with other resources that are readily available to the customer and (ii) the Company’s promise to transfer the product or the service to the customer is separately identifiable from other promises in the contract. Each distinct promise to transfer a product or a service is a unit of accounting for revenue recognition. If a promise to transfer a product or a service is not distinct from other promises in the contract, such promises should be combined into a single performance obligation. The assessment of each of these elements may require significant judgments.
Arrangements that include rights to additional goods or services that are exercisable at a customer’s discretion are generally considered options. If these options provide a material right to the customer, they are
F-55
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
considered performance obligations. The identification of material rights requires judgments related to the determination of the value of the underlying license relative to the option exercise price, including assumptions about technical feasibility and the probability of developing a candidate that would be subject to the option rights.
The transaction price is the amount of consideration the Company is entitled to receive in exchange for the transfer of control of a product or a service to a customer. The Company’s agreements may include both fixed and variable consideration. Fixed payments are included in the transaction price, while variable consideration, such as milestone payments and fees for research services, are estimated and constrained (if required) at the inception of the contract and evaluated on a periodic basis thereafter.
If a contract has multiple performance obligations, the Company allocates the transaction price to each distinct performance obligation based on the relative stand-alone selling price (“SSP”) of the performance obligation. The Company determines SSP at contract inception and at contract modification. Determining the SSP for performance obligations requires significant judgment. Changes in the key assumptions used to determine the SSP could have a significant effect on the allocation of arrangement consideration between multiple performance obligations.
For each distinct performance obligation, revenue is recognized as the Company transfers control of the product or the service applicable to such performance obligations. In instances where the Company first receives consideration in advance of satisfying its performance obligation, the Company classifies such consideration as deferred revenue until the Company satisfies such performance obligations. In instances where the Company first satisfies its performance obligation prior to its receipt of consideration, the consideration is a contract asset recorded in prepaid expenses and other current assets on the consolidated balance sheets.
Grant Income
The Company receives government grants that reimburse the Company for certain allowable costs for funded projects. Grant income is recognized on a systematic basis over the period in which the Company recognizes qualified research and development costs that grant is intended to compensate and there is reasonable assurance that the Company will meet the terms and conditions of the grant. This income is recorded as grant income in the consolidated statements of operations and comprehensive loss.
Grant payments received in excess of grant revenue earned are recognized as deferred revenue on the balance sheets, and grant income earned in excess of grant payments received is recognized as trade and other receivables on the consolidated balance sheets.
Research and Development Expenses
Research and development costs are expensed as incurred. Research and development costs consist of salaries and other personnel-related expenses, including associated stock-based compensation, lab supplies and services, in-license and technology costs, consulting and sponsored research fees, facility costs and depreciation expense.
Nonrefundable advance payments for goods and services that will be used or received in future research and development activities are deferred and recognized as an expense in the period in which the related goods are delivered, or services are performed.
F-56
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
The Company has acquired and may continue to acquire the rights to gene circuit or other technologies from third parties. The upfront payments to acquire a license, product, or rights, as well as any annual maintenance charges and future milestone payments, are immediately recognized as research and development expense provided that there is no alternative future use of the rights in other research and development projects.
Deferred Offering Costs
Deferred offering costs consists of incremental legal, accounting and other fees directly attributable to equity offerings. Deferred offering costs are capitalized within prepaid and other current assets on the consolidated balance sheets and are offset against proceeds of the offering in the consolidated statements of redeemable convertible preferred stock and stockholders’ deficit as a reduction of additional paid-in capital upon the completion of the equity offering. In the event the equity offering is terminated, all of the deferred offering costs are expensed within the Company’s consolidated statements of operations and comprehensive loss. For the year ended December 31, 2021 the Company expensed $2.2 million of previously deferred offering costs related to the suspended IPO within general and administrative expense on the consolidated statement of operations and comprehensive loss. As of December 31, 2021, the Company has recorded $1.4 million of deferred offering costs related to the pending SPAC merger that is included in prepaids and other current assets. There were no deferred offering costs as of December 31, 2020.
Commitments and Contingencies
The Company recognizes a liability with regard to loss contingencies when it believes it is probable a liability has occurred and the amount can be reasonably estimated. If some amount within a range of loss appears at the time to be a better estimate than any other amount within the range, the Company accrues that amount. When no amount within the range is a better estimate than any other amount, the Company accrues the minimum amount in the range. The Company has not recorded any such liabilities as of December 31, 2021 and 2020.
Fair Value Option for Convertible Notes
The Company elected to account for its convertible notes at fair value as of the issuance date in order to measure those liabilities at amounts that more accurately reflect the current economic environment in which the Company operates. Accordingly, the Company recorded these convertible notes issued in August 2020 at fair value with changes in fair value recognized in change in fair value of convertible notes in the consolidated statements of operations and comprehensive loss. As a result of applying the fair value option, direct costs and fees related to the convertible notes were expensed in the period incurred.
Accretion and Classification of Redeemable Convertible Preferred Stock
The Company’s redeemable convertible preferred stock is recorded based on proceeds received, net of the related preferred stock tranche liability and issuance costs, and is classified outside of stockholders’ deficit on the consolidated balance sheets because the holders of such shares have liquidation rights in the event of a deemed liquidation that, in certain situations, are not solely within the control of the Company and would require the redemption of the then-outstanding redeemable convertible preferred stock. The Company’s Series A and Series B redeemable convertible preferred stock are subject to liquidation, dissolution, or winding up of the Company, either voluntary or involuntary (Note 6). Because the occurrence of a deemed liquidation event is not currently probable as of December 31, 2021, the carrying values of the redeemable convertible preferred stock are not being accreted to their redemption values. Subsequent adjustments to accrete the carrying values of the redeemable convertible preferred stock to its redemption price would be made only when a deemed liquidation event becomes probable.
F-57
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
Preferred Stock Tranche Liability
The Company’s Series B redeemable convertible preferred stock included an obligation whereby the investors agreed to buy, and the Company agreed to sell additional shares at a fixed price in the event that certain agreed-upon milestones were achieved or at the election of investors. This obligation was determined to be a freestanding financial instrument that should be accounted for as a liability at fair value (Notes 3 and 6). This preferred stock tranche liability was revalued at each reporting period through settlement with changes in the fair value recorded as a change in preferred stock tranche liability in the consolidated statements of operations and comprehensive loss. The fair value at settlement was reclassified to redeemable convertible preferred stock at such time.
Stock-Based Compensation
The Company recognizes stock-based compensation expense related to employees and non-employees based on the grant date fair value of the awards. For awards that vest solely based on continued service, stock-based compensation expense is recognized in the consolidated statements of operations using the straight-line method. For performance and market awards, stock-based compensation expense is recognized over the requisite service period using the accelerated attribution method. No compensation expense will be recognized for awards subject to performance conditions until it is probable that the performance condition will be met.
The Company has allowed specified option holders to exercise unvested options. The options that are exercised prior to vesting continue to vest according to the respective option agreement, and such unvested shares are subject to repurchase by the Company at the option holder’s original exercise price in the event the option holder’s service with the Company voluntarily or involuntarily terminates.
The Company records proceeds from the early exercise of options as a current and long-term liability in the consolidated balance sheet, and reclassifies this liability to additional paid-in capital as the Company’s repurchase right lapses. The shares purchased by the option holders pursuant to the early exercise of stock options are not deemed, for accounting purposes, to be outstanding until those shares have vested.
Net Loss Per Share
The Company follows the two-class method when computing net loss per share as the Company has issued shares that meet the definition of participating securities. The two-class method determines net loss per share for each class of common and participating securities according to dividends declared or accumulated and participation rights in undistributed earnings. The two-class method requires loss available to common stockholders for the period to be allocated between common and participating securities based upon their respective rights to share in undistributed earnings as if all loss for the period had been distributed.
Basic net loss per share attributable to common stockholders is computed by dividing net loss attributable to common stockholders by the weighted-average number of common shares outstanding for the period. Diluted net loss per share attributable to common stockholders is computed by adjusting net loss attributable to common stockholders for an allocation of the undistributed earnings and dividing it by the weighted-average number of common shares outstanding for the period, including potential dilutive common shares. For purposes of this calculation, the Company’s outstanding stock options, redeemable convertible preferred stock, and potential issuance of redeemable convertible preferred stock under existing preferred stock tranches, are considered potential dilutive common shares.
The Company’s participating securities contractually entitle the holders of such securities to participate in dividends but do not contractually require the holders of such securities to participate in losses of the Company.
F-58
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
Accordingly, in periods in which the Company reports a net loss, such losses are not allocated to such participating securities. In periods in which the Company reports a net loss attributable to common stockholders, diluted net loss per share attributable to common stockholders is the same as basic net loss per share attributable to common stockholders, since dilutive common shares are not assumed to have been issued if their effect is anti-dilutive.
Income Taxes
The Company accounts for income taxes under the asset and liability method, which requires the recognition of deferred tax assets and liabilities for the expected future tax consequences of events that have been included in the consolidated financial statements. Under this method, deferred tax assets and liabilities are determined on the basis of the differences between the consolidated financial statements and tax basis of assets and liabilities using enacted tax rates in effect for the year in which the differences are expected to reverse. The effect of a change in tax rates on deferred tax assets and liabilities is recognized in the consolidated statement of operations in the period that includes the enactment date.
The Company recognizes net deferred tax assets to the extent that the Company believes these assets are more likely than not to be realized. In making such a determination, management considers all available positive and negative evidence, including future reversals of existing taxable temporary differences, projected future taxable income, tax-planning strategies, and results of recent operations. If management determines that the Company would be able to realize its deferred tax assets in the future in excess of their net recorded amount, management would make an adjustment to the deferred tax asset valuation allowance, which would reduce the provision for income taxes.
The Company records uncertain tax positions on the basis of a two-step process whereby (i) management determines whether it is more likely than not that the tax positions will be sustained on the basis of the technical merits of the position and (ii) for those tax positions that meet the more-likely-than-not recognition threshold, management recognizes the largest amount of tax benefit that is more than 50 percent likely to be realized upon ultimate settlement with the related tax authority. The Company recognizes interest and penalties related to unrecognized tax benefits within income tax expense. Any accrued interest and penalties are included within the related tax liability. To date, there have been no interest charges or penalties related to unrecognized tax benefits.
Recently Adopted Accounting Pronouncements
In June 2016, the FASB issued ASU No. 2016-13, Financial Instruments-Credit Losses (Topic 326), which requires entities to measure all expected credit losses for financial assets held at the reporting date based on historical experience, current conditions, and reasonable and supportable forecasts. This replaces the existing incurred loss model and is applicable to the measurement of credit losses on financial assets measured at amortized cost. For trade receivables and other instruments, a new forward-looking expected loss model that generally results in the earlier recognition of allowances for losses will be required. The Company adopted this standard as of January 1, 2021, which did not have a material impact on its consolidated financial statements.
In August 2018, the FASB issued ASU No. 2018-13, Fair Value Measurement (Topic 820), which eliminates, modifies, and adds disclosure requirements for fair value measurements. The Company adopted this standard as of January 1, 2021, and modified its disclosures accordingly. The standard did not have a material impact on the Company’s consolidated financial statements.
In November 2018, the FASB issued ASU No. 2018-18, Collaborative Arrangements, which clarifies that certain transactions between collaborative arrangement participants should be accounted for as revenue when the
F-59
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
collaborative arrangement participant is a customer in the context of a unit of account and precludes recognizing as revenue consideration received from a collaborative arrangement participant if the participant is not a customer. The Company adopted this standard as of January 1, 2021 which did not have a material impact on its consolidated financial statements.
Accounting Pronouncements Not Yet Adopted
In December 2019, the FASB issued ASU No. 2019-12, Simplifying the Accounting for Income Taxes (Topic 740), which removes certain exceptions to the general principles in Topic 740 and improves consistent application of and simplifies GAAP for other areas of Topic 740 by clarifying and amending existing guidance. This ASU is effective for fiscal years beginning after December 15, 2021, and interim periods within those fiscal years with early adoption permitted. The Company is currently evaluating the impact of this standard but does not expect the adoption will have a material impact on its consolidated financial statements and related disclosures.
In March 2020, the Financial Accounting Standards Board issued ASU No. 2020-03, Codification Improvements to Financial Instruments. This standard improves and clarifies various financial instruments topics and includes seven different issues that describe the areas of improvement and the related amendments to GAAP that are intended to make the standards easier to understand and apply by eliminating inconsistencies and providing clarifications. This ASU is effective January 1, 2023 with early adoption permitted. The Company is currently evaluating the impact of this standard.
In August 2020, the FASB issued ASU No. 2020-06, Debt—Debt with Conversion and Other Options (Subtopic 470-20) and Derivatives and Hedging—Contracts in Entity’s Own Equity (Subtopic 815-40): Accounting for Convertible Instruments and Contracts in an Entity’s Own Equity, which simplifies accounting for convertible instruments by removing major separation models required under current GAAP. The ASU removes certain settlement conditions that are required for equity contracts to qualify for the derivative scope exception and it also simplifies the diluted earnings per share calculation in certain areas. This standard is effective for fiscal years beginning after December 15, 2023, including interim periods within those fiscal years with early adoption permitted. The Company is currently evaluating the impact of this standard on its consolidated financial statements and related disclosures.
In October 2020, the FASB issued ASU No. 2020-10, Codification Improvements, which moves all disclosure guidance to the appropriate codification section and makes other improvements and technical corrections. The standard is effective for fiscal years beginning after December 15, 2021, including interim periods within those fiscal years with early adoption permitted. The Company is currently evaluating the impact of this standard on its consolidated financial statements and related disclosures.
In November 2021, the FASB issued ASU 2021-10, Government Assistance (Topic 832) - Disclosures by Business Entities about Government Assistance, which seeks to increase the transparency of government assistance including the disclosure of (1) the types of assistance, (2) an entity’ accounting for the assistance, and (3) the effect of the assistance on an entity’s financial statements. Diversity currently exists in the recognition, measurement, presentation, and disclosure of government assistance received by business entities because of the lack of specific authoritative guidance in U.S. GAAP. ASU 2021-10 is effective for fiscal years beginning after December 15, 2021. Early application of the amendments is permitted. The Company is currently evaluating the impact of this standard on its consolidated financial statements and related disclosures.
In May 2021, the FASB issued ASU 2021-04 Earnings Per Share (Topic 260), Debt-Modifications and Extinguishments (Subtopic 370-50), Compensation-Stock Compensation (Topic 718),and Derivatives and
F-60
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
Hedging-Contracts in Entity’s Own Equity (Subtopic 815-40); Issuer’s Accounting for Certain Modifications or Exchanges of Freestanding Equity-Classified Written Call Options (a consensus of the FASB Emerging Issues Task Force), which clarifies and reduces diversity in an issuer’s accounting for modifications or exchanges of freestanding equity-classified written call options that remain equity classified after modification or exchange. The standard is effective for all entities for fiscal years beginning after December 15, 2021. Adoption of this standard will not have a material impact on the Company’s consolidated financial statements.
3. Fair Value Measurements
The following tables summarize the estimated value of cash equivalents, restricted cash and short-term investments (in thousands):
| December 31, 2021 | ||||||||||||||||
| Amortized Cost | Unrealized Gain | Unrealized Loss | Estimated Fair Value | |||||||||||||
Cash equivalents: | ||||||||||||||||
Money market fund | $ | 56,034 | $ | — | $ | — | $ | 56,034 | ||||||||
Restricted cash: | ||||||||||||||||
Money market fund | 3,257 | $ | — | $ | — | 3,257 | ||||||||||
|
|
|
|
|
|
|
| |||||||||
Total | $ | 59,291 | $ | — | $ | — | $ | 59,291 | ||||||||
|
|
|
|
|
|
|
| |||||||||
| December 31, 2020 | ||||||||||||||||
| Amortized Cost | Unrealized Gain | Unrealized Loss | Estimated Fair Value | |||||||||||||
Cash equivalents: | ||||||||||||||||
Money market fund | $ | 30,387 | $ | — | $ | — | $ | 30,387 | ||||||||
Restricted cash: | ||||||||||||||||
Money market fund | 497 | — | — | 497 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Total | $ | 30,884 | $ | — | $ | — | $ | 30,884 | ||||||||
|
|
|
|
|
|
|
| |||||||||
Financial assets and liabilities measured and recognized at fair value are as follows (in thousands):
| December 31, 2021 | ||||||||||||||||
| Level 1 | Level 2 | Level 3 | Total | |||||||||||||
Assets: | ||||||||||||||||
Cash equivalents: | ||||||||||||||||
Money market fund | $ | 56,034 | $ | — | $ | — | $ | 56,034 | ||||||||
Restricted cash: | ||||||||||||||||
Money market fund | 3,257 | — | — | 3,257 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Total Assets | $ | 59,291 | $ | — | $ | — | $ | 59,291 | ||||||||
|
|
|
|
|
|
|
| |||||||||
F-61
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
| December 31, 2020 | ||||||||||||||||
| Level 1 | Level 2 | Level 3 | Total | |||||||||||||
Assets: | ||||||||||||||||
Cash equivalents: | ||||||||||||||||
Money market fund | $ | 30,387 | $ | — | $ | — | $ | 30,387 | ||||||||
Restricted cash: | ||||||||||||||||
Money market fund | 497 | 497 | ||||||||||||||
|
|
|
|
|
|
|
| |||||||||
Total Assets | $ | 30,884 | $ | — | $ | — | $ | 30,884 | ||||||||
|
|
|
|
|
|
|
| |||||||||
Liabilities: | ||||||||||||||||
Preferred stock tranche liability | $ | — | $ | — | $ | 435 | $ | 435 | ||||||||
|
|
|
|
|
|
|
| |||||||||
Total Liabilities | $ | — | $ | — | $ | 435 | $ | 435 | ||||||||
|
|
|
|
|
|
|
| |||||||||
No securities have contractual maturities of longer than one year. There were no transfers between Levels 1, 2, or 3 for any of the periods presented.
Convertible Notes
Due to certain embedded features within the convertible notes (Note 5), the Company elected to account for the convertible notes under the fair value option.
At issuance in August 2020, the convertible notes were recorded at fair value of $8.9 million, resulting in a loss on issuance of $0.9 million which is included in the change in fair value of convertible note.
The fair value of the convertible notes at issuance was determined using a probability-weighted income approach as the convertible notes contained various settlement outcomes. The following reflects the significant quantitative inputs used to fair value the convertible notes at issuance.
| On Issuance | ||||
Interest rate | 8.00 | % | ||
Discount rate | 6.78 | % | ||
Time to maturity (years) | 0.49 | |||
Probability of automatic conversion upon qualified financing | 95.0 | % | ||
Probability of optional conversion | 2.5 | % | ||
Probability of no conversion | 2.5 | % | ||
Conversion Price | $ | 1.4784 | ||
In connection with the issuance and sale of Series B redeemable convertible preferred stock in October 2020 (Note 6), all of the outstanding principal and accrued interest of $8.1 million under the convertible notes was converted into 5,485,858 shares of Series B redeemable convertible preferred stock and the related preferred stock tranche liability. The fair value of the convertibles notes of $8.7 million on the date of conversion was determined using the Backsolve method based on the price of the Series B redeemable convertible preferred stock and, if purchased, the related preferred stock tranche liability.
F-62
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
The following table provides a roll-forward of the fair value of the convertible notes (in thousands):
| Fair Value | ||||
Proceeds from issuance in August 2020 | $ | 8,000 | ||
Change in fair value of convertible notes | 720 | |||
Conversion to Series B redeemable convertible preferred stock | (7,940 | ) | ||
Recognition of preferred stock tranche liability | (780 | ) | ||
|
| |||
Balance as of December 31, 2020 | $ | — | ||
|
| |||
Preferred Stock Tranche Liability
The initial and subsequent fair values of the preferred stock tranche liability recognized in connection with the issuance of Series B redeemable convertible preferred stock financing were determined with the assistance of a third-party valuation specialist using significant inputs not observable in the market which constitute Level 3 measurements within the fair value hierarchy.
The following reflects the significant quantitative inputs used in the valuation of the preferred stock tranche liability for fiscal year 2020 on initial closing on October 22, 2020, second closing on December 28, 2020 and subsequent measurement as of December 31, 2020 using a Monte Carlo valuation model and/or Black-Scholes option pricing model:
| October 22, 2020 Initial Measurement Date | December 28 and December 31, 2020 Subsequent Measurement Dates | |||||||
| Tranche 2 Call Option | Tranche 3 Call Option | Tranche Features 2 and 3 Call Option | Tranche 2 and 3 Forward Contracts | |||||
Estimated fair value of Series B redeemable convertible preferred stock(1) | $1.25 | $1.25 | $1.62 | $1.62 | ||||
Discount rate | 0.12% | 0.17% | 0.11% | 0.11% | ||||
Time to liquidity (years) | 0.9 | 2.2 | 0.5 | 0.5 | ||||
Expected volatility | 54.9% | 54.9% | 73.8% | N/A | ||||
Probability of call option and forward contract | N/A | N/A | 10% | 90% | ||||
Strike Price | $1.6427 | $1.6427 | $1.6427 | $1.6427 | ||||
Value of each tranche feature | $0.143 | $0.199 | $0.326 | $(0.023) | ||||
| (1) | Fair value of the Series B redeemable convertible preferred stock was estimated using the Backsolve method. |
The weighted-average fair value of the tranche features on a per share basis was $0.172 as of October 22, 2020, $0.012 as of December 28, 2020 and December 31, 2020.
For the October 2020 issuance of Series B redeemable convertible preferred stock, certain investors received the right to participate in two additional closings at a fixed price which were valued as a call option (Note 6) when issued.
F-63
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
In connection with the December 2020 issuance of Series B redeemable convertible preferred stock, certain investors of Series B redeemable convertible preferred stock that held 48.65% of the Company’s outstanding shares and have 2 seats on the Company’s board of directors, forfeited their rights to participate in two additional closings of Series B redeemable convertible preferred stock which resulted in the measurement of the preferred stock tranche liability as a combination of a call option and forward contract.
In January 2021, the Company issued additional Series B redeemable convertible preferred stock, and recorded an addition to the tranche liability of $33 thousand in recognition of the obligation to sell additional shares at a fixed price in the event that certain agreed-upon milestones are achieved or at the election of investors.
In April 2021, the Company’s Board of Directors determined that certain technical milestones within the Series B agreements had been achieved and approved the notice to call tranches 2 and 3, subject to requisite stockholders’ written election and related waivers. The second and third closings occurred on May 14, 2021 and all 39,366,050 shares of Series B redeemable convertible preferred stock were acquired thereby extinguishing the preferred stock tranche liability.
The value of the tranche rights acquired on May 14, 2021 was determined using the current value method as both tranches were called by the Company on the valuation date. The following reflects the significant quantitative inputs used in the valuation of the preferred stock tranche liability as of May 14, 2021 using a weighted comparable guideline IPO (high and low) and SPAC transactions for the public scenario and the Black-Scholes pricing model for the staying private scenario:
| May 14, 2021 | ||||
| Tranches 2 and 3 | ||||
| Public Scenario | Staying Private Scenario | |||
| Call | Call | |||
Estimated fair value of Series B redeemable convertible preferred stock | $2.18 | $1.58 | ||
Scenario weighting | 75.0% | 25.0% | ||
Value of each tranche feature | $1.637 | $0.395 | ||
|
| |||
Weighted-average value of Series B redeemable convertible preferred stock | $2.032 | |||
The difference between the weighted-average value of Series B redeemable convertible preferred stock of $2.032 and the strike price of $1.6427 is the $0.3893 weighted-average fair value of the tranche feature on a per share basis as of May 14, 2021 for a total fair value of $15.2 million.
F-64
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
The following table provides a roll-forward of the change in the preferred stock tranche liability (in thousands):
| Preferred Stock Tranche Liability | ||||
Initial closing on October 22, 2020 | $ | 6,120 | ||
Forfeiture of tranche rights | (780 | ) | ||
Change in fair value | (4,968 | ) | ||
Second closing on December 28, 2020 | $ | 63 | ||
|
| |||
Balance as of December 31, 2020 | 435 | |||
Recognition of tranche rights from January 2021 issuance | 33 | |||
Change in fair value | 14,742 | |||
Tranche liability extinguishment | (15,210 | ) | ||
|
| |||
Balance as of December 31, 2021 | $ | — | ||
|
| |||
4. Other Financial Statement information
Prepaid Expenses and Other Current Assets
Prepaid expenses and other current assets consisted of the following (in thousands):
| December 31, | ||||||||
| 2021 | 2020 | |||||||
Deposits | $ | 1,157 | $ | 25 | ||||
SPAC deferred offering costs | 1,446 | — | ||||||
Unbilled contract | — | 229 | ||||||
Other | 1,073 | 830 | ||||||
|
|
|
| |||||
Total prepaid expenses and other current assets | $ | 3,676 | $ | 1,084 | ||||
|
|
|
| |||||
Property and Equipment, Net
Property and equipment, net consisted of the following (in thousands):
| December 31, | ||||||||
| 2021 | 2020 | |||||||
Lab equipment | $ | 4,988 | $ | 3,459 | ||||
Leasehold improvements | 431 | 158 | ||||||
Computer equipment and software | 262 | 214 | ||||||
Furniture and fixtures | 294 | 232 | ||||||
Construction in progress | 8,048 | 231 | ||||||
|
|
|
| |||||
Property and equipment at cost | 14,023 | 4,294 | ||||||
Less: accumulated depreciation | (1,655 | ) | (982 | ) | ||||
|
|
|
| |||||
Property and equipment, net | $ | 12,368 | $ | 3,312 | ||||
|
|
|
| |||||
F-65
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
Depreciation expense for the years ended December 31, 2021 and 2020 was $0.8 million and $0.6 million, respectively. For the years ended December 31, 2021 and 2020, the Company impaired fixed assets and recorded impairment losses of less than $0.1 million and $0.2 million, respectively.
Accrued Expenses and Other Liabilities
Accrued expenses and other liabilities consisted of the following (in thousands):
| December 31, | ||||||||
| 2021 | 2020 | |||||||
Accrued professional and service fees | $ | 2,555 | $ | 54 | ||||
Accrued employee related expenses | 2,665 | 1,933 | ||||||
Other accrued expenses | 111 | 11 | ||||||
|
|
|
| |||||
Total accrued expenses and other current liabilities | $ | 5,331 | $ | 1,998 | ||||
|
|
|
| |||||
5. Convertible Notes
In August 2020, the Company issued $8.0 million in convertible notes to existing investors, including related parties, with a stated annual interest rate of 8%. The principal and accrued interest was payable upon maturity in February 2021.
The outstanding balance of principal plus accrued and unpaid interest were automatically convertible at the sale of preferred stock of at least $25.0 million (the “Qualified Financing”). On conversion of the convertible notes in a Qualified Financing, the same class of preferred shares would be issued at a price equal to 90% of the fixed price per share paid by the purchasers of preferred stock participating in the Qualified Financing. In connection with the issuance and sale of Series B redeemable convertible preferred stock in October 2020 (Note 6), all of the outstanding principal and accrued interest of $8.1 million under the convertible notes was converted into 5,485,858 shares of Series B redeemable convertible preferred stock and the related preferred stock tranche liability.
For the year ended December 31, 2020, we recorded a fair value loss of $0.7 million that is included in the change in fair value of convertible notes, in the accompanying consolidated statements of operations and comprehensive loss.
6. Redeemable Convertible Preferred Stock
The Company’s redeemable convertible preferred stock consisted of the following (in thousands, except per share amounts):
| December 31, 2021 | ||||||||||||||||||||
| Issue Price | Shares Authorized | Shares Issued and Outstanding | Net Carrying Value | Aggregate Liquidation Preference | ||||||||||||||||
Series A | $ | 1.6427 | 35,199,610 | 35,199,610 | $ | 57,408 | $ | 57,822 | ||||||||||||
Series B | $ | 1.6427 | 64,534,944 | 64,534,933 | $ | 114,425 | $ | 106,012 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Total | 99,734,554 | 99,734,543 | $ | 171,833 | $ | 163,834 | ||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
F-66
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
| December 31, 2020 | ||||||||||||||||||||
| Issue Price | Shares Authorized | Shares Issued and Outstanding | Net Carrying Value | Aggregate Liquidation Preference | ||||||||||||||||
Series A | $ | 1.6427 | 35,199,610 | 35,199,610 | $ | 57,408 | $ | 57,822 | ||||||||||||
Series B | $ | 1.6427 | 64,534,944 | 23,748,457 | $ | 32,254 | $ | 39,012 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Total | 99,734,554 | 58,948,067 | $ | 89,662 | $ | 96,834 | ||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
In October 2020, the Company issued 15,624,670 shares of Series B redeemable convertible preferred stock at a price of $1.6427 per share for total proceeds of $25.7 million, net of issuance costs of $0.1 million, and converted the related convertible notes into 5,485,858 shares of Series B redeemable convertible preferred stock. The terms of the Series B redeemable convertible preferred stock included the obligations for the investors to purchase, and the Company to sell, 16,842,176 and 18,668,438 additional shares of Series B redeemable convertible preferred stock in two additional closings (“Tranche 2” and “Tranche 3”) for a price of $1.6427 per share.
On December 28, 2020, the Company issued 2,637,929 shares of Series B redeemable convertible preferred stock to new and existing investors for gross proceeds of $4.3 million, net of issuance costs of $0.2 million. These Series B redeemable convertible preferred stock also included obligations for the investors to purchase, and the Company to sell, 2,637,929 additional shares of Series B redeemable convertible preferred stock in both Tranche 2 and Tranche 3 for a price of $1.6427 per share. Also on December 28, 2020, certain investors forfeited their rights and obligations to purchase 1,217,506 and 3,043,768 shares of Series B redeemable convertible preferred stock in Tranche 2 and Tranche 3, respectively.
On January 19, 2021, the Company issued 1,420,426 shares of Series B redeemable convertible preferred stock to investors for gross proceeds of $2.3 million, net of issuance costs of $6 thousand. The terms of the Series B redeemable convertible preferred stock sold are the same as the terms of previous issuances of Series B redeemable convertible preferred stock issued in October 2020, and also included obligations for the investors to purchase, and the Company to sell, 1,420,426 additional shares of Series B redeemable convertible preferred stock in each of Tranches 2 and 3 for a price of $1.6427 per share.
In April 2021, the Company’s Board of Directors determined that the Series B milestone had been achieved and approved the notice to call tranches 2 and 3, subject to requisite stockholders’ written election and related waivers. The second and third closings occurred on May 14, 2021 and the Company issued 39,366,050 shares of Series B redeemable convertible preferred stock to investors for proceeds of $64.7 million for which no additional issuance costs were incurred.
The following is a summary of the rights and privileges of the holders of redeemable convertible preferred stock:
Voting Rights
Each share of redeemable convertible preferred stock has voting rights equal to the number of shares of common stock into which such preferred stock is convertible. The holders of redeemable convertible preferred stock vote together with the holders of common stock as a single class for most matters.
The holders of Series A redeemable convertible preferred stock voting as a separate class are entitled to elect two directors. The holders of Series B redeemable convertible preferred stock voting as a separate class are entitled to elect two directors. The holders of common stock, voting as a separate class, are entitled to elect two directors of the Company. The holders of common stock and redeemable convertible preferred stock, voting as a single class, are entitled to elect the balance of the seven total directors of the Company.
F-67
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
Dividends
The holders of redeemable convertible preferred stock are entitled to receive, if and when declared by the Company’s board of directors, non-cumulative cash dividends at a rate of 8.0% per annum of the original issue price. These holders are also entitled to participate in dividends on common stock on an as-converted basis. No dividends have been declared or paid to date.
Conversion
At the option of the holder, each share of redeemable convertible preferred stock is convertible into shares of common stock as determined by dividing the applicable original issue price by the applicable conversion price in effect at the time of conversion. The initial conversion price of both Series A and Series B redeemable convertible preferred stock is equal to the original issue price of $1.6427 per share. The conversion ratio for the redeemable convertible preferred stock shall be subject to appropriate adjustments for stock splits, stock dividends, combinations, recapitalizations, or the like. The conversion ratio at December 31, 2021 and December 31, 2020, respectively, is one-to-one; however, the conversion price is subject to anti-dilution provisions upon issuance of additional shares of common stock or other convertible securities. The holders of the Series A redeemable convertible preferred stock agreed to forfeit the anti-dilution provisions upon the issuance of Series B redeemable convertible preferred stock.
Each share of redeemable convertible preferred stock automatically converts into the number of shares of common stock into which such shares are convertible at the applicable conversion ratio upon the earlier: (i) the closing of the sale of shares of common stock in a qualified initial public offering (“IPO”) resulting in gross proceeds of at least $50.0 million or (ii) the vote or written consent of the holders of the majority of the then-outstanding shares of redeemable convertible preferred stock, voting together as a single class.
If a holder of Series B redeemable convertible preferred stock fails to purchase all of its applicable tranche shares at or prior to the milestone closing, all of the holder’s shares of Series B redeemable convertible preferred stock will automatically convert into the number of shares of common stock into which such shares are convertible at the applicable conversion ratio. Such defaulting holder also forfeits its right to designate a member of or observer to the board of directors and any right to participate in any subsequent debt or equity financing of the Company.
Liquidation
In the event of any liquidation, dissolution, or winding up of the Company, either voluntary or involuntary, the holders of the Series B redeemable convertible preferred stock shall be entitled to receive, prior and in preference to any distribution of any of the assets of the Company to the holders of the Series A redeemable convertible preferred stock and common stock, an amount per share equal to the greater of (i) the Series B original issuance price, plus any dividends declared but unpaid thereon, or (ii) such amount per share as would have been payable had all shares of Series B redeemable convertible preferred stock been converted into shares of common stock immediately prior to such liquidation, dissolution, winding up or deemed liquidation event.
After the distribution to holders of Series B redeemable convertible preferred stock, the holders of the Series A redeemable convertible preferred stock shall be entitled to receive, prior and in preference to any distribution of any of the assets of the Company to the holders of the common stock, an amount per share equal to the greater of (i) the Series A original issuance price, plus any dividends declared but unpaid thereon, or (ii) such amount per share as would have been payable had all shares of Series A redeemable convertible preferred stock been converted into shares of common stock immediately prior to such
F-68
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
liquidation, dissolution, winding up or deemed liquidation event. Upon completion of the distribution to the holders of the redeemable convertible preferred stock, all remaining legally available assets will be distributed ratably to the holders of common stock.
Classification
The Company has classified its redeemable convertible preferred stock as temporary equity on the consolidated balance sheets as the stock is contingently redeemable. Upon the occurrence of certain deemed liquidation events that are outside of the Company’s control, including liquidation, sale, or transfer of the Company, holders of the redeemable convertible preferred stock can cause redemption for cash. During the years ended December 31, 2021 and 2020, the Company did not adjust the carrying value of the redeemable convertible preferred stock to the deemed liquidation value of such shares as a deemed liquidation event was not probable. Additionally, one investor that owns 2,435,016 shares of Series B redeemable convertible preferred stock are redeemable by the holder at the original issuance price in the event that the Company uses any of the proceeds received from such investor for purposes other than operations and research and development activities.
7. Common Stock
Holders of common stock are entitled to one vote per share, and to receive dividends and, upon liquidation or dissolution, are entitled to receive all assets available for distribution to stockholders. The holders have no preemptive or other subscription rights, and there are no redemption or sinking fund provisions with respect to such shares. Common stock is subordinate to the redeemable convertible preferred stock with respect to dividend rights and rights upon liquidation, winding up, and dissolution of the Company. Through December 31, 2021, no cash dividends have been declared or paid.
At December 31, 2021 and 2020, the Company was authorized to issue 138,000,000 shares of common stock, all at a par value of $0.0001 per share, and had reserved the following shares for future issuance:
| December 31, | ||||||||
| 2021 | 2020 | |||||||
Series A and B redeemable convertible preferred stock | 99,734,543 | 58,948,067 | ||||||
Stock options to purchase common stock | 11,711,174 | 4,173,285 | ||||||
Common stock options available for future grant under stock option plan | 3,666,927 | 12,857,369 | ||||||
|
|
|
| |||||
Total | 115,112,644 | 75,978,721 | ||||||
|
|
|
| |||||
In addition to the stock options to purchase common stock in the above table, in association with the Business Combination Agreement with DYNS, the Company awarded certain performance and market awards with vesting contingent upon the consummation of the SPAC merger. See Note 9 - Stock-Based Compensation for further details.
F-69
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
8. Revenue
The Company’s revenue consists of amounts received related to research services provided to customers.
Contract Revenue
In May 2019, the Company entered into a collaborative development agreement. The Company determined that the agreement contained three distinct promises; research and development, design services, and intellectual property, which will be accounted for as a single combined performance obligation of research and development services recognized over time. The development agreement included $0.3 million of fixed consideration allocated to a single performance obligation and an additional $0.3 million of variable consideration. At inception of the development agreement, it was not probable that a significant reversal of revenue would not occur and therefore the variable consideration was fully constrained. Throughout the development agreement period, several parameters of the research and development services were changed, which increased the uncertainty of achieving the remaining performance obligations. Therefore, in December 2021, the contract asset of $0.3 million was reversed due to this increased uncertainty.
In April 2021, the Company entered into a research collaboration and license agreement with Spark Therapeutics, Inc. (“Spark”). Under the agreement, the Company will be responsible for a research program, which includes designing, building and testing five cell type specific-synthetic promoters for use in developing certain gene therapies using the Company’s proprietary technology. The Company received an upfront payment from Spark of $3.0 million and Spark is obligated to reimburse the Company for costs and expenses incurred for the research program. The Company expects to complete the research program over a two-year period.
The Company assessed this agreement in accordance with ASC 606, Revenue Recognition (“ASC 606”) and concluded that the contract counterparty, Spark, is a customer. The Company identified only one combined performance obligation in the agreement, which is to perform research services, the related joint research plan and committees for the five specified promoters. The Company determined that the research activities for each of the five promoters are not distinct given there is one single research plan that is performed by the same research team and research results for one promoter may provide insights for other promoters.
Pursuant to the agreement, once the research program is completed and the Company delivers a data package to Spark, Spark has 24 months (the “evaluation period”) to determine whether Spark will exercise its options to obtain field-limited, royalty-bearing licenses to develop, manufacture and commercialize promoters corresponding to each of the five specified promoters being researched. For each licensed promoter option that is exercised, the Company is eligible to receive a license fee, potential research, development and commercial milestone payments and royalties on product sales. Spark may generally terminate the agreement upon 90 days’ prior written notice or 180 days’ prior written notice if the licensed promoter is in clinical trials or is being commercialized at the time of termination.
The Company evaluated Spark’s optional rights to license, develop, manufacture and commercialize each of the promoter profiles to determine whether they provide Spark with any material rights to purchase the promoter licenses at an incremental discount. The Company’s proprietary technology used to develop the promoters is in early stages of development, so technological feasibility and probability of developing a product is highly uncertain. As a result, determining the SSP for the optional rights is subject to significant judgment. Given the subjectivity associated with determining the SSP for the right to a future license related to unproven technology at contract inception, the Company also evaluated whether the contract consideration associated with the research services represents the SSP for those services. The Company determined the transaction price, inclusive of the
F-70
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
upfront payment and reimbursement of costs and expenses incurred for the research program, is commensurate with SSP for the research being conducted given the specialized nature and reliance on proprietary technology. Based on the Company’s assessment of the optional consideration and the qualitative factors of feasibility and probability of development combined with the quantitative assessment that research services are priced at their SSP, the Company concluded that the license option does not provide Spark with an incremental discount and therefore does not constitute a material right. The transaction price associated with the research services in this agreement consists of the fixed upfront amount of $3.0 million and variable consideration.
For both collaboration agreements, the Company will recognize the transaction price as research and development services are provided, using a cost-based input method to measure the progress toward completion of its performance obligation and to calculate the corresponding amount of revenue to recognize each period. The Company believes that the cost-based input method is the best measure of progress because other measurements would not reflect how the Company transfers the control related to the performance obligation to our customers.
The Company has recorded nil and $0.2 million of revenue for the years ended December 31, 2021 and 2020, respectively, which was previously included in the deferred revenue balances at the beginning of each period. Contract asset balances related to unbilled revenue for our collaboration agreements were nil and $0.2 million as of December 31, 2021 and 2020, respectively, and are presented within prepaid expenses and other current assets on the consolidated balance sheets.
Grant Income
In 2018, the National Institutes of Health awarded the Company a grant in the amount of $0.2 million to be used to support research and development for treating Inflammatory Bowel Disease. Eligible costs under the grant include direct personnel costs and materials and supplies.
In 2021, the Small Business Innovation Research awarded the Company a grant in the amount of $2.0 million over two years subject to meeting certain terms and conditions. The purpose of the grant is to support further development of SENTI-202 for acute myeloid leukemia (“AML”) towards clinical development.
Grant income was recognized when qualified research and development costs were incurred and the Company obtained reasonable assurance that the terms and conditions of the grant were met.
Entity-wide information
During the year ended December 31, 2021, when excluding the $0.3 million contract asset reversal for Customer C, Customer A accounted for 84.3% of revenue, and Customer B accounted for 15.7% of revenue. During the year ended December 31, 2020, Customer B and C accounted for 30.4% and 69.6%, respectively, of revenue.
All net sales were generated in the United States for the years ended December 31, 2021 and 2020.
9. Stock-Based Compensation
In 2016, the Company adopted the 2016 Stock Incentive Plan (the “2016 Stock Incentive Plan”) authorizing the grant of incentive stock options (“ISOs”) and non-statutory stock options (“NSOs”) to eligible employees, officers and directors of, and consultants or advisors to, the Company. As of December 31, 2021, the Company is authorized to issue up to 65,551,165, respectively, of shares of common stock under the Plan in which the
F-71
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
exercise price of an ISO and NSO shall not be less than 100% of the estimated fair value of the shares on the date of grant, as determined by the board of directors. The exercise price of an ISO granted to a 10% stockholder shall not be less than 110% of the estimated fair value of the shares on the date of grant, as determined by the board of directors. Options generally vest over four years and are exercisable for up to 10 years after the date of the grant.
The following table summarizes the Company’s stock option activity, excluding performance and market awards:
| Number of Options | Weighted- Average Exercise Price | Weighted- Average Remaining Contractual Life (Years) | Aggregate Intrinsic Value (in Thousands) | |||||||||||||
Outstanding at December 31, 2020 | 4,173,285 | $ | 0.49 | 8.9 | $ | 199 | ||||||||||
|
|
|
|
|
|
|
| |||||||||
Granted | 10,800,000 | $ | 0.89 | |||||||||||||
Exercised | (3,103,769 | ) | $ | 0.43 | ||||||||||||
Forfeited | (158,342 | ) | $ | 0.65 | ||||||||||||
Expired | — | |||||||||||||||
|
|
|
|
|
|
|
| |||||||||
Outstanding at December 31, 2021 | 11,711,174 | $ | 0.86 | 9.1 | $ | 11,304 | ||||||||||
|
|
|
|
|
|
| �� | |||||||||
Vested and exercisable at December 31, 2021 | 1,381,326 | $ | 0.48 | 7.7 | $ | 1,781 | ||||||||||
|
|
|
|
|
|
|
| |||||||||
The aggregate intrinsic values of options exercised during the years ended December 31, 2021 and 2020 were $0.8 million and $0.2 million, respectively. The weighted-average grant-date fair values of options granted during the years ended December 31, 2021 and 2020 were $0.96 and $0.38, respectively.
Early Exercise of Stock Options into Restricted Stock
For the year ended December 31, 2021, the Company issued 2,619,677 shares of common stock upon exercise of unvested stock options, and as of December 31, 2021, 2,418,871 shares held by employees were subject to repurchase at an aggregate price of $1.2 million. As of December 31, 2020, no options were early exercised and accordingly, the liability related to the payments for unvested shares was nil at each date.
Stock-Based Compensation Expense
In determining the fair value of the stock-based awards, the Company uses the assumptions below for the Black-Scholes option pricing model, which are subjective and generally requires significant judgment.
Fair Value of Common Stock — The fair value of the shares of common stock has historically been determined by the Company’s board of directors as there was no public market for the common stock. The board of directors determines the fair value of the common stock by considering a number of objective and subjective factors, including: third-party valuations of the Company’s common stock, the valuation of comparable companies, the Company’s operating and financial performance, and general and industry-specific economic outlook, amongst other factors.
Expected Term — The expected term represents the period that the Company’s stock options are expected to be outstanding and is determined using the simplified method (based on the mid-point between the vesting date and the end of the contractual term).
F-72
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
Volatility — Because the Company is privately held and does not have an active trading market for its common stock for a sufficient period of time, the expected volatility was estimated based on the average volatility for comparable publicly-traded companies, over a period equal to the expected term of the stock option grants.
Risk-free Rate — The risk-free rate assumption is based on the U.S. Treasury zero-coupon issues in effect at the time of grant for periods corresponding with the expected term of the option.
Dividends — The Company has never paid dividends on its common stock and does not anticipate paying dividends on common stock. Therefore, the Company uses an expected dividend yield of zero.
The assumptions used to determine the grant date fair value of stock options granted to grantees were as follows, presented on a weighted-average basis:
| Year Ended December 31, | ||||
| 2021 | 2020 | |||
Expected term (in years) | 6.03 | 6.03 | ||
Expected volatility | 82.3% | 83.3% | ||
Risk-free interest rate | 0.9% | 0.7% | ||
Dividend yield | — % | — % | ||
Total stock-based compensation expense was as follows (in thousands):
| Year Ended December 31, | ||||||||
| 2021 | 2020 | |||||||
General and administrative | $ | 1,940 | $ | 201 | ||||
Research and development | 355 | 71 | ||||||
|
|
|
| |||||
Total stock-based compensation expense | $ | 2,295 | $ | 272 | ||||
|
|
|
| |||||
As of December 31, 2021, the total unrecognized stock-based compensation was approximately $9.2 million, which is expected to be recognized over a weighted-average period of 3.1 years.
Performance Awards
In connection with the Business Combination Agreement with DYNS, on December 19, 2021, the Company awarded 42,927,654 performance awards to existing employees that vest contingent upon the satisfaction of both a four-year service condition and a performance condition tied to the consummation of the SPAC merger. The grant and the associated recognition of stock-based compensation is contingent on the SPAC merger being consummated which is subject to DYNS shareholder approval. As of December 31, 2021, 42,909,091 performance awards remain outstanding after the forfeiture of 18,563 performance awards during the year.
Market Awards
In connection with the Business Combination Agreement with DYNS, on December 19, 2021, the Company awarded 3,093,776 market awards to the co-founder and CEO, Mr. Lu that vest contingent upon the satisfaction of all three of the following conditions: a service condition, a performance condition tied to the consummation of the SPAC merger, and market conditions. The market condition is achieved in four tranches, where 25% of the
F-73
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
options will vest when the trading price of the Company’s stock is above various thresholds of price per share. The grant and the associated recognition of stock-based compensation is contingent on the SPAC merger being consummated which is subject to DYNS shareholder approval.
10. Operating Leases
The Company’s operating leases are primarily for its corporate headquarters located in South San Francisco, California and for additional office and laboratory space located in Alameda, California (“Alameda lease”) that commenced on July 30, 2021. The corporate headquarters lease has an initial term of eight years expiring in 2027, with an option to renew for additional eight years unless canceled by either party thereafter. The Alameda lease has an initial term of eleven years expiring in 2032, with an option to renew the lease for up to two additional terms of five years. The exercise of these renewal options are not recognized as part of the ROU assets and lease liabilities, as the Company did not conclude, at the commencement date of the leases, that the exercise of renewal options or termination options was reasonably certain. The Alameda lease provides for a tenant improvement allowance of up to $17.5 million for the costs relating to the design, permitting and construction of the improvements, to be disbursed by the landlord no later than December 31, 2023. The Company was deemed to be the accounting owner of the tenant improvements primarily because the Company is the principal in the construction and design of the assets, is responsible for costs overruns and retains substantially all economic benefits from the leasehold improvements over their economic lives. Accordingly, the tenant improvement allowance is considered an incentive and was deducted from the initial measurement of the ROU asset and lease liability. The Company estimated the timing of tenant improvement reimbursements at the lease commencement date and upon receipt of the cash incentives, the Company will recognize the cash received as an increase in the lease liability.
The Company’s operating lease cost was $3.8 million and $2.7 million for the years ended December 31, 2021 and 2020, respectively. Variable lease payments such as common area maintenance and parking fees were included in operating expenses and were $0.7 million and $0.6 million for the years ended December 31, 2021 and 2020, respectively. The Company did record any short-term lease expense during the years ended December 31, 2021 and 2020. No reimbursements have been received from the landlord as of December 31, 2021 and 2020.
Supplemental cash flow and noncash information related to the operating leases were as follows (in thousands):
| Year Ended December 31, | ||||||||
| 2021 | 2020 | |||||||
Supplemental cash flow information: | ||||||||
Operating cash flows from operating lease | $ | (2,669 | ) | $ | (2,577 | ) | ||
ROU assets obtained in exchange for operating lease obligations | 10,153 | 513 | ||||||
The following summarizes additional information related to the operating leases as of December 31, 2021 and 2020:
| December 31, | ||||||||
| 2021 | 2020 | |||||||
Weighted-average remaining lease term | 7.76 years | 6.33 years | ||||||
Weighted-average discount rate | 9.06 | % | 8.91 | % | ||||
F-74
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
As of December 31, 2021 and 2020, amounts disclosed for ROU assets obtained in exchange for lease obligations include amounts added to the carrying amount of ROU assets resulting from lease modifications and reassessments.
Maturities of the Company’s lease liabilities as of December 31, 2021, were as follows (in thousands):
2022 | $ | 2,770 | ||
2023 | 6,272 | |||
2024 | 7,266 | |||
2025 | 7,489 | |||
2026 | 7,723 | |||
Thereafter | 30,229 | |||
|
| |||
Total undiscounted lease payments | 61,749 | |||
Less imputed interest | (21,555 | ) | ||
Tenant improvement reimbursements | (17,463 | ) | ||
|
| |||
Total lease liabilities | $ | 22,731 | ||
|
|
11. Income Taxes
For the calendar years ended December 31, 2021 and 2020, the tax effects of significant items comprising the Company’s deferred taxes are as follows:
| December 31, | ||||||||
| 2021 | 2020 | |||||||
Deferred tax assets: | ||||||||
Net operating losses | $ | 23,104 | $ | 15,543 | ||||
Tax credits | 4,915 | 2,775 | ||||||
Lease Liability | 6,350 | 3,930 | ||||||
Accruals and reserves | 738 | 526 | ||||||
Stock-based compensation | 28 | 17 | ||||||
Other | 600 | 2 | ||||||
|
|
|
| |||||
Total deferred tax assets | 35,735 | 22,793 | ||||||
Deferred tax liabilities: | ||||||||
Operating lease right-of-use assets | (5,789 | ) | (3,590 | ) | ||||
Fixed asset basis | (236 | ) | (178 | ) | ||||
|
|
|
| |||||
Total deferred tax liabilities | (6,025 | ) | (3,768 | ) | ||||
Valuation allowance | (29,710 | ) | (19,025 | ) | ||||
|
|
|
| |||||
Net deferred taxes | $ | — | $ | — | ||||
|
|
|
| |||||
The Company records the tax benefit of net operating losses, temporary differences, and credit carryforwards as assets to the extent that management assesses that realization is “more likely than not.” Realization of the future tax benefits is dependent on the Company’s ability to generate sufficient taxable income within the carryforward period. Because of the Company’s recent history of operating losses, management believes that recognition of the deferred tax assets arising from the above-mentioned future tax benefits is currently not likely to be realized and, accordingly, has provided a valuation allowance.
F-75
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
The valuation allowance increased by approximately $10.7 million and $7.9 million during 2021 and 2020, respectively, and the Company’s deferred tax assets continue to be fully offset by the valuation allowance as at December 31, 2021. For the years ended December 31, 2021 and 2020, the Company did not record an income tax provision.
Net operating losses and tax credit carryforwards as of December 31, 2021 are as follows (in thousands):
| Amount | Expiration Years | |||||||
Net operating losses, federal (Post December 31, 2017) | $ | 86,602 | Do Not Expire | |||||
Net operating losses, federal (Pre January 1, 2018) | $ | 3,508 | 12/31/2031 | |||||
Net operating losses, state | $ | 55,023 | 12/31/2032 | |||||
Tax credits, federal | $ | 3,573 | 12/31/2032 | |||||
Tax credits, state | $ | 3,120 | Do Not Expire | |||||
Net operating losses, foreign | $ | 1,146 | Do Not Expire | |||||
Utilization of the net operating loss carryforwards may be subject to a substantial annual limitation due to the ownership change limitations provided by the Internal Revenue Code of 1986, as amended, and similar state provisions. This annual limitation may result in the expiration of net operating losses and credits before utilization. We have not performed an analysis to determine the limitation of our net operating loss carryforwards.
The effective tax rate of the Company’s provision (benefit) for income taxes differs from the federal statutory rate as follows:
| December 31, | ||||||||
| 2021 | 2020 | |||||||
Statutory rate | 21.00 | % | 21.00 | % | ||||
State tax | 2.98 | % | 11.68 | % | ||||
Other | (0.80 | )% | (0.05 | )% | ||||
Tax credits | 2.29 | % | 2.81 | % | ||||
Fair value of series B preferred stock tranche liability | (5.60 | )% | 6.04 | % | ||||
Valuation allowance | (19.87 | )% | (41.48 | )% | ||||
|
|
|
| |||||
Total | 0.00 | % | 0.00 | % | ||||
|
|
|
| |||||
As of December 31, 2020, gross unrecognized tax benefits were $1.3 million, all of which would not impact the Company’s effective tax rate if recognized. The Company has elected to include interest and penalties as a component of tax expense. For the years ended December 31, 2021 and 2020, the Company did not recognize accrued interest and penalties related to unrecognized tax benefits. The Company does not anticipate that the amount of existing unrecognized tax benefits will significantly increase or decrease during the next 12 months.
The Company files income tax returns in the U.S. federal and California tax jurisdictions. The federal and state income tax returns from inception to December 31, 2021 remain subject to examination.
F-76
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
12. Net Loss Per Share
A reconciliation of net loss available to common stockholders and the number of shares in the calculation of basic and diluted loss per share is as follows:
| Year Ended December 31, | ||||||||
| 2021 | 2020 | |||||||
Net loss | $ | (55,319 | ) | $ | (19,862 | ) | ||
|
|
|
| |||||
Denominator: | ||||||||
Weighted-average shares used in computing net loss per share, basic and diluted | 14,881,325 | 13,862,582 | ||||||
|
|
|
| |||||
Net loss per share attributable to common stockholders, basic and diluted | $ | (3.72 | ) | $ | (1.43 | ) | ||
|
|
|
| |||||
The following potential common shares securities were excluded from the computation of diluted net loss per share attributable to common stockholders for the periods presented because including them would have been anti-dilutive (on an as-converted basis):
| Year Ended December 31, | ||||||||
| 2021 | 2020 | |||||||
Series A and B redeemable convertible preferred stock | 99,734,543 | 58,948,067 | ||||||
Potential issuance of Series B redeemable convertible preferred stock under Tranche 2 | — | 19,683,025 | ||||||
Potential issuance of Series B redeemable convertible preferred stock under Tranche 3 | — | 19,683,025 | ||||||
Stock options to purchase common stock | 11,711,174 | 4,173,285 | ||||||
Unvested early exercised options | 2,418,871 | — | ||||||
|
|
|
| |||||
Total | 113,864,588 | 102,487,402 | ||||||
|
|
|
| |||||
13. Commitments and Contingencies
In the ordinary course of business, we enter into contractual agreements with third parties that include non-cancelable payment obligations, for which we are liable in future periods.
On June 3, 2021, the Company entered into a lease agreement for a new cGMP facility in Alameda, California to support planned initial clinical trials for our product candidates (Note 10). The lease will expire in 2032 with future undiscounted operating lease payments of $46.0 million over an initial lease period of eleven years.
In 2021, the Company began construction of the cGMP facility. As of December 31, 2021 the Company paid $2.6 million in construction costs and the purchase commitments amounted to approximately $35.5 million. The agreements with the construction company provide for termination following a certain period after notice. Upon termination the Company will be responsible for payment for work performed to date.
During the year ended December 31, 2021, the Company entered into a three-year collaboration and option agreement with BlueRock Therapeutics LP (“BlueRock”) under which the Company granted BlueRock an option
F-77
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
to acquire an exclusive or non-exclusive license to develop, manufacture and commercialize cell therapy products (Note 14). In consideration for the option, the Company is responsible for up to $10.0 million in costs and expenses incurred over the three-year term.
As of December 31, 2021, purchase commitments related to sponsored research agreements amounted to approximately $2.2 million.
The Company has entered into license agreements under which they are obligated to make annual maintenance payments of $0.1 million and specified milestone and royalty payments. Future milestone and royalty payments under these agreements are not considered contractual obligations since the payments under these agreements are contingent upon future events, such as the Company’s achievement of specified development, regulatory, and sales milestones, or generating product sales. As of December 31, 2021, the Company is unable to estimate the timing or likelihood of achieving these milestones or generating future product sales.
Leases
The Company’s commitments under its leases are described in Note 10.
Legal Proceedings
The Company is subject to claims and assessments from time to time in the ordinary course of business but does not believe that any such matters, individually or in the aggregate, will have a material adverse effect on the Company’s financial position, results of operations, or cash flows.
Indemnifications
In the ordinary course of business, the Company enters into agreements that may include indemnification provisions. Pursuant to such agreements, the Company may indemnify, hold harmless and defend an indemnified party for losses suffered or incurred by the indemnified party. Some of the provisions will limit losses to those arising from third party actions. In some cases, the indemnification will continue after the termination of the agreement. The maximum potential amount of future payments the Company could be required to make under these provisions is not determinable. The Company has never incurred material costs to defend lawsuits or settle claims related to these indemnification provisions and has never accrued any liabilities related to such obligations in its consolidated financial statements. The Company has also entered into indemnification agreements with its directors and officers that may require the Company to indemnify its directors and officers against liabilities that may arise by reason of their status or service as directors or officers to the fullest extent permitted by Delaware corporate law. The Company currently has directors’ and officers’ insurance.
14. Related Parties
As discussed in Note 6, the Company issued Series A convertible redeemable preferred stock and Series B redeemable convertible preferred stock in February 2018 and October 2020, respectively, to certain related parties, including New Enterprise Associates 15, L.P. and its affiliates (“NEA”) and 8VC and its affiliates (“8VC”).
In February 2018, the outstanding convertible notes held by NEA and 8VC, as well as Timothy Lu, Chief Executive Officer, converted into additional shares of Series A redeemable convertible preferred stock while in October 2020, the outstanding convertible notes held by NEA and 8VC converted into additional shares of Series B redeemable convertible preferred stock, both in accordance with the terms of the note agreements.
F-78
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
NEA held 13,505,035 shares of outstanding Series A redeemable convertible preferred stock as of December 31, 2021 and 2020, as well as 2,742,931 of outstanding Series B redeemable convertible preferred stock as of December 31, 2021 and 2020. 8VC held 9,052,387 of outstanding Series A redeemable convertible preferred stock as of December 31, 2021 and 2020 as well as 1,662,398 of outstanding Series B redeemable convertible preferred stock as of December 31, 2021 and 2020. Timothy Lu held 158,950 of outstanding redeemable convertible preferred stock as of December 31, 2021 and 2020. Timothy Lu and family held 8,100,000 of common stock as of December 31, 2021 and 2020. Timothy Lu, NEA, and 8VC held three of the seven seats on the Company’s Board of Directors as of December 31, 2021 and three of the five seats on the Company’s Board of Directors as of December 31, 2020.
As Chief Executive Officer, Timothy Lu was paid $0.4 million as compensation, and an additional sum of $0.2 million was accrued as a bonus for both the years ended December 31, 2021 and 2020.
On May 21, 2021, the Company entered into a collaboration and option agreement (“BlueRock Agreement”) with BlueRock Therapeutics LP (“BlueRock”), pursuant to which the Company granted to BlueRock an option (“BlueRock Option”), on a collaboration program-by-collaboration program basis, to obtain an exclusive or non-exclusive license to develop, manufacture and commercialize cell therapy products that contain cells of specified types and which incorporate an option gene circuit from such collaboration program or a closely related derivative gene circuit. The Company is responsible for up to $10 million in costs and expenses incurred in connection with the research plan and related activities to be conducted over a term of three years as specified in the collaboration and option agreement. If the Company and BlueRock agree to add new research activities to the research plan, then BlueRock will be obligated to reimburse the Company for the costs and expenses incurred that, together with costs and expenses incurred under the initial research plan, exceed $10 million.
The Company concluded that the Agreement is not within the scope of ASC 808, Collaborative Arrangements, because the Company did not receive any consideration and therefore, is not exposed to both significant risks and rewards for the arrangement. The Company also determined that the agreement is also not currently within the scope of ASC 606 because the BlueRock Agreement does not currently meet the criteria of a contract with a customer, and will not be within scope of ASC 606 until any consideration is paid. Potential future milestone payments and royalties are subject to BlueRock’s exercise of the BlueRock Option and execution of a commercial license agreement by both parties. Under the BlueRock Agreement, the specific financial terms for milestone payments and royalties will be negotiated and agreed to only after the option is exercised.
BlueRock is a wholly-owned subsidiary of Bayer Healthcare LLC which held 27,393,924 and 9,131,308 shares of outstanding Series B redeemable convertible preferred stock as of December 31, 2021 and 2020, respectively, and holds one of the seven seats on the Company’s Board of Directors as of December 31, 2021 and one of the five seats as of December 31, 2020. Bayer Healthcare LLC’s parent company is Bayer AG, which served as the lead investor in our Series B financing through its Leaps by Bayer unit. Accordingly, BlueRock is considered a related party. The Company concluded that the BlueRock Agreement should not be combined with the issuance of the Series B redeemable convertible preferred stock on May 14, 2021 as the price paid per share of $1.6427 was lower than the fair value of $2.03 (Note 3) and therefore, there was no excess value to allocate to the BlueRock Agreement.
15. Subsequent Events
The Company has evaluated subsequent events from the December 31, 2021 balance sheet date through April 1, 2022, the date at which the audited consolidated financial statements were available to be issued.
F-79
SENTI BIOSCIENCES, INC.
Notes to Consolidated Financial Statements
Option Modification
On February 12, 2022, the Company entered into Amendment No. 1 to the Business Combination Agreement, to restructure the performance and market awards made at the time the Business Combination Agreement was signed. In particular, certain Senti executives agreed to forfeit certain options awarded to them at the time the Business Combination Agreement was signed depending on the level of redemptions of DYNS Class A Common Stock upon closing of the merger. In addition, it was agreed that the vesting period for the options held by executives whose options may be subject to forfeiture (as described above) will commence upon closing of the merger instead of on December 19, 2021.
F-80
SENTI BIOSCIENCES, INC.
Condensed Consolidated Balance Sheets
(unaudited)
(in thousands, except share and per share data)
| March 31, | December 31, | |||||||
| 2022 | 2021 | |||||||
Assets | ||||||||
Current assets: | ||||||||
Cash and cash equivalents | $ | 38,140 | $ | 56,034 | ||||
Trade and other receivables | 430 | 483 | ||||||
Prepaid expenses and other current assets | 6,048 | 3,676 | ||||||
|
|
|
| |||||
Total current assets | 44,618 | 60,193 | ||||||
Restricted cash | 3,257 | 3,257 | ||||||
Property and equipment, net | 24,067 | 12,368 | ||||||
Operating lease right-of-use assets | 20,178 | 20,708 | ||||||
Other long-term assets | 186 | 176 | ||||||
|
|
|
| |||||
Total assets | $ | 92,306 | $ | 96,702 | ||||
|
|
|
| |||||
Liabilities and Stockholders’ Deficit | ||||||||
Current liabilities: | ||||||||
Accounts payable | $ | 5,657 | $ | 5,187 | ||||
Early exercise liability, current portion | 325 | 626 | ||||||
Deferred revenue | 1,379 | 1,656 | ||||||
Accrued expenses and other current liabilities | 8,979 | 5,331 | ||||||
Operating lease liabilities | 1,799 | 1,743 | ||||||
|
|
|
| |||||
Total current liabilities | 18,139 | 14,543 | ||||||
Operating lease liabilities, net of current portion | 23,596 | 20,988 | ||||||
Deferred revenue, net of current portion | — | 176 | ||||||
Early exercise liability, net of current portion | 545 | 619 | ||||||
|
|
|
| |||||
Total liabilities | 42,280 | 36,326 | ||||||
|
|
|
| |||||
Commitments and contingencies (Note 11) | ||||||||
Redeemable convertible preferred stock (A and B), $0.0001 par value; 99,734,554 shares authorized at March 31, 2022 and December 31, 2021; 99,734,543 shares issued and outstanding at March 31, 2022 and December 31, 2021; aggregate liquidation preference of $163.8 million at March 31, 2022 and December 31, 2021 | 171,833 | 171,833 | ||||||
Stockholders’ deficit: | ||||||||
Common stock, $0.0001 par value; 138,000,000 shares authorized at March 31, 2022 and December 31, 2021; 16,804,476 and 15,189,091 shares issued and outstanding at March 31, 2022 and December 31, 2021, respectively | 1 | 1 | ||||||
Additional paid-in capital | 5,076 | 3,618 | ||||||
Other comprehensive income | — | — | ||||||
Accumulated deficit | (126,884 | ) | (115,076 | ) | ||||
|
|
|
| |||||
Total stockholders’ deficit | (121,807 | ) | (111,457 | ) | ||||
|
|
|
| |||||
Total liabilities, redeemable convertible preferred stock and stockholders’ deficit | $ | 92,306 | $ | 96,702 | ||||
|
|
|
| |||||
The accompanying notes are an integral part of these condensed consolidated financial statements.
F-81
SENTI BIOSCIENCES, INC.
Condensed Consolidated Statements of Operations and Comprehensive Loss
(unaudited)
(in thousands)
| Three Months Ended March 31, | ||||||||
| 2022 | 2021 | |||||||
Revenue: | ||||||||
Contract revenue | $ | 854 | $ | 44 | ||||
Grant income | 250 | 28 | ||||||
|
|
|
| |||||
Total revenue | 1,104 | 72 | ||||||
Operating expenses: | ||||||||
Research and development | 7,603 | 4,903 | ||||||
General and administrative | 5,259 | 4,311 | ||||||
|
|
|
| |||||
Total operating expenses | 12,862 | 9,214 | ||||||
|
|
|
| |||||
Loss from operations | (11,758 | ) | (9,142 | ) | ||||
|
|
|
| |||||
Other income (expense): | ||||||||
Interest income, net | 4 | 1 | ||||||
Change in preferred stock tranche liability | — | (11,824 | ) | |||||
Other expense | (54 | ) | (37 | ) | ||||
|
|
|
| |||||
Total other income (expense), net | (50 | ) | (11,860 | ) | ||||
|
|
|
| |||||
Net loss and comprehensive loss | (11,808 | ) | (21,002 | ) | ||||
|
|
|
| |||||
Net loss per share, basic and diluted | $ | (0.73 | ) | $ | (1.44 | ) | ||
|
|
|
| |||||
Weighted-average shares outstanding, basic and diluted | 16,204,614 | 14,602,926 | ||||||
|
|
|
| |||||
The accompanying notes are an integral part of these condensed consolidated financial statements.
F-82
SENTI BIOSCIENCES, INC.
Condensed Consolidated Statements of Redeemable Convertible Preferred Stock and Stockholders’ Deficit
(unaudited)
(in thousands, except share data)
| Redeemable Convertible Preferred Stock | Common Stock | Additional Paid-in Capital | Accumulated Deficit | Total Stockholders’ Deficit | ||||||||||||||||||||||||
| Shares | Amount | Shares | Amount | |||||||||||||||||||||||||
Balance as of December 31, 2020 | 58,948,067 | $ | 89,662 | 14,504,193 | $ | 1 | $ | 1,043 | $ | (59,757 | ) | $ | (58,713 | ) | ||||||||||||||
Issuance of Series B redeemable convertible preferred stock, net of preferred stock tranche liability of $33 thousand and issuance costs of $6 thousand | 1,420,426 | 2,294 | — | — | — | — | — | |||||||||||||||||||||
Issuance of common stock | — | — | 2,879,206 | — | 1,432 | — | 1,432 | |||||||||||||||||||||
Early exercise of common stock options | — | — | (2,619,677 | ) | — | (1,329 | ) | — | (1,329 | ) | ||||||||||||||||||
Stock-based compensation | — | — | — | — | 372 | — | 372 | |||||||||||||||||||||
Net loss | — | — | — | — | — | (21,002 | ) | (21,002 | ) | |||||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||||||||||
Balance as of March 31, 2021 | 60,368,493 | $ | 91,956 | 14,763,722 | $ | 1 | $ | 1,518 | $ | (80,759 | ) | $ | (79,240 | ) | ||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||||||||||
| Redeemable Convertible Preferred Stock | Common Stock | Additional Paid-in Capital | Accumulated Deficit | Total Stockholders’ Deficit | ||||||||||||||||||||||||
| Shares | Amount | Shares | Amount | |||||||||||||||||||||||||
Balance as of December 31, 2021 | 99,734,543 | $ | 171,833 | 15,189,091 | $ | 1 | $ | 3,618 | $ | (115,076 | ) | $ | (111,457 | ) | ||||||||||||||
Issuance of common stock | — | — | 881,993 | — | 422 | — | 422 | |||||||||||||||||||||
Vesting of early exercise of common stock options | — | — | 733,392 | — | 375 | — | 375 | |||||||||||||||||||||
Stock-based compensation | — | — | — | — | 661 | — | 661 | |||||||||||||||||||||
Net loss | — | — | — | — | — | (11,808 | ) | (11,808 | ) | |||||||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||||||||||
Balance as of March 31, 2022 | 99,734,543 | $ | 171,833 | 16,804,476 | $ | 1 | $ | 5,076 | $ | (126,884 | ) | $ | (121,807 | ) | ||||||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||||||||||
The accompanying notes are an integral part of these condensed consolidated financial statements.
F-83
SENTI BIOSCIENCES, INC.
Condensed Consolidated Statements of Cash Flows
(unaudited)
(in thousands)
| Three Months Ended March 31, | ||||||||
| 2022 | 2021 | |||||||
Cash flows from operating activities | ||||||||
Net loss | $ | (11,808 | ) | $ | (21,002 | ) | ||
Adjustments to reconcile net loss to net cash from operating activities: | ||||||||
Depreciation | 240 | 165 | ||||||
Amortization of operating lease right-of-use assets | 770 | 375 | ||||||
Change in preferred stock tranche liability | — | 11,824 | ||||||
Stock-based compensation expense | 661 | 372 | ||||||
Loss on write-off of fixed assets | 12 | — | ||||||
Changes in assets and liabilities: | ||||||||
Accounts receivable | 53 | 60 | ||||||
Prepaid expenses and other assets | (381 | ) | (431 | ) | ||||
Accounts payable | (164 | ) | 723 | |||||
Accrued expenses and other current liabilities | (1,413 | ) | (98 | ) | ||||
Deferred revenue | (453 | ) | — | |||||
Operating lease liabilities | 2,424 | (353 | ) | |||||
|
|
|
| |||||
Net cash from operating activities | (10,059 | ) | (8,365 | ) | ||||
|
|
|
| |||||
Cash flows from investing activities | ||||||||
Purchases of property and equipment | (7,380 | ) | (206 | ) | ||||
|
|
|
| |||||
Net cash from investing activities | (7,380 | ) | (206 | ) | ||||
|
|
|
| |||||
Cash flows from financing activities | ||||||||
Proceeds from issuance of common stock upon exercise of stock options | 140 | 1,432 | ||||||
Proceeds from issuance of Series B redeemable convertible preferred stock | — | 2,333 | ||||||
Payment of issuance costs related to Series B redeemable convertible preferred stock | — | (42 | ) | |||||
Payment of deferred offering costs | — | (165 | ) | |||||
Payment of deferred transaction costs related to pending business combination | (595 | ) | — | |||||
|
|
|
| |||||
Net cash from financing activities | (455 | ) | 3,558 | |||||
|
|
|
| |||||
Net change in cash and cash equivalents | (17,894 | ) | (5,013 | ) | ||||
Cash, cash equivalents, and restricted cash, beginning of the year | 59,291 | 31,034 | ||||||
|
|
|
| |||||
Cash, cash equivalents, and restricted cash, end of the year | $ | 41,397 | $ | 26,021 | ||||
|
|
|
| |||||
Reconciliation of cash, cash equivalents and restricted cash | ||||||||
Cash and cash equivalents | 38,140 | 25,524 | ||||||
Restricted Cash | 3,257 | 497 | ||||||
|
|
|
| |||||
Total cash, cash equivalents and restricted cash | $ | 41,397 | $ | 26,021 | ||||
|
|
|
| |||||
Supplemental disclosures of noncash financing and investing items | ||||||||
Purchase of property and equipment in accounts payable and accrued expenses | $ | 8,920 | $ | 115 | ||||
Recognition of Series B preferred stock tranche liability | — | 33 | ||||||
Preferred stock issuance costs included in accounts payable and accrued expenses | — | 5 | ||||||
Deferred transaction costs related to pending business combination in accounts payable and accrued expenses | 2,462 | 94 | ||||||
Receivables in transit from issuance of common stock upon exercise of stock options | 306 | — | ||||||
The accompanying notes are an integral part of these condensed consolidated financial statements.
F-84
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
1. Organization and Description of Business and Basis of Presentation
Senti Biosciences, Inc. or (the “Company”), was incorporated under the laws of the State of Delaware in June 2016, and is a biotechnology company that programs next-generation cell and gene therapies with what we refer to as “gene circuits.” The Company is headquartered in South San Francisco, California.
Basis of Presentation
The accompanying condensed consolidated financial statements have been prepared in conformity with generally accepted accounting principles in the United States of America (“U.S. GAAP”) and the rules and regulations of the Securities and Exchange Commission (“SEC”). Any reference in these notes to applicable guidance is meant to refer to the authoritative U.S. GAAP as found in the Accounting Standards Codification (“ASC”) and as amended by Accounting Standards Updates (“ASU”) of the Financial Accounting Standards Board (“FASB”). The condensed consolidated financial statements include the accounts of Senti Biosciences, Inc., and its wholly-owned subsidiary. All intercompany balances and transactions have been eliminated in consolidation. We have one business activity and operate in one reportable segment.
Reclassification
Certain prior period amounts in Note 4, Other Financial Statement Information, have been reclassified to conform to the current year’s presentation.
Liquidity and Going Concern
The Company has devoted substantially all of its efforts to organizing and staffing, business planning, raising capital, and conducting preclinical studies and has not realized substantial revenues from its planned principal operations. In addition, the Company has a limited operating history, has incurred recurring operating losses and negative cash flows from operations since inception, has an accumulated deficit, has funded its operations primarily with proceeds from sale of redeemable convertible preferred stock and the issuance of convertible notes, and expects that it will continue to incur net losses and negative cash flows from operations into the foreseeable future, particularly as the Company advances its preclinical activities and clinical trials for its product candidates in development.
The Company’s continued existence is dependent upon management’s ability to develop profitable operations. Management is devoting substantially all of its efforts to developing its business and raising capital and there can be no assurance that the Company’s efforts will be successful. No assurance can be given that management’s actions will result in profitable operations or the meeting of ongoing liquidity needs.
The accompanying condensed consolidated financial statements have been prepared on a going concern basis, which contemplates the realization of assets and satisfaction of liabilities in the normal course of business. In 2021 and 2020, the Company received aggregate proceeds of $67.0 million and $30.0 million, respectively, from the issuance of its Series B redeemable convertible preferred stock. Additionally, in 2020, the Company received $8.0 million from the issuance of promissory notes. As of March 31, 2022, the Company had an accumulated deficit of $126.9 million, and cash, cash equivalents and restricted cash of $41.4 million. As of December 31, 2021, the Company had an accumulated deficit of $115.1 million, and cash, cash equivalents and restricted cash of $59.3 million.
As of May 20, 2022, the issuance date of the condensed consolidated financial statements as of and for the three months ended March 31, 2022, the Company expects that its cash and cash equivalents will not be
F-85
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
sufficient to fund its operating expenses and capital expenditure requirements for at least one year from the issuance date of the condensed consolidated financial statements and therefore the Company concluded that substantial doubt existed about the Company’s ability to continue as a going concern.
The Company is seeking to complete a liquidity event via a special purpose acquisition company (“SPAC”) (see pending merger with Dynamics Special Purpose Corp. below). Upon the completion of a qualified public offering on specified terms, the Company’s outstanding convertible preferred stock will automatically convert into shares of common stock. These plans are intended to mitigate the relevant conditions or events that raise substantial doubt about the Company’s ability to continue as a going concern; however, as the plans are not entirely within the Company’s control, management cannot assure they will be effectively implemented. In the event the Company does not complete a SPAC merger, the Company expects to seek additional funding through private equity financings, debt financings, collaborations, licensing arrangements, and/or strategic alliances. The Company may not be able to obtain financing on acceptable terms, or at all, and the Company may not be able to enter into collaborations or other such arrangements. The terms of any financing may adversely affect the holdings or the rights of the Company’s stockholders. If the Company is unable to raise capital when needed, or on attractive terms, it could be forced to delay, reduce or eliminate its research or drug development programs or any future commercialization efforts.
Pending Merger with Dynamics Special Purpose Corp.
On December 19, 2021, the Company entered into a Business Combination Agreement with Dynamics Special Purpose Corp. (“DYNS”), a publicly-traded SPAC. Under the terms of the proposed transaction, DYNS will merge with the Company at an estimated combined enterprise value of approximately $276.0 million. The cash components of the transaction will be funded by DYNS’ cash in trust of $230.0 million (assuming no redemptions) as well as a $66.8 million private placement of common stock at $10.00 per share from various accredited investors.
2. Summary of Significant Accounting Policies and Basis of Presentation
There have been no material changes to the Company’s significant accounting policies as of and for the three months ended March 31, 2022, as compared to the significant accounting policies described in the Company’s audited annual consolidated financial statements as of and for the year ended December 31, 2021, except as discussed below.
Recently Adopted Accounting Pronouncements
In November 2021, the FASB issued Accounting Standards Update (ASU) No. 2021-10, Government Assistance (Topic 832): Disclosures by Business Entities about Government Assistance, which requires business entities to provide certain disclosures when they have received government assistance and use a grant or contribution accounting model by analogy to other accounting guidance. The ASU was effective January 1, 2022, and had no material impact on the Company’s condensed consolidated financial statements and related disclosures.
In May 2021, the FASB issued ASU 2021-04 Earnings Per Share (Topic 260), Debt-Modifications and Extinguishments (Subtopic 370-50), Compensation-Stock Compensation (Topic 718), and Derivatives and Hedging-Contracts in Entity’s Own Equity (Subtopic 815-40); Issuer’s Accounting for Certain Modifications or Exchanges of Freestanding Equity-Classified Written Call Options (a consensus of the FASB Emerging Issues
F-86
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
Task Force), which clarifies and reduces diversity in an issuer’s accounting for modifications or exchanges of freestanding equity-classified written call options that remain equity classified after modification or exchange. The ASU was effective January 1, 2022, and had no material impact on the Company’s condensed consolidated financial statements and related disclosures.
In August 2020, the FASB issued ASU No. 2020-06, Debt—Debt with Conversion and Other Options (Subtopic 470-20) and Derivatives and Hedging—Contracts in Entity’s Own Equity (Subtopic 815-40): Accounting for Convertible Instruments and Contracts in an Entity’s Own Equity, which simplifies accounting for convertible instruments by removing major separation models required under current GAAP. The ASU removes certain settlement conditions that are required for equity contracts to qualify for the derivative scope exception and it also simplifies the diluted earnings per share calculation in certain areas. The ASU was effective January 1, 2022, and had no material impact on the Company’s condensed consolidated financial statements and related disclosures.
In December 2019, the FASB issued ASU No. 2019-12, Simplifying the Accounting for Income Taxes (Topic 740), which removes certain exceptions to the general principles in Topic 740 and improves consistent application of and simplifies GAAP for other areas of Topic 740 by clarifying and amending existing guidance. The ASU was effective January 1, 2022, and had no material impact on the Company’s condensed consolidated financial statements and related disclosures.
3. Fair Value Measurements
The following tables summarize the estimated value of cash equivalents and restricted cash (in thousands):
| March 31, 2022 | ||||||||||||||||
| Amortized Cost | Unrealized Gain | Unrealized Loss | Estimated Fair Value | |||||||||||||
Cash equivalents: | ||||||||||||||||
Money market fund | $ | 38,140 | $ | — | $ | — | $ | 38,140 | ||||||||
Restricted cash: | ||||||||||||||||
Money market fund | 3,257 | — | — | 3,257 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Total | $ | 41,397 | $ | — | $ | — | $ | 41,397 | ||||||||
|
|
|
|
|
|
|
| |||||||||
| December 31, 2021 | ||||||||||||||||
| Amortized Cost | Unrealized Gain | Unrealized Loss | Estimated Fair Value | |||||||||||||
Cash equivalents: | ||||||||||||||||
Money market fund | $ | 56,034 | $ | — | $ | — | $ | 56,034 | ||||||||
Restricted cash: | ||||||||||||||||
Money market fund | 3,257 | — | — | 3,257 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Total | $ | 59,291 | $ | — | $ | — | $ | 59,291 | ||||||||
|
|
|
|
|
|
|
| |||||||||
F-87
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
Financial assets and liabilities measured and recognized at fair value are as follows (in thousands):
| March 31, 2022 | ||||||||||||||||
| Level 1 | Level 2 | Level 3 | Total | |||||||||||||
Assets: | ||||||||||||||||
Cash equivalents: | ||||||||||||||||
Money market fund | $ | 38,140 | $ | — | $ | — | $ | 38,140 | ||||||||
Restricted cash: | ||||||||||||||||
Money market fund | 3,257 | — | — | 3,257 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Total Assets | $ | 41,397 | $ | — | $ | — | $ | 41,397 | ||||||||
|
|
|
|
|
|
|
| |||||||||
| December 31, 2021 | ||||||||||||||||
| Level 1 | Level 2 | Level 3 | Total | |||||||||||||
Assets: | ||||||||||||||||
Cash equivalents: | ||||||||||||||||
Money market fund | $ | 56,034 | $ | — | $ | — | $ | 56,034 | ||||||||
Restricted cash: | ||||||||||||||||
Money market fund | 3,257 | — | — | 3,257 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||
Total Assets | $ | 59,291 | $ | — | $ | — | $ | 59,291 | ||||||||
|
|
|
|
|
|
|
| |||||||||
No securities have contractual maturities of longer than one year. There were no transfers between Levels 1, 2, or 3 for any of the periods presented.
Preferred Stock Tranche Liability
The initial and subsequent fair values of the preferred stock tranche liability recognized in connection with the issuance of Series B redeemable convertible preferred stock financing were determined with the assistance of a third-party valuation specialist using significant inputs not observable in the market which constitute Level 3 measurements within the fair value hierarchy.
The following reflects the significant quantitative inputs used in the valuation of the preferred stock tranche liability for fiscal year 2020 on initial closing on October 22, 2020, second closing on December 28, 2020 and subsequent measurement as of December 31, 2020 using a Monte Carlo valuation model and/or Black-Scholes option pricing model:
| October 22, 2020 Initial Measurement Date | December 28 and December 31, 2020 Subsequent Measurement Dates | |||||||||||||||
| Tranche 2 Call Option | Tranche 3 Call Option | Tranche Features 2 and 3 Call Option | Tranche 2 and 3 Forward Contracts | |||||||||||||
Estimated fair value of Series B redeemable convertible preferred stock(1) | $ | 1.25 | $ | 1.25 | $ | 1.62 | $ | 1.62 | ||||||||
Discount rate | 0.12 | % | 0.17 | % | 0.11 | % | 0.11 | % | ||||||||
Time to liquidity (years) | 0.9 | 2.2 | 0.5 | 0.5 | ||||||||||||
Expected volatility | 54.9 | % | 54.9 | % | 73.8 | % | N/A | |||||||||
Probability of call option and forward contract | N/A | N/A | 10 | % | 90 | % | ||||||||||
Strike Price | $ | 1.6427 | $ | 1.6427 | $ | 1.6427 | $ | 1.6427 | ||||||||
Value of each tranche feature | $ | 0.143 | $ | 0.199 | $ | 0.326 | $ | (0.023 | ) | |||||||
| (1) | Fair value of the Series B redeemable convertible preferred stock was estimated using the Backsolve method. |
F-88
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
The weighted-average fair value of the tranche features on a per share basis was $0.172 as of October 22, 2020, $0.012 as of December 28, 2020 and December 31, 2020 for a preferred stock tranche liability of $0.4 million as of December 31, 2020.
For the October 2020 issuance of Series B redeemable convertible preferred stock, certain investors received the right to participate in two additional closings at a fixed price which were valued as a call option (Note 6) when issued.
In connection with the December 2020 issuance of Series B redeemable convertible preferred stock, certain investors of Series B redeemable convertible preferred stock that held 48.65% of the Company’s outstanding shares and have 2 seats on the Company’s board of directors, forfeited their rights to participate in two additional closings of Series B redeemable convertible preferred stock which resulted in the measurement of the preferred stock tranche liability as a combination of a call option and forward contract.
In January 2021, the Company issued additional Series B redeemable convertible preferred stock and recorded an addition to the tranche liability of $33 thousand in recognition of the obligation to sell additional shares at a fixed price in the event that certain agreed-upon milestones are achieved or at the election of investors.
The following reflects the significant quantitative inputs used in the valuation of the preferred stock tranche liability as of March 31, 2021 using a Black-Scholes pricing model and a scenario analysis:
| March 31, 2021 (unaudited) | ||||||||||||||||||||||||
| Tranche 2 | Tranche 3 (Public) | Tranche 3 (Staying Private) | ||||||||||||||||||||||
| Forward | Call | No Value | Call | Forward | No Value | |||||||||||||||||||
Estimated fair value of Series B redeemable convertible preferred stock(1) | $ | 2.0796 | $ | 2.3386 | N/A | $ | 1.3023 | $ | 1.3023 | N/A | ||||||||||||||
Discount rate | 0.03 | % | 0.05 | % | N/A | 0.06 | % | 0.06 | % | N/A | ||||||||||||||
Time to liquidity (years) | 0.08 | 0.50 | N/A | 0.75 | 0.75 | N/A | ||||||||||||||||||
Probability of call option and forward contract | 100.0 | % | 25.0 | % | 75.0 | % | 45.0 | % | 5.0 | % | 50.0 | % | ||||||||||||
Strike price | $ | 1.6427 | $ | 1.6427 | N/A | $ | 1.6427 | $ | 1.6427 | N/A | ||||||||||||||
Expected volatility | N/A | 80.00 | % | N/A | 80.00 | % | N/A | N/A | ||||||||||||||||
Value of each tranche feature | $ | 0.437 | $ | 0.873 | $ | — | $ | 0.251 | $ | (0.340 | ) | $ | — | |||||||||||
|
|
|
|
|
|
|
|
|
|
|
| |||||||||||||
Total value of tranche feature (in millions) | $ | 8.6 | $ | 4.3 | $ | 1.9 | ||||||||||||||||||
| (1) | Fair value of the Series B redeemable convertible preferred stock for Tranche 3 was estimated using guideline IPO transactions for the public scenario and the Black-Scholes based option pricing model for the staying-private scenario, and for Tranche 2 was based on a weighting of the public and staying-private scenarios used for Tranche 3. |
The total value of Tranche 2 was determined as a forward contract for a total of $8.6 million. The value of Tranche 3 was determined using public company and staying-private scenarios for a total value of $4.3 million and $1.9 million, respectively. The Company applied a 75% weighting to the public scenario and a 25% weighting to the staying-private scenario, resulting in a value of Tranche 3 rights of $3.7 million.
The weighted average fair value of the tranche feature on a per share basis was $0.312 as of March 31, 2021 for a total preferred stock tranche liability of $12.3 million resulting in a change in fair value of the preferred stock tranche liability of $11.8 million for the three months ended March 31, 2021.
F-89
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
In April 2021, the Company’s Board of Directors determined that certain technical milestones within the Series B agreements had been achieved and approved the notice to call tranches 2 and 3, subject to requisite stockholders’ written election and related waivers. The second and third closings occurred on May 14, 2021 and all shares of the Series B redeemable convertible preferred stock were acquired, thereby extinguishing the preferred stock tranche liability.
4. Other Financial Statement information
Prepaid Expenses and Other Current Assets
Prepaid expenses and other current assets consisted of the following (in thousands):
| March 31, 2022 | December 31, 2021 | |||||||
Deposits | $ | 1,324 | $ | 1,157 | ||||
SPAC deferred offering costs | 3,073 | 1,446 | ||||||
Prepaid expenses (including prepaid rent) | 1,003 | 798 | ||||||
Other | 648 | 275 | ||||||
|
|
|
| |||||
Total prepaid expenses and other current assets | $ | 6,048 | $ | 3,676 | ||||
|
|
|
| |||||
Property and Equipment, Net
Property and equipment, net consisted of the following (in thousands):
| March 31, 2021 | December 31, 2021 | |||||||
Lab equipment | $ | 5,301 | $ | 4,988 | ||||
Leasehold improvements | 431 | 431 | ||||||
Computer equipment and software | 309 | 262 | ||||||
Furniture and fixtures | 294 | 294 | ||||||
Construction in progress | 19,599 | 8,048 | ||||||
|
|
|
| |||||
Property and equipment at cost | 25,934 | 14,023 | ||||||
Less: accumulated depreciation | (1,867 | ) | (1,655 | ) | ||||
|
|
|
| |||||
Property and equipment, net | $ | 24,067 | $ | 12,368 | ||||
|
|
|
| |||||
Depreciation expense for the three months ended March 31, 2022 and 2021 was $0.2 million and $0.2 million, respectively. For the three months ended March 31, 2022 and 2021, the Company impaired fixed assets and recorded impairment losses of zero.
F-90
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
Accrued Expenses and Other Liabilities
Accrued expenses and other liabilities consisted of the following (in thousands):
| March 31, 2022 | December 31, 2021 | |||||||
Accrued professional and service fees | $ | 7,680 | $ | 2,555 | ||||
Accrued employee-related expenses | 1,247 | 2,665 | ||||||
Other accrued expenses | 52 | 111 | ||||||
|
|
|
| |||||
Total accrued expenses and other current liabilities | $ | 8,979 | $ | 5,331 | ||||
|
|
|
| |||||
5. Redeemable Convertible Preferred Stock
The Company’s redeemable convertible preferred stock consisted of the following (in thousands, except per share amounts) as of March 31, 2022 and December 31, 2021:
| Issue Price | Shares Authorized | Shares Issued and Outstanding | Net Carrying Value | Aggregate Liquidation Preference | ||||||||||||||||
Series A | $ | 1.6427 | 35,199,610 | 35,199,610 | $ | 57,408 | $ | 57,822 | ||||||||||||
Series B | $ | 1.6427 | 64,534,944 | 64,534,933 | $ | 114,425 | $ | 106,012 | ||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
Total | 99,734,554 | 99,734,543 | $ | 171,833 | $ | 163,834 | ||||||||||||||
|
|
|
|
|
|
|
| |||||||||||||
6. Common Stock
Holders of common stock are entitled to one vote per share, and to receive dividends and, upon liquidation or dissolution, are entitled to receive all assets available for distribution to stockholders. The holders have no preemptive or other subscription rights, and there are no redemption or sinking fund provisions with respect to such shares. Common stock is subordinate to the redeemable convertible preferred stock with respect to dividend rights and rights upon liquidation, winding up, and dissolution of the Company. Through March 31, 2022, no cash dividends have been declared or paid.
At March 31, 2022 and December 31, 2021, the Company was authorized to issue 138,000,000 shares of common stock, all at a par value of $0.0001 per share, and had reserved the following shares for future issuance:
| March 31, 2022 | December 31, 2021 | |||||||
Series A and B redeemable convertible preferred stock | 99,734,543 | 99,734,543 | ||||||
Stock options to purchase common stock | 9,273,083 | 11,711,174 | ||||||
Common stock options available for future grant under stock option plan | 5,646,099 | 3,666,927 | ||||||
|
|
|
| |||||
Total | 114,653,725 | 115,112,644 | ||||||
|
|
|
| |||||
In addition to the stock options to purchase common stock in the above table, in association with the Business Combination Agreement with DYNS, the Company awarded certain performance and market awards with vesting contingent upon the consummation of the SPAC merger. See Note 8 - Stock-Based Compensation for further details.
F-91
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
7. Revenue
The Company’s revenue consists of amounts received related to research services provided to customers.
Contract Revenue
In May 2019, the Company entered into a collaborative development agreement. The Company determined that the agreement contained three distinct promises; research and development, design services, and intellectual property, which will be accounted for as a single combined performance obligation of research and development services recognized over time. The development agreement included $0.3 million of fixed consideration allocated to a single performance obligation and an additional $0.3 million of variable consideration. At the inception of the development agreement, it was not probable that a significant reversal of revenue would not occur and therefore the variable consideration was fully constrained. Throughout the development agreement period, several parameters of the research and development services were changed, which increased the uncertainty of achieving the remaining performance obligations. Therefore, in December 2021, the contract asset of $0.3 million was reversed due to this increased uncertainty.
In April 2021, the Company entered into a research collaboration and license agreement with Spark Therapeutics, Inc. (“Spark”). Under the agreement, the Company will be responsible for a research program, which includes designing, building and testing five cell type specific-synthetic promoters for use in developing certain gene therapies using the Company’s proprietary technology. The Company received an upfront payment from Spark of $3.0 million and Spark is obligated to reimburse the Company for costs and expenses incurred for the research program. The Company expects to complete the research program over a two-year period.
The Company assessed this agreement in accordance with ASC 606, Revenue Recognition (“ASC 606”) and concluded that the contract counterparty, Spark, is a customer. The Company identified only one combined performance obligation in the agreement, which is to perform research services, the related joint research plan and committees for the five specified promoters. The Company determined that the research activities for each of the five promoters are not distinct given there is one single research plan that is performed by the same research team and research results for one promoter may provide insights for other promoters.
Pursuant to the agreement, once the research program is completed and the Company delivers a data package to Spark, Spark has 24 months (the “evaluation period”) to determine whether Spark will exercise its options to obtain field-limited, royalty-bearing licenses to develop, manufacture and commercialize promoters corresponding to each of the five specified promoters being researched. For each licensed promoter option that is exercised, the Company is eligible to receive a license fee, potential research, development and commercial milestone payments and royalties on product sales. Spark may generally terminate the agreement upon 90 days prior written notice or 180 days prior written notice if the licensed promoter is in clinical trials or is being commercialized at the time of termination.
The Company evaluated Spark’s optional rights to license, develop, manufacture and commercialize each of the promoter profiles to determine whether they provide Spark with any material rights to purchase the promoter licenses at an incremental discount. The Company’s proprietary technology used to develop the promoters is in the early stages of development, so technological feasibility and probability of developing a product is highly uncertain. As a result, determining the SSP for the optional rights is subject to significant judgment. Given the subjectivity associated with determining the SSP for the right to a future license related to unproven technology at contract inception, the Company also evaluated whether the contract consideration associated with the research services represents the SSP for those services. The Company determined the transaction price, inclusive of the
F-92
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
upfront payment and reimbursement of costs and expenses incurred for the research program, is commensurate with SSP for the research being conducted given the specialized nature and reliance on proprietary technology. Based on the Company’s assessment of the optional consideration and the qualitative factors of feasibility and probability of development combined with the quantitative assessment that research services are priced at their SSP, the Company concluded that the license option does not provide Spark with an incremental discount and therefore does not constitute a material right. The transaction price associated with the research services in this agreement consists of the fixed upfront amount of $3.0 million and variable consideration.
For both collaboration agreements, the Company will recognize the transaction price as research and development services are provided, using a cost-based input method to measure the progress toward completion of its performance obligation and to calculate the corresponding amount of revenue to recognize each period. The Company believes that the cost-based input method is the best measure of progress because other measurements would not reflect how the Company transfers the control related to the performance obligation to our customers.
For the three months ended March 31, 2022 and 2021, the Company recorded revenue, which was previously included in the deferred revenue at the beginning of each period, of $0.4 million and zero, respectively. Contract asset balances related to unbilled revenue for our collaboration agreements were zero as of March 31, 2022 and 2021, and are presented within prepaid expenses and other current assets on the condensed consolidated balance sheets.
Grant Income
In 2021, the Small Business Innovation Research awarded the Company a grant in the amount of $2.0 million over two years subject to meeting certain terms and conditions. The purpose of the grant is to support the further development of SENTI-202 for acute myeloid leukemia towards clinical development.
Grant income was recognized when qualified research and development costs were incurred and the Company obtained reasonable assurance that the terms and conditions of the grant were met.
Entity-wide information
During the three months ended March 31, 2022, Customer A and B accounted for 77% and 23%, respectively, of revenue. During the three months ended March 31, 2021, Customer B and C accounted for 39% and 61%, respectively, of revenue.
All revenues were generated in the United States for the three months ended March 31, 2022 and 2021.
8. Stock-Based Compensation
In 2016, the Company adopted the 2016 Stock Incentive Plan (the “2016 Stock Incentive Plan”) authorizing the grant of incentive stock options (“ISOs”) and non-statutory stock options (“NSOs”) to eligible employees, officers and directors of, and consultants or advisors to, the Company. As of March 31, 2022, the Company is authorized to issue up to 65,551,165, of shares of common stock under the Plan in which the exercise price of an ISO and NSO shall not be less than 100% of the estimated fair value of the shares on the date of grant, as determined by the board of directors. The exercise price of an ISO granted to a 10% stockholder shall not be less than 110% of the estimated fair value of the shares on the date of grant, as determined by the board of directors. Options generally vest over four years and are exercisable for up to 10 years after the date of the grant.
F-93
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
The following table summarizes the Company’s stock option activity, excluding performance and market awards:
| Number of Options | Weighted- Average Exercise Price | Weighted- Average Remaining Contractual Life (Years) | Aggregate Intrinsic Value (in Thousands) | |||||||||||||
Outstanding at December 31, 2021 | 11,711,174 | $ | 0.86 | 9.1 | $ | 11,304 | ||||||||||
Exercised | (881,993 | ) | 0.48 | — | — | |||||||||||
Forfeited | (1,556,098 | ) | 0.53 | — | — | |||||||||||
|
|
|
|
|
|
|
| |||||||||
Outstanding at March 31, 2022 | 9,273,083 | $ | 0.95 | 8.6 | $ | 8,130 | ||||||||||
|
|
|
|
|
|
|
| |||||||||
Vested and exercisable at March 31, 2022 | 1,978,319 | $ | 0.54 | 6.8 | $ | 2,541 | ||||||||||
|
|
|
|
|
|
|
| |||||||||
The aggregate intrinsic values of options exercised during the three months ended March 31, 2022 and 2021 were $1.2 million and $0.5 million, respectively. The weighted-average grant-date fair values of options granted during the three months ended March 31, 2022 and 2021 were zero and $0.90, respectively.
Early Exercise of Stock Options into Restricted Stock
For the three months ended March 31, 2022 and 2021, the Company issued zero and 2,619,677 shares of common stock upon exercise of unvested stock options, respectively, and as of March 31, 2022 and December 31, 2021, 1,685,479 and 2,418,871 shares were held by employees subject to repurchase at an aggregate price of $0.9 million and $1.2 million, respectively.
Stock-Based Compensation Expense
In determining the fair value of the stock-based awards, the Company uses the assumptions below for the Black-Scholes option pricing model, which are subjective and generally require significant judgment.
Fair Value of Common Stock— The fair value of the shares of common stock has historically been determined by the Company’s board of directors as there was no public market for the common stock. The board of directors determines the fair value of the common stock by considering a number of objective and subjective factors, including: third-party valuations of the Company’s common stock, the valuation of comparable companies, the Company’s operating and financial performance, and general and industry-specific economic outlook, amongst other factors.
Expected Term —The expected term represents the period that the Company’s stock options are expected to be outstanding and is determined using the simplified method (based on the mid-point between the vesting date and the end of the contractual term).
Volatility —Because the Company is privately held and does not have an active trading market for its common stock for a sufficient period of time, the expected volatility was estimated based on the average volatility for comparable publicly-traded companies, over a period equal to the expected term of the stock option grants.
Risk-free Rate —The risk-free rate assumption is based on the U.S. Treasury zero-coupon issues in effect at the time of grant for periods corresponding with the expected term of the option.
Dividends —The Company has never paid dividends on its common stock and does not anticipate paying dividends on common stock. Therefore, the Company uses an expected dividend yield of zero.
F-94
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
The assumptions used to determine the grant date fair value of stock options granted to grantees were as follows, presented on a weighted-average basis:
| Three Months Ended March 31, | ||||
| 2022 | 2021 | |||
Expected term (in years) | — | 6.03 | ||
Expected volatility | — % | 82.9% | ||
Risk-free interest rate | — % | 0.6% | ||
Dividend yield | — % | — % | ||
Total stock-based compensation expense was as follows (in thousands):
| Three Months Ended March 31, | ||||||||
| 2022 | 2021 | |||||||
General and administrative | $ | 458 | $ | 317 | ||||
Research and development | 203 | 55 | ||||||
|
|
|
| |||||
Total stock-based compensation expense | $ | 661 | $ | 372 | ||||
|
|
|
| |||||
As of March 31, 2022, the total unrecognized stock-based compensation was approximately $7.2 million, which is expected to be recognized over a weighted-average period of 3.0 years.
Performance Awards
In connection with the Business Combination Agreement with DYNS, on December 19, 2021, the Company awarded 42,927,654 performance awards to existing employees that vest contingent upon the satisfaction of both a four-year service condition and a performance condition tied to the consummation of the SPAC merger. The award and the associated recognition of stock-based compensation are contingent on the SPAC merger being consummated which is subject to DYNS shareholder approval. As of March 31, 2022 and December 31, 2021, 42,486,017 and 42,909,091 performance awards remain outstanding, respectively, after the forfeiture of 423,074 performance awards during the three months ended March 31, 2022.
Market Awards
In connection with the Business Combination Agreement with DYNS, on December 19, 2021, the Company awarded 3,093,776 market awards to the co-founder and CEO, Mr. Lu that vest contingent upon the satisfaction of all three of the following conditions: a service condition, a performance condition tied to the consummation of the SPAC merger, and market conditions. The market condition is subject to achievement in four tranches, where 25% of the options will vest when the trading price of the Company’s stock is above various thresholds of price per share. The award and the associated recognition of stock-based compensation are contingent on the SPAC merger being consummated which is subject to DYNS shareholder approval.
Option Amendment
On February 12, 2022, the Company entered into Amendment No. 1 to the Business Combination Agreement, to restructure the performance and market awards made at the time the Business Combination Agreement was signed. In particular, certain Senti executives agreed to forfeit certain options awarded to them at
F-95
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
the time the Business Combination Agreement was signed depending on the level of redemptions of DYNS Class A Common Stock upon closing of the merger. In addition, it was agreed that the vesting period for the options held by executives whose options may be subject to forfeiture (as described above) will commence upon closing of the merger instead of on December 19, 2021.
9. Operating Leases
The Company’s operating leases are primarily for its corporate headquarters located in South San Francisco, California and for additional office and laboratory space located in Alameda, California (“Alameda lease”) that commenced on July 30, 2021. The corporate headquarters lease has an initial term of eight years expiring in 2027, with an option to renew for additional eight years unless canceled by either party thereafter. The Alameda lease has an initial term of eleven years expiring in 2032, with an option to renew the lease for up to two additional terms of five years. The exercise of these renewal options is not recognized as part of the ROU assets and lease liabilities, as the Company did not conclude, at the commencement date of the leases, that the exercise of renewal options or termination options was reasonably certain. The Alameda lease provides for a tenant improvement allowance of up to $17.5 million for the costs relating to the design, permitting and construction of the improvements, to be disbursed by the landlord no later than December 31, 2023. The Company was deemed to be the accounting owner of the tenant improvements primarily because the Company is the principal in the construction and design of the assets, is responsible for costs overruns and retains substantially all economic benefits from the leasehold improvements over their economic lives. Accordingly, the tenant improvement allowance is considered an incentive and was deducted from the initial measurement of the ROU asset and lease liability. The Company estimated the timing of tenant improvement reimbursements at the lease commencement date and upon receipt of the cash incentives, the Company will recognize the cash received as an increase in the lease liability.
The Company’s operating lease cost was $1.3 million and $0.7 million for the three months ended March 31, 2022 and 2021, respectively. Variable lease payments such as common area maintenance and parking fees were included in operating expenses and were $0.2 million and $0.2 million for the three months ended March 31, 2022 and 2021, respectively. The Company did not record any short-term lease expenses during the three months ended March 31, 2022 and 2021. As of March 31, 2022, the Company had utilized $2.5 million associated with the tenant improvements allowance.
Supplemental cash flow and noncash information related to the operating leases were as follows (in thousands):
| Three Months Ended March 31, | ||||||||
| 2022 | 2021 | |||||||
Supplemental cash flow information: | ||||||||
Operating cash flows from operating lease | $ | 1,874 | $ | (653 | ) | |||
Remeasurement of ROU and lease liabilities due to changes in the timing of receipt of lease incentives | $ | 239 | $ | — | ||||
F-96
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
The following summarizes additional information related to the operating leases as of March 31, 2022 and 2021:
| March 31, | ||||
| 2022 | 2021 | |||
Weighted-average remaining lease term | 7.91 years | 6.08 years | ||
Weighted-average discount rate | 9.08% | 8.91% | ||
As of March 31, 2022 and 2021, amounts disclosed for ROU assets obtained in exchange for lease obligations include amounts added to the carrying amount of ROU assets resulting from lease modifications and reassessments.
Maturities of the Company’s lease liabilities as of March 31, 2022, were as follows (in thousands):
2022 | $ | 2,090 | ||
2023 | 6,272 | |||
2024 | 7,265 | |||
2025 | 7,489 | |||
2026 | 7,723 | |||
Thereafter | 30,229 | |||
|
| |||
Total undiscounted lease payments | 61,068 | |||
Less imputed interest | (20,759 | ) | ||
Tenant improvement reimbursements | (14,914 | ) | ||
|
| |||
Total lease liabilities | $ | 25,395 | ||
|
|
10. Net Loss Per Share
A reconciliation of net loss available to common stockholders and the number of shares in the calculation of basic and diluted loss per share is as follows:
| Three Months Ended March 31, | ||||||||
| 2022 | 2021 | |||||||
Net loss | $ | (11,808 | ) | $ | (21,002 | ) | ||
|
|
|
| |||||
Weighted-average shares used in computing net loss per share, basic and diluted | 16,204,614 | 14,602,926 | ||||||
|
|
|
| |||||
Net loss per share attributable to common stockholders, basic and diluted | $ | (0.73 | ) | $ | (1.44 | ) | ||
|
|
|
| |||||
F-97
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
The following potential common shares securities were excluded from the computation of diluted net loss per share attributable to common stockholders for the periods presented because including them would have been anti-dilutive (on an as-converted basis):
| Three Months Ended March 31, | ||||||||
| 2022 | 2021 | |||||||
Series A and B redeemable convertible preferred stock | 99,734,543 | 60,368,493 | ||||||
Potential issuance of Series B redeemable convertible preferred stock under Tranche 2 | — | 19,683,025 | ||||||
Potential issuance of Series B redeemable convertible preferred stock under Tranche 3 | — | 19,683,025 | ||||||
Stock options to purchase common stock | 9,273,083 | 8,119,579 | ||||||
Unvested early exercised options | 1,685,478 | — | ||||||
|
|
|
| |||||
Total | 110,693,104 | 107,854,122 | ||||||
|
|
|
| |||||
11. Commitments and Contingencies
In the ordinary course of business, the Company enters into contractual agreements with third parties that include non-cancelable payment obligations, for which the Company is liable in future periods.
On June 3, 2021, the Company entered into a lease agreement for a new cGMP facility in Alameda, California to support planned initial clinical trials for our product candidates (Note 9). The lease will expire in 2032 with future undiscounted operating lease payments of $46.0 million over an initial lease period of eleven years.
In 2021, the Company began construction of the cGMP facility. As of March 31, 2022 the Company paid $8.2 million in construction costs and the purchase commitments amounted to approximately $35.5 million. The agreements with the construction company provide for termination following a certain period after notice. Upon termination, the Company will be responsible for payment for work performed to date.
In 2021, the Company entered into a three-year collaboration and option agreement with BlueRock Therapeutics LP (“BlueRock”) under which the Company granted BlueRock an option to acquire an exclusive or non-exclusive license to develop, manufacture and commercialize cell therapy products (Note 12). In consideration for the option, the Company is responsible for up to $10.0 million in costs and expenses incurred over the three-year term.
As of March 31, 2022, purchase commitments related to sponsored research agreements amounted to approximately $2.1 million.
The Company has entered into license agreements under which they are obligated to make annual maintenance payments of $0.1 million and specified milestone and royalty payments. Future milestone and royalty payments under these agreements are not considered contractual obligations since the payments under these agreements are contingent upon future events, such as the Company’s achievement of specified development, regulatory, and sales milestones, or generating product sales. As of March 31, 2022, the Company is unable to estimate the timing or likelihood of achieving these milestones or generating future product sales.
F-98
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
Legal Proceedings
The Company is subject to claims and assessments from time to time in the ordinary course of business but does not believe that any such matters, individually or in the aggregate, will have a material adverse effect on the Company’s financial position, results of operations, or cash flows.
Indemnifications
In the ordinary course of business, the Company enters into agreements that may include indemnification provisions. Pursuant to such agreements, the Company may indemnify, hold harmless and defend an indemnified party for losses suffered or incurred by the indemnified party. Some of the provisions will limit losses to those arising from third-party actions. In some cases, the indemnification will continue after the termination of the agreement. The maximum potential amount of future payments the Company could be required to make under these provisions is not determinable. The Company has never incurred material costs to defend lawsuits or settle claims related to these indemnification provisions and has never accrued any liabilities related to such obligations in its condensed consolidated financial statements. The Company has also entered into indemnification agreements with its directors and officers that may require the Company to indemnify its directors and officers against liabilities that may arise by reason of their status or service as directors or officers to the fullest extent permitted by Delaware corporate law. The Company currently has directors’ and officers’ insurance.
12. Related Parties
The Company issued Series A convertible redeemable preferred stock and Series B redeemable convertible preferred stock in February 2018 and October 2020, respectively, to certain related parties, including New Enterprise Associates 15, L.P. and its affiliates (“NEA”) and 8VC and its affiliates (“8VC”).
In February 2018, the outstanding convertible notes held by NEA and 8VC, as well as Timothy Lu, Chief Executive Officer, converted into additional shares of Series A redeemable convertible preferred stock while in October 2020, the outstanding convertible notes held by NEA and 8VC converted into additional shares of Series B redeemable convertible preferred stock, both in accordance with the terms of the note agreements.
NEA held 13,505,035 shares of outstanding Series A redeemable convertible preferred stock as of March 31, 2022 and December 31, 2021, as well as 2,742,931 of outstanding Series B redeemable convertible preferred stock as of March 31, 2022 and December 31, 2021, respectively. 8VC held 9,052,387 of outstanding Series A redeemable convertible preferred stock as of March 31, 2022 and December 31, 2021, respectively, as well as 1,662,398 of outstanding Series B redeemable convertible preferred stock as of March 31, 2022 and December 31, 2021, respectively. Timothy Lu held 158,950 of outstanding redeemable convertible preferred stock as of March 31, 2022 and December 31, 2021, respectively. Timothy Lu and family held 8,100,000 of common stock as of March 31, 2022 and December 31, 2021, respectively. Timothy Lu, NEA, and 8VC held three of the seven seats on the Company’s Board of Directors as of March 31, 2022 and December 31, 2021.
As Chief Executive Officer, Timothy Lu was paid $0.1 million as compensation for the three months ended March 31, 2022 and 2021, and less than $0.1 million and $0.2 million were accrued as a bonus on March 31, 2022 and December 31, 2021.
On May 21, 2021, the Company entered into a collaboration and option agreement (“BlueRock Agreement”) with BlueRock Therapeutics LP (“BlueRock”), pursuant to which the Company granted to
F-99
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
BlueRock an option (“BlueRock Option”), on a collaboration program-by-collaboration program basis, to obtain an exclusive or non-exclusive license to develop, manufacture and commercialize cell therapy products that contain cells of specified types and which incorporate an option gene circuit from such collaboration program or a closely related derivative gene circuit. The Company is responsible for up to $10 million in costs and expenses incurred in connection with the research plan and related activities to be conducted over a term of three years as specified in the collaboration and option agreement. If the Company and BlueRock agree to add new research activities to the research plan, then BlueRock will be obligated to reimburse the Company for the costs and expenses incurred that, together with costs and expenses incurred under the initial research plan, exceed $10 million.
The Company concluded that the Agreement is not within the scope of ASC 808, Collaborative Arrangements, because the Company did not receive any consideration and therefore, is not exposed to both significant risks and rewards for the arrangement. The Company also determined that the agreement is also not currently within the scope of ASC 606 because the BlueRock Agreement does not currently meet the criteria of a contract with a customer, and will not be within the scope of ASC 606 until any consideration is paid. Potential future milestone payments and royalties are subject to BlueRock’s exercise of the BlueRock Option and execution of a commercial license agreement by both parties. Under the BlueRock Agreement, the specific financial terms for milestone payments and royalties will be negotiated and agreed to only after the option is exercised.
BlueRock is a wholly-owned subsidiary of Bayer Healthcare LLC which held 27,393,924 shares of outstanding Series B redeemable convertible preferred stock as of March 31, 2022 and December 31, 2021, and holds one of the seven seats on the Company’s Board of Directors as of March 31, 2022 and December 31, 2021. Bayer Healthcare LLC’s parent company is Bayer AG, which served as the lead investor in our Series B financing through its Leaps by Bayer unit. Accordingly, BlueRock is considered a related party.
13. Subsequent Events
The Company has evaluated subsequent events from the March 31, 2022 balance sheet date through May 20, 2022, the date at which the unaudited condensed consolidated financial statements were available to be issued, and determined that there have been no events that have occurred that would require adjustments to our disclosures in the condensed consolidated financial statements except for the transaction described below.
On May 19, 2022, the Company issued a convertible note to Bayer HealthCare LLC for aggregate cash proceeds of approximately $5.2 million. The convertible note accrues interest at 3% per year and has an original maturity date of two years from issuance. The convertible note will automatically convert into shares of DYNS Class A Common Stock upon the closing of the Business Combination Agreement with DYNS at a conversion price of $10.00 per share, and all accrued interest at such time will be canceled and forgiven. The shares of Class A Common Stock will have the same registration rights as the shares to be issued in the $66.8 million private placement discussed in Note 1, Organization and Description of Business and Basis of Presentation.
14. Events (Unreviewed) Subsequent to May 20, 2022
On June 6, 2022, the Company changed its corporate name from Senti Biosciences, Inc. to Senti Sub I, Inc.
On June 8, 2022 (the “Closing Date”), the Company and DYNS consummated the transactions contemplated under the previously announced Business Combination Agreement, dated December 19, 2021 and amended on
F-100
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
February 12, 2022 and May 19, 2022 (as amended, the “Business Combination Agreement”) by and among the Company, DYNS and Explore Merger Sub Inc., a wholly-owned subsidiary of DYNS. Pursuant to the terms of the Business Combination Agreement, Merger Sub merged with and into the Company, with the Company surviving the merger as a wholly-owned subsidiary of DYNS (the “Business Combination”). In connection with the consummation of the Business Combination, DYNS changed its corporate name to Senti Biosciences, Inc. (the “Combined Company”).
At the effective time of the Business Combination (the “Effective Time”):
| • | each outstanding share of common stock of the Company (“Senti Common Stock”) was cancelled and converted into the right to receive a number of shares of Class A common stock of DYNS (“Class A Common Stock”), rounded down to the nearest whole share, equal to the number of shares of Senti Common Stock multiplied by the exchange ratio of 0.1957 (the “Exchange Ratio”); |
| • | each outstanding share of preferred stock of the Company (“Senti Preferred Stock”) was cancelled and converted into the right to receive a number of shares of Class A Common Stock, rounded down to the nearest whole share, equal to the aggregate number of shares of Senti Common Stock issuable upon conversion of the shares of Senti Preferred Stock based on the applicable conversion ratio immediately prior to the Effective Time, which was 1:1, multiplied by the Exchange Ratio; and |
| • | each outstanding option in the Company (whether vested or unvested) was converted into an option to purchase a number of shares of Class A Common Stock (rounded down to the nearest whole share) equal to the number of shares of Senti Common Stock subject to such option immediately prior to the Effective Time, multiplied by the Exchange Ratio, at an exercise price per share equal to the current exercise price per share for such option divided by the Exchange Ratio, rounded up to the nearest whole cent. |
As additional consideration, holders of shares of Senti Common Stock and Senti Preferred Stock immediately prior to the Effective Time became eligible to receive contingent consideration of up to an aggregate of 2,000,000 shares of Common Stock (as defined below), subject to the achievement of certain share price milestones within the first two or three calendar years after the Closing Date or, in certain circumstances, upon a change of control of the Combined Company.
Following the closing of the Business Combination, all shares of Class A Common Stock were redesignated as common stock, par value $0.0001 per share, of the Combined Company (“Common Stock”). On the Closing Date, the Common Stock was listed on the Nasdaq Global Market under the new trading symbol “SNTI”.
The Combined Company received gross proceeds of approximately $140.3 million of the expected $156.5 million in connection with the Business Combination, which included funds held in DYNS’s trust account of $84.5 million (net of the Redemption, as defined below), $50.6 million of the expected $66.8 million in proceeds from the PIPE Investment that closed concurrently with the consummation of the Business Combination, and a recent $5.2 million investment by Bayer Healthcare LLC (“Bayer”) through a Convertible Note Exchange (as defined below).
On the Closing Date, certain investors (the “PIPE Investors”) purchased from the Combined Company an aggregate of 5,060,000 shares of Class A Common Stock (the “PIPE Shares”), for a purchase price of $10.00 per share and an aggregate purchase price of $50.6 million, pursuant to separate subscription agreements (each, a “Subscription Agreement”) entered into and effective as of December 19, 2021 (the “PIPE Investment”). The Combined Company received original commitments under the Subscription Agreements totaling $66.8 million; however, $16.2 million had yet to be funded as of the Closing Date.
F-101
SENTI BIOSCIENCES, INC.
Notes to Condensed Consolidated Financial Statements
(unaudited)
On the Closing Date, an unsecured convertible promissory note (the “Note”) in the principal amount of $5,175,000 that was previously issued by the Company to Bayer Healthcare LLC (“Bayer”) on May 19, 2022 was automatically cancelled and exchanged for 517,500 shares of Class A Common Stock (the “Convertible Note Exchange”). All interest accrued on the Note was also cancelled as part of the Convertible Note Exchange.
F-102
35,444,908 Shares of Common Stock

PROSPECTUS
, 2022
You should rely only on the information contained in this prospectus or any supplement or amendment hereto. We have not authorized anyone to provide you with different information. You should not assume that the information contained in this prospectus or any supplement or amendment hereto is accurate as of any date other than the date of this prospectus or any such supplement or amendment. Neither the Securities and Exchange Commission nor any state securities commission has approved or disapproved of these securities or determined if this prospectus is truthful or complete. Any representation to the contrary is a criminal offense.
PART II
INFORMATION NOT REQUIRED IN PROSPECTUS
Item 13. Other Expenses of Issuance and Distribution.
The following table sets forth the estimated expenses to be borne by the registrant in connection with the securities being registered hereby.
Expense | Estimated Amount | |||
Securities and Exchange Commission registration fee | $ | 7,360.07 | ||
Accounting fees and expenses | * | |||
Legal fees and expenses | * | |||
Financial printing and miscellaneous expenses | * | |||
|
| |||
Total | $ | * | ||
|
| |||
| * | These fees are calculated based on the securities offered and the number of issuances and accordingly cannot be defined at this time. |
Item 14. Indemnification of Directors and Officers
Our amended and restated certificate of incorporation provides that all of our directors, officers, employees and agents shall be entitled to be indemnified by us to the fullest extent permitted by Section 145 of the DGCL. Section 145 of the DGCL concerning indemnification of officers, directors, employees and agents is set forth below.
Section 145. Indemnification of officers, directors, employees and agents; insurance.
| (a) | A corporation shall have power to indemnify any person who was or is a party or is threatened to be made a party to any threatened, pending or completed action, suit or proceeding, whether civil, criminal, administrative or investigative (other than an action by or in the right of the corporation) by reason of the fact that the person is or was a director, officer, employee or agent of the corporation, or is or was serving at the request of the corporation as a director, officer, employee or agent of another corporation, partnership, joint venture, trust or other enterprise, against expenses (including attorneys’ fees), judgments, fines and amounts paid in settlement actually and reasonably incurred by the person in connection with such action, suit or proceeding if the person acted in good faith and in a manner the person reasonably believed to be in or not opposed to the best interests of the corporation, and, with respect to any criminal action or proceeding, had no reasonable cause to believe the person’s conduct was unlawful. The termination of any action, suit or proceeding by judgment, order, settlement, conviction, or upon a plea of nolo contendere or its equivalent, shall not, of itself, create a presumption that the person did not act in good faith and in a manner which the person reasonably believed to be in or not opposed to the best interests of the corporation, and, with respect to any criminal action or proceeding, had reasonable cause to believe that the person’s conduct was unlawful. |
| (b) | A corporation shall have power to indemnify any person who was or is a party or is threatened to be made a party to any threatened, pending or completed action or suit by or in the right of the corporation to procure a judgment in its favor by reason of the fact that the person is or was a director, officer, employee or agent of the corporation, or is or was serving at the request of the corporation as a director, officer, employee or agent of another corporation, partnership, joint venture, trust or other enterprise against expenses (including attorneys’ fees) actually and reasonably incurred by the person in connection with the defense or settlement of such action or suit if the person acted in good faith and in a manner the person reasonably believed to be in or not opposed to the best interests of the corporation |
II-1
| and except that no indemnification shall be made in respect of any claim, issue or matter as to which such person shall have been adjudged to be liable to the corporation unless and only to the extent that the Court of Chancery or the court in which such action or suit was brought shall determine upon application that, despite the adjudication of liability but in view of all the circumstances of the case, such person is fairly and reasonably entitled to indemnity for such expenses which the Court of Chancery or such other court shall deem proper. |
| (c) | To the extent that a present or former director or officer of a corporation has been successful on the merits or otherwise in defense of any action, suit or proceeding referred to in subsections (a) and (b) of this section, or in defense of any claim, issue or matter therein, such person shall be indemnified against expenses (including attorneys’ fees) actually and reasonably incurred by such person in connection therewith. |
| (d) | Any indemnification under subsections (a) and (b) of this section (unless ordered by a court) shall be made by the corporation only as authorized in the specific case upon a determination that indemnification of the present or former director, officer, employee or agent is proper in the circumstances because the person has met the applicable standard of conduct set forth in subsections (a) and (b) of this section. Such determination shall be made, with respect to a person who is a director or officer at the time of such determination, (1) by a majority vote of the directors who are not parties to such action, suit or proceeding, even though less than a quorum, or (2) by a committee of such directors designated by majority vote of such directors, even though less than a quorum, or (3) if there are no such directors, or if such directors so direct, by independent legal counsel in a written opinion, or (4) by the stockholders. |
| (e) | Expenses (including attorneys’ fees) incurred by an officer or director in defending any civil, criminal, administrative or investigative action, suit or proceeding may be paid by the corporation in advance of the final disposition of such action, suit or proceeding upon receipt of an undertaking by or on behalf of such director or officer to repay such amount if it shall ultimately be determined that such person is not entitled to be indemnified by the corporation as authorized in this section. Such expenses (including attorneys’ fees) incurred by former officers and directors or other employees and agents may be so paid upon such terms and conditions, if any, as the corporation deems appropriate. |
| (f) | The indemnification and advancement of expenses provided by, or granted pursuant to, the other subsections of this section shall not be deemed exclusive of any other rights to which those seeking indemnification or advancement of expenses may be entitled under any bylaw, agreement, vote of stockholders or disinterested directors or otherwise, both as to action in such person’s official capacity and as to action in another capacity while holding such office. A right to indemnification or to advancement of expenses arising under a provision of the certificate of incorporation or a bylaw shall not be eliminated or impaired by an amendment to such provision after the occurrence of the act or omission that is the subject of the civil, criminal, administrative or investigative action, suit or proceeding for which indemnification or advancement of expenses is sought, unless the provision in effect at the time of such act or omission explicitly authorizes such elimination or impairment after such action or omission has occurred. |
| (g) | A corporation shall have power to purchase and maintain insurance on behalf of any person who is or was a director, officer, employee or agent of the corporation, or is or was serving at the request of the corporation as a director, officer, employee or agent of another corporation, partnership, joint venture, trust or other enterprise against any liability asserted against such person and incurred by such person in any such capacity, or arising out of such person’s status as such, whether or not the corporation would have the power to indemnify such person against such liability under this section. |
| (h) | For purposes of this section, references to “the corporation” shall include, in addition to the resulting corporation, any constituent corporation (including any constituent of a constituent) absorbed in a consolidation or merger which, if its separate existence had continued, would have had power and authority to indemnify its directors, officers, and employees or agents, so that any person who is or was |
II-2
| a director, officer, employee or agent of such constituent corporation, or is or was serving at the request of such constituent corporation as a director, officer, employee or agent of another corporation, partnership, joint venture, trust or other enterprise, shall stand in the same position under this section with respect to the resulting or surviving corporation as such person would have with respect to such constituent corporation if its separate existence had continued. |
| (i) | For purposes of this section, references to “other enterprises” shall include employee benefit plans; references to “fines” shall include any excise taxes assessed on a person with respect to any employee benefit plan; and references to “serving at the request of the corporation” shall include any service as a director, officer, employee or agent of the corporation which imposes duties on, or involves services by, such director, officer, employee or agent with respect to an employee benefit plan, its participants or beneficiaries; and a person who acted in good faith and in a manner such person reasonably believed to be in the interest of the participants and beneficiaries of an employee benefit plan shall be deemed to have acted in a manner “not opposed to the best interests of the corporation” as referred to in this section. |
| (j) | The indemnification and advancement of expenses provided by, or granted pursuant to, this section shall, unless otherwise provided when authorized or ratified, continue as to a person who has ceased to be a director, officer, employee or agent and shall inure to the benefit of the heirs, executors and administrators of such a person. |
| (k) | The Court of Chancery is hereby vested with exclusive jurisdiction to hear and determine all actions for advancement of expenses or indemnification brought under this section or under any by law, agreement, vote of stockholders or disinterested directors, or otherwise. The Court of Chancery may summarily determine a corporation’s obligation to advance expenses (including attorneys’ fees). |
Insofar as indemnification for liabilities arising under the Securities Act may be permitted to our directors, officers, and controlling persons pursuant to the foregoing provisions, or otherwise, we have been advised that, in the opinion of the SEC, such indemnification is against public policy as expressed in the Securities Act and is, therefore, unenforceable. In the event that a claim for indemnification against such liabilities (other than the payment of expenses incurred or paid by a director, officer or controlling person in a successful defense of any action, suit or proceeding) is asserted by such director, officer or controlling person in connection with the securities being registered, we will, unless in the opinion of its counsel the matter has been settled by controlling precedent, submit to the court of appropriate jurisdiction the question whether such indemnification by it is against public policy as expressed in the Securities Act and will be governed by the final adjudication of such issue.
In accordance with Section 102(b)(7) of the DGCL, our amended and restated certificate of incorporation provides that no director shall be personally liable to us or any of our stockholders for monetary damages resulting from breaches of their fiduciary duty as directors, except to the extent such limitation on or exemption from liability is not permitted under the DGCL. The effect of this provision of our amended and restated certificate of incorporation is to eliminate our rights and those of our stockholders (through stockholders’ derivative suits on our behalf) to recover monetary damages against a director for breach of the fiduciary duty of care as a director, including breaches resulting from negligent or grossly negligent behavior, except, as restricted by Section 102(b)(7) of the DGCL. However, this provision does not limit or eliminate our rights or the rights of any stockholder to seek non-monetary relief, such as an injunction or rescission, in the event of a breach of a director’s duty of care.
If the DGCL is amended to authorize corporate action further eliminating or limiting the liability of directors, then, in accordance with our amended and restated certificate of incorporation, the liability of our directors to us or our stockholders will be eliminated or limited to the fullest extent authorized by the DGCL, as so amended. Any repeal or amendment of provisions of our amended and restated certificate of incorporation limiting or eliminating the liability of directors, whether by our stockholders or by changes in law, or the adoption of any other provisions inconsistent therewith, will (unless otherwise required by law) be prospective
II-3
only, except to the extent such amendment or change in law permits us to further limit or eliminate the liability of directors on a retroactive basis.
Our amended and restated certificate of incorporation also provides that we will, to the fullest extent authorized or permitted by applicable law, indemnify our current and former officers and directors, as well as those persons who, while directors or officers of our corporation, are or were serving as directors, officers, employees or agents of another entity, trust or other enterprise, including service with respect to an employee benefit plan, in connection with any threatened, pending or completed proceeding, whether civil, criminal, administrative or investigative, against all expense, liability and loss (including, without limitation, attorney’s fees, judgments, fines, ERISA excise taxes and penalties and amounts paid in settlement) reasonably incurred or suffered by any such person in connection with any such proceeding.
Notwithstanding the foregoing, a person eligible for indemnification pursuant to our amended and restated certificate of incorporation will be indemnified by us in connection with a proceeding initiated by such person only if such proceeding was authorized by our board of directors, except for proceedings to enforce rights to indemnification.
The right to indemnification which is conferred by our amended and restated certificate of incorporation is a contract right that includes the right to be paid by us the expenses incurred in defending or otherwise participating in any proceeding referenced above in advance of its final disposition, provided, however, that if the DGCL requires, an advancement of expenses incurred by our officer or director (solely in the capacity as an officer or director of our corporation) will be made only upon delivery to us of an undertaking, by or on behalf of such officer or director, to repay all amounts so advanced if it is ultimately determined that such person is not entitled to be indemnified for such expenses under our amended and restated certificate of incorporation or otherwise.
The rights to indemnification and advancement of expenses will not be deemed exclusive of any other rights which any person covered by our amended and restated certificate of incorporation may have or hereafter acquire under law, our amended and restated certificate of incorporation, our bylaws, an agreement, vote of stockholders or disinterested directors, or otherwise.
Any repeal or amendment of provisions of our amended and restated certificate of incorporation affecting indemnification rights, whether by our stockholders or by changes in law, or the adoption of any other provisions inconsistent therewith, will (unless otherwise required by law) be prospective only, except to the extent such amendment or change in law permits us to provide broader indemnification rights on a retroactive basis, and will not in any way diminish or adversely affect any right or protection existing at the time of such repeal or amendment or adoption of such inconsistent provision with respect to any act or omission occurring prior to such repeal or amendment or adoption of such inconsistent provision. Our amended and restated certificate of incorporation will also permit us, to the extent and in the manner authorized or permitted by law, to indemnify and to advance expenses to persons other that those specifically covered by our amended and restated certificate of incorporation.
Our bylaws include the provisions relating to advancement of expenses and indemnification rights consistent with those which are set forth in our amended and restated certificate of incorporation. In addition, our bylaws provide for a right of indemnity to bring a suit in the event a claim for indemnification or advancement of expenses is not paid in full by us within a specified period of time. Our bylaws also permit us to purchase and maintain insurance, at our expense, to protect us and/or any director, officer, employee or agent of our corporation or another entity, trust or other enterprise against any expense, liability or loss, whether or not we would have the power to indemnify such person against such expense, liability or loss under the DGCL.
Any repeal or amendment of provisions of our bylaws affecting indemnification rights, whether by our board of directors, stockholders or by changes in applicable law, or the adoption of any other provisions inconsistent therewith, will (unless otherwise required by law) be prospective only, except to the extent such
II-4
amendment or change in law permits us to provide broader indemnification rights on a retroactive basis, and will not in any way diminish or adversely affect any right or protection existing thereunder with respect to any act or omission occurring prior to such repeal or amendment or adoption of such inconsistent provision.
We have entered into indemnification agreements with each of our officers and directors, a form of which is filed as Exhibit 10.5 to our Registration Statement on Form S-4 that was declared effective by the SEC on May 13, 2022. These agreements require us to indemnify these individuals to the fullest extent permitted under Delaware law against liabilities that may arise by reason of their service to us, and to advance expenses incurred as a result of any proceeding against them as to which they could be indemnified.
These limitations of liability do not alter director liability under the federal securities laws and do not affect the availability of equitable remedies such as an injunction or rescission.
Pursuant to the Business Combination Agreement, we agreed to continue to indemnify DYNS’ directors and officers and have agreed to the continuation of director and officer liability insurance covering such directors and officers.
Item 15. Recent Sales of Unregistered Securities.
On March 8, 2021, the Sponsor was issued 5,750,000 shares of DYNS Class B Common Stock (the Founder Shares) for an aggregate price of $25,000. The Founder Shares included an aggregate of up to 750,000 shares of Class B Common Stock subject to forfeiture by the Sponsor to the extent that the underwriter’s over-allotment option was not exercised in full or in part, so that the Sponsor would own, on an as-converted basis, 20% of DYNS’ issued and outstanding shares after its Initial Public Offering (excluding the Private Placement Shares) and assuming its Sponsor did not purchase any Public Shares in its Initial Public Offering). The underwriter fully exercised the over-allotment option on May 28, 2021; thus, these 750,000 Founder Shares are no longer subject to forfeiture.
Simultaneously with the closing of the DYNS Initial Public Offering, DYNS consummated the sale of 715,500 shares of its Class A Common Stock (the “Private Placement Shares”) at a price of $10.00 per share in a private placement to its Sponsor, generating gross proceeds of $7,155,000. A portion of the proceeds from the sale of the Private Placement Shares was added to the net proceeds from its Initial Public Offering held in the Trust Account. If DYNS did not complete an initial business combination within 24 months from the closing of its Initial Public Offering, the proceeds from the sale of the Private Placement Shares held in the Trust Account would have been used to fund the redemption of Public Shares (subject to the requirements of applicable law).
On March 8, 2021, DYNS issued an unsecured promissory note to its Sponsor (the “Promissory Note”), pursuant to which DYNS could borrow up to an aggregate of $300,000 to cover expenses related to its Initial Public Offering. The Promissory Note was non-interest bearing and was payable on the earlier of December 31, 2021 or the consummation of its Initial Public Offering. In April 2021, DYNS borrowed $250,000 under the Promissory Note, which was repaid on May 26, 2021.
In connection with the Business Combination, DYNS entered into subscription agreements with the PIPE Investors, pursuant to which the PIPE Investors purchased, and DYNS sold to the PIPE Investors, on June 8, 2022, an aggregate of 5,060,000 shares of DYNS Class A Common Stock, for a purchase price of $10.00 per share and an aggregate purchase price of $50.6 million out of an expected $66.8 million, in the PIPE Investment. We gave certain registration rights to the PIPE Investors with respect to the PIPE Shares.
In connection with the Business Combination, DYNS issued 517,500 shares of DYNS Class A Common Stock to Bayer Healthcare LLC on June 8, 2022, in connection with the cancellation and exchange of the Convertible Note simultaneously with the closing of the PIPE Investment. Bayer Healthcare LLC is entitled to registration rights with respect to the shares issued upon the cancellation and exchange of the Convertible Note.
II-5
None of the foregoing transactions involved any underwriters, underwriting discounts or commissions, or any public offering. We believe each of these transactions was exempt from registration under the Securities Act in reliance on Section 4(a)(2) of the Securities Act (and Regulation D promulgated thereunder) as transactions by an issuer not involving any public offering. The recipients of the securities in each of these transactions represented their intentions to acquire the securities for investment only and not with a view to or for sale in connection with any distribution thereof, and appropriate legends were placed on the share certificates issued in these transactions. All recipients had adequate access, through their relationships with us, to information about us. The sales of these securities were made without any general solicitation or advertising.
Item 16. Exhibits and Financial Statements Schedules
(a)Exhibits.
II-6
II-7
| * | Previously filed |
| ^ | Certain exhibits and schedules to this Exhibit have been omitted in accordance with Regulation S-K Item 601(b)(2). The Company agrees to furnish supplementally a copy of all omitted exhibits and schedules to the Securities and Exchange Commission upon its request. |
II-8
| † | Portions of this exhibit (indicated by asterisks) have been omitted because the registrant has determined that the information is both not material and is the type that the registration treats as private or confidential |
| + | Indicates management contract or compensatory plan. |
(b)Financial Statement Schedules.
See the index to the consolidated financial statements included on page F-1 for a list of the financial statements included in this registration statement. Schedules not listed above have been omitted because the information required to be set forth therein is not applicable or is shown in the financial statements or notes thereto.
Item 17. Undertakings
The undersigned registrant hereby undertakes:
| 1. | To file, during any period in which offers or sales are being made, a post-effective amendment to this registration statement: |
| (i) | To include any prospectus required by section 10(a)(3) of the Securities Act; |
| (ii) | To reflect in the prospectus any facts or events arising after the effective date of the registration statement (or the most recent post-effective amendment thereof) which, individually or in the aggregate, represent a fundamental change in the information set forth in the registration statement. Notwithstanding the foregoing, any increase or decrease in volume of securities offered (if the total dollar value of securities offered would not exceed that which was registered) and any deviation from the low or high end of the estimated maximum offering range may be reflected in the form of prospectus filed with the SEC pursuant to Rule 424(b) if, in the aggregate, the changes in volume and price represent no more than 20% change in the maximum aggregate offering price set forth in the “Calculation of Registration Fee” table in the effective registration statement. |
| (iii) | To include any material information with respect to the plan of distribution not previously disclosed in the registration statement or any material change to such information in the registration statement; |
| 2. | That, for the purpose of determining any liability under the Securities Act, each such post-effective amendment shall be deemed to be a new registration statement relating to the securities offered therein, and the offering of such securities at that time shall be deemed to be the initial bona fide offering thereof. |
| 3. | To remove from registration by means of a post-effective amendment any of the securities being registered which remain unsold at the termination of the offering. |
| 4. | That, for the purpose of determining liability under the Securities Act to any purchaser, each prospectus filed pursuant to Rule 424(b) as part of a registration statement relating to an offering, other than registration statements relying on Rule 430B or other than prospectuses filed in reliance on Rule 430A, shall be deemed to be part of and included in the registration statement as of the date it is first used after effectiveness. Provided, however, that no statement made in a registration statement or prospectus that is part of the registration statement or made in a document incorporated or deemed incorporated by reference into the registration statement or prospectus that is part of the registration statement will, as to a purchaser with a time of contract of sale prior to such first use, supersede or modify any statement that was made in the registration statement or prospectus that was part of the registration statement or made in any such document immediately prior to such date of first use. |
| 5. | That, for the purpose of determining liability of the registrant under the Securities Act to any purchaser in the initial distribution of the securities, that in a primary offering of securities of the undersigned registrant pursuant to this registration statement, regardless of the underwriting method used to sell the |
II-9
| securities to the purchaser, if the securities are offered or sold to such purchaser by means of any of the following communications, the undersigned registrant will be a seller to the purchaser and will be considered to offer or sell such securities to such purchaser: |
| (i) | Any preliminary prospectus or prospectus of the undersigned registrant relating to the offering required to be filed pursuant to Rule 424; |
| (ii) | Any free writing prospectus relating to the offering prepared by or on behalf of the undersigned registrant or used or referred to by the undersigned registrant; |
| (iii) | The portion of any other free writing prospectus relating to the offering containing material information about the undersigned registrant or its securities provided by or on behalf of the undersigned registrant; and |
| (iv) | Any other communication that is an offer in the offering made by the undersigned registrant to the purchaser. |
Insofar as indemnification for liabilities arising under the Securities Act may be permitted to directors, officers and controlling persons of the registrant pursuant to the foregoing provisions, or otherwise, the registrant has been advised that in the opinion of the SEC such indemnification is against public policy as expressed in the Securities Act and is, therefore, unenforceable. In the event that a claim for indemnification against such liabilities (other than the payment by the registrant of expenses incurred or paid by a director, officer or controlling person of the registrant in the successful defense of any action, suit or proceeding) is asserted by such director, officer or controlling person in connection with the securities being registered, the registrant will, unless in the opinion of its counsel the matter has been settled by controlling precedent, submit to a court of appropriate jurisdiction the question whether such indemnification by it is against public policy as expressed in the Securities Act and will be governed by the final adjudication of such issue.
II-10
SIGNATURES
Pursuant to the requirements of the Securities Act, the registrant has duly caused this Amendment No. 1 to registration statement to be signed on its behalf by the undersigned, thereunto duly authorized, in the City of South San Francisco, CA on the 29th day of July, 2022.
| SENTI BIOSCIENCES, INC. | ||
| By: | /s/ Timothy Lu | |
| Name: Timothy Lu, M.D., Ph.D. | ||
| Title: Chief Executive Officer and President | ||
Pursuant to the requirements of the Securities Act of 1933, as amended, this registration statement has been signed below by the following person in the capacities and on July 29, 2022.
Signature | Title | |
/s/ Timothy Lu Timothy Lu, M.D., Ph.D. | Chief Executive Officer, President and Director (Principal Executive Officer) | |
/s/ Deborah Knobelman Deborah Knobelman, Ph.D. | Chief Financial Officer (Principal Financial Officer and Principal Accounting Officer) | |
* Susan Berland | Director | |
* Brenda Cooperstone, M.D. | Director | |
* Edward Mathers | Director | |
* James J. (Jim) Collins | Director | |
* Omid Farokhzad | Director | |
* David Epstein | Director | |
| * By: | /s/ Timothy Lu | |
| Timothy Lu | ||
| Attorney-in-Fact |