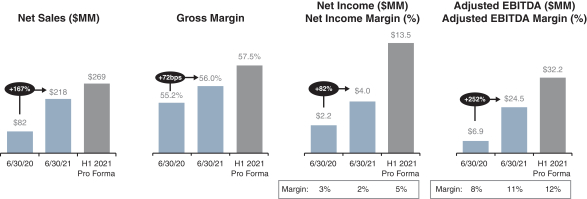
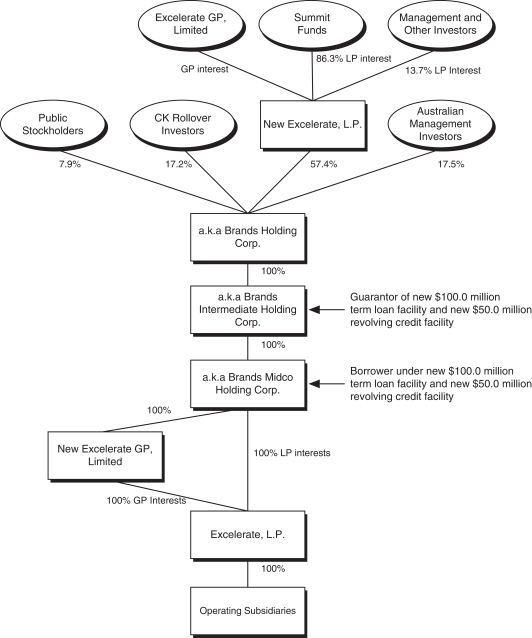
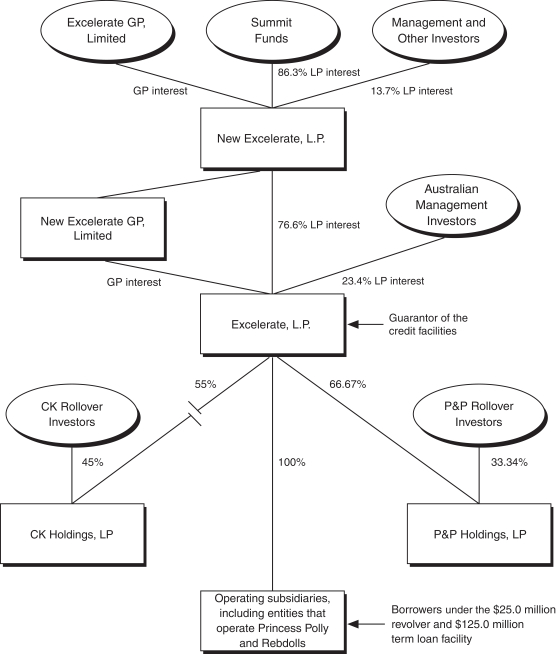
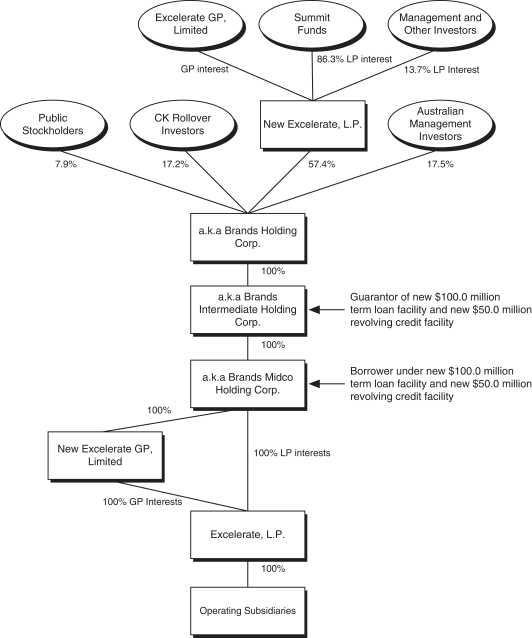
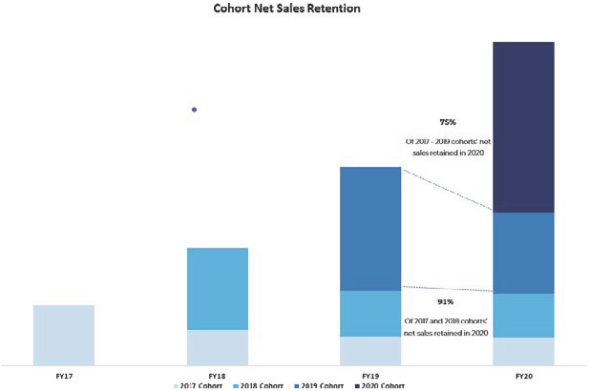
new products. Failure to meet customer orders could result in loss of customers or harm our ability to attract new customers, either of which could have a material and adverse effect on our business, financial condition, results of operations and growth.
Risks Relating to Our Intellectual Property Rights and Our Technology
We rely significantly on information technology. Any inadequacy, interruption, integration failure or security failure of this technology could harm our ability to effectively operate our business.
Our ability to effectively manage and operate our business depends significantly on information technology systems. We rely heavily on information technology to enable, track, and facilitate sales and inventory and manage our supply chain. We are also dependent on information technology, including the internet, for our direct-to-consumer sales, including our eCommerce operations and retail business credit card transaction authorization. Despite our preventative efforts, our systems and those of our third-party service providers may be vulnerable to damage, failure or interruption due to viruses, data security incidents, technical malfunctions, natural disasters or other causes, or in connection with upgrades to our system or the implementation of new systems. The failure of these systems to operate effectively, problems with transitioning to upgraded or replacement systems, difficulty in integrating new systems or systems of acquired businesses or a breach in security of these systems could adversely impact the operations of our business, including our reputation, management of inventory, ordering and replenishment of products, manufacturing and distribution of products, eCommerce operations, retail business credit card transaction authorization and processing, corporate email communications and our interaction with the public on social media.
A security breach or other disruption to our information technology systems could result in the loss, theft, misuse, unauthorized disclosure, or unauthorized access of customer, supplier, or sensitive company information or could disrupt our operations, which could damage our relationships with customers, suppliers or employees, expose us to litigation or regulatory proceedings, or harm our reputation, any of which could materially adversely affect our business, financial condition, or results of operations.
Our business involves the storage and transmission of a significant amount of personal, confidential, or sensitive information, including the personal information of our customers, credit card information, the personal information of our employees, information relating to customer preferences, and our proprietary financial, operational, and strategic information. The protection of this information is vitally important to us as the loss, theft, misuse, unauthorized disclosure, or unauthorized access of such information could lead to significant reputational or competitive harm, result in litigation involving us or our business partners, expose us to regulatory proceedings, and cause us to incur substantial liabilities, fines, penalties, or expenses. As a result, we believe our future success and growth depends, in part, on the ability of our key business processes and systems, including our information technology and global communication systems, to prevent the theft, loss, misuse, unauthorized disclosure, or unauthorized access of this personal, confidential, and sensitive information, and to respond quickly and effectively if data security incidents do occur. As with many businesses, we are subject to numerous data privacy and security risks, which may prevent us from maintaining the privacy of this information, result in the disruption of our business, and require us to expend significant resources attempting to secure and protect such information and respond to incidents, any of which could materially adversely affect our business, financial condition, or results of operations.
The frequency, intensity, and sophistication of cyber-attacks, ransom-ware attacks, and other data security incidents has significantly increased in recent years. As with many other businesses, we have experienced, and are continually at risk of being subject to, attacks and incidents. Due to the increased risk of these types of attacks and incidents, we expend significant resources on information technology and data security tools, measures, and processes designed to protect our information technology systems, as well as the personal, confidential, or sensitive information stored on or transmitted through those systems, and to ensure an effective response to any cyber-attack or data security incident. Whether or not these measures are ultimately successful, these
43