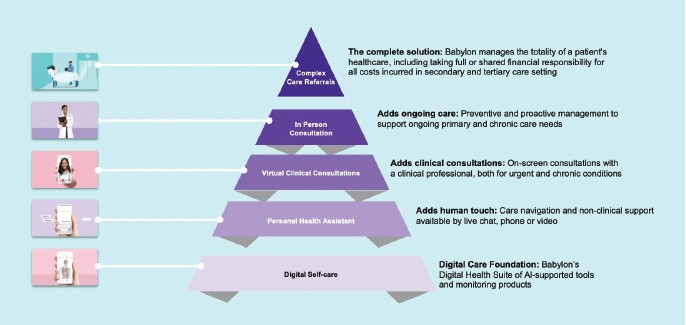
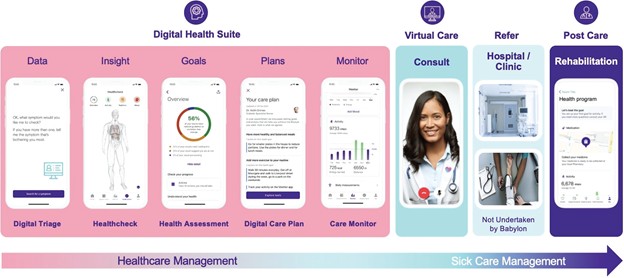
Risks Related to Information Technology and Data
Cyberattacks, security breaches and incidents, and other disruptions have compromised and could in the future compromise sensitive information related to our business or members, or prevent us from accessing critical information or from serving customers and expose us to liability, which could adversely affect our business and our reputation.
In the ordinary course of our business, we collect, store, use and disclose sensitive data, including protected health information (“PHI”), and other types of personal data (as defined in the GDPR and the United Kingdom’s implementation of the GDPR (“UK GDPR”) or personally identifiable information (“PII”). We also process and store, and use additional third party service providers to process and store sensitive information including intellectual property and other proprietary business information, including that of our members and customers (collectively, together with PHI and PII, “Confidential Data”). We manage and maintain our platform and Confidential Data utilizing a combination of on-site systems, managed data center systems and cloud-based computing center systems.
We are highly dependent on information technology infrastructure, networks and systems, including the internet and various hardware and software systems such as cloud technologies (collectively, “IT Systems”), to securely process, transmit and store Confidential Data and to conduct many other critical internal and external operations. Cyberattacks and security breaches involving our IT Systems, including physical or electronic break-ins, computer viruses, attacks by hackers and similar breaches, employee or contractor error, negligence or malfeasance, and bugs, misconfigurations or other vulnerabilities can create system disruptions, shutdowns or unauthorized disclosure or modifications of Confidential Data, causing for example, member health information to be accessed or acquired without authorization or to become publicly available. We utilize third-party service providers for important aspects of the collection, storage, transmission and security of Confidential Data, and therefore rely on third parties to manage functions that have material cybersecurity risks. Because of the sensitivity of Confidential Data that we and our service providers collect, store, transmit, and otherwise process, the security of our IT Systems and other aspects of our services, including those provided or facilitated by our third-party service providers, is critically important to our operations and business strategy. We take certain administrative, physical and technological measures in response to these risks, such as by conducting privacy and security impact assessments, and seeking contractual security commitments from service providers who handle Confidential Data.
We have experienced cyber and other security incidents in the past and continue to experience them from time to time. Despite protective measures taken by us and by third-party service providers, our IT Systems and Confidential Data are and remain vulnerable to cyberattacks and cybersecurity risks posed by hackers or viruses, failures or breaches due to third-party action, employee negligence or error, malfeasance or other disruptions (for example, due to ransomware), bugs, misconfigurations, or other hardware or software vulnerabilities, including supply chain related vulnerabilities and failures during the process of upgrading or replacing software, databases or components thereof, and a host of other cybersecurity threats. We expect the frequency and impact of cyberattacks to accelerate as threat actors are becoming increasingly sophisticated, for example, in using tactics and techniques designed to circumvent security controls, avoid detection, and obfuscate forensic evidence, such that we may be unable to timely or effectively detect, identify, investigate or remediate attacks in the future.
A cyberattack, security breach or incident, or other privacy or data protection violation, that leads to disclosure or unauthorized use, modification of, or other processing, or that prevents access to or otherwise impacts the confidentiality, security, availability or integrity of Confidential Data that we or our subcontractors maintain or otherwise process, could harm our reputation, compel us to comply with breach notification laws, cause us to incur significant costs for remediation, fines, penalties, notification to individuals and for measures intended to repair or replace systems or technology and to prevent future occurrences, potential increases in insurance premiums, and require us to verify the accuracy of database contents or be subject to audits from regulators or customers, resulting in increased costs and loss of revenue. If we are unable to prevent such security breaches or privacy violations or implement satisfactory remedial measures, or if it is perceived that we have been unable to do so, our operations could be disrupted, we may be unable to provide access to our platform, and we could suffer a loss of customers or users or a decrease in the use of our platform, and we may suffer loss of reputation, harm to our market position, adverse impacts on customer, user and investor confidence, financial loss, governmental investigations, litigation or other actions, regulatory or contractual penalties, and other claims and liability. In addition, security breaches and incidents and other unauthorized access to, or acquisition or processing of, Confidential Data can be difficult to detect, and any delay in identifying such incident, mitigating and otherwise responding to any incidents, or in providing any notification of such incidents may lead to increased liability and impact to operations.
Any such breach or incident, or disruption to or interruption of our systems or any of our third-party information technology partners, could compromise our networks or data security processes, disrupt our operations, and sensitive information could be destroyed, corrupted, or inaccessible or could be accessed, obtained, or disclosed by unauthorized parties, publicly disclosed, lost or