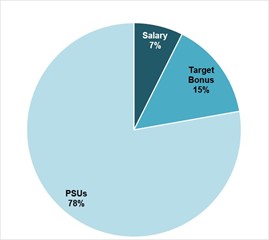
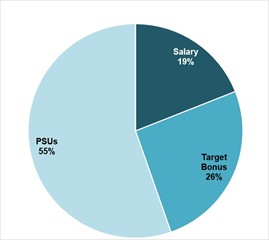
Risks Relating to Cybersecurity and Data Privacy
Cybersecurity and privacy considerations could adversely impact our business.
We maintain information, including confidential and proprietary information, in digital form regarding our business and information of our customers, contractors, business partners, vendors, employees, competitors and other third parties. We also rely on third-party vendors to provide certain digital services in connection with our business. There are numerous and evolving risks to our cybersecurity and privacy, including risks originating from intentional acts of criminal hackers, hacktivists and nation states; from intentional and unintentional acts of customers, contractors, business partners, vendors, employees, competitors and other third parties; and from errors in processes or technologies, as well as the risks associated with an increase in the number of customers, contractors, business partners, vendors, employees and other third parties working remotely as a result of the COVID-19 pandemic. Computer hackers and others routinely attack the security of technology products, services, systems and networks using a wide variety of methods, including ransomware or other malicious software and attempts to exploit vulnerabilities in hardware, software, and infrastructure. Attacks also include social engineering to fraudulently induce customers, contractors, business partners, vendors, employees and other third parties to disclose information, transfer funds or unwittingly provide access to systems or data. We are at risk of security breaches not only of our own services, systems and networks, but also those of customers, contractors, business partners, vendors, employees and other third parties.
Cyber threats are continually evolving, making it difficult to defend against certain threats and vulnerabilities that can persist undetected over extended periods of time. Our services, systems and networks, including cloud-based systems and systems and technologies that we maintain on behalf of our customers, may be used in critical Company, customer or third-party operations, and involve the storage, processing and transmission of sensitive data, including valuable intellectual property, other proprietary or confidential data, regulated data, and personal information of employees, customers and others. These services, systems and networks are also used by customers in heavily regulated industries, including those in the financial services, healthcare, critical infrastructure and government sectors. Successful cybersecurity attacks or other security incidents with respect to our systems or those of our third-party vendors could result in, for example, one or more of the following: unauthorized access to, disclosure, modification, misuse, loss or destruction of Company, customer or other third-party data or systems; theft or import or export of sensitive, regulated or confidential data including personal information and intellectual property; the loss of access to critical data or systems through ransomware, crypto mining, destructive attacks or other means; and business delays, service or system disruptions or denials of service. In the event of such actions, we, our customers and other third parties could be exposed to liability, litigation, and regulatory or other government action, as well as the loss of existing or potential customers, damage to brand and reputation, damage to our competitive position, and other financial loss.
The cost and operational consequences of responding to cybersecurity incidents and implementing remediation measures could be significant. In our industry, security vulnerabilities are increasingly discovered, publicized and exploited across a broad range of hardware, software or other infrastructure, elevating the risk of attacks and the potential cost of response and remediation for us and our customers. In addition, the fast-paced, evolving, pervasive, and sophisticated nature of certain cyber threats and vulnerabilities, as well as the scale and complexity of the business and infrastructure, make it possible that certain threats or vulnerabilities will be undetected or unmitigated in time to prevent or minimize the impact of an attack on us or our customers. Cybersecurity risk to us and our customers also depends on factors such as the actions, practices and investments of customers, contractors, business partners, vendors and other third parties. Cybersecurity attacks or other catastrophic events resulting in disruptions to or failures in power, information technology, communication systems or other critical infrastructure could result in interruptions or delays to Company, customer or other third-party operations or services, financial loss, injury or death to persons or property, potential liability, and damage to brand and reputation. Although we continuously take significant steps to mitigate cybersecurity risk across a range of functions, such measures can never eliminate the risk entirely or provide absolute security. To date, while we continue to monitor for, identify, investigate, respond to, remediate and develop plans to quickly recover from cybersecurity incidents, there have not been cybersecurity incidents that have had a material adverse effect on us, though there is no assurance that there will not be cybersecurity incidents that will have a material adverse effect in the future.
As we are a global enterprise, the regulatory environment with regard to cybersecurity, privacy and data protection issues to which we are subject is increasingly complex and will continue to impact our business, including through increased risk, increased costs, and expanded or otherwise altered compliance obligations. As our reliance on data grows, the potential impact of regulations on our business, risks, and reputation will grow accordingly. The enactment and expansion of data protection and privacy laws and regulations around the globe, including an increased focus on international data transfer mechanisms driven by the European Court of Justice decision in the Schrems II matter; the lack of harmonization of such laws and regulations; the increase in associated litigation