obligations, resulting in a diversion of our time and resources and, potentially, damages. In addition, job candidates and existing employees often consider the value of the share awards they receive in connection with their employment. If the perceived value of our share awards declines, either because we are a public company or otherwise, it may harm our ability to recruit and retain highly skilled employees. Additionally, maintaining a positive company culture is necessary to enable us to retain and hire key talent and have a cohesive, aligned employee base. Our ability to maintain this culture will directly affect the continued growth and success of our company. Our culture could face sustainability challenges as we continue to grow and scale our business. Potential obstacles include reduced adoption of our culture by new employees, limited ability to maintain consistency of culture within business teams, and failure to attract and retain leaders who support our culture and business plans. If we fail to attract new personnel or fail to retain and motivate our current personnel, our business, financial condition, results of operations and prospects could be materially adversely affected.
Security breaches, loss of data, unauthorized uses or disclosures, and other disruptions involving our systems, products or data could compromise sensitive information related to our business or patients, result in operational disruption, or prevent us from accessing critical information, exposing us to liability, and adversely affecting our business, financial condition, results of operation and prospects.
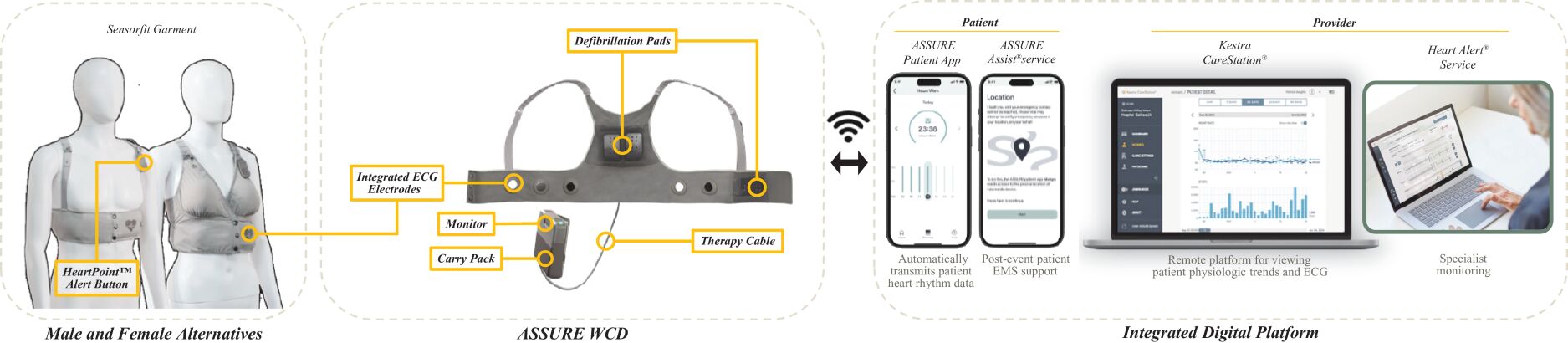
In the ordinary course of our business, we, and certain of our vendors on our behalf, collect, transfer, process and store sensitive data, including legally-protected personally identifiable health information about patients. We also collect, transfer, process and store, and use additional third parties to collect, transfer, process and store on our behalf, sensitive confidential information, including intellectual property, other proprietary business information, and preclinical and clinical trial data, including that of our customers, payors and collaborative partners. We employ administrative, technical and physical controls to secure personally identifiable health information, and we maintain our applications and data utilizing a combination of public cloud platforms and software-as-a-service providers. These applications and data encompass a wide variety of critical information, including patient data collected and processed through the digital solutions and services offered as part of our Cardiac Recovery System platform, clinical evidence collected through our ASSURE Patient Registry, other research and development information, commercial information and business and financial information.
We are highly dependent on information technology networks and systems, including the internet, to securely process, transmit and store this critical information to ensure the effective operation of our business and the timely delivery of our solutions and services. For example, we rely on information technology networks to ensure that our digital solutions, such as our Heart Alert Services and ASSURE Assist services, are able to deliver timely critical alerts to healthcare providers and notify emergency services when therapy is administered to patients. Our third-party information technology systems may not remain available on terms acceptable to us and may require replacement, which could result in substantial operational expense, diversion of our resources, and reduced efficiency, any of which could result in any a material adverse effect on our business, financial condition, results of operations and prospects. Security breaches of our information technology infrastructure, including physical or electronic break-ins, computer viruses, attacks by hackers and similar breaches, can create system disruptions, shutdowns or unauthorized disclosure, access, use or modifications of confidential information, including patient information and trade secrets. The secure collection, use, processing, storage, maintenance, protection and transmission of this critical information are vital to our operations and business strategy, and we devote significant resources to protecting such information. Data security-related incidents and fraudulent activity are increasing in frequency, sophistication, and variety, and can originate from many sources, including third-party suppliers and nation-state actors. Our information technology and infrastructure, and those of our vendors, has been and will continue to be vulnerable to attacks by hackers or viruses or breaches due to employee error, malfeasance or other disruptions. While we have taken steps to identify critical and high-risk vulnerabilities to and protect our infrastructure and sensitive information from unauthorized access, disclosure, or other activity, and while we have implemented compliance measures along those lines, we continue to develop our policies and procedures for protecting such information, and there can be no assurance that these will prevent, detect, or mitigate such issues given the unpredictability of the timing, nature, and scope of data
46