Exhibit 99.1

HUB Security Investor s Presentation March 2023

Disclaimer Page 2 This investor presentation (this “Presentation”) is for informational purposes only to assist interested parties in making their own evaluation with respect to HUB Cyber Security Ltd . (the “Company” or “Hub”) and for no other purpose . This Presentation does not constitute a offer to sell, a solicitation of an offer to buy, or a recommendation to purchase, any securities in any jurisdiction of the Company or any of its affiliates , (ii) a consent or authorization of any sale, issuance or transfer of any securities in any jurisdiction where, or to any person to whom, such offer, solicitation or sale may be unlawful under the laws of such jurisdiction or ( ii i ) a recommendation or advice regarding any securities in any jurisdiction . You should not construe the contents of this Presentation, or any prior or subsequent communications from or with the Company or i t s affiliates or representatives, as legal, tax, accounting or investment advice or a recommendation . You should consult your own counsel and tax and financial advisors as to legal and related matters concerning the matters described herein, and, by accepting this Presentation, you confirm that you are not relying upon the information contained herein to make any decision . The distribution of this Presentation may also be restricted by law and persons into whose possession this Presentation comes should inform themselves about and observe any such restrictions . The recipient acknowledges that it is ( i ) aware that the United States securities laws prohibit any person who has material, non - public information concerning a company from purchasing or selling securities of such company or from communicating such information to any other person under circumstances in which it is reasonably foreseeable that such person is likely to purchase or sell such securities, and (ii) familiar with the Securities Exchange Act of 1934 , as am ended, and the rules and regulations promulgated thereunder (collectively, the “Exchange Act”), and that the recipient will neither use, nor cause any third party to use, this Presentation or any information contained herein in contravention of the Exchange Act, including, without limitation, Rule 10 b - 5 thereunder . None of the Company or its subsidiaries, shareholders , affiliates, representatives, partners, directors, officers, employees, advisers or agents makes any representation or warranty, express or implied, as to the accuracy, completeness or reliability of the information contained in this Presentation . To the fullest extent permitted by law, in no circumstances will the Company or any of its subsidiaries, shareholders , affiliates, representatives, partners, directors, officers, employees, advisers or agents be responsible or liable for any direct, indirect or consequential loss or loss of profit arising from the use of this Presentation, its contents (including the internal economic models), its omissions, reliance on the information contained within it, or on opinions communicated in relation thereto or otherwise arising in connection therewith . The information contained herein does not purport to be all - inclusive or to contain all of the information that may be required to make a full analysis of the Company . Recipients of this Presentation should each make their own evaluation of the Company and of the relevance and adequacy of the information and should make such other investigations as they deem necessary . Forward - Looking Statements This Presentation contains forward - looking statements for purposes of the safe harbor provisions under the United States Private Securities Litigation Reform Act of 1995 , including statements about the anticipated benefits of the transaction, and the financial condition, results of operations, earnings outlook and prospects of the combined company . Forward - looking statements are typically identified by words such as "plan," "believe," "expect," "anticipate," "intend," "outlook," "estimate," "future," "forecast," "project," "continue," "could," "may," "might," "possible," "potential," "predict," "seem," "should," "will," "would" and other similar words and expressions, but the absence of these words does not mean that a statement is not forward - looking . The forward - looking statements are based on the current expectations of the management of HUB, as applicable, and are inherently subject to uncertainties and changes in circumstances and their potential effects and speak only as of the date of such statement . There can be no assurance that future developments will be those that have been anticipated . These forward - looking statements involve a number of risks, uncertainties or other assumptions that may cause actual results or performance to be materially different from those expressed or implied by these forward - looking statements . These risks and uncertainties include, but are not limited to, those discussed and identified in public filings made with the SEC by the HUB and the following : ( i ) expectations regarding HUB's strategies and future financial performance, including its future business plans or objectives, prospective performance and opportunities and competitors, revenues, products and services, pricing, operating expenses, market trends, liquidity, cash flows and uses of cash, capital expenditures, and HUB's ability to invest in growth initiatives and pursue acquisition opportunities ; (ii) the outcome of any legal proceedings that may be instituted against the combined company ; (iii) the ability to meet stock exchange continued listing standards ; (iv) the risk that the consummation of the business combination disrupts HUB's current operations and future plans ; (v) the ability to recognize the anticipated benefits of the transaction, which may be affected by, among other things, competition, the ability of HUB to grow and manage growth profitably, maintain relationships with customers and suppliers and retain its management and key employees ; (vi) costs related to the transaction ; (vii) limited liquidity and trading of HUB’s securities ; (viii) geopolitical risk, including military action and related sanctions, and changes in applicable laws or regulations ; (ix) the possibility that HUB may be adversely affected by other economic, business, and/or competitive factors ; (x) inaccuracies for any reason in the estimates of expenses and profitability and projected financial information for HUB ; and (xi) other risks and uncertainties set forth in the section entitled "Risk Factors" and "Cautionary Note Regarding Forward - Looking Statements" in HUB’s final proxy statement/prospectus filed on December 5 , 2022 . Should one or more of these risks or uncertainties materialize or should any of the assumptions made by the management of HUB prove incorrect, actual results may vary in material respects from those expressed or implied in these forward - looking statements . All subsequent written and oral forward - looking statements addressed in this Presentation and attributable to HUB or any person acting on their behalf are expressly qualified in their entirety by the cautionary statements contained or referred to in this Presentation . Except to the extent required by applicable law or regulation, HUB undertakes no obligation to update these forward - looking statements to reflect events or circumstances after the date of this Presentation to reflect the occurrence of unanticipated events . Industry and Market Data The information, data and statistics contained in this Presentation are derived from various internal (including data that the Company have internally collected) and external third - party sources . While the Company believes such third - party information is reliable, there ca n be no assurance as to the accuracy or completeness of the indicated information . The Company has not independently verified the accuracy or completeness of the information provided by third party sources . No representation is made, by the Company’s management, as to the reasonableness of the assumptions made within or the accuracy or completeness of any projections or modelling or any other information contained herein . Any information, data or statistics on past performance or modelling contained herein is not an indication as to future performance . The Company assumes no obligation to update the information in this Presentation . Trademarks The Company owns or have rights to various trademarks, service marks and trade names that it uses in connection with the operation of its business . This Presentation may also contain trademarks, service marks, trade names and copyrights of third - parties, which are the property of their respective owners . The use or display of third - parties’ trademarks, service marks, trade names or products in this presentation is not intended to, and does not imply, a relationship with the Company, or an endorsement or sponsorship by or of the Company . Solely for convenience, the trademarks, service marks, trade names and copyrights referred to in this presentation may appear without the TM, SM, ®or ©symbols, but such references are not intended to indicate in any way that the Company will not assert to the fullest extent under applicable law their respective rights or the rights of the applicable licensor(s) to these trademarks, service marks, trade names and copyrights .

In this session Opening Introducing HUB 1. What we do? 2. The market opportunity 3. Our products 4. The business model 5. Why Nasdaq? 6. Our Investor Relations (IR) strategy

Opening The purpose of this session is to engage with our new investors on Nasdaq post our move from the Tel Aviv Stock Exchange and introduce our company, strategy, products and technology. We intend to have a continues and open channel of communication and transparency with the investment community as our business develops and strategy unfolds.

Confidential computing allows data to remain encrypted even as it’s being processed and used in applications 5
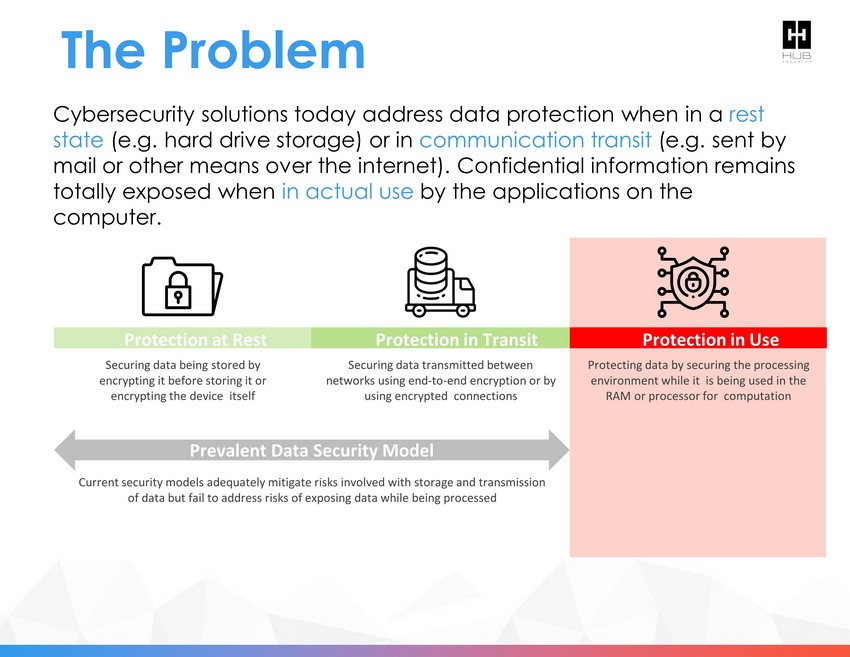
The Problem Prevalent Data Security Model Protection in Transit Protection at Rest Protection in Use Securing data being stored by encrypting it before storing it or encrypting the device itself Securing data transmitted between networks using end - to - end encryption or by using encrypted connections Protecting data by securing the processing environment while it is being used in the RAM or processor for computation Current security models adequately mitigate risks involved with storage and transmission of data but fail to address risks of exposing data while being processed C ybersecurity solutions today address data protection when in a rest state (e.g. hard drive storage) or in communication transit (e.g. sent by mail or other means over the internet). Confidential information remains totally exposed when in actual use by the applications on the computer.
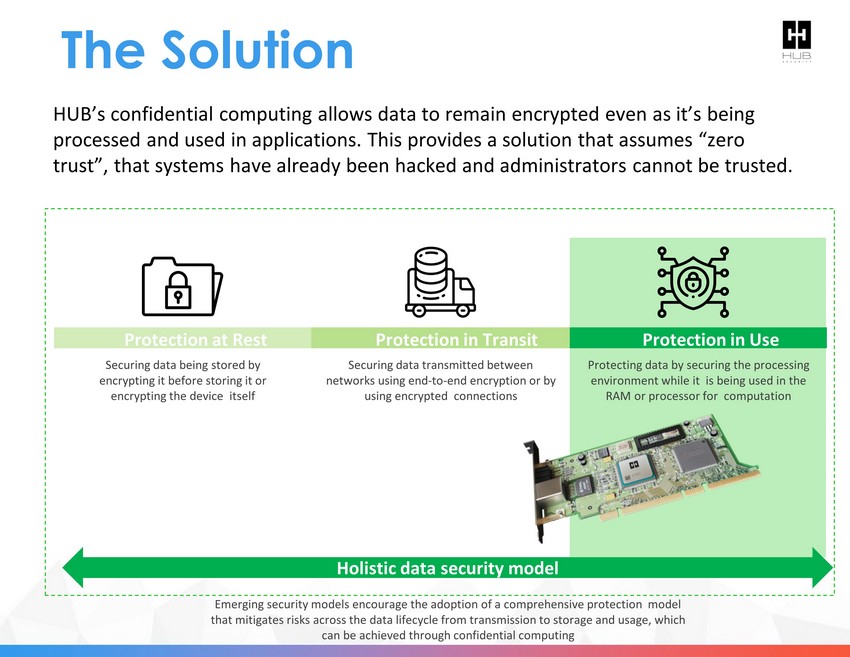
The Solution Protection in Transit Protection at Rest Protection in Use Securing data being stored by encrypting it before storing it or encrypting the device itself Securing data transmitted between networks using end - to - end encryption or by using encrypted connections Protecting data by securing the processing environment while it is being used in the RAM or processor for computation HUB’s confidential computing allows data to remain encrypted even as it’s being processed and used in applications. This provides a solution that assumes “zero trust”, that systems have already been hacked and administrators cannot be trusted. Holistic data security model Emerging security models encourage the adoption of a comprehensive protection model that mitigates ris k s across the data lifecycle from transmission to storage and usage, which can be achieved through confidential computing

7 Market Leadership confidentialcomputing.io Leading and accelerating Confidential Computing adoption via open collaboration between industry leaders, as members of the C onfidential C omputing consortium • Platform abstraction for Trusted Execution Environments (TEEs) enabling creating and running “ private, fungible, serverless ” applications Consortium projects • Open - source framework that allows developers to build Trusted Execution Environment (TEE) applications using a single enclaving abstraction • Open - source project for building trusted execution environments (TEE) with secure hardware enclaves, based on the RISC - V architecture Page 8
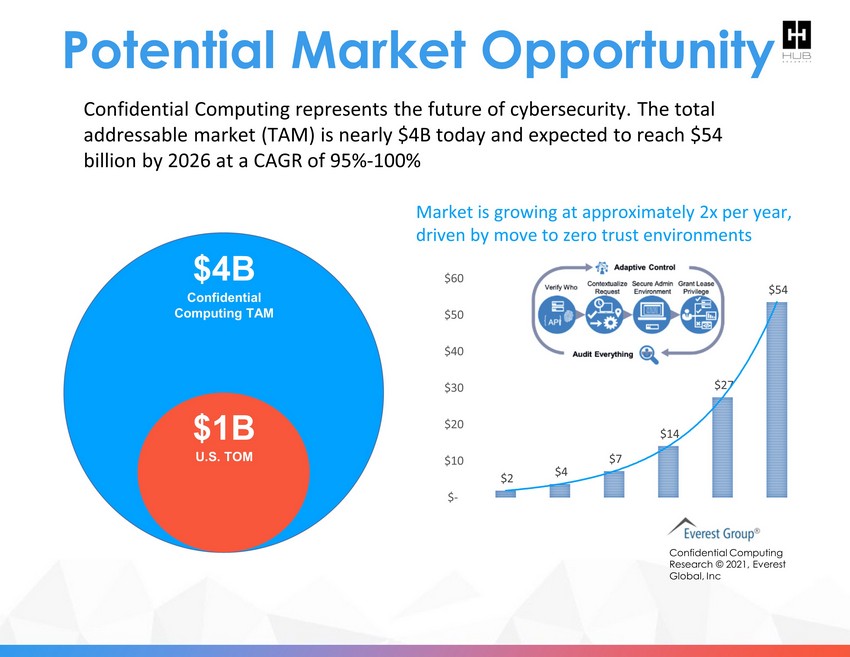
Confidential Computing represents the future of cybersecurity. The total addressable market (TAM) is nearly $4B today and expected to reach $54 billion by 2026 at a CAGR of 95% - 100% Confidential Computing Research © 2021, Everest Global, Inc $ 2 $ 4 $7 $14 $27 $54 $- $10 $20 $30 $40 $50 $60 $4B Confidential Computing TAM $1B U.S. TOM Market is growing at approximately 2 x per year, driven by move to zero trust environments Potential Market Opportunity
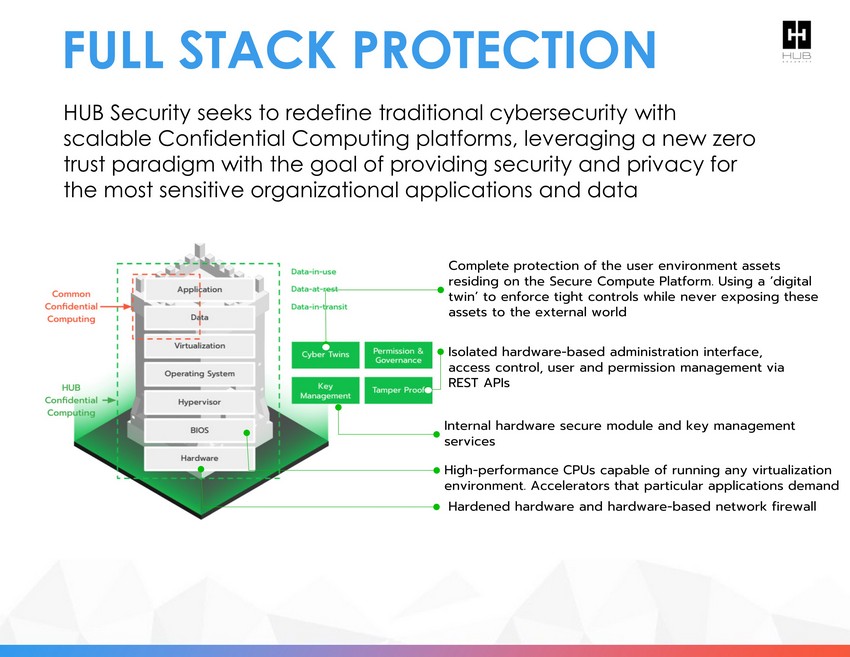
FULL STACK PROTECTION Complete protection of the user environment assets residing on the Secure Compute Platform. Using a ‘digital twin’ to enforce tight controls while never exposing these assets to the external world Hardened hardware and hardware - based network firewall Isolated hardware - based administration interface, access control, user and permission management via REST APIs Internal hardware secure module and key management services High - performance CPUs capable of running any virtualization environment. Accelerators that particular applications demand HUB Security seeks to redefine traditional cybersecurity with scalable Confidential C omputing platforms, leveraging a new zero trust paradigm with the goal of providing security and privacy for the most sensitive organizational applications and data

Confidential Compute Services Professional Services Annual subscription of Confidential Computing Services. Recurring revenues subscription model(with possible one - time CAPEX charge for on - premise solutions): Cyber security related services to support the Confidential Computing business including: • Security Assessments • System Integration • Security Training • Red Teams • Penetration Testing 01 02 Business Model
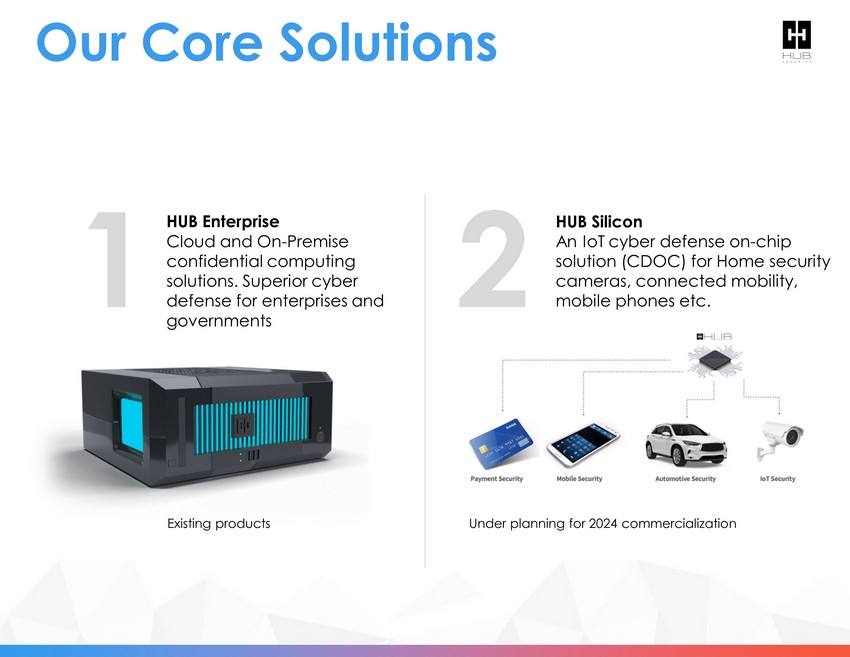
Our Core Solutions 2 1 HUB Enterprise Cloud and On - Premise confidential computing solutions. Superior cyber defense for enterprises and governments HUB Silicon An IoT cyber defense on - chip solution (CDOC) for Home security cameras, connected mobility, mobile phones etc. Existing products Under planning for 2024 commercialization

Product Portfolio 48 U Powerhouse Enterprise Server Rack Unit 1 U, 2 U & 4 U Enterprise Server Module PCI Card Module For integration with Edge Computing and Distributed AI - computing hubs HUB Silicon For IoT devices (Roadmap)

And many others Routes to market • Channel sales via VARs • Direct sales for the intelligence sensitive government projects • Direct sales for cutting - edge technology pilots with governments and global enterprises Primary target sectors • Banking • Insurance • Healthcare • Telecom • Governments HUB ’ Professional Services arm has a recognizable brand in the cyber security market and is a trusted partner to many of the world ’ s largest companies and agencies Professional Services Arm We intend to leverage these valuable clients for introductions of our novel Confidential Computing products

Why Nasdaq • We have migrated from the Tel Aviv Stock Exchange to Nasdaq to get more exposure to the U.S. cyber analysts and investment community • Our stock trading volumes already represent a massive increase from our trading on TASE • We target government and enterprise clients in the insurance and banking arena – most of which are U.S. based • We seek to provide our shareholders and potential investors with the credibility and transparency required of a Nasdaq listed company to promote better access to U.S. and global government and enterprise cyber tenders

HUB IR Strategy 1. Continuous engagement with institutional and retail investors 2. Full transparency on HUB’s business and future plans 3. Building company news - flow on Confidential Computing contracts and partnerships 4. Increasing company coverage by trade and market analysts 5. Ongoing non - deal roadshows and social engagement building retail and institutional investor awareness to our company and stock

Summary • HUB is a frontrunner in Confidential Computing cyber defense • Confidential Computing is a multibillion - dollar market growing at 95 % - 100 % CAGR • HUB believes that it is well positioned with its technology to potentially become a significant player in the Confidential Computing arena • We have the technology and the team to drive vision • HUB has become a publicly listed company in the U.S. traded on Nasdaq in order to attempt to leverage its advantage to grow its U.S. and global business • HUB plans to continue and host sessions such as this aimed to drive awareness to our business within the investment community

Thank you.

















