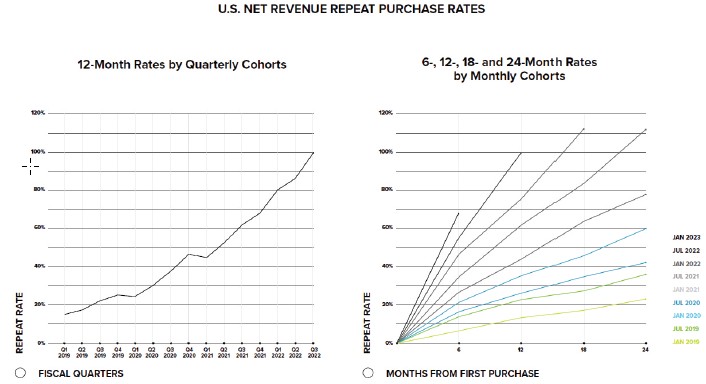
Like other e-commerce companies, we are also vulnerable to damage from fire, floods, hurricanes, earthquakes, natural disasters and other adverse weather conditions, public health emergencies (such as the COVID-19 pandemic) and other catastrophic events, military or political conflicts, power loss, terrorism, breaches, attacks by computer hackers, malicious code (such as malware, viruses and worms), ransomware attacks, insider threats, unauthorized activity or access, password-spraying, acts of vandalism, software or hardware vulnerabilities, employee or contractor theft, misplaced or lost data, fraud, misconduct or misuse, social engineering, phishing, denial-of-service attacks, organized cyberattacks, programming or human errors, telecommunication failures, or failures during the process of upgrading or replacing software, databases, or components. Cyberattacks could also result in the theft of our intellectual property, damage to our information technology systems, or disruption of our ability to make financial reports and other public disclosures required of public companies. Our service providers, vendors, and other partners are also subject to the foregoing risks, and we do not have any control over them.
We and our third-party service providers have been subject to attempted cyber, phishing, and social engineering attacks in the past and may continue to be subject to such attacks and other cybersecurity incidents in the future. If we gain greater visibility, we may face a higher risk of being targeted by cyberattacks that could result in a wide range of negative outcomes, including violations of applicable data privacy or security laws, rules, regulations, and standards, which can result in significant fines, governmental investigations or inquiries and enforcement actions, legal and financial exposure, contractual liability, and damage to our reputation, each of which could adversely affect our business, financial condition, and results of operations. Furthermore, the costs associated with the investigation, remediation, and potential notification of a data breach to counterparties and data subjects could be material, in addition to any payments required to resolve a ransomware attack. For example, laws in the EEA, the UK, and all 50 U.S. states may require businesses to notify regulators within specific timeframes that a breach affecting personal information has occurred and/or to provide notice to individuals whose personal information has been impacted as a result of such breach. Failure to comply with these numerous and complex regulations could subject us to regulatory scrutiny and additional liability.
Advances in computer capabilities, new technological discoveries, or other developments may result in cyberattacks becoming more sophisticated and more difficult to detect. We and our third-party service providers may not have the resources or technical sophistication to anticipate or prevent all such cyberattacks or other security or data breaches, to protect our systems, data, and customer information, or to prevent outages, data loss, and fraud, and the use of third parties for certain cybersecurity services may not provide sufficient security or be adequate for our operations. Techniques used to obtain unauthorized access to systems change frequently and may not be known until launched against us or our third-party service providers. Security breaches can also occur as a result of non-technical issues, including intentional or inadvertent actions by our employees, our third-party service providers, or their personnel. We may be required to invest significant resources in protecting against security breaches and other technological disruption, or to remediate problems and damages caused by such incidents, which could increase the cost of our business and in turn adversely affect our business, financial condition, and results of operations.
Ultimately, any actual or perceived failure to maintain the performance, reliability, security, and availability of our platform and technical infrastructure to the satisfaction of our customers and certain regulators could harm our reputation and result in loss of revenue from the adverse impact to our reputation and brand, disruption to our business, and our decreased ability to attract and retain customers.
We are subject to risks related to online transactions and payment methods.
We accept payments using a variety of methods, including credit card, debit card, Amazon Pay, PayPal, and APM. We rely on third parties to provide these payment methods and payment processing services. We are also subject to payment card association operating rules and certification requirements, including the PCI Standard and rules governing electronic funds transfers, which could change or be reinterpreted to make it difficult or impossible for us to comply.
Under certain circumstances specified in the payment card network rules, we may be required to submit to periodic audits, self-assessments, or other assessments of our compliance with the PCI Standard. Such activities may reveal that we have failed to comply with the PCI Standard. If an audit, self-assessment, or other test determines that we need to take steps to remediate any deficiencies, such remediation efforts may distract our management team and require us to undertake costly and time-consuming remediation efforts. In addition, even if we comply with the PCI Standard, there is no assurance that we will be protected from a security breach. If we fail to comply with the rules or requirements of any provider of a payment method we accept, if the volume of fraud in our transactions limits or terminates our rights to use payment methods we currently accept, or if a data breach occurs relating to our payment systems, we may, among other things, be subject to fines or higher transaction fees and may lose, or face restrictions placed upon, our ability to accept credit card and debit card payments from customers or to facilitate other types of online payments. If any of these events were to occur, our business, financial condition, and results of operations could be adversely affected.