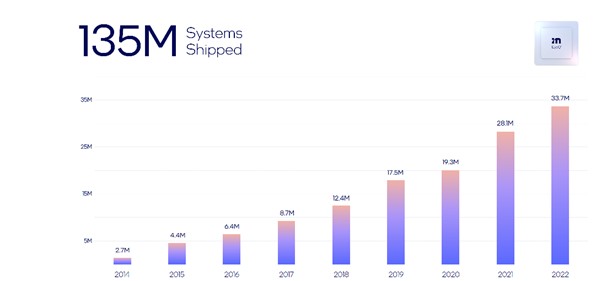
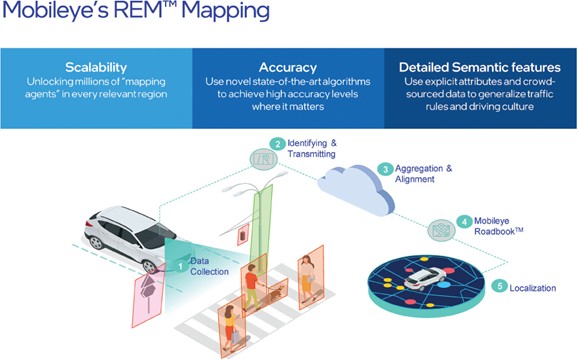
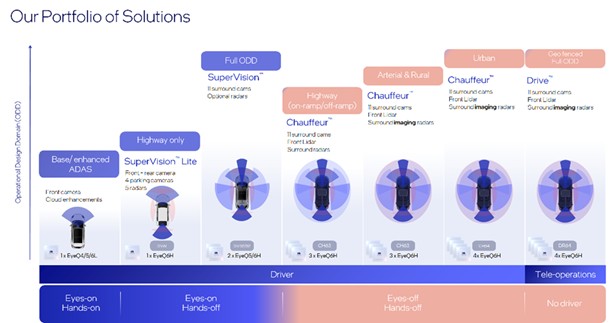
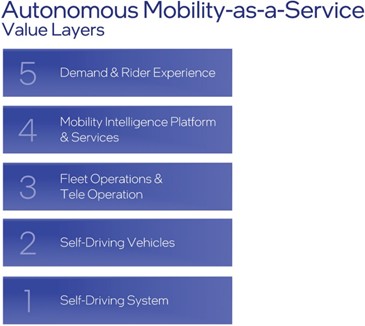
Given the continued and substantial economic uncertainty and volatility created by the pandemic, it is difficult to predict the nature and extent of impacts on demand for our solutions.
The degree to which COVID-19 impacts our results will depend on future developments, which are highly uncertain and cannot be predicted, including the duration and severity of the pandemic, the actions taken to contain the virus and its variants or treat their impact, other actions taken by governments, businesses, and individuals in response to the virus and resulting economic disruption, and how quickly and to what extent normal economic and operating conditions can resume. Additional impacts and risks may arise that we are not aware of or able to respond to effectively. We are similarly unable to predict the extent of the impact of the pandemic on our customers, suppliers, and other partners, but an adverse effect on these parties could also adversely affect us. The impact of COVID-19 can also exacerbate other risks discussed in this Risk Factors section and throughout this report.
We are a holding company.
We are a holding company. Accordingly, our ability to conduct our operations, service any debt that we may incur, and pay dividends, if any, is dependent upon the earnings from the business conducted by our subsidiaries. The distribution of those earnings or advances or other distributions of funds by our subsidiaries to us, as well as our receipt of such funds, are contingent upon the earnings of our subsidiaries and are subject to various business considerations and applicable law, including the laws of Israel. If our subsidiaries are unable to make sufficient distributions or advances to us, or if there are limitations on our ability to receive such distributions or advances, we may not have the cash resources necessary to conduct our corporate operations, which could adversely affect our business, results of operations, and financial condition.
Risks Related to Privacy, Data, and Cybersecurity
Interruptions to our information technology systems and networks and cybersecurity incidents could adversely affect our business, results of operations, and financial condition.
We collect and maintain information in digital form that is necessary to conduct our business, and we rely on information technology systems and networks (“IT systems”) to process, transmit, and store electronic information, and to manage or support our business and consumer facing activities. Our operations routinely involve receiving, storing, processing, and transmitting confidential or sensitive information pertaining to our business, customers, suppliers, employees, and other sensitive matters, including trade secrets, other proprietary business information, and personal information. Although we have established physical, logical, electronic, and organizational measures designed to safeguard and secure our systems to prevent a data breach or compromise, and to prevent damage to or downtime of our systems, and although we rely on commercially available systems, software, tools, and monitoring to provide security for our IT systems and the processing, transmission, and storage of digital information, we cannot guarantee that such measures will be adequate to detect, prevent, or mitigate cyber incidents. The implementation, maintenance, segregation, and improvement of these measures requires significant management time, support, and cost. Moreover, there are inherent risks associated with developing, improving, expanding, and updating current systems, including the disruption of our data management, procurement, production execution, finance, supply chain, and sales and service processes. These risks may affect our ability to manage our data and inventory, procure parts or supplies, or produce, sell, deliver, and service our solutions, adequately protect our intellectual property, or achieve and maintain compliance with, or realize available benefits under, applicable laws, regulations, and contracts.
We cannot be sure that the IT systems upon which we rely, including those of our third-party vendors or suppliers, will be effectively implemented, maintained, or expanded as planned. While cyberattacks against our third-party vendors or suppliers have not materially adversely affected us to date, future cyberattacks on such third parties may cause significant disruptions and materially adversely affect our business, results of operations, and financial condition. In addition, despite the implementation of preventative and detective security controls, such IT systems are vulnerable to damage, shutdown, or interruption from a variety of sources, including telecommunications or network failures or interruptions, system malfunction, natural disasters, terrorism, and war. Additionally, our IT systems and products may be vulnerable to malicious acts by hackers, including through use of computer viruses, malware (including ransomware), phishing attacks, or denial of service attacks.
We regularly face attempts by others to gain unauthorized access, or to introduce malicious software, to our IT systems. Individuals or organizations, including malicious hackers, state-sponsored organizations, insider threats, including employees and third-party service providers, or intruders into our physical facilities, at times may attempt to gain unauthorized access to or corrupt our IT systems, products, or services. Due to the widespread use of our solutions, we are a target for computer hackers and organizations that intend to