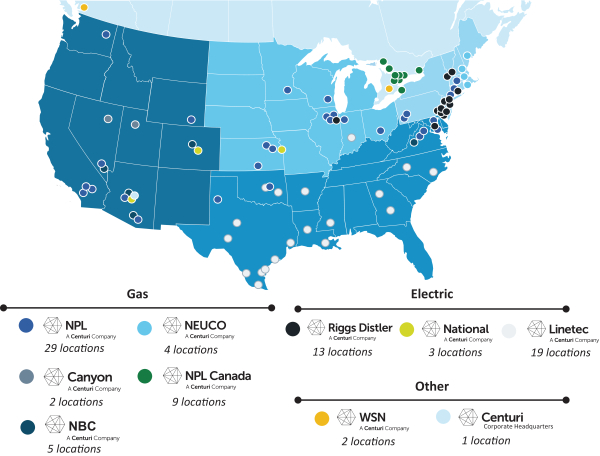
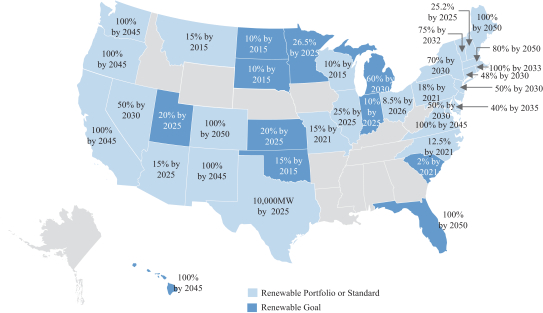
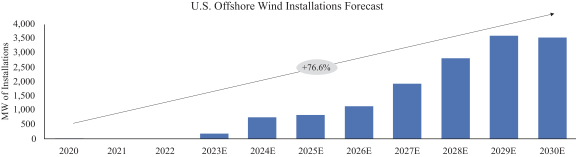
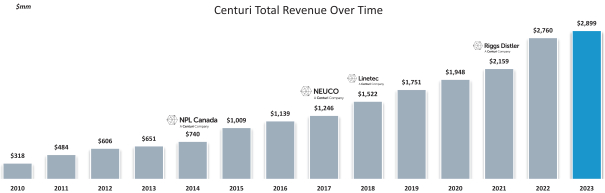
services. For example, a reduction in demand for natural gas or an increase in demand for renewable energy sources could negatively impact certain of our customers and reduce demand for certain of our services. Additionally, a transition to a decentralized electric power grid, which relies on more dispersed and smaller-scale renewable energy sources, could reduce the need for large infrastructure projects and significant maintenance and rehabilitation programs, thereby reducing demand for, or profitability of, our services. Our future success will depend, in part, on our ability to anticipate and adapt to these and other potential changes in a cost-effective manner and to offer services that meet customer demands and evolving industry standards. If we fail to do so or incur significant expenditures in adapting to such change, our businesses, financial condition, results of operations and cash flows could be materially and adversely affected.
Furthermore, we view our portfolio of energized services tools and techniques, as well as our other process and design technologies, as competitive strengths, which we believe differentiate our service offerings. If our work processes become obsolete, through technological advancements or otherwise, we may not be able to differentiate our service offerings and some of our competitors may be able to offer more attractive services to our customers, which could materially and adversely affect our business, financial condition, results of operations and cash flows.
Systems and information technology interruptions and/or data security breaches could materially and adversely affect our operating results and ability to operate, and could result in harm to our reputation.
We are heavily reliant on information and communications technology, computer and other related systems in order to operate. We also rely, in part, on third-party software and information technology to run certain of our critical accounting, project management and financial information systems. From time to time, we experience system interruptions and delays. In certain cases, our information technology systems are also integrated with those of our customers, which exposes us to the additional risk of a third-party breach of the customers’ systems outside of our control. Our operations could be interrupted or delayed, or our data security could be breached, if we are unable to deploy software and hardware, gain access to, or effectively maintain and upgrade, our systems and network infrastructure and/or take other steps to improve and otherwise protect our systems. In addition, our information technology and communications systems, including those associated with acquired businesses, and our operations could be damaged or interrupted by cyber attacks and/or physical security risks. These risks include natural disasters, power loss, telecommunications failures, intentional or inadvertent user misuse or error, failures of information technology solutions, computer viruses, phishing attacks, social engineering schemes, malicious code, ransomware attacks, acts of terrorism and physical or electronic security breaches, including breaches by computer hackers, cyber-terrorists and/or unauthorized access to, or disclosure of, our and/or our employees’ or customers’ data. Furthermore, such unauthorized access or cyber attacks could go unnoticed for some period of time.
These events, among others, could cause system interruptions, delays and/or the loss or release of critical or sensitive data, including the unintentional disclosure of customer, employee, or our information, and could delay or prevent operations, including the processing of transactions and reporting of financial results or cause processing inefficiency or downtime, all of which could have a material adverse effect on our business, results of operations and financial condition, and could materially harm our reputation and/or result in significant costs, fines or litigation. Similar risks could adversely affect our customers, subcontractors or suppliers, indirectly affecting us.
While we have security, internal control and technology measures in place to protect our systems and network, if these measures fail as a result of a cyber attack, other third-party action, employee error, malfeasance or other security failure, and someone obtains unauthorized access to our or our employees’ or customers’ information, our reputation could be damaged, our business may suffer and we could incur significant liability, or, in some cases, we may lose access to our business data or systems, incur significant remediation costs or be subject to demands to pay ransom. In the ordinary course of business, we have been targeted by malicious cyber attacks. Because the techniques used to obtain unauthorized access or sabotage systems change frequently and
29