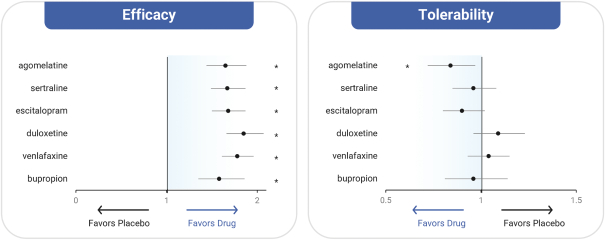
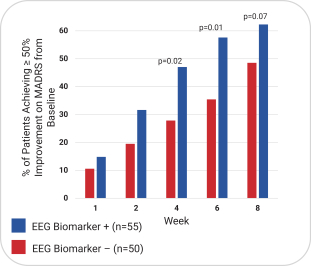
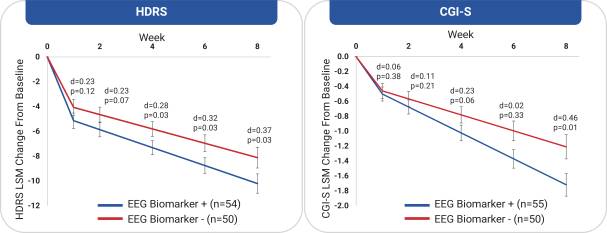
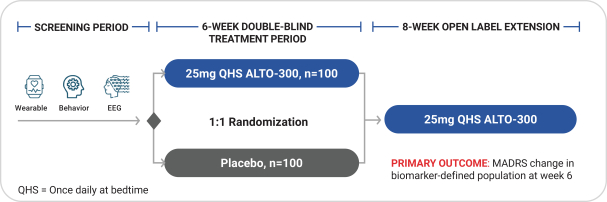
with the applicable FDA review team during product development and, once an NDA is submitted, the application may be eligible for priority review. An NDA submitted for a Fast Track product candidate may also be eligible for rolling review, where the FDA may consider for review sections of the NDA on a rolling basis before the complete application is submitted, if the sponsor provides a schedule for the submission of the sections of the NDA, the FDA agrees to accept sections of the NDA and determines that the schedule is acceptable, and the sponsor pays any required user fees upon submission of the first section of the application. The FDA has broad discretion whether or not to grant this designation, so even if we believe a particular product candidate is eligible for this designation, we cannot assure you that the FDA would decide to grant it. Even if we do receive Fast Track Designation for any of our product candidates, such product candidates may not experience a faster development process, review or approval compared to conventional FDA procedures. The FDA may also withdraw the Fast Track Designation if it believes that the designation is no longer supported by data from our clinical development program. Furthermore, such a designation does not increase the likelihood that any product candidate that may be granted Fast Track Designation will receive regulatory approval in the U.S. Many product candidates that have received Fast Track Designation have ultimately failed to obtain approval.
If our telecommunications or information technology systems, or those used by our collaborators, CROs, CMOs, clinical sites, third-party logistics providers, distributors, or other contractors, consultants, or third party service providers upon which we rely, are or were compromised, become unavailable, or suffer security breaches, loss, or leakage of data or other disruptions, we could suffer adverse consequences resulting from such compromise, including but not limited to, operational or service interruption, harm to our reputation, litigation, fines, penalties and liability, compromise of sensitive information related our business, and other adverse consequences.
In the ordinary course of our business, we, and the third parties upon which we rely, collect, receive, store, process, generate, use, transfer, disclose, make accessible, protect, secure, dispose of, transmit, and share (collectively, “process”) sensitive data and as a result, we and the third parties upon which we rely face a variety of evolving threats that could cause security incidents and other disruptions to such information technology systems. If any of our sensitive or proprietary data is compromised, including our Platform and our internal, proprietary systems for data collection, it may materially and adversely affect our ability to create and develop product candidates and identify biomarkers, and compete effectively.
Our Platform, our internal, proprietary systems for data collection, and our information technology systems and those of our collaborators, CROs, CMOs, clinical sites, third-party logistics providers, distributors, and other contractors and consultants upon which we rely are vulnerable to attack, damage, and interruption from cyberattacks, computer viruses, bugs, worms, or other malicious codes, malware (including ransomware, and as a result of advanced persistent threat intrusions), and other attacks by computer hackers, nation-state and nation-state-supported actors, cracking, application security attacks, social engineering (including through phishing attacks), supply chain attacks and vulnerabilities through our third-party service providers, denial- or degradation-of-service attacks (such as credential stuffing), credential harvesting, personnel misconduct or error, supply-chain attacks, software bugs, server malfunctions, software or hardware failures, loss of data or other information technology assets, adware, telecommunications or electrical failures, natural disasters (e.g., earthquakes, fires, and floods), terrorism, war, and other similar threats. Such systems could also be vulnerable to intentional or inadvertent acts or lack of action by those with authorized access to our systems that lead to exposure or exploitation of those systems.
Such threats are prevalent and continue to rise, are increasingly difficult to detect, and come from a variety of sources, including traditional computer “hackers,” threat actors, “hacktivists,” organized criminal threat actors, personnel (such as through theft or misuse), sophisticated nation states, and nation-state-supported actors. In particular, ransomware attacks, including those from organized criminal threat actors, nation-states, and nation-state supported actors, are becoming increasingly prevalent and severe and can lead to significant interruptions, delays, or outages in our operations, loss of data (including sensitive information), loss of income, significant extra expenses to restore data or systems, reputational loss, and the diversion of funds. To alleviate the negative
39