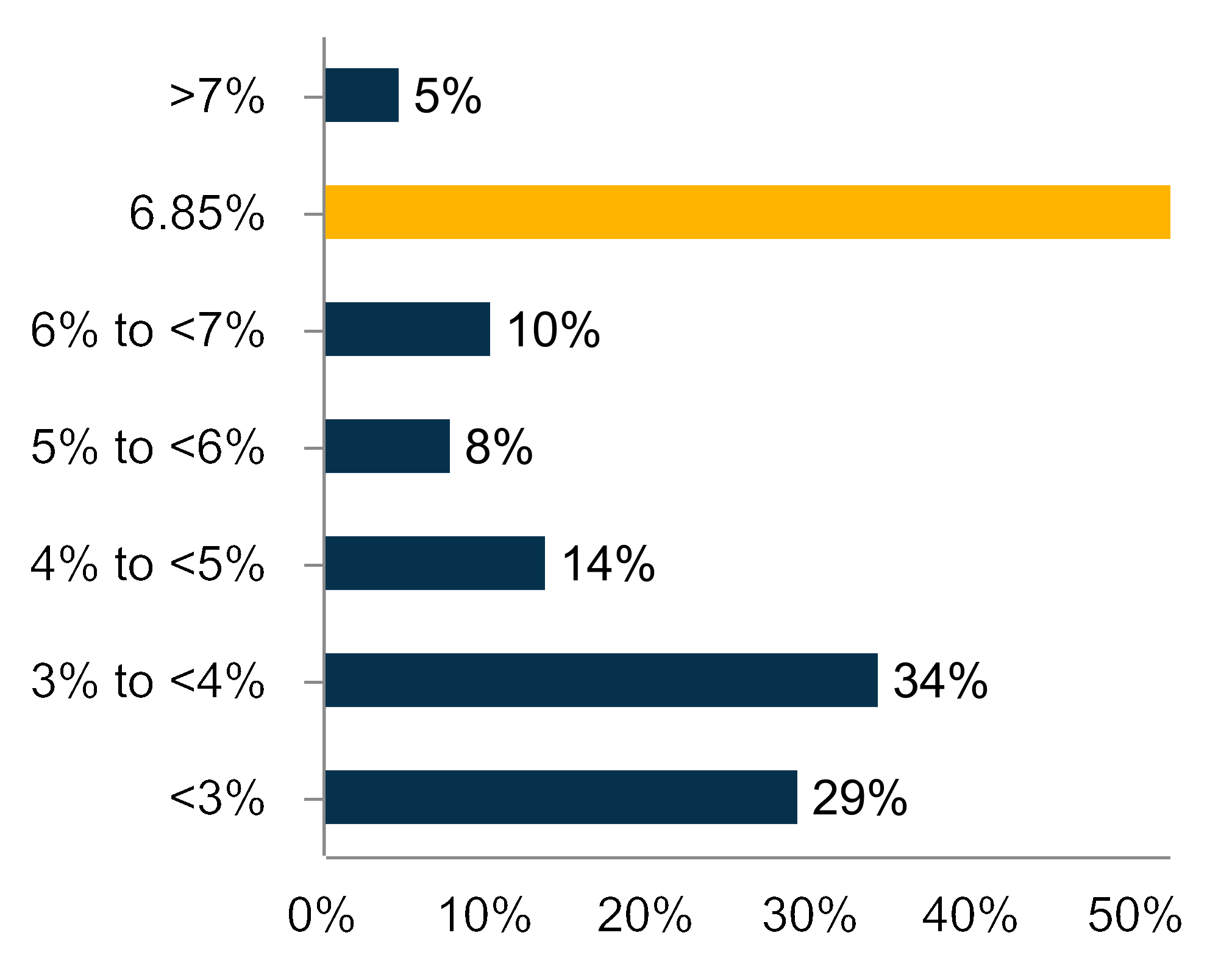
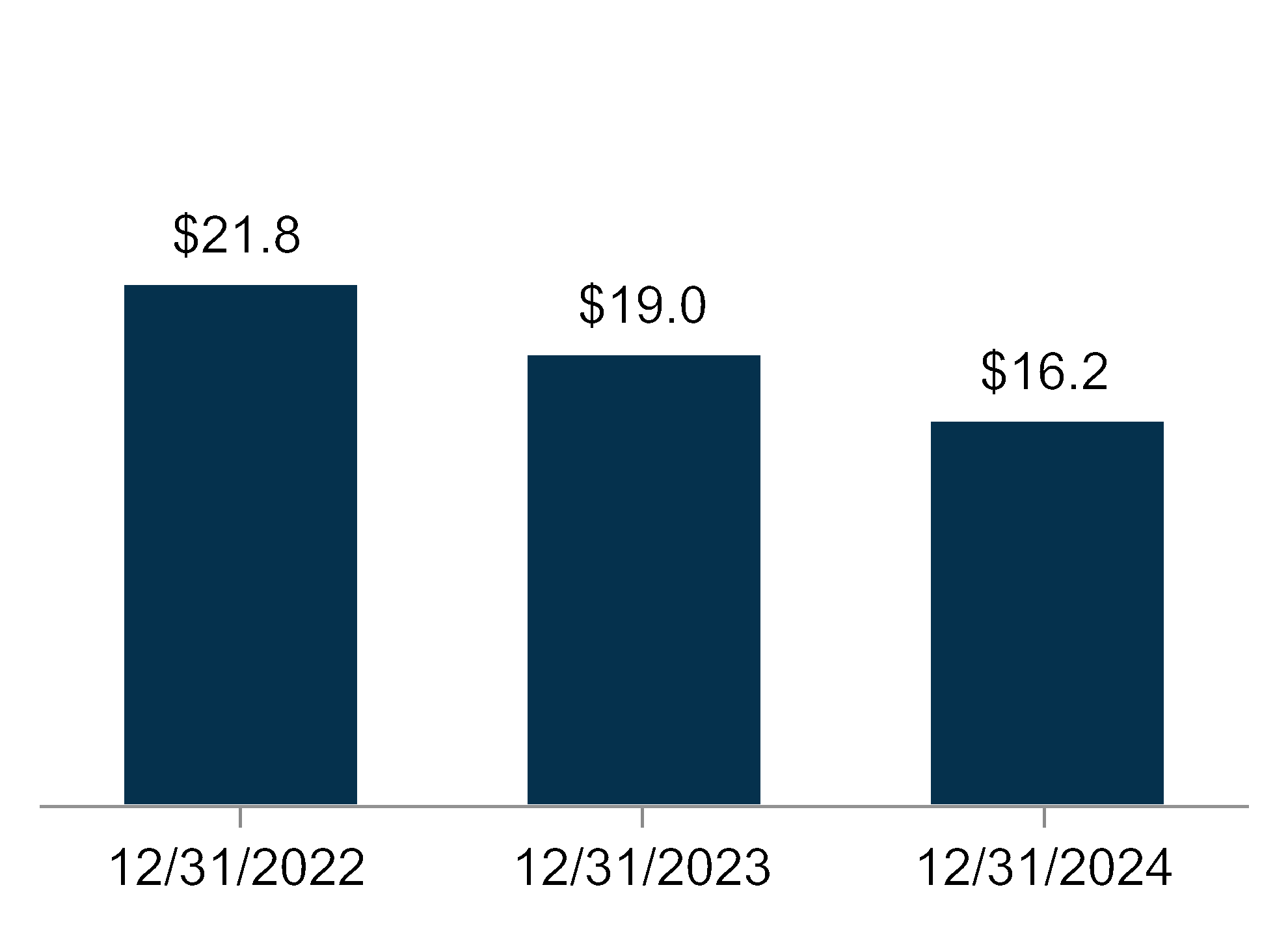
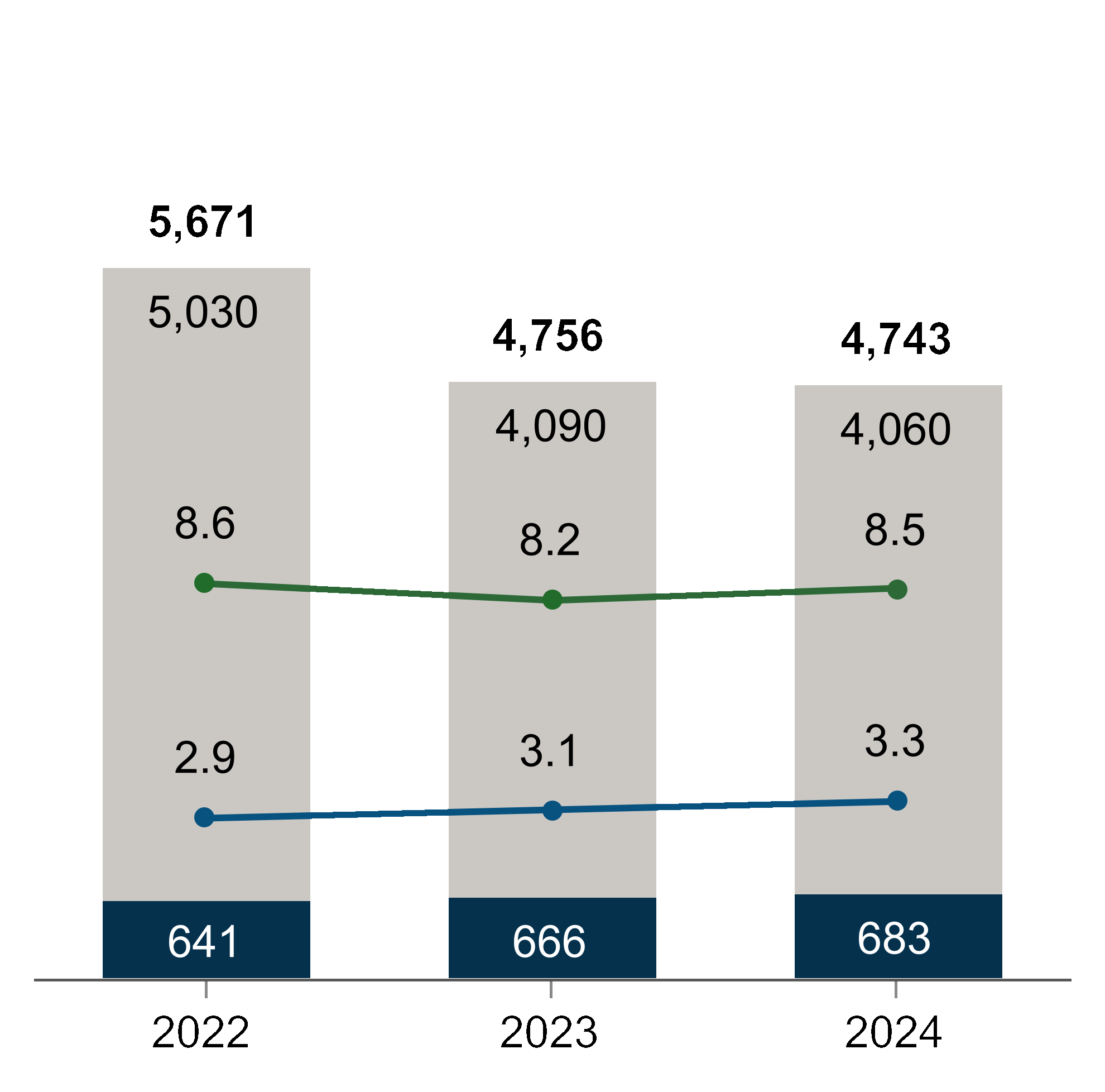
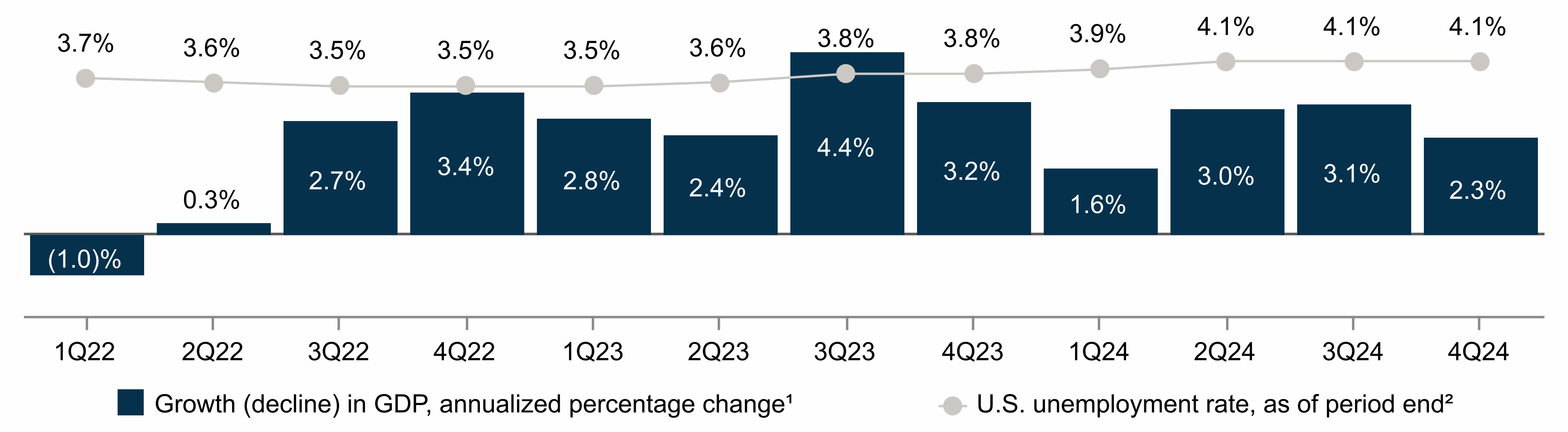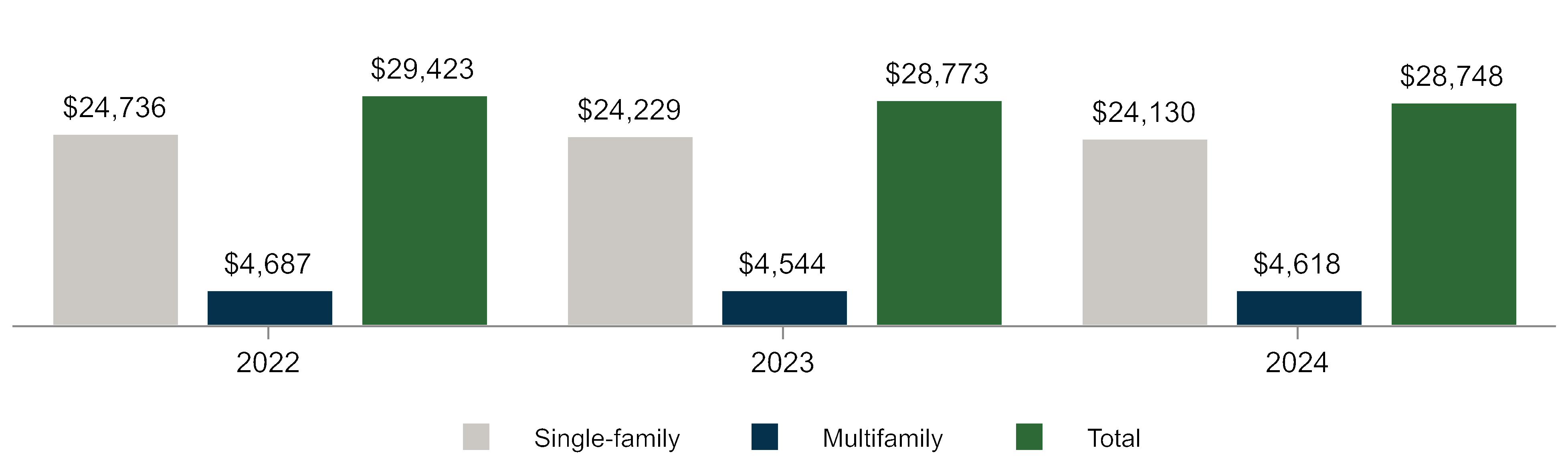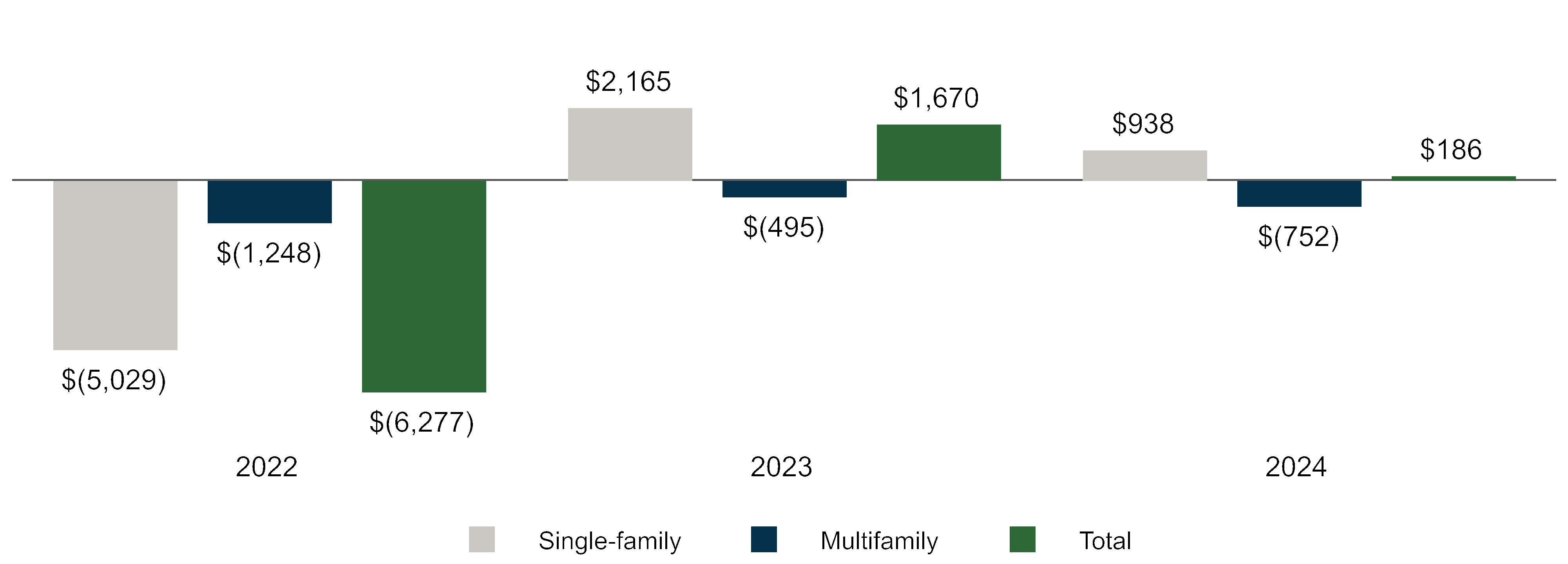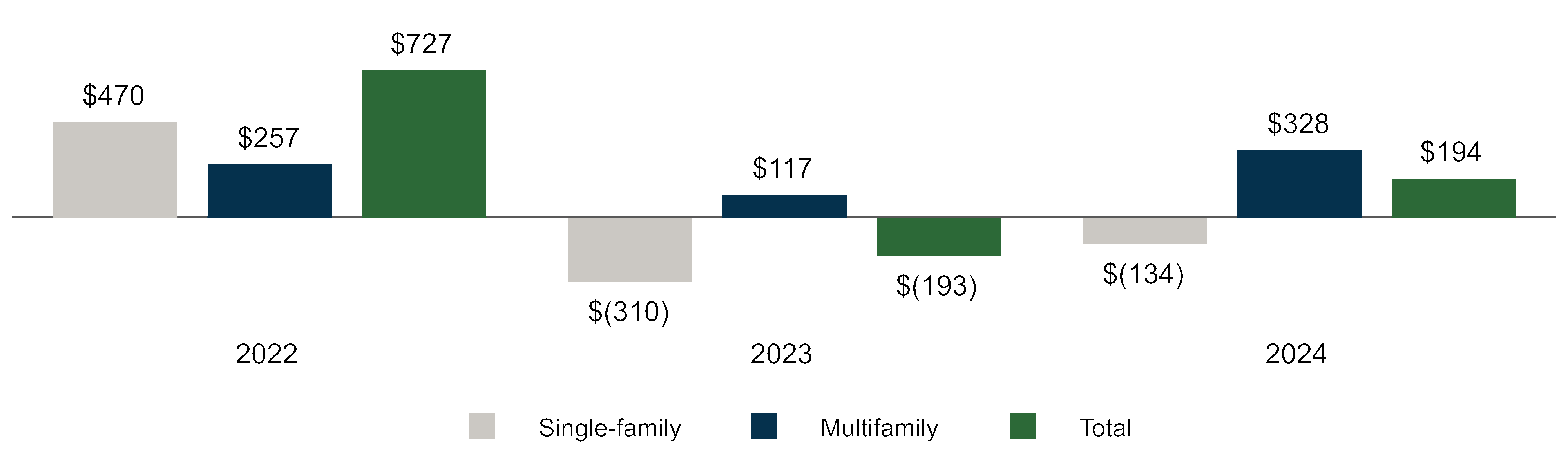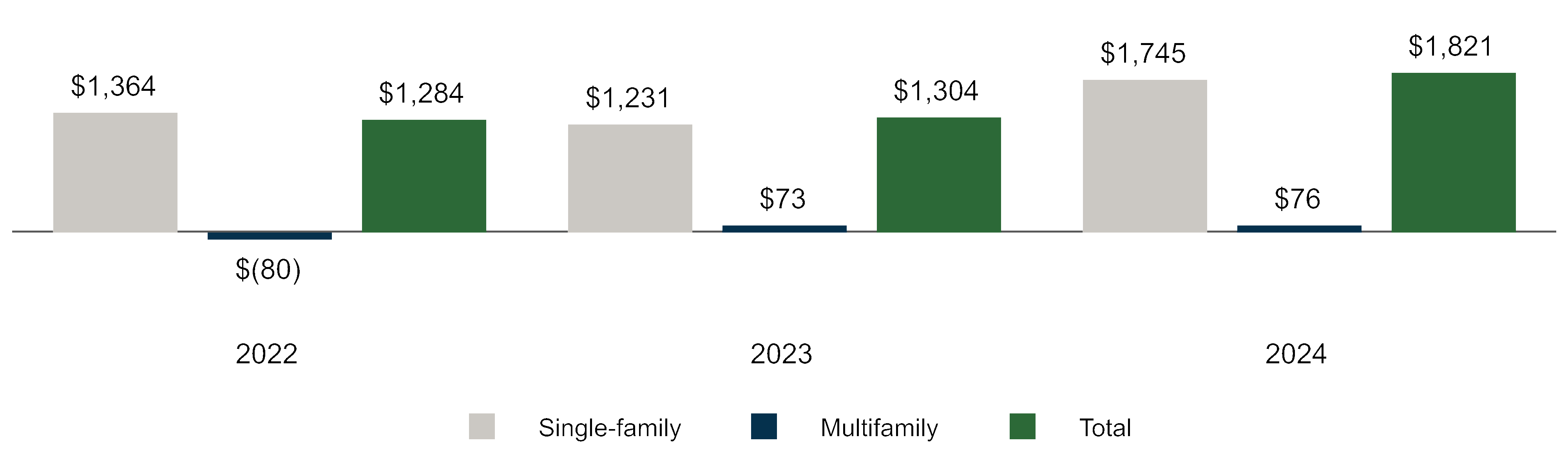We routinely identify cybersecurity threats as well as vulnerabilities in our systems and work to address or mitigate
those we have identified. Some cybersecurity vulnerabilities take a substantial amount of time to resolve or mitigate. We
continue to have cybersecurity vulnerabilities that we have identified but not resolved or mitigated. In addition, efforts to
resolve or mitigate some of our cybersecurity vulnerabilities may be unsuccessful and some cybersecurity vulnerabilities
may not be possible to resolve. We may also have cybersecurity vulnerabilities that we have not yet identified.
Cyber attacks can originate from a variety of sources, including external parties who are affiliated with foreign
governments or are involved with organized crime or terrorist organizations. Cybersecurity risks also derive from human
error, fraud or malice on the part of our employees or third parties. Threat actors have attempted, and we expect will
continue to attempt, to induce employees, lenders, servicers, vendors, service providers, counterparties or other users
of our systems to disclose sensitive information or provide access to our systems or network, or to our data or that of
our counterparties or borrowers, and these types of risks may be difficult to detect or prevent.
Cybersecurity incidents from time to time could result in the theft of important assets or the unauthorized disclosure,
gathering, monitoring, misuse, corruption, loss or destruction of confidential and other information (including personal
information) that belongs to us, our lenders, our servicers, our counterparties, third-party service providers or borrowers
that is processed and stored in, and transmitted through, our computer systems and networks. These incidents could
also result in damage to our systems or otherwise cause interruptions or malfunctions in our, our lenders’, our
counterparties’ or third parties’ operations, systems or networks, which could disrupt our day-to-day business activities
and negatively affect our ability to effect business transactions and manage our exposure to risk. We have experienced
cybersecurity incidents and some of these incidents have resulted in disruptions to our systems and/or those of our
lenders, counterparties and other third parties, as well as financial losses. While to date the impact of these incidents
has not been material to our business strategy, business, financial results or financial condition, cybersecurity incidents
could result in financial losses, loss of lenders, servicers and business opportunities, reputational damage, damage to
our competitive position, litigation, regulatory fines, penalties or intervention, reimbursement or other compensatory
costs or other harms that have a material adverse impact on our business strategy, business, financial results or
financial condition.
Cyber attacks or other cybersecurity incidents can persist for an extended period of time without detection. It may take
considerable time to complete an investigation of a cybersecurity incident and obtain full and reliable information. While
we are investigating a cybersecurity incident, we may not know the full impact of the incident or how to remediate it, and
actions and decisions that are taken or made may further increase the negative impact of the incident. In addition,
announcing that a cyber attack or cybersecurity incident has occurred may worsen the impact of the attack or incident,
and may increase the risk of additional cyber attacks. All or any of these challenges could further increase the costs and
consequences of a cybersecurity incident, as well as hinder our ability to obtain and provide rapid, complete and reliable
information about a cybersecurity incident. We may be required to expend significant additional resources to modify or
add to our protective measures and to investigate and remediate vulnerabilities or other exposures arising from
cybersecurity risks.
Although we maintain insurance coverage relating to cybersecurity risks, our insurance may not be sufficient to provide
adequate loss coverage (including if the insurer denies future claims) and may not continue to be available to us on
economically reasonable terms, or at all. Further, we cannot ensure that any indemnification or limitation of liability
provisions in our agreements with lenders, servicers, service providers, vendors, counterparties and other third parties
with which we do business would be enforceable or adequate or would otherwise protect us from liabilities or damages
with respect to a particular claim in connection with a cybersecurity incident.
Third parties with which we do business and our regulators are also sources of cybersecurity risk. Because we are
interconnected with and dependent on third-party vendors, lenders, servicers, exchanges, clearing houses, fiscal and
paying agents, and other financial intermediaries, including CSS, we could be materially adversely impacted if any of
them is subject to a successful cyber attack or other cybersecurity incident. Some of the third parties with which we do
business have experienced, and we expect will continue to experience, cybersecurity incidents. While third-party
cybersecurity incidents have not had a material impact on our business to date, the inability of a third party with which
we do business to meet its obligations to us as a result of a cybersecurity incident, our response to such an incident, or
other consequences of the incident could materially adversely affect our business.
We routinely transmit and receive personal, confidential and proprietary information by electronic means. We also share
this type of information with regulatory agencies and their vendors. We outsource certain functions and these
relationships allow for the external storage and processing of our information, as well as lender, servicer, counterparty
and borrower information, including on cloud-based systems. In addition, our lenders and servicers maintain personal,
confidential and proprietary information, including personal borrower information. While we engage in actions to mitigate
our exposure resulting from our information-sharing activities with lenders, servicers, regulatory agencies, vendors,
service providers, counterparties and other third parties to protect against cybersecurity incidents, we cannot ensure
that these third parties have appropriate controls in place to protect the confidentiality of the information. An interception,