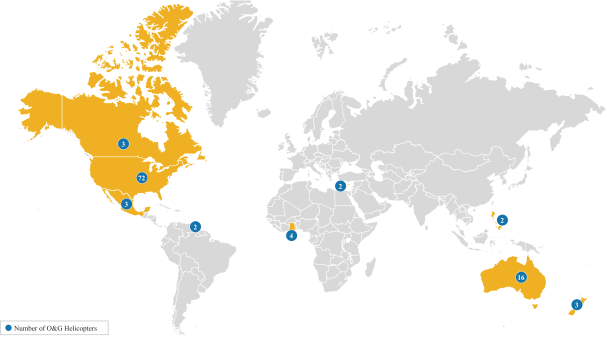
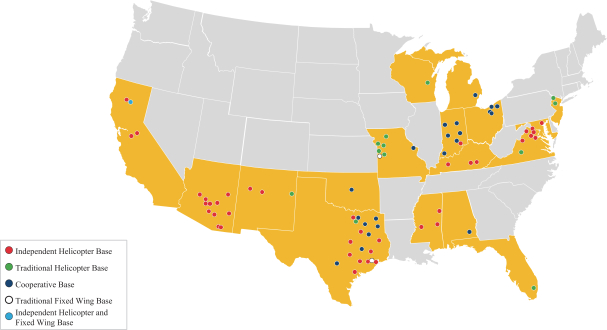
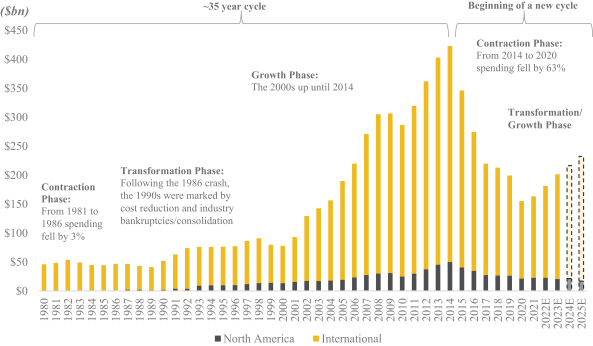
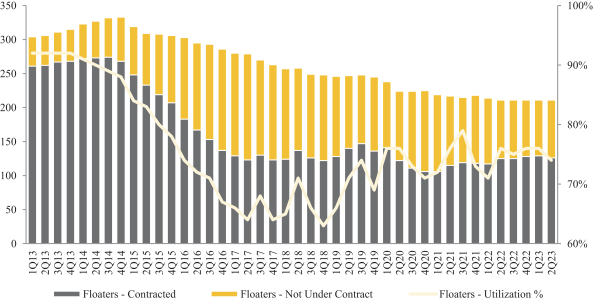
which may include personal information of customers, employees or other third parties, which may include medical information that is subject to and regulated by privacy laws, as described further in the risk factors above. We make significant efforts to maintain the integrity and continuity of our systems and to safeguard the security of these types of information, including maintaining contingency plans in the event of security breaches or other system failures. However, in the past we have been subject to cybersecurity attacks that gained access to certain systems, but they have not had a material impact on our operations. We cannot assure you that our security efforts and measures will in the future prevent service disruptions, unauthorized access to our systems, loss or destruction of data, account takeovers, or other forms of cyber-attacks or similar events, whether caused by mechanical failures, human error, aging equipment or accidental technological failure. We may also experience security breaches that remain undetected for an extended period. Even if identified, we may be unable to adequately investigate or remediate incidents or breaches due to attackers increasingly using tools and techniques that are designed to circumvent controls, to avoid detection, and to remove or obfuscate forensic evidence.
Cybersecurity attacks across industries, including ours, are increasing in sophistication, scope and frequency and may range from uncoordinated individual attempts to measures targeted specifically at us. These attacks include but are not limited to, malicious code, software or viruses (e.g., ransomware), attempts to gain unauthorized access to, or otherwise disrupt, our information systems, attempts to gain unauthorized access to business, proprietary or other confidential information, and other electronic security breaches that could lead to disruptions in critical systems, unauthorized release of confidential or otherwise protected information and corruption of data. Cybersecurity failures may be caused by system errors or vulnerabilities, including vulnerabilities of our vendors, suppliers, and their products or services. In addition, these threats or failures may stem from natural disasters, acts of terrorism, war, telecommunication and other electrical failures, denial or degradation of service attacks, fraud, malice, sabotage or human error or theft on the part of employees, third parties or sophisticated nation-state and nation-state supported actors, including attempts by outside parties to fraudulently induce our employees or customers to disclose or grant access to our data or our customers’ data via phishing attacks or other social engineering schemes.
Failures of our information or communications systems, whether the result of cybersecurity attacks, mechanical failures, natural disasters or otherwise, could result in a breach of critical operational or financial controls and disrupt our operations, commercial activities or financial processes. System failures or cybersecurity attacks may also involve information subject to stringent domestic and foreign data protection laws governing personally identifiable information, protected health information or other similar types of sensitive data and require notification to individuals, governmental authorities, the media and other third parties. Cybersecurity attacks or other disruptions impacting significant customers and/or suppliers could also lead to a disruption of our operations or commercial activities.
Despite our attempts to safeguard our systems and mitigate potential risks, there is no assurance that such actions will be sufficient to prevent cyberattacks or security breaches that manipulate or improperly use our systems or networks, compromise confidential or otherwise protected information, destroy or corrupt data, or otherwise disrupt our operations. The occurrence of such events could damage our reputation, subject us to liability claims or regulatory scrutiny and investigations, potentially resulting in penalties, fines and other enforcement actions. Further, our insurance coverage may not be sufficient to cover the financial, legal, business or reputational losses that may result from an interruption or breach of our systems. Any of the forgoing could adversely affect our business, financial condition and results of operations.
Future investments, acquisitions or business expansions by us would subject us to additional business, operating and financial risks, the impact of which could adversely impact our business.
In an effort to implement our business strategies, we may from time to time in the future pursue acquisition or expansion opportunities, including strategic investments. These transactions could involve acquisitions of entire businesses or investments in start-up or established companies, and could take several forms, including
32