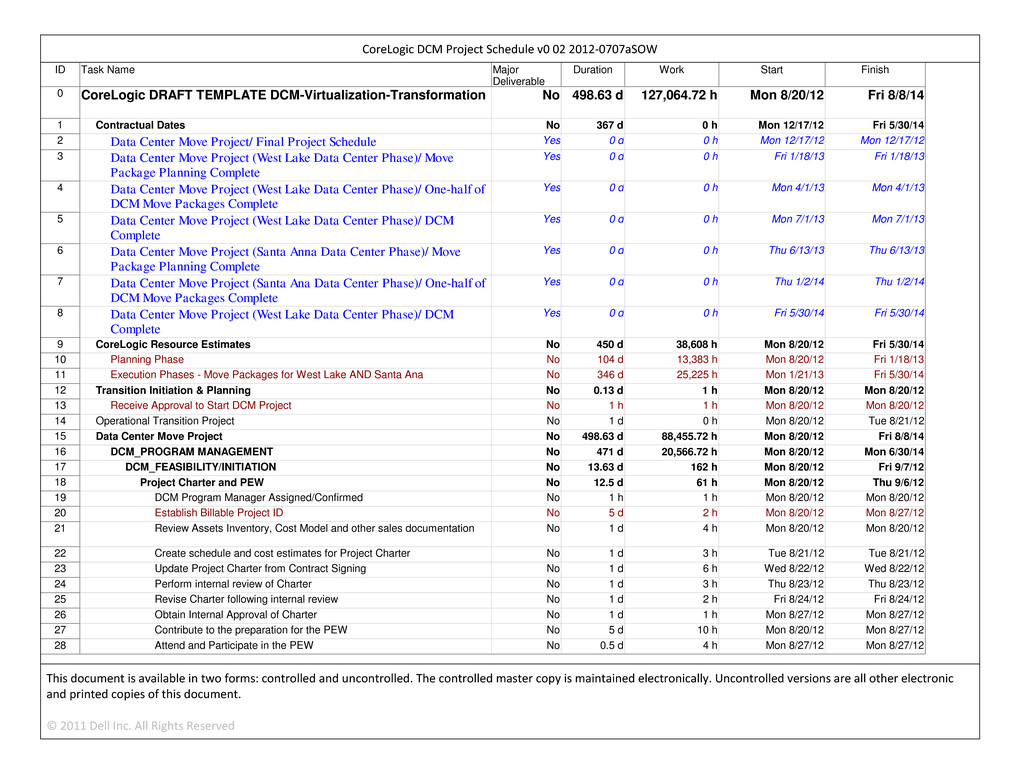
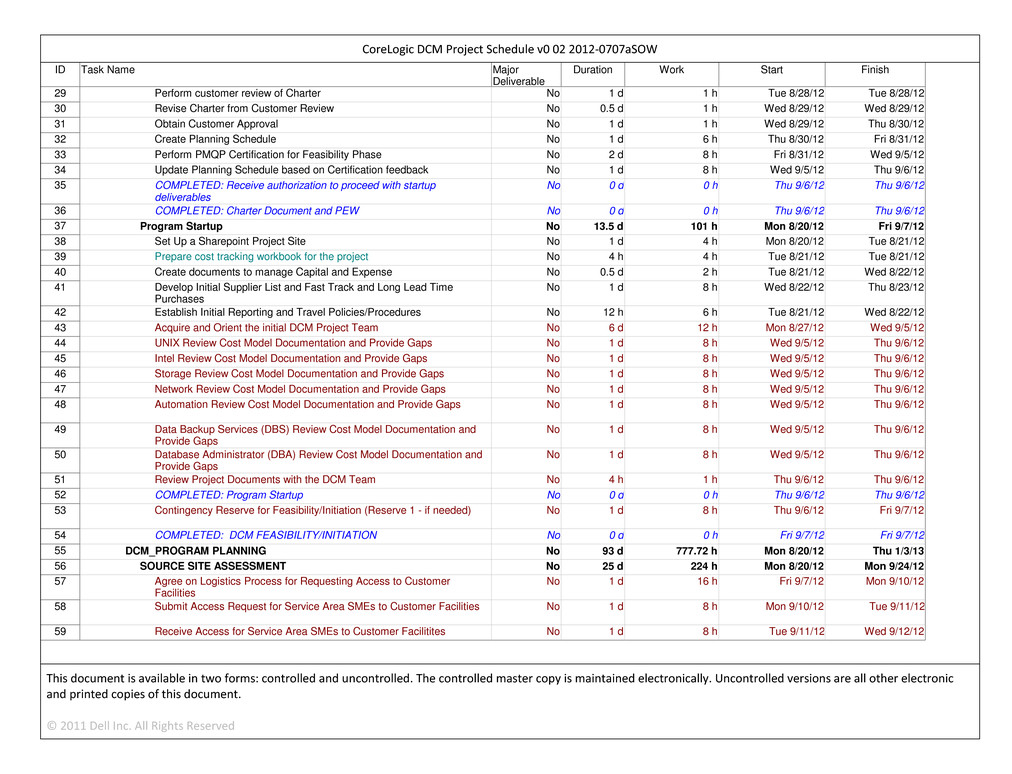
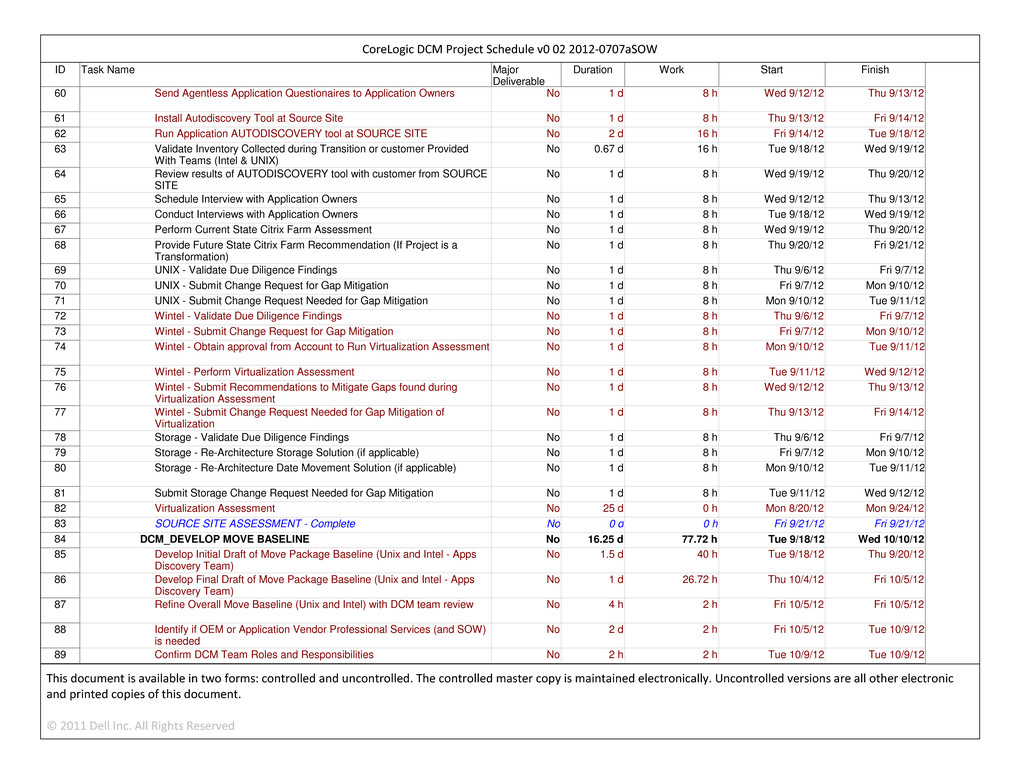
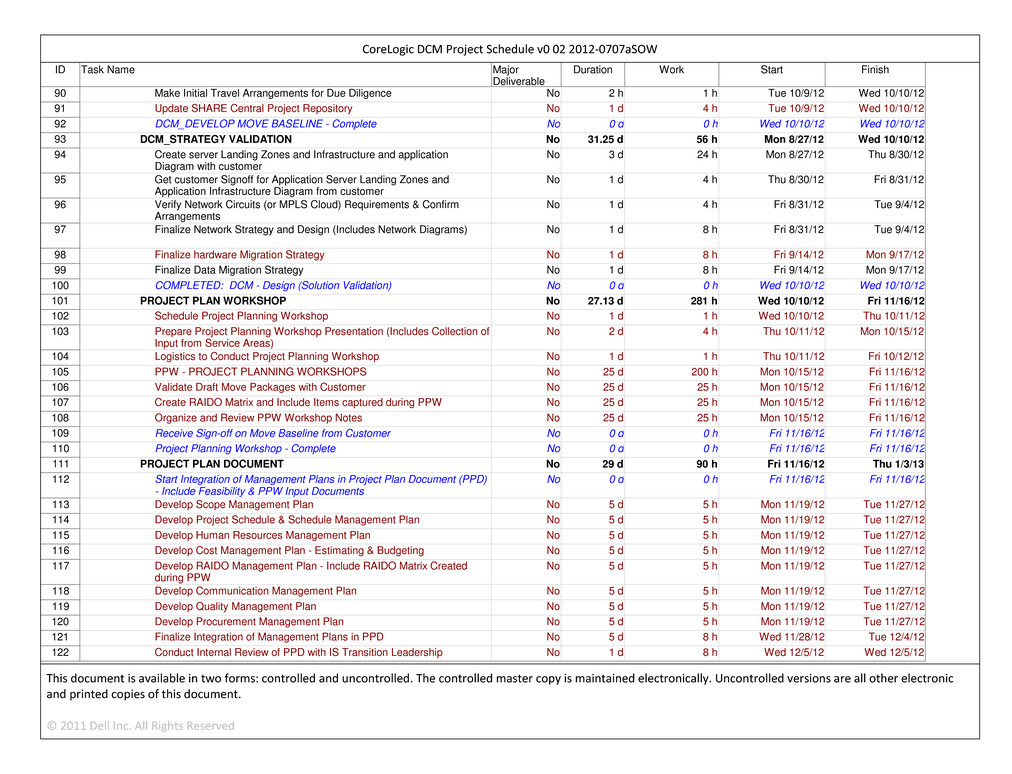
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
by and between
CoreLogic Solutions, LLC
and
Dell Marketing L.P.
Effective as of July 19, 2012
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Table of Contents
|
| | |
| | | Page |
| 1 | Introduction. | |
| 1.1 | Framework Approach. | |
| 1.2 | Definitions. | |
| 2 | CONTRACT DOCUMENTS. | |
| 2.1 | Associated Contract Documents. | |
| 2.2 | Companion Agreements. | |
| 3 | TERM. | |
| 3.1 | Initial Term. | |
| 3.2 | Notice and Extension of Term of Supplements. | |
| 3.3 | Term of Agreement. | |
| 4 | SERVICES. | |
| 4.1 | Overview. | |
| 4.2 | Transition Services. | |
| 4.3 | New Services. | |
| 4.4 | Additional Work or Reprioritization. | |
| 4.5 | Right to In-Source or Use of Third Parties; Cooperation and Management. | |
| 4.6 | Correction of Errors. | |
| 4.7 | Supplier Cooperation. | |
| 4.8 | Transformation Services. | |
| 5 | REQUIRED CONSENTS. | |
| 5.1 | Administrative Responsibility. | |
| 5.2 | Financial Responsibility. | |
| 5.3 | Contingent Arrangements. | |
| 6 | FACILITIES, SOFTWARE, EQUIPMENT, CONTRACTS AND ASSETS ASSOCIATED WITH THE PROVISION OF SERVICES. | |
| 6.1 | Service Facilities. | |
| 6.2 | CoreLogic Facilities. | |
| 6.3 | Supplier’s Responsibilities Regarding CoreLogic’s Network. | |
| 6.4 | CoreLogic Access to Supplier Facilities. | |
| 6.5 | Software, Equipment and Third Party Contracts. | |
| 6.6 | Assignment of Third Party Contracts. | |
| 6.7 | Notice of Defaults. | |
| 7 | SERVICE LEVELS. | |
| 7.1 | Service Levels and Other Performance Standards. | |
| 7.2 | Multiple Service Levels. | |
| 7.3 | Service Level Credits. | |
| 7.4 | Deliverable Credits. | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page i |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | |
| | | Page |
| 8 | SUPPLIER PERSONNEL. | |
| 8.1 | Personnel Transfer. . | |
| 8.2 | Key Supplier Personnel and Knowledge Transfer Personnel. | |
| 8.3 | Customer Executive. | |
| 8.4 | Supplier Personnel Are Not CoreLogic Employees. | |
| 8.5 | Replacement, Qualifications, and Retention of Supplier Personnel. | |
| 8.6 | Reserved. | |
| 8.7 | Conduct of Supplier Personnel. | |
| 8.8 | Substance Abuse. | |
| 9 | SUPPLIER RESPONSIBILITIES. | |
| 9.1 | Policy and Procedures Manual. | |
| 9.2 | Reports. | |
| 9.3 | Governance Model; Meetings. | |
| 9.4 | Quality Assurance and Internal Controls. | |
| 9.5 | CoreLogic Standards. | |
| 9.6 | Change Management. | |
| 9.7 | Software Currency. | |
| 9.8 | Cost Effectiveness and Cost Reduction. | |
| 9.9 | Malicious Code. | |
| 9.1 | Audit Rights. | |
| 9.11 | Subcontractors. | |
| 9.12 | Technology and Business Process Evolution. | |
| 9.13 | Notice of Adverse Impact. | |
| 9.14 | Force Majeure. | |
| 9.15 | Specialized Services. | |
| 9.16 | Government Contracts Flow-Down. | |
| 9.17 | CoreLogic Customer Contracts Flow-Down. | |
| 10 | CoreLogic Responsibilities. | |
| 10.1 | Responsibilities. | |
| 10.2 | Supplier Excused Performance. | |
| 11 | CHARGES. | |
| 11.1 | General. | |
| 11.2 | Administered Expenses. | |
| 11.3 | Taxes. | |
| 11.4 | Extraordinary Events. | |
| 11.5 | Refundable Items. | |
| 11.6 | CoreLogic Benchmarking Reviews. | |
| 11.7 | Financial Forecasting and Budgeting Support. | |
| 11.8 | Reserved. | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page ii |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | |
| | | Page |
| 12 | INVOICING AND PAYMENT. | |
| 12.1 | Invoicing. | |
| 12.2 | Payment Due. | |
| 12.3 | Set Off. | |
| 12.4 | Disputed Charges. | |
| 13 | CoreLogic DATA AND OTHER CONFIDENTIAL INFORMATION. | |
| 13.1 | Confidential Information. | |
| 13.2 | CoreLogic Data. | |
| 13.3 | Personal Data. | |
| 13.4 | Survival. | |
| 14 | OWNERSHIP OF MATERIALS. | |
| 14.1 | CoreLogic Owned Materials. | |
| 14.2 | Developed Materials. | |
| 14.3 | Supplier Owned Materials. | |
| 14.4 | Other Materials. | |
| 14.5 | General Rights. | |
| 14.6 | CoreLogic Rights Upon Expiration or Termination of Agreement. | |
| 15 | REPRESENTATIONS, WARRANTIES and covenants. | |
| 15.1 | Work Standards. | |
| 15.2 | Materials. | |
| 15.3 | Non-Infringement. | |
| 15.4 | Authorization. | |
| 15.5 | Reserved. | |
| 15.6 | Disabling Code. | |
| 15.7 | Compliance with Laws. | |
| 15.8 | Interoperability. | |
| 15.9 | Disclaimer. | |
| 16 | INSURANCE AND RISK OF LOSS. | |
| 16.1 | Insurance. | |
| 16.2 | Risk of Loss. | |
| 17 | INDEMNITIES. | |
| 17.1 | Indemnity by Supplier. | |
| 17.2 | Indemnity by CoreLogic. | |
| 17.3 | Additional Indemnities. | |
| 17.4 | Infringement. | |
| 17.5 | Indemnification Procedures. | |
| 17.6 | Indemnification Procedures – Governmental Claims. | |
| 17.7 | Subrogation. | |
| 18 | LIABILITY. | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page iii |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | |
| | | Page |
| 18.1 | General Intent. | |
| 18.2 | Limitation of Liability. | |
| 19 | DISPUTE RESOLUTION. | |
| 19.1 | Dispute Resolution Procedures. | |
| 19.2 | Jurisdiction. | |
| 19.3 | Continued Performance. | |
| 19.4 | Governing Law. | |
| 19.5 | Injunctive Relief. | |
| 20 | TERMINATION. | |
| 20.1 | Termination for Cause. | |
| 20.2 | Termination for Convenience. | |
| 20.3 | Termination Upon Supplier Change of Control. | |
| 20.4 | Termination Upon CoreLogic Merger or Acquisition. | |
| 20.5 | Termination for Insolvency. | |
| 20.6 | CoreLogic Rights Upon Supplier’s Bankruptcy. | |
| 20.7 | Termination for ***. | |
| 20.8 | Disengagement Services. | |
| 21 | GENERAL. | |
| 21.1 | Binding Nature, Assignment. | |
| 21.2 | Entire Agreement; Amendment. | |
| 21.3 | Notices. | |
| 21.4 | Counterparts, Headings, Language. | |
| 21.5 | Relationship of Parties. | |
| 21.6 | Severability. | |
| 21.7 | Consents and Approval. | |
| 21.8 | Waiver of Default; Cumulative Remedies. | |
| 21.9 | Survival. | |
| 21.1 | Publicity. | |
| 21.11 | Third Party Beneficiaries. | |
| 21.12 | Covenant Against Pledging. | |
| 21.13 | Order of Precedence. | |
| 21.14 | Hiring. | |
| 21.15 | Liens. | |
| 21.16 | Covenant of Cooperation and Good Faith. | |
| 21.17 | Acknowledgment, Further Assurances. | |
| 21.18 | Reference and Customer Satisfaction Survey. | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page iv |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
This Master Services Agreement is entered into effective as of July 19, 2012 (the “Effective Date”) by and between CoreLogic Solutions, LLC, a California limited liability company having a principal place of business at 4 First American Way, Santa Ana, California 92707 (“CoreLogic”), and Dell Marketing L.P., a Texas limited partnership having a principal place of business at One Dell Way, Round Rock, Texas 78682 (“Supplier”).
WHEREAS, CoreLogic and Supplier have engaged in extensive negotiations, discussions and due diligence that have culminated in the formation of the contractual relationship described in this Agreement; and
WHEREAS, CoreLogic desires to procure from Supplier, and Supplier desires to provide to CoreLogic and the other Eligible Recipients, certain services, on the terms and conditions specified in this Agreement;
NOW THEREFORE, in consideration of the mutual promises and covenants contained herein, and of other good and valid consideration, the receipt and sufficiency of which is hereby acknowledged, CoreLogic and Supplier (collectively, the “Parties” and each, a “Party”) hereby agree as follows:
| |
| (a) | Master Services Agreement. The body of this agreement (i.e., the introductory paragraph through Article 21) and all schedules and annexes hereto (the “Master Services Agreement” or “MSA”) sets forth terms and conditions pursuant to which the Parties may enter into supplementary agreements for the provision of Services. |
| |
| (b) | Supplements and Work Orders. To the extent the Parties desire to enter into an agreement for Supplier to perform Services, the Parties shall execute a supplement to this MSA, a form for which is set forth in Annex 1. Each supplement, together with any Work Orders (defined below), exhibits, schedules, attachments or appendices thereto, shall be referred to as a “Supplement”. After execution of a Supplement, the Parties may add Services to be provided under such Supplement by executing a work order referring to such Supplement (each, together with any schedules, exhibits, attachments, appendices or annexes thereto, a “Work Order”). Supplements and Work Orders are not binding on the Parties until fully executed by authorized representatives of each Party. |
| |
| (c) | Relationship of the Master Services Agreement and Supplements. The term “Agreement” means, collectively, the MSA and the Supplements. Unless and to the extent expressly excluded in a particular Supplement, all of the terms and conditions of this MSA shall be deemed to be incorporated into such Supplement, unless, given the context of a particular term or condition, the term or condition is clearly inapplicable to such Supplement. For example, if this MSA contains a term regarding Service Levels, and a particular Supplement does not contain Service Levels, such term would not apply to such Supplement. The terms and conditions of a particular Supplement (including incorporated MSA terms and conditions as such terms and conditions may have been modified for such Supplement), apply only to such Supplement unless otherwise expressly provided. For example, a pricing term in Schedule A-4 to Supplement A will not apply to Supplement B unless otherwise expressly agreed, but a pricing term in Schedule 4 will apply to all Supplements. However, information in a Schedule to the MSA (and all Schedules to this Agreement are marked as such), for example, Schedule 1, will apply to all Supplements. |
| |
| (d) | References. References to a Schedule, Exhibit, Attachment, Appendix or Annex include all documents subsidiary to such document. For example, a reference to Schedule 3 will include reference to Attachments 3-A, 3-B, and 3-C to Schedule 3. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 1 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (a) | Except as otherwise expressly provided in this Agreement, all capitalized terms used in this Agreement shall have the meanings set forth in Schedule 1. |
| |
| (b) | Each reference in this Agreement to “Commencement Date” refers to the applicable Commencement Date for the particular Services as designated in the applicable Supplement or a Companion Agreement for such Supplement or, if no such date is set forth in the applicable Supplement, the Supplement Effective Date. Each reference to “Term” refers to the Term for the applicable Supplement. |
| |
| 2.1 | Associated Contract Documents. |
This MSA includes each of the following Schedules and Annexes, all of which are incorporated into this MSA by this reference.
| |
| Schedule 4 | Pricing and Financial Provisions |
| |
| Schedule 5 | Human Resources Provisions |
| |
| Schedule 8 | Rules, Procedures and Policies |
| |
| Schedule 9 | Insurance Requirements |
| |
| Schedule 10 | Direct CoreLogic Competitors |
| |
| Schedule 11 | Direct Supplier Competitors |
| |
| Schedule 12 | Additional Data Safeguarding Obligations |
| |
| Schedule 13 | Termination Charges Percentage Table |
| |
| Schedule 14 | CoreLogic-Specific Facility and Controls Audits |
| |
| Schedule 15 | Approved Benchmarkers |
| |
| Annex 1 | Form of Supplement |
| |
| Annex 2 | Form of Non-Disclosure Agreement |
| |
| Annex 3 | Form of Companion Agreement |
| |
| Annex 4 | Form of Business Associate Agreement |
| |
| (a) | As specified in a Supplement, Supplier and CoreLogic shall cause their local Affiliates to enter into, one or more companion agreements in the form of Annex 3 with non-U.S. Entities that are Eligible Recipients for the purpose of memorializing the implementation of this Agreement and the applicable Supplement (each, a “Companion Agreement”). All Services shall be provided by Supplier or the applicable Affiliate of Supplier pursuant to this Agreement or an executed Companion Agreement. Unless and to the extent an individual Companion Agreement expressly provides otherwise, each Companion Agreement shall incorporate by reference the terms and conditions of this Agreement and shall not be construed as altering or superseding the rights and obligations of the Parties under this Agreement. |
| |
| (b) | Supplier shall be fully responsible and liable for all obligations of itself or any Supplier Affiliate or Subcontractor to the same extent as if such failure to perform or comply was committed by Supplier, and CoreLogic will have the same rights under this Agreement if an event or circumstance (e.g., bankruptcy) occurs with respect to a Supplier Affiliate or Subcontractor that is a party to a Companion Agreement, that it would have if such party were Supplier. CoreLogic shall be fully responsible and liable for all obligations of any Eligible Recipient to the same extent as if such failure to perform or comply was committed by CoreLogic, and Supplier will have the same rights under this Agreement if an event or |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
circumstance (e.g., bankruptcy) occurs with respect to an Eligible Recipient that is a party to a Companion Agreement, that it would have if such party were CoreLogic.
| |
| (c) | The Customer Executive (and his or her designees(s)) and the CoreLogic Relationship Manager (and his or her designees(s)) shall remain responsible for the administration of this Agreement and the individual Companion Agreements on a day-to-day basis on behalf of Supplier and CoreLogic respectively and shall each provide recommendations to his or her respective Party’s authorized representative to amend, modify, change, waive or discharge their rights and obligations under this Agreement or such Companion Agreements as appropriate. |
| |
| (d) | Notwithstanding anything to the contrary in any Companion Agreement, any and all disputes arising under or relating to any Companion Agreement shall be subject to the provisions of Article 19, and under no circumstances shall CoreLogic or any Eligible Recipient, on the one hand, or Supplier, any Supplier Affiliate or Subcontractor, on the other hand, bring or attempt to bring any claim or other action arising under or relating to any Companion Agreement or this Agreement in any jurisdiction except as provided in Section 19.2. In addition, CoreLogic shall have the right to enforce this Agreement (including the terms of all Companion Agreements) on behalf of each Eligible Recipient that enters into a Companion Agreement, and to assert all rights and exercise and receive the benefits of all remedies (including monetary damages) of each Eligible Recipient, to the same extent as if CoreLogic were such Eligible Recipient, subject to the limitations of liability applicable under this Agreement. Supplier shall have the right to enforce this Agreement (including the terms of all Companion Agreements) on behalf of each Affiliate or Subcontractor that enters into a Companion Agreement, and to assert all rights and exercise and receive the benefits of all remedies (including monetary damages) of each Affiliate or Subcontractor hereunder, to the same extent as if Supplier were such Affiliate or Subcontractor, subject to the limitations of liability applicable under this Agreement. Each reference to “Supplier” in this Agreement shall be deemed to refer to Supplier Affiliates or Subcontractors, to the extent such Supplier Affiliates or Subcontractors perform, or are obligated to perform, Services under any Companion Agreement. |
The Term for each Supplement shall be as set forth therein, unless such Supplement is terminated earlier in accordance with Article 20 or such Supplement.
| |
| 3.2 | Notice and Extension of Term of Supplements. |
CoreLogic may, at its sole option, extend the Term of any Supplement for up to two (2) successive periods of one (1) year each on the terms and conditions then set forth in this Agreement and such Supplement.
Unless otherwise terminated in accordance with Article 20, this MSA shall remain in effect from the Effective Date until the second anniversary of the first date on which no Supplement is then in effect between the Parties.
| |
| (a) | Services. During the periods set forth in the applicable Supplement, Supplier shall provide the following Services as they may evolve during the Term or be supplemented, enhanced, modified or replaced to CoreLogic, and, upon CoreLogic’s request, to Eligible Recipients and Authorized Users designated by CoreLogic: |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 3 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (i) | The services, functions and responsibilities described in the applicable Supplement and elsewhere in this Agreement; |
| |
| (ii) | The services, functions and responsibilities reasonably related to the Services performed in the normal course of business during the *** (***) *** preceding the Commencement Date by CoreLogic Personnel (including CoreLogic contractors) who were *** *** as a result of such Supplement, even if the service, function, or responsibility is not specifically described in such Supplement (provided that, (A) in the event of a direct conflict between the description of services, functions and responsibilities in such Supplement and the scope of services as described in this Section 4.1(a)(ii), the description in such Supplement shall control and (B) such services, functions and responsibilities shall not include services, functions and responsibilities for which CoreLogic has operational responsibility pursuant to the terms of this Agreement, were permanently discontinued before the Commencement Date with CoreLogic approval or were specifically discontinued pursuant to the Transition Plan or this Agreement); and |
| |
| (iii) | To the extent a CoreLogic Base Case is set forth in the applicable Supplement, the services, functions and responsibilities reflected in those categories of such CoreLogic Base Case which Supplier is assuming pursuant to such Supplement (provided that, (A) in the event of a direct conflict between the description of services, functions and responsibilities in such Supplement and the scope of services as described in this Section 4.1(a)(iii), the description in such Supplement shall control and (B) such services, functions and responsibilities shall not include services, functions and responsibilities for which CoreLogic has operational responsibility pursuant to the terms of this Agreement, were permanently discontinued before the Commencement Date with CoreLogic approval or were specifically discontinued pursuant to the Transition Plan or this Agreement). |
| |
| (b) | Included Services. If any services, functions or responsibilities not specifically described in a Supplement are an inherent, necessary or *** the described Services, or are required for proper performance or provision of the Services in accordance with this Agreement, those services, functions and responsibilities shall be deemed to be included within the scope of the Services to be delivered for the Charges, as if such services, functions or responsibilities were specifically described in such Supplement. |
| |
| (c) | Required Resources. Except as otherwise expressly provided in the applicable Supplement or otherwise in this Agreement, Supplier shall be responsible for providing the facilities, personnel, Equipment, Materials, technical knowledge, expertise, supplies and other resources necessary to provide the Services. |
| |
| (d) | Supplier Responsibility. Supplier shall be responsible for the performance of the Services in accordance with this Agreement even if such Services are actually performed or dependent upon services performed by Subcontractors and ***, acting under the direction of Supplier under this Agreement. |
| |
| (a) | Transition. Supplier shall perform the services required to smoothly transfer responsibility for the services to be transitioned from CoreLogic (or Third Party Contractors where applicable) to Supplier (the “Transition Services”), including those described in any transition plan set forth in the applicable Supplement (the “Transition Plan”). CoreLogic will perform or cause to be performed those tasks which are designated to be the responsibility of CoreLogic, Eligible Recipients or Third Party Contractors in the Transition Plan including causing Third Party Contractors to fully cooperate with and work in good faith with Supplier. Supplier agrees that the responsibilities of CoreLogic, as set forth in this Section 4.2(a), are not intended as contractual duties or obligations of CoreLogic giving rise to a claim of breach by Supplier, but rather as conditions precedent to the extent applicable to the related duties and obligations of Supplier under this Agreement for purposes of Section ***. |
| |
| (b) | Transition Plan. Each Supplement will include a Transition Plan that will be attached as a Schedule to such Supplement. To the extent requested by CoreLogic, the Transition Plan shall identify (i) the transition |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 4 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
activities to be performed by Supplier and the significant components, subcomponents and the conditions precedent associated with each such activity, (ii) all deliverables to be completed by Supplier, (iii) the date(s) by which each such activity or deliverable is to be completed (the “Transition Milestones”), (iv) the completion date for each Transition Services task, (v) the contingency or risk mitigation strategies to be employed by Supplier in the event of disruption or delay, (vi) the acceptance criteria (and, if appropriate, description of applicable testing) to be applied by CoreLogic in evaluating Transition Services deliverables, (vii) any transition responsibilities to be performed or transition resources to be provided by CoreLogic, (viii) any related documents contemplated by this Agreement and/or required to effectuate the transition to be executed by the Parties and (ix) a detailed work plan identifying the specific transition activities to be performed by Supplier on a weekly basis during the Transition Period.
| |
| (c) | Detailed Transition Plan. Supplier shall prepare and deliver to CoreLogic a more detailed version of the Transition Plan for CoreLogic’s review, comment and approval within *** (***) *** after the Supplement Effective Date or such other period as is specified in the Supplement. The proposed detailed Transition Plan shall describe in greater detail the specific transition activities to be performed by Supplier, but shall be consistent in all respects with the Transition Plan attached to the applicable Supplement, including the activities, deliverables, Transition Milestones and Deliverable Credits described in such Transition Plan. Supplier shall address and resolve any questions or concerns CoreLogic may have as to any aspect of the proposed detailed Transition Plan and incorporate any modifications, additions or deletions to such Transition Plan requested by CoreLogic within *** (***) *** of receiving them from CoreLogic. The Parties shall reasonably cooperate to permit completion of the detailed Transition Plan within *** (***) *** after the Supplement Effective Date unless another period is agreed upon by the Parties. The detailed Transition Plan as approved by CoreLogic shall be deemed to be appended to and incorporated in the applicable Supplement. |
| |
| (d) | Performance. Supplier shall perform the Transition Services described in the Transition Plan in accordance with the timetable and the Transition Milestones set forth in the Transition Plan. Supplier shall perform the Transition Services in a manner that will not disrupt the business or operations of any of the Eligible Recipients or degrade the Services then being received by any of the Eligible Recipients, except as may be otherwise expressly provided in the Transition Plan. Prior to undertaking any transition activity, Supplier shall discuss with CoreLogic all known *** material risks and shall not proceed with such activity until *** with the plans with regard to such risks (provided that neither Supplier’s disclosure of any such risks to CoreLogic, nor CoreLogic’s acquiescence in Supplier’s plans, shall operate or be construed as limiting Supplier’s responsibility under this Agreement). Subject to Section 4.2(f), Supplier shall identify and resolve, with CoreLogic’s reasonable assistance, any problems that may impede or delay the timely completion of each task in the Transition Plan that is Supplier’s responsibility and shall use commercially reasonable efforts to assist CoreLogic with the resolution of any problems that may impede or delay the timely completion of each task in the Transition Plan that is CoreLogic’s responsibility. If new and unforeseen risks are discovered after final approval of the detailed Transition Plan, the Parties shall work together in good faith to resolve the risks through governance, including, as applicable, through the Change Management Procedures; provided that, unless the Parties agree otherwise (which agreement either Party may withhold in its sole discretion), in no event shall this sentence be used to *** set forth for ***. |
| |
| (e) | Reports. Supplier shall meet at least weekly with CoreLogic to report on its progress in performing its responsibilities set forth in the Transition Plan. Supplier also shall provide written reports to CoreLogic at least weekly regarding such matters, and shall provide oral reports more frequently if reasonably requested by CoreLogic. Promptly, but not later than *** (***) ***, after receiving any information indicating that Supplier may not perform its responsibilities or meet the timetable set forth in the Transition Plan, Supplier shall notify CoreLogic in writing of the potential delays and shall identify for CoreLogic’s consideration and approval specific measures to address such delay and mitigate the risks associated therewith. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 5 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (f) | Suspension or Delay of Transition Activities. CoreLogic reserves the right, in its sole discretion, to suspend or delay the performance of the Transition Services and/or the transition of all or any part of the Services. If CoreLogic elects to exercise such right and CoreLogic’s decision is *** based on Supplier’s failure to plan for or complete necessary activities related to a Transition Milestone, or Supplier’s failure to perform its other obligations under the applicable Supplement or this Section 4.2 (including failure to meet a Transition Milestone), CoreLogic shall not incur any Charges, Termination Charges, or reimbursable expenses in connection with such decision. If CoreLogic’s decision is not primarily based on Supplier’s failure to plan for or complete necessary activities related to a Transition Milestone, or Supplier’s failure to perform its other obligations under the applicable Supplement or this Section 4.2 (including failure to meet a Transition Milestone), CoreLogic shall reimburse Supplier for any additional costs (including stranded time for Supplier Personnel affected by such suspension or delay, at the applicable rates set forth in the Supplement) reasonably incurred by Supplier as a result of such decision (provided that Supplier notifies CoreLogic in advance of such costs, obtains CoreLogic’s approval prior to incurring such costs, and uses commercially reasonable efforts to minimize such costs). |
| |
| (g) | Failure to Meet Transition Milestones. |
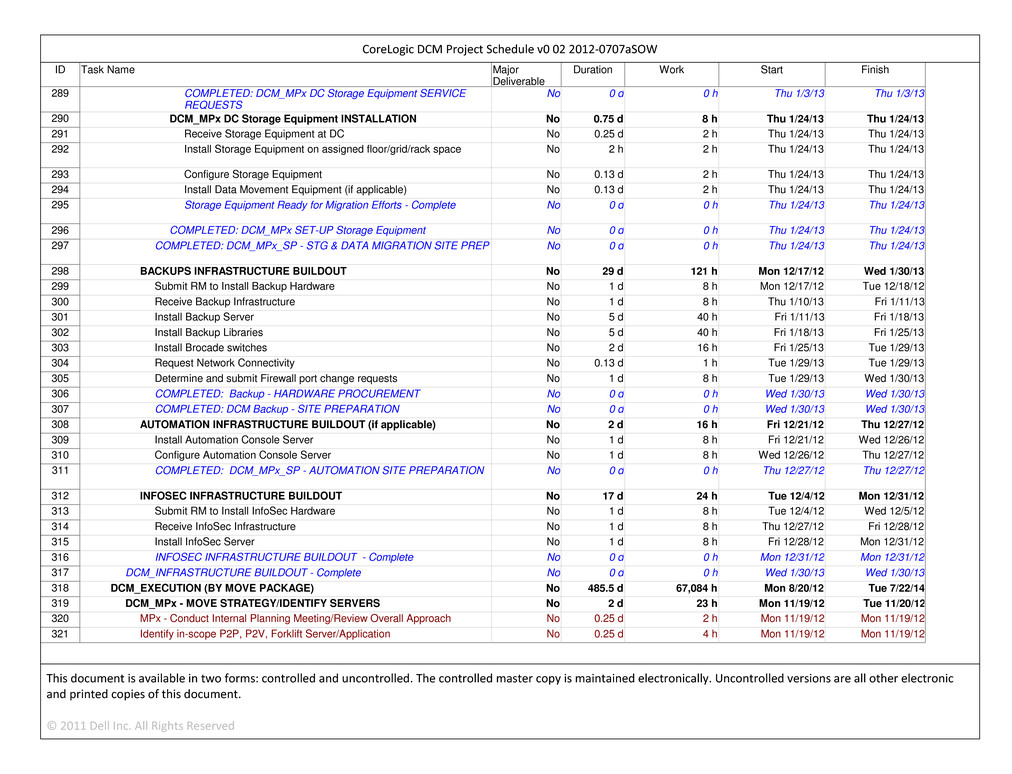
| |
| (i) | If Supplier fails to meet a Transition Milestone, Supplier shall pay CoreLogic any Deliverable Credits specified in the applicable Supplement for such Transition Milestone. |
| |
| (ii) | Neither the Transition Services nor the activities and deliverables associated with individual Transition Milestones will be deemed complete until Acceptance of such activities and deliverables. |
| |
| (iii) | In addition to any Deliverable Credits provided pursuant to Section 4.2(g)(i), if Supplier fails to meet the date specified for any Transition Milestone, Supplier shall *** associated with such Transition Milestone after such date. |
| |
| (h) | Termination for Cause. In addition to any other termination right CoreLogic may have under this Agreement, CoreLogic may terminate the applicable Supplement *** (with respect to such ***) for cause if (i) Supplier materially breaches its obligations with respect to the provision of Transition Services and fails to cure such breach within *** (***) *** after its receipt of notice, (ii) Supplier fails to meet a Transition Milestone and such failure constitutes a material breach of the applicable Supplement and Supplier fails to cure such breach within *** (***) *** after its receipt of notice or (iii) Supplier fails to meet a Transition Milestone designated in the applicable Supplement as a “Critical Transition Milestone” and fails to cure such breach within *** (***) *** after its receipt of notice. In all such events, subject to Section 18.2, CoreLogic may recover the damages suffered by the Eligible Recipients in connection with such a termination, provided that, if such termination is based on Supplier’s failure to meet a Transition Milestone, Supplier shall be entitled to set-off against such damages any Deliverable Credits Supplier has paid for the failure to meet such Transition Milestone. |
| |
| (i) | Establishment of Managed Services. Unless otherwise set forth in an applicable Supplement, Supplier shall assume performance of the Services as of the Commencement Date set forth in such Supplement; provided that, if Supplier fails to meet the final Transition Milestone identified in such Supplement with respect to each applicable Service Area identified in Supplement A to be performed as a Managed Service, Supplier shall not *** until such time as such final Transition Milestone with respect to such Service Area has been Accepted. For purposes of Supplement A, the “final Transition Milestone” shall be deemed to mean completion of the *** (as such term is defined therein) with respect to the applicable Service Area identified in Supplement A to be performed as a Managed Services. Notwithstanding the foregoing, for purposes of Supplement A, the Commencement Date for all Service Areas shall be ***. For clarity, the pricing methodology and Charges set forth in the applicable Supplement with respect to the Managed Services performed after the Commencement Date shall apply during any period between *** and Acceptance of the final Transition Milestone. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 6 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (a) | Procedures. If CoreLogic requests that Supplier perform any New Services reasonably related to the Services, Supplier shall promptly prepare a New Services proposal for CoreLogic’s consideration. Unless otherwise agreed by the Parties, Supplier shall prepare such New Services proposal *** to CoreLogic and shall deliver such proposal to CoreLogic within *** (***) *** of its receipt of CoreLogic’s request, unless a longer period of time is agreed upon by the Parties. Supplier shall use all commercially reasonable efforts to respond more quickly in the case of a pressing business need or an emergency situation. CoreLogic shall provide such information as Supplier reasonably requests in order to prepare such New Services proposal. CoreLogic may accept or reject any New Services proposal in its sole discretion and Supplier shall not be obligated to perform any New Services to the extent the applicable proposal is rejected. If CoreLogic accepts Supplier’s proposal, Supplier will perform the New Services and will be paid in accordance with the proposal submitted by Supplier, or other terms as may be agreed upon by the Parties, and the applicable provisions of this Agreement. Upon CoreLogic’s acceptance of a Supplier proposal for New Services, the scope of the Services will be expanded to include such New Services, and such accepted New Services proposal will be documented in a Work Order or in a new Supplement to this Agreement, as applicable. Notwithstanding any provision to the contrary, (i) Supplier shall act reasonably and in good faith in formulating its pricing proposal, (ii) Supplier shall use commercially reasonable efforts to identify ***, including utilizing Subcontractors as and to the extent appropriate, (iii) such pricing proposal shall be *** set forth in this Agreement for comparable or similar Services, and (iv) such pricing proposal shall take into account *** between CoreLogic and Supplier. If CoreLogic requests additional Services and Supplier and CoreLogic disagree about whether such requested Services constitute New Services, then the Parties shall meet and discuss such disagreement in good faith, provided that during the discussions, Supplier shall *** for *** percent (***%) of ***, without limitation of Section *** or prejudice to the Parties’ rights to claim that *** apply. Promptly after resolution of the dispute, (A) if CoreLogic is the prevailing Party, Supplier shall refund *** paid to Supplier with respect to the requested Services that were the subject of the dispute, together with *** and any applicable Disputed New Services Fee as described below in this Section 4.3(a) and (B) if Supplier is the prevailing Party, Supplier shall invoice CoreLogic for *** of the charges for the requested Services that are determined to be New Services, together with interest at the rate specified in Section 12.2 and any applicable Disputed New Services Fee as described below in this Section 4.3(a). If such disagreement remains unresolved *** (***) *** after Supplier commenced performance of such disputed Services, then upon resolution of such disagreement, in addition to the applicable refunds or payments and associated interest, the non-prevailing Party shall pay the other Party a “Disputed New Services Fee” equal to *** percent (***%) of the total amount paid for the requested Services under dispute (e.g., ***% of the applicable charges proposed by Supplier) by CoreLogic to Supplier during the period of the dispute. If after thirty (30) days of the commencement of discussions, the Parties cannot agree on whether such requested Services constitute New Services, the matter shall be resolved pursuant to the dispute resolution procedures set forth in Article 19. |
| |
| (b) | Use of Third Parties. CoreLogic may elect to solicit and receive bids from third parties to perform any New Services. If CoreLogic elects to use third parties to perform New Services, (i) such New Services shall not be deemed “Services” under the provisions of this Agreement, and (ii) Supplier shall cooperate with such third parties as provided in this Agreement, including Section 4.5. |
| |
| (c) | Services Evolution and Modification. The Parties anticipate that the Services will evolve and be supplemented, modified, enhanced or replaced over time to keep pace with technological advancements and improvements in the methods of delivering Services and changes in the businesses of the Eligible Recipients. The Parties acknowledge and agree that these changes will modify the Services and will not be deemed to result in *** unless the ***. |
| |
| (d) | Authorized User and Eligible Recipient Requests. |
| |
| (i) | Supplier shall promptly inform the CoreLogic Relationship Manager (or his or her designee) of requests for New Services that are within the categories of Services contemplated under this Agreement from Authorized Users or Eligible Recipients, and shall submit any proposals for such |
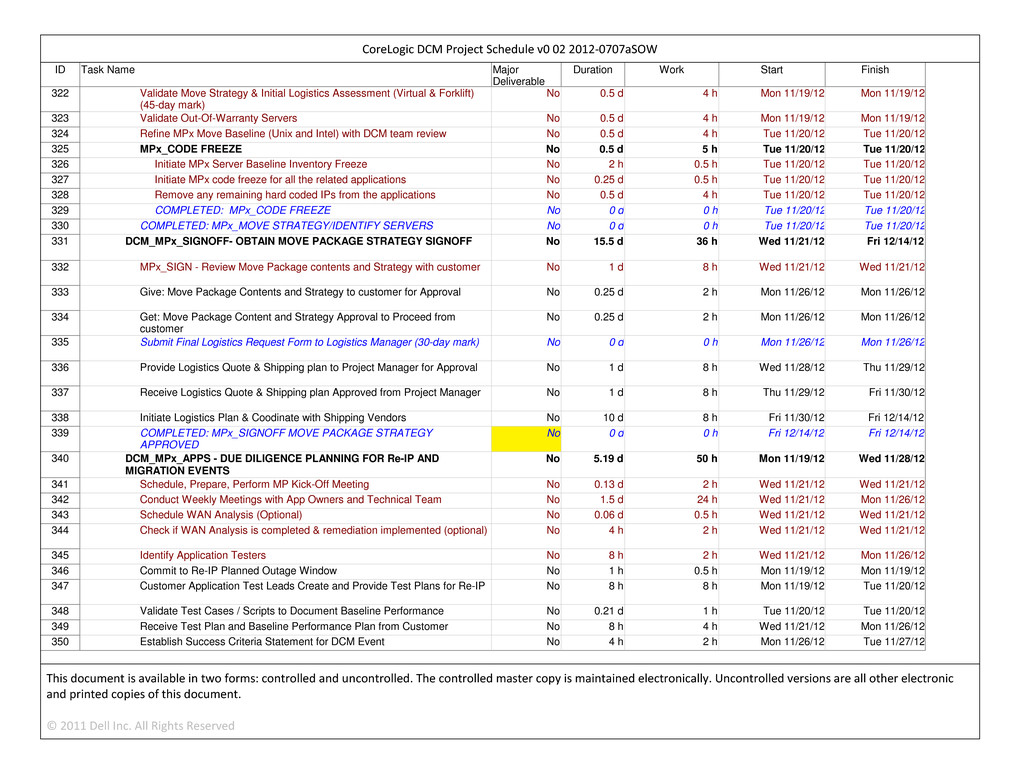
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 7 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
New Services to the CoreLogic Relationship Manager (or his or her designee). Supplier shall not agree to provide New Services under this Agreement to any Authorized Users or Eligible Recipients without the prior written approval of the CoreLogic Relationship Manager (or his or her designee). If Supplier fails to comply with this Section 4.3(d), it shall *** any services rendered to any person or entity in violation of such provision. After the CoreLogic Relationship Manager (or his or her designee) becomes aware that Supplier is providing a New Service to an Authorized User or Eligible Recipient in violation of this Section 4.3(d)(i), Supplier shall continue to perform such New Service only to the extent *** in accordance with Section 4.3; in which case, CoreLogic shall be responsible for *** for such New Services due in accordance with Section 4.3 from the date on which ***. This Section 4.3(d)(i) shall not apply with respect to any Authorized User or Eligible Recipient who obtains New Services by logging into one of Supplier’s commercially-available websites and orders Services or Equipment (provided that such Authorized User is not induced by Supplier or Supplier Personnel).
| |
| (ii) | Supplier shall promptly inform the CoreLogic Relationship Manager (or his or her designee) of requests for New Services, products or services that are outside the categories of Services contemplated by this Agreement from CoreLogic Personnel or CoreLogic Affiliates, and shall submit any proposals for such New Services to the CoreLogic Relationship Manager (or his or her designee). Supplier shall not agree to provide such New Services to any CoreLogic Personnel or CoreLogic Affiliates without the prior written approval of the CoreLogic Relationship Manager (or his or her designee). If Supplier fails to comply with this Section 4.3(d), CoreLogic shall have the right (but not the obligation), in its sole discretion within a reasonable period of time after CoreLogic’s awareness of such failure, to terminate the contract under which such New Services were purchased by CoreLogic. In the event of such a termination, (A) Supplier shall promptly provide CoreLogic with *** CoreLogic or an Eligible Recipient with respect to any *** and (B) CoreLogic shall *** further obligation to *** to Supplier (other than ***) under such terminated contract, including any ***, if any, that are contemplated by such contract. |
| |
| (iii) | This Section 4.3(d) shall not apply with respect to a request for New Services by any CoreLogic Personnel who, with knowledge of the purpose of the provisions of this Section 4.3(d), seeks to circumvent the approval of the CoreLogic Relationship Manager (or his or her designee) with respect to such request for New Services as contemplated by this Section 4.3(d) so as to obtain *** from Supplier. |
| |
| 4.4 | Additional Work or Reprioritization. |
The CoreLogic Relationship Manager (or his or her designee) may identify new or additional work activities to be performed by Supplier (including work activities that would otherwise be treated as New Services) or reprioritize or reset the schedule for existing work activities to be performed by Supplier. With respect to such new or additional work activities, Supplier shall use commercially reasonable efforts to perform such work activities without impacting the established schedule for other tasks or the performance of Services in accordance with the Service Levels. If it is not possible to avoid such an impact or the activities require more than commercially reasonable efforts, Supplier shall notify CoreLogic of the anticipated impact and obtain its consent prior to proceeding with such work activities. Unless otherwise agreed, CoreLogic shall incur *** *** for the performance of such work activities by Supplier. CoreLogic, in its sole discretion, may forego or delay such work activities (in which case, Supplier shall have no obligation to perform such work activities) or temporarily or permanently adjust the work to be performed by Supplier, the schedules associated therewith or the Service Levels to permit the performance by Supplier of such work activities.
| |
| 4.5 | Right to In-Source or Use of Third Parties; Cooperation and Management. |
| |
| (a) | Right of Use. This Agreement shall not be construed as a requirements contract and shall not be interpreted to prevent any Eligible Recipient from obtaining from third parties (each, a “Third Party Contractor”), or providing to itself or any other Eligible Recipient, any New Services or, subject to the Charges provisions |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 8 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
set forth in the applicable Supplement, all of the Services or any other services. Nor shall anything in this Agreement be construed or interpreted as *** CoreLogic’s right or ability to *** or increase or decrease its demand for Services. Nor shall anything in this Agreement be construed or interpreted as *** CoreLogic’s right or ability to change Service volumes or *** any Service *** scope. To the extent CoreLogic adds or deletes Eligible Recipients or any Eligible Recipient increases or decreases its demand for Services or obtains Services from a Third Party Contractor or provides Services to itself or another Eligible Recipient, the amount to be paid to Supplier by CoreLogic will be equitably adjusted, including, if applicable in accordance with Schedule 4 or as otherwise specified in the applicable Supplement. Except as specifically provided in a Supplement and with a specific reference to this Section 4.5(a), CoreLogic will not be obligated to pay Termination Charges in connection with such adjustment.
| |
| (c) | Managed Third Parties. With respect to Third Party Contractors identified in a Supplement as “Managed Third Parties” and any substitutes or replacements for Third Party Contractors so identified by mutual agreement of the Parties (each, a “Managed Third Party”), Supplier shall: (i) manage the Managed Third Parties, including monitoring operational day-to-day service delivery, monitoring performance, escalating problems for resolution, and maintaining technical support relationships; (ii) as requested by CoreLogic, work with CoreLogic to manage new and existing contractual relationships between CoreLogic and Managed Third Parties; (iii) oversee Managed Third Party delivery of services and compliance with the service levels and the performance standards contained in CoreLogic’s agreement with the Managed Third Party; (iv) notify CoreLogic and the Managed Third Party of each Managed Third Party failure to perform in accordance with the performance standards or other terms and conditions contained in CoreLogic’s agreement with the Managed Third Party; (v) escalate Managed Third Party performance failures to Managed Third Party management as necessary to achieve timely resolution; (vi) monitor and manage the Managed Third Party’s efforts to remedy a failure of performance; (vii) communicate to CoreLogic the status of the Managed Third Party’s efforts to remedy a failure of performance; (viii) recommend retention, replacement, modification, or termination of the Managed Third Party based on the performance or cost benefits to CoreLogic as tracked by Supplier; and (ix) participate and assist in the *** (e.g., *** or ***) of such Managed Third Parties if CoreLogic requests that ***. |
As part of the Services and at no additional charge to CoreLogic, Supplier shall promptly correct any errors or inaccuracies ***. Without limiting Supplier’s obligations in Section 13.2(c), as part of the Services and at no additional charge to CoreLogic, Supplier shall promptly correct any errors or inaccuracies in or with respect to the information or data provided by Supplier in relation to the Services (including such data contained in Reports, or other contract deliverables delivered by Supplier).
Supplier shall fully cooperate with and work in good faith with CoreLogic, the other Eligible Recipients and Third Party Contractors as described in this Agreement or requested by CoreLogic and at no additional charge to CoreLogic. If and to the extent requested by CoreLogic, Supplier shall provide such cooperation by, among other things: (i) timely providing reasonable electronic and physical access to the business processes and associated Equipment, Materials and/or Systems to the extent necessary and appropriate for CoreLogic, the other Eligible Recipients *** to perform the work assigned to them; (ii) timely providing reasonably required access to Supplier Facilities; (iii) timely providing written requirements, standards, policies or other documentation for the business processes and associated Equipment, Materials or Systems procured, operated, supported or used by Supplier in connection with the Services; provided that, with respect Managed Services only, such documentation shall be only as necessary to integrate their services with the Services provided by Supplier; (iv) timely providing access to CoreLogic Data to the Eligible Recipients *** in the same manner and to the same extent access to such data is required to be provided by Supplier to CoreLogic; (v) timely providing cooperation and assistance in accordance with Section 20.8 to facilitate the orderly transfer of
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 9 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
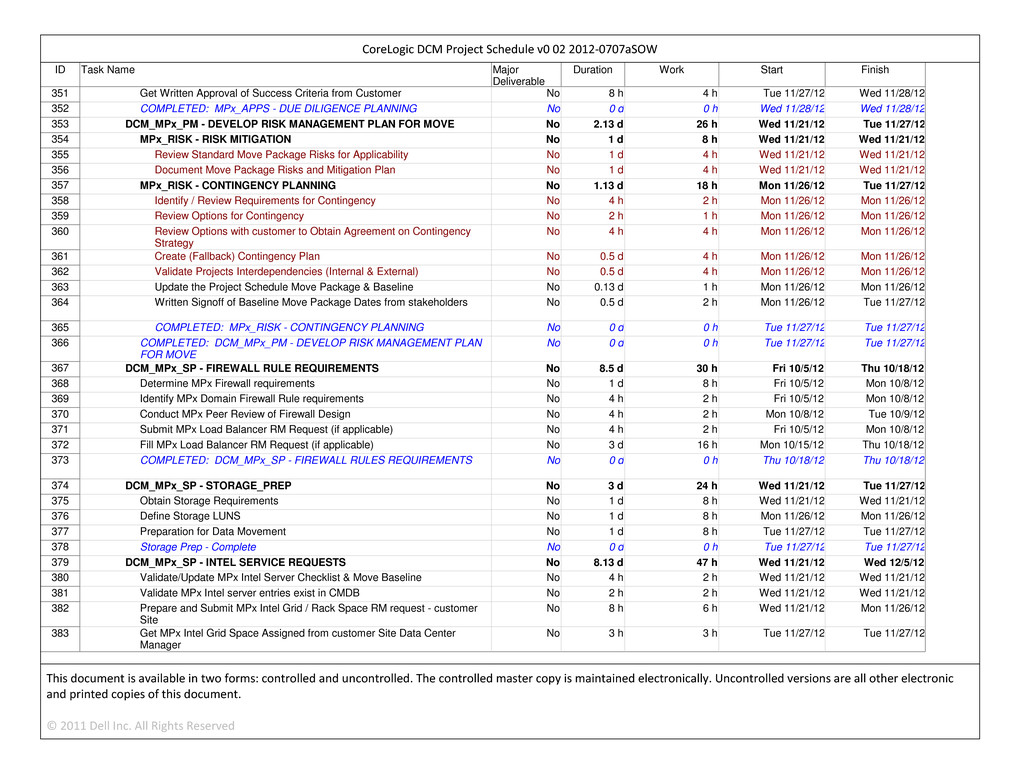
terminated Services from Supplier to CoreLogic, the other Eligible Recipients ***; (vi) ensuring that there is no degradation in the performance of the Services caused by the adjustments made by Supplier following such transfer of Services; (vii) establishing procedures and other arrangements with *** to ensure continuity of seamless service to CoreLogic (e.g., RACI charts, multi-supplier governance procedures); and (viii) any other cooperation or assistance reasonably necessary for CoreLogic, the other Eligible Recipients *** to perform the work in question. CoreLogic Personnel *** shall comply with Supplier’s reasonable security and confidentiality requirements, and shall, to the extent performing work on Materials, Equipment or Systems for which Supplier has operational responsibility, comply with Supplier’s reasonable standards, methodologies, and procedures, use commercially reasonable efforts to avoid adversely affecting Supplier’s ability to perform its obligations under this Agreement, and cooperate and work in good faith with Supplier. If requested by CoreLogic, Supplier shall enter into a mutually agreed joint governance and issue resolution document between Supplier *** who provide services similar or related to the Services to an Eligible Recipient.
| |
| 4.8 | Transformation Services. |
| |
| (a) | Transformation Services. Supplier shall perform the services (the “Transformation Services” or “Transformation”), described in any Transformation plan set forth in the applicable Supplement (the “Transformation Plan”) and any services not specifically described in the Transformation Plan that are an inherent, necessary or customary part of such services or required for the proper performance of such Transformation Plan. CoreLogic will perform or cause to be performed those tasks which are designated in the Transformation Plan to be the responsibility of CoreLogic, Eligible Recipients or Third Party Contractors in the Transformation Plan including causing Third Party Contractors to fully cooperate with and work in good faith with Supplier. Supplier agrees that the responsibilities of CoreLogic, as set forth in this Section 4.8(a), are not intended as contractual duties or obligations of CoreLogic giving rise to a claim of breach by Supplier, but rather as conditions precedent to the extent applicable to the related duties and obligations of Supplier under this Agreement for purposes of Section 10.2. |
| |
| (b) | Transformation Plan. For each Supplement that includes Transformation Services, a Transformation Plan will be attached as a Schedule to such Supplement. To the extent requested by CoreLogic, the Transformation Plan shall identify (i) the Transformation activities to be performed by Supplier and the significant components, subcomponents and any conditions precedent associated with each such activity, (ii) all Deliverables to be completed by Supplier, (iii) the date(s) by which each such activity or Deliverable is to be completed (the “Transformation Milestones”), (iv) the completion date for each Transformation Services task, (v) the contingency or risk mitigation strategies to be employed by Supplier in the event of disruption or delay, (vi) the Acceptance Criteria (and, if appropriate, description of applicable testing) to be applied by CoreLogic in evaluating Transformation Services Deliverables, (vii) any Transformation responsibilities to be performed or Transformation resources to be provided by CoreLogic, (viii) any related documents contemplated by this Agreement and/or required to effectuate the Transformation to be executed by the Parties and (ix) a detailed work plan identifying the specific Transformation activities to be performed by Supplier on a weekly basis during the Transformation Period. |
| |
| (c) | Detailed Transformation Plan. Supplier shall prepare and deliver to CoreLogic a more detailed version of the Transformation Plan for CoreLogic’s review, comment and approval within *** (***) *** after the Supplement Effective Date or such other period as is specified in the Supplement. The proposed detailed Transformation Plan shall describe in greater detail the specific Transformation activities to be performed by Supplier, but shall be consistent in all respects with the Transformation Plan attached to the applicable Supplement, including the activities, Deliverables, Transformation Milestones and Deliverable Credits described in such Transformation Plan. Supplier shall *** any questions or concerns CoreLogic may have as to any aspect of the proposed detailed Transformation Plan and incorporate any modifications, additions or deletions to such Transformation Plan requested by CoreLogic within *** (***) *** of receiving them from CoreLogic. The Parties shall reasonably cooperate to permit completion of the detailed Transformation Plan within *** (***) *** after the Supplement Effective Date unless another period is agreed upon by the Parties. The detailed Transformation Plan as approved by CoreLogic shall be deemed to be appended to and incorporated in the applicable Supplement. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 10 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (d) | Performance. Supplier shall perform the Transformation Services described in the Transformation Plan in accordance with the timetable and the Transformation Milestones set forth in the Transformation Plan. Supplier shall perform the Transformation Services in a manner that will not disrupt the business or operations of any of the Eligible Recipients or degrade the Services then being received by any of the Eligible Recipients, except as may be otherwise expressly provided in the Transformation Plan. Prior to undertaking any Transformation activity, Supplier shall discuss with CoreLogic all known *** material risks and shall not proceed with such activity until *** with the plans with regard to such risks (provided that neither Supplier’s disclosure of any such risks to CoreLogic, nor CoreLogic’s acquiescence in Supplier’s plans, shall operate or be construed as limiting Supplier’ responsibility under this Agreement). Subject to Section 4.8(f), Supplier shall identify and resolve, with CoreLogic’s reasonable assistance, any problems that may impede or delay the timely completion of each task in the Transformation Plan that is Supplier’s responsibility; and shall use commercially reasonable efforts to assist CoreLogic with the resolution of any problems that may impede or delay the timely completion of each task in the Transformation Plan that is CoreLogic’s responsibility. If new and unforeseen risks are discovered after final approval of the detailed Transformation Plan, the Parties shall work together in good faith to resolve the risks through governance, including, as applicable, through the Change Management Procedures; provided that, unless the Parties agree otherwise (which agreement either Party may withhold in its sole discretion), in no event shall this sentence be used to *** set forth ***. |
| |
| (e) | Reports. Supplier shall meet at least *** with CoreLogic to report on its progress in performing its responsibilities set forth in the Transformation Plan. Supplier also shall provide written reports to CoreLogic at least *** regarding such matters, and shall provide oral reports more frequently if reasonably requested by CoreLogic. Promptly, ***, after receiving any information indicating that Supplier may not perform its responsibilities or meet the timetable set forth in the Transformation Plan, Supplier shall notify CoreLogic in writing of the potential delays and shall identify for CoreLogic’s consideration and approval specific measures to address such delay and mitigate the risks associated therewith. |
| |
| (f) | Suspension or Delay of Transformation Activities. CoreLogic reserves the right, in its sole discretion, to suspend or delay the performance of the Transformation Services and/or the Transformation of all or any part of the Services. If CoreLogic elects to exercise such right and CoreLogic’s decision is based on Supplier’s failure to plan for or complete necessary activities related to a Transformation Milestone, or Supplier’s failure to perform its other obligations under the applicable Supplement or this Section 4.8 (including failure to meet a Transformation Milestone), CoreLogic shall ***. If CoreLogic’s decision is not based on Supplier’s failure to plan for or complete necessary activities related to a Transformation Milestone, or Supplier’s failure to perform its other obligations under the applicable Supplement or this Section 4.8 (including failure to meet a Transformation Milestone), CoreLogic shall reimburse Supplier for any additional costs (including stranded time for Supplier Personnel affected by such suspension or delay, at the applicable rates set forth in the Supplement) reasonably incurred by Supplier as a result of such decision (provided that Supplier notifies CoreLogic in advance of such costs, obtains CoreLogic’s approval prior to incurring such costs, and uses commercially reasonable efforts to minimize such costs). |
| |
| (g) | Failure to Meet Transformation Milestones. |
| |
| (i) | If Supplier fails to meet a Transformation Milestone, Supplier shall pay CoreLogic any Deliverable Credits specified in the applicable Supplement for such Transformation Milestone. |
| |
| (ii) | Neither the Transformation Services nor the activities and Deliverables associated with individual Transformation Milestones will be deemed complete until Acceptance of such activities and Deliverables. |
| |
| (h) | Termination for Cause. In addition to any other termination right CoreLogic may have under this Agreement, CoreLogic may terminate the applicable Supplement *** (with respect to ***) for cause if (i) Supplier materially breaches its obligations with respect to the provision of Transformation Services and fails to cure such breach within *** (***) *** after its receipt of notice, or (ii) Supplier fails to meet |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 11 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
a Transformation Milestone and such failure constitutes a material breach of the applicable Supplement and Supplier fails to cure such breach within *** (***) *** after its receipt of notice. In all such events, subject to Section 18.2, CoreLogic may recover the damages suffered by the Eligible Recipients in connection with such a termination, provided that, if such termination is based on Supplier’s failure to meet a Transformation Milestone, Supplier shall be entitled to set-off against such damages any Deliverable Credits Supplier has paid for the failure to meet such Transformation Milestone.
| |
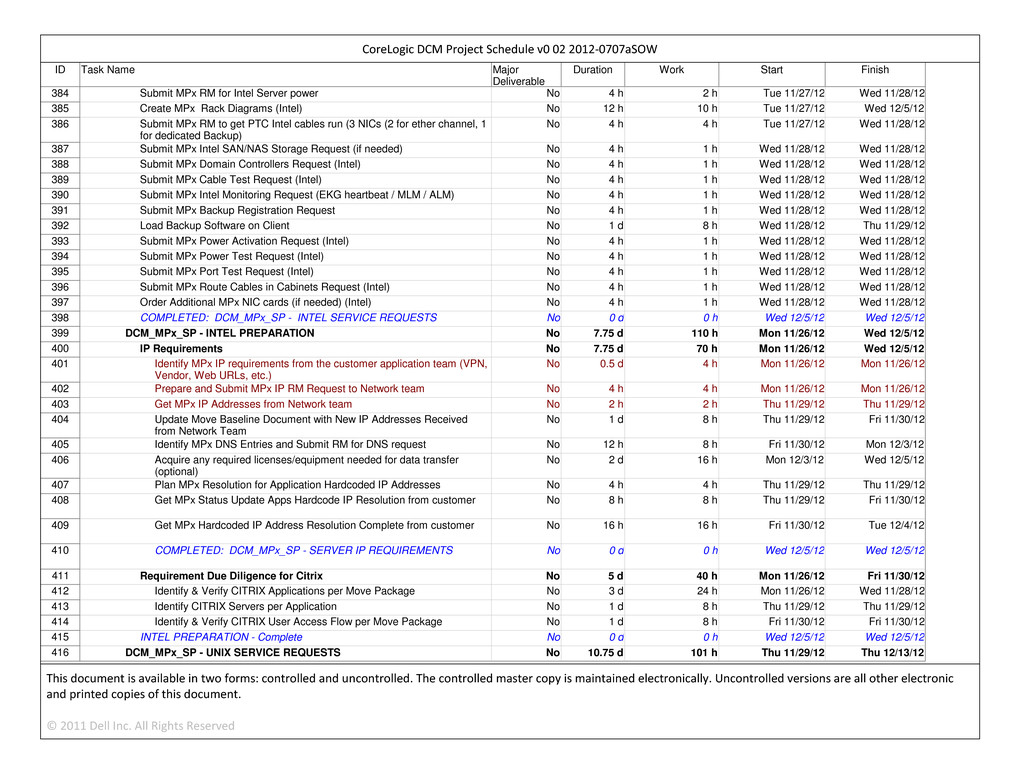
| 5.1 | Administrative Responsibility. |
Each Party shall undertake all administrative activities necessary to obtain the Required Consents for which such Party is financially responsible, as such financial responsibility is designated in Section 5.2. At either Party’s request, the other Party will cooperate with the requesting Party in obtaining the applicable Required Consents by executing appropriate written communications approved by the non-requesting Party and other documents prepared or provided by the requesting Party. The Parties shall cooperate in minimizing or eliminating any costs associated with obtaining Required Consents.
| |
| 5.2 | Financial Responsibility. |
Financial responsibility for obtaining Required Consents shall be as follows: (a) subject to Sections 5.2(b) through (d) below, each Party shall bear the costs of obtaining Required Consents for its contracts and licenses (including those related to volume changes for existing Services), including any termination and re-licensing fees or expenses associated with third-party licenses or contracts as to which such Party is unable to obtain such Required Consents; (b) Supplier shall bear Required Consent costs associated with CoreLogic’s contracts and licenses to the extent Supplier’s performance of the Services requires use or access by a number of Supplier Personnel in excess of what CoreLogic, an Eligible Recipient *** used or accessed as of the applicable Commencement Date under the Supplement (other than as a result of volume changes for existing Services), or use *** than that set forth in the applicable Supplement as of the Commencement Date; (c) Required Consents costs associated with New Services will be handled in a manner to be mutually agreed by the Parties; and (d) Supplier shall undertake all administrative activities and bear the financial responsibility necessary to obtain the Required Consents listed in subsections (iv) and (v) of the definition of Required Consents.
| |
| 5.3 | Contingent Arrangements. |
The following alternative approaches shall apply in the event CoreLogic is unable to obtain the corresponding Required Consent despite using commercially reasonable efforts. If CoreLogic is unable to obtain a Required Consent with respect to CoreLogic’s licensed Third Party Software, Supplier shall, at CoreLogic’s expense and with CoreLogic’s consent: (a) replace the CoreLogic license for such Third Party Software with a Supplier license; (b) replace such Third Party Software with other Software offering equivalent features and functionality; or (c) assist CoreLogic in securing the right for Supplier to manage the CoreLogic licensed Third Party Software on behalf of CoreLogic. Without limiting the foregoing, if such alternative approaches are required, the Parties shall equitably adjust the terms and the prices specified in this Agreement to reflect any additional costs being incurred by CoreLogic or Supplier and any Services not being received by CoreLogic and the Eligible Recipients.
| |
| 6. | FACILITIES, SOFTWARE, EQUIPMENT, CONTRACTS AND ASSETS ASSOCIATED WITH THE PROVISION OF SERVICES. |
| |
| (a) | Service Facilities. Supplier and its Affiliates and Subcontractors will supply or provide the Services only at or from (i) the CoreLogic Facilities and Supplier Facilities identified in Schedule 7 or the applicable Supplement, (ii) any other service locations approved in advance by CoreLogic, or (iii) with respect to |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 12 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Managed Services, such other locations as approved by CoreLogic in accordance with the immediately following sentence. With respect to clause (iii), Supplier shall obtain CoreLogic’s prior approval, which CoreLogic may withhold in its reasonable discretion, for any proposed relocation by Supplier, its Affiliates or Subcontractors of the provision of a Service to a new or different Supplier Facility. For purposes of the preceding sentence, the following reasons for withholding approval shall be deemed reasonable: (1) such location may have a material adverse impact on the Services or the business or reputation of CoreLogic or any Eligible Recipient, (2) events or conditions in such location interfere with CoreLogic’s or any Eligible Recipient’s ability to conduct its business or to exercise and enforce its rights under this Agreement, or to protect its assets and rights generally or to remain in compliance with applicable Laws, (3) CoreLogic’s compliance function has determined that such location is not an acceptable location for the conduct of CoreLogic’s business because such location would pose an adverse impact on the compliance obligations of CoreLogic or an Eligible Recipient, or (4) constraints in the customer agreements of CoreLogic or an Eligible Recipient. Supplier shall obtain CoreLogic’s prior approval for any proposed relocation by Supplier, its Affiliates or Subcontractors of the provision of a Service (e.g., Services in a Functional Service Area or sub-Functional Service Area) to a new or different Supplier Facility. *** shall be *** for *** or *** resulting from any ***, including any costs or expenses incurred or experienced *** as a result of such relocation (***). Without limiting *** obligation to *** contemplated by the immediately preceding sentence, CoreLogic will, to the extent it is aware of any *** at the time of its approval of the Supplier Facility, notify Supplier of such ***. Supplier will store and process CoreLogic Data only in (A) the locations identified in Schedule 7 or the applicable Supplement or (B) any other service locations approved (pursuant to this Section 6.1(a)) in writing in advance by CoreLogic. Supplier shall not transfer CoreLogic Data to any other locations without the direct authorization in writing by CoreLogic.
| |
| (b) | Supplier’s Responsibilities. Except as provided in Sections 6.1(a), 6.2 and 6.5(e), Supplier shall be responsible for providing all furniture, fixtures, space and other facilities required to perform the Services and all upgrades, improvements, replacements and additions to such furniture, fixtures, space and facilities required to perform the Services. Supplier’s responsibilities with respect to provision of Equipment are set forth in Sections 4.1(c) and 6.5. |
| |
| (a) | Access and Use. CoreLogic shall provide Supplier with access to and the use of the CoreLogic Facilities (or equivalent space) identified in Schedule 7 or the applicable Supplement for the periods specified therein solely as necessary for Supplier to perform its obligations under this Agreement. If any given Supplement provides that CoreLogic will make office space or storage space at any CoreLogic Facilities available to Supplier, then CoreLogic will provide such space and any reasonable and customary related office support services (such as parking privileges, access cards or badges, cafeteria services, and furniture) to Supplier, as such level of support services may be modified from time to time, but only to the extent CoreLogic provides such items to its own employees at such CoreLogic Facility. Supplier’s use of any CoreLogic Facility does not constitute or create a leasehold interest, and CoreLogic may, by notice to Supplier from time to time, require that Supplier re-locate to other reasonably equivalent space. THE CORELOGIC FACILITIES ARE PROVIDED BY CORELOGIC TO SUPPLIER ON AN AS-IS, WHERE-IS BASIS. CORELOGIC EXPRESSLY DISCLAIMS ANY WARRANTIES, EXPRESS OR IMPLIED, AS TO THE CORELOGIC FACILITIES, OR THEIR CONDITION OR SUITABILITY FOR USE BY SUPPLIER. |
| |
| (b) | CoreLogic Rules. In performing the Services, Supplier shall observe and comply with (i) all CoreLogic policies, guidelines, rules, and regulations applicable to CoreLogic Facilities or the access and use of CoreLogic Systems, and (ii) those policies, guidelines, rules and regulations set forth on Schedule 8, as the same may be updated from time to time, and those generally applicable policies communicated to Supplier or Supplier Personnel by the means generally used by CoreLogic to disseminate such information to its employees or contractors (collectively, “CoreLogic Rules”). Supplier shall be responsible for the promulgation and distribution of CoreLogic Rules to Supplier Personnel. In addition, Supplier and |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 13 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Supplier Personnel shall be responsible for familiarizing themselves with the premises and operations at each CoreLogic Facility at, to or from which Services are rendered and the CoreLogic Rules applicable to each such CoreLogic Facility. Additions or modifications to the CoreLogic Rules may be (i) communicated orally by an Eligible Recipient directly to Supplier and Supplier Personnel, (ii) disclosed to Supplier and Supplier Personnel in writing, or (iii) conspicuously posted at a CoreLogic Facility, electronically posted or otherwise communicated by means generally used by CoreLogic to disseminate such information to its employees or contractors. Supplier and Supplier Personnel shall observe and comply with such additional or modified CoreLogic Rules. At CoreLogic’s request, Supplier Personnel shall participate in CoreLogic provided training programs regarding CoreLogic Rules.
| |
| 6.3 | Supplier’s Responsibilities Regarding CoreLogic’s Network. |
| |
| (a) | To the extent any Equipment used by Supplier or Supplier Personnel is, with CoreLogic’s approval, to be connected to any network operated by or on behalf of an Eligible Recipient or a customer of an Eligible Recipient (a “CoreLogic Network”), such Equipment (and all Software installed thereon) shall be (i) subject to review and approval in advance by CoreLogic (Supplier shall cooperate with CoreLogic in the testing, evaluation and approval of such Equipment), (ii) in strict compliance with the then-current CoreLogic Rules and CoreLogic Standards that are directly applicable to the CoreLogic Network, unless and to the extent deviations are approved in advance by CoreLogic. With respect to such Equipment for which Supplier has operational responsibility under an applicable Supplement, Supplier shall not install or permit the installation of any other software on such Equipment by any individual (whether or not a Supplier Personnel) without CoreLogic’s prior approval, and with respect to all other such Equipment, Supplier shall not install or permit the installation by Supplier Personnel of any other software on such Equipment. Supplier will use each CoreLogic Network for the sole and limited purpose of and to the limited extent necessary for performing the Services. Supplier shall not access, or attempt to access, any part of any CoreLogic Network that Supplier is not authorized to access, including any part of the CoreLogic Network that is not reasonably necessary for and pertinent to the performing the Services. |
| |
| (b) | Except as otherwise agreed in a Supplement or expressly agreed in writing by CoreLogic, (i) to the extent performance of the Services involves the access or use of the portions of CoreLogic Data that constitute *** thereof, such access or use shall be performed on or utilize *** designated by *** and (ii) all CoreLogic Owned Developed Materials (for clarity, this shall not include Supplier Owned Materials that are joined with such CoreLogic Owned Developed Materials) will be created on *** through such ***. Notwithstanding clause (i) above, CoreLogic hereby agrees that Supplier’s use of *** that do not require access or use of such portions of the CoreLogic Data may be performed on or outside of the ***. |
| |
| (c) | Supplier shall access a CoreLogic Network only using one or more Access Codes provided by CoreLogic, and shall ensure that no one other than the Supplier Personnel who are authorized by CoreLogic to use an Access Code (by name, title, job function or otherwise) use such Access Code to access the CoreLogic Network. Supplier shall inform CoreLogic of the name(s) of each of the Supplier Personnel that Supplier desires CoreLogic to authorize to access any CoreLogic Network. Supplier shall notify CoreLogic promptly if any of the Supplier Personnel who has been granted an Access Code has been (i) terminated from employment or otherwise is no longer one of the Supplier Personnel, or (ii) reassigned and no longer requires access to the CoreLogic Network. Access Codes will be deemed Confidential Information of CoreLogic. |
| |
| (d) | Supplier acknowledges and agrees that, to the extent permitted by applicable Law, CoreLogic has the right to monitor, review, record and investigate all uses of the CoreLogic Network and CoreLogic Systems by Supplier, including all email or other communications sent to, from, or through the CoreLogic Network, regardless of the content of such communications, and Supplier hereby consents to such reviewing, monitoring, recording and investigation. Supplier acknowledges and agrees that it does not have any expectation of privacy with respect to any personal information or communications made by or to it through the CoreLogic Network. Notwithstanding the foregoing, the use by Supplier or its Subcontractors of its virtual private network (VPN) connection while at a CoreLogic Facility, even if such VPN connection |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 14 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
makes use of an internet connection provided by the CoreLogic Network, shall not constitute a communication made by or through the CoreLogic Network for purposes of this Section.
| |
| 6.4 | CoreLogic Access to Supplier Facilities. |
During the Term, subject to CoreLogic’s compliance with Supplier’s reasonable security guidelines and processes, Supplier shall provide to CoreLogic, at no additional charge, reasonable access to reasonable work/conference space at Supplier Facilities, in each case for the exercise of CoreLogic’s rights or the conduct of activities associated with this Agreement. In addition, at CoreLogic’s request, Supplier shall provide reasonable access to and use of such Supplier Facilities by CoreLogic, customers of CoreLogic or an Eligible Recipient, the other Eligible Recipients or Third Party Contractors as and to the extent provided in Section 4.5 and Section 9.10.
| |
| 6.5 | Software, Equipment and Third Party Contracts. |
| |
| (a) | Financial Responsibility. To the extent a Party is financially responsible under the applicable Supplement for certain Third Party Software licenses, Equipment Leases or Third Party Contracts, such Party shall (i) pay all amounts becoming due under such licenses, leases or contracts, *** for periods during which such Party is financially responsible; (ii) where Section 11.5(a) is applicable for a Supplement, refund to CoreLogic any CoreLogic prepayment of such amounts in accordance with Section 11.5(a); (iii) pay all modification, termination, cancellation, late payment, renewal or other fees, penalties, charges, interest or other expenses not caused by the other Party relating to periods during which such Party is financially responsible; (iv) except as provided in Article 5, pay *** associated with the transfer of such licenses, leases and contracts, including all taxes associated with such transfer; and (v) be responsible for *** in such Party’s performance under such licenses, leases and contracts for periods during which such Party is financially responsible. |
| |
| (b) | Operational Responsibility. To the extent Supplier is operationally responsible under the applicable Supplement for certain Software, Equipment, Equipment Leases or related Third Party Contracts, Supplier shall be responsible, to the extent relevant to the Services, for (i) the evaluation, procurement, testing, installation, use, support, management, administration, operation and maintenance of such Software, Equipment, Equipment Leases and Third Party Contracts and new, substitute or replacement items (including Upgrades, enhancements, and new versions or releases of Software); (ii) the ***, availability, reliability, compatibility and interoperability of such Software, Equipment, Equipment Leases and Third Party Contracts, each in accordance with this Agreement; (iii) the compliance with and performance of all operational, administrative and non-financial contractual obligations specified in such licenses, leases and contracts; (iv) the administration and exercise as appropriate of all rights available under such licenses, leases and contracts; and (v) the payment of any fees, penalties, charges, interest or other expenses under such licenses, leases and contracts resulting from Supplier’s failure to comply with or perform its obligations under this Section 6.5(b) (except to the extent that such failure results from a breach by CoreLogic of its obligations under this Agreement). |
| |
| (c) | Rights Upon Expiration/Termination. With respect to all Third Party Software licenses, Equipment Leases and Third Party Contracts for which Supplier is responsible to provide under the applicable Supplement (other than the tools and Equipment, or replacement tools and Equipment) for which no CoreLogic license or use rights are contemplated pursuant to Sections 14.6 and 20.8 or as set forth in such Supplement), Supplier shall use commercially reasonable efforts to (i) obtain for CoreLogic, the other Eligible Recipients and/or their designee(s) (including successor supplier(s)) the license, sublicense, assignment and other rights specified in Sections 14.6 and 20.8, (ii) ensure that the granting of such license, sublicense, assignment and other rights is not subject to subsequent third party approval or the *** by CoreLogic, the other Eligible Recipients and/or their designee(s) of *** (other than ***), and (iii) ensure that the terms, conditions and prices applicable to CoreLogic, the other Eligible Recipients and/or their designee(s) following expiration or termination are no less favorable than those otherwise applicable to Supplier (***), and at least sufficient for the continuation of the activities comprising the |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 15 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Services. If Supplier is unable to obtain any such rights and assurances, it shall notify CoreLogic in advance and shall *** such Third Party Software license, Equipment Lease or Third Party Contract without *** (and *** such ***, *** such license, lease or contract shall result in the consequences contemplated by ***).
| |
| (d) | Evaluation of Third Party Software, Equipment. In addition to its obligations under Sections 6.5(a) and (b) and in order to facilitate CoreLogic’s control of architecture, standards and plans pursuant to Section 9.5, Supplier shall use commercially reasonable efforts to evaluate any Third Party Software and Equipment selected by or for an Eligible Recipient or their customers to determine whether such Software and Equipment will *** their environment or ability to interface with and use the Software, Equipment and Systems and/or Supplier’s ability to provide the Services. Supplier shall complete and report the results of such evaluation to CoreLogic within *** (***) *** of its receipt of CoreLogic’s request where it would be objectively reasonable to complete such evaluation within such period (and where not, as soon as reasonably possible, taking into account the scope of such evaluation); provided that Supplier shall use commercially reasonable efforts to respond more quickly in the case of a pressing business need or an emergency situation. |
| |
| (e) | CoreLogic Provided Equipment. |
| |
| (i) | CoreLogic shall provide Supplier with the use of the CoreLogic owned and/or leased Equipment identified in the applicable Supplement as “CoreLogic Provided Equipment” (collectively, the “CoreLogic Provided Equipment”) for the periods specified therein solely for and in connection with the performance of the Services. Upon the expiration of the period specified in the applicable Supplement for each item of CoreLogic Provided Equipment (or when such CoreLogic Provided Equipment is no longer required by Supplier for the performance of the Services), Supplier shall promptly return such CoreLogic Provided Equipment to CoreLogic, the other Eligible Recipients and/or their designee(s) in condition at least as good as the condition thereof on the date initially provided to Supplier, ordinary wear and tear excepted. THE CORELOGIC PROVIDED EQUIPMENT IS PROVIDED BY CORELOGIC TO SUPPLIER ON AN AS-IS, WHERE-IS BASIS. CORELOGIC EXPRESSLY DISCLAIMS ANY WARRANTIES, EXPRESS OR IMPLIED, AS TO THE CORELOGIC PROVIDED EQUIPMENT, OR ITS CONDITION OR SUITABILITY FOR USE BY SUPPLIER TO PROVIDE THE SERVICES, INCLUDING WARRANTIES OF NON-INFRINGEMENT, MERCHANTABILITY, OR FITNESS FOR A PARTICULAR PURPOSE. |
| |
| (ii) | Surplus CoreLogic Provided Equipment. Where performance of the Services requires Supplier to dispose of certain CoreLogic Provided Equipment, Supplier shall, at its cost, dispose of any such surplus CoreLogic Provided Equipment in accordance with applicable Laws, and Supplier shall pay CoreLogic any money received from disposal of such Equipment, after deducting the reasonable cost incurred by Supplier in disposing of such Equipment. Supplier shall obtain CoreLogic’s consent to dispose of any surplus CoreLogic Provided Equipment before disposing of such Equipment. Supplier shall maintain reasonable documentation regarding the disposition of such surplus Equipment, including the costs of and revenues from disposal, and shall make such documentation available to CoreLogic upon CoreLogic’s request. Prior to disposing of any such surplus Equipment, Supplier shall certify to CoreLogic that all data and information previously stored on or in such surplus CoreLogic Provided Equipment has been *** from such Equipment in accordance with the then current *** standard (as of the Effective Date, the Department of ***) and any other standards set forth in the applicable Supplement or, if no such standards are specified, standards of *** providers of similar services. |
| |
| 6.6 | Assignment of Third Party Contracts. |
| |
| (a) | Assignment and Assumption. Subject to the responsible Party obtaining any Required Consents, on and as of the Commencement Date (or, if later, the date on which Supplier assumes responsibility for the Services in question in accordance with the Transition Plan), CoreLogic shall assign to Supplier, and |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 16 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Supplier shall assume and agree to perform all obligations related to, Third Party Contracts for which Supplier is financially responsible under this Agreement or the applicable Supplement, and which are identified as “to be assigned” to Supplier in the applicable Supplement; provided, however, that such assignment shall not include any assignment or transfer of any intellectual property rights in Materials developed under such Third Party Contracts prior to the date of such assignment and, as between the Parties, CoreLogic hereby expressly reserves and retains such intellectual property rights. The Parties shall execute and deliver a mutually satisfactory assignment and assumption agreement evidencing any such assignments. Notwithstanding the foregoing, CoreLogic shall remain responsible for all payment and other obligations attributable to any period prior to the effective date of assignment of the Third Party Contract.
| |
| (b) | Items Not Assignable by Commencement Date. With respect to any Software licenses, Equipment Leases or other Third Party Contracts that cannot, as of the Commencement Date (or, if later, the date on which Supplier assumes responsibility for the Services in question in accordance with the Transition Plan), be assigned to Supplier without breaching their terms or otherwise adversely affecting the rights or obligations of an Eligible Recipient thereunder, the performance obligations shall be deemed to be subcontracted or delegated to Supplier to the extent permitted under such Third Party Contract until any Required Consent, notice or other prerequisite to assignment can be obtained, given or satisfied by Supplier. It is understood that, from and after the Commencement Date (or, if later, the date on which Supplier assumes responsibility for the Services in question in accordance with the Transition Plan), Supplier, as a subcontractor or delegate under such Third Party Contract shall be financially and operationally responsible for such Third Party Contract as the Eligible Recipient’s agent. The responsible Party shall use all commercially reasonable efforts to satisfy the consent, notice or other prerequisites to assignment and, upon such Party doing so, the Third Party Contract shall immediately be assigned and transferred to and assumed by Supplier. |
| |
| (c) | Non-Assignable Items. If, after the responsible Party has used all commercially reasonable efforts and after the passage of a reasonable period of time, a Third Party Contract cannot be assigned without breaching its terms or otherwise adversely affecting the rights or obligations of an Eligible Recipient thereunder, the Parties shall take all actions and execute and deliver all documents as may be necessary to cause the Parties to realize the practical effects of the allocation of responsibilities intended to be effected by this Agreement. |
| |
| (d) | Modification and Substitution. Notwithstanding anything to the contrary herein, Supplier shall not terminate, shorten or modify without CoreLogic’s prior written consent any license for Third Party Software either created exclusively for the Eligible Recipients or their customers or otherwise not commercially available. Supplier shall reimburse the Eligible Recipient(s) for any termination charges, cancellation charges or other amounts paid by them at Supplier’s direction in connection with obtaining any such modification. Supplier may terminate, shorten, modify or extend the Third Party Contracts assigned to Supplier and for which Supplier is financially responsible and may substitute or change suppliers relating to goods or services covered thereby; provided that, except as otherwise disclosed by Supplier and agreed to by CoreLogic, such change(s) (i) shall not constitute a breach of any obligation of the Eligible Recipients under such Third Party Contracts; (ii) shall not result in additional financial obligations, financial or operational risk or Losses to the Eligible Recipients; (iii) shall not result in any increase to the Eligible Recipients in the cost of receiving the Services; and (iv) shall not provide for less favorable terms, conditions or prices for any Eligible Recipients and/or their respective designee(s) following the expiration or termination of the Term or any applicable Service than would otherwise be applicable to Supplier (except for terms, conditions or prices available to Supplier because of its volume purchases), unless CoreLogic has otherwise agreed that such Third Party Contract is not assumable. |
Each Party shall promptly, and in any case *** (***) *** inform the other Party in writing of any breach of, or misuse or fraud in connection with, any Third Party Contract, Equipment Lease or Third Party Software
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 17 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
license used in connection with the Services of which it becomes aware and shall cooperate with the other Party to prevent or stay any such breach, misuse or fraud.
7. SERVICE LEVELS.
| |
| 7.1 | Service Levels and Other Performance Standards. |
Beginning on the Commencement Date (or, if later, the date specified in the applicable Supplement), Supplier shall perform the Services so as to meet or exceed the performance standards designated as “Service Levels” in the applicable Supplement (the “Service Levels”). For matters not covered by the Service Levels set forth in the applicable Supplement, Supplier shall perform the Services at levels of accuracy, quality, completeness, timeliness, responsiveness and resource efficiency that are *** the documented or otherwise verifiable levels received by the Eligible Recipients during the *** (***) *** prior to the Commencement Date, and at levels that are equal to or higher than the accepted standards of *** providers of similar services. The obligations in the preceding sentence shall not be construed to alter or supersede any Service Level set forth in the applicable Supplement.
| |
| 7.2 | Multiple Service Levels. |
If more than one Service Level applies to any particular obligation of Supplier, Supplier shall perform in accordance with the most stringent of such Service Levels.
| |
| 7.3 | Service Level Credits. |
Supplier recognizes that CoreLogic is paying Supplier to deliver certain Services at specified Service Levels. If Supplier fails to meet any Service Levels, then, in addition to other remedies available to CoreLogic, Supplier shall pay or credit to CoreLogic the performance credit amounts as calculated in accordance with Schedule 3 (the “Service Level Credits”) in recognition of the diminished value of the Services resulting from Supplier’s failure to meet the agreed upon level of performance, and not as a penalty. Under no circumstances shall the imposition of Service Level Credits be construed as CoreLogic’s sole or exclusive remedy for any failure to meet the Service Levels. However, if CoreLogic recovers monetary damages from Supplier as a result of Supplier’s failure to meet a Service Level, Supplier shall be entitled to set-off against such damages any Service Level Credits paid for the failure giving rise to such recovery.
Supplier recognizes that CoreLogic is paying Supplier to provide certain Critical Deliverables by the time and in the manner set forth in the applicable Supplement. If Supplier fails to meet its obligations with respect to Critical Deliverables, then, in addition to other remedies available to CoreLogic, Supplier shall pay or credit to CoreLogic the Deliverable Credits specified in the applicable Supplement or established as part of a project or action plan approval process on a case-by-case basis in recognition of the diminished value of the Services resulting from Supplier’s failure to meet the agreed upon level of performance, and not as a penalty. If CoreLogic recovers monetary damages from Supplier as a result of Supplier’s failure to meet its obligations with respect to one or more Critical Deliverables, Supplier shall be entitled to set-off against such damages any Deliverable Credits paid for the failure(s) giving rise to such recovery.
8. SUPPLIER PERSONNEL.
| |
| 8.1 | Personnel Transfer. Supplier’s obligations with respect to Affected Employees and Transitioned Employees are set forth in Schedule 5 and the applicable Supplement. |
| |
| 8.2 | Key Supplier Personnel and Knowledge Transfer Personnel. |
| |
| (a) | Approval of Key Supplier Personnel. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 18 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (i) | Supplier shall fill the positions specified as “Key Supplier Personnel” positions in the applicable Supplement with Supplier Personnel approved by CoreLogic in accordance with this Section 8.2. Supplier shall identify and obtain CoreLogic’s approval of the initial Key Supplier Personnel prior to the Commencement Date. |
| |
| (ii) | Before assigning an individual to act as a Key Supplier Personnel, whether as an initial or subsequent assignment, Supplier shall notify CoreLogic of the proposed assignment, introduce the individual to appropriate CoreLogic representatives, permit CoreLogic representatives to ***, and provide CoreLogic with a resume and any other information about the individual reasonably requested by CoreLogic. If CoreLogic in good faith objects to the proposed assignment, the Parties shall attempt to resolve CoreLogic’s concerns on a mutually agreeable basis. If the Parties are not able to resolve CoreLogic’s concerns within *** (***) ***, or as otherwise agreed, Supplier shall propose another individual of suitable ability and qualifications. |
| |
| (iii) | Upon ninety (90) days prior notice, CoreLogic may from time to time change the positions designated as Key Supplier Personnel under this Agreement with Supplier’s approval, which shall not be unreasonably withheld. |
| |
| (b) | Continuity of Key Supplier Personnel. Supplier shall cause each of the Key Supplier Personnel to devote *** (***) *** to the provision of Services, at a minimum, unless a different minimum period is specified in the applicable Supplement. Supplier shall not transfer, reassign or remove any of the Key Supplier Personnel (except as a result of voluntary resignation, involuntary termination for cause, illness, disability or death) or announce its intention to do so during the specified period without CoreLogic’s prior approval, which CoreLogic may withhold in its reasonable discretion based on its own self interest. In the event of the voluntary resignation, involuntary termination for cause, illness, disability or death of any of its Key Supplier Personnel during or after the specified period, Supplier shall (i) give CoreLogic as much notice as reasonably possible of such development, and (ii) expeditiously identify and *** a suitable replacement. In addition, unless and to the extent a Key Supplier Personnel position ceases to be so designated after a defined period, even after the minimum period specified above, Supplier shall not transfer, reassign or remove any of the Key Supplier Personnel unless and until Supplier has (1) given CoreLogic reasonable prior notice, (2) identified and *** a suitable replacement in accordance with this Section 8.2 at least thirty (30) days prior to the effective date of such transfer, reassignment or removal, (3) demonstrated to CoreLogic’s reasonable satisfaction that such transfer, reassignment or removal will not have an adverse impact on Supplier’s performance of its obligations under this Agreement, and (4) completed any and all necessary knowledge transfer between the departing Key Supplier Personnel and his or her CoreLogic-approved replacement. Unless otherwise agreed, Supplier shall not transfer, reassign or remove more than *** (***) Key Supplier Personnel in any *** (***) *** period. |
| |
| (c) | Continuity of Knowledge Transfer Personnel. Except as expressly agreed otherwise in an applicable Supplement, Supplier shall cause each of the Knowledge Transfer Personnel to devote full time and effort to the provision of Services under this Agreement during the *** (***) *** period immediately following his or her Employment Effective Date unless a different minimum period is specified in the applicable Supplement. Supplier shall not transfer, reassign or remove any of the Knowledge Transfer Personnel (except as a result of voluntary resignation, involuntary termination for cause, illness, disability or death or as a result of the termination or elimination by CoreLogic of the Services they provide) during the specified period without CoreLogic’s prior approval, which CoreLogic may withhold in its sole discretion. In the event of the voluntary resignation, involuntary termination for cause, illness, disability or death of one of its Knowledge Transfer Personnel during the specified period, Supplier shall (i) give CoreLogic as much notice as reasonably possible of such development and (ii) expeditiously identify and obtain CoreLogic’s approval of a suitable replacement. |
| |
| (d) | Retention and Succession. Supplier shall implement and maintain a retention strategy designed to retain Key Supplier Personnel and Knowledge Transfer Personnel on the CoreLogic account for the prescribed period. Supplier shall also maintain active succession plans for each of the Key Supplier Personnel and |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 19 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Knowledge Transfer Personnel positions and shall provide such succession plans to CoreLogic for its review upon CoreLogic’s request.
Supplier shall designate a “Customer Executive” for this CoreLogic engagement. The Customer Executive shall (i) be one of the Key Supplier Personnel; (ii) be a full time employee of Supplier; (iii) devote his or her full time and effort to managing the Services; (iv) remain in this position for a minimum period of *** (***) *** from the initial assignment (except as a result of voluntary resignation, involuntary termination for cause, illness, disability, or death); (v) serve as the single point of accountability for the Services; (vi) be the single point of contact to whom all CoreLogic communications concerning this Agreement may be addressed; (vii) have authority to act on behalf of Supplier in all day-to-day matters pertaining to this Agreement; (viii) have day-to-day responsibility for service delivery, billing and relationship management; and (ix) have day-to-day responsibility for CoreLogic satisfaction and Service Levels attainment.
| |
| 8.4 | Supplier Personnel Are Not CoreLogic Employees. |
Nothing in this Agreement shall operate or be construed as making CoreLogic (or the other Eligible Recipients) and Supplier partners, joint venturers, principals, joint employers, agents or employees of or with the other. No officer, director, employee, agent, Affiliate, contractor or subcontractor retained by Supplier to perform work on CoreLogic’s behalf hereunder shall be deemed to be an officer, director, employee, agent, Affiliate, contractor or subcontractor of the Eligible Recipients for any purpose. Neither CoreLogic nor the other Eligible Recipients has the right, power, authority or duty to supervise or direct the activities of the Supplier Personnel or to compensate such Supplier Personnel for any work performed by them pursuant to this Agreement. Supplier, and not the Eligible Recipients, shall be responsible and liable for the acts and omissions of Supplier Personnel, including acts and omissions constituting negligence, willful misconduct and/or fraud. Supplier shall be solely responsible for the payment of compensation (including provision for employment taxes, federal, state and local income taxes, workers compensation and any similar taxes) associated with the employment of, or contracting with, Supplier Personnel. Supplier shall also be solely responsible for obtaining and maintaining all requisite work permits, visas and any other documentation for Supplier Personnel.
| |
| 8.5 | Replacement, Qualifications, and Retention of Supplier Personnel. |
| |
| (a) | Sufficiency and Suitability of Personnel. Supplier shall assign (or cause to be assigned) sufficient Supplier Personnel to provide the Services in accordance with this Agreement and all such Supplier Personnel shall possess suitable competence, ability, qualifications, education and training for the Services they are to perform and are performing. |
| |
| (b) | Requested Replacement. If CoreLogic determines in good faith and not for an unlawful purpose that the continued assignment to CoreLogic of any individual Supplier Personnel (including Key Supplier Personnel) is not in the best interests of the Eligible Recipients, then CoreLogic shall give Supplier notice to that effect requesting that such Supplier Personnel be replaced. Supplier shall, as soon as possible, permanently remove and replace such Supplier Personnel with an individual of suitable ability and qualifications. In such event, CoreLogic shall not be obligated to pay any Charges or other fees relating to the replacement of such Supplier Personnel, including any training or other knowledge transfer activities or overlaps in periods of employment. Nothing in this provision shall operate or be construed to limit Supplier’s responsibility for the acts or omissions of the Supplier Personnel, or be construed as joint employment. |
| |
| (c) | Turnover Rate and Data. Supplier shall use commercially reasonable efforts to maintain the turnover rate of Supplier Personnel at a level comparable to or better than *** for *** service providers in the applicable country performing services similar to the Services. If CoreLogic believes that the turnover rate of Supplier Personnel may be excessive (i.e., not in compliance with the requirements described above in this Section 8.5(c)) and so notifies Supplier, Supplier shall provide CoreLogic with data relating |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 20 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
to Supplier’s turnover rate within *** (***) ***, and if such data confirms that it is excessive, Supplier shall within the following *** (***) *** (i) meet with CoreLogic to discuss the reasons for the turnover rate, and (ii) implement a program for reducing the turnover rate, all at no additional cost to CoreLogic. Notwithstanding any transfer or turnover of Supplier Personnel, Supplier shall remain obligated to perform the Services without degradation and in accordance with the Service Levels and shall be responsible for all costs related to the transition of personnel and all required training.
| |
| (d) | Restrictions on Performing Services to Competitors. Neither Supplier nor any Subcontractor shall cause or permit any Restricted Personnel to perform during the period of employment with Supplier or any Subcontractor, services directly or indirectly for a Direct CoreLogic Competitor either while engaged in the provision of Services or during the *** (***) *** immediately following the termination of his or her involvement in the provision of such Services (the “Restricted Period”) without CoreLogic’s prior written consent. “Restricted Personnel” means (i) *** and (ii) any other Supplier Personnel designated by the Parties as “Restricted Personnel” in an applicable Supplement. In addition, in connection with Application development and/or Application maintenance Services and Services of a similar nature, to the extent CoreLogic requests Supplier Personnel to be Restricted Personnel prior to their engagement in the performance of such Services, such addition shall be subject to Supplier’s agreement, not to be unreasonably withheld. |
| |
| (e) | Security Clearances/Background Check/Drug Screening. To the fullest extent permitted by Law, prior to assigning any Supplier Personnel to perform any Services on CoreLogic’s account, Supplier shall (i) verify that Supplier Personnel are authorized to work in any country in which they are assigned to perform Services and (ii) conduct (or shall have conducted) background checks (and shall verify that such checks have been successfully completed), which shall include at a minimum a criminal history background check, drug screening test and education verification check on all Supplier Personnel (other than Transitioned Employees) assigned to work on CoreLogic’s account. Supplier shall conduct fingerprinting and third party credit checks on Supplier Personnel to the extent specified in an applicable Supplement. The scope of the criminal history background checks shall verify that Supplier Personnel (a) have not been convicted of, or accepted responsibility for, (x) a felony or (y) a crime (i.e., felony or misdemeanor) involving a dishonest act, breach of trust, fraud or violent act, and (b) are not present on the most recent version of the “Specially Designated Nationals List” published by the Office of Foreign Assets Controls of the U.S. Department of the Treasury. At CoreLogic’s request, Supplier shall provide evidence of compliance with this Section. Upon becoming aware of any violation of this Section, Supplier will keep CoreLogic apprised of such violations and its actions to remedy the violation, subject to applicable Law and Supplier’s confidentiality commitments to the applicable Supplier Personnel. Supplier Personnel may also be required to execute confidentiality agreements with CoreLogic, at CoreLogic’s request, unless such Supplier Personnel have executed confidentiality agreements with Supplier that are at least as protective as the confidentiality provisions contained in this Agreement. In order to comply with CoreLogic’s and Eligible Recipients’ customers’ requirements, pursuant to the terms of Section 9.17, CoreLogic shall have the right, from time to time and in its reasonable discretion, to designate additions or other changes to Supplier’s obligations under this Section 8.5(e). |
| |
| 8.7 | Conduct of Supplier Personnel. |
| |
| (a) | Conduct and Compliance. While at CoreLogic Facilities, Supplier Personnel shall (i) comply with the CoreLogic Rules and other rules and regulations regarding personal and professional conduct, (ii) comply with reasonable requests of Eligible Recipient personnel pertaining to personal and professional conduct, (iii) attend workplace training offered by CoreLogic at CoreLogic’s request, and (iv) otherwise conduct themselves in a businesslike manner. |
| |
| (b) | Identification of Supplier Personnel. Except as expressly authorized by CoreLogic, Supplier Personnel shall clearly identify themselves as Supplier Personnel and not as employees or representatives of any |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 21 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Eligible Recipient. This shall include any and all communications, whether oral, written or electronic, unless and to the extent authorized by CoreLogic in connection with the performance of specific Services. Each Supplier Personnel shall wear a badge indicating that he or she is employed by Supplier or its Subcontractors when at any CoreLogic Facility.
| |
| (c) | Restriction on ***. Except for marketing representatives designated in writing by Supplier to CoreLogic and activities expressly approved in advance by CoreLogic, none of the Supplier Personnel other than the Customer Executive (who shall restrict any marketing activities to direct communication with the CoreLogic Relationship Manager) shall conduct *** to Eligible Recipient employees or agents (including marketing of any New Services), other than ***. Under no circumstances shall Supplier use information provided by CoreLogic specifically or in the aggregate to advertise or market itself or others. In addition, Supplier shall not use or access CoreLogic System queries or searches, CoreLogic Data, CoreLogic Confidential Information, Personal Data or metadata for any secondary uses beyond the limited extent necessary to provide the Services to CoreLogic and the other Eligible Recipients. For the avoidance of doubt, Supplier shall not use any such information for marketing or market research purposes. |
| |
| (a) | Employee Removal. To the extent permitted by applicable Laws, Supplier shall immediately remove (or cause to be removed) any Supplier Personnel who is known to be or reasonably suspected of engaging in substance abuse while at a CoreLogic Facility, in a CoreLogic vehicle or while performing the Services. In the case of reasonable suspicion, such removal shall be pending completion of the applicable investigation. Substance abuse includes the sale, attempted sale, possession or use of illegal drugs, drug paraphernalia, or alcohol abuse, or the misuse of prescription or non-prescription drugs. |
| |
| (b) | Substance Abuse Policy. Supplier represents and warrants that it has and will maintain substance abuse policies, in each case in conformance with applicable Laws, and Supplier Personnel will be subject to such policies. Supplier represents and warrants that it shall require its Subcontractors and Affiliates providing Services to have and maintain such policies in conformance with applicable Laws and to adhere to this provision. |
| |
| 9. | SUPPLIER RESPONSIBILITIES. |
| |
| 9.1 | Policy and Procedures Manual. |
| |
| (a) | Delivery and Contents. For each Supplement entered into by the Parties under this Agreement, as part of the Services, and at no additional cost to CoreLogic, Supplier shall deliver to CoreLogic for its review, comment and approval a reasonably complete draft of the Policy and Procedures Manual for such Supplement within *** (***) *** after the Supplement Effective *** unless another date is specified in such Supplement. CoreLogic shall have at least *** (***) days to review such draft Policy and Procedures Manual and provide Supplier with comments and revisions. Supplier shall address and resolve any questions or concerns CoreLogic may have as to any aspect of the proposed draft Policy and Procedures Manual and incorporate any modifications, additions or deletions to such Policy and Procedures Manual requested by CoreLogic within *** (***) *** of receiving them from CoreLogic. The Parties shall reasonably cooperate to permit completion of the Policy and Procedures Manual within *** (***) *** after the Supplement Effective Date unless another period is agreed upon by the Parties. |
At a minimum, each Policy and Procedures Manual shall include:
| |
| (i) | a detailed description of the Services performed by Supplier for CoreLogic and the other Eligible Recipients and a description in reasonable detail *** by Supplier for CoreLogic and the other Eligible Recipients to the extent not already described in the applicable Supplement; |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 22 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (ii) | the procedures for CoreLogic/Supplier interaction and communication and descriptions relative to CoreLogic’s use and receipt of Services, including: (A) call lists; (B) procedures for and limits on direct communication by Supplier with CoreLogic Personnel; (C) problem management and escalation procedures; (D) priority and project procedures; (E) Acceptance testing and procedures; (F) Quality Assurance procedures and internal controls applicable to the Services; (G) the Project formation and approval process; (H) a schedule, format and required attendees for performance reporting, account relationship management, issues management, risk management, request management and financial management; and (I) procedures regarding the declaration of a disaster and activation of the applicable disaster recovery/business continuity plans with an identification of the location of each applicable plan to be activated (for clarity, not copies of such plans); and |
| |
| (iii) | practices and procedures addressing any other issues and matters as CoreLogic shall reasonably require. |
Supplier shall *** in each Policy and Procedures Manual.
| |
| (c) | Compliance. Supplier shall perform the Services in compliance with CoreLogic’s then current CoreLogic Policy Sets, a copy of which is included in Schedule 8, until the Policy and Procedures Manual is finalized and agreed upon by the Parties. Thereafter, Supplier shall perform the Services in accordance with the Policy and Procedures Manual and all other terms and conditions of this Agreement. |
| |
| (d) | Maintenance, Modification and Updating. Supplier shall promptly modify and update the Policy and Procedures Manual to reflect changes in the operations or procedures described therein, to reflect changes in the work to be performed, and (except as expressly set forth herein with respect to Managed Services (e.g., in Section 9.5 and 9.6 (other than Section 9.5(a)(i) with respect to compliance with the CoreLogic Policy Sets in the performance of all Services))) to *** as described in ***. Changes to the Services resulting from changes to CoreLogic Standards (including the CoreLogic Information Security Policy Set and CoreLogic Compliance Policy Set), CoreLogic Rules, the Technology and Business Process Plan, CoreLogic Information Security Policy Set and CoreLogic Compliance Policy Set and Strategic Plans shall be subject to Section 4.3. Supplier shall provide the proposed changes in the manual to CoreLogic for review, comment and approval. Supplier shall maintain the Policy and Procedures Manual so as to be accessible electronically to CoreLogic management via a secure web site in a manner consistent with CoreLogic’s security policies. |
| |
| (e) | Annual Review. The Parties shall meet to perform a formal annual review of the Policy and Procedures Manual on a mutually agreed upon date but not later than thirty (30) days from each anniversary of the Effective Date. |
| |
| (f) | Ownership. CoreLogic shall be the sole and exclusive owner of all portions of the Policy and Procedures Manual (i) provided by CoreLogic, or (ii) that are unique to CoreLogic or the Eligible Recipients or their customers or any of their business operations; provided, that Supplier shall own all right, title and interest in the other portions of Policy and Procedures Manual (the “Other PPM Provisions”). Supplier hereby grants to CoreLogic and the Eligible Recipients a worldwide, perpetual, irrevocable, non-exclusive, fully-paid-up, royalty-free, transferable license, for CoreLogic’s and each Eligible Recipient’s business purposes (including business purposes of third parties hired or engaged by CoreLogic or Eligible Recipients to provide services to CoreLogic or Eligible Recipients), to use, execute, reproduce, display, perform, modify, enhance, sublicense, distribute and create derivative works of the Other PPM Provisions and all enhancements and derivative works thereof, including the right to have contractors and agents use the Policy and Procedures Manual and all enhancements and derivative works thereof, on behalf of CoreLogic or such Eligible Recipient. CoreLogic’s proprietary or confidential data contained within the Policy and Procedures Manual will remain confidential pursuant to Article 13, and Supplier shall cease all use of |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 23 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
the portions of the Policy and Procedures Manual that are owned by CoreLogic upon completion of any Disengagement Services.
| |
| (a) | Reports. Supplier shall provide CoreLogic with monthly reports sufficient to *** along with any other reports to be provided under this Agreement (“Reports”). In addition, from time to time, CoreLogic may identify additional Reports to be generated by Supplier and delivered to CoreLogic on an ad hoc or periodic basis. All Reports shall be provided to CoreLogic as part of the Services and at no additional charge to CoreLogic except to the extent the Services required with respect to such Reports meet the definition of New Services. The Reports, to the extent reasonably possible, shall be provided to CoreLogic in a network accessible format with ability for data to be downloaded to CoreLogic’s then current standard spreadsheet application. |
| |
| (b) | Back-Up Documentation. As part of the Services, Supplier shall provide CoreLogic with all documentation and other information available to Supplier as may be reasonably requested by CoreLogic from time to time in order to verify the accuracy of the Reports provided by Supplier. |
| |
| 9.3 | Governance Model; Meetings. |
| |
| (a) | Governance. The Parties shall, in connection with this Agreement, employ the governance model set forth in Schedule 6 and the applicable Supplement. |
| |
| (b) | Meetings. During the term of this Agreement, representatives of the Parties shall meet periodically or as requested by CoreLogic to discuss matters arising under this Agreement, including any such meetings provided for in the applicable Supplement, the Transition Plan, the Transformation Plan, the Policy and Procedures Manual or Schedule 6. Each Party shall bear its own costs in connection with the attendance and participation of such Party’s representatives in such meetings. |
| |
| 9.4 | Quality Assurance and Internal Controls. |
| |
| (a) | Supplier shall develop, implement, and document Quality Assurance and internal control (e.g., financial and accounting controls, organizational controls, input/output controls, system modification controls, processing controls, system design controls, and access controls) processes and procedures, including implementing tools and methodologies, sufficient to ensure that the Services are performed (i) in an accurate and timely manner, in accordance with the Service Levels and other requirements in this Agreement; (ii) to assist CoreLogic in complying with generally accepted accounting principles; (iii) in conformance with standards and practices used by *** providers performing services similar to the Services; (iv) subject to Section 15.7, to assist CoreLogic in complying with Laws applicable to CoreLogic, ***, including by complying with all applicable requirements and guidelines established by CoreLogic in order to assist CoreLogic to meet the requirements of (1) the Sarbanes-Oxley Act of 2002, as amended, and regulations promulgated by the United States Securities and Exchange Commission and Public Company Accounting Oversight Board; (2) the Health Insurance Portability and Accountability Act and Health Information Technology for Economic and Clinical Health Act, as amended, and implementing regulations; (3) the Gramm-Leach-Bliley Act, as amended, and implementing regulations; and (4) the Fair Credit Reporting Act; and (v) to meet standards that are at least as restrictive as the standards set forth in the CoreLogic Information Security Policy Set and/or the CoreLogic Compliance Policy Set. |
| |
| (b) | Without limiting the foregoing, the processes, procedures and controls developed and implemented by Supplier shall require Supplier to: |
| |
| (i) | Maintain a strong control environment in day-to-day operations, to assure that the following fundamental control objectives are met: (1) financial and operational information is valid, complete and accurate; (2) operations are performed efficiently and achieve effective results, consistent with |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 24 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
the requirements of this Agreement; (3) assets are safeguarded; and (4) actions and decisions of the organization are in compliance with applicable Laws, subject to Section 15.7;
| |
| (ii) | Build the following basic control activities into its work processes: (1) accountability clearly defined and understood; (2) access properly controlled; (3) adequate supervision; (4) transactions properly authorized; (5) transactions properly recorded; (6) transactions recorded in proper accounting period; (7) policies, procedures, and responsibilities documented; (8) adequate training and education; (9) adequate separation of duties; and (10) recorded assets compared with existing assets; |
| |
| (iii) | Conduct *** with respect to all Services (such *** to be performed at least *** unless and until CoreLogic approves less frequent ***) and promptly remediate any *** (and promptly report to CoreLogic any items having the potential to impact an Eligible Recipient or any of their customers or CoreLogic Confidential Information); |
| |
| (iv) | On a quarterly basis, (A) facilitate a third party *** using a third party designated by CoreLogic (e.g., ***); provided that CoreLogic shall remain financially responsible for amounts paid to the applicable third party for such testing and (B) promptly notify CoreLogic of any issues discovered by such testing (to the extent that such third party tester has not notified CoreLogic directly) and promptly remediate any issues that are within Supplier’s scope of operational responsibility (and notify CoreLogic of the completion of such remediation promptly thereafter); |
| |
| (v) | Maintain *** sufficient to monitor the processes and Systems used to provide the Services (e.g., ***) and provide summaries of such *** relevant to the Services to CoreLogic every *** (***) ***; provided, however, that CoreLogic shall not be given access to reports or work product generated by such ***; and Supplier shall correct *** identified in such ***; |
| |
| (vi) | Promptly conduct investigations of suspected fraudulent activities within Supplier's organization that impact or could impact an Eligible Recipient or any of their customers or CoreLogic Confidential Information. Supplier shall promptly notify CoreLogic of any such suspected fraudulent activity and the results of any such investigation as they relate to any Eligible Recipient or any of their customers or CoreLogic Confidential Information; |
| |
| (c) | Inclusion in Policy and Procedures Manual. Processes, procedures and controls described in Sections 9.4(a) and 9.4(b) applicable to the Services shall be included in the Policy and Procedures Manual. No failure or inability of the Quality Assurance procedures to disclose any errors or problems with the Services shall excuse Supplier’s failure to comply with the Service Levels and other terms of this Agreement. |
| |
| (d) | Industry Standards, Certifications and Compliance. Supplier has achieved and, to the extent relevant, will maintain certification or compliance with the industry standards set forth in the applicable Supplement, in addition to the other certifications, specifications and standards set forth elsewhere in this Agreement. |
| |
| (a) | CoreLogic Policy Sets, CoreLogic Standards and Strategic Plans. |
| |
| (i) | Notwithstanding anything to the contrary in this Section 9.5(a), CoreLogic shall have the final authority to promulgate and modify from time to time the CoreLogic Information Security Policy Set and/or the CoreLogic Compliance Policy Set (collectively, the “CoreLogic Policy Sets”), and |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 25 |
Supplier shall at all times comply with the CoreLogic Policy Sets in the performance of the Services (i.e., perform in accordance with standards at least as high or protective as those set forth in the CoreLogic Policy Sets), without regard to whether such Services are Managed Services or Classic Services. The CoreLogic Policy Sets shall be deemed to be part of the CoreLogic Standards; provided that this Section 9.5(a)(i) shall control over the remainder of Section 9.5(a). During the period of Supplier’s performance of the Transition Services pursuant to Section 4.2, CoreLogic agrees to make its designated compliance subject matter experts available to meet with Supplier and respond to Supplier’s questions and provide other similar guidance and information as requested by Supplier and to assist in the development of procedures so that the Services comply with the CoreLogic Policy Sets (including compliance with any waivers then granted under such CoreLogic Policy Sets). The Parties will mutually agree on such procedures and, once such procedures are agreed, Supplier shall promptly add such procedures to the Policy and Procedures Manual and begin to comply with such procedures. During the Term, CoreLogic shall notify Supplier of any changes to the CoreLogic Policy Sets in accordance with Section 21.3, and Supplier shall commence the implementation of the CoreLogic Policy Set changes promptly, during which time, CoreLogic will provide assistance to Supplier as described in the immediately preceding sentences. Supplier shall comply with all such changes to the CoreLogic Policy Sets at no additional charge to CoreLogic, except to the extent such changes meet the definition of New Services (in which case, any additional Charges shall be determined subject to, and in accordance with, Section 4.3). If the implementation of CoreLogic Policy Set changes is expected to exceed *** (***) ***, Supplier’s Information Security Manager assigned to CoreLogic shall, within *** (***) *** after receiving the CoreLogic Policy Set changes from CoreLogic, present to CoreLogic a plan that details the method of implementing the CoreLogic Policy Set changes, the implementation timeframe and any additional Supplier costs that will result from implementing the CoreLogic Policy Set changes, to the extent that such costs are due to changes that meet the definition of New Services and satisfy the requirements set forth in Section 4.3(a) (each, a “Policy Set Changes Implementation Plan”). CoreLogic will review and approve or reject the Policy Set Changes Implementation Plan within *** (***) *** after receipt of such plan from Supplier. Supplier shall update the Policy and Procedures Manual not later than *** (***) *** after the CoreLogic Policy Set changes are provided by CoreLogic to Supplier. Supplier shall use commercially reasonable efforts to notify CoreLogic’s compliance group from time to time of any *** that Supplier uses with respect to compliance as compared to the standards required by the CoreLogic Policy Sets. From time to time during the Term, if Supplier has additional questions regarding the CoreLogic Policy Sets, CoreLogic shall make its designated compliance subject matter experts available to respond to Supplier’s questions and provide other similar guidance and information as reasonably requested by Supplier.
| |
| (ii) | Subject to and without limiting Section 9.5(a)(i), with respect to Classic Services only, CoreLogic shall have the final authority to designate the associated standards, policies, practices, procedures, controls and processes, architectures, products, software, systems and technologies to be supported by Supplier in the performance of the Services (collectively, the “CoreLogic Standards”). For clarity, Supplier’s performance of the Classic Services shall at all times be subject to Section 9.6 (and specifically Section 9.6(c)(i)). |
| |
| (iii) | Subject to and without limiting Sections 7.1 and 9.5(a)(i), with respect to Managed Services only, Supplier shall determine the associated standards, policies, practices, procedures, controls and processes, architectures, products, software, systems and technologies to be applied or used by Supplier in the performance of the Managed Services, subject to any minimum requirements or other specifications as may be set forth in a Supplement (including any of the Statements of Work, where the requirements set forth therein shall prevail) or the CoreLogic Policy Sets, and subject to Supplier’s obligations in Sections 7.1 and 15.1. |
| |
| (iv) | CoreLogic also shall have final authority to promulgate Strategic Plans on an annual basis and to modify and update such Strategic Plans on a periodic basis as appropriate; provided that CoreLogic may not mandate changes to the Managed Services through the Strategic Plans. Except with respect |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
to Managed Services, only CoreLogic shall have the authority to modify or grant waivers from such CoreLogic Standards and Strategic Plans. Except with respect to Managed Services (however, subject to and without limiting Section 9.5(a)(i)), Supplier shall (i) comply with and implement the CoreLogic Standards and Strategic Plans in providing the Services, (ii) work with CoreLogic to enforce the CoreLogic Standards and Strategic Plans, (iii) subject to Section 4.3, modify the Services as and to the extent necessary to conform to such CoreLogic Standards and Strategic Plans, and (iv) obtain CoreLogic’s prior written approval for any deviations from such CoreLogic Standards and Strategic Plans.
| |
| (b) | Supplier Support. At CoreLogic’s request, Supplier shall assist CoreLogic on an ongoing basis in developing CoreLogic Standards, annual Strategic Plans and short-term implementation plans. The assistance to be provided by Supplier shall include: (i) active participation with CoreLogic representatives on permanent and ad-hoc committees and working groups addressing such issues; (ii) assessments of the then-current CoreLogic Standards; (iii) analyses of the appropriate direction for such CoreLogic Standards in light of business priorities, business strategies, competitive market forces, and changes in technology; (iv) to the extent that such information is made generally available to Supplier’s customers, the provision of information to CoreLogic regarding Supplier’s technology, business processes and telecommunications strategies for its own business; and (v) recommendations regarding standards, processes, procedures, methodologies and controls and associated information technology architectures, standards, products and systems. With respect to each recommendation, Supplier shall provide the following at a level of detail sufficient to permit CoreLogic to make an informed business decision: (A) the projected cost to the Eligible Recipients and cost/benefit analyses; (B) the changes, if any, in the personnel and other resources Supplier and/or the Eligible Recipients will require to operate and support the changed environment; (C) the resulting impact on the total costs of the Eligible Recipients; (D) the expected performance, quality, responsiveness, efficiency, reliability, security risks and other service levels; and (E) general plans and projected time schedules for development and implementation. Supplier shall provide such assistance at no additional charges to CoreLogic unless such assistance meets the definition of New Services. |
| |
| (c) | Technology and Business Process Plan. Supplier shall develop and implement a technology and business process plan (provided that, to the extent such implementation meets the definition of New Services, the applicable portion of the implementation shall be handled in accordance with Section 4.3) on *** basis, or other more frequent basis, as requested by CoreLogic, and shall modify and update such plan on a periodic basis as appropriate (“Technology and Business Process Plan”); provided that CoreLogic may not mandate changes to the Managed Services through the Technology and Business Process Plan. The Technology and Business Process Plan shall include, among other things, plans for the following with respect to Services that are not Managed Services: (i) implementing the then-current CoreLogic Standards and Strategic Plan; (ii) refreshing Equipment and Software (in accordance with the refresh cycles and responsibilities described in the applicable Supplement); and (iii) adopting new technologies and business processes as part of the Technology and Business Process Evolution (as further described in this Section). The development of the Technology and Business Process Plan will be an iterative process that Supplier shall carry out in consultation with CoreLogic. The timetable for finalization of the Technology and Business Process Plan shall be set *** having regard to the timetable for the Strategic Plan. Following approval by CoreLogic, Supplier shall comply with the Technology and Business Process Plan unless and to the extent CoreLogic agrees to depart from such Technology and Business Process Plan. |
| |
| (a) | Compliance with Change Management Procedures. In making or requesting any change in the Services or the standards, processes, procedures, methodologies or controls or associated technologies, architectures, standards, products, Software, Equipment, Systems, or Materials provided, operated, managed, supported or used in connection with the Services, Supplier and CoreLogic shall comply with the change management procedures and change management standards specified in Schedule 6 (the “Change Management Procedures”). |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (b) | *** Responsibility for Changes. Unless otherwise set forth in this Agreement or approved in accordance with Sections 4.3 or 9.6(c), *** shall *** (including, for clarity, *** from such change (i.e., that are ***)) associated with any change desired by ***, including all *** associated with (i) the design, installation, implementation, testing and rollout of such change, (ii) any modification or enhancement to, or substitution for, any impacted business process or associated Software, Equipment, System, Services or Materials, and (iii) any increase in the cost to the Eligible Recipients of operating, maintaining or supporting any impacted business process or associated Software, Equipment, System, Services or Materials. |
| |
| (c) | CoreLogic Approval – Cost, Adverse Impact. |
| |
| (i) | With Respect to Classic Services. Supplier shall make no change which *** (i) increase any Eligible Recipient’s total cost of receiving the Services; (ii) require material changes to, or have an adverse impact on, any Eligible Recipient’s businesses, operations, environments, facilities, business processes, systems, software, utilities, tools or equipment (including those provided, managed, operated, supported and/or used on their behalf by ***); (iii) require any Eligible Recipients or Supplier to install a new version, release, upgrade of, or replacement for, any Software or Equipment or to modify any Software or Equipment; (iv) have a material adverse impact on the functionality, interoperability, performance, accuracy, speed, responsiveness, quality or resource efficiency of the Services; (v) have a material adverse impact on the cost (individually or in the aggregate), either actual or planned, to CoreLogic of ***; (vi) require changes to or have an adverse impact on the functionality, interoperability, performance, accuracy, speed, responsiveness, quality, cost or resource efficiency of CoreLogic’s Retained Systems and Business Processes; or (vii) violate or be inconsistent with CoreLogic Standards or Strategic Plans as specified in Section 9.5, without first obtaining CoreLogic’s approval, which approval CoreLogic may withhold in ***. |
| |
| (ii) | With Respect to Managed Services. Supplier shall make no change which may (i) increase any Eligible Recipient’s total cost of receiving the Services; (ii) require material changes to, or have an adverse impact on, any Eligible Recipient’s businesses, operations, environments, facilities, business processes, systems, software, utilities, tools or equipment (including those provided, managed, operated, supported and/or used on their behalf by ***); (iii) require any Eligible Recipients to install a new version, release, upgrade of, or replacement for, any Software or Equipment or to modify any Software or Equipment; (iv) have a material adverse impact on the functionality, interoperability, performance, accuracy, speed, responsiveness, quality or resource efficiency of the Services; (v) have a material adverse impact on the cost (individually or in the aggregate) either actual or planned, to CoreLogic of ***; (vi) require changes to or have an adverse impact on the functionality, interoperability, performance, accuracy, speed, responsiveness, quality, cost or resource efficiency of CoreLogic’s Retained Systems and Business Processes; or (vii) violate or be inconsistent with Supplier’s obligations with respect to the CoreLogic Policy Sets as specified in Section 9.5, without first obtaining CoreLogic’s approval, which approval CoreLogic may withhold in its reasonable discretion. |
| |
| (iii) | Notwithstanding Section 9.6(c)(ii), with respect to Managed Services only: |
| |
| (1) | with respect to any Software tool used in the performance of the Managed Services and expressly identified in an applicable Supplement as being subject to this Section 9.6(c)(iii)(1), if Supplier elects to make a change to such Software tool (e.g., upgrading versions or exchanging for different tool), so long as such Software tool (or its replacement) retains functionality that is equal to or better than the Software tool prior to such change, Supplier shall have the right to make such change in accordance with Section 9.6(c)(ii) and the Change Management Procedures for Managed Services set forth in the applicable Supplement; provided, that to the extent that CoreLogic (without Supplier’s approval or as otherwise contemplated by the immediately subsequent sentence) has made CoreLogic Software or CoreLogic processes dependent upon any such identified Software tool, then CoreLogic shall be responsible for the cost to remove or mitigate dependence on the tool, or otherwise to |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 28 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
mitigate the adverse impact arising from CoreLogic’s dependence on such Software tool. Notwithstanding the foregoing, (x) if Supplier has made CoreLogic Software or CoreLogic processes dependent upon any such identified Software tool either (A) *** or (B) ***, Supplier shall be responsible for the cost to remove or mitigate dependence on the tool, or otherwise to mitigate the adverse impact arising from CoreLogic’s dependence on such Software tool; (y) if the Parties jointly develop and implement a solution that makes CoreLogic Software or CoreLogic processes dependent upon any such identified Software tool, the Parties shall *** to remove or mitigate dependence on the tool, or otherwise to mitigate the adverse impact arising from CoreLogic’s dependence on such Software tool.
| |
| (2) | with respect to any Equipment or Software that is used by Supplier to provide Managed Services (whether provided by CoreLogic or Supplier), if commercial support is no longer available for any such Equipment or Software, then CoreLogic may either (i) agree to Supplier changing the Equipment or Software to a commercially-supported version that is equal to or better than the Equipment or Software for which commercial support is no longer available (*** with respect to the change to such commercially-supported version), or (ii) elect to have Supplier continue to use and support such out-of-support Equipment or Software as part of Classic Services. |
| |
| (d) | Temporary Emergency Changes. Notwithstanding the foregoing, Supplier may make temporary changes required by an emergency if it has been unable to contact the CoreLogic Relationship Manager (or his or her designee) to obtain approval after making reasonable efforts. Supplier shall document and report such emergency changes to CoreLogic not later than the next business day after the change is made. Such changes shall not be implemented on a permanent basis unless and until approved by CoreLogic. |
| |
| (e) | Implementation of Changes. Supplier shall schedule and implement all changes so as not to (i) disrupt or adversely impact the business, Systems or operations of the Eligible Recipients and any of their customers, (ii) degrade the Services then being received by them, or (iii) interfere with their ability to obtain the full benefit of the Services. |
| |
| (f) | Planning and Tracking. On a *** basis, Supplier shall prepare, with CoreLogic’s participation and approval, a rolling quarterly “look ahead” schedule for ongoing and planned changes for the next *** (***) ***. The status of changes shall be monitored and tracked by Supplier against the applicable schedule. |
| |
| (a) | Currency of Supplier Owned Software. Subject to and in accordance with Sections 6.5, 9.5, 9.6, 9.7(c) and Schedule 4, Supplier shall maintain reasonable currency for Supplier Owned Software and provide maintenance and support for new releases and versions of such Software. At CoreLogic’s direction, Supplier shall operate, maintain and support *** of Supplier Owned Software on a temporary basis for a reasonable period of time during a technology or business transition (e.g., a software upgrade or business unit acquisition) and shall do so *** the applicable Charges. For purposes of this Section 9.7(a), “reasonable currency” with respect to Classic Services shall mean that, unless otherwise specified in the applicable Supplement or otherwise directed by CoreLogic, Supplier shall (i) maintain Supplier Owned Software at the then current Major Release, or the Major Release level immediately prior to the then-current Major Release, and (ii) install Minor Releases ***. Notwithstanding the foregoing, with respect to Classic Services, if CoreLogic directs Supplier to maintain a release level for Software that is at “end-of-life” as published by Supplier’s applicable Software business unit, Supplier shall use commercially reasonable efforts to so maintain such release level in accordance with the requirements of this Agreement and the Services Levels. If and to the extent, despite such commercially reasonable efforts, a Service Level Default occurs as a result of a failure to so maintain such “end-of-life” Software, then such failure shall be excluded from the calculation of the applicable Service Level and such Service Level shall be recalculated excluding such failure. For purposes of this Section 9.7(a), “reasonable currency” with |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 29 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
respect to Managed Services shall mean that, unless otherwise specified in the applicable Supplement, Supplier shall maintain Supplier Owned Software as necessary to perform of the Services, satisfy Supplier’s obligations with respect to the Service Levels, and to comply with Supplier’s other obligations under this Agreement (including Sections 9.6(c)(ii) and (iii) and Section 15.1) and the applicable Supplement.
| |
| (b) | Currency of Third Party Software. Subject to and in accordance with Sections 6.5, 9.5, 9.6, 9.7(c) and Schedule 4, Supplier shall maintain reasonable currency for Third Party Software for which it is financially responsible under this Agreement and provide maintenance and support for new releases and versions of Third Party Software for which it is operationally responsible. At CoreLogic’s direction, Supplier shall operate, maintain and support *** of Third Party Software on a temporary basis for a reasonable period of time during a technology or business transition (e.g., a software upgrade or business unit acquisition) and shall do so *** the applicable Charges. In addition, unless otherwise directed by CoreLogic, Supplier shall keep Third Party Software within release levels supported by the appropriate third party vendor to ensure compatibility with other Software or Equipment components of the Systems. For purposes of this Section 9.7(a), “reasonable currency” with respect to Classic Services shall mean that, unless otherwise specified in the applicable Supplement or otherwise directed by CoreLogic, Supplier shall (i) maintain Third Party Software at the then current Major Release, or the Major Release level immediately prior to the then-current Major Release, and (ii) install Minor Releases ***. Notwithstanding the foregoing, with respect to Classic Services, if CoreLogic directs Supplier to maintain a release level for Third Party Software that is at “end-of-life” as published by the applicable third party vendor, Supplier shall use commercially reasonable efforts to so maintain such release level in accordance with the requirements of this Agreement and the Services Levels. If and to the extent, despite such commercially reasonable efforts, a Service Level Default occurs as a result of a failure to so maintain such “end-of-life” Third Party Software, then such failure shall be excluded from the calculation of the applicable Service Level and such Service Level shall be recalculated excluding such failure. For purposes of this Section 9.7(a), “reasonable currency” with respect to Managed Services shall mean that, unless otherwise specified in the applicable Supplement, Supplier shall maintain Third Party Software as necessary to perform of the Services, satisfy Supplier’s obligations with respect to the Service Levels, and to comply with Supplier’s other obligations under this Agreement (including Sections 9.6(c)(ii) and (iii) and Section 15.1) and the applicable Supplement. |
| |
| (c) | Approval. Notwithstanding Sections 9.7(a) and 9.7(b) and in accordance with Section 9.6, Supplier shall confer with CoreLogic prior to installing any ***, shall provide CoreLogic with the results of its testing and evaluation and a detailed implementation plan and, except with respect to the Managed Services, shall not install such *** if directed not to do so by CoreLogic. Except with respect to the Managed Services, where specified by CoreLogic, Supplier shall not install new Software releases or make other Software changes until CoreLogic has completed and provided formal signoff on successful user acceptance testing. |
| |
| (d) | Updates by CoreLogic. The Eligible Recipients shall have the right, but not the obligation, to install new releases of, replace, or make other changes to Applications Software or other Software for which CoreLogic is financially responsible under this Agreement. |
| |
| 9.8 | Cost Effectiveness and ***. |
| |
| (a) | Efficiency and Cost Effectiveness. Supplier shall provide the Services in a cost-effective and efficient manner consistent with the level of quality and performance required by this Agreement. Without limiting the generality of the foregoing, such actions shall include efficiently using resources for which CoreLogic is charged hereunder, consistent with industry norms, and compiling data concerning such efficient use in segregated and auditable form whenever possible. |
| |
| (b) | CoreLogic Requests for ***. Without limiting Supplier’s obligations under Section 9.8(a) above, CoreLogic may request from time to time that the Parties work together to identify ways to *** in the |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 30 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
*** in the *** by *** the nature or scope of the ***, the applicable *** or other ***. If requested by CoreLogic, Supplier shall promptly prepare a proposal at a level of detail sufficient to permit CoreLogic to make an informed business decision identifying all viable means of achieving the *** without *** identified by ***. The Parties shall negotiate in good faith about each *** and, without *** of providing ***, Supplier shall identify *** if and to what extent *** implementing various ***. CoreLogic shall not be obligated to accept any proposal and Supplier shall not be obligated to implement any change to the extent CoreLogic does not accept the applicable proposal.
Each Party shall cooperate with the other Party and shall take commercially reasonable actions and precautions consistent with Schedule 8 and the applicable Supplement to prevent the introduction and proliferation of Malicious Code into CoreLogic’s or another Eligible Recipient’s environment or any System used by Supplier to provide the Services (and Supplier shall provide reasonable assistance to Eligible Recipients with respect to any of their customer’s environments in the event of such introduction). Without limiting Supplier’s other obligations under this Agreement, if Malicious Code is found in Equipment, Software or Systems provided, managed or supported by Supplier, Supplier shall, ***, eliminate such Malicious Code and reduce and use commercially reasonable efforts to eliminate the effects of such Malicious Code and, if the Malicious Code causes a loss of operational efficiency or loss of data, to mitigate such losses and restore such data using generally accepted data restoration techniques. If such techniques do not result in the restoration of such data, at CoreLogic’s election, Supplier shall restore such data using *** unless the Malicious Code was introduced by *** (in which case *** for such restoration).
| |
| (a) | Records Retention. Supplier shall, and shall cause its Subcontractors to, maintain complete and accurate records of and supporting documentation relating to the following: Charges, ***, and all transactions, authorizations, changes, implementations, reports, filings, returns, analyses, procedures, or controls, *** in the performance of its obligations under this Agreement, including all invoices and supporting documentation and excluding internal audit reports prepared by Supplier’s corporate internal audit group and other information regarding internal processes and operations that Supplier is not otherwise required to be delivered to CoreLogic as provided in this Agreement (the “Contract Records”). Subject to Supplier’s obligations to return or destroy Confidential Information and/or CoreLogic Data otherwise under this Agreement (e.g., Sections 6.5(e)(ii), 13.1(f), 13.2(b)(v)), Supplier shall maintain such Contract Records in accordance with CoreLogic’s record retention policy (as such policy may be modified from time to time and provided to Supplier in writing) during the Term and any Disengagement Services period and thereafter for the longer of (1) the period required by applicable Laws or (2) the period ending at the end of the fifth (5th) full calendar year after the calendar year in which Supplier ceased performing the Services (including Disengagement Services requested by CoreLogic under Section 20.8(b)(7)) (the “Audit Period”), provided that, at the end of the Audit Period, Supplier shall return or securely erase any remaining Contract Records in accordance with the requirements set forth in Section 13.1(f). |
| |
| (b) | Compliance, Information Security, Privacy, Business Continuity, Disaster Recover, Vendor Risk Management and Operational Audits. During the Audit Period, Supplier shall***, provide to CoreLogic (and internal and external auditors, inspectors, regulators and other representatives that CoreLogic may designate from time to time, *** CoreLogic and/or Eligible Recipients *** (provided that if such auditing entity is a Direct Supplier Competitor, CoreLogic shall first arrange for such auditing entity and Supplier to sign a non-disclosure agreement in substantially the form of Annex 2 (or another form mutually agreed to by Supplier and such entity), provided further that Supplier hereby agrees to sign such agreement with the applicable auditing entity so that CoreLogic’s audit rights hereunder are not obstructed), *** (collectively, “Permitted Auditors”)) access at reasonable hours to Supplier Personnel, to Systems used by Supplier, to the facilities at or from which Services are then being provided and to Contract Records, all to the extent relevant to an applicable audit and the Services, usage of Third Party Software and to ensure Supplier’s compliance with the terms of this Agreement and Schedule 8 or with regulations |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 31 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
applicable to this Agreement. If an audit reveals a non-trivial breach of this Agreement or that Supplier is not in compliance with a Third Party Software license agreement, Supplier shall *** for the *** of *** to verify that such breach has been corrected, and, if applicable, any license fees, penalties and ***. With respect to any such additional usage of Third Party Software discovered pursuant to an audit described in this Section 9.10(b), the Parties will work in good faith to manage and/or mitigate such additional usage during the periods following such discovery. Supplier also agrees to promptly provide all information necessary to complete CoreLogic’s and Eligible Recipients’ Requests For Proposal (“RFP”), Requests For Quotation (“RFQ”), Information Security Risk Assessments, Information Security Questionnaires or similar documentation.
| |
| (c) | Financial Audits. During the Audit Period, Supplier shall, and shall cause its Subcontractors to, provide to CoreLogic and Permitted Auditors access during reasonable hours to Supplier Personnel and to Contract Records and other reasonably related information to conduct financial audits, all to the extent relevant to the performance of Supplier’s financial obligations under this Agreement. If any such audit reveals an overcharge by Supplier, and Supplier does not successfully dispute the amount questioned by such audit in accordance with Article 19, Supplier shall promptly pay to CoreLogic the amount of such overcharge (taking into account any offsetting undercharges (but only to the extent that such offsetting undercharges that are discovered pursuant to such audit are not prohibited from being invoiced by Supplier due to the time limitations set forth in Section 12.1(d)); provided that, such offsetting undercharges shall not exceed the amount of the overcharge determined by such audit (i.e., CoreLogic cannot owe Supplier more Charges in the aggregate on the basis of the applicable audit)), ***. In addition, if any such audit reveals an overcharge of more than *** percent (***%) of the audited Charges, Supplier shall promptly reimburse CoreLogic for the actual cost of such audit. |
| |
| (d) | Audit Assistance. Supplier shall (i) provide any assistance reasonably requested by CoreLogic or a Permitted Auditor in conducting any such audit, including completing any applicable questionnaires and installing and operating audit software, (ii) make reasonably requested personnel, records, Systems and information available to CoreLogic or a Permitted Auditor in response to an audit or request for information, and (iii) in all cases, provide such assistance, personnel, records, Systems and information in an expeditious manner to facilitate the timely completion of such audit. |
| |
| (i) | Notwithstanding the intended breadth of CoreLogic’s audit rights, CoreLogic shall not be given access to (A) the confidential information of other Supplier customers or Supplier vendors who are not Subcontractors, (B) Supplier locations that are not related to CoreLogic, the other Eligible Recipients or the Services, or (C) Supplier’s internal costs, except to the extent such costs are the basis upon which CoreLogic is charged (e.g., reimbursable expenses, Out-of-Pocket Expenses, Administered Expenses or cost-plus Charges). |
| |
| (ii) | CoreLogic shall provide Supplier a *** (***) *** advance notice of an audit, unless such audit is by government or certification or accreditation auditors, inspectors, regulators or representatives or for cause or required by a customer of either CoreLogic or an Eligible Recipient or advance notice is not practical or is inconsistent with the purpose of such audit; provided that, to the extent an audit is required by a customer of either CoreLogic or an Eligible Recipient, CoreLogic shall use commercially reasonable efforts to provide advance notice to Supplier of such audit, work with the applicable customer to attempt to establish a period of reasonable advance notice for such audit, and coordinate with the applicable customer and Supplier in order to minimize disruption to Supplier and its facilities in connection with such customer audit. In performing audits, CoreLogic shall avoid unnecessary disruption of Supplier’s operations and unnecessary interference with Supplier’s ability to perform the Services in accordance with the Service Levels. |
| |
| (iii) | CoreLogic and Permitted Auditors shall be given adequate private workspace in which to perform an audit, plus access to photocopiers, telephones, facsimile machines, computer hook-ups, and any |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 32 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
other facilities or equipment reasonably requested by CoreLogic and needed for the performance of the audit.
| |
| (iv) | Audits shall be subject to Supplier’s reasonable standard security procedures that are generally applied to all auditors and inspectors of its other customers. To the extent Supplier’s standard security procedures make the intended audit *** to perform its relevant audit, *** will work with such auditor, inspector, or regulator *** to enable the auditor, inspector or regulator to perform the audit, by ***. |
| |
| (v) | Permitted Auditors shall not be retained on a contingent fee basis. |
| |
| (f) | Supplier Internal Audit. If Supplier determines as a result of its own internal audit or otherwise that it has overcharged CoreLogic, then Supplier shall promptly pay to CoreLogic the amount of such overcharge (taking into account any offsetting undercharges (but only to the extent that such offsetting undercharges that are discovered pursuant to such audit ***); provided that such offsetting undercharges shall not exceed the amount of the overcharge determined by such audit (i.e., CoreLogic cannot owe Supplier more Charges in the aggregate on the basis of the applicable audit)), ***. |
| |
| (g) | Supplier Response to Audits. Supplier and CoreLogic shall meet promptly upon the completion of any audit conducted pursuant to this Section 9.10 (i.e., an exit interview) and/or the issuance of an interim or final report following such an audit. Supplier shall respond to each exit interview and/or audit report in writing within *** (***) ***, unless a shorter response time is specified in such report. Supplier and CoreLogic shall develop and agree upon an action plan to expeditiously address and resolve any deficiencies, concerns and/or recommendations identified in such exit interview or audit report. Supplier, at its own expense, shall then undertake remedial action in accordance with such action plan and the dates specified therein to the extent necessary to comply with Supplier’s obligations under this Agreement. |
| |
| (h) | Facility and Controls Audit. |
In addition to its other obligations under this Section 9.10, Supplier shall provide on an annual basis a copy of the unqualified (subject to the provisions contained below in this Section 9.10(h)) shared services or generic Service Organization Controls (SOC1) “Type II” report under Statement on Standards for Attestation Engagements (SSAE) No. 16 (or any applicable successor thereto) (“SSAE 16”) concerning Supplier Facilities at or from which the Services are provided (except as otherwise provided in an applicable Supplement) (each, a “Facility and Controls Audit”). Such Facility and Controls Audits shall be conducted by an independent public accounting firm on *** basis. The Facility and Controls Audits shall be those Facilities Controls Audit reports generally provided by Supplier to its customers for such Supplier Facilities, and the scope and timing of such Facilities Controls Audits shall be consistent in all material respects with *** as of the Effective Date. Facility and Controls Audits shall meet the following requirements: (i) the audit shall be performed by a firm of international repute, (ii) except as otherwise approved by CoreLogic, such reports shall cover the period beginning *** through *** (and be dated no later than ***) of ***, and (iii) Supplier shall provide a roll-forward or bridge letter by *** of the *** after the report is issued stating that there were no material changes to the control environment specified in the applicable report for the portion of *** not covered by the audit, or describing any material changes that occurred during the period covered by the bridge letter. CoreLogic and the Eligible Recipients shall be entitled to provide a copy of any such audits to CoreLogic *** subject to their acceptance of the conditions to disclosure (e.g., click-wrap agreement) required by the audit firm. With respect to any audit report issued under this Section 9.10(h), if any auditor opinion (A) concludes that any control objective has not been met, (B) is qualified and identifies one or more material weaknesses, significant deficiencies or any other deficiencies in such operating practices and procedures, or (C) determines that such operating practices and procedures otherwise fail to comply in any material respect with *** designed to minimize operational and financial risk, and, in each such case, such conclusion, determination or qualification relates to the Services (each, an “F&C Audit Deficiency”), then such findings shall be considered a breach by Supplier of this Section 9.10(h). CoreLogic shall permit Supplier to cure its breach of this Section 9.10(h) by allowing Supplier, (1) within *** (***) *** of the issuance of such Report, if Supplier
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 33 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
investigates the results thereof and provides a reasonably detailed plan to CoreLogic proposing remediation of such failures or deficiencies, and (2) upon CoreLogic approval, immediately commences implementation of all necessary remedial measures to eliminate such failures or deficiencies and concludes such implementation within the timeframe established by the CoreLogic-approved remediation plan, all at Supplier’s cost. If Supplier fails to implement the remedial measures as agreed upon by the Parties in connection with the Facility and Controls Audit contemplated by this paragraph, such failure shall be considered a material breach of this Agreement and CoreLogic may terminate this Agreement for cause in accordance with Section 20.1(a)(vii). The Facility and Controls Audits described above in this paragraph shall be conducted and the Reports provided at no additional charge to CoreLogic.
To the extent CoreLogic requests, with reasonable prior notice, that, in addition to the Facility and Controls Audit described above, Supplier conduct a CoreLogic-specific Facility and Controls Audit concerning Supplier Facilities at or from which the Services are provided (each, a “CoreLogic-Specific Facility and Controls Audit”), Supplier shall do so at CoreLogic’s expense with respect to Supplier’s external auditor expenses *** to administer such audits (provided that Supplier notifies CoreLogic of such third party expenses, obtains CoreLogic’s prior approval of, and uses commercially reasonable efforts to minimize, such third party expenses). As of the Effective Date, CoreLogic hereby requests, and Supplier hereby agrees to perform, the CoreLogic-Specific Facility and Controls Audits described in Schedule 14. If a CoreLogic-Specific Facility and Controls Audit reveals an F&C Audit Deficiency, Supplier shall promptly notify CoreLogic of such F&C Audit Deficiency and promptly commence remediation of such F&C Audit Deficiency. Supplier shall meet with CoreLogic promptly after such notification and the Parties shall mutually agree to a plan to complete such remediation. Supplier shall complete such remediation within the timeframe agreed by the Parties in the mutually agreed plan. To the extent that Supplier receives a qualified SSAE 16 as a result of failure of controls for which CoreLogic is responsible, CoreLogic shall promptly implement all necessary remedial measures to eliminate such failures or deficiencies at CoreLogic’s cost. In addition, if Supplier undertakes additional or different Facility and Controls Audits (or equivalent audits) of Supplier Facilities from which Services are provided that Supplier distributes generally to Supplier’s other customers, Supplier shall provide CoreLogic with copies of reports from such Facility and Controls Audits at ***.
| |
| (i) | Facility and Controls Audit Obligations for Subcontractors. Unless otherwise approved by CoreLogic, any Supplier subcontract will require the applicable Subcontractor that store or process CoreLogic Data (excluding those Subcontractors that do not require CoreLogic’s approval pursuant to Section 9.11(b)) to provide an annual Facility and Controls Audit to CoreLogic under terms and conditions identical to those applicable to Supplier under Section 9.10(h) above. |
| |
| (j) | Audit Costs. Except as provided in this Section 9.10, Supplier and its Subcontractors and suppliers shall provide the Services described in this Section 9.10 at ***. |
| |
| (a) | Use of Subcontractors. Supplier shall not use Subcontractors to perform the Services specified in this agreement unless Supplier: (i) obtains CoreLogic’s prior written approval of the proposed Subcontractor and the scope of the Subcontracting services (which approval may take into account any approval rights that may exist under agreements between CoreLogic and CoreLogic customers) (ii) gives CoreLogic reasonable prior notice of any subcontract, specifying the components of the Services affected, the scope of the proposed subcontract, the identity and qualifications of the proposed Subcontractor, the reasons for subcontracting the work in question, the location of the Subcontractor facilities from which the Services will be provided, and the extent to which the subcontract will be dedicated; and (iii) provides CoreLogic with ***, or *** of the proposed subcontract, in either case excluding the *** terms. With respect to dedicated subcontracts with a Subcontractor, Supplier will use commercially reasonable efforts to include CoreLogic as an intended third party beneficiary in such dedicated subcontract. Any pre-approved Subcontractors shall be listed in the applicable Supplement, along with the components and locations of |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 34 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
the Services to be provided by each Subcontractor. However, pre-approval of a Subcontractor does not constitute approval of subcontracting of a Service.
| |
| (b) | Subcontractors Not Requiring Approval. Supplier may, in the ordinary course of business and without CoreLogic’s prior approval, enter into subcontracts for third party services or products that are not exclusively dedicated to CoreLogic and that do not include any direct contact with CoreLogic *** or the performance of Services at CoreLogic Facilities (or as otherwise directly addressed in an applicable Supplement), provided that such subcontracts entered into without CoreLogic’s approval do not comprise greater than *** percent (***%) of the total work effort provided under the applicable Supplement. Such Subcontractors shall possess the training, experience, competence and skill to perform the work in a skilled and professional manner. |
| |
| (c) | Supplier Responsibility. Unless specified in a Supplement with respect to a specific Subcontractor or otherwise approved by CoreLogic, the terms of any subcontract (except for subcontracts that are governed by Section 9.11(b)) must be consistent with this Agreement, including: (i) confidentiality and intellectual property obligations, including obligations that are at least as restrictive as those set forth in Article 13; (ii) CoreLogic’s approval rights (which must ***); (iii) compliance with the ***, and applicable Laws; (iv) compliance with ***; (v) audit rights, as described in Section 9.10; (vi) Key Supplier Personnel; and (vii) insurance coverage with coverage types and limits consistent with the scope of work to be performed by such Subcontractors. Notwithstanding the terms of the applicable subcontract, the approval of such Subcontractor by CoreLogic or the availability or unavailability of Subcontractor insurance, Supplier shall be and remain responsible and liable for any acts or omissions of any Subcontractor or Subcontractor personnel (including failure to perform in accordance with this Agreement or to comply with any duties or obligations imposed on Supplier under this Agreement) to the same extent as if such failure to perform or comply was committed by Supplier or Supplier employees. Supplier shall cause all Subcontractors to comply with the CoreLogic Policy Sets in the performance of the Services. |
| |
| (d) | Right to Require Removal. CoreLogic shall have the right to require Supplier to replace a Subcontractor (notwithstanding any prior approval), *** to CoreLogic, if the Subcontractor’s performance is materially deficient or if there are other reasonable grounds for removal. If directed to do so, Supplier shall remove and replace such Subcontractor as soon as possible. Supplier shall continue to perform its obligations under this Agreement, notwithstanding the removal of the Subcontractor. CoreLogic shall have *** for any *** that *** may be *** to a Subcontractor as a result of the removal of such Subcontractor at CoreLogic’s request. |
| |
| (e) | Release of Subcontractor. If Supplier’s terminates a Subcontractor such that Supplier owes such Subcontractor termination charges or other similar amounts under the applicable subcontract between Supplier and such Subcontractor, CoreLogic shall *** for such termination *** except as may be permitted by an applicable Supplement (e.g., an agreement to pay specified *** in the event of a termination for convenience or other termination event). |
| |
| 9.12 | Technology and Business Process Evolution. |
| |
| (a) | Obligation to Evolve. Subject to Section 9.5, Supplier shall provide the Services using current technologies and business processes that are consistent with *** that will enable the Eligible Recipients to take advantage of the advances in the industry and support their efforts to maintain competitiveness in their markets. Supplier shall identify and propose the implementation of Technology and Business Process Evolutions that are intended to: (i) improve the efficiency and effectiveness of the Services (including cost savings); (ii) improve the efficiency and effectiveness of the *** at or from CoreLogic facilities; (iii) result in cost savings or revenue increases to the Eligible Recipients in *** the Services; (iv) enhance the ability of the Eligible Recipients to conduct their businesses and serve their customers; and (v) achieve the objectives of the Eligible Recipients through receipt of the Services faster and/or more efficiently. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 35 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (b) | Annual Technology and Business Process Review. CoreLogic may elect to conduct, subject to Section 9.10(e), an annual technology and business process review to compare Supplier’s then current technologies and business processes against the industry best standards and practices. If any such review reveals that the technologies and business processes then utilized by Supplier are not at the level of “***,” then the Parties shall review the results of the review and promptly establish and implement a plan to implement identified *** that are agreed-upon by the Parties (such agreement not to be unreasonably withheld (e.g., a reasonable belief by Supplier that such *** but would not be beneficial for Supplier’s provision of the Services)). |
| |
| (c) | Supplier Briefings. At least semi-annually and as described in Schedule 6, Supplier shall meet with CoreLogic to formally brief CoreLogic regarding Technology and Business Process Evolutions of possible interest or applicability to the Eligible Recipients. Such briefing shall include Supplier’s assessment of the business impact, performance improvements and cost savings associated with such Technology and Business Process Evolutions. Subject to its non-disclosure obligation under other customer contracts, Supplier shall obtain information regarding Technology and Business Process Evolutions from other *** and shall communicate such information to CoreLogic on an ongoing basis. |
| |
| (d) | Supplier Developed Advances. If Supplier develops technological advances in or changes to the information technology and business processes and services and associated technologies used to provide the same or substantially similar services to other Supplier customers or Supplier develops new or enhanced processes, services, software, tools, products or methodologies to be offered generally to such customers (collectively, “New Advances”), Supplier shall, subject to Section 4.3 and Schedule 6, (i) where reasonably deemed appropriate by Supplier, offer CoreLogic the opportunity to *** in connection with the implementation of such New Advances; and (ii) if CoreLogic declines such opportunity, offer *** to such New Advances and the opportunity to implement and receive the benefits of any New Advances. |
| |
| (e) | ***. Supplier shall deploy, implement and support Technology and Business Process Evolution and New Advances throughout the Term and such Technology and Business Process Evolution and New Advances shall be *** except as set forth in the applicable Supplement or to the extent such deployment, implementation or support constitutes a New Service. |
| |
| 9.13 | Notice of Adverse Impact. |
If Supplier becomes aware of any failure by Supplier to comply with its obligations under this Agreement or any other situation (i) that has impacted or reasonably could impact the maintenance of any Eligible Recipient’s financial integrity or internal controls, the accuracy of any Eligible Recipient’s financial, accounting, safety, security, manufacturing/production quality or human resources records and reports, or compliance with CoreLogic Rules, CoreLogic Standards or applicable Laws or (ii) that has had or reasonably could have any other material adverse impact on the Services in question or the business operations or reputation of the Eligible Recipients, then Supplier shall expeditiously notify CoreLogic of such situation and the impact or expected impact, and Supplier and CoreLogic shall meet to formulate and implement an action plan to rectify such situation and minimize or eliminate such impact.
| |
| (a) | General. Subject to Section 9.14(e), no Party shall be liable for any default or delay in the performance of its obligations under this Agreement if and to the extent such default or delay is caused, directly or indirectly, by fire, flood, earthquake, elements of nature or acts of God; wars, terrorist acts, site-specific terrorist threats, riots, civil disorders, rebellions or revolutions; strikes, lockouts or labor disputes; or any other similar cause beyond the reasonable control of such Party (a “Force Majeure Event”); except to the extent that the non-performing Party is at fault in failing to prevent or causing such default or delay, and provided that such default or delay cannot be circumvented by the non-performing Party through the use of commercially reasonable alternate sources, workaround plans or other means. A strike, lockout or labor dispute involving Supplier Personnel shall not excuse Supplier from its obligations hereunder. Acts |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 36 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
or omissions of Affiliates, Subcontractors, Third Party Contractors or Managed Third Parties that are themselves due to a Force Majeure Event as set forth herein shall also excuse the relevant Party for any related default or delay in such Party’s performance hereunder. In addition, the refusal of a Supplier Personnel to enter a facility that is the subject of a labor dispute shall excuse Supplier from its obligations hereunder only if and to the extent such refusal is based upon a clear and present danger of physical harm.
| |
| (b) | Duration and Notification. In the event of a Force Majeure Event, the non-performing Party shall be excused from further performance or observance of the obligation(s) so affected for as long as such circumstances prevail and such Party continues to use commercially reasonable efforts to recommence performance or observance whenever and to whatever extent possible without delay. Any Party so prevented, hindered or delayed in its performance shall, as quickly as practicable under the circumstances, notify the Party to whom performance is due by telephone (to be confirmed in writing within *** (***) *** of the inception of such delay) and describe at a reasonable level of detail the circumstances of the Force Majeure Event, the steps being taken to address such Force Majeure Event, and the expected duration of such Force Majeure Event. |
| |
| (c) | Substitute Services. If any Force Majeure Event described in Section 9.14(a) affects (i) Supplier Facilities or Supplier Systems, or (ii) CoreLogic Facilities or CoreLogic Systems for which Supplier has operational responsibility as set forth in a Supplement to implement a disaster recovery plan and has failed to perform its responsibilities with respect to its implementation of such plan, and in either case such event has substantially prevented, hindered or delayed or is reasonably expected to substantially prevent, hinder or delay the performance by Supplier or one of its Subcontractors of Services necessary for the performance of critical Eligible Recipient functions for longer than *** specified in ***, or if there ***, ***(***) ***, Supplier shall, unless and until otherwise directed by CoreLogic, use commercially reasonable efforts to procure such Services from an alternate source at *** for so long as the delay in performance shall continue, up to the ***. If Supplier is unable to procure such substitute services on an expedited basis or CoreLogic elects to contract directly for such services, CoreLogic may procure such Services from an alternate source at Supplier’s expense up to the Charges actually paid to Supplier with respect to the period of non-performance. Supplier shall not *** any Force Majeure Event affecting Supplier’s ability to perform. |
| |
| (d) | Termination. If any Force Majeure Event affects (i) Supplier Facilities or Supplier Systems, or (ii) CoreLogic Facilities or CoreLogic Systems for which Supplier has operational responsibility as set forth in a Supplement to implement a disaster recovery plan and has failed to perform its responsibilities with respect to its implementation of such plan, and in either case such event substantially prevents, hinders or delays the performance by Supplier or one of its Subcontractors of Services necessary for the performance of critical Eligible Recipient functions for more than *** (***) ***, CoreLogic, at its option, may terminate this ***, in which case Termination Charges shall by payable by CoreLogic in accordance with Schedule 13. If, in either event, CoreLogic elects to terminate ***, the *** under this Agreement shall be ***, in accordance with the pricing methodology set forth in Schedule 4, to reflect such *** termination. |
| |
| (e) | Business Continuity and Disaster Recovery Services. Upon the occurrence of a Force Majeure Event or any operational interruption that constitutes a disaster under a disaster recovery/business continuity plan, Supplier shall promptly implement, as appropriate, (x) such CoreLogic-specific disaster recovery plan and provide disaster recovery Services as described in such plan and the applicable Supplement (including meeting Supplier’s obligations with respect to any RTO/RPO requirements stated therein), and (y) Supplier’s own disaster recovery/business continuity plan in effect for Supplier’s Facilities and Supplier Systems. The occurrence of a Force Majeure Event or such an operational interruption shall not relieve Supplier of its obligation to implement the applicable disaster recovery/business continuity plan and provide disaster recovery and business continuity services as described in this Section. Customers of CoreLogic and Eligible Recipients shall have the right to participate in any tests of CoreLogic’s disaster recovery/business continuity plans. Supplier shall not make material adverse changes to *** as they exist as of the applicable Supplement Effective Date. At all times during the Term of a Supplement, in addition to any additional requirements set forth in an applicable Supplement, Supplier shall maintain disaster |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 37 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
recovery/business continuity plans for Supplier Facilities and Supplier Systems that are consistent with plans of *** providers of similar services. Supplier shall make available to CoreLogic a copy of *** to view at Supplier Facilities, and *** that CoreLogic and the Eligible Recipients can share with their respective customers. Without limiting Supplier’s obligations set forth in the applicable Supplement with respect to disaster recovery and business continuity plans, Supplier shall test such plans at least *** and, upon request by CoreLogic, share the results of such test with CoreLogic; provided that, wherever Supplier’s plans are an integral part of the CoreLogic Services or the CoreLogic Applications, then Supplier will participate in the applicable testing on at least a *** basis (or at other frequencies set forth in the applicable Supplement) in connection with the testing of CoreLogic’s associated disaster recovery tests. CoreLogic and the Eligible Recipients reserve the right to participate (i.e., being advised of the date, scope and plan of the test, validating that the test is actually being performed, reviewing results, being informed of remediation and reviewing the progress and results of such remediation) in *** described in this Section 9.14(e). Further, if CoreLogic or an Eligible Recipient is required by customers and/or regulators to demonstrate active participation (e.g., calling a backup service desk site to ensure that calls can be made and responded to adequately), the Parties shall work together in good faith to establish additional levels of participation beyond those contemplated above. Supplier shall remediate and perform re-tests if such initial test (or any re-tests) reveals any issues or problems.
| |
| (f) | Payment Obligation. If Supplier fails to provide Services in accordance with this Agreement due to the occurrence of a Force Majeure Event, all amounts payable to Supplier hereunder shall be equitably adjusted in a manner such that CoreLogic is not required to pay any amounts for Services that it is not receiving whether from Supplier or from an alternate source at Supplier’s expense pursuant to Section 9.14(c). |
| |
| (g) | Allocation of Resources. Without limiting Supplier’s obligations under this Agreement, whenever a Force Majeure Event causes Supplier to allocate limited resources between or among Supplier’s customers and Affiliates, the Eligible Recipients shall receive ***. In no event will Supplier *** in the event of the occurrence of a Force Majeure Event. |
| |
| 9.15 | Specialized Services. |
Upon CoreLogic’s request, Supplier shall provide CoreLogic and the other Eligible Recipients with prompt access to Supplier’s specialized services, personnel and resources pertaining to information technology standards, processes and procedures and associated software, equipment and systems on an expedited basis taking into account the relevant circumstances (the “Specialized Services”). The Parties acknowledge that the provision of such Specialized Services may, in some cases, constitute New Services for which Supplier is entitled to additional compensation, and in such event, Supplier’s performance of such Specialized Services shall be contingent upon CoreLogic’s express prior authorization of the performance of such Specialized Services and such additional compensation. Supplier shall notify CoreLogic in advance if it believes such Specialized Services constitute New Services. If CoreLogic authorizes Supplier to proceed but the Parties disagree as to whether the authorized work constitutes New Services, Supplier shall proceed with such work and the disagreement shall be resolved in accordance with the procedures set forth in Section 4.3(a).
| |
| 9.16 | Government Contracts Flow-Down. |
The Parties acknowledge and agree that, as a matter of federal procurement law, Supplier may be deemed a “subcontractor” to CoreLogic and/or another Eligible Recipient under one or more of their contracts with the federal government, that the Services provided or to be provided by Supplier in such circumstances constitute “commercial items” as that term is defined in the Federal Acquisition Regulation, 48 C.F.R. Section 52.202, and that “subcontractors” providing “commercial items” under government contracts are subject to certain mandatory “flow-down” clauses (currently, (i) Equal Opportunity, (ii) Affirmative Action for Special Disabled and Vietnam Era Veterans, and (iii) Affirmative Action for Handicapped Workers) under the Federal Acquisition Regulation, 48 C.F.R. Section 52.244-6. The Parties agree that, insofar as certain such clauses are be required to be flowed down to Supplier, Supplier shall comply with such clauses ***.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 38 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 9.17 | CoreLogic Customer Contracts Flow-Down. |
The Parties acknowledge that CoreLogic is in the business of providing services similar to the Services to CoreLogic’s customers, and the Services to be provided under this Agreement and its Supplements are the foundation for some of the services to be provided by CoreLogic to CoreLogic’s and the Eligible Recipients’ customers. Supplier agrees to cooperate with and make changes to the Services requested by CoreLogic so as to provide the Services in a manner that will assist CoreLogic and the Eligible Recipients in providing its services to their customers. The Parties acknowledge and agree that Supplier may be deemed a “subcontractor” to CoreLogic and/or another Eligible Recipient under one or more of their contracts with their customers. The Parties agree that, insofar as ***this Section 9.17, Supplier shall *** to CoreLogic, except to the extent that such ***, in which case *** in accordance with Section ***.
10. CORELOGIC RESPONSIBILITIES.
In addition to CoreLogic’s responsibilities as expressly set forth elsewhere in this Agreement, CoreLogic shall be responsible for the following:
| |
| (a) | CoreLogic Relationship Manager. CoreLogic shall designate one (1) individual to whom all Supplier communications concerning this Agreement may be addressed (the “CoreLogic Relationship Manager”), who shall have the authority to act on behalf of the Eligible Recipients in all day-to-day matters pertaining to this Agreement. CoreLogic may change the designated CoreLogic Relationship Manager from time to time by providing notice to Supplier. Additionally, CoreLogic will have the option, but will not be obligated, to designate additional representatives who will be authorized to make certain decisions (e.g., regarding emergency maintenance) if the CoreLogic Relationship Manager is not available. |
| |
| (b) | Cooperation. CoreLogic shall cooperate with Supplier by, among other things, making available, as reasonably requested by Supplier, management decisions, information, approvals and acceptances so that Supplier may accomplish its obligations and responsibilities hereunder. |
| |
| (c) | Requirement of Writing. To the extent Supplier is required under this Agreement to obtain CoreLogic’s approval, consent, authorization or agreement, such approval, consent, authorization or agreement shall be in writing and shall be signed by or directly transmitted by electronic mail from the CoreLogic Relationship Manager or an authorized CoreLogic representative. Notwithstanding the preceding sentence, the CoreLogic Relationship Manager may agree in advance in writing that as to certain specific matters oral approval, consent, authorization or agreement will be sufficient. |
| |
| 10.2 | Supplier Excused Performance. |
Supplier’s failure to perform its obligations under this Agreement (including meeting the Service Levels) or the Policy and Procedures Manual shall be excused only if and to the extent such Supplier non-performance is caused by (i) the *** actions of an Eligible Recipient *** performing obligations on behalf of CoreLogic under this Agreement (unless and to the extent, as to ***, such failure is attributable to Supplier’s failure to properly manage such ***), or (ii) the failure of an Eligible Recipient or such a *** to perform *** obligations under this Agreement, but only if (A) Supplier expeditiously notifies CoreLogic of such wrongful or tortious action or failure to perform and describes in reasonable detail the reason for Supplier’s inability to perform under such circumstances, (B) Supplier provides CoreLogic with a reasonable opportunity to correct such wrongful or tortious action or failure to perform and thereby avoid such Supplier non-performance, (C) Supplier identifies and pursues all commercially reasonable means to avoid or mitigate the impact of such wrongful or tortious action or failure to perform, (D) Supplier uses commercially reasonable efforts to perform notwithstanding such wrongful or tortious action or failure to perform, and (E) Supplier conducts a Root Cause Analysis and thereby demonstrates that such wrongful or tortious action or failure to perform is the cause of Supplier’s non-performance. With respect to clauses (C) and (D) only (and without limiting Supplier’s
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 39 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
obligations therein), if Supplier anticipates that its exercise of commercially reasonable efforts described therein would require activities that would result in significant additional expense to Supplier, prior to incurring such expense, Supplier shall notify CoreLogic and provide a description of the proposed activities and associated significant expense, and CoreLogic shall have the right in its sole discretion to (x) require Supplier to exercise such efforts, whereby CoreLogic shall be financially responsible for such significant expense or (y) elect to have Supplier forego the efforts that are anticipated to result in a significant expense for Supplier, in which case Supplier shall not be obligated to perform such efforts. If CoreLogic elects to require Supplier to exercise such efforts pursuant to clause (x) above, Supplier shall use commercially reasonable efforts to minimize expenses associated with such efforts. Supplier acknowledges and agrees that the circumstances described in this Section 10.2, together with Section *** and any other excuse of performance expressly set forth in an applicable Supplement, are *** in which its *** its obligations under this Agreement (including meeting the Service Levels) will be *** and that Supplier *** any other act or omission of *** as *** any such ***.
11. CHARGES.
| |
| (a) | Payment of Charges. In consideration of Supplier’s performance of the Services, CoreLogic agrees to pay Supplier the applicable Charges. Supplier acknowledges and agrees that there are no separate or additional charges for such Services. Any costs incurred by Supplier prior to the Effective Date are included in the Charges and are not to be separately paid or reimbursed by CoreLogic. |
| |
| (b) | Incidental Expenses. Supplier acknowledges that, except as expressly provided otherwise in this Agreement, expenses that Supplier incurs in performing the Services (including management, travel and lodging, document reproduction and shipping, and long-distance telephone) are included in Supplier’s charges and rates set forth in this Agreement. Accordingly, such Supplier expenses are not separately reimbursable by CoreLogic unless expressly provided otherwise in this Agreement or CoreLogic has agreed in writing in advance to reimburse Supplier for the expense. |
| |
| (c) | Proration. Unless otherwise specified in a Supplement, periodic Charges under this Agreement are to be computed on a calendar month basis, and shall be prorated for any partial month on a calendar day basis. |
| |
| (d) | Charges for Contract Changes. Unless otherwise agreed, changes in the Services (including changes in the CoreLogic Standards, Strategic Plans, Technology and Business Process Plans, business processes, Materials, Equipment and Systems) and changes in the rights or obligations of the Parties under this Agreement (collectively, “Contract Changes”) shall result in changes in the applicable Charges only if and to the extent (i) this Agreement expressly provides for a change in the Supplier Charges in such circumstances; (ii) the agreed upon Charges or pricing methodology provides for a price change in such circumstances (for example, *** to be provided for the quoted price); or (iii) the Contract Change meets the definition of *** are applicable in accordance therewith. |
| |
| (e) | Eligible Recipient Services. |
| |
| (i) | New Eligible Recipients. From time to time CoreLogic may request that Supplier provide Services to Eligible Recipients not previously receiving such Services. Except as provided in Section 4.3 or otherwise agreed by the Parties, such Services shall be performed in accordance with the terms, conditions and prices (excluding any non-recurring transition or start-up activities specific to such Eligible Recipients) then applicable to the provision of the same Services to existing Eligible Recipients. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 40 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (ii) | Existing Supplier Customer. If CoreLogic or an Affiliate acquires an Entity and such Entity has an existing contract with Supplier for services similar to those provided under any Supplement, CoreLogic may, in its discretion, do either of the following in clause (1) or clause (2) below: |
| |
| (1) | designate such Entity as an Eligible Recipient under this Agreement and terminate the other contract for convenience; or |
| |
| (2) | terminate this Agreement for convenience and roll the Services then being provided hereunder under the other contract; provided that, if it would be unreasonable for such Services to be provided under the other contract without changes to such contract (while still maintaining the commercial-based and risk-based balance set forth in such contract), the Parties agree to work in good faith to address such changes and work through any issues so that such Services can be provided under such other contract. |
In either event, Supplier shall reduce and/or rollover to the extent reasonable the applicable termination charges and/or wind-down expenses CoreLogic would otherwise be obligated to pay in connection with such a termination; provided, however, that with respect to Supplement A only, it would not be reasonable to reduce or otherwise decrease the Termination Charges expressly identified as Unconditional Termination Charges in Schedule A-4.9 thereto.
| |
| (iii) | Election Procedure. In the event of a transaction described in clause (c) or (d) of the definition of Eligible Recipient in Schedule 1, CoreLogic may elect, within twelve (12) months after the closing of a transaction and on behalf of the Eligible Recipient in question, either (i) that such Eligible Recipient shall continue to obtain *** the Services (*** or other rational Service portions) subject to and in accordance with the terms and conditions of this Agreement for the remainder of the Term, (ii) that the Entity shall obtain some or all of the Services under a separate agreement between Supplier and such Entity containing the same terms and conditions as this Agreement (subject to such Entity ***) or (iii) that such Eligible Recipient shall no longer receive *** the Services as of a specified date, subject to its receipt of Disengagement Services pursuant to Section 20.8. If CoreLogic elects that such Eligible Recipient shall no longer receive *** the Services pursuant to clause (iii) in the immediately preceding sentence, and such election constitutes a termination as defined in Section 20.2 or the applicable Supplement, CoreLogic shall remain responsible for payment of Termination Charges, if any, to the extent contemplated by the applicable Supplement in connection with such termination. If the Services are provided under a separate agreement, CoreLogic shall *** to *** any fees in relation to the Services provided to such Entity. If such a separate agreement is entered into, as part of creating such separate agreement, the Parties shall equitably allocate Charges, volume and/or revenue sensitive measures and the Termination Charges between CoreLogic and such Entity consistent with the division of the Services between the separate agreements. |
| |
| 11.2 | Administered Expenses. |
| |
| (a) | Procedures and Payment. Unless otherwise agreed by the Parties, CoreLogic shall pay all Administered Expenses directly to the applicable vendors following review, validation and approval of such Administered Expenses by Supplier. No new Administered Expenses may be added without CoreLogic’s prior consent, which it may withhold in its sole discretion. Before submitting any Administered Expenses for payment, Supplier shall (i) review and validate the invoiced charges, (ii) identify any errors or omissions, and (iii) communicate with the applicable vendor so that the vendor corrects any errors or omissions, resolve any questions or issues and obtain any applicable credits, rebates, discounts or other incentives for CoreLogic. Supplier shall deliver to CoreLogic the original vendor invoice, together with any documentation supporting such invoice and a statement that Supplier has reviewed and validated the invoiced charges, within *** (***) *** after Supplier’s receipt of an accurate, error-free invoice from the applicable vendor; provided that, if earlier, Supplier shall use commercially reasonable efforts to deliver such invoice, documentation and statement at least *** (***) *** prior to the date on which payment is due; and provided further that, if it is not possible to deliver such invoice, documentation and statement |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 41 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
at least *** (***) *** prior to the due date, Supplier shall promptly notify CoreLogic and, at CoreLogic’s option, either request additional time for review and validation or submit the invoice for payment subject to subsequent review and validation. In addition, if the vendor offers a discount for payment prior to a specified date, Supplier shall use commercially reasonable efforts to deliver such invoice and associated documentation to CoreLogic at least *** (***) *** prior to such date. During the last month of each calendar quarter, Supplier shall use commercially reasonable efforts to deliver all such invoices and associated documentation to CoreLogic by the end of the month and, to the extent that is not possible, Supplier shall provide CoreLogic with information sufficient to accrue the applicable expenses on or before the end of such month. To the extent Supplier fails to comply with its obligations hereunder, *** for any *** or *** by the ***. In addition, to the extent Supplier fails to process and submit for payment any invoice in accordance with this provision within *** (***) *** after Supplier’s receipt of such invoice (which shall mean, where Supplier reviewed and arranged with the applicable third party vendor to receive a corrected invoice within a period of *** (***) *** after Supplier’s receipt of such invoice, *** (***) *** after Supplier’s receipt of such corrected invoice), CoreLogic shall remain financially responsible for the payment of all such invoiced amounts; however, such amounts shall be paid directly by Supplier and invoiced to CoreLogic on an amortized basis without interest, divided into equal payments over a period of (x) *** (***) *** if the amount paid by Supplier to such vendor is less than *** percent (***%) of the annual base Charges of the applicable Supplement or (y) *** (***) *** if the amount paid by Supplier to such vendor is equal to or greater than *** percent (***%) of the annual base Charges of the applicable Supplement. All Services to be performed by Supplier with respect to Administered Expenses are included in the Charges. Supplier shall not charge any handling or administrative charge in connection with its processing or review of Administered Expenses.
| |
| (b) | Efforts to Minimize. Supplier will continually seek to identify methods of reducing and minimizing CoreLogic’s retained expenses and Administered Expenses and will notify CoreLogic of such methods and the estimated potential savings associated with each such method. |
The Parties’ respective responsibilities for taxes arising under or in connection with this Agreement shall be as follows:
| |
| (a) | Income Taxes. Each Party shall be responsible for its own Income Taxes. |
| |
| (c) | Taxes on Goods or Services Used by Supplier. Supplier shall be responsible for all sales, service, value-added, lease, use, personal property, excise, consumption, and other taxes, tariffs and duties payable by Supplier on any goods or services used or consumed by Supplier in providing the Services (including services obtained from Affiliates and Subcontractors) where the tax is imposed on Supplier’s acquisition or use of such goods or services and the amount of tax is measured by Supplier’s costs in acquiring or procuring such goods or services and not by CoreLogic’s cost of acquiring such goods or services from Supplier. |
| |
| (d) | Service Taxes. CoreLogic shall be financially responsible for all Service Taxes assessed against either Party by a tax authority in the jurisdictions set forth in a Supplement in which the Parties agree that Services are received (“CoreLogic Service Taxes”). If new or higher CoreLogic Service Taxes become applicable to the Services as a result of either Party moving all or part of its operations to a different jurisdiction (e.g., CoreLogic opening a new office, Supplier relocating performance of Services to a shared service center or assigning this Agreement to an Affiliate), *** shall be financially responsible for incremental Service Taxes that result from the relocation. If new or higher CoreLogic Service Taxes become applicable to such Services after the Supplement Effective Date for any reason other than moves described above, the Parties shall negotiate in good faith and diligently seek to agree upon legally permissible means of minimizing such new or higher CoreLogic Service Taxes. Notwithstanding anything |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 42 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
to the contrary in this Agreement, Supplier will be solely responsible for payment of any inter-company Service Taxes, withholding taxes and other similar inter-company charges between Supplier and any Supplier Affiliates or Supplier contractors who are providing Services to CoreLogic and the Eligible Recipients through Supplier, and for any Service Taxes imposed by any tax authority other than a tax authority in those *** that Services are received as set forth in a Supplement associated with the Parties’ performance under this Agreement, and for all other taxes with respect to a matter for which Supplier is responsible under this Agreement (collectively, the “Supplier Service Taxes”).
| |
| (e) | Withholding. Any withholding tax or other tax of any kind that CoreLogic is required by applicable Law to withhold and pay on behalf of Supplier with respect to amounts payable to Supplier under this Agreement shall be deducted from such amounts prior to remittance to Supplier. CoreLogic will provide to Supplier reasonable assistance, which shall include the provision of documentation as required by revenue authorities, to enable Supplier to claim exemption from or obtain a repayment of such withheld taxes and will, upon request, provide Supplier with a copy of the withholding tax certificate or equivalent documentation. |
| |
| (f) | Efforts to Minimize Taxes. Each Party shall cooperate fully with the other Party to accurately determine the tax liability and to minimize such liability to the extent legally permissible. Supplier’s invoices shall separately state the Charges that are subject to taxation and the amount of taxes included therein. Each Party will provide and make available to the other any resale certificates, information regarding out-of-state or out-of-country sales or use of equipment, materials, or services, and other exemption certificates or information reasonably requested by either Party. |
| |
| (g) | Tax Audits or Proceedings. Each Party shall promptly notify the other Party of, and coordinate with the other Party, the response to and settlement of, any claim for taxes asserted by applicable Tax Authorities for which the other Party is financially responsible hereunder. With respect to any claim arising out of a form or return signed by a Party to this Agreement, such Party will have the right to elect to control the response to and settlement of the claim, but the other Party will have the right to participate in the responses and settlements to the extent appropriate given its potential responsibilities or liabilities. Each Party also shall have the right to challenge the imposition of any tax liability for which it is financially responsible under this Agreement or, if necessary, to direct the other Party to challenge the imposition of any such tax liability. If either Party requests the other to challenge the imposition of any tax liability, such other Party shall do so (unless and to the extent it assumes financial responsibility for the tax liability in question), and, the requesting Party shall reimburse the other for all fines, penalties, interest, additions to taxes or similar liabilities imposed in connection therewith, plus the reasonable legal, accounting and other professional fees and expenses it incurs. Each Party shall be entitled to any tax refunds or rebates obtained with respect to the taxes for which such Party is financially responsible under this Agreement. |
| |
| (h) | Tax Filings. Supplier represents, warrants and covenants that it is registered to and will collect and remit Service Taxes in all applicable jurisdictions. At CoreLogic’s request, Supplier shall provide CoreLogic with (i) written confirmation that Supplier has filed all required tax forms and returns and has collected and remitted all applicable amounts in connection with Service Taxes, and (ii) such other information pertaining to applicable Taxes as CoreLogic may reasonably request (in connection with this Section 11.3). |
| |
| 11.4 | Extraordinary Events. |
| |
| (a) | Definition. As used in this Agreement, an “Extraordinary Event” shall mean a circumstance in which an event or discrete set of events has occurred or is planned with respect to the business of the Eligible Recipients that results or will result in a change in the scope, nature or volume of the Services that the Eligible Recipients will require from Supplier, and which is expected to cause the estimated average monthly usage of any single Service Area to increase or decrease by ***percent (***%) or more from the actual average monthly usage for the preceding *** (***) *** (or, if less, the number of months for which such data is available), provided that such increase or decrease is not temporary or seasonal and |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 43 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
that such decrease is not due to CoreLogic resuming the provision of Services itself or transferring the performance of the Services to another service provider. Examples of the kinds of events that might cause such substantial increases or decreases include the following: (i) changes in the locations where the Eligible Recipients operate; (ii) mergers, acquisitions, divestitures or reorganizations of the Eligible Recipients; (iii) changes in the method of service delivery; (iv) changes in the applicable regulatory environment; or (v) changes in the business units being serviced by Supplier.
| |
| (b) | Consequence. If an Extraordinary Event occurs, *** with respect to applicable Charges specified in Schedule 4 in accordance with the following: |
| |
| (1) | Supplier and CoreLogic shall mutually determine on a reasonable basis the efficiencies, economies, savings and resource utilization reductions resulting from such Extraordinary Event and, upon CoreLogic’s approval, Supplier shall then proceed to implement such efficiencies, economies, savings and resource utilization reductions as quickly as practicable and in accordance with the agreed upon schedule. As the efficiencies, economies, savings or resource utilization reductions are realized, the Charges specified on Schedule 4 and any affected pricing components (e.g., resource baselines) shall be promptly and equitably adjusted to *** of such efficiencies, economies, savings and resource utilization reductions; provided, that CoreLogic shall reimburse Supplier for any *** costs or expenses incurred to realize such efficiencies, economies, savings or resource utilization reductions if and to the extent Supplier (i) notifies CoreLogic of such additional costs and obtains CoreLogic’s approval prior to incurring such costs, (ii) uses commercially reasonable efforts to identify and consider practical alternatives, and reasonably determines that there is no other more practical or cost effective way to obtain such savings without incurring such expenses, and (iii) uses commercially reasonable efforts to minimize the additional costs to be reimbursed by CoreLogic. |
| |
| (2) | Subject to Section 4.3, an Extraordinary Event shall *** specified in the applicable Supplement ***. CoreLogic ***, for each Extraordinary Event, at any time *** under this Section 11.4 and ***, apply the rates and charges (e.g., ARCs and RRCs) specified in the applicable Supplement to adjust the Charges. |
| |
| (a) | Prepaid Amounts. If any Eligible Recipient has prepaid for a service or function for which Supplier is assuming financial responsibility under this Agreement, Supplier shall promptly refund to the applicable Eligible Recipient, upon either Party identifying the prepayment, that portion of such prepaid expense which is attributable to periods after the Commencement Date. The Parties acknowledge and agree that this Section 11.5(a) shall not be applicable with respect to Supplement A and any other Supplement that expressly provides that this Section 11.5(a) shall not apply. |
| |
| (b) | Refunds and Credits. If Supplier should receive a refund, credit, discount or other rebate for goods or services paid for by an Eligible Recipient on a Administered Expense, Retained Expense, cost-plus or cost-reimbursement basis, then Supplier shall (i) notify CoreLogic of such refund, credit, discount or rebate and (ii) promptly pay the full amount of such refund, credit, discount or rebate to such Eligible Recipient. |
| |
| 11.6 | CoreLogic Benchmarking Reviews. |
| |
| (a) | Benchmarking Review. At any time after the first anniversary of the Commencement Date and thereafter no more frequently than annually, CoreLogic may, subject to this Section 11.6, engage the services of an independent third party (a “Benchmarker”) to compare the quality, cost and Supplier staffing of the Services as a whole or with respect to one or more Service Areas against the quality and cost of *** to ensure that CoreLogic is receiving from Supplier pricing and levels of service that are competitive with market rates, prices and service levels, given the nature, quality, volume and type of Services provided by Supplier hereunder (“Benchmarking”). The expense paid to the Benchmarker for any such |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 44 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Benchmarking shall be paid by CoreLogic. In making this comparison, the Benchmarker shall use a sufficiently sized reference group to conduct the Benchmarking process consisting of a representative sample of not less than four (4) companies receiving similar outsourced services, and shall consider the following factors and other similar variables and adjust the prices as and to the extent appropriate: (i) whether and to what extent supplier transition charges are paid by the customer as incurred or amortized over the term of this Agreement; (ii) the extent to which supplier pricing includes the purchase of the customer’s existing assets; (iii) the extent to which supplier pricing includes the cost of acquiring future assets; (iv) the extent to which this Agreement calls for Supplier to provide and comply with unique CoreLogic requirements; (v) whether Service Taxes are included in such pricing or stated separately in supplier invoices; and (vi) differences in volume of services (scale), scope of services, service levels, contract terms, financing or payment streams, geographic distribution (including the use of offshore facilities and labor), complexity of supported environment, technologies employed, and terms and conditions.
| |
| (b) | General. The Benchmarker engaged by CoreLogic shall be one of the approved Benchmarkers set forth on Schedule 15 or, to the extent agreed by the Parties, another nationally recognized independent (i.e., not an affiliate of a Direct Supplier Competitor) firm with experience in benchmarking similar services; provided, that in either case, the Benchmarker (i) shall not be retained on a contingent fee basis and (ii) shall execute a non-disclosure agreement substantially in the form attached hereto as Annex 2. Supplier shall cooperate fully with CoreLogic and the Benchmarker during such effort, and shall (1) provide the Benchmarker reasonable access to any premises, equipment, personnel or documents; and (2) provide any assistance required by the Benchmarker to conduct the Benchmarking, all at Supplier’s cost and expense. The Benchmarking shall be conducted so as not to unreasonably disrupt Supplier’s operations under this Agreement. Supplier shall not be obligated to provide the Benchmarker with: (A) proprietary information of Supplier not related to the Eligible Recipients or the Services; (B) any internal cost data; or (C) proprietary information of other Supplier customers. The Parties will require the Benchmarker to closely work with each Party throughout the Benchmarking process, including considering in good faith each Party’s comments and suggestions with respect to the methodology to be employed by the Benchmarker. |
| |
| (c) | Result of Benchmarking. After making the comparison described in Section 11.6(a), the Benchmarker shall submit a written report setting forth such findings and conclusions. If the Benchmarker finds that the Charges paid by CoreLogic for all Services subject to the Benchmarking are greater than *** percent (***%) higher than the *** the prices charged by other *** for work of a similar nature, type or volume (such average, the “Benchmark Standard”), the Parties shall *** a plan to decrease the Charges to eliminate any such unfavorable variance for the current Contract Year and all future Contract Years. If the Parties cannot agree on a plan that will result in a decrease in the Charges to eliminate such unfavorable variance, CoreLogic may, at its option, terminate the benchmarked Services, in which case Termination Charges shall be payable by CoreLogic in accordance with Schedule 13. Any such reductions in Supplier’s Charges shall be implemented effective *** (***) *** after the date the Benchmarker’s report was first provided to Supplier. |
| |
| 11.7 | Financial Forecasting and Budgeting Support. |
To support CoreLogic’s forecasting and budgeting processes, Supplier shall provide the following information regarding the costs to be incurred by the Eligible Recipients in connection with the Services and the cost/benefit to the Eligible Recipients associated therewith: (i) actual and forecasted utilization of Resource Units; (ii) actual and forecasted *** the *** of the Eligible Recipients associated with changes to the environment; (iii) opportunities to modify or improve the Services, to reduce the Charges, Administered Expenses or retained expenses incurred by CoreLogic; and (iv) a review of CoreLogic’s actual savings over the prior twelve (12) month period, as projected in Schedule 4, versus the actual amounts that CoreLogic paid Supplier for the Services during that same period, and if savings are less than those projected in Schedule 4, a justification explaining such variance. Such information shall be provided at CoreLogic’s request, and at no additional charge to CoreLogic, in accordance with the schedule reasonably established by CoreLogic.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 45 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
12. INVOICING AND PAYMENT.
| |
| (a) | Invoice. Unless otherwise provided in the applicable Supplement, on or before the *** (***) *** of each month, Supplier shall present CoreLogic with an invoice for any variable Charges (e.g., ARCs and RRCs) for the preceding month and fixed Charges for the current month (the “Monthly Invoice”). Supplier will also provide CoreLogic with detailed chargeback information as specified in the applicable Supplement available on-line in a database that lends itself to searching and ad hoc reporting. At a minimum, Supplier will provide CoreLogic with all information and assistance specified in the form of invoice attached to the applicable Supplement to enable CoreLogic to chargeback CoreLogic business units at no lesser detail than that delivered by CoreLogic prior to the Supplement Effective Date. Supplier will provide a billable charges volume measurement System to measure the Eligible Recipients’ actual consumption of Services by country and business unit as specified in the applicable Supplement. In such event, Supplier shall, contemporaneous with the delivery of such Monthly Invoices, provide a summary of all such invoices to CoreLogic. Supplier shall not invoice CoreLogic for any advance or concurrent charges or other amounts. |
| |
| (b) | Form and Data. Each invoice shall be in the form specified in the applicable Supplement and shall (i) comply with all applicable legal, regulatory and accounting requirements, and (ii) contain the detail identified in such Supplement to allow CoreLogic to validate volumes and fees, and comply with the chargeback and other billing requirements provided by CoreLogic. Each invoice shall include the pricing calculations and related data utilized to establish the Charges and sufficient information to validate the service volumes and associated Charges. The data underlying each invoice shall be delivered to CoreLogic electronically in a form and format (e.g., Excel or CDF) compatible with CoreLogic’s accounting systems, including CoreLogic’s *** (or any follow-on replacement of such ***) such that CoreLogic is able to identify a reasonable break-down of all resource utilization and assets that contribute to the Charges; provided that, the foregoing in this sentence shall not require Supplier to provide a *** into CoreLogic’s ***. CoreLogic may make reasonable changes to such invoicing requirements in Sections 12.1(a) and (b) (including with respect to chargeback information and other invoicing information and assistance required by CoreLogic) during the Term with no additional charge to CoreLogic, except to the extent such changes meet the definition of New Services. |
| |
| (c) | Credits. To the extent a credit may be due to CoreLogic pursuant to this Agreement, Supplier shall provide CoreLogic with an appropriate credit against amounts then due and owing; if no further payments are due to Supplier, Supplier shall pay such amounts to CoreLogic within thirty (30) days. |
| |
| (d) | Time Limitation. If Supplier fails to provide an invoice to CoreLogic for any amount (with the exception of tax-related Charges and Administered Expenses) (i) within *** (***) *** after the month in which the Services in question are rendered or the expense incurred (or, if later, the month in which Supplier is first entitled to invoice for such amount), then Supplier waives any right it may otherwise have to invoice for and collect such amount, or (ii) within *** (***) *** following the end of CoreLogic’s fiscal year in which the Services in question were rendered (provided that Supplier may satisfy its obligations in this clause (ii) by providing CoreLogic with information sufficient to accrue the applicable expenses on or before such *** (***) *** period), then Supplier waives any right it may otherwise have to invoice for and collect such amount. |
| |
| (e) | Currency. Unless otherwise specified in the applicable Supplement or Companion Agreement, Charges for all Services shall be invoiced and paid in United States Dollars. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 46 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Subject to the other provisions of this Article 12, each Monthly Invoice provided for under Section 12.1 shall be due and payable by wire transfer within thirty (30) days after receipt by CoreLogic of such invoice unless the amount in question is disputed in accordance with Section 12.4. Any invoice due under this Agreement for which a time for payment is not otherwise specified also shall be due and payable within thirty (30) days unless the amount in question is disputed in accordance with Section 12.4. Any amount that remains unpaid ten (10) days after the date when due (the “Grace Period”) will bear interest from the due date until paid at the lesser of (i) the highest rate allowed by law and (ii) *** percent (***%) per month, pro-rated for partial months. During any Contract Year, if CoreLogic pays any invoice after the due date (excluding amounts disputed in accordance with Section 12.4) but during the Grace Period, for the remainder of ***, the Grace Period shall not apply with respect to CoreLogic’s payment of subsequent invoices (i.e., Supplier would have the right to charge interest from the due date) ***. CoreLogic’s right to exercise the Grace Period as described in the immediately preceding sentence shall ***
With respect to any amount to be paid or reimbursed by CoreLogic hereunder, CoreLogic may set off against such amount any amount that Supplier is obligated to pay CoreLogic hereunder if CoreLogic has provided thirty (30) days prior written notice to Supplier and Supplier has failed to issue a credit or payment for the amount identified in such notice within that thirty (30) day period.
CoreLogic may withhold payment of particular Charges that CoreLogic reasonably disputes in good faith subject to the following:
| |
| (a) | Notice of Dispute. If CoreLogic disputes any Charges, CoreLogic shall so notify Supplier and provide a description of the particular Charges in dispute and a reasonably-detailed explanation, including, if available, supporting documentation, of the reason why CoreLogic disputes such Charges. Subject to and without limiting Section 12.4(c), if CoreLogic intends to withhold Charges, it shall notify Supplier before their due date. |
| |
| (b) | Continued Performance. Each Party agrees to continue performing its obligations under this Agreement while any dispute is being resolved unless and until such obligations are terminated by the termination or expiration of this Agreement. |
| |
| (c) | No Waiver. Neither the failure to dispute any Charges prior to payment nor the failure to withhold any amount shall constitute, operate or be construed as a waiver of any right CoreLogic may otherwise have to dispute any Charge or recover any amount previously paid. |
| |
| (d) | Modified Invoice. Upon resolution of the dispute, Supplier will prepare and transmit to CoreLogic a modified invoice with the portion of the disputed Charges (if any) that have been determined to be payable by CoreLogic as a result of such resolution. For clarity, CoreLogic will pay undisputed Charges in accordance with the terms of this Article 12. |
| |
| (e) | Escrow of Disputed Amounts. If the aggregate amount of all Charges then under dispute pursuant to this Section 12.4 exceeds an amount equal to *** (***) *** the *** based upon amounts invoiced over the prior *** (***) *** (i.e., the *** during the prior *** (***) *** by *** (***)), CoreLogic shall, within ten (10) days after notice from Supplier, pay the excess into an interest-bearing escrow account. The escrow account shall be mutually established by the Parties at a financial institution agreed to by the Parties. The escrow shall be maintained pursuant to an escrow agreement to be agreed to by the Parties, and unless and until agreed, shall be substantially in the form of the standard form of escrow agreement provided by the financial institution. The costs of such escrow shall be borne equally by the Parties and, unless otherwise determined in accordance with the dispute resolution process in Article 19, interest on the escrowed amounts shall be allocated to the prevailing Party in the dispute. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 47 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
13. CORELOGIC DATA AND OTHER CONFIDENTIAL INFORMATION.
| |
| 13.1 | Confidential Information. |
Nothing in this Section 13.1 is intended to limit the obligations of Supplier under Sections 13.2 and 13.2(c) of this Agreement with respect to the CoreLogic Data addressed in such Sections and, to the extent the provisions of Sections 13.2 or 13.2(c) conflict with the provisions of this Section 13.1 as they pertain to CoreLogic Data, the provisions of Sections 13.2 or 13.2(c) shall control over the provisions of Section 13.1, as applicable.
| |
| (a) | Confidential Information. As used herein, “Confidential Information” means (i) this Agreement and the terms hereof and thereof, (ii) all information marked confidential, proprietary or similar legend by either Party, and (iii) any other information that is treated as confidential by the disclosing Party and would reasonably be understood to be confidential, whether or not so marked (which, in the case of the Eligible Recipients and any of their customers, shall include information treated or categorized as confidential under the CoreLogic Privacy Policy in Schedule 8, CoreLogic Software, ***, CoreLogic Data, Personal Data, Authorized User information, and (A) any information with respect to any customer of CoreLogic or any Eligible Recipient (including information about customers or clients of any such customers), (B) attorney-client privileged materials, attorney work product, and CoreLogic customer lists, (C) CoreLogic contracts, CoreLogic rates and pricing, information with respect to competitors, strategic plans, account information, and research information, and (D) any information contemplated by clauses (ii) or (iii) above (to the extent not already part of CoreLogic Data) that contains CoreLogic or other Eligible Recipient trade secrets, financial/accounting information, human resources/personnel information, marketing/sales information, contact information, information regarding businesses, plans, operations, mergers, acquisitions, divestitures, third party contracts, licenses, internal or external audits, law suits, arbitrations, mediations, and regulatory compliance or other information or data obtained, received, transmitted, processed, stored, archived, or maintained by Supplier under this Agreement on behalf of CoreLogic). In the case of Supplier, Confidential Information shall include financial information, account information, information regarding Supplier’s business plans and operations (including information relating to Supplier’s relationships with its customers, employees and contractors), and proprietary Systems, software, tools, technologies and methodologies owned or licensed by Supplier and used in the performance of the Services, as well as Supplier Owned Developed Materials, subject to the license rights granted from Supplier to the Eligible Recipients pursuant to Section 14.2(c). |
| |
| (b) | Disclosure of Confidential Information. |
| |
| (i) | During the Term and at all times thereafter as specified in Section 13.4, each receiving Party (A) shall hold Confidential Information received from a disclosing Party in confidence and shall use such Confidential Information only for the purposes of fulfilling its obligations or exercising its rights under this Agreement and for no other purposes, and (B) shall not disclose, provide, disseminate or otherwise make available any Confidential Information of the disclosing Party to any third party without the express written permission of the disclosing Party, unless expressly permitted by Sections 13.1(b)(ii) and 13.1(b)(iii) below or elsewhere in this Agreement. Each receiving Party shall use at least the same degree of care to safeguard and to prevent unauthorized access, disclosure, publication, destruction, loss, alteration or use of the disclosing Party’s Confidential Information as the receiving Party employs to protect its own information (or information of its similarly-situated customers) of a similar nature, but not less than reasonable care. |
| |
| (ii) | A receiving Party may disclose Confidential Information of the disclosing Party to its employees, directors, attorneys, auditors, accountants, financial advisors and similar professionals, contractors and agents provided that (A) such person or entity has a need to know the Confidential Information for purposes of performing his or her obligations under or with or to enforce its rights under or with respect to this Agreement or as otherwise naturally occurs in such person’s scope of responsibility, (B) such disclosure is made pursuant to an obligation of confidentiality that is no less stringent than that set forth in this Section 13.1, and (C) such disclosure is not in violation of Law. The receiving |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 48 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Party assumes full responsibility for the acts or omissions of any person or entity to whom it discloses Confidential Information of the disclosing Party regarding their use of such Confidential Information.
| |
| (iii) | A receiving Party may disclose Confidential Information of a disclosing Party as required to satisfy any legal requirement of a competent government body, provided that, promptly upon receiving any such request, the receiving Party, to the extent it may legally do so, gives notice to the disclosing Party of the Confidential Information to be disclosed and the identity of the third party requiring such disclosure so that the disclosing Party may interpose an objection to such disclosure, take action to assure confidential handling of the Confidential Information, or take such other action as it deems appropriate to protect the Confidential Information. The receiving Party shall reasonably cooperate with the disclosing Party in its efforts to seek a protective order or other appropriate remedy or, in the event such protective order or other remedy is not obtained, to obtain assurance that confidential treatment will be accorded such Confidential Information. |
| |
| (iv) | Unless expressly permitted by this Agreement, neither Party shall (A) make any use or copies of the Confidential Information of the other Party except as expressly contemplated by this Agreement, (B) possess or acquire any right in or assert any lien against the Confidential Information of the other Party, (C) sell, assign, transfer, lease, encumber, or otherwise dispose of or disclose the Confidential Information of the other Party to third parties, (D) commercially exploit, or permit a third party to commercially exploit, such Confidential Information, or (E) refuse for any reason (including a default or material breach of this Agreement by the other Party) to promptly provide the other Party’s Confidential Information (including any copies thereof) to the other Party if requested to do so. |
| |
| (1) | Notwithstanding the foregoing, the terms and conditions of this Agreement that are specific to this transaction (as opposed to the general outsourcing terms and conditions as they existed prior to negotiation of this Agreement, which belong to CoreLogic), including the Charges and the Service Levels (collectively, the “Agreement Terms”), but not its existence and not general descriptions of the Services, shall be deemed to be the Confidential Information of each Party. Each Party shall have the right to disclose the Agreement Terms without notice to or consent of the other Party as necessary to enforce any of that Party’s rights or to perform their obligations as set forth in this Agreement, in connection with any audit or Benchmarking, to a proposed acquirer in connection with any potential merger, sale or acquisition of Supplier or an Eligible Recipient (as the case may be), or a sale or transfer of a portion of the business of an Eligible Recipient which business relies, in whole or in part on the Services hereunder, in connection with Supplier or an Eligible Recipient (as the case may be) obtaining any financing or investment, or as otherwise permitted in this Article 13. Prior to disclosing the Agreement Terms to any *** (other than government auditors, inspectors and regulators or as part of a public regulatory filing as described below) the disclosing Party shall cause the applicable third party to execute a non-disclosure agreement in substantially the form of Annex 2 or another form mutually agreed to by the Parties. |
| |
| (2) | Each Party and its Affiliates shall have the right to disclose the Agreement Terms (as part of any public regulatory filings or otherwise) upon at least five (5) business days’ notice to the other Party to the extent required by rules or regulations promulgated by the Securities and Exchange Commission (“SEC”) or any similar governmental or regulatory body having jurisdiction over such Party in any country or jurisdiction, provided that the Parties shall cooperate and seek to minimize disclosure through redaction consistent with such rules and regulations. Prior to any such disclosure or filing, the disclosing Party shall redact such portions of this Agreement that the other Party reasonably requests to be redacted, unless the disclosing Party concludes, based on advice of legal counsel, that such redaction request is not permitted by the disclosing Party’s obligations under applicable Laws. For any redaction efforts, the Parties shall cooperate in good faith to agree upon the appropriate redactions within a timeframe that permits the Eligible Recipient to comply with the applicable Laws; provided, that nothing shall prevent an Eligible Recipient from filing an unredacted version of the |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 49 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Agreement Terms if the redaction cannot reasonably be completed within the timeframe required for the filing or disclosure. Supplier shall reimburse CoreLogic for CoreLogic’s outside legal fees and expenses incurred in connection with the redaction efforts.
| |
| (3) | In connection with the *** from a *** for the *** of the *** from that ***, CoreLogic may disclose Agreement Terms to that *** relating to the financial or operational terms of this Agreement (e.g., applicable Service Levels and measurements of Supplier’s performance with respect to such Service Levels); provided, however, CoreLogic may not divulge Supplier’s pricing for the Services, the terms of the MSA identified as specifically negotiated with Supplier, Supplier’s actual performance of contractual obligations, or Supplier audit results. |
| |
| (c) | Exclusions. Notwithstanding the above, Section 13.1(b) shall not apply to any particular information which the receiving Party can demonstrate (i) is, at the time of disclosure to it, generally available to the public other than through a breach of the receiving Party’s or a third party’s confidentiality obligations; (ii) after disclosure to it, is published by the disclosing Party or otherwise becomes generally available to the public other than through a breach of the receiving Party’s or a third party’s confidentiality obligations; (iii) was lawfully in the possession of the receiving Party immediately prior to the time of disclosure to it without obligation of confidentiality; (iv) is received from a third party having a lawful right to disclose such information; or (v) is independently developed by the receiving Party without reference to the disclosing Party’s Confidential Information. The exclusions in this Section 13.1(d) shall not apply to Personal Data. |
| |
| (d) | Loss of Confidential Information. Each Party shall (i) immediately notify the other Party of any possession, use, knowledge, disclosure, or loss of such other Party’s Confidential Information in contravention of this Agreement, (ii) promptly furnish to the other Party all known details and assist such other Party in investigating and/or preventing the reoccurrence of such possession, use, knowledge, disclosure, or loss, (iii) cooperate with the other Party in any investigation or litigation deemed necessary by such other Party to protect its rights, and (iv) promptly use all commercially reasonable efforts to prevent further possession, use, knowledge, disclosure, or loss of Confidential Information in contravention of this Agreement. Each Party shall bear any costs it incurs in complying with this Section 13.1(d). |
| |
| (e) | No Implied Rights. Nothing contained in this Section 13.1 shall be construed as obligating a Party to disclose its Confidential Information to the other Party, or as granting to or conferring on a Party, expressly or impliedly, any rights or license to any Confidential Information of the other Party. |
| |
| (f) | Return or Destruction of Confidential Information. Within ten (10) days following a request by CoreLogic as to return or destruction of CoreLogic’s Confidential Information, Supplier must, at CoreLogic’s discretion, either return to the CoreLogic all Confidential Information (including all copies/derivatives thereof); or certify in writing to CoreLogic that such Confidential Information (including all copies/derivatives thereof) has been destroyed in such a manner that it cannot be retrieved. In no event shall Supplier withhold any Confidential Information of the CoreLogic as a means of resolving any dispute. Notwithstanding the foregoing, Supplier may retain one copy of CoreLogic’s Confidential Information as and to the extent required to comply with applicable Laws or enforce its rights under this Agreement; provided that such Confidential Information shall be returned or destroyed in accordance with this provision upon the expiration of the period specified in the applicable Law, the expiration of the applicable statute of limitations and the final resolution of any pending dispute. |
Nothing in this Section 13.2 is intended to limit the obligations of Supplier under Section 13.1 or 13.3 of this Agreement with respect to the Confidential Information addressed in such Sections. To the extent that the provisions pertaining to CoreLogic Data in Section 13.1, this Section 13.2, and Section 13.3, the provisions
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 50 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
of Section 13.3 shall control over the provisions of this Section 13.2, which shall control over the provisions of Section 13.1.
| |
| (a) | Ownership of CoreLogic Data. CoreLogic Data shall be and remain, as between the Parties, the property of the relevant Eligible Recipient and any of its customers regardless of whether Supplier or CoreLogic is in possession of the CoreLogic Data. CoreLogic Data shall be made available to CoreLogic, upon its request, at all times, by the means and manner of storage contemplated by this Agreement and the applicable Supplement and in the then existing form and format as reasonably requested by CoreLogic. At no time shall CoreLogic Data be stored or held by Supplier in a form or manner not readily accessible to CoreLogic in this manner. |
| |
| (b) | Safeguarding of CoreLogic Data. |
Supplier and its Affiliates and Subcontractors to whom CoreLogic Data is provided shall maintain an industry standard comprehensive data security program, which shall include reasonable and appropriate technical, organizational and security measures against the destruction, loss, unauthorized access or alteration of CoreLogic Data with respect to Supplier Systems that access, process, transmit or store CoreLogic Data and CoreLogic Systems for which Supplier has operational responsibility. The information security program and associated technical, organizational and security measures maintained by Supplier with respect to such CoreLogic Data shall comply with the following:
| |
| (A) | Subject to Section 15.7, all applicable Laws (in all material respects); |
| |
| (B) | The CoreLogic Policy Sets (i.e., compliance in accordance with standards at least as high or protective as those set forth in the CoreLogic Policy Sets); and |
| |
| (C) | the *** standards as published by *** and the ***, also known as the *** series, as each may be modified or replaced from time to time (in all material respects); and |
| |
| (D) | the requirements set forth in the Schedule 12, which sets forth Supplier’s obligations with respect to security controls, system logs and remote access. |
The content and implementation of the data security program and associated technical, organizational and security measures with respect to the Services shall be fully documented in writing by Supplier and Supplier shall provide such documentation to CoreLogic upon CoreLogic’s request. Supplier shall permit CoreLogic to review such documentation and/or to inspect Supplier’s compliance with such program in accordance with Section 9.10.
| |
| (i) | In addition to adherence to the information security controls, Supplier shall ensure that all Supplier Personnel are trained on (i) the Supplier information security controls no less than annually, and (ii) at CoreLogic’s expense, the CoreLogic Policy Sets, and CoreLogic Code of Ethics and Conduct no less than annually in a format subject to CoreLogic’s written approval. Supplier hereby agrees to ensure that, prior to being granted access to any CoreLogic Data, all Supplier Personnel have undergone appropriate information security training in the *** (***) *** and that new Supplier Personnel have undergone training prior to accessing CoreLogic Data. Subject to any restriction in contracts with Supplier’s other customers, Supplier shall regularly advise CoreLogic of data security practices, procedures and safeguards in effect for *** that, in Supplier’s reasonable judgment, are (1) relevant to the Services being provided under this Agreement and (2) exceed relevant industry standards pertaining to in-scope services. If requested by CoreLogic, Supplier shall, to the extent reasonably practicable and subject to the Change Management Procedures and Schedule 6, implement such enhanced practices, procedures, and safeguards with respect to its provision of Services to CoreLogic hereunder. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 51 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (ii) | CoreLogic shall have the right to establish backup security for any CoreLogic Data and to keep backup copies of such Data in its possession if it chooses. At CoreLogic’s request, Supplier shall provide CoreLogic with downloads of CoreLogic Data to enable CoreLogic to maintain such backup copies. |
| |
| (iii) | Supplier shall maintain a Security Incident Response Plan (“SIRP”) consistent with the CoreLogic Information Security Policy Set and standards and practices used by tier one providers performing services similar to the Services. The SIRP shall detail procedures to be followed in the event of a suspected or actual breach of security involving unauthorized access to or use of CoreLogic Confidential Information in the possession or under the control of Supplier, including but not limited to unauthorized disclosure, theft or manipulation of information, that has the potential to cause harm to CoreLogic or other Eligible Recipients or any of their customers’ systems or information or any targeted attempt at such breach of security that creates or created a significant risk of such harm (“Security Incident”). The SIRP must include a clear, documented escalation procedure and the process for notifying CoreLogic of a Security Incident on an immediate basis with respect to material risks and otherwise within applicable timelines required by the CoreLogic Policy Sets. Supplier agrees to keep CoreLogic informed of the progress and actions taken in connection with Supplier’s investigation of each Security Incident. Supplier will investigate (with CoreLogic’s participation if reasonably requested by CoreLogic) such Security Incident and mitigate the adverse effects of such Security Incident. Supplier shall promptly (and in any event as soon as reasonably practical) (i) perform a Root Cause Analysis and prepare a corrective action plan, (ii) provide CoreLogic with written reports and detailed information regarding any Security Incident, including how and when such Security Incident occurred and what actions Supplier is taking to remedy such Security Incident, (iii) cooperate in the investigation of the Security Incident at CoreLogic’s request, and (iv) to the extent such Security Incident is within Supplier’s or its Subcontractor’s or Affiliate’s areas of control, remediate such Security Incident and take commercially reasonable actions to prevent its recurrence. Nothing in this Article 13 is intended to create a standard of strict liability for a Security Incident. Supplier’s failure to perform its responsibilities under this Article 13 shall be excused if and to the extent that such Supplier non-performance is caused by an Eligible Recipient’s or Authorized User’s or Third Party Contractor’s failure to comply in any material respect with CoreLogic Rules that must be implemented or followed by them, including as set forth in the CoreLogic Information Security Policy Set and the CoreLogic Compliance Policy Set. Where Supplier is aware of the failure to comply and the circumstances allow, Supplier’s ability to claim excuse of performance under the prior sentence is conditioned on Supplier’s compliance with, and Supplier shall follow the notice and other procedures and requirements of, Section 10.2. |
| |
| (iv) | To the extent Supplier removes CoreLogic Data from any media under its control that is taken out of service, Supplier shall destroy or securely erase such media in accordance with the Policy and Procedures Manual. Under no circumstances shall Supplier use or re-use media on which CoreLogic Data has been stored for any purpose unless such CoreLogic Data has been securely erased in accordance with the Policy and Procedures Manual. |
| |
| (v) | CoreLogic shall solely determine whether to provide notification to CoreLogic customers, employees, agents or government authorities concerning a Security Incident as well as the content of such notification (other than in connection with a *** in which case notification requirements shall be governed solely by ***); provided that if Supplier is obligated under applicable Laws to provide such notification and CoreLogic determines to not provide such notification, Supplier shall have the right to provide such notification, provided that Supplier notifies CoreLogic of its intention and consults with CoreLogic (including with respect to the content of such notification, where CoreLogic shall have the right to approve such communication, such approval not to be unreasonably withheld) in connection with such notification. In addition, if, Supplier has an independent obligation under a separate contract between Supplier and one of CoreLogic’s customers, nothing herein shall limit Supplier’s right to provide notification under the terms therein. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 52 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (c) | Correction of CoreLogic Data. The correction of any errors or inaccuracies in or with respect to CoreLogic Data shall be performed by *** at its sole cost and expense if (i) *** is operationally responsible for inputting such data, or (ii) such errors or inaccuracies are attributable to the failure of *** or *** to comply with *** obligations under this Agreement. In that case, *** shall be financially responsible for any additional resource usage resulting from the re-running of corrected data. |
| |
| (d) | Restoration of CoreLogic Data. The restoration of any destroyed, lost or altered CoreLogic Data shall be performed by the Party that has operational responsibility for maintaining the System on which such CoreLogic Data resides and for creating and maintaining backup copies of such CoreLogic Data. To the extent (i) *** is operationally responsible for performing such restoration or (ii) such destruction, loss or alteration is attributable to the failure of *** or *** to comply with *** obligations under this Agreement, *** shall bear the cost of restoring such data using generally accepted data restoration techniques, including use of last available back-up, and in accordance with the techniques described in the Policy and Procedures Manual and the applicable Supplement to the extent described therein. |
| |
| (e) | Cardholder Data. Supplier shall comply with the Payment Card Industry Data Security Standard (“PCI DSS”) to the extent applicable to the Services. |
| |
| (a) | Privacy Laws. Supplier acknowledges that the CoreLogic Data is subject to Laws, in multiple jurisdictions worldwide, restricting collection, use, processing and free movement of personal data. Supplier also shall hold any Personal Data that it receives in confidence and in compliance with Supplier’s obligations under this Agreement, the Policy and Procedures Manual, the data privacy policy of CoreLogic communicated in advance to Supplier and CoreLogic’s contractual obligations to CoreLogic’s customers communicated to Supplier pursuant to Section 9.17. In addition, and without limiting the foregoing, Supplier shall provide CoreLogic with all assistance as CoreLogic may reasonably require to fulfill the responsibilities of CoreLogic and the other Eligible Recipients and any of their customers under data Privacy Laws. Supplier shall not use terms of use or privacy statements that vary from this Agreement or enter into separate agreements between Supplier and Authorized Users or other individuals of Eligible Recipients or any of their customers that offer less protection with respect to the Personal Data of Authorized Users or other individuals’ Personal Data than the protections provided in this Agreement. As between the Parties, in the event that the applicable Law of a jurisdiction requires consent from a data subject prior to providing such data to Supplier, CoreLogic shall be responsible for obtaining such consent prior to passing the Personal Data to Supplier. |
| |
| (i) | Unless otherwise agreed, Supplier shall process and store all Personal Data in (1) the jurisdiction(s) set forth in Schedule 7, (2) the jurisdiction in which the data subject resides (or, in the case of a data subject residing in the European Economic Area (“EEA”), in the EEA, or for a data subject residing in another jurisdiction that has Privacy Laws or data transfer requirements, in that jurisdiction), (3) the jurisdictions and locations set forth in the applicable Supplement, or (4) any other service locations approved in writing in advance by CoreLogic, and shall not transfer, process, or store CoreLogic Data in any other jurisdiction or location without the prior consent of CoreLogic. |
| |
| (ii) | Supplier and CoreLogic shall not transfer Personal Data from a country within the EEA to countries deemed by the European Union not to have adequate protection without first ensuring that the standard contractual clauses approved by the European Commission in Commission Decision 2010/87/EU as the standard contractual clauses for the transfer of personal data to processors in third countries under applicable EU Directives (e.g., Directive 95/46/EC, 2002 O.J. L6/52 as of the Effective Date) and any implementing legislation are in place between the CoreLogic Affiliate that is the Data Exporter and the Data Importer, and any such contract is filed by CoreLogic with the appropriate regulatory agency if required by applicable Laws. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 53 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (iii) | Supplier shall maintain technical, organizational and security measures to protect the confidentiality of Personal Data in accordance with the obligations contained in this Article 13. |
| |
| (iv) | Notwithstanding any other provision of this Agreement, Supplier shall not undertake or engage in any activity with respect to any Personal Data that would constitute Supplier’s functioning in the capacity of a “controller,” as such capacity may be identified and defined in the respective applicable Privacy Laws and Supplier shall promptly notify CoreLogic if it believes that any use of Personal Data by Supplier contemplated under this Agreement or to be undertaken as part of the Services would constitute Supplier so functioning in the capacity of a “controller”. The Parties acknowledge that, for purposes of the European Data Protection Legislation and similar legislation in other jurisdictions, Supplier will act as a Data Processor in relation to all Personal Data it accesses under this Agreement, that CoreLogic is the Data Controller with respect to such Personal Data, and that Supplier will act in accordance with CoreLogic's instructions in relation to such Personal Data. |
| |
| (v) | Supplier and CoreLogic shall comply with applicable Laws relating to Personal Data and the handling, processing, security and transfer of Personal Data in jurisdictions that impact Services or Personal Data, whether such Laws are in place as of the Commencement Date or are enacted, adopted or otherwise come into effect during the term of this Agreement. Supplier and CoreLogic agree to cooperate to enter into any appropriate agreements relating to such new Laws as and when they apply, including data processing agreements between Supplier or the applicable Supplier Affiliate and the applicable CoreLogic Affiliate(s). Supplier, its Affiliates and Subcontractors shall cooperate with CoreLogic with respect to any registrations, filings or responses for applicable governmental organizations, data protection authorities, data protection working groups or commissions, works councils, or other third party obligations and requests related to the Services. |
| |
| (b) | Limitations on Use. Supplier agrees that Supplier and Supplier Personnel will not use Personal Data for any purpose or to any extent other than as necessary to fulfill Supplier's obligations under this Agreement. Supplier and Supplier Personnel shall not process, transfer or disseminate Personal Data without the approval of CoreLogic unless expressly provided for in this Agreement. Supplier shall take appropriate action to ensure that Supplier Personnel having access to Personal Data are advised of the terms of this Section and trained regarding their handling of Personal Data. All such Supplier Personnel’s access to Personal Data must be governed by a non-disclosure agreement that prohibits the personnel from using, disclosing or copying the Personal Data for any purpose except as required for the performance of this Agreement. Supplier is and Supplier shall be responsible for any failure of Supplier Personnel to comply with the terms and conditions regarding Personal Data. |
| |
| (d) | HIPAA. If Supplier or Supplier Personnel will have access to “protected health information” (as such term is defined by the HIPAA Privacy Rule), Supplier and CoreLogic shall execute a Business Associate Agreement in the form attached hereto as Annex 4. Supplier and Supplier Personnel shall comply with the terms of the Business Associate Agreement in performing the applicable Services. The Eligible Recipients and their personnel shall comply with the terms of the Business Associate Agreement in performing their obligations under this Agreement. |
| |
| (e) | Unauthorized Disclosure or Access. If Supplier or Supplier Personnel have knowledge of or suspect any unauthorized possession, use, knowledge, loss, disclosure of or access to Personal Data in contravention of this Agreement, Supplier shall, in addition to its obligations with regard to Security Incidents set forth in Section 13.2(b)(iii), (i) immediately report to CoreLogic such possession, use, knowledge, loss, disclosure or access to Personal Data and promptly furnish to CoreLogic all known details; (ii) immediately take steps to mitigate any harmful effects of such possession, use, knowledge, loss, disclosure or access; (iii) cooperate with CoreLogic in any investigation, litigation, or provision of notices that CoreLogic deems appropriate and (iv) promptly use all commercially reasonable efforts to prevent further possession, use, knowledge, disclosure or loss of Personal Data in contravention of this |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 54 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Agreement. To the extent any unauthorized disclosure of or access to Personal Data arises out of or is connected to a breach by *** or *** of *** obligations under this Agreement, *** shall bear (A) the costs incurred *** in complying with its legal obligations relating to such breach, and (B) in addition to any other damages *** for under this Agreement, the following costs incurred by *** or any of their *** in responding to such breach, to the extent applicable: (1) the cost of providing notice to affected individuals; (2) the cost of providing notice to government agencies, credit bureaus, and/or other required entities; (3) *** individuals with *** (which *** to the extent *** then owns a business engaged in providing ***) for a specific period not to exceed *** (***) *** or the minimum time period provided by applicable Law, whichever is longer; (4) *** for such *** for a specific period not to exceed thirty (30) days; and (5) the cost of any other measures required under applicable Law (collectively, the “Data Breach Costs”).
Supplier’s obligations under this Article 13 shall survive the expiration or termination of this Agreement and ***.
| |
| 14. | OWNERSHIP OF MATERIALS. |
| |
| 14.1 | CoreLogic Owned Materials. |
| |
| (a) | Ownership of CoreLogic Owned Materials. For purposes of this Agreement, as between the Parties, CoreLogic shall be the sole and exclusive owner of (i) all Materials lawfully owned by the Eligible Recipients or any of their customers as of or after the Effective Date, (ii) all enhancements and Derivative Works of such Materials, including all United States and international patent, copyright and other intellectual property rights in such Materials, (iii) certain Developed Materials as provided in Section 14.2(a) and 14.2(d), and all United States and international patent, copyright and other intellectual property rights in such Materials described in clauses (i) through (iii) (collectively, “CoreLogic Owned Materials”). |
| |
| (b) | License to CoreLogic Owned Materials. CoreLogic hereby grants to Supplier and, to the limited extent necessary for Supplier to provide the Services, to Subcontractors designated by Supplier that are party to a written agreement with Supplier by which they are bound by terms at least as protective as the terms contained herein applicable to such Materials, a non-exclusive, non-transferable, royalty-free limited right and license during the Term (and thereafter to the extent necessary to perform any Disengagement Services requested thereunder by CoreLogic) to access, use, execute, reproduce, display, perform, modify, distribute and create Derivative Works of the CoreLogic Owned Materials for the express and sole purpose of providing the Services. Supplier and its Subcontractors shall have no right to the source code to such CoreLogic Owned Materials unless and to the extent necessary for Supplier to provide the Services or approved in advance by CoreLogic. CoreLogic Owned Materials shall remain the property of CoreLogic. Supplier and its Subcontractors shall not (i) use any CoreLogic Owned Materials for the benefit of any person or Entity other than CoreLogic, the other Eligible Recipients or the Authorized Users, (ii) separate or uncouple any portions of the CoreLogic Owned Materials, in whole or in part, from any other portions thereof unless and to the extent such separation or uncoupling is necessary for Supplier to provide the Services, or (iii) reverse assemble, reverse engineer, translate, disassemble, decompile or otherwise attempt to create or discover any source code, underlying algorithms, ideas, file formats or programming interfaces of the CoreLogic Owned Materials by any means whatsoever, without the prior approval of CoreLogic, which may be withheld at CoreLogic’s sole discretion. Except as otherwise requested or approved by CoreLogic, Supplier and its Subcontractors shall cease all use of CoreLogic Owned Materials upon the end of the Term and the completion of any Disengagement Services requested thereunder by CoreLogic pursuant to Section 20.8(b)(7) and shall certify such cessation to CoreLogic in a notice signed by an authorized representative of Supplier at least at the level of Vice President within Supplier’s organization. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 55 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (c) | License to CoreLogic Licensed Third Party Materials. Subject to Supplier or CoreLogic, as applicable, having obtained any Required Consents, CoreLogic hereby grants to Supplier, during the Term (and thereafter to the limited extent necessary to perform any Disengagement Services requested by CoreLogic), for the sole purpose of performing the Services and solely to the extent of CoreLogic’s underlying rights, the same rights of access and use as CoreLogic possesses under the applicable software licenses with respect to CoreLogic licensed Third Party Materials. CoreLogic also shall grant such rights to *** if and to the extent necessary for Supplier to provide the Services; provided that, *** shall *** associated with the granting of such rights to such *** (other than with respect to ***). Supplier and its Subcontractors shall comply with the duties, including use restrictions and nondisclosure obligations, imposed on CoreLogic by such licenses. If and to the extent, in the course of the performance of the Transition Services for an applicable Supplement, Supplier identifies any deficiency or gap between CoreLogic’s compliance with such licenses as of the Supplement Effective Date and the duties imposed on CoreLogic by such licenses, Supplier shall notify CoreLogic and CoreLogic shall have the right, in its sole discretion to (a) eliminate such deficiency or gap with the reasonable assistance of Supplier, (b) require Supplier to eliminate such deficiency or gap, in which case CoreLogic shall be financially responsible for such elimination, or (c) establish a waiver with respect to such deficiency or gap, in which case Supplier shall use reasonable efforts to become compliant with such duties as soon as reasonably practicable notwithstanding such waiver. In addition, each Subcontractor shall have signed a written agreement with Supplier to be bound by terms consistent with the terms contained herein applicable to such Third Party Materials (including, to the extent relevant, the terms specified in this Section as well as those pertaining to the ownership of such Materials and any Developed Materials, the scope and term of the license, the restrictions on the use of such Materials, and the obligations of confidentiality). Except as otherwise requested or approved by CoreLogic (or the relevant licensor), Supplier and its Subcontractors shall cease all use of such Third Party Materials upon the end of the applicable Term and the completion of any Disengagement Services requested thereunder by CoreLogic pursuant to Section 20.8(b)(7). |
| |
| (d) | Disclaimer. THE CORELOGIC OWNED MATERIALS AND THE CORELOGIC LICENSED THIRD PARTY MATERIALS ARE PROVIDED BY CORELOGIC TO SUPPLIER AND ITS SUBCONTRACTORS ON AN AS-IS, WHERE-IS BASIS. CORELOGIC EXPRESSLY DISCLAIMS ANY REPRESENTATIONS OR WARRANTIES, EXPRESS OR IMPLIED, AS TO SUCH MATERIALS, OR THE CONDITION OR SUITABILITY OF SUCH MATERIALS FOR USE BY SUPPLIER OR ITS SUBCONTRACTORS TO PROVIDE THE SERVICES, INCLUDING WARRANTIES OF NON-INFRINGEMENT, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. |
| |
| (a) | Ownership by ***. Except as provided in Sections 14.2(c) and (d) or otherwise agreed by the Parties, *** shall be the sole and exclusive owner of all Developed Materials (i) that are identified in a Project as to be owned by an Eligible Recipient, (ii) for which Supplier *** in the creation of such Developed Materials or *** CoreLogic Confidential Information *** such Developed Materials, (iii) for which an Eligible Recipient has provided the *** for the production of such Developed Material, (iv) which is *** to an Eligible Recipient’s business, or (v) with respect to any Application of an Eligible Recipient, that are part of, derivative to, or *** such Application and/or associated databases (i.e., ***, extensions, queries and Materials of a similar nature), including all United States and international patent, copyright and other intellectual property rights in such Materials (“CoreLogic Owned Developed Materials”). Such Developed Materials shall be considered works made for hire (as that term is used in Section 101 of the United States Copyright Act, 17 U.S.C. § 101, or in analogous provisions of other applicable Laws) owned by CoreLogic. If any such Developed Materials may not be considered a work made for hire under applicable Law, *** hereby irrevocably assigns, and shall assign, to *** in perpetuity without further consideration, all of *** worldwide rights, title and interest in and to such Developed Materials, including United States and foreign intellectual property rights. *** and the successors and assigns of *** shall have the right to obtain and hold in their own name any intellectual property rights in and to such Developed Materials. *** agrees to execute any documents and take any other actions reasonably requested by *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 56 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
to effectuate the purposes of this Section 14.2(a). *** hereby grants to *** a license to such Developed Materials on the same terms as described in Section 14.1(b). *** may, in its sole discretion and upon such terms and at such financial arrangement as CoreLogic and Supplier may agree, grant *** a license to use the Developed Materials for other purposes and to sublicense such Developed Materials.
| |
| (b) | *** *** Documentation. |
| |
| (i) | With Respect to CoreLogic Owned Developed Materials. If any CoreLogic Owned Developed Material includes Software, Supplier shall, promptly as it is developed by Supplier, provide CoreLogic with all of the *** object code and documentation for such CoreLogic Owned Developed Materials. Such *** technical documentation shall be sufficient to allow a reasonably knowledgeable and experienced *** to maintain and support such Materials, and the user documentation for such Materials shall accurately describe in terms understandable by a *** the functions and features of such Materials and the procedures for exercising such functions and features. |
| |
| (ii) | With Respect to Supplier Owned Developed Materials Other Than Perpetual License Exceptions. If any Supplier Owned Developed Material other than Perpetual License Exceptions includes Software, Supplier shall, promptly as it is developed by Supplier, provide CoreLogic with all of the object code and documentation for such Supplier Owned Developed Materials. If Supplier ceases creating Upgrades and/or maintenance updates of any such Supplier Owned Developed Material (as contemplated by Section 14.2(c)(iii)), upon CoreLogic’s request, Supplier shall provide CoreLogic with the *** and technical documentation for such Supplier Owned Developed Materials. Such *** and technical documentation shall be sufficient to allow a reasonably knowledgeable and experienced programmer to maintain and support such Materials, and the user documentation for such Materials shall accurately describe in terms understandable by a typical end user the functions and features of such Materials and the procedures for exercising such functions and features. |
| |
| (c) | *** Developed Materials. |
| |
| (i) | Ownership. *** shall be the sole and exclusive owner of (i) all Developed Materials notwithstanding Section 14.2(a), that are enhancements or Derivative Works of ***Materials and (ii) all other Developed Materials that are not *** Developed Materials, including all United States and foreign patent, copyright and other intellectual property rights in such Materials (“*** Developed Materials”). *** hereby irrevocably assigns, and shall assign, to *** in perpetuity without further consideration, all of *** worldwide rights, title and interest in and to such *** Developed Materials, including United States and foreign intellectual property rights. *** and the successors and assigns of *** shall have the right to obtain and hold in their own name any intellectual property rights in and to such *** Developed Materials. *** agrees to execute any documents and take any other actions reasonably requested by *** to effectuate the purposes of this Section 14.2(c). |
| |
| (ii) | Perpetual License to Eligible Recipients. Except with respect to Perpetual License Exceptions (as defined in clause (iv)), Supplier hereby grants to the Eligible Recipients (and at CoreLogic’s request, *** that sign a written agreement with CoreLogic to be bound by terms at least as protective as the terms contained herein applicable to such Materials) a *** license, with the right to grant sublicenses (other than to *** for the commercial exploitation by such *** with its other customers), to use, execute, reproduce, display, perform, modify, enhance, distribute and create Derivative Works of Supplier Owned Developed Materials other than the Perpetual License Exceptions for the benefit of CoreLogic, the other Eligible Recipients and their respective Affiliates. |
| |
| (iii) | Upgrades and Maintenance Updates. In addition to the perpetual licenses granted in Section 14.2(c)(ii) with respect to Supplier Owned Developed Materials other than the Perpetual License Exceptions, Supplier shall, at CoreLogic’s request, provide to the Eligible Recipients, Upgrades and/or other maintenance updates (e.g., bug fixes) that Supplier creates with respect to such Supplier Owned Developed Materials (whether or not created for, or on behalf of, CoreLogic) (for the avoidance |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 57 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
of doubt, not including enhancements and Derivative Works created on behalf of a Supplier customer to the extent it is created for such customer’s specific business requirements) during or after the Term, and such Upgrades and other maintenance updates shall be deemed to be part of such Supplier Owned Developed Materials. Supplier’s sole compensation for the provision of such Upgrades and/or other maintenance updates at CoreLogic’s request shall be a maintenance fee calculated at rates consistent with maintenance fees generally commercially available in the industry for similar updates and maintenance services, reduced by an equitable percentage discount (to be determined in good faith by the Parties) reflecting CoreLogic’s initial contribution in the creation of the underlying Supplier Owned Developed Materials.
| |
| (iv) | Perpetual License Exceptions. “Perpetual License Exceptions” means Supplier Owned Developed Materials that are (x) Derivative Works of the Supplier Owned Materials under clause (i) or (ii) of the definition of Supplier Owned Materials or (y) created in Supplier’s performance of IT *** (e.g., ***) (collectively, “Perpetual License Exceptions”). Notwithstanding the preceding sentence, Supplier Owned Developed Materials created in the performance of *** Services, *** Services, *** Services, and Projects that are for the performance of *** Services are not, and shall not be deemed to be Perpetual License Exceptions. In addition, if, in the course of performance of the *** Services, Supplier agrees to build a tool for CoreLogic at CoreLogic’s specific request and at CoreLogic’s expense (i.e., a one-time or project-oriented cost), then any Supplier Owned Developed Materials created in the course of building such tool shall not be a Perpetual License Exception. With respect to Supplement A, the Parties agree that the following Service Areas are *** Services for purposes of the definition of Perpetual License Exceptions: ***. All Perpetual License Exceptions shall be deemed Supplier Owned Materials for which the Eligible Recipients are hereby granted licenses pursuant to, to the extent, and in accordance with Sections 14.3(b) and 14.6. |
| |
| (d) | Third Party Materials. Notwithstanding Sections 14.2(a) and (c), the ownership of Derivative Works of Third Party Materials created by Supplier in the course of providing the Services shall, as between Supplier and CoreLogic, be considered Developed Materials owned by the Party that has the license pursuant to which such Derivative Works are created. For purposes of the foregoing, Supplier shall be deemed the licensee of Third Party Materials licensed by its Subcontractors or Affiliates and CoreLogic shall be deemed the licensee of Third Party Materials licensed by CoreLogic Affiliates or any other Eligible Recipients. Each Party acknowledges and agrees that its ownership of such Derivative Works may be subject to or limited by the terms of the underlying agreement with the owner of the underlying Third Party Materials; provided, that if a Derivative Work is to be made of Third Party Materials provided by Supplier, Supplier shall notify CoreLogic in advance and obtain CoreLogic’s consent prior to proceeding with such Derivative Work if the terms of any such agreement will preclude or limit, as applicable, CoreLogic’s license rights in and to such Derivative Work as contemplated in Sections 14.3 and 14.6. |
| |
| (e) | Disclosure by Supplier of Developed Materials. Supplier shall promptly disclose in writing to CoreLogic each Developed Material that is developed in connection with the Services. With respect to each disclosure, Supplier shall indicate the features or concepts that it believes to be new or different. |
| |
| (f) | Waiver of Moral Rights. To the extent permitted by Law, Supplier hereby waives and shall cause Supplier Personnel who will provide any Services to waive any moral rights in the *** Developed Materials, such as the right to be named as author, the right to modify, the right to prevent mutilation and the right to prevent commercial exploitation, whether arising under the Berne Convention or otherwise. *** acknowledges the receipt of equitable compensation for its assignment and waiver of such moral rights and agrees to provide equitable compensation to *** for any assignment or waiver of moral rights. |
| |
| 14.3 | Supplier Owned Materials. |
| |
| (a) | Ownership of Supplier Owned Materials. For purposes of this Agreement, as between the Parties, Supplier shall be the sole and exclusive owner of the (i) Materials lawfully owned by it prior to the Effective Date, (ii) Materials acquired by Supplier on or after the Effective Date other than acquisitions |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 58 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
for an Eligible Recipient in connection with the performance of the Services, and (iii) Supplier Owned Developed Materials as provided in Section 14.2(c), and all United States and foreign intellectual property rights in such Materials described in clauses (i) through (iii) (“Supplier Owned Materials”).
| |
| (b) | License to Supplier Owned Materials. Without limiting any license grants set forth in Section 14.2(c) with respect to Supplier Owned Developed Materials or Section 14.3(d) with respect to embedded Supplier Owned Materials as described therein, as of the Commencement Date, Supplier hereby grants to the Eligible Recipients (and at CoreLogic’s request, *** that sign a written agreement with CoreLogic to be bound by terms at least as protective as the terms contained herein applicable to such Materials), at no additional charge, a *** right and license, to *** of the Supplier Owned Materials (including all modifications, replacements, Upgrades, enhancements, methodologies, tools, documentation, materials and media related), during the Term and any Disengagement Services period, for the benefit of the Eligible Recipients, solely to (i) receive the *** provided by Supplier, (ii) monitor, access, interface with or use the Materials and Software then being used by Supplier to the extent contemplated by this Agreement, (iii) perform or *** services and functions that are *** to the *** provided by Supplier, (iv) perform*** services or functions previously performed *** in circumstances in which the services or functions in question have *** or *** from ***; provided that this clause (iv) shall not be available to CoreLogic for use in connection with *** are being performed by a *** (i.e., ***), or (v) perform *** services that are the *** to the Services to the extent such Supplier Owned Material is necessary to *** CoreLogic Owned Materials, CoreLogic licensed Third Party Materials or other Materials as to which CoreLogic holds a license under this Agreement. Subject to the rights granted in Section 14.3(d) with respect to Supplier Owned Materials embedded in CoreLogic Owned Developed Materials and Section 14.2(c) with respect to Supplier Owned Developed Materials, the Eligible Recipients *** shall not (1) separate or uncouple any portions of the Supplier Owned Materials, in whole or in part, from any other portions thereof, or (2) reverse assemble, reverse engineer, translate, disassemble, decompile or otherwise attempt to create or discover any source code, underlying algorithms, ideas, file formats or programming interfaces of the Supplier Owned Materials by any means whatsoever, without the prior approval of Supplier, which may be withheld at Supplier’s sole discretion. The rights and obligations of the Eligible Recipients with respect to such Supplier Owned Materials following the expiration or termination of this Agreement or termination of any Service are set forth in Section 14.6. |
| |
| (c) | License to Supplier Third Party Materials. As of the Commencement Date and subject to Supplier having obtained any Required Consents, Supplier hereby grants to the Eligible Recipients (and at CoreLogic’s request, *** that sign a written agreement with CoreLogic to be bound by terms at least as protective as the terms contained herein applicable to such Third Party Materials), at no additional charge, a *** right and license to *** the Third Party Materials that Supplier is required to provide under the terms of this Agreement or the applicable Supplement (e.g., pursuant to a financial responsibilities matrix attached thereto) (including all available modifications, substitutions, Upgrades, enhancements, methodologies, tools, documentation, materials and media related thereto), during the Term and any Disengagement Services period, for the benefit of CoreLogic, the Eligible Recipients and their respective Affiliates, solely to (i) receive *** provided by Supplier, (ii) monitor, access, interface with or use the Materials and Software then being used by Supplier to the extent contemplated by this Agreement, (iii) perform *** services and functions that are *** to the *** provided by Supplier, (iv) perform*** services or functions previously performed *** in circumstances in which the services or functions in question have *** or *** from ***; provided that this clause (iv) shall not be available to CoreLogic for use in connection with *** are being performed by a *** (i.e., ***), or (v) perform *** services that are the *** to the extent such Third Party Materials are necessary to *** CoreLogic Owned Materials, CoreLogic licensed Third Party Materials or other Materials as to which CoreLogic holds a license under this Agreement. The rights and obligations of CoreLogic, the Eligible Recipients *** with respect to such Supplier licensed Third Party Materials following the expiration or termination of this Agreement or termination of any Service are set forth in Section 14.6. |
| |
| (d) | Embedded Materials. To the extent that *** Materials are embedded in any *** Developed Materials, *** shall not be deemed to have assigned its intellectual property rights in such *** Materials to ***, but |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 59 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
*** hereby grants to *** (and at *** request, *** that sign a written agreement with *** to be bound by terms at least as protective as the terms contained herein applicable to such Materials) a *** to *** of such *** Materials for the benefit of *** and *** respective Affiliates for so long as such *** Materials remain embedded in such Developed Materials and are not separately commercially exploited. *** shall, at *** request and subject to Section 14.6(b)(ii), provide to *** the *** and object code for such embedded *** Materials (except for *** Materials that are generally commercially available Software).
This Agreement shall not confer upon either Party intellectual property rights in Materials of the other Party (to the extent not covered by this Article 14) unless otherwise so provided elsewhere in this Agreement.
| |
| (a) | Copyright Legends. Each Party agrees to reproduce copyright legends which appear on any portion of the Materials which may be owned by the other Party or third parties. |
| |
| (b) | No Implied Licenses. Except as expressly specified in this Agreement, nothing in this Agreement shall be deemed to grant to one Party, by implication, estoppel or otherwise, license rights, ownership rights or any other intellectual property rights in any Materials owned by the other Party or any Affiliate of the other Party (or, in the case of Supplier, any Eligible Recipient or any of its customers). |
| |
| (c) | Residuals. Without limiting either Party’s obligations (or the obligations of a Party’s employees or representatives) under this Agreement with respect to the disclosure or use of Confidential Information of the other Party or CoreLogic Data, nothing in this Agreement shall restrict any employee or representative of a Party from using general ideas, concepts, practices, learning or know-how that is (i) relating to the Services and (ii) not Confidential Information or CoreLogic Data, that are retained solely in the unaided memory of such employee or representative after performing the obligations of such Party under this Agreement. |
| |
| (d) | Incorporated Materials. Should either Party incorporate into Developed Materials any intellectual property subject to third party patent, copyright or license rights, any ownership or license rights granted herein with respect to such Materials shall be limited by and subject to any such patents, copyrights or license rights; provided that, prior to incorporating any such intellectual property in any Materials, the Party doing so discloses this fact and obtains the prior approval of the other Party. |
| |
| 14.6 | CoreLogic Rights Upon Expiration or Termination of Agreement. |
Without limiting any license grants set forth in Section 14.2(c) with respect to Supplier Owned Developed Materials or Section 14.3(d) with respect to embedded Supplier Owned Materials as described therein, as part of the Disengagement Services, Supplier shall provide the following to the Eligible Recipients with respect to Materials and Software:
| |
| (a) | CoreLogic Owned Materials and Developed Materials. With respect to CoreLogic Owned Materials (including CoreLogic Owned Developed Materials), Supplier shall, at no cost to CoreLogic: |
| |
| (i) | Deliver to CoreLogic all CoreLogic Owned Materials and all copies thereof in the format and medium in use by Supplier in connection with the Services as of the date of such expiration or termination; and |
| |
| (ii) | Following confirmation by CoreLogic that the copies of the CoreLogic Owned Materials delivered by Supplier are acceptable and the completion by Supplier of any Disengagement Services for which such CoreLogic Owned Materials are required, destroy or securely erase all other copies of such |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 60 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
CoreLogic Owned Materials then in Supplier’s possession and cease using such CoreLogic Owned Materials and any information contained therein for any purpose.
| |
| (b) | Supplier Owned Materials. Subject to the final paragraph of this Section 14.6(b) or as otherwise provided in a Supplement or agreed in advance by CoreLogic in accordance with Section 6.5(c), with respect to Supplier Owned Materials *** (and any modifications, enhancements, Upgrades, methodologies, tools, documentation, materials and media related thereto), unless CoreLogic otherwise agrees prior to ***: |
| |
| (i) | Except with respect to Supplier Owned Materials provided to the Eligible Recipients *** pursuant to Section ***, for a period of *** (***) *** following completion of the Disengagement Services associated with the Affected Services (the “Post-Term IP License Period”) (for clarity, periods prior to which, Supplier’s license to Supplier Owned Materials is as set forth in Section 14.3(b)), Supplier hereby grants to the Eligible Recipients (and, at CoreLogic’s election, to *** that sign a written agreement with CoreLogic to be bound by terms at least as protective as the terms contained herein applicable to such Materials) a *** to *** such Materials, in each case *** of the *** for their business purposes (without separately commercially exploiting such Supplier Owned Materials); provided that for generally commercially available products, such license shall be as set forth in Supplier’s then-current standard terms and conditions offered generally by Supplier to other commercial customers (including the standard license fee); and provided further that such license shall not be available to CoreLogic (or any ***) for use in connection with Services formerly performed by Supplier if and when such Services are being performed by a follow-on third party outsourcer (i.e., re-sourcing Services following termination of Supplier’s performance of such Services); |
| |
| (ii) | Except with respect to Supplier Owned Materials provided to the Eligible Recipients *** pursuant to Section ***, Supplier shall deliver to CoreLogic (A) a copy of such Materials and related documentation, (B) the *** the object code for such Materials that are not generally commercially available products, and (C) the *** and object code *** that are generally commercially available products if Supplier does not offer or provide *** and other *** for such Materials as provided in Section ***; and |
| |
| (iii) | Supplier shall offer to provide to the Eligible Recipients (and, at CoreLogic’s election, to *** that sign a written agreement with CoreLogic to be bound by terms at least as protective as the terms contained herein applicable to such Materials) *** and other *** for *** products on Supplier’s then-current standard terms and conditions for such services. |
| |
| (iv) | Notwithstanding the license granted above in Section 14.6(b)(i) for Supplier Owned Materials during the Post-Term IP License Period, in lieu of (and as an alternative to) the license grant set forth in Section 14.6(b)(i), Supplier may, in its reasonable discretion, elect to provide to the Eligible Recipients (and, at CoreLogic’s election, to *** and that sign a written agreement with CoreLogic to be bound by terms at least as protective as the terms contained herein applicable to such Materials) such Supplier Owned Materials as part of a service during the Post-Term IP License Period upon Supplier’s then-current standard terms and conditions for such service (including the standard service fee); provided that such service shall not be available to CoreLogic (or any ***) for use in connection with Services formerly performed by Supplier if and when such Services are being performed by a follow-on third party outsourcer (i.e., re-sourcing Services following termination of Supplier’s performance of such Services). |
Unless CoreLogic otherwise agrees prior to Supplier’s first use of such Materials in the performance of the Services, the Eligible Recipients (and, at CoreLogic’s election, ***) shall *** in connection with its receipt of the licenses, services and other rights above (other than *** for *** as set forth in Supplier’s then-current standard terms and conditions).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 61 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Supplier shall not *** any such Materials for which it is unable to offer *** without CoreLogic’s prior written approval (and absent such approval, Supplier’s use of any such Materials shall obligate Supplier to provide, ***, such license and other rights to CoreLogic, CoreLogic Affiliates, the Eligible Recipients and designated ***).
| |
| (c) | Third Party Materials. Unless otherwise provided in a Supplement or otherwise agreed in advance by CoreLogic in accordance with Section 6.5(c), with respect to Third Party Materials licensed by Supplier or Supplier Affiliates or Subcontractors and ***, Supplier hereby grants to the Eligible Recipients (and, at CoreLogic’s election, to *** that sign a written agreement with CoreLogic to be bound by terms at least as protective as the terms contained herein applicable to such Third Party Materials) a sublicense offering the same rights and warranties with respect to such Third Party Materials available to Supplier (or the applicable Supplier Affiliates or Subcontractors), on terms and conditions that are at least as favorable in all material respects as those applicable to Supplier (or the applicable Supplier Affiliate or Subcontractor), for the benefit of the Eligible Recipients upon the expiration or termination of the Term with respect to the Services for which such Materials were used; provided that, during the Disengagement Services period, Supplier may*** substitute one of the following for such sublicense: (i) the assignment to CoreLogic, the other Eligible Recipients and such ***, of the underlying license for such Third Party Materials; or (ii) the procurement for CoreLogic, Eligible Recipients and such *** of either a (a) new license (with terms at least as favorable as those in the license held by Supplier or its Affiliates or Subcontractors (unless and to the extent less favorable pricing is based upon volume) and with the right to grant sublicenses) to such Third Party Materials for the benefit of the Eligible Recipients, or (iii) substitute license for Third Party Materials sufficient to perform, ***unless and to the extent ***), support or resources and at the levels of performance and efficiency required by this Agreement, the functions of the Third Party Materials necessary to enable CoreLogic or its designee to provide the Services for which such Third Party Materials were used. |
Unless CoreLogic has otherwise agreed in advance, the Eligible Recipients (and, to the extent applicable, ***) shall *** in connection with its receipt of the licenses, sublicenses and other rights specified in this Section 14.6(c). In addition, unless CoreLogic has otherwise agreed in advance, Supplier shall deliver to the Eligible Recipients (and, to the extent applicable, ***) a copy of such Third Party Materials (including ***, to the extent it has been available to Supplier) and related documentation and shall cause *** to continue to be available to the Eligible Recipients (and, at CoreLogic’s election, to their designee(s)) to the extent it has been available to Supplier. CoreLogic, however, shall be obligated to *** after the expiration or termination of the Term with respect to the Services for which such Third Party Materials were used, for the right to use and receive maintenance or support related thereto, but only to the extent *** if it had *** the licenses in question or *** has agreed in advance to ***.
To the extent CoreLogic has agreed in advance *** in connection with its receipt of such licenses, sublicenses or other rights, Supplier shall, at CoreLogic’s request, identify the licensing and sublicensing options available to the Eligible Recipients and the *** associated with each. Supplier shall use commercially reasonable efforts to obtain the most favorable options and the *** for Third Party Materials. Supplier shall not commit any Eligible Recipient to *** without CoreLogic’s prior approval. If the licensor offers more than one form of license, CoreLogic (not Supplier) shall select the form of license to be received by CoreLogic, the other Eligible Recipients or their designee(s).
15. REPRESENTATIONS, WARRANTIES AND COVENANTS.
Supplier represents, warrants and covenants that: (i) the Services shall be rendered with promptness, due care, skill and diligence; (ii) the Services shall be executed in a workmanlike manner, in accordance with the Service Levels and standards and practices used by *** providers performing services similar to the Services; (iii) Supplier shall use adequate numbers of qualified individuals with suitable training, education, experience, know-how, competence and skill to perform the Services; (iv) Supplier shall provide such individuals with
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 62 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
training as to *** prior to their *** in the CoreLogic's and/or the Eligible Recipients’ environment; and (v) Supplier shall have the resources, capacity, expertise and ability in terms of Equipment, Materials, know-how and personnel to provide the Services.
| |
| (a) | Ownership and Use. Supplier represents, warrants and covenants that it is either the owner of, or authorized to use, any and all Materials provided and used by Supplier in providing the Services. As to any such Materials that Supplier does not own but is authorized to use, Supplier shall advise CoreLogic as to the ownership and extent of Supplier’s rights with regard to such Materials to the extent any limitation in such rights would impair Supplier’s performance of its obligations under this Agreement. |
| |
| (b) | Performance. Supplier represents, warrants and covenants that any Supplier Owned Materials will perform in Compliance with its Specifications and will provide the functions and features and operate in all material respects in the manner described in its Specifications. |
| |
| (c) | Developed Materials Compliance. Supplier represents, warrants and covenants that Developed Materials shall be free from material errors (with respect to Software, in operation and performance), shall Comply with the Specifications in all material respects, shall provide the functions and features and operate in the manner described in the applicable Supplement, Work Order or as otherwise agreed to by the Parties, and will otherwise be free from any material defects for the number of months specified in the applicable Supplement or Work Order after the *** of such Developed Materials by CoreLogic (the “Warranty Period”). Unless otherwise specified in a Supplement or Work Order, the Warranty Period shall be *** for Developed Materials that execute on a *** cycle; *** for Developed Materials that execute on a quarterly cycle; and *** for Developed Materials that execute on an *** cycle. During the Warranty Period, CoreLogic shall notify Supplier of any failure to Comply of which CoreLogic becomes aware as expeditiously as possible (and provide a description of such the non-conformance in reasonable detail), and Supplier shall repair, replace or correct any failure to Comply at no additional charge to CoreLogic and shall use commercially reasonable efforts to do so as expeditiously as possible; provided that the non-conformance is not attributable to (i) a change or modification to the CoreLogic Owned Developed Material that is not recommended, performed or approved by Supplier, or (ii) CoreLogic’s failure to operate such Developed Material (x) in accordance with the applicable documentation and Specifications, or (y) in a manner permitted by the terms of this Agreement. If Supplier fails or is unable to repair, replace or correct such nonconforming Developed Materials, CoreLogic shall, in addition to any and all other remedies available to it hereunder, be entitled to obtain from Supplier a copy of the *** to such Developed Material. The foregoing warranty is *** any obligation Supplier has to repair and maintenance Services pursuant to an applicable Supplement. |
| |
| (d) | Nonconformity of Supplier Owned Software. In addition to the foregoing, if Supplier Owned Materials (excluding Supplier owned Developed Materials, which are addressed in Section 15.2(c)) do not Comply with the Specifications and criteria set forth in this Agreement or the applicable Supplement, and/or adversely affect the Services provided hereunder, Supplier shall expeditiously *** such Supplier Owned Materials ***. |
| |
| (a) | Performance of Responsibilities. Except as otherwise provided in this Agreement, each Party represents, warrants and covenants that it shall perform its responsibilities under this Agreement in a manner that does not infringe, or constitute an infringement or misappropriation of, any patent, copyright, trademark, trade secret or other proprietary rights of any third party; provided, however, that the performing Party shall not have any obligation or liability to the extent any infringement or misappropriation is caused by (i) modifications made by the other Party or its contractors or subcontractors, without the knowledge or approval of the performing Party, (ii) the other Party’s combination of the performing Party’s work product or Materials with items not furnished, specified or reasonably anticipated by the performing Party or |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 63 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
contemplated by this Agreement, (iii) a breach of this Agreement by the other Party, (iv) the failure of the other Party to use corrections or modifications provided by the performing Party offering equivalent features and functionality, (v) the other Party’s use of the allegedly infringing or misappropriated Materials in a manner not contemplated by this Agreement and for which such Materials are not designed, (vi) the performing Party’s compliance with Specifications provided by the other Party (unless and to the extent the performing Party had knowledge of the infringement or misappropriation associated with compliance with such specifications and failed to disclose it to the other Party), or (vii) Third Party Software, except to the extent that such infringement or misappropriation arises from the failure of the performing Party to obtain the necessary licenses or Required Consents or to abide by the limitations of the applicable Third Party Software licenses. Each Party further represents, warrants and covenants that it will not use or create materials in connection with the Services which are libelous, defamatory, obscene or otherwise infringe another individual’s privacy rights.
| |
| (b) | Third Party Software Indemnification. With respect to Third Party Software provided by Supplier pursuant to this Agreement, Supplier covenants that it shall obtain and provide intellectual property indemnification for the Eligible Recipients (or obtain intellectual property indemnification for itself and enforce such indemnification on behalf of the Eligible Recipients) from the suppliers of such Software. Unless otherwise approved in advance by CoreLogic, such indemnification shall be (i) comparable to the intellectual property indemnification provided by Supplier to the Eligible Recipients under this Agreement, or (ii) the indemnification customarily available in the industry for the same or substantially similar types of software products. |
Each Party represents, warrants and covenants to the other that:
| |
| (a) | Corporate Existence. It is a corporation duly incorporated or limited partnership duly organized, validly existing and in good standing under the Laws of its state of incorporation or organization; |
| |
| (b) | Corporate Power and Authority. It has the requisite corporate power and authority to execute, deliver and perform its obligations under this Agreement; |
| |
| (c) | Legal Authority. It has obtained all licenses, authorizations, approvals, consents or permits required to perform its obligations under this Agreement under all applicable Laws of all authorities having jurisdiction over the Services, except to the extent the failure to obtain any such license, authorizations, approvals, consents or permits is, in the aggregate, immaterial; |
| |
| (d) | Due Authorization. The execution, delivery and performance of this Agreement and the consummation of the transactions contemplated by this Agreement have been duly authorized by the requisite corporate action on the part of such Party; |
| |
| (e) | No Violation or Conflict. The execution, delivery, and performance of this Agreement shall not constitute a violation of any judgment, order, or decree; a material default under any material contract by which it or any of its material assets are bound; or an event that would, with notice or lapse of time, or both, constitute such a default; and |
| |
| (f) | Ownership of Supplier Facilities. To the extent that Supplier provides data center or hosting services under a Supplement, at all times during the Term Supplier (or a Subcontractor authorized by CoreLogic to provide data center or hosting services from such Subcontractor’s owned or leased facility) is and shall continue to be the owner or lessee of the facilities from which such services are provided. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 64 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Supplier represents, warrants and covenants that, without the prior written consent of CoreLogic, Supplier shall not insert into the Software any code that *** invoked to disable or otherwise shut down all or any portion of the Services. Supplier represents, warrants and covenants that, with respect to any disabling code that may be part of the Software, Supplier shall not invoke or cause to be invoked such disabling code at any time, including upon expiration or termination of this Agreement for any reason, without CoreLogic’s prior written consent. Supplier also represents, warrants and covenants that it shall not use Third Party Software containing disabling code without the prior approval of CoreLogic. For purposes of this provision, code that serves the function of ensuring software license compliance (including passwords) shall not be deemed disabling code, provided that Supplier notifies CoreLogic in advance of all such code and obtains CoreLogic’s approval prior to installing such code in any Software, Equipment or System.
| |
| 15.7 | Compliance with Laws. |
| |
| (a) | Compliance by Supplier. Subject to ***, Supplier represents, warrants and covenants that, with respect to the Services and the performance of any of its legal and contractual obligations hereunder, it is and shall be in compliance in all material respects with all applicable Supplier Laws during the Term and any Disengagement Services period, including *** applicable permits, certificates, approvals and inspections required under such Laws. If a charge of non-compliance by Supplier with any such Laws occurs and such non-compliance has or would reasonably be expected to have a material adverse impact on the receipt or use of the Services by CoreLogic, Supplier shall promptly notify CoreLogic of such charge. |
| |
| (b) | Compliance by CoreLogic. Subject to Section 15.7(a), (e) and (f), CoreLogic represents and warrants that, with respect to the performance by the Eligible Recipients of CoreLogic’s legal and contractual obligations under this Agreement, it is and shall be in compliance in all material respects with all applicable CoreLogic Laws for the Term and any Disengagement Services period including identifying and procuring applicable permits, certificates, approvals and inspections required under such Laws. If a charge of non-compliance by CoreLogic with any such Laws occurs and such non-compliance has or would reasonably be expected to have a material adverse impact on the performance of the Services by Supplier, CoreLogic shall promptly notify Supplier of such charge. |
| |
| (c) | Compliance Data and Reports. At no additional charge, Supplier shall provide CoreLogic with data and reports in Supplier’s possession that CoreLogic has requested or Supplier should otherwise reasonably know are necessary for CoreLogic to comply with all Laws applicable to the Services. |
| |
| (d) | Notice of Laws. CoreLogic shall be and remain familiar with the Laws and changes in Laws applicable to the Eligible Recipients and to the businesses of the Eligible Recipients (excluding Laws applicable to ***) and shall notify Supplier of such Laws that are specifically applicable to the Services and changes in such Laws to the extent they materially impact Supplier’s performance of the Services or Supplier’s performance of its other obligations under this Agreement (collectively, “CoreLogic Laws”). Supplier shall be and remain familiar with Laws applicable to Supplier and to the business of Supplier, the Services or the performance of Supplier’s obligations under this Agreement (collectively, “Supplier Laws”). Supplier shall notify CoreLogic of Laws specifically applicable to the Services or the performance of Supplier’s obligations under this Agreement and changes in such Laws to the extent they relate to *** the Services. For the avoidance of doubt, Supplier Laws shall include Laws applicable to (i) the technical, organizational and security measures to be implemented and maintained by Supplier and/or at Supplier Facilities to safeguard Personal Data, and (ii) the restrictions or prohibitions on the use or disclosure of Personal Data by Supplier and/or Supplier Personnel to the extent such Laws apply to Supplier and/or Supplier Personnel. Subject to the *** set forth in Section ***, *** will be responsible for *** if and to the extent *** under this Agreement causes *** to be ***. |
Supplier shall, through the Supplier Personnel, maintain general familiarity with CoreLogic Laws, and shall bring additional or changed requirements of which Supplier is aware to CoreLogic’s attention.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 65 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Subject to its non-disclosure obligations and where Supplier reasonably deems appropriate, Supplier also shall make commercially reasonable efforts to communicate information *** regarding Laws applicable to *** that may be of possible interest or applicability to CoreLogic. At CoreLogic’s request, Supplier Personnel shall participate in CoreLogic provided compliance training programs.
| |
| (e) | Interpretation of Laws or Changes in Laws. CoreLogic shall be responsible, with Supplier’s cooperation and assistance, for interpreting CoreLogic Laws or changes in CoreLogic Laws and shall consult with Supplier regarding the impact of CoreLogic Laws or changes in CoreLogic Laws on Supplier’s performance and CoreLogic’s and/or the other Eligible Recipients’ or any of their customers’ receipt and use of the Services. Supplier shall be responsible, with CoreLogic’s cooperation and assistance, for interpreting Supplier Laws or changes in Supplier Laws and shall consult with CoreLogic regarding the impact of Supplier Laws or changes in Supplier Laws on Supplier’s performance and any Eligible Recipients’ *** the Services. To the extent the impact of any Supplier Law, CoreLogic Law, or change in Supplier Law or CoreLogic Law cannot be readily identified by Supplier, the Parties shall cooperate in interpreting such Law or change in Law and shall seek in good faith to identify and agree upon the impact on Supplier’s performance and the Eligible Recipients’ *** the Services. If the Parties are unable to agree upon such impact, each Party shall retain the right, in its sole discretion, to interpret its own Law or change in such Law and determine its impact. |
| |
| (f) | Implementation of Changes in Laws. Each Party shall be operationally responsible for any changes to its own Systems and processes required by any change in Laws. *** shall be *** for the *** with changes in *** Laws. Supplier will also implement changes requested by CoreLogic that are required pursuant to changes in CoreLogic Laws; provided that, if such change meets the definition of New Services, then CoreLogic shall be financially responsible for the costs of compliance with such changes in CoreLogic Laws. However, to the extent such changes in CoreLogic Laws impact other Supplier customers, any additional costs for services performed for work for CoreLogic and other Supplier customers shall be apportioned on an equitable basis ***. If a Party is operationally but not financially responsible for a change in Laws, the financially responsible Party shall reimburse the operationally responsible Party for the reasonable cost of making the required operational changes. |
| |
| (i) | The Parties acknowledge that certain products, technology, technical data and software (including certain services and training) and certain transactions may be subject to export controls and/or sanctions under the Laws of the United States and other countries and jurisdictions (including the Export Administration Regulations, 15 C.F.R. §§730-774, the International Traffic in Arms Regulations, 22 C.F.R. Parts 120-130, and sanctions programs implemented by the Office of Foreign Assets Control of the U.S. Department of the Treasury). No Party shall directly or indirectly export or re-export any such items or any direct product thereof or undertake any transaction or service in violation of any such Laws. |
| |
| (ii) | Subject to Supplier’s obligations in the last sentence of Section 15.7(g)(i), CoreLogic acknowledges that Supplier has employees and independent contractors who are not U.S. persons who will provide Services under this Agreement, and that certain Services will be provided by Supplier Personnel who are located outside the U.S. For any products, technology, technical data or software provided by any Eligible Recipient to Supplier which are subject to export controls and/or sanctions (“CoreLogic Export Materials”), if *** such materials provided to Supplier, then CoreLogic shall inform Supplier of such CoreLogic Export Materials prior to their transfer. |
| |
| (iii) | Subject to CoreLogic’s notification pursuant to Section 15.7(g)(ii), if Supplier requests that any Services be performed from a new country pursuant to Section 6.1(a), Supplier shall provide CoreLogic with all information that is readily-available to Supplier *** based upon Supplier’s knowledge and experience providing services similar to the Services in such country for the export of such CoreLogic Export Materials, which will include, without limitation, all such readily-available |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 66 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
information relating to the export activities contemplated by Supplier, by this Agreement, or as mutually agreed to by both Parties.
| |
| (h) | Compliance with Anti-Corruption Laws. Supplier represents and warrants that it is fully aware of and will comply with, in the performance of its obligations to CoreLogic, (i) U.S. Foreign Corrupt Practices Act, (ii) U.K. Anti-Bribery Act, (iii) India Prevention of Corruption Act of 1988, or (iv) any regulations promulgated under any such laws. As used in this Section, “Official” means an official or employee of any government (or any department, agency or instrumentality of any government), political party, state owned enterprise or a public international organization such as the United Nations, or a representative or any such person. Supplier further represents and warrants that, to its knowledge, neither it nor any of the Supplier Personnel has offered, promised, made or authorized to be made, or provided any contribution, thing of value or gift, or any other type of payment to, or for the private use of, directly or indirectly, any Official for the purpose of influencing or inducing any act or decision of the Official to secure an improper advantage in connection with, or in any way relating to, (i) any government authorization or approval involving CoreLogic, or (ii) the obtaining or retention of business by CoreLogic. Supplier further represents and warrants that it will not in the future offer, promise, make or otherwise allow to be made or provide any payment and that it will take all lawful and necessary actions to ensure that no such payment is promised, made or provided in the future by any of the Supplier Personnel. Any violation of this Section 15.7(h) will be ***. |
Supplier covenants that the Software, Equipment and Systems used by Supplier to provide the Services and for which Supplier is financially or operationally responsible under this Agreement, are and, subject to Sections 4.3 and 9.6, will remain during the Term and any Disengagement Services period, compatible and interoperable with the *** (including the software, equipment and systems used by *** to provide the *** and/or which may deliver records to, receive records from, or otherwise interact with the Software, Equipment and/or Systems used by Supplier to receive the Services) as and to the extent necessary to provide the Services.
EXCEPT AS OTHERWISE EXPRESSLY PROVIDED IN THIS AGREEMENT, NEITHER PARTY MAKES ANY REPRESENTATIONS, CONDITIONS OR WARRANTIES TO THE OTHER PARTY, WHETHER EXPRESS OR IMPLIED, INCLUDING THE IMPLIED WARRANTIES AND CONDITIONS OF MERCHANTABILITY, NON-INFRINGEMENT AND FITNESS FOR A PARTICULAR PURPOSE.
16. INSURANCE AND RISK OF LOSS.
During the Term, Supplier shall keep in full force and effect and maintain at its sole cost and expense the policies of insurance set forth in Schedule 9, with the specified minimum limits of liability specified therein.
| |
| (a) | General. Subject to Section 17.3, Supplier and CoreLogic each shall be responsible for damage, destruction, loss, theft or governmental taking of their respective tangible property or real property (whether owned or leased) and each Party agrees to look only to its own insuring arrangements with respect to such damage, destruction, loss, theft, or governmental taking. Each Party shall promptly notify the other Party of any such damage, destruction, loss, theft, or governmental taking of such other Party’s tangible property or real property (whether owned or leased) in the possession or under the control of such Party. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 67 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (b) | Waiver. Supplier and CoreLogic hereby waive, on behalf of themselves and shall cause their respective insurers to issue appropriate waivers of subrogation rights for, any claims that either may have against the other for loss or damage resulting from perils covered by the *** insurance policy. It is understood that this waiver is intended to extend to all such loss or damage whether or not the same is caused by the fault or neglect of either Supplier or CoreLogic and whether or not insurance is in force. If required by policy conditions, each Party shall secure from its property insurer a waiver of subrogation endorsement to its policy, and deliver a copy of such endorsement to the other Party if requested. |
17. INDEMNITIES.
| |
| 17.1 | Indemnity by Supplier. |
Supplier agrees to indemnify, defend and hold harmless the Eligible Recipients and their respective officers, directors, employees, agents, representatives, successors, and assigns from any and all Losses and threatened Losses paid or payable to non-Parties (whether the subject of a final adjudication or otherwise) due to non-Party claims arising from or in connection with any of the following:
| |
| (a) | Representations, Warranties and Covenants. Supplier’s breach of any of the representations, warranties and covenants set forth in Sections 15.4 and 15.6. |
| |
| (b) | Assigned Contracts. Supplier’s decision to terminate or failure to observe or perform any duties or obligations to be observed or performed on or after the Commencement Date by Supplier under any of the Third Party Software licenses, Equipment Leases or Third Party Contracts assigned to Supplier pursuant to this Agreement. |
| |
| (c) | Licenses, Leases and Contracts. Supplier’s failure to observe or perform any duties or obligations to be observed or performed on or after the Commencement Date by Supplier under Third Party Software licenses, Equipment Leases or Third Party Contracts used by Supplier to provide the Services or for which Supplier has assumed financial or operational responsibility or to which Supplier is a party, or any Required Consents pertaining to such licenses, leases or Third Party Contracts, used by Supplier to provide the Services, each to the extent such failure was not the result of CoreLogic’s failure to perform its obligations under this Agreement including its obligation to provide copies of the contracts or obtain the Required Consents for which it is responsible pursuant to Section 5.1. |
| |
| (d) | *** or ***. Supplier’s breach of its obligations under Article *** with respect to CoreLogic ***. |
| |
| (e) | Infringement. Infringement or misappropriation or alleged infringement or alleged misappropriation of a patent, trade secret, copyright or other proprietary rights in contravention of Supplier’s representations, warranties and covenants in Sections 15.2 and 15.3. |
| |
| (f) | *** with ***. Losses, including ***, interest or other remedies, resulting from Supplier’s failure to perform its responsibilities with respect to *** as required by Section ***. |
| |
| (g) | *** with ***. Losses, including ***, interest or other remedies, resulting from Supplier’s failure to perform its responsibilities with respect to *** as required by Section ***. |
| |
| (h) | Taxes. Taxes, together with interest and penalties, that are the responsibility of Supplier under Section 11.3. |
| |
| (i) | Shared Facility Services. Services, products or systems provided by Supplier to a third party from any shared Supplier facility or using any shared Supplier resources and not constituting Services provided to an Eligible Recipient or consumer pursuant to this Agreement. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 68 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (j) | Affiliate, Subcontractor or Assignee Claims. Any claim, other than an indemnification claim under this Agreement, initiated by (i) a Supplier Affiliate or Subcontractor asserting rights under this Agreement or (ii) any entity to which Supplier assigned, transferred, pledged, hypothecated or otherwise encumbered its rights to receive payments from CoreLogic under this Agreement. |
| |
| (l) | Employment Claims. Any claim (including claims by Transitioned Employees) relating to any: (i) violation by Supplier, Supplier Affiliates or Subcontractors, or their respective officers, directors, employees, representatives or agents, of any Laws or any common law protecting persons or members of protected classes or categories, including Laws prohibiting discrimination or harassment on the basis of a protected characteristic; (ii) liability arising or resulting from the employment of Supplier Personnel (including Transitioned Employees from and after their Employment Effective Date) by Supplier, Supplier Affiliates or Subcontractors (including liability for any social security or other employment taxes, workers’ compensation claims and premium payments, and contributions applicable to the wages and salaries of such Supplier Personnel); (iii) payment or failure to pay any salary, wages, pensions, benefits or other compensation due and owing to any Supplier Personnel (including Transitioned Employees) for amounts arising in periods from and after their Employment Effective Dates); (iv) employee pension or other benefits of any Supplier Personnel (including Transitioned Employees) accruing from and after their Employment Effective Date; (v) other aspects of the employment relationship of Supplier Personnel with Supplier, Supplier Affiliates or Subcontractors or the termination of such relationship, including claims for wrongful discharge, claims for breach of express or implied employment contract and claims of co-employment or joint employment (vi) Supplier’s or any Supplier Personnel’s failure to comply with Schedule 5; and (vii) liability resulting from *** by Supplier, Supplier Affiliates or Subcontractors (or their respective officers, directors, employees, representatives or agents), or other acts or omissions with respect to any such Affected Employee by such persons or entities, including any act, omission or representation made in connection with the ***, the failure to make offers to any such employees or the terms and conditions of such offers (including compensation and employee benefits), except, in each case, to the extent the claims described in (i) through (vii) result from the wrongful actions or omissions of CoreLogic, the other Eligible Recipients, or Third Party Contractors or the failure of CoreLogic, the other Eligible Recipients, or Third Party Contractors to comply with CoreLogic’s responsibilities under this Agreement. |
| |
| 17.2 | Indemnity by CoreLogic. |
CoreLogic agrees to indemnify, defend and hold harmless Supplier and its officers, directors, employees, agents, representatives, successors, and assigns from any and all Losses and threatened Losses paid or payable to non-Parties (whether the subject of a final adjudication or otherwise) due to non-Party claims arising from or in connection with any of the following:
| |
| (a) | Representations, Warranties and Covenants. CoreLogic’s breach of any of the representations, warranties and covenants set forth in Section 15.4. |
| |
| (b) | Assigned Contracts. CoreLogic’s failure to observe or perform any duties or obligations to be observed or performed prior to the Commencement Date by CoreLogic under any of the Third Party Software licenses, Equipment Leases or Third Party Contracts assigned to Supplier by CoreLogic pursuant to this Agreement. |
| |
| (c) | Licenses, Leases or Contracts. CoreLogic’s failure to observe or perform any duties or obligations to be observed or performed on or after the Commencement Date by CoreLogic under Third Party Software licenses, Equipment Leases or Third Party Contracts for which CoreLogic has assumed financial or operational responsibility or to which CoreLogic is a party, or any Required Consents pertaining to such licenses, leases or Third Party Contracts, each to the extent such failure was not the result of Supplier’s |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 69 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
failure to perform its obligations under this Agreement including its obligation to or obtain the Required Consents for which it is responsible pursuant to Section 5.1.
| |
| (d) | Supplier’s Confidential Information. CoreLogic’s breach of its obligations under Article 13 with respect to Supplier’s Confidential Information. |
| |
| (e) | Infringement. Infringement or misappropriation or alleged infringement or alleged misappropriation of a patent, trade secret, copyright or other proprietary rights in contravention of CoreLogic’s representations, warranties and covenants in Section 15.3. |
| |
| (f) | Taxes. Taxes, together with interest and penalties, that are the responsibility of CoreLogic under Section 11.3. |
| |
| (g) | Compliance with Laws. Losses, including government fines, penalties, sanctions, interest or other remedies resulting from CoreLogic’s failure to perform its responsibilities under Section 15.7(b). |
| |
| (h) | CoreLogic Affiliate, Eligible Recipient or Third Party Contractor Claims. Any claim, other than an indemnification claim or insurance claim under this Agreement, initiated by a CoreLogic Affiliate, an Eligible Recipient (other than CoreLogic) or a CoreLogic Third Party Contractor asserting rights under this Agreement. |
| |
| (i) | Employment Claims. Any claim relating to any: (i) violation by CoreLogic or an Eligible Recipient, *** or its respective officers, directors, employees, representatives or agents, of any Laws or any common law protecting persons or members of protected classes or categories, including Laws prohibiting discrimination or harassment on the basis of a protected characteristic; (ii) liability resulting from the employment of the personnel (including Transitioned Employees for periods prior to their Employment Effective Date) by CoreLogic or an Eligible Recipient (including liability for any social security or other employment taxes, workers’ compensation claims and premium payments, and contributions applicable to the wages and salaries of such personnel); (iii) payment or failure to pay any salary, wages, pensions, benefits or other compensation due and owing to any Transitioned Employees, for amounts arising in periods prior to their Employment Effective Dates; (iv) employee pension or other benefits from any Transitioned Employees of CoreLogic or an Eligible Recipient accruing prior to their Employment Effective Date; (v) other aspects of the employment relationship of CoreLogic Personnel with CoreLogic, Eligible Recipients, Affiliates or *** or the termination of such relationship, including claims for wrongful discharge, claims for breach of express or implied employment contract, and (vi) any CoreLogic’s or an Eligible Recipient’s failure to comply with Schedule 5; except, in each case, to the extent claims described in (i) through (vi) result from the wrongful conduct or wrongful act or omission of Supplier or Supplier Personnel, or the failure of Supplier or Supplier Personnel to comply with Supplier’s responsibilities under Schedule 5. |
| |
| 17.3 | Additional Indemnities. |
Supplier and CoreLogic each agree to indemnify, defend and hold harmless the other, and the Eligible Recipients and their respective Affiliates, officers, directors, employees, agents, representatives, successors, and assigns, from any and all Losses and threatened Losses (a) paid or payable to a non-Party to the extent they arise from or in connection with the death or bodily injury of any agent, employee, customer, business invitee, business visitor or other person caused by the negligence or other tortious conduct of the indemnitor ; and (b) except as otherwise provided in Section 16.2, arising from or in connection with the damage, loss or destruction of any real or tangible personal property caused by the negligence or other tortious conduct of the indemnitor.
In the event that (a) any item supplied by Supplier or its Affiliates or Subcontractors that is subject to the indemnity in Section 17.1(e) are found, or in Supplier’s reasonable opinion are likely to be found, to infringe
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 70 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
upon the patent, copyright, trademark, trade secrets, intellectual property or proprietary rights of any third party in any country in which Services are to be performed or received under this Agreement, or (b) the continued use of such Materials, Equipment, Software or Services is enjoined, Supplier shall, in addition to defending, indemnifying and holding harmless CoreLogic as provided in Section 17.1(e) and to the other rights CoreLogic may have under this Agreement, promptly and at its own cost and expense, and in such a manner as to minimize the disturbance to the Eligible Recipients, do one of the following: (i) obtain for the Eligible Recipients the right to continue using such Materials, Equipment, or Services; (ii) modify such Materials, Equipment, or Services so as to no longer be infringing without degrading the performance or quality of the Services or adversely affecting CoreLogic’s and the Eligible Recipients’ intended use; or (iii) replace such item(s) with a non-infringing functional equivalent that does not degrade the performance or quality of the Services or adversely affect the intended use as contemplated by this Agreement.
| |
| 17.5 | Indemnification Procedures. |
With respect to non-Party claims which are subject to indemnification under this Agreement (other than as provided in Section 17.6 with respect to claims covered by Section 17.1(f) or (g)), the following procedures shall apply:
| |
| (a) | Notice. Promptly after receipt by any person or entity entitled to indemnification under this Agreement of notice of the commencement or threatened commencement of any civil, criminal, administrative, or investigative action or proceeding involving a claim in respect of which the indemnitee will seek indemnification hereunder, the indemnitee shall notify the indemnitor of such claim. No delay or failure to so notify an indemnitor shall relieve it of its obligations under this Agreement except to the extent that such indemnitor has suffered actual prejudice by such delay or failure. Within fifteen (15) days following receipt of notice from the indemnitee relating to any claim, but no later than five (5) days before the date on which any response to a complaint or summons is due, the indemnitor shall notify the indemnitee that the indemnitor elects to assume control of the defense and settlement of that claim (a “Notice of Election”). |
| |
| (b) | Procedure Following Notice of Election. If the indemnitor delivers a Notice of Election within the required notice period, the indemnitor shall assume sole control over the defense and settlement of the claim; provided, however, that (i) the indemnitor shall keep the indemnitee fully apprised at all times as to the status of the defense, and (ii) the indemnitor shall obtain the prior written approval of the indemnitee before entering into any settlement of such claim imposing financial or non-financial obligations or restrictions on the indemnitee or constituting an admission of guilt or wrongdoing by the indemnitee or ceasing to defend against such claim. The indemnitor shall not be liable for any legal fees or expenses incurred by the indemnitee following the delivery of a Notice of Election; provided, however, that (i) the indemnitee shall be entitled to employ counsel at its own expense to participate in the handling of the claim, and (ii) the indemnitor shall pay the fees and expenses associated with such counsel if there is a conflict of interest with respect to such claim which is not otherwise resolved or if the indemnitor has requested the assistance of the indemnitee in the defense of the claim or the indemnitor has failed to defend the claim diligently and the indemnitee is prejudiced or likely to be prejudiced by such failure. The indemnitor shall not be obligated to indemnify the indemnitee for any amount paid or payable by such indemnitee in the settlement of any claim if (x) the indemnitor has delivered a timely Notice of Election and such amount was agreed to without the written consent of the indemnitor, (y) the indemnitee has not provided the indemnitor with notice of such claim and a reasonable opportunity to respond thereto, or (z) the time period within which to deliver a Notice of Election has not yet expired. |
| |
| (c) | Procedure Where No Notice of Election Is Delivered. If the indemnitor does not deliver a Notice of Election relating to any claim for which it is obligated to indemnify the other Party hereunder within the required notice period, the indemnitee shall have the right to defend the claim in such manner as it may deem appropriate. The indemnitor shall promptly reimburse the indemnitee for all such reasonable costs and expenses incurred by the indemnitee, including reasonable attorneys’ fees. |
| |
| 17.6 | Indemnification Procedures – Governmental Claims. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 71 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
With respect to claims covered by Section 17.1(f) or (g), the following procedures shall apply:
| |
| (a) | Notice. Promptly after receipt by CoreLogic of notice of the commencement or threatened commencement of any action or proceeding involving a claim in respect of which the indemnitee will seek indemnification pursuant to Section 17.1(f) or (g), CoreLogic shall notify Supplier of such claim. No delay or failure to so notify Supplier shall relieve Supplier of its obligations under this Agreement except to the extent that Supplier has suffered actual prejudice by such delay or failure. |
| |
| (b) | Procedure for Defense. CoreLogic shall be entitled, at its option, to have the claim handled pursuant to Section 17.5 or to retain sole control over the defense and settlement of such claim; provided that, in the latter case, CoreLogic shall (i) keep Supplier reasonably apprised as to the status of the defense and consult with Supplier on a regular basis regarding claim processing (including actual and anticipated costs and expenses) and litigation strategy, (ii) reasonably consider any Supplier settlement proposals or suggestions and consult with Supplier and discuss any settlement agreement that imposes a monetary amount to be paid or reimbursed by Supplier, and (iii) use commercially reasonable efforts to minimize any amounts payable or reimbursable by Supplier. |
Except as otherwise provided in Section 16.1 or 16.2, if an indemnitor shall be obligated to indemnify an indemnitee pursuant to any provision of this Agreement, the indemnitor shall, upon payment of such indemnity in full, be subrogated to all rights of the indemnitee with respect to the claims to which such indemnification relates.
18. LIABILITY.
Subject to the specific provisions and limitations of this Article 18, it is the intent of the Parties that each Party shall be liable to the other Party for any actual damages incurred by the non-breaching Party as a result of the breaching Party’s unexcused failure to perform its obligations in the manner required by this Agreement.
| |
| 18.2 | Limitation of Liability. |
| |
| (a) | Exclusions from Limitations. EXCEPT AS PROVIDED IN THIS SECTION 18.2, NEITHER PARTY SHALL BE LIABLE TO THE OTHER PARTY FOR INDIRECT, CONSEQUENTIAL, INCIDENTAL, COLLATERAL, EXEMPLARY OR PUNITIVE DAMAGES, REGARDLESS OF THE FORM OF THE ACTION OR THE THEORY OF RECOVERY, EVEN IF SUCH PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. |
| |
| (b) | Liability Cap. Except as otherwise provided in this Section 18.2, the total aggregate liability of either Party, for all claims asserted by the other Party under or in connection with this Agreement, regardless of the form of the action or the theory of recovery, shall be limited to (i) ***dollars ($***) if the last act or omission giving rise to liability occurs during the ***(***) *** period immediately after the Effective Date and (ii) after such ***(***) *** period, the *** to *** under this Agreement during the ***(***) *** period preceding the last act or omission giving rise to such liability (with respect to clause (i) or (ii) as applicable, the “Standard Cap”). For avoidance of doubt, this liability cap is an aggregate liability cap for this Agreement, all Supplements and all Companion Agreements. |
| |
| (c) | Exceptions to Limitations of Liability. The limitations of liability set forth in Sections 18.2(a) and (b) shall not apply with respect to: |
| |
| (i) | Losses occasioned by the fraud or willful misconduct of a Party. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 72 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (ii) | Losses that are the subject of ***under Article *** of this Agreement, excluding Losses payable pursuant to Section *** (***), Section *** (*** with ***) and Section *** (***) for which the limitations of liability are as set forth in Section ***. |
| |
| (iii) | Losses occasioned by ***. For purposes of this provision, *** shall mean ***, in a manner impermissible under this Agreement, of the performance of *** of the *** then *** to be *** under this Agreement. |
| |
| (v) | Losses occasioned by any breach of a Party’s representations or warranties under Section ***. |
| |
| (vi) | Losses occasioned by (i) *** of the *** of an Eligible Recipient and (ii) Losses occasioned by *** of the *** of ***. |
| |
| (vii) | Losses occasioned by Supplier’s breach of its obligations under Section *** with respect to ***; provided that if and to the extent any such Supplier breach also constitutes a failure by Supplier to comply with *** as contemplated by either Section *** or *** (each, a “***”), then, subject to the immediately following sentence, any Losses occasioned by such *** shall be subject to the limitations set forth below in Section *** or ***, as each may be applicable depending on the *** involved. Notwithstanding the foregoing, if any *** is also a liability event that may be characterized under additional types of claims under this Agreement (e.g., ***, willful misconduct), the type of claim that carries the *** and types of damages for such claim shall be available to CoreLogic, notwithstanding that a *** limit of liability or *** type of damages may be specified in Section 18.2(d)(ii) or (iii). For example, if a *** also constitutes willful misconduct, the *** of liability and the *** of damages applicable to such claim shall apply, notwithstanding that a *** of liability or *** of damages are specified for breaches of confidentiality in Section 18.2(d)(ii) or (iii). |
| |
| (d) | Modifications to Limitations of Liability. The limitations of liability set forth in Sections 18.2(a) and (b) shall not apply with respect to the following except to the extent set forth below: |
| |
| (i) | For Losses occasioned by the *** of a Party, the Party’s aggregate liability will not exceed ***(***) times the Standard Cap. |
| |
| (ii) | Subject to the last paragraph of Section 18.2(d), for Losses occasioned by Supplier’s failure to comply with Article *** with respect to ***, Supplier’s aggregate liability will not exceed ***(***) times the Standard Cap and such Losses shall include ***, any amounts paid or payable to any non-Party pursuant to an indemnified claim per Article ***, and any and all ***, but shall not include any other damages excluded by Section ***. |
| |
| (iii) | Subject to the last paragraph of Section 18.2(d), for Losses occasioned by Supplier’s failure to comply with Article *** with respect to *** that is not ***, Supplier’s aggregate liability will not exceed ***(***) times the Standard Cap; provided, that (a) Supplier shall not be liable for Losses from *** or *** *** in ***; and (b) for Losses of the type described in Section 18.2(a), only *** may be recovered for that type of Loss under this Section 18.2(d)(iii). “***” means Losses arising from the *** (including, ***) that results in *** for CoreLogic or any other Eligible Recipients. For clarification, nothing in this Section 18.2(d)(iii) is intended to limit CoreLogic’s ability to recover direct damages under this paragraph, which collectively with any ***, shall not exceed in the aggregate *** times the Standard Cap. |
| |
| (iv) | Subject to the last paragraph of Section 18.2(d), for Losses occasioned by an Eligible Recipient’s failure to comply with Article *** with respect to ***, CoreLogic’s aggregate liability will not exceed ***(***) times the Standard Cap; provided, that (a) CoreLogic shall not be liable for Losses from ***; and (b) for Losses of the type described in Section 18.2(a), only *** may be |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 73 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
recovered for that type of Loss under this Section 18.2(d)(iv). “***” means Losses arising from the *** (including, *** that result in *** for Supplier or any of its Affiliates. For clarification, nothing in this Section 18.2(d)(iv) is intended to limit Supplier’s ability to recover direct damages under this paragraph, which collectively with any ***, shall not exceed in the aggregate ***(***) times the Standard Cap.
| |
| (v) | Subject to the last paragraph of Section 18.2(d), for Losses occasioned by Supplier’s breach of the last sentence of Section *** (*** by ***), Supplier’s aggregate liability will not exceed (A) ***(***) times the Standard Cap where CoreLogic has provided Supplier with *** either (x) in the *** (as implemented in accordance with Section ***) or (y) in reasonable detail identifying Section *** to the *** or (B) the Standard Cap where CoreLogic has not provided Supplier with such ***; and such Losses shall include ***, and any amounts paid or payable to any non-Party pursuant to an indemnified claim per Article ***, but shall not include any other damages excluded by Section 18.2(a). |
| |
| (vi) | For any and all liability events described in this Section 18.2(d), (A) each Party’s liability will not exceed, in the aggregate, ***(***) times the Standard Cap and (B) where a Party is liable for any amount in excess of the Standard Cap, the first dollars toward satisfaction of liability for such liability event will come first from the amounts in excess of the Standard Cap, and thereafter from the Standard Cap. In addition, notwithstanding anything to the contrary in Section 18.2, for a single liability event that may be characterized under two or more types of claims under this Agreement, the type of claim that carries the *** and types of damages for such claim shall be available to the claiming Party, notwithstanding that a *** of liability or *** of damages may be specified in this Section 18.2(d) for one type of claim. For example, if a breach of *** covered by Section 18.2(d)(iii) also constitutes willful misconduct or fraud, the *** of liability and the *** damages applicable to such claim shall apply, notwithstanding that a *** or *** of damages are specified for breaches of *** above. |
| |
| (e) | Items Not Considered Damages. The following shall not be considered damages subject to, and shall not be counted toward the liability exclusion or cap specified in, Section 18.2(a) or (b): |
| |
| (i) | *** against Supplier pursuant to this Agreement. |
| |
| (ii) | Amounts withheld by CoreLogic in accordance with this Agreement or paid by CoreLogic but subsequently recovered from Supplier due either to incorrect Charges by Supplier or non-***. |
| |
| (iii) | Invoiced Charges and other amounts that are due and owing to Supplier for Services under this Agreement. |
| |
| (f) | Waiver of Liability Cap. If, at any time, the total aggregate liability of one Party for claims asserted by the other Party under or in connection with this Agreement exceeds ***percent (***%) of the liability cap specified in Section 18.2(b) (as may be increased in accordance with this Section 18.2(e)) and, upon the request of the other Party, the Party incurring such liability refuses to waive such cap and/or increase the available cap to an amount at least equal to the original liability cap, then the other Party may terminate this Agreement, and in the case of CoreLogic exercising its right to terminate, CoreLogic may terminate this Agreement immediately without payment of Termination Charges. |
| |
| (g) | Eligible Recipient Damages. The Parties acknowledge and agree that, to the extent an Eligible Recipient has suffered Losses for which Supplier may be liable under this Agreement, CoreLogic may seek recovery of such Losses on behalf of such Eligible Recipient in the same manner and to the same extent it would be entitled to do so on its own behalf if it had suffered such Losses. |
| |
| (h) | Acknowledged Direct Damages. The following shall be considered direct damages and neither Party shall assert that they are indirect, incidental, collateral, consequential or special damages or lost profits |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 74 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
to the extent they are proximately caused by either Party’s failure to perform in accordance with this Agreement:
| |
| (i) | Costs and expenses of ***. |
| |
| (ii) | Costs and expenses of *** the Services or any part thereof. |
| |
| (iii) | Costs and expenses of ***. |
| |
| (iv) | Cover damages, including the costs and expenses incurred to (A) ***, to the extent *** under this Agreement or (B) *** and, with respect to both (A) and (B), including the costs and expenses associated with the *** to assist with ***. |
| |
| (vi) | *** or related expenses reasonably incurred by either Party in performing items (ii) and (iv), including *** and similar charges. |
| |
| (vii) | Subject to Section ***, damages, *** resulting from ***. |
| |
| (viii) | *** resulting from *** obligations under Section *** |
The absence of a direct damage listed in this Section 18.2(g) shall not be construed or interpreted as an agreement to exclude it as a direct damage under this Agreement.
| |
| (i) | Duty to Mitigate. Each Party shall use appropriate efforts to mitigate its damages to the extent within its reasonable control and consistent with the Parties’ respective performance obligations under this Agreement; provided, however, that this provision is not intended to expand or diminish a Party’s rights or obligations under this Agreement, alter the plain meaning of the provisions contained herein, or limit a Party’s rights to act in its own self-interest. |
19. DISPUTE RESOLUTION.
| |
| 19.1 | Dispute Resolution Procedures. |
Any dispute arising out of or relating to this Agreement and/or the Services provided by Supplier pursuant thereto shall be resolved in accordance with the dispute resolution procedures set forth in Schedule 6.
Each Party irrevocably agrees that any legal action, suit or proceeding brought by it in any way arising out of this Agreement must be brought solely and exclusively in state or federal courts located in Orange County in the state of California, and each Party irrevocably submits to the sole and exclusive jurisdiction of these courts in personam, generally and unconditionally with respect to any action, suit or proceeding brought by it or against it by the other Party. Notwithstanding the foregoing, either Party may seek injunctive or other equitable relief or seek to enforce an arbitration award or other judgment in any court of competent jurisdiction. Each Party hereby waives its right to a jury trial in connection with any dispute or legal proceeding arising out of this Agreement or the subject matter hereof.
| |
| 19.3 | Continued Performance. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 75 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (a) | General. Each Party agrees that it shall, unless otherwise directed by the other Party, continue performing its obligations under this Agreement, and neither Party shall deny, withdraw or restrict such performance, while any dispute is being resolved; provided that this provision shall not operate or be construed as extending the Term or prohibiting or delaying a Party’s exercise of any right it may have to terminate the Term as to all or any part of the Services. For purposes of clarification, CoreLogic Data may not be withheld by Supplier pending the resolution of any dispute. |
| |
| (b) | Non-Interruption of Services. Supplier acknowledges and agrees that any interruption to the Service may cause irreparable harm to the Eligible Recipients and their customers, in which case an adequate remedy at law may not be available. |
This Agreement and performance under it shall be governed by and construed in accordance with the applicable Laws of California, without giving effect to any choice-of-law provision or rule (whether of such State or any other jurisdiction) that would cause the application of the Laws of any other jurisdiction; provided, however, the Uniform Computer Information Transactions Act whether now or hereafter enacted in California (“UCITA”), shall not apply to this Agreement or any performance hereunder and the Parties expressly opt-out of the applicability of UCITA to this Agreement. The application of the United Nations Convention on Contracts for the International Sale of Goods is expressly excluded.
As a recipient of Confidential Information, Supplier agrees that CoreLogic and/or the Eligible Recipients and/or their customers may be irreparably injured by the disclosure of Confidential Information in violation of this Agreement; and in addition to any other remedies available at law or in equity, CoreLogic may seek an injunction to prevent or stop such disclosure.
20. TERMINATION.
| |
| 20.1 | Termination for Cause. |
| |
| (a) | By CoreLogic. If Supplier: |
| |
| (i) | commits a material breach of its obligations with respect to Transition Services, which breach is not cured within the period specified in Section 4.2(h); |
| |
| (ii) | commits a material breach of this Agreement or a Supplement, which breach is not cured within thirty (30) days after notice of the breach from CoreLogic; |
| |
| (iii) | commits a material breach of this Agreement or a Supplement which is not capable of being cured within the period specified pursuant to Section 20.1(a)(ii); |
| |
| (iv) | commits ***, which *** a material breach of this Agreement (which may be a material breach under a Supplement); |
| |
| (v) | becomes liable for or incurs Service Level Credits under a Supplement that, in the aggregate, exceed *** percent (***%) of the cumulative At Risk Amount under a Supplement during any rolling *** (***) *** period; |
| |
| (vi) | fails to perform in accordance with the same Critical Service Level for *** (***) *** or *** (***) *** over a *** (***) *** consecutive period; or |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 76 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (vii) | fails to deliver to CoreLogic a Facility and Controls Audit opinion in accordance with Section 9.10(h) which breach is not cured within thirty (30) days after notice of the breach from CoreLogic or otherwise fails to implement remedial measures to eliminate failures or deficiencies in such Facility and Controls Audit as required by, and in accordance with, Section 9.10(h); |
then CoreLogic may, by giving notice to Supplier, terminate this Agreement or the applicable Supplement, with respect to *** Services as of a date specified in the notice of termination; provided, however, that in the case of a material breach under any Supplement pursuant to Sections 20.1(a)(i) through 20.1(a)(iv) or Service Level Credits incurred under a Supplement pursuant to Section 20.1(a)(v), CoreLogic’s right to terminate shall apply only to the applicable Supplement and not to this Agreement as a whole unless the breach is also a material breach of this Agreement, or separate grounds exist for a material breach of this Agreement, in which case CoreLogic may terminate this Agreement or the applicable Supplement. Supplier shall *** to *** in connection with such a termination for cause. If CoreLogic chooses to terminate this Agreement or a Supplement in part, the Charges payable under this Agreement or such Supplement will be equitably adjusted in accordance with the pricing methodology set forth in the applicable Supplement, to reflect such partial termination. For avoidance of doubt, the Parties acknowledge and agree that a material breach under a Supplement or any Companion Agreement shall be deemed a material breach under all *** for purposes of this provision.
The express acknowledgment that a certain amount of Service Level Credits or number of Service Level defaults constitutes grounds for termination under Section 20.1(a)(v) and (vi) does not imply that a lesser amount or number cannot constitute a material breach of this Agreement and therefore grounds for termination under other subsections, and no Party shall contend otherwise in any dispute or controversy between the Parties.
| |
| (b) | By Supplier. If CoreLogic fails to pay undisputed Charges then due and owing under a Supplement by the specified due date or fails to properly escrow disputed Charges in accordance with Section 12.4(e), and the total of all such overdue undisputed Charges exceeds, in the aggregate, *** dollars ($***), Supplier shall provide notice of such failure and its intention to terminate on the basis of such failure, and if CoreLogic fails to cure such default within *** (***) *** of such notice from Supplier, Supplier may then provide a second notice of such failure and Supplier’s intention to terminate on the basis of such failure. If CoreLogic fails to cure such default within *** (***) *** of such second notice, then Supplier may, by notice to CoreLogic, immediately terminate the applicable Supplement. Supplier acknowledges and agrees that *** describe *** to *** and *** any *** it may have to *** or any ***. |
| |
| 20.2 | Termination for Convenience. |
CoreLogic may terminate any Supplement with respect to *** the Services for convenience and without cause ***. If CoreLogic elects to terminate Services provided under a Supplement on this basis, CoreLogic shall give Supplier at least *** (***) *** prior notice designating the termination date. In either event, CoreLogic shall pay to Supplier a Termination Charge calculated and paid in accordance with Schedule 4 or the applicable Supplement, if any Termination Charges is applicable to the termination under the applicable Supplement. If a purported termination for cause by CoreLogic under Section 20.1 is finally determined by a competent authority not to be properly a termination for cause, then such termination by CoreLogic shall be deemed to be a termination for convenience under this Section 20.2 as of the date of such termination.
| |
| 20.3 | Termination Upon Supplier Change of Control. |
In the event of a change in Control of Supplier (***) or the Entity that Controls Supplier (if any), where such Control is acquired, directly or indirectly, in a single transaction or series of related transactions, or all or substantially all of the assets of Supplier (***) are acquired by any entity, or Supplier (***) is merged with or into another entity to form a new entity, in each such case where such Control is acquired by an Entity that was not an Affiliate of Supplier immediately prior to and independent of such transaction or series of related transactions and provided that CoreLogic has concerns that are reasonable and made in good faith (in the
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 77 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
context of the nature and magnitude of the decision contemplated by this Section 20.3) pertaining to the successor Entity’s reputation in the market, ability to provide the Services in accordance with the provisions of this Agreement and the Supplement (including ***), *** and/or ***, or other *** and ***, then at any time within *** (***) *** after the last to occur of such events, CoreLogic may at its option terminate this Agreement by giving Supplier at least *** (***) *** prior notice and designating a date upon which such termination shall be effective; provided, however, if such change in Control of Supplier involves a Direct CoreLogic Competitor, CoreLogic may terminate this Agreement by giving Supplier at least *** (***) *** prior notice, and such Direct CoreLogic Competitor shall be prohibited from any contact with CoreLogic Data, CoreLogic Confidential Information and any and all other information about the CoreLogic account, including discussions with Supplier Personnel regarding specifics relating to the Services. Supplier shall be entitled to Termination Charges in connection with such a termination to the extent provided in, and in accordance with, Schedule 13.
| |
| 20.4 | Termination Upon CoreLogic Merger or Acquisition. |
If, in a single transaction or series of transactions, CoreLogic is acquired by any other Entity (by stock sale, asset sale or otherwise) or merges with any other Entity, then, at any time within *** (***) *** after the last to occur of such events, CoreLogic may at its option terminate this Agreement by giving Supplier at least *** (***) *** prior notice and designating a date upon which such termination shall be effective. Supplier shall be entitled to Termination Charges in connection with such a termination calculated to the extent provided in, and in accordance with, Schedule 13.
| |
| 20.5 | Termination for Insolvency. |
If any Party (i) files for bankruptcy, (ii) becomes or is declared insolvent, or is the subject of any bona fide proceedings related to its liquidation, administration, provisional liquidation, insolvency or the appointment of a receiver or similar officer for it, (iii) passes a resolution for its voluntary liquidation, (iv) has a receiver or manager appointed over all or substantially all of its assets, (v) makes an assignment for the benefit of all or substantially all of its creditors, (vi) enters into an agreement or arrangement for the composition, extension, or readjustment of substantially all of its obligations or any class of such obligations, (vii) fails or becomes incapable of paying its debts as they become due, or (viii) experiences an event analogous to any of the foregoing in any jurisdiction in which any of its assets are situated, then the other Party may terminate this Agreement as of a date specified in a termination notice; provided, however, that Supplier will not have the *** under this Section so long as *** for the Services to be *** in ***. If any Party elects to terminate this Agreement due to the insolvency of the other Party, such termination will be deemed to be a termination for cause hereunder. Supplier shall not be entitled to any Termination Charges in connection with such a termination.
| |
| 20.6 | CoreLogic Rights Upon Supplier’s Bankruptcy. |
| |
| (a) | General Rights. In the event of Supplier’s bankruptcy or other formal procedure referenced in Section 20.5 or the filing of any petition under bankruptcy laws affecting the rights of Supplier which is not stayed or dismissed within thirty (30) days of filing, in addition to the other rights and remedies set forth herein, to the maximum extent permitted by Law, CoreLogic will have the immediate right to retain and take possession for safekeeping all CoreLogic Data, CoreLogic Confidential Information, CoreLogic licensed Third Party Software, CoreLogic owned Equipment, CoreLogic Owned Materials, CoreLogic owned Developed Materials, and all other Software (including all ***), Equipment, Systems or Materials to which the Eligible Recipients are or would be entitled during the Term or upon the expiration or termination of this Agreement. Supplier shall cooperate fully with the Eligible Recipients and assist the Eligible Recipients in identifying and taking possession of the items listed in the preceding sentence. CoreLogic will have the right to hold such CoreLogic Data, CoreLogic Confidential Information, Software (including all source code), Equipment, Systems and Materials until such time as the trustee or receiver in bankruptcy or other appropriate insolvency office holder can provide adequate assurances and evidence to CoreLogic that they will be protected from sale, release, inspection, publication, or inclusion in any publicly accessible |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 78 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
record, document, material or filing. Supplier and CoreLogic agree that without this material provision, CoreLogic would not have entered into this Agreement or provided any right to the possession or use of CoreLogic Data, CoreLogic Confidential Information, or CoreLogic Software covered by this Agreement.
| |
| (b) | CoreLogic Rights in Event of Bankruptcy Rejection. Notwithstanding any other provision of this Agreement to the contrary, if Supplier becomes a debtor under the United States Bankruptcy Code (11 U.S.C. §101 et. seq. or any similar Law in any other country (the “Bankruptcy Code”)) and rejects this Agreement pursuant to Section 365 of the Bankruptcy Code (a “Bankruptcy Rejection”), (i) any and all of the licensee and sublicensee rights of the Eligible Recipients arising under or otherwise set forth in this Agreement, including the rights of the Eligible Recipients referred to in Section 14.6, shall be deemed fully retained by and vested in the Eligible Recipients as protected intellectual property rights under Section 365(n)(1)(B) of the Bankruptcy Code and further shall be deemed to exist immediately before the commencement of the bankruptcy case in which Supplier is the debtor; (ii) CoreLogic shall have all of the rights afforded to non-debtor licensees and sublicensees under Section 365(n) of the Bankruptcy Code; and (iii) to the extent any rights of the Eligible Recipients under this Agreement which arise after the termination or expiration of this Agreement are determined by a bankruptcy court not to be “intellectual property rights” for purposes of Section 365(n), all of such rights shall remain vested in and fully retained by the Eligible Recipients after any Bankruptcy Rejection as though this Agreement were terminated or expired. CoreLogic shall under no circumstances be required to terminate this Agreement after a Bankruptcy Rejection in order to enjoy or acquire any of its rights under this Agreement, including without limitation any of the rights of CoreLogic referenced in Section 14.6 unless and to the extent required by applicable Laws. |
If Supplier receives a ***, then *** may, in its sole discretion, terminate this Agreement *** by giving Supplier at least *** (***) *** prior notice. Supplier *** to *** in connection with such a termination.
| |
| 20.8 | Disengagement Services. |
| |
| (a) | Availability. As part of the Services, and for the Charges set forth in Sections 20.8(b)(2) and 20.8(d) and the applicable Supplement, Supplier shall provide to CoreLogic and its designee(s) the Services described in Section 20.8(b) and any disengagement services described in the applicable Supplement (collectively, the “Disengagement Services”) with respect to any Services that Supplier will no longer be performing for CoreLogic (whether as a result of termination, expiration or removal) (the “Affected Services”). |
| |
| (1) | Period of Provision. Supplier shall provide the Disengagement Services to CoreLogic and its designee(s), commencing after a request for Disengagement Services, and, at CoreLogic’s request, continuing for up to *** (***) *** following the commencement of such Disengagement Services. |
| |
| (2) | Firm Commitment. Supplier shall provide Disengagement Services regardless of the reason for removal of the Affected Services; provided, that if this Agreement is terminated by Supplier under Section 20.1(b), or if, during the Disengagement Services following any other termination or expiration, CoreLogic commits a breach of CoreLogic’s payment obligations under Section 12.2 (Payment Due) or 12.4 (Disputed Charges) and fails to cure such breach within thirty (30) days after receipt of notice of such breach from Supplier, Supplier may *** for Disengagement Services to be provided or performed under this Section 20.8. Such *** shall be based on an *** with any *** to be *** on the ***. |
| |
| (3) | Performance. All Disengagement Services shall be provided subject to and in accordance with the terms and conditions of this Agreement. Without limiting the foregoing, Supplier shall perform the Disengagement Services with at least the same degree of accuracy, quality, |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 79 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
completeness, timeliness, responsiveness and resource efficiency as it was required to provide the same or similar Services during the Term, including compliance with the Service Levels, payment of Service Level Credits in the event it fails to do so, and if the Disengagement Services occur during the Sarbanes-Oxley reporting period, delivery of the SSAE 16 report in accordance with Section 9.10(h). Supplier Personnel (including all Key Supplier Personnel) *** to be critical to the performance of the Services and Disengagement Services shall be retained on the CoreLogic account through the completion of all relevant Disengagement Services.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 80 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (b) | Scope of Disengagement Services. At CoreLogic's request, the Disengagement Services provided by Supplier shall include the services, functions and responsibilities described below (in addition to any Disengagement Services described in the applicable Supplement). |
| |
| (1) | General Support. To the extent requested by CoreLogic, Supplier shall (i) assist CoreLogic or its designee(s) in developing a written disengagement plan (“Disengagement Plan”) to effect the disengagement, (ii) perform programming and consulting services to assist in implementing the Disengagement Plan, (iii) train personnel designated by CoreLogic or its designee(s) in the use of any business processes, work instructions and work procedures and any Equipment, Software, Systems, Materials and tools used in connection with the performance of the Affected Services and to which CoreLogic or an Eligible Recipient has license rights following the termination or expiration of the Affected Services, (iv) catalog all business processes, work instructions, work procedures, Software, CoreLogic Data, Equipment, Materials, Third Party Contracts and tools used to provide the Affected Services, (v) provide machine readable and printed listings and associated documentation for *** Software owned by any Eligible Recipient and *** to which any Eligible Recipient is entitled under this Agreement or the applicable Supplement and assist in its re-configuration, (vi) provide technical documentation for Software used by Supplier to provide the Affected Services and to which CoreLogic or the Eligible Recipients has rights following the termination or expiration of this Agreement, (vii) assist in the execution of a parallel operation, data migration and testing process until the successful completion of the transition of the Affected Services to CoreLogic or its designee(s), (viii) create and provide copies of the CoreLogic Data related to the Affected Services in the format and on the media reasonably requested by CoreLogic, another Eligible Recipient and/or their designee(s), (ix) provide a complete and up-to-date, electronic copy of the Policy and Procedures Manual and any applicable business processes, work instructions and work procedures, in each case in the format and on the media reasonably requested by CoreLogic, and (x) provide other technical assistance requested by CoreLogic that is reasonably related to the disengagement with respect to the Affected Services. With respect to any designee of an Eligible Recipient as contemplated in this Section 20.8(b)(1), CoreLogic agrees to (i) cause the applicable Eligible Recipient to execute an agreement (or confirm that such an agreement as been executed) with such designee that includes confidentiality terms at least as protective as the confidentiality terms contained herein governing CoreLogic’s use of Supplier’s Confidential Information and (ii) provide written confirmation to Supplier that such agreement has been executed between such Eligible Recipient and the applicable designee. |
| |
| (2) | Continuation of the Affected Services. At CoreLogic’s request, Supplier shall continue providing to the Eligible Recipient(s) any or all of the Affected Services after their anticipated the removal, expiration or termination date. Supplier shall provide any such Affected Services subject to and in accordance with the terms and conditions of this Agreement and CoreLogic shall pay Supplier the Charges specified in the applicable Supplement that CoreLogic would have been obligated to pay Supplier for such Affected Services if this Agreement had not yet expired or been terminated or had the Affected Services not been removed. To the extent CoreLogic requests a portion of the Services included in a particular Charge, the amount to be paid by CoreLogic will be equitably adjusted to reflect the portion of the Affected Services included in such Charge that Supplier will not be providing or performing. |
| |
| (3) | *** Subject to Section 20.8(c), CoreLogic and its designee(s) shall be permitted *** without interference from Supplier, Supplier Subcontractors or Supplier Affiliates, *** effective after the date when Supplier ceases provision of the Affected Services, *** *** during the *** (***) *** preceding such date. Supplier shall waive, and shall cause its Subcontractors (as contemplated in Section 20.8(c) below) and Affiliates to waive, their rights, if any, under *** restricting the ability of ***. Supplier shall provide CoreLogic and its designee(s) with reasonable assistance in their efforts to *** such Supplier Personnel, and shall give CoreLogic and its designee(s) ***. CoreLogic shall conduct the above-described *** activity in a manner that is |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 81 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
not unnecessarily disruptive of the performance by Supplier of its obligations under this Agreement.
| |
| (4) | Software. As provided in Section 14.6, Supplier shall provide, and hereby grants certain license, sublicense and/or other rights to certain Software and other Materials used by Supplier, Supplier Affiliates or Subcontractors in performing the Affected Services. |
| |
| (5) | Equipment. Except as otherwise agreed by the Parties, CoreLogic and its designee(s) shall have the right (but not the obligation) to purchase, or assume the lease for, any Equipment owned or leased by Supplier that is *** used by Supplier, Supplier Subcontractors or Supplier Affiliates to perform the Affected Services. Such Equipment shall be transferred in good working condition, reasonable wear and tear excepted, as of the completion of any Affected Services requiring such Equipment. Supplier shall maintain such Equipment through the date of transfer so as to be eligible for the applicable manufacturer’s maintenance program at no additional charge to CoreLogic or its designee(s). In the case of Supplier-owned Equipment, Supplier shall grant to CoreLogic or its designee(s) a warranty of title and a warranty that such Equipment is free and clear of all liens and encumbrances. Such conveyance by Supplier to CoreLogic or its designee(s) shall be at *** calculated in accordance with ***. At CoreLogic’s request, the Parties shall negotiate in good faith and agree upon the form and structure of the purchase. In the case of Supplier leased Equipment, Supplier shall (i) represent and warrant that the lessee is not in default under the lease and that all lease payments have been made through the date of transfer, and (ii) notify CoreLogic of any lessor defaults of which it is aware at the time. EXCEPT AS EXPRESSLY PROVIDED HEREIN, SUPPLIER MAY DISCLAIM OTHER WARRANTIES OF MERCHANTABILITY, SUITABILITY OR FITNESS FOR A PARTICULAR PURPOSE. |
| |
| (6) | CoreLogic Facilities, Equipment and Software. Supplier shall vacate the CoreLogic Facilities and return to CoreLogic, if not previously returned, any CoreLogic owned Equipment (including CoreLogic Provided Equipment as defined in Section 6.5(e)), CoreLogic leased Equipment, CoreLogic Owned Materials and CoreLogic licensed Third Party Materials (including Software), in condition at least as good as the condition when made available to Supplier, ordinary wear and tear excepted. Supplier shall vacate such CoreLogic Facilities and return such Equipment, Materials and Software to the extent that the Services requiring such CoreLogic Facilities, Equipment, Materials and Software are no longer being provided by Supplier. |
| |
| (7) | Supplier Subcontractors and Third Party Contracts. Supplier shall provide prompt notice to CoreLogic of all subcontracts and Third Party Contracts used by Supplier, *** to perform the Affected Services. Subject to Section 6.5(c), Supplier shall, at CoreLogic’s request, use commercially reasonable efforts to cause any dedicated Subcontractors, Supplier Affiliates, or third party contractors to permit CoreLogic or its designee(s) to *** with CoreLogic or its designee(s) ***. Subject to the terms of the applicable subcontract or Third Party Contract, Supplier shall *** the designated subcontracts and Third Party Contracts or cause such subcontracts or Third Party Contracts *** to CoreLogic or its designee(s) after the Services requiring such subcontracts or Third Party Contracts are no longer being provided by Supplier. Unless otherwise agreed by CoreLogic pursuant to Section 6.5(c), there shall *** CoreLogic or its designee(s) by Supplier or its Subcontractors, Affiliates or third party contractors ***. Supplier shall (i) represent and warrant that it is not in default under such subcontracts and Third Party Contracts and that all payments have been made under such subcontracts and Third Party Contracts through the ***, and (ii) notify CoreLogic of any Subcontractor’s or third party contractor’s default with respect to such subcontracts and Third Party Contracts of which it is aware at the time. |
For the avoidance of doubt, it is understood and agreed that, in all events, the Eligible Recipients retain the right to contract directly with any Subcontractor or third party utilized by Supplier, Supplier Subcontractors or Supplier Affiliates to perform any Services. Supplier shall retain the
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 82 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
right to utilize any such Subcontractor or third party services in connection with the performance of services for other Supplier customers.
| |
| (c) | Rights from Subcontractors. With respect to Subcontractors who provide Services on a dedicated basis to CoreLogic and the Eligible Recipients, Supplier shall use all commercially reasonable efforts to (A) obtain for CoreLogic and its designee(s) the rights specified in Section 20.8(b), and (B) ensure that such rights are not subject to subsequent Subcontractor approval or the payment by CoreLogic or its designee(s) of any fees. If Supplier is unable to obtain any such rights with respect to a Subcontractor, it shall notify CoreLogic in advance and shall not use such Subcontractor without CoreLogic’s approval. |
| |
| (d) | Rates and Charges. Except as provided below and in Section 20.8(b)(7), to the extent the Disengagement Services requested by CoreLogic can be provided by Supplier using personnel and resources already assigned to CoreLogic without adversely affecting its ability to meet its performance obligations, there will be no additional charge to CoreLogic for such Disengagement Services. If material Disengagement Services requested by CoreLogic cannot be provided by Supplier using Supplier Personnel then assigned to CoreLogic without adversely affecting Supplier’s ability to meet its performance obligations, CoreLogic, in its sole discretion, may forego or delay any work activities or temporarily or permanently adjust the work to be performed by Supplier, the schedules associated with such work or the Service Levels to permit the performance of such Disengagement Services using such personnel. To the extent CoreLogic authorizes Supplier to use additional Supplier Personnel to perform material Disengagement Services requested by CoreLogic, *** in the applicable Supplement, or*** in the applicable Supplement, *** which shall be *** to CoreLogic *** reflected by the *** applicable Supplement *** in the applicable Supplement. |
21. GENERAL.
| |
| 21.1 | Binding Nature, Assignment. |
| |
| (a) | Binding Nature. This Agreement will be binding on the Parties and their respective successors and permitted assigns. |
| |
| (b) | Assignment. Neither Party may, or will have the power to, assign this Agreement without the prior written consent of the other, except in the following circumstances: |
| |
| (i) | CoreLogic may assign, in whole but not in part, its rights or obligations under this Agreement or any Supplement, without the approval of Supplier, to an Affiliate which expressly assumes CoreLogic’s obligations and responsibilities hereunder, provided that CoreLogic remains fully liable for and is not relieved from the full performance of its obligations under this Agreement; and |
| |
| (ii) | CoreLogic may assign its rights and obligations under this Agreement or any Supplement without the approval of Supplier to an Entity acquiring, directly or indirectly, Control of CoreLogic, an Entity into which CoreLogic is merged, or an Entity acquiring all or substantially all of CoreLogic’s assets, provided that the acquirer or surviving Entity agrees in writing to be bound by the terms and conditions of this Agreement; provided that, if and to the extent such acquisition or merger would result in the Services being materially different and impose materially different or greater obligations on Supplier, such Services to be provided to the acquirer or surviving entity shall be treated as New Services under Section 4.3. CoreLogic shall cause the acquirer or surviving Entity to agree in writing to be bound by the terms and conditions of this Agreement. |
| |
| (c) | Impermissible Assignment. Any attempted assignment that does not comply with the terms of this Section shall be null and void. |
| |
| 21.2 | Entire Agreement; Amendment. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 83 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
This Agreement, including any Schedules, Annexes and Attachments referred to herein and attached hereto as well as any Supplements, Companion Agreements, and Work Orders entered into from time to time, each of which is incorporated herein for all purposes, constitutes the entire agreement between the Parties with respect to the subject matter hereof. The Schedules and Attachments to any Supplements or Work Orders are incorporated into such Supplement or Work Order by this reference. There are no agreements, representations, warranties, promises, covenants, commitments or undertakings other than those expressly set forth herein. This Agreement supersedes all prior agreements, representations, warranties, promises, covenants, commitments or undertaking, whether written or oral, with respect to the subject matter contained in this Agreement. No amendment, modification, change, waiver, or discharge hereof shall be valid unless in writing and signed by an authorized representative of the Party against which such amendment, modification, change, waiver, or discharge is sought to be enforced.
| |
| (a) | Primary Notices. Any notice, notification, request, demand or determination provided by a Party pursuant to the following: |
Section 4.5(a) (Right to In-Source or Use of Third Parties; Cooperation – Right of Use);
Section 6.7 (Notice of Defaults);
Section 9.13 (Notice of Adverse Impact);
Section 10.2 (Supplier Excused Performance);
Section 11.4 (Extraordinary Events);
Section 13.1(d) (Loss of Confidential Information);
Article 16(Insurance and Risk of Loss);
Sections 17.5 (Indemnification Procedures);
Section 17.6 (Indemnification Procedures – Government Claims);
Section 18.2(f) (Waiver of Liability Cap);
Section 19.1 (Dispute Resolution Procedures);
Article 20 (Termination);
Section 20.8 (Disengagement Services); and
Section 21.1 (Binding Nature, Assignment);
shall be in writing and shall be delivered in hard copy using one of the following methods and shall be deemed delivered upon receipt: (i) by hand, (ii) by an express courier with a reliable system for tracking delivery, or (iii) by registered or certified mail, return receipt requested, postage prepaid. Unless otherwise notified, the foregoing notices shall be delivered as follows:
In the case of CoreLogic: In the case of Supplier:
|
| | |
| 9 First American Way | Dell Marketing L.P. |
| Santa Ana, California 92707 | 2330 West Plano Parkway |
| Attention: Chief Information Officer | Plano, Texas 75075 |
| | Attention: Vice-President and General Manager, Infrastructure and Cloud Computing |
| 12395 First American Way | |
| Poway, California 92064 | |
| Attention: Vice President, Enterprise Technology Services | |
With a copy to:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 84 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| 4 First American Way | Dell Marketing L.P. |
| Santa Ana, California 92707 | 2300 West Plano Parkway |
| Attention: General Counsel | Plano, Texas 75075 |
| | Attention: Vice-President, Services Legal |
| |
| (b) | Other Notices. All notices, notifications, requests, demands or determinations required or provided pursuant to this Agreement, other than those specified in Section 21.3(a), shall be in writing and may be sent in hard copy in the manner specified in Section 21.3(a), or by e-mail transmission (where receipt is affirmatively acknowledged by the recipient, excluding auto-receipts) or facsimile transmission (with acknowledgment of receipt from the recipient’s facsimile machine) to the addresses set forth below: |
In the case of CoreLogic: In the case of Supplier:
|
| |
| 12395 First American Way | Dell Marketing L.P. |
| Poway, California 92064 | 2330 West Plano Parkway |
| Attention: Vice President, Enterprise Technology Services | Plano, Texas 75075 Attention: Customer Executive |
| | |
| E-mail Address: ***@corelogic.com | E-mail Address: ***@dell.com |
| Facsimile Number: *** | Facsimile Number: To be determined |
| |
| (c) | Notice of Change. A Party may from time to time change its address or designee for notification purposes by giving the other prior notice of the new address or designee and the date upon which it shall become effective. |
| |
| 21.4 | Counterparts, Headings, Language. |
This Agreement may be executed in several counterparts, all of which taken together shall constitute one single agreement between the Parties hereto. The Article and Section headings and the table of contents used herein are for reference and convenience only and shall not be considered in the interpretation of this Agreement. All Annexes, Schedules, Exhibits, Attachments, documents, materials, deliverable items, notices and communications of any kind between the Parties and their representatives relating to the Services or this Agreement shall be made in the English language.
| |
| 21.5 | Relationship of Parties. |
Supplier, in furnishing services to the Eligible Recipients hereunder, is acting as an independent contractor, and Supplier has the sole obligation to supervise, manage, contract, direct, procure, perform or cause to be performed, all work to be performed by Supplier or Supplier Personnel under this Agreement. The relationship of the Parties under this Agreement shall not constitute a partnership or joint venture for any purpose. Except as expressly provided in this Agreement, Supplier is not an agent of the Eligible Recipients and has no right, power or authority, expressly or impliedly, to represent or bind the Eligible Recipients as to any matters.
If any provision of this Agreement conflicts with applicable Law or is held void, invalid or unenforceable by a court with jurisdiction over the Parties, such provision shall be deemed to be restated to reflect as nearly as possible the original intentions of the Parties in accordance with applicable Law. The remaining provisions of this Agreement and the application of the challenged provision to persons or circumstances other than those
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 85 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
as to which it is void, invalid or unenforceable shall not be affected thereby, and each such provision shall be valid and enforceable to the full extent permitted by applicable Law.
| |
| 21.7 | Consents and Approval. |
Except where expressly provided as being in the sole discretion of a Party, where agreement, approval, acceptance, consent, confirmation, notice or similar action by either Party is required under this Agreement, such action shall not be unreasonably delayed or withheld. An approval or consent given by a Party under this Agreement shall not relieve the other Party of responsibility for complying with the requirements of this Agreement, nor shall it be construed as a waiver of any rights under this Agreement, except as and to the extent expressly provided in such approval or consent.
| |
| 21.8 | Waiver of Default; Cumulative Remedies. |
| |
| (a) | Waiver of Default. A delay or omission by either Party hereto to exercise any right or power under this Agreement shall not be construed to be a waiver thereof. A waiver by either of the Parties hereto of any of the covenants to be performed by the other or any breach thereof shall not be construed to be a waiver of any succeeding breach thereof or of any other covenant herein contained. All waivers must be in writing and signed by the Party waiving its rights. |
| |
| (b) | Cumulative Remedies. All remedies provided for in this Agreement shall be cumulative and in addition to and not in lieu of any other remedies available to either Party at law, in equity or otherwise. The election by a Party of any remedy provided for in this Agreement or otherwise available to such Party shall not preclude such Party from pursuing any other remedies available to such Party at law, in equity, by contract or otherwise. |
Any provision of this Agreement which contemplates performance or observance subsequent to any termination or expiration of this Agreement shall survive any termination or expiration of this Agreement and continue in full force and effect. Additionally, all provisions of this Agreement will survive the expiration or termination of this Agreement to the fullest extent necessary to give the Parties the full benefit of the bargain expressed herein.
Neither Party shall use the other Party’s (or any Eligible Recipient’s) names, logos, service marks, trade names or trademarks or refer to the other Party directly or indirectly in any media release, public announcement, or public disclosure, in each case, relating to this Agreement, including in any promotional, advertising or marketing materials, customer lists or business presentations except for the use of a Party’s name in customer lists for business presentations (for clarity, in text, but not using stylized name or logo without CoreLogic’s prior approval) without the prior written consent of the other Party prior to each such use or release (except as otherwise required by Law). For clarity, the immediately preceding sentence shall not limit either Party’s (or any Eligible Recipient’s) communications with respect to transactions with mutual customers of the Parties (or the Eligible Recipients) that are unrelated to this Agreement.
| |
| 21.11 | Third Party Beneficiaries. |
Except as expressly provided in this Agreement, this Agreement is entered into solely between, and may be enforced only by, CoreLogic and Supplier. This Agreement shall not be deemed to create any rights or causes of action in or on behalf of any third parties, including employees, supplier and customers of a Party, or to create any obligations of a Party to any such third parties.
| |
| 21.12 | Covenant Against Pledging. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 86 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Supplier agrees that, without the prior written consent of CoreLogic, it shall not assign, transfer, pledge, hypothecate or otherwise encumber its rights to receive payments from CoreLogic under this Agreement for any reason whatsoever. To the extent CoreLogic permits Supplier to assign, transfer, pledge, hypothecate or otherwise encumber its rights to receive payments from CoreLogic under this Agreement, Supplier shall continue to be CoreLogic’s sole point of contact with respect to this Agreement, including with respect to payment. The person or Entity to which such rights are assigned, transferred, pledged, hypothecated or otherwise encumbered shall not be considered a third party beneficiary under this Agreement and shall not have any rights or causes of action against CoreLogic.
| |
| 21.13 | Order of Precedence. |
In the event of a conflict, this MSA shall take precedence over (a) the Schedules and Annexes, and the Schedules and Annexes shall take precedence over the Attachments to those Schedules and Annexes, (b) any Supplement or Work Order, and Supplements shall take precedence over Work Orders and both Supplements and Work Orders shall take precedence over their Schedules and Attachments, and (c) any Companion Agreement, except for any term specifically identified as superseding the terms of this MSA or an applicable Supplement, which term shall control over this MSA or such Supplement, as applicable, for that Annex, Supplement, Attachment, Schedule, Work Order or Companion Agreement only.
| |
| (a) | Solicitation and Hiring. Except as expressly set forth herein, during the Term and for a period of ***(***)*** thereafter, Supplier will not solicit for employment directly or indirectly, nor employ, any employees of an Eligible Recipient or *** with whom Supplier had more than incidental contact with in the course of performing its obligations under this Agreement within the previous ***(***) *** without the prior approval of CoreLogic. Except as expressly set forth herein in connection with the expiration or termination of this Agreement, during the Term and for a period of ***(***)*** thereafter, CoreLogic will not solicit for employment directly or indirectly, nor employ, any employee of Supplier involved in the performance of Supplier’s obligations under this Agreement within the previous ***(***) *** without the prior consent of Supplier. In each case, the prohibition on solicitation and hiring shall extend ***(***) *** after the termination of the employee’s employment or, in the case of Supplier employees, the cessation of his or her involvement in the performance of Services under this Agreement. This provision shall not operate or be construed to prevent or limit any employee’s right to practice his or her profession or to utilize his or her skills for another employer or to restrict any employee’s freedom of movement or association. |
| |
| (b) | Publications. Neither the publication of classified advertisements in newspapers, periodicals, Internet bulletin boards, or other publications of general availability or circulation nor the consideration and hiring of persons responding to such advertisements shall be deemed a breach of this Section 21.14, unless the advertisement and solicitation is undertaken as a means to circumvent or conceal a violation of this provision and/or the hiring party acts with knowledge of this hiring prohibition. |
Supplier shall not file, or by its action or inaction permit, any liens to be filed on or against property or realty of any Eligible Recipient. CoreLogic shall not file, or by its action or inaction permit, any liens to be filed on or against property or realty of Supplier or its Affiliates. If any such liens arise as a result of Supplier’s breach of the foregoing, Supplier shall obtain a bond to fully satisfy such liens or otherwise remove such liens at its sole cost and expense within ten (10) business days.
| |
| 21.16 | Covenant of Cooperation and Good Faith. |
Each Party agrees that, in its respective dealings with the other Party under or in connection with this Agreement, it shall act in good faith.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 87 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 21.17 | Acknowledgment, Further Assurances. |
The Parties each acknowledge that the terms and conditions of this Agreement have been the subject of active and complete negotiations, and that such terms and conditions should not be construed in favor of or against any Party by reason of the extent to which any Party or its professional advisors participated in the preparation of this Agreement. Each Party covenants and agrees that, subsequent to the execution and delivery of this Agreement and without any additional consideration, each Party shall execute and deliver any further legal instruments and perform any acts that are or may become necessary to effectuate the purposes of this Agreement.
| |
| 21.18 | Reference and Customer Satisfaction Survey. |
Unless otherwise directed by CoreLogic, Supplier *** as a reference *** for prospective Supplier customers interested in purchasing services that include the same or substantially similar services to the Services. In conjunction with the foregoing, the CoreLogic Relationship Manager (or equivalent level of CoreLogic management), *** as the contact point for such prospective Supplier customers and *** to all ***. Notwithstanding anything to the contrary in this Agreement, Supplier acknowledges and agrees that the CoreLogic Relationship Manager (or equivalent level of CoreLogic management) may freely discuss all aspects of Supplier's performance and CoreLogic’s satisfaction with such performance with prospective Supplier customers. Supplier *** such prospective Supplier customers with appropriate CoreLogic contact information. The identity of such prospective Supplier customers and all information related thereto shall be considered Supplier Confidential Information. Once per quarter, one or more CoreLogic representatives shall participate in a customer satisfaction survey, using Supplier’s then-current standard methodology (as of the Effective Date, the Net Promoter System), in order to gauge the satisfaction of CoreLogic personnel with the Services as well as Supplier’s performance generally.
SIGNATURE PAGE FOLLOWS
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | MSA | Page 88 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
IN WITNESS WHEREOF, the Parties have caused this Agreement to be executed by their respective duly authorized representatives as of the Effective Date.
|
| | | | |
| CoreLogic Solutions, LLC | | Dell Marketing L.P. |
| By: | | | By: | |
| Title: | | | Title: | |
| Date: | | | Date: | |
CORELOGIC AND DELL CONFIDENTIAL MSA Signature Page
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CoreLogic Solutions, LLC
and
Dell Marketing L.P.
July 19, 2012
SCHEDULE 1
DEFINITIONS
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without their prior written permission. |
CORELOGIC AND DELL CONFIDENTIAL Schedule 1 Page 12
Schedule 1
Definitions
| |
1. | Agreement. This Schedule 1 (this “Schedule”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
2. | References. All references in this Schedule to articles, sections and schedules shall be to this Schedule, unless another reference is provided. |
| |
3. | General. The terms defined in this Schedule include the plural as well as the singular and the derivatives of such terms. Unless otherwise expressly stated, the words “herein,” “hereof,” and “hereunder” and other words of similar import refer to the Agreement as a whole and not to any particular Article, Section, Subsection or other subdivision. Article, Section, Subsection and Attachment references refer to articles, sections and subsections of, and attachments to, the MSA, unless specified otherwise. The words “include” and “including” shall not be construed as terms of limitation and introduce a non-exclusive set of examples. The words “day,” “month,” and “year” mean, respectively, calendar day, calendar month and calendar year. As stated in Section 21.3 of the MSA, the word “notice” and “notification” and their derivatives means notice or notification in writing. Other terms used in the Agreement are defined in the context in which they are used and have the meanings there indicated. |
The following terms, when used in the Agreement, have the meanings specified below.
“Acceptance” means the determination and in accordance with the acceptance criteria set forth in the Supplement, Policy and Procedures Manual or otherwise agreed to by the Parties in writing (“Acceptance Criteria”), that *** and/or Developed Materials Transition Milestones and Transformation Milestones are in Compliance.
“Access Code” means a user identification number, a code or a password (or some combination of the foregoing) permitting access to the CoreLogic Network.
“Administered Expenses” means the expenses identified as “Administered Expenses” in the applicable Supplement.
“Affected Employee” means an employee of an Eligible Recipient who, as of the Supplement Effective Date of an applicable Supplement, is performing Services that will be performed by Supplier under such Supplement and is identified as such in the Supplement.
“Affected Services” has the meaning given in Section 20.8(a).
“Affiliate” means, generally, with respect to any Entity, any other Entity Controlling, Controlled by or under common Control with such Entity.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 1 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Agreement” has the meaning given in Section 1.1(c).
“Agreement Terms” has the meaning given in Section 13.1(b)(v).
“Applications Software” or “Applications” means those software application programs and programming (and all modifications, replacements, Upgrades, enhancements, documentation, materials and media related thereto) used to support day-to-day business operations and accomplish specific business objectives to the extent Supplier has financial or operational responsibility for such programs or programming under the applicable Supplement. Applications Software shall include all such programs or programming in use as of the Supplement Effective Date, including those (i) that are set forth in the applicable Supplement, (ii) that are included in the CoreLogic Base Case, if any, or (iii) as to which Supplier received notice or access prior to the Supplement Effective Date. Applications Software also shall include all such programs or programming developed and/or introduced on or after the Supplement Effective Date to the extent a Party has financial or operational responsibility for such programs or programming under the applicable Supplement. Applications Software does not include the tools, utilities, or Systems Software used to host such Applications Software in a data center.
“At Risk Amount” has the meaning given in the applicable Supplement.
“Audit Period” has the meaning given in Section 9.10(a).
“Authorized User(s)” means, individually and collectively, the employees, customers, agents, representatives and contractors and subcontractors, of CoreLogic or other Eligible Recipients (other than Supplier and its Subcontractors), to the extent designated by CoreLogic or an Eligible Recipient to receive or use the Systems or Services provided by Supplier.
“Bankruptcy Code” has the meaning given in Section 20.6(b).
“Bankruptcy Rejection” has the meaning given in Section 20.6(b).
“Benchmark Standard” has the meaning given in Section 11.6(c).
“Benchmarker” has the meaning given in Section 11.6(a).
“Benchmarking” has the meaning given in Section 11.6(a)
“Cardholder Data” means all data designated as “Cardholder Data” or “Sensitive Authentication Data” in PCI DSS.
“Change Management Procedures” has the meaning given in Section 9.6(a).
“Charges” means the amounts (including rates) set forth in a Supplement, including in Schedule 4 to the Supplement, as charges for the Services under that Supplement, excluding Administered Expenses, Service Taxes, Out-of-Pocket Expenses and CoreLogic Retained Expenses.
“Classic Services” means all Services other than those designated in an applicable Supplement to be performed as Managed Services.
“***” has the meaning given in Section 18.2(c)(vii).
“Commencement Date” has the meaning given in Section 1.2(b).
“Companion Agreement” has the meaning given in Section 2.2(a).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Compliance” and “Comply” means, with respect to *** to be implemented, designed, developed, delivered, integrated, installed and/or tested by Supplier, compliance with the Acceptance Criteria and compliance in all material respects with the applicable Specifications.
“Confidential Information” has the meaning given in Section 13.1(a).
“Contract Changes” has the meaning given in Section 11.1(d).
“Contract Records” has the meaning given in Section 9.10(a).
“Contract Year” means, for the first Contract Year, a period commencing on the Commencement Date and ending twelve (12) months after the Commencement Date and, for each ensuing Contract Year, a twelve (12) month period commencing on the applicable anniversary of the Commencement Date and ending twelve (12) months thereafter. If any Contract Year is less than twelve (12) months, the rights and obligations under this Agreement that are calculated on a Contract Year basis will be proportionately adjusted for such shorter period.
“Control” and its derivatives means: (a) the legal, beneficial, or equitable ownership, directly or indirectly, of (i) at least fifty percent (50%) of the aggregate of all voting equity interests in an Entity or (ii) equity interests having the right to at least fifty percent (50%) of the profits of an Entity or, in the event of dissolution, to at least fifty percent (50%) of the assets of an Entity; (b) the right to appoint, directly or indirectly, a majority of the board of directors; or (c) the right to control, directly or indirectly, the management or direction of the Entity by contract or corporate governance document; or (d) in the case of a partnership, the holding by an Entity (or one of its Affiliates) of the position of sole general partner.
“CoreLogic” has the meaning given in preamble of the Agreement.
“CoreLogic Base Case” means the summary financial base case attached to the applicable Supplement (if any), as well as the detailed financial and budget information underlying such summary base case.
“CoreLogic Data” means any data or information of CoreLogic or any Eligible Recipient or any of their customers that is provided to or obtained by Supplier in connection with the negotiation and execution of this Agreement or the performance of its obligations under this Agreement, including data and information with respect to the intellectual property, trade secrets, businesses, past current and prospective customers, operations, facilities, products, insurance policies, policy holders, applicants or other prospective customers, rates, regulatory compliance, competitors, consumer markets, assets, expenditures, mergers, acquisitions, divestitures, billings, collections, revenues and finances of CoreLogic or any Eligible Recipient, including similar information of any of their customers. CoreLogic Data also means any data or information of CoreLogic or an Eligible Recipient or any of their customers (i) created, generated, collected or processed by Supplier in the performance of its obligations under this Agreement, including data processing input and output, asset information, Reports, third party service and product agreements of CoreLogic or an Eligible Recipient, retained expenses and Administered Expenses or (ii) that resides in or is accessed through Software, Equipment or Systems provided, operated, supported, or used by Supplier in connection with the Services, as well as information derived from this data and information; provided, however, that CoreLogic Data excludes Supplier's Development Tools, Supplier Owned Materials, Supplier Owned Developed Materials, Supplier Owned Software and Third Party Software licensed by Supplier. CoreLogic Data shall not include any Supplier Confidential Information.
“CoreLogic Data Indirect Losses” has the meaning given in Section 18.2(d)(iii).
“CoreLogic Export Materials” has the meaning given in Section 15.7(g)(ii).
“CoreLogic Facilities” means the facilities identified as “CoreLogic Facilities” in the applicable Supplement.
“CoreLogic Laws” has the meaning given in Section 15.7(d).
“CoreLogic Network” has the meaning given in Section 6.3(a).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 3 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“CoreLogic Owned Developed Materials” has the meaning given in Section 14.2(a).
“CoreLogic Owned Materials” has the meaning given in Section 14.1(a).
“CoreLogic Personnel” means the employees, agents, contractors or representatives of CoreLogic employed or contracted by CoreLogic or its Affiliates or Eligible Recipients.
“CoreLogic Policy Sets” or “Policy Sets” has the meaning given in Section 9.5(a).
“CoreLogic Privacy Policy” means CoreLogic's privacy policy listed in Schedule 8.
“CoreLogic Provided Equipment” has the meaning given in Section 6.5(e).
“CoreLogic Relationship Manager” has the meaning given in Section 10.1(a).
“CoreLogic Rules” has the meaning given in Section 6.2(b).
“CoreLogic Service Taxes” has the meaning given in Section 11.3(d).
“CoreLogic-Specific Facility and Controls Audit” has the meaning given in Section 9.10(h).
“CoreLogic Standards” has the meaning given in Section 9.5(a).
“Critical Deliverables” means the deliverables identified in the applicable Supplement, if any, that have associated Deliverable Credits payable to CoreLogic in the event Supplier fails to deliver such deliverables in accordance with such Supplement.
“Critical Service Level” means a Service Level identified as a “Critical Service Level” in a Supplement with respect to which Service Level Credits may be payable to CoreLogic if Supplier fails to meet such Service Level.
“Customer Executive” has the meaning given in Section 8.3.
“Data Breach Costs” has the meaning given in Section 13.3(e).
“Data Controller” has the meaning given in the European Union Data Protection Legislation.
“Data Exporter” has the meaning given in the European Union Data Protection Legislation.
“Data Importer” has the meaning given in the European Union Data Protection Legislation.
“Data Processor” has the meaning given in the European Union Data Protection Legislation.
“Deliverable” means a Developed Material that is identified as a deliverable in the Agreement, or in a Supplement, statement of work, project plan, or other writing by or between the Parties.
“Deliverable Credits” means the amount payable to CoreLogic in the event Supplier fails to deliver a Critical Deliverable or meet certain Transition Milestones in accordance with a Supplement.
“Derivative Work” means a work based on one or more preexisting works, including a condensation, transformation, translation, modification, expansion, or adaptation, that, if prepared without authorization of the owner of the copyright of such preexisting work, would constitute a copyright infringement under applicable Law, but excluding the preexisting work.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 4 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Developed Materials” means any Materials (including Software), or any modifications, enhancements or Derivative Works thereof, developed by or on behalf of Supplier for CoreLogic or the other Eligible Recipients in the course of providing the Services.
“Development Tools” means all software programs and programming (and all modifications, replacements, Upgrades, enhancements, documentation, materials and media related thereto) that are used in the development, testing, deployment and maintenance of Applications to the extent a Party has financial or operational responsibility for such programs or programming under a Supplement. Development Tools shall include all such products in use or required to be used as of the Commencement Date, including those set forth in the applicable Supplement, those as to which the license, maintenance or support costs are included in the CoreLogic Base Case, if any, and those as to which Supplier received reasonable notice and/or access prior to the Commencement Date. Development Tools also shall include all such products selected and/or developed by or for CoreLogic or the other Eligible Recipients on or after the Commencement Date to the extent a Party has financial or operational responsibility for such programs or programming under a Supplement.
“Direct CoreLogic Competitors” means the Entities identified in Schedule 10 of the Agreement, as well as their subsidiaries, successors and assigns, as such list of Entities may reasonably be modified by CoreLogic from time to time upon *** (***) *** prior notice; provided, however, that the number of Direct CoreLogic Competitors may not at any time exceed *** (***) Entities.
“Direct Supplier Competitors” means the Entities identified in Schedule 11 of the Agreement, as well as their subsidiaries, successors and assigns, as such list of Entities may reasonably be modified by Supplier from time to time upon *** (***) days prior notice; provided, however, that the number of Direct Supplier Competitors may not at any time exceed *** (***) Entities.
“Disengagement Plan” has the meaning given in Section 20.8(b)(1).
“Disengagement Services” has the meaning given in Section 20.8(a).
“Disputed New Services Fee” has the meaning given in Section 4.3(a).
“EEA” has the meaning given in Section 13.3(a)(i).
“Effective Date” has the meaning given in the preamble to the MSA.
“Eligible Recipients” means, collectively, the following:
| |
(b) | any Entity that is an Affiliate of CoreLogic on the Supplement Effective Date, or thereafter becomes an Affiliate of CoreLogic; |
| |
(c) | any Entity that purchases after the Supplement Effective Date from ***, all or substantially all of the assets of CoreLogic or such Affiliate, or of any division, marketing unit or business unit thereof, provided that such Entity agrees in writing to be bound by the terms and conditions of this Agreement; |
| |
(d) | any Entity that after the Supplement Effective Date is created using assets of ***, provided that such Entity agrees in writing to be bound by the terms and conditions of this Agreement; |
| |
(e) | any Entity into which *** merges or consolidates, provided that such Entity has assumed CoreLogic's obligations under this Agreement, and provided further that such Entity agrees in writing to be bound by the terms and conditions of this Agreement; |
| |
(f) | any Entity which merges into or consolidates with ***; |
| |
(g) | any Entity in which on or after the Supplement Effective Date, CoreLogic *** has ***, including any corporation, joint venture or partnership; |
| |
(h) | any person or Entity *** in the *** identified in clauses (a) through (g) (e.g., ***), but only in connection with the *** to ***; and |
| |
(i) | other entities to which the Parties agree. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 5 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Employment Effective Date” means the date on which an Affected Employee becomes a Transitioned Employee pursuant to the process described in the applicable Supplement.
“Entity” means a corporation, partnership, joint venture, trust, limited liability company, limited liability partnership, association or other organization or entity.
“Equipment” means all computing, networking and communications equipment procured, provided, operated, supported, or used by an Eligible Recipient, Supplier or an Authorized User in connection with the Services to the extent a Party has financial or operational responsibility for the same under a Supplement, including (i) mainframe, midrange, server and distributed computing equipment and associated attachments, features, accessories, peripheral devices, and cabling, (ii) personal computers, laptop computers, terminals, workstations and personal data devices and associated attachments, features, accessories, printers, multi-functional printers, peripheral or network devices, and cabling, and (iii) voice, data, video and wireless telecommunications and network and monitoring equipment and associated attachments, features, accessories, peripheral devices, cell phones and cabling.
“Equipment Leases” means all leasing arrangements whereby CoreLogic, another Eligible Recipient or a Third Party Contractor leases Equipment as of the Commencement Date which will be used by Supplier (or Subcontractors or Affiliates of Supplier) to provide the Services after such Commencement Date to the extent a Party has financial or operational responsibility for the same under a Supplement. Equipment Leases include those leases identified in the applicable Supplement, those leases as to which the lease, maintenance and support costs are included in the CoreLogic Base Case, if any, and all other such leases as to which Supplier received notice or access prior to the Supplement Effective Date.
“Extraordinary Event” has the meaning given in Section 11.4(a).
“Facility and Controls Audit” has the meaning given in Section 9.10(h).
“F&C Audit Deficiency” has the meaning given in Section 9.10(h).
“Full Time Equivalent” or “FTE” has the meaning given in the applicable Supplement.
“Force Majeure Event” has the meaning given in Section 9.14(a).
“Functional Service Area” means each of the service areas identified in the applicable Supplement as a “Functional Service Area.”
“Grace Period” has the meaning given in Section 12.2.
“HIPAA Privacy Rule” means the Health Insurance Portability and Accountability Act of 1996 and regulations thereunder (45 C.F.R. Parts 160-164), as the same may be amended from time to time.
“Income Taxes” means any tax on or measured by the net income of a Party (including taxes on capital or net worth that are imposed as an alternative to a tax based on net or gross income), or taxes which are of the nature of excess profits tax, minimum tax on tax preferences, alternative minimum tax, accumulated earnings tax, personal holding company tax, capital gains tax or franchise tax for the privilege of doing business.
“Issuers” has the meaning given in Section 13.2(e).
“Key Supplier Personnel” means the Supplier Personnel filling the positions designated as Key Supplier Personnel positions in a Supplement.
“Knowledge Transfer Personnel” means the transitioned employees that are designated as Knowledge Transfer Personnel in a Supplement.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 6 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Laws” means all federal, state, provincial, regional, territorial and local laws, statutes, regulations, rules, executive orders, supervisory requirements, directives, circulars, opinions, interpretive letters and official releases of or by any government, or any authority, department or agency thereof , including Privacy Laws.
“Losses” means all losses, liabilities, damages (including punitive and exemplary damages), fines, penalties, interest and claims (including taxes), and all related costs and expenses (including reasonable legal fees and disbursements and costs of investigation, litigation, experts, settlement, judgment, interest and penalties).
“Major Release” means a new version of Software that includes changes to the architecture and/or adds new features and functionality in addition to the original functional characteristics of the preceding software release. These releases are usually identified by full integer changes in the numbering, such as from “7.0” to “8.0,” but may be identified by the industry as a major release without the accompanying integer change.
“Malicious Code” means (i) any code, program, or sub-program whose knowing or intended purpose is to damage or maliciously interfere with the operation of the computer system containing the code, program or sub-program, or to halt, disable or maliciously interfere with the operation of the Software, code, program, or sub-program, itself, or (ii) any device, method, or token that permits any person to circumvent the normal security of the Software or the system containing the code.
“Managed Services” means the categories of Services expressly identified in an applicable Supplement to be performed by Supplier as “Managed Services” (for example, Service Areas or portions thereof).
“Managed Third Party” has the meaning given in Section 4.5(c).
“Management Tools” means all software products and tools (and all modifications, replacements, Upgrades, enhancements, documentation, materials and media related thereto) that are used by Supplier to deliver and manage the Services to the extent a Party has financial or operational responsibility for such software products and tools under the applicable Supplement. Management Tools shall include all such products or tools in use as of the Supplement Effective Date, including those (i) that are listed in a Supplement, (ii) for which the license, maintenance or support costs are included in the CoreLogic Base Case, if any, or (iii) as to which Supplier otherwise received notice or access prior to the Supplement Effective Date. Management Tools also shall include all such software products and tools selected and/or developed on or after the Effective Date to the extent a Party has financial or operational responsibility for such programs or programming under the applicable Supplement.
“Master Services Agreement” or “MSA” has the meaning given in Section 1.1(a).
“Materials” means, collectively, Software, literary works, other works of authorship, documented specifications, designs, analyses, processes, methodologies, concepts, inventions, know-how, programs, program listings, programming tools, documentation, reports, drawings, databases, spreadsheets, machine-readable text and files financial models and work product, whether tangible or intangible.
“Minimum Service Level” means the level of performance designated as such in the applicable Supplement for each Service Level.
“Minor Release” means a scheduled release containing small functionality updates and/or accumulated resolutions to defects or non-conformances made available since the immediately preceding release (whether Major Release or Minor Release). Minor Releases shall include “Maintenance Releases” which are supplemental to and made available between Major Releases and other Minor Releases, issued and provided under specific vendor service level or maintenance obligations and contain only accumulated resolutions or mandated changes. These releases are usually identified by a change in the decimal numbering of a release, such as “7.12” to “7.13.”
“Monthly Invoice” has the meaning given in Section 12.1(a).
“New Advances” has the meaning given in Section 9.12(d).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 7 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“New Services” means new services or significant changes to existing Services requested or required (including indirectly, through a change by CoreLogic in the CoreLogic Standards, CoreLogic Rules or other CoreLogic requirements as permitted by the Agreement) by CoreLogic, (i) that (x) are *** or (y) impose *** on Supplier and, for each of (x) and (y) require *** from Supplier, or (ii) that require *** from Supplier, and for each of (i) and (ii) for which there is ***.
“Notice of Election” has the meaning given in Section 17.5(a).
“Official” has the meaning given in Section 15.7(h).
“Other PPM Provisions” has the meaning given in Section 9.1(f).
“Out-of-Pocket Expenses” means reasonable and actual out-of-pocket expenses due and payable to a third party by Supplier that are *** for which Supplier is entitled to be reimbursed by CoreLogic under this Agreement. Out-of-Pocket Expenses shall not include *** (or ***), *** or *** and shall be *** of *** and *** attributable to the expense.
“Party” and “Parties” means CoreLogic and Supplier.
“PCI DSS” has the meaning given in Section 13.2(e).
“Permitted Auditors” has the meaning given in Section 9.10(b).
“Perpetual License Exceptions” has the meaning given in Section 14.2(c)(iv).
“Personal Data” means that portion of CoreLogic Data that is subject to any Privacy Laws.
“Policy and Procedures Manual” means the document containing the information described in Section 9.1(a).
“Policy Set Changes Implementation Plan” has the meaning given in Section 9.5(a).
“Post-Term IP License Period” has the meaning given in Section 14.6(b)(i).
“Privacy Laws” means Laws that relate to the confidentiality, security and protection of personally-identifiable information, customer information, electronic data privacy, trans-border data flow or data protection.
“Project” has the meaning given in the applicable Supplement, if any.
“Quality Assurance” means the actions, planned and performed, to provide confidence that all business processes, Systems, Equipment, Software and components that influence the quality of the Services are working as expected, both individually and collectively.
“Reports” has the meaning set forth in Section 9.2(a).
“Required Consents” means the consents (if any) required to be obtained: (i) to assign or transfer to Supplier, or obtain for Supplier the right to use and/or access, any CoreLogic licensed Third Party Software, Third Party Contracts or Equipment Leases or Acquired Assets; (ii) to grant Supplier the right to use and/or access the CoreLogic licensed Third Party Software in connection with providing the Services; (iii) to grant CoreLogic and the Eligible Recipients and their customers the right during the Term, the applicable Supplement Term and any Termination Assistance Services period to use and/or access the Supplier Owned Software, Third Party Software and Equipment acquired, operated, supported or used by Supplier in connection with providing the Services; (iv) to assign or transfer to CoreLogic, the Eligible Recipients or their designee any Developed Materials, Supplier Owned Software, Third Party Software, Third Party Contracts, Equipment leases or other rights following the Term or the applicable Supplement Term to the extent
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 8 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
provided in this Agreement; and (v) all other consents required from third parties in connection with Supplier's provision of the Services or performance of its obligations hereunder.
“Resource Unit” shall have the meaning, if any, set forth in the applicable Supplement.
“Restricted Period” has the meaning set forth in Section 8.5(d).
“Restricted Personnel” has the meaning set forth in Section 8.5(d).
“Retained Expense” means an expense (i) related to a Retained System and Business Process, or (ii) for which CoreLogic has financial responsibility under a Supplement.
“Retained Systems and Business Processes” means those Systems and business processes of CoreLogic or an Eligible Recipient for which Supplier has not assumed responsibility under this Agreement (including those provided, managed, operated, supported and/or used on their behalf by Third Party Contractors). Retained Systems and Business Processes include equipment and software associated with such systems and business processes.
“RFP” has the meaning given in Section 9.10(b).
“RFQ” has the meaning given in Section 9.10(b).
“Root Cause Analysis” is the formal process, specified in the Policy and Procedures Manual, to be used by Supplier to diagnose problems at the lowest reasonable level so that corrective action can be taken that will eliminate, to the extent reasonably possible, repeat failures. Supplier shall implement a Root Cause Analysis as specified in Schedule 3 or as reasonably requested by CoreLogic.
“SEC” has the meaning given in Section 13.1(b)(v).
“Security Incident” has the meaning given in Section 13.2(b).
“Service Area” means a category of Services expressly identified as a “Service Area” in an applicable Supplement.
“Service Level(s)” has the meaning given in Section 7.1.
“Service Level Credits” has the meaning given in Section 7.3.
“Service Taxes” means all sales, use, excise, value-added, consumption, goods and services and other similar taxes that are assessed against either Party on the provision of the Services as a whole, or on any particular Service received by CoreLogic or the Eligible Recipients from Supplier, excluding Income Taxes.
“Services” means, collectively: (i) the services, functions and responsibilities described in Article 4 and elsewhere in this Agreement or in the applicable Supplement (including Transition Services and Termination Assistance Services) as each may be supplemented, enhanced, modified or replaced during the Term or the applicable Supplement Term in accordance with this Agreement; (ii) ongoing Projects and new Projects, *** for such Projects in accordance with Section 4.5 and the other provisions of this Agreement or such Supplement; and (iii) any New Services, *** for such New Services in accordance with Section 4.3 and the other provisions of this Agreement.
“SIRP” has the meaning given in Section 13.2(b)(iv).
“Software” means all software programs and programming for which a Party is financially or operationally responsible under the applicable Supplement (and all modifications, replacements, Upgrades, enhancements, documentation, materials and media related thereto), including Applications, Development Tools, Management Tools, and Systems Software, unless a more specific reference is required by the context.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 9 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Specialized Services” has the meaning given in Section 9.15.
“Specifications” means, with respect to Software, Equipment, Systems or other contract deliverables to be designed, developed, maintained, modified, enhanced, delivered, integrated, installed and/or tested by Supplier, the technical, design and/or functional specifications set forth in the applicable Supplement, in third party vendor standard documentation, in a New Services or Project description requested and/or approved by CoreLogic or otherwise agreed upon in writing by the Parties.
“SSAE 16” has the meaning given in Section 9.10(h).
“Standard Cap” has the meaning given in Section 18.2(b).
“Strategic Plan” means the plans periodically developed by CoreLogic that set forth CoreLogic' key business objectives and requirements and outline its strategies for achieving such objectives and requirements. CoreLogic may revise the Strategic Plan from time to time. The Strategic Plan is likely to include both annual and multi-year strategies, objectives and requirements.
“Subcontractors” means subcontractors (of any tier) of Supplier, including Affiliates of Supplier.
“Supplement” has the meaning given in Section 1.1(b).
“Supplement Effective Date” means, with respect to an individual Supplement, the meaning given in the preamble to such Supplement.
“Supplier” has the meaning given in the preamble of the MSA.
“Supplier Data Indirect Losses” has the meaning given in Section 18.2(d)(iv).
“Supplier Facilities” means, individually and collectively, the facilities owned, leased or used by Supplier or its Affiliates or Subcontractors from which any Services are provided or performed (other than CoreLogic Facilities). Supplier Facilities are listed on Schedule 7 and the applicable Supplements.
“Supplier Laws” has the meaning given in Section 15.7(d).
“Supplier Owned Developed Materials” has the meaning given in Section 14.2(c).
“Supplier Owned Materials” has the meaning given in Section 14.3(a).
“Supplier Owned Software” means any Software owned by Supplier or its Affiliates and used to provide the Services.
“Supplier Personnel” means those employees, representatives, contractors, subcontractors and agents of Supplier, Subcontractors and Supplier Affiliates who perform any Services under this Agreement or a Supplement.
“Supplier Service Taxes” has the meaning given in Section 11.3(d).
“System” means an interconnected grouping of manual or electronic processes, including Equipment, Software and associated attachments, features, accessories, peripherals and cabling, and all additions, modifications, substitutions, Upgrades or enhancements to such System, in each case to the extent a Party has financial or operational responsibility for such System or System components under the applicable Supplement. System shall include all Systems in use as of the Supplement Effective Date, all additions, modifications, substitutions, Upgrades or enhancements to such Systems and all Systems installed or developed by or for CoreLogic or Supplier in connection with its performance of the Services following the Supplement Effective Date.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 10 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Systems Software” means all software programs and programming (and all modifications, replacements, Upgrades, enhancements, documentation, materials and media related thereto) that perform tasks basic to the functioning of the Equipment and are required to operate the Applications Software or otherwise support the provision of Services by Supplier, including operating systems, systems utilities, data security software, compilers, performance monitoring and testing tools and database managers, to the extent a Party has financial or operational responsibility for such programs or programming under the applicable Supplement. Systems Software shall include all such programs or programming in use as of the Supplement Effective Date, including those (i) that are set listed in such Supplement, (ii) for which the license, maintenance or support costs are included in the CoreLogic IT Base Case, if any, or (iii) as to which Supplier otherwise received notice or access prior to the Supplement Effective Date. Systems Software also shall include all such programs or programming developed and/or introduced after the Supplement Effective Date to the extent a Party has financial or operational responsibility for such programs or programming under the applicable Supplement.
“Tax Authority” means any federal, state, provincial, regional, territorial, local or other fiscal, revenue, customers or excise authority, body or official competent to impose, collect or asses tax.
“Technology and Business Process Evolution” means any improvement, upgrade, addition, modification, replacement, or enhancement to the standards, policies, practices, processes, procedures, methods, controls, scripts, product information, technologies, architectures, standards, Applications, Equipment, Software, Systems, tools, products, transport systems, interfaces and personnel skills associated with the performance of the in-scope business process products and services in line with the ***. Supplier's obligations with respect to Technology and Business Process Evolution apply not only to the ***, but also to its *** performed by or for CoreLogic ***. Technology and Business Process Evolution includes: (i) higher capacity, further scaling and commercializing of business processes, more efficient and scalable business processes, new versions and types of applications and systems/network software, new business or IT processes, and new types of hardware and communications equipment that will enable Supplier to perform the Services more efficiently and effectively as well as *** to meet and support their *** and (ii) any change to the Equipment, Software or methodologies used to provide the Services that is necessary to bring that function, Equipment or Software or those methodologies into line with the *** and/or current ***.
“Technology and Business Process Plan” has the meaning given in Section 9.5(c).
“Term” has the meaning given in Section 1.2(b).
“Termination Charge” means the termination charges specified in the applicable Supplement.
“Third Party Contractor” has the meaning given in Section 4.5(a).
“Third Party Contracts” means all agreements between third parties and an Eligible Recipient or between third parties and Supplier (or Subcontractors or Affiliates of Supplier) that have been or will be used in connection with the provision of the Services to the extent a Party is financially or operationally responsible for the same under a Supplement.
“Third Party Materials” means intellectual property or other Materials that are owned by third parties and provided under license to Supplier (or Supplier Affiliates or Subcontractors) or an Eligible Recipient and that have been or will be used or required to be used in connection with the provision of, or receipt of us of, the Services to the extent a Party is financially or operationally responsible for the same under a Supplement. Third Party Materials include Materials owned by Subcontractors and used in the performance of the Services.
“Third Party Software” means all Software products (and all modifications, replacements, Upgrades, enhancements, documentation, materials and media related thereto) that are provided under a Third Party Contract (e.g., a license or lease) to Supplier (or Supplier Affiliates or Subcontractors) or an Eligible Recipient and that have been or will be used or required to be used in connection with the provision of, or receipt of us of, the Services to the extent a Party is financially or operationally responsible for the same under a Supplement. Third Party Software shall include all such programs or programming in use as of the Supplement Effective Date, including those (i) that are identified as such in such Supplement, (ii) for which the acquisition, license, maintenance or support costs are included in the CoreLogic Base Case, if any, or (iii) as to which Supplier received notice or access prior to the Supplement Effective Date. Third
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 11 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Party Software also shall include all such programs or programming licensed and/or leased after the Supplement Effective Date.
“Transformation” or “Transformation Services” has the meaning given in Section 4.8(a).“Transformation Milestone” has the meaning given in Section 4.8(b).
“Transformation Plan” has the meaning given in Section 4.8(a).
“Transition Milestone” has the meaning given in Section 4.2(c).
“Transition Period” means the period that commences on the Supplement Effective Date and expires 12:00:01 a.m., Eastern Time, on the date specified for the completion of the Transition Services as specified in the Transition Plan, unless expressly extended in writing by CoreLogic.
“Transition Plan” has the meaning given in Section 4.2(a).
“Transition Services” has the meaning given in Section 4.2(a).
“Transitioned Employee” means an employee of an Eligible Recipient who accepts Supplier's offer of employment and becomes employed by Supplier pursuant to the terms of Schedule 5 and the applicable Supplement. Upon being employed by Supplier, such Transitioned Employee shall be deemed to be a Supplier Personnel.
“UCITA” has the meaning given in Section 19.4.
“Upgrade” and its derivatives means updates, renovations, enhancements, additions and/or new versions or releases of Software or Equipment. Unless otherwise agreed, financial responsibility for the costs, fees and expenses associated with an Upgrade of Software or Equipment shall be allocated between the Parties in accordance with Section 6.5 or as set forth in the applicable Supplement.
“Warranty Period” has the meaning given in Section 15.2(c).
“Work Order(s)” has the meaning given in Section 1.1(b).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 1 | Page 12 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULES 2 THROUGH 5
SEE SCHEDULES IN EACH APPLICABLE SUPPLEMENT
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULE 6
GOVERNANCE
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule 6
Governance
| |
| 1.1 | Agreement. This Schedule 6 (this “Schedule”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
| |
| 1.4 | Schedules. The following Schedules are incorporated by reference into this Schedule 6: |
Schedule 6.1 Change Management Procedures
| |
| 2.1 | Governance Objectives. The Parties agree that this governance operating model is intended to achieve the following objectives: |
| |
| (a) | To ensure that there are clear executive level obligations, roles, and responsibilities for CoreLogic and Supplier; |
| |
| (b) | To ensure the alignment of CoreLogic's strategic business objectives and business units with the direction of the Services; |
| |
| (c) | To understand CoreLogic’s on-going and evolving business requirements, and issues that may affect the Services, including requirements relating to CoreLogic’s IT architecture, standards, or strategic direction; |
| |
| (d) | To monitor and oversee the performance of the Services; |
| |
| (e) | To drive early identification and resolution of performance issues; |
| |
| (f) | To define the escalation path for issue resolution; |
| |
| (g) | To establish and document required procedures and processes; |
| |
| (h) | To oversee the integration of CoreLogic and Supplier processes; |
| |
| (i) | To develop, monitor and maintain integrated processes such as Project Management, Change Management and Quality Assurance; and |
| |
| (j) | To identify, plan for and control changes to the Services and CoreLogic’s IT environment and ensure that they are implemented in a way that minimizes disruption to CoreLogic’s business operations or the performance of the Services. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6 | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 2.2 | Governance Plan. Within *** (***) *** after the Supplement Effective Date, Supplier shall provide a plan (the “Governance Plan”) to CoreLogic that establishes appropriate communication, management, and interface processes that support the governance organizations between the Parties and any applicable third parties, including CoreLogic’s Third Party Contractors, and that identifies CoreLogic Personnel (designated by CoreLogic) that are authorized to give approvals of various activities under the Agreement (e.g., those authorized to approve Projects). CoreLogic shall have at least *** (***) *** to review such plan and provide comments to Supplier. Supplier shall incorporate any modifications, additions, or deletions to such plan reasonably requested by CoreLogic within *** (***) *** of receiving them from CoreLogic. The Parties shall reasonably cooperate to permit completion of the detailed Governance Plan within *** (***) *** after the Supplement Effective Date unless another period is agreed upon by the Parties. |
| |
| 2.3 | Meetings. Supplier shall be responsible for establishing, coordinating, and leading the meetings described in this Schedule, which shall include producing materials and presentations and taking and distributing minutes, such minutes to be subject to CoreLogic approval. All meetings shall be in person at CoreLogic’s headquarters, unless it is agreed by the parties to meet at other such location or by remote communication. |
| |
| 3.1 | General. The Parties will cause the following committees to be formed in furtherance of the Parties’ governance activities under the Agreement. Each such committee will have both CoreLogic and Supplier representatives as members. No committee will perform any responsibilities or take any action unless a representative from each of the Parties is present and participating. Either Party may, from time to time, recommend adding or removing governance committees. |
| |
| 3.2 | Executive Steering Committee. The Executive Steering Committee shall provide strategic direction with respect to the overall relationship of CoreLogic and Supplier under the Agreement. |
| |
| (a) | Membership. The Executive Steering Committee shall consist of the following executives from CoreLogic and Supplier as indicated below: |
|
| |
| Executive Steering Committee |
| CoreLogic | Supplier |
| *** | |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | |
| |
| (b) | Responsibilities. The Executive Steering Committee shall: |
| |
| (i) | oversee that the goals and expectations of the Parties are in alignment; |
| |
| (ii) | provide executive commitment on behalf of CoreLogic and Supplier; |
| |
| (iii) | periodically review the authority of and recommend changes to the governance committees hereunder and the membership thereof; |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6 | Page 3 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (iv) | participate in an annual review of the relationship of the Parties, including customer and service satisfaction, quality of the relationship and assessments of the general performance, financial performance, and performance of the Services as against the Service Levels and other requirements of the Agreement; |
| |
| (v) | review progress of the Transition Services and Transformation Services activities; |
| |
| (vi) | review trends, issues, and common interests among the CoreLogic business units; |
| |
| (vii) | assign and review operational responsibilities to the Operational Governance Committee and others within CoreLogic and Supplier; |
| |
| (viii) | review Demand Forecast; |
| |
| (ix) | review strategic projects and innovation opportunities; |
| |
| (x) | review divestiture, mergers and acquisition plans, if any; |
| |
| (xi) | discuss CoreLogic strategy as it relates to the Services; |
| |
| (xii) | address and resolve (to the extent reasonably possible) disputes escalated to it; |
| |
| (xiii) | annually review CoreLogic and Supplier business and strategy; |
| |
| (xiv) | review progress of Supplier-sponsored initiatives; and |
| |
| (xv) | track CoreLogic’s overall progress towards business case goals. |
| |
| (c) | Meetings. The Executive Steering Committee will conduct its first meeting on or about *** (***) *** after CoreLogic approval of the Governance Plan, subject to the availability of the committee members. Thereafter, the Executive Steering Committee shall meet at least once every ***(***) ***(***) *** after CoreLogic approval of the Governance Plan and *** thereafter, provided that either Party may call a meeting of the Executive Steering Committee no earlier than upon *** (***) *** notice. |
| |
| 3.3 | Operational Governance Committee. The Operational Governance Committee and the members thereof shall act as the primary liaison between CoreLogic and Supplier for the management of the day-to-day performance of the Services and shall provide oversight for the Services and serve as the initial escalation point for disputes between the Parties. |
| |
| (a) | Membership. The Operational Governance Committee shall consist of the following participants from CoreLogic and Supplier as indicated below: |
|
| |
| Operational Governance Committee |
| CoreLogic | Supplier |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6 | Page 4 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (b) | Responsibilities. The Operational Governance Committee shall: |
| |
| (i) | function as a contact point with the Executive Steering Committee and implement directions from the Executive Steering Committee; |
| |
| (ii) | work to resolve operational issues and disputes escalated to it and to escalate issues and disputes, where appropriate, to the Executive Steering Committee; |
| |
| (iii) | review the monthly performance of the Services as against the Service Levels and other requirements of the Agreement; |
| |
| (iv) | establish enterprise Service Level remediation plans to correct Service delivery deficiencies, combining regional remediation plans if required; |
| |
| (v) | Review status and progress of enterprise Service Level remediation plans; |
| |
| (vi) | review Supplier’s performance of Projects against the applicable performance metrics; |
| |
| (vii) | review the status of Change Orders; |
| |
| (viii) | identify risks and opportunities for improvement in the performance of the Services; |
| |
| (ix) | review Demand Management forecasts; |
| |
| (x) | review results and action plans; |
| |
| (xi) | review global security issues; and |
| |
| (xii) | review the monthly billing reports. |
| |
| (c) | Meetings. The Operational Governance Committee shall conduct its first meeting within *** (***) *** of the Supplement Effective Date; thereafter, the Operational Governance Committee meetings will be held at least ***. |
| |
| 3.4 | Finance Governance Committee. The Finance Governance Committee shall provide financial direction with respect to the overall relationship of CoreLogic and Supplier pursuant to the Agreement and shall serve as the focal point of formal escalation for all financial disputes between the Parties. The Financial Governance Committee establishes and maintains the framework for oversight of all financial activities related to the Agreement and the delivery of Services. |
| |
| (a) | Membership. The Finance Governance Committee shall consist of the following executives from CoreLogic and Supplier as indicated below: |
|
| |
| Finance Governance Committee |
| CoreLogic | Supplier |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| |
| (b) | Responsibilities. The Finance Governance Committee shall: |
| |
| (i) | build financial processes and controls across all aspects of the outsourcing arrangement; |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6 | Page 5 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (ii) | monitor and manage the Charges in connection with each Service areas; |
| |
| (iii) | assist in and supporting, as needed, the review of monthly Charges to assure the accuracy of the Charges, CoreLogic retained costs, and Administered Expenses; |
| |
| (iv) | investigate variances in forecasted expenses or usage; |
| |
| (v) | define and maintain allocation, chargeback, currency, and tax consolidation framework; |
| |
| (vi) | review Asset Management and Software licenses utilization and exchange information necessary to monitor license compliance; |
| |
| (vii) | review general alignment with current version of financial responsibility matrix; |
| |
| (viii) | assist with the development of service catalogs, cost pools, and unit costs; and |
| |
| (ix) | analyze financial reports. |
| |
| (c) | Meetings. The Finance Governance Committee will conduct its first meeting on or about *** (***) *** following the Supplement Effective Date, subject to the committee member’s availability. During the course of the Transition Period, the Finance Committee shall meet at least ***; thereafter, the Finance Governance Committee shall meet at least ***. |
| |
| 3.5 | Technical and Architecture Steering Committee. The Technical and Architecture Steering Committee will focus primarily on the development of the Technology and Business Process Plan which includes identifying technologies, processes, and emerging trends related to the Services. The Technical and Architecture Steering Committee shall not be involved in day-to-day operational issues, but instead shall address long-term issues involving planning, strategy, and technical steering. |
|
| |
| Technical and Architecture Steering Committee |
| CoreLogic | Supplier |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| | *** |
| |
| (a) | Responsibilities. The Technical and Architecture Steering Committee shall: |
| |
| (i) | develop and recommend infrastructure technical and architecture solutions; |
| |
| (ii) | review CoreLogic Technology and Business Development Plans and requested by CoreLogic; and |
| |
| (iii) | suggest and develop technology and innovation solutions in partnership with CoreLogic business units. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6 | Page 6 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (b) | Meetings. The Technical and Architecture Steering Committee shall conduct their first local meetings within three (3) months of the Supplement Effective Date; thereafter, the Technical and Architecture Steering Committee shall meet at least on a *** basis during the first year after the Supplement Effective Date and at least *** thereafter, or at other times as agreed between the Parties. |
| |
| 3.6 | Project Office Steering Committee. The Project Office Steering Committee will manage the delivery of Projects for CoreLogic business units. The Project Office Steering Committee will also monitor Supplier programs and financial performance and provide assistance in reviewing and resolving program-level issues. |
|
| |
| Project Office Steering Committee |
| CoreLogic | Supplier |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| | *** |
| |
| (b) | Responsibilities. The Project Office Steering Committee shall ensure an efficient Project service delivery model through consistent and repeatable process and disciplines, and shall also include the following: |
| |
| (i) | Project governance & methodology; |
| |
| (ii) | Introduce economies of scale (best practices); |
| |
| (iii) | stakeholder communication; |
| |
| (v) | business case benefit tracking; |
| |
| (vi) | Project monitoring & reporting; |
| |
| (vii) | documentation standards & repository; |
| |
| (viii) | demand planning; and |
| |
| (c) | Meetings. The Project Office Steering Committee shall conduct their first local meetings on or about *** (***) *** following the Supplement Effective Date; thereafter, the Project Office Steering Committee shall meet at least *** during the Transformation Period, or as otherwise agreed between the Parties. |
| |
| 3.7 | Information Security Steering Committee. The Information Security Steering Committee will manage implementation of the data security program and associated information security policies and procedures, completion of remediation actions and responses to Security Incidents and audits. Among other thing, the Information Security Steering Committee will provide direction on changes to the Services required by changes to the Information Security Policy Set, Compliance Policy Set, and any other CoreLogic Rules and CoreLogic Standards. The Information Security Steering Committee attendees will include business unit representatives. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6 | Page 7 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| Information Security Steering Committee |
| CoreLogic | Supplier |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| |
| (b) | Meetings and Responsibilities. The Information Security Steering Committee shall conduct its first meetings within thirty (30) days of the Supplement Effective Date; thereafter, the Information Security Committees shall meet as follows: |
| |
| (i) | on *** basis to monitor the monthly performance responsibilities described above for the business unit; and |
| |
| (ii) | on *** basis, the committee will conduct an in-person workshop, led by the supplier, and which will include topics such as a review of the overall security program under the Agreement, a review of SSAE16 scope and control objectives, overall Supplier compliance status, and Policy and Procedures Manual review and updates. |
CoreLogic’s IT Governance Steering Committee shall conduct a meeting on dates set by ***, and *** shall provide *** with at least five (5) business days’ notice prior to any meeting of CoreLogic’s IT Governance Steering Committee and *** the *** of his choosing to *** such meeting.
4.1 Overview. If either Party identifies a dispute or disagreement between the Parties arising out of or related to the Agreement (each, a “Dispute”), the Parties shall comply with the informal dispute resolution procedures described in Section 4.2 (the “Informal Dispute Resolution Procedures”) to seek to resolve such Dispute.
4.2 Informal Dispute Resolution Procedures. The Informal Dispute Resolution Procedures are as follows:
| |
| (a) | Notification: To commence the Informal Dispute Resolution Procedures, either Party may escalate a Dispute by providing written notice to the member(s) of the lowest practical management level of the other Party currently involved in such Dispute. Upon receipt of such notice by the other Party, the Supplier and CoreLogic representatives currently engaged in attempting to resolve such Dispute shall meet to negotiate in good faith a resolution of such Dispute prior to escalating (as further described in Section 4.2(a)(i) below). Supplier and CoreLogic will meet within *** (***) *** after receipt of such notice. If the Parties are unable to resolve such Dispute within *** (***) *** of such meeting, either Party may escalate such Dispute in accordance with the following steps: |
| |
| (i) | The Party escalating the Dispute shall escalate to the next level of management as follows by providing notice to the other Party: |
| |
| (A) | First, to the applicable committee described in Sections 3.3 through 3.7 designated by the Party escalating the Dispute. |
| |
| (B) | If (1) after meeting in accordance with Section 4.2(a)(iii), either Party determines that such escalation above is unsuccessful in resolving the Dispute or (2) the |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6 | Page 8 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
applicable committee under Section 4.2(a)(i)(A) is unable to meet within *** (***) *** of the notice provided in accordance with Section 4.2(a)(ii), unless otherwise agreed, then to the appropriate Supplier governance team member designated by Supplier and appropriate CoreLogic governance team member designated by CoreLogic.
| |
| (C) | If (1) after meeting in accordance with Section 4.2(a)(iii), either Party determines that such escalation above is unsuccessful in resolving the Dispute, or (2) the team members are unable to meet within *** (***) *** of the notice provided in accordance with Section 4.2(a)(ii), unless otherwise agreed, then to the CoreLogic Chief Information Officer and Customer Executive. |
| |
| (D) | If (1) after meeting in accordance with Section 4.2(a)(iii), either Party determines that such escalation above is unsuccessful in resolving the Dispute or (2) the CoreLogic Chief Information Officer and Customer Executive are unable to meet within *** (***) *** of the notice provided in accordance with Section 4.2(a)(ii) unless otherwise agreed, then to the CoreLogic *** and ***. |
| |
| (E) | If (1) after meeting in accordance with Section 4.2(a)(iii), either Party determines that such escalation above is unsuccessful in resolving the Dispute or (2) the CoreLogic *** and *** are unable to meet within ten (10) days of the notice provided in accordance with Section 4.2(a)(ii), unless otherwise agreed, then to the Executive Steering Committee. |
| |
| (ii) | Documentation: Prior to any escalation described in Section 4.2(a)(i), the Party escalating will first provide written notice of such escalation to the other Party. The Parties will then jointly develop a short briefing document called a “Statement of Issue for Escalation” that describes the Dispute, relevant expected impact and positions of both Parties. |
| |
| (iii) | Meeting: During any escalation described in Section 4.2(a)(i), the Parties will meet (via phone or videoconference in most cases) with appropriate individuals as described above and will negotiate in good faith to resolve the Dispute. Such meeting shall occur within *** (***) *** of the notice provided in accordance with Section 4.2(a)(ii) or such other period agreed to by the Parties. The Statement of Issue for Escalation will be sent in advance to the participants attending such meeting. During such meeting, the Parties will negotiate in good faith to resolve such Dispute. |
| |
| (iv) | Dispute Review: If after the Informal Dispute Resolution Procedures (including all escalations described in Section 4.2(a)(i)), either Party believes that resolution is not possible without further escalation, either Party may seek to resolve such Dispute as described in Section 4.4 below. |
4.3 Expedited Dispute Resolution Process. Notwithstanding Section 4.2 above, either Party, on a good faith basis, may designate a Dispute as one requiring expedited resolution. A Dispute may be expedited if the Dispute involves a *** or arises under Section *** of the MSA. In such case, a Party may require, upon written notice to the other Party, that the Dispute be escalated directly to the *** and *** , in which case the Parties will promptly meet and attempt, in good faith, to resolve the Dispute as soon as practicable but not later than *** (***) *** after such notice requiring such escalation.
4.4 Formal Dispute Resolution Procedures. Notwithstanding the foregoing, this Section 4 shall not alter or limit either Party’s right to (a) seek injunctive or other equitable relief as provided in Sections 19.2 and 19.5 of the MSA or (b) seek to resolve a Dispute through litigation and in accordance with Article 19 of the MSA in the event that the Dispute has not been resolved by the Parties within *** (***) *** after the Dispute was initially escalated
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6 | Page 9 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
by the Parties under Section 4.2(a)(i) or *** (***) *** after the Dispute was initially escalated by the Parties under Section 4.3.
4.5 Confidentiality. All meetings of the Informal Dispute Resolution Procedures shall at all times be privately conducted. The Parties agree that the Statement of Issues for Escalation and all information, materials, statements, conduct, communications, negotiations, offers of settlement, documents of either Party, in whatever form and however disclosed or obtained in connection with the Informal Dispute Resolution Procedures (collectively, “Informal Dispute Resolution Information”) (a) shall be Confidential Information of the preparing Party, (b) shall not be offered into evidence, disclosed, or used for any purpose other than the Informal Dispute Resolution Procedures; and (c) will not constitute an admission or waiver of rights; provided, however, that the foregoing shall not prohibit the underlying facts supporting such Informal Dispute Resolution Information from being subject to discovery.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6 | Page 10 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULE 6.1
CHANGE MANAGEMENT PROCEDURES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule 6.1
Change Management Procedures
| |
| 1.1 | Agreement. This Schedule 6.1 (this “Schedule”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
2.1 General.
This Section describes the Change Management Procedures to be used for the Parties to make changes to the existing scope of Services, including changes to *** or a Project’s scope. Such procedures shall be further described in the Policy and Procedures Manual. These procedures will be managed by the Operational Governance Committee.
2.2 Change Management Procedures Requirements.
| |
| (a) | The key steps in the Change Management Procedures include: |
| |
| (i) | reviewing each Change Order (as defined below) to determine whether a proposed Services change is appropriate; |
| |
| (ii) | preparing a more detailed proposal to implement a Change Order; |
| |
| (iii) | prioritizing and reprioritizing Change Orders; and |
| |
| (iv) | tracking and monitoring Change Orders. |
| |
| (b) | No Change Order shall be implemented without the Parties’ prior written approval. |
| |
| (c) | Each Party will be responsible for all costs incurred by it in the preparation, investigation, and approval of Change Orders. |
| |
| (d) | Either Party may initiate a Services change request by delivering to the other Party’s designee a Services change request that describes the proposed Services change and sets forth the basis for such change (each, a “Change Order”). Supplier shall assign a unique number to any such request and shall register the Change Order in the Change Order Log as described below. |
| |
| (e) | Each Party’s designee shall be responsible for reviewing and considering any Change Order, and shall approve it for further investigation, if deemed necessary. If the Parties agree that the Change Order requires further investigation, Supplier shall perform such investigation as requested by CoreLogic. Supplier shall be responsible for updating the status of each Change Order to keep its status current in the Change Order Log as the Change Order progresses through the Change Management Procedures. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6.1 | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
2.3 Change Orders.
Subject in all cases to the *** and Section *** of the Agreement:
| |
| (a) | For each Change Order that the Parties have approved for further investigation, Supplier shall prepare and submit to CoreLogic *** *** (***) *** (or other period as reasonably approved by CoreLogic), with CoreLogic’s reasonable cooperation and provision of information reasonably requested by Supplier, a preliminary specification report (a “Preliminary Specification Report”). Each such Preliminary Specification Report shall contain, to the extent relevant: |
| |
| (i) | description of the change and the anticipated impact on the organization and Services; |
| |
| (ii) | estimated changes in the Charges, if any, associated with the proposed Change Order; |
| |
| (iii) | estimates of any applicable increases and decreases in existing baselines and additional baselines; |
| |
| (iv) | estimated timeframes for implementing the proposed Services change (including any timing constraints); and |
| |
| (v) | an initial analysis of the potential benefits and risks (if any) if the proposed Change Order is or is not implemented. |
| |
| (b) | With respect to all Change Orders, Supplier shall: (a) schedule implementation of such Change Orders so as not to ***; (b) prepare and deliver to CoreLogic *** during the Term a rolling schedule for on-going and planned implementation of Change Orders for the next *** period; and (c) monitor the status of Change Orders against such *** rolling schedule. |
2.4 Preliminary Specification Report Review.
| |
| (a) | CoreLogic and Supplier shall review the Preliminary Specification Report, and CoreLogic shall, within *** (***) *** after delivery of such Preliminary Specification Report in writing, either: |
| |
| (i) | *** Supplier to prepare a Detailed Specification Report (as defined below); and |
| |
| (ii) | notify Supplier that it does not wish to proceed with the proposed Change Order. |
| |
| (b) | Where CoreLogic *** Supplier to prepare a Detailed Specification Report, within thirty (30) days (or as otherwise agreed) after receiving such instruction, Supplier shall prepare and submit a detailed specification report (a “Detailed Specification Report”) including a comprehensive assessment of its ramifications and impact on the following elements of the Agreement, to the extent relevant: |
| |
| (i) | the then-current Services; |
| |
| (ii) | the Service Levels; if applicable, including increases and decreases in existing baselines and additional baselines; |
| |
| (iii) | changes to the Charges, if any; |
| |
| (iv) | any other *** other than ***; |
| |
| (v) | the resources (including human resources, hardware, Software and other Equipment) required for implementing the Change Order; |
| |
| (vi) | timeline, milestones, delivery dates, and consequences for not implementing the Change Order; |
| |
| (vii) | acceptance testing period and Acceptance criteria (which must be included in the final Change Order); |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6.1 | Page 3 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (viii) | any Third Party Contracts, including additions or deletions; |
| |
| (ix) | CoreLogic’s, Supplier’s or any third party’s software, hardware, systems, business operations, personnel requirements or other Services; |
| |
| (x) | any related technical or human resource procedures; |
| |
| (xii) | Disengagement Services; |
| |
| (xiii) | any additional contractual terms and conditions which would apply to the Change Order, and/or any changes required to the contractual terms and conditions of the Agreement which, subject to Sections 21.2 of the MSA, shall be handled in accordance with those procedures; |
| |
| (xiv) | an analysis of the potential benefits and risks (if any) to CoreLogic or Supplier if the Change Order is not implemented; and |
| |
| (xv) | any other matter reasonably requested by CoreLogic or reasonably considered by Supplier to be relevant to the evaluation of the Change. |
2.5 Detailed Specification Report Review.
Once submitted by Supplier, CoreLogic shall review the Detailed Specification Report and, as soon as reasonably practicable, and in any event not more than *** (***) *** (or as otherwise agreed) after receipt of the Detailed Specification Report:
| |
| (a) | the Parties may approve the Detailed Specification Report, and the approved change shall be incorporated into the Agreement in accordance with Section 2.7 below; |
| |
| (b) | CoreLogic may notify Supplier that it does not wish to proceed with the proposed Change Order, in which case no further action shall be taken in respect of the Detailed Specification Report; |
| |
| (c) | the Parties may acquire further information before deciding whether to proceed with the Change Order; or |
| |
| (d) | the Parties may amend some or all of the contents of the Detailed Specification Report, which Supplier shall incorporate into a revised version of the Change Order. |
2.6 Fees for Changes. Supplier agrees that any increase to the Charges with regard to any contemplated Change Order shall be based on Supplier’s net increased costs or expenses in connection with such Change Order.
2.7 Effectiveness of a Change.
| |
| (a) | Upon the written approval of the Parties of the Change Order and the Detailed Specification Report and subject to Section 21.2 of the MSA, the contents of such approved Change Order shall be deemed to be agreed and incorporated into the Agreement on the date of the last signature or as the Parties may otherwise agree. All services added or modified by a Change Order shall be “Services” under the Agreement, and the performance of Change Orders shall in all respects be governed by the Agreement. No part of the discussions or interchanges between the Parties shall obligate the Parties to approve any proposed Change Order or shall be binding on the Parties until reflected in an approved Change Order and adopted. |
| |
| (b) | ***, neither Party shall have any obligation to commence or comply with any proposed Change Order, perform services that would be covered by any proposed Change Order, or pay any fees that would be covered by any proposed Change Order, until such time as the Parties’ designees have approved the appropriate Change Order in writing. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6.1 | Page 4 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
2.8 Change Management Reporting Requirements. Supplier shall provide CoreLogic, as part of the monthly Reports set forth in Schedule A-12, a summary specifying the status of all pending Change Orders.
2.9 Change Order Log.
| |
| (a) | Supplier shall maintain a change order log of Change Orders throughout the Term (“Change Order Log”). The Change Order Log shall include the following level of detail: |
| |
| (i) | control number and date of the Change Order; |
| |
| (ii) | name of the Party requesting the Change Order; |
| |
| (iii) | brief description of the Change Order; and |
| |
| (iv) | current status of the Change Order. |
| |
| (b) | The status of the Change Order in the Change Management Procedures shall be categorized as one of the following stages: |
| |
| (i) | “Open” (i.e., the Change Order has been created and registered); |
| |
| (ii) | “In Review” (i.e., the Change Order has been created and is being reviewed pending approval to proceed); |
| |
| (iii) | “Approved” (i.e., the Change Order has been approved and is awaiting implementation); |
| |
| (iv) | “On Hold” (i.e., the Parties wish to suspend implementation of the change but anticipate the change being implemented at a later date); |
| |
| (v) | “Closed” (i.e., all implementation tasks have been completed and the change has been implemented); or |
| |
| (vi) | “Rejected” (i.e., closed and not implemented). |
2.10 Specified *** Changes. Where the Agreement expressly provides *** with the *** that may result in a Change (including, e.g., changes to the *** or changes to ***), the Parties shall use the foregoing provisions of this Section 2 to document and implement the resulting Change , but the *** and *** shall comply with the resulting Change as approved by *** pursuant to Section 2; provided that nothing in this Section 2.10 is intended to modify or limit *** in the Agreement including under Section *** of the MSA.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 6.1 | Page 5 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULE 7
SEE EACH SUPPLEMENT FOR APPLICABLE FACILITIES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULE 8
RULES, PROCEDURES AND POLICIES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
Schedule 8
Rules, Procedures and Policies
1.INTRODUCTION
| |
| 1.1 | Agreement. This Schedule 8 (this “Schedule”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
2. RULES, PROCEDURES AND POLICIES
The CoreLogic Rules and CoreLogic Policy Sets as of the Effective Date consist of the following policies and procedures set forth in this Section 2.
| |
| (a) | The “Information Security Policy Set” shall include the then-current versions of the following documents. |
Policy 1 – Information Security Organization
Policy 2 – Classifying and Handling Information
Policy 3 – Securing and Accessing Systems
Policy 4 – Personnel and Facilities
Policy 5 – Detecting and Responding to Incidents
Policy 6 – Secure Application Development
Policy 7 – Planning for Business Continuity
Policy 8 – Information Privacy
Policy 9 – Password Management Policy
Policy 10 – Acceptable Use Policy
Application Vulnerability Assessment Standard
Change Management Standard
Information Security Standard
NIST Standard
PCI/EI3PA Standard
Sensitive Data Standard
Facilities Access Standard
Clean Desk Standard
| |
| (b) | The “Compliance Policy Set” shall include the then-current versions of the following documents. |
Vendor Risk Management Policy
Vendor Risk Management Standard
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 8 | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULE 9
INSURANCE REQUIREMENTS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule 9
Insurance Requirements
1.INTRODUCTION
| |
| 1.1 | Agreement. This Schedule 9 (this “Schedule”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
2. INSURANCE
2.1 Requirements. Supplier agrees to keep in full force and effect and maintain at its sole cost and expense the following policies of insurance with at least the specified minimum limits of liability during the term of this Agreement and during any period thereafter for which Supplier is providing Disengagement Services under the Agreement:
| |
| (a) | Workers’ Compensation and Employer’s Liability Insurance the limits of liability of Employer’s Liability Insurance with minimum limits of $*** per employee by accident / $*** per employee by disease / $*** policy limit by disease (or, if higher, the policy limits required by applicable Law). |
| |
| (b) | Commercial General Liability Insurance (including coverage for contractual liability, premises-operations, completed operations-products and independent contractors) providing coverage for bodily injury, personal and advertising injury and property damage with combined single limits of not less than $*** per occurrence. |
| |
| (c) | Commercial Business Automobile Liability Insurance including coverage for all owned, non-owned, leased, and hired vehicles providing coverage for bodily injury and property damage liability with combined single limits of not less than $*** per occurrence, except as may otherwise be required by applicable Law. |
| |
| (d) | Professional Liability (also known as Errors and Omissions Liability) and Cyber Risk Insurance covering acts, errors and omissions arising out of Supplier’s performance of Services in an amount not less than $*** per claim and in the annual aggregate. Policies shall include *** liability, ***, and *** (***) insurance providing protection against: (a) errors and omissions in the performance of professional services; (b) *** arising out of *** (excluding *** and ***); (c) ***; (d) *** any ***, ***; and (e) ***. The Professional Liability Insurance retroactive coverage date shall be no later than the Effective Date. Supplier shall maintain an extended reporting period providing that claims first made and reported to the insurance company within ***) *** after termination or expiration of this Agreement will be deemed to have been made during the policy period. Supplier’s professional liability insurance shall indemnify CoreLogic on a co-defendant basis for damages and claims expenses, including but not limited to legal fees, sustained by CoreLogic due to a lawsuit and/or claim brought by a third party against Supplier and CoreLogic to the extent such lawsuit and/or claim (i) arises or allegedly arises from the acts and omissions of Supplier in performing services under this Agreement; and (ii) triggers coverage for |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 9 | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Supplier as the named insured pursuant to the terms and conditions of the policy. Such indemnification shall not extend to damages and claims expenses that are wholly or partially attributable to CoreLogic’s own negligence or willful misconduct.
| |
| (e) | The coverages specified in subsections (a) through (d) of this Section 2.1 may be provided with a combination of primary and excess insurance policies. The policy limit for excess coverage shall be such that when added to the primary coverages, the combination of the policy limits shall be no less than $*** per occurrence. |
| |
| (f) | Comprehensive Crime Insurance or Blanket Fidelity Bond, including Employee Dishonesty and Computer Fraud Insurance covering losses arising out of or in connection with any fraudulent or dishonest acts committed by Supplier Personnel, acting alone or with others, in an amount not less than $*** per occurrence. |
2.2 Approved Companies. All such insurance shall be procured with reputable insurance companies and in such form as is usual and customary to Supplier’s business. Such insurance companies shall maintain a rating at least “***” and be at least a “financial size category ***” as both criteria are defined in the most current publication of Best’s Policyholder Guide.
2.3 Endorsements. Supplier’s insurance policies as required herein under Sections 2.1(b) and 2.1(c) shall name CoreLogic, its Affiliates and the Eligible Recipients and their respective officers, directors and employees as “additional insureds” for liability arising at any time in connection with Supplier’s or Supplier Personnel’s performance under this Agreement. The Supplier insurance policies required under Section 2.1(f) shall include CoreLogic, its Affiliates and the Eligible Recipients and their respective officers, directors and employees as “loss payees” for liability arising at any time in connection with Supplier’s or Supplier Personnel’s performance under this Agreement. Policies provided pursuant to Sections 2.1(a), 2.1(b) and 2.1(c) shall provide that the insurance companies waive all rights of subrogation against CoreLogic, the Eligible Recipients, and each of their respective officers, directors, and employees to the extent of Supplier’s indemnification obligations. With respect to matters pertaining to the Services or Supplier’s obligations under this Agreement, all insurance afforded to CoreLogic under this Schedule 9 shall be primary insurance, if applicable, and any other valid insurance existing for CoreLogic’s benefit shall be excess of such primary insurance and non-contributory with respect to any insurance or self-insurance maintained by CoreLogic or the Eligible Recipients. Supplier shall obtain such endorsements to its policy or policies of insurance as are necessary to cause the policy or policies to comply with the conditions stated herein.
2.4 Certificates. Prior to the Commencement Date and thereafter upon request by CoreLogic, Supplier shall provide CoreLogic with certificates of insurance evidencing Supplier’s compliance with this Schedule 9 (including certificates evidencing renewal of such insurance or new insurance policies) signed by authorized representatives of the respective carriers for each year that this Agreement is in effect.
2.5 No Implied Limitation. The obligation of Supplier and its Affiliates to provide the insurance specified herein shall not in any way alter or limit any obligation or liability of Supplier provided elsewhere in this Agreement. For the avoidance of doubt, any policy amounts or coverages shall not in any event be construed as limitations or expansions on Supplier’s liability under the Agreement.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 9 | Page 3 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING, L.P.
July 19, 2012
SCHEDULE 10
DIRECT CORELOGIC COMPETITORS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside either Party without the prior written permission of the other Party. |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule 10
Direct CoreLogic Competitors
| |
| 1.1 | Agreement. This Schedule 10 (this “Schedule”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and schedules shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
| |
| 2. | DIRECT CORELOGIC COMPETITORS |
| |
| 2.1 | The Direct CoreLogic Competitors are as follows: |
***
* The restriction on working for *** during the Restricted Period for purposes of Section 8.5(d) of the MSA shall only apply for Restricted Personnel who will work on the *** (but only to the extent relating to ***).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 10 | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULE 11
DIRECT SUPPLIER COMPETITORS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside either Party without the prior written permission of the other Party. |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule 11
Direct Supplier Competitors
| |
| 1.1 | Agreement. This Schedule 11 (this “Schedule”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and schedules shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
| |
| 2. | DIRECT SUPPLIER COMPETITORS |
| |
| 2.1 | The Direct Supplier Competitors are as follows: |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 11 | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
* If CoreLogic elects to use *** as a Permitted Auditor pursuant to Section 9.10(b) of the MSA in its capacity as an auditing or an *** entity, the restriction therein related to signing a non-disclosure agreement shall not apply.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 11 | Page 3 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULE 12
ADDITIONAL DATA SAFEGUARDING OBLIGATIONS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule 12
Additional Data Safeguarding Obligations
| |
| 1.1 | General. This Schedule 12 (this “Schedule”) is attached to and incorporated by reference to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
| |
| 2.1 | Supplier Controls. Supplier shall implement and maintain reasonable and appropriate information security controls to protect against the unauthorized access to or use of CoreLogic Data with respect to Supplier Systems that access, process, transmit or store CoreLogic Data and CoreLogic Systems for which Supplier has operational responsibility. Without limiting the generality of the foregoing, Supplier shall implement and maintain: (i) *** with respect to Supplier Systems that access, process, transmit or store CoreLogic Data and CoreLogic Systems for which Supplier has operational responsibility, including controls to *** to authorized officers, directors, employees, consultants, attorneys, accountants, agents and independent subcontractors (and their employees) and other representatives or other third parties who have a ***; (ii) access restrictions at physical locations with respect to Supplier Systems that access, process, transmit or store CoreLogic Data and CoreLogic Systems for which Supplier has operational responsibility containing CoreLogic Data, such as buildings, computer facilities, and records storage facilities to permit access only to authorized individuals in accordance with the CoreLogic Information Security Policy Set and any CoreLogic-approved waivers thereto;(iii) *** of electronic CoreLogic Data at levels at least as protective as CoreLogic has in place as of the Effective Date (including any waivers), as well as any other levels directed by CoreLogic pursuant to an applicable Supplement; (iv) procedures (including Change Management Procedures) designed to ensure that information System modifications with respect to Supplier Systems that access, process, transmit or store CoreLogic Data and CoreLogic Systems for which Supplier has operational responsibility are consistent with the information security controls contemplated by Section 13.2 and this Section 2 of Schedule 12; (v) *** and *** where required by the Policy Sets with respect to Supplier Systems that access, process, transmit or store CoreLogic Data and CoreLogic Systems for which Supplier has operational responsibility; (vi) *** and procedures to detect *** or *** Supplier Systems that access, process, transmit or store CoreLogic Data and CoreLogic Systems for which Supplier has operational responsibility; (vii) *** that specify *** when *** that access, process, transmit or store CoreLogic Data and CoreLogic Systems for which Supplier has operational responsibility, including reports to CoreLogic in accordance with the requirements of the ***; (viii) measures to protect against *** with respect to Supplier Systems that access, process, transmit or store CoreLogic Data and CoreLogic Systems for which Supplier has operational responsibility due to ***; and (ix) facilitate regular testing of key controls, Systems and procedures of the information security measures by independent third parties or staff independent of those that develop or maintain the security measures as required by Sections 9.10(h) (Facilities and Controls Audit), 9.17 (CoreLogic Customer Contracts Flow-down), 9.14 and 13.2(b). If, in the course of the performance of the Transition Services for an applicable Supplement, *** identifies any deficiency or gaps between the current information security controls implemented and maintained by *** with respect to the CoreLogic Systems for which Supplier has operational responsibility and the information security controls that Supplier is required to implement and maintain as set forth in clauses (i), (ii), (iii) or (viii) above, Supplier shall notify *** and *** shall *** to (a) eliminate such deficiency or gap with the reasonable assistance of Supplier, (b) require Supplier to eliminate such deficiency |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 12 | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
or gap, in which case CoreLogic shall be financially responsible for such elimination, or (c) establish a waiver with respect to such deficiency or gap.
| |
| 2.2 | ***. For all (A) Supplier Systems that access, transmit, process or store CoreLogic Data and (B) CoreLogic Systems for which Supplier has operational responsibility that access, transmit or store CoreLogic Data and allow for the ***, unless otherwise approved by CoreLogic or expressly waived by the CoreLogic Policy Sets, *** shall be in place to *** and *** associated Systems and to *** all attempted or executed ***. If, in the course of the performance of the Transition Services for an applicable Supplement, *** identifies any such CoreLogic Systems that allow for the *** but for which such *** is not *** (and for which a waiver from the CoreLogic Policy Sets has not been issued), *** shall notify *** and *** shall *** to (a) *** with the reasonable assistance of Supplier, (b) require Supplier to ***, in which case CoreLogic shall be financially responsible for such implementation, or (c) establish a waiver with respect to such ***. All Systems *** shall be *** for the applicable Systems (i.e., Supplier or CoreLogic). Reasonable processes shall be in place with respect to such *** to review *** to *** activity within ***. *** shall be secured in a manner to prevent ***, and accidental or deliberate ***. |
| |
| 2.3 | Remote Access. The authentication protocols and access methods used to access the CoreLogic Network while outside a Supplier-managed facility shall be as provided by *** and in accordance with ***. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 12 | Page 3 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULE 13
TERMINATION CHARGES PERCENTAGES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule 13
Termination Charges Percentages
1.INTRODUCTION
| |
| 1.1 | Agreement. This Schedule 13 (this “Schedule”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
“General Termination Charge” shall have the meaning given in the applicable Supplement.
“Unconditional Termination Charge” shall have the meaning given in the applicable Supplement.
“Wind Down Costs Termination Charge” shall have the meaning given in the applicable Supplement.
2. TERMINATION CHARGES PERCENTAGES
The table below sets forth the percentages for calculating Termination Charges under the applicable Supplement.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 13 | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| Section Number in the MSA | Reason for Termination | General Termination Charge Percentage | Unconditional Termination Charge Percentage | Wind Down Costs Termination Charge Percentage |
| 4.2(h) | Transition - Termination by CoreLogic | ***% | ***% | ***% |
| 4.8(h) | Transformation - Termination by CoreLogic | ***% | ***% | ***% |
| 9.10(h) | Facilities and Controls Audit - Termination by CoreLogic | ***% | ***% | ***% |
| 9.14(d) | Force Majeure - Termination by CoreLogic | ***% | ***% | ***% |
| *** | *** | ***% | ***% | ***% |
| 11.6(c) | Benchmarking - Termination by CoreLogic | ***% | ***% | ***% |
| 18.2(f) | Waiver of Liability Cap - Termination by Supplier | ***% | ***% | ***% |
| 18.2(f) | Waiver of Liability Cap - Termination by CoreLogic | ***% | ***% | ***% |
| 20.1(a) | Cause - Termination by CoreLogic | ***% | ***% | ***% |
| 20.1(b) | Cause - Termination by Supplier | ***% | ***% | ***% |
| 20.2 | Convenience - Termination by CoreLogic | ***% | ***% | ***% |
| 20.3 | Supplier Change of Control - Termination by CoreLogic for sale to *** | ***% | ***% | ***% |
| 20.3 | Supplier Change of Control -Termination by CoreLogic other than to *** | ***% | ***% | ***% |
| 20.4 | CoreLogic Change of Control | ***%
| ***%
| ***%
|
| 20.5 | Insolvency - Termination by CoreLogic | ***% | ***% | ***% |
| 20.5 | Insolvency - Termination by Supplier | ***% | ***% | ***% |
| 20.7 | *** - Termination by CoreLogic | ***% | ***% | ***% |
Nothing in this table is intended to limit any *** claim for damages based on any element of *** or ***.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 13 | Page 3 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULE 14
CORELOGIC-SPECIFIC FACILITY AND CONTROLS AUDITS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule 14
CoreLogic-Specific Facility and Controls Audits
1.INTRODUCTION
| |
| 1.1 | Agreement. This Schedule 14 (this “Schedule”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
2. DELL SSAE 16 APPROACH
2.1 Overview and Control Objectives.
CoreLogic will rely on the existing shared services Service Organization Controls 1 (SOC1) Type II reports under SSAE 16 of Dell’s technology centers utilized in the provisioning of services to CoreLogic, which are currently performed by Ernst & Young LLP (“E&Y”) and include Control Objectives for Physical Access and Physical Environment. The Dell SOC1 reports are limited in scope to the below listed Dell Shared Services SSAE 16 SOC1 Control Objectives for the general benefit of all Dell clients.
With respect to the remainder of the controls in the current CoreLogic SSAE 16 SOC1 report dated December 19, 2011 issued by PriceWaterhouseCoopers, which are listed below, plus the additional Control Objective planned for Change Management, Dell shall work with CoreLogic to design a set of compatible Control Objectives, document specific Controls to support those Control Objectives, and provide the necessary support to perform a “CoreLogic-Specific SSAE 16 Audit” that reasonably includes the Control Objectives as directed by CoreLogic to meet the needs of its financial auditors ***. Dell shall choose the accounting firm that performs the review, subject to the audit being performed by a firm of international repute.
2.2 Professional Fees
Audit firm fees for the existing shared services SOC1 reports are financial responsibilities of Dell. The audit firm fees for the CoreLogic-Specific SOC1 report shall be borne by ***. ***, Dell shall not *** *** for *** the CoreLogic-Specific SOC1 audit. The audit firm will be a firm of international repute.
2.3 Timing
CoreLogic acknowledges that Dell’s shared services SOC1 SSAE 16 audit periods commence on *** and conclude on *** of ***, with a *** provided to *** the ***. CoreLogic requires that the audit period for the Core-Logic Specific SOC1 report be *** of *** through *** of the ***.
2.4 Dell Shared Services SSAE 16 SOC1 Control Objectives include:
2.5 Current CoreLogic-Specific SSAE 16 Control Objectives include:
| |
| • | Computer Operations: Controls provide reasonable assurance that production systems and network issues are identified and corrective actions are addressed. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 14 | Page 2 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| • | Tape and Disk Management: Controls provide reasonable assurance that production system data is backed up on a regular basis and available for restoration in the event of processing errors or unexpected interruptions and procedures are in place to ensure media is appropriately protected upon disposal. |
| |
| • | Technical Support: Controls provide reasonable assurance that development of new network components or changes/upgrades to existing network components, production systems, and support tools are authorized, tested, properly implemented, and adequately documented. |
| |
| • | Logical Security - Network - Controls provide reasonable assurance that logical access to the network is restricted to properly authorized individuals. |
| |
| • | Logical Security - Controls provide reasonable assurance that logical access to Windows is restricted to properly authorized individuals. |
| |
| • | Logical Security: Controls provide reasonable assurance that logical access to Linux/Unix is restricted to properly authorized individuals. |
| |
| • | Logical Security: Controls provide reasonable assurance that logical access to the iSeries is restricted to properly authorized individuals. |
| |
| • | Logical Security: Controls provide reasonable assurance that logical access to the zSeries is restricted to properly authorized individuals. |
| |
| • | Data Transmissions: Controls provide reasonable assurance that data transmissions between the service organization and its user organizations are secure and occur in a controlled fashion. |
| |
| • | Change Management: Not included in the above referenced current CoreLogic SSAE 16 SOC1 report, dated December 19, 2011, issued by PriceWaterhouseCoopers to CoreLogic. Additional control objective statement, to be determined. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 14 | Page 3 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SCHEDULE 15
APPROVED BENCHMARKERS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule 15
Approved Benchmarkers
| |
| 1.1 | Agreement. This Schedule 15 (this “Schedule”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
The approved Benchmarkers are as follows:
***
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Schedule 15 | Page 2 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
ANNEX 1
FORM OF SUPPLEMENT
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
Annex 1
Form of Supplement
SUPPLEMENT [_] TO
MASTER SERVICES AGREEMENT
This Supplement [_] (this “Supplement”) is entered into effective [________], 20[__] (the “Supplement Effective Date”) by and between CoreLogic Solutions, LLC, a California limited liability corporation having a principle place of business in Santa Ana, California (“CoreLogic”), and Dell Marketing L.P., a Texas limited partnership having a principal place of business in Round Rock, Texas (“Supplier”) (collectively, the “Parties” and each, a “Party”).
This Supplement is entered into pursuant to and subject to that certain Master Services Agreement (“Master Services Agreement” or “MSA”) dated as of July 19, 2012, by and between the Parties, the terms of which, except as may be expressly modified or excluded herein, are incorporated herein by reference.
NOW THEREFORE, in consideration of the mutual promises contained herein, and of other good and valid consideration, the receipt and sufficiency of which is hereby acknowledged, the Parties hereby agree as follows:
1.INTRODUCTION.
1.1 Precedence of Obligations. The Parties acknowledge that certain obligations may be set forth in both this Schedule and elsewhere in the Agreement, and that in the event of a conflict, such conflict shall be resolved in accordance with Section 21.13 of the MSA.
1.2 References. All references in this Supplement [_] to articles, sections and attachments shall be to this Supplement, unless another reference is provided.
1.3 Associated Supplement Documents.
This Supplement includes each of the following Schedules, all of which are incorporated into this Supplement by this reference:
Schedule [_]-1 Definitions
Schedule [_]-2 Statement of Work
Schedule [_]-3 Service Level Methodology
Schedule [_]-4 Pricing Methodology
Schedule [_]-5 Human Resource Provisions
Schedule [_]-6 Governance
Schedule [_]-7 Facilities
Schedule [_]-8 Rules, Procedures and Policies
Schedule [_]-9 Additional Insurance Requirements
Schedule [_]-10 Transition Schedule
Schedule [_]-11 Customer Satisfaction Survey
Schedule [_]-12 Software and Equipment Inventory
Schedule [_]-13 Third Party Contracts
Schedule [_]-14 Reports
Schedule [_]-15 Disengagement Services
Schedule [_]-16 Third Party Materials
Schedule [_]-17 Disaster Recovery Plan Requirements
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 2 |
1.4 Definitions.
| |
| (a) | Schedule 1 to the MSA is hereby supplemented with the definitions set forth [in Schedule [_]-1 to this Supplement.] or [below:] |
| |
| (b) | The definitions added by this Supplement to Schedule 1 to the MSA shall apply only with respect to the Services provided under this Supplement. |
2. SERVICES.
Schedule 2 to the MSA is hereby supplemented [by Schedule [_]-2 to this Supplement.] or [as follows:]
| |
| 2.1 | Services. Supplier shall perform or cause to be performed the Services set forth [in Schedule [_]-2 to this Supplement during the Term of this Supplement.] or [below:] |
[This section should describe Supplier’s scope of responsibility for providing Services to CoreLogic – it should principally be a description of what Supplier will do, described in broad terms, in contrast to how Supplier will perform the Services. The terms of the MSA give CoreLogic control or approval rights over certain aspects of how Supplier performs the Services.]
2.2 Deliverables. Supplier shall complete the following Deliverables:
[List and describe Deliverables including target dates.]
| |
| 2.3 | CoreLogic Responsibilities. CoreLogic shall perform or cause to be performed the tasks, functions and responsibilities of CoreLogic as set forth in Schedule [_]-2 to this Supplement during the Term of this Supplement.] or [below:] |
[Describe CoreLogic responsibilities.]
3. SERVICE LEVELS.
Schedule 3 to the MSA is hereby supplemented [by Schedule [_]-3 to this Supplement.] or [as follows:]
Supplier shall provide the Services so as to meet or exceed the Service Levels identified [in Schedule [_]-3 to this Supplement.] or [below:]
[This Schedule describes the methodology for establishing service levels and calculating service level credits, as well as the specific service level metrics that Supplier must meet in providing the Services.]
4. PRICING AND FINANCIAL PROVISIONS.
| |
| 4.1 | Charges. Schedule 4 to the MSA is hereby supplemented [by Schedule [_]-4 to this Supplement.] or [as follows:] |
The Charges for this Supplement are set forth [in Schedule [_]-4 to this Supplement.] or [below:]
[Note: This should include the following: Any minimum commitment, ARC/RRCs, Termination Charges, and any additional applicable pricing-related Schedules (e.g., financial responsibilities matrix). Specify if a Base Case applies to the Supplement.]
4.2 Prepaid Items. Section 11.5(a) of the MSA shall not apply with respect to this Supplement.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 3 |
[Note: Delete this Section 4.2 if Section 11.5(a) of the MSA (regarding refunds of amounts paid by CoreLogic under its contracts) will apply.]
5. HUMAN RESOURCES PROVISIONS.
Schedule 5 to the MSA is hereby supplemented [by Schedule [_]-5 to this Supplement.] or [as follows:]
5.1 Key Supplier Personnel.
In accordance with Section 8.2 of the MSA, the following positions are Key Supplier Personnel positions under this Supplement and, to the extent applicable, an individual listed for a position is approved by CoreLogic to hold such position as of the Supplement Effective Date:
[This section identifies the Key Supplier Personnel positions, as well as the persons initially filling those positions, if known at signing. The Key Supplier Personnel are typically personnel who occupy strategically important positions in Supplier’s account team. Supplier must retain these individuals for the level specified in the “Level of Effort” column for the time specified in the “Committed Period” column.]
|
| | | |
| Key Supplier Personnel Position | Individual Approved for Position | Level of Effort | Committed Period |
| [Supplier Account Manager] | | [Full Time] | [24 Months] |
| | | | |
| | | | |
| | | | |
| | | | |
5.2 Knowledge Transfer Personnel.
In accordance with Section 8.2(c) of the MSA, the following positions are Knowledge Transfer Personnel positions under this Supplement and, to the extent applicable, an individual listed for a position is approved by CoreLogic to hold such position as of the Supplement Effective Date:
|
| | |
| Knowledge Transfer Personnel Position | Individual Approved for Position | Committed Period |
| | | [24 months] |
| | | |
5.3 Restricted Personnel.
In accordance with Section 8.5(d) of the MSA, in addition to the Key Supplier Personnel under this Supplement, the following Supplier Personnel are “Restricted Personnel” under this Supplement:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 4 |
|
|
| Name of Restricted Personnel |
| |
| |
6. GOVERNANCE.
Schedule 6 to the MSA is hereby supplemented [by Schedule [_]-6 to this Supplement.] or [as follows:]
[The parties will manage their relationship under the MSA using the governance model described in this Schedule (see Section 9.3 of the MSA).]
6.1 Supplier Account Manager.
In accordance with Section 8.3 of the MSA, the Supplier Account Manager as of the Supplement Effective Date is [_____].
6.2 CoreLogic Relationship Manager.
In accordance with Section 10.1(a) of the MSA, the CoreLogic Relationship Manager as of the Supplement Effective Date is [_____].
6.3 Meetings.
In accordance with Section 9.3(b) of the MSA, in addition to those meetings specified in the MSA, Transition Plan, Policy and Procedures Manual and Schedule 6, representatives of the Parties shall have the following meetings:
[List any additional meeting requirements specific to this Supplement here.]
6.4 Modifications to the Policy and Procedures Manual.
In accordance with Section 9.1(b) of the MSA, Supplier shall make the following modifications to the Policy and Procedures Manual:
[List any specific modifications that need to be made to the Policy and Procedures Manual.]
7. FACILITIES.
Schedule 7 to the MSA is hereby supplemented [by Schedule [_]-7 to this Supplement.] or [as follows:]
7.1 Supplier Facilities.
In accordance with Section 6.1 of the MSA and in addition to any Supplier Facilities described in Schedule 7 to the MSA, Supplier may use the following Supplier Facilities for the type of Services indicated for each such facility:
|
| |
| Facility Name and Address | Services to be Provided From Facility |
| | |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 5 |
7.2 CoreLogic Facilities.
In accordance with Section 6.2 and Schedule 7 of the MSA, CoreLogic will provide Supplier with office space and office furniture and the other accommodations required under Section 6.2 of the MSA in the following CoreLogic Facilities, as more fully described below, for the performance of the Services under this Supplement:
[This section lists the CoreLogic Facilities which Supplier will be permitted to use to provide the Services.]
|
| | | |
| Facility Name and Address | No. of Supplier Personnel | Description | Duration |
| | | | |
| | | | |
7.3 Jurisdictions Where Services are Received.
In accordance with Section 11.3(d) of the MSA, for purposes of determining each Party’s responsibility for Service Taxes under this Supplement, the Parties agree that the Services under this Supplement will be received in the following jurisdictions:
8. RULES, PROCEDURES AND POLICIES.
Schedule 8 to the MSA is hereby supplemented [by Schedule [_]-8 to this Supplement.] or [as follows:]
In accordance with Section 9.1(c) of the MSA, the following sections shall be added to or modified in the Policy and Procedures Manual:
[Supplier must update the Policy and Procedures Manual for each Supplement. This section lists the sections of the Policy and Procedures Manual that should be added or modified for this Supplement.]
9. INSURANCE REQUIREMENTS.
Schedule 9 to the MSA is hereby supplemented [by Schedule [_]-9 to this Supplement.] or [as follows:]
[If this Supplement has any additional insurance requirements, they should be listed here.]
10. COMPANION AGREEMENTS.
In accordance with Section 2.2(a) of the MSA, Supplier and CoreLogic shall cause their following local Affiliates to enter into Companion Agreements:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 6 |
[List any CoreLogic/Supplier Affiliates that should enter into Companion Agreements under this Supplement.]
11. SOFTWARE AND EQUIPMENT INVENTORY.
Software and Equipment that are applicable to this Supplement are set forth in Schedule [_]-12 to this Supplement.
[Note: This may already be captured in a financial responsibility matrix]
| |
| 12. | ADMINISTERED EXPENSES, THIRD PARTY CONTRACTS AND MANAGED THIRD PARTIES. |
12.1 Administered Expenses.
The Administered Expenses described in Section 11.2(a) of the MSA are set forth [below] or [in Schedule [_]-13].
[This section lists any Administered Expenses.]
12.2 Third Party Contracts.
In accordance with Section 6.6(a) of the MSA, CoreLogic shall assign to Supplier the [following Third Party Contracts] or [Third Party Contracts set forth in Schedule [_]-13]:
[This section lists Third Party Contracts which will be assigned to Supplier.]
12.3 Managed Third Parties.
In accordance with Section 4.5(c) of the MSA, Managed Third Parties under this Supplement are set forth [below] or [in Schedule [_]-13].
[This section lists Managed Third Parties applicable to this Supplement.]
13. REPORTS.
In accordance with Section 9.2 of the MSA, Supplier shall provide CoreLogic with the Reports identified in Schedule [_]-14 to this Supplement.
14. THIRD PARTY MATERIALS.
In accordance with Section 14.3(c) of the MSA, Supplier shall provide the Third Party Materials set forth in Schedule [_]-16.
[Include a list of Third Party Materials that Supplier will provide. Note: This may already be covered in a financial responsibility matrix to the Charges schedule. Identify any Materials for which Supplier is unable to provide post-termination rights or licenses in accordance with Sections 6.5(c), 14.6 or 20.8 of the MSA.]
15. CORELOGIC PROVIDED EQUIPMENT.
In accordance with Section 6.5(e) of the MSA, CoreLogic shall provide Supplier with the following CoreLogic Provided Equipment for the purpose of performing the Services for the specified period:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 7 |
|
| | | |
| CoreLogic Facility Location | Quantity | Description of CoreLogic Provided Equipment | Duration |
| | | | |
16. INDUSTRY STANDARDS.
In accordance with Section 9.4(d) of the MSA, Supplier will maintain certification or compliance with the following industry standards:
[List each industry standard certification or compliance here, for example: CCMi Level 3 certification.]
17. EQUIPMENT REFRESH AND SOFTWARE CURRENCY.
In accordance with Section 9.5(c) of the MSA, Supplier’s Technology and Business Process Plan shall include plans for refreshing Equipment and Software in accordance with the following:
[List any Equipment refresh cycles and responsibilities applicable to the Services under this Supplement or modify as appropriate if such refresh cycles and responsibilities are set forth in a responsibilities matrix or other portion of the Supplement.]
18. SUBCONTRACTORS.
In accordance with Section 9.11(a) of the MSA, the following Subcontractors are approved by CoreLogic for the provision of the following types of Services under this Supplement:
[This section identifies the pre-approved Supplier Subcontractors, and also should specify which Services each Subcontractor will provide. This list may include some of CoreLogic’ current third party contractors who will be engaged by or transitioned to Supplier. This section should also identify any pre-approved Subcontractors for which Supplier is unable to obtain audit or other rights described in clauses (i) through (vii) of Section 9.11(c) or other provisions of the MSA.]
|
| | |
| Approved Subcontractor | Service Location | Types of Services |
| | | |
| | | |
19. TECHNOLOGY AND BUSINESS PROCESS EVOLUTION AND NEW ADVANCES.
In accordance with Section 9.12(e) of the MSA, the following Technology and Business Process Evolution and New Advances are not included in the Charges:
[By default Technology and Business Process Evolution and New Advances are included in the Charges (unless they constitute “New Services”). If there are any exceptions, they should be listed here.]
20. PERSONAL DATA.
In accordance with Section 13.3(a) of the MSA, Supplier may process and store Personal Data in the following jurisdictions, in addition to those listed in Schedule 7:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 8 |
[Any additional locations where Supplier has been approved as of the Supplement Effective Date to process and store Personal Data for the Services under this Supplement should be listed here.]
21. SPECIFICATIONS AND WARRANTY PERIOD FOR DEVELOPED MATERIALS.
In accordance with Section 15.2(c) of the MSA, any Developed Materials will comply with the following Specifications:
[This section lists the Specifications to which any Developed Materials must materially comply during the warranty period. Also, if any warranty periods differ from those specified in the MSA for a specific Developed Material, then that should be specified here as well.]
22. INVOICING.
In accordance with Section 12.1(b) of the MSA, Supplier will provide CoreLogic with invoices [in the form as specified in Schedule [__]-4 to this Supplement and in accordance with the following] or [in the accordance with and in the form as specified in Schedule [__]-4 to this Supplement]:
[List in Schedule [__]-4 or here any invoice requirements including w/r/t local billing and payment]
23. TRANSITION.
23.1 Transition Milestones.
Schedule [_]-10 sets forth the Transition Milestones (and associated Deliverable Credits, if any) under this Supplement. [Include a designation of which of the Milestones are “Critical Transition Milestones” (i.e., Milestones that trigger a CoreLogic termination right if Supplier fails to meet them) pursuant to Section 4.2(h)(iii) of the MSA.]
23.2 Initial Transition Plan.
In accordance with Section 4.2(b) of the MSA, Schedule [_]-10 sets forth the initial Transition Plan.
24. DISENGAGEMENT SERVICES.
In accordance with Section 20.8 of the MSA, Supplier shall provide the Disengagement Services specified in Schedule [_]-15 in addition to those Disengagement Services described in Section 20.8.
In accordance with Section 20.8(b)(1) of the MSA, CoreLogic is entitled to the source code specified in Schedule [_]-15.
25. DISASTER RECOVERY AND BUSINESS CONTINUITY.
In accordance with Section 9.14(e) of the MSA, Supplier shall perform disaster recovery Services as described in Schedule [ ]-17
[Describe Supplier’s obligations for disaster recovery in addition to what is required under Section 9.14(e) of the MSA]
26. ENCRYPTION.
In accordance with Schedule 12 to the MSA, Supplier shall maintain encryption of electronic CoreLogic Data at the following levels:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 9 |
[List any specific CoreLogic encryption requirements here.]
27. CLIENT AUTHORIZED SIGNATORIES.
The CoreLogic Personnel set forth below are hereby approved by CoreLogic to execute changes in accordance with the Change Management Procedures and Work Orders, in each case in connection with this Supplement.
28. SUPPLEMENT TERM.
The Term of this Supplement shall commence as of 12:00:01 a.m., Pacific Time on the Supplement Effective Date and continue until 11:59:59 p.m., Pacific Time, on [________], 20[__] unless this Supplement is terminated as provided herein or in the MSA, in which case the Term of this Supplement shall end at 11:59:59 p.m., Pacific Time, on the effective date of such termination or the date to which this Supplement is extended. The Supplement Commencement Date is [__________].
29. MSA TERMS.
In accordance with Section 1.1(c) of the MSA, the following terms and conditions of the MSA shall be excluded from incorporation into this Supplement:
[By default all of the terms and conditions of the MSA apply to this Supplement. If there are any terms and conditions from the MSA that should not apply to this Supplement, they should be listed here.]
SIGNATURE PAGE FOLLOWS
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 10 |
IN WITNESS WHEREOF, the Parties have caused this Supplement to be executed by their respective duly authorized representatives as of the Supplement Effective Date.
|
| |
CORELOGIC SOLUTIONS, LLC | DELL MARKETING L.P. |
| By: _________________________________ | By:_____________________________________ |
| Title:________________________________ | Title:____________________________________ |
| Date:________________________________ | Date:____________________________________ |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 11 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
ANNEX 2
FORM OF NON-DISCLOSURE AGREEMENT
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 12 |
Annex 2
Form of Non-Disclosure Agreement
This Non-Disclosure Agreement (“NDA”) is entered into effective [________], 20[__], by and among Dell Marketing L.P., a Texas limited partnership having a principal place of business in Round Rock, Texas (“Disclosing Party”), and [________], a [________] corporation having a principal place of business in [________] (“Receiving Party”) and CoreLogic Solutions, LLC, a California limited liability corporation having a principal place of business in Santa Ana, California (“CoreLogic”).
WHEREAS, Disclosing Party and CoreLogic are parties to that certain Master Services Agreement, dated as of July 19, 2012 (the “MSA”);
WHEREAS, Disclosing Party is the owner and licensor of certain Confidential Information (as defined below)
WHEREAS, CoreLogic has retained Receiving Party to conduct a review and assessment of certain Confidential Information for the purposes permitted under Section 9.10, Section 11.6, Section 13.1(b)(v) or Section 20.8 of the MSA and set forth in Attachment 1 hereto (the “Purpose”); and
WHEREAS, CoreLogic wishes to disclose, or have Disclosing Party disclose to Receiving Party, and Receiving Party wishes to receive, under the terms and conditions of this NDA, Confidential Information;
NOW THEREFORE, in consideration of the above premises and the promises hereinafter set forth, Receiving Party and Disclosing Party acknowledge and agree as follows:
| |
| 1. | CONFIDENTIAL INFORMATION. |
| |
| 1.1 | “Confidential Information” shall mean (i) this NDA and the terms hereof and thereof, (ii) the MSA and all schedules or annexes thereto as well as any Supplements or Work Orders executed thereunder (including any exhibits, schedules, attachments or appendices thereto, and (iii) all information (written, oral or visual) marked as “Proprietary”, “Confidential”, or with a similar legend, or otherwise identified in writing promptly after disclosure as proprietary or confidential and (iv) all other information that should reasonably be understood to be confidential, whether or not so marked. |
| |
| 1.2 | Confidential Information shall not include information Receiving Party can demonstrate (i) is, at the time of disclosure to it, in the public domain; (ii) after disclosure to it, is published or otherwise becomes part of the public domain through no fault of Receiving Party; (iii) is lawfully in the possession of Receiving Party at the time of disclosure to it without obligation of confidentiality; (iv) is received without obligation of confidentiality from a third party having a lawful right to disclose such information and without breach of this NDA by the Receiving Party; or (v) is independently developed by Receiving Party without reference to Confidential Information. |
| |
| 2. | RECEIVING PARTY’S DUTIES. |
| |
| 2.1 | During the term of this NDA and at all times thereafter, Receiving Party shall not disclose, and shall maintain the confidentiality of, all Confidential Information. Receiving Party shall use at least the same degree of care to safeguard and to prevent disclosing to third parties Confidential Information as it employs to avoid unauthorized disclosure, publication, dissemination, destruction, loss, or alteration of its own information (or information of its customers) of a similar nature, but not less than reasonable care. Receiving Party may disclose Confidential Information to its employees as and to the extent such disclosure is necessary for the performance of such person’s obligations in connection with the Purpose on the condition that, prior to such disclosure, such employees have signed an agreement with Receiving Party with confidentiality provisions substantially equivalent to those set forth herein that are applicable to the Confidential Information or are otherwise bound by confidentiality obligations at least as restrictive as those contained herein. Receiving Party and CoreLogic jointly and severally assume full responsibility for the acts or omissions of such persons and must take all reasonable measures to ensure that Confidential |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 13 |
Information is not disclosed or used in contravention of this NDA; provided, that CoreLogic’s liability shall be limited in accordance with Article 18 of the MSA.
| |
| 2.2 | Receiving Party shall not (i) make any use or copies of Confidential Information except as contemplated by this NDA and required for the Purpose; (ii) acquire any right in or assert any lien against Confidential Information; (iii) sell, assign, transfer, lease, or otherwise dispose of Confidential Information to third parties or commercially exploit such information, including through derivative works; or (iv) refuse for any reason to promptly provide Confidential Information (including copies thereof) to Disclosing Party if requested to do so. |
| |
| 2.3 | Receiving Party shall not be considered to have breached its obligations under this NDA for disclosing Confidential Information as required to satisfy any legal, accounting, or regulatory requirement of a competent government body, provided that, (i) promptly upon receiving any such request and to the extent that it may legally do so, Receiving Party advises Disclosing Party of the Confidential Information to be disclosed and the identity of the third party requiring such disclosure prior to making such disclosure in order that Disclosing Party may interpose an objection to such disclosure, take action to assure confidential handling of the Confidential Information, or take such other action as it deems appropriate to protect the Confidential Information, (ii) Receiving Party discloses only such Confidential Information as is required by the governmental entity, and (iii) Receiving Party uses commercially reasonable efforts to obtain confidential treatment for any Confidential Information so disclosed. |
| |
| 2.4 | Receiving Party shall: (i) promptly notify Disclosing Party of any known possession, use, knowledge, disclosure, or loss of Confidential Information in contravention of this NDA; (ii) promptly furnish to Disclosing Party all known details and assist Disclosing Party in investigating and/or preventing the reoccurrence of such possession, use, knowledge, disclosure, or loss; (iii) reasonably cooperate with Disclosing Party in any investigation or litigation deemed necessary by Disclosing Party to protect its rights; and (iv) promptly use commercially reasonable efforts to prevent further possession, use, knowledge, disclosure, or loss of Confidential Information in contravention of this NDA. Receiving Party shall bear its own costs in complying with this subsection. |
| |
| 3.1 | Upon completion of the Purpose, Receiving Party shall return or destroy, as Disclosing Party directs, all Confidential Information, and retain no copies; provided that the Receiving Party may retain work papers related to audit and benchmarking functions; provided that such work papers shall all times be subject to the restrictions contained in this NDA. |
| |
| 3.2 | The obligations to maintain confidentiality, the restrictions on use, disclosure, duplication, protection, and security of Confidential Information and indemnification for breach thereof by Receiving Party shall survive the rescission, termination, or completion of this NDA, and remain in full force and effect until such Confidential Information, through no fault of Receiving Party, becomes part of the public domain. |
| |
| 4.1 | This NDA shall be governed by and construed, and the legal relations between the parties shall be determined, in accordance with the laws of the State of California, without giving effect to the principles of conflicts of laws. |
| |
| 4.2 | This NDA supersedes all prior understandings and negotiations, oral and written, and constitutes the entire understanding between the parties on this subject. Notwithstanding the foregoing, as between Disclosing Party and CoreLogic, the confidentiality provisions contained in the MSA remain in full force and effect. |
| |
| 4.3 | No waiver, modification, or amendment to this NDA shall be binding upon the parties unless it is in writing signed by an authorized representative of the party against whom enforcement is sought. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 14 |
| |
| 4.4 | Nothing in this NDA nor any disclosure made hereunder shall be deemed to grant to Receiving Party, by implication, estoppel or otherwise, license rights, ownership rights or any other intellectual property rights or other rights in any Confidential Information. |
| |
| 4.5 | Receiving Party agrees that any violation or threatened violation of this NDA may cause irreparable injury to Disclosing Party entitling Disclosing Party, without proof of monetary damages or the inadequacy of other remedies, to seek a preliminary injunction, injunction or other equitable relief in addition to other legal remedies. |
| |
| 4.6 | Disclosing Party makes no warranties (express or implied) regarding the Confidential Information with regard to its accuracy, completeness, freedom from infringement or otherwise. Without limitation of the foregoing, the Confidential Information are made available under this Agreement “AS IS”, with all defects, errors, and deficiencies, and without any representation or warranty as to completeness or accuracy. |
| |
| 4.7 | The parties agree that no agency, partnership to joint venture is in any way created by the parties under this NDA. |
| |
| 4.8 | If any provision of this NDA shall be held by a court of competent jurisdiction to be illegal, invalid or unenforceable, such provision shall be deemed to be restated to reflect as nearly as possible to the original intentions of the parties in accordance with the applicable laws. The remaining provisions of this NDA and the applications of the challenged provision to persons or circumstances other than those as to which it is invalid or unenforceable shall not be affected thereby, and each such provision shall be valid and enforceable to the full extent permitted by the applicable laws. |
| |
| 4.9 | The Receiving Party may not assign this NDA without the prior written approval of the Disclosing Party. |
| |
| 4.10 | If this NDA is executed in counterparts, no signatory is bound until all parties have duly executed this NDA and have received a fully executed NDA. Any signature transmitted by facsimile or e-mail (in .pdf, .tif, or similar format), or a photocopy of such transmission, shall constitute the original signature of such party. |
| |
| 4.11 | The protections afforded to the Confidential Information under this Agreement are in addition to, and not in lieu of, the protections afforded under any applicable trade secrets laws, including the Uniform Trade Secrets Act. |
SIGNATURE PAGE FOLLOWS
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 15 |
IN WITNESS WHEREOF, the parties have caused this NDA to be signed by their authorized representatives effective on the date and year first above written.
|
| | | | |
| Dell Marketing L.P. | | [Receiving Party] |
| By: | | | By: | |
| Name: | | | Name: | |
| Title: | | | Title: | |
| Date: | | | Date: | |
| CoreLogic Solutions, LLC | | | |
| By: | | | | |
| Name: | | | | |
| Title: | | | | |
| Date: | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 16 |
ATTACHMENT 1
PURPOSE
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 17 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
ANNEX 3
FORM OF COMPANION AGREEMENT
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside either Party without the prior written permission of the other Party. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 18 |
Annex 3
Form of Companion Agreement
COMPANION AGREEMENT
[Local Entity Name]
This Companion Agreement – [local entity name] (this “Companion Agreement”) is entered into effective [________], 20[__] (the “Companion Agreement Date”), by and between [________], with an office at [________] (“Local CoreLogic”), and [________], with an office at [________] (“Local Supplier”).
R E C I T A L S:
WHEREAS, CoreLogic Solutions, LLC, a California limited liability corporation having a principal place of business in Santa Ana, California (“CoreLogic”), and Dell Marketing L.P., a Texas limited partnership having its registered office in Round Rock, Texas (“Supplier”), entered into the Master Services Agreement dated July 19, 2012 (the “Master Services Agreement” or “MSA”); and
WHEREAS, the MSA contemplates the provision of certain Services in or for various countries around the world, including [name of country where local entity is located]. The MSA also contemplates that CoreLogic (or an Affiliate designated by CoreLogic) and Supplier (or an Affiliate designated by Supplier) will enter into a Companion Agreement for the provision of such Services. The MSA also contemplates that additional services may be added to the MSA by execution of additional Supplements, which will then become part of the Services under the MSA; and
WHEREAS, the purpose of this Companion Agreement is to set forth the terms and conditions for Local Supplier’s provision of the Services as described in the MSA and the above-referenced Supplement(s) to certain Eligible Recipients or Authorized Users in [name of local entity];
NOW THEREFORE, in consideration of the promises contained in this Companion Agreement and other good and valuable consideration, the receipt and sufficiency of which is hereby acknowledged, Local CoreLogic and Local Supplier agree as follows:
| |
| 1.1 | Precedence of Obligations. The Parties acknowledge that certain obligations may be set forth in both this Companion Agreement and elsewhere in the Agreement, and that in the event of a conflict, such conflict shall be resolved in accordance with Section 21.13 of the MSA. |
| |
| 1.2 | References. All references in this Companion Agreement to articles, sections and schedules shall be to this Companion Agreement, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Companion Agreement with initial capitalized letters but not defined in this Companion Agreement shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
| |
| 2. | TERM. The term of this Companion Agreement will commence on the Companion Agreement Date, and will continue thereafter until the expiration or termination of the MSA or the Supplement(s), whichever is earlier, unless this Companion Agreement is terminated earlier in accordance with the terms of the MSA, the Supplement(s) or this Companion Agreement. |
| |
| 3. | LOCAL SERVICES. During the term of this Companion Agreement, Local Supplier will provide the Services described in the MSA and Supplement(s) No. [_] to the [name of local entity]. Local Supplier will provide such Services in the manner and in accordance with the Service Levels set forth in the MSA and the Supplement. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 19 |
Local Supplier also will timely perform or cause to be performed the obligations of Supplier specified in the MSA with respect to such Services.
| |
| 4. | LOCAL CORELOGIC OBLIGATIONS. Local CoreLogic will timely perform or cause to be performed the obligations of CoreLogic specified in the MSA with respect to the Services provided by Local Supplier under this Companion Agreement. |
| |
| 5.1 | Local Supplier Fee. The Charges for the Services to be provided by Local Supplier under this Companion Agreement are set forth in the MSA and applicable Supplements. |
| |
| 5.2 | Taxes. Unless otherwise specified in this Companion Agreement, the responsibilities of each Party for taxes arising under or in connection with this Companion Agreement will be as set forth in Section 11.3 of the MSA. Without limiting the rights and obligations in Section 11.3 of the MSA, Local CoreLogic shall have the rights and responsibilities of CoreLogic and Local Supplier of Supplier as appropriate under such Section 11.3 of the MSA in applying this Companion Agreement. |
| |
| 5.3 | Invoicing and Payment Terms. Unless otherwise specified in this Companion Agreement, the responsibilities of each Party for invoicing and payment for Services provided under this Companion Agreement will be as set forth in the MSA and, if applicable, the Supplement. //Include here any provisions regarding local billing and payment// |
| |
| 6. | ADDITIONAL PROVISIONS. //Include here TUPE/ARD provisions and any other provisions required by applicable Laws, including changes to any of the terms of the MSA (noting that the change applies with respect to the Companion Agreement notwithstanding Section 21.13 of the MSA and Section 1.1 above) and any additional obligations of either Party// |
| |
| 7. | DISPUTES AND JURISDICTION. For avoidance of doubt, any dispute arising under this Companion Agreement will be resolved in accordance with the provisions of Article 19 of the MSA. |
| |
| 8. | GOVERNING LAW. Except as otherwise provided in this Companion Agreement, this Companion Agreement and performance under it will be governed by and construed in accordance with the applicable Laws of the State of California, USA, without giving effect to the principles thereof relating to conflicts of laws. The application of the United Nations Convention on Contracts for the International Sale of Goods is expressly excluded. Notwithstanding the foregoing, if any provision of this Companion Agreement is expressly required by the mandatory Laws of [name of country] to be subject to specific Laws of [name of country] and the applicability of such mandatory Laws is not subject to contractual waiver or limitation, the construction, interpretation and performance of such provision will be governed by the internal mandatory Laws of [name of country] (without reference to choice or conflict of laws). The election of the Laws of the State of [State] for this purpose will not operate or be construed to result in the extraterritorial application of any Laws of the State of [State] or the United States of America unrelated to the interpretation of contracts. |
| |
| 9. | NOTICE. Each Party shall comply with the notice provisions of Section 21.3 of the MSA for all notices to the other Party that are related to this Companion Agreement. |
| |
| 10. | COUNTERPARTS. This Companion Agreement may be executed in several counterparts, all of which taken together will constitute one single agreement between the parties hereto. |
| |
| 11. | SEVERABILITY. In the event that any provision of this Companion Agreement conflicts with the Law under which this Companion Agreement is to be construed or if any such provision is held invalid or unenforceable by a court with jurisdiction over the parties hereto, such provision will be deemed to be restated to reflect as nearly as possible the original intentions of the Parties in accordance with applicable Law. The remaining provisions of this Companion Agreement and the application of the challenged provision to persons |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 20 |
or circumstances other than those as to which it is invalid or unenforceable will not be affected thereby, and each such provision will be valid and enforceable to the full extent permitted by Law.
| |
| 12. | LANGUAGE. The Parties have requested that this Companion Agreement and all documents contemplated thereby or relating thereto be drawn up in the English language. This document will be translated into an official language of [name of country] if required by Law, but in the event of inconsistencies or conflicts the English version will prevail. |
| |
| 13. | ENTIRE AGREEMENT. Together with the MSA and the Supplement(s), as each may be amended, this Companion Agreement and the Schedules and Attachments thereto constitute the entire agreement between the Parties with respect to the subject matter hereof. There are no agreements, representations, warranties, promises, covenants, commitments or undertakings other than those expressly set forth herein and therein. This Companion Agreement supersedes all prior agreements, representations, warranties, promises, covenants, commitments or undertakings, whether written or oral, with respect to the subject matter contained in this Companion Agreement. No amendment, modification, change, waiver, or discharge hereof will be valid unless in writing and signed by an authorized representative of the Party against which such amendment, modification, change, waiver, or discharge is sought to be enforced (except, however, that amendments to the MSA and/or the Supplement will be applicable to this Agreement). |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 21 |
IN WITNESS WHEREOF, Local CoreLogic and Local Supplier have each caused this Companion Agreement to be executed by their respective duly authorized representatives on the dates set forth below to be effective as of the Companion Agreement Date.
[Local CoreLogic name] [Local Supplier name]
By: By:
Name: Name:
Title: Title:
Date: Date:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 22 |
MASTER SERVICES AGREEMENT
by and between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
ANNEX 4
FORM OF BUSINESS ASSOCIATE AGREEMENT
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 23 |
Annex 4
Form of Business Associate Agreement
1.INTRODUCTION
| |
| 1.1 | Agreement. This Annex 4 (this “Annex”) is attached to and incorporated by reference in that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Annex to articles, sections and attachments shall be to this Annex, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Annex with initial capitalized letters but not defined in this Annex shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
2. FORM OF BUSINESS ASSOCIATE AGREEMENT
Within thirty (30) days after the Effective Date, the Parties will work in good faith to develop a form of Business Associate Agreement for purposes of Section 13.3(d) of the MSA.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Annex | Page 24 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
by and between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
DATA CENTER SERVICES AND RE-PLATFORMING SERVICES
July 19, 2012
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
SUPPLEMENT A TO
MASTER SERVICES AGREEMENT
DATA CENTER SERVICES AND RE-PLATFORMING SERVICES
This Supplement A (this “Supplement”) is entered into effective as of July 19, 2012 (the “Supplement Effective Date”) by and between CoreLogic Solutions, LLC, a California limited liability company having a principle place of business in Santa Ana, California (“CoreLogic”), and Dell Marketing L.P., a Texas limited partnership having a principal place of business in Round Rock, Texas (“Supplier”) (collectively, the “Parties” and each, a “Party”).
This Supplement is entered into pursuant to and subject to that certain Master Services Agreement (“Master Services Agreement” or “MSA”) dated as of July 19, 2012, by and between the Parties, the terms of which, except as may be expressly modified or excluded herein, are incorporated herein by reference.
NOW THEREFORE, in consideration of the mutual promises contained herein, and of other good and valid consideration, the receipt and sufficiency of which is hereby acknowledged, the Parties hereby agree as follows:
1.INTRODUCTION
| |
| 1.1 | Precedence of Obligations. The Parties acknowledge that certain obligations may be set forth in both this Schedule and elsewhere in the Agreement, and that in the event of a conflict, such conflict shall be resolved in accordance with Section 21.13 of the MSA. |
| |
| 1.2 | References. All references in this Supplement to articles, sections and attachments shall be to this Supplement, unless another reference is provided. |
| |
| 1.3 | Associated Supplement Documents. |
This Supplement includes each of the following Schedules, all of which are incorporated into this Supplement by this reference:
Schedule A-1 Supplement Definitions
Schedule A-2 Statements of Work
Schedule A-2.1 Cross Functional Services
Schedule A-2.2 Service Management Services
Schedule A-2.3 Service Desk Services
Schedule A-2.4 Server Services
Schedule A-2.5 Storage and Backup Services
Schedule A-2.6 Desktop End User Messaging Services
Schedule A-2.7 Data Center, Mainframe, Production Control, and Monitoring Services
Schedule A-2.8 Media Services
Schedule A-2.9 Network Services
Schedule A-2.10 Reserved
Schedule A-2.11 Reserved
Schedule A-2.12 Disaster Recovery Services
Schedule A-3 Service Level Methodology
Schedule A-3.1 Service Level Matrix
Schedule A-3.2 Reserved
Schedule A-3.3 Critical Deliverables
Schedule A-4 Pricing Methodology
Schedule A-4.1 Baseline Charges
Schedule A-4.2 Resource Unit Definitions
Schedule A-4.3 Baseline Volumes
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 2 |
Schedule A-4.4 ARC / RRC Rates
Schedule A-4.5 Transition Charges and Transformation Charges
Schedule A-4.5.1 Transition Charges
Schedule A-4.5.2 Transformation Charges
Schedule A-4.6 Financial Responsibility Matrix
Schedule A-4.7 Rate Card
Schedule A-4.8 Termination Charges
Schedule A-4.9 Invoicing
Schedule A-4.10 Chargeable Projects
Schedule A-4.11 Project Pool
Schedule A-4.12 ***
Schedule A-5 Human Resources Provisions
Schedule A-5.1 Key Supplier Personnel
Schedule A-5.2 Affected Employees
Schedule A-5.3 Severance Formula
Schedule A-5.3.1 Directors for Enhanced Severance Benefits
Schedule A-6 Reserved
Schedule A-7 Facilities
Schedule A-7.1 CoreLogic Facilities
Schedule A-7.2 Supplier Facilities
Schedule A-8 Software and Equipment Inventory
Schedule A-8.1 Equipment Inventory
Schedule A-8.2 Supplier Tools & CoreLogic Tools
Schedule A-9 Approved Subcontractors
Schedule A-10 Transition Services
Schedule A-10.1 Initial Transition Plan
Schedule A-10.2 Reserved
Schedule A-10.3 Additional Transition Services Obligations
Schedule A-10.3.1 CoreLogic Projects as of Supplement Effective Date
Schedule A-11 Customer Satisfaction Surveys
Schedule A-12 Reports
Schedule A-13 Transformation Services
Schedule A-13.1 *** Application Scope Components
Schedule A-13.2 Acceptance Criteria for *** and ***
Schedule A-13.3 Natural to COBOL Conversion
| |
| (a) | Schedule 1 to the MSA is hereby supplemented with the definitions set forth in Schedule A-1 to this Supplement. |
| |
| (b) | The definitions added by this Supplement to Schedule 1 to the MSA shall apply only with respect to the Services provided under this Supplement. |
2. SERVICES.
Schedule 2 to the MSA is hereby supplemented by Schedule A-2 to this Supplement. Supplier shall perform the Services set forth in Schedule A-2 to this Supplement during the Term of this Supplement, and CoreLogic shall perform the tasks, functions and responsibilities of CoreLogic set forth in Schedule A-2 to this Supplement during the Term of this Supplement. The Services that will be performed under this Supplement as *** Services are identified as such in Schedule A-2.
3. SERVICE LEVELS.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 3 |
Schedule 3 to the MSA is hereby supplemented by Schedule A-3 to this Supplement. Supplier shall provide the Services so as to meet or exceed the Service Levels identified in Schedule A-3 to this Supplement.
4. PRICING AND FINANCIAL PROVISIONS.
Schedule 4 to the MSA is hereby supplemented by Schedule A-4 to this Supplement. The Charges for this Supplement are set forth in Schedule A-4 to this Supplement.
In accordance with Section 12.1(b) of the MSA, Supplier will provide CoreLogic with invoices in the form as specified in Schedule A-4.10 to this Supplement.
5. HUMAN RESOURCE PROVISIONS.
Schedule 5 to the MSA is hereby supplemented by Schedule A-5 to this Supplement.
In accordance with Section 8.2(b) of the MSA, the Key Supplier Personnel under this Supplement and their minimum retention periods are set forth in Schedule A-5. In accordance with Section 8.5(d) of the MSA, as of the Supplement Effective Date, there are *** *** the ***. In accordance with Section 8.2(c) of the MSA, as of the Supplement Effective Date, there are *** ***.
In accordance with Section 8.5(e) of the MSA, Supplier shall conduct *** Supplier Personnel prior to their performance of Services under this Supplement as required by applicable CoreLogic customers in accordance with the flow-down provisions of Section 9.17 of the MSA; provided, that the first *** Supplier Personnel to be *** shall be at no additional charge to CoreLogic. If, pursuant to the preceding sentence, Supplier is required to *** more than *** Supplier Personnel, Supplier shall do so at CoreLogic’s expense with respect to third party expenses only and Supplier shall not assess additional fees or other Charges to administer such fingerprinting (provided that Supplier notifies CoreLogic of such third party expenses, obtains CoreLogic’s prior approval of, and uses commercially reasonable efforts to minimize, such third party expenses).
As of the Supplement Effective Date, there is no requirement to conduct *** on Supplier Personnel prior to their performance of Services; provided, however, in accordance with Section 8.5(e) of the MSA, Supplier shall conduct *** on Supplier Personnel prior to their performance of Services under this Supplement as required by applicable CoreLogic customers in accordance with the flow-down provisions of Section 9.17 of the MSA.
6. GOVERNANCE.
6.1 Supplier Account Manager.
In accordance with Section 8.3 of the MSA, the Supplier Account Manager as of the Supplement Effective Date is ***.
6.2 CoreLogic Relationship Manager.
In accordance with Section 10.1(a) of the MSA, the CoreLogic Relationship Manager as of the Supplement Effective Date is ***.
7. FACILITIES.
Schedule 7 to the MSA is hereby supplemented by Schedule A-7 to this Supplement.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 4 |
| |
| 7.1 | CoreLogic Facilities. In accordance with Section 6.2 of the MSA, CoreLogic will provide Supplier with space and office furniture and the other accommodations required under Section 6.2 of the MSA in CoreLogic Facilities described in Schedule A-7.1 to this Supplement for the performance of the Services under this Supplement. |
| |
| 7.2 | Supplier Facilities. In accordance with Section 6.1 of the MSA, Supplier may use Supplier Facilities set forth in Schedule A-7.2 to this Supplement for the performance of the Services under this Supplement. |
7.3 Jurisdictions Where Services are Received.
In accordance with Section 11.3(d) of the MSA, for purposes of determining each Party’s responsibility for Service Taxes under this Supplement, the Parties agree that, as of the Supplement Effective Date, the Services under this Supplement will be received in the following jurisdictions in the United States:
***
If CoreLogic requires receipt of a material portion of the Services by Eligible Recipients in jurisdictions outside of the United States, the Parties will work in good faith to determine whether *** will be in local currency or in United States Dollars.
8. SOFTWARE AND EQUIPMENT INVENTORY.
Software and Equipment that are applicable to this Supplement are set forth in Schedule A-8 to this Supplement. Laptop computers, cell phones and pagers used by Transitioned Employees (collectively, “Personal EUC Devices”) may be retained by such employees after each such employee’s Employment Effective Date; provided, that Supplier shall cause the Transitioned Employees to return such Personal EUC Devices to CoreLogic by the end of the Transition Period. CoreLogic shall make reasonably available to Supplier CoreLogic’s inventory tracking and management reports during the Transition Period to assist Supplier in tracking and managing such Personal EUC Devices and shall maintain existing insurance and warranty coverage for such items to cover the loss, theft, damage or breakage of such Personal EUC Devices. All other CoreLogic property and materials in the control or possession of the Transitioned Employees, including calling cards, shall have been returned to CoreLogic by the Transitioned Employees on or prior each such employee’s Employment Effective Date.
9. THIRD PARTY CONTRACTS.
| |
| 9.1 | In accordance with Section 11.2(a) of the MSA, as of the Supplement Effective Date, the Administered Expenses applicable to this Supplement are invoices associated with CoreLogic’s Third Party Contracts for transport charges for circuits and ***, as further described in Schedule A-2.9. |
| |
| 9.2 | In accordance with Section 6.6(a) of the MSA, as of the Supplement Effective Date, there are no Third Party Contracts to be assigned by CoreLogic to Supplier pursuant to this Supplement. |
| |
| 9.3 | In accordance with Section 4.5(c) of the MSA, as of the Supplement Effective Date, there are no Managed Third Parties applicable to this Supplement. |
10. TRANSITION.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 5 |
In accordance with Section 4.2(b) of the MSA, Schedule A-10.1 to this Supplement sets forth the initial Transition Plan. Schedule A-10 describes the Transition Services and Transition Milestones applicable to this Supplement. The Deliverable Credits that may be due to CoreLogic are as set forth in Schedule A-4.5.
11. CUSTOMER SATISFACTION SURVEYS.
Supplier shall conduct customer satisfaction surveys in accordance with Schedule A-11 to this Supplement.
12. TRANSFORMATION.
In accordance with Section 4.8 of the MSA, Schedule A-13.1 to this Supplement sets forth the initial Transformation Plan. Schedule A-13.1 describes the Transformation Services applicable to this Supplement. The Transformation Milestones applicable to this Supplement are set forth in Schedule A-13.2. The Deliverable Credits that may be due to CoreLogic and additional payment amounts that may be achieved by Supplier in connection with certain Transformation Services are as set forth in Schedule A-4.5.
13. REPORTS.
In accordance with Section 9.2 of the MSA, Supplier shall provide CoreLogic with the Reports identified in Schedule A-12 to this Supplement.
14. WARRANTY PERIOD FOR DEVELOPED MATERIALS.
In accordance with Section 15.2(c) of the MSA, the Warranty Period with respect to the Tax Transformation Services and U2L Services is as specified in Schedule A-13.2.
In accordance with Section 9.11(a) of the MSA, Subcontractors approved by CoreLogic for the provision of Services under this Supplement are set forth in Schedule A-9 to this Supplement.
16. CORELOGIC AUTHORIZED SIGNATORIES.
The CoreLogic Personnel set forth below are hereby approved by CoreLogic to execute changes in accordance with the Change Management Procedures and Work Orders, in each case in connection with this Supplement.
|
| |
| Name | Title/Role |
| *** | Chief Information Officer |
| *** | SVP, Business Integration and Process Excellence |
| *** | VP, Enterprise Technology Services |
| *** | SVP, Information Technology |
| *** | VP, Data & Analytics |
17. SUPPLEMENT TERM.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 6 |
The Term of this Supplement shall commence as of 12:00:01 a.m., Pacific Time on the Supplement Effective Date and continue until 11:59:59 p.m., Pacific Time, on July 19, 2020 unless this Supplement is terminated as provided herein or in the MSA, in which case the Term of this Supplement shall end at 11:59:59 p.m., Pacific Time, on the effective date of such termination or the date to which this Supplement is extended. The Commencement Date for all Service Areas is ***.
SIGNATURE PAGE FOLLOWS
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 7 |
IN WITNESS WHEREOF, the Parties have caused this Supplement to be executed by their respective duly authorized representatives as of the Supplement Effective Date.
|
| |
CORELOGIC SOLUTIONS, LLC | DELL MARKETING L.P. |
| By: _________________________________ | By:_____________________________________ |
| Title:________________________________ | Title:____________________________________ |
| Date:________________________________ | Date:____________________________________ |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 8 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-1
SUPPLEMENT DEFINITIONS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 9 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-1
Supplement Definitions
1.INTRODUCTION
| |
| 1.1 | Agreement. This Schedule A-1 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and (“Supplier”) dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
The following terms, when used in Supplement A, have the meanings specified below:
“Actual Uptime” means the aggregate number of minutes during the Scheduled Uptime that the full material functionality of a particular Configuration Item, System, Equipment or other Service component is available for use by CoreLogic and the Eligible Recipients. Actual Uptime will be calculated by subtracting Downtime from Scheduled Uptime.
“Assets” means all elements of Software and hardware that are found in the environment, including CoreLogic Equipment and Software and any Supplier Equipment and Software (excluding Supplier financial and contractual information) used to deliver the Services. This encompasses the “Asset Confirmation Report” (See Schedule A-2.12) and “Asset Management Inventory” (See Section 3.2.1 of Schedule A-2.2).
“Asset Management” means the set of processes that join up-to-date financial, contractual and inventory information to support life cycle management, reporting, and strategic decision making for the Assets.
“Availability” means ability of a Configuration Item (CI) or IT Service to perform its agreed function when required. Availability is determined by reliability, maintainability, serviceability, performance, and security.
“Capacity Management” means the processes, procedures, and reporting related to collaborating and collecting inputs related to infrastructure, Services, technology performance, business plans, procedures, processes, components, forecasts, and related information from CoreLogic and Supplier. (See Schedule A-2.2).
“Change Request” means the process and any related forms required to submit changes requested by Authorized Users, where such changes are within the scope of the existing Services as outlined in Section 3.1 of Schedule A-2.2
“Change Management” means the processes relating to planning and implementing changes to the Services, Systems and Equipment that are requested, approved by CoreLogic or otherwise permitted in connection with the delivery of Services as outlined in Section 3.1 of Schedule A-2.2.
“Configuration Item” or “CI” has the meaning given in Section 3.2.2 of Schedule A-2.2.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 10 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Configuration Management Database” has the meaning given in Section 1.1.3 of Schedule A-4.2.
“Configuration Management” has the meaning given in Section 3.2.2 of Schedule A-2.2.
“Data Leakage Protection” or “DLP” means a solution that includes systems that are designed to detect and prevent potential data breach incidents by monitoring data while in-use (endpoint actions), in-motion (network traffic), and at-rest (data storage).
“Demand Management” means the process and procedures related to analyzing and forecasting CoreLogic demand for the Services.
“Disaster Recovery” means the process, policies and procedures related to executing the recovery or continuation of CoreLogic Applications and Systems as well as Supplier Equipment and Systems critical to the Services after an unforeseen business interruption.
“Disaster Recovery Plan” means a plan that includes procedures and the resources, actions, tasks and data required to manage the IT environment recovery process in the event of a critical business interruption. The plan is designed to assist in restoring the business process within the stated disaster recovery goals.
“Disaster Recovery Services” means the Services described in Schedule A-2.12, including all actions and tasks required to continue the provisioning of the Services in the event of a critical business interruption. The Disaster Recovery Services include support and coordination with the business continuity activities.
“Disaster Recovery Test” means the Services described in Schedule A-2.12 that test the processes, policies and procedures related to execution of the Disaster Recovery Plan.
“Downtime” means the aggregate number of minutes during the Scheduled Uptime that the full material functionality of a particular System, Equipment, or other Service component is not available for use by CoreLogic and the Eligible Recipients or is degraded in a material respect.
“FTE” or “Full Time Equivalent” has the meaning given in Schedule A-4.2.
“IMACD” means End User IMACDs – Campus and End User IMACDs – Remote.
“Incident” any means an unplanned interruption to a Service or System or a degradation in the quality of a Service or System, including the failure of a Configuration Item that has not yet impacted Services or Systems.
“Incident Management” means a process to address Incidents and restore service operations with minimum disruption to business operations.
“Physical Server Provisioning” means building a server and typically includes the following: assigning the data center location, engineering review, racking and stacking, networking, assigning IP, DNS, installing anti-virus software, firewall rules, setup server for IPS/IDS, allocation of SAN, allocation of multi-pathing software, setup of server for Software distribution and asset management, installation of the operating system and associated components, setup server in SIEM if applicable, Equipment configuration for monitoring, backup setup, CMDB setup, job scheduling, installation of agents, participation in a database requirements review, performance of server quality tests, maintenance setup and a “hand off” to CoreLogic.***
“Private Cloud Environment” means a CoreLogic virtual computing environment that includes dedicated storage, dedicated servers, dedicated other hardware and networking components.
“Problem Management” means the processes and procedures to manage and resolve the root causes of incidents, to minimize the re-occurrence of such incidents and their subsequent impact to CoreLogic Systems, the Equipment and Services.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 11 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Restoration” or “Restore” means taking action to return the Services to normal functionality after repair and recovery from an Incident
“Scheduled Downtime” means the number of minutes of scheduled Downtime for System, Equipment or other Service components during any Measurement Period required to perform system maintenance (for example, preventive maintenance, system upgrades, etc.), scheduled in accordance with Change Management Procedures.
“Scheduled Uptime” means the number of minutes during which a particular System, Equipment or other Service component expected to be available during the Measurement Period minus Scheduled Downtime.
“Service Catalog” means a database or structured document/form with information about the Services. The Service Catalogue includes information about deliverables, prices, contact points, ordering and service request process as outlined in Section 4.1 of Schedule A-2.2.
“Severity 1 Incident” means an Incident that: (i) causes a ***or ***or ***to be ***or ***, or (ii) is an ***or ***that ***, or ***performing a *** and for which no workaround solution exists.
“Severity 2 Incident” means an Incident that: (i) causes the ***or ***or ***of ***of a ***or ***or ***, or (ii) is an ***or ***that ***, or ***performing *** and for which a workaround solution may exist which allows for continued essential operations.
“Severity 3 Incident” represents a lower impact problem that involves a ***or ***of ***, or some other problem involving ***. CoreLogic can continue *** operations and a workaround solution may exist which allows for continued *** operations.
“Service Level Management” means the processes and procedures relating to the development, maintenance, monitoring, review and reporting of the performance of the Services using data, metrics, service quality and key performance indicators (KPI) against defined Service Levels.
“Security Information Event Management” or “SIEM” means SIM and SEM.
“Security Information Management” or “SIM” means a technology that provides for log management, which is the collection, reporting, storage and analysis of log data.
“Security Event Management” or “SEM” means the processing of event data from security devices, network devices, systems and Applications in real time to provide security monitoring, event correlation and incident response.
“Virtual Server Provisioning” means the creation of a virtual server and typically includes the following: assigning the data center location, engineering review, networking, assigning IP, DNS, install anti-virus software, firewall rules, setup server for IPS/IDS, allocation of SAN, allocation of multi-pathing software, setup of server for Software distribution and asset management, installation of the operating system and associated components, setup server in SIEM if applicable, Equipment configuration for monitoring, backup setup, CMDB setup, job scheduling, installation of agents, participation in a database requirements review, performance of server quality test, maintenance setup and a “hand off” to CoreLogic.
3. COMMONLY USED ACRONYMS
ACL access control list
ASB architecture standards board
AOS assumption of service
CISO Chief Information Security Officer
DCTMV Data Center Transformation Migration and Virtualization
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 12 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
DHCP dynamic host configuration protocol
DoS denial of services
FAQs frequently asked questions
GAL global address list
IMAC install, move, add, change
ITIL Information Technology Infrastructure Library
ITSM Information Technology Service Management
OEM original equipment manufacturer
PMBOK project management book of knowledge
PMO project management office
PPD project plan document
PPM Policy and Procedures Manual
PPW project planning workshop
QOS quality of service
RCA Root Cause Analysis
RDBMS relational database management system
RPO recovery point objective
RTM requirements traceability matrix
RTO recovery time objective
SIP session initiation protocol
SOP standard operating procedures
SSL secure socket layer
VOIP voice over internet protocol
VPN virtual private network
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 13 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
4. TERMS TO BE DEFINED
Within thirty (30) days after the Supplement Effective Date, the Parties shall work together in good faith to define the following terms with definitions that are consistent with standards and practices used by tier one providers performing services similar to the Services:
|
| |
Active Directory
Asset Confirmation Report
Availability Management Plans
Call Recording System
Change Advisory Board
Change Calendar
Clustering
CoreLogic Cloud Environment
Demand Forecast
Designated CoreLogic Data Centers
Desktop Software
Enterprise Security
Enterprise Storage
Event
Event Management
Expense Management
File Integrity Monitoring
Incident Ticket
Infrastructure
Install, Move, Add, Change and Delete
Intrusion Detection and Prevention Systems
ITSM Self-Service Portal
LAN Devices
Level 1 Support
Level 2 Support
Level 3 Support
Mainframe
Maintenance
Messaging
Monitoring Levels
Natural
Network Equipment
Network Zone
Operational Transition Planning Phase
Problem(s)
Problem Management System | Production
Production Control
Project Management
Project Management Office
Project Management Methodology
Project Plans
Release Management
Remote Sites
Request Management
Request Management Methodology
Resolution
Resolver Group
Storage Area Network
SAN Fabric
SAN Fabric Incidents
Server
Service Desk
Service Improvement
Service Improvement Plan
Service Management Services
Service Portfolio
Service Request
Software License Management
Source Assessment Transformation Approach Report
Special Retention Backups
Standard Server
Standard Template
Storage Equipment
Target Platform
Tool
Transformation Fee Threshold
U2L Services
Virtual Server
Voice Response Unit
Workstation |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 14 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2
STATEMENTS OF WORK
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 15 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-2
Statements of Work
1.Introduction.
1.1 Agreement. This Schedule A-2 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”).
1.2 References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided.
1.3 Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A.
1.4 Schedules. The following Schedules are hereby incorporated by reference into this Schedule, each of which shall be a “Service Area” under this Supplement:
Schedule A-2.1 Cross Functional Services
Schedule A-2.2 Service Management Services
Schedule A-2.3 Service Desk Services
Schedule A-2.4 Server Services
Schedule A-2.5 Storage Backup Services
Schedule A-2.6 End User Device Support and Messaging Services
Schedule A-2.7 Data Center, Mainframe, Production Control, & Monitoring Services
Schedule A-2.8 Electronic Data Exchange Services
Schedule A-2.9 Network Services
Schedule A-2.10 Reserved
Schedule A-2.11 Reserved
Schedule A-2.12 Disaster Recovery Services
2. Managed Services
The following Services are Managed Services under this Supplement:
|
| | | |
| Service Area | Schedule and Section Reference | *** Services | *** Services |
| Service Management Services | Schedule A-2.2 | | |
| Demand Management | Section 2.1 | | X |
| Capacity Management | Section 2.2 | | X |
| Availability Management | Section 2.3 | | X |
Service Level Management1 | Section 2.4 | | X |
____________________
1 Supplier's performance of Service Level management Services as Managed Services shall not alter or limit Supplier's obligations or CoreLogic's rights related to Service Levels under the Agreement (e.g., Schedule A-3).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 16 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Service Area | Schedule and Section Reference | *** Services | *** Services |
*** Management2 | Section *** | X | X |
Change Management3 | Section 3.1 | | X |
| Asset and Configuration Management | Section 3.2 | | X |
| Request Management | Section 4.1 | | X |
| Incident Management | Section 4.3 | | X |
| Problem Management | Section 4.4 | | X |
| Cross Functional Services | Schedule A-2.1 | | |
| Business Assessment | Section 2.1 | X | |
| Strategy & Architecture Planning | Section 2.2 | X | |
| Operations Documentation & Process | Article 3 | X | |
| Project Management | Article 4 | X | |
| Disaster Recovery Services | Schedule A-2.12 | X | |
| Disaster Recovery Planning & Implementation | Article 3 | X | |
| Disaster Recovery Testing | Article 4 | X | |
| Actual Disaster | Article 5 | X | |
| Service Desk Services | Schedule A-2.3 | | |
____________________
(a) The Parties agree that the portions of the *** Management Services that are functions to be performed within Supplier's *** offering (“*** Scope”) shall be deemed to be, and performed as, *** Services; provided that the functions to be performed within the *** Scope shall be determined in accordance with clause (b).
(b) During the Transition Period, the Parties agree to work together in good faith to determine which portions of *** Management Services will be run as *** Services, and to minimize the portions of the *** Management Services that will be *** Services. The resulting balance of *** Services versus *** Services shall be provided by Supplier at no additional charge to the Charges set forth in Schedule A-4. With respect to the *** Scope only, if CoreLogic, in its sole discretion, determines that it is necessary to move away from the *** Services model, then the Parties agree that this would represent a change to the Services, and if such change meets the definition of New Services, such request shall be handled subject to and in accordance with Section 4.3 of the MSA.
(c) During the Transition Period, Supplier agrees to make its *** management leads available to meet with CoreLogic and respond to CoreLogic's questions and provide guidance and information as requested by CoreLogic and to assist in the development of procedures in order to minimize the portions of the *** Management Services as that will be performed as *** Services. The Parties will mutually agree on such procedures and, once such procedures are agreed, Supplier shall promptly add such procedures to the Policy and Procedures Manual and begin to comply with such procedures. From time to time during the Term, if CoreLogic has additional questions regarding the *** Services portion of the *** Management Services, Supplier shall make its *** management leads available to respond to CoreLogic's questions and provide guidance and information as reasonably requested by CoreLogic.
(d) For clarity, during the period of performance of the Steady-State Transition Services and while the Parties are working to determine which portions of the *** Management Services will be performed as *** Services or *** Services pursuant to clause (b) above, Supplier agrees to continue to perform Security Management Services in the same manner in all material respects as CoreLogic performed for itself prior to the Supplement Effective Date (without interfering with Supplier's obligations set forth in Section 2.2 of Schedule A-10.3).
Supplier's performance of Change Management Services as *** Services shall not alter or limit Supplier's obligations or CoreLogic's rights related to changes under the Agreement (e.g., Section 9.6 of the MSA).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 17 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Service Area | Schedule and Section Reference | *** Services | *** Services |
| Contact Center Management & Support | Article 2 | | X |
| Supplier Interface Requirements | Article 3 | | X |
| Service Desk Operational Procedures | Article 4 | | X |
| Service Desk Training | Article 5 | | X |
| Service Desk Reporting | Article 6 | | X |
| End User Desktop Support & Messaging Services | Schedule A-2.6 | | X |
| End User Support Services | Article 2 | | X |
| Messaging Operations and Deployment Support | Article 3 | | X |
| Network Services | Schedule A-2.9 | | |
| LAN, WAN, Network Equipment | Section 1.3.1 | | X |
Firewall Support4 | Section 1.3.2 | | X |
| Telephony (VOIP) | Section 1.3.3 | | X |
| Data Center & Mainframe & Production Control & Monitoring Services | Schedule A-2.7 | | |
| Data Center Operations - CL Facilities | Section 1.2 | X | |
| Data Center Operations - Dell Facilities | Section 1.2 | | X |
| Mainframe Systems | Section 1.3 | | X |
| Production Management & Operations | Section 1.4 | X | |
| Production Control & Scheduling | Section 1.4.1 | X | |
| Monitoring | Section 1.4.2 | | X |
Server Services5 | Schedule A-2.4 | | |
| Server Support | Section 1.2.1 | | X |
| Server Administration | Section 1.2.2 | | X |
____________________
The Parties recognize that *** technologies may benefit CoreLogic's business. To the extent Supplier elects to use such technologies in the performance of the *** Services, such technologies shall be part of the Services at no additional charge. If CoreLogic requests the use of *** technologies that are not currently used by, or required for, the performance the Services, the achievement of the Service Levels and compliance with the CoreLogic Policy Sets, then Supplier will seek to incorporate such *** technologies into Supplier's *** Services offering. If Supplier is unable to incorporate such *** technologies into its *** Services offering within a timeframe that meets CoreLogic's business needs, and CoreLogic requires the incorporation of such *** technologies, at CoreLogic's election in its sole discretion, the Parties will arrange for the inclusion of the *** technologies as a change to the Services; provided that, to the extent such changes meet the definition of New Services, the Parties shall address such requirement in accordance with Section 4.3 of the MSA.
To be clear, CoreLogic retains sole control over the CoreLogic Data, Applications and Materials supported by Supplier through the Server Services that are provided as *** Services.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 18 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Service Area | Schedule and Section Reference | *** Services | *** Services |
| Clustering | Section 1.2.3 | | X |
| CoreLogic Cloud & Virtual Environment Support | Section 1.2.5 | X | |
| Private Cloud & Virtual Environments | Section 1.2.6 | | X |
| Managed Web Services | Section 1.2.7 | | X |
| Patch Management & Update | Section 1.2.8 | | X |
| Storage & Backup Services | Schedule A-2.6 | | X |
| Storage Management Requirements | Section 1.2.2 | | X |
| Storage Management Execution | Section 1.2.3 | | X |
| Storage Performance Monitoring | Section 1.2.4 | | X |
Backup & Restore Management6 | Section 1.2.5 | | X |
| Electronic Data Exchange Services | Schedule A-2.8 | | |
| Electronic Data Exchange Services | Section 1.2 | X | |
____________________
6 CoreLogic Personnel will be responsible for tape operations at remote locations (i.e., at CoreLogic sites outside of the CoreLogic Facilities listed in Schedule A-7).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 19 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.1
CROSS-FUNCTIONAL SERVICES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 20 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-2.1
Cross-Functional Services
| |
| 1.1.1 | Agreement. This Schedule A-2.1 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 1.1.4 | Overview. Supplier shall perform the cross-functional services, functions and responsibilities described in this Schedule as part of the Services (the “Cross-Functional Services”) and in connection with all of the Services described in Schedule A-2. |
| |
| 1.1.5 | Service Availability. Supplier shall provide the Services on a 24x7 basis; unless otherwise agreed by CoreLogic. |
| |
| 1.1.6 | Responsibilities. In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity. |
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party.
This Section details the obligations and responsibilities of the Parties regarding the management and prioritization of CoreLogic’s business objectives and requirements. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 21 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1 | Facilitate *** business assessment and strategy meetings to understand the needs of CoreLogic.
| P | |
| 1.2.2 | On a *** basis, facilitate a meeting with CoreLogic to understand and provide a service improvement plan that identifies opportunities to improve the Services to meet CoreLogic's current and future business requirements and goals. | P | A |
| 1.2 | Proactively work with CoreLogic to identify barriers to meeting Service Levels and make proposals to CoreLogic on eliminating the barriers.
| P | |
| 1.2.4 | Implement Services improvement plan as approved by CoreLogic. | P | |
| 1.2.5 | Monitor and track performance trends and provide to CoreLogic in accordance with Schedule A-12.
| P | |
| 1.2.6 | Proactively provide and implement improvement plans for Services which fail to meet Service Levels and reasonable expectations of CoreLogic.
| P | A |
| |
| 1.3 | STRATEGY AND ARCHITECTURE PLANNING |
This Section details the obligations and responsibilities of the Parties regarding the strategy and planning of the IT architecture. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.3.1 | Review and support the CoreLogic-defined IT operational and project architecture.
| P | |
| 1.3.2 | In collaboration with Supplier, ***, develop and update the three year enterprise technology roadmap and update the IT operational and project architecture.
| A | P |
| 1.3.3 | Provide annual recommendations regarding the CoreLogic enterprise technology roadmap based on Supplier’s best practices and industry best practices.
| P | |
| 1.3.4 | Adhere to the CoreLogic enterprise technology roadmap within the timeframe the Parties mutually agree and develop a written plan for architecture development initiatives to be conducted before the next CoreLogic technology roadmap review.
| P | |
| 1.3.5 | Participate in the CoreLogic architecture standards board (ASB) meetings. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 22 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
This Section details the obligations and responsibilities of the Parties regarding SOX and other *** compliance obligations. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.4.1 | Update and maintain compliance controls in accordance with CoreLogic provided practices, procedures and instructions. | P | |
| 1.4.2 | With respect to CoreLogic provided required *** controls, use Supplier's best practices to conduct periodic reviews and produce required evidence of compliance with such controls.
| P | |
| 1.4.3 | Review *** compliance processes and make recommendations for revisions to achieve higher pass rate for compliance audits and improve the efficiencies required to attain compliance. | P | |
| 1.4.4 | Review and approve Supplier recommendations for revisions to the *** compliance processes.
| | P |
| 1.4.5 | Review *** compliance documentation provided by CoreLogic that is related to the Services; remediate any deficiencies identified by Supplier.
| P | |
| |
| 1.5 | OPERATIONS DOCUMENTATION AND PROCESS REVIEW |
This Section details the obligations and responsibilities of the Parties regarding operations documentation and process review. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.5.1 | Develop, maintain, update, and provide to CoreLogic all available documentation on all operations, procedures, and Services which may become part of the Policy and Procedures Manual in accordance with Section 9.1(d) of the MSA.
| P | |
| 1.5.2 | On a *** basis, meet with CoreLogic to establish guidelines, objectives, and requirements for all documentation activities.
| P | A |
| 1.5.3 | On no less than *** basis, review with and make available to CoreLogic up-to-date versions of the Policy and Procedures Manual and associated documentation.
| P | |
| 1.5.4 | Review all delivered documentation and provide feedback.
| | P |
| 1.5.5 | On a *** basis, make recommendations to CoreLogic to improve CoreLogic processes that interface with Supplier processes.
| P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 23 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Project Management” shall mean the application of knowledge, skills, tools and techniques to Project activities in order to successfully meet Project requirements and goals, including the processes of initiating, planning, budgeting, executing, monitoring, controlling, reporting, correcting and closing each Project activity. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.6.1 | Manage and perform Projects using industry standard Project management methodologies commonly used by *** providers of IT services (e.g., PMBOK).
| P | |
| 1.6.2 | Develop Project plans to meet both the business and user requirements, including description, requirements, estimated durations/schedule, assumptions, constraints, budget, priorities, risks, one-time and ongoing charges, and Supplier Personnel required with estimated hours and their corresponding rates.
| P | A |
| 1.6.3 | Through Project management methodology communication mechanisms, provide communication on all Projects to governance team and impacted CoreLogic teams.
| P | |
| 1.6.4 | Provide Authorized Users access to tools and procedures used by Supplier for Project management.
| P | |
| 1.6.5 | Provide a consistent structure for portfolio/program/Project status reporting across multiple environments.
| P | A |
| 1.6.6 | Allocate and manage appropriate resources to tasks while providing for workload optimization in the provision of Services.
| P | |
| 1.6.7 | Identify risks and potential Incidents and Problems associated with each Project and make mitigation recommendations. Upon CoreLogic approval, implement recommended improvements.
| P | A |
| 1.6.8 | Track and report monthly, in accordance with Schedule A-12 or as mutually agreed to by CoreLogic, the progress of work, time spent, remaining work, budget variances and compliance with scheduled dates and Service Level requirements.
| P | A |
| 1.6.9 | Manage and obtain CoreLogic approval for changes necessary to meet required dates, requirements and budgets and make all CoreLogic-approved corrections.
| P | A |
| 1.6.10 | Maintain all documentation necessary to validate that all Projects meet all CoreLogic-provided *** compliance requirements.
| P | |
| 1.6.11 | Integrate with and provide overall coordination with CoreLogic business units, Third Party Contractors and other applicable third parties to meet Project objectives and schedules.
| P | |
| 1.6.12 | Evaluate Project management effectiveness and performance to recommend and, subject to CoreLogic approval, implement recommendations to improve Project management effectiveness.
| P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 24 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.6.13 | Coordinate and manage monthly portfolio reviews with appropriate CoreLogic staff to review schedule, scope, budget, critical issues and risk mitigation.
| P | |
| 1.6.14 | Define processes with CoreLogic for critical issues escalations and risk mitigations.
| P | A |
| 1.6.15 | Coordinate bi-weekly, or as required, joint status meetings on critical initiatives with CoreLogic Personnel.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 25 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.2
SERVICE MANAGEMENT SERVICES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 26 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-2.2
Service Management Services
| |
| 1.1.1. | Agreement. This Schedule A-2.2 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.1.2. | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.1.3. | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 1.1.4. | Overview. Supplier shall provide the service management services, functions, and responsibilities described in this Schedule (the “Service Management Services”) in connection with all of the Services described in Schedule A-2. |
| |
| 1.1.5. | Hours of Operation. Supplier shall deliver the Service Management Services on a 24x7 basis; unless otherwise agreed by CoreLogic. |
| |
| 1.1.6. | Responsibilities. In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity. |
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party.
| |
| 1.1.7. | Compliance with CoreLogic Policy Sets. For the avoidance of doubt, in accordance with Section 9.5(a)(i) of the MSA, Supplier shall perform all Services described in this Schedule A-2.2 in compliance with the CoreLogic Policy Sets (i.e., perform in accordance with the standards at least as high or protective as those set forth in the CoreLogic Policy Sets), as such CoreLogic Policy Sets are implemented in accordance with Section 9.5(a)(i) of the MSA. |
| |
| 2. | SERVICE STRATEGY & DESIGN |
This Section details the obligations and responsibilities of the Parties regarding the management of workload demands (“Demand Management”). Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the management of workload demands:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 27 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
2.1.1. | Define Demand Management policies and procedures related to Demand Management. | P | A |
2.1.2. | Supplier shall work with CoreLogic to create and analyze demand indicators | P | |
2.1.3. | Identify demand based on CoreLogic business requirements, historical trends and patterns of business activity, and produce a *** Demand Forecast.
| | P |
2.1.4. | On a *** basis, (i) facilitate a Demand Management meeting with CoreLogic and (ii) develop a Demand Forecast, using planning information provided by CoreLogic and capacity forecasting and historical trending information provided by Supplier.
| P | |
2.1.5. | On a *** basis, produce mapping of changes to business and service demand and integrate changes into the Demand Management process.
| P | |
2.1.6. | Monitor, track, and report ***, and in accordance with Schedule A-12, demand and capacity trends and changes, cost avoidance opportunities and, subject to CoreLogic approval, implement changes to capacity and Services to address and meet CoreLogic Demand Forecasts.
| P | A |
2.1.7. | On a *** basis, and in accordance with Schedule A-12, and through an agreed-upon measurement method, report on Demand Management effectiveness and performance.
| P | |
2.1.8. | Review Demand Forecasts. | | P |
| |
| 2.2.1. | Capacity Management, Planning, and Reporting |
This Section details the obligations and responsibilities of the Parties regarding updating the capacity management, planning and reporting. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with updating the capacity management, planning, and reporting:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 28 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.2.1.1 | Coordinate with Supplier and with CoreLogic teams, to perform Capacity Management. | P | |
| 2.2.1.2 | Establish a Capacity Management planning process, including using input and trending information from the Demand Forecast. | P | |
| 2.2.1.3 | On a monthly basis, and in accordance with Schedule A-12, for capacity Reports, collaborate and collect inputs related to capacity, Services, technology performance, business plans, procedures, processes, components, and related information from CoreLogic teams. | P | |
| 2.2.1.4 | Manage and monitor Services, components and resource capacity. | P | |
| 2.2.1.5. | Assess, analyze and communicate to CoreLogic, capacity impacts when adding, removing or modifying Services, and infrastructure components. | P | |
| 2.2.1.6. | Maintain capacity levels to support the Services provided to CoreLogic and to optimize use of existing IT resources and minimize CoreLogic costs. | P | |
| 2.2.1.7. | In accordance with the Demand Forecast and capacity utilization trends, provide adequate capacity within the environment, taking into account input gathered for the creation of capacity Reports, and daily, weekly, and seasonal variations in capacity demands based on CoreLogic business needs. | P | |
| 2.2.1.8. | Identify and in accordance with Schedule A-12, report risks, deficiencies, variances to thresholds and impacts related to capacity. | P | |
| 2.2.1.9. | Implement, configure and manage performance and workload monitoring Tools that allow for capacity monitoring and trending of the Systems. | P | |
| 2.2.1.10. | Proactively predict, analyze and communicate capacity deficiencies, risks, trends and impacts to CoreLogic. | P | |
| 2.2.1.11. | Recommend and, subject to CoreLogic approval, implement outcome of capacity action plans. | P | A |
| 2.2.1.12. | Provide capacity reporting in accordance with Schedule A-12. | P | |
| 2.2.1.13. | Provide CoreLogic access to *** capacity data on Services and associated infrastructure components, in accordance with the requirements of the Supplement. | P | |
| 2.2.1.14. | Evaluate Capacity Management effectiveness and performance. | A | P |
| |
| 2.3. | Availability Management |
| |
| 2.3.1. | Availability Management |
This Section details the obligations and responsibilities of the Parties regarding Availability management planning. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities: associated with Availability management
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 29 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.1.1. | Update Availability Management Plans and facilitate a meeting with CoreLogic, Supplier Personnel and applicable third parties to review the Services and Systems reliability and availability. | P | A |
| 2.3.1.2. | Propose and implement CoreLogic-approved and Supplier-controlled Availability management improvements. | P | A |
| 2.3.1.3. | On a *** basis, On a *** basis, evaluate and report, and in accordance with Schedule A-12, on Availability management effectiveness and performance. | P | |
| 2.3.1.4. | On a *** basis, analyze CoreLogic demand and capacity requirements to assess Availability within CoreLogic's environments (Services and Systems). | P | |
| 2.3.1.5. | Make recommendations to and, subject to CoreLogic approval, update Availability Management Plans, Services and Systems, and communicate with CoreLogic, Supplier Personnel and applicable third parties. | P | A |
| 2.3.1.6. | Define monitoring requirements, metrics, policies and Tools. | P | A |
| 2.3.1.7. | Investigate and conduct risk assessment and report in accordance with Schedule A-12, Incidents of non-Availability with improvement recommendations. | P | |
| |
| 2.4. | Service Level Management |
This Section details the obligations and responsibilities of the Parties regarding Service Level Management. Except where a responsibility is defined as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with reporting:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 30 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
2.4.1. | Perform Service Level reviews, analyze trends, and perform associated reporting in accordance with Schedule A-3. | P | |
2.4.2. | Schedule and facilitate meetings to review Service Levels on a *** basis or as otherwise agreed-upon. | P | |
2.4.3. | Implement Service Improvement Plans on Services which do not meet Service Level or Key Measurement standards in accordance with Schedule A-3. | P | A |
2.4.4. | Provide *** Service Improvement status updates to CoreLogic in accordance with Schedule A-3. | P | |
2.4.5. | ***, provide recommendations to CoreLogic Service Levels and Key Measurement tracking, procedures and processes to meet industry best practices. | P | |
2.4.6. | Subject to CoreLogic’s approval, implement where possible latest ITIL best practices into the CoreLogic relationship to meet best in class IT organization. | P | A |
2.4.7. | Align the Services to CoreLogic’s business and underpin the core business processes. | P | A |
2.4.8. | In collaboration with Corelogic, Implement ITIL best practices to help CoreLogic achieve the following: • improved Services • reduced costs • improved customer satisfaction through a more timely and professional approach to service delivery • improved productivity • improved use of skills and experience • improved delivery of third party service. | P | A |
2.4.9. | Partner with CoreLogic to create new Service Levels and Key Measurements or to promote Key Measurements into Service Levels. | P | |
2.4.10. | Partner with CoreLogic to create requested KPI’s that may progress into Service Levels or Key Measurements for Services provided. Define, develop, analyze and report, in accordance with Schedule A-12, to CoreLogic on a monthly basis. | P | A |
Without limiting Article 13 of the MSA, this Section details the obligations and responsibilities of the Parties regarding security operations with respect to security management. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 31 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
2.5.1. | Operate and maintain Data Leakage Protection (DLP) toolset to monitor and prevent unauthorized movement of CoreLogic Data across the network, email, file shares and end points. | P | |
2.5.2. | Operate and maintain data encryption capabilities including key management lifecycle. | P | A |
2.5.3. | Operate and maintain the Security Information Event Management (SIEM) System to correlate data events that are indicative of unauthorized and/or anomalous data behavior. Build a process around identification, communication and resolution of data security incidents. | P | A |
2.5.4. | Operate and maintain the file integrity monitoring System to monitor critical System files for changes. | P | |
2.5.5. | Operate and maintain the database monitoring Systems to log unauthorized activities on critical databases. Review logs and report anomalies at least daily. | P | |
2.5.6. | Operate and maintain the VPN environment to provide proper access. | P | |
2.5.7. | Operate and maintain the multi-factor authentication environment. | P | |
2.5.8. | Operate and maintain the password safe and secure critical System passwords. | P | A |
2.5.9. | Operate and maintain CoreLogic’s digital certificate environment. | P | |
2.5.10. | Operate and maintain Firewall audit System and produce a *** report, in accordance with Schedule A-12, to be reviewed by CoreLogic management. | P | A |
2.5.11. | Provide cost impacts and upon CoreLogic approval implement additional security methods. | P | A |
| |
| 2.6. | Access and Control Management |
Without limiting Article 13 of the MSA, this Section 2.6 details the obligations and responsibilities of the Parties regarding the control of and compliance with CoreLogic’s IT security policies. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities:
|
| | | |
| No. | Description | Supplier | CoreLogic |
2.6.1. | Perform network intrusion detection on the inscope security Infrastructure and at least ***ly, assess the types of Security Incidents that Supplier has observed and logged, identify security threat trends and adjust Security Incident and logging configurations in the Intrusion Detection and Prevention Systems to reflect such security threat trends and work to remedy Security Incidents. | P | |
2.6.2. | Use the ITSM Incident Management System and perform Security Incident response. | P | |
2.6.3. | Collaborate with and assist Corelogic with forensics and assist with security investigations. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 32 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
2.6.4. | Monitor, and evaluate vulnerabilities and assign criticality, and implement necessary actions. | P | |
2.6.5. | Identify and provide an Enterprise Security officer for direct interactions with the CoreLogic IT Security Team. | P | |
2.6.6. | Apply security patches to all in-scope Systems Software components, as permitted by CoreLogic during approved patching windows. | P | |
2.6.7. | On at least a *** basis and in accordance with the Service Levels and applicable performance targets, provide patch scanning and reporting, in accordance with Schedule A-12. | P | |
2.6.8. | Recommend and document security configuration for all in-scope Systems. | P | A |
2.6.9. | On a *** basis, perform evaluation of security configurations against approved security configurations. In accordance with Schedule A-12, report results and implement corrections. | P | A |
2.6.10. | Configure Systems Software to log security events to a centralized security information event manager (“SIEM”), including use of administrative rights. | P | |
2.6.11. | Provide security logs for reporting in accordance with Reporting Schedule XXand investigation and retain in line with CoreLogic policies. | P | |
2.6.12. | Aggregate and monitor security logs and restrict access to security logs to only CoreLogic-designated Supplier Personnel in order to prevent unauthorized modifications. | P | |
2.6.13. | Aggregate security logs in the SIEM, implement correlation rules to produce actionable intelligence from security logs near real time. Monitor and respond to security events. | P | |
2.6.14. | Configure and support web content filtering. | P | |
2.6.15. | Facilitate *** vulnerability scans and penetration tests on internal and Internet facing Equipment, assess output, and provide a risk assessment and propose for CoreLogic approval a remediation plan and activities required to remediate any vulnerabilities identified.
| P | |
2.6.16. | Control and manage Supplier administrative accounts. Apply multi-factor authentication, when required by CoreLogic policies. | P | |
2.6.17. | On a *** basis, or as required for necessary audits, audit administrative accounts, and re-certify access. | P | |
2.6.18. | Make security processes and configurations applicable to the Systems and CoreLogic Data available to CoreLogic at all times. | P | |
2.6.19. | Recommend and comply with CoreLogic’s physical security requirements for the Designated CoreLogic Data Centers. | P | |
2.6.20. | With mutual agreement, and as scoped within the project, provide security support/consultation for projects | P | |
2.6.21. | As scoped and agreed, execute IT Infrastructure projects related to security management | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 33 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
2.6.22. | Develop and implement a SIRP in accordance with Section 13.2(b)(iii) of the MSA and report Security Incidents to CoreLogic in accordance with Sections 13.2(b)(iii) and 13.3(e) of the MSA.
| P | A |
2.6.23. | Establish policies and procedures for assigning, resetting and disabling IDs and passwords used for data or System access by Authorized Users and perform *** reviews.
| | P |
2.6.24. | Make recommendations to the policies and procedures for assigning, resetting and disabling IDs and passwords used for data or System access by Authorized Users. | P | A |
2.6.25. | Create, modify, disable, and delete Authorized User accounts (e.g. Active Directory, Application) and assign and change passwords of Authorized Users. | P | |
2.6.26. | Adhere to and confirm compliance with CoreLogic policies regarding assigning and resetting, as needed, user passwords. | P | |
2.6.27. | When provided with Authorized User-completed forms requesting new or modified log-on IDs and passwords, respond to access requests within the applicable time frames and as necessary to meet the Service Levels. Suspend and delete inactive log-on IDs in accordance with CoreLogic security policies. | P | |
2.6.28. | Coordinate the creation, change, and deletion of Authorized User accounts (for example, perform account set-up, password resets, account deletions, and terminations) per Service Requests and in accordance with CoreLogic’s security policies. | P | |
2.6.29. | Coordinate and cooperate with the Service Desk and applicable Third Party Contractors to Resolve password related Incidents and Problems. | P | |
This Section details the obligations and responsibilities of the Parties regarding security audits and reporting. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities:
|
| | | |
| No. | Description
| Supplier | CoreLogic |
2.7.1. | Perform security audits in accordance with the Agreement (e.g., Section 9.10 of the MSA) (a) Cooperate and assist with CoreLogic-approved audit self-assessments *** and as needed; (b) Provide written responses to both internal and external technology audits by CoreLogic, CoreLogic's clients or applicable regulators, including necessary responses which may be incorporated into internal technology health checks; (c) Provide both hard copy and soft copy of security Reports ***, in accordance with Schedule A-12, or within such timeframe as CoreLogic may reasonably request.
| P | A |
2.7.2. | Run tests and checks to identify accounts that should be removed in accordance with CoreLogic security and legal hold policies. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 34 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 2.8. | Access Administration. |
This Section details the obligations and responsibilities of the Parties regarding access administration. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities:
|
| | | |
| No. | Description
| Supplier | CoreLogic |
2.8.1. | Develop access requirements for all Systems, networks, Applications, System files and CoreLogic Data. | | P |
2.8.2. | Conduct user management for all Authorized User accounts. Conduct Authorized User on-boarding, transfers, and terminations in accordance with the Service Levels and security protocols. Review Authorized User access certifications on a *** basis. Migrate application user repositories into the authoritative user repository source.
| P | A |
2.8.3. | Provide access requirements and procedures for all Systems, networks, Applications, Software, System files, and CoreLogic Data and notify Supplier of the entities and personnel that will be granted access to the Systems and the level of security access granted to each. | | P |
2.8.4. | Manage and administer access to Systems, networks, Applications, Software, System files and CoreLogic Data. | P | |
2.8.5. | Utilizing tools provided by CoreLogic, maintain existing secure online database of all access requests, access rights, and approval authorities. | P | |
2.8.6. | In accordance with the CoreLogic policies, monitor Authorized Users of the Systems and Services for authorized access, and log, track, and respond to violations and track using the Incident Management System. | P | |
2.8.7. | Capture data regarding routine access and exceptions for audit trail purposes, and make such data available to CoreLogic upon CoreLogic’s request in accordance with Section 13.2(a) of the MSA. | P | |
2.8.8. |
Prepare and retain documentation of breach investigations (including appropriate logging) and provide copies to CoreLogic.
| P | |
2.8.9. | Establish and administer procedures to monitor and control remote access ( e.g. VPN, ***) to CoreLogic Network.
| P | A |
2.8.10. | Coordinate with the Service Desk and all applicable Third Party Contractors to Resolve Incidents and Problems related to access to Systems, networks, Applications, Software, System files, and CoreLogic Data. | P | |
| |
| 2.9. | Virus Protection Administration. |
This Section details the obligations and responsibilities of the Parties regarding virus protection administration. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 35 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 2.9.1. | Install, operate, maintain and regularly update CoreLogicprovided virus protection tools on all Systems that prevent:
(a) Destruction, corruption or facilitation of the theft of data or Software;
(b) unauthorized disabling or locking of all Software or Systems; or (c) Use of undocumented or unauthorized access methods for gaining access to Software, other resources or CoreLogic Data for all Systems. | P | |
| 2.9.2. | Install, operate and maintain appropriate CoreLogic-provided virus protection Software, on designated Systems that are used to deliver or support the Services. | P | |
| 2.9.3. | Update virus protections Software as directed by CoreLogic, in “emergency situations” as defined by CoreLogic. | P | A |
| 2.9.4. | Update virus-protection Software in accordance with Section 9.7 of the MSA.
| P | A |
| 2.9.5. | Respond to virus Incidents upon detection of a virus, by performing the following:
(a) Taking immediate steps to use the Incident Management process for notification in accordance with SIRP.
(b) Assessing the scope of damage;
(c) Stopping the spread and progressive damage from the virus in accordance with Section 9.9 of the MSA;
(d) Eradicating the virus in accordance with Section 9.9 of the MSA; and
(e) In accordance with Section 9.9 of the MSA, restoring all data and Software. Supplier shall coordinate and cooperate with any necessary Third Party Contractors to Resolve virus-related Incidents and Problems. | P | |
| 2.9.6. | Immediately notify CoreLogic designated Authorized Users pursuant to the SIRP when viruses are identified by Supplier in CoreLogic’s environment, describing the Incident involving the virus and what measures Supplier has taken or will take to prevent recurrence. | P | |
| 2.9.7. | Mitigate the risks of System contamination caused by viruses by using virus detection and eradication Software programs in association with each installation, relocation or maintenance action of any Software. | P | |
| 2.9.8. | Provide alerts to Authorized Users regarding current virus threats either specific to CoreLogic’s environment, encountered in Supplier’s environment, or based on industry information. | P | |
| 2.9.9. | Using tools provided by CoreLogic, manage antivirus solution for both Server and CoreLogic workstations. | P | |
| |
| 2.10. | Physical Security Administration. |
This Section details the obligations and responsibilities of the Parties regarding physical security administration. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 36 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
2.10.1. | Install and maintain physical security Software at Supplier’s Facilities. Update such Software in accordance with Section 9.7 of the MSA. | P | |
2.10.2. | Maintain a secure and controlled physical environment for any entrusted Supplier-held CoreLogic information and CoreLogic Data. | P | |
2.10.3. | Develop, maintain, update on a *** basis, and implement physical security procedures in accordance with CoreLogic policies.
| P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 37 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
This Section details the obligations and responsibilities of the Parties regarding the Change Management Process and service assurances. The “Change Management Process” means the process controlling the lifecycle of all changes to the Systems. The primary objective of Change Management is to enable beneficial System changes to be made with minimum disruption to the Services and CoreLogic’s business operations. The Change Management Process is designed to manage the risks associated with a given Change Request.
| |
| 3.1.1. | Change Management Framework. |
This Section details the obligations and responsibilities of the Parties regarding Change Management framework. The Supplier ITSM tool and Change Management procedures are generally assumed for all the tasks. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the Change Management framework:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 38 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 3.1.1.1 | Review and implement Change Management procedures and policies approved by CoreLogic. | P | A |
| 3.1.1.2 | Establish Change authorization process for the Services. | P | A |
| 3.1.1.3 | Complete impact assessment, prioritization and risk classification for Changes. | P | |
| 3.1.1.4 | Document and classify proposed Changes to the Systems, including but not limited to risk, impact and back out plans, and establish Release Management plans for major changes. | P | |
| 3.1.1.5 | Develop and maintain a schedule of planned Changes and provide to CoreLogic for review. | P | A |
| 3.1.1.6 | Publish and grant CoreLogic access to forward schedule of Change calendar. | P | |
| 3.1.1.7 | Adhere to CoreLogic approved change windows. | P | |
| 3.1.1.8 | Provide and implement procedure and tools to classify all changes, including planned maintenance activities. | P | |
| 3.1.1.9 | Implement a process and tools for CoreLogic to pre-approve agreed-upon types of Changes. | P | A |
| 3.1.1.10 | Specify process purpose, scope, goals, pre/post testing, and capabilities in accordance with CoreLogic’s Change Management practices. | | P |
| 3.1.1.11 | Assist in specifying process purpose, scope, goals, and capabilities that align with CoreLogic’s Change Management practices. | P | |
| 3.1.1.12 | Recommend and, subject to CoreLogic approval, define Change Management policies, standards, and conceptual models reporting requirements, roles and responsibilities. | P | A |
| 3.1.1.13 | Evaluate, recommend and, on a *** basis and, subject to CoreLogic approval, implement Change Management improvements to effectiveness and performance.
| P | A |
| 3.1.1.14 | Recommend and, subject to CoreLogic approval, implement procedures, measurement and control definitions, and performance evaluations of the Change Management process. | P | A |
| 3.1.1.15 | Provide an audit trail related to the progression of the change record through the various stages of the Change Management process. | P | |
| 3.1.1.16 | Provide ability for an emergency change process. | P | A |
| 3.1.1.17 | Provide CoreLogic, CoreLogic’s joint ventures and their Third Party Contractors CoreLogic-approved access, and company separation, to Supplier’s ITSM System in order to submit, review, approve, and update Change Requests. | P | A |
| 3.1.1.18 | Provide training to CoreLogic on usage of the ITSM System. | P | |
| |
| 3.1.2. | System Change Requests. |
This Section details the obligations and responsibilities of the Parties regarding the acceptance of Change Requests relating to the Systems. Except where a responsibility is identified as a “P” responsibility for CoreLogic in
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 39 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
the matrix below, Supplier shall be responsible for the following activities associated with the acceptance of System Change Requests:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 3.1.2.1 | Classify Change Requests. | P | A |
| 3.1.2.2 | Update all required fields including but not limited to priority and impact categorization. | P | |
| 3.1.2.3 | Initiate Change Requests in support of in-scope Services. | P | A |
| 3.1.2.4 | Approve Change Requests relating to the Systems. Report in accordance with Schedule A-12, to CoreLogic changes rejected by Supplier or CoreLogic. | P | A |
| 3.1.2.5 | Manage, coordinate and conduct post-implementation System Change review and validation. | P | |
| 3.1.2.6 | Provide Change documentation as required for Changes to in-scope Services. | P | |
| 3.1.2.7 | Modify and close Change Requests relating to the Systems. | P | |
| 3.1.2.8 | Provide CoreLogic full access to Change Management System to support internal CoreLogic Changes-and related processes, including running appropriate and agreed upon Change Advisory Board (CAB)meetings. | P | |
| |
| 3.1.3. | System Change Assessment. |
This Section details the obligations and responsibilities of the Parties regarding the assessment of Change Requests relating to the Systems. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the assessment of System Change Requests:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 3.1.3.1 | Assess and escalate for CoreLogic approval (if required by the Change Management process) System Change Requests for business impacts. | P | A |
| 3.1.3.2 | Assess the Change based on the System Change risk using Supplier and the CoreLogic risk Change Management criteria. Escalate and report System Changes that are deemed high risk to the Change Advisory Board for exception, approval or rejection. If deemed an emergency, follow emergency approval process as defined in the Change Management procedures. | P | A |
| 3.1.3.3 | Collect and deliver System Change assessment results and issues. | P | |
| 3.1.3.4 | Assess System Change approach, testing plan and schedule. | P | |
| 3.1.3.5 | With participation by CoreLogic, conduct an impact assessment of Applications and Systems that need to be updated as a result of proposed System Changes. | P | A |
| 3.1.3.6 | For internal CoreLogic CAB meetings, generate required reporting, in accordance with Schedule A-12. | P | |
| 3.1.3.7 | Identify, assess, recommend and Resolve schedule conflicts due to changes submitted by CoreLogic internal staff. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 40 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 3.1.4. | System Change Approval and Scheduling. |
This Section details the obligations and responsibilities of the Parties regarding the approval of Change Requests relating to the Systems. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the approval of System Change Requests:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 3.1.4.1 | Facilitate the Change Management process and enable compliance with the Change Management procedures. Supplier will have a System Change manager who shall act as lead facilitator for the CAB meeting(s). | P | A |
| 3.1.4.2 | Schedule, facilitate, participate and host Change Management meetings to include review and approval, of planned Changes and results of implemented Changes. | P | A |
| 3.1.4.3 | Review results of Change assessments. | | P |
| 3.1.4.4 | Provide advance notifications of System Change Requests. | P | A |
| 3.1.4.5 | Assign and manage System Change Requests for implementation. | P | |
| 3.1.4.6 | Update System Change schedule (within System Change Request based on outcome of CAB meetings). | P | A |
| 3.1.4.7 | Install and validate System Changes promoted to CoreLogic’s Systems. | P | A |
| 3.1.4.8 | Evaluate, recommend changes to and, subject to CoreLogic approval, implement documented operational readiness review steps. | P | A |
| 3.1.4.9 | Organize, facilitate and document CAB meetings as follows: (a) organize CAB meeting with appropriate stakeholder participation based on Request for System Change; (b) facilitate CAB meeting; (c) document CAB decisions; and (d) log CAB decisions in the ITSM system. | P | A |
| 3.1.4.10 | Maintain System Change calendar and coordinate with appropriate CoreLogic resources. | P | |
| 3.1.4.11 | Validate System Change operations readiness review and implementation. | P | |
| 3.1.4.12 | Schedule System Changes to minimize business disruption and escalate for CoreLogic approval (if required by the Change Management procedures). | P | A |
| 3.1.4.13 | Identify, assess, recommend and Resolve schedule conflicts due to changes submitted by CoreLogic internal staff. | P | |
| 3.1.4.14 | Monitor Changes and report results and impacts of Changes. | P | |
| 3.1.4.15 | Along with CoreLogic participation (as required), verify that Change met objectives and Resolve negative impact from the Change. | P | |
| |
| 3.2. | Asset and Configuration Management. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 41 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
This Section details the obligations and responsibilities of the Parties regarding the management and maintenance of the Equipment and Software, including the creation and utilization of the Asset Management Inventory database. The “Asset Management Inventory” shall mean the detailed and up-to-date record of all CoreLogic Equipment and Software and any Supplier Equipment and Software used to deliver the Services; provided that, with respect to Supplier’s performance of Managed Services only, CoreLogic’s use of such Supplier Equipment and Software information shall not limit Supplier’s rights with respect to Managed Services as set forth in Section 9.5(a)(iii) of the MSA. The Asset Management Inventory shall include the information set forth in the Policy and Procedures Manual.
The Asset Management Inventory Database shall be used to assist Supplier in updating the Incident, change and Problem management system for use by the Service Desk and other parties to meet CoreLogic’s business requirements; to update the CoreLogic asset inventory system; to trace historical IMAC, Incident, Change, request and break/fix activities; and to track the use and distribution of Software and Equipment (collectively, “Asset Management”).
Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the management and maintenance of the Equipment and Software:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 3.2.1.1 | Define Asset Management Inventory processes and document in the Policy and Procedures Manual. | P | A |
| 3.2.1.2 | Establish and maintain the Asset Management Inventory. | P | |
| 3.2.1.3 | Electronically collect asset information regardless of location. | P | |
| 3.2.1.4 | Using an initial inventory performed by Supplier and other information provided by CoreLogic as well as information obtained via Supplier’s Tool, enter Systems and Software information in the Asset Management Inventory database. | P | |
| 3.2.1.5 | As Changes occur, update the Asset Management Inventory. This includes dynamic changes (e.g. ***, Clusters, HA).
| P | A |
| 3.2.1.6 | Configure, deploy and maintain required agents and technology for electronic gathering of asset information. | P | |
| 3.2.1.7 | Audit and report ***, in accordance with Schedule A-12, on all assets captured and logged within the Asset Management Inventory database.
| P | |
| 3.2.1.8 | Perform electronic inventories of CoreLogic EUC Devices and Systems and utilize this information to maintain the Asset Management Inventory. | P | A |
| 3.2.1.9 | Import Authorized User information from authorized payroll Systems to associate with end user asset data. | P | A |
| 3.2.1.10 | Provide CoreLogic access or data extracts to the updated Asset Management Inventory on the frequency set forth in the Policy and Procedures Manual, and as requested. | P | |
| 3.2.1.11 | Verify the accuracy of the Asset Management Inventory on a *** basis by conducting a sample audit in accordance with Schedule A-3 and coordinate audit results with CoreLogic.
| P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 42 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 3.2.1.12 | Leverage the Asset Management Inventory to identify opportunities to redeploy and refresh assets as appropriate and to make other recommendations for improvements and cost reductions. | P | A |
| 3.2.1.13 | In accordance with Schedule A-12, provide Asset Management Inventory reporting. | P | |
| 3.2.1.14 | Use the Asset Management Inventory to recommend refreshes, as needed. | P | |
| 3.2.1.15 | Maintain Asset Management Inventory Database and related changes during the lifecycle of the Asset | P | |
| 3.2.1.16 | ***, evaluate Asset Management effectiveness and performance, recommend and, subject to CoreLogic approval, implement Changes to Asset Management based on such evaluation.
| P | A |
| 3.2.1.17 | Update records in the Asset Management Inventory as a result of IMACs or other Changes. | P | |
| 3.2.1.18 | Sync Asset Management Inventory with CMDB near real-time. | P | |
| 3.2.1.19 | On a *** basis, review Asset Management Inventory and CMDB; reconcile differences as required.
| P | |
| 3.2.1.20 | Provide Supplier with *** forecast of CoreLogic Equipment planned procurements.
| | P |
| 3.2.1.21 | Provide CoreLogic with non binding *** forecast of Equipment replacements or refreshes, and timelines as requested by CoreLogic or known by Supplier.
| P | A |
| 3.2.1.22 | Update and maintain Asset Management Inventory with CoreLogic-owned asset information. | P | |
| 3.2.1.23 | Using CoreLogic-provided processes, confirm that proper procurement operating procedures are followed when requesting CoreLogic-provided Equipment. | P | |
| 3.2.1.24 | Tag all new CoreLogic physical assets deployed by Supplier and create an asset record in the Asset Management Inventory prior to deploying into production. | P | A |
| 3.2.1.25 | Track assets in the Asset Management Inventory as per fields agreed-upon by Supplier and CoreLogic. | P | A |
| 3.2.1.26 | In accordance with Section 9.10(d) of the MSA, manage and assist in CoreLogic third party software and hardware vendor audits, reviews and true-ups. | P | |
| 3.2.1.27 | Decommission assets as requested by CoreLogic and in accordance with CoreLogic standards and in meeting all vendor requirements. | P | |
| 3.2.1.28 | Provide training to CoreLogic on usage of the ITSM System. | P | |
| |
| 3.2.2. | Configuration Management |
This Section details the obligations and responsibilities of the Parties regarding Configuration Management. “Configuration Management” shall mean the process of creating and being responsible for maintaining up-to-date documentation of Configuration Items and Systems which consist of products and version, release definitions and standards required to deliver the Services, including their interrelationships. This
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 43 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
information is managed throughout the lifecycle of the Configuration Item. The primary objective of Configuration Management is to support the delivery of the Services by providing accurate data to the Service Management processes. “Configuration Item” or “CI” shall mean any component that needs to be managed, or required by CoreLogic, in order to deliver a Service, including but not limited to hardware, Software, buildings, people, and formal documentation such as process documentation and Service Levels. Information about each CI is recorded in a configuration record within the Configuration Management Database. CIs are under the control of the Change Management Process.
Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the Configuration Management:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 3.2.2.1 | Define, implement and maintain Configuration Management policies, CI relationships and dependency mapping, tools (i.e., Dell’s Configuration Management Database). | P | A |
| 3.2.2.2 | Create and maintain a CMDB reference architecture for all Systems Configuration Items related to the Services and provide to CoreLogic. | P | |
| 3.2.2.3 | Update the CMDB, utilizing electronic mechanisms whenever possible, in alignment with the Change Management Procedures.
| P | |
| 3.2.2.4 | At least ***, review that the information in the CMDB is current, accurate and complete and that all identified inaccuracies with CIs are corrected in a timely manner. Provide CoreLogic assessment and results.
| P | |
| 3.2.2.5 | Manage and review Configuration Management activities of Systems and report Configuration Management results in accordance with Schedule A-12.
| P | |
| 3.2.2.6 | Provide CoreLogic CMDB information so that CoreLogic can access agreed-upon CIs, business-related CIs, CI relationships and dependency maps.
| P | |
| 3.2.2.7 | Define and implement a CoreLogic-approved process and security for CoreLogic to access, update and maintain CoreLogic related CI business information and associated data within the CMDB.
| P | A
|
| 3.2.2.8 | Proactively monitor expiring CIs and report, in accordance with Schedule A-12, to CoreLogic. Assist Third Party Contractors and CoreLogic to keep the information current.
| P | |
| 3.2.2.9 | Define, manage and maintain CIs between the CMDB and CoreLogic-managed sources to provide for integration to the CMDB through manual or automated means.
| P | |
| 3.2.2.10 | Control and log Configuration Item modifications under a consistent process that supports the integrity of the CMDB, CI relationships and dependency maps and follows the Change Management Process.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 44 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 3.2.2.11 | Provide Configuration Item activity reporting as outlined in accordance with Schedule A-12. | P | |
| 3.2.2.12 | Develop, maintain, recommend Systems Changes to and, subject to CoreLogic approval, implement such Systems Changes to the configuration standards. | P | A |
| 3.2.2.13 | Define, maintain and support a process to handle exceptions to approved configuration standards, and document in the Policy and Procedures Manual. | P | |
| 3.2.2.14 | Review (including review of alternatives to maintain the CoreLogic Standards) and submit to CoreLogic for its approval, exceptions to approved configuration standards.
| P | A |
| 3.2.2.15 | Conform to configuration standards with exceptions approved by CoreLogic. | P | A |
| 3.2.2.16 | Monitor and regularly report to CoreLogic compliance with exceptions to the configuration standards and in accordance with Schedule A-12. | P | |
| 3.2.2.17 | Provide CoreLogic, and in accordance with Schedule A-12, the delta between current and approved state of CI’s. | P | |
| 3.2.2.18 | Provide training to CoreLogic on usage of the ITSM System. | P | |
This Section details the obligations and responsibilities of the Parties regarding Release Management. “Release Management” shall mean the process of deploying Software and hardware across the IT Infrastructure environment and Services. The primary objective of Release Management is to ensure content integrity and consistency throughout the release and ensure the release does not cause problems in the production environment.
Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the Release Management:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 45 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 3.3.1. | Review and approve Release Management procedures and policies. | | P |
3.3.2. | Develop and implement Release Management processes in alignment with CoreLogic processes. | P | |
3.3.3. | Maintain content integrity and consistency through all stages of the Release Management process and distributing, installing and activating approved CIs. | P | |
3.3.4. | Configure, install/release Systems, Software Upgrade releases, patches, fixes, emergency fixes and major Upgrade releases. | P | |
3.3.5. | In accordance with release procedures, record approved changes in the CMDB. | P | |
3.3.6. | Test all releases and validate that post testing meets the release requirements. | P | |
3.3.7. | Coordinate and manage post-release validation efforts with CoreLogic, when required. | P | |
3.3.8. | Schedule and plan releases in conjunction with CoreLogic. | P | |
3.3.9. | Communicate in advance of release to CoreLogic and prepare for releases. | P | |
3.3.10. | In accordance with Change Management and Release Management, distribute and install releases.
| P | |
3.3.11. | Provide training to CoreLogic on usage of the ITSM System. | P | |
| |
| 3.4. | Software License Management |
This Section details the obligations and responsibilities of the Parties regarding the management of CoreLogic’s Software licenses. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the management of CoreLogic’s Software licenses:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 46 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
3.4.1. | Implement a process to capture required data of all Software license information for Software introduced into the CoreLogic IT environment by Supplier (e.g., all Software distributed to the CoreLogic IT environment by Supplier).
Supplier shall integrate license information (e.g., per-user limits, concurrent licenses, number of processors on which Software is installed, versions, per-seat limits, license type, vendor) provided by CoreLogic into the CMDB in order to assist CoreLogic in tracking usage of Software licenses for Data Centers and Remote Sites. | P | |
3.4.2. | Manage and report the Software license data, *** or as requested by CoreLogic, for Systems and advise CoreLogic of any differences from the licensing limits provided by CoreLogic.
| P | |
| | Coordinate and collaborate with CoreLogic and proactively advise CoreLogic of capacity issues (e.g., reporting numbers of Software licenses). | P | |
3.4.3. | Validate Software licensing, secure approvals and confirm compliance with CoreLogic prior to implementation of additional Software by Supplier. | P | A |
3.4.4. | Report availability and existence of Software licenses to CoreLogic. | P | |
3.4.5. | Provide updated Software license counts when Equipment is commissioned and decommissioned or Software is installed or de-installed. | P | |
3.4.6. | Maintain and report information regarding CoreLogic business approvals for new or additional Software, as required by CoreLogic. | P | |
3.4.7. | Maintain contract compliance for CoreLogic-owned Software from Supplier-supplied information. | | P |
3.4.8. | Assist CoreLogic with Software license compliance should CoreLogic be audited by a third party, and assist CoreLogic in providing Software license true-up for Software, as requested by CoreLogic. | P | |
3.4.9. | Recommend *** Software license management improvement and cost efficiencies related to Services.
| P | A |
3.4.10. | Provide training to CoreLogic on usage of tools and processes of Software licensing management. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 47 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
This Section details the obligations and responsibilities of the Parties regarding the management of requests for Services made to the Service Desk. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the management of requests for Services made to the Service Desk:
|
| | | |
| No. | Description | Supplier | CoreLogic |
4.1.1. | Define, develop and maintain and review, on a *** basis, an up-to-date Service Catalog (Business and Infrastructure Service Catalog) that meets the requirements of CoreLogic.
| P | |
4.1.2. | Monitor the status of the resolution of Service Requests in alignment with the applicable performance levels. | P | |
4.1.3. | Communicate with the Authorized Users during the Service Request lifecycle to provide current status of request and Restoration/Resolution confirmations. | P | |
4.1.4. | Maintain and update Supplier’s web-based self-service portal to allow Authorized Users to track the status and progress of Incidents and Service Requests.
| P | |
4.1.5. | Initiate Service Requests through contacts with the Service Desk or Supplier’s web-based self-service portal. | | P |
4.1.6. | Escalate Service Requests through the CoreLogic-approved escalation and notification matrix should standard Service Request timelines not be met or acceptable. | P | |
4.1.7. | Identify to Supplier those CoreLogic Personnel who are required to approve a Service Request and the circumstances under which such approvals are required with updates on a regular basis. | | P |
4.1.8. | Validate approvals have been obtained for Service Requests. | P | |
4.1.9. | Provide input for updates to the Service Catalog, along with associated approval levels and approvers, as well as approved vendors and pricing. | | P |
4.1.10. | Update the Service Catalog when components are added, retired or updated, and communicate all such updates to Service Desk, CoreLogic end users and requested support personnel.
| P | |
4.1.11. | Establish online form to request, authorize and track creation, termination and transfer of Authorized User access, to include, Application, hardware, wireless, facilities and Systems access. | P | |
4.1.12. | Design, configure, install, and maintain custom CoreLogic Service Catalogs only viewable by certain CoreLogic business units. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 48 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
4.1.13. | Provide Service Request System Change Log and activity reporting in accordance with Schedule A-12 (Reports). | P | |
4.1.14. | Supplier to recommend and, subject to CoreLogic approval, implement processes and governance for the addition and retirement of Service Catalog items. | P | A |
4.1.15. | Supply Service Request performance reporting no less than *** in accordance with Schedule A-12 (Reports)
| P | |
4.1.16. | Provide CoreLogic, CoreLogic’s joint ventures and their Third Party Contractors, CoreLogic-approved access to Supplier’s ITSM System in order to submit, view and update Service Requests. | P | A |
4.1.17. | Provide training to CoreLogic on usage of the ITSM System. | P | |
4.1.18. | Provide appropriate access to CoreLogic authorized users to submit and view status of tickets on behalf of others (e.g., admins of senior level executives). | P | |
| |
| 4.2. | Incident and Problem Management Process. |
This Section details the obligations and responsibilities of the Parties regarding the process for managing Incidents and Problems administered. Incidents and Problems are categorized into Severity Levels.
Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the process for managing Incidents and Problems:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| | Implement and manage an Incident Management and Problem Management process that facilitates coordination across Service areas, functions, business units, Service locations, geographic regions, and third parties. | P | A |
4.2.1. | Align Incident Management activities to the defined Change Management procedures. | P | |
4.2.2. | Provide Level 1, 2 and Level 3 Incident Restoration and Problem Resolution for in-scope Services. | P | |
4.2.3. | Maintain Incident and Problem Management processes and lifecycle to facilitate and coordinate Incident Restoration and Problem Resolution. | P | |
| | Confirm that all Incidents are Restored and Problems are Resolved and compliant with applicable performance levels. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 49 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.1.3. | Communicate to CoreLogic and appropriate third parties throughout the Incident and Problem Management lifecycle, identify issues with communication, notify CoreLogic of such issues, follow up such issues to Resolution and closure. | P | |
| 1.1.4. | Employ mutually agreed Incident and Problem escalation processes utilizing ITIL methodology and guidelines. | P | A |
| 1.1.5. | Identify and analyze Incident and Problem trends and produce a *** trending and exceptions Report. Make recommendations to mitigate similar types of Incidents and Problems for the future in accordance with Schedule A-12 (Reports).
| P | |
| 1.1.6. | Recommend and implement, subject to CoreLogic approval, Incident and Problem Management improvement recommendations. | P | A |
| 1.1.7. | Assess and communicate impact of CoreLogic-approved Incident and Problem Management improvement recommendations. | P | |
| 1.1.8. | Monitor impact, outcome, trends and results of CoreLogic-approved Incident and Problem Management improvement recommendations. | P | |
| 1.1.9. | Lead and manage the Root Cause Analysis for applicable Severity Level 1 and Severity Level 2 Incidents. Produce Problem Management record and RCA document in alignment with agreed-upon Service Levels. | P | |
| 1.1.10. | Provide access to Incident and Problem Management tools and data to CoreLogic and appropriate third parties throughout the Incident Management, Problem Management and Service Request lifecycles. | P | |
| 1.1.11. | Perform initial Incident determination to assess impact and Restoration activities (i.e., upon receipt of Incident, conduct initial review of the Incident to determine the Severity Level and proper course for Resolution). | P | |
| 1.1.12. | Reset Incident Severity Levels as approved by CoreLogic Authorized Users. | P | A |
| 1.1.13. | Log, track and facilitate documentation of all elements (e.g., workarounds, known error database, ad hoc reporting for analysis) related to Incidents and Problem records. | P | |
| 1.1.14. | Notify impacted Authorized Users. Coordinate with CoreLogic and applicable third parties to assess the Incident and develop a work plan for Restoration. | P | |
| 1.1.15. | Provide training to Supplier Personnel to enhance troubleshooting skills for the provision of Services. | P | A |
| 1.1.16. | Implement checks and audits and communicate results to CoreLogic to verify that Supplier Personnel are complying with processes and procedures. | P | |
| 1.1.17. | Maintain communications and provide status updates to Authorized Users, affected persons and, as necessary, appropriate third parties. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 50 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.1.18. | Maintain communication protocols in accordance with defined Service Levels on all Severity 1 and Severity 2 incidents. | P | |
| 1.1.19. | Close Incident Tickets when the Authorized User confirms that the Services have been restored. For Incidents that have not been initiated by an Authorized User, actions will be taken based on applicable Resolution procedures. | P | |
| 1.1.20. | Review open and closed Incidents and Problems with technical teams to identify FAQs. Recommend and, subject to CoreLogic approval, add, remove or update FAQs in Supplier's knowledge repository and self-help website on a *** basis.
| P | A |
| 1.1.21. | Re-code and re-open incorrectly closed or incorrectly coded Incident Tickets and Problem Tickets. | P | |
| 1.1.22. | On a *** basis, evaluate Incident Management effectiveness and performance in line with the trending analysis
| P | |
| 1.1.1.1. | Provide training to CoreLogic on usage of the ITSM System. | P | |
This Section details the obligations and responsibilities of the Parties regarding the management of Incidents(“Incident Management”). Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the management of Incidents:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.1.23. | Provide ongoing review of Incident metrics to identify Problems. Develop or recommend corrective and preventative actions to address and mitigate such trends and Problems. | P | |
| 1.1.24. | Resolve Incidents in accordance with Service Levels and in a timely manner for Incidents not covered by the Service Levels. | P | |
| 1.1.25. | Follow Incident Management processes and procedures.
| P | |
| 1.1.26. | Perform active, proactive and reactive troubleshooting in connection with Incidents. | P | |
| 1.1.27. | If an Incident cannot be Resolved, escalate to the appropriate service personnel. | P | |
| 1.1.28. | Provide Incident Management and tracking for external issues impacting the CoreLogic environment (e.g., Social Security system outage). | P | |
| 1.1.29. | Provide necessary 24x365 Incident response to automated alerts and reported issues. | P | |
| 1.1.30. | Provide in-scope Incident support and management on a 24x365 basis. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 51 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.1.31. | Facilitate, govern and oversee Resolution of all Incidents, identify issues with Resolution of Incidents (e.g., failure to meet agreed timeframes for Resolution), notify CoreLogic of such issues, and follow up such issues to Resolution and closure. Supplier will be responsible for Incident Ticket tracking, assignment and follow up of all Incident Tickets. | P | |
| 1.1.32. | Supplier will implement a Severity 1 and Severity 2 Incident Management process to address major Incidents in accordance with the agreed Incident Severity Levels. Supplier will implement an exception process and obtain CoreLogic approval for urgency escalations based on business impact outside definitions and process. | P | A |
| 1.1.33. | On a *** basis, analyze, identify and recommend automation and enhancement recommendations for Incident Restoration.
| P | |
| 1.1.34. | Establish Incident classification, prioritization and workflow, communication, escalation and reporting processes. | P | A |
| 1.1.35. | In accordance with the applicable Service Levels, monitor Systems and proactively report potential outages before they occur. | P | |
| 1.1.36. | Provide Incident Management Services, as follows: (a) providing the level of support required by the CoreLogic Disaster Recovery Plan, when a situation is declared; (b) reporting situation events; (c) providing updates regarding the status of situation Resolution; (d) establishing a telephone line for Authorized Users to call regarding status; (e) providing a conference bridge line to be used in conjunction with CoreLogic disaster recovery efforts. | P | |
| 1.1.37. | Log, track, and manage Incidents in the Supplier’s ITSM database/system and link to appropriate CIs. | P | |
| 1.1.38. | Create and maintain, subject to CoreLogic approval, Resolver Group structures for all Supplier Personnel and Third Party Contractors based on agreed workflow, queues and Service Levels. Supplier to establish Incident coordination process to validate ticket assignment, ticket quality and provide for ticket status and responsiveness to Authorized Users in a timely manner. | P | A |
| 1.1.39. | Establish Incident Management governance process in a multi-provider environment to provide for timely escalation of Incidents and Resolution of Incidents. Facilitate Incident reduction through the Problem Management process and confirm that appropriate Change Management and Configuration Management processes and procedures are followed through the remediation of Incidents. | P | |
| 1.1.40. | Maintain and update list of Incident resolvers and call lists from approved Supplier Personnel, CoreLogic Personnel, and Third Party Contractors. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 52 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.1.41. | In alignment with ITIL, create, manage and execute an event, event correlation, and alert management system that engages Incident Management. | P | |
| 1.1.42. | Provide Incident detection, escalation, tracking, and Resolution with the goal of implementing workarounds/restoring normal service operations as quickly as possible and minimizing the impact to business operations. Provide conference bridge lines to be used in conjunction with CoreLogic Incident Management processes. | P | |
| 1.1.43. | Coordinate Service Restoration efforts across support groups (Supplier Personnel, CoreLogic Personnel, and Third Party Contractors). | P | |
| 1.1.44. |
| P | |
| 1.1.45. | As part of the Incident and Problem Management process, support CoreLogic Application teams with implementing proactive automated steps/scripts to be executed in production environment in order to minimize and reduce future Incidents. | P | A |
| 1.1.46. | Provide CoreLogic access and near real-time communications for the applicable Incidents. | P | |
| 1.1.47. | Provide CoreLogic, CoreLogic’s joint ventures and their Third Party Contractors CoreLogic-approved access (as a resolver) to Supplier’s ITSM System in order to manage, view, and update Incident Tickets. | P | A |
| 1.1.1.1. | Provide training to CoreLogic on usage of the ITSM system. | P | |
This Section details the obligations and responsibilities of the Parties regarding the management of Problems. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the management of Problems:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.1.48. | Provide Problem Management Services to minimize the adverse impact of Severity 1 and Severity 2 Incidents and prevent the re-occurrence of Incidents related to those errors. | P | |
| 1.1.49. | Analyze, identify and recommend automation and enhancements to Problem Management and Root Cause Analysis for the purpose of reducing Incidents. | P | |
| 1.1.50. | Monitor and provide reports on Problems, including analysis and remediation of Root Cause Analysis action items. | P | |
| 1.1.51. | Monitor and report on repeat Incidents and escalate in accordance with the Problem Management process. | P | |
| 1.1.52. | Classify Problems based on urgency and impact; reclassify Problems according to CoreLogic’s direction. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 53 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.1.53. | Manage all Problems from inception through Resolution, Root Cause Analysis, and the implementation of recommendations with Supplier Personnel, CoreLogic Personnel, and Third Party Contractors. | P | |
| 1.1.54. | Perform Root Cause Analyses for Severity 1 Incidents and Severity 2 Incidents or, if applicable, assign and coordinate Root Cause Analysis with CoreLogic Personnel and Third Party Contractors. | P | |
| 1.1.55. | Document and update all workarounds and known Resolutions in appropriate database. | P | |
| 1.1.56. | Determine and recommend if a Change is necessary to Resolve a Problem and, subject to CoreLogic approval, implement such Change. | P | A |
| 1.1.57. | Verify and facilitate Resolution of all Problems and invoke escalation procedures for Problems that are not Resolved within agreed timelines. | P | |
| 1.1.58. | Implement a known error database for Incident and Problem workarounds. | P | |
| 1.1.59. | Update all documentation to reflect any Changes associated with the Resolution of each Problem. | P | |
| 1.1.60. | Close Incident Tickets associated with each resolved Problem. | P | |
| 1.1.61. | Perform proactive analysis of conditions leading to Problems and Incidents and make corrective recommendations and, when CoreLogic approved, implement on agreed schedule. | P | A |
| 1.1.62. | Identify and record the details of Problems in a Problem Management System. Check for multiple supplier involvement and provide updates to any appropriate third party as well as Authorized User Problem databases. | P | |
| 1.1.63. | Evaluate Problem Management effectiveness and performance, recommend and, subject to CoreLogic approval, implement improvements to the Problem Management process. | P | A |
| 1.1.64. | Record all Problems in Supplier’s ITSM system. | P | |
| 1.1.65. | Provide CoreLogic, CoreLogic’s joint ventures and their Third Party Contractors CoreLogic-approved access (as a resolver) to Supplier’s ITSM System in order to manage, view, and update Problem Tickets. | P | A |
| 1.1.1.1. | Provide training to CoreLogic on usage of the ITSM system. | P | |
| |
| 4.5. | Performance Management. |
This Section details the obligations and responsibilities of the Parties regarding performance management. Except where a responsibility is identified as a ”P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the performance management.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 54 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.1.66. | Define performance management requirements, policies, and processes. | P | |
| 1.1.67. | Perform Systems performance management and provide report/metrics in alignment with Schedule A-12 (Reports). | P | |
| 1.1.68. | Provide reporting and analysis performance data. | P | |
| 1.1.69. | Provide performance management tools for Systems and allow appropriate access to CoreLogic. | P | |
| 1.1.70. | Proactively evaluate, identify and recommend configurations or changes to configurations that will enhance performance. | P | |
| 1.1.71. | Based upon analysis of performance data, implement improvement plans and coordinate with CoreLogic, Subcontractors, and Third Party Contractors, as required. | P | A |
| 1.1.72. | Through the request and Incident Management procedures, provide technical advice to improve performance and support to CoreLogic Application maintenance and development staffs. | P | |
| 1.1.73. | Recommend, install, manage and provide System management tools, requirements, and best practices for monitoring and providing performance reporting of the Systems and CoreLogic Applications. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 55 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.3
SERVICE DESK SERVICES
This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 56 |
Schedule A-2.3
Service Desk Services
| |
| 1.1.1 | Agreement. This Schedule A-2.3 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 1.1.4 | Responsibilities. In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity. |
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party.
| |
| 1.1.5 | Service Desk Services. Supplier shall provide Service Desk Services, as detailed in this Schedule. The Service Desk is a primary entry point for Incidents, inquiries, requests from Authorized Users related to the Services. The Service Desk will handle the requests and route to the appropriate resolution teams. |
Severity 1 Incidents that are critical (as defined in the Policy and Procedures Manual) will be passed directly from the Supplier’s Level 1 support personnel to the Supplier’s escalation and notification team designee who will escalate to the appropriate resolver group (which could be Level 2, Level 3, include CoreLogic Application support team members, or other subject matter expert group) or invoke the Service Restoration process to minimize the Restoration time.
| |
| 1.1.6 | Hours of Operation. Supplier shall deliver the Service Desk Services on a 24x365 basis; unless otherwise agreed by CoreLogic. |
| |
| 1.2 | CONTACT CENTER MANAGEMENT AND SUPPORT |
This Section details the obligations and responsibilities of the Parties regarding the management and support of calls handled by the Service Desk. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the management and support of calls handled by the Service Desk. Supplier will:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1 | Provide a single point of contact via phone (24x365) and email responsible for interfacing with Authorized Users for all issues related to Supplier’s delivery of Services from the Service Desk. | P | |
| 1.2.2 | Provide a central telephone number capable of routing callers to the appropriate Supplier Personnel in an efficient manner.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 57 |
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.3 | Implement and maintain security processes that verify that Service Desk callers are authenticated as Authorized Users.
| P | A |
| 1.2.4 | Conduct Level 1 and Level 2 Support, triage and input the Incident into the applicable ITSM System, and if needed, escalate the Incident.
| P | |
| 1.2.5 | Provide appropriately trained/skilled Supplier Personnel, processes, facilities, hardware and Software to handle calls and conduct Level 1 Support and Level 2 Support and facilitate communications.
| P | |
| 1.2.6 | Provide Service Desk Services in the English language.
| P | |
| 1.2.7 | Coordinate the creation, change, and deletion of Authorized User accounts (for example, perform account set-up, password resets, account deletions, and terminations) per Service Requests and in accordance with CoreLogic’s security policies.
| P | A |
| 1.2.8 | Develop, update, and implement policies and procedures regarding Authorized User account administration.
| P | A |
| 1.2.9 | Receive and track in an agreed upon Tool, Service Requests for Authorized User account activation, changes, and terminations.
| P | |
| 1.2.10 | Create, recommend updates to, and, subject to CoreLogic approval, implement a process by which Severity Levels are initially assigned to Incidents.
| P | |
| 1.2.11 | Create, recommend updates to, and, subject to CoreLogic approval, implement a process by which Incidents and Problems that are outside of the scope of the Resolution capabilities of the Service Desk are escalated and routed to CoreLogic or an appropriate third party.
| P | A |
| 1.2.12 | Track, manage, communicate and update Incidents through the lifecycle including coordination of Level 2 Support and Level 3 Support after escalating the call to CoreLogic or the appropriate third party.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 58 |
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.13 | Provide a web-based self-help option and other self-service Tools to enable Authorized Users to raise requests and Resolve Incidents without contacting the Service Desk.
| P | |
| 1.2.14 | Provide and update a list of frequently asked questions (“FAQs”) that help Authorized Users with workarounds and Resolutions for issues and Incidents.
| P | |
| 1.2.15 | Provide a Self-Service Portal with the ability for Authorized Users to: • Search the Knowledge Base and attempt to Resolve their own issues • Submit Service Desk Tickets • Review status of Service Desk Tickets created by the Authorized User • Escalate Service Desk Tickets
| P | |
| 1.2.16 | Analyze (i) CoreLogic-provided Authorized User requirements and (ii) existing self-service content used by CoreLogic, and make recommendations for improvement (and implement such recommendations upon CoreLogic approval). | P | |
| 1.2.17 | Recommend and implement solutions for self-service capabilities.
| P | A |
| 1.2.18 | Provide, configure and maintain a Voice Response Unit (VRU) with a menu configuration to automate call flow through the Service Desk. At a minimum, the VRU shall: (a) Provide status messages (b) Play back pre-recorded cut-in messages to advise callers of major service interruptions (c) Automatically direct calls to an appropriate service analyst (d) offer password reset only option | P | A |
| 1.2.19 | Provide support for remote Authorized Users by creating Service Desk Tickets for Incidents and coordinate additional support with appropriate Resolver Groups, as necessary.
| P | |
| 1.2.20 | Monitor and analyze Service Desk operations, make quarterly recommendations, and, subject to CoreLogic approval, implement improvements. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 59 |
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.21 | Develop and update key documentation related to Service Desk operations, training, CoreLogic policy guides, reference manuals, and policy and procedures documentation.
| P | A |
| 1.2.22 | Design, develop, document, and implement a manual or backup procedure to support Service Desk availability in the event that Service Desk Tools fail. | P | A |
| 1.2.23 | Document, update, and subject to CoreLogic approval, implement key escalation procedures to support Service Desk availability. | P | A |
| 1.2.24 | Using list of names provided by CoreLogic, maintain a list of “VIPs” to be used by the Service Desk for the performance of the Services. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 60 |
| |
| 1.3 | SUPPLIER INTERFACE REQUIREMENTS |
This Section details the obligations and responsibilities of the Parties regarding interfaces and interactions between Supplier and Third Party Contractors. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the interfaces and interactions between Supplier and Third Party Contractors. Supplier will:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.3.1 | Develop, document and, subject to CoreLogic’s approval, implement processes and procedures regarding interfaces and interactions between Third Party Contractors providing support to the Service Desk via interface agreements, operating level agreements, or underpinning contracts.
| P | A |
| 1.3.2 | Use a warm transfer technique to transfer calls to and from a Third Party Contractor with agreement from CoreLogic and the Third Party Contractor.
| P | |
| 1.3.3 | Accept and manage calls from Third Party Contractors based on the applicable procedures.
| P | |
| 1.3.4 | As information is acquired about high priority support issues, gather and communicate status to CoreLogic.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 61 |
| |
| 1.4 | SERVICE DESK OPERATIONAL PROCEDURES |
This Section details the obligations and responsibilities of the Parties regarding procedures relating to the operation of the Service Desk. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the procedures relating to the operation of the Service Desk. Supplier will:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.4.1 | Develop, update, maintain, and document all operational policies and procedures for the Service Desk (for example, Policy and Procedures Manual in accordance with Section 9.1 of the MSA) as well as call scripts.
| P | A |
| 1.4.2 | Amend process, documentation, or scripts. | P | |
| 1.4.3 | Maintain, update, utilize, and share an online repository/knowledge database to assist in Incident and Problem diagnosis and Resolution, including documentation of processes. Supplier shall update the knowledge repository with the completed process documentation.
| P | A |
| 1.4.4 | Using e-mail or web, conduct satisfaction surveys of Authorized Users following the closing of Service Desk Tickets on an ongoing basis.
| P | |
| 1.4.5 | Perform call-backs to Authorized Users who returned surveys with unsatisfactory scores for all Services. | P | |
| 1.4.6 | Provide and maintain telephone Systems that allow reporting and recording of call data. | P | |
| 1.4.7 | Implement procedures to reduce miscoding and misrouting of Service Desk Tickets. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 62 |
This Section details the obligations and responsibilities of the Parties regarding the training of personnel who will staff the Service Desk. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with training of personnel who will staff the Service Desk. Supplier will:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.5.1 | Provide training for and evaluation of all Service Desk personnel with respect to applicable Tools, new products, Services, and new process updates in the CoreLogic IT environment. | P | |
| 1.5.2 | Provide training (either in-person or electronically, as mutually agreed) to CoreLogic IT support groups and support personnel for any new processes or Tools introduced by the Supplier. | P | |
| 1.5.3 | Provide Authorized User training to CoreLogic point of contact, as necessary, for the introduction of any new products, Applications, services, and processes introduced by the Supplier.
| P | |
| 1.5.4 | Analyze on a quarterly basis, Authorized User trends and interactions to recommend additional Authorized User training.
| P | |
| 1.5.5 | Using CoreLogic-provided training subject matter, affected item scripts and available knowledge articles, coordinate and provide troubleshooting and training for Service Desk personnel related to CoreLogic-specific Applications and environments used by CoreLogic.
| P | |
| 1.5.6 | Using CoreLogic training materials, train Service Desk personnel on new Applications and Services introduced using the Change Control Procedure prior to implementation of such products and Services in the CoreLogic business units.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 63 |
| |
| 1.6 | SERVICE DESK REPORTING |
This Section details the obligations and responsibilities of the Parties regarding Service Desk reporting. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the procedures relating to Service Desk reporting. Supplier will:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.6.1 | In accordance with Schedule A-12, design, develop, maintain, track, update, and analyze monthly Service Desk performance reports and Authorized User satisfaction surveys.
| P | |
| 1.6.2 | Provide a “scorecard” on Key Measurements in accordance with Schedule A-12.
| P | |
| 1.6.3 | Upon CoreLogic’s request, provide ad-hoc individual Service Desk Ticket Root Cause Analysis and closed loop corrective actions in regards to issues raised by CoreLogic.
| P | |
| 1.6.4 | Participate in a monthly Service Desk operations review meeting with CoreLogic and, in accordance with Schedule A-12, provide all metrics, Reports, corrective action statements, and recommendations developed by the Supplier for review and discussion. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 64 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.4
SERVER SERVICES
This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 65 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-2.4
Server Services
| |
| 1.1.1 | Agreement. This Schedule A-2.4 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 1.1.4 | Overview. Supplier shall perform the Server services, functions and responsibilities in this Schedule as part of the Services (the “Server Services”). |
| |
| 1.1.5 | Service Availability. Supplier shall provide the Services on a 24x7 basis; unless otherwise agreed by CoreLogic. |
| |
| 1.1.6 | Responsibilities. In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity. |
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party.
| |
| 1.2 | SERVER SUPPORT AND ADMINISTRATION |
This Section details the obligations and responsibilities of the Parties regarding Server management. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1.1 | Comply with or improve current and future Equipment and Software technical Specifications as necessary to deliver the Services.
| P | A |
| 1.2.1.2 | Follow original equipment manufacturer (OEM) standards and industry best practices in performing Server Services. | P | |
| 1.2.1.3 | Support, create, test, and implement scripts for Systems administration and automation of maintenance tasks. | P | A |
| 1.2.1.4 | Manage file Systems, including optimizing logical and physical attributes. | P | |
| 1.2.1.5 | Provide support for CoreLogic stress testing and perform performance tuning activities for in-scope Systems, as reasonably requested by CoreLogic.
| P | |
| 1.2.1.6 | Configure and reconfigure Systems as requested by CoreLogic, including any required third party support.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 66 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1.7 | Defragment hard drives (e.g., compress hard drives to recapture space). | P | |
| 1.2.1.8 | Perform Server commands or actions as requested (e.g., reboot). | P | |
| 1.2.1.9 | Identify hot fixes and service packs for in-scope Systems and apply such hot fixes and service packs. | P | |
| 1.2.1.10 | Install, configure, administer, maintain, optimize and troubleshoot the Server Operating Systems. | P | |
| 1.2.1.11 | Troubleshoot System issues and provide support for determining/resolving Application-related issues. | P | |
| 1.2.1.12 | Manage file permissions, shares and print queues with permissions.
| P | |
| 1.2.1.13 | Configure and manage Microsoft Distributed File System (MS-DFS). | P | |
| 1.2.1.14 | Create and manage service accounts. | P | A |
| 1.2.1.15 | Define core images, update schedules and Server build processes. | P | A |
| 1.2.1.16 | Perform Server management, Asset Management, patch management, antivirus and Software distribution for OS.
| P | A |
| 1.2.1.17 | Store/archive previous images. | P | |
| 1.2.1.18 | At the request of CoreLogic, restore individual System to previous state including base build and Authorized User-specific features.
| P | A |
| 1.2.1.19 | Define System administration requirements and policies for CoreLogic approval and document in the Policy and Procedures Manual. | P | A |
| 1.2.1.20 | Manage CoreLogic Server asset life cycle from procurement to retire, including staging, installation, third-party management and (at Supplier locations and CoreLogic Campus Sites (***)) decommission and disposal.
| P | A |
| 1.2.1.21 | At other CoreLogic Facilities, manage the decommissioning and disposal of Servers by the responsible CoreLogic Third Party Contractor.
| P | |
| 1.2.1.22 | Manage and troubleshoot Citrix environment to include: • Infrastructure and Software, patching and Upgrades • Maintain performance and publish Applications • Application troubleshooting • Maintain a test environment • Capacity Management – User licenses, CPU, RAM • Integration with AD
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 67 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1.23 | Provide a test environment as needed for Supplier to maintain and test changes.
Note: If CoreLogic *** perform this obligation, Supplier shall *** required to provide *** under Section *** of the MSA if Supplier complies with the other requirements of Section *** of the MSA and provides prompt notice of the *** to the CoreLogic Relationship Manager by e-mail (where receipt is affirmatively acknowledged by the recipient).
| | P |
| 1.2.1.24 | Where test environments exist, perform System changes in test environment, prior to making change in production environment.
| P | A |
| 1.2.1.25 | Where test environments do not exist, and Supplier reasonably deems a planned change has material risk without the use of a test environment, Supplier will provide CoreLogic its analysis of such material risk associated with such change. If Supplier provides such analysis in advance of implementing such change, CoreLogic shall review such analysis and will, in its reasonable discretion, *** an *** of any *** arising from such change from the calculation of the applicable *** (i.e., *** would be excluded); provided however, if CoreLogic does not *** an ***, any *** arising from Supplier's implementation of such change shall be *** from the calculation of the such *** if such change would have been mitigated through a test environment (as demonstrated by a *** performed by Supplier and provided to CoreLogic).
| | P |
1.2.1.26
| Perform quarterly *** Server true-up reporting reconciling all ***Servers deployed in the previous quarter from the ***capacity-on-demand pool for all CoreLogic-owned hardware. | P | A |
| 1.2.1.27 | Implement technology refresh for hardware. | P | A |
| 1.2.1.28 | Install and maintain SAN multi-pathing Software. | P | |
| 1.2.1.29 | Install, configure and maintain monitoring agents to meet CoreLogic monitoring requirements.
| P | |
| |
| 1.2.2 | Server Administration. |
This Section details the obligations and responsibilities of the Parties regarding Server administration. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.2.1 | Maintain responsibility for privileged System accounts (e.g., administrator and root) and delegate access to Authorized Users upon request. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 68 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.2.2 | Administer accounts to make certain that only those privileges and authorities required for such accounts are provided to CoreLogic authorized Supplier Personnel or authorized Authorized Users.
| P | A |
| 1.2.2.3 | Record the activities of all accounts, including privileged System accounts, and provide such records (e.g. domain administrator logs, System logs, etc.) to CoreLogic upon request.
| P | A |
| 1.2.2.4 | Assign and manage access permissions associated with Authorized User accounts. | P | A |
| 1.2.2.5 | Perform administrative activities including: OS performance management, Incident Resolution, file system management, Server disk and storage administration, package administration, event log management, OEM coordination, Root Cause Analysis, change management and security log management. | P | A |
| 1.2.2.6 | Perform capacity planning for High Servers and Standard Servers. | P | |
| 1.2.2.7 | Change administrative passwords (including local) and service account on supported Systems at required intervals in accordance with CoreLogic policies.
| P | |
| 1.2.2.8 | Using Software license information provided by CoreLogic, provide notification to *** parties of changes to Servers that may impact any retained Software license compliance.
| P | |
| 1.2.2.9 | Establish and maintain physical hardware standards and requirements for Systems. | P | A |
| 1.2.2.10 | Generate and apply SSL Certificates associated with middleware (e.g. Apache, Weblogic) on the appropriate Operating Systems.
| P | A |
1.2.2.11
| Configure and administer Systems Software (e.g. NIS, DNS, SMTP and FTP). | P | |
| 1.2.2.12 | Perform swap space administration. | P | |
| 1.2.2.13 | Configure System logs. | P | |
| 1.2.2.14 | Modify Operating System environment variables.
| P | A |
| 1.2.2.15 | Administer the Operating System job scheduler. | P | |
| 1.2.2.16 | Create permissions for Authorized Users to schedule jobs using the Operating System job scheduler.
| P | |
| 1.2.2.17 | Perform Operating System backup using applicable Tools.
| P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 69 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.2.18 | Maintain and manage LDAP /Directory for access control and authorization.
| P | A |
| 1.2.2.19 | Perform firmware and driver updates, including Servers, HBAs, NICs, and enclosure components.
| P | |
This Section details the obligations and responsibilities of the Parties regarding Unix, Windows and Linux clustering. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.3.1 | For High Servers and Standard Servers, plan, install and implement clusters and N+1 redundant architecture.
| P | |
| 1.2.3.2 | For Low Servers, plan, install and implement clusters and N+1 redundant architecture, upon request by CoreLogic.
| P | |
| 1.2.3.3 | Coordinate with CoreLogic Application and database teams to configure clusters.
| P | |
| 1.2.3.4 | Re-configure cluster resources.
| P | |
| 1.2.3.5 | Validate cluster failover and failback.
| P | A |
This Section details the obligations and responsibilities of the Parties regarding Active Directory management with respect to the Infrastructure Services. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 70 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 1.2.4.1 | Manage Active Directory in support of the Services. | P | |
| 1.2.4.2 | Monitor Active Directory replication and configuration between sites and raise alerts in the ITSM System (e.g., alerts relating to issues with performance, Active Directory Objects and replication). | P | |
| 1.2.4.3 | Install, configure, maintain, troubleshoot and secure domain controllers. | P | |
| 1.2.4.4 | Design, configure and support Microsoft Operating System Software Active Directory integrated DNS Services.
| P | A |
| 1.2.4.5 | Manage and maintain the Active Directory forest, domains, and OU structure. | P | |
| 1.2.4.6 | Design, build, configure and support global, local and individual group policy objects. | P | A |
| 1.2.4.7 | Maintain security and maintenance best practices in alignment with CoreLogic’s standards and best practices.
| P | |
| 1.2.4.8 | Design, configure and support public key Infrastructure within Active Directory. | P | A |
| 1.2.4.9 | Design, configure and support of Windows Time service, domain and forest trusts, global catalogs, and domain controllers.
| P | A |
| |
| 1.2.5 | CoreLogic Cloud Environment Support. |
This Section details the obligations and responsibilities of the Parties regarding the CoreLogic Cloud Environment management with respect to the Services. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 1.2.5.1 | Provide management for *** (and other hypervisor) and supporting Software and Servers. | P | |
| 1.2.5.2 | Provide lifecycle management for hypervisor Software including patch management and version Upgrades. | P | |
| 1.2.5.3 | Configure virtual networking components including vSwitches and virtual Firewalls. | P | |
| 1.2.5.4 | Define system administration policies for the in-scope CoreLogic Cloud Environment.
| P | A |
| 1.2.5.5 | Perform changes in the CoreLogic Cloud Environment and lead coordination of changes across all components and Services.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 71 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 1.2.5.6 | Perform Server configuration, Operating System image management, Operating System installation, SAN connectivity, disk provisioning, volume, and patch management in the CoreLogic Cloud Environment.
| P | |
| 1.2.5.7 | Provide and maintain CoreLogic Cloud Environment monitoring and alert capabilities and integrate such alerts within the ITSM System such that alerts automatically create Incidents within the ITSM System.
| P | |
| 1.2.5.8 | Install, configure, manage and maintain an Infrastructure environment for the CoreLogic Cloud Services that shall include: (i) physical Servers that will administer the CoreLogic Cloud Environment and host and provision Virtual Servers, (ii) redundant Equipment components (e.g., power, networking, connectivity to storage); (iii) *** Hypervisor; (iv) ***; (v) virtual Network Switches (vi) virtual and non-virtual storage; (vii) reporting Systems; (viii) high availability failover capabilities for Server High,(ix) virtual networking (VLANs); (xi) Systems for performing Virtual Server templates, snapshots and clones; and (xii) patch management.
| P | |
| 1.2.5.9 | Provision standard Virtual Servers as requested through the ITSM Self-Service Portal using: (i) a Standard Template; (ii) a custom template using a Standard OS; or (iii) a standard Virtual Server clone on which such standard Virtual Server will be based (including assignment of unique IP and hostname changes). Configure Virtual Servers at the time of provisioning to include: (i) the requested amount of ***; (ii) the requested amount of ***; (iii) the requested Network Zone placement; and (iv) Enterprise Storage allocations. | P | |
| 1.2.5.10 | Review the computing resources, memory utilization, capacity limits and expected capacity needs to: (i) determine whether additional capacity is needed; (ii) develop and deliver forecasts of growth and other changes each calendar quarter; and (iii) validate capacity forecasts against actual utilization and make recommendations based on such forecasts.
| P | |
| 1.2.5.11 | Perform capacity planning for High Servers and Standard Servers. | P | |
| 1.2.5.12 | Perform all changes in the CoreLogic Cloud Environment, including changes to individual components and coordination of changes across all components and Services. | P | |
| 1.2.5.13 | Install, configure, manage and maintain high availability failover functionality within the Cloud Environment such that each Virtual Server configured in a Server High configuration will be automatically restarted upon failure of its ***host Server on a different ***host Server in the CoreLogic Cloud Environment. | P | |
| 1.2.5.14 | Install, configure, manage and maintain redundant connectivity to storage SAN groups in the CoreLogic Cloud Environment. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 72 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 1.2.5.15 | As *** Software, other related Software or related Equipment evolves or is updated from time to time, Supplier shall evaluate and implement such Software and Equipment, including any additional features, functionality or advances provided by such Software and related Equipment. | P | A |
| 1.2.5.16 | For scheduled maintenance activity for the CoreLogic Cloud Environment, and for Server High systems needing zero downtime, Supplier will utilize “maintenance mode” functionality of the applicable ***host Servers to invoke Tools to migrate all affected Virtual Servers to other ***host Servers providing Virtual Servers with continued functionality, interoperability and performance with zero downtime. | P | |
| 1.2.5.17 | Develop, manage and maintain a standard set of pre-defined templates (“Standard Templates”) that include standard profile and configuration settings for Virtual Servers, which shall be used for Virtual Server provisioning. | P | |
| 1.2.5.18 | Create Virtual Server custom templates as required by Authorized Users.
| P | |
| 1.2.5.19 | Implement affinity rules, as requested, for Virtual Servers that will allow: (i) a Virtual Server to reside on the same ***host Server as another Virtual Server, or (ii) a Virtual Server to not reside on the same ***host Server as another Virtual Server. | P | |
| 1.2.5.20 | Increase or decrease virtual disk allocations for Virtual Servers. | P | |
| 1.2.5.21 | Enable the increase or decrease of *** and *** resources for Virtual Servers by Authorized Users and effect such change during the next available maintenance window. | P | |
| 1.2.5.22 | Provision Virtual Server ***, through an Authorized User’s use of Request Management, that allows for each Virtual Server *** to: (i) be created from an existing Virtual Server; (ii) be made available for provisioning by creating a template from the *** within the ITSM Self-Service Portal; and (iii) be made available to the Authorized User by providing such Authorized User with the capability to *** an *** of such Virtual Server ***. | P | |
| 1.2.5.23 | Assess physical Servers that are candidates for virtualization and work with CoreLogic to assess valid candidates for virtualization. | P | A |
| 1.2.5.24 | Perform P2V migrations as requested or scheduled using the ITSM Self-Service Portal with parameters selected by the Authorized User to migrate a physical Server and its associated content to a Virtual Server. | P | |
| 1.2.5.25 | Perform V2V migrations as requested via the Self-Service Portal to migrate a source Virtual Server and its associated content to a new Virtual Server. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 73 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 1.2.6 | Supplier Private Cloud Environment Support. |
This Section details the obligations and responsibilities of the Parties regarding the Private Cloud Environment management with respect to the Services. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 1.2.6.1 | Provide management for *** (and other hypervisor) and supporting Software and Servers.
| P | |
| 1.2.6.2 | Provide lifecycle management for hypervisor Software including patch management and version Upgrades.
| P | |
| 1.2.6.3 | Configure virtual networking components including vSwitches and virtual Firewalls.
| P | |
| 1.2.6.4 | Provide and maintain Private Cloud Environment monitoring and alert capabilities and integrate such alerts within the ITSM System such that alerts automatically create Incidents within the ITSM System.
| P | |
| 1.2.6.5 | Provide, install, configure, manage and maintain an Infrastructure environment for the Private Cloud Services that shall include: (i) physical Servers that will administer the Private Cloud Environment and host and provision Virtual Servers; (ii) redundant Equipment components (e.g., power, networking, connectivity to storage); (iii) ***Hypervisor; (iv) ***; (v) virtual Networking Switches; (vi) virtual and non-virtual storage; (vii) Virtual Server provisioning portal via the ITSM Self-Service Portal; (viii) reporting Systems; (ix) high availability failover capabilities for Server High; (x) virtual networking (“VLANs”); (xi) Systems for performing Virtual Server templates, snapshots and clones; and (xii) patch management.
| P | |
1.2.6.6
| Develop for the use of the Private Cloud Environment (i) materials regarding creation of provisioning templates and the provisioning of Virtual Servers using such templates; (ii) materials regarding backup and restoration of provisioning templates; and (iii) Authorized User training materials for the Private Cloud Environment Services.
| P | |
| 1.2.6.7 | Provision standard Virtual Servers as requested and using: (i) a Standard Template; (ii) a custom template using a Standard OS; or (iii) a standard Virtual Server clone on which such standard Virtual Server will be based (including assignment of unique IP and hostname changes). Configure Virtual Servers at the time of provisioning to include: (i) the requested amount of ***; (ii) the requested amount of ***; (iii) the requested Network Zone placement; and (iv) Enterprise Storage allocations; via the ITSM Self-Service Portal. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 74 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 1.2.6.8 | Install, configure, and maintain *** to show billing and alignment with Resource Unit and invoicing.
| P | |
| 1.2.6.9 | Review the computing resources, memory utilization, capacity limits and expected capacity needs to: (i) determine whether additional capacity is needed; (ii) develop and deliver forecasts of growth and other changes each calendar quarter; and (iii) validate capacity forecasts against actual utilization and make recommendations based on such forecasts.
| P | |
| 1.2.6.10 | Perform capacity planning for Server High and Standard configurations. | P | |
| 1.2.6.11 | Perform all changes in the Private Cloud Environment, including changes to individual components and the coordination of changes across all components and Services. | P | |
| 1.2.6.12 | Provide, install, configure, manage and maintain high availability failover functionality within the Private Cloud Environment such that each Virtual Server configured in a Server High configuration will be automatically restarted upon failure of its ***host Server on a different ***host Server in the Private Cloud Environment. | P | |
| 1.2.6.13 | Provide, install, configure, manage and maintain balanced functionality within the Private Cloud Environment such that each Virtual Server will be dynamically balanced across the aggregate computing capacity of each Private Cloud Environment for automated workload balancing. | P | |
| 1.2.6.14 | Provide, install, configure, manage and maintain redundant connectivity to storage SAN groups in the Private Cloud Environment. | P | |
| 1.2.6.15 | As ***Software, other related Software or related Equipment evolves or is updated from time to time, Supplier shall evaluate and implement such Software and Equipment, including any additional features, functionality or advances provided by such Software and related Equipment. | P | A |
| 1.2.6.16 | For scheduled maintenance activity for the Private Cloud Environment and for Server High systems needing *** downtime, Supplier will utilize “maintenance mode” functionality of the applicable ***host Servers to invoke Tools to migrate all affected Virtual Servers to other *** host Servers providing Virtual Servers with continued functionality, interoperability and performance with zero downtime. | P | |
| 1.2.6.17 | Utilize Tools for initial placement of a Virtual Server into the Private Cloud Environment. | P | |
| 1.2.6.18 | Develop, manage and maintain a standard set of pre-defined templates (“Standard Templates”) that include standard profile and configuration settings for Virtual Servers, which shall be used for Virtual Server provisioning. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 75 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 1.2.6.19 | Create Virtual Server custom templates as required by Authorized Users.
| P | |
| 1.2.6.20 | Implement affinity rules, as requested via the ITSM Self-Service Portal for Virtual Servers that will allow: (i) a Virtual Server to reside on the same ***host Server as another Virtual Server, or (ii) a Virtual Server to not reside on the same ***host Server as another Virtual Server. | P | |
| 1.2.6.21 | Increase or decrease virtual disk allocations for Virtual Servers as requested via the ITSM Self-Service Portal. | P | |
| 1.2.6.22 | Enable the increase or decrease of *** and *** resources for Virtual Servers by Authorized Users through the ITSM Self-Service Portal and effect such change during the next available maintenance window. | P | |
| 1.2.6.23 | Provision Virtual Server ***, through an Authorized User’s use of the ITSM Self-Service Portal that allows for each Virtual Server *** to: (i) be created from an existing Virtual Server; (ii) be made available for provisioning by creating a template from the *** within the ITSM Self-Service Portal; and (iii) be made available to the Authorized User by providing such Authorized User with the capability to *** an *** of such Virtual Server ***. | P | |
| 1.2.6.24 | Assess physical Servers that are candidates for virtualization and work with CoreLogic to assess valid candidates for virtualization. | P | A |
| 1.2.6.25 | Perform P2V migrations as requested or scheduled using the ITSM Self-Service Portal in accordance with parameters selected by the Authorized User to migrate a physical Server and its associated content to a Virtual Server. | P | |
| 1.2.6.26 | Perform V2V migrations as requested via the ITSM Self-Service Portal to migrate a source Virtual Server and its associated content to a new Virtual Server. | P | |
| |
| 1.2.7 | Manage Web Services. |
This Section details the obligations and responsibilities of the Parties regarding the Server-related Web Services requests. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 76 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 1.2.7.1 | Manage DNS in support of the Server Services.
| P | |
| 1.2.7.2 | Assist CoreLogic in promotion of website code within the respective environments.
| P | A |
| 1.2.7.3 | Manage Infrastructure Servers, proxies, and domains.
| P | |
| 1.2.7.4 | Manage renewal of expired SSL Certificates.
| P | |
| 1.2.7.5 | Install, maintain and administer new and existing SSL certificates.
| P | A |
| 1.2.7.6 | Develop and provide for CoreLogic approval Web, internet, architecture and design policies.
| P | A |
| 1.2.7.7 | Review and approve Web, internet, architecture and design policies.
| | P |
| 1.2.7.8 | Perform domain management duties as they relate to service ownership for domain-names.
| P | |
| 1.2.7.9 | Review and approve internal domain and zone additions, changes, and deletions.
| | P |
| |
| 1.2.8 | Patch Management and Update. |
This Section details the obligations and responsibilities of the Parties regarding patch management and updates. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.8.1 | Download and install patches as per instructions from ***. | P | A |
| 1.2.8.2 | Where development and test environments exist, install System Software patches and test in development, then promote to test environment, and finally promote to production and DR environments.
| P | A |
| 1.2.8.3 | Where development or test environments do not exist, install System Software patches and test in the environments in which CoreLogic directs.
| P | |
| 1.2.8.4 | Assess and coordinate with all applicable parties the impact of patch installs and create a back-out plan for patch installation. | P | A |
| 1.2.8.5 | Prepare patch deployment schedules. | P | |
| 1.2.8.6 | Approve patch deployment schedules. | | P |
| 1.2.8.7 | Implement patch deployments. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 77 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.5
STORAGE & BACKUP SERVICES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 78 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-2.5
Storage and Backup Services
| |
| 1.1.1 | Agreement. This Schedule A-2.5 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 1.1.4 | Overview. Supplier shall be responsible for performing the storage and backup services, functions and responsibilities in this Schedule (the “Storage and Backup Services”). |
| |
| 1.1.5 | Service Availability. Supplier shall provide the Services on a 24x7 basis; unless otherwise agreed by CoreLogic. |
In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity.
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party.
| |
| 1.2 | Storage/Backup and Restore Management and Operations. |
This Section details the obligations and responsibilities of the Parties regarding storage and backup and Restore management. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrices below, Supplier shall be responsible for the following activities:
This Section details the obligations and responsibilities of the Parties regarding storage management.
| |
| 1.2.2 | Storage Management Requirements. |
This Section details the obligations and responsibilities of the Parties regarding the storage management requirements.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 79 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.2.1 | Define, update, and communicate storage requirements across platforms and Services. | | P |
| 1.2.2.2 | In accordance with Schedule A-12, provide a monthly summary of pending storage provisioning requests to CoreLogic.
| P | |
| 1.2.2.3 | Initiate requests for new storage resources or for increases/decreases of existing storage resources.
| P | A |
| 1.2.2.4 | On a *** basis and in accordance with Schedule A-12, provide detailed report of storage provisioned, by business unit in support of allocations model.
| P | A |
| |
| 1.2.3 | Storage Management Execution. |
This Section details the obligations and responsibilities of the Parties regarding the execution of the storage management requirements.
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.3.1 | Develop, maintain and update as appropriate existing detailed SAN design, engineering, SAN testing and integration procedures that meet CoreLogic’s requirements.
| P | A |
| 1.2.3.2 | Identify and Resolve storage equipment and SAN Fabric Incidents. | P | |
| 1.2.3.3 | Interface with Authorized Users and manage file share access and space requests. | P | |
| 1.2.3.4 | Provide storage space allocations. | P | |
| 1.2.3.5 | Provide, manage and maintain Tape libraries and Tape drives.
| P | |
| 1.2.3.6 | Maintain inventory of storage media equipment, volumes allocated and naming assignments within the Designated Data Center environments and Remote Sites set forth in Schedule A-7.
| P | |
| 1.2.3.7 | Mount, dismount, initialize and manage storage media as required within the Designated Data Centers and CoreLogic Facilities set forth in Schedule A-7.
| P | |
| 1.2.3.8 | Perform storage management functions with respect to the Windows and UNIX attached SAN (e.g., RAID array, SAN, NAS, tape, optical), as well as locally attached storage.
| P | |
| 1.2.3.9 | Manage storage data in a manner that shall meet the Availability requirements set forth in Schedule A-3.1. | P | |
| 1.2.3.10 | Manage and optimize storage performance in support of the Services. | P | |
| 1.2.3.11 | Allocate, de-allocate, and re-allocate storage as required or requested by CoreLogic. | P | |
| 1.2.3.12 | Migrate data as required or requested by CoreLogic. | P | |
| 1.2.3.13 | Implement security practices (e.g., logical unit masking) to prevent unauthorized storage access. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 80 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.3.14 | Perform data replication in accordance with Schedule A-12, and data recovery Services in accordance with Section13.2(d) of the MSA and CoreLogic’s requirements.
| P | |
| 1.2.3.15 | Update/manage storage recovery procedures and processes across the storage platforms. | P | |
| 1.2.3.16 | Monitor storage systems for reliability and malfunction. | P | |
| 1.2.3.17 | Maintain and improve storage resource efficiency and space requirements. | P | |
| 1.2.3.18 | Provision storage from arrays to host(s) in accordance with CoreLogic requirements.
| P | |
| 1.2.3.19 | Through mutual agreement on replication requirements, configure and maintain local and remote SAN-based replication.
| P | A |
| 1.2.3.20 | Configure and reconfigure Storage Equipment and Software as required or requested by CoreLogic, including any required third party support.
| P | |
| 1.2.3.21 | In accordance with Schedule A-12, perform *** true-up reporting reconciling all storage deployed in the previous quarter from the CoreLogic *** capacity-on-demand pool for all *** storage hardware used to provide storage Services.
| P | |
| 1.2.3.22 | Load and maintain removable media Equipment (including peripheral Equipment, such as Tape drives) with appropriate media for operating runs. | P | |
| 1.2.3.23 | Coordinate transport and delivery of media to and from the applicable third party offsite secure storage Supplier (e.g., Iron Mountain) to CoreLogic-designated locations as required to perform the Services and required by CoreLogic and store removable media returned by such third party supplier. | P | |
| 1.2.3.24 | Manage the distribution of all Tapes. | P | |
| 1.2.3.25 | Maintain a media inventory catalog of all files and Tapes (or alternative media) used to store CoreLogic Data.
| P | |
| 1.2.3.26 | Retain backups in accordance with the retention period for Contract Records set forth in Section 9.10(a) of the MSA for auditing purposes and change backup retention periods and create and maintain new backup jobs as required by CoreLogic in connection with CoreLogic’s legal requirements (e.g. litigation holds, Human Resource investigations, special retention backups).
| P | |
| 1.2.3.27 | Coordinate management of media. | P | |
| 1.2.3.28 | Develop and document manual media (e.g., Tapes) processing procedures that meet CoreLogic’s requirements and data retention policies and include the following: (i) procedures governing cycling/rotation/disposal of media; and (ii) media management and media retention periods (including for auditing purposes).
| P | |
| 1.2.3.29 | Perform a *** audit of offsite stored media against the offsite inventory catalog. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 81 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 1.2.4 | Storage Performance Monitoring. |
This Section details the obligations and responsibilities of the Parties regarding monitoring storage performance.
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.4.1 | Resolve exceptions and alerts related to Enterprise Storage and the Storage Equipment. | P | |
| 1.2.4.2 | Analyze storage capacity on a *** basis and propose to CoreLogic changes to the Enterprise Storage (e.g., elimination of unused Enterprise Storage and appropriate allocations of Enterprise Storage, recommended additional capacity of Enterprise Storage). | P | |
| 1.2.4.3 | Develop and implement data migration, archival, backup, catalogue maintenance, and retention management procedures. | P | A |
| 1.2.4.4 | Perform storage performance analysis in response to Incidents, Service Requests, and as needed to provide the Services.
| P | |
| 1.2.4.5 | Configure and maintain existing Storage Management Software for storage reporting, monitoring and management.
| P | |
| |
| 1.2.5 | Backup and Restore Management. |
This Section details the obligations and responsibilities of the Parties regarding backup and R estore management.
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.5.1 | Perform data backups and monitor for the successful completion of backups and create Incidents for failed backups. Install and configure backup Equipment, schedule backups, and through Request Management procedures, execute on-demand backups.
| P | |
| 1.2.5.2 | Perform and monitor the successful completion of backup procedures and create Incidents for unsuccessful backups. Install and configure backup equipment, schedule backup processes, and through Request Management Procedures, execute on-demand backup. | P | |
| 1.2.5.3 | Perform and monitor for the successful completion of recovery procedures, including online, partial, or other recovery procedures and create Incidents for unsuccessful recoveries.
| P | |
| 1.2.5.4 | Resolve exceptions and alerts related to the Enterprise Storage and Storage Equipment. | P | |
| 1.2.5.5 | Subject to the capabilities of the replication method selected, provide a recovery procedure for restoring a data image to a previous level within the applicable timeframes.
| P | |
| 1.2.5.6 | On a *** basis, provide recommendations to CoreLogic regarding backup and recovery considerations, such as improved levels of protection, efficiencies and cost reductions. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 82 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.5.7 | Implement CoreLogic-approved recommendations on backup and recovery considerations.
| P | A |
| 1.2.5.8 | Backup CoreLogic Data and information in accordance with CoreLogic backup, archive and retention schedules and other requirements, as provided by CoreLogic, including regular backups on all Systems.
| P | |
| 1.2.5.9 | Maintain and manage backup schedule and backup windows per environment to minimize the impact on the CoreLogic environments. | P | |
| 1.2.5.10 | Resolve backup failure Incidents in accordance with applicable Incident Management requirements. | P | |
| 1.2.5.11 | Through agreed upon Restore criteria and requirements, perform random sample test Restores from backups for validity checks and troubleshoot and remediate any issues relating from such test.
| P | |
| 1.2.5.12 | Restore backup data image to the appropriate target Server, including multiple data sets restores, as required to perform the Services or to fulfill CoreLogic requests.
| P | |
| 1.2.5.13 | Create scripts for customized backups as required to meet backup windows. | P | |
| 1.2.5.14 | Implement procedures for retrieving backed-up and archived storage media (onsite or offsite) as requested by CoreLogic or as required to support the Services.
| P | |
| 1.2.5.15 | Configure and schedule backup and recovery Tools. | P | |
| 1.2.5.16 | Following Incidents related to the Storage Equipment or Software, implement improvements in backup procedures and Tools.
| P | |
| 1.2.5.17 | Perform load balancing on backup schedules to optimize performance. | P | |
| 1.2.5.18 | Load and configure backup Software on Systems. | P | |
| 1.2.5.19 | Maintain and manage the scratch Tape queue.
| P | |
| 1.2.5.20 | Escalate Tape library or Tape drive failures to applicable Third Party Contractors (e.g., Sun).
| P | |
| 1.2.5.21 | Perform all activities necessary to connect new Infrastructure components to shared storage and backup Infrastructure.
| P | |
| 1.2.5.22 | Implement changes to the backup/recovery system based on generally accepted industry and manufacturer best practices.
| P | A |
| 1.2.5.23 | Dispose of storage media (e.g. Tapes, disks, etc.) at CoreLogic Facilities in accordance with Section 6.5(e)(ii) of the MSA and CoreLogic security and compliance policies. | P | A |
| 1.2.5.24 | Implement procedures for recycling media regularly, managing media replacement and recopying media to provide data integrity and quality.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 83 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.5.25 | In accordance with CoreLogic encryption requirements and Schedule 12 to the MSA, implement necessary capability and procedures for encrypting removable media (for backup purposes).
| P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 84 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.6
END USER DEVICE SUPPORT AND MESSAGING SERVICES
This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 85 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-2.6
End User Device Support and Messaging Services
| |
| 1.1 | Agreement. This Schedule A-2.6 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 1.4 | Overview. Supplier shall perform the end-user desktop support and messaging services, functions and responsibilities described in this Schedule as part of the Services (the “End User Device Support and Messaging Services”). *** |
| |
| 1.5 | Service Availability. Supplier shall provide the Services on a 24x7 basis; unless otherwise agreed by the Parties. |
| |
| 1.6 | Responsibilities. In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity. |
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party.
2. END USER DEVICE SUPPORT SERVICES
This Section details the obligations and responsibilities of the Parties regarding support for remote and local Authorized User Equipment, and device IMACD setup, support, and maintenance. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier will:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.1 | Perform engineering Services to develop new and to support existing personal computing (PC) solutions within CoreLogic’s Infrastructure, including EUC Devices, Operating Systems (OS) Software, Applications, support processes, and self-service solutions. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 86 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.2 | Provide and manage EUC Devices life-cycle Services including: (i) Asset Management, (ii) installation management, (iii) recovery, (iv) redeployment, (v) at the CoreLogic Facilities, collecting the devices from Authorized Users and taking them to a secure on-site area provided by CoreLogic for disposal by CoreLogic’s authorized disposal vendor and (vi) on-site support.
| P | |
| 2.3 | Provide solutions and support full interoperability within the Authorized User Equipment Infrastructure. | P | |
| 2.4 | Provide retained CoreLogic support employees with system access as required to provide support. | P | |
| 2.5 | Provide retained CoreLogic support employees with training as required to provide support. | P | |
| 2.6 | Verify that the Authorized User is authorized to receive the requested Authorized User Equipment and/or Software. | P | |
| 2.7 | Coordinate, execute and manage the installation of Authorized User Equipment and Software. | P | |
| 2.8 | Resolve technical issues in coordination with third parties. | P | |
| 2.9 | Provide onsite support or remote support, or dispatch support specialists, to designated CoreLogic Facilities as necessary to provide Authorized Users with Level 2 support and Level 3 operational and technical support (in the English language) for Authorized User Equipment and standard products.
| P | |
| 2.10 | Coordinate activities with the Service Desk and appropriate third parties, and provide support to the Service Desk and Authorized Users as applicable.
| P | |
| 2.11 | Resolve Incidents associated with Authorized User Equipment and Software, and provide break/fix support, advice and assistance to Authorized Users. | P | |
| 2.12 | Coordinate efforts with third party service and maintenance providers as appropriate to service Authorized User Equipment and Software. | P | |
| 2.13 | Provide assistance to Authorized Users to enable the use of Authorized User Equipment, Software, and access to and use of related technologies within the standard images and Services. | P | |
| 2.14 | Support, and as applicable during the Incident and Request Management Resolution process, provide backup and recovery of Authorized User workstations.
| P | |
| 2.15 | Manage, maintain and provide Asset Management information to support warranty service for EUC Devices.
| P | |
| 2.16 | Manage and maintain hot spares and spare parts inventory.
| P | |
| 2.17 | Provide Mobile Device management support, including managing the CoreLogic process for authorizing the provisioning of Mobile Devices. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 87 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.18 | Install routine and emergency third party-supplied corrections and patches to Software at designated end user locations/sites, as applicable.
| P | A |
| 2.19 | Perform or supervise, as appropriate, all Authorized User IMACDs for Authorized User Equipment, Software, and related Services at Designated CoreLogic Data Centers and Remote Sites set forth in Schedule A-7.
| P | |
| 2.20 | Provide support for the installation of Authorized User Equipment and Software related security patches that are routinely scheduled or scheduled in the event of a “critical” update that may cause issues at time of installation. | P | |
| 2.21 | Provide, manage and maintain Desktop Software distribution, including package creation and maintenance for approved standard images. | P | |
| 2.22 | Maintain hardware-independent EUC Device images. | P | A |
| 2.23 | Develop support processes and solution knowledge articles. | P | |
| 2.24 | Manage and execute the decommission and refresh of Authorized User Equipment.
| P | |
| 2.25 | After break/fix repairs, test Authorized User Equipment and Software to ensure functionality.
| P | |
| 2.26 | Maintain a list of individuals authorized by CoreLogic to approve Authorized User IMACDs and project IMACDs requests, including obtaining specific approval and authorization required for Authorized User IMACDs.
| P | |
| 2.27 | Validate the Authorized User IMACDs request for correctness, request from the Authorized User any Authorized User IMACDs prerequisites and any procedures that need to be followed prior to such Authorized User IMACDs and proper authorization.
| P | |
| 2.28 | Provide a mechanism for expedited handling of Authorized User IMACDs and project IMACDs.
| P | |
| 2.29 | Develop and maintain Authorized User IMACD scripts.
| P | |
| 2.30 | Perform Authorized User IMACDs in the deployment or rearrangement of Authorized User Equipment.
| | |
| 2.31 | Remotely (where applicable) and on-site (where necessary) conduct all Authorized User IMACDs for Authorized User Equipment and Software and update the CMDB.
| P | |
| 2.32 | Coordinate, execute and manage the installation of Authorized User Equipment and Software.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 88 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.33 | Recover Authorized User Equipment and Software from terminated CoreLogic employees, and prepare such Authorized User Equipment and Software for redeployment or transfer to CoreLogic’s authorized disposal vendor, and update the CMDB.
| P | |
| 2.34 | Redeploy recovered EUC Device Software licenses to fulfill new requests and update the CMDB/Software License Management System.
| P | |
| 2.35 | Develop and execute managed refresh plans to replace Authorized User Equipment. | P | |
| 2.36 | Manage Subcontractors to Resolve issues with sourcing, recovery, certification, and Upgrades. | P | |
| 2.37 | Transfer Authorized User Equipment and Network printers with internal hard disks (which are not redeployed or subject to return under a lease) to CoreLogic’s authorized disposal vendor, for transportation by CoreLogic’s disposal vendor, according to CoreLogic specifications and update the CMDB. | P | |
| 2.38 | Develop and implement a process, subject to CoreLogic approval, to facilitate the reporting to CoreLogic and prompt replacement of stolen or damaged Authorized User Equipment and Software.
| P | A |
| 2.39 | Return or replace all non-performing EUC Devices to the warranty provider including, at the CoreLogic Facilities, collecting the devices from Authorized Users and taking them to a secure on-site area provided by CoreLogic for transfer to CoreLogic’s authorized disposal vendor . | P | |
3. MESSAGING OPERATIONS AND DEPLOYMENT SUPPORT
This Section details the obligations and responsibilities of the Parties regarding messaging management with respect to the Infrastructure Services (“Messaging Services”). Messaging Services include management of CoreLogic’s messaging environments (e.g., email, instant messaging, calendar, contacts, etc.) and push / pull mail Services (e.g., personal digital assistants, etc.) (collectively, “Messaging”) for all Authorized Users and all CoreLogic Facilities. Supplier shall manage, administer, operate, install and maintain the Messaging environments including the activities described in this Schedule. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier will:
Messaging Operations
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 3.1 | Support, maintain (including the Software lifecycle) and monitor Messaging functionality and Services accessed through *** (***).
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 89 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 3.2 | Support, maintain (including the Software lifecycle) and monitor instant messaging functionality and Services accessed through *** and ***.
| P | |
| 3.3 | Provide Email Mailboxes capable of sending and receiving corporate email to and from CoreLogic-approved Software and Equipment.
| P | |
| 3.4 | Support Email Mailboxes as is required by CoreLogic policy.
| P | |
| 3.5 | Provide an Email Mailbox for administering mail Services, including providing a *** email address where errors in email processing are directed. | P | |
| 3.6 | Support, maintain and monitor the Messaging Servers and domains.
| P | |
| 3.7 | Perform stress testing and performance tuning of Messaging Servers or environments.
| P | A |
| 3.8 | Support, maintain and monitor enterprise fax Services. | P | |
| 3.9 | Recommend and implement spam message blocking policies. | P | A |
| 3.10 | Update anti-spam Software and manage subscription to spam blacklist services in order to reduce spam before it reaches the Authorized User computing environment.
| P | |
| 3.11 | Provide mass-mailing email Services for internal and externally bound email. | P | |
| 3.12 | Develop and recommend Messaging Systems’ use standards (e.g., mailbox size, message retention, message deletion) on an annual basis.
| P | A |
| 3.13 | Implement and enforce approved Messaging Systems’ use standards. | P | |
| 3.14 | Support long-term storage of email in accordance with CoreLogic policy. | P | |
| 3.15 | Disable and remove Authorized User accounts Email Mailboxes, instant messaging and calendaring systems, as requested by CoreLogic.
| P | |
| 3.16 | Restrict access to company email distribution groups as directed by CoreLogic and implement security measures restricting unauthorized users from sending group email distributions to company distribution groups.
| P | A |
| 3.17 | Administer directory services and meta-directory synchronization, email, and shared mailbox/public folder management.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 90 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 3.18 | Provide distribution lists (both user maintained and auto-populated). | P | |
| 3.19 | Administer and synchronize email global address lists (GALs). | P | |
| 3.20 | Establish and maintain email routing. | P | |
| 3.21 | Monitor and review email system backups and Resolve backup Incidents. | P | |
| 3.22 | Provide mail and attachment virus scanning, policy management, transport layer encryption and authentication. | P | |
| 3.23 | Provide secure remote access to email Services. | P | |
| 3.24 | Provide personal as well as shared or restricted mailboxes for non-end user purposes (e.g., shared calendars, mailboxes, conference rooms, etc.). | P | |
| 3.25 | Support, manage and maintain an encrypted email gateway. | P | |
| 3.26 | Provide support for “legal holds” or emergency access removal. | P | A |
| 3.27 | Provide necessary support to keep CoreLogic off email “blacklists”. | P | |
| 3.28 | Deliver audit trails of activity, including tracking information on email and instant messaging, per legal and compliance requirements. | P | |
Messaging Deployment Support
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 91 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description
| Supplier | CoreLogic |
| 3.29 | Provide architecture, administration and engineering Services related to email in compliance with CoreLogic standards.
| P | |
| 3.30 | Provide mail relay service for Data Centers and Remote Sites set forth in Schedule A-7, with multiple internet points of presence.
| P | |
| 3.31 | With CoreLogic provided growth forecast input, configure Messaging Infrastructure, including all required Messaging Servers and networking Equipment for current and future CoreLogic messaging workloads.
| P | |
| 3.32 | Use generally accepted security best practices to configure the Messaging Infrastructure so that known denial of service (DoS) attacks and other common email attacks are mitigated to lessen the impact to email Services.
| P | |
| 3.33 | With growth and forecasting input from CoreLogic, plan for business volume changes and specific project implementation requirements, based on information supplied by CoreLogic. Review plans with CoreLogic on a semi-annual basis for CoreLogic's approval.
| P | |
| 3.34 | Add and remove Messaging Servers to and from a domain to support Systems.
| P | |
| 3.35 | Provide proactive and reactive capacity planning to minimize problems caused by lack of capacity (for example, full file Systems).
| P | |
| 3.36 | Install, maintain and support Messaging Software products. | P | |
| 3.37 | Test and implement Messaging environment changes. | P | |
| 3.38 | Participate in determining Messaging requirements changes, determine the impact of development and maintenance work, and implement necessary changes to relevant messaging components subject to CoreLogic's approval.
| P | A |
| 3.39 | Route mail to non-customer addresses and other ".com" domains for CoreLogic and its Eligible Recipients.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 92 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.7
DATA CENTER, MAINFRAME, PRODUCTION CONTROL, AND MONITORING SERVICES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 93 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-2.7
Datacenter, Mainframe, Production Control, and Monitoring Services
| |
| 1.1.1 | Agreement. This Schedule A-2.7 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided.
Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A.
Supplier shall perform the data center, mainframe, production control, and monitoring services, functions and responsibilities described in this Schedule as part of the Services (the “Data Center Services”).
| |
| 1.1.5 | Service Availability. |
Supplier shall provide the Services on a 24x7 basis, unless otherwise agreed by the Parties.
In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity.
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the review and approval of the “Approve” Party.
| |
| 1.2 | DATA CENTER OPERATIONS |
| |
| 1.2.1 | Data Center Facilities and Operations. |
This Section details the obligations and responsibilities of the Parties regarding the Supplier’s and CoreLogic Data Center operations. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1.1 | For CoreLogic and Supplier Data Centers identified in Schedule A-7, manage, maintain, control, and operate designated Data Center environments that meet Uptime Institute’s Tier *** standards, temperature and humidity conditions with heating, ventilation and air conditioning (“HVAC”) systems. | P | |
| 1.2.1.2 | Provide resources and coordinate with CoreLogic as applicable, to meet scheduled requests, locally or remotely, as required at CoreLogic and Supplier Data Centers identified in Schedule A-7. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 94 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1.3 | Schedule, perform and oversee repairs for CoreLogic and Supplier Data Centers identified in Schedule A-7, coordinate as applicable with CoreLogic and third parties (e.g., ***), and inform CoreLogic of any critical repairs to meet required Service and performance requirements. | P | A |
| 1.2.1.4 | Coordinate with all third-party Equipment and Software suppliers (e.g., ***, *** and ***, HVAC, maintenance, etc.) and collaborate as applicable with CoreLogic to Resolve all Incidents and Problems related to Data Center Services. | P | |
| 1.2.1.5 | Provide operational support for CoreLogic and Supplier Data Centers identified in Schedule A-7 to Resolve Incidents or as required for new Equipment implementation. | P | |
| 1.2.1.6 | For the CoreLogic and Supplier Data Centers identified in Schedule A-7, provide, manage & maintain redundant power and cooling to meet required Service and performance requirements. | P | |
| 1.2.1.7 | In accordance with capacity requirements provided by CoreLogic, provide sufficient space to meet Infrastructure requirements. | P | |
| 1.2.1.8 | Restrict unescorted access to secure areas to those with proper authorization for CoreLogic and Supplier Data Centers identified in Schedule A-7. | P | |
| 1.2.1.9 | For CoreLogic and Supplier Data Centers identified in Schedule A-7, provide physical access to Equipment as requested by CoreLogic and in accordance with applicable access control policies. | P | |
| 1.2.1.10 | Provide physical site badge reader access control and management at the Designated Data Centers. | P | |
| 1.2.1.11 | At Supplier Data Centers, provide physical site security through premise and access control and access control lists. | P | |
| 1.2.1.12 | Manage and maintain monitoring system for the environmental variables for CoreLogic and Supplier Data Centers identified in Schedule A-7. | P | |
| 1.2.1.13 | Provide a monthly report, in accordance with Schedule A-12, of the maintenance performed on environment elements for CoreLogic and Supplier Data Centers identified in Schedule A-7 | P | |
| 1.2.1.14 | Manage and maintain UPS/generator set and other power Equipment for CoreLogic and Supplier Data Centers identified in Schedule A-7. | P | |
| 1.2.1.15 | Retire or decommission data center Equipment, including racks and cabling, in accordance with CoreLogic standards and guidelines for CoreLogic and Supplier Data Centers identified in Schedule A-7. | P | |
| 1.2.1.16 | Perform Equipment cabling, rack and stack operations guidelines for CoreLogic and Supplier Data Centers identified in Schedule A-7. | P | |
| 1.2.1.17 | Document all Data Center facilities changes per policy and guidelines for CoreLogic and Supplier Data Centers identified in Schedule A-7. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 95 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
This Section details the obligations and responsibilities of the Parties regarding Mainframe Systems support. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrices below, Supplier shall be responsible for the following activities such as Mainframe production support, operations, access, hardware, Software, network, security, storage, and scheduling:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.3.1.1 | Perform network Software tasks • Define TCP/IP printers • Add, change, delete printers • Make IP changes • Add, change, delete VTAM APPLID’s | P | |
| 1.3.1.2 | Install authorization keys for program products. | P | |
| 1.3.1.3 | Install, maintain and support Mainframe Systems’ OS and 3rd-party ISV Systems Software (z/OS, z/VM, and z/Linux) across LPARS, maintain Software at current versions and apply PTFs, Highly Pervasive (HIPER) PTFs as required for stability and to meet the Services. | P | A |
| 1.3.1.4 | Install, maintain and support Mainframe transaction processing Systems (e.g. CICS, MQ, DB2, etc.). Maintain software at current versions and apply PTFs, Highly Pervasive (HIPER) PTFs as required for stability and to meet the Services. | P | |
| 1.3.1.5 | Install, maintain and support Mainframe network Systems Software to include OSAs and FEPs including both SNA and TCP/IP environments. Maintain software at current versions and apply PTFs, Highly Pervasive (HIPER) PTFs as required for stability and to meet the Services. | P | |
| 1.3.1.6 | Install, configure, maintain and support middleware (e.g., MQSeries). Maintain Software at current versions and apply PTFs, Highly Pervasive (HIPER) PTFs as required for stability and to meet the Services. | P | |
| 1.3.1.7 | Manage Mainframe Servers for in-scope Software license compliance using Software license data provided by CoreLogic. | P | |
| 1.3.1.8 | In accordance with Software license data provided by CoreLogic provide notification to responsible parties of changes to Mainframe Servers that may impact any retained Software license compliance.
| P | A |
| 1.3.1.9 | Adhere to technical standards as required by the Agreement (e.g., Sections 9.4, 9.5 and Article 13 of the MSA)
| P | A |
| 1.3.1.10 | Develop, document, execute and maintain backup and recovery methodologies for the Mainframe Operating System support, transaction processing (e.g., CICS) and middleware Systems environments. | P | A |
| 1.3.1.11 | Provide 24x365 technical support for Mainframe Operating Systems (z/OS, z/VM, and z/Linux), the support environments and transaction processing Systems, such as CICS, DB2, MQ, etc., and their environments. Perform regular System maintenance during maintenance windows. | P | |
| 1.3.1.12 | Through Request and Incident Management procedures, interface with the Application teams to Resolve Incidents and to perform the Services. | P | |
| 1.3.1.13 | Propose to CoreLogic new technologies for the Systems environment that improve performance. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 96 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.3.1.14 | Provide Configuration Management for the Mainframe environment, including hardware configuration, planning, Upgrading, updating, configuring, managing, installing and de-installing as appropriate in support of all Mainframe processors and peripherals. All Software/hardware Upgrades will be planned and implemented in alignment with generally accepted industry best practices.
| P | |
| 1.3.1.15 | Provide ACF2 security administration support for the Mainframe environment. | P | |
| 1.3.1.16 | The following items will be documented in an appropriate client repository: - Software inventory - Hardware inventory - System Z usage and operation procedures - Disaster recovery testing procedures - Disaster recovery data replication procedures | P | |
| 1.3.1.17 | Perform performance/capacity planning to perform Services: - Monitor, customize, and maintain z/OS, z/VM, and z/Linux performance as required. - Work collaboratively with CoreLogic to identify potential performance improvements. - Provide capacity planning reports in accordance in Schedule A-12 and as reasonably requested by CoreLogic. | P | A |
| 1.3.1.18 | Per CoreLogic request, evaluate new Software and hardware products for acquisition. | P | A |
| |
| 1.4 | PRODUCTION MANAGEMENT AND OPERATIONS |
| |
| 1.4.1 | Production Control and Scheduling. |
This Section details the obligations and responsibilities of the Parties regarding production control and scheduling for all applicable environments. Except where a responsibility is identified as a “P responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with production control and scheduling:
|
| | | |
| No. | Description | Supplier | CoreLogic
|
| 1.4.1.1 | Develop, manage, adjust and tune job schedules, including backup schedules • Identify critical paths based on statistics of execution. • Identify jobs eligible for parallel processing (on same CPU or multiple CPUs) and reorganization of normal batch schedules. • Support load balancing across platforms when required and applicable. • Support special batch schedules (e.g., for known peak periods). • Suggest and implement improvements approved by CoreLogic. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 97 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic
|
| 1.4.1.2 | Administer and maintain an automated production scheduling system, including Upgrades, Maintenance and security updates. | P | |
| 1.4.1.3 | Integrate the schedules in accordance with CoreLogic policies and as necessary to deliver Services. | P | |
| 1.4.1.4 | Publish CoreLogic-approved batch job processing schedule and execute across all applicable environments per CoreLogic’s requirements. | P | A |
| 1.4.1.5 | Identify and Resolve scheduling conflicts in the schedule cycles. | P | A |
| 1.4.1.6 | Schedule ad hoc request batch jobs that require immediate or time-specific execution. | P | |
| 1.4.1.7 | Update parameters, holiday schedules and control cards. | P | |
| 1.4.1.8 | Run, monitor, and maintain processing tasks (including production, development, quality assurance and other processing tasks) according to the established schedules. | P | |
| 1.4.1.9 | Complete processing within published time frames, in the correct sequence and fulfill requests for expedited and/or special processing needs by Authorized Users. | P | |
| 1.4.1.10 | Develop and implement a process to determine job run prioritization and optimization. | P | A |
| 1.4.1.11 | Develop and implement methods for Application groups to request higher priority and job scheduling additions for job execution. | P | |
| 1.4.1.12 | Perform an impact analysis on a request for higher priority for job execution and make a recommendation to CoreLogic for approval before implementation. | P | |
| 1.4.1.13 | Administer access to production control and scheduling Software tools such as ***,*** | P | |
| 1.4.1.14 | Generate and provide to CoreLogic *** Reports on production control and scheduling (in accordance with Schedule A-12 (Reports), including (i) batch reports for critical Applications, (ii) failed jobs, and (iii) alarms.
| P | |
| 1.4.1.15 | Support and troubleshoot failed/abandoned jobs, diagnose Problems, and implement solutions to prevent recurrence. CoreLogic to provide job dependencies and sequence. | P | A |
| 1.4.1.16 | Perform trend analysis to identify production problems; plan and obtain CoreLogic approval to implement solutions to remediate and prevent issues proactively. | P | |
| 1.4.1.17 | Provide CoreLogic with notifications and updates, including the impact of special requests on the timing of other tasks, and any other identified issues which may negatively affect the timely completion of batch jobs. | P | |
| 1.4.1.18 | Identify job dependencies and establish priorities for batch job and report distribution schedules, and take all steps necessary to prepare Applications job streams for production scheduling and execution. | | P |
| 1.4.1.19 | Repair and Resolve abnormal batch terminations when possible, communicate terminations to Authorized Users and perform job restarts. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 98 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic
|
| 1.4.1.20 | Manage job schedules during outage windows and maintenance activities. | P | |
This Section details the obligations and responsibilities of the Parties regarding the installation and configuration of monitoring Tools. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with the installation and configuration of the monitoring Tools:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 99 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.4.2.1 | Provide monitoring for Infrastructure-related Equipment, Operating Systems, Software, Services, databases and Application monitoring. | P | A |
| 1.4.2.2 | Install and configure tools for receiving alerts related to Equipment, Operating Systems, Services, databases and Applications. | P | |
| 1.4.2.3 | Perform on-going Systems maintenance activities including patching and Upgrades for monitoring tools, including database and application monitoring tools. | P | |
| 1.4.2.4 | Perform troubleshooting activities for Incidents related to monitoring Systems/tools. | P | |
| 1.4.2.5 | In accordance with the ITSM System configurations and CoreLogic input, automatically create Incidents and route to appropriate Resolver Groups based on alerts generated by the monitoring tools. | P | |
| 1.4.2.6 | Configure monitoring tools to meet Service Levels, and CoreLogic alerting requirements at CoreLogic-approved threshold levels and error conditions. | P | A |
| 1.4.2.7 | Through Request Management, create, modify, maintain and implement scripts as required by CoreLogic to monitor databases and Applications via synthetic transactions or as required by monitoring tool. | P | |
| 1.4.2.8 | Participate in CoreLogic-initiated operational readiness tests (add monitored Servers and related devices from the management console in a manner consistent with the agreed Incident, Change and Release Management processes).
| P | |
| 1.4.2.9 | Coordinate, attend and document CoreLogic scripting design meetings to determine the scripting requirements to meet CoreLogic monitoring requirements. | P | |
| 1.4.2.10 | Perform quarterly review of false alerts and propose corrective actions. | P | |
| 1.4.2.11 | Implement corrective action resulting from *** review of false alerts. | P | A |
| 1.4.2.12 | With CoreLogic approval, design, implement, and maintain automated Event Resolution scripts which include auto restart of services and Servers. | P | A |
| 1.4.2.13 | Provide support and guidance for CoreLogic to utilize Supplier’s monitoring tools by sending alerts to tool(s) for reporting and escalation | P | |
This Section details the obligations and responsibilities of the Parties regarding status monitoring, (e.g., the monitoring of Infrastructure status). Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the following activities associated with status monitoring:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 100 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.4.2.1 | Monitor, support, and report the status of the in-scope Infrastructure and other monitoring Events in the respective environments. | P | |
| 1.4.2.2 | Configure monitoring on the Infrastructure, databases and Applications to respond to System alerts and Events in accordance with the monitoring requirements. | P | |
| 1.4.2.3 | Monitor for and respond to backup failures within the environment. | P | |
| 1.4.2.4 | Monitor scratch tape queue. | P | |
| 1.4.2.5 | Escalate third party issues and coordinate Restoration with Third Party Contractors. | P | |
| 1.4.2.6 | Analyze and notify CoreLogic or appropriate Third Party Contractor regarding storage capacity for existing Systems. | P | |
| 1.4.2.7 | Monitor backup logs in accordance with the backup schedules. | P | |
| 1.4.2.8 | Perform on-going alert detection and escalation for the in-scope Infrastructure and other monitoring Events. | P | |
| 1.4.2.9 | In accordance with Monitoring Levels, add, update, or delete monitored Infrastructure and database and Applications scripts from the management console.
| P | |
| 1.4.2.10 | Implement ITIL Event Management processes and procedures. | P | |
| 1.4.2.11 | Implement Event correlation processes to identify critical Events for immediate proactive Resolution. | P | |
| 1.4.2.12 | Assist CoreLogic product teams in setting up alerting using Dell alerting tools and processes. | P | |
| 1.4.2.13 | Control and manage monitoring during “black-out” periods as requested by CoreLogic for System/Application related changes. | P | |
| 1.4.2.14 | Provide monitoring scripting support during Event alerting and verify Event is not a false Event before escalating to Application teams. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 101 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.8
ELECTRONIC DATA EXCHANGE SERVICES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 102 |
Schedule A-2.8
Electronic Data Exchange Services
This Schedule A-2.8 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”).
All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided.
Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A.
Supplier shall perform the media and electronic data exchange services, functions and responsibilities described in this Schedule as part of the Services (the “Electronic Data Exchange Services”)
| |
| 1.1.5 | Service Availability. |
Supplier shall provide the Services on a 24x7 basis; unless otherwise agreed by the Parties.
In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity.
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party.
| |
| 1.2 | ELECTRONIC DATA EXCHANGE SERVICES. |
This Section details the obligations and responsibilities of the Parties regarding Electronic Data Exchange Services, such as file handling. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier will:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 103 |
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1.1 | Execute and support the inbound and outbound file transmission process, including performing any programming support to automate the file transmission processes on appropriate platforms.
| P | |
| 1.2.1.2 | Test and remediate any issues identified for any programs created to automate the file transmission process for specific files prior to implementing into the production environment. | P | |
| 1.2.1.3 | Attend business unit and customer planning and design meetings to determine the file transmission setup requirements.
| P | |
| 1.2.1.4 | Perform daily and after hours support for file transmission issues, including researching missing files, trouble-shooting connectivity issues and after receipt of the information required for Supplier to complete the request, resending files upon CoreLogic customer or business unit request and supporting changes in connectivity setup as initiated by CoreLogic customers. | P | |
| 1.2.1.5 | Report on transmission issues and implement process changes to reduce errors/failures. | P | |
| 1.2.1.6 | Provide scripting support for business unit reports and notifications.
| P | |
| 1.2.1.7 | Install and configure Third Party Software for Windows and Unix platforms that will be used in automated transmissions. | P | |
| 1.2.1.8 | Coordinate with internal CoreLogic teams for file transmissions that are configured to monitor for server space and file cleanup. | P | |
| 1.2.1.9 | Work directly with CoreLogic customers during business hours to configure and maintain file transmissions. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 104 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.9
NETWORK SERVICES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 105 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-2.9
Network Services
| |
| 1.1.1 | Agreement. This Schedule A-2.9 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 1.1.4 | Overview. Supplier shall be responsible for performing the network and network management services, functions and responsibilities described in this Schedule as part of the Services (the “Network Services”). |
| |
| 1.1.5 | Service Availability. Supplier shall provide the Services on a 24x365 basis; unless otherwise set forth in the Agreement. |
| |
| 1.1.6 | Responsibilities. In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity. |
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party.
| |
| 1.2 | NETWORK MANAGEMENT SUPPORT |
This Section details the obligations and responsibilities of the Parties regarding LAN, WAN, Firewall and telephony support. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities.
| |
| 1.2.1 | LAN, WAN, Devices, Network Equipment, and Telephony Support. |
This Section details the obligations and responsibilities of the Parties regarding LAN, WAN, network operations, and telephony support. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1.1 | Adhere to CoreLogic network service (data, voice and voice services) requirements, including: • Aligning with or improving current and future architecture technical specifications • Comply with applicable CoreLogic network operational guidelines (that have been communicated to Supplier) and CoreLogic-approved Supplier policies • Following generally accepted original equipment manufacturer (OEM) standards and industry best practices.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 106 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1.2 | Provide operational support, configuration, network design, and monitoring for in-scope LAN and WAN Devices and Network Equipment.
| P | |
| 1.2.1.3 | Monitor in-scope voice and data network environments to measure availability and identify Incidents.
| P | |
| 1.2.1.4 | Transport voice, data, and video protocols over the internet protocol (“IP”) LAN and WAN between in-scope CoreLogic locations and CoreLogic partner locations.
| P | |
| 1.2.1.5 | Provide secure internet communications and terminations per the Information Security Policy Set and the Compliance Policy Set.
| P | |
| 1.2.1.6 | Provide proxy/caching Services.
| P | |
| 1.2.1.7 | Provide access control list (“ACL”) Services at and within LAN boundaries.
| P | |
| 1.2.1.8 | Manage and maintain wireless local area networks at CoreLogic Facilities designated in Schedule A-7.
| P | |
| 1.2.1.9 | On a *** basis, review usage data and recommend bandwidth optimization.
| P | |
| 1.2.1.10 | Provide, support, and maintain dynamic host configuration protocol (“DHCP”) Services.
| P | |
| 1.2.1.11 | Through Request Management procedures, provide appropriate tunneling capabilities for transport.
| P | |
| 1.2.1.12 | Engineer proper circuit path and carrier diversity for required CoreLogic Facilities.
| P | A |
| 1.2.1.13 | Manage and maintain the secure perimeter structure to comply with Supplier’s obligations under the MSA to comply with the Information Security Policy Set and the Compliance Policy Set.
| P | |
| 1.2.1.14 | Manage internet access points of presence at CoreLogic Facilities as requested by CoreLogic.
| P | |
| 1.2.1.15 | Provide primary and secondary DNS Services for internal domains required for internet access Services and maintain registration for domains.
| P | |
| 1.2.1.16 | Provide IP address management.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 107 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1.17 | Support secure access to the internet, including, • Session termination services for secure socket layer (“SSL”) connections • Web Acceleration (TCP buffering and offload) • File Transfer Protocol • Web content filtering
| P | |
| 1.2.1.18 | Manage connectivity to in-scope remote CoreLogic Facilities including third party connections.
| P | |
| 1.2.1.19 | Administer and provide access controls and auditing for CoreLogic’s network (data and voice) environments including: • Maintaining responsibility for privileged system accounts (e.g. “access control strings”) and delegating access to Authorized Users • Administering IDs to personnel with only those privileges and authorities required for such IDs • Recording the activities of all users, including privileged system accounts, and providing such records (e.g. domain administrator logs, system logs, etc.) to CoreLogic upon request
| P | |
| 1.2.1.20 | Manage the retirement and replacement of Network Equipment at the CoreLogic Campus Sites (Santa Ana, Westlake, Poway) and Supplier Facilities designated in Schedule 8, including: • Purging data and configurations • For Equipment intended to be redeployed, upgrading such Equipment according to CoreLogic specifications • For Equipment subject to a lease, returning such leased Equipment to lessors at the termination of such lease in accordance with lessor guidelines and requirements
| P | |
| 1.2.1.21 | At other CoreLogic Facilities, manage the performance of these services by the responsible CoreLogic Third Party Contractor.
| P | |
| 1.2.1.22 | Perform support for network connectivity issues related to CoreLogic Remote Sites and CoreLogic-defined external customer sites for data transfer.
| P | A |
| 1.2.1.23 | Provide load balancing support and optimization for high available configurations.
| P | |
| 1.2.1.24 | Perform Software/firmware Upgrades on in scope Network Equipment.
| P | |
| 1.2.1.25 | Configure and maintain Quality of Service (QOS) on the LAN and WAN.
| P | |
| 1.2.1.26 | Configure and manage site-tosite VPN connections to in-scope remote CoreLogic locations and CoreLogic partners.
| P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 108 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.1.27 | Monitor and manage intrusion detection systems, intrusion prevention systems, remote access servers and VPN concentrators.
| P | |
| 1.2.1.28 | Monitor and manage DNS, Load Balancers and proxy Servers.
| P | |
| 1.2.1.29 | Manage and track IP addresses.
| P | |
| 1.2.1.30 | Perform and analyze network packet captures as needed in support of troubleshooting efforts.
| P | |
| 1.2.1.31 | Maintain and manage network management Systems.
| P | |
| 1.2.1.32 | Configure, manage and maintain the connectivity between Supplier’s network and the CoreLogic Network. | P | |
| 1.2.1.33 | Troubleshoot and Resolve all network-related issues and provide support for determining/resolving Application Operating System-related issues.
| P | |
| 1.2.1.34 | Monitor Network Services for capacity issues and/or react to Incidents regarding performance, and coordinating Resolution.
| P | |
| 1.2.1.35 | Perform Equipment and Software maintenance in accordance with manufacturer warranties.
| P | |
| 1.2.1.36 | Maintain appropriate Software patch levels on Equipment as approved by CoreLogic and permitted during approved patching windows.
| P | |
| 1.2.1.37 | Provide break-fix support in accordance with manufacturer warranty and CoreLogic requirements.
| P | |
| 1.2.1.38 | In the event Supplier must replace Equipment and/or Software, Restore the environment to the previous state including configuration and data, and providing replacement Equipment and/or Software that is identical or an improvement.
| P | |
| 1.2.1.39 | Perform Network IMADs in the deployment or rearrangement of existing Network Equipment and Software, and coordinate with CoreLogic Facilities when planning for moves.
| P | |
| 1.2.1.40 | Provide Reports on network bandwidth usage by sites and/or by business unit, and in accordance with Schedule A-12.
| P | |
This Section details the obligations and responsibilities of the Parties regarding daily Firewall support. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 109 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.2.1 | Manage Firewall rules that provide access to network devices and Systems in accordance with the Information Security Policy Set.
| P | |
1.2.2.2
| Implement and verify Firewall configuration.
| P | A |
| 1.2.2.3 | Perform Firewall rule support and management
| P | |
1.2.2.4
| Provide connectivity to applicable environments through CoreLogic LAN/WAN to enable Application owners and other CoreLogic Personnel access to Applications.
| P | |
| 1.2.2.5 | Perform *** Firewall audit.
| P | |
| 1.2.2.6 | Perform Software/firmware Upgrades on in-scope Firewalls.
| P | |
This Section details the obligations and responsibilities of the Parties regarding telephony support. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.3.1 | Support voice telephony services including: • Inbound and outbound national and international calls • Voicemail • Enforcing security policies including appropriate password rules • Fixed-to-mobile call direction • Desk sharing (user specific services) and number portability
| P | |
| 1.2.3.2 | Manage audio and video conferencing services at CoreLogic Facilities (***, ***, ***). | P | |
| 1.2.3.3 | Perform VOIP Systems configuration and new VOIP Phone setup, excluding non-VOIP systems.
| P | |
| 1.2.3.4 | Maintain and manage in scope VOIP Systems including Software, firmware and patch Upgrades as approved by CoreLogic and permitted during approved Upgrade windows excluding non-VOIP systems.
| P | |
| 1.2.3.5 | Consolidate voice and data transport services onto common, redundant access at sites where it is economical and technically feasible.
| P | |
| 1.2.3.6 | Provide access to all statutory geographic specific emergency services.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 110 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1.2.3.7 | Provide telecommunications expense management as it relates to Mobile Devices.
| P | A |
| 1.2.3.8 | Review all invoices for CoreLogic’s telecommunications Third Party Contractors.
| P | |
| 1.2.3.9 | Validate that only valid toll charges have been applied to CoreLogic. | P | |
| 1.2.3.10 | Review telecommunications invoices and report on potential abuses of long distance services.
| P | |
| 1.2.3.11 | Investigate whenever CoreLogic exceeds designated thresholds and coordinate activities with the transport provider, including wireless and conferencing charges. | P | |
| 1.2.3.12 | Administer CoreLogic Third Party Contractor conferencing services.
| P | |
| 1.2.3.13 | Perform voice System administration.
| P | |
| 1.2.3.14 | Recover extension numbers upon receiving termination notices.
| P | |
| 1.2.3.15 | Manage and maintain in-scope call recording Systems.
| P | |
| 1.2.3.16 | Configure and maintain SIP interfaces with CoreLogic’s data services providers.
| P | |
| 1.2.3.17 | Administer audio conference System (interfacing between *** and ***).
| P | |
| 1.2.3.18 | In accordance with Schedule A-12, report on usage by users and sites coming from call manager.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 111 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.10
RESERVED
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 112 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.11
RESERVED
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 113 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-2.12
DISASTER RECOVERY SERVICES
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 114 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-2.12
Disaster Recovery Services
| |
| 1.1 | Agreement. This Schedule A-2.12 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity. In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 1.4 | Schedules. The following Schedules are incorporate into this Schedule by this reference: |
Schedule A-2.12.1 RTO-RPO: This Schedule identifies the RTO and RPO
associated with the applicable Disaster Recover Plan.
2. GENERAL OBLIGATIONS
|
| | | |
| No. | Description | Supplier
| CoreLogic |
| 2.1 | Provide ongoing “Business Continuity” (i.e., the ability of an organization to provide service and support for its customers and to maintain its viability before, during, and after a business continuity event) planning with respect to Eligible Recipients and their businesses.
| | P |
| 2.2 | Provide management and overall responsibility for Eligible Recipient Business Continuity including in the case of a Business Continuity event.
| | P |
| 2.3 | Provide ongoing Business Continuity planning with respect to Supplier, Supplier Affiliate and Subcontractor, and their business.
| P | |
| 2.4 | Provide management and overall responsibility for Supplier Business Continuity.
| P | |
| 2.5 | Provide coordination and management of overall disaster recovery program for in-scope Services as described in this Schedule.
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 115 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier
| CoreLogic |
| 2.6 | With respect to the Disaster Recovery Plans (“DRPs”) identified in Schedule A-2.12.1 that have been implemented and are in effect as of the Supplement Effective Date (the “Existing DRPs”), administer a central repository for all Existing DRPs and associated technical backup, recovery, retention and contingency procedures documentation which is accessible by CoreLogic.
| P | |
| 2.7 | With respect to the new or additional DRPs developed by the Parties pursuant to the processes described in this Schedule (“New DRPs”), administer a central repository for all New DRPs and associated technical backup, recovery, retention and contingency procedures documentation which is accessible by CoreLogic.
| P | |
| 2.8 | Provide tool that serves as the repository for DRPs. | P | |
| 2.9 | Communicate to Supplier changes in the business requirements for the DRPs and request necessary changes thereto.
| | P |
| 2.10 | Update Existing DRPs and New DRPs as necessary, but no less than semi-annually, to address material changes in the environment or DR solution.
| P | A |
| 2.11 | Maintain all changes to the DRPs.
| P | |
| 2.12 | Coordinate and manage planning meetings with CoreLogic staff to align and communicate all tasks, timelines, dependencies and goals.
| P | |
| 2.13 | Provide annual assessment and risk analysis to define industry best practice disaster management and recovery plans appropriate to the Services. Communicate analysis to CoreLogic. | P | |
| 2.14 | Develop detailed roles and responsibilities matrix for all parties involved in disaster recovery planning, maintenance and execution. Review and update annually or as required. | P | A |
| 2.15 | Arrange and schedule for secure shipment pickup and storage of off-site media during disaster recovery (“DR”) test and DR declaration. | P | |
| 2.16 | Maintain and support current Equipment, Software, Third Party Agreements and other Infrastructure employed in connection with Existing DRPs and New DRPs. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 116 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
3. DISASTER RECOVERY PLANNING AND IMPLEMENTATION
|
| | | |
No.
| Description | Supplier | CoreLogic |
| 3.1 | Provide disaster recovery (“DR”) requirements based upon information regarding critical business Applications, prioritization of critical business Applications and established recovery time objectives (“RTOs”) and recovery point objectives (“RPOs”).
| | P |
| 3.2 | Facilitate the gathering of DR requirements from CoreLogic; manage and maintain DRP-related documentation provided by CoreLogic.
| P | |
| 3.3 | Prepare gap analysis, including cost savings ideas, between DR requirements identified as per above and scope of Existing DRPs, associated documentation and existing DR capability. | P | |
| 3.4 | Facilitate and assist in review of CoreLogic’s business impact analyses regarding gaps identified by Supplier as per above.
| P | |
| 3.5 | Develop specific recommendations to address identified gaps to Existing DRPs including recommendations regarding Equipment, Software, Third Party Contracts and Services to support Existing DRPs.
| P | A |
| 3.6 | Finalize gap analysis and DR strategy assessment, and modify Existing DRPs as required.
| P | A |
| 3.7 | At CoreLogic’s request, develop additional New DRPs in accordance with Supplier processes and methodologies.
| P | A |
| 3.8 | In connection with the Existing DRPs, manage, maintain and test the existing CoreLogic designated recovery environments.
| P | |
| 3.9 | In connection with the New and Existing DRPs and the gap analysis described above, as requested by CoreLogic, provide specifications and pricing information for Equipment that is not covered by Resource Unit-Based Charges.
For Equipment and other applicable Infrastructure covered under a Resource Unit-Based Charge, Supplier shall provide Equipment to remediate identified gaps.
| P | A |
| 3.10 | As requested by CoreLogic, implement the Equipment, Software, Third Party Contracts and Services and update the corresponding DRP promptly after the completion of such implementation Project to record any changes to the DRP required by such implementation.
| P | A |
| 3.11 | Monitor changes to the production environment and update the DR environment accordingly. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 117 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
4. DISASTER RECOVERY TESTING
|
| | | |
No.
| Description | Supplier | CoreLogic |
| 4.1 | After an update to an existing DRP, or the creation of a new DRP, perform table top DR simulation exercise to test workability.
| P | |
| 4.2 | Review backup, recovery and data replication procedures specified in the DRPs *** each year or as otherwise requested by CoreLogic.
| P | |
| 4.3 | Implement changes to backup and recovery system requested by CoreLogic as well as an agreed upon data replication schedule based on recommendations provided by Supplier to meet Existing and New RTO/RPO times.
| P | A |
| 4.4 | In accordance with the CoreLogic established Disaster Recovery Test schedule, conduct, document and lead functional DRP tests (***) starting in *** and during the established testing window for all applications within the defined Data Center environment, and *** DRP tests per year for the CoreLogic business units unable to meet the scheduled DR test cycle.
| P | A |
| 4.5 | Confirm that recovery environment is operational and available for CoreLogic Application recovery and testing activities.
| P | A |
| 4.6 | Perform business Application recovery activities, including database and Application restores, data validity checks, executing test scripts, and testing end user connectivity.
| | P |
| 4.7 | Manage and participate in scheduled DRP tests and provide test results in a CoreLogic-approved format within *** days of test completion that includes (i) identified deficiencies, (ii) RTO/RPO successes and failures; (iii) actual recovery and recovery point performance; (iv) detailed timeline of disaster recovery activities; (v) proposals for improvement and changes (vi) scope and objectives of test with criteria for measuring their success (vii) performance against scope and objectives (viii) plans for mitigating any deficiencies identified in testing to the DRP for CoreLogic’s review and approval. Store results in central repository accessible by CoreLogic.
| P | A |
| 4.8 | Coordinate with CoreLogic and CoreLogic business unit personnel in DRP planning, and testing of DRP tests.
| P | |
| 4.9 | In accordance with the DRP, manage, document and coordinate the logistics and resources to support the execution of recovery plans.
| P | |
| 4.10 | For each DRP test, manage and execute disaster recovery activities in accordance with the DRPs.
| P | |
| 4.11 | Coordinate directly with CoreLogic personnel to perform business unit testing during Disaster Recovery Tests.
| P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 118 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| 4.12 | Create, maintain and update for CoreLogic’s review and approval a document that provides an overview of the DRP testing program that CoreLogic may distribute to its customers.
| P | A |
| 4.13 | If the Existing or New DRP fails to meet its success criteria, promptly identify any failures, and within *** days, provide a remediation plan for Disaster Recovery Test failures, including a schedule to revalidate the test, and, if required, conduct another test of the DRP to validate failure has been remediated. | P | |
| 4.14 | Identify, create and maintain appropriate test environment to perform required tests of Existing and New DRP | P | |
| 4.15 | Coordinate as appropriate with CoreLogic customers during DR testing. | P | A |
| 4.16 | Make reasonable effort to resolve issues encountered during DRP test. | P | |
| 4.17 | In accordance with DRP, meet all RPO and RTO objectives. Supplier shall provide and configure Supplier Services and Systems such that a disaster will only interrupt such Services and Systems for a time no greater than the CoreLogic defined Recovery Time Objectives (RTO) and loss of data will not exceed CoreLogic defined Recovery Point Objectives (RPO). | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 119 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
5. ACTUAL DISASTER
|
| | | |
No.
| Description | Supplier | CoreLogic |
| 5.1 | Advise CoreLogic and any applicable third party providing the recovery infrastructure (if applicable) of Incidents or events that may impact CoreLogic business, and provide information to assist CoreLogic in the declaration of disaster.
| P | A |
| 5.2 | In accordance with the DRPs, provide and coordinate with CoreLogic regarding all stages of disaster reporting (e.g., executing call trees, communication protocols, etc.), from notification or knowledge of the disaster through and including resuming normal operations.
| P | |
| 5.3 | Provide business users and other CoreLogic staff specified in the DRP to support recovery as required under the DRP.
| | P |
| 5.4 | Provide Supplier Personnel who will perform the Supplier-required DRP activities throughout the period of time that the disaster is declared until normal processing capability is restored.
| P | |
| 5.5 | Execute Supplier responsibilities under the applicable DRP by confirming that recovery environment is operational and available for Application and database recovery and use.
| P | |
| 5.6 | Execute CoreLogic’s responsibilities under the applicable DRP including performing database restores, data validity check and Application restores, executing recovery scripts and confirming end user connectivity.
| | P |
| 5.7 | Communicate appropriate messages regarding disaster to Authorized Users as designated by the CoreLogic Relationship Manager.
| P | A |
| 5.8 | Provide Supplier staff for the duration of the disaster until processing capabilities are restored to pre-disaster state. | P | |
| 5.9 | Supplier will support CoreLogic’s declaration of a disaster which will require Supplier to execute one or all DRPs | | P |
| 5.10 | In accordance with DRP, meet all RPO and RTO objectives. Supplier shall provide and configure *** such that a disaster will only interrupt such Services and Systems for a time no greater than the CoreLogic defined Recovery Time Objectives (RTO) and loss of data will not exceed CoreLogic defined Recovery Point Objectives (RPO). | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 120 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| BU Name | DR Application | Actual RPO | Dell | Total End-to-end | RPO Comments |
| | | | Infrastructure | RTO | |
| | | | RTO | (Infrastructure and | |
| | | | (Infrastructure) | Apps) | |
| Advisory Data Valuations | *** | *** | *** | *** | |
| Advisory Data Valuations | *** | *** | *** | *** | |
| Appraisal Management Services | *** | *** | *** | *** | |
| Appraisal Management Services | *** | *** | *** | *** | |
| Appraisal Management Services | *** | *** | *** | *** | |
| Appraisal Management Services | *** | *** | *** | *** | |
| BPO Services | *** | *** | *** | *** | |
| BPO Services | *** | *** | *** | *** in last test - project 7237
*** | |
| Claims Services | *** | *** | *** | *** | |
| Claims Services | *** | *** | *** | *** | |
| Claims Services CMAX | *** | *** | *** | *** | |
| Commercial Real Estate Services | *** | *** | *** | *** | |
| Commercial Real Estate Services | *** | *** | *** | *** | |
| Commercial Real Estate Services | *** | *** | *** | *** | |
| Commercial Real Estate Services | *** | *** | *** | *** | |
| Commercial Real Estate Services | *** | *** | *** | *** | |
| Consumer Services | *** | *** | *** | *** | |
| Consumer Services | *** | *** | *** | *** | |
| CoreLogic Financial Systems | *** | *** | *** | *** | |
| CoreLogic Financial Systems | *** | *** | *** | *** | |
| CoreLogic Financial Systems | *** | *** | *** | *** | |
| CoreLogic Financial Systems | *** | TBD | | TBD | In-Flight Project Objectives not set |
| CoreLogic Financial Systems | *** | *** | *** | *** | |
| CoreLogic Financial Systems | *** | *** | *** | *** | |
| CoreLogic Financial Systems | *** | *** | *** | *** | |
| CoreLogic Financial Systems | *** | *** | *** | *** | |
| CoreLogic Financial Systems | *** | *** | *** | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 121 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| BU Name | DR Application | Actual RPO | Dell | Total End-to-end | RPO Comments |
| | | | Infrastructure | RTO | |
| | | | RTO | (Infrastructure and | |
| | | | (Infrastructure) | Apps) | |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| CoreLogic Information Solutions | *** | RPO Managed by CoreLogic | *** | *** | RPO Managed by CoreLogic |
| Corporate Services Marketing | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Credco | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Credco | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Credco | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Credco | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Credco | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Credco | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Credco | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Credco | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Credco | *** | *** | *** | *** | RPO Managed by CoreLogic |
| CredStar | *** | *** | *** | *** | RPO Managed by CoreLogic |
| CredStar | *** | *** | *** | *** | RPO Managed by CoreLogic |
| CredStar | *** | *** | *** | *** | RPO Managed by CoreLogic |
| CredStar | *** | *** | *** | *** | RPO Managed by CoreLogic |
| CredStar | *** | *** | *** | *** | RPO Managed by CoreLogic |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 122 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| BU Name | DR Application | Actual RPO | Dell | Total End-to-end | RPO Comments |
| | | | Infrastructure | RTO | |
| | | | RTO | (Infrastructure and | |
| | | | (Infrastructure) | Apps) | |
| CredStar | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Data Operations | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Data Operations | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Data Operations | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Data Trace | *** | *** | *** | *** | Server RPO Managed by First American |
| Default Technologies | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Default Technologies | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Default Technologies | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Default Technologies | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Document Solutions | *** | *** | *** | *** | |
| Document Solutions | *** | *** | *** | *** | |
| Due Diligence | *** | TBD | | TBD | In-Flight Project Objectives not set |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 123 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| BU Name | DR Application | Actual RPO | Dell | Total End-to-end | RPO Comments |
| | | | Infrastructure | RTO | |
| | | | RTO | (Infrastructure and | |
| | | | (Infrastructure) | Apps) | |
| Enterprise Technology Services | *** | *** | *** | *** | |
| Enterprise Technology Services | *** | *** | *** | TBD since production upgrade, Goal ***or less. | |
| Enterprise Technology Services | *** | *** | *** | More than ***, but less than *** | |
| Enterprise Technology Services | *** | *** | *** | *** | |
| Enterprise Technology Services | *** | *** | *** | *** | |
| Enterprise Technology Services | *** | *** | *** | *** | |
| ETS Corporate Systems | *** | *** | *** | *** | |
| ETS Corporate Systems | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Field Services | *** | *** | *** | ***Minutes | |
| Field Services | *** | *** | *** | TBD since 2009 - project 7239
*** | |
| Field Services | *** | *** | *** | TBD since 2009 - project 7239 *** | |
| Field Services | *** | *** | *** | TBD since 2009 - project 7239
*** | |
| Finiti | *** | TBD | *** | TBD | |
| Finiti | *** | TBD | *** | TBD | |
| Finiti | *** | TBD | *** | TBD | |
| Finiti | *** | TBD | *** | TBD | |
| Flood Services | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Flood Services | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Flood Services | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Flood Services | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Flood Services | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Flood Services | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Flood Services | *** | *** | *** | *** | RPO Managed by CoreLogic |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 124 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| BU Name | DR Application | Actual RPO | Dell | Total End-to-end | RPO Comments |
| | | | Infrastructure | RTO | |
| | | | RTO | (Infrastructure and | |
| | | | (Infrastructure) | Apps) | |
| Flood Services | *** | *** | *** | *** | RPO Managed by CoreLogic |
| International Tax Service | *** | *** | *** | *** | |
| International Tax Service | *** | *** | *** | *** | |
| MarketLinx | *** | *** | *** | *** | RPO Managed by CoreLogic |
| Operational Services | *** | *** | *** | *** | |
| Operational Services | *** | *** | *** | *** | |
| Operational Services | *** | *** | *** | *** | |
| Operational Services | *** | *** | *** | *** | |
| Operational Services | *** | *** | *** | *** | |
| Operational Services | *** | *** | *** | *** | |
| Operational Services | *** | *** | *** | *** | |
| REO Services | *** | *** | *** | *** | |
| REO Services | *** | *** | *** | *** | |
| REO Services | *** | *** | *** | *** | |
| REO Services | *** | *** | *** | *** | |
| REO Services | *** | *** | *** | *** | |
| REO Services | *** | *** | *** | *** | |
| SafeRent (Multi-Family Services) | *** | *** | *** | TBD | Server RPO Managed by CoreLogic
iSeries RPO Managed by Dell |
| SafeRent (Multi-Family Services) | *** | *** | *** | TBD | Server RPO Managed by CoreLogic
iSeries RPO Managed by Dell |
| SafeRent (Multi-Family Services) | *** | *** | *** | TBD | Server RPO Managed by CoreLogiciSeries RPO Managed by Dell |
| SafeRent (Multi-Family Services) | *** | *** | *** | TBD | Server RPO Managed by CoreLogic
iSeries RPO Managed by Dell |
| SafeRent (Multi-Family Services) | *** | *** | *** | TBD | Server RPO Managed by CoreLogic
iSeries RPO Managed by Dell |
| Solutions Express | *** | *** | *** | *** | |
| STARS | *** | TBD | *** | TBD | |
| STARS | *** | TBD | *** | TBD | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 125 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| BU Name | DR Application | Actual RPO | Dell | Total End-to-end | RPO Comments |
| | | | Infrastructure | RTO | |
| | | | RTO | (Infrastructure and | |
| | | | (Infrastructure) | Apps) | |
| STARS | *** | TBD | *** | TBD | |
| STARS | *** | TBD | *** | TBD | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Tax Services | *** | *** | *** | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 126 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| BU Name | DR Application | Actual RPO | Dell | Total End-to-end | RPO Comments |
| | | | Infrastructure | RTO | |
| | | | RTO | (Infrastructure and | |
| | | | (Infrastructure) | Apps) | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Tax Services | *** | TBD | | TBD | In-Flight Project Objectives not set |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Tax Services | *** | *** | *** | *** | |
| Verification Services | *** | TBD | | TBD | In-Flight Project Objectives not set |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 127 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-3
SERVICE LEVEL METHODOLOGY
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 128 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-3
Service Level Methodology
| |
| 1.1 | Agreement. This Schedule A-3 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to this Supplement, or the other Schedules to the MSA or this Supplement. |
The following terms have the meanings given below:
“At-Risk Amount” shall mean, for any given month during the Term, *** percent (***%) of the actual Charges payable by CoreLogic to Supplier during such month (***, ***, and any ***).
“Critical Service Level” shall have the meaning set forth in Schedule 1 to the MSA.
“Critical Service Level Default” shall have the meaning set forth in Section 5.1(b).
“Key Measurement” means a Service Level identified in Schedule A-3.1 as a “Key Measurement” that represents a level of performance for which no Service Level Credit is payable in the event of a Service Level Default, but which is meaningful to CoreLogic’s business. In many cases, Key Measurements are derived from CoreLogic’s SLA Books in existence prior to the Supplement Effective Date.
“Key Measurement Default” shall have the meaning set forth in Section 5.1(c).
“Key Measurement Default Threshold” shall have the meaning set forth in Section 5.2(b).
“Low Volume” shall have the meaning set forth in Section 7.
“Measurement Methods” shall have the meaning set forth in Section 1.6.
“Measurement Period” means the time during, or frequency by, which a Service Level shall be measured. Unless otherwise set forth in Schedule A-3.1 for a specific Service Level, the Measurement Period for each Service Level shall be on a monthly basis.
“Measured Volume” shall have the meaning set forth in Section 7.
“Rolling Three Month Period” shall have the meaning set forth in Section 5.2.
“Service Level” shall have the meaning set forth in Schedule 1 to the MSA.
“Service Level Credit” shall have the meaning set forth in Schedule 1 to the MSA.
“Service Level Credit Allocation” shall have the meaning set forth in Section 5.2.
“Service Level Default” shall mean a Critical Service Level Default or a Key Measurement Default.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 129 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 1.4 | Schedules. The following Schedules are attached hereto and are hereby incorporated by reference into this Schedule A-3: |
Schedule A-3.1 (Service Level Matrix). Schedule A-3.1 sets forth (a) the required performance level for each Service Level, as well as the Service Level Credit Allocation Percentage for such Service Level, (b) description and definition of each Service Level and (c) the tools and methodologies (including Measurement Methods) Supplier shall use to monitor and report on the Service Levels and Supplier’s reporting commitments consistent with the Agreement (including this Schedule A-3).
Schedule A-3.2 Reserved.
Schedule A-3.3 (Critical Deliverables). Schedule A-3.3 sets forth the Critical Deliverables for Supplement A, along with the due date and Deliverable Credit for each Critical Deliverable.
| |
| 1.5 | Cooperation. The achievement of the Service Levels by Supplier may require the coordinated, collaborative effort of Supplier with Third Party Contractors. Supplier shall provide a single point of contact for the prompt resolution of all failures to provide the Services in accordance with the Service Levels, regardless of whether the reason for each such failure was caused by Supplier or a Third Party Contractor. |
| |
| 1.6 | Measuring and Monitoring Tools. |
| |
| (a) | Supplier shall measure and monitor its performance of the Services against the Service Levels using the necessary measurement and monitoring tools and procedures set forth in Schedule A-3.1 (the “Measurement Methods”). Upon *** (***) *** prior written notice to CoreLogic and subject to Section 9.6(c) of the MSA, Supplier may make changes to the Measurement Methods for Service Levels applicable to *** provided such change is being implemented with respect to all similarly situated Supplier customers and Supplier can demonstrate that the Measurement Method accurately measures such Service Level and does not affect the required level of performance for such Service Level. |
| |
| (b) | A failure by Supplier to measure Service Level performance for a Critical Service Level, in accordance with the Measurement Methods shall be a Service Level Default, and continue to be a Service Level Default each month until Supplier measures the Service Level performance in accordance with the Measurement Methods, unless Supplier can otherwise prove that a Service Level Default did not occur (i.e., by validating that the received Service met the Critical Service Level) and *** to *** explanation. |
| |
| (c) | If there are any Critical Service Levels for which the Measurement Methods have not been agreed upon as of the Supplement Effective Date, and if Supplier fails to propose and implement a Measurement Method for such Critical Service Level that is *** in *** prior to the date when Service Level Credits apply to such Critical Service Level, then such failure shall be a Service Level Default each month until such time as Supplier proposes and implements a Measurement Methodology *** in ***. |
| |
| (d) | Measurement Methods for new Service Levels and changes to Measurement Methods for existing Service Levels shall be agreed upon by the Parties in connection with the process described in Section 5.6(a) and implemented in accordance with the Agreement. |
| |
| (e) | *** (***) *** following the Supplement Effective Date and every *** (***) *** thereafter until the *** anniversary of the Supplement Effective Date and thereafter as agreed by the Parties, Supplier shall review all Service Levels and related Measurement Methods and assess whether any changes in such Measurement Methods are required to collect and accurately reflect Supplier’s performance and related data. Supplier shall promptly notify CoreLogic of any recommended |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 130 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
changes in Measurement Methods as a result of such assessment, and promptly implement such changes to the extent approved by CoreLogic.
| |
| (f) | Detailed performance information used to calculate each Service Level will be maintained by Supplier as Contract Records during the period required by Section 9.10(a) of the MSA. |
| |
| (g) | Upon CoreLogic’s request, Supplier shall provide, or provide access to, such performance information to allow CoreLogic to verify the accuracy of reported Service Level measurements. |
| |
| 2. | CRITICAL SERVICE LEVELS |
In the event of a Critical Service Level Default in any given month, Supplier shall issue CoreLogic a Service Level Credit in accordance with Section 5.2. Supplier’s required level of performance associated with each Critical Service Level is set forth in Schedule A-3.1.
The Key Measurements are set forth in Schedule A-3.1. Key Measurements are not subject to Service Level Credits except as provided in Section 5.1(c) and Section 5.2(b). All of Supplier’s obligations related to Service Levels shall apply to Key Measurements. Key Measurement Defaults shall be allocated in accordance with Section 5.2.
Unless otherwise provided in this Schedule, Supplier shall measure and report on its performance of the Services against each Critical Service Level and Key Measurement on a monthly basis. Supplier shall provide, as part of the Services and Supplier’s monthly performance reports, a set of hard- and soft-copy reports to verify Supplier’s performance and compliance with such Service Levels. Upon CoreLogic’s reasonable request, Supplier shall provide detailed supporting information for each report to CoreLogic in machine-readable form suitable for use on a personal computer. The raw data and detailed supporting information shall be CoreLogic Confidential Information (provided that Supplier shall have the right to use such raw data and detailed supporting information for its internal business purposes in measuring and improving its service performance and delivery across Supplier’s customers so long as CoreLogic’s confidentiality is preserved in accordance with Article 13 of the MSA), and CoreLogic may access such information at any time during the Term (which access shall be on-line and real-time, where reasonably feasible).
| |
| 5.1 | Service Level Defaults. |
| |
| (a) | Schedule A-3.1 sets forth the information required to calculate Service Level Credits that Supplier shall apply against monthly Charges in the event of a Critical Service Level Default and such failure is not excused pursuant to Section 9.3. |
| |
| (b) | A “Critical Service Level Default” shall be deemed to occur whenever Supplier’s level of performance for a particular Critical Service Level fails to meet or exceed the level performance specified in Schedule A-3.1 for such Critical Service Level in a given month. |
| |
| (c) | A “Key Measurement Default” shall be deemed to occur whenever Supplier’s level of performance for a particular Key Measurement fails to meet or exceed the level of performance specified in Schedule A-3.1 for such Service Level in a given month. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 131 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (d) | If Supplier fails to meet a Service Level in a given month, CoreLogic may, in its discretion and at no additional cost to CoreLogic, require Supplier to perform a Root Cause Analysis to investigate such failure to meet such Service Level. CoreLogic may, in its discretion, take reasonable steps to verify the results of such Root Cause Analysis. |
| |
| 5.2 | Calculation of Service Level Credits. |
| |
| (a) | For each Critical Service Level Default, Supplier shall pay to CoreLogic a Service Level Credit that will be computed in accordance with the following formula: |
Service Level Credit = A x B x C
Where:
A = The applicable percentage allocated to the applicable Critical Service Level in which the Critical Service Level Default occurred (the “Service Level Credit Allocation”). CoreLogic may from time to time during the Term change the Service Level Credit Allocations in accordance with Section 5.6 of this Schedule; provided that in no event shall the Service Level Credit Allocation for any single Service Level be more than *** percent (***%). As of the Supplement Effective Date, the Service Level Credit Allocations are set forth in Schedule A-3.1.
B = The monthly At Risk Amount, in dollars.
C = a number determined as follows:
C = *** (***) if during the *** (***) *** months, including the current month in which the Service Level Default occurred, (the “*** Month Period”) the number of Critical Service Level Defaults that have occurred with respect to the applicable Critical Service Level are less than *** (***).
C = *** (***) if during the *** Month Period the number of Critical Service Level Defaults that have occurred with respect to the applicable Critical Service Level are equal to *** (***).
C = *** (***) if during the *** Month Period the number of Critical Service Level Defaults that have occurred with respect to the applicable Critical Service Level are greater than *** (***).
| |
| (b) | For every *** (***) Key Measurement Defaults that occur during a given month (the “Key Measurement Default Threshold”), Supplier shall pay to CoreLogic a Service Level Credit equal to *** percent (***%) of the At Risk Amount. For example, in a given month, if there are between *** (***) and *** (***) Key Measurement Defaults, Supplier shall pay to CoreLogic a Service Level Credit equal to *** percent (***%) of the At Risk Amount for such month, and if there are between *** (***) and *** (***) Key Measurement Defaults, Supplier shall pay to CoreLogic a Service Level Credit equal to *** percent (***%) of the At Risk Amount for such month, each as calculated in the prior sentence. If the number of Key Measurements is in excess of *** (***), the Key Measurement Default Threshold shall be adjusted to equal *** and *** percent (***%) of the total number of Key Measurements, rounded down to the largest whole number. For example, if there are *** (***) Key Measurements, the Key Measurement Default Threshold would be *** (***). |
5.3 Multiple Critical Service Level Defaults, the At Risk Amount, Notification, Reporting and Invoicing
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 132 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (a) | Subject to Section 9.3, if more than one Critical Service Level Default has occurred in a single month, the sum of the corresponding Service Level Credits shall be credited to CoreLogic. |
| |
| (b) | In no event shall the amount of Service Level Credits credited to CoreLogic with respect to all Critical Service Level Defaults and Key Measurement Defaults occurring in a single month exceed, in total, the At Risk Amount. |
| |
| (c) | Supplier shall notify CoreLogic in writing if CoreLogic becomes entitled to a Service Level Credit, which notice shall be provided in the monthly performance report. |
| |
| (d) | The total Service Level Credits that Supplier will be obligated to pay to CoreLogic with respect to Service Level Defaults occurring each month shall be reflected as a credit to CoreLogic on the invoice for the month after the month in which the Service Level Default(s) giving rise to such credit(s) occurred. For example, if there is a Service Level Default in January, the Service Level Credit associated with such Service Level Default shall be credited to CoreLogic on the invoice submitted in February.*** |
| |
| 5.4 | Sample Calculation. Assume that Supplier fails to meet the Critical Service Level with respect to Availability of Production Online Systems (as defined in the Attachments). Assume that Supplier’s total charges to CoreLogic included in the At Risk Amount for the month in which the Service Level Default occurred were $***. The Service Level Credit due to CoreLogic for such Service Level Default would be computed as follows: |
A = ***% (i.e., the Service Level Credit Allocation Availability of Production Online Systems as shown on Schedule A-3.1),
multiplied by
B = $*** (i.e., *** percent (***%) of $***)
Multiplied by
C = *** (see Section 5.2)
= $*** (i.e., the amount of the Service Level Credit)
| |
| 5.5 | Deletions and Demotions, and Promotions of Service Levels. CoreLogic may delete, demote or promote Critical Service Levels or Key Measurements as follows: |
| |
| (b) | Deletions and Demotions. CoreLogic may delete Key Measurements or demote Critical Service Levels to become Key Measurements by sending notice to Supplier at least *** (***) *** prior to the date that such changes are to be effective. |
| |
| (c) | Promotions. CoreLogic may promote Key Measurements to become Critical Service Levels by sending notice to Supplier at least *** (***) *** prior to the date that such promotions of such Key Measurements are to be effective. CoreLogic will adjust the sum total of the Service level Credit Allocations percentages for all Critical Service Levels identified in Schedule A-3.1 as necessary to equal 100%. |
| |
| 5.6 | Additions of Service Levels and Modifications of Service Level Credit Allocations. CoreLogic may add, modify or delete Key Measurement or Critical Service Levels as follows: |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 133 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (a) | Additions. Except as provided in the next sentence, CoreLogic may add Key Measurements by sending notice to Supplier at least *** (***) *** prior to the date that such additions to Service Levels are to be effective. The sum total of the Service level Credit Allocations percentages for new and existing Critical Service Levels identified in Schedule A-3.1 will be adjusted as necessary to equal 100%. The Parties shall agree upon the required level of performance for each Service Level. In the event that the Parties are unable to reach agreement upon such Service Levels, such Service Levels shall be established in one of the following ways: |
| |
| (i) | Where at least *** (***) months of service measurements exist for the Service that is being provided by Supplier, the Parties agree that the Critical Service Level shall be defined as the *** of (A) the *** *** measurement achieved during those prior *** months and (B) the result of (1) the *** of such service measurements (excluding the *** measurement) for such *** (***) month period, *** (2) *** multiplied by the *** of such measurements. |
| |
| (ii) | Where no measurements exist for a particular Service, the Parties shall attempt to agree on the Service Level using industry standard measures or third party advisory services (e.g., Gartner). If the Parties are unable to agree on the Service Level, |
Supplier will implement and report on the actual performance of Supplier as to the new Service Level for *** (***) months on a monthly basis, and the level of performance required for such Service Level will be set to the *** of such *** (***) monthly measures.
| |
| (c) | Modifications. CoreLogic may modify the Service Level Credit Allocations for any Critical Service Levels by sending notice to Supplier at least *** (***) days prior to the date that such modifications to the Service Level Credit Allocations are to be effective. CoreLogic will adjust the sum total of the Service level Credit Allocations percentages for all Critical Service Levels identified in Schedule A-3.1 as necessary to equal 100%. |
| |
| 5.7 | Notices. CoreLogic may send a notice described in Section 5.5 and Section 5.6 (which notice may contain multiple changes of a type described in either section) not more than once each calendar month. The Parties acknowledge that the intent of the changes described in Section 5.5 and Section 5.6 shall be in order to achieve a fair, accurate, and consistent measurement of Supplier’s performance of the Services. All new Service Levels shall be quantifiable, measurable and objective. |
The Parties agree to the concept of continuous improvement in Supplier’s delivery of the Services and that the Service Levels will be modified during the Term to reflect this concept. To accomplish this, beginning with the *** anniversary of the Supplement Effective Date and continuing with every anniversary of the Supplement Effective Date thereafter, the Parties will meet and, using the previous twelve (12) months’ data, attempt in good faith to determine appropriate modifications to the Service Levels to reflect, among other things, improvements in Supplier’s delivery of the Services and advancements in the market. If, within *** (***) *** after the applicable anniversary of the Supplement Effective Date, the Parties are unable to agree upon such modifications, then each Service Level (subject to the following sentence, and other than Service Levels expressly marked as not being subject to continuous improvement in Schedule A-3.1, if any) shall be modified in accordance with the formula set forth below. For any Service Level added after the Supplement Effective Date, this Section shall apply beginning *** following the effective date of such Service Level; provided that, if, prior to the effective date of such Service Level, *** can demonstrate to *** that an equivalent Service Level exists for which this Section ***, *** may determine whether *** Service Level
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 134 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
(and if *** cannot demonstrate to *** that an equivalent Service Level exists for which this Section ***, then *** may determine whether this Section *** Service Level).
| |
| (a) | Each Service Level will be reset by adding to such Service Level a sum equal to *** percent (***%) of the difference between *** percent (***%) and the then-current Service Level. |
| |
| (b) | For example, if the Service Level being adjusted were ***%, the increase would be ***% (i.e., from ***% to ***%). |
Definition and Calculation. With respect to Service Levels identified in Schedule A-3.1 as “Low Volume Eligible” where the measurement of the Service Level is based on a volume of data points in any given Measurement Period (“Measured Volume”) that is so low that a *** would otherwise result in a Service Level Default (“***”), subject to the additional requirements that apply in such case as described in the “***” column in Schedule A-3.1, then a *** that would otherwise result in a Service Level Default shall not result in a Service Level Default (unless perfect (100%) performance is required):
| |
| 7.1 | For example, if an applicable “Low Volume Eligible” Service Level is ***%, there would need to be at least *** measured tasks in order to allow Supplier to meet the Service Level in a Measurement Period in which it has *** (***) ***. Thus, if the Service Level is ***%, and if the total Measured Volume for such Service Level in the Measurement Period is 18, then a single miss of such Service Level in such Low Volume Measurement Period would not result in a Service Level Default. |
| |
| 7.2 | Effect of Zero Measured Volumes. If the Measured Volume for any Critical Service Level during a Measurement Period is zero (0), then no Service Level Default shall be deemed to have occurred and there shall be no Service Levels Credits applicable for such Service Level for such Measurement Period. |
| |
| 7.3 | *** Service Levels. When *** Service Level is ***, the Service Level shall be ***, if at all, in a *** with the *** in which *** Service Levels are adjusted in Schedule A-3.1. If *** Service Levels are not *** low volumes, the *** Service Level will not be *** low volumes. |
| |
| 8.1 | Schedule A-3.3 sets forth the Critical Deliverables for Supplement A and the Deliverable Credits that shall be payable by Supplier to CoreLogic as specified in Schedule A-3.3. The Deliverable Credits imposed for Supplier’s failure(s) to meet Critical Deliverables shall be in addition to, and shall not be included in, the calculation related to the At Risk Amount. The Deliverable Credits for Critical Deliverable failures shall be reflected on the monthly invoice containing Charges for the month after the Critical Deliverable failure occurred. For example, the amount of a Deliverable Credit payable for a Critical Deliverable failure in August shall be set forth in the monthly invoice for September Charges issued in September. |
| |
| 9.1 | Times. Unless otherwise provided in this Schedule, all references in this Schedule to times shall refer to Pacific Standard Time or Pacific Daylight Time, as applicable. |
| |
| 9.2 | Single Incident / Multiple Defaults. If a single incident results in the failure of Supplier to meet more than one Service Level, *** shall have the right to *** of the associated Service Level Defaults for which it will be entitled to receive a Service Level Credit. CoreLogic shall not be entitled to a Service Level Credit for each of such Service Level Defaults. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 135 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 9.3 | Excused Performance. Supplier shall not be responsible for a failure to meet a Service Level or a due date associated with a Critical Deliverable to the extent such failure is *** attributable to circumstances where Supplier is relieved of its obligations pursuant to Sections 10.2 (Supplier Excused Performance) or 9.14 (Force Majeure) of the MSA or as provided in the “Exceptions” column of Schedule A-3.1. |
| |
| 9.4 | Commencement of Obligations. Except as provided otherwise in Schedule A-3.1, Supplier shall commence measuring and reporting its performance against the Service Levels on the Commencement Date of the applicable Services. Service Level Credits shall apply with effect from ***, 20*** or such other date as the Parties may agree (and provided that, if Supplier requests to change the date on which Service Level Credits will begin to apply for specific Service Levels based upon good faith business reasons, CoreLogic will not unreasonably withhold its consent to change such date). Prior to ***, 20*** Supplier shall perform the Service Levels in accordance with the standard set forth in the second sentence of Section 7.1 of the MSA. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 136 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
Schedule A-3.1
Service Level MATRIX
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 137 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
1.1 Agreement. This Schedule A-3.1 (this “Schedule”) is attached to and incorporated by reference in Supplement A, dated July 19, 2012, to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”).
1.2 References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided.
1.3 Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A‑1 to Supplement A or elsewhere in the Agreement.
The terms below shall have the following meanings:
“Enterprise Infrastructure Applications” include *** anything defined as enterprise system in ***.
“High Availability” or “HA” means redundancy such that a single operating system or device failure will not degrade the performance of a Service or cause a Service to become unavailable.
“Normal Patch” has the meaning giveb by the applicable product vendor.
“*** Hardware Exception” means Supplier’s failure to meet the timing requirements of any single Unit that is subject to the applicable Service Level shall be excused if and to the extent such failure is caused by the failure of a *** to repair or replace ***, other than *** that is included within Supplier’s ***; but only if (i) Supplier uses commercially reasonable efforts to cause such *** to perform within the time frame required for such Unit, (ii) Supplier notifies CoreLogic promptly after such ***’s failure or delay and (iii) Supplier documents such failure in a Root Cause Analysis after such failure. Any time for which Supplier’s failure to meet the applicable timing requirement is excused by the immediately preceding sentence shall be removed (i.e., excluded) from the calculation of total time to restore such Unit as defined in the Service Level definition. For purposes of the *** Exception, “Unit” means the applicable unit of measurement for the applicable Service Level (e.g., Incident or other applicable unit that is being measured in accordance with the definition and formula for such Service Level).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 138 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Incident Management | | | | | | | | | | | | |
| | Incident Handling - Severity 1 (Critical): Percent of Severity 1 Incidents that are restored within the target timeframe | Critical Service Level | ***% of Incidents are restored within *** hours | Measures the time interval between an Incident record being registered in the service management tool for Severity 1 Incidents to the time normal service operation is restored via implementing a solution to the known error or by employing a workaround | Service Level Achievement = (A/B) * 100% | A = Count of Severity 1 Incidents resolved on time | B = Count of Severity 1 Incidents resolved for the Measurement Period | Restoration Time does not include the following:
* Time that Incident Tickets are in “suspend mode” due to previously unknown third-party software defects.
* Time that Incident Tickets are in “suspend mode” for equipment-related failures at non-Supplier Facilities.
* Time incurred restoring Application data and/or functionality from tape media after Supplier has returned Equipment to service.
* Third Party Hardware Exception
* Adjustments to the Service Levels approved by CoreLogic in its sole discretion pursuant to the last sentence of Section 4.4 of the MSA in order to permit the performance of new or additional work activities as contemplated by Section 4.4 of the MSA | OPAS Incident Tickets | 24x7 | Yes, provided that if any single Incident is not resolved within ***hours, then this *** exception shall not apply | No | ***% |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 139 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Incident Handling - Severity 2 (High): Percent of Severity 2 Incidents that are restored within the target timeframe | Critical Service Level | ***% of Incidents are restored within *** hours | Measures the time interval between an Incident record being registered in the service management tool for Severity 2 Incidents to the time normal service operation is restored via implementing a solution to the known error or by employing a workaround | Service Level Achievement = (A/B) * 100% | A = count of Severity 2 Incidents resolved on time | B = count of Severity 2 Incidents resolved for the Measurement Period | Restoration Time does not include the following:
* Time that Incident Tickets are in “suspend mode” due to previously unknown third-party software defects.
* Time that Incident Tickets are in “suspend mode” for equipment-related failures at non-Supplier Facilities.
* Time incurred restoring Application data and/or functionality from tape media after Supplier has returned Equipment to service.
* Third Party Hardware Exception
* Adjustments to the Service Levels approved by CoreLogic in its sole discretion pursuant to the last sentence of Section 4.4 of the MSA in order to permit the performance of new or additional work activities as contemplated by Section 4.4 of the MSA | OPAS Incident Tickets | 24x7 | Yes, provided that if any single Incident is not resolved within ***hours, then this *** exception shall not apply | Yes | ***% |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 140 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Incident Communication - Initial: Percentage of Severity 1 and Severity 2 Incidents that are communicated within the target timeframe | Key Measurement | ***% of Incidents are communicated within *** min | Measures the time interval between an Incident record being registered in the service management tool for Severity 1 and Severity 2 Incidents and the time a page/phone and email is sent to CoreLogic via OPAS’s FYI paging functionality. Elapsed number of minutes between the creation of a Severity Level 1 Incident and the time that Dell activates the Major Incident Management process (MIM), including notifying CoreLogic via using the standard High Priority Incident Notification Email template, to resolve such Severity Level 1 Incident, as reflected in the corresponding Incident Ticket. | Service Level Achievement = (A/B) * 100% | A = count of all Severity 1 & Severity 2 Incidents communicated within timeframe | B = count of Severity 1 and Severity 2 Incidents for the Measurement Period | * Does not include actual timestamp of receipt or any communication outside the automated Dell OPAS solution. | OPAS Incident Tickets | 24x7 | Yes, provided that if any single Incident is not resolved within ***minutes, then this *** exception shall not apply. | No | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 141 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Percentage of notifications (including automated alerts) that are accurately ***, *** and *** into the appropriate *** | Key Measurement | ***% of Severity 1 and 2 Incident notifications are accurately***, *** and *** into *** | Measures the percentage of incidents that are submitted to the ticketing system and have initial accurate categorization and assignment. For greatest accuracy, an Incident record should be created to track each inaccuracy. This would be measured using OPAS Incidents and reporting exceptions. | Service Level Achievement = (A/B) * 100% | A = count of total Severity 1 and 2 Incidents - count of Severity 1 and 2 inaccurate Incidents | B = total count of Severity 1 and 2 Incidents for the Measurement Period | * Any trusted or custom event source incidents (those submitted from outside the current Supplier tools or teams) will be agreed upon before being included in this calculation. | OPAS Incident Tickets | 24x7 | Yes | Yes | *** |
| | Incident Communication - Continual: Percentage of Incidents where updates are sent within the target | Key Measurement | 97% of Severity 1 updates sent every *** min | Measures the percentage of Incidents where communication to applicable stakeholders is performed within the appropriate timeframes for Severity 1 Incidents. Measurement of this will be through an agreed-upon process and timestamp within the OPAS system or transmission mechanism. | Service Level Achievement = (A/B) * 100% | A = count of total Severity 1 Incidents - count of Severity 1 Incidents with missed communication targets | B = total count of Severity 1 Incidents for the Measurement Period | * This does not include any communication outside the Supplier Service Management process. | OPAS Incident Tickets | 24x7 | Yes, provided that if any single updateis not resolved within ***(***) minutes, then this *** exception shall not apply. | No | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 142 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Problem Management | | | | | | | | | | | | *** |
| | Percentage of times a service impact document that covers the items listed below is completed for Severity 1 and Severity 2 Incidents and a Problem Review Meeting is completed within the target timeframe.
* Incident details through restoration
* Business impact
* RCA - if known
* Long term - fix if known | Key Measurement | ***% of service impact documents are created within*** for Severity*** Incidents | Within *** day, an initial Problem record is created (service impact document), and within *** business days, a draft Root Cause Analysis (RCA) is created. Measures the percentage of times a service impact document that covers the items listed below is completed for Severity 1 Incidents and a Problem Review Meeting is completed within the target timeframe.
* Incident details through restoration
* Business impact
* RCA - if known
* Long term - fix if known
Problem review meeting will be held and draft RCA will be ready within 48 hours. Actual closure of the RCA and Problem record is dependent on change activities needed. | Service Level Achievement = (A/B) * 100% | A =count of service impact documents created on time | B = total count of service impact documents required for the measurement period | * Excludes Problem records where CoreLogic critical/key stakeholder participation was not included within the target timeframe. | OPAS Problem Records | Business Hours | No | Yes | *** |
| | Asset Management | | | | | | | | | | | | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 143 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Asset inventory accuracy percentage | Key Measurement | ***% | Measures the accuracy of 10% of CIs and associated attributes (as defined in the Policy and Procedures Manual) stored in the Supplier Asset Management Database | Service Level Achievement = (A/B) * 100% | A = count of accurate reported CIs and associated attributes within sample set | B = total count of sample set CIs and associated attributes within the asset database for the Measurement Period | • Any assets within the sample set that are unavailable or inaccessible to Supplier tools and/or Supplier Personnel will be excluded from this calculation. | OPAS Asset Management and KACE | Business Hours | No | No | *** |
| | CSAT SLA | | | | | | | | | | | | *** |
| | CoreLogic Operation Managers customer satisfaction | Key Measurement | >=*** | Measures Supplier’s performance through a jointly created quarterly survey to ‘CoreLogic Operational Managers’ (Measured on a 1 - 5 scale). Expected survey set of 15-20 individuals. Average of all of the numeric scores selected by an Operational Managers in such survey (on a scale of 1 to 5, with 5 representing the highest level of satisfaction | Service Level Achievement = (A/B) * 100% | A = Sum of score responses from Operational Managers | B = Number of responses received | * Minimum acceptable returned surveys:: ***% of surveys returned | OPAS | NA | No | No | *** |
| | End User customer satisfaction | Key Measurement | >=*** | Measures Supplier’s performance through a survey sent to 30% of ‘End Users’ (Measured on a 1 - 5 scale). Average of all of the numeric scores selected by an Authorized User in such survey (on a scale of 1 to 5, with 5 representing the highest level of satisfaction | Service Level Achievement = (A/B) * 100% | A = Sum of score responses from Authorized Users | B = Number of responses received | * Minimum acceptable sample: ***% of surveys distributed | OPAS | NA | No | No | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 144 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | End User customer satisfaction drop | Key Measurement | *** | Number of months in a year (measured annually) when end user CSAT dropped below the prior month. Auto surveys based on services requested across all towers/functions. Compiled and summarized monthly. | Count of number of months with Auhtorized User satisfaction below prior month | NA | NA | * Measured at the anniversary of Service Commencement Date
* Drops in Authorized User satisfaction due to exceptional business events or due to CoreLogic directed | OPAS | NA | No | No | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 145 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Average Speed to Answer (ASA) - Percentage of help desk calls that are responded to within a target timeframe | Critical Service Level | ***% of calls answered <=*** seconds | Average Speed to Answer (ASA) is the average across all calls to the Service Desk for the time taken from when a call is deemed to have entered the “wait queue” (once the caller has made their final selection from the IVR (interactive voice response) menu) to the time a Service Desk agent answers the call for the purposes of providing Services | Service Level Achievement = A / B | A = the aggregate elapsed time in the Measurement Period within which telephone calls placed to the Service Desk by Authorized Users are answered | B = the total number of telephone calls to Service Desk in the applicable Measurement Period that are answered | Excludes abandoned calls. | Automatic Call Distribution (ACD) | 24x7 | No | Yes | ***% |
| | Average Handle Time (AHT) - Percentage of help desk calls that are handled to within the target timeframe | Key Measurement | KPI | Average Handle Time (AHT) is the average across all calls to the Service Desk for a Measurement Period of the time taken on the phone by the Service Desk agent for each call. Need to immediately make this a KPI on Day 1 | Service Level Achievement = A / B | A = total time in seconds of all calls answered by a Service Desk agent during the Measurement Period | B = number of answered calls | None | Automatic Call Distribution (ACD) | 24x7 | No | Yes, but capped at *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 146 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Abandon Rate - Maximum percentage of help desk calls that are abandoned | Key Measurement | <=***% | Call Abandon Rate measured as a percentage by adding the total number of calls to the Service Desk that hang up after selecting an option on the Voice Response Unit and before the call is answered by a live person and dividing this by the total number of calls to the Service Desk during the Measurement Period | Service Level Achievement = (A/B) * 100% | A = The number of abandoned calls queued to an agent | B = total calls answered + number of abandoned calls queued | None | Automatic Call Distribution (ACD) | 24x7 | No | Yes | *** |
| | First Call Resolution - Percentage of help desk calls that are resolved on the first call in less than *** minutes. | Critical Service Level | >=***% | First Call Resolution is the measurement of how many calls are resolved by the Service Desk upon first contact by the Authorized User. | Service Level Achievement = (A/B) * 100% | A = Total Incidents where Authorized User’s Incident is resolved on 1st contact at the Service Desk | B = Total Incident Tickets received by the Service Desk via phone contact | * Incidents received by the Service Desk by means other than telephone (for example, e‑mail, fax, self service portal) will be excluded when calculating attainment for this Service Level; Calls for which a ticket has already been opened for the same Incident. Incidents that cannot be resolved by the Service Desk, as defined in a list to be developed by Dell during Transition Period and updated from time to time, in each case approved by CoreLogic. | OPAS Incident Tickets | 24x7 | No | Yes | ***% |
|
| | |
| 2.3 | End User Device Support and Engineering | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 147 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | End User Devices (Desktops, Laptops, Printers, Phones and Wireless Devices) Note: Includes call center agents | | | | | | | | | | | | |
| | End User Device Setup (new user) - Percentage of new user setups that are successfully completed within the target timeframe | Key Measurement | ***% of requests completed within *** days | Measures the percentage of New Authorized User setup requests that are completed within the required timeframes during the Measurement Period | Service Level Achievement = (A/B) * 100% | A = Number of On-Time End User Device Setup Service Requests | B = Total number of End User Device Setup Service Requests for the Measurement Period | * Batch new user setups will be excluded from the On-Time Completion percentage calculation.
* Time before arrival of assets will be excluded from this measurement (i.e., ticket is submitted after arrival of all necessary assets.) | OPAS Service Requests | Business Hours | Yes, provided that if any single request is not resolved within *** (***) days, then this *** exception shall not apply | Yes | *** |
| | End User Device Services Support - Percentage of end user device service support Incidents that are successfully completed within the target timeframe | Key Measurement | ***% of Incidents completed within *** at staffed sites and within *** *** for non-staffed sites | Measures the time interval between an Incident record being registered in the service management tool for Desktop Services related Incidents to the time that operation is restored | Service Level Achievement = (A/B) * 100% | A = count of Desktop Services related Incidents resolved on time | B = count of Desktop Services related Incidents for the Measurement Period | Restoration Time does not include the following:
* Time that Incident Tickets are in "suspend mode" due to previously unknown third-party Software defects
* Time that Incident Tickets are in "suspend mode" for equipment-related failures at non-Dell facilities.
* Time incurred restoring Application data and/or functionality from tape media after Dell has returned Equipment to service.
* Third Party Hardware Exception
* Adjustments to the Service Levels approved by CoreLogic in its sole discretion pursuant to the last sentence of Section 4.4 of the MSA in order to permit the performance of new or additional work activities as contemplated by Section 4.4 of the MSA | OPAS Incident Tickets | Business Hours | Yes, provided that if any single Incident is not resolved within *** (***) days at staffed sites and more than *** (***) days for non-staffed sites, then this *** exception shall not apply | Yes | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 148 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | End User Device Termination - Percentage of employee end user device termination requests that are successfully completed within the target timeframe | Key Measurement | ***% of requests completed within *** days | Measures the degree of compliance of request for End User Device termination within the time period specified. The time period used is the elapsed time from activation of a task to closure of the Service Management Workflow System record. | Service Level Achievement = (A/B) * 100% | A = Number of On-Time End User Device Termination Service Requests | B = Total number of End User Device Termination Service Requests for the Measurement Period | * This excludes any recovery of employee physical assets (for assets not in CoreLogic offices) | OPAS Service Requests | Business Hours | Yes, if single Incident resulting in default is restored in less than *** days | Yes | *** |
| | Packaging (Develop and Push) - Percentage of packaging requests that are successfully completed within the target timeframe | Key Measurement | ***% of work requests are completed within *** days | Measures the time taken to package software from the receipt of a request for new software to the time that the software is available for the Authorized User to install via the software distribution system | Service Level Achievement = (A/B) * 100% | A = Number of packaging Service Requests completed within the required timeframe | B = Total number of packaging Service Requests for the Measurement Period | * Any time greater than *** business days for CoreLogic to perform applicable testing of the software package | OPAS Service Requests | Business Hours | Yes, provided that if any single request is not resolved within *** (***) days, then this *** exception shall not apply | No | *** |
| | End User Device Moves/Adds/Changes - Percentage of move requests that are successfully completed within the target timeframe | Key Measurement | ***% of requests completed within *** days at staffed sites and *** days at non-staffed sites | Measures the percentage of Moves/Adds/Changes (MACs) Service Requests completed within the required timeframes during the Measurement Period | Service Level Achievement = (A/B) * 100% | A = Number of MAC Service Requests completed within the required timeframes | B = Total number of MAC Service Requests received during the Measurement Period | * Batch (*** IMACDs in a day per CoreLogic Facility) Moves/Adds/Changes will be excluded from the on-Time Completion percentage calculation. | OPAS Service Requests | Business Hours | Yes, provided that if any single Incident is not resolved within *** (***) days at staffed sites and more than*** (***) days for non-staffed sites, then this *** exception shall not apply | Yes | *** |
|
| | |
| 2.4 | Enterprise Services, Exchange & Email | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 149 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Enterprise Services | | | | | | | | | | | | |
| | Patch management: Servers - Percentage of servers that are successfully patched within the target timeframe (from release of patch) | Key Measurement | ***% of normal patches applied in *** and critical patches applied in *** hours | Apply Patches to all instances of enterprise infrastructure applications including acquiring, testing, and installing multiple patches (Service Pack) Patch management tasks include: maintaining current knowledge of available patches, deciding what patches are appropriate, ensuring that patches are installed properly, testing systems after installation, and documenting all associated procedures, such as specific configurations required | Service Level Achievement = (A/B) * 100% | A = Total number of Enterprise Patches that are successfully installed in accordance with the Patch Management Policy | B = Total number of Enterprise Patches that are scheduled to be completed during the Measurement Period | * Post implementation of service pack, if Microsoft through their website releases a bug notification related to that specific Service Pack & that has caused unsuccessful implementation of patch.
* Time between Dell’s request for CoreLogic’s approval and when CoreLogic provides its approval | OPAS Change Records
Measurement Method will be manual and a combination of timestamp release by Microsoft and change management records. Clock starts at release of patch; clock stops when patch is successfully applied. | 24x7 | No | No | *** |
| | Percentage Availability of Right Fax Service | Key Measurement | ***% | Service availability for Right Fax (including SQL server database) server to send and receive faxes. | Service Level Achievement = (A/B) * 100% | A=Total number of hours of Right Fax Availability excluding Scheduled Downtime from maintenance | B=Total number of hours in a month | * Single point of failure of hardware, Software, or carrier services | OPAS Incident Tickets
Will be measured using an Incident RCA based measurement approach. | 24x7 | No | No | *** |
| | Exchange | | | | | | | | | | | | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 150 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Percentage Availability of Exchange E‑mail Service (including domain authentication and OWA) | Critical Service Level | ***% | Service Availability is defined as the ability of an Authorized User on an Exchange account to (a) access and retrieve information from an individual mailbox, and (b) send and receive messages via his or her mailbox using the Services (Outlook MAPI, OWA, IMAP or POP3). | Service Level Achievement = (A/B) * 100% | A=Total number of hours of Exchange availability excluding Scheduled Downtime from maintenance | B=Total number of hours in a month | * Individual mailbox or mobile device Availability, individual incoming and outgoing mail delivery time.
* Single point of failure (excluding RAID0 mail stores) of hardware, Software, or carrier services | OPAS Incident Tickets
Will be measured using an Incident RCA based measurement approach. | 24x7 | No | No | ***% |
| | Percentage Availability of Citrix Metaframe Service (Can encompass multiple farms) | Critical Service Level | ***% | Service Availability is defined by availability of core Citrix services like IMA service, Print spooler, XML service and published applications. | Service Level Achievement = (A/B) * 100% | A=Total number of hours of Citrix Availability excluding Scheduled Downtime from maintenance | B=Total number of hours in a month | * Individual Citrix clients, individual Citrix Desktop Availability
* For published applications, where the application is the root cause of the unavailability. | OPAS Incident Tickets
Will be measured using an Incident RCA based measurement approach. | 24x7 | No | No | ***% |
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Data Network | | | | | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 151 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Percentage Availability of Connectivity required for business operations - LAN (Data Center locations) | Critical Service Level | ***% | Availability within data center, common communication between computing and associated devices. Redundant equipment is required. The service is determined to be available if either side of the redundancy is up and operational. | Service Level Achievement = (A/B) * 100% | A=Total number of seconds of LAN Availability excluding Scheduled Downtime from maintenance | B=Total number of seconds in a month excluding Scheduled Downtime from maintenance | * Third Party Hardware Exception | OPAS Incident Tickets
Will be measured using an Incident RCA based measurement approach. | 24x7 | No | No | ***% |
| | Percentage Availability of Connectivity required for business operations - WAN (Data Center locations) | Critical Service Level | ***% | Availability for inter-data center connection, internet, intranet, extranet, devices and circuits. Reachability; measurement of the total number of hours of Availability through VLANS and firewalls to internet service provider circuits, intranet and extranet circuit service providers, communication between data centers. Redundant equipment is required. The service is determined to be available if either side of the redundancy is up and operational. | Service Level Achievement = (A/B) * 100% | A=Total number of seconds of WAN Availability excluding Scheduled Downtime from maintenance | B=Total number of seconds in a month excluding Scheduled Downtime from maintenance | *Third Party Hardware Exception | OPAS Incident Tickets
Will be measured using an Incident RCA based measurement approach. | 24x7 | No | No | ***% |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 152 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Percentage availability of LAN (Campus Sites) | Key Measurement | ***% | Availability within campus buildings, common communication between computing and associated devices. Assume redundant equipment exists at some level. The service is determined to be available if either side of the redundancy is up and operational. | Service Level Achievement = (A/B) * 100% | A=Total number of seconds of LAN Availability excluding Scheduled Downtime from maintenance | B=Total number of seconds in a month excluding Scheduled Downtime from maintenance | * Third Party Hardware Exception | OPAS Incident Tickets
Will be measured using an incident RCA based measurement approach | 24x7 | No | Yes | *** |
| | IT Security - Percent of Firewall requests, I.P. Address Add, Change or Open HTTP Port requests that are successfully completed within Target timeframe | Key Measurement | ***% of requests completed within***; ***% completed within *** | Measures the time taken between processing of approved request (s) | Service Level Achievement = (A/B) * 100% | A=Number of successfully completed requests | B= Total number of requests in the measurement period | * Any hold in approval processes or change request initiated by CoreLogic
* Supplier’s failure to meet this Service Level in respect of any hardware-related Incidents shall be excused to the extent that such failure is caused by any Supplier third party provider’s failure to perform, or delay in performing, any repair or replacement actions required to be performed by such third party provider in connection with the resolution of any such Incident; provided, that (i) Supplier uses commercially reasonable efforts to cause such third party providers to perform within the required time frame and (ii) to the extent documented in Supplier’s Root Cause Analysis.” | OPAS Service Requests | 24x7 | No | No | *** |
| | Voice Network | | | | | | | | | | | | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 153 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Percentage Availability of Voice Service (includes VOIP) | Critical Service Level | ***% | Voice Availability consists of time voice communication between users was available. Includes contact center and end user. Redundant equipment and circuits are required. | Service Level Achievement = (A/B) * 100% | A=Total number of seconds of VOIP Availability excluding Scheduled Downtime from maintenance | B=Total number of seconds in a month excluding Scheduled Downtime from maintenance | * Connection unavailability from provider of the network pipe;
*Third Party Hardware Exception
* Excludes Avaya, Nortel and other non‑enterprise VOIP systems | Cisco operations manager or equivalent
Will be measured using an Incident RCA based measurement approach. | 24x7 | No | No | ***% |
| | New contact center workflow service request. | Key Measurement | ***%***complete with in *** | Measures the time taken between processing of approved request(s) | Service Level Achievement = (A/B) * 100% | A=Number of successfully completed requests | B= Total number of requests in the Measurement Period | * Any hold in approval processes or change request initiated by CoreLogic Note: change requests should be after initial submission
* Excludes batch submissions and limited to <=4 or more call flow requests at one time. | OPAS Service Requests | 24x7 | Yes, provided that if any single request is not resolved within***days, then this *** exception shall not apply | Yes | *** |
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Overall Server Availability | | | | | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 154 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Server Availability - High | Critical Service Level | ***% | Measures the Availability of an individual cluster or System that are classified as High | Service Level Achievement = (A/B) * 100% | Sum total of individual cluster Actual Uptime or System Actual Uptime classified as High | Sum total Scheduled Uptime for individual cluster or system classified as High during the Measurement Period | * Lack of availability caused by CoreLogic or Third Party Contractor as documented in Supplier’s Root Cause Analysis
* Third Party Hardware Exception
* If any node of the cluster is not available and cluster it self is available then cluster is considered available.
* Any server classified as High which does not meet the minimal configuration requirements as defined in Resource Unit Definition Schedule A 4.2 at any time during the Measurement Period will be excluded
* Unavailability caused by a CoreLogic employee, as documented in the Root Cause Analysis | OPAS Incident Tickets | 24x7 | No | No | ***% |
| | Server Availability - Standard | Critical Service Level | ***% | Measures the Availability of an individual cluster or System that are classified as Standard | Service Level Achievement = (A/B) * 100% | Sum total of individual cluster Actual Uptime or System Actual Uptime classified as Standard | Sum total Scheduled Uptime for individual cluster or system classified as Standard during the Measurement Period | * Lack of availability caused by CoreLogic or Third Party Contractors as documented in Supplier’s Root Cause Analysis
* Third Party Hardware Exception | OPAS Incident Tickets | 24x7 | No | No | ***% |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 155 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Server Availability - Low | Key Measurement | ***% | Measures the Availability of servers that are classified as Low Availability with no single Low server having downtime > 10 hours. Any single server with downtime >10 hours will result in service level default for “Low” servers.
Note: Availability for servers under the control of application development staff will be excluded from the measurement and will be treated as a KPI with a target measurement of 95% | Service Level Achievement = (A/B) * 100% or with single Low server having downtime > 10 hours | Sum total Actual Uptime for all systems designated as Low Availability | Sum total Scheduled Uptime for all Systems designated as Low Availability during the Measurement Period | *if the RCA for “Low” category server is not available due to configuration changes by CoreLogic application development team that server will be excluded from the measurement.
*Third Party Hardware Exception | OPAS Incident Tickets | 24x7 | No | Yes, provided that not more than ***% of the servers have an aggregate availability less than***% | *** |
| | Physical Server | | | | | | | | | | | | *** |
| | Physical Server Provisioning - Percentage of physical server installation requests that are successfully completed within the target timeframe (includes server configuration, backup and other workload automation) | Key Measurement | ***% of requests completed within *** | Measures the percentage of Physical Service Provisioning Service Requests that are fulfilled by Supplier within the required timeframe. This Service Level applies to standard configuration x86 servers | Service Level Achievement = (A/B) * 100% | Total number of Physical Service Provisioning Service Requests completed within defined timeframe | Total number of Physical Service Provisioning Service Requests that are scheduled to be completed during the Measurement Period | * Greater than 10 in single request is batch and will be excluded from the on-Time Completion percentage calculation.
* Time before arrival of assets will be excluded from this measurement (i.e. ticket is submitted after arrival of all necessary assets.) | OPAS Service Requests | Business Hours | Yes, provided that if any single request is not resolved within *** (***) hours, then this *** exception shall not applys | Yes | *** |
| | Virtual Server | | | | | | | | | | | | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 156 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Add server(s) into Cloud Environment: Less than Ten (10) VM’s - Percentage of server provisioning requests that are successfully completed within the target timeframe | Key Measurement | ***% of requests completed within *** | Measures the percentage of Virtual Service Provisioning Requests (less than ten {10}) that are fulfilled by Supplier within the required timeframe | Service Level Achievement = (A/B) * 100% | Total number of Virtual Service Provisioning Service Requests that are less than ten {10} VMs during the Measurement Period for which the Completion Time is met | Total number of Virtual Service Provisioning Service Requests that are less than ten {10} VM’s that are scheduled to be completed during the Measurement Period | * Any requests for 10 or more VMs will be an exception | OPAS Service Requests | Business Hours | Yes, provided that if any single request is not resolved within *** (***) days, then this *** exception shall not apply | Yes | *** |
| | Patch management: Servers - Percentage of servers that are successfully patched within the target timeframe (from release of patch)
Note: This is for non-Enterprise Servers (employee systems) | Key Measurement | ***% of normal patches applied *** and critical patches applied in *** | Patch Management of Non-Enterprise Servers” means a patch scheduled to be deployed by Dell for Server Operating Systems in accordance with the Patch Management Policy. This will be a quarterly Service Level. | Service Level Achievement = (A/B) * 100% | Total number of Non-Enterprise Patches that are successfully installed in accordance with the Patch Management Policy for Server Equipment and Software | Total number of Non-Enterprise Patches that are scheduled to be completed during the Measurement Period | * Excludes time between Dell’s request for CoreLogic’s approval and when CoreLogic provides its approval. | OPAS Change Records and associated Server logs. | Business Hours | No | No | *** |
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Storage | | | | | | | | | | | | |
| | Percentage Availability of Storage | Crticial Service Level | 99.9% | Measures the average percentage of time that Storage Frames are Available for use during Scheduled Uptime in the applicable Measurement Period | Service Level Achievement = (A/B) * 100% | Sum total of Uptime for all storage Systems | Sum total of Scheduled Uptime for all storage systems during the Measurement Period | Availability excludes the following:
* Incidents caused by CoreLogic or Third Party Contractors as documented in Supplier’s Root Cause Analysis
* Third Party Hardware Expense | OPAS Incident Tickets | 24x7 | No | Yes | ***% |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 157 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Tier 1, 2, 3 Storage Provisioning <5% of allocated - Percentage of requests that are successfully completed within the target timeframe | Key Measurement | ***% of requests completed within *** day | Measures the percentage of Tier 1, 2, and 3 storage configuration service requests, less than 5% of all allocated storage, that are performed within the required timeframe during the Measurement Period | Service Level Achievement = (A/B) * 100% | Number of On-Time Tier 1, 2, and 3 Storage Provisioning Service Requests that are <5% of allocated | Number of On-Time Tier 1, 2, and 3 Storage Provisioning Service Requests that are <5% of allocated Requests | * Any Storage provisioning requests which exceed (in sum) more than 5% of allocated storage during the designated Measurement Period will be excluded.
* Locally attached storage
* Third Party Hardware Exception | OPAS Service Requests | Business Hours | Yes, provided that if any single request is not resolved within *** (***) days, then this *** exception shall not apply | Yes | *** |
| | Tier 1, 2, 3 Storage Provisioning >5% of allocated - Percentage of requests that are successfully completed within the target timeframe | Key Measurement | ***% of requests completed within ***s | Measures the percentage of Tier 1, 2, and 3 storage configuration service requests, greater than 5% of all allocated storage, that are performed within the required timeframe during the Measurement Period | Service Level Achievement = (A/B) * 100% | Number of On-Time Tier 1, 2, and 3 Storage Provisioning Service Requests that are >5% of allocated | Number of On-Time Tier 1, 2, and 3 Storage Provisioning Service Requests that are >5% of allocated Requests | * Locally attached storage. | OPAS Service Requests | Business Hours | No | Yes | *** |
| | Backup | | | | | | | | | | | | *** |
| | Add backup service - Percentage of requests to add servers to backup that are successfully completed within the target timeframe | Key Measurement | ***% of requests completed within *** days | Measures the percentage of new backup Service Requests that are performed within the required timeframe during the Measurement Period | Service Level Achievement = (A/B) * 100% | Number of backup Service Requests completed within the required timeframe | Total number of backup Service Requests for the Measurement Period | * Add backup service requests - If the number of Add backup service requests is greater than 10 per business day, this will be considered a batch submission and executed as a project. | OPAS Service Requests | Business Hours | Yes, provided that if any single request is not resolved within ***(***)***days, then this *** exception shall not applys | Yes | *** |
| | Emergency Restore Requests - Percentage of restoration requests for business critical restore of file(s), folder(s), sub directory which is currently offsite completed within the target timeframe | Key Measurement | ***% of requests initiated within*** day | Measures the percentage of emergency restore Service Requests that are (initiated via the physical restore) within the required timeframe during the Measurement Period | Service Level Achievement = (A/B) * 100% | Number of emergency physical restore Service Requests initiated within the required timeframe | Total number of emergency physical restore Service Requests for the Measurement Period | * Emergency restore requests - If the number of emergency restore requests is greater than 10 per business day, this will be considered a batch submission and executed as a project. | OPAS Service Requests | 24x7 | No | No | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 158 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Business critical, backup job failure - Percentage of backup job failures that are successfully addressed within the target timeframe | Key Measurement | ***% of failures are successfully completed within*** days | Measures the percentage of backup job failures that are successfully completed within the required timeframe during the Measurement Period | Service Level Achievement = (A/B) * 100% | Number of backup job failures Incident Tickets that are resolved within the required timeframe | Total number of backup job failures incident tickets for the Measurement Period | Restoration Time does not include the following:
* Time that Incident Tickets are in “suspend mode” due to previously unknown third party software defects.
* Time that Incident Tickets are in “suspend mode” for equipment related failures at non‑Dell facilities.
* Third Party Hardware Exception
* Adjustments to the Service Levels approved by CoreLogic in its sole discretion pursuant to the last sentence of Section 4.4 of the MSA in order to permit the performance of new or additional work activities as contemplated by Section 4.4 of the MSA | OPAS Incident Tickets | 24x7 | Yes, provided that if any single failure successfully completed is not resolved within *** (***) days, then this *** exception shall not apply | No | *** |
| | CoreLogic requested restore of up to 1.0% of the backup media per/ semiannual or per compliance policy - Percentage of restores successfully completed within the target timeframe | Key Measurement | ***% of restores are successfully completed without fault and within *** days. | Measures the percentage of random restores that are successfully completed during designated Change Window | Service Level Achievement = (A/B) * 100% | Number of random restores change tickets completed within the required timeframe | Total number of random restores change tickets executed | | OPAS Change Tickets | Reported semi-annually | Yes, provided that if any single restore is not resolved within *** (***) days, then this *** exception shall not apply | No | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 159 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | zO/S and Communications Components: Percentage of the agreed upon hours the System is on the wire and Available | Critical Service Level | ***% | Measures the Availability of the mainframe environment, including zO/S and associated Communication Components | Service Level Achievement = (A/B) * 100% | Total Uptime for all mainframe systems | Total Scheduled Uptime for all mainframe systems during the Measurement Period | Availability excludes the following:
* Non-production environments
*Third Party Hardware Exception | OPAS Incident Tickets | 24x7 | No | No | ***% |
| | CICS Production Availability | Critical Service Level | ***% | Measures the Availability of the CICS environment | Service Level Achievement = (A/B) * 100% | Total Uptime for all CICS systems | Total Scheduled Uptime for all CICS systems during the Measurement Period | Availability excludes the following:
* Non-production environments
* Third Party Hardware Exception | OPAS Incident Tickets | 24x7 | No | No | ***% |
| | Percentage availability of ADABAS | Key Measurement | ***% | Measures the Availability of the production ADABAS environment | Service Level Achievement = (A/B) * 100% | Total Uptime for production ADABAS system | Total Scheduled Uptime for production ADABAS systems during the Measurement Period | Availability excludes the following:
* Non-production environments
* Third Party Hardware Exception | OPAS Incident Tickets | 24x7 | No | Yes | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 160 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | EAPM – Percent of monitoring setup (server based) completed in the following timeframe: | Key Measurement | ***% of requests completed in the target timeframe:
*** or fewer servers – ***hrs.
*** to *** servers – *** hrs.
*** or more servers – *** hrs. | Measures the amount of time between receipt of a monitoring setup request and the completion of the monitoring setup activity | Service Level Achievement = (A/B) * 100% | A = total number of monitoring setup request tickets where the closure time is greater than the target | B = total number of monitoring setup requests in the Measurement Period | None | OPAS Service Requests | Business Hours | Yes, provided that if any single request is not resolved within *** (***) times, then this *** exception shall not apply | No | *** |
| | EAPM – Percent of Synthetic Transaction monitoring setup completed in the following timeframe: | Key Measurement | ***% of transactions (web page calls) completed in the target timeframe:
***or fewer transactions - *** business hours
*** to *** transactions - *** business hours
*** to *** transactions - ***business hours | Measures the amount of time between receipt of a monitoring setup request and the completion of the monitoring setup activity | Service Level Achievement = (A/B) * 100% | A = total number of monitoring setup request tickets where the closure time is greater than the target | B = total number of monitoring setup requests in the Measurement Period | None | OPAS Service Requests | Business Hours | Yes, provided that if any single request is not resolved within ***(***)***times, then this *** exception shall not apply | No | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 161 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | |
| 2.1 | Central Account Provisioning | |
|
| | | | | | | | | | | | | |
| | Service Level | Category | Service Level Metric | Definition | Formula | Formula Variable A | Formula Variable B | Exceptions | Measurement Method | Associated Hours of Operation | *** Eligible | Continuous Improvement Eligible | Weighting |
| | Percent of new user account setup requests completed within the target timeframe | Key Measurement | ***% of requests completed within *** days | Measures the time taken between processing of approved request to setup the account(s) | Service Level Achievement = (A/B) * 100% | A=Number of successfully completed requests | B= Total number of requests in the Measurement Period | Any hold in approval processes or Change Request initiated by CoreLogic | OPAS Service Requests | Business Hours | Yes, provided that if any single request is not resolved within *** (***) days, then this *** exception shall not apply | No | *** |
| | Percent of user terminations that are completed within the target timeframe | Critical Service Level | ***% within *** hours and 100% within ***hours | Measures the time taken between processing of approved request to terminate the account(s) | Service Level Achievement = (A/B) * 100% | A=Number of successfully completed requests | B= Total number of requests in the Measurement Period | Any hold in approval processes or Change Request initiated by CoreLogic
Any termination requests over 40 during a given day will not be measured | OPAS Service Requests | 24x7 | No | No | ***% |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 162 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-3.2
RESERVED
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 163 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-3.3
CRITICAL DELIVERABLES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 164 |
Schedule A-3.3
Critical Deliverables
| |
| 1.1 | Agreement. This Schedule A-3.3 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
As of the Supplement Effective Date, there are no Critical Deliverables applicable to this Supplement.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 165 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-4
PRICING AND FINANCIAL PROVISIONS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed without the prior written permission of the Parties. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 166 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-4
Pricing and Financial Provisions
| |
| 1.1 | Agreement. This Schedule A-4 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
The following documents are attached to and incorporated by reference in this Schedule:
Schedule A-4.1 Baseline Charges
Schedule A-4.2 Resource Unit Definitions
Schedule A-4.3 Baseline Volumes
Schedule A-4.4 ARC/RRC Rates
Schedule A-4.5 Transition Charges and Transformation Charges
Schedule A-4.6 Financial Responsibility Matrix
Schedule A-4.7 Rate Card
Schedule A-4.8 Termination Charges
Schedule A-4.9 Invoicing
Schedule A-4.10 Chargeable Projects
Schedule A-4.11 Project Pool
Schedule A-4.12 ***
| |
| 3. | DEFINITIONS. The following capitalized terms shall have the meanings set forth in this Section. Other capitalized terms used in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or Schedule A-1 to Supplement A. |
“Actual RU” has the meaning given in Section 5.2(d).
“Additional Resource Charge” or “ARC” means the additional per Resource Unit Charge, as calculated in accordance with Section 5.3(b), if the Actual RU for a Resource Unit is greater than the Resource Unit Baseline applicable to such Resource Unit.
“ARC Rate” means the rate provided in Schedule A-4.4 to be charged by Supplier to CoreLogic for any ARC for the applicable Resource Unit. The ARC Rate shall be equal to the RRC Rate.
“ARC/RRC Rate” means the rate that is the ARC Rate and RRC Rate.
“Band” has the meaning given in Section 5.3(c).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 167 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Baseline Charges” for any Resource Unit and Contract Year (or other time period as specified in this Supplement) means the fixed Charges to CoreLogic for CoreLogic’s utilization of the quantity of Resource Units included in the Resource Baseline for such Resource Unit and Contract Year (or other time period as specified in this Supplement) as set out in Schedule A-4.1.
“Chargeable Project” has the meaning given in Schedule A-4.10.
“Fixed Fee” means those Charges under this Supplement or a Work Order that are not subject to adjustment (e.g., by ARCs or RRCs) within the scope of the associated Service.
“Fixed Fee Breakdown” has the meaning given in Section 7.2(a).
“Fixed Fee Project” has the meaning given in Section 7.2(a).
“***” has the meaning given in Section 5.1(b).
“Productive Hours” has the meaning given in Section 7.3(a).
“Project” means a Chargeable Project or a New Service that the Parties agree to be performed as a project.
“Project Charges” has the meaning given in Section 7.1.
“Resource Unit” or “RU” means, with respect to Resource Unit-Based Services, a unit of consumption of resources that is to be measured under Supplement A to determine CoreLogic’s actual utilization compared to the applicable Resource Unit Baseline.
“Resource Unit-Based Charges” has the meaning given in Section 5.2(a).
“Resource Unit-Based Services” means Services that are charged on a Resource Unit basis.
“Resource Unit Baseline” for a Resource Unit means the quantity of such Resource Units that are included in the Baseline Charges set forth in Schedule A-4.3 for such Resource Unit.
“Reduced Resource Credit” or “RRC” means the reduced per Resource Unit credit, as calculated in accordance with Section 5.3(b), if the Actual RU for a Resource Unit is less than the Resource Unit Baseline applicable to such Resource Unit.
“RRC Rate” means the rate provided in Schedule A-4.4 to be charged by Supplier to CoreLogic for any RRC for the applicable Resource Unit. The RRC Rate shall be equal to the ARC Rate.
“Service Area” means the Services associated with a statement of work set forth in Schedule A-2 (e.g., Cross Functional, Service Management, Service Desk).
“Supplier Overhead Functions” has the meaning given in Section 13.
“T&M Project” has the meaning given in Section 7.2(b).
“Wind Down Costs” has the meaning given in Schedule A-4.8.3.
| |
| 4.1 | Generally. The Charges for the Services provided under this Supplement for each month shall consist of the following, as they may be adjusted pursuant to Sections 9 (Economic Change Adjustment) and 10 (Other Adjustments) and subject to any applicable credits: |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 168 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (a) | Fixed Fees for such month, in accordance with Section 5.1; |
| |
| (b) | Resource Unit-Based Charges for such month, in accordance with Section 5; |
| |
| (c) | Charges for New Services, in accordance with Section 6 (which may include Charges for New Services performed as Projects, in accordance with Section 7); |
| |
| (d) | Charges for Projects, in accordance with Section 7; |
| |
| (e) | Charges for Transition Services, in accordance with Section 8; |
| |
| (f) | Termination Charges, in accordance with Section 11; |
| |
| (g) | Charges for Transformation Services, in accordance with Section 14; and |
| |
| (h) | Charges for Disengagement Services, in accordance with Section 20.8(d) of the MSA. |
| |
| 4.2 | Full Compensation. Except as otherwise expressly specified in the Agreement, the Charges specified in Section 4.1 shall fully compensate Supplier for providing the Services, and CoreLogic shall not be required to pay Supplier any amounts for the Services in addition to such Charges. Supplier is responsible for the accuracy and completeness of the operational and financial assumptions it has made in developing its pricing, and if such assumptions, except those assumptions expressly stated in this Schedule A-4 or the applicable Work Order, are incorrect or incomplete, Supplier shall not be entitled to adjust its pricing or any other terms of this Supplement, or to assess additional fees for the Services. If an assumption is explicitly stated in this Schedule A-4 or the applicable Work Order, Supplier shall have the right to adjust its pricing or the other terms of this Supplement or assess additional fees for the Services only to the extent that the assumption states the consequence of the assumption being incorrect and, if applicable, the *** for making such adjustment. |
| |
| 4.3 | First and Last Month’s Charges. The Charges for the first and last months of the Supplement Term in which such Charges are owed Supplier under this Supplement shall be prorated on a per diem basis based on the number of days the applicable Services are provided by Supplier to CoreLogic in the relevant month. |
| |
| 4.4 | Charging Method For Each Service Area. As of the Supplement Effective Date, the Services for the Service Areas shall be charged as follows: |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 169 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | |
| Service Area | Schedule Reference | Charging Method |
| Cross Functional Services | Schedule A-2.1 | *** |
| Service Management Services | Schedule A-2.2 | *** |
| Service Desk Services | Schedule A-2.3 | *** |
| Server Services | Schedule A-2.4 | *** |
| Storage Backup Services | Schedule A-2.5 | *** |
| End User Device Support and Messaging Services | Schedule A-2.6 | *** |
| Data Center, Mainframe, Production Control, & Monitoring Services | Schedule A-2.7 | *** |
| Electronic Data Exchange Services | Schedule A-2.8 | *** |
| Network Services | Schedule A-2.9 | *** |
| Disaster Recovery Services | Schedule A-2.12 | *** |
| |
| (a) | If this Supplement specifies a Charge for a Service without specifying a Resource Unit, such Charge shall be a Fixed Fee. For Services specified to be performed as a Fixed Fee, unless otherwise specified in this Supplement, Charges for all resources, Systems, Materials, products and Deliverables *** by Supplier are included with the Fixed Fees. |
| |
| (b) | “***” shall mean recurring Fixed Fees that are not subject to adjustment based on the consumption of Resource Units. Schedule A-4.12 sets forth the *** for each calendar year of the Supplement Term. For avoidance of doubt, Fixed Fees for Transition Services are not ***. |
| |
| (c) | All *** shall be specifically set forth in the applicable Work Order or this Supplement. If the applicable Work Order or this Supplement specifies a ***, Supplier shall invoice the amount of such *** for the applicable month as provided in Section 12.1(a) of the MSA. If the applicable Work Order or this Supplement specifies an ***, unless otherwise expressly specified in such Work Order or this Supplement, Supplier shall invoice CoreLogic in each month when such *** applies an amount equal to such Ongoing Fixed Fee divided by twelve (12). |
| |
| 5.2 | Overview of Resource Unit-Based Charges. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 170 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (a) | Resource Unit-Based Charges. All Resource Unit-Based Services shall be charged in accordance with this Section 5 (such Charges, “Resource Unit-Based Charges”). Resource Unit-Based Charges consist of Baseline Charges, as adjusted by Additional Resource Charges and Reduced Resource Credits. For clarity, Resource Unit-Based Charges shall be calculated in accordance with Section 5.2(b) below (i.e., based upon the actual number of Resource Units consumed by CoreLogic). |
| |
| (b) | Calculation of Resource Unit-Based Charges. The total Resource Unit-Based Charges for each applicable Service Area shall be equal to the sum of all Baseline Charges and incremental Additional Resource Charges for such Service Area, less any Reduced Resource Credits for such Service Area, all as described in this Section 5. |
| |
| (c) | Resource Unit-Based Charges are Cost-Inclusive. For the avoidance of doubt, the Resource Unit-Based Charges include: |
| |
| (i) | All labor costs (e.g., overhead and management) of Supplier with respect to the Supplier Personnel performing the Resource Unit-Based Services. |
| |
| (ii) | All other costs and expenses for all resources, supplies, Systems, Materials, products and deliverables *** by Supplier in the provision of the Resource Unit-Based Services. |
| |
| (d) | Measurement and Reporting of Actual Resource Units. Subject to and without limiting Section 5.1(a), Supplier shall, on the *** (***) day of each calendar month of the Supplement Term, track the number of Resource Units consumed by Service Area during such month (“Actual RUs”) and Supplier shall provide such information to CoreLogic as part of the applicable monthly invoice. |
| |
| 5.3 | Resource Unit Baseline and Baseline Charges. Schedule A-4.3 sets forth the Resource Unit Baseline for each month of the Term. Schedule A-4.1 lists the Baseline Charge for each Service Area. |
| |
| (b) | Additional Resource Charges and Reduced Resource Credits |
| |
| (i) | To calculate Additional Resource Charges, Supplier shall compare the Actual RUs during each month of the Term with the Resource Unit Baseline for that Resource Unit as specified in Schedule A-4.3. If Actual RUs for a Resource Unit for a month exceeds the Resource Unit Baseline for such Resource Unit, the Additional Resource Charge shall be equal to A x (B - C), where: |
| |
| A | = the ARC/RRC Rate for such Resource Unit during such month, |
| |
| B | = the Actual RUs for such Resource Unit for such month, and |
| |
| C | = the Resource Unit Baseline for such Resource Unit for such month. |
For avoidance of doubt, if B < C, the ARC will be zero.
For example, if:
| |
| B. | The Resource Unit Baseline = 100; and |
| |
| C. | The ARC/RRC Rate = $5.00; |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 171 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
then
| |
| (ii) | To calculate Reduced Resource Credits, Supplier shall compare the Actual RUs during each month of the Term with the Resource Baseline for that Resource Unit as specified in Schedule A-4.3. If the Actual RUs for a Resource Unit for a month are less than the Resource Baseline for such Resource Unit, the Reduced Resource Credit shall be A x (C - B), where: |
| |
| A | = the ARC/RRC Rate for such Resource Unit during such month, |
| |
| B | = the Actual RUs for such Resource Unit for such month, and |
| |
| C | = the Resource Unit Baseline for such Resource Unit for such month. |
For avoidance of doubt, if B > C, the RRC will be zero.
For example, if:
| |
| B. | The Resource Unit Baseline is 100; and |
| |
| C. | The ARC/RRC Rate is $5.00; |
then
| |
| (c) | The “***” Resource Unit identified in Schedule A-4.3 has a “Band” or number of Resource Units associated with such Resource Unit and the applicable ARC/RRC Rates. The Band for such Resource Unit shall be calculated as follows: (i) the upper end of the Band shall be calculated as the largest whole number included within the Band percentage and (ii) the lower end of the Band shall be calculated as the smallest whole number included within the Band percentage. If the number of Resource Units in any Resource Category is outside the Band for any *** (***) *** months, then: |
| |
| (1) | Supplier shall prepare and present to CoreLogic a written proposal at least *** (***) *** prior to the proposed effective date of the *** described in such proposal, which proposal will set forth *** to the applicable ***, ***, ***, *** and *** based upon the *** of the *** upon ***, including the effect of any ***, and any ***, ***, *** and *** that have been lost or can be achieved; |
| |
| (2) | CoreLogic will have at least *** (***) days to review and respond to such ***; |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 172 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (3) | the Parties shall attempt to agree upon *** to the applicable ***, ***, ***, *** and *** described in Supplier’s ***; |
| |
| (4) | if the Parties are unable to agree upon the *** within *** (***) *** after CoreLogic responds to Supplier’s ***, the matter shall be addressed through the *** set forth in ***; and |
| |
| (5) | until the matter is so resolved, the ***, ***, ***, ***, and *** (as the case may be) that shall apply to the Resource Unit outside of the Band shall ***. |
If, and to the extent that, CoreLogic requires Supplier to perform any New Services in accordance with the Agreement, the Charges for such New Services shall be priced in accordance with the applicable Change Order, Work Order, or this Supplement in accordance with Section 4.3 of the MSA. CoreLogic may *** Supplier to perform activities that constitute New Services on a Project basis in accordance with Section *** of the MSA and Section 7 below.
| |
| 7. | NEW SERVICES PERFORMED AS PROJECTS. |
| |
| 7.1 | Overview. Work activities can only be performed and charged by Supplier as a Project (a) as specified in Schedule A-4.10 with respect to Chargeable Projects or (b) to the extent such activities are New Services, and only if such New Services are to be performed as a Project in accordance with this Section 7. If CoreLogic *** Supplier to perform such New Services on a Project basis, Supplier shall perform such New Services in accordance with this Section 7, and such New Services will be charged as “Project Charges”. |
| |
| 7.2 | Remuneration Models for Projects. |
CoreLogic may engage Supplier to perform Projects or New Services as Projects in accordance with an applicable Work Order that will be established by the Parties for such Project. The specific pricing mechanism applicable to such Work Order (e.g., one of the mechanisms described below in this Section or another mechanism mutually agreed by the Parties) will be agreed by the Parties and specified therein. Examples of pricing mechanisms that may be used for such Projects are as follows:
| |
| (a) | Fixed Fee Projects. To the extent that a Project is identified as a “Fixed Fee Project”, Supplier shall perform the New Services specified in the applicable Work Order for the Fixed Fees that are specified in such Work Order. Fixed Fees are not adjusted based on the actual time expended by Supplier Personnel in the performance of the New Services. Unless otherwise specified in a Work Order, the Fixed Fee shall be invoiced based upon CoreLogic’s Acceptance of Deliverables. Each Work Order should specify the portion of the Fixed Fees to be invoiced by Supplier upon CoreLogic’s Acceptance of a Deliverable. If the applicable Work Order does not specify the portion of the Fixed Fees associated with each Deliverable, then Supplier shall invoice the portion of the Fixed Fees allocated to a specific month in the month after the month *** all *** Deliverables. With respect to each Fixed Fee Project, Supplier shall provide a *** breakdown of the estimated effort required to complete each Deliverable for such Project, by resource category, skill type, skill level and location (the “Fixed Fee Breakdown”). The Fixed Fee Breakdown must demonstrate that the Fixed Fee is based on the applicable hourly rates in Schedule A-4.7, with an additional risk contingency applied as Supplier reasonably deems appropriate, and any pricing for specific Supplier assets. |
| |
| (b) | Time and Materials (T&M) Projects. To the extent a Project is identified as a “T&M Project”, payment shall be based, subject to Section 7.3, on the number of Productive Hours spent by Supplier Personnel in performing the Services and providing CoreLogic the applicable Deliverables as defined in the applicable Work Order. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 173 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 7.3 | T&M Project Calculation Rules. |
| |
| (a) | “Productive Hours” means the number of hours actually worked by Supplier Personnel to provide the Services. Productive Hours do not include: |
| |
| (i) | Vacation time, holiday time, medical leave, jury duty, military leave, non-productive commuter travel time, or other analogous time, |
| |
| (ii) | Time not authorized under an applicable Work Order or otherwise in writing (including, for clarity, by email) by CoreLogic, or |
| |
| (iii) | Time devoted to any Supplier Overhead Functions (as defined below). |
| |
| (b) | Supplier will invoice CoreLogic in each month for, and CoreLogic will pay in accordance with Sections 12.1 and 12.2 of the MSA, with respect to each individual Supplier Personnel, the product of: |
| |
| (i) | the hourly rate applicable to him or her in his or her role in such month as set forth in the hourly rate card set forth in Schedule A-4.7 |
multiplied by
| |
| (ii) | subject to the limitations in Section 7.3(c), the number of Productive Hours that he or she devoted to providing Services during such month. |
| |
| (c) | Invoicing is subject to the following limitation: |
| |
| (i) | If the Parties have expressly agreed on a maximum number of Productive Hours in a Work Order (i.e., a fee cap and not an estimate), Supplier will not charge for Productive Hours beyond such maximum. |
| |
| 7.4 | Productive Hours Reports. Supplier shall provide a monthly report showing all Productive Hours worked by Supplier Personnel for all work performed for T&M Projects and capped T&M Projects. |
| |
| (a) | Unless otherwise provided in a Work Order, CoreLogic may terminate a Work Order for Project Services for convenience by providing Supplier at least *** (***) business days’ notice prior to the effective date of such termination. |
| |
| (b) | In such case, CoreLogic shall pay (i) with respect to all such Work Orders except Fixed Fee Project Work Orders, for all Services rendered by Supplier under such Work Order through the effective date of such termination in accordance with the pricing mechanism specified in such Work Order, (ii) with respect to Fixed Fee Project Work Orders, (A) the Fixed Fees attributable to completed Project deliverables that have been Accepted prior to the effective date of termination; and (B) a pro rata portion of the Fixed Fees associated with any Project deliverables in progress or not yet Accepted as of the effective date of termination (based upon the actual percentage of the work performed and to the extent Supplier has not, without CoreLogic approval, begun work on a Project deliverable in advance of the Project schedule). The maximum number of hours included in the calculation of such early termination payment shall not exceed the planned Supplier hours (in accordance with the then-current Project plan) through the effective date of such termination by more than *** percent (***%). |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 174 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (c) | If a Work Order for Project Services performed under a T&M Project is terminated by CoreLogic for convenience, the applicable hourly rates for the Supplier Personnel performing the terminated Project Services shall be deemed to be the rates that would have applied had the initial commitment been for a period of time ending on the date of actual termination. With respect to Fixed Fee Project Work Orders terminated by CoreLogic for convenience, the Fixed Fee shall be *** in the same way based upon the *** and the rates that would have applied had the initial commitment been for a period of time ending on the date of actual termination. |
| |
| (d) | If CoreLogic terminates a Work Order for Project Services for convenience, CoreLogic shall reimburse Supplier for any travel and living expenses identified as “non cancelable” travel and living expenses in such Work Order that would otherwise be due under Section 7.6. If the Work Order specified that Supplier was to procure third party Equipment or Third Party Software in order to provide the Project Services, *** shall *** *** for the *** of the Equipment or Software but only to the extent such *** would qualify as *** under Schedule ***. Upon *** of such ***, Supplier shall cause the title and ownership of such third party Equipment or Third Party Software to pass to CoreLogic. |
| |
| 7.6 | Project Services Out-of-Pocket Expenses. Unless otherwise agreed in the applicable Work Order, CoreLogic shall reimburse Supplier for actual and necessary travel and living expenses reasonably incurred by Supplier Personnel in providing Project Services, subject to and in accordance with the terms set forth below: |
| |
| (a) | The travel and living expenses to be reimbursed by CoreLogic shall not exceed the cap agreed upon and specified in the applicable Work Order. The actual amount of reimbursable expenses shall not thereafter exceed such agreed cap by greater than *** of the budgeted Charges under such Work Order, unless agreed otherwise. |
| |
| (b) | Supplier will comply with CoreLogic’s travel policies. If compliance with Supplier’s travel policies will result in lower reimbursable expenses for CoreLogic, Supplier shall report such policies to CoreLogic and, upon CoreLogic’s approval, comply with such policies. |
| |
| (c) | CoreLogic shall not be obligated to pay or reimburse Supplier or Supplier Personnel for non-productive commuter travel time. |
| |
| (d) | CoreLogic shall not be obligated to reimburse Supplier for travel and living expenses incurred by Supplier Personnel in performing Project Services at any CoreLogic Facility located within the same number of miles for a round trip between that individual’s place of residence and his or her local office. |
| |
| (e) | CoreLogic shall not be obligated to pay moving expenses or other relocation expenses incurred by Supplier Personnel who are working on a Project (e.g., if Supplier elects to transfer an existing Supplier employee from one city to another instead of using a local employee or hiring a new employee locally, or if Supplier hires a new employee from elsewhere in the country who thus must move to start work). |
| |
| (f) | Entertainment by or on behalf of Supplier Personnel shall be at no cost to CoreLogic or the Eligible Recipients. |
| |
| (g) | Supplier shall provide a summary report of expenses broken down by major categories (e.g., airfare, hotels and meals). CoreLogic or Eligible Recipient-specific requirements for this report may vary by Work Order. Without limitation of Section 9.10(a) of the MSA, Supplier shall maintain documentation for all invoiced travel and living expenses and, at CoreLogic’s request, shall provide CoreLogic with copies of such documentation. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 175 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
CoreLogic shall pay fixed Charges for Transition Services (“Transition Charges”) as set forth in Schedule A-4.5.
| |
| 9. | ECONOMIC CHANGE ADJUSTMENT. |
| |
| (a) | “Actual Economic Change Percentage” means the percentage calculated by comparing the then-current December Economic Change Index as of the date of applicable Annual ECA Event with the Economic Change Index published in *** the previous year. For example, for an Annual ECA Event on January 1, ***, the Actual Economic Change Percentage would be calculated by comparing the *** index with the *** index. |
| |
| (b) | “Annual ECA Event” has the meaning given in Section 9.2(a). |
| |
| (c) | “ECA Element” means an element of the Charges described in this Schedule A-4 that is subject to Economic Change Adjustments. The only ECA Elements for Supplement A are identified in Section 9.3. |
| |
| (d) | “ECA Percentage” means, for each ECA Element, the applicable Actual Economic Change Percentage; provided, that if the Actual Economic Change Percentage is *** than *** percent (***%), the ECA Percentage shall equal *** percent (***%) plus *** of the percentage by which the *** exceeds *** percent (***%). For example, if *** is *** percent (***%), the ECA Percentage would be *** percent (***%). |
| |
| (e) | “Economic Change Adjustment” or “ECA” means a change to the amount or rate of an ECA Element in accordance with this Section 9. |
| |
| (f) | “Economic Change Index” means percent change in *** for *** city average, *** (***) by the *** (available at ***). |
| |
| (g) | “Sensitivity-Adjusted Economic Change Percentage” has the meaning given in Section 9.2(b). |
| |
| (h) | “Sensitivity Factor” means, for each ECA Element, the percentage identified in Section 9.3 for such ECA Element, which represents the portion of the ECA Element costs that are sensitive to economic change. The Sensitivity Factors shall not be adjusted except as agreed by the Parties. |
| |
| 9.2 | Application of ECA to ECA Elements. |
| |
| (a) | Annual Application. On January 1, ***, and annually thereafter (each, an “Annual ECA Event”), the Parties will apply an Economic Change Adjustment to each of the ECA Elements in accordance with this Section 9.2. The Parties will calculate such Economic Change Adjustment in accordance with this Section 9.2 after the *** publishes the then-current *** Economic Change Index (which may occur on or after the date of the applicable Annual ECA Event); provided, however, that such Economic Change Adjustments shall be retroactively effective as of January 1 of the calendar year of such Annual ECA Event (e.g., January 1, ***, January 1, ***). |
| |
| (b) | Calculation of ECA. For each ECA Element, the Economic Change Adjustment shall be calculated by multiplying the ECA Percentage (using the applicable ECA Percentage for such ECA Element, as identified in Section 9.3) with the applicable Sensitivity Factor for such ECA Element to create the “Sensitivity-Adjusted Economic Change Percentage”. For example, if there is an ECA Percentage of 3% with a Sensitivity Factor of 50%, the Sensitivity-Adjusted |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 176 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Economic Change Percentage would be ((0.03 * 0.5) * 100), or 1.5%. The new value of the ECA Element shall be equal to (A * (1 + B)), where A is the value of the ECA Element prior to the Annual ECA Event and B is the Sensitivity-Adjusted Economic Change Percentage. For example, if a monthly Baseline Charge is $100 prior to the Annual ECA Event and the Sensitivity-Adjusted Economic Change Percentage is 1.5%, the updated value of such monthly Baseline Charge shall be (100 * (1 + 0.03)), or $101.5.
| |
| 9.3 | ECA Elements and Sensitivity Factors. |
|
| |
| ECA Element | Sensitivity Factor |
| *** | ***% |
| *** | ***% |
*** as set forth in Schedule *** | ***% |
The pricing in this Schedule A-4 may be subject to additional adjustments pursuant to Section 11.4 (Extraordinary Events) and Section 11.6 (CoreLogic Benchmarking Reviews) of the MSA.
The Termination Charges associated with this Supplement A are set forth in (a) Schedule A-4.8 and (b) Section 7.5 above with respect to the payment of amounts identified therein in connection of a termination of a Work Order for Project Services, and the Parties agree that there are no additional Termination Charges that are applicable to this Supplement A.
All invoices shall be in accordance with Section 12.1 of the MSA and in the applicable format set forth in Schedule A-4.9.
| |
| 13. | SUPPLIER OVERHEAD FUNCTIONS. |
Supplier shall *** Supplier Overhead Functions *** of the Services. Subject to Section 13(b) below, Supplier Overhead Functions shall not constitute *** or ***, unless otherwise expressly agreed by the Parties. “Supplier Overhead Functions” mean functions performed by Supplier to support its business or delivery of Services, including the following:
| |
| (a) | Management other than by project managers, project staff, team leaders/supervisors and their immediate managers; |
| |
| (b) | Performing any *** functions, except to the extent that CoreLogic has specifically engaged Supplier to perform *** functions in a Project or as New Services); |
| |
| (c) | Performing monitoring, measurement and reporting activities required by the Agreement to measure Supplier’s performance and resource usage, including Service Level administration, monitoring, and metrics/measurement tools implementation related to the delivery of the Services, |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 177 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
except to the extent CoreLogic has specifically engaged Supplier to perform such activities in a Project or as New Services (and as specifically set forth in the pricing for such Project or New Services);
| |
| (d) | Performing resource management activities internal to Supplier such as Supplier-dictated recruiting and Supplier internal human resources functions; |
| |
| (e) | Performing Supplier’s internal account management functions, such as performing as a member of Supplier’s pricing, financial or accounting teams; |
| |
| (f) | Performing Supplier’s internal administrative functions, such as billing functions, administrative and secretarial assistance, promotion, publicity and internal management; |
| |
| (g) | Performing quality assurance activities to monitor Supplier’s performance; |
| |
| (i) | All Supplier ***-related activities (technology, business, financial/budget, data center capacity support, etc.); |
| |
| (j) | Performing activities required to train Supplier Personnel, including skills training, orientation on all applicable CoreLogic safety, security and environmental rules, policies and procedures, and orientation to the CoreLogic environment, but not including training required by CoreLogic that is specific to CoreLogic’s business and not general to the Services provided by Supplier; |
| |
| (k) | The development, implementation and execution of *** programs for Supplier Personnel and the *** of standard project management processes and methodologies; |
| |
| (l) | Implementing activities and tools to promote *** of *** except to the extent CoreLogic has specifically engaged Supplier to perform such activities in a Project or as New Services (and as specifically set forth in the pricing for such Project or New Services); |
| |
| (m) | Performing work to develop *** as a result of any Service Level Default and work associated with rework that is due to the fault of Supplier or for which Supplier is otherwise responsible for the cost of performing under the MSA; |
| |
| (n) | Using *** or other *** groups within Supplier’s organization, so long as such use is in connection with the performance of the Services, where such use has been approved by the Supplier or where such use is required to enable Supplier to provide the Services; |
| |
| (o) | Activities and tools implemented by Supplier either at its discretion or as required to meet its obligations under the MSA; |
| |
| (p) | Managing *** relationships and resources as required under the MSA; |
| |
| (q) | Preparing all *** and proposals for Projects and/or New Services; and |
| |
| (r) | Performing all activities associated with transitioning Supplier Personnel to the CoreLogic account, including with respect to new or replacement personnel, and associated knowledge transfer and training as necessary or appropriate for the provision of the Services. |
| |
| 14. | TRANSFORMATION SERVICES. |
CoreLogic shall pay Charges for Transformation (“Transformation Charges”) as set forth in Schedule A-4.5.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 178 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 179 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | |
| Schedule A-4.1 Baseline Charges | | | | | | | | | | |
| | | | | | | | | | | |
| Baseline Charges | 2012 | 2013 | 2014 ** | 2015 | 2016 | 2017 | 2018 | 2019 | 2020 * | Total |
| *** | | | | | | | | | | *** |
| Account and Service Management | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| DR | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Chargeable Project Management | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Telecom Expense Management | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| *** | | | | | | | | | | *** |
| Network | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End User Device Support and Messaging | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Employee Service Desk | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Midrange and Server | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Storage | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cross Functional and Media Center | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| | | | | | | | | | | *** |
| Totals | - | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| | * | 2020 fees represent charges for January of 2020 only | | | | | |
| | ** | 2014 Mainframe fees cover charges for the first six months of the year. | | | | |
| | | | | | | | | | | |
| On the January 2013 invoice, *** will provide a*** to *** in the amount of $*** | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 180 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-4.2
RESOURCE UNIT DEFINITIONS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
***
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 181 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-4.2
Resource Unit Definitions
| |
| 1.1.1 | Agreement. This Schedule A-4.2 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
The following terms have the meanings specified below:
“Configuration Management Database” or “CMDB” is a database that identifies and tracks relevant information and relationships about Configuration Items (CI) and any changes made to CI in a comprehensive and systematic fashion.
“FTE” or “Full Time Equivalent” means the full-time equivalent of a Supplier Personnel performing Services for a minimum of *** Hours per Contract Year effort (whether by one person or more than one person). Each dedicated FTE shall be deemed to be a fraction of an FTE equal to the number of *** Hours worked by such dedicated FTE in a Contract Year divided by ***.
“Service Request” means any request from the authorized user to add, remove or change to a service. One request may contain one or more related tasks.
| |
| 1.1.4 | General. This Schedule describes the terms and definitions of billable Resource Units applicable to Supplement A. There are no other billable Resource Units applicable to Supplement A. |
This Section details the Resource Units associated with Schedule A-2.9 (Network Services)
| |
| 1.2.1 | Network Switch/Router |
“Network Switch/Router” means a network switch/router device for which Supplier performs Network Services that is installed and located outside of a Supplier Data Center. For clarity, Supplier owned routers and switches located within a Supplier Facility are supported in accordance with Schedule A-2, but are excluded from the measurement of this Resource Unit unless the router or switch is specifically requested by CoreLogic and is not otherwise required to provide Services in accordance with this Agreement and Service Levels.
Resource Unit Definition: Each Network Switch/Router as measured using data from the CMDB (excluding Network Switch/Routers that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.2.2 | Physical Firewall - Clustered |
“Physical Firewall - Clustered” means a physical firewall device that is configured in an active/passive or active/active pair with failover mode, for which
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 182 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Supplier performs Network Services that is installed and located outside of a Supplier Data Center. For clarity, Supplier provided Firewalls located within a Supplier Facility are supported in accordance with Schedule A-2, but are excluded from the measurement of this Resource Unit unless the additional Physical Firewall - Clustered is specifically requested by CoreLogic and is not otherwise required to provide Services in accordance with this Agreement and Service Levels.
Resource Unit Definition: Each Physical Firewall - Clustered as measured using data from the CMDB (excluding Firewalls that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.2.3 | Physical Firewall - Standalone |
“Physical Firewall - Standalone” means a single standalone physical firewall device for which Supplier performs Network Services that is installed and located outside of a Supplier Data Center. For clarity, Supplier provided Firewalls located within a Supplier Facility are supported in accordance with Schedule A-2, but are excluded from the measurement of this Resource Unit unless the additional Physical Firewall - Standalone is specifically requested by CoreLogic and is not otherwise required to provide Services in accordance with this Agreement and Service Levels.
Resource Unit Definition: Each Physical Firewall - Standalone as measured using data from the CMDB (excluding Firewalls that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.2.4 | Virtual Firewall - Clustered |
“Virtual Firewall - Clustered” means a virtual firewall device that is configured in an active/passive or active/activepair with failover mode, for which Supplier performs Network Services that is installed and located outside of a Supplier Data Center. For clarity, Supplier provided Firewalls located within a Supplier Facility are supported in accordance with Schedule A-2, but are excluded from the measurement of this Resource Unit unless the additional Virtual Firewall - Clustered is specifically requested by CoreLogic and is not otherwise required to provide Services in accordance with this Agreement and Service Levels.
Resource Unit Definition: Each Virtual Firewall - Clustered as measured using data from the CMDB (excluding Firewalls that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.2.5 | Virtual Firewall - Standalone |
“Virtual Firewall - Standalone” means a single standalone physical firewall device for which Supplier performs Network Services that is installed and located outside of a Supplier Data Center. For clarity, Supplier provided Firewalls located within a Supplier Facility are supported in accordance with Schedule A-2, but are excluded from the measurement of this Resource Unit unless the additional Virtual Firewall - Standalone is specifically requested by CoreLogic and is not otherwise required to provide Services in accordance with this Agreement and Service Levels.
Resource Unit Definition: Each Virtual Firewall - Standalone as measured using data from the CMDB (excluding Firewalls that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 183 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Security Appliance” means a purpose built Security Appliance including adaptive security appliances, web security appliances, key management appliances, encryption appliances, IPS devices, IDS devices, Security Information and Event Management appliances, and content filters that are in production and located outside of a Supplier Data Center. For clarity, Supplier provided Security Appliances located within a Supplier Facility are supported in accordance with Schedule A-2, but are excluded from the measurement of this Resource Unit unless the additional Security Appliance is specifically requested by CoreLogic and is not otherwise required to provide Services in accordance with this Agreement and Service Levels
Resource Unit Definition: Each Security Appliance as measured using data from the CMDB (excluding Security Appliances that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
“VOIP Phone” means a VOIP phone device at supported Facilities for which Supplier performs VOIP Services.
Resource Unit Definition: Each VOIP Phone as measured using data from the call management system on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.2.8 | Miscellaneous Network Devices |
“Miscellaneous Network Device” means a purpose-built network device for which Supplier performs Network Services which is not included in the other network device charges in this Schedule A-4.2. Miscellaneous Network Devices include *** and ***. For clarity, Supplier provided Miscellaneous Network Devices located within a Supplier Facility are supported in accordance with Schedule A-2, but are excluded from the measurement of this Resource Unit unless the additional Miscellaneous Network Device is specifically requested by CoreLogic and is not otherwise required to provide Services in accordance with this Agreement and Service Levels.
Resource Unit Definition: Each Miscellaneous Network Device as measured using data from the CMDB (excluding Miscellaneous Network Devices that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.2.9 | Load Balancer - Clustered |
“Load Balancer - Clustered” means two purpose-built devices configured in an active/passive or active/active pair with failover mode used to manage and distribute workload across multiple computing resources. For clarity, Supplier provided Load Balancers located within a Supplier Facility are supported in accordance with Schedule A-2, but are excluded from the measurement of this Resource Unit unless the additional Load Balancer - Clustered is specifically requested by CoreLogic and is not otherwise required to provide Services in accordance with this Agreement and Service Levels.
Resource Unit Definition: Each Load Balancer – Clustered as measured using data from the CMDB (excluding Load Balancers that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 184 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 1.2.10 | Load Balancer - Standalone |
“Load Balancer - Standalone” means a purpose-built device used to manage and distribute workload across multiple computing resources. For clarity, Supplier provided Load Balancers located within a Supplier Facility are supported in accordance with Schedule A-2, but are excluded from the measurement of this Resource Unit unless the additional Load Balancer - Standalone is specifically requested by CoreLogic, and is not otherwise required to provide Services in accordance with this Agreement and Service Levels.
Resource Unit Definition: Each Load Balancer - Standalone as measured using data from the CMDB (excluding Load Balancers that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.2.11 | Wireless Access Points |
“Wireless Access Point” means a Network wireless access point device located at CoreLogic Facilities for which Supplier performs Network wireless Services.
Resource Unit Definition: Each Wireless Access Point as measured using data from CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
“Network IMAD” means installs, moves, adds or removals (deletes) of Network devices as requested by CoreLogic excluding IMADs resulting from activities performed under Schedule A-13.
Resource Unit Definition: Each Network IMAD as measured using data from the Supplier’s service management system during the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.3 | End User Desktop Support. |
This Section details the Resource Units associated with Schedule A-2.6 (End User Desktop Support and Messaging Services).
| |
| 1.3.1 | EUC (Desktop/Laptop) |
“EUC Device” means an end user computing device that is a desktop or laptop personal computing device running a single Microsoft or Apple Operating System.
EUC Device Resource Unit represents the Charges for the Services (e.g., EUC Services and Network Services) for all EUC Devices (other than Mobile Devices and Thin Clients).
Resource Unit Definition: Each EUC Device as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
“Network Printer” means: (A) a printing device that: (i) is connected to the CoreLogic Network via Ethernet, (ii) is located at a CoreLogic Facility, and (iii) to which Authorized Users are able to print using a EUC Device; and (B) is in-service.
Resource Unit Definition: Each Network Printer as measured using data from CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 185 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Email Mailbox” means an authorized account on the CoreLogic email system for which Supplier is required to provide content-filtering, including user mailboxes, group mailboxes, or system mailboxes. *** Email Accounts shall not include any accounts on the CoreLogic email system allocated to Supplier.
Resource Unit Definition: Each Email Mailbox as measured using data from Exchange Messaging System (excluding Email Mailboxes that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
A “Mobile Device” means a personal hand-held device used by an Authorized User that provides the functions of a cellular phone and/or also allows the receipt and creation of email messages. Mobile Devices exclude bar code readers, digital scanners and RFI devices. The Resource Unit includes support of the Enterprise Server for Active Sync.
Resource Unit Definition: Each Mobile Device as measured using data from the Supplier’s mobile device management system (excluding Mobile Device that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.3.5 | Desktop Application Packages |
“Desktop Application Package” means any custom compilation of a commercial-off-the-self ("COTS") or custom in-house application, packaged for automated delivery and requested by CoreLogic, by image type as applicable (e.g., *** variations, etc.). Desktop Application Packages include de-install packages required for proper installation to an end user device. The pricing for the Desktop Applications Package Resource Unit categories is on a services-only basis.
Resource Unit Definition: Each Desktop Application Package as measured using data from the Supplier’s service management system during the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.3.6 | Desktop Image Management |
“Desktop Image Management” means a pre-configured, deployable image validated on one (1) or more currently supported desktop hardware platforms in the CoreLogic environment. The pricing for the Desktop Image Management Resource Unit categories is on a services-only basis.
Resource Unit Definition: Each Desktop Image Management as measured using data from the Supplier Desktop Management System on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.3.7 | End User IMACDs - Campus |
“End User IMACD - Campus” means physical installs, moves, adds, changes or deletions for End User Devices as requested by CoreLogic at sites designated as Campus facilities.
Resource Unit Definition: Each End User IMACD – Campus as measured using data from the Supplier’s service management system during the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.3.8 | End User IMACDs - Remote |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 186 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“End User IMACD - Remote” means physical installs, moves, adds, changes or deletions for End User Devices as requested by CoreLogic at sites not designated as Campus facilities.
Resource Unit Definition: Each End User IMACD – Remote as measured using data from the Supplier’s service management system during the applicable calendar month shall be equal to one (1) Resource Unit.
This Section details the Resource Units associated with Schedule A-2.3 (Service Desk Services).
| |
| 1.4.1 | Service Desk Tickets |
“Service Desk Ticket” means a ticket created by a Service Desk agent that is initiated by the Authorized User by telephone or Self Service. One (1) such Ticket equals one (1) Resource Unit. Tickets that are routed by the Supplier’s service management system to Resolver Groups other than the Service Desk are excluded from this Resource Unit.
Resource Unit Definition: Each Service Desk Ticket as measured using data from the Supplier’s service management system during the applicable calendar month shall be equal to one (1) Resource Unit.
This Section details the Resource Units associated with Schedule A-2.7 (, Mainframe, Services).
“Mainframe Services Unit” means a Mainframe Service that provides installed mainframe processing capabilities of *** Millions of Instructions Per Second (MIPS) and useable Direct Access Storage Drive (DASD) storage of *** terabytes.
Resource Unit Definition: Each Mainframe Services Unit as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
“ Mainframe Tape” means a physical tape mount associated with the mainframe.
Resource Unit Definition: Each Mainframe Tape as measured using data from the mainframe system management facility records (SMF) during the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.6 | Server (Services Only). This Section details the Resource Units associated with Schedule A-2.4 (Server Services). Any Operating System instances that are used to deliver Services already charged by different Resource Units (e.g., *** Email Mailboxes, monitoring, DLP, etc.) as identified in CMDB will be excluded from the device count. |
| |
| 1.6.1 | Linux High OS Instance |
“Linux High OS Instance” means an Operating System instance that operates on a Linux Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to (i) receive the “Linux High OS Instance” Services described in Schedule A-2.4 (Server Services); and (ii) have the applicable minimum computing requirements described in Appendix A below.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 187 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Resource Unit Definition: Each Linux High OS Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.6.2 | Linux Standard OS Instance |
“Linux Standard OS Instance” means an Operating System instance that operates on a Linux Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to (i) receive the “Linux Standard OS Instance” described in Schedule A-2.4 (Server Services); and (ii) have the applicable minimum computing requirements described in Appendix A below.
Resource Unit Definition: Each Linux Standard OS Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.6.3 | Linux Low OS Instance |
“Linux Low OS Instance” means an Operating System instance that operates on a Linux Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to (i) receive the “Linux Low OS Instance” described in Schedule A-2.4 (Server Services); and (ii) have the applicable minimum computing requirements described in Appendix A below.
Resource Unit Definition: Each Linux Low OS Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.6.4 | Windows High OS Instance |
“Windows High OS Instance” means an Operating System instance that operates on a Microsoft Windows Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to (i) receive the “Windows High OS Instance” described in Schedule A-2.4 (Server Services); and (ii) have the applicable minimum computing requirements described in Appendix A)
Resource Unit Definition: Each Windows High OS Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.6.5 | Windows Standard OS Instance |
“Windows Standard OS Instance” means an Operating System instance that operates on a Microsoft Windows Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to (i) receive the “Windows Standard OS Instance” described in Schedule A-2.4 (Server Services); and (ii) have the applicable minimum computing requirements described in Appendix A below.
Resource Unit Definition: Each Windows Standard OS Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.6.6 | Windows Low OS Instance |
“Windows Low OS Instance” means an Operating System instance that operates on a Microsoft Windows Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to (i) receive the “Windows Low OS Instance” described in Schedule A-2.4 (Server Services); and
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 188 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
(ii) have the applicable minimum computing requirements described in Appendix A below.
Resource Unit Definition: Each Windows Low OS Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.6.7 | UNIX High OS Instance |
“UNIX High OS Instance” means an Operating System instance that operates on the Solaris or AIX Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to (i) receive the “UNIX High OS Instance” described in Schedule A-2.4 (Server Services); and (ii) have the applicable minimum computing requirements described in Appendix A below.
Resource Unit Definition: Each Unix High OS Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.6.8 | UNIX Standard OS Instance |
“UNIX Standard OS Instance” means an Operating System instance that operates on a the Solaris or AIX Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to (i) receive the “UNIX Standard OS Instance” described in Schedule A-2.4 (Server Services); and (ii) have the applicable minimum computing requirements described in Appendix A below.
Resource Unit Definition: Each Unix Standard OS Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.6.9 | UNIX Low OS Instance |
“UNIX Low OS Instance” means an Operating System Instance that operates on a the Solaris or AIX Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to (i) receive the “UNIX Low OS Instance” described in Schedule A-2.4 (Server Services); and (ii) have the applicable minimum computing requirements described in Appendix A below.
Resource Unit Definition: Each Unix Low OS Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
“ESX/Xen Host” means device running the ESX or XenServer Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to receive the “ESX /XenServer OS Instance” described in Schedule A-2.4 (Server Services).
Resource Unit Definition: Each ESX /Xen Host Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.6.11 | iSeries OS Instance |
“iSeries OS Instance” means an Operating System instance that operates on a the iSeries (AS 400) Operating System platform on a Server at a CoreLogic Data Center or Supplier Facility that CoreLogic has designated to receive the “iSeries OS Instance” described in Schedule A-2.4 (Server Services).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 189 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 1.7 | Resource Unit Definition: Each iSeries OS Instance as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.Supplier Server Hardware |
This Section details the Resource Units associated with Schedule A-2.4 (Server Services). All of the *** and *** associated with providing the Server Services are included in the Charges for the Resource Units covered in this Section.
| |
| 1.7.1 | Physical Server Small Server |
“Physical Server Small” means a physical Server that operates on a Microsoft Windows or Linux Standard OS platform and has a baseline of computing resources up to *** GB MEM and up to *** Cores of CPU and boot drive storage (which is not *** to CoreLogic).
Resource Unit Definition: Each Physical Server Small as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.7.2 | Physical Server Medium Server |
“Physical Server Medium” means a physical Server that operates on a Microsoft Windows or Linux Standard OS platform and has a baseline of computing resources greater than ***- but less than *** GB MEM and up to *** Cores of CPU and boot drive storage (which is not *** to CoreLogic).
Resource Unit Definition: Each Physical Server Medium as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.7.3 | Physical Server Large Server |
“Physical Server Large” means a physical Server that operates on a Microsoft Windows or Linux Standard OS platform and has a baseline of computing resources equal to or greater than ***- but less than ***- GB MEM and up to *** Cores of CPU and boot drive storage (which is not *** to CoreLogic).
Resource Unit Definition: Each Physical Server Large as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.7.4 | Physical Server Extra-Large Server |
“Physical Server Extra-Large” means a physical Server that operates on a Microsoft Windows or Linux Standard OS platform and has a baseline of computing resources equal to or greater than *** GB MEM and up to *** Cores of CPU and boot drive storage (which is *** to CoreLogic).
Resource Unit Definition: Each Physical Server Extra-Large as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
All of the *** and *** associated with providing private cloud Services are included in the Charges for the Resource Units covered in this Section.
| |
| 1.8.1 | Private Cloud Small Server |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 190 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
“Private Cloud Small Server” means a Virtual Server that operates on a Microsoft Windows or Linux Non-Standard OS platform in the Private Cloud Environment that has a baseline of computing resources up to *** GB vMEM and *** – *** Cores of vCPU.
Resource Unit Definition: Each Private Cloud Small Server as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.8.2 | Private Cloud Medium Server |
“Private Cloud Medium Server” means a Virtual Server that operates on a Microsoft Windows or Linux Non-Standard OS platform in the Private Cloud Environment that has a baseline of computing resources between *** and *** GB vMEM and up to *** Cores of vCPU.
Resource Unit Definition: Each Private Cloud Medium Server as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.8.3 | Private Cloud Large Server |
“Private Cloud Large Server” means a Virtual Server that operates on a Microsoft Windows or Linux Non-Standard OS platform in the Private Cloud Environment that has a baseline of computing resources between *** and *** GB vMEM and up to *** Cores of vCPU.
Resource Unit Definition: Each Private Cloud Large Server as measured using data from the CMDB on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
This Section details the Resource Units associated with Schedule A-2.1 (Cross Functional Services).
| |
| 1.9.1 | Service Management Resolver Licenses |
“Service Management Resolver License” means a license required for CoreLogic employees and contractors (“Resolvers”) to create, update, and/or close tickets in the Supplier’s service management system. For clarity, (i) a resolver license is not required for CoreLogic employees and contractors to open and check status for Incidents and Requests, and (ii) a resolver license for Supplier employees and contractors is excluded.
Resource Unit Definition: Each Service Management Resolver License as measured using data from the Supplier’s service management system (excluding Service Management Resolver Licenses that do not meet the definition above) on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.9.2 | Electronic Data Exchange (EDE) |
“Electronic Data Exchange” means the number of dedicated FTEs required to perform file transfer Services as defined in Schedule A-2.8
Resource Unit Definition: Each named FTE supporting file transfer service as set forth in Schedule A-2.8 within the applicable calendar month, shall be equal to one (1) Resource Unit.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 191 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 1.10 | Security Administration Services |
This Section details the Resource Units associated with Security Administration Services.
| |
| 1.10.1 | User Security Administration: |
A "User Security Administration Request" means an add, delete or change for access or secure authentication to an Application or Systems Software.
Resource Unit Definition: Each User Security Administration Request measured in Supplier’s service management system in the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.10.2 | End Point Log Retention and Monitoring Sources |
“End Point Log Retention and Monitoring Source” means an end point log source captured and monitored by the Supplier’s security information event management system. All end points must be directly connected to the CoreLogic network and be approved for consolidated logging by the CoreLogic security team.
Resource Unit Definition: Each End Point Log Retention and Monitoring Source as measured using data from Supplier’s security information and event management system on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.10.3 | Firewall Rule Changes |
“Firewall Rule Change” means a Service Request covering additions, changes or deletions to the Firewall rules, including system or group definitions, Network routing tables, access control lists and authentication configurations.
Resource Unit Definition: Each Firewall Rule Change as measured by Supplier’s service management system during the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.11 | Storage and Backup Services. |
This Section details the Resource Units associated with Schedule A-2.5 (Storage and Backup Services).
| |
| 1.11.1 | Storage Management (Services Only) |
“Storage Management (Services Only)” means CoreLogic provided storage for which Supplier performs Services.
Storage Management (Services Only) is measured based on the aggregate amount of usable TBs of CoreLogic storage identified in the Storage Management software that is allocated to a Server.
Resource Unit Definition: Each usable TB of Storage Management (Service Only) allocated to a server measured in the storage management system on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.11.2 | Backup Management (Services Only) |
“Backup Management (Services Only)” means operation, support and management of the CoreLogic provided backup systems by the Supplier as set forth in Schedule A-2.5.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 192 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Resource Unit Definition: Each gigabyte of data that is processed by the Backup Management System during applicable calendar month as measured by CoreLogic’s Backup Management System shall be equal to one (1) Resource Unit.
| |
| 1.11.3 | Tier 1 Storage (Services and Hardware) |
“Tier 1 Supplier SAN Storage” means Supplier-owned, configured and CoreLogic-usable SAN Supplier storage (with a drive geometry of ***GB or ***GB @ *** RPM and a redundant array of independent disks (RAID) level of ***) that is allocated to a Server. Tier 1 Supplier SAN Storage is measured based on usable TBs of Tier 1 Supplier SAN Storage identified in the Storage Management Software that is allocated to Servers.
The Tier 1 Storage Resource Unit represents the Charges for all of the Equipment, Software and Services associated with Tier 1 Supplier Storage.
Resource Unit Definition: Each usable TB of Tier 1 Supplier SAN Storage allocated to a Server measured by Supplier’s storage management system on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.11.4 | Tier 2 Storage (Services and Hardware) |
“Tier 2 Supplier SAN Storage” means Supplier-owned, configured and CoreLogic-usable Supplier storage (with a drive geometry of ***GB or ***GB @ ***RPM and a redundant array of independent disks (RAID) level of ***) that is allocated to a Server.
Tier 2 Supplier SAN Storage is measured based on usable TBs of Tier 2 Supplier SAN Storage identified in the Storage Management Software that is allocated to Servers.
The Tier 2 Storage Resource Unit represents the Charges for all of the Equipment, Software and Services associated with Tier 2 Supplier Storage.
Resource Unit Definition: Each usable TB of Tier 2 Supplier SAN Storage measured by Supplier’s storage management system allocated to Server on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.11.5 | Tier 3 Storage (Services and Hardware) |
“Tier 3 Supplier SAN Storage” means Supplier-owned, configured and CoreLogic-usable Supplier storage (with a drive geometry of ***, ***, or *** @ ***RPM and a redundant array of independent disks (RAID) level of ***) that is allocated to a Server. Tier 3 Supplier SAN Storage is measured based on TBs of Tier 3 Supplier Storage identified in the Storage Management software that is allocated to Servers.
The Tier 3 Storage Resource Unit represents the Charges for all of the Equipment, Software and Services associated with Tier 2 Supplier Storage.
Resource Unit Definition: Each TB of Tier 3 Supplier SAN Storage allocated to a Server as measured by Supplier’s storage management system on the fifteenth day of the applicable calendar month shall be equal to one (1) Resource Unit.
| |
| 1.11.6 | Backup Management (Services and Hardware) |
“Backup Management (Services and Hardware)” means a backup of CoreLogic Data to tape media that is performed by Supplier using Supplier-owned Backup
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 193 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Management Systems and that is managed by Supplier on-site at a Supplier Facility or off-site at a Supplier vaulting service provider.
Backup Management (Services and Hardware) Resource Unit represents the Charges for all of the Equipment (e.g., Supplier’s management Systems), Software and Services associated with Backup Management (Services and Hardware).
.Resource Unit Definition: Each gigabyte of data that is processed by the Backup Management System during applicable calendar month as measured by Supplier’s Backup Management System shall be equal to one (1) Resource Unit.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 194 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Appendix A – Minimum Server Requirements
|
| | | |
| | Windows, UNIX Linux OS High | Windows, UNIX Linux OS Standard | Windows, UNIX Linux OS Low |
Clustering Required
| *** | *** | *** |
| Software Requirements | *** | *** | *** |
| Hardware Requirements | *** | *** | *** |
| LAN | *** | *** | *** |
| SAN & Storage | *** | *** | *** |
| Load Balancer (if required by application) | *** | *** | *** |
| Firewall | *** | *** | *** |
| IDS/ IPS | *** | *** | *** |
| Vendor 24x7, 4 hour response Maintenance and Support Required | *** | *** | *** |
| Dell Data Center Location / CoreLogic Location / Both | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 195 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | |
| Schedule A-4.3 Baseline Volumes | | | | | | | | | | | |
| The definitions associated with these Resource Units are set forth in Schedule A-4.2 | | | | | | | | | |
| Description | Banding | | 2013 Monthly Volumes | |
| Network | | | Jan | Feb | Mar | Apr | May | Jun | Jul | Aug | Sept | Oct | Nov | Dec | |
| Network Switch /Router | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Physical Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Physical Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Virtual Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Virtual Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Security Appliances | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Wireless Access Points | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Load Balancer - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Load Balancer - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Misc. Network Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| VoIP Phones | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Network IMADS | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | # |
| End User Device Support and Messaging | | | | | | | | | | | | | | | |
| EUC (Desktop/Laptop) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Desktop IMACS - Campus | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Desktop IMACS - Remote | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Network Printer | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Exchange Email Account | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Mobile Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Desktop Application Package | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Desktop Image Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Employee Service Desk | | | | | | | | | | | | | | | |
| Service Desk Tickets | *** | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Mainframe | | | | | | | | | | | | | | | |
| Mainframe Service | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Mainframe Tapes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Midrange and Server | | | | | | | | | | | | | | | |
| Hardware | | | | | | | | | | | | | | | |
| Physical Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Physical Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Physical Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Physical Server Extra Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 196 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | |
| Cloud Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | # |
| Cloud Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | # |
| Cloud Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Services | | | | | | | | | | | | | | | |
| Linux OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Linux OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Linux OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Windows OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Windows OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Windows OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| UNIX Low OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| UNIX Medium OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| UNIX High OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| i-Series | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| ESX/Xen Host | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Storage and Backup Services | | | | | | | | | | | | | | | |
| Services Only | | | | | | | | | | | | | | | |
| Storage Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Services and Hardware | | | | | | | | | | | | | | | |
| Tier 1 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Tier 2 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Tier 3 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Cross Functional Services | | | | | | | | | | | | | | | |
| Service Management Resolver Licenses | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Electronic Data Exchange (EDE) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Security Administration Services | | | | | | | | | | | | | | | |
| User Security Administration | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| End Point Log Retention & Monitoring | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| Firewall Rule Changes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
|
| | | | | | | | | | | | | | |
| Description | Banding | | 2014 Monthly Volumes |
| Network | | | Jan | Feb | Mar | Apr | May | Jun | Jul | Aug | Sept | Oct | Nov | Dec |
| Network Switch /Router | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 197 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Virtual Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Appliances | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Wireless Access Points | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Misc. Network Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| VoIP Phones | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network IMADS | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End User Device Support and Messaging | | | | | | | | | | | | | | |
| EUC (Desktop/Laptop) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Campus | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Remote | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network Printer | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Exchange Email Account | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mobile Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Application Package | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Image Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Employee Service Desk | | | | | | | | | | | | | | |
| Service Desk Tickets | *** | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe | | | | | | | | | | | | | | |
| Mainframe Service | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe Tapes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Midrange and Server | | | | | | | | | | | | | | |
| Hardware | | | | | | | | | | | | | | |
| Physical Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Extra Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services | | | | | | | | | | | | | | |
| Linux OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 198 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Windows OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Low OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Medium OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX High OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| i-Series | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| ESX/Xen Host | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Storage and Backup Services | | | | | | | | | | | | | | |
| Services Only | | | | | | | | | | | | | | |
| Storage Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services and Hardware | | | | | | | | | | | | | | |
| Tier 1 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 2 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 3 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cross Functional Services | | | | | | | | | | | | | | |
| Service Management Resolver Licenses | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Electronic Data Exchange (EDE) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Administration Services | | | | | | | | | | | | | | |
| User Security Administration | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End Point Log Retention & Monitoring | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Firewall Rule Changes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | | | | | | | | | | | | | |
| Description | Banding | | 2015 Monthly Volumes |
| Network | | | Jan | Feb | Mar | Apr | May | Jun | Jul | Aug | Sept | Oct | Nov | Dec |
| Network Switch /Router | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Appliances | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Wireless Access Points | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Misc. Network Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| VoIP Phones | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network IMADS | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 199 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| End User Device Support and Messaging | | | | | | | | | | | | | | |
| EUC (Desktop/Laptop) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Campus | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Remote | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network Printer | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Exchange Email Account | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mobile Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Application Package | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Image Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Employee Service Desk | | | | | | | | | | | | | | |
| Service Desk Tickets | *** | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe | | | | | | | | | | | | | | |
| Mainframe Service | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe Tapes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Midrange and Server | | | | | | | | | | | | | | |
| Hardware | | | | | | | | | | | | | | |
| Physical Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Extra Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services | | | | | | | | | | | | | | |
| Linux OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Low OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Medium OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX High OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| i-Series | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| ESX/Xen Host | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Storage and Backup Services | | | | | | | | | | | | | | |
| Services Only | | | | | | | | | | | | | | |
| Storage Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 200 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services and Hardware | | | | | | | | | | | | | | |
| Tier 1 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 2 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 3 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cross Functional Services | | | | | | | | | | | | | | |
| Service Management Resolver Licenses | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Electronic Data Exchange (EDE) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Administration Services | | | | | | | | | | | | | | |
| User Security Administration | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End Point Log Retention & Monitoring | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Firewall Rule Changes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | | | | | | | | | | | | | |
| Description | Banding | | 2016 Monthly Volumes |
| Network | | | Jan | Feb | Mar | Apr | May | Jun | Jul | Aug | Sept | Oct | Nov | Dec |
| Network Switch /Router | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Appliances | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Wireless Access Points | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Misc. Network Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| VoIP Phones | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network IMADS | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End User Device Support and Messaging | | | | | | | | | | | | | | |
| EUC (Desktop/Laptop) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Campus | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Remote | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network Printer | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Exchange Email Account | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mobile Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Application Package | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Image Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 201 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Employee Service Desk | | | | | | | | | | | | | | |
| Service Desk Tickets | *** | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe | | | | | | | | | | | | | | |
| Mainframe Service | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe Tapes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Midrange and Server | | | | | | | | | | | | | | |
| Hardware | | | | | | | | | | | | | | |
| Physical Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Extra Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services | | | | | | | | | | | | | | |
| Linux OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Low OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Medium OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX High OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| i-Series | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| ESX/Xen Host | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Storage and Backup Services | | | | | | | | | | | | | | |
| Services Only | | | | | | | | | | | | | | |
| Storage Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services and Hardware | | | | | | | | | | | | | | |
| Tier 1 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 2 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 3 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cross Functional Services | | | | | | | | | | | | | | |
| Service Management Resolver Licenses | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Electronic Data Exchange (EDE) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 202 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Security Administration Services | | | | | | | | | | | | | | |
| User Security Administration | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End Point Log Retention & Monitoring | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Firewall Rule Changes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | | | | | | | | | | | | | |
| Description | Banding | | 2017 Monthly Volumes |
| Network | | | Jan | Feb | Mar | Apr | May | Jun | Jul | Aug | Sept | Oct | Nov | Dec |
| Network Switch /Router | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Appliances | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Wireless Access Points | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Misc. Network Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| VoIP Phones | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network IMADS | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End User Device Support and Messaging | | | | | | | | | | | | | | |
| EUC (Desktop/Laptop) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Campus | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Remote | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network Printer | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Exchange Email Account | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mobile Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Application Package | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Image Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Employee Service Desk | | | | | | | | | | | | | | |
| Service Desk Tickets | *** | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe | | | | | | | | | | | | | | |
| Mainframe Service | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe Tapes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Midrange and Server | | | | | | | | | | | | | | |
| Hardware | | | | | | | | | | | | | | |
| Physical Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 203 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Physical Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Extra Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services | | | | | | | | | | | | | | |
| Linux OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Low OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Medium OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX High OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| i-Series | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| ESX/Xen Host | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Storage and Backup Services | | | | | | | | | | | | | | |
| Services Only | | | | | | | | | | | | | | |
| Storage Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services and Hardware | | | | | | | | | | | | | | |
| Tier 1 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 2 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 3 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cross Functional Services | | | | | | | | | | | | | | |
| Service Management Resolver Licenses | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Electronic Data Exchange (EDE) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Administration Services | | | | | | | | | | | | | | |
| User Security Administration | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End Point Log Retention & Monitoring | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Firewall Rule Changes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | | | | | | | | | | | | | |
| Description | Banding | | 2018 Monthly Volumes |
| Network | | | Jan | Feb | Mar | Apr | May | Jun | Jul | Aug | Sept | Oct | Nov | Dec |
| Network Switch /Router | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 204 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Physical Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Appliances | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Wireless Access Points | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Misc. Network Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| VoIP Phones | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network IMADS | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End User Device Support and Messaging | | | | | | | | | | | | | | |
| EUC (Desktop/Laptop) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Campus | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Remote | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network Printer | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Exchange Email Account | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mobile Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Application Package | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Image Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Employee Service Desk | | | | | | | | | | | | | | |
| Service Desk Tickets | *** | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe | | | | | | | | | | | | | | |
| Mainframe Service | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe Tapes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Midrange and Server | | | | | | | | | | | | | | |
| Hardware | | | | | | | | | | | | | | |
| Physical Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Extra Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services | | | | | | | | | | | | | | |
| Linux OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 205 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Windows OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Low OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Medium OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX High OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| i-Series | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| ESX/Xen Host | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Storage and Backup Services | | | | | | | | | | | | | | |
| Services Only | | | | | | | | | | | | | | |
| Storage Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services and Hardware | | | | | | | | | | | | | | |
| Tier 1 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 2 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 3 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cross Functional Services | | | | | | | | | | | | | | |
| Service Management Resolver Licenses | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Electronic Data Exchange (EDE) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Administration Services | | | | | | | | | | | | | | |
| User Security Administration | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End Point Log Retention & Monitoring | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Firewall Rule Changes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | | | | | | | | | | | | | |
| Description | Banding | | 2019 Monthly Volumes |
| Network | | | Jan | Feb | Mar | Apr | May | Jun | Jul | Aug | Sept | Oct | Nov | Dec |
| Network Switch /Router | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Appliances | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Wireless Access Points | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Clustered | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Standalone | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Misc. Network Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 206 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| VoIP Phones | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network IMADS | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End User Device Support and Messaging | | | | | | | | | | | | | | |
| EUC (Desktop/Laptop) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Campus | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Remote | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network Printer | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Exchange Email Account | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mobile Device | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Application Package | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Image Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Employee Service Desk | | | | | | | | | | | | | | |
| Service Desk Tickets | *** | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe | | | | | | | | | | | | | | |
| Mainframe Service | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe Tapes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Midrange and Server | | | | | | | | | | | | | | |
| Hardware | | | | | | | | | | | | | | |
| Physical Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Extra Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Small | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Medium | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Large | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services | | | | | | | | | | | | | | |
| Linux OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Low | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS Standard | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows OS High | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Low OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Medium OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX High OS Instance | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| i-Series | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| ESX/Xen Host | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Storage and Backup Services | | | | | | | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 207 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Services Only | | | | | | | | | | | | | | |
| Storage Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services and Hardware | | | | | | | | | | | | | | |
| Tier 1 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 2 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 3 Storage | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cross Functional Services | | | | | | | | | | | | | | |
| Service Management Resolver Licenses | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Electronic Data Exchange (EDE) | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Administration Services | | | | | | | | | | | | | | |
| User Security Administration | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End Point Log Retention & Monitoring | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Firewall Rule Changes | No Band | | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | | |
| Description | Banding | | 2020 Monthly Volumes |
| Network | | | Jan |
| Network Switch /Router | No Band | | *** |
| Physical Firewall - Clustered | No Band | | *** |
| Physical Firewall - Standalone | No Band | | *** |
| Virtual Firewall - Clustered | No Band | | *** |
| Virtual Firewall - Standalone | No Band | | *** |
| Security Appliances | No Band | | *** |
| Wireless Access Points | No Band | | *** |
| Load Balancer - Clustered | No Band | | *** |
| Load Balancer - Standalone | No Band | | *** |
| Misc. Network Device | No Band | | *** |
| VoIP Phones | No Band | | *** |
| Network IMADS | No Band | | *** |
| End User Device Support and Messaging | | | |
| EUC (Desktop/Laptop) | No Band | | *** |
| Desktop IMACS - Campus | No Band | | *** |
| Desktop IMACS - Remote | No Band | | *** |
| Network Printer | No Band | | *** |
| Exchange Email Account | No Band | | *** |
| Mobile Device | No Band | | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 208 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Desktop Application Package | No Band | | *** |
| Desktop Image Management | No Band | | *** |
| Employee Service Desk | | | |
| Service Desk Tickets | *** | | *** |
| Mainframe | | | |
| Mainframe Service | No Band | | *** |
| Mainframe Tapes | No Band | | *** |
| Midrange and Server | | | |
| Hardware | | | |
| Physical Server Small | No Band | | *** |
| Physical Server Medium | No Band | | *** |
| Physical Server Large | No Band | | *** |
| Physical Server Extra Large | No Band | | *** |
| Cloud Server Small | No Band | | *** |
| Cloud Server Medium | No Band | | *** |
| Cloud Server Large | No Band | | *** |
| Services | | | |
| Linux OS Low | No Band | | *** |
| Linux OS Standard | No Band | | *** |
| Linux OS High | No Band | | *** |
| Windows OS Low | No Band | | *** |
| Windows OS Standard | No Band | | *** |
| Windows OS High | No Band | | *** |
| UNIX Low OS Instance | No Band | | *** |
| UNIX Medium OS Instance | No Band | | *** |
| UNIX High OS Instance | No Band | | *** |
| i-Series | No Band | | *** |
| ESX/Xen Host | No Band | | *** |
| Storage and Backup Services | | | |
| Services Only | | | |
| Storage Management | No Band | | *** |
| Backup Management | No Band | | *** |
| Services and Hardware | | | |
| Tier 1 Storage | No Band | | *** |
| Tier 2 Storage | No Band | | *** |
| Tier 3 Storage | No Band | | *** |
| Backup Management | No Band | | *** |
| Cross Functional Services | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 209 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Service Management Resolver Licenses | No Band | | *** |
| Electronic Data Exchange (EDE) | No Band | | *** |
| Security Administration Services | | | |
| User Security Administration | No Band | | *** |
| End Point Log Retention & Monitoring | No Band | | *** |
| Firewall Rule Changes | No Band | | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 210 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | |
| The definitions associated with these Resource Units are set forth in Schedule A-4.2 | ARC/RRC Rates |
| 2012 | 2013 | 2014 | 2015 | 2016 | 2017 | 2018 | 2019 | 2020 |
| Network | | | | | | | | | |
| Network Switch /Router | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Clustered | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Firewall - Standalone | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Clustered | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Virtual Firewall - Standalone | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Appliances | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Wireless Access Points | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Clustered | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Load Balancer - Standalone | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Miscellaneous Network Device | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| VoIP Phones | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network IMACS | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End User Device Support and Messaging | | | | | | | | | |
| EUC (Desktop/Laptop) | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Campus | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop IMACS - Remote | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Network Printer | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Exchange Email Account | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mobile Device | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Application Package | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Desktop Image Management | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Employee Service Desk | | | | | | | | | |
| Service Desk Tickets | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe | | | | | | | | | |
| Mainframe Service | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Mainframe Tapes | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Midrange and Server | | | | | | | | | |
| Hardware | | | | | | | | | |
| Physical Server Small | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Medium | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Physical Server Large | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 211 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | |
| The definitions associated with these Resource Units are set forth in Schedule A-4.2 | ARC/RRC Rates |
| 2012 | 2013 | 2014 | 2015 | 2016 | 2017 | 2018 | 2019 | 2020 |
| Physical Server Extra Large | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Small | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Medium | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cloud Server Large | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services | | | | | | | | | |
| Linux Low OS Instance | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux Medium OS Instance | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Linux High OS Instance | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows Low OS Instance | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows Medium OS Instance | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Windows High OS Instance | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Low OS Instance | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX Medium OS Instance | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| UNIX High OS Instance | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| | | | | | | | | | |
| i-Series | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| ESX/Xen Host | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Storage and Backup Services | | | | | | | | | |
| Services Only | | | | | | | | | |
| Storage Management | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Services and Hardware | | | | | | | | | |
| Tier 1 Storage | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 2 Storage | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Tier 3 Storage | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Backup Management | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Cross Functional Services | | | | | | | | | |
| Service Management Resolver Licenses | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Electronic Data Exchange (EDE) | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Security Administration Services | | | | | | | | | |
| User Security Administration | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| End Point Log Retention & Monitoring | *** | *** | *** | *** | *** | *** | *** | *** | *** |
| Firewall Rule Changes | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 212 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-4.5
TRANSITION CHARGES AND TRANSFORMATION CHARGES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 213 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-4.5
Transition Charges and Transformation Charges
| |
| 1.1 | Agreement. This Schedule A-4.5 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
| |
| 2. | TRANSFORMATION CHARGES AND TRANSFORMATION MILESTONES |
| |
| 2.1 | Transformation Charges. The Transformation Charges are set forth in Schedule A-4.5.2. Supplier will invoice CoreLogic at the beginning of each month for the amount corresponding to such month as set forth in Schedule A-4.5.2, and in accordance with Section 12.1 of the MSA. |
| |
| 2.2 | Transformation Milestones. If Supplier fails to meet the Transformation Milestones set forth in this Section 2.2 (and further described in Schedule A-13), Supplier shall pay the applicable Deliverable Credits set forth this Section 2.2. If Supplier is entitled to the “additional monthly payments” described in this Section2.2, CoreLogic shall pay such amounts as further described in this Section 2.2. |
| |
| (a) | *** Transformation Milestone - Mainframe Resource Units |
If Supplier fails to meet *** System Transformation Milestone Number 4 within Schedule A-13.2 and migrate the in-scope Application components identified in Section 2.3 of Schedule A-13 prior to the applicable “Completion Date”, to the “Target Platforms” described therein, *** shall not *** for the *** during the period of *** beyond the ***
(ii) If, in the performance of the *** Transformation Services, Supplier is able to migrate the in-scope Application components identified in Section 2.3 of Schedule A-13 before the “Completion Date” listed for *** System Transformation Milestone Number 4 within Schedule A-13.2 , notwithstanding Section 5.3(b)(ii) of Schedule A-04, *** will continue to *** the *** through the *** within Schedule A-13.2.
| |
| (b) | Midrange Environment Transformation Milestone |
| |
| (i) | The midrange environment resulting from the *** System Transformation Services is expected to consist of no more than *** physical Servers Resource Units, *** Private Cloud Servers (*** Private Cloud Small Servers, *** Private Cloud Medium Servers, *** Private Cloud Large Servers), *** Linux OS Instances (*** Linux Low OS Instance, *** Linux Medium OS Instances, *** Linux High OS Instances), and *** Windows OS Instances (*** Windows Medium OS Instances, and *** Windows High OS Instances). |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 214 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (ii) | With respect to Supplier’s performance of the *** Transformation Services, (a) if and to the extent there are no material increases in *** after the commencement of the *** Transformation Services, and (b) if there are more physical Servers, Private Cloud Servers, Linux OS Instances or Windows OS Instances in the CoreLogic environment than the amounts listed in Section 2.2(b)(i), *** shall *** a *** for *** such Resource Unit that is greater than the applicable amount depicted in Section 2.2(b)(i) multiplied by the applicable *** for *** shown in the table in Section 2.2(b)(iv). Any such *** shall continue to apply for *** or until the applicable Resource Unit is *** by ***. |
| |
| (iii) | With respect to Supplier’s performance of the *** Transformation Services, (a) if and to the extent there are no material decreases in CoreLogic’s business volumes after the commencement of the *** Transformation Services, and (b) if Supplier achieves an environment which is less than the volumes of physical Servers, Private Cloud Servers, Linux OS Instances, or Windows OS Instances set forth in Section 2.2(b)(i), *** shall *** an ***, equal to the applicable *** for *** shown in the table in Section 2.2(b)(iv), multiplied by the volume each Resource Unit is less than the maximum applicable amount permitted under Section 2.2(b)(i). Any such *** shall continue to apply for ***. |
| |
| (iv) | The following table shall be used to calculate the Deliverable Credits or payments under this Section 2.2(b): |
|
| | |
| Resource Unit | Volume Limit | Credit Rate as set forth in Schedule A-4.4 |
| Physical Servers (small, medium, and large) | *** physical servers | Physical Server – Medium rate |
| Cloud Servers (small, medium, and large) | *** Cloud servers | Cloud Server – Medium rate |
| OS Instances (Windows and Linux) | *** OS Instances | Windows OS Standard rate |
| |
| (c) | U2L Transformation Milestone – UNIX and Linux Physical Server Resource Units |
| |
| (i) | If Supplier fails to meet U2L Transformation Milestone 4 for *** and ***within Schedule A-13.2 and does not transform the UNIX OS instances on at least *** Physical Servers (“UNIX Physical Servers”) to servers operating Linux OS Instances (such that the UNIX Physical Server can be removed from service) before the applicable “Completion Date”, *** shall *** a *** for each such UNIX Physical Server for which the UNIX OS Instances cannot be so transitioned multiplied by the *** for a *** ***. Any such *** shall continue to apply *** are transitioned by Supplier or the *** is *** by ***. |
| |
| (ii) | If, in the performance of the U2L Transformation Services, Supplier is able to transition more than *** UNIX Physical Servers onto Linux Servers before the “Completion Date” listed for U2LTransformation Milestone 4 for *** and ***within Schedule A-13, *** shall *** an ***, equal to the *** for a ***, for each such additional UNIX Physical Server greater than *** for which the UNIX OS Instances have been transitioned. Any such *** shall continue to apply for ***. |
| |
| (iii) | If, as part of the U2L Transformation Services, Supplier requires more than *** Linux Servers after the “Completion Date” listed for U2L Transformation Milestone 4 for *** and ***within Schedule A-13 to host the Applications previously hosted on the UNIX Physical Servers in service as of the Supplement Effective Date, *** shall *** a *** for |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 215 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
each such Linux Server required multiplied by the *** for a ***. Any such *** shall continue to apply until the *** is *** by CoreLogic.
| |
| (iv) | If, as part of the U2L Transformation Services, Supplier requires less than *** Linux Servers after the “Completion Date” listed for U2L Transformation Milestone 4 for *** and ***within Schedule A-13 to host the Applications previously hosted on the UNIX Physical Servers in service as of the Supplement Effective Date, *** shall *** an ***, equal to the *** for a ***, for each such Linux Server (i.e., less than ***) that is not required. Any such *** shall continue to apply for ***. |
| |
| (v) | By way of example, if after the “Completion Date” listed for U2L Transformation Milestone 4 for *** and ***within Schedule A-13, the UNIX OS instances on *** UNIX Physical Servers are transitioned to *** Linux Servers, *** would (i) *** a *** equal to four (*** target Unix Physical Servers minus *** actual Linux Servers) multiplied by the *** for a Unix Standard OS Instance Resource Unit and (ii) *** an *** to four multiplied by the *** for a ***. |
| |
| 3. | TRANSITION CHARGES AND TRANSITION MILESTONES |
| |
| 3.1 | Transition Charges. The Transition Charges are set forth in Schedule A-04.5.1. Supplier will invoice CoreLogic at the beginning of each month during the Transition Period for the amount corresponding to such month as set forth in Schedule A-4.5.1 and in accordance with Section 12.1 of the MSA. |
| |
| 3.2 | Credits for Transition Services. If Supplier fails to meet the Transition Milestones set forth this Section 3.2 (and further described in Schedule A-10), Supplier shall pay the applicable Deliverable Credits set forth this Section 3.2. If Supplier is entitled to the “additional monthly payments” described in this Section 3.2, CoreLogic shall pay such amounts as further described in this Section 3.2 . |
| |
| (a) | DCTMV Transition Milestone – Linux Physical to Virtual Server Resource Units |
| |
| (i) | If Supplier fails to meet DCTMV Transition Milestone 7 within Schedule A-10 and does not transform the OS Instances on less than *** Linux Physical Servers to operate as a Virtual Server after the applicable “Completion Date”, *** shall *** a *** for each such Linux Physical Server for which the OS Instances cannot be so transitioned multiplied by the *** for a ***. Any such *** shall continue to apply until *** on the *** are *** by *** or the *** is *** by CoreLogic. |
| |
| (ii) | If, in the performance of the DCTMV Services, Supplier is able to transition the OS Instances on more than *** Physical Linux Servers to operate as a Virtual Server before the “Completion Date” for DCTMV Transition Milestone 7 within Schedule A-10 , *** shall *** an *** for each such additional Physical Linux Server transitioned. The amount of the *** shall equal the *** for a Physical Server Medium Resource Unit. Any such *** shall continue to apply ***. |
| |
| (iii) | By way of example, if after the date listed for DCTMV Transition Milestone 7 within Schedule A-10, the OS instances on *** Linux Physical Servers are transitioned to Virtual Servers, *** would *** a *** equal to eight (*** target Linux Physical Servers minus *** actual Linux Physical Servers) multiplied by the *** for ***. |
| |
| (b) | DCTMV Transition Milestone – Windows Physical to Virtual Server Resource Units |
| |
| (i) | If Supplier fails to transform the Windows OS Instances on less than *** Physical Servers (“Windows Physical Servers”) to operate as a Virtual Server after the “Completion |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 216 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Date” for DCTMV Transition Milestone 7 within Schedule A-10 , *** shall *** a *** for each such Windows Physical Server for which the OS Instances are not transitioned multiplied by the *** *** for a ***. Any such *** shall continue to apply until the *** on the *** are *** by *** or the *** is *** by CoreLogic.
| |
| (ii) | If, in the performance of the DCTMV Services, Supplier is able to transition the OS Instances on more than *** Physical Windows Servers to operate as a Virtual Server before the “Completion Date” for DCTMV Transition Milestone 7 within Schedule A-10 , *** shall *** an *** for each such additional Physical Windows Server transitioned. The amount of the *** shall equal the *** for a ***. Any such *** shall continue to apply for ***. |
| |
| (iii) | By way of example, if after the date listed for DCTMV Transition Milestone 7 within Schedule A-10, the OS instances on *** Windows Physical Servers are transitioned to Virtual Servers, *** would *** a *** equal to nine (*** target Windows Physical Servers minus *** actual Windows Physical Servers) multiplied by the *** for ***. |
| |
| (c) | Storage Transition Milestone |
| |
| (i) | For the production storage environment that is tiered using auto tier, starting on July 1, 2014, and every six months thereafter, Supplier shall use the invoicing reports for storage during the previous six months and calculate the average amount of Tier 1, Tier 2, and Tier 3 storage over such six month period. For clarity, any storage that CoreLogic specifies to a specific tier will not be counted in such average and will be excluded from the calculation of this Section 3.2(c). |
| |
| (ii) | If such report indicates that greater than ***% of such storage is categorized as Tier 1 and Tier 2, then Supplier shall provide a Deliverable Credit to CoreLogic as follows: |
| |
| (1) | If Tier 1 TB storage is greater than ***% of the total auto tier storage environment, the Deliverable Credit shall be equal to (i) the number of Tier 1TB storage that exceeds ***% of the total auto tier storage environment multiplied by (ii) $*** (delta in *** between *** and ***) multiplied by (iii) six (6). |
| |
| (2) | If Tier 2 TB storage is greater than ***% of the total auto tier storage environment, the Deliverable Credit shall be equal to (i) the number of Tier 2TB storage that exceeds ***% of the total auto tier storage environment multiplied by (ii) $*** (delta in *** between *** and *** multiplied by (iii) six (6). |
| |
| (3) | For clarity, if Tier 1 TB storage is greater than ***% of the total auto tier storage environment and if Tier 2 TB storage is greater than ***% of the total auto tier storage environment, then Supplier shall pay Deliverable Credits to CoreLogic in accordance with both (1) and (2) above. |
| |
| (iii) | If such report indicates that less than ***% of such storage is categorized as Tier 1 and Tier 2 storage, but more than ***% of such storage is categorized as Tier 1 storage, Supplier shall provide a Deliverable Credit to CoreLogic as follows: |
If Tier 1 TB storage is greater than ***% of the total auto tier storage environment, the credit shall be equal to (i) the number of Tier 1TB storage that exceeds ***% of the total auto tier storage environment multiplied by (ii) $*** (delta in *** between *** and ***) multiplied by (iii) six (6).
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 217 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 3.3 | DCTMV Transition Milestones. Schedule A-10 sets forth the Transition Milestones applicable to Supplier’s performance of the DCTMV Services (the “DCTMV Transition Milestones”) and the associated Deliverable Credit if Supplier fails to meet the applicable Transition Milestone (the “DCTMV Deliverable Credits”). The portion of the applicable DCTMV Deliverable Credit to be provided to CoreLogic will depend on the ultimate Transition Milestone completion date of the applicable DCTMV Transition Milestone, as described in the following sentence. Specifically, ***% of the total DCTMV Deliverable Credit amounts set forth in the table below shall be provided to CoreLogic if the applicable DCTMV Transition Milestone is not completed by Supplier on or before each of (1) the date that is *** days after the Transition Milestone completion date, (2) the date that is *** days after the Transition Milestone completion date. Any DCTMV Deliverable Credit to be provided to CoreLogic will be reflected on the first monthly invoice that Supplier provides to CoreLogic after completion of the final DCTMV Transition Milestone. If the DCTMV Transition Plan is changed with CoreLogic’s approval in accordance with the processes described in Schedule A-10, the associated completion date of such Transition Milestone shall be appropriately adjusted based upon the change and without the necessity of amending this Schedule. |
|
| |
| Transition Milestone | Deliverable Credit Amount |
| Transition Milestone 1 -Data Center Move Project/ Final Project Schedule | *** |
| Transition Milestone 2-Data Center Move Project (West Lake Data Center Phase)/ Move Package Planning Complete | *** |
| Transition Milestone 3- Data Center Move Project (West Lake Data Center Phase)/ One-half of DCM Move Packages Complete | *** |
| Transition Milestone 4-Data Center Move Project (West Lake Data Center Phase)/ DCM Complete | *** |
| Transition Milestone 5 Data Center Move Project (Santa Ana Data Center Phase)/ Move Package Planning Complete | *** |
| Transition Milestone 6-Data Center Move Project (Santa Ana Data Center Phase)/ One-half of DCM Move Packages Complete | *** |
| Transition Milestone 7-Data Center Move Project (Santa Ana Data Center Phase)/ DCM Complete | *** |
| |
| 3.4 | Deliverable Credits for Operational Transition Services. If Supplier fails to meet the below Transition Milestone in accordance with Schedule A-10, Supplier shall pay to CoreLogic the associated Deliverable Credit as set forth in the table below. Any such Deliverable Credit to be provided to CoreLogic will be reflected on the first monthly invoice that Supplier provides to CoreLogic after completion of the Transition Milestone. If the Transition Plan is changed with CoreLogic’s approval in accordance with the processes described in Schedule A-10, the associated completion date of such Transition Milestone shall be appropriately adjusted based upon the change and without the necessity of amending this Schedule. |
|
| |
| Transition Milestone | Deliverable Credit Amount |
| Transition Milestone 27 - Transition complete and (FMO) Future Model Go-live | $ *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 218 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Schedule 4-5.1 Transition Charges | | | |
| Month | Operational Transition | Stabilization and reboot | DCTMV Planning | DCTMV Migration | Total |
| Aug-12 | $ *** | $ *** | $ - | $ *** | $ *** |
| Sep-12 | $ *** | $ *** | $ *** | $ *** | $ *** |
| Oct-12 | $ *** | $ *** | $ *** | $ *** | $ *** |
| Nov-12 | $ *** | $ *** | $ *** | $ *** | $ *** |
| Dec-12 | $ *** | $ *** | $ *** | $ *** | $ *** |
| Jan-13 | $ *** | | $ *** | $ *** | $ *** |
| Feb-13 | | | | $ *** | $ *** |
| Mar-13 | | | | $ *** | $ *** |
| Apr-13 | | | | $ *** | $ *** |
| May-13 | | | | $ *** | $ *** |
| Jun-13 | | | | $ *** | $ *** |
| Jul-13 | | | | $ *** | $ *** |
| Aug-13 | | | | $ *** | $ *** |
| Sep-13 | | | | $ *** | $ *** |
| Oct-13 | | | | $ *** | $ *** |
| Nov-13 | | | | $ *** | $ *** |
| Dec-13 | | | | $ *** | $ *** |
| Jan-14 | | | | $ *** | $ *** |
| Feb-14 | | | | $ *** | $ *** |
| Mar-14 | | | | $ *** | $ *** |
| Apr-14 | | | | $ *** | $ *** |
| May-14 | | | | $ *** | $ *** |
| Jun-14 | | | | $ *** | $ *** |
| Total | $ *** | $ *** | $ *** | $ *** | $ *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 219 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Month | Mainframe Planning and Assessment | Mainframe Configuration, Coding and Testing | U2L Planning and Assessment | U2L Configuration, Coding and Testing | Total Transformation |
| Aug-12 | $*** | $*** | $*** | $*** | $*** |
| Sep-12 | $*** | $*** | $*** | $*** | $*** |
| Oct-12 | $*** | $*** | $*** | $*** | $*** |
| Nov-12 | $*** | $*** | $*** | $*** | $*** |
| Dec-12 | $*** | $*** | $*** | $*** | $*** |
| Jan-13 | $*** | $*** | $*** | $*** | $*** |
| Feb-13 | $*** | $*** | $*** | $*** | $*** |
| Mar-13 | $*** | $*** | $*** | $*** | $*** |
| Apr-13 | $*** | $*** | $*** | $*** | $*** |
| May-13 | $*** | $*** | $*** | $*** | $*** |
| Jun-13 | $*** | $*** | $*** | $*** | $*** |
| Jul-13 | $*** | $*** | $*** | $*** | $*** |
| Aug-13 | $*** | $*** | $*** | $*** | $*** |
| Sep-13 | $*** | $*** | $*** | $*** | $*** |
| Oct-13 | $*** | $*** | $*** | $*** | $*** |
| Nov-13 | $*** | $*** | $*** | $*** | $*** |
| Dec-13 | $*** | $*** | $*** | $*** | $*** |
| Jan-14 | $*** | $*** | $*** | $*** | $*** |
| Feb-14 | $*** | $*** | $*** | $*** | $*** |
| Mar-14 | $*** | $*** | $*** | $*** | $*** |
| Apr-14 | $*** | $*** | $*** | $*** | $*** |
| May-14 | $*** | $*** | $*** | $*** | $*** |
| Jun-14 | $*** | $*** | $*** | $*** | $*** |
| Jul-14 | $*** | $*** | $*** | $*** | $*** |
| Aug-14 | $*** | $*** | $*** | $*** | $*** |
| Sep-14 | $*** | $*** | $*** | $*** | $*** |
| Oct-14 | $*** | $*** | $*** | $*** | $*** |
| Nov-14 | $*** | $*** | $*** | $*** | $*** |
| Total | $*** | $*** | $*** | $*** | $*** |
| | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 220 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Optional Pricing Section per Schedule A.13 | | | | |
| | | | | | |
| | Natural to COBOL Optional Pricing | | | | |
| | $*** | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 221 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
Schedule A-4.6
FINANCIAL RESPONSIBILITY MATRIX
This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 222 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
1. INTRODUCTION
1.1 Agreement. This Schedule A-4.6 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”).
1.2 References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided.
1.3 Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement.
1.4. Shipping Expenses. Shipping costs associated with the Equipment will be the responsibility of the party that owns the Equipment.
Mainframe
|
| | | | | |
| | | CoreLogic Facilities | Supplier Facilities |
| # | Details | Supplier | CoreLogic | Supplier | CoreLogic |
| Hardware | | | | |
| 1 | CPU | | *** | *** | |
| 2 | DASD | | *** | *** | |
| 3 | Tapes | | *** | *** | |
| 4 | Maintenance | | *** | *** | |
| 5 | Upgrades | | *** | *** | |
| 6 | Replacements | | *** | *** | |
| 7 | Administrative Procurement | | *** | *** | |
| Software | | | | |
| 8 | Software AG and maintenance | | *** | | *** |
| 9 | Content Management Software and maintenance | | *** | | *** |
| 10 | Clerity Software License + maintenance | | | | *** |
| 11 | Ateras and maintenance | | *** | | *** |
| 12 | IBM (Websphere, Tivoli, DB2) and maintenance | | *** | | *** |
| 13 | IBM OS (zOS, CICS, IBM Compiler / Library,OGL,PPFA,PSAF,PSF,QFM) and maintenance | | *** | *** | |
| 14 | CA Technologies and maintenance | | *** | | *** |
| 15 | Applications Software and maintenance | | *** | | *** |
| 16 | Job scheduling and maintenance | | *** | | *** |
| 17 | Monitoring and management Software and maintenance | | *** | | *** |
| 18 | Tools and Software to provide Services | *** | | *** | |
| 19 | Administrative Procurement | | *** | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 223 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Midrange and Server
|
| | | | | |
| | | CoreLogic Facilities | Supplier Facilities |
| # | Details | Supplier | CoreLogic | Supplier | CoreLogic |
| Linux and Windows Servers | | | | |
| Hardware | | | | |
| 1 | CoreLogic owned and leased assets, including Upgrades and replacement parts | | *** | *** | *** |
| 2 | Supplier owned and leased assets including Upgrades and replacement parts | *** | | *** | |
| 3 | Refreshes of hardware at end of lease or end of depreciation | *** | | *** | |
| 4 | Maintenance on CoreLogic owned assets | | *** | *** | *** |
| 5 | Maintenance on Supplier owned assets | *** | | *** | |
| 6 | Administrative procurement | | *** | *** | |
| Software | | | | |
| 7 | System Software and maintenance, including Operating Systems for CoreLogic owned assets | | *** | *** | *** |
| 8 | System Software and maintenance, including Operating Systems for Supplier owned assets | | *** | | *** |
| 9 | VMWare / Hypervisor and Software maintenance for CoreLogic owned assets | | *** | *** | *** |
| 10 | VMWare/Hypervisor and Software maintenance for Supplier owned assets | *** | | *** | |
| 11 | Application, Middleware & DB Software and maintenance | | *** | | *** |
| 12 | Monitoring and management Tools /Software maintenance | *** | | *** | |
| 13 | Tools and Software to provide Services | *** | | *** | |
| 14 | Administrative procurement for LINUX and Windows | | *** | *** | |
| AS/400 (iSeries) Servers | | | | |
| Hardware | | | | |
| 1 | Existing leases and owned assets (until end of life) | | *** | | *** |
| 2 | Future leases and owned assets | | *** | | *** |
| 3 | Maintenance | | *** | | *** |
| 4 | Upgrades | | *** | | *** |
| 5 | Replacements | | *** | | *** |
| 6 | Administrative procurement For AS400 | | *** | | *** |
| 7 | Procurement assistance for AS400 | *** | | *** | |
| Software | | | | |
| 8 | System Software and maintenance, including Operating Systems for CoreLogic owned assets | | *** | | *** |
| 9 | Virtualization Tools | | *** | | *** |
| 10 | Application, middleware & DB Software and maintenance | | *** | | *** |
| 11 | Monitoring and management tools / Software maintenance | *** | | *** | |
| 12 | Tools and Software to provide Services | *** | | *** | |
| 13 | Administrative procurement For AS400 | | *** | | *** |
| 14 | Procurement assistance for AS400 | *** | | *** | |
| Unix Servers | | | | |
| Hardware | | | | |
| 1 | Existing leases and owned assets (until end of life) | | *** | | *** |
| 2 | Future leases and owned assets | | *** | | *** |
| 3 | Maintenance | | *** | | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 224 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| | | CoreLogic Facilities | Supplier Facilities |
| 4 | Upgrades | | *** | | *** |
| 5 | Replacements | | *** | | *** |
| 6 | Administrative procurement For UNIX | | *** | | *** |
| 7 | Procurement assistance for UNIX | *** | | *** | |
| Software | | | | |
| 8 | System Software and maintenance, including Operating Systems for CoreLogic owned assets | | *** | | *** |
| 9 | Virtualization Tools | | *** | | *** |
| 10 | Application, middleware & DB Software and maintenance | | *** | | *** |
| 11 | Monitoring and management tools / Software maintenance | *** | | *** | |
| 12 | Tools and Software to provide Services | *** | | *** | |
| 13 | Administrative procurement For UNIX | | *** | | *** |
| 14 | Procurement assistance for UNIX | *** | | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 225 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Storage and Backup
|
| | | | | |
| | | CoreLogic Facilities | Supplier Facilities |
| # | Details | Supplier | CoreLogic | Supplier | CoreLogic |
| Storage Equipment | | | | |
| Hardware | | | | |
| 1 | CoreLogic owned and leased storage and backup assets, including Upgrades and replacement parts | | *** | *** | *** |
| 2 | Supplier owned and leased storage assets including Upgrades, refreshes and replacement parts | *** | | *** | |
| 3 | Refresh of storage assets at end of lease or end of depreciation | *** | | *** | |
| 4 | Supplier owned and leased backup assets including Upgrades, refreshes and replacement parts | | | *** | |
| 5 | Refresh of backup assets at end of lease or end of depreciation | *** | | *** | |
| 6 | Maintenance on CoreLogic owned assets | | *** | | |
| 7 | Maintenance on Supplier owned assets | *** | | *** | |
| 8 | Consumables (tape media) | | *** | *** | |
| 9 | Administrative procurement | | *** | *** | |
Software | | | | |
| 10 | CoreLogic owned backup Software and maintenance (Symantec NetBackup, Enterprise, etc.) | | *** | *** | *** |
| 11 | Supplier owned backup Software and maintenance | | | *** | |
| 12 | CoreLogic owned storage Software, Tools and maintenance (Netapp, EMC, etc.) | | *** | | *** |
| 13 | Supplier owned storage Software, Tools and maintenance | *** | | *** | |
| 14 | Tools and Software to provide Services | *** | | *** | |
| 15 | Administrative procurement | | *** | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 226 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Desktop and Laptops
|
| | | | | |
| | | CoreLogic Facilities | Supplier Facilities |
| # | Details | Supplier | CoreLogic | Supplier | CoreLogic |
| Desktop and Laptops for CoreLogic Personnel | | | | |
| Hardware | | | | |
| 1 | CoreLogic owned equipment | | *** | *** | *** |
| 2 | Existing leases | | *** | *** | *** |
| 3 | Future leases | | *** | *** | *** |
| 4 | Maintenance | | *** | *** | *** |
| 5 | Upgrades | | *** | *** | *** |
| 6 | Replacements | | *** | *** | *** |
| Software | | | | |
| 7 | Existing licenses | | *** | *** | *** |
| 8 | New licenses | | *** | *** | *** |
| 9 | Upgrades | | *** | *** | *** |
| 10 | Replacements | | *** | *** | *** |
| 11 | Maintenance fees | | *** | *** | *** |
| Desktop and Laptops for Supplier Personnel | | | | |
| Hardware | | | | |
| 1 | Supplier owned Equipment | *** | | *** | |
| 2 | Existing leases | *** | | *** | |
| 3 | Future leases | *** | | *** | |
| 4 | Maintenance | *** | | *** | |
| 5 | Upgrades | *** | | *** | |
| 6 | Replacements | *** | | *** | |
| Software | | | | |
| 7 | Existing licenses | *** | | *** | |
| 8 | New licenses | *** | | *** | |
| 9 | Upgrades | *** | | *** | |
| 10 | Replacements | *** | | *** | |
| 11 | Maintenance fees | *** | | *** | |
| Printers (desktop and network), Scanners, Fax machines, plasma screens, tele-presence Equipment, Desk phones, PDA's and Mobile phones, etc.) | | | | |
| Hardware | | | | |
| 1 | CoreLogic owned Equipment | | *** | *** | *** |
| 2 | Existing leases | | *** | *** | *** |
| 3 | Future leases | | *** | *** | *** |
| 4 | Maintenance | | *** | *** | *** |
| 5 | Upgrades | | *** | *** | *** |
| 5 | Replacements | | *** | *** | *** |
| 6 | Consumables (ink, paper, cables etc.) | | *** | *** | *** |
| Software | | | | |
| 7 | Existing licenses | | *** | *** | *** |
| 8 | New licenses | | *** | *** | *** |
| 9 | Upgrades | | *** | *** | *** |
| 10 | Replacements | | *** | *** | *** |
| 11 | Maintenance fees | | *** | *** | *** |
| Electronic Fax services and Citrix | | | | |
| 1 | Existing licenses | | *** | *** | *** |
| 2 | New licenses | | *** | *** | *** |
| 3 | Upgrades | | *** | *** | *** |
| 4 | Replacements | | *** | *** | *** |
| 5 | Maintenance fees | | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 227 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Network
|
| | | | | |
| | | CoreLogic Facilities | Supplier Facilities |
| # | Details | Supplier | CoreLogic | Supplier | CoreLogic |
| Data Network (Switches/Routers, Firewalls, Load Balancers, Misc. Network Devices, WAP) | | | | |
| Hardware | | | | |
| 1 | CoreLogic owned and leased assets, including Upgrades and replacement parts | | *** | | *** |
| 2 | Supplier owned and leased assets including Upgrades, refreshes and replacement parts | | | *** | |
| 3 | Maintenance on CoreLogic owned assets | | *** | | *** |
| 4 | Maintenance on Supplier owned assets | | | *** | |
| 5 | Administrative procurement for CoreLogic owned assets | | *** | | *** |
| 6 | Procurement assistance for CoreLogic owned assets | *** | | *** | |
| 7 | Administrative procurement for Supplier owned assets | | | *** | |
| Software | | | | |
| 8 | System Software and maintenance, including Operating Systems for CoreLogic owned assets | | *** | | *** |
| 9 | System Software and maintenance, including Operating Systems for Supplier owned assets | | | *** | |
| Voice Systems | | | | |
| Hardware | | | | |
| 1 | Existing leases and CoreLogic owned assets | | *** | | *** |
| 2 | Future leases and CoreLogic owned assets | | *** | | *** |
| 3 | VOIP Infrastructure hardware and maintenance | | *** | *** | |
| 4 | Maintenance on CoreLogic owned assets | | *** | | *** |
| 5 | Upgrades | | *** | | *** |
| 6 | Replacements | | *** | | *** |
| Software | | | | |
| 7 | Licenses | | *** | | *** |
| 8 | Maintenance | | *** | | *** |
| 9 | Upgrades | | *** | | *** |
| 10 | Replacements | | *** | | *** |
| 11 | Contact center Software | | *** | | *** |
| Lines/Circuits | | | | |
| 1 | Internet connectivity | | *** | | *** |
| 2 | Dedicated bandwidth for data migration only between Supplier and CoreLogic Data Centers (until completion of data center migration) | *** | | *** | |
| 3 | Dedicated bandwidth between Supplier Data Centers and CoreLogic offices and partners (such as MPLS and dedicated circuits). | | *** | | *** |
| 4 | Dedicated bandwidth between Supplier Data Centers. | | | *** | |
| Security Equipment | | | | |
| Hardware | | | | |
| 1 | CoreLogic owned and leased assets, including Upgrades and replacement parts | | *** | | *** |
| 2 | Supplier owned and leased assets including Upgrades, refreshes and replacement parts | | | *** | |
| 3 | Maintenance on CoreLogic owned assets | | *** | | *** |
| 4 | Maintenance on Supplier owned assets | | | *** | |
| 5 | Administrative procurement for CoreLogic owned assets | | *** | | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 228 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| | | CoreLogic Facilities | Supplier Facilities |
| 6 | Procurement assistance for CoreLogic owned assets | *** | | *** | |
| 7 | Administrative procurement for Supplier owned assets | *** | | *** | |
Software | | | | |
| 8 | System Software and maintenance, including Operating Systems for CoreLogic owned assets | | *** | | *** |
| 9 | System Software and maintenance, including Operating Systems for Supplier owned assets | | | *** | |
| Appliances(IDS and IPS) | | | | |
| 1 | Owned Equipment and leases | | *** | *** | |
| 2 | Existing Leases | | *** | *** | |
| 3 | Future Leases | | *** | *** | |
| 4 | Maintenance | | *** | *** | |
| 5 | Upgrades | | *** | *** | |
| 6 | Replacements | | *** | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 229 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Facilities
|
| | | | | |
| | | CoreLogic Facilities | Supplier Facilities |
| # | Details | Supplier | CoreLogic | Supplier | CoreLogic |
| Data Center Facilities | | | | |
| 1 | Environmental (e.g., HVAC, PDUs, fire suppression) | | *** | *** | |
| 2 | Space upgrades, additions, set-up | | *** | *** | |
| 3 | Furniture & fixtures | | *** | *** | |
| 4 | Wiring & cabling | | *** | *** | |
| 5 | Building depreciation/lease | | *** | *** | |
| 6 | Office Equipment | | *** | *** | |
| 7 | Building maintenance/security | | *** | *** | |
| 8 | Utilities | | *** | *** | |
| 9 | Other space Charges | | *** | *** | |
| 10 | Facilities management staff | | *** | *** | |
| Office Space | | | | |
| 1 | Environmental (e.g., HVAC, PDUs, fire suppression) | | *** | *** | |
| 2 | Space upgrades, additions, set-up | | *** | *** | |
| 3 | Furniture & fixtures | | *** | *** | |
| 4 | Wiring & cabling | | *** | *** | |
| 5 | Building depreciation/lease | | *** | *** | |
| 6 | Office Equipment | | *** | *** | |
| 7 | Building maintenance/security | | *** | *** | |
| 8 | Utilities | | *** | *** | |
| 9 | Other space Charges | | *** | *** | |
| Supplier Personnel CoreLogic Facilities During Data Center Migration (As outlined in Schedule A-7.1) | | | | |
| 1 | Long-distance phone calls | | *** | *** | *** |
| 2 | International phone calls | *** | | *** | *** |
| 3 | Local phone calls | | *** | *** | *** |
| 4 | Use of office space | | *** | *** | *** |
| 5 | Use of other office Equipment | | *** | *** | *** |
| 6 | Laptop/desktop/PDAs/tablets for rebadged Personnel until OT Go Live | | *** | *** | *** |
| 7 | Laptop/desktop/PDAs/tablets for rebadged Personnel after OT Go Live | *** | | *** | *** |
| 8 | Laptop/desktop/PDAs/tablets for non rebadged Supplier Personnel | *** | | *** | *** |
| Supplier Personnel at CoreLogic Facilities Following Data Center Migration (As outlined in Schedule A‑7.1) | | | | |
| 1 | Long-distance phone calls | | *** | *** | *** |
| 2 | International phone calls | *** | | *** | *** |
| 3 | Local phone calls | | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 230 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| 4 | Use of office space | | *** | *** | *** |
| 5 | Use of other office Equipment | | *** | *** | *** |
| 6 | Laptop/desktop/PDAs/tablets | *** | | *** | *** |
Personnel
|
| | | | |
| # | Details | CoreLogic | Supplier | Change Control |
| Transitioned Employees | | | |
| 1 | Salary & benefits | | *** | |
| 2 | Incentive pay/bonus | | *** | |
| 3 | Travel | | *** | |
| 4 | Training | | *** | |
| 5 | Relocation | | *** | |
| 6 | Staffing increase /decrease | | *** | |
| 7 | Severance1 | | *** | |
| 8 | Retention payments | | *** | |
| 9 | Payroll Taxes | | *** | |
| 10 | All other employee expenses not defined in Schedule A-5 | | *** | |
| Supplemental Supplier Personnel (Employees and Subcontractors) | | | |
| 1 | Salary & benefits | | *** | |
| 2 | Incentive pay/bonus | | *** | |
| 3 | Travel | | *** | |
| 4 | Training | | *** | |
| 5 | Relocation | | *** | |
| 6 | Staffing increase/decrease | | *** | |
| 7 | Severance1 | | *** | |
| 8 | Retention payments | | *** | |
| 9 | Payroll taxes | | *** | |
| 10 | All other employee expenses | | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 231 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
CoreLogic Services Agreements with third parties
|
| | | |
| # | Details | Supplier | CoreLogic |
| 1 | First American Financial Services Agreement | | *** |
| 2 | MMC Colocation Services Agreement | | *** |
Note:
| |
| 1 | First American Financial(FAF) TSA agreement - Contractual agreement between CoreLogic (CITG) and FAF to provide mainframe services to FA |
| |
| 2 | MMC Colocation contract - Contractual agreement between CoreLogic and MMC for subleasing Datacenter space to MMC |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 232 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Resource Type | Resource Location | Role Description | Years of Experience | Bill Rate (per FTE/Hr) for a project of LESS than 3 months of duration | Bill Rate (per FTE/Hr) for a project of GREATER than 3 months of duration |
| Help Desk Agent | Onsite | Service Desk Support - T1 | US 1-5 | $ *** | $ *** |
| Offshore | Service Desk Support - T1 | India 1-5 | $ *** | $ *** |
| Unix Midrange Engineer - Senior | Onsite | Systems Engineering - T3 | US 8+ | $ *** | $ *** |
| Offshore | Systems Engineering - T3 | Malaysia 8+ | $ *** | $ *** |
| Unix Midrange Engineer - Junior | Onsite | Systems Engineering - T1 | US 1-3 | $ *** | $ *** |
| Offshore | Systems Engineering - T1 | Malaysia 1-3 | $ *** | $ *** |
| Wintel Midrange Engineer - Senior | Onsite | Systems Engineering - T3 | US 8+ | $ *** | $ *** |
| Offshore | Systems Engineering - T3 | Malaysia 8+ | $ *** | $ *** |
| Wintel Midrange Engineer - Junior | Onsite | Systems Engineering - T1 | US 1-3 | $ *** | $ *** |
| Offshore | Systems Engineering - T1 | Malaysia 1-3 | $ *** | $ *** |
| SAN/Backup Storage Engineer - Senior | Onsite | Storage Services Open - T3 | US 8+ | $ *** | $ *** |
| Offshore | Storage Services Open - T3 | India 8+ | $ *** | $ *** |
| SAN/Backup Storage Engineer - Junior | Onsite | Storage Services Open - T1 | US 1-3 | $ *** | $ *** |
| Offshore | Storage Services Open - T1 | India 1-3 | $ *** | $ *** |
| Messaging Engineer - Senior | Onsite | Messaging Services - T3 | US 8+ | $ *** | $ *** |
| Offshore | Messaging Services - T3 | Malaysia 8+ | $ *** | $ *** |
| Messaging Engineer - Junior | Onsite | Messaging Services - T1 | US 1-3 | $ *** | $ *** |
| Offshore | Messaging Services - T1 | Malaysia 1-3 | $ *** | $ *** |
| Network (Data) Engineer - Senior | Onsite | Network Design - T3 | US 8+ | $ *** | $ *** |
| Offshore | Network Design - T3 | India 8+ | $ *** | $ *** |
| Network (Data) Engineer - Junior | Onsite | Network Design - T1 | US 1-3 | $ *** | $ *** |
| Offshore | Network Design - T1 | India 1-3 | $ *** | $ *** |
| Network (Voice) Engineer - Senior | Onsite | Network Convergence - T3 | US 8+ | $ *** | $ *** |
| Offshore | Network Design - T3 | India 8+ | $ *** | $ *** |
| Network (Voice) Engineer - Junior | Onsite | Network Convergence - T1 | US 1-3 | $ *** | $ *** |
| Offshore | Network Convergence - T1 | India 1-3 | $ *** | $ *** |
| EUC Technician - Senior | Onsite | Client Technical Support - T3 | US 8+ | $ *** | $ *** |
| Offshore | Client Technical Support - T3 | India 8+ | $ *** | $ *** |
| EUC Technician - Junior | Onsite | Client Technical Support - T1 | US 1-3 | $ *** | $ *** |
| Offshore | Client Technical Support - T1 | India 1-3 | $ *** | $ *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 233 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Resource Type | Resource Location | Role Description | Years of Experience | Bill Rate (per FTE/Hr) for a project of LESS than 3 months of duration | Bill Rate (per FTE/Hr) for a project of GREATER than 3 months of duration |
| Project Manager - Senior | Onsite | Project Services - T3 | US 5+ | $ *** | $ *** |
| Offshore | Project Services - T3 | India 5+ | $ *** | $ *** |
| Nearshore | Project Services - T3 | Mexico 5+ | $ *** | $ *** |
| Project Manager - Junior | Onsite | Project Services - T1 | US 2-5 | $ *** | $ *** |
| Offshore | Project Services - T1 | India 2-5 | $ *** | $ *** |
| Nearshore | Project Services - T1 | Mexico 2-5 | $ *** | $ *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 234 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-4.8
TERMINATION CHARGES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed without the prior written permission of the Parties. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 235 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-4.8
Termination Charges
1.INTRODUCTION
1.1 Agreement. This Schedule A-4.8 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”).
1.2 References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided.
1.3 Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or Schedule A-1 to Supplement A.
2. SCHEDULES.
The following documents are attached to and incorporated by reference in this Schedule:
| |
| Schedule A-4.8.1 | General Termination Charge Table |
| |
| Schedule A-4.8.2 | Unconditional Termination Charge Table |
| |
Schedule A-4.8.3 | Wind Down Costs Termination Charge Provisions |
3. TERMINATION CHARGES
3.1 General. This Schedule sets forth the Termination Charges due under Supplement A and methodology to be used by the Parties to calculate the Termination Charges. Termination Charges shall consist of (a) the General Termination Charge as described in Section 4, (b) the Unconditional Termination Charge as described in Section 4, and (c) if applicable, the Wind Down Costs Termination Charge as described in Schedule A-4.8.3. Except as provided in this Schedule, there are no Termination Charges payable upon a termination or expiration of the Services.
3.2 Methodology. If CoreLogic is required to pay a Termination Charge under the MSA, such Termination Charge shall be calculated for the portion of the Services that are Affected Services. The Termination Charge shall equal the applicable percentage specified in the Termination Charge Percentages Table in Schedule 13 to the MSA (the “Termination Charge Percentage”) multiplied by each of the following:
| |
| (a) | the applicable amount specified in the General Termination Charge Table in Schedule A-4.8.1 for the Affected Services determined in accordance with Section 4.2 (the “General Termination Charge”); |
| |
| (b) | the applicable amount specified in the Unconditional Termination Charge Table in Schedule A-4.8.2 for the Affected Services determined in accordance with Section 4.3 (the “Unconditional Termination Charge”); and |
| |
| (c) | the calculated Termination Charge for the Affected Services determined in accordance with Schedule A-4.8.3 (the “Wind Down Costs Termination Charge”); and |
| |
| 4. | CALCULATION AND PAYMENT OF TERMINATION CHARGES. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 236 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 4.1 | General. The General Termination Charge and Unconditional Termination Charge shall be calculated and invoiced in accordance with this Section. Wind Down Costs Termination Charge shall be calculated and invoiced as and when specified in Schedule A-4.8.3. |
| |
| 4.2 | Calculation of General Termination Charge. The General Termination Charge shall include the amount set forth in Schedule A-4.8.1 for the last month in which the Affected Services at issue are performed (including any such Services performed as Disengagement Services for Resource Unit-Based Charges) (“Termination Effective Date”),calculated as per the following formula when the Termination Effective Date is after 2012: |
| |
| (a) | General Termination Charge in the year following the Termination *** Date as defined *** plus ((General Termination Charge in the current year minus General Termination Charge in the year following the Termination *** Date), divided by 12, multiplied by the number of months remaining in the current calendar year (e.g., August would be 4)). |
| |
| 4.3 | Calculation of Unconditional Termination Charge. The Unconditional Termination Charge shall include the amount set forth in Schedule A-4.8.2 for the month of the applicable Termination Effective Date calculated per the following formula when the Termination Effective Date is after 2012: |
Unconditional Termination Charge in the year following the Termination *** Date as defined below plus ((Unconditional Termination Charge in the current year minus Unconditional Termination Charge in the year following the Termination *** Date), divided by 12, multiplied by the number of months remaining in the current calendar year (e.g., August would be 4))
| |
| 4.4 | Calculation of Wind Down Costs Termination Charge. The Wind Down Costs Termination Charge shall be calculated as of the dates specified in Schedule A-4.8.3. |
| |
| 4.5 | Partial Termination. If the Affected Services include less than all of the Services (a) the General Termination Charge shall include a portion of the applicable amount set forth in Schedule A-4.8.1 proportional to the Charges eliminated as a result of the termination, as determined as of the month prior to the month in which the notice of termination is provided (the “Termination *** Date”); (b) the Unconditional Termination Charge shall include a portion of the applicable amount set forth in Schedule A-4.8.2 proportional to the Charges eliminated as a result of the termination, as determined as of the month prior to the Termination *** Date, and (c) the Wind Down Costs Termination Charge shall be calculated based upon the Affected Services as described in Schedule A-4.8.3. |
| |
| 4.6 | Invoicing. Supplier shall invoice CoreLogic for the General Termination Charge and Unconditional Termination Charge within *** (***) *** after the effective date of termination of the Affected Services. Supplier shall invoice CoreLogic for the Wind Down Costs Termination Charge as provided in Schedule A-4.8.3. Any such invoice shall be due and payable in accordance with Section 12.2 of the MSA. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 237 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-4.8.1
General Termination Charge Table
|
| | | | | | | | |
| Category of Services | Jan-13 | Jan-14 | Jan-15 | Jan-16 | Jan-17 | Jan-18 | Jan-19 | Jan-20 |
| Termination Fees | | | | | | | | |
| Network | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** |
| Desktop Support and Engineering | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** |
| Employee Service Desk | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** |
| Mainframe | $ - | $ *** | $ *** | $ - | $ - | $ - | $ - | $ - |
| Midrange and Server | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** |
| Project Management | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** |
| Storage | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** |
| Media Center Services | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 238 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-4.8.2
Unconditional Termination Charge Table
|
| | | | | | | | | |
| Category of Services | Aug-12 | Jan-13 | Jan-14 | Jan-15 | Jan-16 | Jan-17 | Jan-18 | Jan-19 | Jan-20 |
| Unconditional Termination Fees | $ *** | $ *** | $ *** | $ *** | $ *** | $ *** | $ - | $ - | $ - |
Schedule A-4.8.3
Wind Down Costs Termination Charge Provisions
1. General.
“Eligible Equipment” shall mean (a) *** and *** Equipment and (b) *** Equipment.
“Eligible Materials” shall mean (a) *** Software and (b) *** Software.
“Wind-Down Costs” or “Wind Down Costs Termination Charge” shall mean the following actual direct costs as described in this Schedule A-4.8.3 with respect to the Eligible Equipment and the Eligible Materials only, and subject to any limitations herein, that are reasonably incurred by Supplier, Supplier Subcontractors or Supplier Affiliates (each, a “Supplier Party”) as a direct result of the early termination of Affected Services.
| |
| 1.2 | Invoicing and Audit. Within *** (***) *** after the Termination *** Date, Supplier shall prepare and deliver to CoreLogic an itemized calculation of Supplier’s good faith estimate of the Wind Down Costs Termination Charge for the Affected Services as of the Termination Date. Supplier shall provide sufficient supporting documentation to allow CoreLogic to validate such calculation. CoreLogic shall be entitled to audit Supplier’s actual Wind Down Costs Termination Charge and supporting documentation in accordance with Section 9.10(c) of the MSA. Supplier shall invoice CoreLogic for amounts payable under this Schedule as they are incurred by a Supplier Party and such invoice shall be due and payable in accordance with Section 12.2 of the MSA. |
| |
| 2. | Supplier Mitigation. Supplier Parties shall use commercially reasonable efforts to avoid incurring any Wind Down Costs and to minimize the costs incurred including, for *** (***) *** after the Termination *** Date, seeking to recover amounts previously paid to a third party where appropriate. |
| |
| 2.1 | General. The commercially reasonable efforts to be employed by a Supplier Party shall include, to the extent applicable: |
| |
| (a) | providing CoreLogic with a list of all Eligible Equipment and Eligible Materials used exclusively to provide the Affected Services and the costs associated with each within *** (***) *** after the Termination *** Date; |
| |
| (b) | working with CoreLogic to identify commercially reasonable means to avoid or minimize such costs, including using commercially reasonable efforts to avoid agreeing in any applicable Third-Party Software licenses, Equipment leases or other Third Party Contracts for the Eligible Equipment and the Eligible Materials to termination or cancellation fees or non-cancelable Charges; |
| |
| (c) | offering to make such Eligible Equipment, Eligible Materials and any such leases, licenses and other Third Party Contracts available to CoreLogic; |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 239 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (d) | for *** (***) *** after the applicable Termination *** Date, redeploying the remainder of any such Eligible Equipment or Eligible Materials within Supplier’s organization if, and as soon as, commercially reasonable; |
| |
| (e) | for *** (***) *** after the applicable Termination *** Date, negotiating with any applicable third party to eliminate or reduce the fees or charges to be incurred; and |
| |
| (f) | subject to any limitations contained in the applicable lease, licenses or other Third Party Contracts and for *** (***) *** after the applicable Termination Effective Date, selling, canceling or otherwise disposing of any such Eligible Equipment and Eligible Materials and any such leases, licenses and other Third Party Contracts that cannot be redeployed. |
| |
| 2.2 | Exception for Assets Purchased by CoreLogic. Notwithstanding the foregoing, Wind Down Costs Termination Charge shall not include any amounts paid to Supplier with respect to Eligible Equipment and Eligible Materials to the extent CoreLogic elects to purchase such Eligible Equipment or Eligible Materials pursuant to Section 20.8(b) of the MSA. |
| |
| 3. | Eligible Equipment. The Wind Down Costs Termination Charge shall include the following for Eligible Equipment that Supplier is unable to *** or otherwise *** pursuant to Section 2 of this Schedule. |
| |
| 3.1 | Leased Eligible Equipment. With respect to such Eligible Equipment that is leased by Supplier, the Wind Down Costs Termination Charge shall consist of: |
| |
| (a) | any *** or *** charges (or similar amounts) that Supplier is contractually required to pay to *** in connection with the *** of such lease, |
| |
| (b) | subject to clause (c), any *** charges that Supplier is contractually required to pay to *** *** during the *** of such lease; and |
| |
| (c) | any *** or *** payments previously paid by Supplier under Eligible Equipment leases which are not *** (on the basis regularly and consistently used by Supplier for such items) as of the date that such Eligible Equipment leases are no longer used in the provision of Services. |
| |
| 3.2 | Supplier Owned Eligible Equipment. With respect to such Eligible Equipment that is owned by Supplier, the Wind Down Costs Termination Charge shall consist of the *** of such Eligible Equipment as of the Termination Effective Date (calculated using a *** over a period *** to the applicable ***), whereupon title to such Eligible Equipment shall be transferred to CoreLogic pursuant to Section 20.8(b) of the MSA. |
| |
| 4. | Eligible Materials. The Wind Down Costs Termination Charge shall include the following for any Eligible Materials or Third Party Contract that requires a Supplier Party to pay termination or cancellation charges: |
| |
| (a) | any *** or *** charges (or similar amounts) that a Supplier Party is contractually required to pay to *** in connection with the *** of such lease, license or other contract; |
| |
| (b) | subject to clause (c), any *** charges that a Supplier Party is contractually required to pay to *** during the *** of such lease, license or other contract; and |
| |
| (c) | any ***, *** or *** or *** payments previously paid by a Supplier Party under the Third Party Contract which are not *** (on the basis regularly and consistently used by a Supplier Party for such items) as of the date that the same are no longer used in the provision of Services. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 240 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING, L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-4.9
INVOICING PROVISIONS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 241 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-4.9
Invoicing Provisions
| |
| 1.1 | Agreement. This Schedule A-4.9 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement. |
| |
| 1.4 | Schedules. The following documents are attached to and incorporated by reference in this Schedule: |
Schedule A-4.9.1 Form of Invoice
Schedule A-4.9.2 Form of Chargeback
| |
| 2.1 | General. Invoices shall be provided in accordance with Section 12.1 of the MSA. |
| |
| 2.2 | Detail. Without limiting any requirements set forth in Section 12 of the MSA, each invoice shall separately identify, to the extent applicable for the period covered by the invoice, and for each Resource Unit Category, fees and adjustments to fees with respect to the following: |
| |
| (a) | Fixed Fees for such month; |
| |
| (b) | Resource Unit-Based Charges for such month; |
| |
| (i) | Monthly Baseline Charges; |
| |
| (c) | Charges for New Services; |
| |
| (e) | Charges for Transition Services; |
| |
| (g) | Charges for Transformation Services |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 242 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (h) | Charges for Disengagement Services; |
| |
| (j) | Credits due to Customer; |
| |
| (k) | Pass-Through Expenses and incidental expenses; and |
| |
| (l) | Time and materials charges by assignment; |
| |
| 3.1 | General. *** shall provide a chargeback report along with each invoice to provide *** to *** the invoice and chargeback to business units. |
| |
| 3.2 | Chargeback Reports. Supplier acknowledges that CoreLogic intends to use *** that all business units are accountable for their respective use of the Services. Accordingly, *** shall provide chargeback reports to *** as shown in Schedule A-4.9.2 (Form of Chargeback). The information should be provided in a readable electronic form with *** for ***. |
| |
| 3.3 | Changes to Chargeback Reports. *** shall adjust the business units included in the monthly chargeback report to stay current with the CoreLogic environment. Updates will be made based on acquisitions, divestitures, and changes in CoreLogic business units. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 243 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING, L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-4.9.1
FORM OF INVOICE
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 244 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
1. INTRODUCTION
1.1 Agreement. This Schedule A-4.9.1 (this “Schedule”) is attached to and incorporated by reference in
Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19,
2012 (the “MSA”).
1.2 References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided.
1.3 Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement.
Invoice Summaries and volume information need to be broken down into the following 19 categories
|
| |
| BU | BU Company Code |
| Data & Analytics | Core Logic info Solutions |
| Data & Analytics | Multifamily Services (multiple company codes) |
| Data & Analytics | RP Data |
| Data & Analytics | MarketLinx (MLS) |
| Data & Analytics | Teletrack |
| Data & Analytics | Data & Analytics |
| Mortgage Origination Services | Tax |
| Mortgage Origination Services | Lender Services (CredCo) |
| Mortgage Origination Services | Flood (includes Spatial) |
| Mortgage Origination Services | Dorado Network Systems |
| Mortgage Origination Services | BIS Holding with NJV (multiple company codes) |
| Mortgage Origination Services | Mortgage Origination Services |
| Default Services | Field Services |
| Default Services | Default Services |
| Default Services | Residential Value View (BPO) |
| Default Services | RealtyBid |
| Default Services | Default Services |
| Corporate | ETS Retained Org |
| Corporate | Corp Shared Services |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 245 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| | | Supplier Name: | |
| | | Supplier Address: | |
| | | | |
| | | | |
| | | Supplier Tax ID: | |
| | Form of Invoice | | |
| | | | |
| Customer ID: | TBD | Client Contact: | |
| Customer Name: | CoreLogic Solutions, LLC | Client Contact Phone: | |
| Business Unit | All Business Units | Supplier Contact: | |
| Contract: | TBD | Supplier Contact Phone: | |
| Billing period from: | 7th Jan 2013 | | |
| Billing period To: | 31st Jan 2013 | | |
| PO NO: | TBD | | |
| SOW No: | CoreLogic Schedule A | | |
| SOW Date: | 16th July 2012 | | |
| Invoice Descr: | DC Services | | |
| | | | |
| Type of Charge | Tower | Associated SOW | Amount |
| *** | Account and Service Management | | — |
|
| *** | DR | | — |
|
| *** | Project Management | | — |
|
| *** | Telecom Expense Management | | — |
|
| *** | Employee Service Desk | | — |
|
| *** | Desktop Support and Engineering | | — |
|
| *** | Mainframe | | — |
|
| *** | Midrange and Server | | — |
|
| *** | Storage | | — |
|
| *** | Backup | | — |
|
| *** | Security | | — |
|
| *** | Network | | — |
|
| *** | Media Center Services | | — |
|
| *** | Various | | X,XXX,XXX.XX |
| | | | X,XXX,XXX.XX |
| | | | |
| | | | |
| Remarks: | | | |
| | | | |
| PAYABLE | | | |
| | | | |
| By Check Mailing Address | | By Wire Transfer | |
| | | Bank Name: | |
| | | Routing Number: | |
| | | Account Name: | |
| | | Account Number: | |
| | | Swift Code: | |
| | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 246 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| | | Supplier Name: | |
| | | Supplier Address: | |
| | | | |
| | | | |
| | | Supplier Tax ID: | |
| | Form of Invoice | | |
| | | | |
| Customer ID: | TBD | Client Contact: | |
| Customer Name: | CoreLogic Solutions, LLC | Client Contact Phone: | |
| Business Unit | Mortgage Origination Services | Supplier Contact: | |
| Contract: | TBD | Supplier Contact Phone: | |
| Billing period from: | 7th Jan 2013 | | |
| Billing period To: | 31st Jan 2013 | | |
| PO NO: | TBD | | |
| SOW No: | CoreLogic Schedule A | | |
| SOW Date: | 16th July 2012 | | |
| Invoice Descr: | DC Services | | |
| | | | |
| Type of Charge | Tower | Associated SOW | Amount |
| *** | Account and Service Management | | — |
|
| *** | DR | | — |
|
| *** | Project Management | | — |
|
| *** | Telecom Expense Management | | — |
|
| *** | Employee Service Desk | | — |
|
| *** | Desktop Support and Engineering | | — |
|
| *** | Mainframe | | — |
|
| *** | Midrange and Server | | — |
|
| *** | Storage | | — |
|
| *** | Backup | | — |
|
| *** | Security | | — |
|
| *** | Network | | — |
|
| *** | Media Center Services | | — |
|
| *** | Various | | X,XXX,XXX.XX |
| | | | X,XXX,XXX.XX |
| | | | |
| | | | |
| Remarks: | | | |
| | | | |
| PAYABLE | | | |
| | | | |
| By Check Mailing Address | | By Wire Transfer | |
| | | Bank Name: | |
| | | Routing Number: | |
| | | Account Name: | |
| | | Account Number: | |
| | | Swift Code: | |
| | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 247 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| | | Supplier Name: | |
| | | Supplier Address: | |
| | | | |
| | | | |
| | | Supplier Tax ID: | |
| | Form of Invoice | | |
| | | | |
| Customer ID: | TBD | Client Contact: | |
| Customer Name: | CoreLogic Solutions, LLC | Client Contact Phone: | |
| Business Unit | Data and Analytics | Supplier Contact: | |
| Contract: | TBD | Supplier Contact Phone: | |
| Billing period from: | 7th Jan 2013 | | |
| Billing period To: | 31st Jan 2013 | | |
| PO NO: | TBD | | |
| SOW No: | CoreLogic Schedule A | | |
| SOW Date: | 16th July 2012 | | |
| Invoice Descr: | DC Services | | |
| | | | |
| Type of Charge | Tower | Associated SOW | Amount |
| *** | Account and Service Management | | — |
|
| *** | DR | | — |
|
| *** | Project Management | | — |
|
| *** | Telecom Expense Management | | — |
|
| *** | Employee Service Desk | | — |
|
| *** | Desktop Support and Engineering | | — |
|
| *** | Mainframe | | — |
|
| *** | Midrange and Server | | — |
|
| *** | Storage | | — |
|
| *** | Backup | | — |
|
| *** | Security | | — |
|
| *** | Network | | — |
|
| *** | Media Center Services | | — |
|
| *** | Various | | X,XXX,XXX.XX |
| | | | X,XXX,XXX.XX |
| | | | |
| | | | |
| Remarks: | | | |
| | | | |
| PAYABLE | | | |
| | | | |
| By Check Mailing Address | | By Wire Transfer | |
| | | Bank Name: | |
| | | Routing Number: | |
| | | Account Name: | |
| | | Account Number: | |
| | | Swift Code: | |
| | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 248 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| | | Supplier Name: | |
| | | Supplier Address: | |
| | | | |
| | | | |
| | | Supplier Tax ID: | |
| | Form of Invoice | | |
| | | | |
| Customer ID: | TBD | Client Contact: | |
| Customer Name: | CoreLogic Solutions, LLC | Client Contact Phone: | |
| Business Unit | Default Services | Supplier Contact: | |
| Contract: | TBD | Supplier Contact Phone: | |
| Billing period from: | 7th Jan 2013 | | |
| Billing period To: | 31st Jan 2013 | | |
| PO NO: | TBD | | |
| SOW No: | CoreLogic Schedule A | | |
| SOW Date: | 16th July 2012 | | |
| Invoice Descr: | DC Services | | |
| | | | |
| Type of Charge | Tower | Associated SOW | Amount |
| *** | Account and Service Management | | — |
|
| *** | DR | | — |
|
| *** | Project Management | | — |
|
| *** | Telecom Expense Management | | — |
|
| *** | Employee Service Desk | | — |
|
| *** | Desktop Support and Engineering | | — |
|
| *** | Mainframe | | — |
|
| *** | Midrange and Server | | — |
|
| *** | Storage | | — |
|
| *** | Backup | | — |
|
| *** | Security | | — |
|
| *** | Network | | — |
|
| *** | Media Center Services | | — |
|
| *** | Various | | X,XXX,XXX.XX |
| | | | X,XXX,XXX.XX |
| | | | |
| | | | |
| Remarks: | | | |
| | | | |
| PAYABLE | | | |
| | | | |
| By Check Mailing Address | | By Wire Transfer | |
| | | Bank Name: | |
| | | Routing Number: | |
| | | Account Name: | |
| | | Account Number: | |
| | | Swift Code: | |
| | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 249 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| | | Supplier Name: | |
| | | Supplier Address: | |
| | | | |
| | | | |
| | | Supplier Tax ID: | |
| | Form of Invoice | | |
| | | | |
| Customer ID: | TBD | Client Contact: | |
| Customer Name: | CoreLogic Solutions, LLC | Client Contact Phone: | |
| Business Unit | Corporate | Supplier Contact: | |
| Contract: | TBD | Supplier Contact Phone: | |
| Billing period from: | 7th Jan 2013 | | |
| Billing period To: | 31st Jan 2013 | | |
| PO NO: | TBD | | |
| SOW No: | CoreLogic Schedule A | | |
| SOW Date: | 16th July 2012 | | |
| Invoice Descr: | DC Services | | |
| | | | |
| Type of Charge | Tower | Associated SOW | Amount |
| *** | Account and Service Management | | — |
|
| *** | DR | | — |
|
| *** | Project Management | | — |
|
| *** | Telecom Expense Management | | — |
|
| *** | Employee Service Desk | | — |
|
| *** | Desktop Support and Engineering | | — |
|
| *** | Mainframe | | — |
|
| *** | Midrange and Server | | — |
|
| *** | Storage | | — |
|
| *** | Backup | | — |
|
| *** | Security | | — |
|
| *** | Network | | — |
|
| *** | Media Center Services | | — |
|
| *** | Various | | X,XXX,XXX.XX |
| | | | X,XXX,XXX.XX |
| | | | |
| | | | |
| Remarks: | | | |
| | | | |
| PAYABLE | | | |
| | | | |
| By Check Mailing Address | | By Wire Transfer | |
| | | Bank Name: | |
| | | Routing Number: | |
| | | Account Name: | |
| | | Account Number: | |
| | | Swift Code: | |
| | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 250 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
ARC & RRC Summary
Jan-13 |
| | | | | | | |
| Description | Unit of Measure | Baseline Volume | Actual Volumes | Delta | | ARC / RRC Rate | Monthly ARC / RRC |
| Network | | | | | | | |
| Network Switch/Router | Devices Per Month | X | | X | | X | X |
| Physical Firewall - Clustered | Devices Per Month | X | | X | | X | X |
| Physical Firewall - Standalone | Devices Per Month | X | | X | | X | X |
| Virtual Firewall - Clustered | Devices Per Month | X | | X | | X | X |
| Virtual Firewall - Standalone | Devices Per Month | X | | X | | X | X |
| Security Appliances | Devices Per Month | X | | X | | X | X |
| Wireless Access Points | Devices Per Month | X | | X | | X | X |
| Load Balancer - Clustered | Devices Per Month | X | | X | | X | X |
| Load Balancer - Standalone | Devices Per Month | X | | X | | X | X |
| Misc. Network Device | Devices Per Month | X | | X | | X | X |
| VoIP Phones | Phone devices Per Month | X | | X | | X | X |
| Network IMADS | IMADs Per Month | X | | X | | X | X |
| End User Support | | | | | | | |
| EUC (Desktops / Laptops) | Devices Per Month | X | | X | | X | X |
| Desktop IMACDS - Campus | Per Month | X | | X | | X | X |
| Desktop IMACDS - Remote | Per Month | X | | X | | X | X |
| Network Printer | Devices Per Month | X | | X | | X | X |
| Exchange Email Account | Accounts Per Month | X | | X | | X | X |
| Mobile Device | Devices Per Month | X | | X | | X | X |
| Desktop Applications Package | Applications Packaged Per Month | X | | X | | X | X |
| Desktop Image Management | Images Per Month | X | | X | | X | X |
| Employee Service Desk | | | | | | | |
| Service Desk Tickets | Tickets per month | X | | X | | X | X |
| Mainframe | | | | | | | |
| Mainframe Service | Installed Mainframe Service per month | X | | X | | X | X |
| Mainframe DASD | Installed Mainframe DASD TB Per Month | X | | X | | X | X |
| Mainframe Tapes | Mainframe Tapes per Month | X | | X | | X | X |
| Midrange and Server | | | | | | | |
| Hardware | | | | | | | |
| Physical Server Small | Servers Per Month | X | | X | | X | X |
| Physical Server Medium | Servers Per Month | X | | X | | X | X |
| Physical Server Large | Servers Per Month | X | | X | | X | X |
| Physical Server Extra Large | Servers Per Month | X | | X | | X | X |
| Cloud Server Small | Servers Per Month | X | | X | | X | X |
| Cloud Server Medium | Servers Per Month | X | | X | | X | X |
| Cloud Server Large | Servers Per Month | X | | X | | X | X |
| Services | | | | | | | |
| Linux OS Low | OS Instances Per Month | X | | X | | X | X |
| Linux OS Standard | a | X | | X | | X | X |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 251 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| Description | Unit of Measure | Baseline Volume | Actual Volumes | Delta | | ARC / RRC Rate | Monthly ARC / RRC |
| Linux OS High | OS Instances Per Month | X | | X | | X | X |
| | | | | | | | |
| Windows OS Low | OS Instances Per Month | X | | X | | X | X |
| Windows OS Standard | OS Instances Per Month | X | | X | | X | X |
| Windows OS High | OS Instances Per Month | X | | X | | X | X |
| | | | | | | | |
| UNIX Low OS Instance | OS Instances Per Month | X | | X | | X | X |
| UNIX Medium OS Instance | OS Instances Per Month | X | | X | | X | X |
| UNIX High OS Instance | OS Instances Per Month | X | | X | | X | X |
| | | | | | | | |
| i-Series | OS Instances Per Month | X | | X | | X | X |
| ESX/Xen Host | Servers Per Month | X | | X | | X | X |
| Storage and Backup Services | | | | | | | |
| Services Only | | | | | | | |
| Storage Management | Allocated TB per month | X | | X | | X | X |
| Backup Management | GBs Per Month | X | | X | | X | X |
| Services and Hardware | | | | | | | |
| Tier 1 Storage | Allocated TB per month | X | | X | | X | X |
| Tier 2 Storage | Allocated TB per month | X | | X | | X | X |
| Tier 3 Storage | Allocated TB per month | X | | X | | X | X |
| Backup Management | GBs Per Month | X | | X | | X | X |
| Cross Functional Services | | | | | | | |
| Service Management Resolver Licenses | Licenses Per Month | X | | X | | X | X |
| Electronic Data Exchange (EDE) | FTE Per Month | X | | X | | X | X |
| Security Administration Services | | | | | | | |
| User Security Administration | Touches per Month | X | | X | | X | X |
| End Point Log Retention & Monitoring | Devices Logging Per Month | X | | X | | X | X |
| Firewall Rule Changes | Changes Per Month | X | | X | | X | X |
| | | | | | | | |
| Total Monthly ARC or (RRC) | | | | | | | XXXX |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 252 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Network
Detail to include each chargeable unit with detail sufficient for CoreLogic sign-off
Service Desk
Detail to include each chargable unit with detail sufficient for CoreLogic sign-off
End User Device Support and Messaging
Detail to include each chargable unit with detail sufficient for CoreLogic sign-off
Data Center, Mainframe, Production Control & Monitoring
Detail to include each chargable unit with detail sufficient for CoreLogic sign-off
Server
Detail to include each chargable unit with detail sufficient for CoreLogic sign-off
Storage
Detail to include each chargable unit with detail sufficient for CoreLogic sign-off
Storage Backup
Detail to include each chargable unit with detail sufficient for CoreLogic sign-off
Security
Detail to include each chargeable unit with detail sufficient for CoreLogic sign-off
Cross Functional and Media Center
Detail to include each chargable unit with detail sufficient for CoreLogic sign-off
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 253 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING, L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-4.9.2
FORM OF CHARGEBACK
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 254 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
1. INTRODUCTION
1.1 Agreement. This Schedule A-4.9.2 (this “Schedule”) is attached to and incorporated by reference in
Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19,
2012 (the “MSA”).
1.2 References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided.
1.3 Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement.
Volume and Invoice detail need to be broken down into the following 19 Business Units for chargeback purposesr
|
| | |
| BU | BU Company | 3 Digit Identifier |
| Data & Analytics | Core Logic info Solutions | TBD |
| Data & Analytics | Multifamily Services (multiple company codes) | TBD |
| Data & Analytics | RP Data | TBD |
| Data & Analytics | MarketLinx (MLS) | TBD |
| Data & Analytics | Teletrack | TBD |
| Data & Analytics | Data & Analytics | TBD |
| Mortgage Origination Services | Tax | TBD |
| Mortgage Origination Services | Lender Services (CredCo) | TBD |
| Mortgage Origination Services | Flood (includes Spatial) | TBD |
| Mortgage Origination Services | Dorado Network Systems | TBD |
| Mortgage Origination Services | BIS Holding with NJV (multiple company codes) | TBD |
| Mortgage Origination Services | Mortgage Origination Services | TBD |
| Default Services | Field Services | TBD |
| Default Services | Residential Value View (BPO) | TBD |
| Default Services | RealtyBid | TBD |
| Default Services | Default Services | TBD |
| Corporate | ETS Retained Org | TBD |
| Corporate | Corp Shared Services | TBD |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 255 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Month of January 2013
Volume and Invoice detail need to be broken down into the following 19 Business Units for chargeback purposes
|
| | | | | |
| | | | | Month of January 2013 |
| Description | Dell Expense Type | Chargeback Metric | | CL Price (MSC + ARC/RRC) | Total CL Volumes |
| Account and Service Management | *** | # Headcount | | XXXX | XXXX |
| DR | *** | # Headcount | | XXXX | XXXX |
| Project Management | *** | # Headcount | | XXXX | XXXX |
| Telecom Expense Management | *** | # Headcount | | XXXX | XXXX |
| | | | | | |
| Service Desk | | | | | |
| Support Center | *** | # Headcount | | XXXX | XXXX |
| | | | | | |
| End User Computing | | | | | |
| EUC (Desktops / Laptops) | *** | # of Devices | | XXXX | XXXX |
| Desktop IMACDS - Campus | *** | # of Desktop IMACDs | | XXXX | XXXX |
| Desktop IMACDS - Remote | *** | # of Desktop IMACDs | | XXXX | XXXX |
| Network Printer | *** | # of Printers | | XXXX | XXXX |
| Exchange Email Account | *** | # Headcount | | XXXX | XXXX |
| Mobile Device | *** | # Headcount | | XXXX | XXXX |
| Desktop Applications Package | *** | # Headcount | | XXXX | XXXX |
| Desktop Image Management | *** | # Headcount | | XXXX | XXXX |
| | | | | | |
| Mainframe | | | | | |
| Mainframe Service | *** | # MIPS | | XXXX | XXXX |
| Mainframe Tapes | *** | # TAPES | | XXXX | XXXX |
| | | | | | |
| Midrange and Server - Hardware | | | | | |
| Physical Server Small | *** | # of Servers | | XXXX | XXXX |
| Physical Server Medium | *** | # of Servers | | XXXX | XXXX |
| Physical Server Large | *** | # of Servers | | XXXX | XXXX |
| Physical Server Extra Large | *** | # of Servers | | XXXX | XXXX |
| Cloud Server Small | *** | # of Servers | | XXXX | XXXX |
| Cloud Server Medium | *** | # of Servers | | XXXX | XXXX |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 256 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| | | | | Month of January 2013 |
| Description | Dell Expense Type | Chargeback Metric | | CL Price (MSC + ARC/RRC) | Total CL Volumes |
| Cloud Server Large | *** | # of Servers | | XXXX | XXXX |
| Midrange and Server - Software | | | | | |
| Linux OS Low | *** | # OS Instances | | XXXX | XXXX |
| Linux OS Standard | *** | # OS Instances | | XXXX | XXXX |
| Linux OS High | *** | # OS Instances | | XXXX | XXXX |
| Windows OS Low | *** | # OS Instances | | XXXX | XXXX |
| Windows OS Standard | *** | # OS Instances | | XXXX | XXXX |
| Windows OS High | *** | # OS Instances | | XXXX | XXXX |
| UNIX Low OS Instance | *** | # OS Instances | | XXXX | XXXX |
| UNIX Medium OS Instance | *** | # OS Instances | | XXXX | XXXX |
| UNIX High OS Instance | *** | # OS Instances | | XXXX | XXXX |
| i-Series | *** | # OS Instances | | XXXX | XXXX |
| ESX/Xen Host | *** | # of Servers | | XXXX | XXXX |
| | | | | | |
| Storage and Backup Services | | | | | |
| Storage Management | *** | # Terabytes | | XXXX | XXXX |
| Backup Management (Svcs Only) | *** | # Gigabytes | | XXXX | XXXX |
| Backup Management (Svcs & Hardware) | *** | # Gigabytes | | XXXX | XXXX |
| Storage - Tier 1 | *** | # Terabytes | | XXXX | XXXX |
| Storage - Tier 2 | *** | # Terabytes | | XXXX | XXXX |
| Storage - Tier 3 | *** | # Terabytes | | XXXX | XXXX |
| | | | | | |
| Network | | | | | |
| Network Switch/Router | *** | # Devices | | XXXX | XXXX |
| Physical Firewall - Clustered | *** | # Devices | | XXXX | XXXX |
| Physical Firewall - Standalone | *** | # Devices | | XXXX | XXXX |
| Virtual Firewall - Clustered | *** | # Devices | | XXXX | XXXX |
| Virtual Firewall - Standalone | *** | # Devices | | XXXX | XXXX |
| Security Appliances | *** | # Devices | | XXXX | XXXX |
| Wireless Access Points | *** | # Devices | | XXXX | XXXX |
| Load Balancer - Clustered | *** | # Devices | | XXXX | XXXX |
| Load Balancer - Standalone | *** | # Devices | | XXXX | XXXX |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 257 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| | | | | Month of January 2013 |
| Description | Dell Expense Type | Chargeback Metric | | CL Price (MSC + ARC/RRC) | Total CL Volumes |
| Misc. Network Device | *** | # Devices | | XXXX | XXXX |
| VoIP Phones | *** | Devices | | XXXX | XXXX |
| Network IMADS | *** | # of IMADs | | XXXX | XXXX |
| | | | | | |
| Cross Functional Services | | | | | |
| Service Management Resolver Licenses | *** | # Headcount | | XXXX | XXXX |
| Electronic Data Exchange (EDE) | *** | # Headcount | | XXXX | XXXX |
| | | | | | |
| Security Administration Services | | | | | |
| User Security Administration | *** | # Headcount | | XXXX | XXXX |
| End Point Log Retention & Monitoring | *** | # Headcount | | XXXX | XXXX |
| Firewall Rule Changes | *** | # Changes | | XXXX | XXXX |
| | | | | | |
| Total | | | | XXXX | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 258 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | |
| | | | | Metric Count |
| Description | Dell Expense Type | Chargeback Metric | | Data and Analytics | Core Logic info Solutions | Multifamily Services (multiple company codes) | RP Data | MarketLinx (MLS) | Teletrack | Tax | Lender Services (CredCo) | Flood (includes Spatial) | Dorado Network Systems |
| Account and Service Management | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| DR | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Project Management | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Telecom Expense Management | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| | | | | XXXX | | | | | | | | | |
| Service Desk | | | | XXXX | | | | | | | | | |
| Support Center | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| | | | | XXXX | | | | | | | | | |
| End User Computing | | | | XXXX | | | | | | | | | |
| EUC (Desktops / Laptops) | *** | # of Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Desktop IMACDS - Campus | *** | # of Desktop IMACDs | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Desktop IMACDS - Remote | *** | # of Desktop IMACDs | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Network Printer | *** | # of Printers | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Exchange Email Account | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Mobile Device | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Desktop Applications Package | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Desktop Image Management | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| | | | | XXXX | | | | | | | | | |
| Mainframe | | | | XXXX | | | | | | | | | |
| Mainframe Service | *** | # MIPS | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Mainframe Tapes | *** | # TAPES | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| | | | | | | | | | | | | | |
| Midrange and Server - Hardware | | | | | | | | | | | | | |
| Physical Server Small | *** | # of Servers | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
|
| Physical Server Medium | *** | # of Servers | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Physical Server Large | *** | # of Servers | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Physical Server Extra Large | *** | # of Servers | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Cloud Server Small | *** | # of Servers | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Cloud Server Medium | *** | # of Servers | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Cloud Server Large | *** | # of Servers | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Midrange and Server - Software | | | | | | | | | | | | | |
| Linux OS Low | *** | # OS Instances | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
|
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 259 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | |
| Linux OS Standard | *** | # OS Instances | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
|
| Linux OS High | *** | # OS Instances | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Windows OS Low | *** | # OS Instances | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Windows OS Standard | *** | # OS Instances | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Windows OS High | *** | # OS Instances | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| UNIX Low OS Instance | *** | # OS Instances | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| UNIX Medium OS Instance | *** | # OS Instances | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| UNIX High OS Instance | *** | # OS Instances | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| i-Series | *** | # OS Instances | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| ESX/Xen Host | *** | # of Servers | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| | | | | | | | | | | | | | |
| Storage and Backup Services | | | | | | | | | | | | | |
| Storage Management | *** | # Terabytes | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Backup Management (Svcs Only) | *** | # Gigabytes | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Backup Management (Svcs & Hardware) | *** | # Gigabytes | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Storage - Tier 1 | *** | # Terabytes | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Storage - Tier 2 | *** | # Terabytes | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Storage - Tier 3 | *** | # Terabytes | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| | | | | | | | | | | | | | |
| Network | | | | | | | | | | | | | |
| Network Switch/Router | *** | # Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Physical Firewall - Clustered | *** | # Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Physical Firewall - Standalone | *** | # Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Virtual Firewall - Clustered | *** | # Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Virtual Firewall - Standalone | *** | # Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Security Appliances | *** | # Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Wireless Access Points | *** | # Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Load Balancer - Clustered | *** | # Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Load Balancer - Standalone | *** | # Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Misc. Network Device | *** | # Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| VoIP Phones | *** | Devices | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Network IMADS | *** | # of IMADs | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| | | | | | | | | | | | | | |
| Cross Functional Services | | | | | | | | | | | | | |
| Service Management Resolver Licenses | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 260 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | |
| Electronic Data Exchange (EDE) | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| | | | | | | | | | | | | | |
| Security Administration Services | | | | | | | | | | | | | |
| User Security Administration | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| End Point Log Retention & Monitoring | *** | # Headcount | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| Firewall Rule Changes | *** | # Changes | | XXXX | XXXX | XXXX | XXXX | XXXX | XXXX | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
|
| | | | | | | | | | | | | | |
| Total | | | | | | | | | | | | | |
|
| | | | | | | | | | | | | | | | | | | | | |
| | | | | Metric Count |
| Description | Dell Expense Type | Chargeback Metric | | BIS Holding with NJV (multiple company codes) | Mortgage Origination Services | Field Services | Residential Value View (BPO) | RealtyBid | Default Services | ETS Retained Org | Corp Shared Services | Total |
| Account and Service Management | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| DR | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Project Management | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Telecom Expense Management | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| | | | | | | | | | | | | |
| Service Desk | | | | | | | | | | | | |
| Support Center | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| | | | | | | | | | | | | |
| End User Computing | | | | | | | | | | | | |
| EUC (Desktops / Laptops) | *** | # of Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Desktop IMACDS - Campus | *** | # of Desktop IMACDs | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Desktop IMACDS - Remote | *** | # of Desktop IMACDs | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Network Printer | *** | # of Printers | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Exchange Email Account | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Mobile Device | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Desktop Applications Package | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Desktop Image Management | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| | | | | | | | | | | | | |
| Mainframe | | | | | | | | | | | | |
| Mainframe Service | *** | # MIPS | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Mainframe Tapes | *** | # TAPES | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| | | | | | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 261 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | |
| Midrange and Server - Hardware | | | | | | | | | | | | |
| Physical Server Small | *** | # of Servers | | 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 42,108 |
|
| Physical Server Medium | *** | # of Servers | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Physical Server Large | *** | # of Servers | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Physical Server Extra Large | *** | # of Servers | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Cloud Server Small | *** | # of Servers | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Cloud Server Medium | *** | # of Servers | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Cloud Server Large | *** | # of Servers | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Midrange and Server - Software | | | | | | | | | | | | |
| Linux OS Low | *** | # OS Instances | | 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 42,108 |
|
| Linux OS Standard | *** | # OS Instances | | 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 3,509 |
| 42,108 |
|
| Linux OS High | *** | # OS Instances | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Windows OS Low | *** | # OS Instances | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Windows OS Standard | *** | # OS Instances | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Windows OS High | *** | # OS Instances | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| UNIX Low OS Instance | *** | # OS Instances | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| UNIX Medium OS Instance | *** | # OS Instances | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| UNIX High OS Instance | *** | # OS Instances | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| i-Series | *** | # OS Instances | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| ESX/Xen Host | *** | # of Servers | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| | | | | | | | | | | | | |
| Storage and Backup Services | | | | | | | | | | | | |
| Storage Management | *** | # Terabytes | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Backup Management (Svcs Only) | *** | # Gigabytes | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Backup Management (Svcs & Hardware) | *** | # Gigabytes | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Storage - Tier 1 | *** | # Terabytes | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Storage - Tier 2 | *** | # Terabytes | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Storage - Tier 3 | *** | # Terabytes | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| | | | | | | | | | | | | |
| Network | | | | | | | | | | | | |
| Network Switch/Router | *** | # Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Physical Firewall - Clustered | *** | # Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Physical Firewall - Standalone | *** | # Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Virtual Firewall - Clustered | *** | # Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Virtual Firewall - Standalone | *** | # Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Security Appliances | *** | # Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Wireless Access Points | *** | # Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Load Balancer - Clustered | *** | # Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 262 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | |
| Load Balancer - Standalone | *** | # Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Misc. Network Device | *** | # Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| VoIP Phones | *** | Devices | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Network IMADS | *** | # of IMADs | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| | | | | | | | | | | | | |
| Cross Functional Services | | | | | | | | | | | | |
| Service Management Resolver Licenses | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Electronic Data Exchange (EDE) | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| | | | | | | | | | | | | |
| Security Administration Services | | | | | | | | | | | | |
| User Security Administration | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| End Point Log Retention & Monitoring | *** | # Headcount | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| Firewall Rule Changes | *** | # Changes | | 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 4,840 |
| 58,080 |
|
| | | | | | | | | | | | | |
| Total | | | | | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 263 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | |
| | | | | Chargeback Cost |
| Description | Dell Expense Type | Chargeback Metric | | Data and Analytics | Core Logic info Solutions | Multifamily Services (multiple company codes) | RP Data | MarketLinx (MLS) | Teletrack | Tax | Lender Services (CredCo) | Flood (includes Spatial) |
| Account and Service Management | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| DR | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Project Management | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Telecom Expense Management | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | |
| Service Desk | | | | | | | | | | | | |
| Support Center | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | |
| End User Computing | | | | | | | | | | | | |
| EUC (Desktops / Laptops) | *** | # of Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Desktop IMACDS - Campus | *** | # of Desktop IMACDs | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Desktop IMACDS - Remote | *** | # of Desktop IMACDs | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Network Printer | *** | # of Printers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Exchange Email Account | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Mobile Device | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Desktop Applications Package | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Desktop Image Management | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | |
| Mainframe | | | | | | | | | | | | |
| Mainframe Service | *** | # MIPS | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Mainframe Tapes | *** | # TAPES | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | |
| Midrange and Server - Hardware | | | | | | | | | | | | |
| Physical Server Small | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Physical Server Medium | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Physical Server Large | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Physical Server Extra Large | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Cloud Server Small | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Cloud Server Medium | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Cloud Server Large | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Midrange and Server - Software | | | | | | | | | | | | |
| Linux OS Low | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Linux OS Standard | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Linux OS High | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 264 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | |
| Windows OS Low | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Windows OS Standard | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Windows OS High | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| UNIX Low OS Instance | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| UNIX Medium OS Instance | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| UNIX High OS Instance | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| i-Series | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| ESX/Xen Host | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | |
| Storage and Backup Services | | | | | | | | | | | | |
| Storage Management | *** | # Terabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Backup Management (Svcs Only) | *** | # Gigabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Backup Management (Svcs & Hardware) | *** | # Gigabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Storage - Tier 1 | *** | # Terabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Storage - Tier 2 | *** | # Terabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Storage - Tier 3 | *** | # Terabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | |
| Network | | | | | | | | | | | | |
| Network Switch/Router | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Physical Firewall - Clustered | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Physical Firewall - Standalone | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Virtual Firewall - Clustered | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Virtual Firewall - Standalone | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Security Appliances | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Wireless Access Points | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Load Balancer - Clustered | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Load Balancer - Standalone | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Misc. Network Device | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| VoIP Phones | *** | Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Network IMADS | *** | # of IMADs | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | |
| Cross Functional Services | | | | | | | | | | | | |
| Service Management Resolver Licenses | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Electronic Data Exchange (EDE) | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | |
| Security Administration Services | | | | | | | | | | | | |
| User Security Administration | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| End Point Log Retention & Monitoring | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 265 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | |
| Firewall Rule Changes | *** | # Changes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | |
| Total | | | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
|
| | | | | | | | | | | | | |
| | | | | Chargeback Cost |
| Description | Dell Expense Type | Chargeback Metric | | Dorado Network Systems | BIS Holding with NJV (multiple company codes) | Mortgage Origination Services | Field Services | Residential Value View (BPO) | RealtyBid | Default Services | ETS Retained Org | Corp Shared Services | Total |
| Account and Service Management | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| DR | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Project Management | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Telecom Expense Management | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | | |
| Service Desk | | | | | | | | | | | | | |
| Support Center | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | | |
| End User Computing | | | | | | | | | | | | | |
| EUC (Desktops / Laptops) | *** | # of Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Desktop IMACDS - Campus | *** | # of Desktop IMACDs | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Desktop IMACDS - Remote | *** | # of Desktop IMACDs | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Network Printer | *** | # of Printers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Exchange Email Account | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Mobile Device | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Desktop Applications Package | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Desktop Image Management | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | | |
| Mainframe | | | | | | | | | | | | | |
| Mainframe Service | *** | # MIPS | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Mainframe Tapes | *** | # TAPES | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | | |
| Midrange and Server - Hardware | | | | | | | | | | | | | |
| Physical Server Small | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Physical Server Medium | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Physical Server Large | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Physical Server Extra Large | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Cloud Server Small | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Cloud Server Medium | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Cloud Server Large | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Midrange and Server - Software | | | | | | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 266 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| Linux OS Low | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Linux OS Standard | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Linux OS High | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Windows OS Low | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Windows OS Standard | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Windows OS High | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| UNIX Low OS Instance | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| UNIX Medium OS Instance | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| UNIX High OS Instance | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| i-Series | *** | # OS Instances | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| ESX/Xen Host | *** | # of Servers | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | | |
| Storage and Backup Services | | | | | | | | | | | | | |
| Storage Management | *** | # Terabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Backup Management (Svcs Only) | *** | # Gigabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Backup Management (Svcs & Hardware) | *** | # Gigabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Storage - Tier 1 | *** | # Terabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Storage - Tier 2 | *** | # Terabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Storage - Tier 3 | *** | # Terabytes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | | |
| Network | | | | | | | | | | | | | |
| Network Switch/Router | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Physical Firewall - Clustered | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Physical Firewall - Standalone | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Virtual Firewall - Clustered | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Virtual Firewall - Standalone | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Security Appliances | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Wireless Access Points | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Load Balancer - Clustered | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Load Balancer - Standalone | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Misc. Network Device | *** | # Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| VoIP Phones | *** | Devices | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Network IMADS | *** | # of IMADs | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | | |
| Cross Functional Services | | | | | | | | | | | | | |
| Service Management Resolver Licenses | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Electronic Data Exchange (EDE) | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| | | | | | | | | | | | | | |
| Security Administration Services | | | | | | | | | | | | | |
| User Security Administration | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| End Point Log Retention & Monitoring | *** | # Headcount | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
| Firewall Rule Changes | *** | # Changes | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 267 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | |
| | | | | | | | | | | | | | |
| Total | | | | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! | #VALUE! |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 268 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Corporate Shares Services |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 269 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 270 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| ETS |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 271 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 272 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Default Services - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 273 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 274 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Reality- Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 275 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 276 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Residential VV - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 277 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 278 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Field Services - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 279 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 280 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Mortgage Origination Services - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 281 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 282 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| BIS Holding - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 283 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 284 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Dorado - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 285 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 286 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Flood - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 287 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | X | X | X |
|
| | Telephony | | % of Telecom Spend | | X | X | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | X | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | X | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | X | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 288 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Credco - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 289 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 290 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Tax - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 291 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 292 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| TeleTrack - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 293 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 294 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| MarketLinx - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 295 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 296 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| RP Data - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 297 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 298 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| MultiFamily- Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 299 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 300 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| CL Info Solution - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 301 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 302 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | | | | | | | | |
| Data and Analytics - Summary |
| | | | | | | | | |
| | Business Unit Name: | | | | | | | |
| | Service Line | | Metric | | Recovery Unit Price | | Metric Count | Monthly Allocation |
| | | | | | | | | |
| | Account and Service Management | | Headcount | | X | | X | X |
|
| | DR | | Headcount | | X | | X | X |
|
| | Project Management | | Headcount | | X | | X | X |
|
| | Telecom Expense Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Service Desk | | | | | | | |
| | Support Center | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | End User Computing | | | | | | | |
| | EUC (Desktops / Laptops) | | Desktops / Laptops | | X | | X | X |
|
| | Desktop IMACDS - Campus | | Desktop IMACDs | | X | | X | X |
|
| | Desktop IMACDS - Remote | | Desktop IMACDs | | X | | X | X |
|
| | Network Printer | | Printers | | X | | X | X |
|
| | Exchange Email Account | | Headcount | | X | | X | X |
|
| | Mobile Device | | Headcount | | X | | X | X |
|
| | Desktop Applications Package | | Headcount | | X | | X | X |
|
| | Desktop Image Management | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Mainframe | | | | | | | |
| | Mainframe Service | | MIPS | | X | | X | X |
|
| | Mainframe Tapes | | Tapes | | X | | X | X |
|
| | | | | | | | | |
| | Midrange and Server - Hardware | | | | | | | |
| | Physical Server Small | | Servers | | X | | X | X |
|
| | Physical Server Medium | | Servers | | X | | X | X |
|
| | Physical Server Large | | Servers | | X | | X | X |
|
| | Physical Server Extra Large | | Servers | | X | | X | X |
|
| | Cloud Server Small | | Servers | | X | | X | X |
|
| | Cloud Server Medium | | Servers | | X | | X | X |
|
| | Cloud Server Large | | Servers | | X | | X | X |
|
| | Midrange and Server - Software | | | | | | | |
| | Linux OS Low | | OS Instances | | X | | X | X |
|
| | Linux OS Standard | | OS Instances | | X | | X | X |
|
| | Linux OS High | | OS Instances | | X | | X | X |
|
| | Windows OS Low | | OS Instances | | X | | X | X |
|
| | Windows OS Standard | | OS Instances | | X | | X | X |
|
| | Windows OS High | | OS Instances | | X | | X | X |
|
| | UNIX Low OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX Medium OS Instance | | OS Instances | | X | | X | X |
|
| | UNIX High OS Instance | | OS Instances | | X | | X | X |
|
| | i-Series | | OS Instances | | X | | X | X |
|
| | ESX/Xen Host | | Servers | | X | | X | X |
|
| | | | | | | | | |
| | Storage and Backup Services | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 303 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | |
| | Storage Management | | Terabytes | | X | | X | X |
|
| | Backup Management (Svcs Only) | | Gigabytes | | X | | X | X |
|
| | Backup Management (Svcs & Hardware) | | Gigabytes | | X | | X | X |
|
| | Storage - Tier 1 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 2 | | Terabytes | | X | | X | X |
|
| | Storage - Tier 3 | | Terabytes | | X | | X | X |
|
| | | | | | | | | |
| | Network | | | | | | | |
| | Network Switch/Router | | Devices | | X | | X | X |
|
| | Physical Firewall - Clustered | | Devices | | X | | X | X |
|
| | Physical Firewall - Standalone | | Devices | | X | | X | X |
|
| | Virtual Firewall - Clustered | | Devices | | X | | X | X |
|
| | Virtual Firewall - Standalone | | Devices | | X | | X | X |
|
| | Security Appliances | | Devices | | X | | X | X |
|
| | Wireless Access Points | | Devices | | X | | X | X |
|
| | Load Balancer - Clustered | | Devices | | X | | X | X |
|
| | Load Balancer - Standalone | | Devices | | X | | X | X |
|
| | Misc. Network Device | | Devices | | X | | X | X |
|
| | VoIP Phones | | Headcount | | X | | X | X |
|
| | Network IMACDS | | IMACs | | X | | X | X |
|
| | | | | | | | | |
| | Cross Functional Services | | | | | | | |
| | Service Management Resolver Licenses | | Headcount | | X | | X | X |
|
| | Electronic Data Exchange (EDE) | | Headcount | | X | | X | X |
|
| | | | | | | | | |
| | Security Administration Services | | | | | | | |
| | User Security Administration | | Headcount | | X | | X | X |
|
| | End Point Log Retention & Monitoring | | Headcount | | X | | X | X |
|
| | Firewall Rule Changes | | Changes | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation Before G&A and Corp Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | General & Administrative | | | | | | | |
| | Gen., Admin., & Corp. | | % of IT Spend | | X | | X | X |
|
| | Telephony | | % of Telecom Spend | | X | | X | X |
|
| | Corp. SW Licensing & Corp. Email | | % of Revenue | | X | | X | X |
|
| | | | | | | | | |
| | Corporate Systems | | | | | | | |
| | Financial Systems | | % of Revenue | | X | | X | X |
|
| | Corporate Systems | | % of IT Spend | | X | | X | X |
|
| | | | | | | | | |
| | Total Estimated General, Administrative and Corporate Systems | | | | | | | $ | — |
|
| | | | | | | | | |
| | Total Estimated Monthly Allocation | | | | | | | $ | — |
|
| | Comments | | | | | | | |
| | | | | | | | | |
| | | | | | | | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 304 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-4.10
CHARGEABLE PROJECTS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 305 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-4.10
Chargeable Projects
| |
| 1.1 | Agreement. This Schedule A-4.10 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to this Supplement, or the other Schedules to the MSA or this Supplement. The following terms have the meanings given below: |
“Annual Carryover Amount” has the meaning given in Section 2.6.
“Annual Chargeable Project Pool” has the meaning given in Section 2.5.
“Chargeable Project” means (a) a Supplier obligation expressly identified to be performed as a Chargeable Project in the Supplement (including in any Statement of Work in which work above a defined threshold shall be identified as being a Chargeable Project) or separately agreed in writing by the Parties to be performed as a Chargeable Project or (b) any other discrete unit of non-recurring (i.e., not recurring on a regular basis unless otherwise agreed by the Parties) work expressly requested or approved by CoreLogic’s VP, ETS that (i) is not an inherent, necessary or *** of the day-to-day (i.e., regular, not daily) Services, (ii) is not required to be performed by Supplier to meet the existing Service Levels (other than Service Levels related to Chargeable Project performance), (iii) is not otherwise part of the Services to be provided within the Charges, as provided in this Supplement, and (iv) requires more than *** (***) hours of effort (***). A Chargeable Project may consist of or include work that would otherwise be treated as New Services.
“Chargeable Project Management” has the meaning given in Section 2.3.
“Monthly Predicted Hours” has the meaning given in Section 2.7.
“Plus-*** Chargeable Project” has the meaning given in Section 2.4.
“Project Initiation Time” has the meaning given in Section 2.4.
| |
| 1.4 | General. This Schedule A-4.10 sets forth the means by which CoreLogic may request, and Supplier shall perform, Chargeable Projects. |
| |
| 1.5 | Resource Units. For clarity, any Services performed as Chargeable Projects shall not also be charged as Resource Units, even if Supplier would otherwise have the right to charge a Resource Unit pursuant to Schedule A-4. |
| |
| 1.6 | Application Only As of Commencement Date. This Schedule A-4.10 shall not be applicable for periods prior to January 1, 2013. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 306 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 2.1 | General. From time to time during the Term, CoreLogic may request, and Supplier shall perform, Chargeable Projects. Schedule A-4.10.1 sets forth a list of the Services that are deemed to be Chargeable Projects as of the Supplement Effective Date. |
| |
| 2.2 | Charges. Unless otherwise agreed by the Parties, Supplier shall perform all Chargeable Projects on an hourly services basis in accordance with the charging mechanisms set forth in Section 7.3 (T&M Project Calculation Rules) of Schedule A-4 (i.e., as a T&M Project). If the Parties mutually agree that a Chargeable Project shall be performed on a *** basis, such Chargeable Project shall be charged as a Fixed Fee Project in accordance with Section 7.2(a) of Schedule A-4. |
| |
| 2.3 | Support *** of Chargeable Projects. Notwithstanding Section 7.3 of Schedule A-4, time expended by Supplier Personnel *** Chargeable Projects (“Chargeable Project Management”) *** as part of the Chargeable Project being managed. Rather, such *** shall be performed and charged for through the Chargeable Project ***; provided, however, any Supplier Personnel support needed for *** then-active Chargeable Projects that are in excess of the *** of the *** (***) *** FTEs funded by the *** (as determined by the Supplier PMO and the CoreLogic PMO using Project Management Institute standards) shall be chargeable as part of the Chargeable Project being managed on a Productive Hours basis at the applicable project management hourly rate set forth in Schedule A-4.7. The *** (***) *** FTEs funded by the *** shall be full-time Supplier Personnel dedicated to ***. |
| |
| 2.4 | Chargeable Project Descriptions. For each Chargeable Project, the Parties shall meet and agree to a description of the activities to be performed for such Chargeable Project, a project plan, an estimate of the hours to be expended in the performance of such activities, as well as the skill type and applicable hourly rates (in accordance with Schedule A-4.7) for such estimated hours (or, for ***, the *** and associated milestones and credits), and the project management time and requirements, if any, required to complete such Chargeable Project. All Supplier Personnel time associated with discussing and agreeing to the elements described above in this Section 2.4 (“Project Initiation Time”) shall be *** and the hours expended in the performance of the Chargeable Project (i.e., such time shall not ***); provided that, with respect to any Chargeable Project that is reasonably expected to require *** (***) or more Productive Hours to complete (a “Plus-*** Chargeable Project”), if Supplier spends Project Initiation Time and CoreLogic then decides not to proceed with the Chargeable Project or elects not to have Supplier perform such Chargeable Project, then all actual and reasonable Project Initiation Time shall be charged as a Chargeable Project in accordance with this Schedule A-4.10, except as provided otherwise in the immediately following sentence. Notwithstanding the foregoing, ***. |
| |
| 2.5 | Annual Chargeable Project Pool. For each of the Contract Years 2013 through 2019, CoreLogic shall be charged no less than $*** for Supplier’s performance of Chargeable Projects (each such $*** commitment, an “Annual Chargeable Project Pool”) in accordance with this Schedule A-4.10. For the avoidance of doubt, the Annual Chargeable Project Pool shall not be an ECA Element. For each Contract Year, Charges associated with Supplier’s performance of Chargeable Projects during such Contract Year shall result in a debit (i.e., a reduction) of such Annual Chargeable Project Pool equal to the Charges that have been invoiced by Supplier and paid by CoreLogic for such Chargeable Projects. For example, if during Contract Year 2013, CoreLogic requests two (2) T&M Chargeable Projects performed by Supplier for $*** and $*** respectively and one (1) Fixed Fee Chargeable Project performed by Supplier for $***, then $*** of the 2013 Annual Chargeable Project Pool would be debited and $*** would remain in the 2013 Annual Chargeable Project Pool. |
| |
| 2.6 | The Annual Chargeable Project Pool shall be subject to the following rules: |
| |
| (a) | CoreLogic may elect to carry over up to a maximum of $*** of the Annual Chargeable Project Pool for any Contract Year (an “Annual Carryover Amount”) to the subsequent Contract Year. In such case, in the subsequent Contract Year, CoreLogic shall be responsible for such Annual Carryover Amount in addition to the Annual Chargeable Project Pool for the subsequent Contract |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 307 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Year. For example, if, at the end of Contract Year 2013, there is an Annual Carryover Amount of $***, in Contract Year 2014, CoreLogic would be responsible for such $*** in addition to the $*** Annual Chargeable Project Pool for Contract Year 2013. Notwithstanding the foregoing, no such carryover shall be permitted from Contract Year 2019. If, at the end of Contract Year 2019, CoreLogic (i) has not satisfied the Annual Chargeable Project Pool for such Contract Year (including any Annual Carryover Amount from Contract Year 2018) and (ii) had requested Chargeable Projects within the Monthly Predicted Hours during the last *** (***) months of Contract Year 2019, and Supplier failed to provide Supplier Personnel to perform such Chargeable Projects by the end of Contract Year 2019, then the Parties will discuss and agree to an equitable remedy (e.g., a credit against other Charges or a commitment by Supplier to provide additional Services) to account for any lost portions of the Annual Chargeable Project Pool for Contract Year 2019; provided, however, that such equitable remedy shall only be available if the Monthly Predicted Hours during the last *** (***) months of Contract Year 2019 were no greater than the average of Monthly Predicted Hours for such two-month period during Contract Year 2018.
| |
| (b) | At the end of each Contract Year, any unutilized amount of the Annual Chargeable Project Pool that is (i) in excess of the Annual Carryover Amount or (ii) existing at the end of Contract Year 2019, shall be invoiced by Supplier and paid by CoreLogic subject to and in accordance with Article 12 of the MSA. If any such unutilized amounts are due to Supplier’s failure to perform Chargeable Projects that were requested by CoreLogic within the applicable Monthly Predicted Hours during the last *** (***) months of the applicable Contract Year, then the Parties will discuss and agree to an equitable remedy (e.g., a credit against other Charges or a commitment by Supplier to provide additional Services) to account for any lost portions of the Annual Chargeable Project Pool for such Contract Year; provided, however, that such equitable remedy shall only be available if the Monthly Predicted Hours during the last *** (***) months of the applicable Contract Year were no greater than the average of Monthly Predicted Hours for the *** (***) months in the applicable Contract Year preceding such *** (***) month period. |
| |
| (c) | If, during any applicable Contract Year, the Chargeable Project Pool is depleted, then Supplier shall charge for such Chargeable Projects in accordance with Section 7.3 of Schedule A-4 for T&M Projects or Section 7.2(a) of Schedule A-4 for Fixed Fee Projects. |
| |
| 2.7 | Monthly Predicted Hours. With respect to any Contract Year where there is an Annual Chargeable Project Pool, within the first five (5) days of each month, CoreLogic will provide to Supplier a forecast of expected Chargeable Projects to be performed by Supplier during each of the next three (3) subsequent months (i.e., a rolling 3-month forecast). For example, CoreLogic would provide a forecast to Supplier by January 5th for forecasting possible work to be performed by Supplier in February, March and April. Such forecast shall not be binding on CoreLogic and shall not constitute a commitment by CoreLogic to have Supplier perform any particular Chargeable Project contemplated by the forecast. The Parties will jointly scope the estimated hours required for such work for each of the three (3) forecasted months, with the first month of such forecast being the “Monthly Predicted Hours”. For example, after receiving CoreLogic’s forecast provided in January for February through April, the Parties would establish the Monthly Predicted Hours for February and begin planning for March and April. If, in any month, the number of Chargeable Project hours requested by CoreLogic to be performed in such month is substantially higher than the number of Monthly Predicted Hours established by the Parties for such month, Supplier shall use commercially reasonable efforts to provide such chargeable resources substantially in excess of the Monthly Predicted Hours to accommodate such additional requested Chargeable Project work above the Monthly Predicted Hours, but only to the extent Supplier Personnel are available to perform such Chargeable Projects. |
| |
| 2.8 | Reporting. Promptly after the end of each month (and as otherwise requested by CoreLogic), Supplier shall report to CoreLogic the Productive Hours expended in the performance of each Chargeable Project during the preceding month, together with a report of the aggregate number of Productive Hours expended in the performance of all Chargeable Projects during such month and to date for such Contract Year. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 308 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 2.9 | Scheduling. CoreLogic shall have the right to reprioritize or reset the schedule for existing Chargeable Projects, or to terminate any Chargeable Project in accordance with Section 7.5 (Project Termination) of Schedule A-4. |
| |
| 2.10 | Disputes. Any disputes regarding Chargeable Projects shall be subject to the dispute resolution procedures set forth in Article 19 of the MSA. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 309 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19,2012
SUPPLEMENT A
SCHEDULE A-4.10.1
DEEMED CHARGEABLE PROJECTS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 310 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 1.1 | Agreement. This Schedule A-4.10.1 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to this Supplement, or the other Schedules to the MSA or this Supplement. |
| |
| 2. | DEEMED CHARGEABLE PROJECTS. |
Pursuant to clause (a) of the definition of Chargeable Projects, the following Services shall be deemed to be Chargeable Projects that are charged in accordance with Schedule A-4.10:
| |
| a) | Supplier’s installation, at CoreLogic’s direction, of CoreLogic-provided Equipment at Supplier Data Centers or CoreLogic Facilities (excluding Services that are described in Schedules A-10 or 13) that do not have a corresponding one-time installation Resource Unit rate, but only where the scope of such installation is not covered by, or is not otherwise required for the performance of the Services, and only if the particular request requires more than *** (***) Productive Hours of effort. |
| |
| b) | Supplier’s installation of new CoreLogic-retained circuits or changes to CoreLogic-provided circuits for CoreLogic Facilities that are not covered by any Resource Unit, but only where the scope of such installation is not covered by, or is not otherwise required for the performance of the Services, and only if the particular request requires more than *** (***) Productive Hours of effort. |
| |
| c) | Supplier’s coordination and execution of disaster recovery testing, at CoreLogic’s request, beyond the *** or *** as documented in ***. |
| |
| d) | Supplier’s creation of new disaster recovery plans (DRPs) for new Applications, in accordance with Schedule A-2.12, but only if the particular request requires more than *** (***) Productive Hours of effort. |
| |
| e) | Pursuant to Section 11.1(e)(ii) of the MSA, in connection with an acquisition of an Entity by an Eligible Recipient, Supplier’s assistance, at CoreLogic’s request, in planning, preparing and implementing any transition or changes related to the Services as a result of an acquisition, including performing an analysis of the current IT services of the acquired Entity and impacts to the acquired Entity and CoreLogic, but only if the particular request requires more than *** (***) Productive Hours of effort. Such assistance may include: (i) performing infrastructure migrations resulting from the acquisition; (ii) making changes to the ITSM System and CMDB; and (iii) assessing skills of the acquired Entity’s IT personnel. |
| |
| f) | Pursuant to Section 11.1(e)(iii) of the MSA, Supplier’s assistance, at CoreLogic’s request, in planning, preparing and implementing any transition or changes related to the Services as a result of the divestiture of an Entity by an Eligible Recipient, including the performance of infrastructure changes due to such divestiture, but only if the particular request requires more than *** (***) Productive Hours of effort. |
| |
| g) | OPAS Integration. Supplier’s creation, at CoreLogic’s request, of non-standard, custom Application Programming Interfaces (APIs) or OPAS work requests, but only if the particular request requires more than *** (***) Productive Hours of effort. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 311 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| h) | End User Device IMACD. Supplier’s performance of more than *** (***) Desktop IMACD Service Requests for an individual Designated remote Sites and *** (***) Desktop IMACD Service Requests for an individual Designated Campus Sites ***, but only where CoreLogic has directed Supplier to perform all such End User Device IMACD Service Requests ***. |
| |
| i) | Virtual Server Provisioning. Supplier’s performance of more than *** (***) Provisioning Requests for Virtual Servers ***, but only where CoreLogic has directed Supplier to perform all such Server Provisioning Service Requests ***. |
| |
| j) | Physical Server Provisioning. Supplier’s performance of more than *** (***) Provisioning Requests ***, but only where CoreLogic has directed Supplier to perform all such Server Provisioning Service Requests ***. |
| |
| k) | Infrastructure Support & Architecture. Supplier’s performance, at CoreLogic’s request, of architecture assistance services with respect to CoreLogic-retained Equipment or Systems, but only if the particular request requires more than *** (***) business hours of effort over the course of *** (***) ***. Notwithstanding the foregoing, any such assistance services that are performed (a) in connection with the Managed Services or (b) by Supplier Personnel responsible for performing Service and Account Management Services, shall not be considered Chargeable Projects. For clarity, “in connection with” above shall not be considered to mean that architecture assistance with respect to an Application fits within the exception set forth in clause (a), solely on the basis that such Application runs on a hosted server being provided by Supplier as a Managed Service. |
| |
| l) | Central Account Provisioning. Supplier’s performance of more than *** (***) Central Account Provisioning Service Requests for Employee Termination Requests, but only where CoreLogic has directed Supplier to perform all such Central Account Provisioning Service Requests ***. |
| |
| m) | Supplier’s performance of more than *** (***) Central Account Provisioning Service Requests for New Employee Setup, but only where CoreLogic has directed Supplier to perform all such Central Account Provisioning Service Requests ***. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 312 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-4.11 Project Pool
|
| | | | | | | | | | |
| | | | | | | | | | | |
| Discretionary Projects | 2012 | 2013 | 2014 | 2015 | 2016 | 2017 | 2018 | 2019 | 2020 | Total |
| Discretionary Project Pool | | *** | *** | *** | *** | *** | *** | *** | | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 313 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-4.12
***
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 314 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-4.12
***
| |
| 1.1 | Agreement. This Schedule A-4.12 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
| |
| 1.4 | Purpose. This Schedule sets forth the definitions of the *** that are set forth in Schedule A-4.1. |
| |
| 2.1 | Account and Service Management. The *** identified as “Account and Service Management” in Schedule A-4.1 shall be *** for the Service Management tools, support, reporting, OPAS licenses for Supplier Personnel and the performance of the Services described in Schedule A-2.2, as well as all account management function and overhead costs associated with *** under the Supplement. |
| |
| 2.2 | Chargeable Project Management. The *** identified as “Chargeable Project Management” in Schedule A-4.1 shall be *** for Supplier’s provision of *** (***) *** project management Supplier Personnel resources to manage Supplier’s performance of Chargeable Projects as provided for in Schedule A-4.10. |
| |
| 2.3 | Disaster Recovery (DR). The *** identified as “Disaster Recovery” in Schedule A-4.1 shall be *** for Supplier’s performance of the Services described in Schedule A-2.12. |
| |
| 2.4 | Telecom Expense Management. The *** identified as “Telecom Expense Management” shall be *** for Supplier’s performance of the Services described in Sections 1.2.3.7 through Section 1.2.3.11 of Schedule A-2.9. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 315 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING, L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-5
HUMAN RESOURCES PROVISIONS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 316 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-5
Human Resources Provisions
| |
| 1.1 | Agreement. This Schedule A-5 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or the other Schedules to the MSA. |
| |
| (a) | “Benefit Plan” has the meaning given in Section 3.1(a). |
| |
| (b) | “Initial Stabilization Period” has the meaning given in Section 2.4. |
| |
| (c) | “Visa Transitioned Employee” has the meaning given in Section 3.11. |
| |
| 1.4 | Schedules. The following documents are attached to and incorporated by reference in this Schedule: |
Schedule A-5.1 Key Supplier Personnel
Schedule A-5.2 Affected Employees
Schedule A-5.3 Severance Formula
| |
| 2. | TRANSITIONED EMPLOYEES. |
| |
| 2.1 | Supplier Offers of Employment. Within 48 hours of an employee satisfactorily completing Supplier’s standard new hire process (i.e., the employee’s completion of all screens in Supplier’s on-line employee intake tool), Supplier shall offer employment to each of the employees of CoreLogic or its applicable Affiliate designated in Schedule A-5.2 as an “Affected Employee” on the terms provided in this Section 2.1 and Section 2.2. All such offers shall be made subject to, the employee’s satisfactory completion of Supplier’s standard new hire process (i.e., the employee’s completion of all screens in Supplier’s on-line employee intake tool), ***, credit checks and drug testing and/or medical examinations, but including execution of Supplier’s form of associate agreement and other authorizations that are generally applicable to other similarly situated potential employees of Supplier. |
| |
| 2.2 | Terms of Offer. Each such offer shall be for employment with Supplier commencing ***, 20***, in a *** and *** that he or she held with CoreLogic, and with ***, and *** (i.e., *** (“***”) ***, where applicable) that is *** to the *** as of the date of such offer (except in ***, for those *** for whom *** have ***), and *** and ***, and *** that, ***, are *** to the *** as of the ***. To the extent that the Affected Employee is not actively at work with CoreLogic as of the planned date of the offer due to a CoreLogic-approved leave of absence, such Affected Employee shall remain an employee of CoreLogic until he or she returns to active employment with physician’s release or other appropriate documentation, as applicable, releasing such Affected Employee to resume his or her prior work schedule. If such leave of absence expires within two (2) months of the Supplement |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 317 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Effective Date, Supplier shall extend an offer of employment to such Affected Employee as set forth in Sections 2.1 and 2.2 for such Affected Employee to become an employee of Supplier on the date upon which he or she returns to active employment (as provided in the preceding sentence). Without limiting Section 21.14 of the MSA, for a period of *** (***) *** after the Supplement Effective Date, unless otherwise approved by CoreLogic, Supplier shall not (and shall not permit its Affiliates to) (i) offer employment to any employee of CoreLogic or another Eligible Recipient, including any such employees who, prior to the Supplement Effective Date, performed any of the Services to be provided by Supplier after the Supplement Effective Date, other than the Affected Employees in accordance with the provisions of this Schedule A-5 and (ii) notwithstanding clause (i), make an offer of employment to any of the Affected Employees who do not accept Supplier’s initial offer of employment made pursuant to Section 2.1 above.
| |
| 2.3 | Offers to Comply with Laws. Each of CoreLogic and Supplier will comply with all applicable Laws, including local, state, and federal laws and regulations related to employment requirements and employment transfers, in offering employment to and employing the Affected Employees and the processes contemplated by this Schedule. |
| |
| 2.4 | Minimum Retention. From their Employment Effective Date until ***, 20*** (“Initial Stabilization Period”), Supplier shall employ and retain the Transitioned Employees in accordance with the requirements set forth in this Schedule A-5, provided that nothing shall require Supplier to retain a Transitioned Employee whose employment is terminated due to (i) a violation of generally applicable work rules and policies of Supplier; (ii) insubordination or misconduct; or (iii) violation of Supplier policies or other circumstances reasonably viewed as constituting cause for termination under Supplier’s human resource policies (including job performance-related cause for termination) (the items in clauses (i)-(iii) collectively being referred to as “cause”). |
| |
| 2.5 | Interviewing of Transitioned Employees. During the first three (3) months of the Initial Stabilization Period, Supplier *** interview all Transitioned Employees for consideration for continued placement with Supplier after the end of the Initial Stabilization Period (either in positions on CoreLogic’s account or for other comparable positions within Supplier). Supplier shall *** to ***. Subject to preceding sentence, ***, at *** (i) *** and (ii) ***. |
| |
| 2.6 | *** for Transitioned Employees. Subject to Supplier’s obligations in Section 2.5, if (i) a Transitioned Employee’s employment ends on or before ***, ***, (ii) such Transitioned Employee is working on CoreLogic’s account as of the date such Transitioned Employee’s employment ends, and (iii) *** is ***, *** will pay *** (and any other ***) to such Transitioned Employee, and *** shall *** the *** with the *** set forth in Schedule ***. *** shall *** for *** associated with *** the *** the *** of *** set forth in Schedule *** and ***. |
| |
| 2.7 | Notification. If any of the Transitioned Employees employment with Supplier is terminated during the Initial Stabilization Period, Supplier shall notify CoreLogic within twenty-four (24) hours of such termination. |
| |
| 2.10 | Additional Transitioned Employees. During the *** (***) *** following the Supplement Effective Date, *** may *** additional employees of CoreLogic or an Eligible Recipient to whom offers of employment are to be extended by Supplier. |
| |
| 2.11 | Reemployment of Transitioned Employees. During the *** (***) *** following the Supplement Effective Date, *** may *** one or more Transitioned Employees to whom CoreLogic or another Eligible Recipient may extend offers of reemployment that were hired by Supplier or its Affiliates |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 318 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
or Subcontractors. Supplier shall not interfere with efforts by CoreLogic or another Eligible Recipient to reemploy any such Transitioned Employee.
| |
| 2.12 | *** to CoreLogic *** or ***. As a condition to employment by Supplier, *** may require each Transitioned Employee to acknowledge in writing to CoreLogic that his or her employment *** to have been “***” by *** and, therefore, such Transitioned Employee’s acceptance of Supplier’s offer of employment *** a *** under any *** or ***. |
| |
| (a) | Transitioned Employees will be employees of Supplier or its applicable Affiliate for all purposes on and after their Employment Effective Date. In addition, Supplier shall conduct its business in a manner to ***, following any Transitioned Employee’s Employment Effective Date, CoreLogic (or the applicable Eligible Recipient) will be considered an employer, co-employer or joint employer of any Transitioned Employees. On and after their Employment Effective Date, Transitioned Employees will not be deemed employees or agents of CoreLogic for any purpose including, without limitation, for: (i) federal, state or local tax, employment, withholding or reporting; (ii) provident fund, gratuity, bonus, workers’ compensation, employee state insurance or disability coverage, severance pay and paid vacation or sick pay; or (iii) eligibility or entitlement to participate in Benefit Plans. “Benefit Plans” means employee benefit plans, incentive, compensation and other employee programs and policies. |
| |
| (b) | Prior to the Employment Effective Date, Transitioned Employees shall be employees of CoreLogic or its applicable Affiliate for all purposes. Prior to their Employment Effective Date, Transitioned Employees will not be deemed employees or agents of Supplier or its Affiliates for any purpose including, without limitation, for: (i) federal, state or local tax, employment, withholding or reporting; (ii) provident fund, gratuity, bonus, workers’ compensation, employee state insurance or disability coverage, severance pay and paid vacation or sick pay; or (iii) eligibility or entitlement to participate in Benefit Plans. |
| |
| 3.2 | Merit Increases. Supplier shall provide each Transitioned Employee with performance appraisal and merit reviews consistent with its policies generally applicable to similarly situated employees. |
| |
| 3.3 | Tuition Assistance. As of their Employment Effective Date, Transitioned Employees shall be eligible to participate in any tuition assistance or reimbursement programs provided by Supplier to its similarly situated employees subject to Supplier rules, procedures and policies as set each year for Supplier employees. CoreLogic shall remain financially responsible, in accordance with CoreLogic’s policy, for courses which are in progress prior to the enrolled Transitioned Employee’s Employment Effective Date and for which tuition assistance has been approved by CoreLogic. Courses approved for Transitioned Employees by Supplier after the Employment Effective Date shall be reimbursed by Supplier in accordance with Supplier’s rules, procedures and policies for such benefits. |
| |
| 3.4 | Training and Skill Development. Supplier shall provide training, skill development and career growth opportunities to Transitioned Employees consistent with its policies generally applicable to similarly situated Supplier employees. |
| |
| 3.6 | Equal Employment Opportunity Employers Statement. Each of CoreLogic and Supplier represents and warrants to the other that it is an equal employment opportunity employer and is in compliance in all material respects with any and all applicable employment anti-discrimination laws, rules and regulations related to the provisioning of Services under this Agreement. In regards to the |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 319 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
delivery of the Services, each of CoreLogic and Supplier agrees not to harass, discriminate against or retaliate against any of the other Party’s employees on the grounds of race, national origin, age, sex, religion, disability, marital status or other category protected by law, nor shall it cause or request such other Party to engage in such discrimination, harassment or retaliation in its provisioning of the Services (including but not limited to any refusal to use or remove any Transitioned Employee for reasons not permitted by applicable employment laws).
| |
| 3.7 | Other Employee Matters. *** shall be responsible for *** and ***, *** with ***, *** and *** and *** the Transitioned Employees. In addition, Supplier shall be responsible for funding and distributing benefits under the benefit plans in which Transitioned Employees participate on or after the Transitioned Employee’s Employment Effective Date (except to the limited extent provided in Section 2.6) and, for paying any compensation and remitting any income, disability, withholding and other employment taxes for such Transitioned Employees beginning on the Employment Effective Date. |
| |
| 3.8 | Employee Benefit Plans. |
| |
| (a) | General. Supplier shall provide Transitioned Employees with employee benefits at least comparable to the benefits provided generally by Supplier to other similarly situated Supplier employees. |
| |
| (b) | ***. Unless otherwise noted and agreed by the Parties, Transitioned Employees shall *** under each employee benefit plan for purposes of career advancement and promotion consideration, vesting, participation, eligibility for benefits, retiree medical, benefit *** and/or optional forms of payment. |
| |
| (c) | Employee Welfare Benefit Plans. Each Transitioned Employee shall be eligible as of his or her Employment Effective Date to *** in Supplier’s employee welfare benefit plans (“welfare plans”), which shall include ***. Subject to the general comparability requirements of Section 3.8(a), eligibility for, the benefits of, and the amount, if any, of employee contributions toward welfare plan coverage will be determined by Supplier; provided, however, that each of Supplier’s welfare plans shall *** for each such Transitioned Employee and, subject to Supplier’s policies, any eligible spouse or covered dependents. Any deductible, co-payment or co-insurance amounts, or out of pocket expenses paid by any Transitioned Employee in the calendar year of his or her Employment Effective Date *** be applied toward any deductible, co-payment or co-insurance amounts, or out of pocket requirement by Supplier’s group insurance program for the calendar year of his or her Employment Effective Date. |
| |
| (d) | Paid-Time-Off (Vacation/Sick Leave). Beginning on his or her Employment Effective Date, Supplier shall make available to each Transitioned Employee paid-time-off benefits for vacation and sick leave under its applicable plans, with *** of such Transitioned Employee determined in accordance with Section ***, pro-rated for calendar year 2012. The paid-time-off benefits provided by Supplier shall be comparable to the vacation and sick leave benefits generally available to similarly situated employees of Supplier. Supplier shall recognize documented vacation plans made by any Transitioned Employee and approved by CoreLogic or another Eligible Recipient prior to his or her Employment Effective Date and shall permit such Transitioned Employee to incur negative leave balances for this purpose. |
| |
| (e) | Holidays. Transitioned Employees will be eligible for the Supplier holiday schedule of eight (8) days. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 320 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (g) | Supplier 401(k) Savings Plan. Each Transitioned Employee shall be eligible to participate *** in Supplier’s 401(k) Savings Program pursuant to the plans and policies applicable to similarly situated Supplier employees. All Transitioned Employees who enroll in Supplier’s 401(k) Savings Program will become *** their respective Employment Effective Dates for Supplier matching contributions and earnings. Supplier matching contributions will ***. Each Transitioned Employee may rollover his/her from a CoreLogic’s qualified 401(k) into the Supplier’s 401(k) Savings Plan at any time pursuant to the plans and policies applicable to similarly situated Supplier employees. |
| |
| (h) | Bonus Programs. Supplier shall provide that each Transitioned Employee will be eligible for variable compensation (i.e., bonus and LTI targets, where applicable) *** to that provided to the Affected Employee as of the date of offer (except for those Transitioned Employees for whom *** adjustments to base salary have been made to account for a ***). |
| |
| (i) | Severance Pay Plans. Subject to Section 2.6 above, beginning on his or her Employment Effective Date, Supplier shall make available to all Transitioned Employees severance pay plans consistent with its plans generally applicable to similarly situated employees of Supplier. |
| |
| (j) | Retiree Medical. Beginning on his or her Employment Effective Date, Supplier shall make available to all Transitioned Employees retiree medical plans consistent with its plans generally applicable to similarly situated employees of Supplier. |
| |
| 3.9 | Union Agreements and WARN Act. |
| |
| (b) | WARN Act Commitment. Supplier shall not after their Employment Effective Dates, cause any of the Transitioned Employees to suffer “employment loss” as that term is construed under the WARN Act (or any equivalent federal or state Law), if such employment loss could create any ***, unless Supplier delivers notices under the WARN Act (or the applicable equivalent federal or state Law) in a manner and at a time *** with respect thereto. |
| |
| 3.10 | Responsibility. Supplier shall be responsible for any liability, cost, claim, expense, obligation or sanction attributable to any breach by Supplier of Section 3.9(b) that results in *** being in violation of the WARN Act or the regulations promulgated thereunder. |
| |
| 3.11 | Immigration. For each Transitioned Employee possessing an H1-B visa to work in the United States (each, a “Visa Transitioned Employee”), *** shall be solely liable for all costs, fees and requirements relating to the transfer of such H1-B visa from CoreLogic to Supplier and *** will pay all legal costs and government filing fees associated with such Transitioned Employee’s H1-B visa process. For each Visa Transitioned Employee who does not secure continued placement with Supplier pursuant to Section 2.5 above, will receive severance in accordance with Section 2.6 above and will be provided with an airplane ticket to his or her home country by ***. |
The Key Supplier Personnel under this Supplement are set forth in Schedule A-5.1.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 321 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-5.1
KEY SUPPLIER PERSONNEL
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 322 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-5.1
Key Supplier Personnel
| |
| 1.1 | Agreement. This Schedule A-5.1 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement. |
| |
| 1.4 | General. This Schedule sets forth the Key Supplier Personnel under this Supplement. |
In accordance with Section 8.2 of the MSA, the following positions are Key Supplier Personnel positions under this Supplement and, to the extent applicable, an individual listed for a position is approved by CoreLogic to hold such position as of the Supplement Effective Date:
|
| | | |
| Key Supplier Personnel Position | Individual Approved for Position | Level of Effort | Committed Period |
| Customer Executive | *** | Full Time | *** |
| Infrastructure Customer Delivery Executive | *** | Full Time | *** |
| Deputy Infrastructure Customer Delivery Executive | TBD in accordance with Section 8.2 of the MSA. | Full Time | *** |
| Transformation Leader | *** | Full Time | *** |
| PMO Leader | TBD in accordance with Section 8.2 of the MSA. | Full Time | *** |
| Service Manager | TBD in accordance with Section 8.2 of the MSA. | Full Time | *** |
| Solution and Innovation Leader | *** | 1/3 Time | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 323 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-5.2
AFFECTED EMPLOYEES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 324 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-5.2
Affected Employees
| |
| 1.1 | Agreement. This Schedule A-5.2 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement. |
In accordance with Schedule A-5, the Affected Employees under this Supplement as of the Supplement Effective Date are as follows:
|
| |
| First Name | Last Name |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 325 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| First Name | Last Name |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 326 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| First Name | Last Name |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 327 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| First Name | Last Name |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 328 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| First Name | Last Name |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 329 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| First Name | Last Name |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 330 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| First Name | Last Name |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 331 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| First Name | Last Name |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 332 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| First Name | Last Name |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 333 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-5.3
SEVERANCE FORMULA
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 334 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-5.3
Severance Formula
| |
| 1.1 | Agreement. This Schedule A-5.3 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement. |
| |
| 1.4 | Schedules. The following Schedules are incorporated to this Schedule by reference: |
Schedule A-5.3.1 Enhanced *** Benefits
2.1 The following formulas shall be used to calculate the amount that ***will ***to ***in connection with ***of ***to a Transitioned Employee in accordance with Section 2.6 of Schedule A-5:
(a) For those Transitioned Employees set forth on Schedule A-5.3.1, the ***shall be equal to: *** (***of salary per ***of service *** *** (***) ***of salary, up to a maximum of *** (***of salary.
(b) For all other Transitioned Employees, the ***shall be equal to: *** (***) ***of salary per ***of service *** *** (***) ***of salary, up to a maximum of *** (***) ***of salary.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 335 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES
AGREEMENT
between
CORELOGIC
SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-5.3.1
ENHANCED SEVERANCE BENEFITS
|
|
| This document contains proprietary and confidential information of CoreLogic and Supplier The information contained in this document may not be disclosed outside either Party without the prior written permission of the other Party. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 336 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
1. INTRODUCTION
1.1 Agreement. This Schedule A-5.3.1 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”).
1.2 References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided.
1.3 Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 337 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| Employee Number* | Job Title** | Location | Job Title | Location |
| *** | *** | *** | *** | *** |
| *** | *** | *** | *** | *** |
| *** | *** | *** | *** | *** |
| *** | *** | *** | *** | *** |
| *** | *** | *** | *** | *** |
| *** | *** | *** | *** | *** |
| *** | *** | *** | *** | *** |
| *** | *** | *** | *** | *** |
| *** | *** | *** | *** | *** |
| | | | | |
| * Employee Number as an employee of CoreLogic or one of its Affiliates prior to the Employment Effective Date. |
| ** Job Title as an employee of CoreLogic or one of its Affiliates prior to the Employment Effective Date. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 338 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-6
RESERVED
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 339 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-7
FACILITIES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 340 |
Schedule A-7
Facilities
| |
| 1.1 | Agreement. This Schedule A-7 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement. |
| |
| 1.4 | Schedules. The following documents are attached to and incorporated by reference in this Schedule: |
Schedule A-7.1 CoreLogic Facilities
Schedule A-7.2 Supplier Facilities
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 341 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-7.1
CORELOGIC FACILITIES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 342 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
1. INTRODUCTION
1.1 Agreement. This Schedule A-7.1 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated dated July 19, 2012 (the “MSA”).
1.2 References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided.
1.3 Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement.
|
| | | | | |
| Office | Business Unit | Onsite Support Staff | Data Center CoreLogic Managed / Data Center Supplier Managed / No | Space Required for Transitioned Employees | Other Space To Be Provided |
| *** | *** | Dispatch | No | 5 cubicles | - |
| *** | *** | Dispatch | No | 1 cubicle | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | 1 cubicle | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 343 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Office | Business Unit | Onsite Support Staff | Data Center CoreLogic Managed / Data Center Supplier Managed / No | Space Required for Transitioned Employees | Other Space To Be Provided |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | 1 cubicle | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Onsite | No | 1 office and 7 cubicles | 2 cubicles and 5X5 (approximate) sq ft lockable storage closet |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | 1 cubicle | - |
| *** | *** | Dispatch | No | | - |
| *** | *** | Dispatch | No | 1 cubicle | - |
| *** | *** | Dispatch | No | 1 cubicle | - |
| *** | *** | Dispatch | No | 1 cubicle | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | 2 cubicles | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Onsite | No | - | - |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 344 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Office | Business Unit | Onsite Support Staff | Data Center CoreLogic Managed / Data Center Supplier Managed / No | Space Required for Transitioned Employees | Other Space To Be Provided |
| *** | *** | Onsite | Data Center Supplier Managed | 16 offices and 66 cubicles | 1 office space, 8 cubicles, and 20X20 (approximate) sq ft lockable storage space; One 12-person (approximate) conference room |
| *** | *** | Onsite | No | - | - |
| *** | *** | Onsite | No | - | - |
| *** | *** | Onsite | Data Center Supplier Managed | 10 offices and 59 cubicles | 9 cubicles and 10X10 (approximate) sq ft lockable storage space; One 12-person conference room |
| *** | *** | Dispatch | No | 1 cubicle | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
| *** | *** | Dispatch | No | - | - |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 345 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-7.2
SUPPLIER FACILITIES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 346 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Note: Supplier may only change locations from which it delivers Services to CoreLogic in accordance with Section 6.1(a) of the MSA. |
| | | | | | | | | | | | | | |
| Supplier Facility Name and Address | SSAE16 Facility and Controls Audit Report Provided by Supplier to its Customers | Cross Functional Services | Service Management and Security Services | Service Desk Services | Server Services | Storage Backup Services | Desktop End User Services | Data Center, Mainframe, Production Control, and Monitoring | Media Services | Network Services | Transition Services | Transformation Services | Supplier Data Center | Notes |
| *** | Yes | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | Yes | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | Yes | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 347 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Supplier Facility Name and Address | SSAE16 Facility and Controls Audit Report Provided by Supplier to its Customers | Cross Functional Services | Service Management and Security Services | Service Desk Services | Server Services | Storage Backup Services | Desktop End User Services | Data Center, Mainframe, Production Control, and Monitoring | Media Services | Network Services | Transition Services | Transformation Services | Supplier Data Center | Notes |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 348 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Supplier Facility Name and Address | SSAE16 Facility and Controls Audit Report Provided by Supplier to its Customers | Cross Functional Services | Service Management and Security Services | Service Desk Services | Server Services | Storage Backup Services | Desktop End User Services | Data Center, Mainframe, Production Control, and Monitoring | Media Services | Network Services | Transition Services | Transformation Services | Supplier Data Center | Notes |
| *** | Yes | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | Yes | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 349 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Supplier Facility Name and Address | SSAE16 Facility and Controls Audit Report Provided by Supplier to its Customers | Cross Functional Services | Service Management and Security Services | Service Desk Services | Server Services | Storage Backup Services | Desktop End User Services | Data Center, Mainframe, Production Control, and Monitoring | Media Services | Network Services | Transition Services | Transformation Services | Supplier Data Center | Notes |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
| *** | Yes | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | Pursuant to Section 6.1(a) of the MSA, Supplier will not store and process CoreLogic Data at these locations unless approved in writing by CoreLogic |
| *** | No | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 350 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | |
| Supplier Facility Name and Address | SSAE16 Facility and Controls Audit Report Provided by Supplier to its Customers | Cross Functional Services | Service Management and Security Services | Service Desk Services | Server Services | Storage Backup Services | Desktop End User Services | Data Center, Mainframe, Production Control, and Monitoring | Media Services | Network Services | Transition Services | Transformation Services | Supplier Data Center | Notes |
| *** | Yes | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | *** | |
1The following shall apply with respects to audits of the *** under Section 9.10 of the MSA and access under Sections 4.7 and 6.4 of the MSA to the Supplier Facility that is the ***, from which the *** will be performed or delivered. In the event of a conflict between this Section and the provisions of Sections 4.7, 6.4 and 9.10 of the MSA, the provisions of this Section shall control.
(a) CoreLogic, the other Eligible Recipients, their customers and Third Party Contractors shall *** to (i) the secured ***at the *** from which the*** is delivered (“Security Facilities”) and to which only *** are ***under the requirements of the Federal Financial Institutions Examination Council (“FFIEC”) and Supplier’s *** (“Restricted Security Areas”) or (ii) the leveraged *** and/or *** located within the Restricted Security Areas used to provide the *** (“Restricted Security Area Systems”). For clarity, CoreLogic shall otherwise***to such Supplier Facilities and ***the Restricted Security Area and Restricted Security Area Systems from the *** within the Supplier Facilities and access to Supplier knowledgeable personnel who can answer questions relating to ***.
(b) Documentation regarding the Restricted Security Area and Restricted Security Area Systems (e.g., the control framework and other materials audited by the FFIEC) may be examined by Permitted Auditors but may not be removed from the premises. These materials shall not be disclosed or made available to CoreLogic or Eligible Recipient customers or Permitted Auditors who are not parties to a non-disclosure agreement with either Supplier or CoreLogic that contains terms at least as restrictive as the terms set forth in Section 13.1. However, CoreLogic or Eligible Recipient customers and Permitted Auditors shall be permitted to remove *** summary documentation and collateral materials generally available to *** customers.
(c) CoreLogic may not require the installation or operation of *** on Restricted Security Area Systems.
(d) Unless otherwise approved by Supplier, (i) CoreLogic shall provide Supplier with reasonable advance notice of not less than*** days of an audit requiring access to a Security Facility, (ii) access to a Security Facility shall be limited to *** per calendar quarter and (iii) audits of the Restricted Security Area and Restricted Security Area Systems under Section 9.10(b) of the MSA shall not be conducted more than *** in any *** (***) *** period unless there has been a Security Incident ***.
(e) Subsection (d) shall not apply with respect to audits and access to a Security Facility by CoreLogic or Eligible Recipient customers required under the terms of CoreLogic’s ***. However, the Parties shall work together in good faith to minimize the number of *** and schedule *** so that they do not unreasonably interfere with Supplier’s other regulatory and SSAE 16 audit requirements.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 351 |
MASTER SERVICES AGREEMENT
by and between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-8
SOFTWARE AND EQUIPMENT INVENTORY
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 352 |
Schedule A-8
Software and Equipment Inventory
| |
| 1.1 | Agreement. This Schedule A-8 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement. |
| |
| 1.4 | Schedules. The following documents are attached to and incorporated by reference in this Schedule: |
Schedule A-8.1 Equipment Inventory
Schedule A-8.2 Supplier Tools and CoreLogic Tools
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 353 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
|
| |
| MASTER SERVICES AGREEMENT |
| between |
| CORELOGIC SOLUTIONS, LLC |
| and |
| DELL MARKETING L.P. |
| July 19, 2012 |
| |
| |
| |
| |
| |
| SUPPLEMENT A |
| |
| |
| |
| |
| |
| |
| SCHEDULE A-8.1 |
| EQUIPMENT INVENTORY |
| |
| |
| |
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 354 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
1. INTRODUCTION
1.1 Agreement. This Schedule A-8.1 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”).
1.2 References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided.
1.3 Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement.
1.4 General. This Schedule A-8.1 identifies the Equipment that, as of the Supplement Effective Date, CoreLogic will provide to Supplier in support of Supplier’s provision of the Services under this Supplement.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 355 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Servers
|
| | | | | | | | | | | | | | | | | | | | | | | |
| HostName | Location | Role | OS Type | Availability Level | HW Type | HW Level | Environment | DeviceType | VirtualDeviceType | ManufacturerName | Model | SerialNumber | AssetTagNumber | OSVersion | TotalNumberOfSockets | TotalNumberOfCores | total CPU core | RamInGB | U2L App Grouping |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530795 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530772 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530791 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530771 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530800 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530798 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530776 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530773 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530792 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530789 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530794 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530790 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530765 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530763 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530762 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530761 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530764 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Test | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | BL680c | *** | 530788 | W2003 ENT | 4 |
| 24 |
| 24 |
| 64 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Dell | 2,900 | *** | N/A | W2003 Std | 2 |
| — |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL785 | *** | 530878 | W2003 Ent | 8 |
| 4 |
| 32 |
| 128 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Large | Physical | Server | Physical | HP | BL495c | *** | 530722 | Suse Linux Ent Server 9 | 8 |
| 4 |
| 32 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Large | Physical | Server | Physical | HP | BL495c | *** | 530708 | Suse Linux Ent Server 9 | 8 |
| 4 |
| 32 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530815 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530803 | W2003 ENT | 2 |
| 1 |
| 2 |
| 68 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530818 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 356 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 357 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521558 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 358 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521555 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521556 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521557 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521016 | W2003 Ent | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521026 | W2003 Ent | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Large | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100732 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 359 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100485 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL380 | *** | 530700 | W2003 ENT | 2 |
| 8 |
| 16 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL380 | *** | 530701 | W2003 ENT | 2 |
| 8 |
| 16 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL580 | *** | 530586 | W2003 Ent | 4 |
| 6 |
| 24 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520464 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 360 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520465 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | Bluecat | Proteus 5000 | *** | 530914 | Proprietary | 1 |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | Bluecat | Adonis 750 | *** | 530908 | Proprietary | 1 |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | Bluecat | Adonis 750 | *** | 530909 | Proprietary | 1 |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521290 | Cisco VOS | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521299 | Cisco VOS | 1 |
| — |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520916 | W2003 Std | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520367 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 100962 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 316558 | W2008 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 313947 | W2008 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 316556 | W2008 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 316559 | W2008 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 316557 | W2008 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 318778 | W2008 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521428 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521427 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL585 | *** | 521515 | VMWare ESX | 4 |
| 4 |
| | | |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319126 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319131 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319127 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL580 | *** | 521397 | Red Hat Enterprise Server 4 | — |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | Dell | PowerEdge 1850 | *** | 521416 | W2003 Std | 2 |
| 1 |
| 2 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | Dell | PowerEdge 750 | *** | 521419 | W2003 Ent | 1 |
| 1 |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | Fujitsu | PP450 | *** | 522966 | Solaris | 4 |
| — |
| 4 |
| | Misc |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | 4 |
| 4 |
| 5 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 361 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520809 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520811 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL685c | *** | 530743 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 362 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Redhat 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v480 | *** | N/A | Solaris | 2 |
| 2 |
| 4 |
| | Infra |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100731 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530591 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530594 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | IBM | x3550 | *** | 521654 | W2003 Ent | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL380 | *** | 530356 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 100958 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 100959 | Red Hat Enterprise Server 5 | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 363 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520166 | W2000 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520485 | W2003 Std | 2 |
| 1 |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530975 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530969 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531011 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Staging | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | QA | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522452 | W2000 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DeskPro | *** | 520846 | W2000 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 364 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL740 | *** | 313585 | W2003 Ent | 8 |
| 4 |
| 32 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL585 | *** | 530573 | Red Hat Enterprise Server 4 | 16 |
| 16 |
| 16 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | Bluecat | Adonis 750 | *** | 101661 | Proprietary | 1 |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | HP | DL380 | *** | 500366 | Cisco VOS | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | HP | DL380 | *** | 500367 | Cisco VOS | 3 |
| — |
| 3 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 523127 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Development | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL495c | *** | 530623 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 4 |
| 64 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | Bluecat | Adonis 750 | *** | 530912 | Proprietary | 1 |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | Bluecat | Adonis 750 | *** | 531046 | Proprietary | 1 |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | Bluecat | Adonis 750 | *** | 530911 | Proprietary | 1 |
| — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL380 | *** | 520420 | VMWare ESX | 2 |
| 2 |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521620 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Lantronix | SLC32 | *** | 520484 | Solaris | | — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL385 | *** | 520230 | Red Hat Enterprise Server 4 | | — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL385 | *** | 520220 | Red Hat Enterprise Server 4 | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Lantronix | SCS1620 | *** | 521523 | Solaris | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Web | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Web | 1 |
| 1 |
| 1 |
| 2 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 365 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530660 | Solaris | 2 |
| 8 |
| | 32 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530663 | Solaris | 2 |
| 8 |
| | 32 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530661 | Solaris | 2 |
| 8 |
| | 32 |
| Service Tier |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 366 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530476 | W2003 Std | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 530563 | W2008 Ent | 2 |
| 8 |
| 16 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 530560 | W2008 Ent | 2 |
| 8 |
| 16 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL460c | *** | 530441 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL460c | *** | 530408 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL460c | *** | 530413 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 101027 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | DR | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | C600 | *** | 100570 | | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 524083 | W2003 Std | 2 |
| 1 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522316 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V240 | *** | 507690 | Solaris | 2 |
| — |
| 2 |
| | Infra |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522357 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522378 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522543 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 524115 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522467 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522383 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 524086 | W2003 Std | 2 |
| 2 |
| 4 |
| 3 |
| |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522506 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522414 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL580 | *** | 524088 | W2003 Std | 4 |
| 4 |
| 16 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 367 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530468 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530486 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530420 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530519 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530923 | VMWare ESX | 4 |
| 4 |
| | 62 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521351 | W2003 STD | 2 |
| — |
| 2 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 313984 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 530946 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 530947 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 313981 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 313982 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521535 | W2003 Std | 2 |
| 1 |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521534 | W2003 Std | 2 |
| 1 |
| 2 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 313983 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520197 | W2003 Ent | 2 |
| 1 |
| 2 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521293 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521291 | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521300 | W2003 Std | 1 |
| — |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521276 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521285 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521277 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 368 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 369 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL480c | *** | 100657 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100030 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100705 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100719 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100655 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101329 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101330 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101331 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 370 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101332 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL380 | *** | 520518 | VMWare ESX | 2 |
| 2 |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL380 | *** | 520519 | VMWare ESX | 2 |
| 2 |
| | | |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | Fujitsu | PP650 | *** | 520114 | Solaris | 4 |
| 8 |
| | 32 |
| Infra |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521430 | VMWare ESX | 4 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521426 | VMWare ESX | 4 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521424 | VMWare ESX | 4 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521473 | VMWare ESX | 4 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 524070 | Red Hat Enterprise Server 3 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | MS Host | HP | BL460c | *** | 520911 | W2003 Ent | 2 |
| 4 |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 507966 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520623 | W2003 Web | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520627 | W2003 Web | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521344 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521434 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101565 | W2003 STD | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101566 | W2003 STD | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2008 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2008 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 500533 | Red Hat Enterprise Server 3 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 500531 | Red Hat Enterprise Server 3 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | Google | GB-1001 | *** | 100956 | Proprietary | 2 |
| — |
| | | |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | Fujitsu | PP650 | *** | 522275 | Solaris | 4 |
| 8 |
| | 32 |
| Infra |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 371 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 530753 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 530748 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 530756 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 530749 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | xw460c | *** | 530750 | WXP | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 521856 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | xw460c | *** | 521857 | WXP | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521326 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521327 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 372 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| — |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | Dell | PowerEdge 750 | *** | 521417 | W2003 Std | 1 |
| 1 |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521413 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL465c | *** | 100044 | VMWare ESX | 2 |
| 4 |
| | | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | IBM | xSeries 342 | *** | 316967 | W2000 Std | 1 |
| 1 |
| 1 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | IBM | xSeries 345 | *** | 316970 | W2000 Std | 1 |
| 1 |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522417 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 522456 | Red Hat Enterprise Server 3 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 522388 | Red Hat Enterprise Server 3 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 522663 | Red Hat Enterprise Server 3 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 373 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520127 | W2003 STD | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520132 | W2003 STD | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521569 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522621 | W2003 Std | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522520 | W2003 Std | 2 |
| — |
| 2 |
| 2 |
| |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522558 | W2003 STD | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530820 | W2003 Std | 2 |
| 1 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530804 | W2003 Std | 2 |
| 1 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL680c | *** | 530797 | W2003 ENT | 4 |
| 1 |
| 4 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530807 | W2003 ENT | 2 |
| 1 |
| 2 |
| 24 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530822 | W2003 ENT | 2 |
| 1 |
| 2 |
| 24 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530816 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530808 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530802 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530805 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530813 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530821 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530924 | VMWare ESX | 4 |
| 4 |
| | 62 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530927 | VMWare ESX | 4 |
| 4 |
| | 62 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530926 | VMWare ESX | 4 |
| 4 |
| | 62 |
| |
| *** | SATC | Development | Windows | Low | Physical | Extra Large | Physical | Server | PHYSICAL | HP | BL685c | *** | 521641 | W2008 Ent | 4 |
| 4 |
| 4 |
| 256 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL685c | *** | 530731 | Red Hat Enterprise Server 4 | | 4 |
| 4 |
| 64 |
| |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 374 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 375 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521846 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521847 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521848 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 376 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521849 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521850 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521851 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 521788 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521845 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL785 | *** | 530562 | W2008 Ent | 8 |
| 4 |
| 32 |
| 256 |
| |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521646 | W2008 Ent | 2 |
| 8 |
| 16 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 521644 | Red Hat Enterprise Server 5 | 4 |
| — |
| 4 |
| 64 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | C650 | *** | 521800 | Proprietary | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | C350 | *** | 521801 | Proprietary | | — |
| | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521647 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521643 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521642 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521645 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521648 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL685c | *** | 521517 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL685c | *** | 521516 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 377 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 STD | — |
| — |
| | 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521778 | W2003 STD | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 521739 | Red Hat Enterprise Server 5 | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521737 | VMware ESX | 4 |
| 16 |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | N/A | — |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | N/A | — |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | N/A | — |
| — |
| | | |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100486 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100493 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100699 | W2003 ENT | 2 |
| 4 |
| 8 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100504 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100672 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100736 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 378 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100670 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 5 |
| |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100734 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100696 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100487 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100475 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100488 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100769 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Training | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100484 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100594 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL320 | *** | 101469 | W2003 STO | 1 |
| 4 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100856 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100853 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 100936 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL580 | *** | 100937 | W2003 ENT | 4 |
| 4 |
| 16 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | HP | HP PRINT SERVER APPLIANCE | *** | 316958 | Proprietary | | — |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL480c | *** | 100700 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL480c | *** | 100156 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL740 | *** | 318274 | W2003 ENT | 8 |
| 8 |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318280 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100839 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | HP | HP PRINT SERVER APPLIANCE | *** | 100649 | Proprietary | | — |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318276 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100844 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 7 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 379 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531085 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 531007 | W2003 Std | 2 |
| — |
| 2 |
| 64 |
| |
| *** | SATC | QA | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 531018 | W2003 Std | 2 |
| — |
| 2 |
| 64 |
| |
| *** | SATC | Development | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 530994 | W2003 Std | 2 |
| — |
| 2 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 531005 | W2003 Std | 2 |
| — |
| 2 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 530997 | W2003 Std | 2 |
| — |
| 2 |
| 64 |
| |
| *** | SATC | QA | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 531008 | W2003 Std | 2 |
| — |
| 2 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101550 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101542 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101546 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520250 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 521301 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520255 | W2003 Std | 2 |
| — |
| 2 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 380 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520252 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 522377 | Red Hat Enterprise Server 3 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Unix - Solaris | Low | Virtual | N/A | Shared | Server | LPAR | Fujitsu | M4000 | *** | N/A | Solaris | — |
| — |
| | | Misc |
| *** | DTC | Test | Unix - Solaris | Low | Virtual | N/A | Shared | Server | LPAR | Fujitsu | M4000 | *** | N/A | Solaris | — |
| — |
| | | Misc |
| *** | DTC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Unix Host | Fujitsu | M4000 | *** | 101643 | Proprietary | | — |
| 1 |
| | Tax |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| 1.6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 381 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7835 | *** | 319144 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521380 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7835 | *** | 319143 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 530680 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 ENT | 2 |
| 2 |
| 2 |
| 7 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 382 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Lantronix | SCS1620 | *** | 521601 | | 1 |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | M1050 | *** | 521579 | Proprietary | 2 |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | DR | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520096 | Red Hat Enterprise Server 3 | 4 |
| — |
| 4 |
| 4 |
| |
| *** | SATC | DR | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520094 | Red Hat Enterprise Server 3 | 4 |
| — |
| 4 |
| 4 |
| |
| *** | SATC | DR | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520095 | Red Hat Enterprise Server 3 | 4 |
| — |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522596 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 523157 | W2003 STD | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522643 | W2003 STD | 2 |
| — |
| 2 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 383 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520260 | W2003 STD | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | PHYSICAL | Fujitsu | PP450 | *** | 520591 | Solaris | 4 |
| — |
| 4 |
| | Oracle Fin |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522642 | W2003 STD | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520753 | W2003 STD | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522644 | W2003 STD | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL580 | *** | 522539 | W2003 STD | 4 |
| 4 |
| 16 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | N/A | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | N/A | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL380 | *** | 530357 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 313556 | W2008 Web R2 | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 313557 | W2008 Web R2 | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 316707 | W2008 Ent | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530595 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL580 | *** | 530577 | W2003 Ent | 4 |
| 6 |
| 24 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL580 | *** | 530585 | W2003 Ent | 4 |
| 6 |
| 24 |
| 64 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 384 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530655 | Solaris | 1 |
| 4 |
| 4 |
| 16 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530654 | Solaris | 1 |
| 4 |
| 4 |
| 32 |
| Service Tier |
| *** | DTC | DR | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | SUN | V440 | *** | 312480 | Solaris | 4 |
| — |
| 4 |
| 8 |
| Service Tier |
| *** | DTC | DR | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | SUN | V440 | *** | 312481 | Solaris | 4 |
| — |
| 4 |
| 8 |
| Service Tier |
| *** | DTC | DR | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | SUN | V440 | *** | 312482 | Solaris | 4 |
| — |
| 4 |
| 8 |
| Service Tier |
| *** | DTC | DR | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | SUN | V440 | *** | 312483 | Solaris | 4 |
| — |
| 4 |
| 8 |
| Service Tier |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | MS Host | HP | BL460c | *** | 520917 | W2003 Ent | 2 |
| 4 |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100029 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100477 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL25P | *** | 100687 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100509 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100510 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100806 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100805 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100614 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 316864 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100833 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100808 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100807 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 385 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100624 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 316865 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100548 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Development | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL585 | *** | 318693 | VMWare ESX | 2 |
| 4 |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100159 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100160 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100170 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100690 | W2003 ENT | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520188 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100552 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100557 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100706 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100795 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100796 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100797 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520187 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 312578 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 101558 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 STD | — |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101548 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101538 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101549 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101541 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101551 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 386 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server | 1 |
| 1 |
| 1 |
| 12 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 6 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | DTC | Staging | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100151 | Red Hat Enterprise Server 4 | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 100867 | W2003 STD | 4 |
| 2 |
| 8 |
| | |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100161 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100162 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 100648 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100470 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100558 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100471 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100474 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100476 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100489 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Unix - Solaris | Low | Physical | Small | Physical | Server | PHYSICAL | SUN | V20Z | *** | 523006 | Solaris | 2 |
| — |
| 2 |
| | Oracle Fin |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | PHYSICAL | SUN | V20Z | *** | 523001 | Solaris | 2 |
| — |
| 2 |
| | Oracle Fin |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 520123 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530592 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530593 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| — |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 387 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 4 |
| 4 |
| 4 |
| 5 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 4 |
| 4 |
| 4 |
| 5 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 4 |
| 4 |
| 4 |
| 5 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL580 | *** | 521311 | Red Hat Enterprise Server 4 | 8 |
| — |
| 8 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | Cisco | MCS 7835 | *** | 521331 | W2003 STD | 2 |
| — |
| 2 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520993 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520992 | W2008 Ent | 1 |
| 4 |
| 4 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520991 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520996 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520995 | W2008 Ent | 1 |
| 4 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520994 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520990 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530719 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 388 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530704 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530715 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530705 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530714 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Dell | 2,900 | *** | N/A | W2003 Std | 2 |
| — |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Dell | 2,900 | *** | N/A | W2003 Std | 2 |
| — |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 100725 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 389 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521296 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 523111 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 531754 | Red Hat Enterprise Server 5 | 4 |
| — |
| 4 |
| 12 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100688 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL25P | *** | 100684 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL25P | *** | 100686 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100640 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100651 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL580 | *** | 100659 | W2003 ENT | 4 |
| 8 |
| 8 |
| | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL465c | *** | 100971 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521669 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520581 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 390 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520583 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520586 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 522329 | Red Hat Enterprise Server 4 | 2 |
| — |
| | | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Suse | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530977 | VMWare ESX | 4 |
| 4 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530978 | VMWare ESX | 4 |
| 4 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530979 | VMWare ESX | 4 |
| 4 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530980 | VMWare ESX | 4 |
| 4 |
| | 128 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530724 | Suse Linux Ent Server 9 | 1 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530711 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530720 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530709 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530706 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530690 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 391 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530682 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530692 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530688 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530625 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530723 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530717 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530721 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530707 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530686 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530691 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530683 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530710 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530713 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530718 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530716 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL495c | *** | 530629 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 64 |
| |
| *** | SATC | Test | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL495c | *** | 530632 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 64 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530634 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 1 |
| — |
| 1 |
| 0.5 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100717 | W2003 WEB | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100503 | W2003 WEB | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100495 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100671 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100698 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 392 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100500 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100501 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100161 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL685c | *** | 521021 | W2008 Ent | 4 |
| 8 |
| 8 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL685c | *** | 521031 | W2008 Ent | 4 |
| 8 |
| 8 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Web | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Web | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520626 | W2003 Web | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520625 | W2003 Web | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520624 | W2003 Web | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL685c | *** | 520649 | W2003 Ent | 4 |
| 8 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520458 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520459 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520462 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520463 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520460 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520461 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 523124 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Staging | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522646 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521533 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521532 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL585 | *** | 520456 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520457 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 316681 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 523126 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V240 | *** | 500651 | Solaris | 1 |
| — |
| 1 |
| | Infra |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | WNT | 1 |
| 1 |
| 1 |
| 2 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 393 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Development | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | xw460c | *** | 530751 | WXP | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | xw460c | *** | 530752 | WXP | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 530755 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 530754 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 316835 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 316839 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | Proprietary | — |
| — |
| | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530694 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530689 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530684 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530695 | Suse Linux Ent Server 9 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 394 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL580 | *** | 530570 | W2003 Ent | 4 |
| 6 |
| 24 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 12 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | BlueCat | Adonis 750 | *** | 101657 | Proprietary | 1 |
| — |
| | | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | BlueCat | Adonis 750 | *** | 101658 | Proprietary | 1 |
| — |
| | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 524058 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 522354 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521564 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521565 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 520466 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 520467 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 522537 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 507748 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521568 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521561 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521562 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521559 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521560 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521563 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521570 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521571 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 521566 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 505569 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521567 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100708 | W2003 STD | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100709 | W2003 STD | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530665 | Solaris | 2 |
| 4 |
| 8 |
| 32 |
| Service Tier |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 395 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Netscout | nGenius Probe | *** | 521283 | | 1 |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Netscout | nGenius Probe | *** | 521304 | | 1 |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 100713 | W2008 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 100716 | W2008 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 100715 | W2008 Std | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101564 | W2003 STD | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL585 | *** | 100875 | VMWare ESX | 4 |
| — |
| | | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL585 | *** | 100874 | VMWare ESX | 4 |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100721 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 100595 | W2003 ENT | 2 |
| 8 |
| 16 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100565 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100577 | W2008 ENT | 1 |
| 4 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100643 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100654 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 396 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL685c | *** | 530732 | Red Hat Enterprise Server 4 | | 4 |
| 4 |
| 64 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL685c | *** | 530747 | Red Hat Enterprise Server 4 | | 4 |
| 4 |
| 64 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL685c | *** | 530733 | Red Hat Enterprise Server 4 | | 4 |
| 4 |
| 64 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530729 | Red Hat Enterprise Server 4 | | 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530726 | Red Hat Enterprise Server 4 | | 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530727 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530728 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530650 | Solaris | 1 |
| 4 |
| 4 |
| 32 |
| Service Tier |
| *** | SATC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530653 | Solaris | 1 |
| 4 |
| 4 |
| 32 |
| Service Tier |
| *** | SATC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530649 | Solaris | 1 |
| 4 |
| 4 |
| 32 |
| Service Tier |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521292 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520253 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | Dell | PowerEdge 1850 | *** | 530879 | Red Hat Enterprise Server | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520406 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520407 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520257 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520256 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7835 | *** | 521281 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521268 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520258 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520251 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520254 | W2003 Std | 2 |
| — |
| 2 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 397 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520249 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100468 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100492 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100697 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100597 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Cistera | CS 2500 | *** | 521294 | | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7835 | *** | 521295 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521273 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Mirapoint | DS500 | *** | 520531 | Proprietary | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 316680 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Mirapoint | DS450 | *** | 316674 | Proprietary | 2 |
| — |
| | | |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V240 | *** | 523023 | Solaris | 2 |
| — |
| 2 |
| | Misc |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522429 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522439 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522328 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen host | HP | BL460c | *** | 530414 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen host | HP | BL460c | *** | 530423 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | V210 | *** | 523028 | Solaris | 2 |
| — |
| 2 |
| | Service Tier |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | SUN | V210 | *** | 523012 | Solaris | 2 |
| — |
| 2 |
| | Service Tier |
| *** | SATC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522300 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522384 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 524112 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Lantronix | SCS1620 | *** | 520835 | Sys Console Linux | 1 |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 7 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318279 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318282 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100842 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 398 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100931 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 101494 | VMWare ESX | 4 |
| 8 |
| | | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 101485 | VMWare ESX | 4 |
| 8 |
| | | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 101490 | VMWare ESX | 4 |
| 8 |
| | | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 101491 | VMWare ESX | 4 |
| 8 |
| | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 318304 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101497 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL45P | *** | 100166 | W2003 ENT | 4 |
| 4 |
| 16 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL45P | *** | 100165 | W2003 ENT | 4 |
| 4 |
| 16 |
| | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522592 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522623 | W2003 Std | 2 |
| 2 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 524339 | Red Hat Enterprise Server 3 | 2 |
| — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 524342 | Red Hat Enterprise Server 4 | 2 |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | �� |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 ENT | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 ENT | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 6 |
| 6 |
| 6 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521790 | W2008 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521791 | W2008 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521796 | W2008 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 531052 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521765 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521793 | W2008 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521794 | W2008 STD | 1 |
| 4 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521766 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 399 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521773 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521760 | W2008 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521770 | W2008 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521769 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521771 | W2008 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 100593 | W2003 ENT | 2 |
| 8 |
| 16 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100733 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100694 | W2003 ENT | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318295 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318291 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318290 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100511 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100512 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL25P | *** | 100675 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL45P | *** | 100676 | W2003 ENT | 4 |
| 4 |
| 16 |
| | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100490 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Dell | PowerEdge 2850 | *** | 530351 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 400 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 100042 | W2000 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 520725 | W2000 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 100043 | W2000 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 520738 | W2000 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 520703 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 100964 | W2000 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530757 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Test | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | BL680c | *** | 530759 | W2003 ENT | 4 |
| 24 |
| 24 |
| 64 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 318696 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100495 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL580 | *** | 521876 | W2008 ENT | 4 |
| 24 |
| 24 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL580 | *** | 521877 | W2008 ENT | 4 |
| 24 |
| 24 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521889 | W2003 ENT | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521885 | W2003 ENT | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 521892 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 521891 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 521888 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 521890 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 521886 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 401 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Physical | HP | BL460c | *** | 521896 | VMWare ESX | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 521884 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 521887 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 521895 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 1 |
| 1 |
| 1 |
| 0.5 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Advanced Server | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 402 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | SUN | V245 | *** | 521484 | Solaris | 2 |
| — |
| 2 |
| | Infra |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 403 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Advanced Server | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL580 | *** | 521539 | W2003 Ent | 4 |
| 16 |
| 16 |
| 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 521470 | VMWare ESX | 4 |
| 16 |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 521465 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 521467 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 521468 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Mainframe | N/A | Physical | N/A | Physical | Server | Physical | IBM | Z-Series 2098 | *** | 530863 | z/OS 1.10 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | IBM | x335 | *** | 521508 | W2003 Ent | | — |
| 1 |
| | |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | Fujitsu | T5220 | *** | 521482 | Solaris 10 | 1 |
| 8 |
| | 32 |
| Infra |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 521469 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521471 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521474 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521475 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521476 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 521466 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | Sun | V240 | *** | 521459 | Solaris | 2 |
| — |
| 2 |
| | Infra |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | Sun | V240 | *** | 521458 | Solaris | 2 |
| — |
| 2 |
| | Infra |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521022 | W2003 Std | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521032 | W2003 Std | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521023 | W2003 Std | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521033 | W2003 Std | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521017 | W2008 Ent | 2 |
| 8 |
| 16 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521035 | W2008 Ent | 2 |
| 8 |
| 16 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530213 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530215 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530244 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521025 | W2008 Web R2 | 2 |
| 4 |
| 8 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 404 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521018 | W2003 Std | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530216 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530220 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530217 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530214 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530212 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530218 | Suse Linux Ent Server 9 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 531751 | W2003 Ent | 2 |
| — |
| 2 |
| 12 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 405 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | QA | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530406 | W2008 Ent | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | QA | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530398 | W2008 Ent | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530516 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530494 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530513 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530422 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530631 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530633 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530712 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530636 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530635 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530451 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530394 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530506 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530412 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 316614 | W2003 Std | 2 |
| 1 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530532 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530424 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530400 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V240 | *** | 520525 | Solaris | 2 |
| — |
| 2 |
| | Infra |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V240 | *** | 520526 | Solaris | 2 |
| — |
| 2 |
| | Infra |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 316665 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | QA | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530644 | Solaris | 1 |
| 4 |
| 4 |
| 16 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530656 | Solaris | 1 |
| 4 |
| 4 |
| 16 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530657 | Solaris | 1 |
| 4 |
| 4 |
| 16 |
| Service Tier |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 406 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | Dell | N/A | *** | 318697 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | Dell | N/A | *** | 318698 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | Dell | N/A | *** | 318700 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100467 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100499 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100473 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 7 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 7 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | PP250 | *** | 521373 | Solaris | 1 |
| — |
| 1 |
| | Service Tier |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 522332 | Red Hat Advanced Server | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Mainframe | N/A | Physical | N/A | Physical | Server | Physical | IBM | Z-Series 2098 | *** | 530862 | z/OS 1.10 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 522446 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 407 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | Fujitsu | T5220 | *** | 530294 | Solaris | 1 |
| 8 |
| | 4 |
| Infra |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | Fujitsu | T5220 | *** | 530296 | Solaris | 1 |
| 8 |
| | 4 |
| Infra |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530918 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530920 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530919 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531051 | W2008 Std | 2 |
| 4 |
| 8 |
| 12 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531036 | W2008 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531037 | W2008 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 313826 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Advanced Server | | — |
| 1 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | BlueCat | Adonis 750 | *** | 101659 | Proprietary | 1 |
| — |
| | | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | BlueCat | Adonis 750 | *** | 101660 | Proprietary | 1 |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 507948 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 507937 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 507945 | W2003 Ent | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 507944 | W2003 Ent | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | Dell | PowerEdge 1750 | *** | 520843 | W2000 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 520293 | Suse Linux Ent Server 10 | | — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 408 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL465c | *** | 100961 | VMWare ESX | 2 |
| 4 |
| | | |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL465c | *** | 100968 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| | | |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL465c | *** | 100969 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| | | |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL465c | *** | 100970 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| | | |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL465c | *** | 100972 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| | | |
| *** | DTC | Test | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100150 | Red Hat Enterprise Server 4 | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100171 | Red Hat Enterprise Server 4 | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL25p | *** | 100125 | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Staging | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100152 | Red Hat Enterprise Server 5 | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Staging | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 409 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100119 | Solaris | 1 |
| 1 |
| 1 |
| | Tax |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100110 | Solaris | 1 |
| 1 |
| 1 |
| | Tax |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL25p | *** | 100136 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100153 | Red Hat Enterprise Server 4 | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100154 | Red Hat Enterprise Server 4 | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 101414 | Red Hat Enterprise Server 4 | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Development | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL25p | *** | 100134 | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Development | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100149 | Red Hat Enterprise Server 4 | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Unix - Solaris | Low | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100108 | Solaris 9 | 1 |
| 1 |
| 1 |
| | Tax |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100105 | Solaris | 2 |
| 1 |
| 2 |
| | Misc |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v100 | *** | 312144 | Solaris | 1 |
| 1 |
| 1 |
| | Misc |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 100615 | Red Hat Enterprise Server | 4 |
| 2 |
| 8 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL25p | *** | 100666 | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100932 | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 100617 | Red Hat Enterprise Server | 4 |
| 2 |
| 8 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 100868 | Red Hat Enterprise Server | 4 |
| 2 |
| 8 |
| | |
| *** | DTC | Production | Unix - Solaris | Standard | Virtual | N/A | Shared | Server | LPAR | Fujitsu | M5000 | *** | N/A | Solaris | | 8 |
| | | Misc |
| *** | DTC | Production | Unix - Solaris | Standard | Virtual | N/A | Shared | Server | LPAR | Fujitsu | M5000 | *** | N/A | Solaris | | 4 |
| | | Misc |
| *** | DTC | Production | Unix - Solaris | Standard | Virtual | Medium | Shared | Server | LPAR | Fujitsu | M5000 | *** | N/A | Solaris | 12 |
| 1 |
| | | Oracle Fin |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v480 | *** | 312153 | Solaris | 2 |
| 2 |
| 4 |
| | Infra |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 410 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100727 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | Dell | N/A | *** | 318699 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | Dell | N/A | *** | 100668 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | Dell | N/A | *** | 100669 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100703 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100505 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100506 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100472 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100466 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100701 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100491 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100496 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100574 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100498 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 318159 | W2003 STD | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 316872 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL45P | *** | 100677 | W2003 ENT | 4 |
| 4 |
| 16 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100515 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100641 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100652 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL580 | *** | 314305 | W2003 Ent | 4 |
| — |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530810 | W2003 ENT | 2 |
| 12 |
| 12 |
| 32 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 411 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Large | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 31 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530782 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530785 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530779 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530780 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530783 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530799 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530784 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530786 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530796 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530778 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530774 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530777 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | Dell | PowerEdge 2850 | *** | 521303 | Red Hat Enterprise Server | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Netscout | nGenius Probe | *** | 521272 | | 1 |
| — |
| | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 412 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL380 | *** | 520421 | VMWare ESX | 2 |
| 2 |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520129 | W2003 STD | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520124 | W2003 STD | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL580 | *** | 521878 | W2008 ENT | 4 |
| 24 |
| 24 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | BL685c | *** | 520648 | W2003 Ent | 4 |
| 8 |
| 32 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | MS Host | HP | BL460c | *** | 520629 | W2003 Ent | 2 |
| 4 |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530379 | Solaris | 1 |
| 4 |
| 4 |
| 16 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530381 | Solaris | 1 |
| 4 |
| 4 |
| 16 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530382 | Solaris | 2 |
| 8 |
| | 16 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530872 | Solaris | 2 |
| 4 |
| 8 |
| 32 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530662 | Solaris | 2 |
| 4 |
| 8 |
| 32 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | T5220 | *** | 530295 | Solaris | 1 |
| 4 |
| 4 |
| 8 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Medium | Physical | Server | Physical | Fujitsu | M5000 | *** | 530358 | Solaris | 4 |
| 16 |
| | 48 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Medium | Physical | Server | Physical | Fujitsu | M5000 | *** | 530359 | Solaris | 4 |
| 16 |
| | 48 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Medium | Physical | Server | Physical | Fujitsu | M5000 | *** | 530360 | Solaris | 4 |
| 16 |
| | 48 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Medium | Physical | Server | Physical | Fujitsu | M5000 | *** | 530361 | Solaris | 4 |
| 16 |
| | 48 |
| Service Tier |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 12 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530383 | Solaris | 2 |
| 8 |
| | 16 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530385 | Solaris | 2 |
| 8 |
| | 16 |
| Service Tier |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530645 | Solaris | 1 |
| 4 |
| 4 |
| 16 |
| Service Tier |
| *** | SATC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530647 | Solaris | 1 |
| 4 |
| 4 |
| 16 |
| Service Tier |
| *** | SATC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530648 | Solaris | 1 |
| 4 |
| 4 |
| 32 |
| Service Tier |
| *** | DTC | Test | Unix - Solaris | Low | Physical | Small | Physical | Server | Unix Host | Fujitsu | M5000 | *** | 101644 | Proprietary | | — |
| 1 |
| | Tax |
| *** | DTC | Test | Unix - Solaris | Low | Physical | Small | Physical | Server | Unix Host | Fujitsu | M4000 | *** | 101646 | Proprietary | | — |
| 1 |
| | Tax |
| *** | DTC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Unix Host | Fujitsu | M5000 | *** | 101645 | Proprietary | | — |
| 1 |
| | Tax |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | Unix Host | Fujitsu | M5000 | *** | 101648 | Proprietary | | — |
| 1 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | Unix Host | Fujitsu | M5000 | *** | 101647 | Proprietary | | — |
| 1 |
| | |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 32 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 32 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 413 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | T5120 | *** | 530907 | Solaris | — |
| — |
| 1 |
| | Oracle Fin |
| *** | SATC | DR | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | T5120 | *** | 530906 | Solaris | — |
| — |
| 1 |
| | Oracle Fin |
| *** | SATC | DR | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | T5120 | *** | 530905 | Solaris | — |
| — |
| 1 |
| | Oracle Fin |
| *** | SATC | DR | Unix - Solaris | Low | Virtual | Medium | Shared | Server | LPAR | Fujitsu | M5000 | *** | N/A | Solaris | 8 |
| — |
| | | Oracle Fin |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530970 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531013 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530972 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531019 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531009 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530993 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531006 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531020 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530996 | Suse Linux Ent Server 9 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | | | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | | | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | | | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 414 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 101637 | W2003 Std | 2 |
| — |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 101638 | W2003 Std | 2 |
| — |
| 2 |
| 4 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530664 | Solaris | 2 |
| 4 |
| 8 |
| 32 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530384 | Solaris | 2 |
| 8 |
| | 16 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530386 | Solaris | 2 |
| 8 |
| | 16 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530387 | Solaris | 2 |
| 8 |
| | 16 |
| Service Tier |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 530555 | Red Hat Enterprise Server 5 | | — |
| 4 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 530542 | Red Hat Enterprise Server 5 | | — |
| 4 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530651 | Solaris | 1 |
| 4 |
| 4 |
| 32 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530643 | Solaris | 1 |
| 4 |
| 4 |
| 16 |
| Service Tier |
| *** | SATC | QA | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530646 | Solaris | 1 |
| 4 |
| 4 |
| 16 |
| Service Tier |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | C650 | *** | 520894 | Proprietary | 2 |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | M1050 | *** | 520898 | Proprietary | 2 |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | C650 | *** | 521518 | Proprietary | 2 |
| — |
| | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 520833 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520313 | W2003 STD | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520128 | W2003 STD | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520877 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520878 | W2003 STD | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520879 | W2003 STD | | — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 415 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 316655 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL385 | *** | 520376 | Red Hat Enterprise Server | 2 |
| — |
| | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520374 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL385 | *** | 520528 | Red Hat Enterprise Server 4 | 2 |
| — |
| | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 520121 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 520122 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 520120 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 520119 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| | |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL385 | *** | 520207 | Red Hat Enterprise Server 4 | 2 |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520588 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520589 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 416 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | WXP | 1 |
| — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 522924 | Red Hat Enterprise Server 5 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Web R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | BL685c | *** | 521542 | W2003 Ent | 4 |
| 8 |
| 32 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | BL685c | *** | 521543 | W2003 Ent | 4 |
| 8 |
| 32 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL585 | *** | 520578 | W2003 Ent | 4 |
| 8 |
| 32 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL585 | *** | 520590 | W2003 Ent | 4 |
| 8 |
| 32 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | MS Host | HP | BL460c | *** | 520918 | W2003 DC | 2 |
| 4 |
| | | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522923 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522922 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520560 | Red Hat Enterprise Server 5 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520576 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520903 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520909 | W2008 Ent R2 | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520905 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520899 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | DR | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | DL580 | *** | 520203 | W2003 Ent | 4 |
| 4 |
| 16 |
| | |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | PP250 | *** | 520592 | Solaris | 2 |
| — |
| 2 |
| | Service Tier |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 101500 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 417 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 101499 | VMWare ESX | 4 |
| 8 |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100644 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100656 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100564 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100718 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 100613 | VMWare ESX | 4 |
| 8 |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100590 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100563 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL580 | *** | 100838 | W2003 ENT | 4 |
| 8 |
| 32 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL580 | *** | 100847 | W2003 ENT | 4 |
| 8 |
| 32 |
| | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL740 | *** | 318272 | VMWare ESX | 4 |
| 8 |
| | | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL740 | *** | 318271 | VMWare ESX | 4 |
| 8 |
| | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100945 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100835 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318283 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318284 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318285 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318286 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318287 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100942 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 101313 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318289 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100943 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318294 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318293 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318292 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 418 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100567 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100730 | W2003 WEB | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100502 | W2003 WEB | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522569 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 520487 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 520489 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520486 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520770 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 520766 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 520756 | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 520760 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 419 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 4 |
| 4 |
| 4 |
| 5 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 4 |
| 4 |
| 4 |
| 5 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL385 | *** | 520377 | VMWare ESX | 2 |
| 2 |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520178 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520177 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL685c | *** | 530538 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521638 | VMWare ESX | 4 |
| 16 |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Std | — |
| — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521636 | VMWare ESX | 4 |
| 16 |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521635 | VMWare ESX | 4 |
| 16 |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521640 | VMWare ESX | 4 |
| 16 |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521639 | VMWare ESX | 4 |
| 16 |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521637 | VMWare ESX | 4 |
| 16 |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | DR | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V480 | *** | 507678 | Solaris | 2 |
| — |
| 2 |
| | Tax |
| *** | SATC | DR | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V490 | *** | 313979 | Solaris | 4 |
| — |
| 4 |
| | Tax |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 420 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | DR | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V480 | *** | 316987 | Solaris | 4 |
| — |
| 4 |
| | Tax |
| *** | SATC | DR | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V480 | *** | 316992 | Solaris | 4 |
| — |
| 4 |
| | Tax |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100691 | W2003 ENT | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100156 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100157 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100158 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL480c | *** | 521005 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Staging | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL480c | *** | 521004 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7825 | *** | 521990 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V490 | *** | 313980 | Solaris | 4 |
| — |
| 4 |
| | Tax |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 421 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521672 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | MS Host | HP | DL380 | *** | 521670 | W2003 Std | 2 |
| 8 |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | MS Host | HP | DL380 | *** | 521671 | W2003 Std | 2 |
| 4 |
| | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL580 | *** | 520455 | W2003 Std | 4 |
| 4 |
| 16 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Std | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520173 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL385 | *** | 520370 | Red Hat Enterprise Server 4 | 2 |
| — |
| | | |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100099 | Solaris | 1 |
| 1 |
| 1 |
| | Tax |
| *** | DTC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100106 | Solaris | 1 |
| 1 |
| 1 |
| | Tax |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Physical | HP | DL380 | *** | 520513 | VMWare ESX | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520512 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520516 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520517 | W2003 ENT | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520520 | W2003 ENT | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520522 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530219 | Suse | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530211 | Suse | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530210 | Suse | | — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 422 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | Sun | V240 | *** | 520402 | Solaris | 2 |
| — |
| 2 |
| | Infra |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | Sun | V240 | *** | 520403 | Solaris | 2 |
| — |
| 2 |
| | Infra |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | Fujitsu | T5220 | *** | 530292 | Solaris | 1 |
| 8 |
| | 4 |
| Infra |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | Fujitsu | T5220 | *** | 530293 | Solaris | 1 |
| 8 |
| | 4 |
| Infra |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 423 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 530209 | VMWare ESX | 4 |
| 6 |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 530208 | VMWare ESX | 4 |
| 6 |
| | | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 530221 | Suse | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 530222 | Suse | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 1 |
| — |
| 1 |
| 0.5 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 313990 | W2003 STD | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 520536 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 520537 | W2003 STD | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520323 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522484 | W2003 Std | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 521323 | W2003 Std | 2 |
| 1 |
| 2 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 521324 | W2003 Std | 2 |
| 1 |
| 2 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 521321 | W2003 Std | 2 |
| 1 |
| 2 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520285 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520496 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520497 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520808 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520807 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520810 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521483 | VMWare ESX | 4 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521425 | VMWare ESX | 4 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521429 | VMWare ESX | 4 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521431 | VMWare ESX | 4 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520506 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 313991 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 424 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Staging | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| 1.5 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530626 | Suse | 1 |
| 4 |
| 4 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530627 | Suse | 1 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530624 | Suse | 1 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530685 | Suse | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530687 | Suse | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530681 | Suse | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL495c | *** | 530693 | Suse | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL495c | *** | 530630 | Suse | 2 |
| 4 |
| 8 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530514 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100116 | Solaris | 2 |
| 1 |
| 2 |
| | Infra |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 8 |
| |
| *** | DTC | Development | Unix - Solaris | Low | Virtual | Medium | Shared | Server | LPAR | Fujitsu | M5000 | *** | N/A | Solaris | 8 |
| 1 |
| | | Oracle Fin |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 425 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Test | Unix - Solaris | Low | Virtual | Medium | Shared | Server | LPAR | Fujitsu | M5000 | *** | N/A | Solaris | 8 |
| 1 |
| | | Oracle Fin |
| *** | DTC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100112 | Solaris | 1 |
| 1 |
| 1 |
| | Tax |
| *** | DTC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100098 | Solaris | 1 |
| 1 |
| 1 |
| | Tax |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Fujitsu | T5220 | *** | 700048 | Solaris | 4 |
| 64 |
| | 32 |
| Infra |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100109 | Solaris | 2 |
| 1 |
| 2 |
| | Tax |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100118 | Solaris | 2 |
| 1 |
| 2 |
| | Tax |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Development | Unix - Solaris | Low | Virtual | Small | Shared | Server | LPAR | Fujitsu | M5000 | *** | N/A | Solaris | 4 |
| 1 |
| | | Oracle Fin |
| *** | DTC | Test | Unix - Solaris | Low | Virtual | Small | Shared | Server | LPAR | Fujitsu | M5000 | *** | N/A | Solaris | 4 |
| 1 |
| | | Oracle Fin |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v480 | *** | 316995 | Solaris | 2 |
| 2 |
| 4 |
| | Infra |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v480 | *** | 316990 | Solaris | 2 |
| 2 |
| 4 |
| | Infra |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Fujitsu | T5220 | *** | 700046 | Solaris | 4 |
| 1 |
| 4 |
| 32 |
| Infra |
| *** | DTC | Development | Unix - Solaris | Low | Physical | N/A | Physical | Server | PHYSICAL | Sun | v240 | *** | 100097 | Solaris | 1 |
| 1 |
| 1 |
| | Tax |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | IBM | 7310-CR3 | *** | 101475 | Sys Console Linux | 1 |
| 1 |
| | | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | IBM | 7310-CR3 | *** | 101484 | Sys Console Linux | 1 |
| 1 |
| | | |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | v100 | *** | 318009 | Solaris | 1 |
| 1 |
| 1 |
| | Infra |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | V245 | *** | 101333 | Solaris | 2 |
| 2 |
| 4 |
| | Infra |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Development | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL495c | *** | 530622 | Suse | 2 |
| 4 |
| 8 |
| 64 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 426 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530652 | Solaris | 1 |
| 4 |
| 4 |
| 32 |
| Service Tier |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL580 | *** | 530584 | W2008 Ent | 4 |
| 24 |
| 24 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 530942 | W2003 STD | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL680c | *** | 530781 | W2003 ENT | 4 |
| 1 |
| 4 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530814 | W2003 ENT | 2 |
| 1 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530809 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530801 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530819 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530825 | W2003 ENT | 2 |
| 1 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL680c | *** | 530787 | W2003 ENT | 4 |
| 1 |
| 4 |
| 32 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL25p | *** | 100133 | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 100935 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318278 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 7 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100836 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 100850 | W2003 STD | 2 |
| 8 |
| 16 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100944 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 101313 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 100181 | W2003 STD | 2 |
| 8 |
| 16 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 100947 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 427 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100837 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 318288 | W2003 STD | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL20P | *** | 100168 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 4 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100592 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100566 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100723 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530590 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 522348 | Red Hat Enterprise Server 3 | 2 |
| — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 524099 | Red Hat Enterprise Server 3 | 2 |
| — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 522454 | Red Hat Enterprise Server 3 | 2 |
| — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 522578 | Red Hat Enterprise Server 3 | 2 |
| — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 524341 | Red Hat Enterprise Server 4 | 2 |
| — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 522455 | Red Hat Enterprise Server 4 | 2 |
| — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 524348 | Red Hat Enterprise Server 4 | 2 |
| — |
| | | |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 524345 | Red Hat Enterprise Server 4 | 2 |
| — |
| | | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 4 |
| 4 |
| 4 |
| 5 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 4 |
| 4 |
| 4 |
| 5 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 4 |
| 4 |
| 4 |
| 5 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 500544 | W2003 Std | 2 |
| 2 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 428 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521736 | VMware ESX | 4 |
| 16 |
| | | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521744 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521741 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521738 | W2008 Std | 1 |
| 4 |
| 4 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| — |
| 1 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| — |
| 1 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| — |
| 1 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Advanced Server | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL320 | *** | 521282 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520180 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 521740 | Linux | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 521743 | Linux | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Test | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 521742 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| 1 |
| |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| — |
| 2 |
| 1 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 531016 | W2003 Std | 2 |
| — |
| 2 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 531021 | W2003 Std | 2 |
| — |
| 2 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 531015 | W2003 Std | 2 |
| — |
| 2 |
| 64 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 1 |
| 1 |
| 1 |
| 0.5 |
| |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL465c | *** | 520729 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| | | |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL465c | *** | 520705 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| | | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 429 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL465c | *** | 100973 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| | | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 520721 | W2000 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 100051 | W2000 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 100049 | W2000 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 100052 | W2000 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL465c | *** | 100967 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Redhat 8 | | — |
| 1 |
| | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | DTC | DR | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V210 | *** | 313952 | Solaris | 2 |
| — |
| 2 |
| 2 |
| Infra |
| *** | DTC | DR | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | PP850 | *** | 520523 | Solaris | 8 |
| — |
| 8 |
| 24 |
| Service Tier |
| *** | DTC | DR | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | SUN | V440 | *** | 312479 | Solaris | 4 |
| — |
| 4 |
| 8 |
| Service Tier |
| *** | DTC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | Dell | PowerEdge 2650 | *** | 316977 | W2000 Std | 1 |
| 1 |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 522346 | Red Hat Enterprise Server 3 | 2 |
| — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 524119 | Red Hat Enterprise Server 3 | 2 |
| — |
| | 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522442 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522321 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522541 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 18 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 1 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 531029 | VMWare ESX | 4 |
| 4 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530461 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530482 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530467 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530485 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530509 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530466 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530495 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530479 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Development | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530535 | W2003 Std | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 530929 | W2003 Std | 2 |
| 4 |
| 8 |
| 6 |
| |
| *** | SATC | DR | Windows | Low | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 530928 | W2003 Std | 2 |
| 4 |
| 8 |
| 6 |
| |
| *** | SATC | DR | Windows | Low | Physical | Large | Physical | Server | PHYSICAL | HP | DL380 | *** | 530930 | W2003 Std | 4 |
| 8 |
| 32 |
| 6 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530448 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7835 | *** | 521280 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7835 | *** | 521287 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7835 | *** | 521288 | W2003 Std | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520179 | W2003 Std | | — |
| 1 |
| | |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521278 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521279 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521286 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521274 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521284 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521269 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 520408 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100591 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100514 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100707 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 100573 | W2003 STD | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530858 | W2008 Std | 2 |
| 8 |
| 16 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | VMware Host | HP | DL380 | *** | 522468 | W2003 Std | 2 |
| 2 |
| | 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| — |
| 1 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522428 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL380 | *** | 520131 | VMWare ESX | 2 |
| 2 |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL380 | *** | 520133 | VMWare ESX | 2 |
| 2 |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520468 | W2003 Ent | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 7 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | DTC | DR | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520923 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Unix - Solaris | Standard | Virtual | N/A | Multi-Tenant - Virtualization | Server | Zone | N/A | N/A | *** | N/A | Solaris | | — |
| | | Infra |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | Fujitsu | PP450 | *** | 500364 | Solaris | 2 |
| — |
| 2 |
| | Infra |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7835 | *** | 520825 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Development | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520116 | Red Hat Advanced Server | 2 |
| 4 |
| 8 |
| 24 |
| |
| *** | SATC | Development | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520106 | Red Hat Advanced Server | 2 |
| 4 |
| 8 |
| 24 |
| |
| *** | SATC | DR | Linux | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520100 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 520265 | W2003 STD | 2 |
| 4 |
| 8 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL360 | *** | 520261 | W2003 STD | 2 |
| — |
| 2 |
| | |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V210 | *** | 523032 | Solaris | 2 |
| — |
| 2 |
| 2 |
| Misc |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 521376 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 507946 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 507922 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | EndRun | Tempus LX | *** | 507805 | | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520773 | W2003 STD | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520757 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520759 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 520769 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521544 | W2008 Web R2 | 1 |
| 4 |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521546 | W2008 Web R2 | 1 |
| 4 |
| 4 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521545 | W2008 Web R2 | 1 |
| 2 |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521547 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521548 | W2003 Std | 1 |
| 4 |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 520755 | Red Hat Enterprise Server 4 | — |
| — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 520764 | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 520762 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520316 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | DR | Unix - Solaris | Low | Virtual | Small | Shared | Server | LPAR | Fujitsu | M5000 | *** | N/A | Solaris | — |
| — |
| | | Oracle Fin |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530976 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531003 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530998 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530973 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530974 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530995 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531025 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531010 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530971 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531004 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531017 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531014 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531012 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530992 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531002 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531000 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530999 | Suse | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | DR | Linux | Low | Physical | Small | Physical | Server | Physical | Fujitsu | M5000 | *** | 530904 | Proprietary | | — |
| 1 |
| | |
| *** | DTC | Production | Unix - Solaris | Standard | Virtual | Medium | Shared | Server | LPAR | Fujitsu | M5000 | *** | N/A | Solaris | | 8 |
| | | Oracle Fin |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7825 | *** | 531110 | Cisco VOS | | — |
| 1 |
| | |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7825 | *** | 531111 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520343 | W2003 Std | 2 |
| 2 |
| 2 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520570 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520587 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 520577 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 520579 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520567 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520569 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520904 | W2003 DC | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | MS Host | HP | BL460c | *** | 520910 | W2003 DC | 2 |
| 4 |
| | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520585 | Red Hat Enterprise Server 4 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520901 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520907 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 520902 | W2008 Ent | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 520908 | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | DL585 | *** | 520410 | W2003 Ent | 4 |
| 4 |
| 16 |
| | |
| *** | SATC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520607 | W2003 Std | 2 |
| 2 |
| 4 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520356 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520355 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520368 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL385 | *** | 520369 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520906 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 520900 | W2003 Ent | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 522305 | W2003 Std | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520562 | Red Hat Enterprise Server 4 | 2 |
| — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 523110 | Red Hat Enterprise Server 4 | 4 |
| — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520561 | Red Hat Enterprise Server 4 | 2 |
| — |
| 1 |
| | |
| *** | SATC | Development | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520378 | Red Hat Enterprise Server 4 | 2 |
| — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520373 | Red Hat Enterprise Server 4 | 2 |
| — |
| 1 |
| | |
| *** | SATC | QA | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 520375 | Red Hat Enterprise Server 4 | 2 |
| — |
| 1 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 520920 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 521541 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 520921 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 520914 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 520922 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 520915 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 520912 | WXP | 1 |
| 2 |
| 2 |
| | |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 520919 | WXP | 1 |
| 2 |
| 2 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | xw460c | *** | 520913 | WXP | 2 |
| 4 |
| 8 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M4000 | *** | 530666 | Solaris | 2 |
| 4 |
| 8 |
| 32 |
| Service Tier |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530921 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | DL380 | *** | 524335 | Red Hat Enterprise Server 4 | 2 |
| — |
| | | |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | N/A | — |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | N/A | — |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | N/A | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 7 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 16 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7835 | *** | 521825 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 521863 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 521852 | VMWare ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Red Hat Enterprise Server | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | SUN | V240 | *** | 100809 | Solaris | 2 |
| — |
| 1 |
| | Tax |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 12 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL460c | *** | 530522 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL460c | *** | 530496 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL460c | *** | 530396 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL460c | *** | 530528 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL460c | *** | 530411 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | Xen Host | HP | BL460c | *** | 530527 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL380 | *** | 530567 | W2003 Std | 2 |
| 8 |
| 16 |
| 20 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | DL380 | *** | 530565 | W2003 Std | 2 |
| 8 |
| 16 |
| 20 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 101814 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 101515 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 101816 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 101517 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 102500 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 102501 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 102502 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL495c | *** | 101675 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 101677 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 101676 | VMWare ESX | 2 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | | — |
| 1 |
| 0.5 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 530515 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 530480 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Physical | Medium | Physical | Server | PHYSICAL | HP | DL380 | *** | 530556 | W2008 Std | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 530568 | Red Hat Enterprise Server 5 | | — |
| 1 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 530547 | Red Hat Enterprise Server 5 | | — |
| 1 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL685c | *** | 530540 | Red Hat Enterprise Server 4 | 4 |
| 16 |
| 16 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | QA | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 531480 | Red Hat Enterprise Server 4 | 2 |
| 12 |
| 12 |
| 64 |
| |
| *** | SATC | Test | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 531481 | Red Hat Enterprise Server 4 | 2 |
| 12 |
| 12 |
| 64 |
| |
| *** | SATC | Development | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530536 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL585 | *** | 530583 | Red Hat Enterprise Server 4 | | — |
| 1 |
| 62 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL585 | *** | 530587 | Red Hat Enterprise Server 4 | | — |
| 1 |
| 62 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 530543 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Large | Physical | Server | Physical | HP | DL380 | *** | 530550 | Red Hat Enterprise Server 5 | 8 |
| 4 |
| 32 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Large | Physical | Server | Physical | HP | DL380 | *** | 530559 | Red Hat Enterprise Server 5 | 8 |
| 4 |
| 32 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 531032 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 530541 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 530561 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 530582 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL585 | *** | 530572 | Red Hat Advanced Server 4 | 4 |
| 16 |
| 16 |
| 64 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 530580 | Red Hat Advanced Server | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 530581 | Red Hat Advanced Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 530579 | Red Hat Advanced Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 530575 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL585 | *** | 530571 | Red Hat Advanced Server 4 | | — |
| 1 |
| | |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 530558 | Red Hat Enterprise Server 4 | | 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 530618 | Red Hat Advanced Server 4 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Large | Physical | Server | Physical | HP | DL385 | *** | 530569 | Red Hat Enterprise Server 4 | 8 |
| 4 |
| 32 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 531447 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| | |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL385 | *** | 531448 | Red Hat Enterprise Server 4 | 4 |
| — |
| 4 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL580 | *** | 530578 | W2003 Std | 4 |
| 24 |
| 24 |
| 24 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530989 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530988 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | SUN | V480 | *** | 318010 | Solaris | | — |
| 1 |
| | Misc |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530483 | VMWare ESX | 2 |
| 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530432 | VMWare ESX | 2 |
| 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530521 | VMWare ESX | 2 |
| 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530493 | VMWare ESX | 2 |
| 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 531027 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 531028 | VMWare ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 531479 | Red Hat Advanced Server 4 | 2 |
| 12 |
| 12 |
| 64 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 703897 | Red Hat Advanced Server 4 | 2 |
| 12 |
| 12 |
| 64 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 101854 | W2008 Std R2 | 4 |
| 16 |
| 16 |
| 12 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL685c | *** | 530539 | W2003 Ent | 4 |
| 4 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530395 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530367 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530428 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | | | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| — |
| 1 |
| | |
| *** | SATC | QA | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Facetime | USG530 | *** | 531472 | Proprietary | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Facetime | USG530 | *** | 531473 | Proprietary | | — |
| | | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 530537 | Red Hat Advanced Server 4 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 531125 | W2008 Std | 2 |
| 8 |
| 16 |
| 12 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 531715 | W2003 Std | 2 |
| 8 |
| 16 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 101796 | VMware ESX | 4 |
| 24 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 101774 | W2008 STD | 2 |
| 8 |
| 16 |
| 12 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 101772 | W2008 STD | 2 |
| 8 |
| 16 |
| 12 |
| |
| *** | DTC | Production | TBD | TBD | TBD | TBD | Physical | Server | Physical | HP | DL380 | *** | 101773 | Proprietary | 2 |
| 8 |
| 16 |
| 12 |
| |
| *** | DTC | Production | TBD | TBD | TBD | TBD | Physical | Server | Physical | HP | DL380 | *** | 101771 | Proprietary | 2 |
| 8 |
| 16 |
| 12 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 531467 | W2008 Std | 2 |
| 8 |
| 16 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 531464 | W2008 Std | 2 |
| 8 |
| 16 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 531466 | W2008 Std | 2 |
| 8 |
| 16 |
| 4 |
| |
| *** | SATC | Production | TBD | TBD | TBD | TBD | Physical | Server | PHYSICAL | HP | DL380 | *** | 531468 | Proprietary | 2 |
| 8 |
| 16 |
| 4 |
| |
| *** | SATC | Production | TBD | TBD | TBD | TBD | Physical | Server | PHYSICAL | HP | DL380 | *** | 531465 | Proprietary | 2 |
| 8 |
| 16 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319132 | Cisco VOS | | — |
| 1 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 700108 | Cisco VOS | | — |
| 1 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319133 | Cisco VOS | | — |
| 1 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 100804 | Cisco VOS | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319141 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319090 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7825 | *** | 101907 | Win - Cisco | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cistera | CS 2500 | *** | 100810 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319139 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319140 | W2003 Std | 2 |
| 4 |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 101403 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 101405 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319146 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319147 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319142 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319134 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319130 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319135 | W2003 Std | | — |
| 1 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319136 | Cisco VOS | | — |
| 1 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319137 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 530453 | W2008 Std | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530426 | W2008 ENT | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 101553 | W2003 Std | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 101800 | W2003 Std | 2 |
| 8 |
| 16 |
| 4 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Generic | Generic | *** | 100478 | Alerton WebTalk 2.11 | | — |
| 1 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Generic | Generic | *** | 100479 | Alerton WebTalk 2.11 | | — |
| 1 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Generic | Generic | *** | 100533 | Alerton WebTalk 2.11 | | — |
| 1 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Generic | Generic | *** | 100534 | Alerton WebTalk 2.11 | | — |
| 1 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 100034 | W2003 Std | 1 |
| 1 |
| 1 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL25P | *** | 100138 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL25P | *** | 100137 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL25P | *** | 100139 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 316807 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | QA | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 316809 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | QA | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 316810 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 316811 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 316812 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 316813 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 316814 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 316820 | W2003 Web | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 316821 | W2003 Web | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 316824 | W2003 Web | 2 |
| — |
| 2 |
| | |
| *** | DTC | QA | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313554 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313752 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313575 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | DTC | QA | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313558 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313715 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313717 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313559 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313721 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | QA | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 312309 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 313722 | W2003 Ent | | — |
| 1 |
| | |
| *** | DTC | QA | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL740 | *** | 313569 | W2003 Ent | 8 |
| — |
| 8 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL740 | *** | 313586 | W2003 Ent | 8 |
| — |
| 8 |
| | |
| *** | DTC | QA | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL740 | *** | 313584 | W2003 Ent | 8 |
| — |
| 8 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313560 | W2003 Ent | 2 |
| — |
| 2 |
| | |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313580 | W2003 Web | | — |
| 1 |
| | |
| *** | DTC | QA | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313565 | W2003 Web | 2 |
| — |
| 2 |
| | |
| *** | DTC | QA | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313564 | W2003 Web | 2 |
| — |
| 2 |
| | |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313563 | W2003 Web | 2 |
| — |
| 2 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 313719 | W2008 Std | 2 |
| 2 |
| 2 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313750 | W2003 Web | 2 |
| — |
| 2 |
| | |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313749 | W2003 Web | 2 |
| — |
| 2 |
| | |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | SUN | V480 | *** | 318011 | Solaris | | — |
| 1 |
| | Infra |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | IBM | x3550 | *** | 101935 | W2008 Ent | | — |
| 1 |
| | |
| *** | DTC | Training | iSeries | N/A | Physical | N/A | Physical | Server | Physical | IBM | I-Series | *** | 101274 | V7R1 | | — |
| 1 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530520 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530502 | VMWare ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | zVM Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| | | |
| *** | DTC | Development | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | zVM Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| | | |
| *** | DTC | Development | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | zVM Guest | N/A | N/A | *** | N/A | Red Hat | | — |
| | | |
| *** | DTC | Development | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | zVM Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 531713 | Red Hat Enterprise Server 5 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 531714 | Red Hat Enterprise Server 5 | 2 |
| — |
| 2 |
| | |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531745 | Red Hat Enterprise Server 5 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL465c | *** | 531746 | Red Hat Enterprise Server 5 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Web R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 522284 | W2003 Std | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Cisco | PhoneProxy 500 | *** | 521329 | | | — |
| | | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | Xen Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 12 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 531478 | VMware ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | n/a | Suse | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | n/a | Suse | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Google | MINI-002X | *** | 531739 | | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL320 | *** | 531391 | W2008 Std | 1 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | DL320 | *** | 531390 | W2008 Std | 1 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319129 | Cisco VOS | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 319138 | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 10440 | Cisco VOS | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530425 | W2008 Std | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530435 | W2008 ENT | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530517 | W2003 Std | 2 |
| 8 |
| 16 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531803 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531804 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531805 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531806 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531807 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Staging | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531801 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Development | Linux | Low | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531802 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 530518 | W2008 Std | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | XEN Host | HP | BL460c | *** | 530438 | Red Hat Enterprise Server 4 | | 8 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 531778 | VMware ESX | 2 |
| 8 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Web | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Web | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL480c | *** | 521002 | W2008 ENT | 2 |
| 8 |
| 16 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL480c | *** | 521001 | W2008 ENT | 2 |
| 8 |
| 16 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL480c | *** | 520997 | W2008 STD | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL480c | *** | 521003 | W2008 STD | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 531814 | W2008 STD | 2 |
| 8 |
| 16 |
| 12 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 531817 | W2008 STD | 2 |
| 8 |
| 16 |
| 12 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 531821 | W2008 STD | 2 |
| 8 |
| 16 |
| 12 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | PHYSICAL | HP | BL460c | *** | 531819 | W2008 STD | 2 |
| 8 |
| 16 |
| 12 |
| |
| *** | SATC | DR | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 100403 | W2003 Std | 2 |
| 4 |
| 8 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 100402 | W2003 Std | 2 |
| 4 |
| 8 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 311372 | W2003 Std | 2 |
| 2 |
| 4 |
| 2.3 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | IEA | *** | 531387 | | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | IEA | *** | 531389 | | | — |
| | | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | zVM Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| | | |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Netscout | nGenius Probe | *** | 530869 | | 1 |
| — |
| | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | | *** | N/A | Red Hat Enterprise Server | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL140 | *** | 522824 | Red Hat | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL140 | *** | 522825 | Red Hat | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Extra Large | Physical | Server | PHYSICAL | HP | DL785 | *** | 532035 | W2008 Ent | 8 |
| 48 |
| | 256 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 102505 | VMware ESX | 2 |
| 8 |
| | | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 102507 | VMware ESX | 2 |
| — |
| | | |
| *** | SATC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 532111 | VMWare ESX | 4 |
| 4 |
| | | |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530758 | VMware ESX | 4 |
| 4 |
| | 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 530760 | VMware ESX | 4 |
| 4 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 532026 | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Redhat 7 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Redhat 7 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 11 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL580 | *** | 102504 | VMware ESX | | — |
| | | |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 101072 | W2003 Std | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | WS460c | *** | 532114 | W7 | 2 |
| 8 |
| | | |
| *** | SATC | Development | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | WS460c | *** | 532115 | W7 | 2 |
| 8 |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 521894 | W2003 ENT | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 101939 | VMware ESX | 2 |
| 8 |
| | 146 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 531724 | W2003 Ent | 2 |
| 4 |
| 8 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 531846 | W2003 Std | 2 |
| 4 |
| 8 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 531845 | W2003 Std | 1 |
| 4 |
| 4 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 531847 | W2003 Std | 1 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 531723 | W2003 Web | | 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7845 | *** | 531844 | W2003 Web | | 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 532130 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 532128 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 532127 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 532129 | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Large | Physical | Server | PHYSICAL | HP | DL580 | *** | 530873 | W2003 Ent | 4 |
| 6 |
| 24 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Fujitsu | PP450 | *** | 520138 | Solaris | | 4 |
| 4 |
| | Misc |
| *** | SATC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | PHYSICAL | Fujitsu | PP450 | *** | 520136 | Solaris | | 2 |
| 2 |
| | Misc |
| *** | DTC | QA | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | N/A | N/A | N/A | N/A | Physical | Server | Physical | Cisco | MCS 7845 | *** | 520409 | N/A | | — |
| 1 |
| | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 100720 | VMware ESX | 2 |
| 4 |
| | 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 532083 | W2008 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 532082 | W2008 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 7 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 531813 | W2008 Ent | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 531815 | W2008 Ent | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | MS Host | HP | DL380 | *** | 531811 | W2008 Ent | 2 |
| 8 |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | MS Host | HP | DL380 | *** | 531812 | W2008 Ent | 2 |
| 8 |
| | | |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703506 | W2008 Web R2 | 2 |
| 12 |
| 12 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703507 | W2008 Web R2 | 2 |
| 12 |
| 12 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703508 | W2008 Web R2 | 2 |
| 12 |
| 12 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 530498 | W2008 Std | 2 |
| 8 |
| 16 |
| | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 520944 | Proprietary | 1 |
| 1 |
| 1 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 703509 | Red Hat Enterprise Server 5 | 2 |
| — |
| 2 |
| | |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 703510 | Red Hat Enterprise Server 5 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 703511 | Red Hat Enterprise Server 5 | 2 |
| — |
| 2 |
| | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Redhat 8 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Redhat 8 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700005 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700006 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700007 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700008 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700009 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700010 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700011 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700012 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700013 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700014 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700015 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700016 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703519 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703520 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703521 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703522 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Test | Windows | Low | Physical | Large | Physical | Server | Physical | HP | DL580 | *** | 530874 | w2003 std | 4 |
| 6 |
| 24 |
| 64 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703523 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703524 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703525 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703526 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703527 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703528 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703529 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703530 | VMware ESX | 2 |
| 6 |
| | 128 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | C670 | *** | 703502 | Proprietary | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | C370 | *** | 703501 | Proprietary | 2 |
| — |
| | | |
| *** | SATC | Development | Unix - Solaris | Low | Physical | N/A | Physical | Server | Physical | SUN | V240 | *** | 316693 | Solaris | | — |
| 1 |
| | Infra |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | Physical | HP | DL580 | *** | 703512 | W2008 Ent | 4 |
| 24 |
| 24 |
| | |
| *** | SATC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 522483 | Red Hat | 2 |
| 2 |
| 4 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 6 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Physical | Large | Physical | Server | Physical | HP | BL680c | *** | 530793 | W2008 Ent | 4 |
| 24 |
| 24 |
| 64 |
| |
| *** | SATC | Development | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL680c | *** | 530775 | W2003 Ent | 4 |
| 24 |
| 24 |
| 64 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531820 | W2008 Ent R2 | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531816 | W2008 DC R2 | | — |
| 1 |
| | |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 531818 | W2008 DC R2 | | — |
| 1 |
| | |
| *** | SATC | Development | Windows | Low | Physical | Extra Large | Physical | Server | Physical | HP | DL785 | *** | 703539 | W2008 Ent | 4 |
| 24 |
| | 256 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Web | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Large | Physical | Server | Physical | Fujitsu | M4000 | *** | 703540 | Solaris | 2 |
| 16 |
| | 64 |
| Service Tier |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Large | Physical | Server | Physical | Fujitsu | M4000 | *** | 703541 | Solaris | 2 |
| 16 |
| | 64 |
| Service Tier |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 12 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 12 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Training | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 12 |
| |
| *** | SATC | Training | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Training | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Training | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL360 | *** | 703603 | Red Hat Enterprise Server 5 | 2 |
| 16 |
| 16 |
| 12 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | M3000 | *** | 530380 | Solaris | 1 |
| 4 |
| 4 |
| 32 |
| Service Tier |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703534 | W2008 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703531 | W2008 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703533 | W2008 Std | 2 |
| 12 |
| 12 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703532 | W2008 Std | 2 |
| 12 |
| 12 |
| 32 |
| |
| *** | SATC | Staging | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703549 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | SATC | Staging | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703551 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | SATC | Staging | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703550 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530391 | VMware ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530497 | VMware ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530530 | VMware ESX | 2 |
| 4 |
| | 32 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700049 | W2008 Ent R2 | 2 |
| 6 |
| 12 |
| 120 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Physical | Large | Physical | Server | Physical | HP | BL460c | *** | 700021 | W2008 Ent R2 | 2 |
| 6 |
| 12 |
| 120 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 700054 | W2003 Std | 2 |
| 4 |
| 8 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Proprietary | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Proprietary | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700032 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700033 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL685c | *** | 520998 | VMware ESX | 4 |
| 2 |
| | 64 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL685c | *** | 703661 | VMware ESX | 4 |
| 2 |
| | 64 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 101486 | VMware ESX | 2 |
| 4 |
| | | |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | SUN | V480 | *** | 318012 | Solaris | 2 |
| 2 |
| 4 |
| 4 |
| Infra |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703575 | W2003 Ent | 2 |
| 8 |
| 16 |
| 72 |
| |
| *** | SATC | Staging | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703573 | W2003 Ent | 2 |
| 8 |
| 16 |
| 72 |
| |
| *** | SATC | Staging | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703571 | W2003 Ent | 2 |
| 8 |
| 16 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703572 | W2008 Std | 1 |
| 4 |
| 4 |
| 36 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703574 | W2008 Ent | 1 |
| 4 |
| 4 |
| 36 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703569 | W2008 Ent | 1 |
| 6 |
| 6 |
| 36 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703570 | W2003 Ent | 2 |
| 4 |
| 8 |
| 36 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703567 | W2008 Std | 1 |
| 6 |
| 6 |
| 36 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703563 | W2008 Std | 1 |
| 6 |
| 6 |
| 36 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703562 | W2008 Ent | 2 |
| 8 |
| 16 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703558 | W2003 Ent | 2 |
| 8 |
| 16 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703561 | W2008 Ent | 1 |
| 6 |
| 6 |
| 36 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703568 | W2003 Ent | 2 |
| 8 |
| 16 |
| 72 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700041 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700040 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700045 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Development | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700062 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 32 |
| |
| *** | DTC | Development | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700061 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Large | Physical | Server | Physical | HP | BL460c | *** | 700060 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 120 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Large | Physical | Server | Physical | HP | BL460c | *** | 700059 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 120 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Unix - AIX | Standard | Physical | N/A | Physical | Server | Physical | IBM | Power 770 | *** | 703621 | AIX | 23 |
| 23 |
| | 110 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Physical | N/A | Physical | Server | Physical | IBM | 7042 HMC | *** | 703729 | AIX | 1 |
| 2 |
| 2 |
| 8 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Physical | N/A | Physical | Server | Physical | IBM | Power 770 | *** | 703622 | AIX | 26 |
| 26 |
| | 145 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Physical | N/A | Physical | Server | Physical | IBM | 7042 HMC | *** | 703727 | AIX | 1 |
| 2 |
| 2 |
| 8 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Physical | N/A | Physical | Server | Physical | IBM | Power 770 | *** | 703623 | AIX | 24 |
| 24 |
| | 128 |
| Credco |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700034 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700029 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530823 | VMware ESX | 2 |
| 2 |
| | 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Large | Physical | Server | Physical | HP | DL380 | *** | 530545 | Red Hat Enterprise Server 5 | 8 |
| 4 |
| 32 |
| 32 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Unix - AIX | Standard | Physical | N/A | Physical | Server | Physical | IBM | Power 770 | *** | 700038 | AIX | 12 |
| 12 |
| | 32 |
| Infra |
| *** | DTC | Production | Unix - AIX | Standard | Physical | N/A | Physical | Server | Physical | IBM | 7042 HMC | *** | 700036 | AIX | 1 |
| 2 |
| 2 |
| 8 |
| Infra |
| *** | DTC | Production | Unix - AIX | Standard | Physical | N/A | Physical | Server | Physical | IBM | Power 770 | *** | 700037 | AIX | 12 |
| 12 |
| | 32 |
| Infra |
| *** | DTC | Production | Unix - AIX | Standard | Physical | N/A | Physical | Server | Physical | IBM | 7042 HMC | *** | 700035 | AIX | 1 |
| 2 |
| 2 |
| 8 |
| Infra |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700023 | VMware ESX | 2 |
| 8 |
| | 104 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700026 | VMware ESX | 2 |
| 8 |
| | 104 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700024 | VMware ESX | 2 |
| 8 |
| | 104 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700030 | VMware ESX | 2 |
| 8 |
| | 104 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700027 | VMware ESX | 2 |
| 8 |
| | 104 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent R2 | — |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent R2 | — |
| — |
| | | |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent R2 | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent R2 | — |
| — |
| | | |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700053 | W2008 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700052 | W2008 Std | 2 |
| 12 |
| 12 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700020 | W2008 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700019 | W2008 Std | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 703578 | Suse | 1 |
| 16 |
| 16 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 703601 | W2008 Ent | 2 |
| 24 |
| 24 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 703602 | W2008 Ent | 2 |
| 24 |
| 24 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | — |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703611 | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 72 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703612 | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 72 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703613 | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 72 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703614 | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 72 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 3 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 703579 | W2008 Ent | 2 |
| 24 |
| 24 |
| | |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | Fujitsu | T5220 | *** | 700047 | Solaris | 4 |
| 64 |
| | 32 |
| Infra |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700025 | VMware ESX | 2 |
| 8 |
| | 96 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | SQL Instance | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | SQL Instance | N/A | N/A | *** | N/A | W2008 Ent R2 | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | SQL Instance | N/A | N/A | *** | N/A | W2008 Ent R2 | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | SQL Instance | N/A | N/A | *** | N/A | W2008 Ent R2 | | — |
| | | |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | | SQL Instance | N/A | N/A | *** | N/A | W2008 Ent R2 | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | SQL Instance | N/A | N/A | *** | N/A | W2008 Ent R2 | | — |
| | | |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 2 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 2 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 2 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 2 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 1 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 1 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 3 |
| | 4 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 3 |
| | 24 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 3 |
| Credco |
| *** | SATC | Test | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 4 |
| Credco |
| *** | SATC | Test | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 3 |
| Credco |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 2 |
| Credco |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 2 |
| Credco |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 2 |
| Credco |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 16 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 3 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 1 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 2 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 15 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 3 |
| | 24 |
| Credco |
| *** | SATC | Test | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 1 |
| Credco |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 1 |
| Credco |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 3 |
| | 19 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 2 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 3 |
| | 24 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 3 |
| | 24 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 16 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 1 |
| Credco |
| *** | SATC | QA | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 2 |
| Credco |
| *** | SATC | QA | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 2 |
| Credco |
| *** | SATC | QA | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 6 |
| Credco |
| *** | SATC | QA | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 6 |
| Credco |
| *** | SATC | QA | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 6 |
| Credco |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 4 |
| Credco |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 2 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 16 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 5 |
| | 9 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 2 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 1 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 2 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 3 |
| | 24 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 16 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 8 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 12 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | — |
| | 2 |
| Credco |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 3 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700069 | W2003 Ent | 2 |
| 6 |
| 12 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703636 | W2008 Web R2 | 2 |
| 12 |
| 12 |
| 44 |
| |
| *** | SATC | QA | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703637 | W2008 Web R2 | 2 |
| 12 |
| 12 |
| 44 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 700070 | W2003 Std | 2 |
| 4 |
| 8 |
| 6 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | — |
| — |
| | | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | — |
| — |
| | | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | — |
| — |
| | | |
| *** | DTC | DR | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | IronPort | C370 | *** | 703503 | | 4 |
| 1 |
| | 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 703608 | W2003 Std | 2 |
| 4 |
| 8 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | Physical | HP | BL460c | *** | 703559 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 120 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Large | Physical | Server | Physical | HP | BL460c | *** | 703564 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 120 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703645 | W2008 Web R2 | 2 |
| 12 |
| 12 |
| 44 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703646 | W2008 Web R2 | 2 |
| 12 |
| 12 |
| 44 |
| |
| *** | SATC | QA | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703647 | W2008 Web R2 | 2 |
| 12 |
| 12 |
| 44 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 4 |
| 16 |
| | 128 |
| Next Gen Fraud |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 4 |
| 16 |
| | 128 |
| Next Gen Fraud |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 4 |
| 16 |
| | 128 |
| Next Gen Fraud |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 4 |
| 16 |
| | 128 |
| Next Gen Fraud |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 4 |
| 16 |
| | 128 |
| Next Gen Fraud |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 4 |
| 16 |
| | 128 |
| Next Gen Fraud |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 4 |
| 16 |
| | 128 |
| Next Gen Fraud |
| *** | SATC | Development | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 4 |
| 16 |
| | 128 |
| Next Gen Fraud |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 1 |
| 1 |
| 1 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 703598 | W2003 Std | 2 |
| 4 |
| 8 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521883 | W2003 Ent | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521882 | W2003 Ent | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521027 | W2008 Std | 2 |
| 8 |
| 16 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521028 | W2008 Std | 2 |
| 8 |
| 16 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 10 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | | — |
| 1 |
| | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 101555 | VMware ESX | 2 |
| 4 |
| | 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | | — |
| 1 |
| | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Test | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 530875 | W2003 Ent | 4 |
| 24 |
| 24 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | Fujitsu | T5120 | *** | 703599 | Solaris 10 | 1 |
| 8 |
| | 32 |
| Infra |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| | 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| | 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703672 | W2008 Ent | 1 |
| 6 |
| 6 |
| 36 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703673 | W2008 Ent R2 | 1 |
| 6 |
| 6 |
| 36 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 703654 | W2008 Ent | 2 |
| 24 |
| 24 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 703655 | W2008 Ent | 2 |
| 24 |
| 24 |
| 72 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703553 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703552 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703554 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530824 | VMware ESX | 1 |
| 2 |
| | 16 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 703657 | VMware ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703676 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 520943 | Red Hat Advanced Server 4 | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL360 | *** | 316831 | Red Hat Advanced Server 4 | 2 |
| 2 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 507935 | Red Hat Advanced Server 4 | 2 |
| 2 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 507936 | Red Hat Advanced Server 4 | 2 |
| 2 |
| 4 |
| 8 |
| |
| *** | SATC | Development | Linux | Low | Physical | Medium | Physical | Server | Physical | Netezza | Skimmer | *** | 703662 | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 16 |
| 24 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | Netezza | TwinFin6 | *** | 703731 | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 16 |
| 24 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | Netezza | TwinFin6 | *** | 703732 | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 16 |
| 24 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | Netezza | TwinFin6 | *** | 703733 | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 16 |
| 24 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | Netezza | TwinFin6 | *** | 703734 | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 16 |
| 24 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Web | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 8 |
| 8 |
| 8 |
| 16 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 8 |
| 8 |
| 8 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W7 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W7 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700031 | VMware ESX | 2 |
| 8 |
| | 104 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 700084 | W2008 Ent | 4 |
| 24 |
| 24 |
| 64 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 700085 | W2008 Ent | 4 |
| 24 |
| 24 |
| 64 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL680c | *** | 703665 | VMware ESX | 4 |
| 16 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703560 | W2003 Ent | 2 |
| 12 |
| 12 |
| 32 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703684 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Staging | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703685 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Staging | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703686 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Staging | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703687 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Advanced Server 4 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Large | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 6 |
| 6 |
| 6 |
| 32 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Medium | Physical | Server | Physical | SUN | T2000 | *** | 703697 | Solaris 10 | 4 |
| 16 |
| | 32 |
| Flood |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Medium | Physical | Server | Physical | SUN | T2000 | *** | 703696 | Solaris 10 | 4 |
| 16 |
| | 32 |
| Flood |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL360 | *** | 703688 | W2008 Std | 1 |
| 4 |
| 4 |
| 36 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL480c | *** | 101309 | VMware ESX | 2 |
| 4 |
| | 32 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL480c | *** | 101801 | VMware ESX | 2 |
| 4 |
| | 16 |
| |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | DR | Linux | Low | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 6 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 6 |
| 6 |
| 6 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 6 |
| 6 |
| 6 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 6 |
| 6 |
| 6 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 101680 | VMware ESX | 2 |
| 4 |
| | 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | SUN | V240 | *** | 313770 | Solaris 10 | 1 |
| 1 |
| 1 |
| 2.5 |
| Misc |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Ingrian | i430 | *** | 700092 | N/A | — |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | SafeNet | i430 | *** | 703660 | N/A | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | w2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | w2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | w2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | w2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | w2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | w2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | w2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | w2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | w2008 STD | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700105 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700103 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700099 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700100 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700096 | W2003 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700098 | W2003 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703678 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 98.3 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703692 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 98.3 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | SATC | Development | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | DL385 | *** | 703642 | Suse Linux Ent Server 11 | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | QA | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 2 |
| 2 |
| | 16 |
| Next Gen Fraud |
| *** | DTC | QA | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 2 |
| 2 |
| | 16 |
| Next Gen Fraud |
| *** | DTC | QA | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 2 |
| 2 |
| | 16 |
| Next Gen Fraud |
| *** | DTC | QA | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 1 |
| 1 |
| | 8 |
| Next Gen Fraud |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700407 | VMware ESX | 2 |
| 6 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700406 | VMware ESX | 2 |
| 6 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700044 | VMware ESX | 2 |
| 6 |
| | 96 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | WS460c | *** | 703679 | W2008 Ent | 2 |
| 12 |
| | 98 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703680 | W2008 Ent | 2 |
| 12 |
| 12 |
| 98 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | SUN | V240 | *** | 313630 | Solaris 10 | 2 |
| 2 |
| 4 |
| 8 |
| Misc |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703711 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703712 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Staging | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703713 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703710 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Test | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Lantronix | SCS1620 | *** | 507203 | Sys Console Linux | | — |
| | | |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 12 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 12 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Google | MINI-002X | *** | 703706 | | | — |
| | | |
| *** | SATC | PRODUCTION | Windows | Standard | Virtual | Medium | Multi-tenant - Virtualization | SERVER | VMWARE Guest | N/A | N/A | *** | N/A | W2008 ENT | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | PRODUCTION | Windows | Standard | Virtual | Medium | Multi-tenant - Virtualization | SERVER | VMWARE Guest | N/A | N/A | *** | N/A | W2008 ENT | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | PRODUCTION | Windows | Standard | Virtual | Medium | Multi-tenant - Virtualization | SERVER | VMWARE Guest | N/A | N/A | *** | N/A | W2008 ENT | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | PRODUCTION | Windows | Standard | Virtual | Medium | Multi-tenant - Virtualization | SERVER | VMWARE Guest | N/A | N/A | *** | N/A | W2008 ENT | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | PRODUCTION | Windows | Standard | Virtual | Medium | Multi-tenant - Virtualization | SERVER | VMWARE Guest | N/A | N/A | *** | N/A | W2008 ENT | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | PRODUCTION | Windows | Standard | Virtual | Medium | Multi-tenant - Virtualization | SERVER | VMWARE Guest | N/A | N/A | *** | N/A | W2008 ENT | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | PRODUCTION | Windows | Standard | Virtual | Medium | Multi-tenant - Virtualization | SERVER | VMWARE Guest | N/A | N/A | *** | N/A | W2008 ENT | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | PRODUCTION | Windows | Standard | Virtual | Medium | Multi-tenant - Virtualization | SERVER | VMWARE Guest | N/A | N/A | *** | N/A | W2008 ENT | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | PRODUCTION | N/A | N/A | N/A | N/A | Multi-tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | DTC | Development | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Test | Windows | Low | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 100735 | W2003 Ent | 2 |
| 4 |
| 8 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | T5210 | *** | 100074 | Solaris 10 | 1 |
| 4 |
| 4 |
| 32 |
| Oracle Fin |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | T5210 | *** | 100073 | Solaris 10 | 1 |
| 4 |
| 4 |
| 32 |
| Oracle Fin |
| *** | DTC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | Fujitsu | T5210 | *** | 100071 | Solaris 10 | 1 |
| 8 |
| | 32 |
| Oracle Fin |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | Fujitsu | T5210 | *** | 100072 | Solaris 10 | 1 |
| 8 |
| | 32 |
| Oracle Fin |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 24 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 12 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 700114 | Suse Linux Ent Server 10 | 2 |
| 8 |
| 16 |
| 64 |
| |
| *** | DTC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 700115 | Suse Linux Ent Server 10 | 2 |
| 8 |
| 16 |
| 64 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Unix - AIX | Standard | Physical | N/A | Physical | Server | Physical | IBM | P570-SC | *** | 101472 | AIX | — |
| — |
| 1 |
| | Infra |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 12 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Proprietary | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Proprietary | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Large | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 8 |
| 8 |
| 8 |
| 32 |
| |
| *** | SATC | Development | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | DL385 | *** | 703644 | Suse Linux Ent Server 11 | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700128 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700124 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 530393 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 530524 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700130 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700123 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700129 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700127 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703760 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703762 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703761 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703758 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | QA | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | QA | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | DR | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700102 | W2003 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | DR | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700097 | W2003 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | | — |
| | | |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | | — |
| | | |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | | — |
| | | |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | | — |
| | | |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 703693 | W2008 Ent | 4 |
| 24 |
| 24 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 703694 | W2008 Ent | 4 |
| 24 |
| 24 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | SATC | Staging | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | HP | TippingPoint SMS | *** | 703683 | Linux | 1 |
| 4 |
| | 4 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Large | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 8 |
| 8 |
| 8 |
| 64 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Large | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 8 |
| 8 |
| 8 |
| 64 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700110 | W2008 Ent | 2 |
| 8 |
| 12 |
| 70 |
| |
| *** | DTC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 100704 | Suse Linux Ent Server 10 | 2 |
| 8 |
| 16 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 703709 | W2008 Std | 2 |
| 12 |
| 12 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 703708 | W2008 Std | 2 |
| 12 |
| 12 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703787 | W2008 Std | 2 |
| 12 |
| 12 |
| 24 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703788 | W2008 Std | 2 |
| 12 |
| 12 |
| 24 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703782 | W2008 Std | 2 |
| 12 |
| 12 |
| 24 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703783 | W2008 Std | 2 |
| 12 |
| 12 |
| 24 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | DL585 | *** | 703643 | VMware ESX | 2 |
| 4 |
| | 64 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 703784 | W2008 Ent | 2 |
| 24 |
| 24 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703707 | W2008 Ent | 2 |
| 8 |
| 16 |
| 70 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Extra Large | Physical | Server | Physical | HP | DL785 | *** | 703728 | W2008 ENT | 8 |
| 48 |
| | 192 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | DTC | Test | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 700149 | W2008 Std | 4 |
| 32 |
| 32 |
| 64 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 12 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 12 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 12 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Extra Large | Physical | Server | Physical | HP | DL380 | *** | 703698 | Red Hat Enterprise Server 5 | 2 |
| 36 |
| 36 |
| 12 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700189 | Red Hat Enterprise Server 5 | 2 |
| 12 |
| 12 |
| 96 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700090 | W2008 Ent | 2 |
| 12 |
| 12 |
| 98 |
| |
| *** | DTC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700190 | Red Hat Enterprise Server 5 | 2 |
| 12 |
| 12 |
| 96 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700405 | W2008 Ent | 2 |
| 12 |
| 12 |
| 98 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 700104 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | DTC | Test | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700101 | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 16 |
| 16 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700125 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700126 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700122 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 700136 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 700134 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 700137 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700155 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700151 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700152 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700153 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700154 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700158 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700159 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700162 | W2008 Ent | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | DTC | Staging | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700169 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700167 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700170 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700172 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700171 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL465c | *** | 703730 | W2003 Ent | 2 |
| 8 |
| 16 |
| 64 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | QA | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 703576 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703677 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | DR | Windows | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703810 | W2008 Ent R2 | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 703715 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703759 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703757 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 703756 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 703742 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 703739 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 703749 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703767 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703768 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703769 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703766 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703779 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703777 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703778 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703775 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703793 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703791 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Staging | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703790 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Test | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703792 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 32 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWARE Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL460c | *** | 530806 | VMware ESX | 2 |
| 2 |
| | 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | MS Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Physical | Large | Physical | Server | Physical | HP | DL380 | *** | 700113 | Red Hat Enterprise Server 5 | | 24 |
| 24 |
| 36 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 12 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | XEN Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 STD R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 700160 | Solaris 10 | 1 |
| 4 |
| 4 |
| | Flood |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 101691 | Solaris 10 | 1 |
| 4 |
| 4 |
| | Flood |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 101689 | Solaris 10 | 1 |
| 4 |
| 4 |
| | Flood |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 3 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Staging | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700211 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703826 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Staging | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703825 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703827 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | DTC | Production | Linux | Standard | Physical | Large | Physical | Server | Physical | HP | BL460c | *** | 700094 | Suse Linux Ent Server 10 | 2 |
| 8 |
| 16 |
| 144 |
| |
| *** | DTC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700095 | Suse Linux Ent Server 10 | 2 |
| 8 |
| 16 |
| 72 |
| |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 700183 | W2003 Std | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | DR | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703726 | Suse Linux Ent Server 10 | 2 |
| 4 |
| 8 |
| 64 |
| |
| *** | SATC | DR | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703725 | Suse Linux Ent Server 10 | 2 |
| 4 |
| 8 |
| 64 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703816 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703817 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703818 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703819 | VMware ESX | 2 |
| 12 |
| | 144 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700194 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 700192 | VMware ESX | 2 |
| 12 |
| | 96 |
| |
| *** | SATC | DR | Unix - Solaris | Low | Physical | Large | Physical | Server | Physical | Fujitsu | M4000 | *** | 703765 | Solaris 10 | 4 |
| 4 |
| 16 |
| 64 |
| Flood |
| *** | SATC | DR | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 101709 | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520659 | W2008 Ent R2 | 2 |
| 4 |
| 8 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 520661 | W2008 Ent R2 | 2 |
| 4 |
| 8 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521024 | W2008 Std R2 | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 521034 | W2008 Std R2 | 2 |
| 4 |
| 8 |
| 4 |
| |
| *** | DTC | Development | iSeries | N/A | Physical | N/A | Physical | Server | Physical | IBM | i525 | *** | 700419 | V7R1 | 2 |
| 2 |
| 4 |
| 15 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703802 | W2008 Ent | 2 |
| 12 |
| 12 |
| 48 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703803 | W2008 Ent | 2 |
| 12 |
| 12 |
| 48 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703804 | W2008 Ent | 2 |
| 12 |
| 12 |
| 48 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2008 Ent | | — |
| | | |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 9 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | Physical | Fujitsu | M4000 | *** | 703809 | Solaris 10 | 2 |
| 8 |
| | 65 |
| Misc |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Medium | Physical | Server | Physical | SUN | T2000 | *** | 700139 | Solaris 10 | 4 |
| 16 |
| | 32 |
| Flood |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Medium | Physical | Server | Physical | SUN | T2000 | *** | 700138 | Solaris 10 | 4 |
| 16 |
| | 32 |
| Flood |
| *** | DTC | Test | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 700106 | Solaris 10 | 1 |
| 4 |
| 4 |
| 16 |
| Flood |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 700156 | Solaris 10 | 1 |
| 4 |
| 4 |
| 32 |
| Flood |
| *** | SATC | DR | Unix - Solaris | Low | Physical | Medium | Physical | Server | Physical | SUN | T2000 | *** | 101649 | Solaris 10 | 4 |
| 16 |
| | 16 |
| Flood |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 703829 | Solaris 10 | 1 |
| 4 |
| 4 |
| 16 |
| Flood |
| *** | SATC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 703830 | Solaris 10 | 1 |
| 4 |
| 4 |
| 16 |
| Flood |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700205 | Red Hat Enterprise Server 5 | 2 |
| 8 |
| 16 |
| 72 |
| |
| *** | DTC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 700206 | Red Hat Enterprise Server 5 | 2 |
| 8 |
| 16 |
| 72 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 32 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | | | — |
| | | |
| *** | SATC | Test | N/A | N/A | N/A | N/A | Multi-Tenant - Virtualization | Appliance | VMware Guest | N/A | N/A | *** | N/A | Proprietary | 4 |
| 4 |
| | 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Large | Physical | Server | Physical | Fujitsu | M4000 | *** | 700144 | Solaris 10 | 4 |
| 4 |
| 16 |
| 64 |
| Flood |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Large | Physical | Server | Physical | Fujitsu | M4000 | *** | 700145 | Solaris 10 | 4 |
| 4 |
| 16 |
| 64 |
| Flood |
| *** | DTC | Test | Unix - Solaris | Low | Physical | Large | Physical | Server | Physical | Fujitsu | M4000 | *** | 700148 | Solaris 10 | 4 |
| 4 |
| 16 |
| 64 |
| Flood |
| *** | DTC | Development | Unix - Solaris | Low | Physical | Large | Physical | Server | Physical | Fujitsu | M4000 | *** | 700146 | Solaris 10 | 4 |
| 4 |
| 16 |
| 64 |
| Flood |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Large | Physical | Server | Physical | Fujitsu | M4000 | *** | 700147 | Solaris 10 | 4 |
| 4 |
| 16 |
| 64 |
| Flood |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703797 | W2008 Std R2 | 2 |
| 12 |
| 12 |
| 24 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703798 | W2008 Std R2 | 2 |
| 12 |
| 12 |
| 24 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703799 | W2008 Std R2 | 2 |
| 12 |
| 12 |
| 24 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | t2000 | *** | 700107 | Solaris 10 | 1 |
| 4 |
| 4 |
| 16 |
| Flood |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 101650 | Solaris 10 | 1 |
| 4 |
| 4 |
| 16 |
| Flood |
| *** | SATC | DR | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 101690 | Solaris 10 | 1 |
| 4 |
| 4 |
| 16 |
| Flood |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703796 | W2008 Std R2 | 2 |
| 12 |
| 12 |
| 24 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703800 | W2008 Std R2 | 2 |
| 12 |
| 12 |
| 24 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 530698 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 530699 | W2008 Ent | 2 |
| 8 |
| 16 |
| 32 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 3 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | BL460c | *** | 703795 | W2008 Ent | 2 |
| 12 |
| 12 |
| 12 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 8 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 703849 | Red Hat Enterprise Server 5 | 2 |
| 4 |
| 8 |
| 12 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Linux | Standard | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 703850 | Red Hat Enterprise Server 5 | 2 |
| 4 |
| 8 |
| 12 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 700186 | W2008 ENT | 2 |
| 12 |
| 12 |
| 48 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 700185 | W2008 ENT | 2 |
| 12 |
| 12 |
| 48 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 700184 | W2008 ENT | 2 |
| 12 |
| 12 |
| 48 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7825 | *** | 700270 | W2008 Ent | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | Vmware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 3 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 703831 | Solaris 10 | 1 |
| 4 |
| 4 |
| 16 |
| Flood |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Unix - Solaris | Low | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 700225 | Solaris 10 | 1 |
| 4 |
| 4 |
| 16 |
| Flood |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | T2000 | *** | 700224 | Solaris 10 | 1 |
| 4 |
| 4 |
| 16 |
| Flood |
| *** | DTC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | QA | Virtual Host | N/A | Physical | N/A | Physical | Server | Physical | HP | DL585 | *** | 500859 | VMware ESX | 2 |
| 4 |
| 8 |
| 64 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | CentOS 5 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | Cisco | UCS B200 M2 | *** | 703872 | VMWare ESX | 2 |
| 4 |
| | 12 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | Cisco | UCS B200 M2 | *** | 703836 | VMWare ESX | 2 |
| 4 |
| | 12 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | Cisco | UCS B200 M2 | *** | 703837 | VMWare ESX | 2 |
| 4 |
| | 12 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | Cisco | UCS B200 M2 | *** | 703838 | VMWare ESX | 2 |
| 4 |
| | 12 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | Cisco | UCS B200 M2 | *** | 703839 | VMWare ESX | 2 |
| 4 |
| | 12 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | Cisco | UCS B200 M2 | *** | 703840 | VMWare ESX | 2 |
| 4 |
| | 12 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | Cisco | UCS B200 M2 | *** | 703841 | VMWare ESX | 2 |
| 4 |
| | 12 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | Cisco | UCS B200 M2 | *** | 703842 | VMWare ESX | 2 |
| 4 |
| | 12 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMWare Host | Cisco | UCS B200 M2 | *** | 700262 | VMWare ESX | 2 |
| 4 |
| | 48 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMWare Host | Cisco | UCS B200 M2 | *** | 700258 | VMWare ESX | 2 |
| 4 |
| | 48 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMWare Host | Cisco | UCS B200 M2 | *** | 700235 | VMWare ESX | 2 |
| 4 |
| | 48 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMWare Host | Cisco | UCS B200 M2 | *** | 700261 | VMWare ESX | 2 |
| 4 |
| | 48 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMWare Host | Cisco | UCS B200 M2 | *** | 700260 | VMWare ESX | 2 |
| 4 |
| | 48 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMWare Host | Cisco | UCS B200 M2 | *** | 700259 | VMWare ESX | 2 |
| 4 |
| | 48 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMWare Host | Cisco | UCS B200 M2 | *** | 700256 | VMWare ESX | 2 |
| 4 |
| | 48 |
| |
| *** | DTC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMWare Host | Cisco | UCS B200 M2 | *** | 700255 | VMWare ESX | 2 |
| 4 |
| | 48 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Extra Large | Physical | Server | Physical | HP | DL580 | *** | 703853 | Red Hat Enterprise Server 5 | 4 |
| 40 |
| 40 |
| 128 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Extra Large | Physical | Server | Physical | HP | DL580 | *** | 703854 | Red Hat Enterprise Server 5 | 4 |
| 40 |
| 40 |
| 128 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | QA | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | SafeNet | i450 | *** | 703633 | Ingrian Hardened Linux | — |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | SafeNet | i450 | *** | 703631 | | — |
| — |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | SafeNet | i450 | *** | 703632 | | — |
| — |
| | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Unix - Solaris | Low | Virtual | N/A | Multi-Tenant - Virtualization | Server | Zone | N/A | N/A | *** | N/A | Solaris 10 | 8 |
| 8 |
| | 12 |
| Infra |
| *** | DTC | Production | Unix - Solaris | Standard | Virtual | N/A | Multi-Tenant - Virtualization | Server | Zone | N/A | N/A | *** | N/A | Solaris 10 | 8 |
| 8 |
| | 12 |
| Infra |
| *** | DTC | Test | Unix - Solaris | Low | Virtual | N/A | Multi-Tenant - Virtualization | Server | Zone | N/A | N/A | *** | N/A | Solaris 10 | 8 |
| 8 |
| | 12 |
| Misc |
| *** | DTC | Test | Unix - Solaris | Low | Virtual | N/A | Multi-Tenant - Virtualization | Server | Zone | N/A | N/A | *** | N/A | Solaris 10 | 8 |
| 8 |
| | 12 |
| Misc |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | SPARC T3-1 | *** | 700180 | Solaris 10 | 2 |
| 16 |
| | 24 |
| Infra |
| *** | DTC | Test | Unix - Solaris | Low | Physical | N/A | Physical | Server | PHYSICAL | Sun | SPARC T3-1 | *** | 700179 | Solaris 10 | 2 |
| 16 |
| | 24 |
| Misc |
| *** | DTC | Development | Unix - Solaris | Low | Physical | Medium | Physical | Server | PHYSICAL | Sun | SPARC T3-1 | *** | 700177 | Solaris 10 | 2 |
| 16 |
| | 24 |
| Oracle Fin |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Medium | Physical | Server | PHYSICAL | Sun | SPARC T3-1 | *** | 700178 | Solaris 10 | 2 |
| 16 |
| | 24 |
| Oracle Fin |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | N/A | Physical | Server | PHYSICAL | Sun | SPARC T3-1 | *** | 700181 | Solaris 10 | 2 |
| 16 |
| | 24 |
| Misc |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Ingrian | i430 | *** | 700274 | N/A | — |
| — |
| | | |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Development | N/A | N/A | N/A | N/A | Physical | Server | Physical | Apple | Mac Mini | *** | 703875 | Mac OS X Lion 10 Server | 4 |
| 4 |
| 16 |
| 8 |
| |
| *** | DTC | QA | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX 6 | 2 |
| 2 |
| | 8 |
| Next Gen Fraud |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 24 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Cloud | Appliance | VMware Guest | N/A | N/A | *** | N/A | N/A | 4 |
| 4 |
| | 8 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Cloud | Appliance | VMware Guest | N/A | N/A | *** | N/A | N/A | 4 |
| 4 |
| | 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Development | Windows | Low | Physical | Small | Physical | Server | Physical | HP | DL380 | *** | 313573 | W2003 Ent | 2 |
| 4 |
| 8 |
| 2 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W7 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W7 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Large | Physical | Server | Physical | HP | DL580 | *** | 703615 | Red Hat Enterprise Server 5 | 4 |
| 24 |
| 24 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | PHYSICAL | HP | BL460c | *** | 530811 | W2008 Ent R2 | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 1 |
| 1 |
| 1 |
| 12 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 4 | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | DR | Linux | Low | Physical | Small | Physical | Server | Physical | IBM | x335 | *** | 703884 | Linux | — |
| — |
| 4 |
| 32 |
| |
| *** | SATC | DR | iSeries | N/A | Physical | N/A | Physical | Server | Physical | IBM | i570 | *** | 703885 | V7R1 | | 4 |
| 4 |
| 36 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Fedora 12 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 3 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Development | N/A | N/A | N/A | N/A | Physical | Server | Physical | Apple | Mac Mini | *** | 703886 | Mac OS X Lion 10 Server | 4 |
| 4 |
| 16 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Unix - Solaris | Standard | Virtual | N/A | Multi-Tenant - Virtualization | Server | Zone | N/A | N/A | *** | N/A | Solaris | | — |
| | | Infra |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | Cisco | MCS 7825 | *** | 703881 | W2008 Std | 1 |
| 2 |
| 2 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | PHYSICAL | BlueCat | Proteus 5000 | *** | 700210 | Proprietary | 1 |
| — |
| | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | | CLUSTER | N/A | N/A | *** | N/A | W2003 Ent | — |
| — |
| | | |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Linux | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Linux | 1 |
| 1 |
| 1 |
| — |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Linux | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | WXP | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | HP | DL185 | *** | 703895 | Red Hat Enterprise Server 5 | — |
| 8 |
| | 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 2 |
| |
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | DR | Linux | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Linux | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Linux | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703890 | Red Hat Enterprise Server 5 | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703891 | Red Hat Enterprise Server 5 | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703892 | Red Hat Enterprise Server 5 | 2 |
| 12 |
| 12 |
| 72 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL380 | *** | 703893 | Red Hat Enterprise Server 5 | 2 |
| 12 |
| 12 |
| 72 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | DTC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| — |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 15 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Linux | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Linux | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMWare Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMWare Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | | W2003 Std | 2 |
| — |
| 2 |
| | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 6 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 6 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 8 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 2 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 10 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 10 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 10 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 10 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 10 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 10 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 10 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 14 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | SATC | Test | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 4 |
| 4 |
| 4 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 STD | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | DR | Windows | Low | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 ENT | 4 |
| 4 |
| 4 |
| | |
| *** | SATC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 10 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Virtual Host | N/A | Physical | N/A | Physical | Server | VMware Host | HP | BL490c | *** | 703873 | VMware ESX | 2 |
| 4 |
| | 64 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Dell | PowerEdge R710 | *** | 703900 | Proprietary | 2 |
| 2 |
| | | |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Dell | PowerEdge R710 | *** | 703901 | Proprietary | 2 |
| 2 |
| | | |
| *** | SATC | Development | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | QA | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | DTC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | 2 |
| 2 |
| | | Infra |
| *** | DTC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | 2 |
| 2 |
| | | Infra |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 12 |
| |
| *** | SATC | QA | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 6 |
| 6 |
| 6 |
| 4 |
| |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 4 |
| Credco |
| *** | SATC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Infra |
| *** | SATC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Infra |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Test | N/A | N/A | N/A | N/A | Cloud | Appliance | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| | 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 2 |
| Credco |
| *** | DTC | DR | Unix - AIX | Low | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 1 |
| | 2 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | Power 770 | *** | N/A | AIX | | 2 |
| | 4 |
| Credco |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 6 |
| |
| *** | DTC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 6 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 255 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 16 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 2 |
| 2 |
| 2 |
| 14 |
| |
| *** | SATC | DR | Windows | Low | Physical | Small | Physical | Server | PHYSICAL | HP | DL380 | *** | 520366 | W2008 Std | 2 |
| 2 |
| 4 |
| 4 |
| |
| *** | SATC | Staging | Linux | Low | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 703896 | Red Hat Enterprise Server 5 | 2 |
| 8 |
| 16 |
| 64 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Ent | 4 |
| 4 |
| 4 |
| 7 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Single-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2000 Std | 4 |
| 4 |
| 4 |
| 32 |
| |
| *** | DTC | Test | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 1 |
| 1 |
| 1 |
| 8 |
| |
| *** | DTC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | P570-SC | *** | N/A | AIX | 1 |
| 1 |
| | 2 |
| Infra |
| *** | DTC | Production | Unix - AIX | Standard | Virtual | N/A | Shared | Server | LPAR | IBM | P570-SC | *** | N/A | AIX | 1 |
| 1 |
| | 2 |
| Infra |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Test | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Websense | V10000 | *** | | Red Hat Enterprise Server 5 | 2 |
| 8 |
| | 12 |
| |
| *** | DTC | Production | N/A | N/A | N/A | N/A | Physical | Appliance | Physical | Websense | V10000 | *** | | Red Hat Enterprise Server 5 | 2 |
| 8 |
| | 12 |
| |
| *** | SATC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | N/A | N/A | N/A | N/A | Cloud | Appliance | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| | 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 1 |
| 1 |
| 1 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Ent | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Large | Physical | Server | Physical | HP | DL580 | *** | 703899 | Red Hat Enterprise Server 5 | 4 |
| 8 |
| 32 |
| 64 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Staging | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 1 |
| 1 |
| 1 |
| 1 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 12 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 12 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 703905 | W2003 Ent | 1 |
| 4 |
| 4 |
| 24 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 1 |
| 1 |
| 1 |
| 2 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | DTC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | HP | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 6 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Staging | Linux | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 16 |
| |
| *** | SATC | Production | Windows | Standard | Physical | Small | Physical | Server | Physical | HP | BL460c | *** | 703889 | W2008 Ent | 2 |
| 4 |
| 8 |
| 32 |
| |
| *** | SATC | Development | Windows | Low | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 4 |
| 4 |
| 4 |
| 16 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 703902 | Red Hat Enterprise Server 5 | 2 |
| 8 |
| 16 |
| 64 |
| |
| *** | SATC | Production | Linux | Standard | Physical | Medium | Physical | Server | Physical | HP | DL580 | *** | 703904 | Red Hat Enterprise Server 5 | 2 |
| 8 |
| 16 |
| 64 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Suse Linux Ent Server 11 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Small | Multi-Tenant - Virtualization | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std | 2 |
| 2 |
| 2 |
| 2 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | SATC | Development | Linux | Low | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
| *** | SATC | Production | Linux | Standard | Virtual | Large | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | Red Hat Enterprise Server 5 | 6 |
| 6 |
| 6 |
| 32 |
| |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | | | | | | | | | | | | | | | | | |
| *** | DTC | Production | Windows | Standard | Virtual | Small | Cloud | Server | VMware Guest | N/A | N/A | *** | | W2003 Std | 2 |
| 2 |
| 2 |
| 4 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | HP | | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | HP | | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | HP | | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | HP | | *** | N/A | W2008 Ent R2 | 4 |
| 4 |
| 4 |
| 8 |
| |
| *** | DTC | Staging | Windows | Low | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2003 Std | 4 |
| 4 |
| 4 |
| 4 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | SATC | Production | Windows | Standard | Virtual | Medium | Cloud | Server | VMware Guest | N/A | N/A | *** | N/A | W2008 Std R2 | 2 |
| 2 |
| 2 |
| 8 |
| |
| *** | DTC | Production | Unix - Solaris | Standard | Physical | Small | Physical | Server | Physical | SUN | M3000 | *** | 703832 | Solaris 10 | 1 |
| 4 |
| 4 |
| | Flood |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Networks - Data Centers
|
| | | | | | | |
| Serial Number | Dell Category | Host Name | Mfr Name | Mfr Model | Asset Tag | Location | Service Type |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327603 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327607 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327547 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327553 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327609 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327608 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327573 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327574 | Westlake | Managed |
| *** | Wireless | *** | Cisco | 4400 Wireless LAN Controller | 100536 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327602 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327517 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327518 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327599 | Westlake | Managed |
| *** | Wireless | *** | Cisco | 2700 Series Wireless Location Appliance | 100541 | Westlake | Managed |
| *** | Wireless | *** | Cisco | 4400 Wireless LAN Controller | 100540 | Westlake | Managed |
| *** | Wireless | *** | Cisco | 4400 Wireless LAN Controller | 100539 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 319043 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327527 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327614 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327530 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327613 | Westlake | Managed |
| *** | Router | *** | Cisco | 3,630 | 316605 | Westlake | Managed |
| *** | Router | *** | Cisco | 3,630 | 313685 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3560 | 316604 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3560 | 100820 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3560 | 100821 | Westlake | Managed |
| *** | WAN | *** | Digital Link | DL3800 | 100822 | Westlake | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 100823 | Westlake | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 100824 | Westlake | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 100826 | Westlake | Managed |
| *** | Router | *** | Cisco | 26xx Series Modular Access Router | 100827 | Westlake | Managed |
| *** | Router | *** | Cisco | 26xx Series Modular Access Router | 100829 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3560 | 100778 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 100779 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 100780 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3750 | 100781 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3550 | 100782 | Westlake | Hosted |
| *** | Router | *** | Cisco | 2801 Integrated Services Router | 319084 | Westlake | Hosted |
| *** | Router | *** | Cisco | 2801 Integrated Services Router | 319085 | Westlake | Hosted |
| *** | Phys FW Standalone | *** | Cisco | PIX 525 Security Appliance | 319087 | Westlake | Hosted |
| *** | Phys FW Standalone | *** | Cisco | PIX 525 Security Appliance | 319086 | Westlake | Hosted |
| *** | Phys FW Standalone | *** | Cisco | PIX 525 Security Appliance | 100777 | Westlake | Hosted |
| *** | Security | *** | IBM ISS | G2000 Intrusion Prevention Appliance | 100265 | Westlake | Managed |
| *** | Security | *** | IBM ISS | G2000 Intrusion Prevention Appliance | 100264 | Westlake | Managed |
| *** | Security | *** | IBM ISS | G2000 Intrusion Prevention Appliance | 100263 | Westlake | Managed |
| *** | Security | *** | IBM ISS | GX5108 Intrusion Prevention System | 327570 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 100270 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 100269 | Westlake | Managed |
| *** | Sniffer | *** | Network General | Sniffer S4100 ET03 | 318494 | Westlake | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 522 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Sniffer | *** | Network General | Sniffer S4100 ET03 | 318493 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 100276 | Westlake | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 327534 | Westlake | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 316095 | Westlake | Managed |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | 327525 | Westlake | Managed |
| *** | Security | *** | IBM ISS | GX5108 Intrusion Prevention System | 327528 | Westlake | Managed |
| *** | Security | *** | IBM ISS | G2000 Intrusion Prevention Appliance | 100279 | Westlake | Managed |
| *** | Security | *** | IBM ISS | G2000 Intrusion Prevention Appliance | 100281 | Westlake | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 100286 | Westlake | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 100287 | Westlake | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 100288 | Westlake | Managed |
| *** | Router | *** | Cisco | 3,745 | 313765 | Westlake | Managed |
| *** | Router | *** | Cisco | 18xx | 100291 | Westlake | Managed |
| *** | Router | *** | Cisco | 1700 Series Modular Access Routers | 100293 | Westlake | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 327532 | Westlake | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 327536 | Westlake | Managed |
| *** | VPN | *** | Cisco | AS53XX | 100294 | Westlake | Managed |
| *** | VPN | *** | Cisco | AS53XX | 100295 | Westlake | Managed |
| *** | VPN | *** | Cisco | VPN 3000 Series Concentrator, 2U | 318547 | Westlake | Managed |
| *** | Router | *** | Cisco | 26xx Series Modular Access Router | 319145 | Westlake | Managed |
| *** | Router | *** | Cisco | 3845 Integrated Services Router | 319148 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327544 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327545 | Westlake | Managed |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | 327538 | Westlake | Managed |
| *** | VPN | *** | Cisco | VPN 3000 Series Concentrator, 2U | 318550 | Westlake | Managed |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | 327537 | Westlake | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 327533 | Westlake | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 327535 | Westlake | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 327531 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327526 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327523 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327522 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 327582 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 327581 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327542 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327543 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 327580 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 327595 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 327589 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 327591 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 327590 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 327617 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 327594 | Westlake | Managed |
| *** | Phys FW Standalone | *** | f5 | BIG-IP 1500 Series | 327633 | Westlake | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 1500 Series | 327584 | Westlake | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 100313 | Westlake | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 327593 | Westlake | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 327592 | Westlake | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 327540 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 327631 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 327629 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 327616 | Westlake | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 523 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Router | *** | Cisco | 2821 Integrated Services Router | 100742 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3750 | 313661 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327561 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327565 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327566 | Westlake | Managed |
| *** | Security | *** | nCircle | nCircle IP360 | 101320 | Westlake | Managed |
| *** | Security | *** | nCircle | nCircle IP360 | 101321 | Westlake | Managed |
| *** | Security | *** | nCircle | nCircle IP360 | 101322 | Westlake | Managed |
| *** | Security | *** | nCircle | nCircle IP360 | 101324 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327604 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327610 | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | 101506 | Westlake | Hosted |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | 101507 | Westlake | Hosted |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | 101508 | Westlake | Hosted |
| *** | Router | *** | Cisco | 2821 Integrated Services Router | 101552 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3560 | | Westlake | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 101568 | Westlake | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 327585 | Westlake | Managed |
| *** | Switch | *** | 3Com | 3C16472 | 101572 | Westlake | Managed |
| *** | Security | *** | IBM ISS | ES 1500 Enterprise Scanner | 520065 | Santa Ana | Managed |
| *** | Security | *** | Symantec | SIM 9550 Security Information Manager | 520118 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522809 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522810 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522828 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 531351 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522829 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 541353 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522826 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522827 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100/1000 + 4 SFP Std | 530844 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5200 | 522818 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 522819 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 522820 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 522821 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Cisco | PIX 525 Security Appliance | 522790 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Cisco | PIX 525 Security Appliance | 522791 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 522782 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 522779 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 | 522792 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100/1000 + 4 SFP Enh | 319014 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 | 522786 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | 522787 | Santa Ana | Managed |
| *** | VPN | *** | Cisco | VPN 3000 Series Concentrator, 2U | 522785 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3620 Mulitfunction Platform Router | 523233 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3620 Mulitfunction Platform Router | 523234 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 520074 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 520073 | Santa Ana | Managed |
| *** | Security | *** | IBM ISS | G2000 Intrusion Prevention Appliance | 523220 | Santa Ana | Managed |
| *** | Security | *** | IBM ISS | G2000 Intrusion Prevention Appliance | 523215 | Santa Ana | Managed |
| *** | Security | *** | BlueCoat | ProxySG 800 | 521347 | Santa Ana | Managed |
| *** | Security | *** | BlueCoat | ProxySG 800 | 521350 | Santa Ana | Managed |
| *** | Security | *** | BlueCoat | ProxySG 800 | 523213 | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 524 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Security | *** | BlueCoat | ProxySG 800 | 523214 | Santa Ana | Managed |
| *** | Router | *** | Cisco | CISCO 7609 Internet Router | 522717 | Santa Ana | Managed |
| *** | Router | *** | Cisco | CISCO 7609 Internet Router | 522716 | Santa Ana | Managed |
| *** | Security | *** | IBM ISS | G2000 Intrusion Prevention Appliance | 530740 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 522822 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 522823 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522811 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522812 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 | 522794 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100/1000 + 4 SFP Enh | 522795 | Santa Ana | Managed |
| *** | VPN | *** | Cisco | VPN 3000 Series Concentrator, 2U | 522783 | Santa Ana | Managed |
| *** | VPN | *** | Cisco | VPN 3000 Series Concentrator, 2U | 522784 | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | 52563 | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Aironet 1200 Access Point AIR-AP1231G-A-K9 | | Santa Ana | Managed |
| *** | Wireless | *** | Cisco | Wireless LAN Solution Engine | 522815 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522813 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 | 523248 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3845 Integrated Services Router | 523247 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 530311 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 530312 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 1700 Series Modular Access Routers | 523232 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3845 Integrated Services Router | 521271 | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 521412 | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 525 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 521411 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 1700 Series Modular Access Routers | 523231 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 18xx | 520068 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Enh | 523299 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 522800 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 522799 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 520081 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 523242 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 522803 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-port 10/100 + 4 SFP Std | 522797 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | WS-C3550-24 24-Port 10/100 2 100BaseX | 520055 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 522801 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 531336 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 523250 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 523249 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 522802 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 522798 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 522796 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 522804 | Santa Ana | Managed |
| *** | Phys FW Standalone | *** | Cisco | PIX 515E Security Appliance | 523237 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 1700 Series Modular Access Routers | 523238 | Santa Ana | Managed |
| *** | Phys FW Standalone | *** | Juniper | ISG 2000 | 523200 | Santa Ana | Managed |
| *** | Phys FW Standalone | *** | Juniper | ISG 2000 | 522760 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 531335 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 531343 | Santa Ana | Managed |
| *** | Phys FW Standalone | *** | Juniper | ISG 2000 | 522759 | Santa Ana | Managed |
| *** | Phys FW Standalone | *** | Cisco | PIX 515E Security Appliance | 523202 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 1700 Series Modular Access Routers | 523201 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 531334 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 531341 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 12-port SFP Standard | 522768 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522735 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 531365 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 12-port SFP Standard | 522770 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 523205 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 522773 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 523239 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 522838 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 530847 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 522830 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 522833 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 520079 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 531177 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 523230 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 522834 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 522831 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 530184 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 522832 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 522839 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 522836 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 522835 | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 526 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Router | *** | Cisco | 2611XM | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 523241 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 2960 48 10/100 + 2 T/SFP LAN Base Image | 531404 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 521043 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | NetScreen-5400 | 521042 | Santa Ana | Managed |
| *** | Security | *** | nCircle | nCircle IP360 | 521404 | Santa Ana | Managed |
| *** | Security | *** | nCircle | nCircle IP360 | 521405 | Santa Ana | Managed |
| *** | Router | *** | Adtran | Atlas 830 | 521328 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2801 Integrated Services Router | 521435 | Santa Ana | Managed |
| *** | Security | *** | nCircle | nCircle IP360 | 521683 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 531344 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2611XM | 531671 | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 521445 | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 530189 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2801 Integrated Services Router | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2801 Integrated Services Router | 520083 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3725 Multiservice Access Router | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 | 521777 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 | | Santa Ana | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 6400 Series | 101342 | Santa Ana | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 3400 Series | | Santa Ana | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 3400 Series | | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 3400 Series | | Santa Ana | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 6400 Series | 521922 | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 521989 | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 530658 | Santa Ana | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 6400 Series | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2621 Modular Access Router | 530132 | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 2960 48 10/100 + 2 T/SFP LAN Lite Image | | Santa Ana | Managed |
| *** | Switch | *** | HP | ProCurve Switch 2824 J4903A | 101592 | Westlake | Hosted |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120G-S for HP | 101626 | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120G-S for HP | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120G-S for HP | | Westlake | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327612 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 327611 | Westlake | Managed |
| *** | Router | *** | Cisco | 26xx Series Modular Access Router | 101628 | Westlake | Hosted |
| *** | Router | *** | Cisco | 18xx | 100172 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100/1000 + 4 SFP Std | 319031 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 319043 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327549 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 531350 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-port 10/100 + 4 SFP Std | 541352 | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 527 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 530843 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 530841 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 530842 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 101636 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-port 10/100 + 4 SFP Std | 530836 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-port 10/100 + 4 SFP Std | 530837 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3560 | 101639 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 101640 | Westlake | Hosted |
| *** | Security | *** | IBM ISS | G400 Intrusion Prevention Appliance | 523217 | Santa Ana | Managed |
| *** | DNS | *** | Bluecat | Adonis 750 DNS/DHCP Management | 530908 | Santa Ana | Managed |
| *** | DNS | *** | Bluecat | Adonis 750 DNS/DHCP Management | 530909 | Santa Ana | Managed |
| *** | DNS | *** | Bluecat | Adonis 750 DNS/DHCP Management | 531046 | Santa Ana | Managed |
| *** | DNS | *** | Bluecat | Adonis 750 DNS/DHCP Management | 530911 | Santa Ana | Managed |
| *** | DNS | *** | Bluecat | Adonis 750 DNS/DHCP Management | 530912 | Santa Ana | Managed |
| *** | Security | *** | Imperva | SecureSphere G4 FTL Gateway | 530915 | Santa Ana | Managed |
| *** | Security | *** | nCircle | nCircle IP360 | 531094 | Santa Ana | Managed |
| *** | Security | *** | Imperva | SecureSphere G8 FTL Gateway | 101653 | Westlake | Managed |
| *** | Security | *** | Imperva | SecureSphere MX FTL Management Server | 101654 | Westlake | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | 101662 | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | 101663 | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | 101664 | Westlake | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 521997 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2821 Integrated Services Router | 101692 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 2960 48 10/100 + 2 T/SFP LAN Base Image | 101696 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 2960 48 10/100 + 2 T/SFP LAN Base Image | 101694 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 101695 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 101693 | Westlake | Hosted |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 101717 | Westlake | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 101718 | Westlake | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 101720 | Westlake | Hosted |
| *** | Security | *** | 3Com | Tipping Point 400 | 101724 | Westlake | Hosted |
| *** | LB Clustered | *** | f5 | BIG-IP 6400 Series | 530990 | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | DNS | *** | Bluecat | Adonis 750 DNS/DHCP Management | 101661 | Westlake | Managed |
| *** | DNS | *** | Bluecat | Adonis 750 DNS/DHCP Management | 101660 | Westlake | Managed |
| *** | DNS | *** | Bluecat | Adonis 750 DNS/DHCP Management | 101658 | Westlake | Managed |
| *** | DNS | *** | Bluecat | Adonis 750 DNS/DHCP Management | 101659 | Westlake | Managed |
| *** | DNS | *** | Bluecat | Adonis 750 DNS/DHCP Management | 101657 | Westlake | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 318325 | Westlake | Hosted |
| *** | Router | *** | Cisco | 7206 VXR Router | 531106 | Westlake | Managed |
| *** | Router | *** | Cisco | 7206 VXR Router | 531100 | Westlake | Managed |
| *** | Router | *** | Cisco | 2801 Integrated Services Router | 101733 | Westlake | Managed |
| *** | Router | *** | Cisco | 7204 VXR Router | 531313 | Santa Ana | Managed |
| *** | Security | *** | SafeNet | Link Encryptor | 101820 | Westlake | Hosted |
| *** | Sniffer | *** | Network General | Sniffer S4100 ET03 | 531174 | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 528 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Security | *** | IBM ISS | G400 Intrusion Prevention Appliance | 531197 | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120G-S for HP | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120G-S for HP | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120G-S for HP | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 1600 Series | 101809 | Westlake | Hosted |
|
| | | | | | | |
| *** | Switch | *** | Cisco | Catalyst 2350 48-port 10/100/1000 + 2 X2 TwinGig | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 2350 48-port 10/100/1000 + 2 X2 TwinGig | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 529 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Enh | 531328 | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327552 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 530857 | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 530 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 531 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | 531384 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | 531385 | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 532 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Switch | *** | Cisco | Catalyst 4900M Switch | 531474 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4900M Switch | 531475 | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 1500 Series | | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 1500 Series | | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 1500 Series | | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 1500 Series | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 2950 24-port | 500380 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 2950 24-port | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 531442 | Santa Ana | Hosted |
| *** | Router | *** | Cisco | 2611XM | 531441 | Santa Ana | Hosted |
| *** | Router | *** | Cisco | 2611XM | 531440 | Santa Ana | Hosted |
| *** | Router | *** | Cisco | 2611XM | 531439 | Santa Ana | Hosted |
| *** | Router | *** | Cisco | 2611XM | 531438 | Santa Ana | Hosted |
| *** | Phys FW Clustered | *** | Cisco | PIX 525 Security Appliance | 531437 | Santa Ana | Hosted |
| *** | Phys FW Clustered | *** | Cisco | PIX 525 Security Appliance | 531436 | Santa Ana | Hosted |
| *** | Phys FW Clustered | *** | Cisco | PIX 525 Security Appliance | 531435 | Santa Ana | Hosted |
| *** | Phys FW Clustered | *** | Cisco | PIX 525 Security Appliance | 531434 | Santa Ana | Hosted |
| *** | Phys FW Clustered | *** | Cisco | PIX 525 Security Appliance | 531433 | Santa Ana | Hosted |
| *** | Phys FW Clustered | *** | Cisco | PIX 525 Security Appliance | 531432 | Santa Ana | Hosted |
| *** | Router | *** | Cisco | 1700 Series Modular Access Routers | 531430 | Santa Ana | Hosted |
| *** | Router | *** | Cisco | 1700 Series Modular Access Routers | 531429 | Santa Ana | Hosted |
| *** | Switch | *** | Cisco | Catalyst 6509 Switch | 531428 | Santa Ana | Hosted |
| *** | Router | *** | Cisco | 2801 Integrated Services Router | 531499 | Santa Ana | Hosted |
| *** | Switch | *** | NETGEAR | GS516T 16-port 10/100/1000 Mbps Gigabit Switch | 531500 | Santa Ana | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 531501 | Santa Ana | Hosted |
| *** | Phys FW Clustered | *** | Cisco | PIX 525 Security Appliance | 531502 | Santa Ana | Hosted |
| *** | Phys FW Clustered | *** | Cisco | PIX 525 Security Appliance | 531503 | Santa Ana | Hosted |
| *** | Security | *** | Barracuda | Spam & Virus Firewall Model 400 | 531509 | Santa Ana | Hosted |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Hosted |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 531539 | Santa Ana | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 531540 | Santa Ana | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 531555 | Santa Ana | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 531556 | Santa Ana | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 531582 | Santa Ana | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 531583 | Santa Ana | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3560 | 530231 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 1841 Integrated Services Router | | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 531584 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | 101777 | Westlake | Managed |
| *** | Router | *** | Cisco | 3845 Integrated Services Router | 101778 | Westlake | Managed |
| *** | Router | *** | Cisco | 3845 Integrated Services Router | 101779 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 531712 | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 531717 | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 531718 | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 531719 | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 531720 | Santa Ana | Managed |
| *** | WAN | *** | Riverbed | Steelhead 2050 WAN Optimization Appliance | 101845 | Westlake | Hosted |
| *** | WAN | *** | Riverbed | Steelhead 2050 WAN Optimization Appliance | 101847 | Westlake | Hosted |
| *** | Switch | *** | HP | ProCurve Switch 2848 J4904A | 101848 | Westlake | Hosted |
| *** | Switch | *** | HP | ProCurve Switch 2848 J4904A | 101849 | Westlake | Hosted |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 533 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | 101760 | Westlake | Hosted |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | 101761 | Westlake | Hosted |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | 531748 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 531761 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 531762 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 531763 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 531764 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4900M Switch | 531766 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4900M Switch | 531767 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4900M Switch | 101883 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4900M Switch | 101882 | Westlake | Managed |
| *** | Security | *** | IBM ISS | G2000 Intrusion Prevention Appliance | 101898 | Westlake | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 1600 Series | 531841 | Westlake | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 1600 Series | 531842 | Santa Ana | Managed |
| *** | Switch | *** | HP | ProCurve Switch 2824 J4903A | 531872 | Santa Ana | Managed |
| *** | Switch | *** | HP | ProCurve Switch 2848 J4904A | 531870 | Santa Ana | Managed |
| *** | Switch | *** | HP | ProCurve Switch 2848 J4904A | 531871 | Santa Ana | Managed |
| *** | WAN | *** | Riverbed | Steelhead 2050 WAN Optimization Appliance | 531157 | Santa Ana | Managed |
| *** | WAN | *** | Riverbed | Steelhead 2050 WAN Optimization Appliance | 531158 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 531702 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 532058 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 532059 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 532060 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | 532061 | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 1500 Series | 101887 | Westlake | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 1500 Series | 101886 | Westlake | Managed |
| *** | Router | *** | Cisco | 18xx | | Westlake | Hosted |
| *** | Router | *** | Cisco | 2620 Modular Access Router | | Westlake | Hosted |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3020 | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 1841 Integrated Services Router | | Westlake | Managed |
| *** | Router | *** | Cisco | 3945 Integrated Services Router | 102508 | Westlake | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 1500 Series | | Westlake | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Switch | *** | HP | Cisco Catalyst Blade Switch 3120X-S for HP | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 534 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Router | *** | Cisco | 7200 VXR Router | 703544 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7204 VXR Router | 703597 | Santa Ana | Managed |
| *** | Security | *** | IBM ISS | GX5108 Intrusion Prevention System | 703629 | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 3900 Series | 703638 | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 3900 Series | 703639 | Santa Ana | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 3900 Series | 703640 | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect Flex-10 10Gb Ethernet Module | | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect Flex-10 10Gb Ethernet Module | | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect 4Gb Fibre Channel Module | | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect 4Gb Fibre Channel Module | | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect Flex-10 10Gb Ethernet Module | | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect Flex-10 10Gb Ethernet Module | | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect 8Gb Fibre Channel 24-Port Module | | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect 8Gb Fibre Channel 24-Port Module | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2801 Integrated Services Router | 703648 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2801 Integrated Services Router | 703649 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 1900 Series Router | 703650 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2821 Integrated Services Router | 703658 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2821 Integrated Services Router | 703699 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2821 Integrated Services Router | 703700 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 1841 Integrated Services Router | 703667 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 1841 Integrated Services Router | 703668 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 1900 Series Router | 700081 | Westlake | Hosted |
| *** | Router | *** | Cisco | 1900 Series Router | 700082 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 4948 | 700087 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 700088 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100 + 2 SFP Std | 319046 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 703763 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 703764 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 700091 | Westlake | Managed |
| *** | Router | *** | Cisco | 2801 Integrated Services Router | 700080 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 521058 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 521063 | Santa Ana | Managed |
| *** | Security | *** | IBM ISS | GX5208 Intrusion Prevention System | | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 521059 | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 521062 | Santa Ana | Managed |
| *** | Security | *** | IBM ISS | GX5208 Intrusion Prevention System | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-port 10/100 + 4 SFP Std | 700140 | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 3750 48-port 10/100 + 4 SFP Std | 700141 | Westlake | Hosted |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 700165 | Westlake | Managed |
| *** | Security | *** | IBM ISS | GX5108 Intrusion Prevention System | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | | Santa Ana | Managed |
| *** | Router | *** | 3Com | Multi-Service Router 20-40 | | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 3600 Series | | Santa Ana | Managed |
| *** | LB Standalone | *** | f5 | BIG-IP 6900 Series | 703517 | Santa Ana | Managed |
| *** | Switch | *** | NETGEAR | GS516T 16-port 10/100/1000 Mbps Gigabit Switch | | Santa Ana | Managed |
| *** | Security | *** | nCircle | nCircle IP360 | 703794 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3825 Integrated Services Router | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 521132 | Santa Ana | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 535 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Router | *** | 3Com | Multi-Service Router 20-40 | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | | Santa Ana | Managed |
| *** | VPN | *** | Check Point | VPN-1 Edge Appliance | | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 703805 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 703806 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 700203 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 327567 | Westlake | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 703815 | Santa Ana | Managed |
| *** | Security | *** | SafeNet | Link Encryptor | 13699 | Santa Ana | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6900 Series | 700208 | Westlake | Managed |
| *** | LB Clustered | *** | f5 | BIG-IP 6900 Series | 700209 | Westlake | Managed |
| *** | Security | *** | Imperva | SecureSphere G4 FTL Gateway | 703828 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 2811 Integrated Services Router | 700219 | Westlake | Managed |
| *** | Security | *** | nCircle | nCircle IP360 | 703846 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 48-Port 10/100/1000T, 4 SFP GE | | Santa Ana | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 700223 | Westlake | Managed |
| *** | Phys FW Clustered | *** | Juniper | ISG 2000 | 700222 | Westlake | Managed |
| *** | Switch | *** | Cisco | UCS 6120XP 20-Port Fabric Interconnect | 703844 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | UCS 6120XP 20-Port Fabric Interconnect | 703843 | Santa Ana | Managed |
| *** | Switch | *** | Cisco | Catalyst 6506-E Switch | 327504 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100/1000 + 4 SFP Std | 319037 | Westlake | Managed |
| *** | Router | *** | Cisco | 26xx Series Modular Access Router | 700416 | Westlake | Managed |
| *** | Phys FW Standalone | *** | Juniper | SSG 20 | 700417 | Westlake | Managed |
| *** | Router | *** | Cisco | 26xx Series Modular Access Router | 700418 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 101634 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 4948 | 101635 | Westlake | Managed |
| *** | Switch | *** | Cisco | Catalyst 3750 24-port 10/100/1000 + 4 SFP Std | 101633 | Westlake | Managed |
| *** | WAN | *** | Verizon | Non-Std Cabinet Verizon Network Rack | | Westlake | Managed |
| *** | WAN | *** | Verizon | Non-Std Cabinet Verizon Network Rack | | Westlake | Managed |
| *** | WAN | *** | Verizon | Non-Std Cabinet Verizon Network Rack | | Westlake | Managed |
| *** | Switch | *** | Cisco | UCS 6120XP 20-Port Fabric Interconnect | 700263 | Westlake | Managed |
| *** | Switch | *** | Cisco | UCS 6120XP 20-Port Fabric Interconnect | 700264 | Westlake | Managed |
| *** | Security | *** | Cisco | ASA 5585-X Adaptive Security Appliance | 700265 | Westlake | Managed |
| *** | Security | *** | Cisco | ASA 5585-X Adaptive Security Appliance | 700266 | Westlake | Managed |
| *** | Router | *** | Cisco | 3945 Integrated Services Router | 700267 | Westlake | Managed |
| *** | Router | *** | Cisco | 3945 Integrated Services Router | 700268 | Westlake | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 700269 | Westlake | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 703855 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3945 Integrated Services Router | 703857 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3945 Integrated Services Router | 703858 | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 703859 | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 703860 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3945 Integrated Services Router | 700276 | Westlake | Managed |
| *** | Router | *** | Cisco | 3945 Integrated Services Router | 700275 | Westlake | Managed |
| *** | Security | *** | SafeNet | Link Encryptor | 703877 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3945 Integrated Services Router | 703878 | Santa Ana | Managed |
| *** | Router | *** | Cisco | 3845 Integrated Services Router | 703879 | Santa Ana | Managed |
| *** | WAN | *** | AboveNet | Non-Std Cabinet AT&T Network Rack | | Westlake | Hosted |
| *** | WAN | *** | AboveNet | Non-Std Cabinet AT&T Network Rack | | Westlake | Hosted |
| *** | WAN | *** | AT&T | Non-Std Cabinet AboveNet Network Rack | | Westlake | Hosted |
| *** | Switch | *** | Cisco | Catalyst 2950 24-port | | Westlake | Managed |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 536 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| *** | Switch | *** | Cisco | Catalyst 3750 | 703906 | Santa Ana | Managed |
| *** | Security | *** | IBM ISS | ISS Proventia | 703907 | Santa Ana | Managed |
| *** | Security | *** | IBM ISS | ISS Proventia | 703908 | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect Flex-10 10Gb Ethernet Module | | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect Flex-10 10Gb Ethernet Module | | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect 8Gb Fibre Channel 24-Port Module | | Santa Ana | Managed |
| *** | Switch | *** | HP | Virtual Connect 8Gb Fibre Channel 24-Port Module | | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | 703910 | Santa Ana | Managed |
| *** | Security | *** | Websense | V10000 Web Security Appliance | 700285 | Westlake | Managed |
| *** | Security | *** | Websense | V10000 Web Security Appliance | 700286 | Westlake | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 703911 | Santa Ana | Managed |
| *** | Switch | *** | HP | ProLiant BL p-Class GbE2 Switch | | Santa Ana | Managed |
| *** | Router | *** | Cisco | 7200 VXR Router | 703916 | Santa Ana | Managed |
| *** | Security | *** | IBM ISS | GX5208 Intrusion Prevention System | 703917 | Santa Ana | Managed |
| *** | Security | *** | Cisco | ASA 5500 Series Adaptive Security Appliance | | Westlake | Managed |
Networks - Remote
|
| | | | | | | |
| Minor Category | Dell Category | Business Unit | Address | City | State | Description | Serial Number |
| Router /Switch | Router | Credco | *** | *** | *** | CISCO 2951/K9 | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | WS-C3560-24PS | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | WS-C3560-24PS | *** |
| Router /Switch | Switch | National Joint Ventures | *** | *** | *** | WS-C3560-24PS | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Baystack 255 Hub | *** |
| Router /Switch | Router | BPO Services (formerly Residential Value View - RVV) | *** | *** | *** | Cisco 1721 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 1721 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 1721 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 1760 | *** |
| Router /Switch | Router | Appraisal Management Services (formerly eAppraiseIT and Quantrix) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | Claims Services CMAX | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | Claims Services CMAX | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | National Joint Ventures | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | TeleTrack | *** | *** | *** | Cisco 1841 | *** |
| Router /Switch | Router | First Advantage | *** | *** | *** | Cisco 1841/VPN | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 1841/VPN | *** |
| Router /Switch | Router | TeleTrack | *** | *** | *** | Cisco 1841/VPN | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 537 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| Router /Switch | Router | Appraisal Management Services (formerly eAppraiseIT and Quantrix) | *** | *** | *** | Cisco 2610 | *** |
| Router /Switch | Router | COLO (AT&T) | *** | *** | *** | Cisco 2610 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 2610 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2610 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2610 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2610 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2610 | *** |
| Router /Switch | Router | COLO (AT&T) | *** | *** | *** | Cisco 2611 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2611 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2611 | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 2621 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2801 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2801 | *** |
| Router /Switch | Router | Marketlinx | *** | *** | *** | Cisco 2801 | *** |
| Router /Switch | Router | Appraisal Management Services (formerly eAppraiseIT and Quantrix) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | Flood Services | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | Flood Services | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | Flood Services | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | Marketlinx | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | RealtyBid | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | RELS | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | RELS | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | SafeRent | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | SafeRent | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | SafeRent | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | TeleTrack | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | TeleTrack | *** | *** | *** | Cisco 2811 | *** |
| Router /Switch | Router | American Driving Records (Transportation) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | American Driving Records (Transportation) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | Appraisal Management Services (formerly eAppraiseIT and Quantrix) | *** | *** | *** | Cisco 2821 | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 538 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| Router /Switch | Router | BPO Services (formerly Residential Value View - RVV) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | Claims Services (formerly National Claims Outsourcing - FANCO) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | Default Technology (FADT) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | First Advantage | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | First Advantage | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | Flood Services | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | Global Offshore Services - GOS | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | Marketlinx | *** | *** | *** | Cisco 2821 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 2851 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 2851 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 2851 | *** |
| Router /Switch | Router | Marketlinx | *** | *** | *** | Cisco 2851 | *** |
| Router /Switch | Router | Marketlinx | *** | *** | *** | Cisco 2851 | *** |
| Router /Switch | Router | National Joint Ventures | *** | *** | *** | Cisco 2851 | *** |
| Router /Switch | Router | SafeRent | *** | *** | *** | Cisco 2851 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | CISCO 2901 / K9 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | CISCO 2921 / K9 | *** |
| Router /Switch | Switch | CoLo (Verizon Business) | *** | *** | *** | Cisco 2950 (Switch) | *** |
| Router /Switch | Switch | CoLo (Verizon Business) | *** | *** | *** | Cisco 2950 (Switch) | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco 2950 (Switch) | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | Cisco 2950 (Switch) | *** |
| Router /Switch | Router | Appraisal Management Services (formerly eAppraiseIT and Quantrix) | *** | *** | *** | Cisco 3725 | *** |
| Router /Switch | Router | Claims Services (formerly National Claims Outsourcing - FANCO) | *** | *** | *** | Cisco 3725 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 3745 | *** |
| Router /Switch | Router | American Driving Records (Transportation) | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | American Driving Records (Transportation) | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | BPO Services (formerly Residential Value View - RVV) | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | Corelogic/ STARS | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | Marketlinx | *** | *** | *** | Cisco 3825 | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 539 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| Router /Switch | Router | Marketlinx | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | Marketlinx | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | National Joint Ventures | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | REO Services | *** | *** | *** | Cisco 3825 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 3845 | *** |
| Router /Switch | Router | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 3845 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 3845 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 3845 | *** |
| Router /Switch | Router | Flood Services | *** | *** | *** | Cisco 3845 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 3845 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 3845 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 3845 | *** |
| Router /Switch | Router | SafeRent | *** | *** | *** | Cisco 3845 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 3925-CME-SRST/K9 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 3925-CME-SRST/K9 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 3945 | *** |
| Router /Switch | Router | Flood Services | *** | *** | *** | Cisco 3945 | *** |
| Router /Switch | Router | Flood Services | *** | *** | *** | Cisco 3945 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 3945 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Cisco 3945 | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 4507R (Switch) | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 4507R (Switch) | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | Cisco 4507R (Switch) | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 6506 | *** |
| Router /Switch | Switch | Flood Services | *** | *** | *** | Cisco 6506 | *** |
| Router /Switch | Switch | Flood Services | *** | *** | *** | Cisco 6506 | *** |
| Router /Switch | Switch | Flood Services | *** | *** | *** | Cisco 6506 | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 6509/Sup 720 | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco 6509/Sup 720 | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | Cisco 6509/Sup 720 | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 7204VXR | *** |
| Router /Switch | Router | COLO (AT&T) | *** | *** | *** | Cisco 7206VXR | *** |
| Router /Switch | Router | COLO (AT&T) | *** | *** | *** | Cisco 7206VXR | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 7206VXR | *** |
| Router /Switch | Router | Corelogic/ STARS | *** | *** | *** | Cisco 7206VXR | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 7206VXR | *** |
| Router /Switch | Router | Credco | *** | *** | *** | Cisco 7206VXR | *** |
| Router /Switch | Router | Marketlinx | *** | *** | *** | Cisco 7206VXR | *** |
| Router /Switch | Router | Marketlinx | *** | *** | *** | Cisco 7206VXR | *** |
| Router /Switch | Router | COLO (AT&T) | *** | *** | *** | Cisco 7206VXR NPE-G1 | *** |
| Router /Switch | Router | COLO (AT&T) | *** | *** | *** | Cisco 7206VXR NPE-G1 | *** |
| Router /Switch | Router | CoLo (Verizon Business) | *** | *** | *** | Cisco 7206VXR NPE-G1 | *** |
| Router /Switch | Router | COLO (AT&T) | *** | *** | *** | Cisco 871/VPN | *** |
| Router /Switch | WAP | Marketlinx | *** | *** | *** | Cisco AIR-AP1242 | *** |
| Router /Switch | Security | LAS (TAX Services) | *** | *** | *** | Cisco ASA 5510 | *** |
| Router /Switch | Security | Marketlinx | *** | *** | *** | Cisco ASA 5510 | *** |
| Router /Switch | Security | Appraisal Management Services (formerly eAppraiseIT and Quantrix) | *** | *** | *** | Cisco ASA5505 | *** |
| Router /Switch | Security | CoLo (Verizon Business) | *** | *** | *** | Cisco ASA5505 | *** |
| Router /Switch | Security | CoLo (Verizon Business) | *** | *** | *** | Cisco ASA5505 | *** |
| Router /Switch | Security | CoLo (Verizon Business) | *** | *** | *** | Cisco ASA5505 | *** |
| Router /Switch | Security | COLO (AT&T) | *** | *** | *** | Cisco ASA5520 | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 540 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| Router /Switch | Security | COLO (AT&T) | *** | *** | *** | Cisco ASA5520 | *** |
| Router /Switch | Security | CoLo (Verizon Business) | *** | *** | *** | Cisco ASA5520 | *** |
| Router /Switch | Security | Global Offshore Services - GOS | *** | *** | *** | Cisco ASA5520 | *** |
| Router /Switch | Security | LAS (TAX Services) | *** | *** | *** | Cisco ASA5520 | *** |
| Router /Switch | Security | Marketlinx | *** | *** | *** | Cisco ASA5520 | *** |
| Firewall | Phys FW Standalone | Appraisal Management Services (formerly eAppraiseIT and Quantrix) | *** | *** | *** | Cisco Pix 515 Firewall | *** |
| Firewall | Phys FW Standalone | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco Pix 515 Firewall | *** |
| Firewall | Phys FW Standalone | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco Pix 515 Firewall | *** |
| Firewall | Phys FW Standalone | First Advantage | *** | *** | *** | Cisco Pix 515 Firewall | *** |
| Firewall | Phys FW Standalone | Marketlinx | *** | *** | *** | Cisco Pix 515 Firewall | *** |
| Firewall | Phys FW Standalone | COLO (AT&T) | *** | *** | *** | Cisco Pix 525 Firewall | *** |
| Firewall | Phys FW Standalone | Marketlinx | *** | *** | *** | Cisco Pix 525 Firewall | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | Cisco RC32300 | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | Cisco RC32300 | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | Cisco RC32300 | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | Cisco RC32300 | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | Cisco RC32300 | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | Cisco RC32300 | *** |
| Router /Switch | Switch | Flood Services | *** | *** | *** | Cisco WS-3560-24PS | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco WS-3560-48PS | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco WS-3560-48PS | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco WS-3560-48PS | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | Cisco WS-3560-48PS | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-3560-48PS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-3560-48PS | *** |
| Router /Switch | Switch | REO Services | *** | *** | *** | Cisco WS-3560G-24PS | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco WS-3560G-48PS | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | Cisco WS-3560G-48PS | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | Cisco WS-3560G-48PS | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | Cisco WS-3560G-48PS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-3560G-48PS | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-3750G-24TS | *** |
| Router /Switch | Switch | Claims Services (formerly National Claims Outsourcing - FANCO) | *** | *** | *** | Cisco WS-6509 | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco WS-6509-E (Switch) | *** |
| Router /Switch | Switch | Claims Services CMAX | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | COLO (AT&T) | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | CoLo (Verizon Business) | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | CoLo (Verizon Business) | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C2950-24 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C2950SX-48-SI | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C2950SX-48-SI | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 541 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C2950SX-48-SI | *** |
| Router /Switch | Switch | National Joint Ventures | *** | *** | *** | Cisco WS-C2950SX-48-SI | *** |
| Router /Switch | Switch | National Joint Ventures | *** | *** | *** | Cisco WS-C2950SX-48-SI | *** |
| Router /Switch | Switch | Claims Services (formerly National Claims Outsourcing - FANCO) | *** | *** | *** | Cisco WS-C2960S-48TD-L | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C2960S-48TD-L | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C2960S-48TD-L | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C2960S-48TD-L | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C2960S-48TD-L | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C2960S-48TD-L | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C3548-XL | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C3548-XL | *** |
| Router /Switch | Switch | COLO (AT&T) | *** | *** | *** | Cisco WS-C3750-24TS | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C3750-24TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C3750-24TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C3750-24TS | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | Cisco WS-C3750-48TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C3750-48TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C3750-48TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C3750-48TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | Cisco WS-C3750G-12S | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | Cisco WS-C3750V2-24PS-S | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | Cisco WS-C3750V2-24PS-S | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco WS-C4503 | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco WS-C4506 | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco WS-C4506 | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco WS-C4506 | *** |
| Router /Switch | Switch | Default Technology (FADT) | *** | *** | *** | Cisco WS-C4506 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C4506 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C4506 | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Cisco WS-C4948 | *** |
| Router /Switch | Switch | CoreLogic/DARES (FACL) | *** | *** | *** | Cisco WS-C6509-E | *** |
| Router /Switch | Switch | REO Services | *** | *** | *** | Cisco WS-C6509-E | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | HP Procurve 4000M-01 | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | HP Procurve 4000M-01 | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | HP Procurve 4000M-01 | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | HP Procurve 4000M-01 | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | HP Procurve 4000M-01 | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | HP Procurve 4000M-01 | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | HP Procurve 4000M-01 | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | HP Procurve 4000M-01 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Paradyne 9124 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Paradyne 9124 | *** |
| Router /Switch | Router | LAS (TAX Services) | *** | *** | *** | Paradyne 9124 | *** |
| Router /Switch | Switch | BPO Services (formerly Residential Value View - RVV) | *** | *** | *** | Unknown | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | Unknown | *** |
| Router /Switch | Switch | BPO Services (formerly Residential Value View - RVV) | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | BPO Services (formerly Residential Value View - RVV) | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | BPO Services (formerly Residential Value View - RVV) | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | BPO Services (formerly Residential Value View - RVV) | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | WS-C2960-48PST-S | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 542 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | | | |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | LAS (TAX Services) | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | RealtyBid | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | RealtyBid | *** | *** | *** | WS-C2960-48PST-S | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | WS-C3560G-48TS | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | WS-C3560G-48TS | *** |
| Router /Switch | Switch | Credco | *** | *** | *** | WS-C3750-48TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | WS-C3750-48TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | WS-C3750-48TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | WS-C3750-48TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | WS-C3750-48TS-E | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | WS-C3750G-24TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | WS-C3750G-24TS | *** |
| Router /Switch | Switch | SafeRent | *** | *** | *** | WS-C4507R | *** |
| Router /Switch | Switch | Claims Services (formerly National Claims Outsourcing - FANCO) | *** | *** | *** | WS-C6504-E | *** |
| Router /Switch | Switch | Claims Services (formerly National Claims Outsourcing - FANCO) | *** | *** | *** | WS-C6504-E | *** |
| Router /Switch | Switch | Marketlinx | *** | *** | *** | WS-C6509 | *** |
| Router /Switch | Switch | Flood Services | *** | *** | *** | WS-C6513 | *** |
| Router /Switch | Switch | Flood Services | *** | *** | *** | WS-C6513 | *** |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-8.2
SUPPLIER TOOLS AND CORELOGIC TOOLS
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 543 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 544 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
1. INTRODUCTION
1.1 Agreement. This Schedule A-8.2 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”).
1.2 References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided.
1.3 Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 545 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Supplier Software | Supplier Owner Software or Third Party Software | Service Tower | Function | Encrypted | Post-termination Rights |
| *** | Third Party Software | AS400 (iSeries) | Remote Console monitoring and Automation software | No | No |
| *** | Third Party Software | Server Services | Server virtualization software | No | No |
| *** | Third Party Software | Server Services | Server P2V software | No | No |
| *** | Third Party Software | Server Services | Server V2V software | No | No |
| *** | Third Party Software | Server Services | Virtualization AOI provisioning/request management | No | No |
| *** | Supplier Owned Software | Server Services | Virtualization AOI provisioning/request and template management | No | Yes |
| *** | Third Party Software | Server Services | Virtualization AOI image/template management | No | No |
| *** | Third Party Software | Server Services | Cloud capacity planning | No | No |
| *** | Third Party Software | Server Services | Virtualization candidacy (e.g., is server appropriate for P2V, what are the required CPU/memory settings) | No | No |
| *** | Third Party Software | Server Services | Virtualization Monitoring and alerting | No | No |
| *** | Third Party Software | Collaboration Services | Email Server-level Anti-virus software | No | No |
| *** | Third Party Software | Collaboration Services | Email Content Anti-spam/Anti-virus filtering | No | No |
| *** | Third Party Software | Collaboration Services | Email system monitoring . | No | No |
| *** | Supplier Owned Software | Cross Functional | Reporting Portal. Presents aggregated data from multiple tools | No | Yes |
| *** | Third Party Software | Cross Functional | Reporting Portal. Presents aggregated data from multiple tools | No | No |
| *** | Third Party Software | Cross Functional | Collecting relevant events from Dell's monitoring tools, screening to prevent duplicate or non -relevant events being generated in ticketing system | No | No |
| *** | Supplier Owned Software | Cross Functional | Collecting relevant events from Dell's monitoring tools, screening to prevent duplicate or non -relevant events being generated in ticketing system | No | Yes |
| *** | Third Party Software | Cross Functional | Supplier CMDB | No | No |
| *** | Third Party Software | Storage and Backup Systems | Backup Management System | No | No |
| *** | Third Party Software | Storage and Backup Systems | Backup Management System | No | No |
| *** | Third Party Software | End User computing | Desktop Incident Management | No | No |
| *** | Supplier Owned Software | End User Computing | EUC Inventory collection and patching (Intel), EUC Image Management and Support | No | Yes |
| *** | Third Party Software | Server Services | Electronic Software Distribution software (Intel) | No | No |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 546 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Supplier Software | Supplier Owner Software or Third Party Software | Service Tower | Function | Encrypted | Post-termination Rights |
| *** | Supplier Owned Software | End User computing | EUC ESD - Electronic Software Distribution software | No | Yes |
| *** | Supplier Owned Software | Information Security services | Security monitoring, analysis and response | No | Yes |
| *** | Third Party Software | Information Security services | Security Analysis | No | No |
| *** | Third Party Software | Information Security services | Internet Content Filter | No | No |
| *** | Third Party Software | Information Security services | Security Intrusion and Detection | No | No |
| *** | Third Party Software | Network Services | Console Logs consolidation | No | No |
| *** | Third Party Software | Network Services | Network monitoring - monitoring performance, utilization, top talkers and availability/status of network devices and links/circuits. | No | No |
| *** | Third Party Software | Network services | Third party Extranet (VPN) | No | No |
| *** | Third Party Software | Network services | RAS client server access , | No | No |
| *** | Third Party Software | Network Services | Data Center Core Switches | No | No |
| *** | Third Party Software | Network Services | Network device configuration backup and archiving , Network Monitoring | No | No |
| *** | Third Party Software | Network Services | Network Security | No | No |
| *** | Third Party Software | Server services – Unix and Linux | Unix/Linux Server Inventory collection and patching software | No | No |
| *** | Third Party Software | Server services – Unix and Linux | Mid-level alerting and performance monitoring for Unix-based servers for hardware, software and applications (Limited historical trending or reporting) | No | No |
| *** | Third Party Software | Server services – All Platforms | Advanced alerting and performance monitoring for Unix/Linux and Wintel servers for Unix, Linux for hardware, software and applications. (Historical trending and reporting) | No | No |
| *** | Third Party Software | Server services – Intel | Collection of server performance data for capacity planning. Provides detailed capacity planning monitoring to provide a more detailed analysis of systems, applications and environments | No | No |
| *** | Third Party Software | Server services – Intel | Intel Server Inventory collection and patching software | No | No |
| *** | Third Party Software | Server services – Intel | Intel Server Inventory collection and patching software | No | No |
| *** | Third Party Software | Server services – All Platforms | Advanced alerting and performance monitoring for Windows-based servers for hardware, software, and applications (Historical trending and reporting) | No | No |
| *** | Third Party Software | Server services – All Platforms | Heartbeat Monitoring to test for server up/down status | No | No |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 547 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Supplier Software | Supplier Owner Software or Third Party Software | Service Tower | Function | Encrypted | Post-termination Rights |
| *** | Third Party Software | Service Desk | Secure FTP | No | No |
| *** | Supplier Owned Software | Service Desk | ITSM System software. Ticketing system (Incident, Problem, Change, Request, Configuration Management) | No | Yes |
| *** | Third Party Software | Service Desk | User Self-Help Content | No | No |
| *** | Third Party Software | Service Desk | Knowledgebase used by Service Desk Agents and CoreLogic End Users for self help | No | No |
| *** | Third Party Software | Service Desk | Tracks call volume, queue and statistics. | No | No |
| *** | Third Party Software | Service Management | Reports | No | No |
| *** | Supplier Software | Storage services | Reporting for enterprise storage - Storage utilization reporting. | No | Yes |
| *** | Supplier Software | Storage services | Remote Data Replication | No | Yes |
| *** | Supplier Software | Storage services | Local Data Replication | No | Yes |
| *** | Supplier Software | Storage services | NAS Data Replication | No | Yes |
| *** | Supplier Software | Storage services | Storage Management tools for storage management and monitoring. | No | Yes |
| *** | Third Party Software | Technical Architecture Diagrams | Documentation of Infrastructure Components used to provide delivery of services | No | No |
| *** | Third Party Software | Mobility | Telecom Expense Management | No | No |
| *** | Third Party Software | Server Services | Server capacity measurement and planning | No | No |
| *** | Third Party Software | Server Services | Discovery of physical and virtual IT assets and applications — and the relationships between them | No | No |
| *** | Third Party Software | Server Services | Server capacity measurement, planning, and reporting | No | No |
| *** | Third Party Software | Network Services | Network monitoring, capacity measurement, planning, and reporting | No | No |
| *** | Third Party Software | Storage Services | Data Replication | No | No |
| *** | Supplier Owned Software | Service Desk | Service Desk to Service Desk integration | No | Yes |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 548 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
.
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-9
APPROVED SUBCONTRACTORS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 549 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-9
Approved Subcontractors
| |
| 1.1 | Agreement. This Schedule A-9 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this schedule to articles, sections and exhibits shall be to this schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this schedule with initial capitalized letters but not defined in this schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to this Supplement, or the other Schedules to the MSA or this Supplement. |
In accordance with Section 9.11(a) of the MSA, the following Subcontractors are approved by CoreLogic for the provision of the following types of Services under this Supplement under the terms described herein:
|
| | | | |
| Approved Subcontractor | Service Location | Types of Services | *** (1) | Approved Subcontract Exceptions (2) |
| *** | USA CoreLogic Facilities | *** | X | X |
| *** | USA CoreLogic Facilities | *** | X | X |
| *** | USA Virtual and CoreLogic Facilities | *** | X | X |
| *** | USA CoreLogic and Supplier Facilities | *** | X | X |
| *** | USA Supplier Facilities | *** | X | X |
| *** | USA Supplier Facilities | *** | X | X |
| *** | CoreLogic Facilities | *** | X | X |
| *** | Supplier Facilities | *** | X | X |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 550 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
(1) Supplier is not required to provide *** from the Subcontractors as described in Section 9.10(i) of the MSA.
(2) CoreLogic is not an intended third party beneficiary under Supplier’s contracts with the Subcontractor as described in Section 9.11(a) of the MSA (regarding dedicated Subcontractors).
Supplier is not required to ensure that the Subcontractors provide directly to CoreLogic and Permitted Auditors the *** to the *** and *** described in Section *** of the MSA.
The terms of Supplier’s subcontracts with the Subcontractors do not specifically include, as described in Section *** of the MSA: (i) CoreLogic’s *** rights (which apply directly to the Subcontractor); (ii) compliance with *** and ***; (iii) compliance with CoreLogic’s policies and directions; or (iv) *** rights in favor of CoreLogic including as described in Section 9.10 of the MSA.
For clarity, Supplier shall remain responsible for obtaining audit rights and information from its Subcontractors such that Supplier may comply with its audit obligations under the Agreement and, as provided in Section 9.11(c) of the MSA. Supplier shall be and remain responsible and liable for any acts or omissions of any Subcontractor or Subcontractor personnel (including failure to perform in accordance with this Agreement or to comply with any duties or obligations imposed on Supplier under this Agreement) to the same extent as if such failure to perform or comply was committed by Supplier or Supplier employees.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 551 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-10
TRANSITION SERVICES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 552 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-10
Transition Services
ARTICLE 1.
GENERAL
| |
| 1.1.1 | Agreement. This Schedule A-10 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 1.1.4 | Schedules. The following Schedules are incorporated into this Schedule by reference: |
Schedule A-10.1 Initial Operational Transition Services Transition Plan
Schedule A-10.2 Initial DCM Plan
Schedule A-10.3 Additional Transition Services Obligations
| |
| 1.1.5 | Overview. This Schedule sets forth the Transition Services to be performed by Supplier and the Transition Milestones applicable to this Supplement. The Charges associated with Transition Services are set forth in Schedule A-4.5. |
In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity.
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party.
ARTICLE 2.
OPERATIONAL TRANSITION SERVICES
This Section 2.1 details the obligations and responsibilities of the Parties regarding the operational Transition Services activities (the “Operational Transition Services”).
The Transition Period for the Operational Transition Services shall commence on the Supplement Effective Date and expire 12:00:01 a.m., Pacific Time, on the date specified for the completion of the Operational Transition Services as specified in the Transition Plan, unless expressly extended in writing by CoreLogic.
Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. Supplier shall:
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.1.1 | Provide a Project Management Office that will manage, report on, oversee, and run transition activities as outlined in the Transition Plan
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 553 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.1.2 | Assign functional area leads to provide reasonable assistance (to the extent provided in this Schedule A-10) to Supplier in the implementation of the Transition Plan throughout the duration of operational transition
| | P |
| 2.1.3 | Execute transition activities in line with the Transition Plan | P | |
| 2.1.4 | Conduct transition workshops aligning to the Supplier Transition and project management methodology
| P | |
| 2.1.5 | Develop formal communication plan to inform CoreLogic stakeholders and key staff of activities, risks, schedules and impacts related to the Transition Services | P | A |
| 2.1.6 | Inform CoreLogic stakeholders and key staff on the methodology, scope, communication and identification of operational impacts (risks, issues and mitigations) related to the Transition Services | P | |
| 2.1.7 | Lead joint collaborative working sessions to create, revise and finalize the Transition Plan in accordance with Section 4.2(c) of the MSA
| P | |
| 2.1.8 | Participate in and make appropriate CoreLogic Personnel reasonably available for joint collaborative working sessions and cooperate with Supplier in finalizing the Transition Plan in accordance with Section 4.2(c) of the MSA
| | P |
| 2.1.9 | Manage and execute knowledge transfer activities (including processes, procedures, policies, and operational requirements) from Transitioned Employees and retained CoreLogic Personnel to transition Services from CoreLogic to Supplier for all Services
| P | |
| 2.1.10 | In collaboration with CoreLogic, define knowledge transfer acceptance criteria prior to Transition execution
| P | |
| 2.1.11 | Review and approve knowledge transfer acceptance criteria prior to Transition execution without unreasonable delay | | P |
| 2.1.12 | Develop, maintain and execute Transition Plan in line with CoreLogic Service Level requirements, CoreLogic Systems, applications or business operations during Transition Period
| P | |
| 2.1.13 | Conduct in-person meetings with CoreLogic prior to submission of Critical Transition Deliverables to communicate proposed Transition Deliverables and Milestones to CoreLogic
| P | |
| 2.1.14 | Use commercially reasonable efforts, and in collaboration with CoreLogic, resolve issues and concerns raised by CoreLogic | P | |
| 2.1.15 | Review Transition Deliverables submitted by Supplier for Acceptance and provide feedback or written Acceptance in accordance with the schedule set forth in the Transition Plan
| | P |
| 2.1.16 | Confirm CoreLogic Acceptance of each Transition Deliverable by the applicable Transition Milestone as set forth in Schedule A-4.5
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 554 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.1.17 | Implement and configure and maintain the Supplier Asset Inventory Database and populate the Asset Inventory with agreed upon configuration items and attributes in line with applications and server dependency mapping
| P | A |
| 2.1.18 | As described in Schedule A-2.12, perform a gap analysis of existing Disaster Recovery Plans and provide recommendations to address any identified gaps between CoreLogic and Supplier’s best practice disaster recovery plan
| P | |
| 2.1.19 | As described in Schedule A-2.12, review Disaster Recovery gap analysis, recommendations and remediation activities and timelines with CoreLogic
| P | A |
| 2.1.20 | Plan, schedule and execute Disaster Recovery remediation activities as agreed upon by CoreLogic and Supplier | P | A |
| 2.1.21 | Provide the Policy and Procedures Manual (“PPM”) articles (as they become available) to CoreLogic for review and Acceptance, as further described in Section 9.1 of the MSA
| P | |
| 2.1.22 | Review draft of the PPM as further described in Section 9.1 of the MSA | | P |
| 2.1.23 | Following revisions and updates provided by CoreLogic, update the PPM as further described in Section 9.1 of the MSA
| P | |
| 2.1.24 | Provide a final draft of the PPM to CoreLogic for approval, as further described in Section 9.1 of the MSA
| P | |
| 2.1.25 | Review the final draft of the PPM as further described in Section 9.1 of the MSA without unreasonable delay
| | P |
| 2.1.26 | In addition to reporting required by Section 4.2(e) of the MSA and Section 3 below, create and deliver any Reports Supplier and CoreLogic mutually agree to be necessary as part of providing the Transition Services
| P | |
| 2.1.27 | Develop all Reports, listed in Schedule A-12, for operational functionality and oversight
| P | |
| 2.1.28 | With CoreLogic’s reasonable assistance, complete Security Operations Center (SOC) readiness to meet or exceed CoreLogic security requirements
| P | |
| 2.1.29 | Develop Service Management processes, technical services, and guidelines in alignment with CoreLogic Standards and business requirements and document in the PPM
| P | |
| 2.1.30 | Implement tools described in Schedule A-3 and processes to prepare for Service Levels measurement in preparation for assumption of service in accordance with Schedule A-3
| P | |
| 2.1.31 | Implement tools and processes to measure operational metrics, reports and Service Levels in preparation for assumption of service
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 555 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.1.32 | Incorporate into the Transition Plan and maintain *** and *** standards as identified by CoreLogic during the Operational Transition Planning Phase
| P | A |
| 2.1.33 | As requested, provide reasonable assistance to CoreLogic in discussions with CoreLogic customers regarding Transition Services
| P | |
| 2.1.34 | Provide oversight and act as point of escalation for Third Party Contractors
| | P |
| 2.1.35 | Define Operational Transition tasks and collaborate with ***, to execute tasks
| P | |
| 2.1.36 | Convert CoreLogic from existing ITSM tool (Service-Now.com, Tracker) to OPAS
| P | |
| 2.1.37 | Migrate all open tickets in CoreLogic ITSM tool tickets to OPAS using a CoreLogic-approved approach and in accordance with the Transition Plan
| P | |
| 2.1.38 | Reasonably assist CoreLogic in its maintenance of historical ticket information as required by CoreLogic compliance requirements
| P | |
| 2.1.39 | Using a CoreLogic-approved approach related to the interfaces configured within Service Now, migrate existing CoreLogic ITSM tool catalog items, forms, workflows and interfaces supporting CoreLogic Systems (e.g. Palm, Altiris, Tracker, HR, Active Directory, etc.) into OPAS (e.g., through an API, email or other means)
| P | |
| 2.1.40 | Develop test scripts and perform testing for all agreed-upon OPAS implementation scenarios
| P | |
| 2.1.41 | Perform OPAS and Dell IT service management tool training and documentation for CoreLogic users
| P | |
| 2.1.42 | Perform governance, relationship management and service management training for CoreLogic users
| P | |
| 2.1.43 | Incorporate CoreLogic provided feedback on Transition activities via agreed upon Governance as further described in Schedule 6
| P | |
| 2.1.44 | Except for information that can be provided by Transitioned Employees as described in Schedule A-10.3, provide information (e.g. available critical knowledge and data regarding the specifications of underlying Software and Equipment) requested by Supplier as further described in Section 10.1(b) of the MSA | | P |
| 2.1.45 | Provide Supplier with an updated In-Flight Project list and information regarding such Projects to assist Supplier in identifying projects that could interfere with the Transition | | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 556 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.1.46 | Review project planning documents (PPDs), the Project Plans and subordinate documentation to identify CoreLogic information not included in such plans and documentation that, to CoreLogic’s knowledge, would cause Supplier’s responsibilities under the Project Plan to be delayed, fail or be unacceptable to CoreLogic; provided, that this does not limit Supplier’s obligations under Section 4.2(d) of the MSA | | P |
| 2.1.47 | Adhere to agreed upon maintenance windows for Transition Plan activities
| P | |
| 2.1.48 | In accordance with the Transition Plan, allow reasonable down-time of Systems, and timely notify Supplier of any CoreLogic or Third Party Contractor black-out periods | | P |
| 2.1.49 | Provide required OPAS access to CoreLogic | P | |
| |
| 2.2 | DCTMV Transition Services. |
This Section 2.2 details the obligations and responsibilities of the Parties regarding the Transition Services relating to Supplier’s transformation, migration and virtualization of CoreLogic’s Servers located in Data Centers in***and the facilities in***and*** to Supplier Data Centers (the “DCTMV Transition Services”). The Parties shall work together in good faith to minimize the costs incurred by the other Party in connection with DCTMV Transition Services for such facilities in ***and ***.
The Transition Period for the DCTMV Transition Services shall commence on the Supplement Effective Date and expire 12:00:01 a.m., Pacific Time, on the date specified for the completion of the DCTMV Transition Services as specified in the DCTMV Plan, unless expressly extended in writing by CoreLogic.
Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities.
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 1. | Provide an overall program manager to lead and manage the Data Center transformation, migration and virtualization from planning through execution and completion of each task as described in the Transition Plan specific to the DCTMV Services (the “DCTMV Plan”). | P | |
| 2. | Manage changes to Supplier Data Center environment to ensure operational readiness as described in the DCTMV Plan. | P | |
| 3. | Provide a resource as the liaison to the Supplier program manager | | P |
| 4. | Provide Supplier Personnel to participate in the planning, execution, and implementation tasks of the project | P | |
| 5. | Provide CoreLogic Personnel to participate in the planning, execution, and implementation tasks of the project | | P |
| 6. | Provide: • Information (in a timely manner) from Third Party suppliers of regarding CoreLogic’s Third Party Contractors for Equipment • Access to relevant Systems and Application documentation and records. . | | P |
| 7. | Install and configure logical mapping auto discovery Tool in CoreLogic Data Center environment | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 557 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 8. | Complete Application to Server mapping and Application dependency mapping to be used in coordination, grouping and prioritization of project activities | P | |
| 9. | Review Application to Server mapping and Applications dependency mapping with CoreLogic experts and obtain agreement on content, accuracy and prioritization of project activities | | P |
| 10. | Assist Supplier in the implementation of Tools and Equipment needed for the DCTMV project | | P |
| 11. | Develop a detailed draft migration plan that will address individual move packages and means of System (physical to virtual, virtual to virtual, physical to physical), Application and data movement which accounts for minimizing downtime for CoreLogic Applications and Systems | P | |
| 12. | Provide existing information and documentation about the CoreLogic network topology and security configurations (e.g. network segmentation, Firewall rules, link bandwidth and utilization levels, etc.) | | P |
| 13. | Provide existing information about the CoreLogic logical and physical access requirements for Servers and databases (Server/database logon credentials and privileges, network Firewall rule exceptions, etc.) | | P |
| 14. | Review data output from auto-discovery Tools and discuss potential implications for migration planning | P | |
| 15. | Identify prioritization from CoreLogic Campus Sites at *** to Supplier Data Centers | P | A |
| 16. | Identify move packages and associated code freeze windows | P | A |
| 17. | Participate in the development of move packages including by providing Application subject matter expertise, notifying of any Application down-time and freeze or blackout requirements | | P |
| 18. | Present DCTMV Plan to CoreLogic governance board | P | A |
| 19. | Within the DCTMV Plan, identify the destination and disposition of all Equipment, whether it will move to Supplier Data Center or remain at a CoreLogic Facility | P | A |
| 20. | Identify potential risks associated with the DCTMV Plan and notify CoreLogic of such | P | |
| 21. | Develop plan that includes information learned during the project’s planning phase including data from working sessions with CoreLogic Infrastructure, business and Application teams. The plan’s execution tasks include the migration and transformation strategy, move packages, package timing, code-freeze windows, black-out windows, Infrastructure testing and responsibilities of CoreLogic staff. Plan also includes sections for resource management, quality management, Change Management and communication management. | P | |
| 22. | Lead joint collaborative working sessions to create, revise and formalize the DCTMV Plan | P | |
| 23. | Participate in and make appropriate CoreLogic Personnel reasonably available for joint collaborative working sessions and cooperate with Supplier in finalizing the DCTMV Plan in accordance with Section 4.2(c) of the MSA | | P |
| 24. | Review DCTMV Plan deliverables submitted by Supplier for Acceptance and provide written feedback or written Acceptance in accordance with the schedule set forth in the plan | | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 558 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 25. | Review project planning documents , plans, and project schedules and subordinate documentation to identify CoreLogic information not included in such plans and documentation that, to CoreLogic’s knowledge, would cause Supplier’s responsibilities under the plan to be delayed, fail or be unacceptable to CoreLogic; provided, that this does not limit Supplier’s obligations under Section 4.2 of the MSA | | P |
| 26. | As part of the DCTMV Plan, develop and manage a communication plan to provide CoreLogic enterprise advance notification of changes and outages | P | |
| 27. | Manage the execution of the move packages as described in the DCTMV Plan | P | |
| 28. | Review completion of move packages for Acceptance against Acceptance criteria described in the DCTMV Plan | | P |
| 29. | Prior to the final execution of a move package and after the completion of a move package, ensure the receiving environment is operating as planned in the Supplier Data Center. | P | |
| 30. | For each move package, validate that all databases were successfully migrated to the applicable Supplier Facility | | P |
| 31. | For each move package, confirm that the data migration was successful and that all unstructured data was successfully transferred to the applicable Supplier Facility | P | A |
| 32. | For each move package, execute full backup of all migrated data and Systems as part of post-migration activities, as described in the DCTMV Plan | P | |
| 33. | For the Data Center migration project, install, manage and de-install network connectivity between CoreLogic Data Centers and Supplier Data Centers
| P | |
| 34. | Install and manage network connectivity between CoreLogic MPLS cloud (Intranet & Extranet) and Supplier Data Centers | P | |
| 35. | Perform Application testing for each move package and each impacted Application or business unit of a move package | | P |
| 36. | Provide resources to participate in the move execution, including data preparation( if required) and validation, and validation and acceptance of each moved Application and its data | | P |
| 37. | Perform virtualization assessment of the CoreLogic environment to identify virtualization opportunities and document them in the DCTMV Plan | P | |
| 38. | Develop a comprehensive physical-to-virtual plan for applicable Applications and data sources moving to a Virtual Server and document them in the DCTMV Plan | P | A |
| 39. | For select Servers as approved by CoreLogic during planning session, being migrated to Supplier Data Center develop pre-migration (baseline) and post-migration (realized) Infrastructure metrics for comparison, collected from the same Tools (metrics may be augmented with historical data from CoreLogic System management Tools). The metrics shall include CPU utilization, disk I/O, and memory utilization and the comparison shall yield performance consistent with current performance. In instances where performance is not acceptable to CoreLogic, CoreLogic and Supplier will develop an action plan with the intent of achieving acceptable performance and, upon CoreLogic’s approval of such plan, Supplier will implement such plan. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 559 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 40. | For select Applications being migrated to a Supplier Data Center, develop a *** pre-migration (baseline) and post-migration (realized) Application metrics for comparison, collected from the same Tool (the metrics in use with the CoreLogic Tools for that Application at time of migration). The comparison shall yield performance consistent with baseline performance. In instances where performance is not acceptable to CoreLogic, CoreLogic and Supplier will develop an action plan with the intent of achieving acceptable performance and, upon CoreLogic’s approval of such plan, Supplier will implement such plan.
| P | A |
| 41. | Activate the post-move environment’s management and monitoring Tools as part of the move activities | P | |
| 42. | Execute physical to virtual and virtual to virtual transformations as specified in the Data Center transformation, migration and virtualization plan | P | |
| 43. | Resolve Infrastructure defects identified in Application testing (user, business, Application, etc.) | P | |
| 44. | Address in-scope Application and Application data defects identified in Application testing (user, business, Application, etc.) where Infrastructure changes were not the cause | | P |
| 45. | Configure the receiving Data Center to the specified computing standards in respective Statements of Work and as defined in the MSA | P | |
| 46. | To the extent possible, line-up the Supplier transformation processes (e.g., physical to Virtual Server conversions) to the CoreLogic environment to be used as a repeatable transformation framework by Supplier for future transformations/ and migration, including aspects of: • Scheduling of activities (pre-transformation, transformation, post-transformation) • Change Management, • Configuration management • Transformation execution procedures • Data transport and verification of completeness and accuracy of data transported • Escalation processes • Contingency planning | P | |
| 47. | Perform asset disposal activities (including project management activities) as approved by CoreLogic for Data Centers and in accordance with Section 6.5(e)(ii) of the MSA. With respect to the other facilities described above, Supplier will manage disposal of the assets by CoreLogic’s Third Party Contractor | P | |
| 48. | Perform CoreLogic Data Center clean-up activities in accordance with Schedule A-2.7 as required by CoreLogic | P | |
| 49. | For each move package, update existing Disaster Recovery Plans and validate that disaster recovery solution is active. | P | |
| 50. | Schedule, coordinate and manage migration, post-migration and testing activities for both Supplier and CoreLogic until acceptance of the move package has been received | P | |
| 51. | Supplier will identify during the DCTMV Plan data replication strategies and tactics that account for and balance quality, minimize down time and Application changes of CoreLogic Systems | P | |
| 52. | Supplier will include tasks for training of applicable CoreLogic Personnel where Supplier’s processes changed as a result of DCTMV activities | P | |
| 53. | Locate Supplier Personnel at CoreLogic Facilities, as mutually agreed. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 560 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 2.3 | Operational Transition Services Roles and Responsibilities. |
This Section details the transition roles and associated responsibilities of the Parties during the Transition Period for Operational Transition Services.
| |
| 2.3.1 | Supplier Roles and Responsibilities. |
|
| |
| Role | Description |
| Customer Executive | Responsible for overall performance of Supplier’s transition team; maintain the relationship and interface with the CoreLogic Project Executive; complete Transition Services within agreed timeframe in accordance with Section 4.2 of the MSA; replace Supplier Personnel as needed to complete Transition Services deliverables; and agree to contract amendments on behalf of Supplier.
|
| Transition Project Executive | Responsible for overall success of the Transition Plan; interface with CoreLogic’s Transition Manager; coordinate all transition activities; provide transition status updates on a *** basis to CoreLogic and as requested by CoreLogic, provide risk and gap mitigation; ensure transition readiness; ensure overall transition of responsibility for the Services from CoreLogic to Supplier is successful and on-time; and manage stabilization activities.
|
| Knowledge Transfer Team / SMEs | Shadow the CoreLogic SMEs; complete the operational transition activities indicated in this Schedule; assist with projects and stabilization activities; support transition workshops; and provide tower expertise on migration and transition activities and deliverables.
|
| Transitioned Employees / SMEs | Participate in transition workshops; and assist Supplier in the transition activities. Generally leadership level and team lead level (for e.g. Intel sub-tower manager)
|
| |
| 2.3.2 | CoreLogic Roles and Responsibilities. |
|
| | |
| Role | *** Estimated Time Commitment to Transition | Description |
| Project Executive | *** | Provide a single point of contact for Supplier’s Account Executive; manage the overall relationship with Supplier and provide point of escalation in relation to any transition activities.
|
| Transition Manager | *** | Provide single point of contact for Supplier’s Transition Project Executive; provide input and sign-offs on transition deliverables; and approve the Transition Plan.
|
| Tower Leads / SMEs | *** | Provide a single point of contact for all tower knowledge transfer activities; participate in transition workshops; and assist Supplier in the transition activities. |
ARTICLE 3.
TRANSITION REPORTS
This Section describes the Reports that Supplier shall create and deliver to CoreLogic during the Transition Period.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 561 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| No. | Name | Frequency | Distribution Method | Start Date |
| 1. | Operational Transition Summary Status Report PDF/PPT Includes: • Key Program milestones, with progress • Schedule Variance and mitigations • Risk and issues with dependencies and current status • Recent accomplishments • Upcoming Plans • Key Messages from Program • G-Y-R indicator for scope, schedule, resources, risk and overall | *** | SharePoint | *** |
| 2. | Operational Transition work stream status Reports PDF/PPT • Key work stream milestones, with progress • Schedule Variance and mitigations • Risk and issues with dependencies and current status • Recent accomplishments • Upcoming Plans • Draft Project Schedules • Key Messages from Program • G-Y-R indicator for scope, schedule, resources, risk and overall | *** | SharePoint | *** |
| 3. | Operational Transition Project Milestone Schedule PDF (progressed) | *** | SharePoint | *** |
| 4. | Operational Transition Project Schedule PDF (progressed) | *** | SharePoint | *** |
| 5. | Operational Transition RAID Lists | *** | SharePoint | *** |
| 6. | Operational Transition Change Control List | *** | SharePoint | *** |
| 7. | Operational Transition RTM Deliverable Checklist | *** | SharePoint | *** |
ARTICLE 4.
INITIAL TRANSITION PLANS
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 562 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
The initial Transition Plan applicable to Operational Transition Services is set forth in Schedule A-10.1. The Parties acknowledge that such attached initial plan reflects dates that are not current or aligned with the dates identified in this Schedule A-10 (which Schedule accurately reflects the agreement of the Parties), and Supplier agrees to provide CoreLogic with an updated version of such initial plan that is consistent with this Schedule A-10 promptly after the Supplement Effective Date. Thereafter, such Transition Plan applicable to Operational Transition Services shall be updated, reviewed and approved in accordance with Section 4.2 of the MSA.
The initial DCTMV Plan is set forth in Schedule A-10.2.
ARTICLE 5.
TRANSITION MILESTONES
| |
| 5.1 | Transition Milestones for Operational Transition Services. |
The Transition Milestones applicable to Operational Transition Services are set forth in the table below. The Deliverable Credits that may be payable to CoreLogic if Supplier fails to meet a Transition Milestone are as set forth in Schedule A-4.5.
|
| | | |
| Transition Milestone # | Transition Milestone Name/Description | Acceptance Criteria | Transition Milestone
Completion Date |
| 1 | Execution of Offer Letters to Affected Employees | All offers electronically sent to CoreLogic employees who have completed the on-line application. | *** |
| 2 | On-boarding of all Transitioned Employees | Employees loaded into PeopleSoft, attended New Hire Orientation, received log-in and passwords for Dell Intranet and email, invitations to enroll in benefits including 401(k) were sent, and time and labor training completed. | *** |
| 3 | Interview completion for On-going Dell positions | Interviews completed for all requisitions opened to support the CoreLogic account on an on-going basis. | *** |
| 4 | Program Executive Workshop Complete | · Supplier produces meeting material that addresses Transition scope, project approach, timeline, Supplier and CoreLogic roles and responsibilities, confirmation of stakeholders, communication, and impacts to CoreLogic customers for all Services | *** |
| · Meeting is held presenting the material to CoreLogic and Dell leadership; Supplier introduces Transition leads to CoreLogic executives during PEW |
| · Supplier addresses Transition resource/skill concerns in accordance with resource/skill specific feedback provided by CoreLogic |
| · Materials are updated with feedback provided by CoreLogic |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 563 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Transition Milestone # | Transition Milestone Name/Description | Acceptance Criteria | Transition Milestone
Completion Date |
| 5 | Transition Resource Requirements | · Initial list of Dell Transition resources and type of systems access required by resources | *** |
| · Updated description of CoreLogic resource requirements and time commitments, accounting for feedback from PIW |
| · Initial list of supporting Transition documentation to be provided by CoreLogic (for existing environment) |
| 6 | Transition Initiation and Kick-off meeting (PIW) | · Supplier produces updated meeting material that formally addresses project introduction to project stakeholders (invitees) including scope, timeline, stakeholder confirmation, communication, introduction to methodology and project approach, governance, risk, assumptions, issues, and definitions for all Services | *** |
| · Meeting held and hosted by Dell Transition PMO with attendance by Dell and CoreLogic designated leaders, as approved by CoreLogic |
| · Supplier provided first draft of RTM with content from contract and Dell best practices |
| · Supplier introduces Transition leads to CoreLogic during PIW |
| · Supplier remediates Transition resource/skill concerns identified by CoreLogic |
| · Supplier collects feedback from PIW attendees and CoreLogic Transition leads, presents to Transition Governance and provides remediation for any deficiencies |
| 7 | Operational Transition Project Planning Workshop (PPW)and Meetings | · Supplier produces updated meeting material that formally address project detail planning phase of Operational Transition | *** |
| · Meeting addresses, by each work stream, the following: scope objective, requirements, deliverables, timeline, identification of stakeholder roles and responsibilities, OPAS requirements, communication, ongoing planning approach and governance for all Services |
| · Supplier collects feedback from PPW attendees and CoreLogic Transition leads and adjusts plan to reflect scope and approach details |
| · Agreement that ongoing planning meetings will be conducted in collaboration with CoreLogic, work stream by work stream, where continued detail will be addressed to complete work stream WBS, final deliverables with acceptance criteria, RAID |
| · Supplier highlights Operational Transition progress, issues and concerns |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 564 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| | Transition Milestone # | Transition Milestone Name/Description | Acceptance Criteria | Transition Milestone
Completion Date |
| | 8 | Operational Transition – Transition Plan Documents and Review | · Supplier produces material that defines the execution plan for the project that has taken account of the planning activities for all Services. | *** |
| | · Project Plan Document (PPD) is provided with a description of drivers for changes in scope, schedule, CoreLogic resources and effort from the Transition Plan in Section 1.6 and recommendations to remediate the timeline slippage and/or minimize the TCO financial impact |
| | · Updated MS Project Schedule (MPP) is provided as first project schedule baseline Requirements Traceability Matrix (RTM) is provided including feedback from PPW and additional input gathered through Operational Transition Planning Meetings and knowledge transfer sessions |
| | · Supplier provides walkthrough of the Transition Plan (PPD, MPP and PPW) in-person to aid CoreLogic in their review |
| | 9 | Final Policy & Procedures Manual | · RTM acceptance criteria for deliverable have been met and document’s components have been reviewed and approved by CoreLogic | *** |
| | 10 | OPAS Functionally Ready prior to “Go Live”. | · OPAS tool has been loaded as described in the Transition Plan | *** |
| | · OPAS tool has work flow loaded as described in Transition Plan |
| | · OPAS tool has been updated with information required for Supplier to perform support as described in the Transition Plan. |
| | · OPAS tool has been updated with information required for use by other CoreLogic users and process as described in the Transition Plan. |
| | · Service Management Assumption of Service (AOS) Checklist is completed for OPAS deliverables as described in the RTM, including successful completion of all agreed-upon test scenarios |
| | 11 | RTM Pre-Go Live Review | · Review RTM prior to “go-live” | *** |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 565 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Transition Milestone # | Transition Milestone Name/Description | Acceptance Criteria | Transition Milestone
Completion Date |
| 12 | Security Management Transition Complete | · RTM acceptance criteria for deliverable have been met, including: | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
| 13 | Service Management Transition Complete | · RTM acceptance criteria for deliverable have been met, including: | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| 14 | Messaging / Exchange Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 566 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Transition Milestone # | Transition Milestone Name/Description | Acceptance Criteria | Transition Milestone
Completion Date |
| 15 | End User Computing Transition Complete | o RTM acceptance criteria for deliverable have been met, including; Ability to connect to all required systems | *** |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
| 16 | Server Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Updated PPM |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
| 17 | Service Desk Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Demonstrated ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 567 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Transition Milestone # | Transition Milestone Name/Description | Acceptance Criteria | Transition Milestone
Completion Date |
| 18 | Network Transition Complete | o RTM acceptance criteria for deliverable have been met, including; Ability to connect to all required systems | *** |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
| 19 | Mainframe Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
| 20 | Storage and Backup Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 568 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Transition Milestone # | Transition Milestone Name/Description | Acceptance Criteria | Transition Milestone
Completion Date |
| 21 | Media Services Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
| 22 | Data Center Operations Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 569 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Transition Milestone # | Transition Milestone Name/Description | Acceptance Criteria | Transition Milestone
Completion Date |
| 23 | Production Control Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
| 24 | Monitoring Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 570 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Transition Milestone # | Transition Milestone Name/Description | Acceptance Criteria | Transition Milestone
Completion Date |
| 25 | Disaster Recovery Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
| 26 | Cross Functional Transition Complete | · RTM acceptance criteria for deliverable have been met, including; | *** |
| o Ability to connect to all required systems |
| o Successful achievement of Operational Readiness test through a pass/fail mechanism or a mutually agreed upon evaluation process |
| o In-person meeting to walk through FMO workflows and all business process changes |
| o Ability to measure all agreed-upon service levels, KPIs and reports |
| o Final PPM for sign-off |
| · Operational readiness includes awareness of the overall Transition, DCM and Transformation scope and deliverables |
| 27 | Transition complete and (FMO) Future Model Go-live | · RTM acceptance criteria for all Operational Transition deliverables have been met, including: | *** |
| o Sign-off for all Services |
| o Dell Tools, Reports, Processes and Systems are implemented and are able to measure service levels and key performance indicators |
| o Completed Dell supported tools, processes and systems training for CoreLogic Personnel |
| |
| 5.2 | Transition Milestones for DCTMV Transition Services. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 571 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
The Transition Milestones applicable to DCTMV Transition Services are set forth in the table below. The Deliverable Credits that may be payable to CoreLogic if Supplier fails to meet a Transition Milestone are as set forth in Schedule A-4.5.
|
| | |
| Transition Milestone Description | Transition Milestone Completion Date | Acceptance Criteria |
| Transition Milestone 1 -Data Center Move Project/ *** | *** | Supplier’s Work Breakdown Structure provides a level of granularity such that each task has at most a duration of ***.
Supplier’s Work Breakdown Structure assigns individual names, groups, or roles to each task.
Supplier has established mechanisms and methods for the agreed upon mitigation or contingency plan for risks identified by the Parties in the risk management section of the DCTMV Plan.
Supplier’s DCTMV Plan contains necessary tasks and milestones to complete the Data Center Move Project. |
| Transition Milestone 2-Data Center Move Project *** | *** | Supplier has included detailed move package plans for 2013 in the DCTMV Plan, including all System configuration changes and Change Management strategy, transformation strategy per application, detailed transformation work steps, system validation plans, contingency plans, backout plans, and has incorporated CoreLogic’s plans for application review, approval and validation by CoreLogic. |
| Transition Milestone 3- Data Center Move Project *** | *** | Supplier has completed the transformation of one-half of the planned move packages for 2013.
Target environment equals or exceed the pre-migration performance (baseline) for Application, CPU utilization, disk I/O, and memory. |
| Transition Milestone 4-Data Center Move Project *** | *** | Supplier has completed the transformation of the move packages for 2013.
Supplier has demonstrated that it has enabled all required monitoring, instrumentation and configuration services related to the transformation of such move packages. |
| Transition Milestone 5 Data Center Move Project *** | *** | Supplier has included detailed move package plans for 2014 in the DCTMV Plan, including all System configuration changes and Change Management strategy, transformation strategy per application, detailed transformation work steps, system validation plans, contingency plans, backout plans, and has incorporated CoreLogic’s plans for application review, approval and validation by CoreLogic. |
| Transition Milestone 6-Data Center Move Project *** | *** | Supplier has completed the transformation of one-half of the planned move packages for 2014.
Target environment equals or exceed the pre-migration performance (baseline) for Application, CPU utilization, disk I/O, and memory. |
| Transition Milestone 7-Data Center Move Project *** | *** | Supplier has completed the transformation of the move packages for 2014. Supplier has demonstrated that it has enabled all required monitoring, instrumentation and configuration services related to the transformation of such move packages. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 572 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 573 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 574 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 575 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 576 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 577 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 578 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 579 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 580 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 581 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 582 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 583 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 584 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 585 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 586 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 587 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 588 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 589 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 590 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 591 |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 592 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-10.3
ADDITIONAL TRANSITION SERVICES OBLIGATIONS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 593 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-10.3
Additional Transition Services Obligations
| |
| 1.1 | Agreement. This Schedule A-10.3 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to this Supplement, or the other Schedules to the MSA or this Supplement. The following terms shall have the meanings given below: |
“2012 CoreLogic Project Pool” has the meaning given in Section 3.1.
“Additional Personnel” has the meaning given in Section 2.5.
“CoreLogic Projects” has the meaning given in Section 2.3.
“Joint PMO” has the meaning given in Section 2.3.
“Steady-State Transition Services” has the meaning given in Section 2.2.
“Supplier Technical Leads” has the meaning given in Section 2.8.
“Steady-State Transition Services Period” has the meaning given in Section 2.2.
| |
| 2. | ADDITIONAL TRANSITION SERVICES OBLIGATIONS. |
| |
| 2.1 | Overview. As part of the Transition Services, and in addition to the other Transition Services obligations described in Section 4.2 of the MSA and Schedule A-10, Supplier shall perform the Transition Services described in this Schedule A-10.3. |
| |
| 2.2 | Steady-State Transition Services. Commencing August 13, 2012 and continuing through *** (the “Steady-State Transition Services Period”), Supplier shall perform the Services at levels of accuracy, quality, completeness, timeliness, responsiveness and resource efficiency that are at least equal to the documented or otherwise verifiable levels received by the Eligible Recipients during the *** (***) *** prior to the Supplement Effective Date, and at levels that are equal to or higher than the accepted standards of *** providers of similar services (the “Steady-State Transition Services”). For clarity, the Service Levels set forth in Schedule A-3 shall not be applicable until the Commencement Date (or later, to the extent a later date is expressly provided in Schedule A-3). |
| |
| 2.3 | CoreLogic Projects. During the Steady-State Transition Services Period, Supplier will provide resources to perform in-flight projects, “reboot” projects, stabilization projects and any other projects identified by CoreLogic (collectively, “CoreLogic Projects”) in the *** and staffing as determined by the Supplier PMO and the CoreLogic PMO (collectively, the “Joint PMO”) in accordance with Section 3 below. Schedule A-10.3.1 sets forth a list of CoreLogic Projects identified by CoreLogic as of the Supplement Effective Date. Supplier *** to assist primarily with performance of the CoreLogic Projects. CoreLogic shall have the right to *** to be performed by the Additional Personnel between the CoreLogic Projects, Steady-State Transition Services, and the other Transition Services, in accordance with Section 2.7. |
| |
| 2.4 | Transitioned Employees. Supplier shall maintain all Transitioned Employees on CoreLogic’s account for the performance of (i) the Services ***Section ***, (ii) CoreLogic Projects as agreed by the Joint PMO in accordance with Section 3 and (iii) other Transition Services to be performed by Supplier (e.g., those |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 594 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
contemplated by the Transition Plan, including DCTMV activities as described in the DCTMV Plan), but only to the extent permitted pursuant to Section 2.7. For the avoidance of doubt, the day-to-day management of the Transitioned Employees shall be the responsibility of Supplier. Unless otherwise agreed by the Supplier PMO and the CoreLogic PMO, in accordance with Section 3.3 below, the Transitioned Employees shall continue to perform their assigned responsibilities with respect to CoreLogic Projects on which they were engaged as of the Supplement Effective Date, providing a level of effort that is no less than such Transitioned Employees provided prior the Supplement Effective Date.
| |
| 2.5 | Additional Personnel. In addition to the Transitioned Employees provided by Supplier during the Steady-State Transition Services Period pursuant to Section 2.4, Supplier will provide an additional ***(***) FTEs of Supplier Personnel resources (“Additional Personnel”) during the Steady-State Transition Services Period for (i) the Services as contemplated by Section 2.2, (ii) CoreLogic Projects as contemplated by Section 2.3 and (iii) other Transition Services to be performed by Supplier (e.g., those contemplated by the Transition Plan, including DCTMV activities as described in the DCTMV Plan), but only to the extent permitted pursuant to Section 2.7. |
| |
| 2.6 | Backfilling Transitioned Employees. If, at any time during the Steady-State Transition Services Period, any Transitioned Employee is unable to continue to perform his or her respective obligations as described in Section 2.2 (e.g., due to voluntary departure from Supplier’s organization, sickness or death) notwithstanding Supplier’s obligation to maintain such personnel on CoreLogic’s account during the Steady-State Transition Services Period, Supplier shall, ***, promptly (in any event *** (***) ***) replace such personnel with a Supplier Personnel that has suitable ability and qualifications. |
| |
| 2.7 | Support of Other Transition Services. Notwithstanding Sections 2.4 and 2.5, Supplier shall have the right to use the Transitioned Employees and Additional Personnel in the performance of the other Transition Services to be performed by Supplier (e.g., those contemplated by the Transition Plan), at FTE levels substantially consistent with a level of effort equal to *** (***) FTEs in any month. If Supplier would like to use Transitioned Employees or Additional Personnel in the performance of the other Transition Services (e.g., those contemplated by the Transition Plan) at FTE levels higher than *** (***) FTEs in any month, Supplier shall propose such additional FTE usage to CoreLogic and provide appropriate documentation and presentations that Supplier is meeting Supplier’s obligations set forth in this Schedule A-10.3. It shall be in the *** of CoreLogic’s Chief Information Officer or VP, ETS as to *** given Supplier’s actual performance of its obligations in accordance with the requirements of this Schedule A-10.3. |
| |
| 2.8 | Supplier Technical Leads. In addition to the Transitioned Employees and the Additional Personnel provided by Supplier during the Steady-State Transition Services Period pursuant to Sections 2.4 and 2.5 respectively, during the Steady-State Transition Services Period, Supplier shall provide Supplier Personnel for the technical lead assistance topics identified in Schedule A-10.3.1 (the “Supplier Technical Leads”). The Supplier Technical Leads shall be assigned to the CoreLogic account and shall remain under the direction of Supplier. In addition to their obligations performing other Transition Services (e.g., those contemplated by the Transition Plan, including DCTMV activities as described in the DCTMV Plan), the Supplier Technical Leads shall be responsible for providing management support for the Steady-State Transition Services, technology architecture guidance and support, operational advice and guidance to the Eligible Recipients in connection with readying themselves to receive the Services and other specific technical and/or architectural questions that arise from or are related to the CoreLogic Projects and/or the Services that will be performed by Supplier beginning on the Commencement Date. |
| |
| 2.9 | Procurement Subject Matter Expert. During the first *** (***) *** of the Steady-State Transition Services Period, Supplier shall provide procurement expertise for the amount of time necessary to assist CoreLogic in reviewing all of CoreLogic’s third party software contracts to determine whether there are any opportunities to further reduce CoreLogic’s retained third party software contract expenditures. |
| |
| 2.10 | Provision of Pricing Information Related to CoreLogic-Retained Equipment and Systems. With respect to Equipment and Systems that (i) are CoreLogic’s financial responsibility under this Supplement to obtain in connection with the Services (and are not otherwise contemplated by the pricing mechanisms set forth in Schedule A-4) and (ii) are available to be purchased from Supplier (either directly or through resale), upon CoreLogic’s request, Supplier shall *** provide pricing and availability information for such Equipment and |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 595 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Systems so that CoreLogic can make a procurement decision as to whether to procure such Equipment and Systems from Supplier. Nothing in this Section 2.10 shall be deemed to constitute an offer, commitment or obligation for CoreLogic to procure such Equipment or Software from Supplier.
| |
| 2.11 | PMO Cooperation. The respective PMO of each Party shall cooperate in good faith to monitor the respective obligations of each Party contemplated by this Schedule A-10.3 and Schedule A-10.1 and work together to identify, address and resolve any issues that arise therefrom in accordance with the governance procedures set forth in Schedule 6. |
| |
| 3. | MANAGEMENT OF CORELOGIC PROJECTS. |
| |
| 3.1 | 2012 CoreLogic Project Pool. During calendar year 2012, the Supplier Personnel available to work on CoreLogic Projects shall consist of the Transitioned Employees and the Additional Personnel (collectively, the “2012 CoreLogic Project Pool”). |
| |
| 3.2 | Not Determinative as to Chargeable Project Status. For the avoidance of doubt, whether an activity or Project is identified as a *** shall not be determinative as to whether such activity or Project or a similar activity or Project constitutes a Chargeable Project after the Steady-State Transition Services Period, which determination shall be based solely on the provisions of Schedule A-4.10. |
| |
| 3.3 | Staffing of CoreLogic Projects and Transition Services. |
| |
| (a) | Initial Validation and Assignment. Within *** (***) *** after the Supplement Effective Date, the Supplier PMO and CoreLogic PMO shall meet to (i) validate the scope, schedule and resources for all existing CoreLogic Projects and (ii) assign personnel within the 2012 CoreLogic Project Pool to such CoreLogic Projects in accordance with this Section 3. *** shall retain the right to balance the 2012 Project Pool between the Steady-State Transition Services and CoreLogic Projects; provided, that such balancing does not adversely affect or interfere with (i) the Steady-State Transition Services (subject to Section 2.2, and further subject to the provisions Section 4.4 of the MSA with respect to reprioritization of such Steady-State Transition Services, where Supplier is unable to accommodate such reprioritization) and (ii) subject to Section 2.7, the other Transition Services to be performed by Supplier (e.g., those contemplated by the Transition Plan, including the DCTMV activities). Subject to the foregoing, the Joint PMO shall work together to manage the 2012 Project Pool to balance the Steady-State Transition Services and the CoreLogic Projects. |
| |
| (b) | Weekly Meetings on CoreLogic Projects. The Supplier PMO and CoreLogic PMO shall meet *** to affirm, reprioritize or update the schedule for CoreLogic Projects (in accordance with Section 2.3 regarding CoreLogic’s right to re-prioritize), as needed, to enable the CoreLogic Projects to be most efficiently performed concurrently with, and without adversely affecting or interfering with (i) the Steady-State Transition Services (subject to Section 2.2, and further subject to the provisions Section 4.4 of the MSA with respect to reprioritization of such Steady-State Transition Services, where Supplier is unable to accommodate such reprioritization) and (ii) subject to Section 2.7, the other Transition Services to be performed by Supplier (e.g., those contemplated by the Transition Plan, including the DCTMV activities). |
| |
| (c) | Notwithstanding anything to the contrary in this Schedule, the Parties agree that this Schedule A-4.10 shall not constitute an agreement that the CoreLogic Projects shall be completed during calendar year 2012. |
| |
| 3.4 | CoreLogic agrees to provide reasonable guidance and advice with respect to the CoreLogic Projects, the Steady-State Transition Services and the other Transition Services. |
| |
| 3.5 | To the extent that additional resources are required to work on CoreLogic Projects, CoreLogic may request that Supplier provide additional Supplier Personnel for the performance of CoreLogic Projects. The Productive Hour rates for such additional resources are set forth in Schedule A-4.7 (Rate Card). |
| |
| 3.6 | The methodology described in this Schedule A-10.3 with regard to CoreLogic Projects shall only be applicable during the Steady-State Transition Services Period and shall not be applicable thereafter. For the avoidance of doubt, Schedule A-4.10 shall not be applicable until ***. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 596 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 597 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-10.3.1
CORELOGIC PROJECTS AS OF THE SUPPLEMENT EFFECTIVE DATE
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 598 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-10.3.1
CoreLogic Projects as of the Supplement Effective Date
| |
| 1.1 | Agreement. This Schedule A-10.3.1 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to this Supplement, or the other Schedules to the MSA or this Supplement. |
| |
| 2. | CORELOGIC PROJECTS AS OF THE SUPPLEMENT EFFECTIVE DATE. |
|
| | | |
| Type | State | Project Name | Project Description |
| In-Flight | Pending Request | *** Services: *** | Establish DR environment for *** application |
| In-Flight | Pending Request | Data Operations: *** Online | Establish DR environment for *** Online |
| In-Flight | Pending Request | *** Services: *** | Establish DR environment for *** application |
| In-Flight | Pending Request | *** Services: *** | Establish DR environment for ***application |
| In-Flight | Pending Request | *** Services: *** | Establish DR environment for ***application |
| In-Flight | (1) Proposed | 7269 *** Services - Infrastructure Migration to Corporate Data Centers | Migrate all managed infrastructure from the *** remote service centers to Corporate Data Centers. |
| In-Flight | (1) Proposed | 7293 *** Fortify | Project Fortify represents the overall program to deliver stability and resiliency back to the *** platform. Areas of focus will include: Service Tier capacity Service Tier resiliency Service Tier Isolation *** capacity *** resiliency *** capacity Application resiliency Monitoring |
| In-Flight | (1) Proposed | 7294 *** *** | Use *** to *** all respective *** in Dallas and Santa Ana in order to ensure we meet the *** audit requirements for BU which do business with ***. BU's in scope are; *** |
| Reboot | (1) Proposed-Approved/
Pending Assignment | 7137 *** Server Lease Refresh (445, 446, 450, 451) | Refresh servers as identified for the following leases: 445 - ~146 446 - ~68 450 - ~43 451 - ~6 |
| In-Flight | (1) Proposed-Approved/
Pending Assignment | 7287 *** (*** of accts required for *** Reporting) | Upgrade the *** to Release *** from its current version of ***. This project will occur in multiple phase with the first phase being the *** module by the end of 2012. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 599 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Type | State | Project Name | Project Description |
| In-Flight | (1) Proposed-Approved/
Pending Assignment | 7292 *** and Migration from Colo (Colo termination is end of year) | Move *** systems fromcolo (located in San Francisco),disconnect circuits, decommission servers as appropriate. While *** systems are no longer in use, email and application data will need to be preserved so that information requests that occur as part of litigation can be satisfied.Will need to determine specific requirements for access, and how long data will need to be retained. *** environment consists of approx. *** Windows servers (mostly VM on ESXi ***). DBMS is *** Server. |
| In-Flight | (1) Proposed-Deferred | 7285 *** and *** Update Firmware, BIOS, Drivers | Update *** Servers with the following: 1) *** drivers and software updates 2) *** drivers and software updates 3) *** drivers and software updates The list of servers is available on this *** site: |
| In-Flight | (1) Proposed-Deferred | 7289 *** and *** (changed date from 5/31/13 - 12/31/12- talk with Eric) | *** |
| In-Flight | (1) Proposed-On Hold | 7261 DR for *** system | Implement DR for the *** system. The production environment for this application is in the SATC, so DR will be established in the DTC. |
| In-Flight | (1) Proposed-On Hold | 7270 DR for *** | Build DR environment for ***. |
| In-Flight | (1) Proposed-On Hold | 7271 DR for *** | Build DR environment for ***.• Status – o Proposed & On Hold; Originally requested on *** and has been on hold since ***; Placed lower on the priority list for DR; asked to hold off on activation to focus on higher priorities.• Project Description –o Build DR environment for ***.• Scope of Work –o Design and implement a DR environment for ***.o Some of the servers identified in the OnBoarding documentation may be included in the active *** DR project 7100.• Effort expected – o Low to moderate• ETS Teams Impacted –o DBA; o ESM - SAN Design & Architecture; o ESM - SAN Engineering; o InfoSec Engineering; o InfoSec Services; o IT Service Continuity; o Network/Firewall Design; o Network/Firewall Engineering - Windows |
| In-Flight | (1) Proposed-On Hold | 7275 DR for *** | *** and *** DR |
| In-Flight | (2) Active | 6180 *** | The purpose of *** (previously ***) is to achieve the following objectives: Transform and re-design the core tax processing using a business component-based design; *** and *** requirements into a single *** system; Eliminate the use of *** products which includes the ***programming language, the ***database and other technical products. The systems that use Software AG products include (but are not limited to): ***, ***, ***, ***, ***, ***, ***, ***, ***, ***and ***; Eliminate and consolidate applications and databases; Provide graphical user interfaces and full use of ***; Eliminate All *** applications and databases. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 600 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Type | State | Project Name | Project Description |
| In-Flight | (2) Active | 7036 *** | The *** project (***) will encompass the efforts to move data capture, processing and extract to products onto a new, distributed platform. |
| In-Flight | (2) Active | 7041 *** Data Center Migrations | 7041 *** Data Center Migrations ***, ***Services, ***. In addition, migration of all ancillary servers and equipment. Projects 7038 and 7041 have been combined. |
| In-Flight | (2) Active | 7100 *** DR | |
| Reboot | (2) Active | 7128 *** VoIP Integration | Migrate *** VOIP environment into the CITG Corporate VOIP infrastructure. |
| In-Flight | (2) Active | 7130 SharePoint 2010 Implementation | Date is still influx. Sharepoint 2010 implementation. This will include infrastructure, application setup and configuration for all environments (QA, UAT, Production). DR systems are included in scope, but yet to be kicked off. |
| In-Flight | (2) Active | 7144 *** Project | We need to standardize the ***onfiguration to ***. The work will be accomplished on the *** devices in both SATC and DTC. |
| In-Flight | (2) Active | 7145 ***and *** System Upgrade for *** (DR SYSTEM) | Upgrade of ***and ***production environments to ***11.x Build out of a Dev/QA and DR environment. Production completed DR systems are in scope but yet to be kicked off and prioritized. |
| In-Flight | (2) Active | 7149 ***for all in scope applications with *** | For regulatory reasons, *** requires an *** solution implemented for all internet applications that display sensitive customer information. |
| Reboot | (2) Active | 7161 CoreLogic VoIP Technology Refresh Program | The Program will consist of a technology refresh for the corporate VoIP IPTel infrastructure and will encompass the following subprojects; *** upgrade, *** migrations and migration of all sites that were on the legacy VoIP IPTelsystem as of June 2011; as well as the migration of the ***, ***users. |
| In-Flight | (2) Active | 7176 Remediate *** Owned Domain Names | *** |
| Reboot | (2) Active | 7208 Santa Ana Storage Refresh | Leases are set to expire on 13 storage frames in the next 12 months. The servers and data from the following storage arrays are in *** |
| In-Flight | (2) Active | 7209 ***DR *** | Create a DR environment for the ***)and ***applications. |
| In-Flight | (2) Active | 7212 SNA *** 2797 Migration | Storage Frame *** 2797 has performance that have been prevalent since it was installed. *** has provided a new frame called *** 4350. All storage will be migrated to the new frame |
| In-Flight | (2) Active | 7220 Move ***and ***Training Software | Migrate ***/ ***training software from ***systems (2 web/1 db/app server) to CoreLogic. Also, identify the support ownership for this software going forward as ***currently is providing support and does not use the software. This is required to complete company "split" activities between *** and CoreLogic |
| Reboot | (2) Active | 7225 Site Migrations to SIP | The purpose of this project is to migrate 13 key sites to SIP. Many other sites are being migrated to SIP but these sites were carved out to complete early so cost savings could be captured earlier as opposed to waiting until other VoIP activity was completed and starting then. Cost savings are targeted at $***k in 2012 and $***k YOY |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 601 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Type | State | Project Name | Project Description |
| Reboot | (2) Active | 7226 VoIP Technology Refresh Migration | As part of 7161 VoIP technology refresh program, this project will address the actual migration of each site from the legacyETS managed VoIP environment as of June of 2011, over to the new refreshed VoIP environment. |
| Reboot | (2) Active | 7228 VoIP Infrastructure Refresh | Refresh entire telephony hardware with new technology: *** and upgrade software from *** to ***. This will also incorporate the implementation of CER. |
| In-Flight | (2) Active | 7230 *** Network Services Separation | Seamless migration of *** and assets off of the CoreLogic network and onto the *** network. Majority of items will be complete by ***, however, additional work due to ***'s will extend timeline. |
| In-Flight | (2) Active | 7232 *** Enterprise Services Separation | Ensure that all *** resources are moved out of the *** domain while ensuring that user access remains the same. |
| In-Flight | Completed | 7236 *** True Up 2012 | Our Enterprise Agreement (EA) with *** enables us to use additional licenses for any product covered by our EA. Once a year we are required to align our EA with the number of total licenses we’ve added in the previous 12 months. The True Up is a census of all the qualified desktops, users, and processors added to our organization over the course of the year. It’s a way to actively manage our assets—to determine what we have, what we’re missing, and what we need to add to increase efficiencies in our organization. To determine our True Up, we must first inventory all of our desktops, servers and operating systems. Next, we will analyze our owned licenses compared to the Microsoft software deployed to optimize said licenses and purchase any additional deficiencies to keep CoreLogic compliant. The 2012 True Up will also have some additional scope related to (1) DR and (2) access license requirements for *** New BUs RP Data, Dorado and Realty Bid will also need to be included |
| In-Flight | (2) Active | 7237 *** Services DR Environment Redesign | Set up *** DR at SATC using CITG standard processes and procedures |
| In-Flight | (2) Active | 7240 *** Services DR Build | Build DR at SATC |
| In-Flight | (2) Active | 7245 Santa Ana Office Move to Irvine | Move the business offices of CoreLogic in Santa Ana and associated offices to the new office in Irvine, CA |
| In-Flight | (2) Active | 7249 Data Fulfillment Server build in SNA | The owner, ***, in Sunrise works for Data Operations Data Fulfillment and has a current environment in Florida that has outgrown the current infrastructure. The request is to move Data Fulfillment to SNA on to a physical server that is already here in the SNA data center. This server is being given to *** from Anton. *** also wants 2 new VMS one for development and another as a failover server that will have the same capacity of the production server. There is a need for 6TB storage and DR with 24 hour recovery must be set up in Dallas. This DR is *** *** agreement. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 602 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Type | State | Project Name | Project Description |
| Reboot | (2) Active | 7250 DARES *** Application Upgrade and Migration to Cloud | *** plans to upgrade the existing *** application in order to streamline and simplify the platform and to re-brand the domains from ***. ETS work has completed, however, waiting on BU to complete testing. |
| In-Flight | (2) Active | 7255 *** Prod Migration to Dallas DC | Credco's largest client, *** gives *** volume between *** and ***. However, if there is an issue with SNA infrastructure, both *** systems can be down. The business would like to move *** into Dallas to segregate these environments to have better redundancy for their clients and availability of systems over both Data Centers |
| In-Flight | (2) Active | 7258 Enterprise Access Management | Standardize workflow for access management for all *** systems to avoid recurring deficiencies in *** key control testing. |
| Reboot | (2) Active | 7262 *** Migration to CoreLogic Datacenters | Complete the migration of *** to CoreLogic Data Centers |
| In-Flight | (2) Active | 7267 *** Refresh | As part of the 7161 VoIP technology refresh program, this project will refresh the call recording infrastructure (***). |
| In-Flight | (2) Active | 7272 Migrate *** to Consumer Zone Network | *** has experienced numerous outages from activities on shared services. It has been recommended for environment stability to isolate *** network. |
| In-Flight | (2) Active | 7274 *** Isolate SAN | *** has experienced numerous outages from activities on shared services. It has been recommended for environment stability to isolate *** SAN infrastructure and fabric. This will not complete by 6/30. Pending a detailed plan from the ESM team so that a new target date can be established. |
| In-Flight | (2) Active | 7276 *** Service Restoration Program | Program is being initiated to coordinate the efforts to stabilize the *** environment and bring service availability levels at or below the baseline level from October 2011. |
| In-Flight | (2) Active | 7277 *** Office Move | The *** office needs to move to a new location before July 1st, 2012. The new location for the office has not been confirmed yet. Facilities (***) is currently looking at locations. |
| Reboot | (2) Active | 7280 *** Migration to CoreLogic Datacenters | Migrate the computing platform (production currently located in *** with DR in ***) to the CoreLogic Corporate Data Centers located in Westlake, Tx and Santa Ana, CA. The relocated data center will support ***'instance of the *** settlement services platform and other employee services. |
| In-Flight | (2) Active | 7282 SATC FW Hardware and OS Upgrade | Upgrade *** FW hardware and OS on the SYS, DMZ and APP tier firewall pairs in Santa Ana, CA. |
| Reboot | (2) Active | 7283 SATC and DTC SAN Fabric Refresh | Compete refresh of the SAN fabric in both DCs. Requires significant recabling. Must be complete by 12/31 to return existing switches for credit. This project is to coordinate the installation, and migration efforts. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 603 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Type | State | Project Name | Project Description |
| In-Flight | (2) Active | 7284 SOX 2012 | Identify and manage remediation initiatives to ensure that we have minimal deficiencies for SOX in 2012. Major activities in this project include commonizing the Change Management process for the SOX applications, addressing account management problems, and expanding the coverage to new applications such as RP Data and ***. |
| In-Flight | (2) Active | 7287 Upgrade *** | Upgrade the *** from its current version of ***. This project will occur in multiple phase with the first phase being the *** module by the end of 2012. |
| In-Flight | (2) Active | 7288 Storage Reporting Tool Roll Out | Install, configure and rool out the *** performance and reporting tool. |
| In-Flight | (2) Active | *** DR Remediation | Remediate *** issues identified during the DTC Spring 2012 DR Test. |
| In-Flight | (2) Active | *** DR Environment | Address the *** DR Environment so it can be tested successfully in DR tests. A successful test includes connectivity to the appropriate servers, and proper execution of jobs in the DR environment. |
| In-Flight | (2) Active | *** DR Environment Review | In the recent SATC DR test it was discovered that several of *** servers were inaccessible. This effort will perform a thorough review of *** DR environment to ensure all servers are present and functioning, OS and patching levels are current, and application code and data is current. |
| In-Flight | Completed | Establish VDI for SATC Testing | Establish VDIs for SATC DR Testing. To be included is the standard image, firewall rules, access, etc. |
| In-Flight | (4) On Hold | 7020 Employee Provisioning Program | • This is the “umbrella” program. No activities at this level.
• This has included the following projects (all are closed / on hold)
o 7030 *** Development - closed
o 7034 *** Implementation - closed
o 7042 Enterprise Device Control - closed
o 7094 PC Refresh - closed
o 7146 OneForm – on hold (Service Online Development) |
| Reboot | (4) On Hold | 7057 FACL *** Migration to VMware | Migrate approximately185 *** *** sessions over to VMWare platform in SATC. |
| In-Flight | KOH | 7108 FADV Credit Services' *** Helpdesk Migration to Service Online | To migrate Credit Services' *** Helpdesk to Service Online |
| In-Flight | (4) On Hold | 7146 One Form | Create a provisioning form that will be available in SOL. |
| Reboot | (4) On Hold | 7217 Rationalize Data, Storage and Backup | Identify more cost effective methods for storing and managing static data throughout CoreLogic. The overall goal of the project is to achieve cost savings by reducing storage, data, and backups without requiring changes to business unit applications. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 604 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Type | State | Project Name | Project Description |
| Reboot | (4) On Hold | 7218 IT Transformation Initiative – Moving Into Cloud | Perform a financial analysis of the x86 technology servers in the Dallas and Santa Ana Technology Centers. The analysis scope includes three major areas: (1) the migration of physical servers to virtual platforms, (2) moving virtual clusters into the Cloud and (3) creating a Cloud 2.0 environment to enable auto-provisioning of test/dev servers. The overall goal of the project is to achieve cost savings by migrating existing servers into lower cost platforms by taking advantage of virtualization and multi-tenant Cloud environments |
| In-Flight | (4) On Hold | 7239 *** DR Environment Redesign | Build DR for *** at SATC |
| In-Flight | KOH | 7244 *** Enterprise Management Tool | Evaluation, Selection and Implementation of *** Enterprise Management tool to be able to accomplish the following two major initiatives: 1) Regular *** Management 2) Asset Management - Software & Hardware Inventory This project will be done in 2 phases - evaluation & selection of tool as first phase & implementation/roll-out as the second phase. |
| Reboot | (4) On Hold | 7246 *** Upgrade (out of support) | Upgrade all of the *** servers running *** This project needs to be coordinated with other CITG efforts/projects in progress - 7218 - IT Transformation Initiative - Moving to Cloud, 7212 - *** 2797 Migration, etc. |
| In-Flight | (4) On Hold | 7251 *** Disaster Recovery and Environment Resizing | Implement a disaster recovery solution in Dallas for ***. An additional requirement is to review the size of the current Santa Ana webfarm and resize according to current need. |
| In-Flight | KOH | 7252 *** DR | Create the DR environment for ***s application of Product Management & Analytics. |
| In-Flight | *** | *** | Move *** Production Environment Behind *** Firewall. Migrate production environment to new secure VLAN environment to *** and prospects.
• Status –
o Placed on hold 2/23/12 due to requirement to focus on *** stabilization efforts instead, which took a higher priority. Probably need to start this up again soon.
• Work remaining –
o Identify vmotion strategy for four staging and one prod virtual SQL servers
o Prerun cable for Production physical SQL servers SAN connection
o Staging servers cutover to new IP
o Move Production SQL servers to new rack location
o Production servers cutover to new IP
• Effort expected –
o Moderate
• ETS Teams involved –
o PMO – *** o Client Mgmt – *** o Network – ***; ***; ***; *** o Windows / Cloud - ***; ***o EDE – ***o EAPM – ***; *** o ESM - *** o DBA - ***, Danny |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 605 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| Type | State | Project Name | Project Description |
| In-Flight | (2) Active | *** Ops Stabilization | This is driven by the BU and includes *** (including networking and even a review of their power resiliency), Citrix and RightFax capacity and performance & VOIP
Enterprise Systems, Telephony, Network |
| Reboot | (2) Active | Hardware Maintenance Rationalization | Seek significant reductions in the cost of information technology hardware maintenance through eliminations or reductions in service levels. |
| Reboot | (2) Active | Telecom Cost Reduction | Reduce CoreLogic's investment costs for backup data circuits through eliminations or reductions of bandwidth. |
| Reboot | (2) Active | Third-Party Software
Rationalization | This project seeks to reduce the cost of CoreLogic third-party software through eliminations, volume reductions and supplier negotiations. |
| Reboot | (2) Active | Wireless Device & Services Rationalization | Reduce the cost of wireless and conferencing services. |
| Reboot | (2) Active | Data Center Consolidations | Complete data center consolidation for *** locations have 11/30 termination date. |
| Reboot | (2) Active | Data Center Consolidations | Complete data center consolidation for Las Vegas |
| Reboot | (2) Active | Data Center Consolidations | Complete data center consolidation for Greensboro. 03/13 expiration |
| Reboot | (2) Active | U-L | Migrate to Linux servers and cancel/retire UNIX. Also in scope is migration from *** and back-level ***. |
| Reboot | (4) On Hold | 7256 *** 300+ Single Tenant Virtual Servers to the Cloud | *** requests to move all their Virtual Servers to the CoreLogic Cloud. 1. 300+ single tenant virtual servers - include the 15 Vancouver virtual servers (see attached spreadsheet from ***) 2. Prioritize 42 Virtual Servers that are causing production issues (see attached email from *** dated 10/27) |
|
| | |
| Technical Assistance Topic | Project Name | Project Description |
| ALL | Stabilization | Need to support day-to-day operations and stabilization staff. |
| Network | Next Gen Firewall | We did a POC and selected *** to replace ***. It has been with *** for months who is supposed to be negotiating with *** but it hasn't gone anywhere. I haven't pushed it because of *** |
| Cloud | Dell Cloud in CoreLogic Data Centers | Need strategy (POD) for what components would be included. Need to address Business needs and balance long term strategy and migration approach. |
| Storage | *** stabilization | SNA *** system is performing well enough to have solid ***. Performing POC with *** appliance. |
| UNIX | U-L Migration (Transformation)
REBOOT Initiative | Migrate to LINUX servers and cancel / retire *** boxes |
| Telephony | New VoIP system stabilization | Audit and review the system and processes |
| Various | Migrate *** to Data Center | Migrate the *** ***) Data Center and associated DR. Due date Oct 31, 2012 |
| Various | Migrate *** to Data Center | Migrate the Primary and Backup Data Centers *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 606 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | |
| Technical Assistance Topic | Project Name | Project Description |
| Various | Migrate *** to Data Center | Migrate the Backup Data Center |
| Various | Migrate *** to Data Center | Migrate the *** Data Center |
| Information Security | *** | Need to build *** to gain visibility and proactively manage *** in the ETS environment. |
| Information Security | Patch Management | Need to solve the Patch and Asset Management problem for Windows, Unix and Linux. Combined initiatives from Hannah, Don, *** to POC three solutions: *** |
| Information Security | Roles and Controls | IT controls for ***. Initially dedicated to address *** but this has to be expanded to cover all *** including ***. We need to standardize *** inventory, *** connectivity standards*** monitoring and *** management for all our *** activities. |
| Information Security | *** Audit | *** audit for *** with ***. Requirement from ***. |
| Contracts | *** Mainframe Upgrade | There is an initiative that has been in progress for months to handle the hardware and software issues related to the *** mainframe in Westlake. We are close to making recommendations and decisions, but need the Tetris partner to agree to strategy and direction. |
| Contracts | Software AG Terms Restriction | The Software AG contract has a problematic clause in it which *** our ***. This is very relevant to planning for the Tax mainframe in Westlake. |
| Open Systems | *** Chassis return | *** has created some risk because we have deployed many more chassis than we have paid for. We need to move servers to free up chassis |
| Windows | *** Lease returns/refreshes | Satisfy our contract obligation regarding upcoming leases:
7137 *** Server Lease Refresh (445, 446, 450, 451) |
| Corp Systems | Migrate off ***to *** | Migrate Request, Change, Incident forms and processes off ***tool onto ***. |
| Corp Systems | Deploy SSO on-premise solution | Deploy SSO on-premise solution |
| Corp Systems | Deploy unified ESB | Deploy unified ESB (using ***), establish SOA Governance and Registry with dev, qa, prod environment |
| Infrastructure | Remote Office Support | Discuss *** strategy for remote office support (file and print servers, backups, etc) |
| Infrastructure | 7275 DR for *** | *** DR |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 607 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-11
CUSTOMER SATISFACTION SURVEYS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 608 |
Schedule A-11
Customer Satisfaction Surveys
| |
| 1.1 | Agreement. This Schedule A-11 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and attachments shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 2. | CUSTOMER SATISFACTION SURVEYS |
Within thirty (30) days after the Supplement Effective Date, the Parties will work in good faith to develop the customer satisfactions surveys that Supplier will conduct in connection with the customer satisfaction Service Levels set forth in the “Service Mgmt – SLA” tab of Schedule A-3.1.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 609 |
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-12
REPORTS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 610 |
Schedule A-12
Reports
| |
| 1.1 | Agreement. This Schedule A-12 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA, Schedule A-1 to Supplement A or elsewhere in the Agreement. |
Supplier shall provide, at the frequency specified in the table below, the following Reports to permit CoreLogic to monitor and manage Supplier’s performance under the Supplement. Additional Reports shall be provided by Supplier on an ad hoc or periodic basis, subject to Section 9.2(a) of the MSA. Supplier shall maintain at least twelve months of historical data for all Reports. Supplier shall also provide other Reports, required under the MSA or this Supplement. For all Reports listed below, where possible, and for other Reports, where applicable, Supplier will provide reporting data (i.e., extracts) with such Reports.
|
| | | | | |
| Report | Category | Network Accessible at CoreLogic | Due Date | Frequency | Description |
1. DEMAND MANAGEMENT | Demand | No | 5th business day following reporting *** | *** | • Report demand and capacity trends and changes, and effectiveness of Demand Management performance. |
2. CAPACITY | Capacity | Yes | Various | *** | • Report current state and deficiencies, variances to thresholds and impacts related to capacity; inputs related to capacity, Services, technology performance, business plans, procedures, processes, components, and related information from CoreLogic. • Should include trending, forecasting, and comparison to historical data • Should include: o Physical and Virtual Servers (includes i/zSeries, zVM, zLinux) – CPU, memory, etc o Storage and SAN utilization and consumption – including VTS and other Tape storage o Network utilization (all device types, including routers, switches, FWs, LBs, etc) o WAN utilization o Backup o Databases o Infrastructure Applications (Exchange, Active Directory, Citrix, DNS, etc) |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 611 |
|
| | | | | |
| Report | Category | Network Accessible at CoreLogic | Due Date | Frequency | Description |
3. SERVER & NETWORK PERFORMANCE | Performance | Yes | Various | ***, *** | • Report performance for Server and network. • The Reports for network will include: o LAN and WAN utilization o WAN / LAN / SAN fabric performance reporting (including network device CPU, memory, connection pool, etc utilization for routers, switches, FWs, LBs, etc) • The Reports for Servers will include the following metrics (includes i/zSeries, zVM, zLinux): o Servers per Network Zone: physical and virtual and cluster o Top and bottom resource consumers o Percent CPU and memory used by Server (host and guest/LPAR if virtual) o CPU Ready, network and SAN I/O statistics by Server (host and guest/LPAR if virtual) o For virtual, guest: host ratios by cluster, and cluster configuration (including high availability and N+x configuration) |
4. AVAILABILITY MANAGEMENT | Availability | No | 5th business day following reporting *** | *** | • Report Availability Management Plans to include Incidents of non-availability, reliability and availability for Systems. • Report on effectiveness and performance of the Availability Management Plan. |
5. SERVICE LEVEL REPORTING | Service Management | Yes | 5th business day following reporting *** | *** | • Report on performance against Critical Service Level review, analyzing trends, reporting in accordance with Schedule A-3. • Report on performance against any requested Key Measures or KPIs for Services provided. |
6. SERVICE IMPROVEMENT | Service Management | Yes | 5th business day following reporting *** | *** | • Report on Service Improvement plans and provide timely status updates. |
7. FIREWALL AUDIT REPORT | Security | Yes | 5th business day following reporting *** | *** | • In connection with maintaining the Firewall audit system, produce a *** Firewall audit Report. |
8. SECURITY BREACHES | Security | Yes | By *** following the reporting *** | *** | • Reports log of actual or suspected unauthorized activity for: Servers, domains, file Systems, databases, etc. |
9. PATCH REPORT | Security | Yes | 5th business day following reporting *** | *** | • Report of change records detailing patching activity and identifies requested patches awaiting CoreLogic approval. |
10. SECURITY CONFIGURATION | Security | No | 5th business day following reporting *** | *** | • Report on evaluation of security configurations within Systems against approved security configurations. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 612 |
|
| | | | | |
| Report | Category | Network Accessible at CoreLogic | Due Date | Frequency | Description |
11. FACILITY AND CONTROLS AUDIT REPORT | Audit | No | Per MSA Section 9.10(h) | *** | • As required by Section 9.10(h) of the MSA. |
12. SECURITY AUDITS | Security | Yes | 10th business day following reporting *** | *** | • Report on results of security audits conducted in accordance with Section 9.10 of the MSA. |
13. REQUEST MANAGEMENT REPORTS | Service Management | Yes | Various | *** | • Track/summarize all incoming requests by assignment and provide Reports that include: o Total completed requests o Total requests added o Total added by assigned to o Total added by assignment group o Total added by originator o Total added by request type o Total added by priority o Total added by status o Total added by contact type o Total added by category o Status of all open service requests (aging reporting – including last update time and age of request) o Detail of requests o Time to complete by type; by assignee group, etc o Assignment group (e.g. Deskside support, remote support) o Requestor’s name o Requestor’s location • Request information for VIP Users should be flagged • Should include self-service type tickets |
14. INCIDENT MANAGEMENT – RESOLUTION *** | Service Management | Yes | 2nd business day of the following reporting *** | *** | • Summary Report for the reporting period displaying the: o Total number of Incidents o Total number of Incidents opened o Total number of Incident Resolved o Incident resolution – elapsed time average and maximum o Range, mean, and median time for Incident resolution by affected item o Assignee/Resolver Group (e.g. Deskside support, remote support, CoreLogic, Third Party Contractor) o Originator’s name o Originator’s location |
15. INCIDENT MANAGEMENT SUMMARY REPORTS | Service Management | Yes | 5th business day of the following *** | *** | • Summary Report of Incident Tickets for the reporting period including the same information defined in the *** Reports. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 613 |
|
| | | | | |
| Report | Category | Network Accessible at CoreLogic | Due Date | Frequency | Description |
16. INCIDENT MANAGEMENT - *** PRIORITY ONE AND TWO INCIDENTS | Service Management | Yes | By *** the reporting *** | *** | • Report of all Severity One and Severity Two Incidents opened the ***. Minimally includes: Incident number, status, assignee group, customer name, location, Incident description, and Resolution summary, date/time occurred, date/time service restored, any ticket suspensions and their durations. |
17. INCIDENT MANAGEMENT - AGING DETAIL | Service Management | Yes | By *** following the reporting *** | *** | • Report reflecting all Incidents opened that have not been resolved within a ***. Includes: Incident id, status, acknowledged, Severity, initial Severity, date/time occurred, assignee, source, Incident category, facility location, Incident age (days), assignee group, average age, manager, any ticket suspensions and their durations. |
18. *** INCIDENT AGING ROLLING REPORT - ALL SEVERITY/PRIORITY INCIDENTS | Service Management | Yes | By *** following the reporting *** | *** | • Graphical Report that shows Incidents assigned and their Severity; Incident counts per status (e.g. open, closed) reflecting the average backlog of Incidents from month to month. Report includes: alignment, assignee group, Severity, current status, last modified, age distribution, average age by distribution, any ticket suspensions and their durations. |
19. REQUEST AGING DETAIL | Service Management | Yes | By *** following the reporting *** | *** | • Report reflecting all requests opened and that are older than a *** period. Report includes: request id, create date, elapsed days, request type, short description, last modified, modified by, average age, any ticket suspensions and their durations. |
20. PROBLEM MANAGEMENT REPORT | Service Management | Yes | 1st business day of the following reporting *** | *** | • Summary Report of Problem Tickets for the reporting period which includes the number, type and status (e.g. open, wip, closed) for all Problem Tickets and list of available Root Cause Analysis Reports. • Reports shall include: o Initiating Incident, Problem description, business impact, root cause (if applicable), cause code, action item(s), workaround, solution proposal, Resolution summary, Resolution code, changes initiated to Resolve Problem, assigned to, age |
21. ROOT CAUSE ANALYSIS REPORT | Service Management | Yes | 1st business day of the following reporting *** | *** | • Results of each Root Cause Analysis (RCA) performed. |
22. CHANGE MANAGEMENT SUMMARY | Service Management | Yes | 2nd business day of the following reporting *** | *** | • Summary list and descriptions of scheduled and completed changes, including initiator, dates, times, priority, change ID, assignee group, short description, change type, risk (from TBD), start date/time, end date/time, total duration, disposition code, classification (includes “failures”). |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 614 |
|
| | | | | |
| Report | Category | Network Accessible at CoreLogic | Due Date | Frequency | Description |
23. CHANGE MANAGEMENT | Service Management | Yes | As required | *** | • Emergency or exception change list including: o Priority of changes o Initiator and approver of changes o Emergency, exception identifier o Change Id, Assignee Group, Short Description, Change type, Risk (from TBD), Start Date/Time, End Date/Time, Total Duration, Disposition Code, Classification
|
24. FORWARD CHANGE SCHEDULE/CAB | Service Management | Yes | 2nd business day of the following reporting *** | *** | • List and description of scheduled changes for the next *** including: o Priority of changes o Initiator and approver of changes o Planned vs. emergency identifier o Change Id, Assignee Group, Short Description, Change type, Risk (from TBD), Start Date/Time, End Date/Time, Total Duration, Disposition Code, Classification • Reports on change approval states of proposed and scheduled changes for the next *** – including changes that were denied approval. • Reports required for CoreLogic CAB specific meetings specific business unit changes. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 615 |
|
| | | | | |
| Report | Category | Network Accessible at CoreLogic | Due Date | Frequency | Description |
25. ASSET REPORTING | Asset Inventory | Yes | 15th business day following each *** | *** | • Report for identified Equipment and Software that includes: o All attributes as applicable, including: device name, serial number, manufacturer, product, version, release, CPU and core counts, memory sizes, etc. o Software licenses and counts by product/vendor, including counts per version with attributes for Software licensing reporting o Systems not covered by maintenance, no longer supportable (end of life), or no longer eligible for maintenance o Equipment and Software not covered by manufacturer support o Supplier decommissioned assets o “Re-purposable” assets o End User Computing Devices (including wireless devices and telephony); Servers & Appliances; Network Devices; Printers o CoreLogic owned assets • Includes known assets identified by the Supplier that are not in the asset database. • For assets disposed by Supplier, information on final disposition (e.g., destroyed, sold, salvaged), the entity performing the disposal and the date of the disposal certification o Certificates of proper disposal security disposals by each asset |
26. CONFIGURATION MANAGEMENT | Service Management | Yes | 5st business day of the following reporting *** | *** | • Summary Report of Configuration Items which includes the number, type and status of the Configuration Items. • Reports shall include: o CI’s, CI description, CI attributes, relationship mapping between CI’s - Software, Applications, hardware, and Systems o Expiring CIs for proactive action o CI activity o CI standard configuration exceptions o Delta between current and approved CIs Data extract of CMS information CoreLogic specific information contained within CMS
|
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 616 |
|
| | | | | |
| Report | Category | Network Accessible at CoreLogic | Due Date | Frequency | Description |
27. CALL MANAGER/ACD | Call Center | Yes | Various | *** | • Report of usage by users and sites from call manager/ACD. • Reports shall include: o Calls offered, calls answered, calls abandoned, call agent levels, total inbound and outbound calls, average handle time |
28. SERVICE DESK | Service Desk | Yes | Various | *** | • Summary Report, aligned to the Service Levels, reporting call statistics, and trends, (FCR, average handle time, etc.). |
29. HP SERVER | Server | Yes | 5th business day of the following reporting *** | *** | • Perform *** HP Server true-up reporting reconciling all HP Servers deployed in the previous *** from the HP capacity-on-demand pool. |
30. STORAGE REQUESTS | Storage | Yes | 5th business day of the following reporting *** | *** | • Summary of pending storage requests from the ITSM System • Summary of storage provisioned by approving BU. • Summary of ITSM change records. |
31. STORAGE | Storage | Yes | 5th business day of the *** reporting *** | *** | • *** true-up reporting reconciling all storage deployed in the previous *** from the capacity-on-demand pool for all managed storage Equipment. |
32. STORAGE REPLICATION | Storage | Yes | 5th business day of the following reporting *** | *** | • Replication reporting, including status of all data that is being replicated and any failures encountered. |
33. DATA CENTER | Data Center | Yes | 5th business day of the following reporting *** | *** | • Maintenance performed on environment elements (i.e., UPS, HVAC, Electrical, etc.) at the Designated Data Centers. |
34. PRODUCTION CONTROL | Production Control | Yes | 5th business day of the following reporting *** | *** | • Reports on production control and scheduling, including (i) batch reports for critical Applications identified in Schedule A-8.2, (ii) failed jobs, and (iii) alarms. • Reporting should be separated between Mainframe and distributed Systems.
|
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 617 |
|
| | | | | |
| Report | Category | Network Accessible at CoreLogic | Due Date | Frequency | Description |
35. BACKUP | Backup | Yes | 2nd business day of the following reporting *** | *** | • Reports on backup activities, including storage used, failed backups, etc. • Overall utilization of the backup infrastructure: o Tapes/Tape drives o Netbackup servers o Network/SAN utilization and I/O |
36. OFFSITE STORAGE | Data Center | Yes | 5th business day of the following reporting *** | *** | • Reports on media shipping, retrieval to and from offsite storage, and inventory. |
37. DATABASE | Data Center | Yes | 5th business day of the following reporting *** | *** | • Reports on inventory, utilization, versions, and environment. |
38. FINANCE | Finance | Yes | 5th business day of the following reporting *** | *** | • Reports on CoreLogic cost center chargebacks and allocations. • Summary of Services Charges and counts. |
39. MONITORING | Monitoring | Yes | 5th business day of the following reporting *** | *** | • Report on monitoring Tool usage and configuration (transactions, points, thresholds, etc). • Summary of all monitoring events received by platform, device, area, category, false-positive, etc. Includes report on all items that are NOT monitored. |
40. CUSTOMER SATISFACTION | Customer Satisfaction | Yes | 5th business day of the following reporting *** | *** | • Reports on survey results of user satisfaction of items relating to request and Service fulfillment. |
41. APPLICATION PERFORMANCE | Performance | Yes | 10th business day following reporting *** | *** | • Report performance for Applications. • Dependent on specific monitors for each Application (end user experience, latency, reachability, response time, etc). |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 618 |
|
| | | | | |
| Report | Category | Network Accessible at CoreLogic | Due Date | Frequency | Description |
42. EDE | Data Transmissions | Yes | 5th business day of the following reporting *** | *** | • Reports summary of transmission activity to/from CoreLogic related EDE Systems. |
43. DATA CENTER | Data Center | Yes | 5th business day of the following reporting *** | *** | • Reports power utilization and Rackspace utilization for CoreLogic related systems while in CoreLogic Data Centers |
44. RESOURCE MANAGEMENT/
ACCESS ADMIN | Resources | No | 2nd business day of the following reporting *** | *** | • Report on resource forecast and trending. • Report on central account provisioning activities relating to CoreLogic user provisioning and de-provisioning. |
45. DISASTER RECOVERY | Disaster Recovery | Yes | 5th business day of the following reporting *** | *** | • ***: o DR Servers by business unit – BU, DR host name, domain platform, VLAN, IP address, purpose, replication method, prod host name o DR Servers by location – BU, DR location, prod location o DR Servers by Application – BU, Application name, DB Servers, App servers, Web servers o Applications by Business Unit – BU, RPO, RTO, last test date, last test results, next test date o Databases in DR – BU, DB name, DB type (SQL, Oracle, etc.), DB Server, Applications using o Databases by Server – BU, DB Server, DB name
• Testing results (*** of test conclusion): o Results by Application – BU, Application name, RPO achieved, RTO achieved, recovery success/fail, remediation required |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 619 |
|
| | | | | |
| Report | Category | Network Accessible at CoreLogic | Due Date | Frequency | Description |
46. PMO | PMO | Yes | 2nd business day of the following reporting *** | *** | • Executive summary and analysis of the Project portfolio. • Performance and status summary for the Project portfolio . • Project Status Report - Individual Projects -The project schedule, cost, budget, milestones, tracking Tool, risk and issues logs, CR log, etc. • Action plans for Governance Report - Newly activated Projects. |
47. PMO | PMO | Yes | 5th business day of the following reporting *** | *** | • Project requests - Input/receipt of Project request forms from approved requesters. • Benefits realization summary - Portfolio - Financial Reports, other measures • Project Resource Utilization Plan. • Root Cause Analysis and improvement - Post Project implementation. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 620 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
And
SUPPLIER MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-13
TRANSFORMATION SERVICES
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 621 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-13
Transformation Services
| |
| 1.1 | Agreement. This Schedule A-13 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 1.4 | Overview. This Schedule sets forth the Transformation Services to be performed by Supplier including services, functions, responsibilities, governance requirements, assumptions and charging methodologies for the transformational activities to be undertaken by Supplier as part of the Services, and the corresponding tasks to be performed by CoreLogic in order for Supplier to perform the Transformation Services. |
| |
| 1.5 | Attachments. Attached and incorporated into this Schedule are the following Schedules related to the Transformation Services: |
| |
| Schedule A-13.1 | Application Scope Components for *** Transformation Services ***Schedule A-13.2 Acceptance Criteria and Milestones for *** Transformation and U2L |
| |
| Schedule A-13.3 | Natural to Cobol Conversion |
| |
| 1.6 | Responsibilities. In the matrices in this Schedule, “P” means “Perform”. The Party identified as “Perform” for an activity is responsible for the successful and appropriate completion of such activity. |
In the matrices in this Schedule, “A” means “Approve”. Approve means that the applicable activity performed by the “Perform” Party will be subject to the approval of the “Approve” Party.
2. TRANSFORMATION SERVICES
| |
| 2.1 | Transformation Services. |
The Transformation Services are comprised of (i) the transformation of the *** System from the legacy Mainframe of *** to the proposed x86 platforms (the “*** Transformation Services”); and (ii) the transformation of certain physical CoreLogic UNIX Servers to physical and virtual Linux Servers (the “U2L Services”), all as more specifically described in this Schedule. The Transformation Services will be conducted as two separate projects managed in accordance with the program and project management processes described in Section 2.2.
Supplier will prepare and deliver to CoreLogic a detailed Transformation Plan in accordance with Section 4.8 of the MSA which will align with the Transformation Milestones within Schedule A-13.2 and Schedule A-4.5. Each version (*** Transformation Services and U2L Transformation Services) will describe in greater detail the specific Transformation Services to be performed by the Parties during the Transformation Period and will incorporate the
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 622 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
additional information gathered during the activities described in this Schedule (e.g., in the project initiation workshops). Unless otherwise agreed by the Parties, each new version of the Transformation Plan shall be consistent in all material respects with this Schedule and the prior version of the Transformation Plan approved by CoreLogic.
Supplier has responsibility for planning and management of the Transformation Services as described in Section 2.2. Each Party shall perform the functions and responsibilities identified as its responsibility in this Schedule and in the Transformation Plans, as such plans are updated from time to time as approved by CoreLogic. CoreLogic will provide access to technical and business personnel and provide Supplier with necessary data and information regarding CoreLogic’s business and Systems as required for Supplier to perform the Transformation Services. CoreLogic will make decisions and obtain required management approvals as required to complete the Transformation Services within the timeframes required by the Transformation Plans.
| |
| 2.1 | Transformation Services Program Management. |
This Section details the obligations and responsibilities of the Parties regarding the general program management activities to be undertaken by Supplier with respect to the Transformation Services. Except where a responsibility is identified as a “P” CoreLogic responsibility in the matrices below, Supplier shall be responsible for the following activities:
|
| | | |
No.
| Description | Supplier | CoreLogic |
| 2.2.1 | Define a single Project Management Office (“PMO”) structure, scope and objectives that will apply to all three (3) transformation projects | P | A |
| 2.2.2 | Implement a PMO to oversee all Transformation Services activities performed | P | |
| 2.2.3 | Manage Transformation Services activities in support of the completion of the projects | P | |
| 2.2.4 | Develop list of project deliverables to be created by the Parties and applicable Acceptance criteria | P | A |
| 2.2.5 | Provide CoreLogic with updates on the progress of deliverables | P | |
| 2.2.6 | Present completed deliverables for review and Acceptance by CoreLogic in accordance with the timeframes set forth in the applicable Transformation Plan | P | |
| 2.2.7 | Review deliverables for Acceptance and sign-off | | P |
| 2.2.8 | Identify and address transformation project issues and communicate and escalate issues to CoreLogic as required | P | |
| 2.2.9 | Manage the project in accordance with the approved project schedules | P | |
| 2.2.10 | Utilize the Change Management Procedures to communicate and address changes to the projects | P | |
| 2.2.11 | Utilize the Change Management Procedures to request changes to the projects | | P |
| 2.2.12 | Manage procurement of Supplier assets to be acquired for the Transformation Services | P | |
| 2.2.13 | Act as a central administrative point for Transformation Plan management, work management, and communications | P | |
| 2.2.14 | Provide *** status and reporting cycle updates to CoreLogic | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 623 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
No.
| Description | Supplier | CoreLogic |
| 2.2.15 | Identify, prioritize, authorize and manage Transformation Services program and project activities | P | |
| 2.2.16 | Facilitate the Transformation Services activities by providing analysis and critical reporting to support governance boards and CoreLogic | P | |
| 2.2.17 | Conduct project resource management, encompassing capacity planning, forecasting, utilization, analysis, and reporting, as well as allocation of resources across the portfolio of transformation projects | P | |
| 2.2.18 | Conduct transformation project portfolio management, including identifying, prioritizing, authorizing, managing, and controlling programs, projects, and other related work to maximize the value and achieve specific strategic business objectives of the portfolio | P | |
| 2.2.19 | As part of the Transformation Plan, develop and manage a quality management plan, including *** performance monitoring, standardized performance metrics and reporting, red/yellow action plan reviews and intervention and remediation activities | P | |
| 2.2.20 | Lead PMO organization (e.g., plan, design, develop, and manage the PMO organization, including project management staff) | P | |
| 2.2.21 | Utilize Supplier’s project management methodologies | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 624 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 2.3 | *** System Transformation |
The *** System Transformation Services provided by Supplier will include (i) converting Natural (batch), COBOL (online/batch) Applications to COBOL, (ii) re-hosting Natural Online to the Application Transparency Platform (ATP), (iii) converting ADABAS file design and data to an ANSI Standard Database, (iv) installing / configuring replacement Infrastructure, monitoring, and security Software, (v) providing Server-side Entire / X replacement services to Natural and COBOL Applications, (vi) providing batch environment that addresses JCL utilities, and (vii) TSO development replacement.
| |
| (a) | Regarding the CICS (non-Natural)/ *** Transaction Processing Environment source components on Linux, the CICS online non-Natural (and related assembler modules) Application components will be moved by Supplier to the Intel x86-based Linux “Target Platform” and will execute within the *** TPE Application execution environment. In performing the migration, the number of *** TPE regions on the Target Platform will be the same number of the CICS regions on the Mainframe (excluding those regions consisting largely of online Natural objects). The presentation Application layer will continue to use the BMS maps to communicate with end user correspondents in the same manner that they do today with CICS. The business logic layer (implemented as COBOL programs) will be retained. COBOL will remain COBOL and Assembler will be converted to COBOL. COBOL ADASQL calls will be converted to EXEC SQL calls and Adabas Direct Calls will be converted by Supplier to *** DAL (Data Access Layer) to interpret the database request, format the request to the ANSI standard, and return the correct results to the originating program. |
| |
| • | *** TPE tables will be configured by Supplier from the CICS System converted information. This information will need to be provided in a specific format (as specified in Supplier asset download instructions) for conversion. |
| |
| • | BMS maps will be re-hosted by Supplier. |
| |
| • | CICS COBOL programs will be adapted by Supplier to run in the *** TPE *** Application execution environment. |
| |
| • | CICS assembler modules called by CICS COBOL will be replaced by Supplier depending upon the function of the module, one of the following approaches will be used unless otherwise agreed. |
| |
| • | The assembler module will be re-implemented by Supplier in COBOL or C as an Application module. |
| |
| • | The assembler module will be replaced by Supplier by configuration options, user exit code or COBOL functions (e.g., date functions). |
| |
| • | The assembler module will be deleted by Supplier if the function was not required or not accessible. An existing higher-level language Application module would need to be changed to adapt to this change in function. |
| |
| • | All direct end user interactive communication with the Applications in the *** TPE will be through TN3270 clients connections. |
| |
| • | The Supplier *** Secure environment will be used for the *** TPE transaction processing user identification, authentication, transaction access control, other transaction processing resource access control, transaction processing audit logs, etc. on the Target Platform. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 625 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (b) | For the CICS (Natural)/ *** ATP source components on Windows, the Natural CICS online Application components (and related replacement assembler to COBOL modules) will be moved by Supplier to the Intel x86-based Windows Target Platform and will execute within the *** ATP Application execution environment. |
The presentation Application layer will create terminal emulation to a Standard Windows interface that can be customized with master style sheets and rules. The business logic layer (implemented as Natural programs) will be retained and Assembler will be converted to COBOL. The data layer will interface to a replacement RDBMS from Adabas.
| |
| - | CICS Natural programs will be adapted by Supplier to run in the *** ATP environment on the Windows “Target Platform.” |
| |
| - | CICS assembler modules called by Natural will be replaced by Supplier. The intent is to re-implement in COBOL although Natural or C programming languages can instead be used subject to the Change Management Procedures. |
| |
| - | All direct end user interactive communication with the Applications in the *** ATP will be through a standard Windows “Window”. |
| |
| - | *** ATP security will be used by Supplier for the online Natural programs. |
The Entire/X Broker communication Mainframe Server-side replacement (including the specified client Software interfaces) will be replaced by Supplier to remove *** Software dependency. Entire/X non-Mainframe Application client-side modifications to incorporate Entire-X replacement is out of Supplier scope and will need to be addressed by CoreLogic
| |
| (c) | With respect to the Batch / *** Batch Processing Environment source components on Linux, Batch Application components will be moved by Supplier to the *** BPE environment in an Intel x86-based Linux “Target Platform.” *** BPE will provide JCL translation, job/proc step processing capabilities, dynamic submission of JCL jobs from Natural / COBOL programs, GDG/concatenated data set support, and monitoring/accounting facilities for a production batch Application execution environment on the Target Platform. |
| |
| - | Batch COBOL programs will be adapted by Supplier to run in the *** BPE vCOBOL environment. |
| |
| - | Batch Natural programs (both submitted from JCL and through Natural via RJE) will be converted by Supplier to (replaced by) COBOL programs that will execute in the *** BPE vCOBOL environment. |
| |
| - | Batch DYL280 programs will be transformed by Supplier to COBOL that will execute in the *** *** environment. |
| |
| - | Batch assembler modules will be replaced by Supplier. JCL for Jobs/Procs will be adapted / translated by Supplier to *** BPE macro scripts. |
| |
| - | JCL will be developed / extended by Supplier on the Target Platform. |
| |
| - | Supplier will migrate all IDCAMS, IEFBR14, IEBGENER, SORT (and similar Mainframe sort utilities like DFSORT, ICEMAN, SYNCSORT), FTP, NDMBATCH, RDBMS, IKJEFTxx utilities invoking RDBMS utilities, MTPBATCH, file back-up, and WTO utilities as well as CoreLogic abend programs (e.g., ILOABN0). Other utilities will be considered within scope if an existing replacement utility is available or if a replacement utility can be written in two |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 626 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
days. Out of scope utilities will be identified as soon as possible so CoreLogic can identify short-term work around options and long-term solutions.
| |
| - | Standard Target Platform operating System (OS) level security will be used by Supplier for batch processing identification and authentication. Standard Target Platform operating System (OS) level security will be used by Supplier to manage access to individual files on disk. CoreLogic will configure security parameters for all operating System instances of the Target Platform. |
| |
| (d) | For the TSO / uni-SPF Extended for *** on Linux migration, the CLIST modules / scripts will be converted by Supplier to REXX to be compatible with uni-REXX or converted to scripts on uni-SFP Extended for *** on the Intel x86-based Linux Target Platform. The specific transformation option for each module is influenced by what capabilities are used in the module. No CoreLogic ISPF panels will be migrated for the Applications. |
| |
| (e) | Sequential / GDG Data Files will be migrated by Supplier to sequential/GDG files on the batch processing Intel x86-based Linux Target Platform. |
| |
| (f) | Regarding VSAM files and Adabas database files / RDBMS on Linux (***)), Adabas database file data needs will be migrated by Supplier to RDBMS tables (***). RDBMS DDL, ADABAS data extract programs, and Adabas data conversion programs will be generated from the ADABAS definitions. VSAM file data will be migrated by Supplier to *** RDBMS database tables. Standard RDBMS security will be used by Supplier for the selected RDBMS. |
| |
| (g) | Regarding other Linux operating environment products, BMC Control-M is the current Mainframe batch scheduler and the expected batch scheduler on the Target Platform will be BMC Control-M (although the master schedule may be on Windows with an agent on the Linux System). $avrs, XPTR, LPserve / VPS (AFP/PSF) products are used for print distribution and archival on the Mainframe. The print distribution facility on the Target Platform will be Levi, Ray and Shoup VPSX and related products, although this selection will be refined by Supplier, as needed, during the operational planning phase. *** will be the sort package. Subversion is expected to be the target source code change control management system. |
| |
| (h) | The Application source components listed by type and counts in Schedule A-13.1 will be in scope for Supplier’s performance of the *** Transformation Services. Analysis, collection or conversion of components that do not reside on the CoreLogic Mainframe or written in languages other than those specifically listed above is out of scope. Any Application under consideration for transformation that is not currently active or is not presently used in production today will be addressed through the Change Control Procedures. Following asset confirmation at the start the project, CoreLogic will continue to update the Mainframe *** System in parallel with the Transformation Services project. Prior to Application source freeze period, CoreLogic Application changes and the Supplier transformation changes will be synchronized in an Application Source Retrofit process. The scope of the Application Source Retrofit will include the following. |
| |
| (1) | CoreLogic will be able to create or change up to *** of the BMS Maps, COBOL modules (e.g., programs, subprograms, copybooks, include files), DYL280 programs, TSO CLIST modules, assembler modules and JCL modules (e.g., jobs, procs, parmlib members, control cards) of those same modules of the baseline defined in the asset confirmation (e.g., the number changed COBOL programs would not exceed *** of the COBOL programs counted for in the asset confirmation) for the Application source retrofit where the total lines of code in each changed module does not change more than ***. |
| |
| (2) | CoreLogic will be able to create up to *** new total sequential, GDG, and / or VSAM files of the baseline defined in the asset confirmation. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 627 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (3) | CoreLogic will be able to update up to *** total of the existing sequential file, GDG file, and / or VSAM files of the baseline defined in the asset confirmation. |
| |
| (4) | CoreLogic will use the same external interfaces in the Application as was used in the baseline defined in the asset confirmation. |
| |
| (5) | Corelogic will use the same batch scheduler functions as was done at the time of receiving the batch schedule. |
| |
| (i) | In connection with the *** Transformation Services *** after the Supplement Effective Date, (i) CoreLogic and ***, shall execute a Binary Code License Agreement and Maintenance and Support Agreement and (ii) CoreLogic and *** shall execute a Software License and Maintenance Agreement). CoreLogic’s warranty, license and other rights with respect to the *** and *** Materials shall be as specified in such agreements and the terms of the Agreement shall not apply to such Materials. |
| |
| (j) | CoreLogic’s shall have the option to require Supplier perform Natural to COBOL Services as described in Schedule A-13.3. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 628 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| (k) | This Section details the obligations and responsibilities of the Parties regarding the *** Transformation Services. Except where a responsibility is identified as a “P” responsibility for CoreLogic in the matrix below, Supplier shall be responsible for the associated activities. |
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.1 | Identify Application source to be migrated. Natural source code for the transformation implementation will be collected only from partitioned datasets and/or ADABAS/Natural data dictionaries. Verify that source code to be converted is able to be compiled in the Mainframe environment error free | | P |
| 2.3.2 | Identify Application data to be migrated | | P |
| 2.3.3 | Develop a comprehensive strategy for in-scope Applications and data sources then-located on the Mainframe | P | A |
| 2.3.4 | Provide reasonable access to Application owners/developers who possesses relevant knowledge of the technical Application details and who will be responsible to participate actively throughout the Transformation Period process as required (i.e., from beginning through end) | | P |
| 2.3.5 | Provide a primary and secondary point of contact in database administration, Application development resources or subject matter experts on Mainframe who are responsible for: • Completing the source code collection • Assisting in the definition of the logical Applications • Resolving missing, duplicate and other special interest components • Locating appropriate CoreLogic Personnel to answer questions from the Supplier team
| | P |
| 2.3.6 | Provide: • information and support from Third Party Contractors of Corelogic Equipment without unreasonable delay • Access to relevant System and Application documentation and records. • Participation in planning and preparation meetings | | P |
| 2.3.7 | Provide the Supplier US and international teams access to the CoreLogic test environment on Target Platform (***) | | P |
| 2.3.8 | Provide Supplier US and international teams with remote access to the existing CoreLogic test Mainframe environment | | P |
| 2.3.9 | Provide Supplier with read-only access to the dictionaries and partitioned datasets that contain the source code and definitions that will be converted | | P |
| 2.3.10 | Provide Supplier with authority to use the in-scope Application and database Tools and any other Tools necessary for Supplier to research issues, locate code version differences, monitor execution or performance, or perform other activities to assist CoreLogic with fast conversion issue resolution | | P |
| 2.3.11 | Provide Supplier with remote access to environments where necessary for Supplier to assist with issue resolution | | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 629 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.12 | Resolve any issues related to Supplier connectivity and/or access to any of the CoreLogic environments • Test the connectivity and access between Supplier and CoreLogic environments • Provide details on any connectivity issues encountered • Resolve any connectivity, authority or training issues that are under its control | P | |
| 2.3.13 | Resolve, where applicable, or assist Supplier in resolving, where applicable, any issues related to Supplier connectivity and/or access to any of the CoreLogic environments • Test the connectivity and access between Supplier and CoreLogic environments • Provide details on any connectivity issues encountered Resolve any connectivity, authority or training issues that are under its control | | P |
| 2.3.14 | Provide student profiles *** (***) *** prior to *** training | | P |
| 2.3.15 | Provide *** (***) *** product training session for administrators and Application development staff (one training session at West Lake for up to *** (***) *** for up to *** in class duration and one training session in an India location for up to *** (***) *** for up to **** in class duration), such training to cover: • *** Transaction Processing Environment, • *** Manager, • *** Secure, and • *** Batch Processing Environment with *** COBOL compiler and runtime | P | |
| 2.3.16 | Attend *** product training (***) | | P |
| 2.3.17 | Provide student profiles *** (***) *** prior to training | | P |
| 2.3.18 | Provide *** on *** ATP (and related conversion framework) and Data Access Layer (that bridges Adabas direct calls to a RDBMS) for up to *** (***) *** for up to *** (***) *** | P | |
| 2.3.19 | Conduct transformation planning including asset cataloging (AC), source planning (SP), operational planning (OP), and project planning (PP) | P | |
| 2.3.20 | AC: Using Supplier-provided instructions, provide the following inputs to Supplier via FTP / SFTP as prerequisites for the Asset cataloging: • Program source code, JCL, copy books, parameter libraries, BMS maps and other relevant source modules being considered for Application re-host transformation to be submitted to Supplier in a mutually acceptable format. | A | P |
| 2.3.21 | AC: Establish and populate a project directory of source component modules by type of source component at the Supplier Facilities. | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 630 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.22 | AC: Create project change request, to be addressed through the Change Control Procedures, if source programs that are not COBOL, DYL280, CLIST or assembler are encountered and the Application component counts received exceed the Application component counts in Schedule A-13.1. | | P |
| 2.3.23 | AC: Perform an analysis of the Application source components. The analysis addresses source code classification, quantification, inventory issues, and interface usage | P | |
| 2.3.24 | AC: Examine Application program (e.g., COBOL) source and JCL to determine missing and unused source components | P | |
| 2.3.25 | AC: Produce an initial list (Initial Missing List Report) of detected missing Application source inventory components (e.g., missing programs, copybooks, include files, JCL Procs, parmlibs) for CoreLogic | P | |
| 2.3.26 | AC: Review Initial Missing List Report | | P |
| 2.3.27 | AC: Submit changes to the source code inventory by adding to, replacing, or deleting members of the current inventory (within five (5) business days of receiving Initial Missing List Report) in one delivery to Supplier to address the items determined to be missing or unused from the Initial Missing List Report prior to any final Asset cataloging iteration and provide a single list of changes to the source code inventory | | P |
| 2.3.28 | AC: Receive and integrate CoreLogic-provided changes to the source code inventory | P | |
| 2.3.29 | AC: Conduct a final analysis on the findings from the analysis of Application source components to provide an Asset cataloging Report | P | |
| 2.3.30 | SP: Using the source code inventory received from the AC phase, prepare to perform source planning | P | |
| 2.3.31 | SP: Examine BMS maps, COBOL source modules (programs, copybooks, include files), JCL (jobs, procs, utilities, parmlibs), and CICS configuration tables for non-Natural CICS regions. Identify areas requiring custom adaptation including, but not limited to syntax differences, collating sequence related differences, features used that are not in underlying supported products, etc. | P | A |
| 2.3.32 | SP: Examine source modules that require transformation prior to or as a part of re-hosting to the Target Platform. These source modules (e.g., assembler, TSO CLIST, DYL280) will need to be transformed, re-engineered, replaced, or deleted | P | |
| 2.3.33 | SP: Document the analysis results in a Source Assessment Transformation Approach Report • Identify issues that will need further investigation before and as part of the transformation • Present an analysis outlining the discovered transformation issues that require special attention and/or custom conversion | P | |
| 2.3.34 | SP: Document the refined/ updated transformation approach in the Source Assessment Transformation Approach Report. Refine project and technical scope assumptions and transformation approach for specific Application source and Application data transformation | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 631 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.35 | OP: Review the Software mapping information for the following o Application Development Environment (Text Editing, compiling, testing / debugging, change / version control) o Sort utility requirements o Batch Scheduler o Print Distribution Facility o Security: Transaction Processing Security (Identification, Authentication, Authorization, Audit, Programmatic interface requirements) o Security: System security (Identification, Authentication, Authorization, Audit, Programmatic interface requirements, Directory Services) o CICS connectivity (sockets, ECI/EPI, TN3270, CICS Web API) o Entire / X Broker “Server-side” replacement o File transfer facilities o Database capabilities o System / Storage / Network Management (including monitoring, alerts, automated responses, hierarchical storage management, tape management) o Data Back-up / Availability (mirror) • The following areas will not be addressed in the Operational Assessment Software Mapping sub-activity: o System platform availability – Hot Back-up Availability o System platform availability – Disaster Recovery Synchronization o Security: Any Message Privacy / Integrity considerations (Message Encryption) o Web Server / Application Server o SNA Communications (SNA terminal / SNA printer or emulator (SNA LU2/3), SNA LU0, peer to peer (SNA LU6.2)) o SNA Communications (RJE / NJE) o SOA / Web Service Communications o MQSeries integration o Data Reporting / Data Editing Tools o Email o Software product interfaces (Input / Output Impact) o Operational requirements specifically related exclusively to Application(s) not being rehosted by Supplier as part of a larger Application rehost transformation. | P | |
| 2.3.36 | Perform o System platform availability – Hot Back-up Availability o System platform availability – Disaster Recovery Synchronization
| P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 632 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.37 | OP: Review the following operational data transformation requirements o Batch schedule transformation o ACF2 CICS security configuration to *** Secure transformation o Source code control transformation • The following topics are not included in the Operational Assessment Operational Data Transformation sub-activity o System and RDBMS security configuration mapping to the underlying Target Platform o Archive Tape Migration | P | |
| 2.3.38 | OP: Review the Software mapping information and discuss operational data transformation in an onsite operational planning workshop for up to a four (4) day period | P | |
| 2.3.39 | OP: Review the Software mapping information and discuss operational data transformation in an onsite operational planning workshop for up to a four (4) day period | | P |
| 2.3.40 | OP: Provide completed Supplier Infrastructure questionnaire and Supplier Software solution mapping document | | P |
| 2.3.41 | OP: Provide list of all Mainframe Software products in use that support the Application being re-hosted | | P |
| 2.3.42 | OP: Provide list of CoreLogic Software standards, recommended practices, or Software usage on open System platforms | | P |
| 2.3.43 | OP: Identify external interfaces and make necessary changes to the interfaces | | P |
| 2.3.44 | OP: Review the Mainframe batch schedule characteristics to assess transformation options for moving the batch schedule from Mainframe BMC Control-M to Target Platform BMC Control-M | P | |
| 2.3.45 | OP: Review the Mainframe security characteristics to assess transformation options for moving selected Mainframe CICS-related security configuration parameters from ACF2 to Supplier *** Secure repository | P | |
| 2.3.46 | OP: Review the Mainframe change control System characteristics to assess transformation options for setting up the source code parameters from Mainframe CA-Endevour to Subversion | P | |
| 2.3.47 | SP: Complete an operational assessment Report consisting of a one-to-one mapping of operational requirements to the appropriate distributed System target | | P |
| 2.3.48 | OP: Define the findings in the operational assessment Report consisting of a one-to-one mapping of operational Software requirements (including some alternative products for consideration) to the appropriate distributed System target. This will include appropriate configuration information
| P | |
| 2.3.49 | Inform CoreLogic that the collating sequence for ASCII differs from that of EBCDIC | P | A |
| 2.3.50 | Provide an environment on which the Mainframe Applications and storage will migrate | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 633 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.51 | Install re-hosting Software as necessary for Application transition | P | |
| 2.3.52 | Provide to Supplier Personnel valid user-ids and log-on permissions with sufficient authority to perform installations services, batch schedule transformation, *** Secure security configuration, source code control source transformation, compiles, or access to a person with sufficient System access and authority to participate in Supplier installation services of Supplier Software products and licenses on Target Platform | | P |
| 2.3.53 | License the *** Software to include *** TPE, *** BPE, *** Secure, appropriate C compiler (e.g., Linux GCC 4.1.2 C Compiler), *** COBOL compiler and runtime, *** , *** and other requisite Software products | | P |
| 2.3.54 | Order, receive, and provide third party vendor Software products (or authorized internet access to the Software products) to be installed | | P |
| 2.3.55 | Provide third party vendor Software product installation instructions and Software product license keys | | P |
| 2.3.56 | Install the following vendor Software products on *** (***) *** System instance on the Target Platform • *** ATP • Linux GCC 4.1.2 C Compiler • Subversion for source control management System • *** for external sort • *** Batch Processing Environment for batch processing environment (Supplier) • *** Transformation Toolkit (Supplier) • *** Secure • *** Transaction Processing Environment for transaction processing environment and VSAM file services (Supplier) • uni-REXX (The Workstation Group) • uni-SPF Extended for *** for text editing (Supplier) • *** Development System and *** Runtime Environment | P | |
| 2.3.57 | Conduct a walk-through of the *** ATP Software installation process and the target architecture and provide guidance on the target folder configuration and run time structures on the Windows platform, and provide guidance regarding any compilation settings | P | |
| 2.3.58 | Provide third party vendor Software product selection, acquisition, installation, configuration, implementation, integration, and testing of any product that is necessary for Supplier to complete the Transformation Services but is not identified as Supplier responsibility in this Schedule including, but not limited to, other programming language compilers / runtimes, print output management / print distribution facility, text editor, source change / version control package, System / storage management facilities, file transfer packages, relational database management System (RDBMS) Software, etc.
| | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 634 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.59 | Provide • Additional Software product installation on additional operating System instances. • Any tape specific processing. • Back-up procedures and related utilities.
| P | A |
| 2.3.60 | Provide • Finalized *** Secure security configuration such as password changes following transformation. • *** Secure configuration for other operating System instances not required to be addressed by Supplier (if required)
| | P |
| 2.3.61 | Complete Application source transformation (including migrate the COBOL, Assembler ALC, Natural and ADABAS components using *** ATP technology) | P | |
| 2.3.62 | Review any updates to project pricing and duration in the Source Assessment Transformation Approach report | | P |
| 2.3.63 | Set up a remote transformation environment with Application component inventory in a Supplier defined directory structure. This transformation environment will use Application source components as provided by CoreLogic during the Source Assessment (which is completed prior to this service activity) | P | |
| 2.3.64 | Provide knowledgeable personnel to provide information during the Application re-host transformation. The following areas of expertise are required: • User Application knowledge • Application development knowledge of the specific Application logic and data layout characteristics | | P |
| 2.3.65 | Assist CoreLogic with reconciling the Application component inventory to be migrated by identifying missing and apparently unused components in each CoreLogic-submitted source update prior to the Asset confirmation Report. Supplier will issue an Asset confirmation Report following either reaching the desired thresholds (***% ***) or maximum number of iterations (***) (whichever happens first) to confirm the Application components to be migrated | P | |
| 2.3.66 | Identify / reconcile the Application source components to be included in the project in at most *** (***) iterations (Asset confirmation). The new/updated source components are to be supplied in one (1) delivery to Supplier for each iteration (i.e., not a series of multiple deliveries for each iteration). This step must be completed within *** (***) *** of the start of this Application source and data transformation service activity. | | P |
| 2.3.67 | Convert CICS table configuration to generate initial *** TPE table production region configuration | P | |
| 2.3.68 | Adapt BMS (basic mapping set) maps to address differences between the source and target environment so that maps will assemble without “fatal” error on the Target Platform | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 635 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.69 | Adapt COBOL programs to: • Change ADASQL calls to embedded EXEC SQL, Adabas Direct Calls to *** DAL (Data Access Layer) to interpret the database request, format the request to the ANSI standard, VSAM calls to access a RDBMS, and return the correct results to the originating program • Address differences between the source and target environment so that programs will compile without “fatal” error in the Target Platform | P | |
| 2.3.70 | Convert batch Natural programs to COBOL that use EXEC SQL. Adapt generated-COBOL programs to address differences between the source and target environment so that programs will compile without “fatal” error in the Target Platform | P | |
| 2.3.71 | Adapt online Natural objects to be migrated to the *** ATP environment on Windows. • Define Application master style sheets and standard rules with CoreLogic • Compile the converted online Application code in the Supplier Windows environment | P | |
| 2.3.72 | Participate in an Application walkthrough with CoreLogic on each Application to be converted with the intent to document the screen flow, screen specific features for online Natural objects being moved to *** ATP on Windows. | P | |
| 2.3.73 | Define Application master style sheets and standard rules with Supplier for online Natural objects being moved to *** ATP on Windows | | P |
| 2.3.74 | Transform batch DYL280 Application programs to batch COBOL programs that will compile without material error when compiled for the without “fatal” error in the Target Platform | P | |
| 2.3.75 | Convert Assembler programs to COBOL for the target environment so that programs will compile without “fatal” error in the Target Platform | P | |
| 2.3.76 | Adapt Jobs and Procs • Create an initial file map from the JCL • Convert sort parameters to operate with *** on the Target Platform • Adapt utilities in JCL that have different parameters or syntax on Target Platform • Replace utilities in JCL that are not available on Target Platform as depicted within the scope of the assumptions • Adapt JCL and translate Jobs and Procs to *** Batch Processing Environment macro scripts | P | |
| 2.3.77 | Provide a list of preferred utility replacement options to Supplier to determine acceptable replacement steps in the JCL where the operational utilities differ substantially in functionality between the Mainframe and the Target Platform | | P |
| 2.3.78 | Transform TSO CLIST modules to REXX (operating under uni-REXX) or scripts for the Target Platform | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 636 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.79 | Provide more detailed *** TPE and *** BPE configuration to integrate with *** Runtime Environment, *** sort product, BMC Control-M batch scheduler, Oracle RDBMS, an LP-based interface print distribution facility, Linux, and JCL utilities integration | P | |
| 2.3.80 | Provide file data layout information, rules for interpreting any redefined fields or record types, and test data for data conversion tasks for VSAM files, sequential files, and / or GDG files whose data needs to be migrated (e.g.,master/ input / historical files, but not intermediate results files or non-historical output files). Supplier will provide instructions for providing this information in a format that can be readily processed by Supplier Tools | | P |
| 2.3.81 | Establish data conversion procedures for VSAM files for those files whose data needs to be migrated to Target RDBMS on the Target Platform: • Generate data conversion programs from CoreLogic-provided file data record layout definitions for *** • Generate scripts to sort and load converted data in to Target RDBMS • Data will be converted / transformed in to a format that can be loaded in to the RDBMS. During the load process, multi-record type files will be split across multiple database tables • Test data conversion programs and conversion scripts with a small amount of data (less than *** per file, *** for all files) that includes a separate file for each unique file data record layout
| P | |
| 2.3.82 | Establish data conversion procedures for sequential/GDG files for those files whose data needs to be migrated to Target Platform: • Generate data conversion programs from CoreLogic-provided file data record layout definitions • Customize conversion scripts for specific file types • Test data conversion programs and conversion scripts with a small amount (less than *** per file, *** for all files) of data that includes a separate file for each unique file data record layout | P | |
| 2.3.83 | For Adabas to ANSI standard RDBMS database parameter and preference setup for each SOURCE database file that is scheduled for conversion: • Provide a file definition worksheet for each SOURCE database file definition • Provide reports regarding occurs clauses, redefines clauses, group levels and potential date fields • Provide guidance in correctly and completely filling out the database definition workbook • Apply all preferences, standards and parameters as rules • Verify and manage the rules throughout the conversion lifecycle | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 637 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.84 | For Adabas to ANSI standard RDBMS database parameter and preference setup: • Respond to Supplier questions regarding the conversion • Provide additional information as required to allow the full definition of the target databases | | P |
| 2.3.85 | For ADABAS test data creation: • Create test environments for use in testing the new Applications and the new ANSI standard databases • Define processes that will allow the for testing and refreshing the unrestricted data in the target ANSI standard database environment and existing Mainframe test environment | P | |
| 2.3.86 | For ADABAS test data creation: • Locate or create a full set of SOURCE data that contains no sensitive data and can be used in its entirety in testing by Supplier and CoreLogic • Ensure that the created data is suitable to allow the Applications to execute completely • Test the execution of the CoreLogic Applications against the new set of unrestricted data • Execute the deliver SOURCE extract processes against the unrestricted data in the Mainframe SOURCE • Resolve any data cleansing issues in the unrestricted data so that no cleansing rule changes are applied to the unrestricted data during the extract process UAT test | | P |
| 2.3.87 | For ADABAS test data creation: • Define processes that will allow Supplier to test and refresh the data in SOURCE and in a target ANSI standard environment • Create test scripts, test cases, and use cases for each process using the data
| P | |
| 2.3.88 | For ADABAS unrestricted test data creation in UAT: • Create working test scripts, test cases, and use cases for the execution of the Applications using the unrestricted test data • Create test environments for use in testing the new Applications and the new ANSI standard databases • Define processes that will allow the for testing and refreshing the unrestricted data in the target ANSI standard database environment and existing Mainframe test environment | | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 638 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.89 | For Adabas SOURCE database file definitions that are scheduled for conversion: • Import the SOURCE file definition report(s) for the file definition(s) as collected • Generate the first-pass SQL Imager reports for the file definition(s) • Review the reports for the file definition(s) • Review log messages for any errors during the import and initial parse phases • Load the table and column naming rules defined by CoreLogic in the Conversion Workbook • Load the date rules for each SOURCE date element as defined by CoreLogic • Load the CoreLogic adjustment rules for any redefines, occurs clauses and group levels • Present questions regarding the first-pass conversion • Conduct a walkthrough of the deliverables and the processing instructions • Implement the first-pass ANSI standard database DDL for the databases at Supplier • Review and test the resulting database structures using the ANSI standard database Tools and other Tools as desired • Deliver the resulting DDL for the new databases to the CoreLogic teams • Respond to CoreLogic questions regarding the DDL • Conduct a post-conversion walkthrough of the resulting databases • Apply table, column and other naming changes based upon CoreLogic team input • Apply data cleansing rules as submitted by CoreLogic team • Re-generate the ANSI Standard Database DDL or SOURCE extracts as required • Enable referential integrity on the target databases as required • Respond to CoreLogic questions regarding the first-pass conversion
| P | |
| 2.3.90 | For First-Pass ANSI Standard Database DDL delivery and installation: • Respond to Supplier questions regarding the first-pass conversion • Provide additional information as required to allow the full definition of the target databases
| | P |
| 2.3.91 | For First-Pass ANSI Standard Database DDL delivery and installation: • Receive and implement the first-pass ANSI Standard Database DDL for the databases at the CoreLogic site • Review and test the resulting database structures using the ANSI Standard Database Tools and other Tools as | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 639 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| | For First-Pass Data Extract and Population: • Generate the data extract JCL and modules for the file definitions that are being converted • Deliver the date extract JCL and modules and instructions to CoreLogic for execution in the CoreLogic SOURCE environment. • Receive and review the extracted data files • Populate the new ANSI Standard databases at Supplier with the unrestricted data provided by CoreLogic • Review and touch test the resulting ANSI Sstandard database structure using ANSI standard Tools • Log and document any issues with the received data • Present the CoreLogic with details regarding any data issues encountered • Make any adjustments in order to make the initial database data useable for the initial pass • Backup the populated ANSI standard databases • Deliver the backups to CoreLogic for installation in the CoreLogic test environment | P | |
| 2.3.92 | For First-Pass Data Extract and Population: • Receive and install the data extract JCL and modules on the CoreLogic Mainframe • Compile and execute the data extract JCL and modules against the predefined SOURCE unrestricted databases for each SOURCE file definition according to the instructions provided • Ensure that all jobs and steps are executed in the correct sequence and with successful return codes • Provide Supplier with all extracted data and completed job output in text format as extracted using the Supplier supplied data extract JCL and modules without any manual change pre-extract or post-extract
| | P |
| 2.3.93 | For First-Pass Data Extract and Population: • Restore the backups into the CoreLogic environment Review and touch test the resulting ANSI standard database structure using ANSI standard Tools or other Tools • Backup the populated ANSI standard databases • Define and manage procedures for controlling instances of ANSI standard data for testing. | P | |
| 2.3.94 | Implement a one-time retrofit process (Application source retrofit) to synchronize Mainframe CoreLogic Application extensions and Supplier Application transformation changes during the transformation implementation phase of the project. CoreLogic Application extensions will include new modules and updated modules within the scope defined in Section 2.3 (g).
| P | |
| 2.3.95 | At the time of Application source production freeze, provide the Mainframe Application source in scope for input to the Application source retrofit process within scope as defined in Section 2.3 (g). | | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 640 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.96 | Create file data record layouts for all new VSAM files, sequential files, and GDG files for the Application source retrofit for scope defined in Section 2.3 (g). | | P |
| 2.3.97 | Provide any updated file data record layouts for changes to VSAM, sequential, and GDG file formats from the previous baseline definitions for VSAM files, sequential files, and GDG files within scope as defined in Section 2.3 (g). | | P |
| 2.3.98 | For each SOURCE file definition that is scheduled for conversion, the following activities will take place during the collection and definition process: • Provide a file definition worksheet for each SOURCE file definition • Provide reports regarding occurs clauses, redefines clauses, group levels and potential date fields • Provide guidance in completing the database definition workbook • Apply all preferences, standards and parameters as rules • Verify and manage the rules throughout the conversion lifecycle | P | |
| 2.3.99 | For each SOURCE file definition scheduled for conversion: • Respond to questions regarding the conversion • Provide additional information as required to allow the full definition of the target databases | | P |
| 2.3.100 | Provide transformation planning services including, but not limited to, Application source module categorization and quantification, source planning, and operational requirements planning | P | |
| 2.3.101 | Complete usability and UI design of converted components | | P |
| 2.3.102 | Customize Natural Windows style sheets | P | |
| 2.3.103 | Complete the Application and data conversion to the Target Platform | P | A |
| 2.3.104 | Prior to delivering re-hosted source components for testing, Supplier will have completed the following • Installed, configured the following with regards to the migrated environment o Open System hardware and operating System environment o third party vendor Software products (e.g., batch scheduler, C, print distributed facility, Syncsort DMExpress, etc.) • Prepare a set of test plans to be used for the various testing stages • Plan staffing for testing and production cutover. Set up development and testing environments | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 641 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.105 | Prior to receiving re-hosted source components for testing, CoreLogic will have completed the following: • Selected, acquired and provide to Supplier, the following with regards to the migrated environment o third party vendor Software products (e.g., batch scheduler, C, print distributed facility, Syncsort DMExpress, etc.) • Prepare a set of UAT test plans to be used for Application acceptance • Plan staffing for UAT testing and production cutover • Attend training sessions on the open System environment products | | P |
| 2.3.106 | Provide valid remote user-ids and log-on permissions with sufficient authority to perform Application source drops, data conversion Tool drops, compilations, Application discrepancy support. | P | A |
| 2.3.107 | Provide drop(s) of the migrated Application source and the generated data conversion programs to one (1) unique operating System instance each for Linux (for non-Natural components) and Windows (for Natural components) | P | |
| 2.3.108 | Provide test data for data conversion tasks. Test data will be limited in size for the initial test data. For final testing there will not be any limitation on size of database | | P |
| 2.3.109 | Unload Mainframe VSAM files. Transfer sequential files with VSAM file data, sequential file data, and GDG file data to Target Platform for so that the data can be converted | P | |
| 2.3.110 | Assist Supplier in unloading Mainframe VSAM files, transferring sequential files with VSAM file data, sequential file data, and GDG file data to Target Platform so that the data can be converted | | P |
| 2.3.111 | The testing team and production cutover team use the Supplier-provided data conversion procedures (programs and scripts) to convert data from unloaded VSAM files, sequential files, and GDG files (for those files whose data needs to be migrated to target platform) for Application testing and prior to production cutover | P | |
| 2.3.112 | Review the data conversion report which covers the testing procedure results. (Some errors / warnings are the result of acceptable conditions (e.g., low values in some uninitialized alphanumeric fields) while other errors / warnings may identify bad data in the original records) | P | |
| 2.3.113 | Correct or re-create bad or missing data in the data conversion report provided by Supplier | | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 642 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.114 | During conversion: • Import the SOURCE file definition report(s) for the file definition(s) as collected • Generate the first-pass SQL Imager reports for the file definition(s) • Review the reports for the file definition(s) • Review log messages for any errors during the import and initial parse phases • Load the table and column naming rules defined by CoreLogic in the conversion workbook • Load the date rules for each SOURCE date element as defined by CoreLogic • Load the CoreLogic adjustment rules for any redefines, occurs clauses and group levels • Present questions regarding the first-pass conversion • Conduct a walkthrough of the deliverables and the processing instructions • Implement the first-pass ANSI standard DDL for the databases • Review and test the resulting database structures using the ANSI standard Tools and other Tools as desired • Deliver the resulting DDL for the new databases to the CoreLogic teams • Respond to CoreLogic questions regarding the DDL • Conduct a post-conversion walkthrough of the resulting databases • Apply table, column and other naming changes based upon team input • Apply data cleansing rules as submitted by CoreLogic team • Re-generate the ANSI standard DDL or SOURCE extracts as required | P | |
| 2.3.115 | For the SOURCE file definitions that are scheduled for conversion, the following activities will take place during the First-Pass Data Extract and Population. • Generate the data extract JCL and modules for the file definitions that are being converted • Deliver the date extract JCL and modules and instructions for execution in the CoreLogic SOURCE environment. • Receive and review the extracted data files • Populate the new ANSI standard databases with the unrestricted data provided by CoreLogic • Review and touch test the resulting ANSI standard database structure using ANSI standard Tools • Log and document any issues with the received data • Present CoreLogic with details regarding any data issues encountered • Make any adjustments in order to make the initial database data useable for the initial pass • Backup the populated ANSI standard databases • Deliver the backups to CoreLogic for installation in the CoreLogic test environment | P | |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 643 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.116 | Correct material Application discrepancies discovered by testers and analyzed by CoreLogic during testing for the current Mainframe environment, and the Target Platform. For cases where result discrepancies arise from where results on the Mainframe are different from results on the Target Platform for the same programs and data, the tester and CoreLogic will isolate the discrepancy cause and Supplier will address the discrepancy. Once corrected, the test will need to be re-run until the results match the corresponding run on the Mainframe or the discrepancy is resolved to the mutual satisfaction of CoreLogic and Supplier. • For wrong results, Supplier will adapt the Application components to correct the discrepancy. CoreLogic will assign a person to assist in isolating the cause of the discrepancy. • For different, but not wrong, functional results (e.g., sorted data in a different collating sequence), Supplier will work with CoreLogic to determine whether this difference requires any further adaptation or not. • All CoreLogic source assets (code, data definition language, BMS map, JCL, etc.) directly or indirectly related to a discrepancy must be available to our team. If a problem in any CoreLogic program (or job) is reported, if CoreLogic has not provided to Supplier the available CoreLogic source to all modules called by that program (or job) after Supplier request for source, Supplier will immediately turn that entire program over to CoreLogic and Supplier has no further responsibility to correct, debug, or test (as applicable). • Supplier will provide Application discrepancy correction support of Application transformation testing across multiple operating System instances where § Supplier is provided remote access to the operating System instance and related test environment and § The operating System instances are of the same operating System and the same vendor Software product versions • Supplier will Resolve Application discrepancies for in-scope testing tasks, through the earlier of: o *** (***) *** following the initial migrated source delivery or o Production cutover | P | |
| 2.3.117 | Application subject matter experts shall be available to assist in isolating Application discrepancy areas or causes | | P |
| 2.3.118 | Log discrepancies in a defect / bug tracking system that is accepted by both CoreLogic and Supplier. Discrepancy descriptions and supporting information need to provide sufficient details for analysis or reproduction of the situation | P | |
| 2.3.119 | During UAT, log discrepancies in a defect / bug tracking system that is accepted by both CoreLogic and Supplier. Discrepancy descriptions and supporting information need to provide sufficient details for analysis or reproduction of the situation | | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 644 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.120 | Prior to submitting discrepancy reports: • Confirm that test set-up and input data is correct • Identify the first job step or screen image from which the results begin to differ in the particular test case | P | |
| 2.3.121 | During UAT and prior to submitting discrepancy reports: • Confirm that test set-up and input data is correct • Identify the first job step or screen image from which the results begin to differ in the particular test case | | P |
| 2.3.122 | Implement job scheduler transformation, ACF / 2 security profile transformation to Supplier *** Secure, and source code transformation to selected distributed source code management solution | P | |
| 2.3.123 | Provide unloaded Mainframe electronic copy of the batch schedule to be migrated in a Supplier-specified format | | P |
| 2.3.124 | After the assessment, provide the required format for CoreLogic batch schedule | P | |
| 2.3.125 | Transform schedule so that migrated schedule uses features provided in the Control-M on Target Platform, conforms to an input format required by Control-M on Target Platform load utility or command line interface (in script format), and provides the required information that supports integration with the *** batch processing environment | P | |
| 2.3.126 | Use the Control-M load utility or command line interface (in script format) to load the transformed schedule into the Control-M repository for *** (***) *** – *** before the retrofit process and *** the retrofit process. Additional features not required for the transformation are out of Supplier scope | P | |
| 2.3.127 | Integrate batch scheduler with *** batch processing environment | P | |
| 2.3.128 | Perform Mainframe Control-M batch schedule transformation for any schedule beyond that which was initially provided to Supplier for transformation. | | P |
| 2.3.129 | Perform Target Platform Control-M schedule upload for any schedule which was initially provided to Supplier for transformation | | P |
| 2.3.130 | Load the migrated schedule in to Control-M for all operating System instances except *** (***) operating System *** (if required) | | P |
| 2.3.131 | Manage the synchronization of the Mainframe Control-M batch schedule and the Target Platform-based Control-M batch schedule after the batch schedule transformation following the retrofit. Activate the relevant parts of the Target Platform Control-M schedule and deactivate the relevant parts of the Mainframe Control-M schedule when necessary (e.g., production cutover) | | P |
| 2.3.132 | Provide a Mainframe ACF2 dump file whose data will be adapted to be compatible for import in to *** Secure repository for the initial project start and as part of the final retrofit process | | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 645 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.133 | Provide criteria for Application-specific security configuration filtering for online CICS related security configuration and will generate an ACF2 dump file (as specified by Supplier) that can be processed electronically | | P |
| 2.3.134 | Transform the filtered CoreLogic security information to map to *** Secure features and to conform to an input format required by *** Secure load command. | P | |
| 2.3.135 | Identify / configure parameters to implement global security policies (e.g., password expiration, min/max password length) and any additional user id-specific policy options to the transformed security information | P | A |
| 2.3.136 | Use the *** Secure load command to load the transformed security information into the *** Secure repository for up to one time - following the retrofit process in the production operating System instance | P | |
| 2.3.137 | Use the *** Secure load command to load the transformed security information into the *** Secure repository for all other operating System instances (if required) | | P |
| 2.3.138 | Perform any additional administrative / configuration required in the environment following the initial load (e.g., changing passwords) | | P |
| 2.3.139 | Execute *** Secure load command to populate security configuration input being loaded in to the *** Secure repository for all operating System instances except one (1) production operating System instance | | P |
| 2.3.140 | Manage any required synchronization of ACF2 and *** Secure security definitions after the security definition transformation | | P |
| 2.3.141 | Perform simple *** TPE / *** BPE print output integration with the print distribution Software. This integration will consider print output insertion into the print distribution Software | P | |
| 2.3.142 | Customize and integrate uni-SPF Extended for *** panels with the change control System to be able to: • Check out an existing Application branch or source component from the agreed upon source code change management facility • Check in an Application source component from the agreed upon source code change management facility. o New Application source component – An error notification will be received by the user if the agreed upon source code change management facility does not accept the new Application source component. o Updated Application source component – An error notification will be received by the user if the agreed upon source code change management facility does not accept the updated Application source component • Request promotion / demotion of Application source component | P | |
| 2.3.143 | Populate the source code change management repository *** (***) *** | P | |
| 2.3.144 | Perform and have full backups of data prior to beginning of each transformation. | | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 646 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.145 | Complete Application data transformation | P | |
| 2.3.146 | Conduct testing (, baseline test preparation, regression testing and stress testing, and testing program management). Supplier to assist CoreLogic in acceptance testing specific to resolving testing issues. | P | |
| 2.3.147 | Conduct end to end User Acceptance Testing; provide existing functional, performance and regression test scripts | | P |
| 2.3.148 | Sign off on test results within three (3) business days | | P |
| 2.3.149 | Provide all existing test scripts to Supplier for consideration in testing the migrated environment. | | P |
| 2.3.150 | Develop test cases (System/Integration/Performance/Security/) | P | |
| 2.3.151 | Perform System integration testing • Local integration testing (covers sub-system testing) • End-to-end integration testing (covers full System, and applicable interfaces) using end-to-end test cases
| P | A |
| 2.3.152 | Perform data transformation testing for ADABAS to SQL/Oracle environments and VSAM, sequential and GDGs file types. • Reports BI, Check DDL • Data Validation • PK Validation • FK Validation • Anomalies Validation • SK Validation • IUD Validation | P | A |
| 2.3.153 | Perform regression testing
• Functional testing of the Applications
• System testing of the Applications
• Regression testing during defect fix or any enhancement or scope change
. | P | A |
| 2.3.154 | Perform performance testing against baseline benchmarks
• Performance test requirement analysis
• Test planning, defining workload scenarios
• Test scripts review and customization
• Test execution, monitoring and analysis
• Report delivery and sign off | P | A |
| 2.3.155 | Perform security testing (i.e. access rights)
• Security testing of Java based web Applications.
• Security standards to be tested: OWASP | P | A |
| 2.3.156 | Complete User Acceptance Test cases preparation and execution | | P |
| 2.3.157 | Provide test data (functional & performance)
• Core Logic to provide test data for all types of test activities.
• Supplier to validate test data provided by CoreLogic | A | P |
| 2.3.158 | Provide test cases sign off | | P |
| 2.3.159 | Provide testing Tool procurement for performance testing | A | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 647 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.160 | Provide SME support for all testing phases as required and agreed to in the Project plan | | P |
| 2.3.161 | Review test scenarios and results and provide sign off. Testing result validation & testing sign off for all phases | | P |
| 2.3.162 | Configure test environment setup for in-scope types and phases of testing | P | A |
| 2.3.163 | Configure a hardware/Software test environment similar to the production environment that is (or will be) implemented for the converted Application at CoreLogic site | P | |
| 2.3.164 | Set up regression and client acceptance test environments | P | |
| 2.3.165 | Provide Supplier with remote access to the target environments where the new Applications and databases will be delivered and tested using the unrestricted data | | P |
| 2.3.166 | Define and manage procedures for controlling instances of the ANSI standard (e.g., Oracle, SQL Server) data (from Adabas database files) used for testing. | P | |
| 2.3.167 | Perform test preparation phases including the transformation of VSAM, sequential, GDG, and Adabas data to their replacement file / database on Target Platform. | P | |
| 2.3.168 | Conduct CoreLogic acceptance testing of the migrated Application on the target environment. Validate the functional capability and performance of the migrated asset prior to moving the Applications into a production environment • Implement staffing for testing to begin the testing and apply testing resources to complete this testing in the scheduled time period • Provide exported VSAM, sequential, GDG file data • Provide exported Adabas database file data • Execute the test plan, perform initial analysis of Application discrepancies and work with Supplier to resolve the discrepancies • End users will participate to validate ability for end user access • CoreLogic or Third Party support Application developers will interact with end users during the testing as part of learning how to support end users on this platform. Supplier support interaction with end users during this Activity will be done jointly with CoreLogic Application development staff and will be specific to problem clarification if CoreLogic Application developers have difficulties in gathering the information themselves
| | P |
| 2.3.169 | Locate or create a full set of SOURCE data that can be used in its entirety in testing by Supplier and CoreLogic
| | P |
| 2.3.170 | Develop production readiness and cutover plan and review plan with CoreLogic | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 648 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | |
| No. | Description | Supplier | CoreLogic |
| 2.3.171 | For the deployment of the online Natural in the *** ATP and the final transformation of Adabas data to production RDBMS: • Work with CoreLogic to define the data and time for the final deployment of the database and online Natural objects to the production environment on Windows • Provide up to two resources for onsite support during the cutover window • Provide additional remote offsite support • Work with CoreLogic to manage the cutover process including the staging of the source code and the final extract and load of the data | P | |
| | For the deployment of the online Natural in the *** ATP and the final transformation of Adabas data to production RDBMS: • Work with Supplier to define the data and time for the final deployment of the database and online Natural objects to the production environment on Windows • Work with Supplier to manage the cutover process including the staging of the source code and the final extract and load of the data • Provide end user training • Communicate with the end-user community throughout the cutover period • Monitor the Applications in the new environment | | P |
| 2.3.172 | Complete Systems architecture document and review in concert with existing distributed CoreLogic Applications. | P | A |
| 2.3.173 | Implement/ develop any Application functionality changes including functional changes to any Application or programs, design changes to the original SOURCE file definitions, the addition or elimination of any SOURCE records and changes to any SOURCE field definition | | P |
| 2.3.174 | Complete Systems architecture document and review in concert with existing distributed CoreLogic Applications. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 649 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 2.4 | UNIX TO LINUX TRANSFORMATION |
This Section details the obligations and responsibilities of the Parties regarding the U2L Services. Supplier will assess the UNIX environment to develop an inventory of the Applications and dependencies in the environment. ***Supplier will develop a detailed plan to migrate ***, *** and *** from Unix to Linux. The target environment from Weblogic could be different for each Application (*** or ***) depending on the Application architecture determined by CoreLogic. ***The third business Application that Supplier will migrate from Unix to Linux is ***. The *** version to be migrated from Unix to Linux will be Oracle 11.5.10 or Oracle Release 12. Supplier will not perform any Application Upgrade or apply any maintenance packs or patches (unless required to complete the migration) and will only migrate Oracle *** from a Unix to Linux platform.
Specifically for Oracle database running on ***, Supplier will migrate *** or higher Oracle DB version databases in production, test, development, QA, or Staging environments running on not more than *** Servers to a Linux based x86 architecture and Oracle 11g database environment. If more *** of the databases are larger than *** TB, the Parties will execute a Change Order under the Change Management Procedures to compensate Supplier for the additional effort required of Supplier. The entire database with all of its objects of any type should be migrated without exception or limitation
Except where a responsibility is identified as a “P” CoreLogic responsibility in the matrices below, Supplier shall be responsible for the following activities:
|
| | | | | |
| No. | Description | Supplier | CoreLogic |
| 2.4.1 | Complete analysis of Application transformation complexity factors for three in scope Java based Applications, *** databases, C, C++ Applications and scripts | P | |
| 2.4.2 | Size Applications Infrastructures, identify physical and virtual targets for target Infrastructure | P | A |
| 2.4.3 | Collaborate with CoreLogic to determine UNIX Baseline load testing methodology | P | |
| 2.4.4 | Collaborate with Supplier to determine UNIX Baseline load testing methodology | | P |
| 2.4.5 | Provide UNIX Baseline load testing Tools | | P |
| 2.4.6 | Collaborate with CoreLogic to perform UNIX Baseline load testing and present findings | P
| |
| 2.4.7 | Collaborate with Supplier to perform UNIX Baseline load testing and present findings | | P |
| 2.4.8 | Provide UNIX Baseline load test windows | A | P |
| 2.4.9 | Conduct transformation planning activities | P
| A |
| 2.4.10 | Coordinate with CoreLogic for project planning | P | |
| 2.4.11 | For the Java based business Applications the *** database Servers, C, C++ Applications and scripts in scope, develop a strategy for each Application and data source currently residing on the UNIX platform identifying a cost effective transformation plan that minimizes impact to the business | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 650 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| 2.4.12 | Develop and present a hardware mapping plan for the transformation based on existing hardware up to a week prior to migration and the hardware capabilities at that time just prior to migration and Application requirements in place up to a week prior to migration | P | A |
| 2.4.13 | If available, provide existing Application and Infrastructure test scripts to be utilized by Supplier | A | P |
| 2.4.14 | If test scripts are not available, Supplier to create them as part of scope | P | A |
| 2.4.15 | Provide System inventories showing IP level communications of UNIX Systems with other Systems | P | |
| 2.4.16 | Map identifiable business Applications across the Server the environment | P | A |
| 2.4.17 | For business Applications as defined in the scope section of Section 2.4, review architecture, source code, databases, documentation, test scripts and other relevant elements of Systems to develop a transformation plan for each business Application. | P | |
| 2.4.18 | Present the plan prepared after review of architecture, source code, databases, documentation, test scripts, shell scripts and other relevant elements of System | P | A |
| 2.4.19 | Identify Application dependencies that will be impacted in the transformation | P | A |
| 2.4.20 | Conduct workshops, surveys and interviews during planning and implementation phases | P | |
| 2.4.21 | Assist Supplier in conducting workshops, surveys and interviews during planning and implementation phases | | P |
| 2.4.22 | Provide environment for load testing (benchmarking, testing and validation)work including agreed upon test windows | A | P |
| 2.4.23 | Determine the approach and plan to migrate the UNIX environment | P
| A |
| 2.4.24 | Install and configure re-hosting hardware and storage environment to which the UNIX Applications and storage will migrate | P | A |
| 2.4.25 | Install and configure re-hosting Software to ensure successful Application transition | P | A |
| 2.4.26 | Provide management and monitoring Tools that will be used in the transformation effort | P | A |
| 2.4.27 | Complete code conversion and data conversion in the test environment | P
| |
| 2.4.28 | Complete code conversion and data conversion in the production environment | P | |
| 2.4.29 | Provide user acceptance testing (UAT) including unit testing, Application testing, data loading testing and end to end System integration testing of the Applications in the new environment | | P |
| 2.4.30 | Assist CoreLogic in conducting customer acceptance testing specific to resolving issues found in the course of UAT | P | |
| 2.4.31 | Correct defects identified through UAT; ( excluding pre-existing defects which can be duplicated in the existing Solaris / Weblogic environment are not in scope) | P | |
| 2.4.32 | Perform Application, System and data processing related load testing on the new environment and present findings compared to the baseline load testing | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 651 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| 2.4.33 | Assist in Application, System and data processing related load testing on the new environment and present findings compared to the baseline load testing | | P |
| 2.4.34 | Validate Applications and complete testing | P | |
| 2.4.35 | Migrate Applications into production environment and refresh production with current data and complete final “go live” testing and cutover | P | A |
| 2.4.36 | Provide continued support until all defects and Incidents identified in the *** are remediated as provided in ***. | P | A |
| 2.4.37 | Review Application Java code to ensure that it has no dependencies on Weblogic, deployment descriptors, security, JNDI, EJB transformation and third-party libraries for conversion to new Java container | P | A |
| 2.4.38 | Collaborate on *** vs. *** and agree on optimal approach | P | P |
| 2.4.39 | Build and deploy environment necessary for the new Java container Application and transformation as identified in planning phase | P | |
| 2.4.40 | Conduct functional testing of the business Application and provide dependent Applications an environment to test other Application dependencies. Application dependencies and roles and responsibilities will be identified during the assessment / planning phase | P | A |
| 2.4.41 | Assist in functional testing of the business Application and provide dependent Applications an environment to test other Application dependencies. Application dependencies and roles and responsibilities will be identified during the assessment / planning phase | | P |
| 2.4.42 | Conduct tests of dependent Applications for Applications being migrated | | P |
| 2.4.43 | Identify potential transformation risks and mitigation activities | P | |
| 2.4.44 | Develop the testing strategy and production rollout strategy | P | A |
| 2.4.45 | Complete entire transformation in accordance with the Transformation Plan | P | |
| 2.4.46 | Conduct detailed interviews or workshops on Oracle Database architecture with CoreLogic personnel to capture operational procedures, key business requirements, and Service Level requirements | P | |
| 2.4.47 | Testing to be done for relevant databases after Oracle database services is available. Validate data objects have been moved | P | A |
| 2.4.48 | Validate that non migrated Applications & databases are communicating properly with the migrated Applications & databases | | P |
| 2.4.49 | Provide Tools to conduct the database transformation | | P |
| 2.4.50 | Provide downtime windows for the production transformation / cutover | | P |
| 2.4.51 | Provide Linux and hardware environment for testing & validation and target environment | P | |
| 2.4.52 | Provide database and Application layer for testing on the target environment | | P |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 652 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| 2.4.53 | Perform performance testing on production target environment and present findings | P | A |
| 2.4.54 | Provide plan and mechanism to freeze and branch code and data for migration. | P | A |
| 2.4.55 | Provide plan and mechanism to merge code and data changes that occur during freeze window to back target System | P | A |
| 2.4.56 | Review existing Oracle database architecture requirements including disaster recovery, storage, availability, and Application dependencies | P | |
| 2.4.57 | Conduct transformation planning sessions to capture and document identified candidate databases for transformation and prioritize transformation order to include following •Oracle database current version and desired version • Identify potential data conversion issues • New Oracle 11 G feature usage will be identified but not implemented as part of the transformation.) • Number of databases and associated schemas that will be analyzed • Timeframe for transformation (transformation windows) • Transformation Tools and techniques • Required patches • Customizations
| P | A |
| 2.4.58 | Configure the Infrastructure as follows: • Validate accessibility to external storage from each node • Configure Operating System parameters for Oracle, as needed • Configure and create partitions needed for each environment • Configure the IP addresses for each node, as needed • Install and configure an Oracle ASM instances, if required • Configure high-availability options, if required • Install the latest supported Oracle database binaries on each database node • Create Oracle seed database instance using DBCA to test functionality • Install and configure default Oracle Listeners using NETCA where relevant • Install OEM agent, and verify registration with the repository • Perform post-deployment patches and fixes for Oracle database binaries, as needed, taking into account any Oracle recommendations | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 653 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| 2.4.59 | Verify transformation plan developed in previous phase for targeted databases to include: • Confirm change control approved • Recommend source database backup process • Preparation steps for transformation to target environment • Tools to be used • Recommended System cutover and roll-back procedures • Review transformation plan with CoreLogic for approval | P | A |
| 2.4.60 | For database scope as referenced in Section 2.4, perform initial transformations and validate initial transformations. Transformation processes will be modified as necessary: • Perform iterative transformations perform second transformation. This transformation will include detailed timings that will be used for final cutover transformation • Validate second transformation and modify transformation process. The transformation process is iterative. Problems uncovered during the second transformation will be documented and fixed for subsequent transformations • Perform third transformation (if needed). This is the “benchmark” transformation that will be used to determine the final timings and used to plan the final transformation • Validate third transformation and modify transformation process. Some minor changes may require retesting if significant modifications are done | P | |
| 2.4.61 | Provide *** access to Application and database environment to CoreLogic staff for Application UAT | P | |
| 2.4.62 | Implement mechanism to bring current data to Supplier environment to maintain currency of data from CoreLogic environment | P | |
| 2.4.63 | Determine any changes needed in advanced queues and Oracle streams, modify processes and migrate | P | |
| 2.4.64 | Receive CoreLogic approval for final transformation and cutover | P | |
| 2.4.65 | Perform final transformations and production cutovers during approved downtime periods | P | A |
| 2.4.66 | Provide scheduled downtime windows for conversions / transformation that will be defined during the planning phase | | P |
| 2.4.67 | For the Unix to Linux scope defined in Section 2.4, perform and have full backups of data prior to beginning of each transformation. | P | A |
| 2.4.68 | Complete Infrastructure, new Java container and database Systems architecture document and review in concert with existing in scope distributed CoreLogic Applications. | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 654 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| 2.4.69 | Knowledge transfer – Unix to Linux includes:
• *** for each of the *** and an *** for the Oracle database. These sessions may include but would not be limited to: • Overview of changes or modifications, a list of modified files, and a Q/A session with CoreLogic SMEs • Application change (C++/Java): This will include a formal handoff of any source code, modified files, and SME Q/A • New OS and container configurations | P | A |
| 2.4.70 | As part of acceptance criteria, all source code migrated during the project including unmodified or newly written shall be checked into and managed in the CoreLogic source control management | P | A |
| 2 | As part of acceptance criteria, all migrated Applications shall be able to compiled, deployed and released with the same level of automation and repeatability as before the migration. CoreLogic existing Tools and processes should be used with only necessary modifications | P | A |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 655 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
2.5 TRANSFORMATION MILESTONES
2.5.1 *** System Transformation
Schedule A-4.5 and Schedule A-13.2 sets forth the Transformation Milestones applicable to Supplier’s performance of the *** Transformation Services, the required completion date and the Acceptance criteria applicable to each milestone. The Deliverable Credits and other credits applicable to the *** Transformation Services are set forth in Schedule A-4.5. If the Transformation Plan is changed by the Parties in accordance with the processes described in this Schedule, the associated completion date shall be appropriately adjusted based upon the change and without the necessity of amending this Schedule.
2.5.2 Unix to Linux Transformation
Schedule A-4.5 and Schedule A-13.2 sets forth the Transformation Milestones applicable to Supplier’s performance of the U2L Services, the required completion date and the Acceptance criteria applicable to each milestone. The Deliverable Credits and other credits applicable to the U2L Services are set forth in Schedule A-4.5. If the Transformation Plan is changed by the Parties in accordance with the processes described in this Schedule, the associated completion date shall be appropriately adjusted based upon the change and without the necessity of amending this Schedule.
2.6 CHANGE MANAGEMENT PROCEDURES
Any Change to this Schedule or the Transformation Services requested by a Party shall only be made in accordance with Schedule 6.1 to the MSA (Change Management Procedures). Any Dispute between the Parties regarding such matters shall be subject to the dispute resolution procedures in Schedule 6.
2.7 TRANSFORMATION CHARGES
CoreLogic shall pay Supplier *** for the *** Transformation and U2L Services in the amount specified in Schedule A-4.5.2. These *** shall be invoiced in the installments on the dates and in the amounts set forth in Schedule A-4-5.2. The amounts set forth in Schedule A-4.5 are inclusive of travel and living expenses incurred by Supplier Personnel in providing *** Transformation Services and U2L Services.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 656 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
***
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-13.1
*** SYSTEM APPLICATION SOURCE CHARACTERISTICS AND COMPONENTS
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
***
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 657 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-13.1
*** System Application Source Characteristics and Components
| |
| 1.1. | Agreement. This Schedule A-13.1 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2. | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3. | Definitions. Terms used in this Schedule with initial capitalized letters but not defined in this Schedule shall have the respective meanings set forth in Schedule A-1 to Supplement A, Schedule 1 to the MSA or the other Schedules to the MSA or Supplement A. |
| |
| 2. | *** SYSTEM APPLICATION CHARACTERISTICS |
The following tables list the Application characteristics, counts and Application source components for the asset cataloging and source assessment and Application re-host migration design and implementation that were used as a guideline for estimating the level of effort required for the Transformation Services. If the Application characteristics, counts and Application source components are significantly different, the Parties shall work together in good faith to address the difference through governance; provided, unless the Parties agree otherwise (which agreement either Party may withhold in its sole discretion), in no event shall this sentence be used to change the *** set forth for completion of the Transformation Services. However, if the *** *** more than *** modules or *** lines of code, *** shall either perform the *** or execute an appropriate *** for the *** and ***.
| |
| 2.1. | *** Transformation Services. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 658 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| |
| *** System Application Characteristics | Quantity |
| *** | *** |
| *** | *** |
| CICS COBOL SQL Prgms Migration (to UniKix TPE/vCOBOL/***) | 1990 COBOL Programs |
| CICS / Batch Assembler LOC (552 modules, 255000 LOC) | 255000 Assembler Lines of Code |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
| *** | *** |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 659 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 2.2. | *** System Application Source Components. |
|
| | | | |
| | Application Name | Platform / Programming Language | Sub Category | Size |
| | *** | *** | Interface | Medium |
| | *** | *** | Interface | Medium |
| |
| | *** | *** | Component | Medium |
| |
| | *** | *** | Component | Medium |
| |
| | *** | *** | Custom Tool | Medium |
| |
| | *** | *** | Custom Tool | Medium |
| |
| | *** | *** | Component | Medium |
| |
| |
| | *** | *** | Interface | Medium |
| | *** | *** | Component | Medium |
| |
| |
| | *** | *** | Custom Tool | Medium |
| | *** | *** | Component | Medium |
| | *** | *** | Component | Medium |
| | *** | *** | Custom Tool | Medium |
| | *** | *** | Custom Tool | Medium |
| |
| | *** | *** | Component | Medium |
| |
| | *** | *** | TBD | Medium |
| | *** | *** | Component | Medium |
| |
| | *** | *** | Interface | Medium |
| |
| |
| | *** | *** | Interface | Medium |
| |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 660 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| | Application Name | Platform / Programming Language | Sub Category | Size |
| | *** | *** | Interface | Medium |
| |
| |
| | *** | *** | Application | Medium |
| |
| | *** | *** | Application | Medium |
| |
| | *** | *** | Application | Medium |
| |
| | *** | *** | Application | Large |
| |
| | *** | *** | Interface | Medium |
| |
| | *** | *** | Application | Large |
| |
| | *** | *** | Application | Large |
| |
| | *** | *** | TBD | Medium |
| | *** | *** | Application | Large |
| |
| | *** | *** | Component | Medium |
| |
| |
| | *** | *** | Application | Large |
| |
| |
| | *** | *** | Application | Large |
| |
| | *** | *** | Application | Large |
| |
| | *** | *** | Application | Large |
| |
| | *** | *** | Application | Large |
| |
| | *** | *** | TBD | Medium |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 661 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| | Application Name | Platform / Programming Language | Sub Category | Size |
| | *** | *** | Component | Medium |
| |
| | *** | *** | Component | Medium |
| |
| | *** | *** | Component | Medium |
| | *** | *** | Application | Large |
| |
| | *** | *** | Application | Large |
| |
| | *** | *** | Application | Medium |
| |
| | *** | *** | Component | Medium |
| | *** | *** | Component | Medium |
| |
| |
| | *** | *** | Component | Medium |
| |
| | *** | *** | Component | Medium |
| |
| | *** | *** | Component | Medium |
| |
| | *** | *** | Third Party Application | Medium |
| |
| | *** | *** | Application | Large |
| |
| |
| | *** | *** | Component | Medium |
| |
| | *** | *** | TBD | Medium |
| |
| | *** | *** | Application | Large |
| |
| |
| | *** | *** | Application | Large |
| |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 662 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | |
| | Application Name | Platform / Programming Language | Sub Category | Size |
| | *** | *** | Application | Large |
| |
| | *** | *** | Application | Large |
| |
| | *** | *** | Application | Large |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 663 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-13.2
ACCEPTANCE PROCESS AND CRITERIA FOR DCTMV, *** TRANSFORMATION AND ***
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
***
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 664 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-13.2
Acceptance Process and Criteria for DCTMV, *** Transformation and ***
| |
| 1.1 | Agreement. This Schedule A-13.2 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. The following capitalized terms shall have the meanings set forth in this Section. Other capitalized terms used in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or Schedule A-1 to Supplement A. |
“Application Architecture” means the applicable application architecture developed by Supplier and approved by CoreLogic for purposes of the Transformation Services.
“Fatal Defect” means a Defect in which the Migrated Application Component *** or *** when executing a UAT Test Script, and *** or *** is available in the Migrated Application Component to ***. The Defect would affect multiple users performing critical functionality.
“Major Defect” means a Defect in which the Migrated Application Component *** but does *** for a UAT Test Script in accordance with the Test Plan, a work around or alternative approach *** in the Migrated Application Component to obtain the correct result but the workaround or alternative approach ***. Some processing cannot be done in some areas but overall processing continues.
“Minor Defect” means a Defect in which the Migrated Application Component *** but does not produce the correct result that is required for a UAT Test Script in accordance with the Test Plan, and a reasonable work around or alternative approach *** in the Migrated Application Component to obtain the correct result. The Defect results in a *** or *** but processing ***.
“Test Plan” means the document developed by Supplier and approved by CoreLogic which defines the objectives, process and expected outcomes of the testing process generally, including the user acceptance testing (“UAT”) process.
“UAT Test Data Set” shall mean the data to be used to support the UAT Test Script conditions during the UAT process of the in-scope Application components migrated pursuant to each of the Milestones identified below in this Schedule (i.e., the *** Application migrated as pursuant to the *** Transformation Services and the Service Tier, Flood, Oracle Databases and Oracle EBS Financials Applications migrated as pursuant to the *** Transformation Services) (each, a “Migrated Application Component”). Such data shall be defined in a mutually agreed upon format such as unicode test files, Excel documents, Microsoft Word documents or database tables. The UAT Test Data Set will be used to define: (1) the data input criteria for a given UAT Test Script or set of UAT Test Scripts, (2) the database data content required to execute a UAT Test Script or set of UAT Test Scripts, and (3) the configuration settings of the Migrated Application Component for a given UAT Test Script or set of UAT Test Scripts.
“UAT Test Scripts” shall mean the detailed tests that are a component of the Test Plan to be performed by CoreLogic during the UAT process to confirm compliance with the Acceptance Criteria. The UAT Test Scripts define the entrance and exit criteria that must be met for each
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 665 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
specific test. An agreed upon template will be developed by the Parties to define the criteria that must be met for each test.
| |
| 2. | *** SYSTEM TRANSFORMATION MILESTONES AND ACCEPTANCE CRITERIA |
|
| | | | | |
| Transformation Milestone Description | Transformation Milestone Completion Date | Acceptance Criteria |
| Milestone 1-Transformation Planning | *** | Supplier completes and delivers the following items in compliance with the requirements of this Schedule: (1) detailed Transformation Plan, (2) “to be” Application architecture, (3) revised “to be” transformed Application component type counts discovered during planning and (4) proposed Application component transformation. |
| Milestone 2-Transformation Testing | *** | Supplier completes and delivers Test Plan and completes its regression testing responsibilities in compliance with the requirements of Schedule A-13. |
| Milestone 3-Production cutover preparation and readiness | *** | Supplier completes and delivers Cutover Plans in compliance with the requirements of Schedule A-13. Supplier delivers final production source code to CoreLogic via CoreLogic’s source code management system, with corresponding required scripts, build files and utilities in accordance with CoreLogic standards such that CoreLogic can create the production system for deployment. Target environment equals or exceed the pre-migration performance (baseline) for Application, CPU utilization, disk I/O, and memory. |
| Milestone 4-Tax System Transformation completion | *** | Number of UAT Defects demonstrated within the UAT Test Scripts pursuant to the UAT process described in Section 4 is not more than the following for the Migrated Application Component: |
| | *** Application | |
| | Fatal | *** | |
| | Major | *** | |
| | Minor | *** | |
| Categorization of Defect will be done in consultation with Supplier PMO team and CoreLogic with mutual agreement based on technical and business impact. Acceptance criteria will be applied for an application or set of applications going through the UAT at that stage. |
| |
| 3. | *** TRANSFORMATION MILESTONES AND ACCEPTANCE CRITERIA |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 666 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
|
| | | | | |
| Transformation Milestone Description | Transformation Milestone Completion Date | Acceptance Criteria |
Milestone 1- Transformation Planning and Assessment
| *** | Supplier completes and delivers the following items in compliance with the requirements of Schedule A-13: (1) detailed Transformation Plan, and (2) “to be” Application architecture. |
| Milestone 2-Transformation Testing | *** | Supplier completes and delivers Test Plan and completes its regression testing responsibilities in compliance with the requirements of Schedule A-13. |
| Milestone 3-Production cutover preparation and readiness | *** | Supplier completes and delivers Cutover Plans for groups of databases and applications in compliance with the requirements of Schedule A-13. Supplier delivers final production source code to CoreLogic via CoreLogic’s source code management system, with corresponding required scripts, build files and utilities in accordance with CoreLogic standards such that CoreLogic can create the production system for deployment.
Target environment equals or exceeds the pre-migration performance (baseline) for Application, CPU utilization, disk I/O, and memory. |
| Milestone 4-Unix to Linux Transformation completion | *** | Number of UAT Defects demonstrated within the UAT Test Scripts pursuant to the UAT process described in Section 4 is not more than the number set forth below for the applicable Migrated Application Components: |
| | Service Tier | |
| | Fatal | *** | |
| | Major | *** | |
| | Minor | *** | |
| | Flood | |
| | Fatal | *** | |
| | Major | *** | |
| | Minor | *** | |
| | Oracle Database | |
| | Fatal | *** | |
| | Major | *** | |
| | Minor | *** | |
| | Oracle EBS Financials | |
| | Fatal | *** | |
| | Major | *** | |
| | Minor | *** | |
| Categorization of Defect will be done in consultation with Supplier PMO team and CoreLogic with mutual agreement based on technical and business impact. Acceptance criteria will be applied for an application or set of applications going through the UAT at that stage. |
| |
| 4. | ACCEPTANCE TESTING PROCESS FOR *** SYSTEM AND *** TRANSFORMATION |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 667 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
| |
| 4.1 | Test Plans. With respect to each Migrated Application Component, CoreLogic will develop appropriate Test Scripts based upon the Test Plan that will include any associated UAT Test Data Sets required to complete UAT. The Test Scripts shall be designed to determine whether the Migrated Application Component maintains the required business functionality that it possessed before the applicable migration activity. The reference for acceptance during UAT will be the business functionality as documented in the Test Plan and the test results approved by CoreLogic from the baseline testing phase. |
| |
| 4.2 | Execution of Test Plan. Supplier shall give written notice to the CoreLogic Relationship Manager advising CoreLogic when the Migrated Application Components have been migrated, completed regression testing by Supplier and are ready for testing by CoreLogic. Within the timeframe set forth in the Transformation Plan, CoreLogic shall conduct a regression test cycle. Upon competition of successful regression test cycle that meets the criteria above, CoreLogic shall conduct UAT in order to test/verify that the Migrated Application Components function and perform in accordance with the Test Plan in all material respects. If the Migrated Application Components do not execute the UAT Test Scripts in accordance with the Test Plan (each such failure, a “Defect”), CoreLogic shall promptly submit a problem report in the agreed upon format and tool to Supplier that (a) includes reasonably detailed documentation and a description of the Defect (together with underlying data when possible), and (b) specifies how the Migrated Application Components fail to execute the UAT Test Scripts. CoreLogic will also identify, to the best of its knowledge, where the Migrated Application Components are failing. Defects exclude any *** and applicable to the Migrated Application Components. |
5. WARRANTY SUPPORT FOR *** SYSTEM AND *** TRANSFORMATION.
The warranty for Developed Materials set forth in Section 15.2(c) of the MSA shall apply to *** System and *** Transformation, except that the Warranty Period shall be for a period of *** following the applicable Developed Material’s use in a production basis on the applicable CoreLogic System(s). Supplier shall repair, replace or correct any nonconforming Developed Materials hereunder within *** following notice of such nonconformity by CoreLogic pursuant to Section 4.2 with respect to Defects or Section 15.2(c) of the MSA.
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 668 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
MASTER SERVICES AGREEMENT
between
CORELOGIC SOLUTIONS, LLC
and
DELL MARKETING L.P.
July 19, 2012
SUPPLEMENT A
SCHEDULE A-13.3
NATURAL TO COBOL CONVERSION
|
|
| This document contains proprietary and confidential information of CoreLogic and Dell. The information contained in this document may not be disclosed outside your company without the prior written permission of CoreLogic and Dell. |
***
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 669 |
CONFIDENTIAL MATERIAL APPEARING IN THIS DOCUMENT HAS BEEN OMITTED AND FILED SEPARATELY WITH THE SECURITIES AND EXCHANGE COMMISSION IN ACCORDANCE WITH THE SECURITIES ACT OF 1933, AS AMENDED, AND RULE 24B-2 PROMULGATED THEREUNDER. OMITTED INFORMATION HAS BEEN REPLACED WITH ASTERISKS
Schedule A-13.3
Natural to COBOL Conversion
| |
| 1.1 | Agreement. This Schedule A-13.3 (this “Schedule”) is attached to and incorporated by reference in Supplement A to that certain Master Services Agreement by and between CoreLogic and Supplier dated July 19, 2012 (the “MSA”). |
| |
| 1.2 | References. All references in this Schedule to articles, sections and exhibits shall be to this Schedule, unless another reference is provided. |
| |
| 1.3 | Definitions. The following capitalized terms shall have the meanings set forth in this Section. Other capitalized terms used in this Schedule shall have the respective meanings set forth in Schedule 1 to the MSA or Schedule A-1 to Supplement A. |
| |
| 2. | NATURAL TO COBOL CONVERSION. |
| |
| 2.1 | Option for Natural to COBOL Conversion. Within the *** days after the Supplement Effective Date, CoreLogic may, at its option, elect to have Supplier perform a conversion of Natural components within the *** System to COBOL (the “Natural to COBOL Services”). Upon CoreLogic’s election of such option, the Parties shall work in good faith to make changes to this Schedule A-13.3 to indentify Transformation Milestones and Deliverable Credits associated with the Natural to COBOL Services, and the specific tasks that Supplier will complete as part of the Natural to COBOL Services, which changes shall be consistent with the terms of Schedule A-13. |
| |
| 2.2 | Natural to COBOL Services Overview. If CoreLogic exercises its option under Section 2.1, for the *** System Mainframe scope of Transformation Services, Supplier will no longer retain CICS Natural online source components to be executed in the Ateras ATP Application execution environment. Supplier will instead Transform CICS Natural online source components (programs, subprograms, subroutines, help routines, maps, local data areas, parameter data areas, global data areas) to COBOL to be executed in the Supplier *** Transaction Processing Environment (***) Application execution environment. The resulting code base will have no dependency on Ateras Software or services. |
| |
| 2.3 | Charges for Natural to COBOL Services. The Charges for the Natural to COBOL Services are set forth as *** in Schedule A-4.5.2. |
|
| | |
| CORELOGIC AND DELL CONFIDENTIAL | Supplement A | Page 670 |