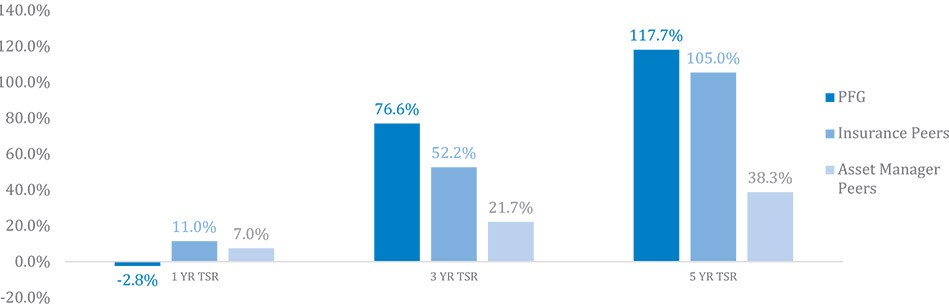
Our ability to increase and retain customer funds is directly related to the performance of our investments as measured against market averages and the performance of our competitors. If we and our affiliates are unable to attract and retain qualified portfolio managers, we may face reduced sales and increased cash outflows in our asset accumulation business.
Interruptions in information technology, infrastructure or other internal or external systems used for our business operations, or a failure to maintain the confidentiality, integrity or availability of data residing on such systems, could disrupt our business, damage our reputation and adversely impact our profitability.
We rely on external infrastructure, proprietary information technology and third party systems and services to conduct business, including customer service, marketing and sales activities, customer relationship management, producing financial statements and technology/data centers. In addition, we store and process confidential and proprietary business information on both company-owned and third party and/or vendor managed systems, including cloud service providers. We increasingly rely on the internet in order to conduct business and may be adversely impacted by outages in critical infrastructure such as electric grids, undersea cables, satellites or other communications used by us or our third parties.
Financial services companies are regularly targeted by cyber criminals, and face various cybersecurity risks, resulting in unauthorized access, theft of funds, extortion, disruption or degradation of service or other damage. These attacks may take a variety of forms, including web application attacks, denial of service attacks, ransomware, malware, and social engineering, including phishing. We may also be adversely impacted by successful cyberattacks of partners, vendors and others in our supply chain with whom we conduct business or share information. Information security incidents may also occur due to the failure to control access to, and use of, sensitive systems or information by our workforce. The tactics and techniques used by cyber criminals to obtain unauthorized access, or otherwise impact our business negatively change frequently, and we, and our supply chain partners, may be unable to anticipate their schemes to implement preventative measures. The failure of our controls (such as policies, procedures, monitoring, software testing, incident response and backup plans) designed to prevent, or limit the effect of, failure, inadvertent use or abuse could result in disruptions, reputational damage, legal liability, regulatory actions, remediation costs and competitive disadvantage.
Loss of key vendor relationships or failure of a vendor to protect information of our customers or employees could adversely affect our business or result in losses.
We rely on services and products provided by many vendors in the United States and abroad. These include, for example, vendors of computer hardware and software and vendors of services. In the event that one or more of our vendors suffers a bankruptcy or otherwise becomes unable to continue to provide products or services or fails to protect personal information of our customers or employees of Principal Workforce, we may suffer operational impairments, reputational damage and financial losses.
Our enterprise risk management framework may not be fully effective in identifying or mitigating all the risks to which we are exposed.
We utilize an integrated risk management framework, which is designed to manage material risks within established risk appetites and risk tolerances. Nonetheless, our policies and procedures may not be fully effective in identifying or mitigating every risk to which we are exposed. Many of our methods for managing and mitigating risk rely on models and assumptions that are based, in part, on observed historical data. As a result, these methods, models or assumptions may not accurately predict future exposures,
which may be significantly greater than our historical measures indicate. We may be exposed to unanticipated risks as a result of changes in market conditions, new products or new business strategies, catastrophes or other unforeseen circumstances. If our risk management framework proves ineffective, we may suffer unexpected losses, which may adversely affect our results of operations and financial condition.
Cybersecurity
Risk management is an essential component of our culture and business model. Guarding against the specific risks posed by cybersecurity threats has been and will continue to be very dynamic in nature, requiring that we remain agile and aware of internal and external changes. We recognize that cybersecurity threats can be among the most critical risks facing large companies. As a result,