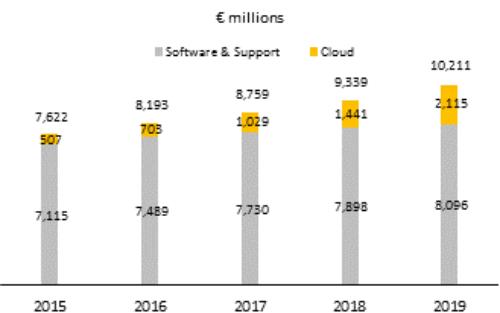
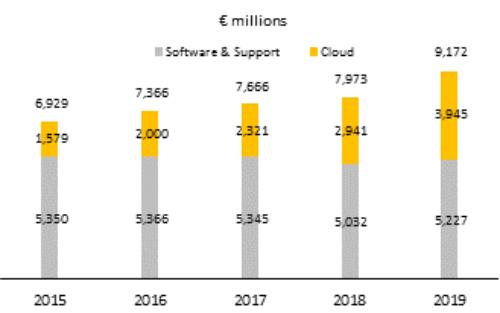
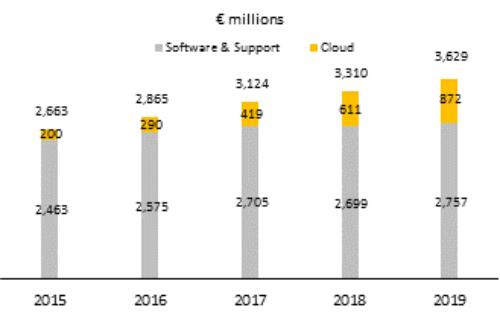
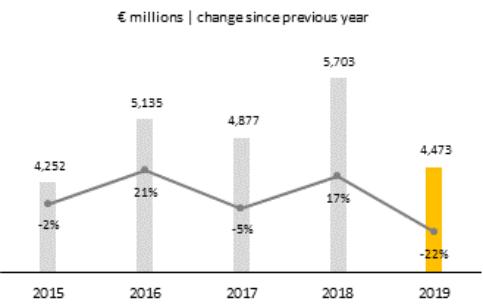
Cybersecurity and Security: A cybersecurity attack or breach, or cybersecurity vulnerabilities in our products, infrastructure, or services, or economic espionage could result in significant legal and financial exposure and have a material adverse effect on our customers, partners, financial performance, profit, cash flows, operations, brand, reputation, competitive position, the perception of our products and services by current and prospective customers, and our business in general.
As we continue to grow organically and through acquisitions, deliver a full portfolio of solutions via the cloud, host or manage elements of our customers’ businesses in the cloud, process large amounts of data and offer more mobile solutions to users, in each case either directly or through partners and other third parties, we face a progressively more complex and threatening cybersecurity environment. The severity of the challenges posed by this cybersecurity environment is amplified due to the increasingly sophisticated and malicious global cybersecurity threat landscape in which we operate, including third-party data, products, and services that we incorporate into SAP products and services, and the continually evolving and increasingly advanced techniques employed by threat actors targeting IT products and businesses in general. Such threat actors include, but are not limited to, highly sophisticated parties such as nation-states and organized criminal syndicates. As a leading cloud company and service provider to some of the largest and best-known customers in the world, we are naturally a prominent target for cybersecurity attacks. We have observed increased threat activity to our products and systems, and we experience cybersecurity attacks of varying types and degrees on a regular basis. When we become aware of unauthorized access to our systems, we take steps intended to identify and remediate the source and impact of the incursions, and steps to comply with related necessary notification and disclosure obligations. To date, none of the incursions we have identified has had a material adverse effect on our business. However, we do not have visibility into all unauthorized incursions, and our systems may be experiencing ongoing incursions of which we are not aware. In addition, while we are continually taking steps to enhance our cybersecurity defenses, increased investments, coordination, and resources are required to achieve our objective of ensuring over time that our cybersecurity infrastructure meets or exceeds evolving industry standards. Achieving this objective will require continued effort and vigilance, including sustained investment of money and management resources in order to support the ongoing development and maintenance of systems that meet these standards. As a result, we are subject to risks and associated consequences in the following areas, among others:
- Identified or undetected cybersecurity defects and vulnerabilities
- Increased complexity and risk of exploitation due to utilization of open-source software components
- Exposure of our business operations and service delivery due to a number of threats, including virtual attack, disruption, damage, and/or unauthorized access, theft, destruction, industrial and/or economic espionage, serious or organized crime, and other illegal activities, as well as violent extremism and terrorism
- Abuse of data, social engineering, misuse, or trespassers in our facilities, or systems being rendered unusable
- State-driven economic espionage or competitor-driven industrial espionage, and criminal activities including, but not limited to, cyberattacks and breaches against cloud services and hosted on-premise software, whether managed by us or our customers, partners, or other third parties
- Disruptions to back-up, disaster recovery, or business continuity management processes
- Disruptions due to exposure of our network systems to cybersecurity attacks via defects and vulnerabilities in the IT systems of our customers, or in the systems of third parties that facilitate our business activities such as cloud service providers, including those that are beyond SAP’s cybersecurity infrastructure and protocols
- Failure to securely and successfully deliver cloud services by any cloud service provider could have a negative impact on customer trust in cloud solutions
- Cybersecurity threats for SAP and customers due to delayed or insufficient responses to identified cybersecurity issues attributable to complexity, interdependencies or other factors
- Challenges in effectively synchronizing cybersecurity processes across our various lines of business in a heterogeneous environment
- Insufficient or ineffective asset management potentially endangering secure operations
- Customer systems or systems operated by SAP being compromised by vulnerabilities due to threat actor exploitation
- Operational disruptions due to an increasing number of destructive malware, ransomware, or other cybersecurity attacks
- Breach of cybersecurity measures due to, for example but not limited to, employee error or wrongdoing, system vulnerabilities, malfunctions, or attempts of third parties to fraudulently induce employees, users, partners, or customers to gain access to our systems, data, or customers’ data
- Failure to maintain a sufficient complement of personnel with sufficient levels of knowledge, experience, and training in cybersecurity matters necessary to support SAP’s evolving cybersecurity needs and commensurate with the increasingly complex and sophisticated threat landscape
- Increased challenges due to an expanding and morphing cyber-attack surface attributable to interconnected technologies such as Internet of Things (IoT) accompanied by an elevation of entry and endpoints
- Expansion of cybersecurity attack surface due to increased connectivity of operational data
- Material recovery costs as well as significant contractual and legal claims by customers, partners, authorities (including state, federal, and non-U.S.), and third-party service providers which could expose us to significant expense and liability and/or result in the issuance of orders, judgments, or consent decrees that could require us to modify our business practices
- Material costs to attempt to detect, prevent, and mitigate any successful attacks, including but not limited to the costs of third-party legal and cybersecurity experts and consultants, insurance costs, additional personnel and technologies, organizational changes, and incentives to customers and partners to compensate for any losses and/or retain their business
- Increasing sophistication, proliferation, and escalation in frequency, severity, and impact of cybersecurity attacks
- Inability to discover a cybersecurity breach or a loss of information either fully, in a timely manner, for a significant amount of time after the breach, or at all
- Inability to anticipate attacks or implement sufficient mitigating measures
- Insufficient investment, coordination, or resources to achieve our objective of ensuring over time that our cybersecurity infrastructure meets or exceeds evolving industry standards, and defending against the ever-evolving and emerging threat landscape
- Material costs and time associated with enhancing our cybersecurity infrastructure, which may impact the ongoing pace of development and delivery of our products and services, and our financial performance
- Failure to integrate SAP’s cybersecurity infrastructure and protocols with other network systems obtained through acquisition, including addressing cybersecurity defects and vulnerabilities in acquired systems
- Failure to maintain SAP’s cybersecurity infrastructure and protocols in connection with the divestiture of businesses and network systems from SAP
- Inaccurate or incomplete third-party or SAP audit results, certifications, or representations concerning the adequacy of our cybersecurity infrastructure and protocols
- Customer concerns and loss of confidence in the current or future security and reliability of our products and services, including cloud solutions, and the resulting termination of key contracts by customers and partners